The 7 th Balkan Conference on Operational Research BACOR 05 Constanta, May 2005, Romania REDUCING FRAUD IN ELECTRONIC PAYMENT SYSTEMS
|
|
|
- Kelly King
- 8 years ago
- Views:
Transcription
1 The 7 th Balkan Conference on Operational Research BACOR 05 Constanta, May 2005, Romania REDUCING FRAUD IN ELECTRONIC PAYMENT SYSTEMS DEJAN SIMIÃ University of Belgrade, Faculty of Organizational Sciences, Belgrade, Serbia and Montenegro Abstract The number of fraudulent activities is increasing dramatically in telecommunication networks, mobile communications, and E-commerce. Fraud is a major problem in electronic payment systems. For example, card fraud losses are growing every year. Consequently, fraud detection is becoming an important issue for research. Fraud begins to rise as new technologies and new weaknesses are found. Reducing fraud is a complex process which includes the knowledge from many scientific areas and demands a multidisciplinary approach. In this paper the problem of fraud prevention and detection is addressed. Several techniques for fraud prevention and detection are presented. It is important that fraud can be detected as it is happening. Detecting fraud in real-time is not easy so it is not surprising that many fraud systems have serious limitations. New solutions such as fraud management systems can reduce fraud significantly by using and combining many existing techniques, as well as new ones. Keywords: Fraud prevention and detection, e-commerce, electronic payment systems, security 1. INTRODUCTION Information technology continually changes [9, 12, 13, 15]. E-commerce is evolving rapidly and now it is reality. Efficient and effective electronic payment services are already established and accepted by businesses and consumers. On-line banking and card payments over the Internet are now commonplace. Advances in e-commerce, expansion of modern technologies and global communication provide a large number of business opportunities, as well as new threats for the banking and financial services. E-commerce provides the capability of buying and selling products, services and information on the Internet by using electronic payment systems. In electronic payment systems the exchange of value is represented by the exchange of data. It is easy, cheap
2 and fast to transfer data, but the main challenge is security. Contemporary electronic payment systems may be classified into two groups: account-based or credit-debit systems and token-based or electronic currency systems. Both groups have important characteristics such as trust, security, reliability, easy of use, efficiency, flexibility, convertibility, interoperability, etc. However, in this paper the focus is on the security of the system. Credit card transactions have become a de facto standard for Internet and Webbased payments. There are millions of credit card transactions processed each day. System architecture of contemporary electronic payment systems is shown in Figure 1. The system is distributed, heterogeneous and hierarchical. The main participants are: Issuer, Acquirer, Payment Gateway, Merchant, Certification Authority, and Cardholder or Buyer. Payment devices such as ATM (Automatic Teller Machine), POS (Point Of Sale) terminal, and kiosk may be located at merchant site. Communication between an acquirer and an issuer is based on ISO 8583 standard for bank card originated messages [7, 8]. Cardholder (buyer) Merchant Internet Certification Authority Payment gateway/ Acquirer Issuer Financial network Figure 1 System architecture of electronic payment systems
3 Fraud is a global problem. Fraudsters operate in all countries and industries. Possible frauds are: credit card fraud, money laundering, mobile communications fraud, insurance fraud and computer intrusion. Credit card fraud may be for card-not-present transactions and for card-present transactions. The fraud for card-not-present transactions is significantly higher than the fraud for card-present transactions [14]. Card fraud losses are growing every year. APACS (UK payment authority) forecasts that industry losses will rise to $11 per card issued by Bearing this in mind in this paper the various techniques that are available and can be used to prevent and detect fraudulent activities are addressed and discussed. The rest of the paper is organized as follows: Section 2 describes the problem of fraud in electronic payment systems. Section 3 presents the fraud prevention and detection as a solution. Section 4 describes the most important techniques that may be used for fraud prevention and detection. A proactive Fraud Management Systems is also proposed. Section 5 concludes the paper. 2. THE PROBLEM STATEMENT In this paper credit card fraud is defined as a transaction when an individual uses another individuals credit card or corresponding data for payment of goods or services while the owner of the card and the card issuer are not aware of that. There are many types of fraud in electronic payment systems. Fraud can occur in a number of ways including: - Counterfeit fraud, - Merchant fraud, - Card-not-present fraud, - ATM fraud, - Internet fraud, - Lost or stolen cards, - Identity theft, - Skimming or copying of electronic data contained on magnetic stripe, and - MOTO (mail order telephone order) fraud. Credit card fraud is increasing over the Internet. As fraud grows in both number and variety, financial institutions are challenged with the need for cost effective, risk management solutions which can identify and avoid fraudulent activities in real-time. The fraudulent activity on a card affects the cardholder, the merchant, the acquirer, and the issuer. The most affected participant is the merchant regarding the cost of the fraud. The cost of a fraudulent transaction is greater than the cost of goods sold. There are many hidden cost components such as card association fee, merchant bank fee, administrative cost (each chargeback requires one to two hours to process at the merchant site), and loss of reputation. Fraudsters are becoming more sophisticated and skillful at discovering any weakness they can exploit. During the time fraud constantly changes as well as behavior of legitimate users. Therefore fraud management tools should learn and adapt to the changing behavior of both fraudsters and legitimate users. There are many methods in the areas of Knowledge Discovery in Databases, Data Mining, Machine Learning and Statistics which are quite applicable in many different
4 areas. However, the naïve application of these methods can cause difficulties in the area of credit card fraud detection. 3. FRAUD PREVENTION AND DETECTION Fraud prevention and detection is an important form of risk management in the credit card industry. Fraud prevention describes measures to stop fraud occurring in the first place. When prevention fails then fraud detection comes into play. The objective is to detect fraud quickly when it does occur and stop it as soon as possible. However, detecting fraud in real-time is not easy [1], so it is not surprising that many fraud systems have serious limitations. Credit card fraud detection is confidential and is not much described in public. Fraud prevention and detection involve monitoring the behavior of customers to estimate, plan, detect and avoid risk. The cost of wrongly accusing a customer of fraudulent behavior is high. Therefore false detection of fraud is a big disadvantage and must be avoided. Different techniques may be needed for different kinds of fraud. The fraudulent data are highly skewed because distribution is not uniform and many more transactions are legitimate than fraudulent. A small percentage of all transactions are fraudulent. Anti-fraud software modules need to: - Detect fraud accurately and early, - Provide relevant information to fraud analysts just in time, - Automate processes where possible, - Self adapt to changing patterns of fraud, and - Self adapt to changing behavior of customers. Fraud prevention and detection may be implemented on issuer or acquirer side. The major difference is that a suspicious transaction on issuer side may be declined. In this paper the most important techniques which can be applied on both sides are chosen and presented. Card fraud cycle is shown in Figure 2. There are three stages in the cycle. Stage 1 represents familiarity with weaknesses in cards and technology which drives up the value of fraud. Fraud begins to rise as new technologies and new weaknesses are found. Stage 2 represents new solutions implemented to reduce fraud. The solutions are not implemented immediately, and therefore Stage 3 represents time lag for solutions to take effect. Figure 2 Card fraud cycle
5 4. TECHNIQUES FOR FRAUD PREVENTION AND DETECTION The usability of a system depends on its performance, reliability and scalability in the real world. An efficient algorithm of detection has to be found for each method of fraud. Also, every fraud detection technique has its limitation and no tool can identify all types of fraud. The total cost of fraud includes the financial loss due to fraud and the cost of fraud prevention and detection system. Therefore the goal is to use an efficient fraud prevention and detection system that minimizes the total cost of fraud. There are many techniques that may be used for fraud prevention and detection. The techniques can be grouped into the following groups: - Applying a set of simple rules, - Implementing EMV Level 2, - Using advanced security protocols, and - Using intelligent tools for fraud prevention and detection. 4.1 APPLYING A SET OF SIMPLE RULES Rule based systems can be used to identify specific types of high-risk transactions. Online or a real-time authorization for a transaction may include implementation of some simple detection rules such as for example: - Rule A: That the card has not been reported as lost or stolen, - Rule B: That the card number is validated with Luhn formula control for check digit, - Rule C: That CVV2 (for VISA) or CVC2 (for Master Card) or CID code (for American Express) is used as security function, - Rule D: That orders that come from free services should be rejected, - Rule E: That international orders should be specially checked with more controls, - Rule F: That the number of transactions with the same card number from the same merchant is not greater than a predefined number of transactions for specified time period, - Rule G: That more than one session from different countries is active at the same time, - Rule H: That the number of deposits exceeds the normal customer activity, - Rule I: That the amount of deposit exceeds the normal customer activity, - Rule J: That the card has valid expiration date, - Rule K: That the transaction is coming from IP address, which is not on IP black list. Some rules, such as rule A, G or I are sufficient for transaction decline. Some others, such as rule F may require a manual review. A more sophisticated rule based system can combine several simple rules for example, in the following way: IF D AND E AND H THEN Review It is important to say that rule based systems rely on a set of expert rules designed to identify fraudulent transactions. The effectiveness of the system depends directly on the knowledge and expertise of the person designing the rules. The fraud can be reduced also by using negative and positive lists of customers. An example of a negative list is a file containing all the card numbers that have produced chargebacks in the past. An example of a positive list is a file containing all the card numbers for trusted customers.
