Secure Data Transfer to/from CSAC
|
|
|
- Eleanor Booker
- 8 years ago
- Views:
Transcription
1 Secure Data Transfer to/from CSAC 1
2 Protecting Data in Transit Confidential data cannot be sent via unsecured channels or media Includes , fax, CDROM, paper, magnetic media (ie( ie,, floppy, disk, tape), USB/flash memory devices, etc. Use encryption or encrypted communication channels 2
3 WebGrants Secure Transfer WebGrants now has a secure data transfer capability built in with normal WebGrants account access! Upload via Data Transfer->File Upload->Secure File Transfer Download via Data Transfer->Report Download->Secure File Transfer Documents for download are seen only when they are available 3
4 WebGrants Secure Data Transfer Benefits Files securely transferred online between CSAC and your school! (Contact the proper CSAC department if they re not expecting the data transfer.) No additional need to encrypt data and send it via or post office! Schools can only see their data, not shared between schools. No encryption passwords to remember! No new software to buy or install! 4
5 WebGrants Secure Data Upload 5
6 WebGrants Secure Data Download 6
7 Non WebGrants access Confidential data should be sent via encrypted or physical media instructions seen in following pages 7
8 Encryption tools WinZip - Free during evaluation period, requires payment after eval period. Compresses most files, encrypts 7Zip - Free, no license restrictions Compatible w/winzip and many other archive tools, encrypts Use ZIP-AES AES-256 encryption 8
9 Encrypting Confidential Data & Mailing It Securely - WinZip Right click on file(s) to be encrypted/sent Select WinZip->Zip and Plus (only!) (Winzip->Zip and will NOT encrypt the file) Use Zip and Plus 9
10 Encrypting Confidential Data & Mailing It Securely WinZip (cont) Turn on the Encryption option, press OK Enter the same password in each field Select 256-Bit AES Encryption. Press OK WEAK! 10
11 Encrypted send windows appears with encrypted document(s) attached. Do NOT send the password with the attachment call recipient or send it in a separate . Encrypted attachment 11
12 Encrypting with older versions or other software Establish a new Zip archive in a desired directory. Name the file with the student s CSAC ID & date (ie, _ zip) Specify that you want the zipped file to be encrypted. Use STRONG encryption (ie, AES) - Some are very weak. Add files to the archive (may be asked to encrypt them at this time) Save and close the archive. Test it by double-clicking it, and ensuring that it requests a decryption password. Open a new Attach the Encrypted, zipped file, add a message, then send it off. Do not include the password in the message send it separately in a new message or call the recipient. Ensure arrival of the file, as some filters block zip files. 12
13 Secure FAX At this time, there is no good solution to send an encrypted fax Too many standards not all machines set up to txfer/receive encrypted faxes. Instead, Scan your document to a file, then encrypt it and send via , or Redact all Confidential information before faxing. 13
14 Questions? Suggestions? Contact Info Contact the CSAC Helpdesk at CSAC Information Security Officer PO Box Rancho Cordova, CA
Recommended Approach to Encrypting GNL Files
 Recommended Approach to Encrypting GNL Files 1 2 The Needs Identify a method to securely transport and store personal and/or confidential government information, which is readily accessible to government
Recommended Approach to Encrypting GNL Files 1 2 The Needs Identify a method to securely transport and store personal and/or confidential government information, which is readily accessible to government
SecureZIP User Guide
 SecureZIP User Guide SecureZIP is an application for zipping files to save storage space as well as encrypting files with password control to protect information. SecureZIP not only works alone to perform
SecureZIP User Guide SecureZIP is an application for zipping files to save storage space as well as encrypting files with password control to protect information. SecureZIP not only works alone to perform
INFORMATION SECURITY GUIDELINE How to Encrypt Files Using Common Applications Revision 1.1
 INFORMATION SECURITY GUIDELINE How to Encrypt Files Using Common Applications Revision 1.1 Contents Introduction... 1 Safely Delivering the Encryption Password to the Recipient... 2 How to Encrypt Files
