Repeater. BrowserStack Local. browserstack.com 1. BrowserStack Local makes a REST call using the user s access key to browserstack.
|
|
|
- Shannon Norris
- 10 years ago
- Views:
Transcription
1 Connection Setup Process makes a REST call using the user s access key to chooses a repeater for establishing a secure connection for Local Testing. The repeater exists within the BrowserStack cloud infrastructure. supplies with the information necessary to establish a connection to the repeater. initiates a connection to the repeater on port, using our custom SSL-encrypted protocol. Note: The repeater cannot directly initiate a connection to. A secure, bi-directional and persistent connection is established between the end user machine and the repeater. We use Secure WebSockets as part of our communication framework. If your enterprise firewall blocks the WebSocket protocol, we fall back to a legacy protocol which is also SSL encrypted, but much slower than WebSockets. For best results, we would recommend that outgoing WebSocket connections be allowed in your firewall. Note: The secure connection is only established up to the user s machine (i.e. ). Neither the repeater nor any BrowserStack machine can directly access your local or internal servers. Only the servers specified for establishing a Local Testing connection, can be accessed through the app.
2 Data Flow Process Remote machines Staging / Internal Server The user sends a request to to start the remote browsing session. identifies a virtual machine from the cloud, and allocates it to the user. The remote browser is started on this virtual machine, and the user will interact with it during their testing session. Requests from the remote browser are first routed to, through the secure connections described in the previous step. then forwards these requests to the local server. All responses are sent back via the same channel. instructs the repeater to connect to the virtual machine in the cloud. The repeater sets up a secure, SSL-encrypted, bi-directional connection with the virtual machine. Once the connection is established, the remote browser on the virtual machine can send requests to the user s local servers.
3 Teardown Process Part : Stopping remote browsing session Remote machines Staging / Internal Server The user sends a request to to end the remote browsing session. instructs the repeater to sever the secure connection to the virtual machine in the cloud. The repeater then severs the connection to and from the virtual machine. takes the virtual machine offline, to securely erase all user information such as browser history, cookies, cache, form data, downloaded files (if any), saved passwords, etc. and restore it to its original, pristine state. This ensures that the virtual machine does not retain absolutely any information pertaining to the user s session. confirms to BrowserStack Local that the virtual machine has been disconnected. closes any open connections it had established to the local servers, ending the Local Testing session. The secure connection between BrowserStack Local and the repeater remains alive, and can be used for another remote testing session on another platform or with another browser.
4 Teardown Process Part : Stopping the local testing connection The user requests a teardown of the Local Testing connection by clicking the disconnect button or by hitting Ctrl + C (terminal). Immediately, severs the secure connection with the repeater. It also deletes all the information it had about the repeater. Thus it cannot set up another connection unless the user initiates it. makes sure the repeater also closes the connection from its end and deletes any information about the concluded Local Testing session. informs about the disconnect request.
5 Recommended Setup BrowserStack Local Proxy is capable of establishing the Local Testing connection through most enterprise proxy servers and firewalls. The app makes two types of outgoing connections which may require special rules in your enterprise proxy and firewall: The proxy server should support WebSockets and the CONNECT method to allow TLS/SSL connections. Type : HTTP(S) requests to www. in the form of web requests (when the website is opened in the user s browser) and AJAX calls (for setting up Local Testing) at port 80 and. Type : Secure WebSocket (WSS) connections to the repeater (*.) at port.
6 Internal Architecture Connection Manager HTTP Server TCP Level Proxy Local / Staging Server Local folder has three main modules: The Connection Manager Responsible for authenticating the user using their access key and establishing a secure connection to the repeater. It makes sure the connection does not drop while the user is testing and closes the connection when the user disconnects. TCP Level Proxy The Local Testing connection is designed to provide a transparent communication channel between the remote web browsers (on BrowserStack infrastructure) and the user s local servers. Unlike traditional HTTP proxies, BrowserStack does not look into the request headers or any user data. enables a TCP level connection to be established between the remote browser and the local servers. This allows for testing of HTTPS websites and technologies such as WebSockets. HTTP Server This applies to local folder testing only. When the user wishes to test local HTML design files, starts a tiny HTTP server within the app on a random unprivileged (>0000) port. This HTTP server has read-only access to the folder mentioned by the user. It loads a file from disk only when requested and does not cache file data. It is shut down when the Local Testing connection is disconnected. This HTTP server is treated as a local server and the aforementioned mechanism takes over.
What is the Barracuda SSL VPN Server Agent?
 The standard communication model for outgoing calls is for the appliance to simply make a direct connection to the destination host. This paradigm does not suit all business needs. The Barracuda SSL VPN
The standard communication model for outgoing calls is for the appliance to simply make a direct connection to the destination host. This paradigm does not suit all business needs. The Barracuda SSL VPN
Re-associating.ica file extension on Vista/Windows 7 machines
 Troubleshooting This page provides answers to common problems you may have encountered when using TENGRAPH Online. Re-associating.ica file extension on Vista/Windows 7 machines There is a known issue that
Troubleshooting This page provides answers to common problems you may have encountered when using TENGRAPH Online. Re-associating.ica file extension on Vista/Windows 7 machines There is a known issue that
Installation and Setup: Setup Wizard Account Information
 Installation and Setup: Setup Wizard Account Information Once the My Secure Backup software has been installed on the end-user machine, the first step in the installation wizard is to configure their account
Installation and Setup: Setup Wizard Account Information Once the My Secure Backup software has been installed on the end-user machine, the first step in the installation wizard is to configure their account
Introduction to Mobile Access Gateway Installation
 Introduction to Mobile Access Gateway Installation This document describes the installation process for the Mobile Access Gateway (MAG), which is an enterprise integration component that provides a secure
Introduction to Mobile Access Gateway Installation This document describes the installation process for the Mobile Access Gateway (MAG), which is an enterprise integration component that provides a secure
PROTECTING DATA IN TRANSIT WITH ENCRYPTION IN M-FILES
 M-FILES CORPORATION PROTECTING DATA IN TRANSIT WITH ENCRYPTION IN M-FILES VERSION 8 24 SEPTEMBER 2014 Page 1 of 8 CONTENTS 1. Overview... 3 2. Encryption of Data in Transit in M-Files... 4 HTTPS... 4 RPC
M-FILES CORPORATION PROTECTING DATA IN TRANSIT WITH ENCRYPTION IN M-FILES VERSION 8 24 SEPTEMBER 2014 Page 1 of 8 CONTENTS 1. Overview... 3 2. Encryption of Data in Transit in M-Files... 4 HTTPS... 4 RPC
Hosted Microsoft Exchange Client Setup & Guide Book
 Hosted Microsoft Exchange Client Setup & Guide Book Section 1 Microsoft Outlook Web Access (OWA) access directions Section 2 Windows Mobile Phone ActiveSync setup & configuration Section 3 - Apple iphone
Hosted Microsoft Exchange Client Setup & Guide Book Section 1 Microsoft Outlook Web Access (OWA) access directions Section 2 Windows Mobile Phone ActiveSync setup & configuration Section 3 - Apple iphone
NovaBACKUP xsp Version 15.0 Upgrade Guide
 NovaBACKUP xsp Version 15.0 Upgrade Guide NovaStor / November 2013 2013 NovaStor, all rights reserved. All trademarks are the property of their respective owners. Features and specifications are subject
NovaBACKUP xsp Version 15.0 Upgrade Guide NovaStor / November 2013 2013 NovaStor, all rights reserved. All trademarks are the property of their respective owners. Features and specifications are subject
WebEx Remote Access White Paper. The CBORD Group, Inc.