6 4.2 IMPLEMENTING EMV LEVEL 2 Chip or smart cards provide the basis for better security for card transactions. Chip cards have the ability to support future additional services in the fields of electronic commerce and home banking such as loyalty schemes and electronic purse. EMV is the abbreviation for Europay, MasterCard and Visa - the card organizations that have jointly specified the standard [3, 4, 5, 6]. Visa s and MasterCard s implementations of EMV are VSDC (Visa Smart Debit Credit) and M/Chip respectively. There are many advantages of migration from magnetic to chip cards. First of all, chip cards provide higher security compared with magnetic stripe. For example, fraud can be significantly reduced because chip cards are much more difficult to counterfeit than magnetic stripe cards. EMV provides higher security through use of hardware, software and cryptographic processes. Also, offline capability of the chip enables lower transaction costs. A comparison of magnetic stripe and CHIP&PIN solutions regarding various types of card fraud is shown in Table 4.1. As can be seen, card-not-present fraud is not solved by using CHIP&PIN payment, as well as Internet fraud, Identity theft, and MOTO fraud. Due to the complexity of the chip, fraudsters will find it uneconomic to copy smart cards. Also, chargebacks and the associated administrative costs will be minimised by using smart cards. CHIP&PIN payment is less time consuming than magnetic stripe payment with signature, because there is no need for the signature. TYPE OF FRAUD MAGNETIC STRIPE CHIP&PIN Counterfeit fraud No Yes Merchant fraud No Yes Card-not-present fraud No No ATM fraud No Yes Internet fraud No No Lost or stolen cards No Yes Identity theft No No Skimming or copying of electronic No Yes data MOTO No No Table 4.1 Credit card fraud types and possible solutions EMV does not specify the cryptographic algorithms and key management schemes to be used for authentication of transactions. The cryptogram is handled only by the card itself and Issuers transaction authorization systems. 4.3 USING ADVANCED SECURITY PROTOCOLS Secure Sockets Layer (SSL) protocol is used to establish a secure communication channel between two computers. SSL uses authentication based on asymmetric (public key) cryptography. Systems based on SSL are widely used and have enabled the growth of e-commerce. However, SSL was designed as a generic secure communication
7 protocol, not a payment protocol and therefore a more secure payment protocol is needed. Easy of use is the most important factor for customers. Some attempts to create and implement a very low risk system as a dominant payment solution have failed. For instance, Secure Electronic Transaction (SET) protocol was designed to provide trusted electronic transactions [10, 11]. SET uses digital certificates to validate the identities of all parties involved in a purchase and encrypts credit card information before sending it across the Internet. However, SET failed to become dominant payment protocol due to the complexities of deployment. Also, the following advanced security protocols: 3D SET, Visa s 3D Secure and MasterCard s Secure Payment Application (SPA) are very important protocols in electronic payment systems. Their purpose is to replace SET and SSL protocols providing higher level of security in relation to SSL and simpler deployment in relation to SET. 3D Secure is an authentication method designed to allow Merchants, Issuers, Acquirers and cardholders identify themselves in the Internet world for online card not present payments. After agreeing a transaction with an online merchant, cardholder s web browser is redirected to a card issuer server for cardholder authentication. After authentication cardholder s browser is redirected back to the merchant server. Merchants who implement a 3D Secure compliant solution can diminish fraudulent activity. Therefore, acquiring banks are required to support 3D Secure for their online Merchants. 4.4 USING INTELLIGENT TOOLS FOR FRAUD PREVENTION AND DETECTION Without intelligent tools it is not possible to significantly reduce fraud in electronic payment systems. Important characteristics of credit card transactions data are: large volumes of data, non-uniform distribution of fraudulent data, and changing behaviors of customers and fraudsters. Although performance may be the problem, the best tools are able to work in real-time. Detection procedures can be programmed into separate software modules integrated with electronic payment systems to stop or at least, report problems at the time of transaction. Intelligent tools for fraud prevention and detection can be subdivided into those that focus on people and those that focus on transactions and reports. Techniques that focus on people are based on fuzzy logic to score personal files or matching individuals against known bad lists. Focusing on transactions makes possible to proactively reduce fraud. An example of intelligent tool is Address Verification Service (AVS). AVS was developed to help MOTO merchants to reduce fraud. AVS checks the numeric part of the street address and the ZIP code information provided by the consumer against the information stored in issuer s database and returns a match/mismatch response. A serious limitation of AVS is that it only works for addresses in some region and it is not much useful in case of international transactions. Risk scoring systems provide one of the most effective fraud prevention tools available. They are based on statistical models which use the patterns derived from cardholder historical transactions as well as the current transaction attributes. The main difference from rule based systems is a calculation of the final score by weighting several dozens of fraud indicators.
8 Neural networks approach is a very popular tool for credit card fraud detection. However, due to the lack of available data set it is sometimes difficult to implement. A recently published paper [16] presents a concept involving the use of neural networks to correlate information from a variety of technological and database sources to identify suspicious account activity. Distributed data-mining techniques that combine multiple models produce effective fraud and intrusion detectors [2, 17]. A proposal for proactive rule-based Fraud Management System (FMS) is shown in Figure 3. There are the following three software modules: Web interface for adding and configuring rules (WIAC), Run-time module (RM) and Fraud reporting module (FRM). All modules access to a relational database. WIAC is intended for adding, deleting and modifying rules and for changing configuration parameters for already existing ones. In such way FMS has the ability to generate, manage and implement rules as often as required. RM updates data about current transaction in real-time. FRM is intended for generating various reports, which may be printed on the screen, printer, sent as or SMS to mobile phones of responsible persons, or delivered in various formats such as PDF, HTML, CSV, XLS, and XML files. FMS may be integrated with any transaction processing system by using Request and Response type of communication. An adequate textual message can be transferred to the merchant through a Response. Web interface for adding and configuring rules (WIAC) Run-time module (RM) Fraud reporting module (FRM) Relational database Figure 3 Proactive rule-based Fraud Management System RM includes various controls such as: hotlist control, velocity control, statistical rules, Luhn formula control, and custom rules as shown in Figure 4. Transactions come from different communication channels and various payment devices. Depending on the result of a control the corresponding decision must be made: to accept, reject or manually review the current transaction.
9 A combination of tools is always a better solution to any single tool. The best solution is to use layers of fraud protection. Sometimes it is not appropriate to automate everything in transaction processing including fraud detection. It is important to know that there may be a need to manually review a small percentage of orders. The risk of accepting an order is always balanced with the risk of loosing the customer. ATM Fraud management POS Internet Kiosk Hotlist control Velocity control Statistical rules Luhn formula control Custom rules Decision Accept, Reject, Review MOTO Figure 4 Run-time fraud management module 5. CONCLUSION In this paper the problem of fraud in electronic payment systems is addressed. Reducing fraud is a very important goal in electronic payment systems, which may be achieved by using prevention and detection techniques. Detecting known and unknown fraud in real-time is not easy but it is feasible. There are many techniques that may be used. In this paper the most important techniques for fraud prevention and detection are chosen and presented. No tool can identify all types of fraud and every tool is best at identifying one particular type of fraud. In addition to industry standard security rules, solutions such as Fraud Management System, described in the paper, are necessary to provide advanced protection from all types of online and offline transaction fraud in electronic payment systems. Card fraud methods evolve continuously. Therefore fraud prevention and detection techniques have to be proactive and always be ready to minimize fraudulent activities. Combination of different techniques gives best results.