INFORMATION SECURITY GUIDELINE How to Encrypt Files Using Common Applications Revision 1.1 Contents Introduction... 1 Safely Delivering the Encryption Password to the Recipient... 2 How to Encrypt Files
For: All FSA Employees (Federal and Non-Federal) and Contractors
 UNITED STATES DEPARTMENT OF AGRICULTURE Farm Service Agency Washington, DC 20250 Notice IRM-372 For: All FSA Employees (Federal and Non-Federal) and Contractors Interim Encryption Solution Approved for
UNITED STATES DEPARTMENT OF AGRICULTURE Farm Service Agency Washington, DC 20250 Notice IRM-372 For: All FSA Employees (Federal and Non-Federal) and Contractors Interim Encryption Solution Approved for
How To Encrypt a File using Windows Explorer and WinZip. For Use With All PII Data
 How To Encrypt a File using Windows Explorer and WinZip For Use With All PII Data As an employee or a contractor, you share in the responsibility for protecting the privacy of individuals whose information
How To Encrypt a File using Windows Explorer and WinZip For Use With All PII Data As an employee or a contractor, you share in the responsibility for protecting the privacy of individuals whose information
Wakefield Council Secure email and file transfer User guide for customers, partners and agencies
 Wakefield Council Secure email and file transfer User guide for customers, partners and agencies The nature of the work the council carries out means that we often deal with information that is sensitive
Wakefield Council Secure email and file transfer User guide for customers, partners and agencies The nature of the work the council carries out means that we often deal with information that is sensitive
tips A quick and easy guide to securing your private information www.pkware.com
 tips A quick and easy guide to securing your private information tips A quick and easy guide to securing your private information Basic Information 1. How to install SecureZIP for Windows Desktop for individual
tips A quick and easy guide to securing your private information tips A quick and easy guide to securing your private information Basic Information 1. How to install SecureZIP for Windows Desktop for individual
Online Backup Client User Manual
 Online Backup Client User Manual Software version 3.21 For Linux distributions January 2011 Version 2.0 Disclaimer This document is compiled with the greatest possible care. However, errors might have
Online Backup Client User Manual Software version 3.21 For Linux distributions January 2011 Version 2.0 Disclaimer This document is compiled with the greatest possible care. However, errors might have
Call Recorder Quick CD Access System
 Call Recorder Quick CD Access System V4.0 VC2010 Contents 1 Call Recorder Quick CD Access System... 3 1.1 Install the software...4 1.2 Start...4 1.3 View recordings on CD...5 1.4 Create an archive on Hard
Call Recorder Quick CD Access System V4.0 VC2010 Contents 1 Call Recorder Quick CD Access System... 3 1.1 Install the software...4 1.2 Start...4 1.3 View recordings on CD...5 1.4 Create an archive on Hard
1 of 10 1/31/2014 4:08 PM
 1 of 10 1/31/2014 4:08 PM copyright 2014 How to backup Microsoft SQL Server with Nordic Backup Pro Before creating a SQL backup set within Nordic Backup Pro it is first necessary to verify that the settings
1 of 10 1/31/2014 4:08 PM copyright 2014 How to backup Microsoft SQL Server with Nordic Backup Pro Before creating a SQL backup set within Nordic Backup Pro it is first necessary to verify that the settings
Air Resources Board File Transfer Protocol (FTP)
 Air Resources Board File Transfer Protocol (FTP) A Handbook for External Users (those not connected to the ARB network) July 2006 How do I use ARB FTP? What is the FTP server and who can use it? What software
Air Resources Board File Transfer Protocol (FTP) A Handbook for External Users (those not connected to the ARB network) July 2006 How do I use ARB FTP? What is the FTP server and who can use it? What software
Encrypting a Single Customer View file using WinZip
 Encrypting a Single Customer View file using WinZip Introduction As part of the Financial Services Compensation Scheme (FSCS) Faster Payout project, deposit takers are required to send a sample Single
Encrypting a Single Customer View file using WinZip Introduction As part of the Financial Services Compensation Scheme (FSCS) Faster Payout project, deposit takers are required to send a sample Single
Encrypting Files Using AxCrypt
 Encrypting Files Using AxCrypt Documents, spreadsheets, databases, and other files that contain personal information or other sensitive information MUST BE encrypted when being transmitted to someone else