 WebEx Remote Access White Paper The CBORD Group, Inc. Document Revision: 1 Last revised: October 30, 2007 Changes are periodically made to the information contained in this document. While every effort
WebEx Remote Access White Paper The CBORD Group, Inc. Document Revision: 1 Last revised: October 30, 2007 Changes are periodically made to the information contained in this document. While every effort
Configuring your email client to connect to your Exchange mailbox
 Configuring your email client to connect to your Exchange mailbox Contents Use Outlook Web Access (OWA) to access your Exchange mailbox... 2 Use Outlook 2003 to connect to your Exchange mailbox... 3 Add
Configuring your email client to connect to your Exchange mailbox Contents Use Outlook Web Access (OWA) to access your Exchange mailbox... 2 Use Outlook 2003 to connect to your Exchange mailbox... 3 Add
TECHNICAL CONDITIONS REGARDING ACCESS TO VP.ONLINE. User guide. vp.online 2011 2011-10-01
 TECHNICAL CONDITIONS REGARDING ACCESS TO VP.ONLINE vp.online 2011 2011-10-01 Contents 1 PROBLEMS SEEING VP.ONLINE... 3 2 BROWSER CONFIGURATION... 6 3 WRITE ACCESS TO DISK DRIVE... 7 4 SESSION TIMEOUT AND
TECHNICAL CONDITIONS REGARDING ACCESS TO VP.ONLINE vp.online 2011 2011-10-01 Contents 1 PROBLEMS SEEING VP.ONLINE... 3 2 BROWSER CONFIGURATION... 6 3 WRITE ACCESS TO DISK DRIVE... 7 4 SESSION TIMEOUT AND
BlackBerry Enterprise Service 10. Version: 10.2. Configuration Guide
 BlackBerry Enterprise Service 10 Version: 10.2 Configuration Guide Published: 2015-02-27 SWD-20150227164548686 Contents 1 Introduction...7 About this guide...8 What is BlackBerry Enterprise Service 10?...9
BlackBerry Enterprise Service 10 Version: 10.2 Configuration Guide Published: 2015-02-27 SWD-20150227164548686 Contents 1 Introduction...7 About this guide...8 What is BlackBerry Enterprise Service 10?...9
CONNECT-TO-CHOP USER GUIDE
 CONNECT-TO-CHOP USER GUIDE VERSION V8 Table of Contents 1 Overview... 3 2 Requirements... 3 2.1 Security... 3 2.2 Computer... 3 2.3 Application... 3 2.3.1 Web Browser... 3 2.3.2 Prerequisites... 3 3 Logon...
CONNECT-TO-CHOP USER GUIDE VERSION V8 Table of Contents 1 Overview... 3 2 Requirements... 3 2.1 Security... 3 2.2 Computer... 3 2.3 Application... 3 2.3.1 Web Browser... 3 2.3.2 Prerequisites... 3 3 Logon...
Architecture and Data Flow Overview. BlackBerry Enterprise Service 10 721-08877-123 Version: 10.2. Quick Reference
 Architecture and Data Flow Overview BlackBerry Enterprise Service 10 721-08877-123 Version: Quick Reference Published: 2013-11-28 SWD-20131128130321045 Contents Key components of BlackBerry Enterprise
Architecture and Data Flow Overview BlackBerry Enterprise Service 10 721-08877-123 Version: Quick Reference Published: 2013-11-28 SWD-20131128130321045 Contents Key components of BlackBerry Enterprise
Wakanda Studio Features
 Wakanda Studio Features Discover the many features in Wakanda Studio. The main features each have their own chapters and other features are documented elsewhere: Wakanda Server Administration Data Browser
Wakanda Studio Features Discover the many features in Wakanda Studio. The main features each have their own chapters and other features are documented elsewhere: Wakanda Server Administration Data Browser
How to Setup an IMAP account in Outlook Express to Connect to Your Arrowmail Mailbox
 How to Setup an IMAP account in Outlook Express to Connect to Your Arrowmail Mailbox Why would you want to use Outlook Express? If you have Microsoft Outlook installed on your PC you should use it, with
How to Setup an IMAP account in Outlook Express to Connect to Your Arrowmail Mailbox Why would you want to use Outlook Express? If you have Microsoft Outlook installed on your PC you should use it, with
Interwise Connect. Working with Reverse Proxy Version 7.x
 Working with Reverse Proxy Version 7.x Table of Contents BACKGROUND...3 Single Sign On (SSO)... 3 Interwise Connect... 3 INTERWISE CONNECT WORKING WITH REVERSE PROXY...4 Architecture... 4 Interwise Web
Working with Reverse Proxy Version 7.x Table of Contents BACKGROUND...3 Single Sign On (SSO)... 3 Interwise Connect... 3 INTERWISE CONNECT WORKING WITH REVERSE PROXY...4 Architecture... 4 Interwise Web
NETASQ SSO Agent Installation and deployment
 NETASQ SSO Agent Installation and deployment Document version: 1.3 Reference: naentno_sso_agent Page 1 / 20 Copyright NETASQ 2013 General information 3 Principle 3 Requirements 3 Active Directory user
NETASQ SSO Agent Installation and deployment Document version: 1.3 Reference: naentno_sso_agent Page 1 / 20 Copyright NETASQ 2013 General information 3 Principle 3 Requirements 3 Active Directory user
Elluminate Live! Access Guide. Page 1 of 7
 This guide is provided to Elluminate Live! users to assist them to make a successful connection to an Elluminate Live! session through a proxy firewall. In some cases settings discussed in this document
This guide is provided to Elluminate Live! users to assist them to make a successful connection to an Elluminate Live! session through a proxy firewall. In some cases settings discussed in this document
Semantic based Web Application Firewall (SWAF V 1.6) Operations and User Manual. Document Version 1.0
 Semantic based Web Application Firewall (SWAF V 1.6) Operations and User Manual Document Version 1.0 Table of Contents 1 SWAF... 4 1.1 SWAF Features... 4 2 Operations and User Manual... 7 2.1 SWAF Administrator
Semantic based Web Application Firewall (SWAF V 1.6) Operations and User Manual Document Version 1.0 Table of Contents 1 SWAF... 4 1.1 SWAF Features... 4 2 Operations and User Manual... 7 2.1 SWAF Administrator
www.mvatcybernet.com PRODUCT VERSION: LYNC SERVER 2010, LYNC SERVER 2013, WINDOWS SERVER 2008
 PRODUCT VERSION: LYNC SERVER 2010, LYNC SERVER 2013, WINDOWS SERVER 2008 With Forefront Threat Management Gateway 2010 now discontinued, we sought a suitable reverse proxy solution that works with Lync
PRODUCT VERSION: LYNC SERVER 2010, LYNC SERVER 2013, WINDOWS SERVER 2008 With Forefront Threat Management Gateway 2010 now discontinued, we sought a suitable reverse proxy solution that works with Lync
How To Understand The Architecture Of An Ulteo Virtual Desktop Server Farm
 ULTEO OPEN VIRTUAL DESKTOP V4.0.2 ARCHITECTURE OVERVIEW Contents 1 Introduction 2 2 Servers Roles 3 2.1 Session Manager................................. 3 2.2 Application Server................................
