Managing and Controlling External Information Sharing Using SharePoint 2013 Online and Windows Azure Rights Management (IRM) Functionality
|
|
|
- Elmer Thornton
- 8 years ago
- Views:
Transcription
1 Managing and Controlling External Information Sharing Using SharePoint 2013 Online and Windows Azure Rights Management (IRM) Functionality The ability to share information easily and readily, either within an organization or outside of it, is one of SharePoint 2013 s signature feature enhancements. SharePoint provides new features and functions for sharing information as well as managing and controlling the sharing of information. In addition Microsoft Information Rights Management (IRM) capabilities are fully integrated within SharePoint 2013 and for online deployments, IRM is now offered as a cloud service Windows Azure Rights Management. Furthermore, Windows Azure Rights Management includes Office 365 Message Encryption. This document attempts to describe all of the Microsoft service assets that can be deployed and implemented separately or together, to support managed information sharing with external parties. As such this document is organized into four sections corresponding to these service assets: the first section describes SharePoint 2013 capabilities and scenarios for sharing information with external parties (both online and on-premises). The second section describes the OneDrive Pro functionality introduced in SharePoint 2013 and its offline synchronization capabilities. The third section describes the Windows Azure Rights Management functionality that adds another layer of control over the distribution and access to sensitive information within an organization to prevent both the intentional and/or unintentional dissemination of restricted information. The fourth section describes the new Office 365 Message Encryption capabilities for sending encrypted s, that is an extension of the Windows Azure Rights Management platform. Section 1 SharePoint 2013 Enhanced Capabilities for Sharing Information Providing access to a SharePoint Site to parties outside of an organization Providing access to a SharePoint Site to parties outside of an organization is one of SharePoint 2013 s new features. When you share a site with external users, you send them an invitation they can use to log in to your site. You can send this invitation to any address. When the recipient accepts the invitation, they can log in using either a Microsoft account or an Office 365 user ID. When you share a site, you can select the type of permissions you want that person to have on the site. You need to be a Site Owner or have full control permissions to share a site with external users. Additionally, the external sharing feature must be turned on for your Office 365 subscription (depending on which plan you have, your Office 365 admin or your SharePoint Online admin can do this). 1. Go to the site you want to share with external users. 2. Click Share. 3. In the Share dialog box, type the names of the external users you want to invite. For example: someone@outlook.com or someone@contoso.com. 1
2 You can also use the Share command to grant internal licensed users access to a site. If you want to do this, just type the names of the people you want to invite. Type a message to include with the invitation. 4. To assign the external user to a specific permissions group, click Show Options, and then select the group you want. It s a good idea to give people the least amount of permissions they might require to perform the desired task. For example, if the people you re inviting only need to read content, assign them to the Visitors group, which has Read permissions by default. If the external users need to be able to edit or update content, add them to the Members group, which has Edit permissions by default. Be extremely careful about adding external users to any group that has Full Control permissions. By default, any invitations you send to external users will expire in 7 days. If an invitee does not accept the invitation within 7 days, and you still want that person to have access to your site, you ll need to send a new invitation. When the external users receive their invitations, they click a button that takes them to a page where they sign into your SharePoint Online site by using a Microsoft account or an Office 365 user ID. If users don t have at least a Microsoft account, they can sign up for a free Microsoft account. Best practices for sharing sites If you ve shared an entire site with a user, then that user will be able to log in to the site and function like a full member of the site. They will be able to browse, search for, view, and edit content (depending on which permission group you assign them to). They will be able to do things like see the names of other site users in the People Picker or view document metadata. External users will also appear in the People Picker as site users. This means that other people who use your site could grant different permissions to these users than you initially granted when you shared the site with them. Be sure you know the identity of external users before you invite them to your site. 2
3 If you invite external users to your Team site, they will be able to view content on the Team site and all sub sites. If you want to avoid having external users gain access to important or sensitive content on your Team site, you should create a subsite of your Team site that has unique permissions, and then share only that subsite with external users. To learn more about permissions inheritance, see What is permissions inheritance? Similarly, if you want to share a subsite that you ve created on your OneDrive Pro location, you might want to ensure that it has unique permissions so that you do not accidentally grant users permission to additional sites or content on your My Site. Sharing documents by sending or posting an anonymous guest link You can create an anonymous guest link, and then share the link using whatever media suits you. For example, post it on a social media page, or paste it into an . You can create a guest link that provides editing permission or only viewing permission. You must be a Site Owner or have full control permissions to share a document with external users. Additionally, the external sharing feature must be turned on in either the Office 365 Service Settings or the SharePoint Online admin center (depending on which plan you have). External sharing must also be turned on for your site collection (enterprise plans only). 1. Click the ellipses (...) next to the document to open its callout window and then click Share. 2. In the Share dialog box, select Get a link. 3. Select Create a link for the type of permission you want to grant. A guest link URL is created. 4. Select the guest link URL and copy it. 3
4 If a document is in a team site library, other site members can find the guest links in the Share dialog box and send them to others. If the file you are attempting to share is located in a library that is using Information Rights Management, you will not be able to share it externally. Anonymous guest links could potentially be forwarded or shared with other people, who might also be able to view or edit the content without signing in. Avoid using anonymous guest links for sensitive content. People who are invited to access documents using anonymous guest links will only be able to view or read files in the relevant Office Web App. They will not be able to open files in a corresponding desktop version of the Office program. If external sharing is turned off globally in the Office 365 Service Settings or the SharePoint Online Admin center, any shared links will stop working. If the feature is later reactivated, these links will resume working. It is also possible to disable individual links that have been shared if you want to revoke access to a specific document. Allow people to create guest links with documents you ve shared with them You may want to share some documents widely, and you might want to encourage people to re-share them. For such documents you can allow people to create anonymous guest links with documents you share with them. To allow this capability, you must have full control permission. The following are the instructions for creating these links: 1. Go to the library where you want to allow people to create guest links. 2. Select the gear icon, and the select Site settings. 3. On the Site Settings page, under Users and Permissions, select Site permissions. 4. On the Permissions tab, select Access Request Settings. 5. In the Access Requests Settings dialog box, check Allow members to share the site and individual files and folders. Now when people select documents you ve shared with them and open the Share dialog box, they can create a guest link. Note, however, that they can only create guest links that allow guests to edit the document if you gave them edit permission when you first shared the document. If they only have view permission, they can only create guest links that allow view permission. Share a document requiring sign in to your site You must be a Site Owner or have full control permissions to share a document with external users. Additionally, the external sharing feature must be turned on in either the Office 365 Service Settings or the SharePoint Online admin center (depending on which plan you have). External sharing must also be turned on for your site collection (enterprise plans only). 4
5 1. Click the ellipses (...) next to the document to open its callout window and then click Share. 2. Type the addresses of people you re inviting to share the document. For example: or or 3. In the drop-down list, select the permission level you d like to grant these users. 4. If you want, type a message to be included with the . The message might include information or instructions about the document you ve shared. 5. Select the Require sign-in check box. Best practices for sharing documents If you share documents using anonymous guest links, then it is possible for invitation recipients to share those guest links with others, who could use them to view content. Do not use guest links to share documents that are sensitive. If you want to minimize the risk that someone might share an anonymous link, share a document by requiring sign-in instead. Deciding how to share information with external parties When considering if and how you want to share content externally, think about the following: To whom do you want to grant access to content on your Team site and any sub sites, and what do you want them to be able to do? To whom in your organization do you want to grant permission to share content externally? Is there content you want to ensure is never available to be viewed by people external to your organization? See who has access to a specific site or document You can also use the Share command to quickly see the list of people a document has been shared with. To see who has access to a site, click Share at the top right of the page, and then click the link after Shared with in the Share dialog box to view a list of people who have access to the site. To see who has access to a document, folder, or Document Set, select the item in the document library, and then flick Shared With on the Files tab. Withdrawing invitations If you want to withdraw an invitation you have sent to an external user, you can revoke the invitation before it is accepted. Go to the site on which you want to withdraw an invitation. 5
6 1. Go to Site Settings. 2. Under Users and Permissions, click Access requests and invitations. 3. Under External User Invitations, find the person you would like to uninvited to the site and click Open Menu. 4. In the properties window, click Withdraw. If the external user has already accepted an invitation, and you want to remove them from your site, you can do so by removing them from the SharePoint permissions group to which you assigned them. The person in your organization who has permissions as the Office 365 admin or SharePoint Online admin may also remove them from the list of users for your environment. For more information, see the articles listed in the Manage external sharing section. Disable an anonymous guest link When a document has been shared through a guest link, you can see this information in the document callout. You can revoke access to a document that has been shared through a guest link by disabling the link. 1. Go to the library that contains the document for which you want to remove a guest link. 2. Point to the document, and click Open Menu. 3. Click a guest link in the sentence Open to anyone with a guest link. 4. Next to the URL for the guest link, click the Disable button. 6
7 5. When you are asked if you want the link disabled, click Disable Link. When people outside your organization attempt to access the content using the guest link, they will see a message telling them they cannot access it. Administrative management of external sharing While sharing sites and documents easily is a prominent aspect of SharePoint 2013 this functionality can be turned off entirely at the Site Collection level. In SharePoint online this is accomplished in the SharePoint administration on the site collections page by selecting a site and clicking the Sharing button as shown in the image below. The image below shows the three sharing settings that are available to set for an entire site collection. 7
8 If Sharing is enabled on a site collection Access Requests can be managed by going to the Site Settings Page for a Site Collection or Site and selecting Site Permissions and then Access Request Settings. The Access Requests Setting page will display as shown in the image below where a Site manager can set Sharing controls and have all access requests ed to a specific address. 8
9 From the Site Settings page a Site manager can access the Access requests and invitations page where all pending and historic information access invitations and requests can be managed as shown in the image below. At the library level a user manages document sharing by selecting Settings and the Shared with The Share dialogue screen will display as shown in the image below. 9