Encrypting Files Using AxCrypt Documents, spreadsheets, databases, and other files that contain personal information or other sensitive information MUST BE encrypted when being transmitted to someone else
Page 1 Rev Date: February 2010. User Manual for Encrypted Email Services
 Page 1 User Manual for Encrypted Email Services Instructions for Using Encrypted Email Services This document is being provided to assist you in opening encrypted emails sent from Century Bank. The following
Page 1 User Manual for Encrypted Email Services Instructions for Using Encrypted Email Services This document is being provided to assist you in opening encrypted emails sent from Century Bank. The following
1. Product Information
 ORIXCLOUD BACKUP CLIENT USER MANUAL LINUX 1. Product Information Product: Orixcloud Backup Client for Linux Version: 4.1.7 1.1 System Requirements Linux (RedHat, SuSE, Debian and Debian based systems such
ORIXCLOUD BACKUP CLIENT USER MANUAL LINUX 1. Product Information Product: Orixcloud Backup Client for Linux Version: 4.1.7 1.1 System Requirements Linux (RedHat, SuSE, Debian and Debian based systems such
Online Backup Client User Manual Linux
 Online Backup Client User Manual Linux 1. Product Information Product: Online Backup Client for Linux Version: 4.1.7 1.1 System Requirements Operating System Linux (RedHat, SuSE, Debian and Debian based
Online Backup Client User Manual Linux 1. Product Information Product: Online Backup Client for Linux Version: 4.1.7 1.1 System Requirements Operating System Linux (RedHat, SuSE, Debian and Debian based
Mobility and Young London Annex 4: Sharing Information Securely
 Young London Matters April 2009 Government Office For London Riverwalk House 157-161 Millbank London SW1P 4RR For further information about Young London Matters contact: younglondonmatters@gol.gsi.gov.uk
Young London Matters April 2009 Government Office For London Riverwalk House 157-161 Millbank London SW1P 4RR For further information about Young London Matters contact: younglondonmatters@gol.gsi.gov.uk
Introweb Remote Backup Client for Mac OS X User Manual. Version 3.20
 Introweb Remote Backup Client for Mac OS X User Manual Version 3.20 1. Contents 1. Contents...2 2. Product Information...4 3. Benefits...4 4. Features...5 5. System Requirements...6 6. Setup...7 6.1. Setup
Introweb Remote Backup Client for Mac OS X User Manual Version 3.20 1. Contents 1. Contents...2 2. Product Information...4 3. Benefits...4 4. Features...5 5. System Requirements...6 6. Setup...7 6.1. Setup
RecoveryVault Express Client User Manual
 For Linux distributions Software version 4.1.7 Version 2.0 Disclaimer This document is compiled with the greatest possible care. However, errors might have been introduced caused by human mistakes or by
For Linux distributions Software version 4.1.7 Version 2.0 Disclaimer This document is compiled with the greatest possible care. However, errors might have been introduced caused by human mistakes or by
Online Backup Linux Client User Manual
 Online Backup Linux Client User Manual Software version 4.0.x For Linux distributions August 2011 Version 1.0 Disclaimer This document is compiled with the greatest possible care. However, errors might
Online Backup Linux Client User Manual Software version 4.0.x For Linux distributions August 2011 Version 1.0 Disclaimer This document is compiled with the greatest possible care. However, errors might
Online Backup Client User Manual
 For Linux distributions Software version 4.1.7 Version 2.0 Disclaimer This document is compiled with the greatest possible care. However, errors might have been introduced caused by human mistakes or by
For Linux distributions Software version 4.1.7 Version 2.0 Disclaimer This document is compiled with the greatest possible care. However, errors might have been introduced caused by human mistakes or by
Encryption. Introduction to using 7-Zip
 IT Services Training Guide Encryption Introduction to using 7-Zip It Services Training Team The University of Manchester email: its.training@manchester.ac.uk www.itservices.manchester.ac.uk/trainingcourses/coursesforstaff
IT Services Training Guide Encryption Introduction to using 7-Zip It Services Training Team The University of Manchester email: its.training@manchester.ac.uk www.itservices.manchester.ac.uk/trainingcourses/coursesforstaff
Secure File Transfer Protocol Updated Procedures. June 20, 2011