10 BIBLIOGRAPHY [1] Cahill M. H., Lambert D., Pinheiro J. C., Sun D. X. (2000), Detecting fraud in the real world, Handbook of Massive Datasets, Kluwer Academic Publishers, pp ; [2] Chan K. Philip, Fan W., Prodromidis A., and Stolfo S. (1999), Distributed data mining in credit card fraud detection, IEEE Intelligent Systems, Vol. 14, No. 6, 67-74, available at ; [3] EMV (2004) EMV 2000 Integrated Circuit card Specification for Payment Systems Version 4.1 Book 1: Application Independent IC Card to Terminal Interface Requirements, EMVCo; [4] EMV (2004) EMV 2000 Integrated Circuit card Specification for Payment Systems Version 4.1 Book 2: Security and Key Management, EMVCo; [5] EMV (2004) EMV 2000 Integrated Circuit card Specification for Payment Systems Version 4.1 Book 3: Application Specification, EMVCo; [6] EMV (2004) EMV 2000 Integrated Circuit card Specification for Payment Systems Version 4.1 Book 4: CardHolder, Attendant, and Acquirer Interface Requirements, EMVCo; [7] ISO 8583 (1987) ISO 8583: Bank Card Originated Messages Interchange Message Specifications Content for Financial Transactions, available at [8] ISO 8583 (1993) ISO 8583: Financial Transaction Card Originated Messages Interchange Message Specifications, available at [9] Mrkiã Mladen, Simiã Dejan (2004), "Porting a Java Web application to z/os", MVS Update, Published by Xephon London Road Newbury Berkshire RG14 1JL, England, April 2004, pp. 9-23; [10] SET (1997), SET Secure Electronic Transaction Specification Book 1: Business Description, available at (accessed May 2005); [11] SET (1997), SET Secure Electronic Transaction Specification Book 2: Programmer s Guide, available at (accessed May 2005); [12] Simiã Branka, Simiã Dejan (2001), Executing applet methods in Lotus Domino forms from Netscape 6, Domino Update, March, published by Xephon London Road, Newbury Berkshire RG14 1JL, England, 3-6; [13] Simiã Dejan, Starèeviã Dušan (1997), A Distributed Multimedia Bank Office Information System, Multimedia Technology and Applications, Springer-Verlag Singapore Pte. Ltd., ; [14] Simiã Dejan, Starèeviã Dušan (2002), E-Commerce Security: Challenges and Solutions for Credit and Debit Cards Payment Systems, 6 th Balkan Conference on Operational Research, A Challenge for Scientific and Business Collaboration, Thessaloniki, Greece, (CD Edition); [15] Starèeviã Dušan, Simiã Dejan, Pantoviã Vladan (1996), The evolution of software architecture, International Conference on information products, processes and technologies, Moskva, November, Proceedings of the Conference, 45-47; [16] Vikram Ashish, Chennuru Sivakumar, Rao H. R., Upadhyaya Shambhu (2004), A
11 Solution Architecture for Financial Institutions to Handle Illegal Activities: A Neural Networks Approach, IEEE Proceedings of the 37 th Hawaii International Conference on System Sciences, available at (accessed May 2005 ); [17] Wang Huaiqing, Mylopoulos John, Liao Stephen (2002), Intelligent agents and financial risk monitoring systems, Communications of the ACM, March, Volume 45 Issue 3,
Mitigating Fraud Risk Through Card Data Verification
 Risk Management Best Practices 11 September 2014 Mitigating Fraud Risk Through Card Data Verification AP, Canada, CEMEA, LAC, U.S. Issuers, Processors With a number of cardholder payment options (e.g.,
Risk Management Best Practices 11 September 2014 Mitigating Fraud Risk Through Card Data Verification AP, Canada, CEMEA, LAC, U.S. Issuers, Processors With a number of cardholder payment options (e.g.,
MOBILE CHIP ELECTRONIC COMMERCE: ENABLING CREDIT CARD PAYMENT FOR MOBILE DEVICES
 MOBILE CHIP ELECTRONIC COMMERCE: ENABLING CREDIT CARD PAYMENT FOR MOBILE DEVICES Marko Schuba and Konrad Wrona Ericsson Research, Germany ABSTRACT This paper describes the Mobile Chip Electronic Commerce
MOBILE CHIP ELECTRONIC COMMERCE: ENABLING CREDIT CARD PAYMENT FOR MOBILE DEVICES Marko Schuba and Konrad Wrona Ericsson Research, Germany ABSTRACT This paper describes the Mobile Chip Electronic Commerce
Online Payment Processing Definitions From Credit Research Foundation (http://www.crfonline.org/)
 Online Payment Processing Definitions From Credit Research Foundation (http://www.crfonline.org/) The following glossary represents definitions for commonly-used terms in online payment processing. Address
Online Payment Processing Definitions From Credit Research Foundation (http://www.crfonline.org/) The following glossary represents definitions for commonly-used terms in online payment processing. Address
2015-11-02. Electronic Payments Part 1
 Electronic Payments Part Card transactions Card-Present Smart Cards Card-Not-Present SET 3D Secure Untraceable E-Cash Micropayments Payword Electronic Lottery Tickets Peppercoin Bitcoin EITN4 - Advanced
Electronic Payments Part Card transactions Card-Present Smart Cards Card-Not-Present SET 3D Secure Untraceable E-Cash Micropayments Payword Electronic Lottery Tickets Peppercoin Bitcoin EITN4 - Advanced
Understand the Business Impact of EMV Chip Cards
 Understand the Business Impact of EMV Chip Cards 3 What About Mail/Telephone Order and ecommerce? 3 What Is EMV 3 How Chip Cards Work 3 Contactless Technology 4 Background: Behind the Curve 4 Liability
Understand the Business Impact of EMV Chip Cards 3 What About Mail/Telephone Order and ecommerce? 3 What Is EMV 3 How Chip Cards Work 3 Contactless Technology 4 Background: Behind the Curve 4 Liability
A Guide to EMV. Version 1.0 May 2011. Copyright 2011 EMVCo, LLC. All rights reserved.
 A Guide to EMV Version 1.0 May 2011 Objective Provide an overview of the EMV specifications and processes What is EMV? Why EMV? Position EMV in the context of the wider payments industry Define the role
A Guide to EMV Version 1.0 May 2011 Objective Provide an overview of the EMV specifications and processes What is EMV? Why EMV? Position EMV in the context of the wider payments industry Define the role
Unified Payment Platform Payment Pos Server Fraud Detection Server Reconciliation Server Autobill Server e-point Server Mobile Payment Server
 Unified Payment Platform Payment Pos Server Detection Server Reconciliation Server Autobill Server e-point Server Mobile Payment Server Securing Payment & Beyond Infinitium E-Payment is a Unified Payment
Unified Payment Platform Payment Pos Server Detection Server Reconciliation Server Autobill Server e-point Server Mobile Payment Server Securing Payment & Beyond Infinitium E-Payment is a Unified Payment
How To Protect A Smart Card From Being Hacked
 Chip Terms Explained A Guide to Smart Card Terminology Contents 1 AAC Application Authentication Cryptogram AID Application Identifier Applet ARQC Authorization Request Cryptogram ARPC Authorization Response
Chip Terms Explained A Guide to Smart Card Terminology Contents 1 AAC Application Authentication Cryptogram AID Application Identifier Applet ARQC Authorization Request Cryptogram ARPC Authorization Response
EMV and Small Merchants:
 September 2014 EMV and Small Merchants: What you need to know Mike English Executive Director, Product Development Heartland Payment Systems 2014 Heartland Payment Systems, Inc. All trademarks, service
September 2014 EMV and Small Merchants: What you need to know Mike English Executive Director, Product Development Heartland Payment Systems 2014 Heartland Payment Systems, Inc. All trademarks, service
EMV FAQs. Contact us at: CS@VancoPayments.com. Visit us online: VancoPayments.com
 EMV FAQs Contact us at: CS@VancoPayments.com Visit us online: VancoPayments.com What are the benefits of EMV cards to merchants and consumers? What is EMV? The acronym EMV stands for an organization formed
EMV FAQs Contact us at: CS@VancoPayments.com Visit us online: VancoPayments.com What are the benefits of EMV cards to merchants and consumers? What is EMV? The acronym EMV stands for an organization formed
Merchant e-solutions Payment Gateway Back Office User Guide. Merchant e-solutions January 2011 Version 2.5
 Merchant e-solutions Payment Gateway Back Office User Guide Merchant e-solutions January 2011 Version 2.5 This publication is for information purposes only and its content does not represent a contract
Merchant e-solutions Payment Gateway Back Office User Guide Merchant e-solutions January 2011 Version 2.5 This publication is for information purposes only and its content does not represent a contract
welcome to liber8:payment
 liber8:payment welcome to liber8:payment Our self-service kiosks free up staff time and improve the overall patron experience. liber8:payment further enhances these benefits by providing the convenience
liber8:payment welcome to liber8:payment Our self-service kiosks free up staff time and improve the overall patron experience. liber8:payment further enhances these benefits by providing the convenience
Visa Recommended Practices for EMV Chip Implementation in the U.S.