10 Selecting the Share option for an individual document in a library will open the dialogue screen for the sharing options to share a specific document as shown in the image below. Section 2 Review of OneDrive Pro Functionality in SharePoint 2013 OneDrive Pro is a business storage facility of the SharePoint 2013 online and on premise offerings. It is instantiated for each individual SharePoint user. OneDrive Pro is available with all Office 365 and SharePoint Server 2013 Server licenses. OneDrive Pro is a library associated with an individual SharePoint subscriber and it is used to store and share the documents they control, while providing corporate oversight of the process. The documents can be accessed from a variety of devices and places, and viewing and editing permissions can be specified by the document owner. It is however, a corporate managed resource, like any other SharePoint site artifact, and it behaves like any standard SharePoint library. SharePoint Server 2013 creates the OneDrive Pro document library in the personal site collection of a user's My Site when the user requests creation of the My Site. The OneDrive Pro document library is a special document library built by using the standard document library template. Many of the features and processes applicable to a standard document library can be applied to the OneDrive Pro document library. All of the Sharing management functionality described in Section 1 above applies to OneDrive Pro. With OneDrive Pro on Office 365, each user gets 25 GB of space that can be upgraded to 100 GB. This storage is not counted against the overall SharePoint storage quota (which is part of the plan you pay for). For SharePoint Server 2013 on premise installations, administrators can configure the OneDrive Pro space quota on an individual basis. While you can purchase add-on space to pool more available gigabytes for your overall SharePoint sites and workspaces on Office 365, you can't currently buy more storage to extend OneDrive Pro spaces. 10
11 OneDrive Pro imposes the following restrictions: In your OneDrive Pro library, you can synchronize up to 20,000 items, including folders and files. No single file can be greater than 250 MB in size. You can download files up to 2 GB from your library. To implement OneDrive Pro Office 365 (or SharePoint 2013 on-premise) personal sites (previously known as My Sites) must be deployed and the user profile service must be running. Social features, such as sharing documents, depend on personal sites and user profiles. To support Sync in OneDrive Pro (the ability to synchronize OneDrive Pro documents with local desktops), Office 2013 (Standard or Professional) or an Office 365 subscription that includes the Office 2013 is required. Architecture of OneDrive Pro The OneDrive Pro architecture includes several layers that span SharePoint Server 2013, Office 2013, and Windows Explorer. The following diagram shows the components that make up the OneDrive Pro architecture. OneDrive Pro Windows Sync client The OneDrive Pro Windows Sync client enables users to take documents offline from document libraries in SharePoint Server 2013, and use them when they are disconnected from SharePoint Server Later, when the client workstation reconnects to SharePoint Server 2013, the files are synchronized. The OneDrive Pro Windows Sync client synchronizes files with any document library in SharePoint Server 2013 including the OneDrive Pro document library. 11
12 The OneDrive Pro client exchanges information with SharePoint using externally provisioned secure mechanisms such as those provided by VPNs or Secure Socket Layer (SSL) technology. OneDrive Pro data is not encrypted over the network when the OneDrive Pro client talks to SharePoint (which is required to support OneDrive Pro), unless the transport protocol is being used for server communication is through https (which uses SSL or Transport Layer Security TLS). Server administrators can configure SSL encryption for data sent over the network between the OneDrive Pro and the SharePoint servers. On-disk data can be encrypted using the Windows BitLocker Drive Encryption. A user can choose to synchronize a document library with a client workstation. As shown in the illustration above. When a document library is synchronized with a client workstation, synchronized files are stored in specific Windows folders on the client workstation. As shown in the diagram: A is a user's personal OneDrive folder. When Office 2013 is installed, a OneDrive folder is created in the Favorites section of Windows Explorer. B is the SharePoint folder. Files in document libraries on team sites are synchronized with the SharePoint folder. C is the Contoso folder. Files in document libraries on team sites in a SharePoint Online tenancy are synchronized with the Contoso folder. D is the OneDrive Pro folder. Files in a user's OneDrive Pro document library are synchronized with the OneDrive Pro folder. E is a user's OneDrive Pro document library on the user's My Site. F is a document library on a team site. A user accesses the OneDrive Pro Windows Sync client from the notification area in Windows. From the OneDrive Pro Windows Sync client, a user can select Sync Now, Pause Syncing, Open your OneDrive Pro folder, and so on. The OneDrive Pro Windows Sync client establishes a synchronization relationship with the document library when the user clicks the Sync button in SharePoint Server When a synchronization relationship is set up, files and folders can be synchronized between the client workstation and the SharePoint Server. The OneDrive Pro Windows Sync client creates shortcuts displayed in Windows Explorer to Windows folders and labeled B, C, or D as shown in the diagram above to store files from the synchronized document library. The OneDrive Pro Windows Sync client automatically synchronizes with SharePoint Server 2013 every 10 minutes. When the OneDrive Pro Windows Sync client makes the request to synchronize with SharePoint Server 2013, SharePoint Server 2013 might respond by indicating that it is experiencing high server resource utilization and cannot synchronize now. When this occurs, the OneDrive Pro Windows Sync client cancels the current synchronization request, and resends a new synchronization request later. If the file type is a Word, Excel, or PowerPoint file, the OneDrive Pro Windows Sync client performs a differential synchronization, which is a synchronization of only the changes that were made to the document between the last synchronization and the current synchronization. For all other file types, the OneDrive Pro Windows Sync client synchronizes the whole file, not just the changes that were made to the file from the last synchronization. While mobile apps for accessing OneDrive Pro (and OneDrive) files are available for ios and Android phones and tablets, you can only sync files to a PC running Windows 7 or 8. 12
13 Section 3 Windows Azure Rights Management Windows Azure Rights Management provides the ability to safeguard sensitive information created using Office applications and services such as or other memos or correspondence that requires confidential treatment. Rights are assigned to content when it is published and the content is distributed in an encrypted form that provides persistent protection wherever the content travels. Rights that can be assigned include the ability to allow or deny viewing, Information Rights Management (IRM) enables you to limit the actions that users can take on files that have been downloaded from lists or libraries. IRM encrypts the downloaded files and limits the set of users and programs that are allowed to decrypt these files. IRM can also limit the rights of the users who are allowed to read files, so that they cannot take actions such as print copies of the files or copy text from them. You can use IRM on lists or libraries to limit the dissemination of sensitive content. For example, if you are creating a document library to share information about upcoming products with selected marketing representatives, you can use IRM to prevent these individuals from sharing this content with other employees in the company. On a site, you apply IRM to an entire list or library, rather than to individual files. This makes it easier to ensure a consistent level of protection for an entire set of documents or files. IRM can thus help your organization to enforce corporate policies that govern the use and dissemination of confidential or proprietary information. How IRM can help protect content IRM helps to protect restricted content in the following ways: Helps to prevent an authorized viewer from copying, modifying, printing, faxing, or copying and pasting the content for unauthorized use Helps to prevent an authorized viewer from copying the content by using the Print Screen feature in Microsoft Windows Helps to prevent an unauthorized viewer from viewing the content if it is sent in after it is downloaded from the server Restricts access to content to a specified period of time, after which users must confirm their credentials and download the content again Helps to enforce corporate policies that govern the use and dissemination of content within your organization How IRM CANNOT help protect content IRM cannot protect restricted content from the following: Erasure, theft, capture, or transmission by malicious programs such as Trojan horses, keystroke loggers, and certain types of spyware Loss or corruption because of the actions of computer viruses Manual copying or retyping of content from the display on a screen Digital or film photography of content that is displayed on a screen Copying through the use of third-party screen-capture programs Copying of content metadata (column values) through the use of third-party screen-capture programs or copy-and-paste action How IRM works for lists and libraries IRM protection is applied to files at the list or library level. When you enable IRM for a list or library, you can protect any file type in that list or library for which a protector is installed on all front-end Web servers. A protector is a program that controls the encryption and decryption of rights-managed files of a specific file format. 13
14 SharePoint includes protectors for the following file types: Microsoft Office InfoPath forms The file formats for the following Microsoft Office programs: Word, Excel, and PowerPoint The Office Open XML Formats for the following Microsoft Office programs: Word, Excel, and PowerPoint The XML Paper Specification (XPS) format If your organization plans to use IRM to protect any other file types in addition to those listed above, your server administrator must install protectors for these additional file formats. When people download files in an IRM-enabled list or library, the files are encrypted so that only authorized people can view them. Each rights-managed file also contains an issuance license that imposes restrictions on the people who view the file. Typical restrictions include making a file read-only, disabling the copying of text, preventing people from saving a local copy, and preventing people from printing the file. Client programs that can read IRM-supported file types use the issuance license within the rights-managed file to enforce these restrictions. This is how a rights-managed file retains its protection even after it is downloaded from the server. Within SharePoint, IRM protection is applied to files at the list and library level. Before your organization can use IRM protection, you must first set up Rights Management. SharePoint Online IRM relies on the Windows Azure Active Directory Rights Management (Windows Azure AD RM) service to encrypt and assign usage restrictions. Some Office 365 plans include a Windows Azure AD RM subscription, but not all. The following table describes the external sharing scenarios where you would use IRM to control the sharing of information and protect files. Safely share financial information with somebody I trust who is outside my organization You work with a partner company and want to them an Excel spreadsheet that contains projected sales figures. You want them to be able to view the figures but not change them. Safely send a document by to somebody who uses an ios device You want to a highly confidential Word document to a coworker, who you know, regularly checks on their ios device. Read an attachment I ve received in an message that has a securely shared file attachment but I can t read it because my company doesn t use Rights Management The sender is somebody who you trust because you ve done business with them in the past and you suspect that they might be sending you information about a potential new business opportunity. You use the Share Protected button on the ribbon in Excel, type the addresses of the two people that you work with in the partner company, select Viewer on the slider, and click Send. When the arrives at the partner company, only the recipients in the can view the spreadsheet and they cannot save, edit, print, or forward it. You use File Explorer to right-click the file, and select Share Protected. In the RMS sharing application, you select the Allow consumption on all devices option, and send the file as an attachment to your coworker.. The recipient receives the on their ios device, clicks the link in the that tells them how to download the sharing application, installs the version for ios devices, and then views the document. You follow the instructions in the and click the link to sign up for Microsoft Rights Management. Microsoft confirms that your organization does not have a subscription to Office 365, sends you an to complete the free signup process, and you sign in with your new account. You click the second link in the to install the Rights Management sharing app and can then open the attachment to read about the new business opportunity.. 14
15 How Permissions Assigned to a SharePoint Library Correspond to IRM Permissions The types of restrictions that are applied to a file when it is downloaded from a list or library are based on the individual user's permissions on the site that contains the file. The following table explains how the permissions on sites correspond to IRM permissions. PERMISSIONS Manage Permissions, Manage Web Site Edit Items, Manage Lists, Add and Customize Pages View Items Other IRM PERMISSIONS Full control (as defined by the client program): This permission generally allows a user to read, edit, copy, save, and modify permissions of rights-managed content. Edit, Copy, and Save: A user can print a file only if the Allow users to print documents check box is selected on the Information Rights Management Settings page for the list or library. Read: A user can read the document, but cannot copy or modify its content. A user can print only if the Allow users to print documents check box is selected on the Information Rights Management Settings page for the list or library. No other permissions correspond directly to IRM permissions. Before your organization can IRM-protect SharePoint lists and libraries, you must first activate the Rights Management service for your organization. To configure IRM, it requires you turn it on in two places: in the Office 365 Portal and in SharePoint Online tenant administration. From the Office 365 Portal you select Service Settings > Rights Management. Rights Management is disabled by default, so you need to activate it. On this screen click Manage and you will be taken to the Windows Azure Directory Rights Management site. From there, you can start the activation process. 15