 Secure File Transfer Protocol Updated Procedures June 20, 2011 Table Of Contents Section Subject 1 Overview 2 Installation and Environment Considerations 3 Preparing the Files for Transfer 4 Connecting
Secure File Transfer Protocol Updated Procedures June 20, 2011 Table Of Contents Section Subject 1 Overview 2 Installation and Environment Considerations 3 Preparing the Files for Transfer 4 Connecting
BillQuick Assistant 2008 Start-Up Guide
 Time Billing and Project Management Software Built With Your Industry Knowledge BillQuick Assistant 2008 Start-Up Guide BQE Software, Inc. 2601 Airport Drive Suite 380 Torrance CA 90505 Support: (310)
Time Billing and Project Management Software Built With Your Industry Knowledge BillQuick Assistant 2008 Start-Up Guide BQE Software, Inc. 2601 Airport Drive Suite 380 Torrance CA 90505 Support: (310)
Secure Data Transfer
 Secure Data Transfer INSTRUCTIONS 3 Options to SECURELY TRANSMIT DATA 1. FTP 2. WinZip 3. Password Protection Version 2.0 Page 1 Table of Contents Acronyms & Abbreviations...1 Option 1: File Transfer Protocol
Secure Data Transfer INSTRUCTIONS 3 Options to SECURELY TRANSMIT DATA 1. FTP 2. WinZip 3. Password Protection Version 2.0 Page 1 Table of Contents Acronyms & Abbreviations...1 Option 1: File Transfer Protocol
WebGrants for Students User Guide
 Updated: December 7, 2005 Overview of is the California Student Aid Commission s (Commission) website that allows students to check the status of their Cal Grant and Chafee Grant applications and, in the
Updated: December 7, 2005 Overview of is the California Student Aid Commission s (Commission) website that allows students to check the status of their Cal Grant and Chafee Grant applications and, in the
BillQuick HR 2008 Start-Up Guide
 Time Billing and Project Management Software Built With Your Industry Knowledge BillQuick HR 2008 Start-Up Guide BQE Software, Inc. 2601 Airport Drive Suite 380 Torrance CA 90505 Support: (310) 602-4030
Time Billing and Project Management Software Built With Your Industry Knowledge BillQuick HR 2008 Start-Up Guide BQE Software, Inc. 2601 Airport Drive Suite 380 Torrance CA 90505 Support: (310) 602-4030
Instructions for Secure Email Cisco Registered Envelope Service (CRES)
 Instructions for Secure Email Cisco Registered Envelope Service (CRES) Please read the official Cisco Guidance on the Cisco Registered Envelope Service And Frequently Asked Questions A courtesy attempt
Instructions for Secure Email Cisco Registered Envelope Service (CRES) Please read the official Cisco Guidance on the Cisco Registered Envelope Service And Frequently Asked Questions A courtesy attempt
Online Backup Client User Manual Mac OS
 Online Backup Client User Manual Mac OS 1. Product Information Product: Online Backup Client for Mac OS X Version: 4.1.7 1.1 System Requirements Operating System Mac OS X Leopard (10.5.0 and higher) (PPC
Online Backup Client User Manual Mac OS 1. Product Information Product: Online Backup Client for Mac OS X Version: 4.1.7 1.1 System Requirements Operating System Mac OS X Leopard (10.5.0 and higher) (PPC
Online Backup Client User Manual Mac OS
 Online Backup Client User Manual Mac OS 1. Product Information Product: Online Backup Client for Mac OS X Version: 4.1.7 1.1 System Requirements Operating System Mac OS X Leopard (10.5.0 and higher) (PPC
Online Backup Client User Manual Mac OS 1. Product Information Product: Online Backup Client for Mac OS X Version: 4.1.7 1.1 System Requirements Operating System Mac OS X Leopard (10.5.0 and higher) (PPC
Phoenix 10835 N. 25 th Avenue, Suite 350, Phoenix, AZ 85029 Phone: (602) 866-8199 Website www.digisolaz.com
 Phoenix 10835 N. 25 th Avenue, Suite 350, Phoenix, AZ 85029 Phone: (602) 866-8199 Website www.digisolaz.com Introduction...2 General Information and Helpful Hints...3 Verify Your Company s IRS Information...4
Phoenix 10835 N. 25 th Avenue, Suite 350, Phoenix, AZ 85029 Phone: (602) 866-8199 Website www.digisolaz.com Introduction...2 General Information and Helpful Hints...3 Verify Your Company s IRS Information...4
IBM Aspera Add-in for Microsoft Outlook 1.3.2
 IBM Aspera Add-in for Microsoft Outlook 1.3.2 Windows: 7, 8 Revision: 1.3.2.100253 Generated: 02/12/2015 10:58 Contents 2 Contents Introduction... 3 System Requirements... 5 Setting Up... 6 Account Credentials...6
IBM Aspera Add-in for Microsoft Outlook 1.3.2 Windows: 7, 8 Revision: 1.3.2.100253 Generated: 02/12/2015 10:58 Contents 2 Contents Introduction... 3 System Requirements... 5 Setting Up... 6 Account Credentials...6
SYSTEM REQUIREMENTS...