ULTEO OPEN VIRTUAL DESKTOP V4.0.2 ARCHITECTURE OVERVIEW Contents 1 Introduction 2 2 Servers Roles 3 2.1 Session Manager................................. 3 2.2 Application Server................................
Initial Setup of Microsoft Outlook 2011 with IMAP for OS X Lion
 Initial Setup of Microsoft Outlook Concept This document describes the procedures for setting up the Microsoft Outlook email client to download messages from Google Mail using Internet Message Access Protocol
Initial Setup of Microsoft Outlook Concept This document describes the procedures for setting up the Microsoft Outlook email client to download messages from Google Mail using Internet Message Access Protocol
Hosted Microsoft Exchange Client Setup & Guide Book
 Hosted Microsoft Exchange Client Setup & Guide Book Section 1 Microsoft Outlook Web Access (OWA) access directions Section 2 Windows 10 Mail App setup & configuration Section 3 Windows Mobile Phone ActiveSync
Hosted Microsoft Exchange Client Setup & Guide Book Section 1 Microsoft Outlook Web Access (OWA) access directions Section 2 Windows 10 Mail App setup & configuration Section 3 Windows Mobile Phone ActiveSync
Laptop Backup - Administrator Guide (Windows)
 Laptop Backup - Administrator Guide (Windows) Page 1 of 86 Page 2 of 86 Laptop Backup - Administrator Guide (Windows) TABLE OF CONTENTS OVERVIEW PREPARE COMMCELL SETUP FIREWALL USING PROXY SETUP FIREWALL
Laptop Backup - Administrator Guide (Windows) Page 1 of 86 Page 2 of 86 Laptop Backup - Administrator Guide (Windows) TABLE OF CONTENTS OVERVIEW PREPARE COMMCELL SETUP FIREWALL USING PROXY SETUP FIREWALL
Step into the Future: HTML5 and its Impact on SSL VPNs
 Step into the Future: HTML5 and its Impact on SSL VPNs Aidan Gogarty HOB, Inc. Session ID: SPO - 302 Session Classification: General Interest What this is all about. All about HTML5 3 useful components
Step into the Future: HTML5 and its Impact on SSL VPNs Aidan Gogarty HOB, Inc. Session ID: SPO - 302 Session Classification: General Interest What this is all about. All about HTML5 3 useful components
Contents Notice to Users
 Web Remote Access Contents Web Remote Access Overview... 1 Setting Up Web Remote Access... 2 Editing Web Remote Access Settings... 5 Web Remote Access Log... 7 Accessing Your Home Network Using Web Remote
Web Remote Access Contents Web Remote Access Overview... 1 Setting Up Web Remote Access... 2 Editing Web Remote Access Settings... 5 Web Remote Access Log... 7 Accessing Your Home Network Using Web Remote
http://alice.teaparty.wonderland.com:23054/dormouse/bio.htm
 Client/Server paradigm As we know, the World Wide Web is accessed thru the use of a Web Browser, more technically known as a Web Client. 1 A Web Client makes requests of a Web Server 2, which is software
Client/Server paradigm As we know, the World Wide Web is accessed thru the use of a Web Browser, more technically known as a Web Client. 1 A Web Client makes requests of a Web Server 2, which is software
Web Remote Access. User Guide
 Web Remote Access User Guide Notice to Users 2005 2Wire, Inc. All rights reserved. This manual in whole or in part, may not be reproduced, translated, or reduced to any machine-readable form without prior
Web Remote Access User Guide Notice to Users 2005 2Wire, Inc. All rights reserved. This manual in whole or in part, may not be reproduced, translated, or reduced to any machine-readable form without prior
QUANTIFY INSTALLATION GUIDE
 QUANTIFY INSTALLATION GUIDE Thank you for putting your trust in Avontus! This guide reviews the process of installing Quantify software. For Quantify system requirement information, please refer to the
QUANTIFY INSTALLATION GUIDE Thank you for putting your trust in Avontus! This guide reviews the process of installing Quantify software. For Quantify system requirement information, please refer to the
Quick Note 026. Using the firewall of a Digi TransPort to redirect HTTP Traffic to a proxy server. Digi International Technical Support December 2011
 Quick Note 026 Using the firewall of a Digi TransPort to redirect HTTP Traffic to a proxy server Digi International Technical Support December 2011 Contents 1 Introduction... 3 1.1 Outline... 3 1.2 Assumptions...
Quick Note 026 Using the firewall of a Digi TransPort to redirect HTTP Traffic to a proxy server Digi International Technical Support December 2011 Contents 1 Introduction... 3 1.1 Outline... 3 1.2 Assumptions...