16 Click the Activate button and you ll be taken to a screen to confirm. Click the Activate button again and the process gets started. Now, go to SharePoint tenant administration to activate it there. Click on Admin > SharePoint and then Settings. In the middle of the page, look for the Information Rights Management (IRM) section and check Use the IRM service specified in your configuration. When site owners enable IRM for a list or library, they can protect any supported file types in that list or library. When IRM is enabled for a library, rights management applies to all of the files in that library. When people download files in an IRM-enabled list or library, the files are encrypted so that only authorized people can view them. Each rights-managed file also contains an issuance license that imposes restrictions on the people who view the file. Typical restrictions include making a file read-only, disabling the copying of text, preventing people from saving a local copy, and preventing people from printing the file. Client programs that can read IRM-supported file types use the issuance license within the rights-managed file to enforce these restrictions. This is how a rights-managed file retains its protection even after it is downloaded. To enable IRM on a list or library, see Apply Information Rights Management to a list or library To apply IRM to a list or library, you must have at least the Design permission level for that list or library. 1. Go to the list or library for which you want to configure IRM. 16
17 2. On the ribbon, click the Library tab, and then click Library Settings (If you are working in a list, click the List tab, and then click List Settings). 3. Under Permissions and Management, click Information Rights Management. If the Information Rights Management link does not appear, IRM might not be enabled for your site. Contact your server administrator to see if it is possible to enable IRM for your site. The Information Rights Management link does not appear for picture libraries. 4. On the Information Rights Management Settings page, select the Restrict permission to documents in this library on download check box to apply restricted permission to documents that are downloaded from this list or library. 5. In the Create a permission policy title box, type a descriptive name for the policy that you can use later to differentiate this policy from other policies. For example, you can type Company Confidential if you are applying restricted permission to a list or library that will contain company documents that are confidential. 6. In the Add a permission policy description box, type a description that will appear to people who use this list or library that explains how they should handle the documents in this list or library. For example, you can type Discuss the contents of this document only with other employees if you want to restrict access to the information in these documents to internal employees. To apply additional restrictions to the documents in a list or library, click Show Options, and do any of the following: TO DO THIS: Allow people to print documents from this list or library Allow people with at least the View Items permission to run embedded code or macros on a document. Require that people verify their credentials at specific intervals. Select this option if you want to restrict access to content to a specified period of time. If you select this option, people's issuance licenses to access the content will expire after the specified number of days, and people will be required to return to the server to verify their credentials and download a new copy. Prevent people from uploading documents that do not support IRM to this list or library. If you select this option, people will not be able to upload any of the following file types: File types that do not have corresponding IRM protectors installed on all of the front-end Web servers. File types that SharePoint Server 2010 cannot decrypt. File types that are IRM protected in another program Remove restricted permissions from this list or library on a specific date. Control the interval that credentials are cached for the program that is licensed to open the document. Allow group protection so that users can share with members of the same group. DO THIS: Select the Allow users to print documents check box. Select the Allow users to access content programmatically check box. NOTE If you select this option, users could run code to extract the contents of a document. Select the Users must verify their credentials every check box, and then specify the number of days for which you want the document to be viewable. Select the Do not allow users to upload documents that do not support IRM check box. Select the Stop restricting permissions to documents in this library on check box, and then select the date that you want. In the Set group protection and credentials interval, enter the interval for caching credentials in number of days. Select Allow group protection, and enter the group s name for sharing. 17
18 End-user experience of working with IRM To use IRM in SharePoint a user opens a document from within a library, and clicks File and then Protect Document and then Restrict Access. The first time this is done, there is an option to connect to rights management services. Once it connects, the user will see options for protecting the document. In the illustration above Restricted Access is selected and the user is brought to a second screen as shown below where they are prompted to assign who can view the document or edit the document. 18
19 In this example, the user is granting read permission to Sara Davis. This means she will be able to open the document and view it, but cannot save or print it. Clicking on More Options, the user can set even more granular permissions such as expiring the document, allowing printing, as well as an address that gets used to request additional permissions. Once finished, the user saves the document back to SharePoint. When Sara opens the document, she will be presented with information that access is restricted and she clicks View Permission, it will show what she is allowed to do. 19
20 If a user without IRM permissions attempts to open the document, Office will present the following message and prevent them from opening the document. Furthermore, when a document is protected with IRM, Office Web Apps will be unable to show a preview of the document s contents. The following image shows the message that is presented to an unauthorized viewer. Section 4 - Office 365 Message Encryption for sending encrypted s to anyone! Office 365 Message Encryption is a new service that lets you send encrypted s to people outside your company. No matter what the destination-outlook.com, Yahoo, Gmail, Exchange Server, Lotus Notes, GroupWise, Squirrel Mail, you can send sensitive business communications with an additional level of protection against unauthorized access. There are many business situations where this type of encryption is essential such as the following scenarios. A bank sending credit card statements to customers over . An insurance company providing details about the policy to clients. A mortgage broker requesting financial information from a customer for a loan application. A healthcare provider using encrypted messages to send healthcare information to patients. An attorney sending confidential information to a client or another attorney. A consultant sending a contract to a client. A therapist providing a patient diagnosis to an insurance company. 20
21 Office 365 Message Encryption is the new version of Exchange Hosted Encryption (EHE). This version includes all of the capabilities of EHE plus new features, such as the ability to apply your company s branding to encrypted messages. Like EHE, Office 365 Message Encryption works with Office 365 mailboxes as well as with on-premises mailboxes that use Exchange Online Protection. Office 365 Message Encryption is an online service that s built on Windows Azure Rights Management. With Windows Azure Rights Management set up for an organization, administrators can enable message encryption by defining transport rules that determine the conditions for encryption. A rule can require the encryption of all messages addressed to a specific recipient, for example. When Exchange Online a user sends an message that matches an encryption rule, the message is sent out with an HTML attachment. A recipient opens the HTML attachment in the message, recognizes a familiar brand if that s present, and follows the embedded instructions to sign in, open, and read the encrypted message on the Office 365 Message Encryption portal. The sign-in process helps ensure that only intended recipients can view encrypted messages. The diagram that follows illustrates the passage of an message through the encryption process. 1. An Exchange Online user sends a message to the recipient. 2. The message is filtered based on administrator-defined rules that define conditions for encryption. 3. The tenant key for your Office 365 organization is accessed and the message is encrypted. 4. The encrypted message is delivered to the recipient s Inbox. 5. The recipient opens the HTML attachment and connects to the Office 365 encryption portal. 6. The recipient authenticates using a Microsoft account or an Office 365 organizational account. 7. The tenant key for your Office 365 organization is accessed to remove encryption from the message and the user views the unencrypted message. Service information for Office 365 Message Encryption 21
22 Service details Client device requirements Encryption algorithm and Federal Information Processing Standards (FIPS) compliance Message size limits Exchange Online retention policies Description Encrypted messages can be viewed on any client device, as long as the HTML attachment can be opened in a modern browser that supports Form Post. Office 365 Message Encryption uses the same encryption keys as Windows Azure Information Rights Management (IRM) and supports Cryptographic Mode 2 (2K key for RSA and 256 bits key for SHA-1 systems). For more information about the underlying IRM cryptographic modes, see AD RMS Cryptographic Modes. Office 365 Message Encryption can encrypt messages of up to 25 megabytes. For more details about message size limits, see Exchange Online Limits. Exchange Online doesn t store the encrypted messages. Office 365 Message encryption supports Office 365 languages, as follows: Language support for Office 365 Message Encryption Incoming messages and attached HTML files are localized based on the sender s language settings. The viewing portal is localized based on the recipient's browser settings. The body (content) of the encrypted message isn't localized. Office 365 Message Encryption requires that you have an Office 365 organizational account with an Exchange Online or Exchange Online Protection (EOP) subscription and that you ve set up Windows Azure Rights Management. If your setup meets these requirements, all you need to do to enable Office 365 Message Encryption is define rules that trigger encryption. Defining rules for Office 365 Message Encryption Administrators enable Office 365 Message Encryption by creating Exchange transport rules that determine under what conditions messages should be encrypted. There are also rules for defining conditions where encryption should be removed from messages. Once you ve set the encryption action within the rule, any messages that match the rule conditions are encrypted before they re sent out. Transport rules are flexible, letting you combine conditions so you can meet specific security requirements in a single rule. For example, you can create a rule to encrypt all messages that contain specified keywords and are addressed to external recipients. Office 365 Message Encryption also encrypts replies from recipients of encrypted , and you can create a rule that decrypts those replies as a convenience for your users. That way, users in your organization won t have to sign in to the encryption portal to view replies. Customizing encrypted messages with Office 365 Message Encryption As an administrator, you can add your company s brand to encrypted messages. For example, you can customize the introduction and disclaimer text in the message that accompanies encrypted messages as well as some text that appears on the portal where the recipient views the messages. You can also add a logo to the message and encrypted message viewing portal. Sending, viewing, and replying to encrypted messages With Office 365 Message Encryption, messages are encrypted automatically, based on administrator-defined rules. An that bears an encrypted message arrives in the recipient s Inbox with an attached HTML file that lets the recipient to sign-in to view the encrypted message. 22
23 Recipients follow instructions in the message to authenticate by using a Microsoft account or an organizational account. If recipients don t have either account, they re directed to create a Microsoft account that will let them sign in to view the encrypted message. After being authenticated, recipients can view the decrypted message and reply to it with an encrypted message. Setting up encryption Administrators set up transport rules to apply Office 365 Message Encryption when s match specified criteria. Transport rules provide great flexibility and control, and can be managed via a web-based interface or PowerShell. Setting up the transport rules is simple. Administrators simply select the action to apply encryption or remove encryption in the Exchange admin center. This is an improvement over EHE, which required complex headers and multiple setup steps. Once the admin sets up the rules, whenever anyone in the company sends a message that matches the conditions, the message is encrypted using Office 365 Message Encryption. The outgoing message is encrypted before it is delivered to the outside mail server to prevent any spoofing or misdirection. Receiving and responding to encrypted messages When an external recipient receives an encrypted message from your company, they see an encrypted attachment and an instruction to view the encrypted message. 23