 Contents INTRODUCTION... 1 BillQuick HR Setup Checklist... 2 SYSTEM REQUIREMENTS... 3 HARDWARE REQUIREMENTS... 3 SOFTWARE REQUIREMENTS... 3 Operating System Requirements... 3 Other System Requirements...
Contents INTRODUCTION... 1 BillQuick HR Setup Checklist... 2 SYSTEM REQUIREMENTS... 3 HARDWARE REQUIREMENTS... 3 SOFTWARE REQUIREMENTS... 3 Operating System Requirements... 3 Other System Requirements...
Using the Filex File Distribution System
 Using the Filex File Distribution System Contents Introduction... 1 Section 1: Creating and Sharing Folders... 1 Section 2: Sharing Files... 6 Important notes... 10 Introduction Filex is a file distribution
Using the Filex File Distribution System Contents Introduction... 1 Section 1: Creating and Sharing Folders... 1 Section 2: Sharing Files... 6 Important notes... 10 Introduction Filex is a file distribution
P309 - Proofpoint Encryption - Decrypting Secure Messages Business systems
 Procedure P309 - Proofpoint Encryption - Decrypting Secure Messages Business systems P309 - Page: Page 1 of 12 Date of Release: 23 February 2011 Status: Final Document Reference: Title: P309 Release Number:
Procedure P309 - Proofpoint Encryption - Decrypting Secure Messages Business systems P309 - Page: Page 1 of 12 Date of Release: 23 February 2011 Status: Final Document Reference: Title: P309 Release Number:
Using etoken for Securing E-mails Using Outlook and Outlook Express
 Using etoken for Securing E-mails Using Outlook and Outlook Express Lesson 15 April 2004 etoken Certification Course Securing Email Using Certificates Unprotected emails can be easily read and/or altered
Using etoken for Securing E-mails Using Outlook and Outlook Express Lesson 15 April 2004 etoken Certification Course Securing Email Using Certificates Unprotected emails can be easily read and/or altered
How to use Certificate in Microsoft Outlook
 How to use Certificate in Microsoft Outlook Macau Post esigntrust Version. 2006-01.01p Agenda Configure Microsoft Outlook for using esigntrust Certificate Use certificate to sign e-mail Use Microsoft Outlook
How to use Certificate in Microsoft Outlook Macau Post esigntrust Version. 2006-01.01p Agenda Configure Microsoft Outlook for using esigntrust Certificate Use certificate to sign e-mail Use Microsoft Outlook
Symantec Endpoint Encryption (SEE Client) Installation Instructions. Version 8.2
 Symantec Endpoint Encryption (SEE Client) Installation Instructions Version 8.2 Warning: This software is labor intensive, therefore it is important to validate that the hard drive is healthy by first
Symantec Endpoint Encryption (SEE Client) Installation Instructions Version 8.2 Warning: This software is labor intensive, therefore it is important to validate that the hard drive is healthy by first
Sending Files to a Social Security Laptop
 Sending Files to a Social Security Laptop Introduction There are multiple options to send files to your Social Security laptop. A couple of options are to encrypt files and then send them by email or transfer
Sending Files to a Social Security Laptop Introduction There are multiple options to send files to your Social Security laptop. A couple of options are to encrypt files and then send them by email or transfer
Yale Secure File Transfer User Guide
 Yale Secure File Transfer For assistance contact the ITS Help Desk 203-432-9000, helpdesk@yale.edu Yale Secure File Transfer User Guide This document provides information and detailed steps for using Yale's
Yale Secure File Transfer For assistance contact the ITS Help Desk 203-432-9000, helpdesk@yale.edu Yale Secure File Transfer User Guide This document provides information and detailed steps for using Yale's
PrestoFax User Guide Version 3.0
 PrestoFax User Guide Version 3.0 Page 1 of 12 PrestoFax User Guide Table of Contents Incoming Faxes... 3 Outgoing Faxes... 3 PrestoFax Web Interface Instructions... 4 Logging into the PrestoFax Web Interface...
