DEFENSE NETWORK FAQS DATA SHEET
|
|
|
- Hubert Pearson
- 8 years ago
- Views:
Transcription
1 DATA SHEET VERISIGN INTERNET DEFENSE NETWORK FAQS WHAT IS A DOS OR DDOS ATTACK? A Denial of Service attack or Distributed Denial of Service attack occurs when a single host (DoS), or multiple hosts (DDoS), send legitimate traffic to a target with malicious intent for the purpose of disrupting an application or service either temporarily or permanently. Targets can include, but are not limited to Web servers, DNS servers, application servers, routers, firewalls, and Internet bandwidth. WHAT IS IN-THE-CLOUD? The term cloud is used as a symbol or metaphor for the Internet, based on the way the Internet is depicted in network diagrams. In-the-Cloud typically refers to a service that is provided/performed for a customer before it enters their Internet service connection(s)/ infrastructure. Essentially, an In-the-Cloud DDoS protection service redirects traffic destined for an organization through an Internet data center, where undesirable items like DDoS packets are dropped. The cleansed traffic is then delivered to the organization. IS THE VERISIGN INTERNET DEFENSE NETWORK A COMPLEMENTARY SERVICE OR WOULD IT REPLACE OUR FIREWALL, INTRUSION PREVENTION SYSTEM (IPS)/ INTRUSION DETECTION SYSTEM (IDS), AND/OR OTHER SECURITY PRODUCTS WITHIN OUR NETWORK INFRASTRUCTURE? The Verisign Internet Defense Network is a complementary service and is not intended to replace existing security infrastructure. I HAVE MULTIPLE INTERNET CARRIER CIRCUITS FROM DIFFERENT INTERNET SERVICE PROVIDERS (ISP S). CAN THE VERISIGN INTERNET DEFENSE NETWORK WORK WITH MY SOLUTION? Yes, the Verisign Internet Defense Network can monitor and mitigate DDoS attacks on any ISP, and can provide the same level of service for customers who are multi-homed through more than one ISP. This means a customer only has to deal with one team and one threat remediation process in order to knock down the attack, rather than relying on multiple bandwidth providers to reach similar conclusions on the same timelines. Since our solution is network agnostic, you have the flexibility to change your infrastructure to suit your changing business needs. HOW LONG DOES IT TAKE TO DEPLOY THE VERISIGN INTERNET DEFENSE NETWORK? It typically takes less than fourteen (14) calendar days to set up the monitoring solution and start receiving customer flow traffic. HOW LONG BEFORE I AM CONTACTED ABOUT A DDOS ATTACK TO MY NETWORK OR APPLICATION? WHAT KIND OF SERVICE LEVEL AGREEMENT (SLA) IS PROVIDED WITH THE VERISIGN INTERNET DEFENSE NETWORK? Typically, customers are notified of a potential attack within five minutes of a monitoring alert being generated. The SLA currently provided states that Verisign will contact the customer in accordance with its escalation plan within 15 minute of receipt of a monitoring alert. Upon contact, Verisign will work with the customer to determine if mitigation is required or if the alert was caused by legitimate customer activity. If mitigation is needed, Verisign will recommend the best course of action.
2 In the event that redirecting the customer s traffic is the recommended course of action, the customer s traffic will be redirected to Verisign s Internet Defense Network sites before reaching the customer s network. Verisign will apply layered filters to the traffic redirected to the Verisign Internet Defense Network sites which progressively block traffic aimed at disrupting or disabling the customer s Internet-based services. Legitimate traffic is then redirected from the Verisign Internet Defense Network sites back to the Customer s network. When the DDoS attack has abated, Verisign will coordinate with the Customer in order to return the Customer to its normal operations. IS THERE ANY MANUAL INTERVENTION DONE ON MY INFRASTRUCTURE DURING A DDOS ATTACK? Verisign establishes event mitigation procedures with you to fit your service model. Optimal solutions vary and depend upon network size and types of services utilized, among other considerations. If Internet traffic is redirected using our BGP off-ramping, no manual intervention is needed on the customer network. If traffic is redirected via DNS, you will need to point your A records to a Verisign IP address and set the time-to-live, TTL, to the minimum time for redistribution. After mitigation, traffic is proxied back to you. WHAT IS THE PROCESS FLOW DURING AN ATTACK SITUATION? When an alert is generated the Verisign support team contacts the customer, provides them with a ticket number and begins investigation. Once the alert is determined to be a DDoS event a recommendation is made to mitigate. Our SLA is to contact the customer with a recommendation on a mitigation strategy within 15 minutes after receipt of an alert. With customer permission, in order to mitigate the DDoS attack Verisign will swing traffic to a mitigation facility or facilities. The Verisign Internet Defense Network support team begins further analysis of the source of the attack and begins to reach to upstream providers to resolve the attack closer to the source, as needed. DO YOU CONTACT THE CUSTOMER AFTER THE DOS/ DDOS ATTACK HAS STOPPED? Yes. One of our Verisign Security Operations personnel will contact the company representative identified in the escalation plan to discuss moving traffic back to its original path. CAN I SETUP MY ROUTER TO THWART A DDOS ATTACK? Routers cannot block spoofed IP sources or manually traceback to thousands of IP addresses, which makes Access Control Lists (ACLs) useless against DDoS attacks. CAN I SETUP MY FIREWALL TO THWART A DDOS ATTACK? Firewalls are not designed to mitigate DDoS attacks. Using a firewall for mitigation could cause the CPU to spike and deplete memory resources. Also, firewalls don t have anomaly detection capabilities. CAN I SETUP MY INLINE IPS OR MY IDS TO THWART A DDOS ATTACK? Yes, but IPSs and IDSs require extensive manual tuning that takes time and can leave you vulnerable. An IDS traditionally sits behind the firewall with an uplink to a router or switch that sits in front of the firewall. An IDS issues an alert when it detects an anomaly. At that point, the attack traffic is already consuming your internet bandwidth with the potential of saturating the link, which can cause the CPU to spike and deplete memory resources. An IPS has the capability to work as an anomaly detector; however, it requires several weeks for an IPS to understand normal traffic patterns and frequent manual tuning to specify which traffic is allowed and which should be alerted or blocked. I HAVE OVER-PROVISIONED X AMOUNT OF BANDWIDTH TO TRY TO PREVENT DDOS ATTACKS. WHAT CAN THE VERISIGN INTERNET DEFENSE NETWORK DO FOR ME? Over-provisioning is not a cost effective solution. For example, if you know your normal amount of traffic
3 could reach 15Mbps, but provision 30Mbps in the event of a DDoS attack, you have over-provisioned by 100 percent and doubled your monthly recurring charges. And attackers can easily increase the volume of their attacks. Since some DDoS attacks now reach more than 40 Gbps, over-provisioning an Internet circuit could become very costly. WHAT ABOUT BLACKHOLING THE IP ADDRESS(ES)? Blackholing an IP address or a range of IP addresses can result in legitimate packets being discarded along with malicious attack traffic, which means the attacker wins. If an ISP performs the blackhole, they must first identify the source of the traffic, which can cost valuable time, and may still end up blocking legitimate traffic. WHERE ARE THE VERISIGN MITIGATION DATACENTERS LOCATED? Ashburn, Virginia San Francisco, California Amsterdam, Netherlands Tokyo, Japan ARE THE VERISIGN INTERNET DEFENSE NETWORK DATACENTERS IDENTICAL IN TYPES OF MITIGATION GEAR AND CAPACITY? All the Verisign Internet Defense Network datacenters are identical in capacity: dual 10 Gigabit Ethernet. Because we are NOT dependent on any hardware vendor or service provider, our datacenters do NOT have identical gear. WHAT DOES THE VERISIGN SOLUTION DO WITH DATA RETENTION? HOW LONG IS DATA KEPT IN STORAGE? Our current data retention policy is: Mitigation Events = 1 year DoS alerts (low) = 30 days DoS alerts (medium) = 60 days DoS alerts (high) = 90 days Traffic Reports = 60 days This is subject to change and does not constitute a guarantee. Please consult your Verisign representative for details. HOW DO CUSTOMERS GET TRAFFIC REPORTS? Traffic reports can be generated via the portal and then exported to a XML or PDF file. WHAT KIND OF DEVICE OR DEVICES DOES A POTENTIAL CUSTOMER NEED AT THEIR FACILITY? The Verisign Internet Defense Network supports the following equipment: Cisco routers Peakflow SP 4.5 supports the following Cisco routers Cisco traditional IOS-based routers that run IOS 12.0 or later (Netflow v5 and v9) Cisco Catalyst 4500 family w/sup IV or later and NFFC (Netflow v5) Cisco Catalyst 5500 family w/suitable Sup and NFFC (Netflow v7) Cisco Catalyst 6500 family w/sup 2 or later, hybrid or native (Netflow v5 and v7) Cisco CRS-1 (Netflow v9) Important: Cisco Catalyst routers do not support TCP flags. Juniper cflowd v9 traffic Juniper cflowd v9 is supported only for IP traffic. Cflowd data from MPLS-derived traffic might not work with current JunOS software and Peakflow SP does not officially support it.