Elluminate Live! Access Guide. Page 1 of 7
 This guide is provided to Elluminate Live! users to assist them to make a successful connection to an Elluminate Live! session through a proxy firewall. In some cases settings discussed in this document
This guide is provided to Elluminate Live! users to assist them to make a successful connection to an Elluminate Live! session through a proxy firewall. In some cases settings discussed in this document
Aspera Connect User Guide
 Aspera Connect User Guide Mac OS X 10.4/10.5 Browser: Firefox 2+, Safari 2+ Version 2.2 Chapter 1 Chapter 2 Chapter 3 Appendix Introduction Setting Up 2.1 Installation 2.2 Configure the Network Environment
Aspera Connect User Guide Mac OS X 10.4/10.5 Browser: Firefox 2+, Safari 2+ Version 2.2 Chapter 1 Chapter 2 Chapter 3 Appendix Introduction Setting Up 2.1 Installation 2.2 Configure the Network Environment
ReadyNAS Replicate. Software Reference Manual. 350 East Plumeria Drive San Jose, CA 95134 USA. November 2010 202-10727-01 v1.0
 ReadyNAS Replicate Software Reference Manual 350 East Plumeria Drive San Jose, CA 95134 USA November 2010 202-10727-01 v1.0 2010 NETGEAR, Inc. All rights reserved. No part of this publication may be reproduced,
ReadyNAS Replicate Software Reference Manual 350 East Plumeria Drive San Jose, CA 95134 USA November 2010 202-10727-01 v1.0 2010 NETGEAR, Inc. All rights reserved. No part of this publication may be reproduced,
Campus VPN. Version 1.0 September 22, 2008
 Campus VPN Version 1.0 September 22, 2008 University of North Texas 1 9/22/2008 Introduction This is a guide on the different ways to connect to the University of North Texas Campus VPN. There are several
Campus VPN Version 1.0 September 22, 2008 University of North Texas 1 9/22/2008 Introduction This is a guide on the different ways to connect to the University of North Texas Campus VPN. There are several
Configuring Outlook 2013 For IMAP Connections
 Configuring Outlook 2013 For IMAP Connections VERSION 1.0 1 P a g e U A C o n n e c t C o n f i g u r i n g O u t l o o k 2013 f o r I M A P 12/2013 Configuring Outlook 2013 for IMAP Connections Overview
Configuring Outlook 2013 For IMAP Connections VERSION 1.0 1 P a g e U A C o n n e c t C o n f i g u r i n g O u t l o o k 2013 f o r I M A P 12/2013 Configuring Outlook 2013 for IMAP Connections Overview
How to configure Enterprise Cloud
 How to configure Enterprise Cloud Note: Before configuring Enterprise Cloud on GajShield, make sure you have Cloud license. Important: Below configuration can be used in all type of browsing mode. When
How to configure Enterprise Cloud Note: Before configuring Enterprise Cloud on GajShield, make sure you have Cloud license. Important: Below configuration can be used in all type of browsing mode. When
BlackBerry Enterprise Service 10. Secure Work Space for ios and Android Version: 10.1.1. Security Note
 BlackBerry Enterprise Service 10 Secure Work Space for ios and Android Version: 10.1.1 Security Note Published: 2013-06-21 SWD-20130621110651069 Contents 1 About this guide...4 2 What is BlackBerry Enterprise
BlackBerry Enterprise Service 10 Secure Work Space for ios and Android Version: 10.1.1 Security Note Published: 2013-06-21 SWD-20130621110651069 Contents 1 About this guide...4 2 What is BlackBerry Enterprise
GoToMyPC Corporate Advanced Firewall Support Features
 F A C T S H E E T GoToMyPC Corporate Advanced Firewall Support Features Citrix GoToMyPC Corporate features Citrix Online s advanced connectivity technology. We support all of the common firewall and proxy
F A C T S H E E T GoToMyPC Corporate Advanced Firewall Support Features Citrix GoToMyPC Corporate features Citrix Online s advanced connectivity technology. We support all of the common firewall and proxy
DEPLOYMENT GUIDE Version 1.2. Deploying the BIG-IP system v10 with Microsoft Exchange Outlook Web Access 2007
 DEPLOYMENT GUIDE Version 1.2 Deploying the BIG-IP system v10 with Microsoft Exchange Outlook Web Access 2007 Table of Contents Table of Contents Deploying the BIG-IP system v10 with Microsoft Outlook Web
DEPLOYMENT GUIDE Version 1.2 Deploying the BIG-IP system v10 with Microsoft Exchange Outlook Web Access 2007 Table of Contents Table of Contents Deploying the BIG-IP system v10 with Microsoft Outlook Web
ReadyNAS Remote White Paper. NETGEAR May 2010
 ReadyNAS Remote White Paper NETGEAR May 2010 Table of Contents Overview... 3 Architecture... 3 Security... 4 Remote Firewall... 5 Performance... 5 Overview ReadyNAS Remote is a software application that
ReadyNAS Remote White Paper NETGEAR May 2010 Table of Contents Overview... 3 Architecture... 3 Security... 4 Remote Firewall... 5 Performance... 5 Overview ReadyNAS Remote is a software application that
Business mail 1 MS OUTLOOK CONFIGURATION... 2
 Business mail Instructions for configuration of Outlook, 2007, 2010, 2013 and mobile devices CONTENT 1 MS OUTLOOK CONFIGURATION... 2 1.1 Outlook 2007, 2010 and 2013 adding new exchange account, automatic
Business mail Instructions for configuration of Outlook, 2007, 2010, 2013 and mobile devices CONTENT 1 MS OUTLOOK CONFIGURATION... 2 1.1 Outlook 2007, 2010 and 2013 adding new exchange account, automatic
WhatsUp Gold v16.3 Installation and Configuration Guide
 WhatsUp Gold v16.3 Installation and Configuration Guide Contents Installing and Configuring WhatsUp Gold using WhatsUp Setup Installation Overview... 1 Overview... 1 Security considerations... 2 Standard
WhatsUp Gold v16.3 Installation and Configuration Guide Contents Installing and Configuring WhatsUp Gold using WhatsUp Setup Installation Overview... 1 Overview... 1 Security considerations... 2 Standard
Chapter 6 Virtual Private Networking Using SSL Connections
 Chapter 6 Virtual Private Networking Using SSL Connections The FVS336G ProSafe Dual WAN Gigabit Firewall with SSL & IPsec VPN provides a hardwarebased SSL VPN solution designed specifically to provide
Chapter 6 Virtual Private Networking Using SSL Connections The FVS336G ProSafe Dual WAN Gigabit Firewall with SSL & IPsec VPN provides a hardwarebased SSL VPN solution designed specifically to provide
G-Lock EasyMail7. Admin Guide. Client-Server Email Marketing Solution for Windows. Copyright G-Lock Software. All Rights Reserved.