 CHIP ADVISORY #20, UPDATED JULY 11, 2012 Visa Recommended Practices for EMV Chip Implementation in the U.S. Summary As issuers, acquirers, merchants, processors and vendors plan and begin programs to adopt
CHIP ADVISORY #20, UPDATED JULY 11, 2012 Visa Recommended Practices for EMV Chip Implementation in the U.S. Summary As issuers, acquirers, merchants, processors and vendors plan and begin programs to adopt
EMV EMV TABLE OF CONTENTS
 2 TABLE OF CONTENTS Intro... 2 Are You Ready?... 3 What Is?... 4 Why?... 5 What Does Mean To Your Business?... 6 Checklist... 8 3 U.S. Merchants 60% are expected to convert to -enabled devices by 2015.
2 TABLE OF CONTENTS Intro... 2 Are You Ready?... 3 What Is?... 4 Why?... 5 What Does Mean To Your Business?... 6 Checklist... 8 3 U.S. Merchants 60% are expected to convert to -enabled devices by 2015.
Your Single Source. for credit, debit and pre-paid services. Fraud Risk and Mitigation
 Your Single Source for credit, debit and pre-paid services Fraud Risk and Mitigation Agenda Types of Fraud Fraud Identification Notifications Next Steps 11/8/2013 2 Types of Fraud Lost and Stolen Cards
Your Single Source for credit, debit and pre-paid services Fraud Risk and Mitigation Agenda Types of Fraud Fraud Identification Notifications Next Steps 11/8/2013 2 Types of Fraud Lost and Stolen Cards
THE FIVE Ws OF EMV BY DAVE EWALD GLOBAL EMV CONSULTANT AND MANAGER DATACARD GROUP
 THE FIVE Ws OF EMV BY DAVE EWALD GLOBAL EMV CONSULTANT AND MANAGER DATACARD GROUP WHERE IS THE U.S. PAYMENT CARD INDUSTRY NOW? WHERE IS IT GOING? Today, payment and identification cards of all types (credit
THE FIVE Ws OF EMV BY DAVE EWALD GLOBAL EMV CONSULTANT AND MANAGER DATACARD GROUP WHERE IS THE U.S. PAYMENT CARD INDUSTRY NOW? WHERE IS IT GOING? Today, payment and identification cards of all types (credit
Merchant Account Glossary of Terms
 Merchant Account Glossary of Terms From offshore merchant accounts to the truth behind free merchant accounts, get answers to some of the most common and frequently asked questions. If you cannot find
Merchant Account Glossary of Terms From offshore merchant accounts to the truth behind free merchant accounts, get answers to some of the most common and frequently asked questions. If you cannot find
A multi-layered approach to payment card security.
 A multi-layered approach to payment card security. CARD-NOT-PRESENT 1 A recent research study revealed that Visa cards are the most widely used payment method at Canadian websites, on the phone, or through
A multi-layered approach to payment card security. CARD-NOT-PRESENT 1 A recent research study revealed that Visa cards are the most widely used payment method at Canadian websites, on the phone, or through
EMP's vision is to be the leading electronic payments processing company in the emerging markets of Africa and the Middle East.
 EMP's vision is to be the leading electronic payments processing company in the emerging markets of Africa and the Middle East. EMP's mission is to be at the forefront of the region's electronic payments
EMP's vision is to be the leading electronic payments processing company in the emerging markets of Africa and the Middle East. EMP's mission is to be at the forefront of the region's electronic payments
EMV in Hotels Observations and Considerations
 EMV in Hotels Observations and Considerations Just in: EMV in the Mail Customer Education: Credit Card companies have already started customer training for the new smart cards. 1 Questions to be Answered
EMV in Hotels Observations and Considerations Just in: EMV in the Mail Customer Education: Credit Card companies have already started customer training for the new smart cards. 1 Questions to be Answered
A Guide to EMV Version 1.0 May 2011
 Table of Contents TABLE OF CONTENTS... 2 LIST OF FIGURES... 4 1 INTRODUCTION... 5 1.1 Purpose... 5 1.2 References... 5 2 BACKGROUND... 6 2.1 What is EMV... 6 2.2 Why EMV... 7 3 THE HISTORY OF EMV... 8
Table of Contents TABLE OF CONTENTS... 2 LIST OF FIGURES... 4 1 INTRODUCTION... 5 1.1 Purpose... 5 1.2 References... 5 2 BACKGROUND... 6 2.1 What is EMV... 6 2.2 Why EMV... 7 3 THE HISTORY OF EMV... 8
Euronet s EMV Chip Solutions Superior Protection with Enhanced Security against Fraud
 Serving millions of people worldwide with electronic payment convenience. Euronet s EMV Chip Solutions Superior Protection with Enhanced Security against Fraud Copyright 2011 Euronet Worldwide, Inc. All
Serving millions of people worldwide with electronic payment convenience. Euronet s EMV Chip Solutions Superior Protection with Enhanced Security against Fraud Copyright 2011 Euronet Worldwide, Inc. All
EMV and Restaurants: What you need to know. Mike English. October 2014. Executive Director, Product Development Heartland Payment Systems
 October 2014 EMV and Restaurants: What you need to know Mike English Executive Director, Product Development Heartland Payment Systems 2014 Heartland Payment Systems, Inc. All trademarks, service marks
October 2014 EMV and Restaurants: What you need to know Mike English Executive Director, Product Development Heartland Payment Systems 2014 Heartland Payment Systems, Inc. All trademarks, service marks
Payment Methods. The cost of doing business. Michelle Powell - BASYS Processing, Inc.
 Payment Methods The cost of doing business Michelle Powell - BASYS Processing, Inc. You ve got to spend money, to make money Major Industry Topics Industry Process Flow PCI DSS Compliance Risks of Non-Compliance
Payment Methods The cost of doing business Michelle Powell - BASYS Processing, Inc. You ve got to spend money, to make money Major Industry Topics Industry Process Flow PCI DSS Compliance Risks of Non-Compliance
CREDIT CARD PROCESSING GLOSSARY OF TERMS
 CREDIT CARD PROCESSING GLOSSARY OF TERMS 3DES A highly secure encryption system that encrypts data 3 times, using 3 64-bit keys, for an overall encryption key length of 192 bits. Also called triple DES.
CREDIT CARD PROCESSING GLOSSARY OF TERMS 3DES A highly secure encryption system that encrypts data 3 times, using 3 64-bit keys, for an overall encryption key length of 192 bits. Also called triple DES.
Mitigating Fraudulent CNP Transactions
 Examination of Safeguards Electronic commerce has become a wildly successful channel for merchants and their customers. While the ability to shop online or through mail order catalogs is not new, the explosion
Examination of Safeguards Electronic commerce has become a wildly successful channel for merchants and their customers. While the ability to shop online or through mail order catalogs is not new, the explosion
EMV and Chip Cards Key Information On What This Is, How It Works and What It Means
 EMV and Chip Cards Key Information On What This Is, How It Works and What It Means Document Purpose This document is intended to provide information about the concepts behind and the processes involved
EMV and Chip Cards Key Information On What This Is, How It Works and What It Means Document Purpose This document is intended to provide information about the concepts behind and the processes involved
An access number, dialed by a modem, that lets a computer communicate with an Internet Service Provider (ISP) or some other service provider.