4 Juniper routers Peakflow SP 4.5 supports the following Juniper routers Juniper T-series (cflowd v5, or v9 with services PIC) Juniper M-series with Internet Processor II (cflowd v5, or v9 with services PIC) Juniper J-series (cflowd v5) Juniper TX-series (cflowd v9) Juniper MX960 (cflowd v5) Devices or other vendors that can provide flow data or IPFIX will be handled on a case-by-case basis. Foundry routers Peakflow SP supports Foundry routers with sflow v2, v4, and v5. Foundry does not support ACL generation Force10 routers Peakflow SP supports Force10 routers with sflow DO I NEED TO PURCHASE A CIRCUIT TO THE VERISIGN INTERNET DEFENSE NETWORK DATACENTER SO MY TRAFFIC CAN BE REDIRECTED? You have the option to purchase a circuit to one of the Verisign Internet Defense Network datacenters or we can redirect/on-ramp your traffic with a GRE tunnel (most preferred) or a VPN tunnel. ARE THERE ANY REQUIREMENTS REGARDING IP ADDRESS SPACE? In order for Verisign to off-ramp your traffic via BGP, you must have a minimum of /24 or 254 continuous IP address spaces. The /24 can be obtained from your Internet Service Provider or from ARIN, APNIC, RIPE, AFRINIC or LACNIC. North America Asia Pacific Europe Africa Latin America and Carribbean IS IT POSSIBLE FOR THE VERISIGN INTERNET DEFENSE NETWORK SOLUTION TO PROTECT JUST A SINGLE WEB SERVER? Yes, in the case of a single Web server we can divert traffic with a DNS change. However, you will need to make some changes to your system. We will provide Verisign IP addresses for you so you can change the A record in your (or your ISP s) managed DNS server to the newly assigned Verisign IP address. WHEN THE CUSTOMER S TRAFFIC IS OFF-RAMPED TO VERISIGN, IS THERE ANY LATENCY THAT NEEDS TO BE FACTORED INTO THE EQUATION? Latency is determined by the distance between the customer s protected facility and the Verisign Internet Defense Network data center. Verisign has extensive public and private peering at most of the global Internet exchange points; this allows Verisign optimal routing paths throughout the Internet. Verisign also distributes data centers geographically to minimize latency. Centers are located in the Washington DC Metro area, Silicon Valley/San Francisco Bay area, Amsterdam, and Tokyo. Customers in these markets should expect no measurable latency increase (<5 ms). Beyond these metro markets, customers in the US could experience additional latency of ms per 1,000 miles of distance from the data center. Past experience indicates that from one US coast to the other US coast latency averages around 30-35ms. IT CAN TAKE OVER 30 MINUTES FOR BORDER GATEWAY PROTOCOL (BGP) TO ANNOUNCE A CUSTOMER NETWORK BLOCK. BEFORE VERISIGN HAS THE ABILITY TO START FILTERING TRAFFIC, WHAT MEASURES ARE USED TO DECREASE THE CONVERGENCE TIME? Verisign has studied the issue of BGP convergence time in depth. Verisign uses a BGP route monitoring industry leader that has hundreds of BGP probes all over the globe with thousands of BGP feeds. Verisign uses this tool to track the time it takes
5 for BGP updates to propagate across the Internet. While convergence time isn t completely controllable or predictable, we typically see all the BGP feeds converge on the new protected path in two (2) minutes or less. Verisign advises customers to expect convergence time to be around five (5) minutes, but we have seen the time be much less. Verisign has been using BGP announcement techniques to failover critical.com and.net critical infrastructure services for years. HOW DOES VERISIGN LEVERAGE THEIR RELATIONS WITH OTHER ISPS DURING AN ATTACK THAT THE CUSTOMER CANNOT MITIGATE ON ITS OWN? Verisign has extensive public and private peering at most of the global Internet exchange points, giving Verisign the ability to reach close to 60% of the Internet via peering. As a critical infrastructure provider, Verisign participates with most large networks in the same operational security forums Tier 1, 2, and 3 carriers use to interact with each other. When a customer has an issue, Verisign can leverage those relationships to interact directly with the carriers in the same forums and ways those networks work with one another. HOW DOES VERISIGN BEST WORK WITH ENCRYPTED DATA (SSL) TO UNDERSTAND THE NATURE OF AN ATTACK? If only the payload is encrypted and customers do not want to exchange keys, we can filter only the headers or anything outside the payload. If the customer is willing to provide exchange keys, we can decrypt -> filter -> and re-encrypt the packet and send it to the customer via a secure return path. CAN THE VERISIGN INTERNET DEFENSE NETWORK WORK WITH THE CUSTOMER S MONITORING, MITIGATION OR CORRELATION GEAR DEPLOYED IN THE NETWORK INFRASTRUCTURE? Verisign will evaluate such deployed gear on a case-by-case basis and determine whether it can be integrated with the Verisign Internet Defense Network. DOES THE VERISIGN SUPPORT IPV6? We are testing IPv6 with the Verisign Internet Defense Network, but do not have an availability date yet. ABOUT VERISIGN Verisign is the trusted provider of Internet infrastructure services for the digital world. Billions of times each day, companies and consumers rely on our Internet infrastructure to communicate and conduct commerce with confidence. LEARN MORE For more information about the Verisign Internet Defense Network, please contact a Verisign representative by phone at or , by at ddos@verisign.com, or visit us at VerisignInc.com 2011 Verisign, Inc. All rights reserved. VERISIGN and other trademarks, service marks, and designs are registered or unregistered trademarks of Verisign, Inc. and its subsidiaries in the United States and in foreign countries. PMS is a trademark of Pantone, Inc. All other trademarks are property of their respective owners.