PrestoFax User Guide Version 3.0 Page 1 of 12 PrestoFax User Guide Table of Contents Incoming Faxes... 3 Outgoing Faxes... 3 PrestoFax Web Interface Instructions... 4 Logging into the PrestoFax Web Interface...
Encrypting*a*Windows*7*Hard*Disk* with%bitlocker%disk%encryption!
 Encrypting*a*Windows*7*Hard*Disk* with%bitlocker%disk%encryption Thisdocumentcontainsthenecessarystepstoencryptthecontentsofaharddrive usingbitlockerandwindows7. Thefollowinginstructionsarederivedfromdocumentationat:
Encrypting*a*Windows*7*Hard*Disk* with%bitlocker%disk%encryption Thisdocumentcontainsthenecessarystepstoencryptthecontentsofaharddrive usingbitlockerandwindows7. Thefollowinginstructionsarederivedfromdocumentationat:
How To Install Ru-Vpn On A Pc Or Macbook Or Ipad (For Macbook) With A Microsoft Macbook (For Pc) With An Ipad Or Ipa (For A Macbook). Pc (For An
 RU-VPN Installation Instructions (Windows Vista and Windows 7) An RU-VPN id allows authorized users to access Ryerson s Administrative Systems via the internet. RU-VPN utilizes a digital certificate that
RU-VPN Installation Instructions (Windows Vista and Windows 7) An RU-VPN id allows authorized users to access Ryerson s Administrative Systems via the internet. RU-VPN utilizes a digital certificate that
Online Backup Client User Manual
 For Mac OS X Software version 4.1.7 Version 2.2 Disclaimer This document is compiled with the greatest possible care. However, errors might have been introduced caused by human mistakes or by other means.
For Mac OS X Software version 4.1.7 Version 2.2 Disclaimer This document is compiled with the greatest possible care. However, errors might have been introduced caused by human mistakes or by other means.
BillQuick HR Getting Started Guide2015
 GETTING STARTED GUIDE: BillQuick HR 2015 BillQuick HR Getting Started Guide2015 BillQuick Power Up Your Business (866) 945-1595 www.bqe.com info@bqe.com GETTING STARTED GUIDE: BillQuick HR 2015 Contents
GETTING STARTED GUIDE: BillQuick HR 2015 BillQuick HR Getting Started Guide2015 BillQuick Power Up Your Business (866) 945-1595 www.bqe.com info@bqe.com GETTING STARTED GUIDE: BillQuick HR 2015 Contents
Searching your Archive in Outlook (Normal)
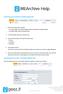 Searching your Archive in Outlook (Normal) 1. View the Archive Add in toolbar. In Outlook 2007, the toolbar displays below the standard Outlook toolbars. In Outlook 2010, select the McAfee tab. 2. In the
Searching your Archive in Outlook (Normal) 1. View the Archive Add in toolbar. In Outlook 2007, the toolbar displays below the standard Outlook toolbars. In Outlook 2010, select the McAfee tab. 2. In the
Implementation of Encrypting File System (EFS) on Portable Computers Approved by: Acting Deputy Administrator, Management
 UNITED STATES DEPARTMENT OF AGRICULTURE Farm Service Agency Washington, DC 20250 Notice IRM-378 For: FSA Employees and Contractor Employees Implementation of Encrypting File System (EFS) on Portable Computers
UNITED STATES DEPARTMENT OF AGRICULTURE Farm Service Agency Washington, DC 20250 Notice IRM-378 For: FSA Employees and Contractor Employees Implementation of Encrypting File System (EFS) on Portable Computers
Installing and Configuring Microsoft Dynamics Outlook Plugin to Use with ipipeline MS CRM
 Installing and Configuring Microsoft Dynamics Outlook Plugin to Use with ipipeline MS CRM Downloading 1. Download zip file for your version of Outlook (32-bit or 64-bit) and save to computer. (This is
Installing and Configuring Microsoft Dynamics Outlook Plugin to Use with ipipeline MS CRM Downloading 1. Download zip file for your version of Outlook (32-bit or 64-bit) and save to computer. (This is
Using Microsoft Windows Encrypted File System (EFS)
 Using Microsoft Windows Encrypted File System (EFS) Agenda Protecting our Data Types of Data What is EFS How to use EFS Best Practices Protecting our Data Two types of disk encryption: Full Disk Encryption