 TERM DEFINITION Access Number Account Number Acquirer Acquiring Bank Acquiring Processor Address Verification Service (AVS) Association Authorization Authorization Center Authorization Fee Automated Clearing
TERM DEFINITION Access Number Account Number Acquirer Acquiring Bank Acquiring Processor Address Verification Service (AVS) Association Authorization Authorization Center Authorization Fee Automated Clearing
Fighting Online Fraud
 White Paper Fighting Online Fraud Maintaining tight security, including using both standard and advanced fraud detection and prevention tools, is crucial to maintaining a successful business. No merchant
White Paper Fighting Online Fraud Maintaining tight security, including using both standard and advanced fraud detection and prevention tools, is crucial to maintaining a successful business. No merchant
Credit Card Processing Overview
 CardControl 3.0 Credit Card Processing Overview Overview Credit card processing is a very complex and important system for anyone that sells goods. This guide will hopefully help educate and inform new
CardControl 3.0 Credit Card Processing Overview Overview Credit card processing is a very complex and important system for anyone that sells goods. This guide will hopefully help educate and inform new
Acceptance to Minimize Fraud
 Best Practices for Credit Card Acceptance to Minimize Fraud By implementing best practices in credit card processing, you decrease the likelihood of fraudulent transactions and chargebacks. In general,
Best Practices for Credit Card Acceptance to Minimize Fraud By implementing best practices in credit card processing, you decrease the likelihood of fraudulent transactions and chargebacks. In general,
Smart Cards for Payment Systems
 White Paper Smart Cards for Payment Systems An Introductory Paper describing how Thales e-security can help banks migrate to Smart Card Technology Background In this paper: Background 1 The Solution 2
White Paper Smart Cards for Payment Systems An Introductory Paper describing how Thales e-security can help banks migrate to Smart Card Technology Background In this paper: Background 1 The Solution 2
RSA Adaptive Authentication For ecommerce
 RSA Adaptive Authentication For ecommerce Risk-based 3D Secure for Credit Card Issuers SOLUTION BRIEF RSA FRAUD & RISK INTELLIGENCE The Threat of ecommerce Fraud ecommerce fraud is a threat to both issuers
RSA Adaptive Authentication For ecommerce Risk-based 3D Secure for Credit Card Issuers SOLUTION BRIEF RSA FRAUD & RISK INTELLIGENCE The Threat of ecommerce Fraud ecommerce fraud is a threat to both issuers
The Canadian Migration to EMV. Prepared By:
 The Canadian Migration to EMV Prepared By: December 1993 Everyone But The USA Is Migrating The international schemes decided Smart Cards are the way forward Europay, MasterCard & Visa International Produced
The Canadian Migration to EMV Prepared By: December 1993 Everyone But The USA Is Migrating The international schemes decided Smart Cards are the way forward Europay, MasterCard & Visa International Produced
Fraud Detection. Configuration Guide for the Fraud Detection Module v.4.2.0. epdq 2014, All rights reserved.
 Configuration Guide for the Fraud Detection Module v.4.2.0 Table of Contents 1 What is the... Fraud Detection Module? 4 1.1 Benefits 1.2 Access 1.3 Contents... 4... 4... 4 2 Fraud detection... activation
Configuration Guide for the Fraud Detection Module v.4.2.0 Table of Contents 1 What is the... Fraud Detection Module? 4 1.1 Benefits 1.2 Access 1.3 Contents... 4... 4... 4 2 Fraud detection... activation
ACFS PRODUCT FLYER. Its modular architecture allows a tailored integration, with a short time-to-market for different information systems.
 PRODUCT FLYER General Routing Financial System is modular software suite designed to support enterprises providing a MOTO Gateway (Mail Order Telephone Order), complete with tokenization, multi-acquiring
PRODUCT FLYER General Routing Financial System is modular software suite designed to support enterprises providing a MOTO Gateway (Mail Order Telephone Order), complete with tokenization, multi-acquiring
Heartland Secure. By: Michael English. A Heartland Payment Systems White Paper 2014. Executive Director, Product Development
 A Heartland Payment Systems White Paper 2014 Heartland Secure. By: Michael English Executive Director, Product Development 2014 Heartland Payment Systems. All trademarks, service marks and trade names
A Heartland Payment Systems White Paper 2014 Heartland Secure. By: Michael English Executive Director, Product Development 2014 Heartland Payment Systems. All trademarks, service marks and trade names
INTRODUCTION AND HISTORY
 INTRODUCTION AND HISTORY EMV is actually younger than we all may think as it only became available, as a specification that could be implemented, in 1996. The evolution of EMV can be seen in the development
INTRODUCTION AND HISTORY EMV is actually younger than we all may think as it only became available, as a specification that could be implemented, in 1996. The evolution of EMV can be seen in the development
U.S. Smart Card Migration: Stripe to EMV Claudia Swendseid, Federal Reserve Bank of Minneapolis Terry Dooley, SHAZAM Kristine Oberg, Elavon
 U.S. Smart Card Migration: Stripe to EMV Claudia Swendseid, Federal Reserve Bank of Minneapolis Terry Dooley, SHAZAM Kristine Oberg, Elavon UMACHA Navigating Payments 2014 October 8, 2014 Who We Are Claudia
U.S. Smart Card Migration: Stripe to EMV Claudia Swendseid, Federal Reserve Bank of Minneapolis Terry Dooley, SHAZAM Kristine Oberg, Elavon UMACHA Navigating Payments 2014 October 8, 2014 Who We Are Claudia
Guideline on Debit or Credit Cards Usage
 CMSGu2012-04 Mauritian Computer Emergency Response Team CERT-MU SECURITY GUIDELINE 2011-02 Enhancing Cyber Security in Mauritius Guideline on Debit or Credit Cards Usage National Computer Board Mauritius
CMSGu2012-04 Mauritian Computer Emergency Response Team CERT-MU SECURITY GUIDELINE 2011-02 Enhancing Cyber Security in Mauritius Guideline on Debit or Credit Cards Usage National Computer Board Mauritius
ACFS PRODUCT FLYER. Its modular architecture allows a tailored integration, with a short time-to-market for different payment methods.
 PRODUCT FLYER Internet Gateway Financial Systems is a modular software suite designed to support financial institutions and enterprises, providing a single interface for the optimized management of e-commerce
PRODUCT FLYER Internet Gateway Financial Systems is a modular software suite designed to support financial institutions and enterprises, providing a single interface for the optimized management of e-commerce
ACFS PRODUCT FLYER. Its modular architecture allows a tailored integration, with a short time-to-market for different payment methods.
 PRODUCT FLYER Internet Gateway Financial Systems is a modular software suite designed to support financial institutions and enterprises, providing a single interface for the optimized management of e-commerce
PRODUCT FLYER Internet Gateway Financial Systems is a modular software suite designed to support financial institutions and enterprises, providing a single interface for the optimized management of e-commerce
ACQUIRER OR ACQUIRING BANK A financial institution (often a bank) where a merchant has an account to process transactions and card payments
 A TO Z JARGON BUSTER A ACQUIRER OR ACQUIRING BANK A financial institution (often a bank) where a merchant has an account to process transactions and card payments ATM Automated Teller Machine. Unattended,
A TO Z JARGON BUSTER A ACQUIRER OR ACQUIRING BANK A financial institution (often a bank) where a merchant has an account to process transactions and card payments ATM Automated Teller Machine. Unattended,
What is EMV? What is different?