24 You can open the attachment right from your inbox, and the attachment opens in a new browser window. To view the message, you just follow the simple instructions for authenticating via your Office 365 ID or Microsoft Account. The Message Encryption interface, based on Outlook Web App, is modern and easy to navigate. You can easily find information and perform quick tasks such as reply, forward, insert, attach, and so on. As an added measure of protection, when the receiver replies to the sender of the encrypted message or forwards the message, those s are also encrypted. 24
25 Applying custom branding Office 365 Message Encryption allows you to customize the branding on your company s encrypted messages and portal where the message is viewed. The customization is not limited just to your company logo, but can also extend to the text in the header, disclaimer, and the portal text in the sent . 25
26 Administrators can use PowerShell cmdlets to set up the branding for these texts and images. With Office 365 Message Encryption you can send sensitive information to people outside your organization with the confidence that that information is protected. We re excited to bring its new capabilities to you, and we look forward to hearing your feedback. Office 365 Message Encryption FAQ: Q: How do I get Office 365 Message Encryption? A: Office 365 Message Encryption will be available as part of Windows Azure Rights Management. Office 365 Enterprise E3 and E4 users will get Office 365 Message Encryption at no extra cost. We re including it in Windows Azure Rights Management, which is already part of the E3 and E4 plans. We re also including it in the standalone version of Windows Azure Rights Management, without raising the price of that service. Office 365 Message Encryption is available as an add-on for other Office 365 plans and for standalone plans. For example, Exchange Online Kiosk Plan 1 and Plan 2 customers will be able to add the service to their subscriptions at a cost of $2 per user per month. 26
27 Office 365 Message Encryption is also available to Exchange on-premises customers who purchase Windows Azure Rights Management service. Office 365 Message Encryption requires on-premises customers to route through Exchange Online, either by using Exchange Online Protection for filtering or by establishing hybrid mail-flow. Q. I am currently an Exchange Hosted Encryption (EHE) Subscriber. What happens to my subscription? Customers who are currently using Exchange Hosted Encryption (EHE) will be upgraded to Office 365 Message Encryption beginning in the first quarter of EHE customers can learn more information about the upgrade by visiting the EHE Upgrade Center. Q. How does Office 365 Message Encryption relate to other encryption technologies? A. A variety of encryption technologies work together in Office 365 to provide protection for s at rest and in transit: TLS encrypts the tunnel between mail server to help prevent snooping/eavesdropping. SSL encrypts the connection between mail clients and Office 365 servers. BitLocker encrypts the data on the hard drives in the datacenter so that if someone gets unauthorized access to the machine they can t read it. Information Rights Management. Windows Azure Rights Management in Office 365 prevents sensitive information from being printed, forwarded, or copiedby unauthorized people inside the organization. S/MIME is an encryption scheme that uses client-side encryption keys, popular for some government B2B scenarios. Read more about the upcoming S/MIME enhancements in Office 365 here. Office 365 Message Encryption is designed to help you send confidential messages to people outside your company simply and securely, without the administrative overhead required to use S/MIME or similar technologies. It s an outside-the-company companion to Information Rights Management, which is why it s included as part of the Windows Azure Rights Management offering. Q. My users send encrypted messages to recipients outside our organization. Is there anything that external recipients have to do differently in order to read and reply to messages that are encrypted with Office 365 Message Encryption? Recipients outside your organization who receive encrypted messages from senders in your organization are asked to create a Microsoft account if they don t have one so they can sign in to view and reply to encrypted messages. Q. Are Office 365 encrypted messages stored in the cloud or on Microsoft servers? No, the encrypted messages are kept on the recipient s system, and when the recipient opens the message, it is temporarily posted for viewing on Office 365 servers. The messages are not stored there. Q. Can I customize encrypted messages with my brand? Yes. You can use Windows PowerShell cmdlets to customize the default text that appears at the top of encrypted messages, the disclaimer text, and the logo that you want to use for the message and the encryption portal. Q. Is there a trial version of Office 365 Message Encryption available? Office 365 Message Encryption is included with Windows Azure Rights Management. You can sign-up for a 30-day trial of the service from the Office 365 Rights Management trial portal here: Azure Rights Management plan. In order to use the new encryption service, you must meet the following criteria: 27
28 If using Office 365, you must be using the newest version. If using on-premises mailboxes, you must be using Exchange Online Protection. If you re a Forefront Online Protection for Exchange (FOPE) customer, you must have upgraded to Exchange Online Protection. Q. I am using Exchange Will Office 365 Message Encryption be made available to me? Yes, as long as you are using Exchange Online Protection or have a hybrid deployment in which mail flow is routed through EOP. You can purchase Windows Azure Rights Management and then configure rules to encrypt using Office 365 Message Encryption. Q. How can I purchase the Office 365 Message Encryption? Office 365 Message Encryption will be available as part of Windows Azure Rights Management. Office 365 Enterprise E3 and E4 users already have Windows Azure Rights Management as part of their service, while Office 365 Enterprise E1 and K1, Exchange Online Kiosk, Plan 1 and Plan 2 customers will be able to add the service to their subscriptions at a cost of $2 per user per month. Enterprise E1 plan subscribers can add Office 365 Message Encryption on a per-user basis by purchasing Windows Azure Rights Management. On-premises customers can gain access to Office 365 Message Encryption by purchasing Windows Azure Rights Management for their users at a cost of $2 per user per month and purchasing Exchange Online Protection to set up mail-flow through Exchange Online. Q. Does the service require a license for every user in my organization? A license is required for every user in the organization who sends encrypted . Q. Do external recipients require subscriptions? No, external recipients do not require a subscription to read or reply to encrypted messages. Q. Will Office 365 Message Encryption be available in Office 365 Dedicated? Yes. You must first purchase Exchange Online Protection (EOP) and configure mail flow via EOP. Once that is done, customers can purchase Windows Azure Rights Management and configure rules to encrypt . Q. How is Office 365 Message Encryption different than Rights Management Services (RMS)? RMS provides Information Rights Protection capabilities for an organization s internal s by providing built-in templates, such as: Do not forward and Company Confidential. Office 365 Message Encryption supports message encryption for messages that are sent to external recipients as well as internal recipients. Q. How is Office 365 Message Encryption different than S/MIME? S/MIME is essentially a client-side encryption technology, and requires complicated certificate management and publishing infrastructure. Office 365 Message Encryption uses transport rules and does not depend on certificate publishing. 28
Information Rights Management in SharePoint. by André Vala
 Information Rights Management in SharePoint by André Vala About Me... André Vala SharePoint Solutions Architect Office & SharePoint Solutions Team Leader andre.vala@create.pt @atomicvee http://blogit.create.pt/andrevala
Information Rights Management in SharePoint by André Vala About Me... André Vala SharePoint Solutions Architect Office & SharePoint Solutions Team Leader andre.vala@create.pt @atomicvee http://blogit.create.pt/andrevala
OneDrive for Business User Guide
 OneDrive for Business User Guide Contents OneDrive for Business and Office 365... 2 Storing University Information in the Cloud... 2 Signing in... 2 The Office 365 Interface... 3 The OneDrive App... 3
OneDrive for Business User Guide Contents OneDrive for Business and Office 365... 2 Storing University Information in the Cloud... 2 Signing in... 2 The Office 365 Interface... 3 The OneDrive App... 3
OneDrive for Business User Guide
 OneDrive for Business User Guide Contents OneDrive for Business and Office 365... 2 Storing University Information in the Cloud... 2 Signing in... 2 The Office 365 Interface... 3 The OneDrive App... 3
OneDrive for Business User Guide Contents OneDrive for Business and Office 365... 2 Storing University Information in the Cloud... 2 Signing in... 2 The Office 365 Interface... 3 The OneDrive App... 3
WatchDox for Windows User Guide. Version 3.9.0
 Version 3.9.0 Notice Confidentiality This document contains confidential material that is proprietary WatchDox. The information and ideas herein may not be disclosed to any unauthorized individuals or
Version 3.9.0 Notice Confidentiality This document contains confidential material that is proprietary WatchDox. The information and ideas herein may not be disclosed to any unauthorized individuals or
Using Entrust certificates with Microsoft Office and Windows
 Entrust Managed Services PKI Using Entrust certificates with Microsoft Office and Windows Document issue: 1.0 Date of issue: May 2009 Copyright 2009 Entrust. All rights reserved. Entrust is a trademark
Entrust Managed Services PKI Using Entrust certificates with Microsoft Office and Windows Document issue: 1.0 Date of issue: May 2009 Copyright 2009 Entrust. All rights reserved. Entrust is a trademark
Overview of Active Directory Rights Management Services with Windows Server 2008 R2
 Overview of Active Directory Rights Management Services with Windows Server 2008 R2 Student Manual Module 3: Active Directory Rights Management Clients and Information Rights Management on Desktop Applications
Overview of Active Directory Rights Management Services with Windows Server 2008 R2 Student Manual Module 3: Active Directory Rights Management Clients and Information Rights Management on Desktop Applications
OneDrive for Business User Guide
 OneDrive for Business User Guide Contents About OneDrive for Business and Office 365... 2 Storing University Information in the Cloud... 2 Signing in... 2 The Office 365 Interface... 3 The OneDrive for
OneDrive for Business User Guide Contents About OneDrive for Business and Office 365... 2 Storing University Information in the Cloud... 2 Signing in... 2 The Office 365 Interface... 3 The OneDrive for
Configuration Guide. BES12 Cloud
 Configuration Guide BES12 Cloud Published: 2016-04-08 SWD-20160408113328879 Contents About this guide... 6 Getting started... 7 Configuring BES12 for the first time...7 Administrator permissions you need
Configuration Guide BES12 Cloud Published: 2016-04-08 SWD-20160408113328879 Contents About this guide... 6 Getting started... 7 Configuring BES12 for the first time...7 Administrator permissions you need
Save and Share Files in the Cloud with OneDrive for Business
 Work Smart by Microsoft IT Save and Share Files in the Cloud with OneDrive for Business Microsoft OneDrive for Business is your professional file library your OneDrive for your business needs. OneDrive
Work Smart by Microsoft IT Save and Share Files in the Cloud with OneDrive for Business Microsoft OneDrive for Business is your professional file library your OneDrive for your business needs. OneDrive
BTC STUDENT EMAIL GUIDE
 BTC STUDENT EMAIL GUIDE All students have a BTC email account. If you are unable to access your account, please contact your instructor. Student Email Each student has an email account. Your email address
BTC STUDENT EMAIL GUIDE All students have a BTC email account. If you are unable to access your account, please contact your instructor. Student Email Each student has an email account. Your email address
Abila Grant Management. Document Management
 Abila Grant Management This is a publication of Abila, Inc. Version 2014 2014 Abila, Inc. and its affiliated entities. All rights reserved. Abila, the Abila logos, and the Abila product and service names
Abila Grant Management This is a publication of Abila, Inc. Version 2014 2014 Abila, Inc. and its affiliated entities. All rights reserved. Abila, the Abila logos, and the Abila product and service names
Get started with cloud hybrid search for SharePoint
 Get started with cloud hybrid search for SharePoint This document supports a preliminary release of the cloud hybrid search feature for SharePoint 2013 with August 2015 PU and for SharePoint 2016 Preview,
Get started with cloud hybrid search for SharePoint This document supports a preliminary release of the cloud hybrid search feature for SharePoint 2013 with August 2015 PU and for SharePoint 2016 Preview,
DigitalPersona Privacy Manager Pro
 DigitalPersona Privacy Manager Pro DigitalPersona Privacy Manager Pro is a centrally-managed secure communication solution for businesses. It allows sensitive documents and communications to remain private,
DigitalPersona Privacy Manager Pro DigitalPersona Privacy Manager Pro is a centrally-managed secure communication solution for businesses. It allows sensitive documents and communications to remain private,
WatchDox for Windows. User Guide. Version 3.9.5
 WatchDox for Windows User Guide Version 3.9.5 Notice Confidentiality This document contains confidential material that is proprietary WatchDox. The information and ideas herein may not be disclosed to
WatchDox for Windows User Guide Version 3.9.5 Notice Confidentiality This document contains confidential material that is proprietary WatchDox. The information and ideas herein may not be disclosed to
Copyright 2013 Trend Micro Incorporated. All rights reserved.