 G-Lock EasyMail7 Client-Server Email Marketing Solution for Windows Admin Guide Copyright G-Lock Software. All Rights Reserved. 1 Table of Contents This document is your admin guide for G-Lock EasyMail7
G-Lock EasyMail7 Client-Server Email Marketing Solution for Windows Admin Guide Copyright G-Lock Software. All Rights Reserved. 1 Table of Contents This document is your admin guide for G-Lock EasyMail7
How To Set Up Dataprotect
 How To Set Up Dataprotect This document will show you how to install and configure your computer for a Typical installation. If you have questions about configuring a Custom installation please contact
How To Set Up Dataprotect This document will show you how to install and configure your computer for a Typical installation. If you have questions about configuring a Custom installation please contact
Millbeck Communications. Secure Remote Access Service. Internet VPN Access to N3. VPN Client Set Up Guide Version 6.0
 Millbeck Communications Secure Remote Access Service Internet VPN Access to N3 VPN Client Set Up Guide Version 6.0 COPYRIGHT NOTICE Copyright 2013 Millbeck Communications Ltd. All Rights Reserved. Introduction
Millbeck Communications Secure Remote Access Service Internet VPN Access to N3 VPN Client Set Up Guide Version 6.0 COPYRIGHT NOTICE Copyright 2013 Millbeck Communications Ltd. All Rights Reserved. Introduction
Sync Security and Privacy Brief
 Introduction Security and privacy are two of the leading issues for users when transferring important files. Keeping data on-premises makes business and IT leaders feel more secure, but comes with technical
Introduction Security and privacy are two of the leading issues for users when transferring important files. Keeping data on-premises makes business and IT leaders feel more secure, but comes with technical
Managing Multi-Hypervisor Environments with vcenter Server
 Managing Multi-Hypervisor Environments with vcenter Server vcenter Server 5.1 vcenter Multi-Hypervisor Manager 1.0 This document supports the version of each product listed and supports all subsequent
Managing Multi-Hypervisor Environments with vcenter Server vcenter Server 5.1 vcenter Multi-Hypervisor Manager 1.0 This document supports the version of each product listed and supports all subsequent
Introduction to the AirWatch Cloud Connector (ACC) Guide
 Introduction to the AirWatch Cloud Connector (ACC) Guide The AirWatch Cloud Connector (ACC) provides organizations the ability to integrate AirWatch with their back-end enterprise systems. This document
Introduction to the AirWatch Cloud Connector (ACC) Guide The AirWatch Cloud Connector (ACC) provides organizations the ability to integrate AirWatch with their back-end enterprise systems. This document
for Networks Installation Guide for the application on the server July 2014 (GUIDE 2) Lucid Rapid Version 6.05-N and later
 for Networks Installation Guide for the application on the server July 2014 (GUIDE 2) Lucid Rapid Version 6.05-N and later Copyright 2014, Lucid Innovations Limited. All Rights Reserved Lucid Research
for Networks Installation Guide for the application on the server July 2014 (GUIDE 2) Lucid Rapid Version 6.05-N and later Copyright 2014, Lucid Innovations Limited. All Rights Reserved Lucid Research
for Networks Installation Guide for the application on the server August 2014 (GUIDE 2) Lucid Exact Version 1.7-N and later
 for Networks Installation Guide for the application on the server August 2014 (GUIDE 2) Lucid Exact Version 1.7-N and later Copyright 2014, Lucid Innovations Limited. All Rights Reserved Lucid Research
for Networks Installation Guide for the application on the server August 2014 (GUIDE 2) Lucid Exact Version 1.7-N and later Copyright 2014, Lucid Innovations Limited. All Rights Reserved Lucid Research
Outlook Express POP Instructions - Bloomsburg University Students
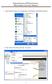 1. Open Outlook Express by clicking Start, All Programs, and Outlook Express. 2. Click on the Tools menu and click Accounts. 1 3. Click on Add Mail 4. Enter your name and click Next. 2 5. Enter your full
1. Open Outlook Express by clicking Start, All Programs, and Outlook Express. 2. Click on the Tools menu and click Accounts. 1 3. Click on Add Mail 4. Enter your name and click Next. 2 5. Enter your full
Secure Transfers. Contents. SSL-Based Services: HTTPS and FTPS 2. Generating A Certificate 2. Creating A Self-Signed Certificate 3
 Contents SSL-Based Services: HTTPS and FTPS 2 Generating A Certificate 2 Creating A Self-Signed Certificate 3 Obtaining A Signed Certificate 4 Enabling Secure Services 5 A Note About Ports 5 Connecting
Contents SSL-Based Services: HTTPS and FTPS 2 Generating A Certificate 2 Creating A Self-Signed Certificate 3 Obtaining A Signed Certificate 4 Enabling Secure Services 5 A Note About Ports 5 Connecting
User Guide. Time Warner Cable Business Class Cloud Solutions Control Panel. Hosted Microsoft Exchange 2007 Hosted Microsoft SharePoint 2007
 Chapter Title Time Warner Cable Business Class Cloud Solutions Control Panel User Guide Hosted Microsoft Exchange 2007 Hosted Microsoft SharePoint 2007 Version 1.1 Table of Contents Table of Contents...
Chapter Title Time Warner Cable Business Class Cloud Solutions Control Panel User Guide Hosted Microsoft Exchange 2007 Hosted Microsoft SharePoint 2007 Version 1.1 Table of Contents Table of Contents...
This presentation covers virtual application shared services supplied with IBM Workload Deployer version 3.1.