 U.S. consumers are receiving new debit and credit cards with embedded chip technology that better stores and protects cardholder information. These new chip cards are part of the new card standard, Europay,
U.S. consumers are receiving new debit and credit cards with embedded chip technology that better stores and protects cardholder information. These new chip cards are part of the new card standard, Europay,
CardControl. Credit Card Processing 101. Overview. Contents
 CardControl Credit Card Processing 101 Overview Credit card processing is a very complex and important system for anyone that sells goods. This guide will hopefully help educate and inform new and old
CardControl Credit Card Processing 101 Overview Credit card processing is a very complex and important system for anyone that sells goods. This guide will hopefully help educate and inform new and old
What Merchants Need to Know About EMV
 Effective November 1, 2014 1. What is EMV? EMV is the global standard for card present payment processing technology and it s coming to the U.S. EMV uses an embedded chip in the card that holds all the
Effective November 1, 2014 1. What is EMV? EMV is the global standard for card present payment processing technology and it s coming to the U.S. EMV uses an embedded chip in the card that holds all the
Fraud Detection Module (basic)
 Table of contents 1. Introduction 1.1 Benefits 1.2 Contents 2. Activation and configuration 2.1 Blocking rules 2.1.1 Card country 2.1.2 IP address country 2.1.3 Country consistency 2.1.4 3-D Secure 2.2
Table of contents 1. Introduction 1.1 Benefits 1.2 Contents 2. Activation and configuration 2.1 Blocking rules 2.1.1 Card country 2.1.2 IP address country 2.1.3 Country consistency 2.1.4 3-D Secure 2.2
The Comprehensive, Yet Concise Guide to Credit Card Processing
 The Comprehensive, Yet Concise Guide to Credit Card Processing Written by David Rodwell CreditCardProcessing.net Terms of Use This ebook was created to provide educational information regarding payment
The Comprehensive, Yet Concise Guide to Credit Card Processing Written by David Rodwell CreditCardProcessing.net Terms of Use This ebook was created to provide educational information regarding payment
ACFS PRODUCT FLYER MTFS
 PRODUCT FLYER Mail Telephone Order Financial Systems is a fully-featured, modular software suite designed to support financial institutions and enterprises in the management and optimization of recurring
PRODUCT FLYER Mail Telephone Order Financial Systems is a fully-featured, modular software suite designed to support financial institutions and enterprises in the management and optimization of recurring
A Study of an On-Line Credit Card Payment Processing and Fraud Prevention for e-business
 A Study of an On-Line Credit Card Payment Processing and Fraud Prevention for e-business Nucharee Premchaiswadi*, James G. Williams** and Wichian Premchaiswadi*** *Faculty of Information Technology Dhurakij
A Study of an On-Line Credit Card Payment Processing and Fraud Prevention for e-business Nucharee Premchaiswadi*, James G. Williams** and Wichian Premchaiswadi*** *Faculty of Information Technology Dhurakij
EMV: Integrated Circuit Card Specifications for Payment Systems
 : Integrated Circuit Card Specifications for Payment Systems Jan Krhovják Faculty of Informatics, Masaryk University Jan Krhovják (FI MU) EMV (Europay, MasterCard, Visa) 20. 3. 2006 1 / 13 Outline EMV
: Integrated Circuit Card Specifications for Payment Systems Jan Krhovják Faculty of Informatics, Masaryk University Jan Krhovják (FI MU) EMV (Europay, MasterCard, Visa) 20. 3. 2006 1 / 13 Outline EMV
Enhancing Payment Card Security New Measures to be Phased in from 2 nd Quarter 2010 to 1 st Quarter 2011
 Enhancing Payment Card Security New Measures to be Phased in from 2 nd Quarter 2010 to 1 st Quarter 2011 On 5 th March 2010, The Association of Banks in Singapore announced key measures to adopt a holistic
Enhancing Payment Card Security New Measures to be Phased in from 2 nd Quarter 2010 to 1 st Quarter 2011 On 5 th March 2010, The Association of Banks in Singapore announced key measures to adopt a holistic
PCI 3.1 Changes. Jon Bonham, CISA Coalfire System, Inc.
 PCI 3.1 Changes Jon Bonham, CISA Coalfire System, Inc. Agenda Introduction of Coalfire What does this have to do with the business office Changes to version 3.1 EMV P2PE Questions and Answers Contact Information
PCI 3.1 Changes Jon Bonham, CISA Coalfire System, Inc. Agenda Introduction of Coalfire What does this have to do with the business office Changes to version 3.1 EMV P2PE Questions and Answers Contact Information
FOR A BARRIER-FREE PAYMENT PROCESSING SOLUTION
 FOR A BARRIER-FREE PAYMENT PROCESSING SOLUTION MAKE THE SWITCH TO MONEXgroup ecommerce I Mobile I Wireless I Integrated I Countertop Solutions IN-STORE ON-THE-GO ONLINE Accept secure debit and credit card
FOR A BARRIER-FREE PAYMENT PROCESSING SOLUTION MAKE THE SWITCH TO MONEXgroup ecommerce I Mobile I Wireless I Integrated I Countertop Solutions IN-STORE ON-THE-GO ONLINE Accept secure debit and credit card
CRM4M Accounting Set Up and Miscellaneous Accounting Guide Rev. 10/17/2008 rb
 CRM4M Accounting Set Up and Miscellaneous Accounting Guide Rev. 10/17/2008 rb Topic Page Chart of Accounts 3 Creating a Batch Manually 8 Closing a Batch Manually 11 Cancellation Fees 17 Check Refunds 19
CRM4M Accounting Set Up and Miscellaneous Accounting Guide Rev. 10/17/2008 rb Topic Page Chart of Accounts 3 Creating a Batch Manually 8 Closing a Batch Manually 11 Cancellation Fees 17 Check Refunds 19
toast EMV in 2015: How Restaurants Can Prepare for the New Chip-and-Pin Standard
 toast EMV in 2015: How Restaurants Can Prepare for the New Chip-and-Pin Standard Table of Contents For more than 40 years, merchants and consumers have used magnetic stripe credit cards and compatible
toast EMV in 2015: How Restaurants Can Prepare for the New Chip-and-Pin Standard Table of Contents For more than 40 years, merchants and consumers have used magnetic stripe credit cards and compatible
M/Chip Functional Architecture for Debit and Credit
 M/Chip Functional Architecture for Debit and Credit Christian Delporte, Vice President, Chip Centre of Excellence, New Products Engineering Suggested routing: Authorization, Chargeback, Chip Technology,
M/Chip Functional Architecture for Debit and Credit Christian Delporte, Vice President, Chip Centre of Excellence, New Products Engineering Suggested routing: Authorization, Chargeback, Chip Technology,
Your Gateway to Online Success
 The NETBANX gateway is a leading, proprietary online payment processing platform operating on a world class technology infrastructure. Trusted by global brands and companies around the world, the NETBANX
The NETBANX gateway is a leading, proprietary online payment processing platform operating on a world class technology infrastructure. Trusted by global brands and companies around the world, the NETBANX
Securing the Payments System. The facts about fraud prevention
 Securing the Payments System The facts about fraud prevention Contents Introduction 3 Visa s Security Programme 4 Fraud Types and Threats 6 Fraud Statistics and Research 7 Visa s Security Agenda for New
Securing the Payments System The facts about fraud prevention Contents Introduction 3 Visa s Security Programme 4 Fraud Types and Threats 6 Fraud Statistics and Research 7 Visa s Security Agenda for New
Credit/Debit Card Processing Requirements and Best Practices. Adele Honeyman Oregon State Treasury Training Specialist
 Credit/Debit Card Processing Requirements and Best Practices Adele Honeyman Oregon State Treasury Training Specialist 1 What? What do I need to know about excepting credit cards? Who s involved, how it
Credit/Debit Card Processing Requirements and Best Practices Adele Honeyman Oregon State Treasury Training Specialist 1 What? What do I need to know about excepting credit cards? Who s involved, how it
ETSI TR 102 071 V1.2.1 (2002-10)
 TR 102 071 V1.2.1 (2002-10) Technical Report Mobile Commerce (M-COMM); Requirements for Payment Methods for Mobile Commerce 2 TR 102 071 V1.2.1 (2002-10) Reference RTR/M-COMM-007 Keywords commerce, mobile,
TR 102 071 V1.2.1 (2002-10) Technical Report Mobile Commerce (M-COMM); Requirements for Payment Methods for Mobile Commerce 2 TR 102 071 V1.2.1 (2002-10) Reference RTR/M-COMM-007 Keywords commerce, mobile,
EMV Frequently Asked Questions for Merchants May, 2014
 EMV Frequently Asked Questions for Merchants May, 2014 Copyright 2014 Vantiv All rights reserved. Disclaimer The information in this document is offered on an as is basis, without warranty of any kind,
EMV Frequently Asked Questions for Merchants May, 2014 Copyright 2014 Vantiv All rights reserved. Disclaimer The information in this document is offered on an as is basis, without warranty of any kind,
EMV : Frequently Asked Questions for Merchants
 EMV : Frequently Asked Questions for Merchants The information in this document is offered on an as is basis, without warranty of any kind, either expressed, implied or statutory, including but not limited
EMV : Frequently Asked Questions for Merchants The information in this document is offered on an as is basis, without warranty of any kind, either expressed, implied or statutory, including but not limited
Your gateway to card acceptance.
 MERCHANT SERVICES Authorize.Net Solutions Your gateway to card acceptance. Processing transactions reliably and securely is essential to your business. That s why BBVA Compass and Authorize.Net, a leading
MERCHANT SERVICES Authorize.Net Solutions Your gateway to card acceptance. Processing transactions reliably and securely is essential to your business. That s why BBVA Compass and Authorize.Net, a leading
Chargeback Reason Code List - U.S.