DDoS Protection. How Cisco IT Protects Against Distributed Denial of Service Attacks. A Cisco on Cisco Case Study: Inside Cisco IT
 DDoS Protection How Cisco IT Protects Against Distributed Denial of Service Attacks A Cisco on Cisco Case Study: Inside Cisco IT 1 Overview Challenge: Prevent low-bandwidth DDoS attacks coming from a broad
DDoS Protection How Cisco IT Protects Against Distributed Denial of Service Attacks A Cisco on Cisco Case Study: Inside Cisco IT 1 Overview Challenge: Prevent low-bandwidth DDoS attacks coming from a broad
How Cisco IT Protects Against Distributed Denial of Service Attacks
 How Cisco IT Protects Against Distributed Denial of Service Attacks Cisco Guard provides added layer of protection for server properties with high business value. Cisco IT Case Study / < Security and VPN
How Cisco IT Protects Against Distributed Denial of Service Attacks Cisco Guard provides added layer of protection for server properties with high business value. Cisco IT Case Study / < Security and VPN
VERISIGN DDOS PROTECTION SERVICES IN-THE-CLOUD SOLUTION FOR SCALABLE, RELIABLE, AND FLEXIBLE DDOS MONITORING AND MITIGATION
 WHITE PAPER VERISIGN DDOS PROTECTION SERVICES IN-THE-CLOUD SOLUTION FOR SCALABLE, RELIABLE, AND FLEXIBLE DDOS MONITORING AND MITIGATION VerisignInc.com CONTENTS DDOS GAINING GROUND ON ALL FRONTS 3 THE
WHITE PAPER VERISIGN DDOS PROTECTION SERVICES IN-THE-CLOUD SOLUTION FOR SCALABLE, RELIABLE, AND FLEXIBLE DDOS MONITORING AND MITIGATION VerisignInc.com CONTENTS DDOS GAINING GROUND ON ALL FRONTS 3 THE
Traffic Diversion Techniques for DDoS Mitigation using BGP Flowspec. Leonardo Serodio leonardo.serodio@alcatel-lucent.com May 2013
 Traffic Diversion Techniques for DDoS Mitigation using BGP Flowspec Leonardo Serodio leonardo.serodio@alcatel-lucent.com May 2013 Distributed Denial of Service (DDoS) Attacks DDoS attack traffic consumes
Traffic Diversion Techniques for DDoS Mitigation using BGP Flowspec Leonardo Serodio leonardo.serodio@alcatel-lucent.com May 2013 Distributed Denial of Service (DDoS) Attacks DDoS attack traffic consumes
VERISIGN DDoS PROTECTION SERVICES CUSTOMER HANDBOOK
 HANDBOOK VERISIGN DDoS PROTECTION SERVICES CUSTOMER HANDBOOK CONSIDERATIONS FOR SERVICE ADOPTION Version 1.0 July 2014 VerisignInc.com CONTENTS 1. WHAT IS A DDOS PROTECTION SERVICE? 3 2. HOW CAN VERISIGN
HANDBOOK VERISIGN DDoS PROTECTION SERVICES CUSTOMER HANDBOOK CONSIDERATIONS FOR SERVICE ADOPTION Version 1.0 July 2014 VerisignInc.com CONTENTS 1. WHAT IS A DDOS PROTECTION SERVICE? 3 2. HOW CAN VERISIGN
How To Stop A Ddos Attack On A Network From Tracing To Source From A Network To A Source Address
 Inter-provider Coordination for Real-Time Tracebacks Kathleen M. Moriarty 2 June 2003 This work was sponsored by the Air Force Contract number F19628-00-C-002. Opinions, interpretations, conclusions, and
Inter-provider Coordination for Real-Time Tracebacks Kathleen M. Moriarty 2 June 2003 This work was sponsored by the Air Force Contract number F19628-00-C-002. Opinions, interpretations, conclusions, and
DDoS Overview and Incident Response Guide. July 2014
 DDoS Overview and Incident Response Guide July 2014 Contents 1. Target Audience... 2 2. Introduction... 2 3. The Growing DDoS Problem... 2 4. DDoS Attack Categories... 4 5. DDoS Mitigation... 5 1 1. Target
DDoS Overview and Incident Response Guide July 2014 Contents 1. Target Audience... 2 2. Introduction... 2 3. The Growing DDoS Problem... 2 4. DDoS Attack Categories... 4 5. DDoS Mitigation... 5 1 1. Target
Availability Digest. www.availabilitydigest.com. Prolexic a DDoS Mitigation Service Provider April 2013
 the Availability Digest Prolexic a DDoS Mitigation Service Provider April 2013 Prolexic (www.prolexic.com) is a firm that focuses solely on mitigating Distributed Denial of Service (DDoS) attacks. Headquartered
the Availability Digest Prolexic a DDoS Mitigation Service Provider April 2013 Prolexic (www.prolexic.com) is a firm that focuses solely on mitigating Distributed Denial of Service (DDoS) attacks. Headquartered
CISCO INFORMATION TECHNOLOGY AT WORK CASE STUDY: CISCO IOS NETFLOW TECHNOLOGY
 CISCO INFORMATION TECHNOLOGY AT WORK CASE STUDY: CISCO IOS NETFLOW TECHNOLOGY CISCO INFORMATION TECHNOLOGY SEPTEMBER 2004 1 Overview Challenge To troubleshoot capacity and quality problems and to understand
CISCO INFORMATION TECHNOLOGY AT WORK CASE STUDY: CISCO IOS NETFLOW TECHNOLOGY CISCO INFORMATION TECHNOLOGY SEPTEMBER 2004 1 Overview Challenge To troubleshoot capacity and quality problems and to understand
Fireware How To Dynamic Routing
 Fireware How To Dynamic Routing How do I configure my Firebox to use BGP? Introduction A routing protocol is the language a router speaks with other routers to share information about the status of network
Fireware How To Dynamic Routing How do I configure my Firebox to use BGP? Introduction A routing protocol is the language a router speaks with other routers to share information about the status of network
Securing data centres: How we are positioned as your ISP provider to prevent online attacks.