 This presentation covers virtual application shared services supplied with IBM Workload Deployer version 3.1. WD31_VirtualApplicationSharedServices.ppt Page 1 of 29 This presentation covers the shared
This presentation covers virtual application shared services supplied with IBM Workload Deployer version 3.1. WD31_VirtualApplicationSharedServices.ppt Page 1 of 29 This presentation covers the shared
Configuring Outlook 2002-2003 for IMAP. Creating a New IMAP Account. Modify an Existing Account
 mai l. uml. edu mai l. uml. edu Configuring Outlook 2002-2003 for IMAP This document will show you how to setup or modify Outlook 2003 as an IMAP client. It is intended for Faculty and Staff whose mailboxes
mai l. uml. edu mai l. uml. edu Configuring Outlook 2002-2003 for IMAP This document will show you how to setup or modify Outlook 2003 as an IMAP client. It is intended for Faculty and Staff whose mailboxes
Using Remote Web Workplace Version 1.01
 Using Remote Web Workplace Version 1.01 Remote web workplace allows you to access your Windows XP desktop through Small Business Server 2003 from a web browser. 1. Connect to the Internet in your remote
Using Remote Web Workplace Version 1.01 Remote web workplace allows you to access your Windows XP desktop through Small Business Server 2003 from a web browser. 1. Connect to the Internet in your remote
NovaBACKUP xsp Version 12.2 Upgrade Guide
 NovaBACKUP xsp Version 12.2 Upgrade Guide NovaStor / August 2011 Rev 20110815 2011 NovaStor, all rights reserved. All trademarks are the property of their respective owners. Features and specifications
NovaBACKUP xsp Version 12.2 Upgrade Guide NovaStor / August 2011 Rev 20110815 2011 NovaStor, all rights reserved. All trademarks are the property of their respective owners. Features and specifications
SSL User Authentication with the HTTP Security Server
 SSL User Authentication with the HTTP Security Server Authored By: Lewis Colascione/Udi Ben-Reuven Date: April 2000 Purpose: To describe and document how to configure SSL User Authentication Credits: Version:
SSL User Authentication with the HTTP Security Server Authored By: Lewis Colascione/Udi Ben-Reuven Date: April 2000 Purpose: To describe and document how to configure SSL User Authentication Credits: Version:
Customer Tips. Xerox Network Scanning TWAIN Configuration for the WorkCentre 7328/7335/7345. for the user. Purpose. Background
 Xerox Multifunction Devices Customer Tips dc07cc0432 October 19, 2007 This document applies to these Xerox products: X WC 7328/7335/7345 for the user Xerox Network Scanning TWAIN Configuration for the
Xerox Multifunction Devices Customer Tips dc07cc0432 October 19, 2007 This document applies to these Xerox products: X WC 7328/7335/7345 for the user Xerox Network Scanning TWAIN Configuration for the
SSL Enforcer Documentation
 SSL Enforcer Documentation Introduction Install and Uninstall Getting Started Main Settings Options Log Introduction Today a vast majority of Internet activities like social networking, streaming videos,
SSL Enforcer Documentation Introduction Install and Uninstall Getting Started Main Settings Options Log Introduction Today a vast majority of Internet activities like social networking, streaming videos,
Step-by-Step Setup Guide Wireless File Transmitter FTP Mode
 EOS Step-by-Step Setup Guide Wireless File Transmitter FTP Mode Infrastructure Setup Windows 7 2012 Canon U.S.A., Inc. All Rights Reserved. Reproduction in whole or in part without permission is prohibited.
EOS Step-by-Step Setup Guide Wireless File Transmitter FTP Mode Infrastructure Setup Windows 7 2012 Canon U.S.A., Inc. All Rights Reserved. Reproduction in whole or in part without permission is prohibited.
Network Configuration Settings
 Network Configuration Settings Many small businesses already have an existing firewall device for their local network when they purchase Microsoft Windows Small Business Server 2003. Often, these devices
Network Configuration Settings Many small businesses already have an existing firewall device for their local network when they purchase Microsoft Windows Small Business Server 2003. Often, these devices
Accessing the FTP Server - User Manual
 CENTRAL BANK OF CYPRUS Accessing the FTP Server - User Manual IT Department, CENTRAL BANK OF CYPRUS TABLE OF CONTENTS 1 EXECUTIVE SUMMARY... 1 1.1 AUDIENCE... 1 1.2 SCOPE... 1 2 CHANGES FROM THE OLD FTP
CENTRAL BANK OF CYPRUS Accessing the FTP Server - User Manual IT Department, CENTRAL BANK OF CYPRUS TABLE OF CONTENTS 1 EXECUTIVE SUMMARY... 1 1.1 AUDIENCE... 1 1.2 SCOPE... 1 2 CHANGES FROM THE OLD FTP
Load Balancing and Sessions. C. Kopparapu, Load Balancing Servers, Firewalls and Caches. Wiley, 2002.
 Load Balancing and Sessions C. Kopparapu, Load Balancing Servers, Firewalls and Caches. Wiley, 2002. Scalability multiple servers Availability server fails Manageability Goals do not route to it take servers
Load Balancing and Sessions C. Kopparapu, Load Balancing Servers, Firewalls and Caches. Wiley, 2002. Scalability multiple servers Availability server fails Manageability Goals do not route to it take servers
Access Your Cisco Smart Storage Remotely Via WebDAV
 Application Note Access Your Cisco Smart Storage Remotely Via WebDAV WebDAV (Web-based Distributed Authoring and Versioning), is a set of extensions to the HTTP(S) protocol that allows a web server to
Application Note Access Your Cisco Smart Storage Remotely Via WebDAV WebDAV (Web-based Distributed Authoring and Versioning), is a set of extensions to the HTTP(S) protocol that allows a web server to
Jetico Central Manager. Administrator Guide
 Jetico Central Manager Administrator Guide Introduction Deployment, updating and control of client software can be a time consuming and expensive task for companies and organizations because of the number
Jetico Central Manager Administrator Guide Introduction Deployment, updating and control of client software can be a time consuming and expensive task for companies and organizations because of the number
Remote Desktop Gateway. Accessing a Campus Managed Device (Windows Only) from home.