 AL Airline Transaction Dispute AP Automatic Payment AW Altered Amount CA Cash Advance Dispute CD Credit Posted as Card Sale CR Cancelled Reservation This chargeback occurs because of a dispute on an Airline
AL Airline Transaction Dispute AP Automatic Payment AW Altered Amount CA Cash Advance Dispute CD Credit Posted as Card Sale CR Cancelled Reservation This chargeback occurs because of a dispute on an Airline
Unified Payment Platform Payment Pos Server Fraud Detection Server Reconciliation Server Autobill Server e-point Server Mobile Payment Server
 Unified Payment Platform Payment Pos Server Fraud Detection Server Reconciliation Server Autobill Server e-point Server Mobile Payment Server E-PAYMENT Group of Companies Infinitium E-Payment is a Unified
Unified Payment Platform Payment Pos Server Fraud Detection Server Reconciliation Server Autobill Server e-point Server Mobile Payment Server E-PAYMENT Group of Companies Infinitium E-Payment is a Unified
DATA SECURITY, FRAUD PREVENTION AND COMPLIANCE
 DATA SECURITY, FRAUD PREVENTION AND COMPLIANCE December 2015 English_General This presentation was prepared exclusively for the benefit and internal use of the J.P. Morgan client or potential client to
DATA SECURITY, FRAUD PREVENTION AND COMPLIANCE December 2015 English_General This presentation was prepared exclusively for the benefit and internal use of the J.P. Morgan client or potential client to
Using EMV Cards to Protect E-commerce Transactions
 Using EMV Cards to Protect E-commerce Transactions Vorapranee Khu-Smith and Chris J. Mitchell Information Security Group, Royal Holloway, University of London, Egham, Surrey, TW20 0EX, United Kingdom {V.Khu-Smith,
Using EMV Cards to Protect E-commerce Transactions Vorapranee Khu-Smith and Chris J. Mitchell Information Security Group, Royal Holloway, University of London, Egham, Surrey, TW20 0EX, United Kingdom {V.Khu-Smith,
Information Technology
 Credit Card Handling Security Standards Overview Information Technology This document is intended to provide guidance to merchants (colleges, departments, organizations or individuals) regarding the processing
Credit Card Handling Security Standards Overview Information Technology This document is intended to provide guidance to merchants (colleges, departments, organizations or individuals) regarding the processing
Fraud Protection, You and Your Bank
 Fraud Protection, You and Your Bank Maximize your chances to minimize your losses Presentation for Missouri GFOA April 2011 By: Terry Endres, VP, Government Treasury Solutions Phone: 314-466-6774 Terry.m.endres@baml.com
Fraud Protection, You and Your Bank Maximize your chances to minimize your losses Presentation for Missouri GFOA April 2011 By: Terry Endres, VP, Government Treasury Solutions Phone: 314-466-6774 Terry.m.endres@baml.com
Payment Card Industry (PCI) Data Security Standard. PCI DSS Applicability in an EMV Environment A Guidance Document Version 1
 Payment Card Industry (PCI) Data Security Standard PCI DSS Applicability in an EMV Environment A Guidance Document Version 1 Release date: 5 October 2010 Table of Contents 1 Executive Summary... 3 1.1
Payment Card Industry (PCI) Data Security Standard PCI DSS Applicability in an EMV Environment A Guidance Document Version 1 Release date: 5 October 2010 Table of Contents 1 Executive Summary... 3 1.1
Fraud Prevention and Program Security Gord Jamieson Director Risk Management & Security Visa Canada Association
 Fraud Prevention and Program Security Gord Jamieson Director Risk Management & Security Visa Canada Association Evolution of Risk Management Controls Presentation text goes here. Presentation text goes
Fraud Prevention and Program Security Gord Jamieson Director Risk Management & Security Visa Canada Association Evolution of Risk Management Controls Presentation text goes here. Presentation text goes
Understanding Credit Card Frauds
 Cards Business Review#2003 01 Understanding Credit Card Frauds Tej Paul Bhatla, Vikram Prabhu & Amit Dua June 2003 Tata Consultancy Services 2002. All rights reserved. CONTENTS OVERVIEW...1 INTRODUCTION...1
Cards Business Review#2003 01 Understanding Credit Card Frauds Tej Paul Bhatla, Vikram Prabhu & Amit Dua June 2003 Tata Consultancy Services 2002. All rights reserved. CONTENTS OVERVIEW...1 INTRODUCTION...1
Practically Thinking: What Small Merchants Should Know about EMV
 Practically Thinking: What Small Merchants Should Know about EMV 1 Practically Thinking: What Small Merchants Should Know About EMV Overview Savvy business owners know that payments are about more than
Practically Thinking: What Small Merchants Should Know about EMV 1 Practically Thinking: What Small Merchants Should Know About EMV Overview Savvy business owners know that payments are about more than
Payment Cardholder Data Handling Procedures (required to accept any credit card payments)
 Payment Cardholder Data Handling Procedures (required to accept any credit card payments) Introduction: The Procedures that follow will allow the University to be in compliance with the Payment Card Industry
Payment Cardholder Data Handling Procedures (required to accept any credit card payments) Introduction: The Procedures that follow will allow the University to be in compliance with the Payment Card Industry
PROTECT YOUR BUSINESS FROM LOSSES WHILE ACCEPTING CREDIT CARDS
 PROTECT YOUR BUSINESS FROM LOSSES WHILE ACCEPTING CREDIT CARDS TABLE OF CONTENTS Introduction...1 Preventing Fraud in a Card-Present Environment...2 How to Reduce Chargebacks in a Card-Present Environment...4
PROTECT YOUR BUSINESS FROM LOSSES WHILE ACCEPTING CREDIT CARDS TABLE OF CONTENTS Introduction...1 Preventing Fraud in a Card-Present Environment...2 How to Reduce Chargebacks in a Card-Present Environment...4
The Adoption of EMV Technology in the U.S. By Dave Ewald Global Industry Sales Consultant Datacard Group
 The Adoption of EMV Technology in the U.S. By Dave Ewald Global Industry Sales Consultant Datacard Group Abstract: Visa Inc. and MasterCard recently announced plans to accelerate chip migration in the
The Adoption of EMV Technology in the U.S. By Dave Ewald Global Industry Sales Consultant Datacard Group Abstract: Visa Inc. and MasterCard recently announced plans to accelerate chip migration in the
A RE T HE U.S. CHIP RULES ENOUGH?