 Securing data centres: How we are positioned as your ISP provider to prevent online attacks. Executive Summary In today s technologically-demanding world, an organisation that experiences any internet
Securing data centres: How we are positioned as your ISP provider to prevent online attacks. Executive Summary In today s technologically-demanding world, an organisation that experiences any internet
FortiDDos Size isn t everything
 FortiDDos Size isn t everything Martijn Duijm Director Sales Engineering April - 2015 Copyright Fortinet Inc. All rights reserved. Agenda 1. DDoS In The News 2. Drawing the Demarcation Line - Does One
FortiDDos Size isn t everything Martijn Duijm Director Sales Engineering April - 2015 Copyright Fortinet Inc. All rights reserved. Agenda 1. DDoS In The News 2. Drawing the Demarcation Line - Does One
TDC s perspective on DDoS threats
 TDC s perspective on DDoS threats DDoS Dagen Stockholm March 2013 Lars Højberg, Technical Security Manager, TDC TDC in Sweden TDC in the Nordics 9 300 employees (2012) Turnover: 26,1 billion DKK (2012)
TDC s perspective on DDoS threats DDoS Dagen Stockholm March 2013 Lars Højberg, Technical Security Manager, TDC TDC in Sweden TDC in the Nordics 9 300 employees (2012) Turnover: 26,1 billion DKK (2012)
Cisco Network Foundation Protection Overview
 Cisco Network Foundation Protection Overview June 2005 1 Security is about the ability to control the risk incurred from an interconnected global network. Cisco NFP provides the tools, technologies, and
Cisco Network Foundation Protection Overview June 2005 1 Security is about the ability to control the risk incurred from an interconnected global network. Cisco NFP provides the tools, technologies, and
Cisco IOS Flexible NetFlow Technology
 Cisco IOS Flexible NetFlow Technology Last Updated: December 2008 The Challenge: The ability to characterize IP traffic and understand the origin, the traffic destination, the time of day, the application
Cisco IOS Flexible NetFlow Technology Last Updated: December 2008 The Challenge: The ability to characterize IP traffic and understand the origin, the traffic destination, the time of day, the application
MANAGED SECURITY SERVICES : IP AGNOSTIC DDOS AN IP AGNOSTIC APPROACH TO DISTRIBUTED DENIAL OF SERVICE DETECTION AND MITIGATION
 AN IP AGNOSTIC APPROACH TO DISTRIBUTED DENIAL OF SERVICE DETECTION AND MITIGATION Overview Distributed Denial of Service (DDoS) attacks saturate target networks with service requests that consume the capacity
AN IP AGNOSTIC APPROACH TO DISTRIBUTED DENIAL OF SERVICE DETECTION AND MITIGATION Overview Distributed Denial of Service (DDoS) attacks saturate target networks with service requests that consume the capacity
We keep internet traffic flowing Frank Ip VP of Marketing and Business Development
 We keep internet traffic flowing Frank Ip VP of Marketing and Business Development WHD 2015 Presentation SLA 1 I will make it short 2 3 Hopefully, it will be informative You can ask questions, but I probably
We keep internet traffic flowing Frank Ip VP of Marketing and Business Development WHD 2015 Presentation SLA 1 I will make it short 2 3 Hopefully, it will be informative You can ask questions, but I probably
Telecom Business Continuity Solutions FOR INTERNAL USE ONLY
 Telecom Business Continuity Solutions FOR INTERNAL USE ONLY Business continuity? Perception versus reality Perceived biggest threats in 2005* Events causing disruption in 2003-04** IT / Telecom protection
Telecom Business Continuity Solutions FOR INTERNAL USE ONLY Business continuity? Perception versus reality Perceived biggest threats in 2005* Events causing disruption in 2003-04** IT / Telecom protection
Data Sheet. V-Net Link 700 C Series Link Load Balancer. V-NetLink:Link Load Balancing Solution from VIAEDGE
 Data Sheet V-Net Link 700 C Series Link Load Balancer V-NetLink:Link Load Balancing Solution from VIAEDGE V-NetLink : Link Load Balancer As the use of the Internet to deliver organizations applications
Data Sheet V-Net Link 700 C Series Link Load Balancer V-NetLink:Link Load Balancing Solution from VIAEDGE V-NetLink : Link Load Balancer As the use of the Internet to deliver organizations applications
Pacnet Premium Dedicated Internet Access Dedicated Internet Access for Web-Centric Enterprises
 Products and Services INTERNET ACCESS Pacnet Premium Dedicated Internet Access Dedicated Internet Access for Web-Centric Enterprises MEETING THE CRITICAL DEMANDS OF TODAY S MULTI-SITE ENTERPRISES Enterprises
Products and Services INTERNET ACCESS Pacnet Premium Dedicated Internet Access Dedicated Internet Access for Web-Centric Enterprises MEETING THE CRITICAL DEMANDS OF TODAY S MULTI-SITE ENTERPRISES Enterprises
Virtual Privacy vs. Real Security
 Virtual Privacy vs. Real Security Certes Networks at a glance Leader in Multi-Layer Encryption Offices throughout North America, Asia and Europe Growing installed based with customers in 37 countries Developing
Virtual Privacy vs. Real Security Certes Networks at a glance Leader in Multi-Layer Encryption Offices throughout North America, Asia and Europe Growing installed based with customers in 37 countries Developing
KASPERSKY DDOS PROTECTION. Discover how Kaspersky Lab defends businesses against DDoS attacks
 KASPERSKY DDOS PROTECTION Discover how Kaspersky Lab defends businesses against DDoS attacks CYBERCRIMINALS ARE TARGETING BUSINESSES If your business has ever suffered a Distributed Denial of Service (DDoS)
KASPERSKY DDOS PROTECTION Discover how Kaspersky Lab defends businesses against DDoS attacks CYBERCRIMINALS ARE TARGETING BUSINESSES If your business has ever suffered a Distributed Denial of Service (DDoS)
HOW TO PREVENT DDOS ATTACKS IN A SERVICE PROVIDER ENVIRONMENT
 HOW TO PREVENT DDOS ATTACKS IN A SERVICE PROVIDER ENVIRONMENT The frequency and sophistication of Distributed Denial of Service attacks (DDoS) on the Internet are rapidly increasing. Most of the earliest
HOW TO PREVENT DDOS ATTACKS IN A SERVICE PROVIDER ENVIRONMENT The frequency and sophistication of Distributed Denial of Service attacks (DDoS) on the Internet are rapidly increasing. Most of the earliest
Service Description DDoS Mitigation Service
 Service Description DDoS Mitigation Service Interoute, Walbrook Building, 195 Marsh Wall, London, E14 9SG, UK Tel: +800 4683 7681 Email: info@interoute.com Contents Contents 1 Introduction...3 2 An Overview...3
Service Description DDoS Mitigation Service Interoute, Walbrook Building, 195 Marsh Wall, London, E14 9SG, UK Tel: +800 4683 7681 Email: info@interoute.com Contents Contents 1 Introduction...3 2 An Overview...3
Analyzed compe.tors Cisco RadWare Top Layer RioRey IntruGuard. January 2009. Cristian Velciov. ceo@andrisoft.com (+40) 721 250246
 Analyzed compe.tors Cisco RadWare Top Layer RioRey IntruGuard January 2009 Cristian Velciov ceo@andrisoft.com (+40) 721 250246 Andrisoft Solution WANGuard Platform is an enterprise-grade Linux-based software
Analyzed compe.tors Cisco RadWare Top Layer RioRey IntruGuard January 2009 Cristian Velciov ceo@andrisoft.com (+40) 721 250246 Andrisoft Solution WANGuard Platform is an enterprise-grade Linux-based software
DDoS Mitigation Techniques
 DDoS Mitigation Techniques Ron Winward, ServerCentral CHI-NOG 03 06/14/14 Consistent Bottlenecks in DDoS Attacks 1. The server that is under attack 2. The firewall in front of the network 3. The internet
DDoS Mitigation Techniques Ron Winward, ServerCentral CHI-NOG 03 06/14/14 Consistent Bottlenecks in DDoS Attacks 1. The server that is under attack 2. The firewall in front of the network 3. The internet