 Trend Micro Incorporated reserves the right to make changes to this document and to the products described herein without notice. Before installing and using the software, please review the readme files,
Trend Micro Incorporated reserves the right to make changes to this document and to the products described herein without notice. Before installing and using the software, please review the readme files,
WatchDox Administrator's Guide. Application Version 3.7.5
 Application Version 3.7.5 Confidentiality This document contains confidential material that is proprietary WatchDox. The information and ideas herein may not be disclosed to any unauthorized individuals
Application Version 3.7.5 Confidentiality This document contains confidential material that is proprietary WatchDox. The information and ideas herein may not be disclosed to any unauthorized individuals
Amicus Link Guide: Outlook/Exchange E-mail
 Amicus Link Guide: Outlook/Exchange E-mail Applies to: Amicus Premium 2015 Synchronize your Amicus and Outlook e-mail. Choose a client-side link with your local Microsoft Outlook or a Server-side link
Amicus Link Guide: Outlook/Exchange E-mail Applies to: Amicus Premium 2015 Synchronize your Amicus and Outlook e-mail. Choose a client-side link with your local Microsoft Outlook or a Server-side link
Colligo Email Manager 6.0. Offline Mode - User Guide
 6.0 Offline Mode - User Guide Contents Colligo Email Manager 1 Key Features 1 Benefits 1 Installing and Activating Colligo Email Manager 2 Checking for Updates 3 Updating Your License Key 3 Managing SharePoint
6.0 Offline Mode - User Guide Contents Colligo Email Manager 1 Key Features 1 Benefits 1 Installing and Activating Colligo Email Manager 2 Checking for Updates 3 Updating Your License Key 3 Managing SharePoint
Bridging People and Process. Bridging People and Process. Bridging People and Process. Bridging People and Process
 USER MANUAL DATAMOTION SECUREMAIL SERVER Bridging People and Process APPLICATION VERSION 1.1 Bridging People and Process Bridging People and Process Bridging People and Process Published By: DataMotion,
USER MANUAL DATAMOTION SECUREMAIL SERVER Bridging People and Process APPLICATION VERSION 1.1 Bridging People and Process Bridging People and Process Bridging People and Process Published By: DataMotion,
imail Frequently Asked Questions (FAQs) 27 July 2015 Version 2.2
 imail Frequently Asked Questions (FAQs) 27 July 2015 Version 2.2 Owner: Cynthia Tan IT Services Table of Contents GENERAL FAQS... 4 1. How to access to Sunway imail account?... 4 2. I can t login to my
imail Frequently Asked Questions (FAQs) 27 July 2015 Version 2.2 Owner: Cynthia Tan IT Services Table of Contents GENERAL FAQS... 4 1. How to access to Sunway imail account?... 4 2. I can t login to my
User Guide for the VersaMail Application
 User Guide for the VersaMail Application Copyright and Trademark 2004 palmone, Inc. All rights reserved. palmone, HotSync, the HotSync logo, Palm, Palm OS, the Palm logo, and VersaMail are among the trademarks
User Guide for the VersaMail Application Copyright and Trademark 2004 palmone, Inc. All rights reserved. palmone, HotSync, the HotSync logo, Palm, Palm OS, the Palm logo, and VersaMail are among the trademarks
Policy Based Encryption E. Administrator Guide
 Policy Based Encryption E Administrator Guide Policy Based Encryption E Administrator Guide Documentation version: 1.2 Legal Notice Legal Notice Copyright 2012 Symantec Corporation. All rights reserved.
Policy Based Encryption E Administrator Guide Policy Based Encryption E Administrator Guide Documentation version: 1.2 Legal Notice Legal Notice Copyright 2012 Symantec Corporation. All rights reserved.
Policy Based Encryption E. Administrator Guide
 Policy Based Encryption E Administrator Guide Policy Based Encryption E Administrator Guide Documentation version: 1.2 Legal Notice Legal Notice Copyright 2012 Symantec Corporation. All rights reserved.
Policy Based Encryption E Administrator Guide Policy Based Encryption E Administrator Guide Documentation version: 1.2 Legal Notice Legal Notice Copyright 2012 Symantec Corporation. All rights reserved.
Cloud. Hosted Exchange Administration Manual
 Cloud Hosted Exchange Administration Manual Table of Contents Table of Contents... 1 Table of Figures... 4 1 Preface... 6 2 Telesystem Hosted Exchange Administrative Portal... 7 3 Hosted Exchange Service...
Cloud Hosted Exchange Administration Manual Table of Contents Table of Contents... 1 Table of Figures... 4 1 Preface... 6 2 Telesystem Hosted Exchange Administrative Portal... 7 3 Hosted Exchange Service...
Microsoft Outlook Quick Reference Sheet
 Microsoft Outlook is an incredibly powerful e-mail and personal information management application. Its features and capabilities are extensive. Refer to this handout whenever you require quick reminders
Microsoft Outlook is an incredibly powerful e-mail and personal information management application. Its features and capabilities are extensive. Refer to this handout whenever you require quick reminders
Colligo Briefcase Enterprise. Administrator s Guide
 Enterprise Administrator s Guide CONTENTS Introduction... 2 Target Audience... 2 Overview... 2 Key Features... 2 Platforms Supported... 2 SharePoint Security & Privileges... 2 Deploying Colligo Briefcase...
Enterprise Administrator s Guide CONTENTS Introduction... 2 Target Audience... 2 Overview... 2 Key Features... 2 Platforms Supported... 2 SharePoint Security & Privileges... 2 Deploying Colligo Briefcase...
OneDrive for Business User Guide
 OneDrive for Business User Guide Contents OneDrive for Business... 1 User Guide... 1 Contents... 1 2. OneDrive for Business and Office365... 2 3. Signing in... 2 4. Help... 3 5. OneDrive... 3 5.1 Create,
OneDrive for Business User Guide Contents OneDrive for Business... 1 User Guide... 1 Contents... 1 2. OneDrive for Business and Office365... 2 3. Signing in... 2 4. Help... 3 5. OneDrive... 3 5.1 Create,
Egnyte for Power and Standard Users. User Guide
 Egnyte for Power and Standard Users User Guide Egnyte Inc. 1350 West Middlefield Road. Mountain View, CA 94043, USA Phone: 877-7EGNYTE (877-734-6983) Revised June 2015 Table of Contents Chapter 1: Getting
Egnyte for Power and Standard Users User Guide Egnyte Inc. 1350 West Middlefield Road. Mountain View, CA 94043, USA Phone: 877-7EGNYTE (877-734-6983) Revised June 2015 Table of Contents Chapter 1: Getting
E-mail Encryption Recipient Guidelines
 E-mail Encryption Recipient Guidelines Canadian Western Bank Group Human Resources Department November 1, 2013 This reference guide was developed for training and reference use only. Any discrepancies
E-mail Encryption Recipient Guidelines Canadian Western Bank Group Human Resources Department November 1, 2013 This reference guide was developed for training and reference use only. Any discrepancies
INTRODUCTION TO CLOUD STORAGE
 University of North Carolina at Chapel Hill Libraries Carrboro Cybrary Chapel Hill Public Library Durham County Public Library INTRODUCTION TO CLOUD STORAGE GETTING STARTED PAGE 02 Class Overview What
University of North Carolina at Chapel Hill Libraries Carrboro Cybrary Chapel Hill Public Library Durham County Public Library INTRODUCTION TO CLOUD STORAGE GETTING STARTED PAGE 02 Class Overview What
ShareSync Get Started Guide
 ShareSync Get Started Guide WHAT IS SHARESYNC? ShareSync is a cloud file sync and share service. ShareSync allows you to easily sync files between multiple computers, the ShareSync web portal and mobile
ShareSync Get Started Guide WHAT IS SHARESYNC? ShareSync is a cloud file sync and share service. ShareSync allows you to easily sync files between multiple computers, the ShareSync web portal and mobile
Frequently Asked Questions. Frequently Asked Questions. 2013 SSLPost Page 1 of 31 support@sslpost.com
 Frequently Asked Questions 2013 SSLPost Page 1 of 31 support@sslpost.com Table of Contents 1 What is SSLPost Cloud? 3 2 Why do I need SSLPost Cloud? 4 3 What do I need to use SSLPost Cloud? 5 4 Which Internet
Frequently Asked Questions 2013 SSLPost Page 1 of 31 support@sslpost.com Table of Contents 1 What is SSLPost Cloud? 3 2 Why do I need SSLPost Cloud? 4 3 What do I need to use SSLPost Cloud? 5 4 Which Internet
Administration Guide. WatchDox Server. Version 4.8.0
 Administration Guide WatchDox Server Version 4.8.0 Published: 2015-11-01 SWD-20151101091846278 Contents Introduction... 7 Getting started... 11 Signing in to WatchDox... 11 Signing in with username and
Administration Guide WatchDox Server Version 4.8.0 Published: 2015-11-01 SWD-20151101091846278 Contents Introduction... 7 Getting started... 11 Signing in to WatchDox... 11 Signing in with username and
Background Information
 User Guide 1 Background Information ********************************Disclaimer******************************************** This is a government system intended for official use only. Using this system
User Guide 1 Background Information ********************************Disclaimer******************************************** This is a government system intended for official use only. Using this system
WatchDox for Mac User Guide
 WatchDox for Mac User Guide Version 2.3.0 Confidentiality This document contains confidential material that is proprietary to WatchDox. The information and ideas herein may not be disclosed to any unauthorized
WatchDox for Mac User Guide Version 2.3.0 Confidentiality This document contains confidential material that is proprietary to WatchDox. The information and ideas herein may not be disclosed to any unauthorized
Save and share files in the cloud by using
 Save and share files in the cloud by using OneDrive for Business Microsoft OneDrive for Business is your professional document library the business version of the OneDrive consumer service. OneDrive for
Save and share files in the cloud by using OneDrive for Business Microsoft OneDrive for Business is your professional document library the business version of the OneDrive consumer service. OneDrive for
Vodafone Hosted Services. Getting your email. User guide
 Vodafone Hosted Services Getting your email User guide Welcome. This guide will show you how to get your email, now that it is hosted by Vodafone Hosted Services. Once you ve set it up, you will be able
Vodafone Hosted Services Getting your email User guide Welcome. This guide will show you how to get your email, now that it is hosted by Vodafone Hosted Services. Once you ve set it up, you will be able
ShareSync Get Started Guide
 ShareSync Get Started Guide WHAT IS SHARESYNC? ShareSync is a cloud file sync and share service. ShareSync allows you to easily sync files between multiple computers, the ShareSync web portal and mobile
ShareSync Get Started Guide WHAT IS SHARESYNC? ShareSync is a cloud file sync and share service. ShareSync allows you to easily sync files between multiple computers, the ShareSync web portal and mobile
DESLock+ Basic Setup Guide Version 1.20, rev: June 9th 2014
 DESLock+ Basic Setup Guide Version 1.20, rev: June 9th 2014 Contents Overview... 2 System requirements:... 2 Before installing... 3 Download and installation... 3 Configure DESLock+ Enterprise Server...