 August 2015 A RE T HE U.S. CHIP RULES ENOUGH? A longer term view of security and the payments landscape is needed. Abstract: The United States is finally modernizing its card payment systems and confronting
August 2015 A RE T HE U.S. CHIP RULES ENOUGH? A longer term view of security and the payments landscape is needed. Abstract: The United States is finally modernizing its card payment systems and confronting
Merchant Guide to the Visa Address Verification Service
 Merchant Guide to the Visa Address Verification Service Merchant Guide to the Visa Address Verification Service TABLE OF CONTENTS Table of Contents Merchant Guide to the Visa Address Verification Service
Merchant Guide to the Visa Address Verification Service Merchant Guide to the Visa Address Verification Service TABLE OF CONTENTS Table of Contents Merchant Guide to the Visa Address Verification Service
Card Technology Choices for U.S. Issuers An EMV White Paper
 Card Technology Choices for U.S. Issuers An EMV White Paper This white paper is written with the aim of educating Issuers in the United States on the various technology choices that they have to consider
Card Technology Choices for U.S. Issuers An EMV White Paper This white paper is written with the aim of educating Issuers in the United States on the various technology choices that they have to consider
How To Understand The Law Of Credit Card Usage
 Glossary Note: All definitions listed in this section are also available in the Course Glossary. You can access the course Glossary online by clicking the Glossary link in the Materials section of the
Glossary Note: All definitions listed in this section are also available in the Course Glossary. You can access the course Glossary online by clicking the Glossary link in the Materials section of the
Merchant Payment Solutions
 Merchant Payment Solutions What We Do Connecting your Web site to the payment processing networks is typically beyond the technical resources of most merchants. Instead, you can easily connect to the Authorize.Net
Merchant Payment Solutions What We Do Connecting your Web site to the payment processing networks is typically beyond the technical resources of most merchants. Instead, you can easily connect to the Authorize.Net
GLOSSARY OF MOST COMMONLY USED TERMS IN THE MERCHANT SERVICES INDUSTRY
 GLOSSARY OF MOST COMMONLY USED TERMS IN THE MERCHANT SERVICES INDUSTRY Acquiring Bank The bank or financial institution that accepts credit and/or debit card payments for products or services on behalf
GLOSSARY OF MOST COMMONLY USED TERMS IN THE MERCHANT SERVICES INDUSTRY Acquiring Bank The bank or financial institution that accepts credit and/or debit card payments for products or services on behalf
Payment Card Industry (PCI) Data Security Standard
 Payment Card Industry (PCI) Data Standard Attestation of Compliance for Self-Assessment Questionnaire D Service Providers Version 3.1 April 2015 Section 1: Assessment Information Instructions for Submission
Payment Card Industry (PCI) Data Standard Attestation of Compliance for Self-Assessment Questionnaire D Service Providers Version 3.1 April 2015 Section 1: Assessment Information Instructions for Submission
Fall Conference November 19 21, 2013 Merchant Card Processing Overview
 Fall Conference November 19 21, 2013 Merchant Card Processing Overview Agenda Industry Definition Process Flows Processing Costs Chargeback's Payment Card Industry (PCI) Guidelines for Convenience Fees
Fall Conference November 19 21, 2013 Merchant Card Processing Overview Agenda Industry Definition Process Flows Processing Costs Chargeback's Payment Card Industry (PCI) Guidelines for Convenience Fees
Payment Card Industry (PCI) Data Security Standard
 Payment Card Industry (PCI) Data Security Standard Attestation of Compliance for Self-Assessment Questionnaire D Service Providers For use with PCI DSS Version 3.1 Revision 1.1 July 2015 Section 1: Assessment
Payment Card Industry (PCI) Data Security Standard Attestation of Compliance for Self-Assessment Questionnaire D Service Providers For use with PCI DSS Version 3.1 Revision 1.1 July 2015 Section 1: Assessment
Payments Transformation - EMV comes to the US
 Accenture Payment Services Payments Transformation - EMV comes to the US In 1993 Visa, MasterCard and Europay (EMV) came together and formed EMVCo 1 to tackle the global challenge of combatting fraudulent
Accenture Payment Services Payments Transformation - EMV comes to the US In 1993 Visa, MasterCard and Europay (EMV) came together and formed EMVCo 1 to tackle the global challenge of combatting fraudulent
Fundamentals of EMV. Guy Berg Senior Managing Consultant MasterCard Advisors guy_berg@mastercard.com 914.325.8111
 Fundamentals of EMV Guy Berg Senior Managing Consultant MasterCard Advisors guy_berg@mastercard.com 914.325.8111 EMV Fundamentals Transaction Processing Comparison Magnetic Stripe vs. EMV Transaction Security
Fundamentals of EMV Guy Berg Senior Managing Consultant MasterCard Advisors guy_berg@mastercard.com 914.325.8111 EMV Fundamentals Transaction Processing Comparison Magnetic Stripe vs. EMV Transaction Security
Merchant Payment Solutions
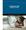 Merchant Payment Solutions Credit Card Processing Diagram CUSTOMER S CREDIT CARD ISSUING BANK CUSTOMER 4 5 $ MERCHANT S BUSINESS MERCHANT S BANK ACCOUNT MERCHANT S BANK 9 CREDIT CARD NETWORK 8 INTERNET
Merchant Payment Solutions Credit Card Processing Diagram CUSTOMER S CREDIT CARD ISSUING BANK CUSTOMER 4 5 $ MERCHANT S BUSINESS MERCHANT S BANK ACCOUNT MERCHANT S BANK 9 CREDIT CARD NETWORK 8 INTERNET
E M V I M P L E M E N TAT I O N T O O L S F O R S U C C E S S, P C I & S E C U R I T Y. February 2014
 E M V I M P L E M E N TAT I O N T O O L S F O R S U C C E S S, P C I & S E C U R I T Y February 2014 A G E N D A EMV Overview EMV Industry Announcements EMV Transaction Differences, What to Expect Solution
E M V I M P L E M E N TAT I O N T O O L S F O R S U C C E S S, P C I & S E C U R I T Y February 2014 A G E N D A EMV Overview EMV Industry Announcements EMV Transaction Differences, What to Expect Solution
The need for a secure & trusted payment instrument in e-commerce. Ali AlMeshal
 The need for a secure & trusted payment instrument in e-commerce Ali AlMeshal In Physical/Real World Hand over card Visual check Swipe in POS Online authorization Receipt with signature panel Sign or Pin
The need for a secure & trusted payment instrument in e-commerce Ali AlMeshal In Physical/Real World Hand over card Visual check Swipe in POS Online authorization Receipt with signature panel Sign or Pin
How To Comply With The New Credit Card Chip And Pin Card Standards
 My main responsibility as a Regional Account Manager for IMD is obtain the absolute lowest possible merchant fees for you as a business. Why? The more customers we can save money, the more volume of business
My main responsibility as a Regional Account Manager for IMD is obtain the absolute lowest possible merchant fees for you as a business. Why? The more customers we can save money, the more volume of business
Credit card: permits consumers to purchase items while deferring payment
 General Payment Systems Cash: portable, no authentication, instant purchasing power, allows for micropayments, no transaction fee for using it, anonymous But Easily stolen, no float time, can t easily
General Payment Systems Cash: portable, no authentication, instant purchasing power, allows for micropayments, no transaction fee for using it, anonymous But Easily stolen, no float time, can t easily
NEWS BULLETIN 2015-16
 NEWS BULLETIN Maine Automobile Dealers Association 180 Civic Center Drive P. O. Box 2667 Augusta, Maine 04338-2667 DIAL 623-3882 e-mail:info@maineautodealers.com FAX 623-2318 DISTRIBUTION General Manager
NEWS BULLETIN Maine Automobile Dealers Association 180 Civic Center Drive P. O. Box 2667 Augusta, Maine 04338-2667 DIAL 623-3882 e-mail:info@maineautodealers.com FAX 623-2318 DISTRIBUTION General Manager
OT PRODUCTS AND SOLUTIONS EMV-IN-A-BOX
 OT PRODUCTS AND SOLUTIONS EMV-IN-A-BOX FOR A SMOOTH MIGRATION EMV DUAL INTERFACE CARDS WILL REPRESENT 50% OF 2016 SHIPMENTS FRAUD PERCENTAGE IS DIVIDED BY 6 IN EMV COUNTRIES COMPARED TO WORLDWIDE AVERAGE
OT PRODUCTS AND SOLUTIONS EMV-IN-A-BOX FOR A SMOOTH MIGRATION EMV DUAL INTERFACE CARDS WILL REPRESENT 50% OF 2016 SHIPMENTS FRAUD PERCENTAGE IS DIVIDED BY 6 IN EMV COUNTRIES COMPARED TO WORLDWIDE AVERAGE
The following information was prepared to assist you in understanding potential Electronic Value Transfer terminology.
 ELECTRONIC VALUE TRANSFER CONTRACT (EVT) GLOSSARY OF TERMS The following information was prepared to assist you in understanding potential terminology. Term Description ACH Automated Clearing House is
ELECTRONIC VALUE TRANSFER CONTRACT (EVT) GLOSSARY OF TERMS The following information was prepared to assist you in understanding potential terminology. Term Description ACH Automated Clearing House is
Realex Payments Integration Guide - Ecommerce Remote Integration. Version: v1.1
 Realex Payments Integration Guide - Ecommerce Remote Integration Version: v1.1 Document Information Document Name: Realex Payments Integration Guide Ecommerce Remote Integration Document Version: 1.1 Release
Realex Payments Integration Guide - Ecommerce Remote Integration Version: v1.1 Document Information Document Name: Realex Payments Integration Guide Ecommerce Remote Integration Document Version: 1.1 Release
Enabling cross-border expansion through fraud management. 24 September, 2015 Anthony Yeung
 Enabling cross-border expansion through fraud management 24 September, 2015 Anthony Yeung 1 Biggest strategic challenges over next 12 Months Cross-border 18% of merchants felt that international expansion
Enabling cross-border expansion through fraud management 24 September, 2015 Anthony Yeung 1 Biggest strategic challenges over next 12 Months Cross-border 18% of merchants felt that international expansion
Address Verification System (AVS) Checking
 Address Verification System (AVS) Checking The Address Verification System (AVS) is a service provided by credit card Issuers intended to authenticate the Purchaser (Customer) as the authorized cardholder.
Address Verification System (AVS) Checking The Address Verification System (AVS) is a service provided by credit card Issuers intended to authenticate the Purchaser (Customer) as the authorized cardholder.
Becoming PCI Compliant
 Becoming PCI Compliant Jason Brown - brownj52@michigan.gov Enterprise Security Architect Enterprise Architecture Department of Technology, Management and Budget State of Michigan @jasonbrown17 History
Becoming PCI Compliant Jason Brown - brownj52@michigan.gov Enterprise Security Architect Enterprise Architecture Department of Technology, Management and Budget State of Michigan @jasonbrown17 History