SURE 5 Zone DDoS PROTECTION SERVICE
 SURE 5 Zone DDoS PROTECTION SERVICE Sure 5 Zone DDoS Protection ( the Service ) provides a solution to protect our customer s sites against Distributed Denial of Service (DDoS) attacks by analysing incoming
SURE 5 Zone DDoS PROTECTION SERVICE Sure 5 Zone DDoS Protection ( the Service ) provides a solution to protect our customer s sites against Distributed Denial of Service (DDoS) attacks by analysing incoming
Game changing Technology für Ihre Kunden. Thomas Bürgis System Engineering Manager CEE
 Game changing Technology für Ihre Kunden Thomas Bürgis System Engineering Manager CEE Threats have evolved traditional firewalls & IPS have not Protection centered around ports & protocols Expensive to
Game changing Technology für Ihre Kunden Thomas Bürgis System Engineering Manager CEE Threats have evolved traditional firewalls & IPS have not Protection centered around ports & protocols Expensive to
PART D NETWORK SERVICES
 CONTENTS 1 ABOUT THIS PART... 2 2 PUBLIC NETWORK... 2 Internet... 2 3 PRIVATE NETWORK... 3 Global WAN services... 3 4 SECURITY SERVICES... 3 Firewall... 4 Intrusion Prevention (Network)... 5 SSL/IPSEC
CONTENTS 1 ABOUT THIS PART... 2 2 PUBLIC NETWORK... 2 Internet... 2 3 PRIVATE NETWORK... 3 Global WAN services... 3 4 SECURITY SERVICES... 3 Firewall... 4 Intrusion Prevention (Network)... 5 SSL/IPSEC
WAN Traffic Management with PowerLink Pro100
 Whitepaper WAN Traffic Management with PowerLink Pro100 Overview In today s Internet marketplace, optimizing online presence is crucial for business success. Wan/ISP link failover and traffic management
Whitepaper WAN Traffic Management with PowerLink Pro100 Overview In today s Internet marketplace, optimizing online presence is crucial for business success. Wan/ISP link failover and traffic management
Cisco Application Networking for IBM WebSphere
 Cisco Application Networking for IBM WebSphere Faster Downloads and Site Navigation, Less Bandwidth and Server Processing, and Greater Availability for Global Deployments What You Will Learn To address
Cisco Application Networking for IBM WebSphere Faster Downloads and Site Navigation, Less Bandwidth and Server Processing, and Greater Availability for Global Deployments What You Will Learn To address
How To Block A Ddos Attack On A Network With A Firewall
 A Prolexic White Paper Firewalls: Limitations When Applied to DDoS Protection Introduction Firewalls are often used to restrict certain protocols during normal network situations and when Distributed Denial
A Prolexic White Paper Firewalls: Limitations When Applied to DDoS Protection Introduction Firewalls are often used to restrict certain protocols during normal network situations and when Distributed Denial
How valuable DDoS mitigation hardware is for Layer 7 Sophisticated attacks
 How valuable DDoS mitigation hardware is for Layer 7 Sophisticated attacks Stop DDoS before they stop you! James Braunegg (Micron 21) What Is Distributed Denial of Service A Denial of Service attack (DoS)
How valuable DDoS mitigation hardware is for Layer 7 Sophisticated attacks Stop DDoS before they stop you! James Braunegg (Micron 21) What Is Distributed Denial of Service A Denial of Service attack (DoS)
Report of Independent Auditors
 Ernst & Young LLP Suite 3300 370 17th Street Denver, Colorado 80202-5663 Tel: +1 720 931 4000 Fax: +1 720 931 4444 www.ey.com Report of Independent Auditors To the Management of NTT America, Inc.: We have
Ernst & Young LLP Suite 3300 370 17th Street Denver, Colorado 80202-5663 Tel: +1 720 931 4000 Fax: +1 720 931 4444 www.ey.com Report of Independent Auditors To the Management of NTT America, Inc.: We have
Appendix A: Configuring Firewalls for a VPN Server Running Windows Server 2003
 http://technet.microsoft.com/en-us/library/cc757501(ws.10).aspx Appendix A: Configuring Firewalls for a VPN Server Running Windows Server 2003 Updated: October 7, 2005 Applies To: Windows Server 2003 with
http://technet.microsoft.com/en-us/library/cc757501(ws.10).aspx Appendix A: Configuring Firewalls for a VPN Server Running Windows Server 2003 Updated: October 7, 2005 Applies To: Windows Server 2003 with
Data Sheet. DPtech Anti-DDoS Series. Overview
 Data Sheet DPtech Anti-DDoS Series DPtech Anti-DDoS Series Overview DoS (Denial of Service) leverage various service requests to exhaust victims system resources, causing the victim to deny service to
Data Sheet DPtech Anti-DDoS Series DPtech Anti-DDoS Series Overview DoS (Denial of Service) leverage various service requests to exhaust victims system resources, causing the victim to deny service to
Flow Analysis Versus Packet Analysis. What Should You Choose?
 Flow Analysis Versus Packet Analysis. What Should You Choose? www.netfort.com Flow analysis can help to determine traffic statistics overall, but it falls short when you need to analyse a specific conversation
Flow Analysis Versus Packet Analysis. What Should You Choose? www.netfort.com Flow analysis can help to determine traffic statistics overall, but it falls short when you need to analyse a specific conversation
CloudFlare advanced DDoS protection
 CloudFlare advanced DDoS protection Denial-of-service (DoS) attacks are on the rise and have evolved into complex and overwhelming security challenges. 1 888 99 FLARE enterprise@cloudflare.com www.cloudflare.com
CloudFlare advanced DDoS protection Denial-of-service (DoS) attacks are on the rise and have evolved into complex and overwhelming security challenges. 1 888 99 FLARE enterprise@cloudflare.com www.cloudflare.com
Mitigating DDoS Attacks at Layer 7
 Mitigating DDoS Attacks at Layer 7 Detect, Localize and Mitigate using DNS GSLB Allan Jude ScaleEngine Inc. Introductions Allan Jude 12 Years as FreeBSD Server Admin Architect of the ScaleEngine CDN (HTTP
Mitigating DDoS Attacks at Layer 7 Detect, Localize and Mitigate using DNS GSLB Allan Jude ScaleEngine Inc. Introductions Allan Jude 12 Years as FreeBSD Server Admin Architect of the ScaleEngine CDN (HTTP
ARTICLE 3. CUSTOM INSTALATION FEES Ethernet Dedicated Internet Services PSA Ver. 1.5
 COMCAST ENTERPRISE SERVICES PRODUCT- SPECIFIC ATTACHMENT ETHERNET DEDICATED INTERNET SERVICES ATTACHMENT IDENTIFIER: Ethernet Dedicated Internet, Version 1.5 The following additional terms and conditions
COMCAST ENTERPRISE SERVICES PRODUCT- SPECIFIC ATTACHMENT ETHERNET DEDICATED INTERNET SERVICES ATTACHMENT IDENTIFIER: Ethernet Dedicated Internet, Version 1.5 The following additional terms and conditions
Automated Mitigation of the Largest and Smartest DDoS Attacks
 Datasheet Protection Automated Mitigation of the Largest and Smartest Attacks Incapsula secures websites against the largest and smartest types of attacks - including network, protocol and application
Datasheet Protection Automated Mitigation of the Largest and Smartest Attacks Incapsula secures websites against the largest and smartest types of attacks - including network, protocol and application
State of Texas. TEX-AN Next Generation. NNI Plan
 State of Texas TEX-AN Next Generation NNI Plan Table of Contents 1. INTRODUCTION... 1 1.1. Purpose... 1 2. NNI APPROACH... 2 2.1. Proposed Interconnection Capacity... 2 2.2. Collocation Equipment Requirements...
State of Texas TEX-AN Next Generation NNI Plan Table of Contents 1. INTRODUCTION... 1 1.1. Purpose... 1 2. NNI APPROACH... 2 2.1. Proposed Interconnection Capacity... 2 2.2. Collocation Equipment Requirements...