DESLock+ Basic Setup Guide Version 1.20, rev: June 9th 2014 Contents Overview... 2 System requirements:... 2 Before installing... 3 Download and installation... 3 Configure DESLock+ Enterprise Server...
IBM Aspera Add-in for Microsoft Outlook 1.3.2
 IBM Aspera Add-in for Microsoft Outlook 1.3.2 Windows: 7, 8 Revision: 1.3.2.100253 Generated: 02/12/2015 10:58 Contents 2 Contents Introduction... 3 System Requirements... 5 Setting Up... 6 Account Credentials...6
IBM Aspera Add-in for Microsoft Outlook 1.3.2 Windows: 7, 8 Revision: 1.3.2.100253 Generated: 02/12/2015 10:58 Contents 2 Contents Introduction... 3 System Requirements... 5 Setting Up... 6 Account Credentials...6
Welcome to Sookasa. Getting Started Guide for SafeMonk users
 Welcome to Sookasa Getting Started Guide for SafeMonk users Welcome to Sookasa! About Us Like Safemonk, Sookasa provides Dropbox encryption to protect your information at the file level, so it s safe both
Welcome to Sookasa Getting Started Guide for SafeMonk users Welcome to Sookasa! About Us Like Safemonk, Sookasa provides Dropbox encryption to protect your information at the file level, so it s safe both
Virtual Data Centre. User Guide
 Virtual Data Centre User Guide 2 P age Table of Contents Getting Started with vcloud Director... 8 1. Understanding vcloud Director... 8 2. Log In to the Web Console... 9 3. Using vcloud Director... 10
Virtual Data Centre User Guide 2 P age Table of Contents Getting Started with vcloud Director... 8 1. Understanding vcloud Director... 8 2. Log In to the Web Console... 9 3. Using vcloud Director... 10
ShareSync Get Started Guide for Windows
 WHAT IS SHARESYNC? ShareSync Get Started Guide for Windows ShareSync is an enterprise-class cloud file backup and sharing service. ShareSync allows you to back up your files in real-time to protect against
WHAT IS SHARESYNC? ShareSync Get Started Guide for Windows ShareSync is an enterprise-class cloud file backup and sharing service. ShareSync allows you to back up your files in real-time to protect against
MailEnable Connector for Microsoft Outlook
 MailEnable Connector for Microsoft Outlook Version 2.23 This guide describes the installation and functionality of the MailEnable Connector for Microsoft Outlook. Features The MailEnable Connector for
MailEnable Connector for Microsoft Outlook Version 2.23 This guide describes the installation and functionality of the MailEnable Connector for Microsoft Outlook. Features The MailEnable Connector for
Cloud-Accelerated Hybrid Scenarios with SharePoint and Office 365
 Cloud-Accelerated Hybrid Scenarios with SharePoint and Office 365 Contents Contents 1 About this guide 3 Overview 9 Authentication and authorization 10 Getting started with identity integration 26 Getting
Cloud-Accelerated Hybrid Scenarios with SharePoint and Office 365 Contents Contents 1 About this guide 3 Overview 9 Authentication and authorization 10 Getting started with identity integration 26 Getting
Share files with people outside the University
 Share files with people outside the University You can create an anonymous guest link, and then share the link using whatever media suits you. For example, post it on a social media page, or paste it into
Share files with people outside the University You can create an anonymous guest link, and then share the link using whatever media suits you. For example, post it on a social media page, or paste it into
Colligo Contributor File Manager 4.6. User Guide
 Colligo Contributor File Manager 4.6 User Guide Contents Colligo Contributor File Manager Introduction... 2 Benefits... 2 Features... 2 Platforms Supported... 2 Installing and Activating Contributor File
Colligo Contributor File Manager 4.6 User Guide Contents Colligo Contributor File Manager Introduction... 2 Benefits... 2 Features... 2 Platforms Supported... 2 Installing and Activating Contributor File
Zimbra Connector for Microsoft Outlook User Guide 7.1
 Zimbra Connector for Microsoft Outlook User Guide 7.1 March 2011 Legal Notices Copyright 2005-2011 VMware, Inc. All rights reserved. This product is protected by U.S. and international copyright and intellectual
Zimbra Connector for Microsoft Outlook User Guide 7.1 March 2011 Legal Notices Copyright 2005-2011 VMware, Inc. All rights reserved. This product is protected by U.S. and international copyright and intellectual
Colligo Email Manager 6.2. Offline Mode - User Guide
 6.2 Offline Mode - User Guide Contents Colligo Email Manager 1 Benefits 1 Key Features 1 Platforms Supported 1 Installing and Activating Colligo Email Manager 3 Checking for Updates 4 Updating Your License
6.2 Offline Mode - User Guide Contents Colligo Email Manager 1 Benefits 1 Key Features 1 Platforms Supported 1 Installing and Activating Colligo Email Manager 3 Checking for Updates 4 Updating Your License
Copyright 2012 Trend Micro Incorporated. All rights reserved.
 Trend Micro Incorporated reserves the right to make changes to this document and to the products described herein without notice. Before installing and using the software, please review the readme files,
Trend Micro Incorporated reserves the right to make changes to this document and to the products described herein without notice. Before installing and using the software, please review the readme files,
Sign in to view your Office 365 encrypted message
 Sign in to view your Office 365 encrypted message If you ve received an encrypted message from an organization that uses Microsoft Office 365 Message Encryption, you can view your message by using a Microsoft
Sign in to view your Office 365 encrypted message If you ve received an encrypted message from an organization that uses Microsoft Office 365 Message Encryption, you can view your message by using a Microsoft
What is OneDrive for Business at University of Greenwich? Accessing OneDrive from Office 365
 This guide explains how to access and use the OneDrive for Business cloud based storage system and Microsoft Office Online suite of products via a web browser. What is OneDrive for Business at University
This guide explains how to access and use the OneDrive for Business cloud based storage system and Microsoft Office Online suite of products via a web browser. What is OneDrive for Business at University
SharePoint Online Setting site up for S drive data
 SharePoint Online Setting site up for S drive data Establishing team site locations and managing shared drive data file conversions and migration 8-18-2015 1 Introduction This storyboard is designed to
SharePoint Online Setting site up for S drive data Establishing team site locations and managing shared drive data file conversions and migration 8-18-2015 1 Introduction This storyboard is designed to
OneDrive for Business from Desktop or Laptop Windows devices
 OneDrive for Business from Desktop or Laptop Windows devices OneDrive for Business (previously called SkyDrive Pro) is cloud based file store that comes as part of the Uel Office365 subscription. It provides
OneDrive for Business from Desktop or Laptop Windows devices OneDrive for Business (previously called SkyDrive Pro) is cloud based file store that comes as part of the Uel Office365 subscription. It provides
Policy Based Encryption Z. Administrator Guide
 Policy Based Encryption Z Administrator Guide Policy Based Encryption Z Administrator Guide Documentation version: 1.2 Legal Notice Legal Notice Copyright 2012 Symantec Corporation. All rights reserved.
Policy Based Encryption Z Administrator Guide Policy Based Encryption Z Administrator Guide Documentation version: 1.2 Legal Notice Legal Notice Copyright 2012 Symantec Corporation. All rights reserved.