 Remote Desktop Gateway Accessing a Campus Managed Device (Windows Only) from home. Contents Introduction... 2 Quick Reference... 2 Gateway Setup - Windows Desktop... 3 Gateway Setup Windows App... 4 Gateway
Remote Desktop Gateway Accessing a Campus Managed Device (Windows Only) from home. Contents Introduction... 2 Quick Reference... 2 Gateway Setup - Windows Desktop... 3 Gateway Setup Windows App... 4 Gateway
How To Test Your Web Site On Wapt On A Pc Or Mac Or Mac (Or Mac) On A Mac Or Ipad Or Ipa (Or Ipa) On Pc Or Ipam (Or Pc Or Pc) On An Ip
 Load testing with WAPT: Quick Start Guide This document describes step by step how to create a simple typical test for a web application, execute it and interpret the results. A brief insight is provided
Load testing with WAPT: Quick Start Guide This document describes step by step how to create a simple typical test for a web application, execute it and interpret the results. A brief insight is provided
Collax E-Mail Archive
 Collax E-Mail Archive Howto This howto describes how a Collax server can easily be set up as an e-mail archive in order to enable team members to access their own e-mail archive. Additionally, auditor
Collax E-Mail Archive Howto This howto describes how a Collax server can easily be set up as an e-mail archive in order to enable team members to access their own e-mail archive. Additionally, auditor
Web Application Firewall
 Web Application Firewall Getting Started Guide August 3, 2015 Copyright 2014-2015 by Qualys, Inc. All Rights Reserved. Qualys and the Qualys logo are registered trademarks of Qualys, Inc. All other trademarks
Web Application Firewall Getting Started Guide August 3, 2015 Copyright 2014-2015 by Qualys, Inc. All Rights Reserved. Qualys and the Qualys logo are registered trademarks of Qualys, Inc. All other trademarks
How-to setup a proxy in the cloud
 This article describes the setup of a proxy-server in a cloud. You can use a proxy like this from everywhere through the internet. Reasons to do this could be: Your internet access is filtered but you
This article describes the setup of a proxy-server in a cloud. You can use a proxy like this from everywhere through the internet. Reasons to do this could be: Your internet access is filtered but you
Protected Trust Setup Guide for Brother MFC Devices
 Protected Trust Setup Guide for Brother MFC Devices Summary Protected Trust Email Encryption is a versatile secure email service. This guide details three use cases between Protected Trust and your Brother
Protected Trust Setup Guide for Brother MFC Devices Summary Protected Trust Email Encryption is a versatile secure email service. This guide details three use cases between Protected Trust and your Brother
Stealth OpenVPN and SSH Tunneling Over HTTPS
 Stealth OpenVPN and SSH Tunneling Over HTTPS Contents Tunneling OpenVPN and SSH via HTTPS for Windows,MAC and Linux... 1 Benefits of HTTPS Tunneling:... 2 Pre-Requisites:... 3 Part A: Step by Step Instructions
Stealth OpenVPN and SSH Tunneling Over HTTPS Contents Tunneling OpenVPN and SSH via HTTPS for Windows,MAC and Linux... 1 Benefits of HTTPS Tunneling:... 2 Pre-Requisites:... 3 Part A: Step by Step Instructions
Copyright 2013, 3CX Ltd. http://www.3cx.com E-mail: [email protected]
 Manual Copyright 2013, 3CX Ltd. http://www.3cx.com E-mail: [email protected] Information in this document is subject to change without notice. Companies names and data used in examples herein are fictitious
Manual Copyright 2013, 3CX Ltd. http://www.3cx.com E-mail: [email protected] Information in this document is subject to change without notice. Companies names and data used in examples herein are fictitious
Barracuda Link Balancer Administrator s Guide
 Barracuda Link Balancer Administrator s Guide Version 1.0 Barracuda Networks Inc. 3175 S. Winchester Blvd. Campbell, CA 95008 http://www.barracuda.com Copyright Notice Copyright 2008, Barracuda Networks
Barracuda Link Balancer Administrator s Guide Version 1.0 Barracuda Networks Inc. 3175 S. Winchester Blvd. Campbell, CA 95008 http://www.barracuda.com Copyright Notice Copyright 2008, Barracuda Networks
Webmail Using the Hush Encryption Engine
 Webmail Using the Hush Encryption Engine Introduction...2 Terms in this Document...2 Requirements...3 Architecture...3 Authentication...4 The Role of the Session...4 Steps...5 Private Key Retrieval...5
Webmail Using the Hush Encryption Engine Introduction...2 Terms in this Document...2 Requirements...3 Architecture...3 Authentication...4 The Role of the Session...4 Steps...5 Private Key Retrieval...5
User Manual. Onsight Management Suite Version 5.1. Another Innovation by Librestream
 User Manual Onsight Management Suite Version 5.1 Another Innovation by Librestream Doc #: 400075-06 May 2012 Information in this document is subject to change without notice. Reproduction in any manner
User Manual Onsight Management Suite Version 5.1 Another Innovation by Librestream Doc #: 400075-06 May 2012 Information in this document is subject to change without notice. Reproduction in any manner
Deployment for Network Proxy in Simpana Environment
 Deployment for Network Proxy in Simpana Environment There are multiple ways you can use the proxy for Simpana communication. 1. Use proxy to communicate for CommNet DataCenter CS will also have CommNet
Deployment for Network Proxy in Simpana Environment There are multiple ways you can use the proxy for Simpana communication. 1. Use proxy to communicate for CommNet DataCenter CS will also have CommNet
ShadowControl ShadowStream
 ShadowControl ShadowStream Revision 1.3 4/12/2012 Table of Contents Introduction... 3 Download ShadowStream Server... 3 Installation... 4 Configuration... 5 Creating Users... 6 Testing the User Rights...
ShadowControl ShadowStream Revision 1.3 4/12/2012 Table of Contents Introduction... 3 Download ShadowStream Server... 3 Installation... 4 Configuration... 5 Creating Users... 6 Testing the User Rights...
RDM+ Desktop for Windows Getting Started Guide
 RDM+ Remote Desktop for Mobiles RDM+ Desktop for Windows Getting Started Guide Introduction... 3 1. Installing RDM+ Desktop on a computer... 3 2. Preparing for remote connection... 4 3. RDM+ Desktop window...
RDM+ Remote Desktop for Mobiles RDM+ Desktop for Windows Getting Started Guide Introduction... 3 1. Installing RDM+ Desktop on a computer... 3 2. Preparing for remote connection... 4 3. RDM+ Desktop window...
Tenrox. Single Sign-On (SSO) Setup Guide. January, 2012. 2012 Tenrox. All rights reserved.
 Tenrox Single Sign-On (SSO) Setup Guide January, 2012 2012 Tenrox. All rights reserved. About this Guide This guide provides a high-level technical overview of the Tenrox Single Sign-On (SSO) architecture,
Tenrox Single Sign-On (SSO) Setup Guide January, 2012 2012 Tenrox. All rights reserved. About this Guide This guide provides a high-level technical overview of the Tenrox Single Sign-On (SSO) architecture,
MaaS360 Mobile Enterprise Gateway
 MaaS360 Mobile Enterprise Gateway Administrator Guide Copyright 2013 Fiberlink Communications Corporation. All rights reserved. Information in this document is subject to change without notice. The software
MaaS360 Mobile Enterprise Gateway Administrator Guide Copyright 2013 Fiberlink Communications Corporation. All rights reserved. Information in this document is subject to change without notice. The software
Web File Management with SSH Secure Shell 3.2.3
 Web File Management with SSH Secure Shell 3.2.3 June 2003 Information Technologies Copyright 2003 University of Delaware. Permission to copy without fee all or part of this material is granted provided
Web File Management with SSH Secure Shell 3.2.3 June 2003 Information Technologies Copyright 2003 University of Delaware. Permission to copy without fee all or part of this material is granted provided
State Health Repository Tool (SHRT) Testing Instructions
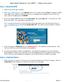 Step 1 - Access the SHRT State Health Repository Tool (SHRT) Testing Instructions 1. Close out any other open browsers. 2. Enter https://shrt.adp.com in the Address field of your browser and press Enter
Step 1 - Access the SHRT State Health Repository Tool (SHRT) Testing Instructions 1. Close out any other open browsers. 2. Enter https://shrt.adp.com in the Address field of your browser and press Enter
Experian Secure Transport Service
 Experian Secure Transport Service Secure Transport Overview In an effort to provide higher levels of data protection and standardize our file transfer processes, Experian will be utilizing the Secure Transport
Experian Secure Transport Service Secure Transport Overview In an effort to provide higher levels of data protection and standardize our file transfer processes, Experian will be utilizing the Secure Transport
VMware Software Manager - Download Service User's Guide
 VMware Software Manager - Download Service User's Guide VMware Software Manager 1.1 This document supports the version of each product listed and supports all subsequent versions until the document is
VMware Software Manager - Download Service User's Guide VMware Software Manager 1.1 This document supports the version of each product listed and supports all subsequent versions until the document is
Setting Up Scan to SMB on TaskALFA series MFP s.