Cisco Application Networking for BEA WebLogic
 Cisco Application Networking for BEA WebLogic Faster Downloads and Site Navigation, Less Bandwidth and Server Processing, and Greater Availability for Global Deployments What You Will Learn To address
Cisco Application Networking for BEA WebLogic Faster Downloads and Site Navigation, Less Bandwidth and Server Processing, and Greater Availability for Global Deployments What You Will Learn To address
DDoS attacks in CESNET2
 DDoS attacks in CESNET2 Ondřej Caletka 15th March 2016 Ondřej Caletka (CESNET) DDoS attacks in CESNET2 15th March 2016 1 / 22 About CESNET association of legal entities, est. 1996 public and state universities
DDoS attacks in CESNET2 Ondřej Caletka 15th March 2016 Ondřej Caletka (CESNET) DDoS attacks in CESNET2 15th March 2016 1 / 22 About CESNET association of legal entities, est. 1996 public and state universities
Service Provider Solutions. DDoS Protection Solution. Enabling Clean Pipes Capabilities
 Service Provider Solutions Enabling Clean Pipes Capabilities June 2005 1 Service Provider Security Highlights Security is the heart of internetworking s future A secure infrastructure forms the foundation
Service Provider Solutions Enabling Clean Pipes Capabilities June 2005 1 Service Provider Security Highlights Security is the heart of internetworking s future A secure infrastructure forms the foundation
DDoS Mitigation via Regional Cleaning Centers
 SPRINT ATL RESEARCH REPORT RR04-ATL-013177 - JANUARY 2004 1 DDoS Mitigation via Regional Cleaning Centers Sharad Agarwal Travis Dawson Christos Tryfonas University of California, Berkeley Sprint ATL Kazeon
SPRINT ATL RESEARCH REPORT RR04-ATL-013177 - JANUARY 2004 1 DDoS Mitigation via Regional Cleaning Centers Sharad Agarwal Travis Dawson Christos Tryfonas University of California, Berkeley Sprint ATL Kazeon
F5 Silverline DDoS Protection Onboarding: Technical Note
 F5 Silverline DDoS Protection Onboarding: Technical Note F5 Silverline DDoS Protection onboarding F5 Networks is the first leading application services company to offer a single-vendor hybrid solution
F5 Silverline DDoS Protection Onboarding: Technical Note F5 Silverline DDoS Protection onboarding F5 Networks is the first leading application services company to offer a single-vendor hybrid solution
RID-DoS: Real-time Inter-network Defense Against Denial of Service Attacks. Kathleen M. Moriarty. MIT Lincoln Laboratory.
 : Real-time Inter-network Defense Against Denial of Service Attacks Kathleen M. Moriarty 22 October 2002 This work was sponsored by the Air Force Contract number F19628-00-C-002. Opinions, interpretations,
: Real-time Inter-network Defense Against Denial of Service Attacks Kathleen M. Moriarty 22 October 2002 This work was sponsored by the Air Force Contract number F19628-00-C-002. Opinions, interpretations,
Welcome to SoftLayer. Welcome. How to Get Started. Portal Overview. Support Guidelines. Technical Resources. First 48 Hours
 First 48 Hours Welcome Welcome to SoftLayer. This document will outline your first 48 hours as a customer and hopefully answer all initial questions. Dedicated server administration is a challenging task
First 48 Hours Welcome Welcome to SoftLayer. This document will outline your first 48 hours as a customer and hopefully answer all initial questions. Dedicated server administration is a challenging task
Distributed Denial of Service (DDoS) attacks. Imminent danger for financial systems. Tata Communications Arbor Networks.
 Distributed Denial of Service (DDoS) attacks Imminent danger for financial systems Presented by Tata Communications Arbor Networks 1 Agenda Importance of DDoS for BFSI DDoS Industry Trends DDoS Technology
Distributed Denial of Service (DDoS) attacks Imminent danger for financial systems Presented by Tata Communications Arbor Networks 1 Agenda Importance of DDoS for BFSI DDoS Industry Trends DDoS Technology
Zscaler Internet Security Frequently Asked Questions
 Zscaler Internet Security Frequently Asked Questions 1 Technical FAQ PRODUCT LICENSING & PRICING How is Zscaler Internet Security Zscaler Internet Security is licensed on number of Cradlepoint devices
Zscaler Internet Security Frequently Asked Questions 1 Technical FAQ PRODUCT LICENSING & PRICING How is Zscaler Internet Security Zscaler Internet Security is licensed on number of Cradlepoint devices
The Regional Internet Registries
 The Regional Internet Registries Managing Internet Number Resources www.afrinic.net www.apnic.net www.arin.net www.lacnic.net www.ripe.net www.nro.net Global Coordination A Fair and Stable Platform Whether
The Regional Internet Registries Managing Internet Number Resources www.afrinic.net www.apnic.net www.arin.net www.lacnic.net www.ripe.net www.nro.net Global Coordination A Fair and Stable Platform Whether
This document is licensed for use, redistribution, and derivative works, commercial or otherwise, in accordance with the Creative Commons
 This document is licensed for use, redistribution, and derivative works, commercial or otherwise, in accordance with the Creative Commons Attribution-ShareAlike 4.0 International license. As a provider
This document is licensed for use, redistribution, and derivative works, commercial or otherwise, in accordance with the Creative Commons Attribution-ShareAlike 4.0 International license. As a provider
Pravail 2.0 Technical Overview. Exclusive Networks
 Pravail 2.0 Technical Overview Exclusive Networks Pravail Features and Benefits Arbor Pravail APS is the a CPE-based security appliance focused on stopping availability threats Arbor Pravail APS Arbor
Pravail 2.0 Technical Overview Exclusive Networks Pravail Features and Benefits Arbor Pravail APS is the a CPE-based security appliance focused on stopping availability threats Arbor Pravail APS Arbor
Active Visibility for Multi-Tiered Security // Solutions Overview
 Introduction Cyber threats are becoming ever more sophisticated and prevalent. Traditional security approaches such as firewalls and anti-virus protection are not equipped to mitigate and manage modern
Introduction Cyber threats are becoming ever more sophisticated and prevalent. Traditional security approaches such as firewalls and anti-virus protection are not equipped to mitigate and manage modern
What's inside the cloud?!
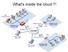 What's inside the cloud?! Initial Arpanet Initial Arpanet Interface Message Processors - DDP-516 mini-computers - 24 Kbyte of Core memory - Store-and-forward packet switching - Predecessors of present
What's inside the cloud?! Initial Arpanet Initial Arpanet Interface Message Processors - DDP-516 mini-computers - 24 Kbyte of Core memory - Store-and-forward packet switching - Predecessors of present
Radware s Attack Mitigation Solution On-line Business Protection
 Radware s Attack Mitigation Solution On-line Business Protection Table of Contents Attack Mitigation Layers of Defense... 3 Network-Based DDoS Protections... 3 Application Based DoS/DDoS Protection...
Radware s Attack Mitigation Solution On-line Business Protection Table of Contents Attack Mitigation Layers of Defense... 3 Network-Based DDoS Protections... 3 Application Based DoS/DDoS Protection...
Distributed Denial of Service protection
 Distributed Denial of Service protection The cost in terms of lost business caused by a successful DDoS attacks can be significant. Our solution recognises when a DDoS attack is happening and identifies
Distributed Denial of Service protection The cost in terms of lost business caused by a successful DDoS attacks can be significant. Our solution recognises when a DDoS attack is happening and identifies
Security Toolsets for ISP Defense
 Security Toolsets for ISP Defense Backbone Practices Authored by Timothy A Battles (AT&T IP Network Security) What s our goal? To provide protection against anomalous traffic for our network and it s customers.
Security Toolsets for ISP Defense Backbone Practices Authored by Timothy A Battles (AT&T IP Network Security) What s our goal? To provide protection against anomalous traffic for our network and it s customers.