Amazon WorkMail. User Guide Version 1.0
 Amazon WorkMail User Guide Amazon WorkMail: User Guide Copyright 2016 Amazon Web Services, Inc. and/or its affiliates. All rights reserved. Amazon's trademarks and trade dress may not be used in connection
Amazon WorkMail User Guide Amazon WorkMail: User Guide Copyright 2016 Amazon Web Services, Inc. and/or its affiliates. All rights reserved. Amazon's trademarks and trade dress may not be used in connection
Active Directory Rights Management Services integration (AD RMS)
 MOSS Information Rights Management Ashish Bahuguna ashish.bahuguna@bitscape.com Active Directory Rights Management Services integration (AD RMS) Agenda AD RMS Overview AD RMS Architecture Components MOSS
MOSS Information Rights Management Ashish Bahuguna ashish.bahuguna@bitscape.com Active Directory Rights Management Services integration (AD RMS) Agenda AD RMS Overview AD RMS Architecture Components MOSS
IT Transformation email Consolidation Project Frequently Asked Questions
 Table of Contents Office 365: General... 3 What is Office365?... 3 Why did the State select Office365?... 3 What agencies are moving to Office365?... 3 I thought this was just an email project.... 3 What
Table of Contents Office 365: General... 3 What is Office365?... 3 Why did the State select Office365?... 3 What agencies are moving to Office365?... 3 I thought this was just an email project.... 3 What
Business 360 Online - Product concepts and features
 Business 360 Online - Product concepts and features Version November 2014 Business 360 Online from Software Innovation is a cloud-based tool for information management. It helps you to work smarter with
Business 360 Online - Product concepts and features Version November 2014 Business 360 Online from Software Innovation is a cloud-based tool for information management. It helps you to work smarter with
Student Office 365 Outlook Web App OWA Quick Guide. Getting you up to speed quickly.
 Student Office 365 Outlook Web App OWA Quick Guide Getting you up to speed quickly. Information Services 9-5-2014 Contents Logging into the CWU Student Outlook Web App... 3 Getting Started with Office
Student Office 365 Outlook Web App OWA Quick Guide Getting you up to speed quickly. Information Services 9-5-2014 Contents Logging into the CWU Student Outlook Web App... 3 Getting Started with Office
Receiving Secure Email from Citi For External Customers and Business Partners
 Citi Secure Email Program Receiving Secure Email from Citi For External Customers and Business Partners Protecting the privacy and security of client information is a top priority at Citi. Citi s Secure
Citi Secure Email Program Receiving Secure Email from Citi For External Customers and Business Partners Protecting the privacy and security of client information is a top priority at Citi. Citi s Secure
Disabling Microsoft SharePoint in order to install the OneDrive for Business Client
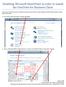 Disabling Microsoft SharePoint in order to install the OneDrive for Business Client If you try to setup and sync your OneDrive online documents with the client software and Microsoft SharePoint opens,
Disabling Microsoft SharePoint in order to install the OneDrive for Business Client If you try to setup and sync your OneDrive online documents with the client software and Microsoft SharePoint opens,
Word 2010 to Office 365 for business
 Word 2010 to Office 365 for business Make the switch Microsoft Word 2013 desktop looks different from previous versions, so here s a brief overview of new features and important changes. Quick Access Toolbar
Word 2010 to Office 365 for business Make the switch Microsoft Word 2013 desktop looks different from previous versions, so here s a brief overview of new features and important changes. Quick Access Toolbar
Novell Filr. Mobile Client
 Novell Filr Mobile Client 0 Table of Contents Quick Start 3 Supported Mobile Devices 3 Supported Languages 4 File Viewing Support 4 FILES THAT CANNOT BE VIEWED IN THE FILR APP 4 FILES THAT GIVE A WARNING
Novell Filr Mobile Client 0 Table of Contents Quick Start 3 Supported Mobile Devices 3 Supported Languages 4 File Viewing Support 4 FILES THAT CANNOT BE VIEWED IN THE FILR APP 4 FILES THAT GIVE A WARNING
Getting Started with Office 365 Contents
 Getting Started with Office 365 Contents What is Office 365?... 2 Key Service Highlights for Students:... 2 Summary of Benefits of Office 365 for IOE Students... 3 Learn More with Videos... 3 Logging onto
Getting Started with Office 365 Contents What is Office 365?... 2 Key Service Highlights for Students:... 2 Summary of Benefits of Office 365 for IOE Students... 3 Learn More with Videos... 3 Logging onto
Microsoft Office System Tip Sheet
 Experience the 2007 Microsoft Office System The 2007 Microsoft Office system includes programs, servers, services, and solutions designed to work together to help you succeed. New features in the 2007
Experience the 2007 Microsoft Office System The 2007 Microsoft Office system includes programs, servers, services, and solutions designed to work together to help you succeed. New features in the 2007
I. Configuring Digital signature certificate in Microsoft Outlook 2003:
 I. Configuring Digital signature certificate in Microsoft Outlook 2003: In order to configure Outlook 2003 to use the new message security settings please follow these steps: 1. Open Outlook. 2. Go to
I. Configuring Digital signature certificate in Microsoft Outlook 2003: In order to configure Outlook 2003 to use the new message security settings please follow these steps: 1. Open Outlook. 2. Go to
Get Started Guide for Admins
 Get Started Guide for Admins This Admin Guide will provide instructions for getting started with SecuriSync, provide tips for setting up your SecuriSync environment, and overview the superior management
Get Started Guide for Admins This Admin Guide will provide instructions for getting started with SecuriSync, provide tips for setting up your SecuriSync environment, and overview the superior management
Subscribe to RSS in Outlook 2007. Find RSS Feeds. Exchange Outlook 2007 How To s / RSS Feeds 1of 7
 Exchange Outlook 007 How To s / RSS Feeds of 7 RSS (Really Simple Syndication) is a method of publishing and distributing content on the Web. When you subscribe to an RSS feed also known as a news feed
Exchange Outlook 007 How To s / RSS Feeds of 7 RSS (Really Simple Syndication) is a method of publishing and distributing content on the Web. When you subscribe to an RSS feed also known as a news feed
Grapevine Mail User Guide
 Grapevine Mail User Guide Table of Contents Accessing Grapevine Mail...2 How to access the Mail portal... 2 How to login... 2 Grapevine Mail user guide... 5 Copying your contacts to the new Grapevine Mail
Grapevine Mail User Guide Table of Contents Accessing Grapevine Mail...2 How to access the Mail portal... 2 How to login... 2 Grapevine Mail user guide... 5 Copying your contacts to the new Grapevine Mail
FAQs. OneDrive for Business?
 Contents FAQs... 1 From a Web Browser (for PCs and mobile devices)... 1 From the OneDrive for Business Sync Application (for PCs only)... 2 From Office 2013 (for PCs only)... 3 From the OneDrive for Business
Contents FAQs... 1 From a Web Browser (for PCs and mobile devices)... 1 From the OneDrive for Business Sync Application (for PCs only)... 2 From Office 2013 (for PCs only)... 3 From the OneDrive for Business
White Paper. Anywhere, Any Device File Access with IT in Control. Enterprise File Serving 2.0
 White Paper Enterprise File Serving 2.0 Anywhere, Any Device File Access with IT in Control Like it or not, cloud- based file sharing services have opened up a new world of mobile file access and collaborative
White Paper Enterprise File Serving 2.0 Anywhere, Any Device File Access with IT in Control Like it or not, cloud- based file sharing services have opened up a new world of mobile file access and collaborative
Microsoft Office 365 Microsoft Office 2013 Pro Plus for PC Installation and Activation Walkthrough
 Microsoft Office 365 Microsoft Office 2013 Pro Plus for PC Installation and Activation Walkthrough Contents Introduction... 2 System Requirements... 2 Installing Microsoft Office 2013... 2 Manage/Deactivate
Microsoft Office 365 Microsoft Office 2013 Pro Plus for PC Installation and Activation Walkthrough Contents Introduction... 2 System Requirements... 2 Installing Microsoft Office 2013... 2 Manage/Deactivate
CITY OF BURLINGTON PUBLIC SCHOOLS MICROSOFT EXCHANGE 2010 OUTLOOK WEB APP USERS GUIDE
 CITY OF BURLINGTON PUBLIC SCHOOLS MICROSOFT EXCHANGE 2010 OUTLOOK WEB APP USERS GUIDE INTRODUCTION You can access your email account from any workstation at your school using Outlook Web Access (OWA),
CITY OF BURLINGTON PUBLIC SCHOOLS MICROSOFT EXCHANGE 2010 OUTLOOK WEB APP USERS GUIDE INTRODUCTION You can access your email account from any workstation at your school using Outlook Web Access (OWA),
CTERA Agent for Mac OS-X
 User Guide CTERA Agent for Mac OS-X June 2014 Version 4.1 Copyright 2009-2014 CTERA Networks Ltd. All rights reserved. No part of this document may be reproduced in any form or by any means without written
User Guide CTERA Agent for Mac OS-X June 2014 Version 4.1 Copyright 2009-2014 CTERA Networks Ltd. All rights reserved. No part of this document may be reproduced in any form or by any means without written
WatchDox SharePoint Beta Guide. Application Version 1.0.0
 Application Version 1.0.0 Confidentiality This document contains confidential material that is proprietary WatchDox. The information and ideas herein may not be disclosed to any unauthorized individuals
Application Version 1.0.0 Confidentiality This document contains confidential material that is proprietary WatchDox. The information and ideas herein may not be disclosed to any unauthorized individuals
Microsoft Outlook 2013 -And- Outlook Web App (OWA) Using Office 365
 1 C H A P T E R Microsoft Outlook 2013 -And- Outlook Web App (OWA) Using Office 365 1 MICROSOFT OUTLOOK 2013 AND OUTLOOK WEB ACCESS (OWA) Table of Contents Chapter 1: Signing Into the Microsoft Email System...
1 C H A P T E R Microsoft Outlook 2013 -And- Outlook Web App (OWA) Using Office 365 1 MICROSOFT OUTLOOK 2013 AND OUTLOOK WEB ACCESS (OWA) Table of Contents Chapter 1: Signing Into the Microsoft Email System...
Office 365 SharePoint Setup and Admin Guide
 Setup and Admin Guide Contents About this guide... 2 Introduction to SharePoint... 2 SharePoint sites... 3 Team sites, Websites and personal sites... 3 Site structures... 4 Choosing a site structure...
Setup and Admin Guide Contents About this guide... 2 Introduction to SharePoint... 2 SharePoint sites... 3 Team sites, Websites and personal sites... 3 Site structures... 4 Choosing a site structure...