 Setting Up Scan to SMB on TaskALFA series MFP s. There are three steps necessary to set up a new Scan to SMB function button on the TaskALFA series color MFP. 1. A folder must be created on the PC and
Setting Up Scan to SMB on TaskALFA series MFP s. There are three steps necessary to set up a new Scan to SMB function button on the TaskALFA series color MFP. 1. A folder must be created on the PC and
MaaS360 Mobile Enterprise Gateway
 MaaS360 Mobile Enterprise Gateway Administrator Guide Copyright 2014 Fiberlink, an IBM Company. All rights reserved. Information in this document is subject to change without notice. The software described
MaaS360 Mobile Enterprise Gateway Administrator Guide Copyright 2014 Fiberlink, an IBM Company. All rights reserved. Information in this document is subject to change without notice. The software described
GV-iView HD V1 for ipad
 GV-iView HD V1 for ipad Article ID: GV10-11-03-07 Release Date: 03/07/2011 GV-iView HD V1 function is introduced to support ipad for the mobile surveillance application. System Requirements Handheld Device
GV-iView HD V1 for ipad Article ID: GV10-11-03-07 Release Date: 03/07/2011 GV-iView HD V1 function is introduced to support ipad for the mobile surveillance application. System Requirements Handheld Device
Introduction to the Mobile Access Gateway
 Introduction to the Mobile Access Gateway This document provides an overview of the AirWatch Mobile Access Gateway (MAG) architecture and security and explains how to enable MAG functionality in the AirWatch
Introduction to the Mobile Access Gateway This document provides an overview of the AirWatch Mobile Access Gateway (MAG) architecture and security and explains how to enable MAG functionality in the AirWatch
Xopero Backup Build your private cloud backup environment. Getting started
 Xopero Backup Build your private cloud backup environment Getting started 07.05.2015 List of contents Introduction... 2 Get Management Center... 2 Setup Xopero to work... 3 Change the admin password...
Xopero Backup Build your private cloud backup environment Getting started 07.05.2015 List of contents Introduction... 2 Get Management Center... 2 Setup Xopero to work... 3 Change the admin password...
Sharp Remote Device Manager (SRDM) Server Software Setup Guide
 Sharp Remote Device Manager (SRDM) Server Software Setup Guide This Guide explains how to install the software which is required in order to use Sharp Remote Device Manager (SRDM). SRDM is a web-based
Sharp Remote Device Manager (SRDM) Server Software Setup Guide This Guide explains how to install the software which is required in order to use Sharp Remote Device Manager (SRDM). SRDM is a web-based
NETASQ MIGRATING FROM V8 TO V9
 UTM Firewall version 9 NETASQ MIGRATING FROM V8 TO V9 Document version: 1.1 Reference: naentno_migration-v8-to-v9 INTRODUCTION 3 Upgrading on a production site... 3 Compatibility... 3 Requirements... 4
UTM Firewall version 9 NETASQ MIGRATING FROM V8 TO V9 Document version: 1.1 Reference: naentno_migration-v8-to-v9 INTRODUCTION 3 Upgrading on a production site... 3 Compatibility... 3 Requirements... 4
BROWSER AND SYSTEM REQUIREMENTS
 BROWSER AND SYSTEM REQUIREMENTS Minimum and Recommended System Requirements To ensure that CSIU Student Information System performs seamlessly, please adhere to the requirements listed in the chart below:
BROWSER AND SYSTEM REQUIREMENTS Minimum and Recommended System Requirements To ensure that CSIU Student Information System performs seamlessly, please adhere to the requirements listed in the chart below:
efolder BDR for Veeam Cloud Connection Guide
 efolder BDR for Veeam Cloud Connection Guide Setup Connect Preload Data uh6 efolder BDR Guide for Veeam Page 1 of 36 INTRODUCTION Thank you for choosing the efolder Cloud for Veeam. Using the efolder Cloud
efolder BDR for Veeam Cloud Connection Guide Setup Connect Preload Data uh6 efolder BDR Guide for Veeam Page 1 of 36 INTRODUCTION Thank you for choosing the efolder Cloud for Veeam. Using the efolder Cloud
TELSTRA BUSINESS MAIL QUICK REFERENCE GUIDE
 1.1 Introduction 01 1.2 The Checklist 02 1.3 Business Mail Requirements 03 1.4 Downloading & Installing Outlook 2003 04 BEFORE YOU START 1.1 INTRODUCTION 1.1.1 Who this Guide is For 1.1.2 What s in this
1.1 Introduction 01 1.2 The Checklist 02 1.3 Business Mail Requirements 03 1.4 Downloading & Installing Outlook 2003 04 BEFORE YOU START 1.1 INTRODUCTION 1.1.1 Who this Guide is For 1.1.2 What s in this
Security. TestOut Modules 12.6 12.10
 Security TestOut Modules 12.6 12.10 Authentication Authentication is the process of submitting and checking credentials to validate or prove user identity. 1. Username 2. Credentials Password Smart card
Security TestOut Modules 12.6 12.10 Authentication Authentication is the process of submitting and checking credentials to validate or prove user identity. 1. Username 2. Credentials Password Smart card
http://docs.trendmicro.com
 Trend Micro Incorporated reserves the right to make changes to this document and to the products described herein without notice. Before installing and using the product, please review the readme files,
Trend Micro Incorporated reserves the right to make changes to this document and to the products described herein without notice. Before installing and using the product, please review the readme files,