Company Overview. October 2014
 Company Overview October 2014 Presentation Structure 1 DDoS Attacks 2 Black Lotus DDoS Defense Solution 3 About Black Lotus What Does Black Lotus Do? We are a security company that protects businesses
Company Overview October 2014 Presentation Structure 1 DDoS Attacks 2 Black Lotus DDoS Defense Solution 3 About Black Lotus What Does Black Lotus Do? We are a security company that protects businesses
Achieving Low-Latency Security
 Achieving Low-Latency Security In Today's Competitive, Regulatory and High-Speed Transaction Environment Darren Turnbull, VP Strategic Solutions - Fortinet Agenda 1 2 3 Firewall Architecture Typical Requirements
Achieving Low-Latency Security In Today's Competitive, Regulatory and High-Speed Transaction Environment Darren Turnbull, VP Strategic Solutions - Fortinet Agenda 1 2 3 Firewall Architecture Typical Requirements
SHARE THIS WHITEPAPER
 Denial-of-Service (DoS) Secured Virtual Tenant Networks (VTN) Value-added DoS protection as a service for Software Defined Network (SDN) a solution paper by Radware & NEC Corporation of America Whitepaper
Denial-of-Service (DoS) Secured Virtual Tenant Networks (VTN) Value-added DoS protection as a service for Software Defined Network (SDN) a solution paper by Radware & NEC Corporation of America Whitepaper
Network provider filter lab
 Network provider filter lab Olof Hagsand Pehr Söderman KTH CSC Group Nr Name 1 Name 2 Name 3 Name 4 Date Instructor s Signature Table of Contents 1 Goals...3 2 Introduction...3 3 Preparations...3 4 Lab
Network provider filter lab Olof Hagsand Pehr Söderman KTH CSC Group Nr Name 1 Name 2 Name 3 Name 4 Date Instructor s Signature Table of Contents 1 Goals...3 2 Introduction...3 3 Preparations...3 4 Lab
Introduction to The Internet
 Introduction to The Internet ISP Workshops Last updated 5 September 2014 1 Introduction to the Internet p Topologies and Definitions p IP Addressing p Internet Hierarchy p Gluing it all together 2 Topologies
Introduction to The Internet ISP Workshops Last updated 5 September 2014 1 Introduction to the Internet p Topologies and Definitions p IP Addressing p Internet Hierarchy p Gluing it all together 2 Topologies
Traffic Monitoring using sflow
 Making the Network Visible www.sflow.org Traffic Monitoring using sflow With the ever-increasing reliance on network services for business critical applications, the smallest change in network usage can
Making the Network Visible www.sflow.org Traffic Monitoring using sflow With the ever-increasing reliance on network services for business critical applications, the smallest change in network usage can
Cheap and efficient anti-ddos solution
 Cheap and efficient anti-ddos solution Who am I? Alexei Cioban Experience in IT 13 years CEO & Founder IT-LAB 7 years IT trainings 5 years 2 About company Year of foundation - 2007 12 employees www.it-lab.md
Cheap and efficient anti-ddos solution Who am I? Alexei Cioban Experience in IT 13 years CEO & Founder IT-LAB 7 years IT trainings 5 years 2 About company Year of foundation - 2007 12 employees www.it-lab.md
BT Internet Connect Global - Annex to the General Service Schedule
 1. Definitions The following definitions apply, in addition to those in the General Terms and Conditions and the General Services Schedule. ARP means Address Resolution Protocol. Border Gateway Protocol
1. Definitions The following definitions apply, in addition to those in the General Terms and Conditions and the General Services Schedule. ARP means Address Resolution Protocol. Border Gateway Protocol
Firewalls and Intrusion Detection
 Firewalls and Intrusion Detection What is a Firewall? A computer system between the internal network and the rest of the Internet A single computer or a set of computers that cooperate to perform the firewall
Firewalls and Intrusion Detection What is a Firewall? A computer system between the internal network and the rest of the Internet A single computer or a set of computers that cooperate to perform the firewall
How To Protect A Dns Authority Server From A Flood Attack
 the Availability Digest @availabilitydig Surviving DNS DDoS Attacks November 2013 DDoS attacks are on the rise. A DDoS attack launches a massive amount of traffic to a website to overwhelm it to the point
the Availability Digest @availabilitydig Surviving DNS DDoS Attacks November 2013 DDoS attacks are on the rise. A DDoS attack launches a massive amount of traffic to a website to overwhelm it to the point
Security Design. thm@informatik.uni-rostock.de http://wwwiuk.informatik.uni-rostock.de/
 Security Design thm@informatik.uni-rostock.de http://wwwiuk.informatik.uni-rostock.de/ Content Security Design Analysing Design Requirements Resource Separation a Security Zones VLANs Tuning Load Balancing
Security Design thm@informatik.uni-rostock.de http://wwwiuk.informatik.uni-rostock.de/ Content Security Design Analysing Design Requirements Resource Separation a Security Zones VLANs Tuning Load Balancing
Scrutinizer. Getting Started Guide. A message from Plixer International:
 Scrutinizer Getting Started Guide A message from Plixer International: Thank you for taking the time to download and install Scrutinizer NetFlow & sflow Analyzer. We believe that Scrutinizer is a useful
Scrutinizer Getting Started Guide A message from Plixer International: Thank you for taking the time to download and install Scrutinizer NetFlow & sflow Analyzer. We believe that Scrutinizer is a useful
white paper DDoS Mitigation Best Practices for
 DDoS Mitigation Best Practices for a Rapidly Changing Threat Landscape Contents 1 Executive Summary 1 Smarter, Stealthier, and More Adaptive 2 DDoS Mitigation Challenges: Why Traditional Tactics Aren t
DDoS Mitigation Best Practices for a Rapidly Changing Threat Landscape Contents 1 Executive Summary 1 Smarter, Stealthier, and More Adaptive 2 DDoS Mitigation Challenges: Why Traditional Tactics Aren t
Private IP Overview. Feature Description Benefit to the Customer
 Private IP Overview Private IP is a network-based virtual private network (VPN) enabling customers to effectively communicate over a secure network. It also provides the foundation for automating business
Private IP Overview Private IP is a network-based virtual private network (VPN) enabling customers to effectively communicate over a secure network. It also provides the foundation for automating business
Radware s Smart IDS Management. FireProof and Intrusion Detection Systems. Deployment and ROI. North America. International. www.radware.
 Radware s Smart IDS Management FireProof and Intrusion Detection Systems Deployment and ROI North America Radware Inc. 575 Corporate Dr. Suite 205 Mahwah, NJ 07430 Tel 888 234 5763 International Radware
Radware s Smart IDS Management FireProof and Intrusion Detection Systems Deployment and ROI North America Radware Inc. 575 Corporate Dr. Suite 205 Mahwah, NJ 07430 Tel 888 234 5763 International Radware
Network Management for Common Topologies How best to use LiveAction for managing WAN and campus networks
 Network Management for Common Topologies How best to use LiveAction for managing WAN and campus networks April 2014 www.liveaction.com Contents 1. Introduction... 1 2. WAN Networks... 2 3. Using LiveAction
Network Management for Common Topologies How best to use LiveAction for managing WAN and campus networks April 2014 www.liveaction.com Contents 1. Introduction... 1 2. WAN Networks... 2 3. Using LiveAction
SHARE THIS WHITEPAPER. On-Premise, Cloud or Hybrid? Approaches to Mitigate DDoS Attacks Whitepaper
 SHARE THIS WHITEPAPER On-Premise, Cloud or Hybrid? Approaches to Mitigate DDoS Attacks Whitepaper Table of Contents Overview... 3 Current Attacks Landscape: DDoS is Becoming Mainstream... 3 Attackers Launch
SHARE THIS WHITEPAPER On-Premise, Cloud or Hybrid? Approaches to Mitigate DDoS Attacks Whitepaper Table of Contents Overview... 3 Current Attacks Landscape: DDoS is Becoming Mainstream... 3 Attackers Launch
Four Considerations for Addressing the DDoS Risk for Carrier and Cloud Hosting Providers
 Four Considerations for Addressing the DDoS Risk for Carrier and Cloud Hosting Providers Whitepaper SHARE THIS WHITEPAPER Table of Contents The Rising Threat of Cyber-Attack Downtime...3 Four Key Considerations
Four Considerations for Addressing the DDoS Risk for Carrier and Cloud Hosting Providers Whitepaper SHARE THIS WHITEPAPER Table of Contents The Rising Threat of Cyber-Attack Downtime...3 Four Key Considerations
Approaches for DDoS an ISP Perspective. barry@null0.net ognian.mitev@viawest.com
 Approaches for DDoS an ISP Perspective barry@null0.net ognian.mitev@viawest.com Home School How everyone starts It s all up to you It s inexpensive (compared to other forms of education) Quality may not
Approaches for DDoS an ISP Perspective barry@null0.net ognian.mitev@viawest.com Home School How everyone starts It s all up to you It s inexpensive (compared to other forms of education) Quality may not
The OpenDNS Global Network Delivers a Secure Connection Every Time. Everywhere.