How To Configure A Windows 8.1 On A Windows 7.1.1 (Windows) With A Powerpoint (Windows 8) On A Blackberry) On An Ipad Or Ipad (Windows 7) On Your Blackberry Or Black
 Introduction to Cloud-Based Mobile Device Management with Intune Information in this document, including URLs and other Internet Web site references, is subject to change without notice. Unless otherwise
Introduction to Cloud-Based Mobile Device Management with Intune Information in this document, including URLs and other Internet Web site references, is subject to change without notice. Unless otherwise
ShareSync Get Started Guide
 ShareSync Get Started Guide WHAT IS SHARESYNC? ShareSync is a cloud backup and file sync and share service. ShareSync allows you to easily sync files between multiple computers, the ShareSync web App and
ShareSync Get Started Guide WHAT IS SHARESYNC? ShareSync is a cloud backup and file sync and share service. ShareSync allows you to easily sync files between multiple computers, the ShareSync web App and
One of the fundamental kinds of Web sites that SharePoint 2010 allows
 Chapter 1 Getting to Know Your Team Site In This Chapter Requesting a new team site and opening it in the browser Participating in a team site Changing your team site s home page One of the fundamental
Chapter 1 Getting to Know Your Team Site In This Chapter Requesting a new team site and opening it in the browser Participating in a team site Changing your team site s home page One of the fundamental
SHAREPOINT 2010 FOUNDATION FOR END USERS
 SHAREPOINT 2010 FOUNDATION FOR END USERS WWP Training Limited Page i SharePoint Foundation 2010 for End Users Fundamentals of SharePoint... 6 Accessing SharePoint Foundation 2010... 6 Logging in to your
SHAREPOINT 2010 FOUNDATION FOR END USERS WWP Training Limited Page i SharePoint Foundation 2010 for End Users Fundamentals of SharePoint... 6 Accessing SharePoint Foundation 2010... 6 Logging in to your
FileCruiser. Desktop Agent Guide
 FileCruiser Desktop Agent Guide FileCruiser Desktop Agent Guide Contents Contents Getting Started with FileCruiser 1 Using the FileCruiser Agent 2 Desktop Shortcut 2 Log in to FileCruiser Agent 3 Using
FileCruiser Desktop Agent Guide FileCruiser Desktop Agent Guide Contents Contents Getting Started with FileCruiser 1 Using the FileCruiser Agent 2 Desktop Shortcut 2 Log in to FileCruiser Agent 3 Using
1. How to Register... 2. 2. Forgot Password... 4. 3. Login to MailTrack Webmail... 5. 4. Accessing MailTrack message Centre... 6
 MailTrack How To Document 27 March 2014 Table of Contents 1. How to Register... 2 2. Forgot Password... 4 3. Login to MailTrack Webmail... 5 4. Accessing MailTrack message Centre... 6 5. Creating a MailTrack
MailTrack How To Document 27 March 2014 Table of Contents 1. How to Register... 2 2. Forgot Password... 4 3. Login to MailTrack Webmail... 5 4. Accessing MailTrack message Centre... 6 5. Creating a MailTrack
Save and share documents in the cloud with OneDrive
 Work Smart Save and share documents in the cloud with OneDrive OneDrive for Business is your professional document library. OneDrive uses Office 365 (SharePoint Online) to safely store your documents in
Work Smart Save and share documents in the cloud with OneDrive OneDrive for Business is your professional document library. OneDrive uses Office 365 (SharePoint Online) to safely store your documents in
NETWRIX EVENT LOG MANAGER
 NETWRIX EVENT LOG MANAGER ADMINISTRATOR S GUIDE Product Version: 4.0 July/2012. Legal Notice The information in this publication is furnished for information use only, and does not constitute a commitment
NETWRIX EVENT LOG MANAGER ADMINISTRATOR S GUIDE Product Version: 4.0 July/2012. Legal Notice The information in this publication is furnished for information use only, and does not constitute a commitment
System Administration Training Guide. S100 Installation and Site Management
 System Administration Training Guide S100 Installation and Site Management Table of contents System Requirements for Acumatica ERP 4.2... 5 Learning Objects:... 5 Web Browser... 5 Server Software... 5
System Administration Training Guide S100 Installation and Site Management Table of contents System Requirements for Acumatica ERP 4.2... 5 Learning Objects:... 5 Web Browser... 5 Server Software... 5
GREEN HOUSE DATA. E-Mail Services Guide. Built right. Just for you. greenhousedata.com. Green House Data 340 Progress Circle Cheyenne, WY 82007
 GREEN HOUSE DATA Built right. Just for you. E-Mail Services Guide greenhousedata.com 1 Green House Data 340 Progress Circle Cheyenne, WY 82007 Table of Contents Getting Started on Business Class Email
GREEN HOUSE DATA Built right. Just for you. E-Mail Services Guide greenhousedata.com 1 Green House Data 340 Progress Circle Cheyenne, WY 82007 Table of Contents Getting Started on Business Class Email
Okta/Dropbox Active Directory Integration Guide
 Okta/Dropbox Active Directory Integration Guide Okta Inc. 301 Brannan Street, 3rd Floor San Francisco CA, 94107 info@okta.com 1-888- 722-7871 1 Table of Contents 1 Okta Directory Integration Edition for
Okta/Dropbox Active Directory Integration Guide Okta Inc. 301 Brannan Street, 3rd Floor San Francisco CA, 94107 info@okta.com 1-888- 722-7871 1 Table of Contents 1 Okta Directory Integration Edition for
How to install and use the File Sharing Outlook Plugin
 How to install and use the File Sharing Outlook Plugin Thank you for purchasing Green House Data File Sharing. This guide will show you how to install and configure the Outlook Plugin on your desktop.
How to install and use the File Sharing Outlook Plugin Thank you for purchasing Green House Data File Sharing. This guide will show you how to install and configure the Outlook Plugin on your desktop.
Lab SBS14.FARM_Hyper-V - Using SharePoint with Outlook and Lync
 Lab SBS14.FARM_Hyper-V - Using SharePoint with Outlook and Lync Study Chapter 14 in the course book Microsoft SharePoint 2013 Step by Step. Lue kurssikirjan Microsoft SharePoint 2013 Step by Step luku
Lab SBS14.FARM_Hyper-V - Using SharePoint with Outlook and Lync Study Chapter 14 in the course book Microsoft SharePoint 2013 Step by Step. Lue kurssikirjan Microsoft SharePoint 2013 Step by Step luku
FAQs. OneDrive for Business?
 Contents FAQs... 1 From a Web Browser (for PCs and mobile devices)... 1 From the OneDrive for Business Sync Application (for PCs only)... 2 From Office 2013 (for PCs only)... 3 From the OneDrive for Business
Contents FAQs... 1 From a Web Browser (for PCs and mobile devices)... 1 From the OneDrive for Business Sync Application (for PCs only)... 2 From Office 2013 (for PCs only)... 3 From the OneDrive for Business
Citrix Virtual Classroom. Deliver file sharing and synchronization services using Citrix ShareFile. Self-paced exercise guide
 Deliver file sharing and synchronization services using Citrix ShareFile Self-paced exercise guide Table of Contents Table of Contents... 2 Overview... 3 Exercise 1: Setting up a ShareFile Account... 6
Deliver file sharing and synchronization services using Citrix ShareFile Self-paced exercise guide Table of Contents Table of Contents... 2 Overview... 3 Exercise 1: Setting up a ShareFile Account... 6
Colligo Email Manager 6.0. Connected Mode - User Guide
 6.0 Connected Mode - User Guide Contents Colligo Email Manager 1 Benefits 1 Key Features 1 Platforms Supported 1 Installing and Activating Colligo Email Manager 2 Checking for Updates 3 Updating Your License
6.0 Connected Mode - User Guide Contents Colligo Email Manager 1 Benefits 1 Key Features 1 Platforms Supported 1 Installing and Activating Colligo Email Manager 2 Checking for Updates 3 Updating Your License
SharePoint Online Best Practices
 Maximizing 2013 for the Small-Medium Business SharePoint 2013 comes with a fresh interface, new features, and the capabilities SharePoint was founded on. The following are a handful of the great features
Maximizing 2013 for the Small-Medium Business SharePoint 2013 comes with a fresh interface, new features, and the capabilities SharePoint was founded on. The following are a handful of the great features
Microsoft Outlook 2010. Reference Guide for Lotus Notes Users
 Microsoft Outlook 2010 Reference Guide for Lotus Notes Users ContentsWelcome to Office Outlook 2010... 2 Mail... 3 Viewing Messages... 4 Working with Messages... 7 Responding to Messages... 11 Organizing
Microsoft Outlook 2010 Reference Guide for Lotus Notes Users ContentsWelcome to Office Outlook 2010... 2 Mail... 3 Viewing Messages... 4 Working with Messages... 7 Responding to Messages... 11 Organizing
OFFICE 365 TRAINING GUIDE
 OFFICE 365 TRAINING GUIDE Presented by: GATEWAY UNIFIED SCHOOL DISTRICT 4411 MOUNTAIN LAKES BLVD, REDDING, CA 96003 gateway schools.org TABLE OF CONTENTS About Office 365... 2 Signing Into Email/Outlook
OFFICE 365 TRAINING GUIDE Presented by: GATEWAY UNIFIED SCHOOL DISTRICT 4411 MOUNTAIN LAKES BLVD, REDDING, CA 96003 gateway schools.org TABLE OF CONTENTS About Office 365... 2 Signing Into Email/Outlook
Introduction to the EIS Guide
 Introduction to the EIS Guide The AirWatch Enterprise Integration Service (EIS) provides organizations the ability to securely integrate with back-end enterprise systems from either the AirWatch SaaS environment
Introduction to the EIS Guide The AirWatch Enterprise Integration Service (EIS) provides organizations the ability to securely integrate with back-end enterprise systems from either the AirWatch SaaS environment
Learn how to create web enabled (browser) forms in InfoPath 2013 and publish them in SharePoint 2013. InfoPath 2013 Web Enabled (Browser) forms
 Learn how to create web enabled (browser) forms in InfoPath 2013 and publish them in SharePoint 2013. InfoPath 2013 Web Enabled (Browser) forms InfoPath 2013 Web Enabled (Browser) forms Creating Web Enabled
Learn how to create web enabled (browser) forms in InfoPath 2013 and publish them in SharePoint 2013. InfoPath 2013 Web Enabled (Browser) forms InfoPath 2013 Web Enabled (Browser) forms Creating Web Enabled
Getting Started Guide: Getting the most out of your Windows Intune cloud
 Getting Started Guide: Getting the most out of your Windows Intune cloud service Contents Overview... 3 Which Configuration is Right for You?... 3 To Sign up or Sign in?... 4 Getting Started with the Windows
Getting Started Guide: Getting the most out of your Windows Intune cloud service Contents Overview... 3 Which Configuration is Right for You?... 3 To Sign up or Sign in?... 4 Getting Started with the Windows