 The OpenDNS Global Network Delivers a Secure Connection Every Time. Everywhere. Network Performance Users devices create multiple simultaneous connections each time we exchange data with other Internet
The OpenDNS Global Network Delivers a Secure Connection Every Time. Everywhere. Network Performance Users devices create multiple simultaneous connections each time we exchange data with other Internet
Networking and High Availability
 TECHNICAL BRIEF Networking and High Availability Deployment Note Imperva appliances support a broad array of deployment options, enabling seamless integration into any data center environment. can be configured
TECHNICAL BRIEF Networking and High Availability Deployment Note Imperva appliances support a broad array of deployment options, enabling seamless integration into any data center environment. can be configured
SecurityDAM On-demand, Cloud-based DDoS Mitigation
 SecurityDAM On-demand, Cloud-based DDoS Mitigation Table of contents Introduction... 3 Why premise-based DDoS solutions are lacking... 3 The problem with ISP-based DDoS solutions... 4 On-demand cloud DDoS
SecurityDAM On-demand, Cloud-based DDoS Mitigation Table of contents Introduction... 3 Why premise-based DDoS solutions are lacking... 3 The problem with ISP-based DDoS solutions... 4 On-demand cloud DDoS
Networking for Caribbean Development
 Networking for Caribbean Development BELIZE NOV 2 NOV 6, 2015 w w w. c a r i b n o g. o r g N E T W O R K I N G F O R C A R I B B E A N D E V E L O P M E N T BELIZE NOV 2 NOV 6, 2015 w w w. c a r i b n
Networking for Caribbean Development BELIZE NOV 2 NOV 6, 2015 w w w. c a r i b n o g. o r g N E T W O R K I N G F O R C A R I B B E A N D E V E L O P M E N T BELIZE NOV 2 NOV 6, 2015 w w w. c a r i b n
Network Performance Monitoring at Minimal Capex
 Network Performance Monitoring at Minimal Capex Some Cisco IOS technologies you can use to create a high performance network Don Thomas Jacob Technical Marketing Engineer About ManageEngine Network Servers
Network Performance Monitoring at Minimal Capex Some Cisco IOS technologies you can use to create a high performance network Don Thomas Jacob Technical Marketing Engineer About ManageEngine Network Servers
SHARE THIS WHITEPAPER. Top Selection Criteria for an Anti-DDoS Solution Whitepaper
 SHARE THIS WHITEPAPER Top Selection Criteria for an Anti-DDoS Solution Whitepaper Table of Contents Top Selection Criteria for an Anti-DDoS Solution...3 DDoS Attack Coverage...3 Mitigation Technology...4
SHARE THIS WHITEPAPER Top Selection Criteria for an Anti-DDoS Solution Whitepaper Table of Contents Top Selection Criteria for an Anti-DDoS Solution...3 DDoS Attack Coverage...3 Mitigation Technology...4
Acquia Cloud Edge Protect Powered by CloudFlare
 Acquia Cloud Edge Protect Powered by CloudFlare Denial-of-service (DoS) Attacks Are on the Rise and Have Evolved into Complex and Overwhelming Security Challenges TECHNICAL GUIDE TABLE OF CONTENTS Introduction....
Acquia Cloud Edge Protect Powered by CloudFlare Denial-of-service (DoS) Attacks Are on the Rise and Have Evolved into Complex and Overwhelming Security Challenges TECHNICAL GUIDE TABLE OF CONTENTS Introduction....
Guideline on Firewall
 CMSGu2014-02 Mauritian Computer Emergency Response Team CERT-MU SECURITY GUIDELINE 2011-02 Enhancing Cyber Security in Mauritius Guideline on Firewall National Computer Board Mauritius Version 1.0 June
CMSGu2014-02 Mauritian Computer Emergency Response Team CERT-MU SECURITY GUIDELINE 2011-02 Enhancing Cyber Security in Mauritius Guideline on Firewall National Computer Board Mauritius Version 1.0 June
Quality Certificate for Kaspersky DDoS Prevention Software
 Quality Certificate for Kaspersky DDoS Prevention Software Quality Certificate for Kaspersky DDoS Prevention Software Table of Contents Definitions 3 1. Conditions of software operability 4 2. General
Quality Certificate for Kaspersky DDoS Prevention Software Quality Certificate for Kaspersky DDoS Prevention Software Table of Contents Definitions 3 1. Conditions of software operability 4 2. General
Protecting DNS Critical Infrastructure Solution Overview. Radware Attack Mitigation System (AMS) - Whitepaper
 Protecting DNS Critical Infrastructure Solution Overview Radware Attack Mitigation System (AMS) - Whitepaper Table of Contents Introduction...3 DNS DDoS Attacks are Growing and Evolving...3 Challenges
Protecting DNS Critical Infrastructure Solution Overview Radware Attack Mitigation System (AMS) - Whitepaper Table of Contents Introduction...3 DNS DDoS Attacks are Growing and Evolving...3 Challenges
Arbor s Solution for ISP
 Arbor s Solution for ISP Recent Attack Cases DDoS is an Exploding & Evolving Trend More Attack Motivations Geopolitical Burma taken offline by DDOS attack Protests Extortion Visa, PayPal, and MasterCard
Arbor s Solution for ISP Recent Attack Cases DDoS is an Exploding & Evolving Trend More Attack Motivations Geopolitical Burma taken offline by DDOS attack Protests Extortion Visa, PayPal, and MasterCard
Why an Intelligent WAN Solution is Essential for Mission Critical Networks
 Why an Intelligent WAN Solution is Essential for Mission Critical Networks White Paper Series WP100135 Charles Tucker Director of Marketing June 1, 2006 Abstract: Reliable Internet connectivity is now
Why an Intelligent WAN Solution is Essential for Mission Critical Networks White Paper Series WP100135 Charles Tucker Director of Marketing June 1, 2006 Abstract: Reliable Internet connectivity is now
Technology Blueprint. Defend Against Denial of Service Attacks. Protect each IT service layer against exploitation and abuse
 Technology Blueprint Defend Against Denial of Service (DOS and DDOS) Attacks Protect each IT service layer against exploitation and abuse LEVEL 1 2 3 4 5 SECURITY CONNECTED REFERENCE ARCHITECTURE LEVEL
Technology Blueprint Defend Against Denial of Service (DOS and DDOS) Attacks Protect each IT service layer against exploitation and abuse LEVEL 1 2 3 4 5 SECURITY CONNECTED REFERENCE ARCHITECTURE LEVEL
FIREWALLS & CBAC. philip.heimer@hh.se
 FIREWALLS & CBAC philip.heimer@hh.se Implementing a Firewall Personal software firewall a software that is installed on a single PC to protect only that PC All-in-one firewall can be a single device that
FIREWALLS & CBAC philip.heimer@hh.se Implementing a Firewall Personal software firewall a software that is installed on a single PC to protect only that PC All-in-one firewall can be a single device that