Using Microsoft Windows Encrypted File System (EFS) Agenda Protecting our Data Types of Data What is EFS How to use EFS Best Practices Protecting our Data Two types of disk encryption: Full Disk Encryption
Use your UNNCNetID and password to log in. The first time you login to the system, you may receive the following screen:
 (Secure FTP to/from Outside (non-unmc Parties) Information Technology Services July 2012 Contact the ITS Helpdesk at 402-559-7700 or helpdesk@unmc.edu with questions. Personnel at UNMC occasionally need
(Secure FTP to/from Outside (non-unmc Parties) Information Technology Services July 2012 Contact the ITS Helpdesk at 402-559-7700 or helpdesk@unmc.edu with questions. Personnel at UNMC occasionally need
About DropSend. Sending Files with DropSend
 About DropSend DropSend is a service that allows businesses and individuals to send large files, store files online and collaborate in a quick and easy way. DropSend Business Plan will help your company
About DropSend DropSend is a service that allows businesses and individuals to send large files, store files online and collaborate in a quick and easy way. DropSend Business Plan will help your company
Dictamus Manual. Dictamus is a professional dictation app for iphone, ipod touch and ipad. This manual describes setup and use of Dictamus version 10.
 Dictamus Manual Dictamus is a professional dictation app for iphone, ipod touch and ipad. This manual describes setup and use of Dictamus version 10. Table of Contents Settings! 3 General! 3 Dictation!
Dictamus Manual Dictamus is a professional dictation app for iphone, ipod touch and ipad. This manual describes setup and use of Dictamus version 10. Table of Contents Settings! 3 General! 3 Dictation!
Installing your certificate on your Mac
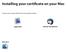 Installing your certificate on your Mac Choose your email software from the options below. Apple Mail Using Apple Mail Apple Mail 1 of 2 Step one Visit Comodo for your free secure email certificate by
Installing your certificate on your Mac Choose your email software from the options below. Apple Mail Using Apple Mail Apple Mail 1 of 2 Step one Visit Comodo for your free secure email certificate by
PhoneCrypt Desktop. Phone Encryption Software. PhoneCrypt Manual Mobile phone encryption for Windows Platforms
 PhoneCrypt Desktop Phone Encryption Software PhoneCrypt Manual Mobile phone encryption for Windows Platforms Introduction Contents http:// www. securstar.com info@securstar.com 2009 by SecurStar GmbH,
PhoneCrypt Desktop Phone Encryption Software PhoneCrypt Manual Mobile phone encryption for Windows Platforms Introduction Contents http:// www. securstar.com info@securstar.com 2009 by SecurStar GmbH,
Installing the Microsoft Network Driver Interface
 Installing the Microsoft Network Driver Interface Overview This guide explains how to install the PictureTel Live200 Microsoft Network Driver Interface (NDIS) software you have downloaded from PictureTel's
Installing the Microsoft Network Driver Interface Overview This guide explains how to install the PictureTel Live200 Microsoft Network Driver Interface (NDIS) software you have downloaded from PictureTel's
Using Voltage SecureMail
 Using Voltage SecureMail Using Voltage SecureMail Desktop Based on the breakthrough Identity-Based Encryption technology, Voltage SecureMail makes sending a secure email as easy as sending it without encryption.
Using Voltage SecureMail Using Voltage SecureMail Desktop Based on the breakthrough Identity-Based Encryption technology, Voltage SecureMail makes sending a secure email as easy as sending it without encryption.
Real Vision Imaging. Use a Proxy Server to Connect Your IBM i to the Web. IBM Has Discontinued Service and Support for ALL 3995/3996 Optical Libraries
 January 2013 YOUR DOCUMENT MANAGEMENT SOLUTION Real Vision Imaging Use a Proxy Server to Connect Your IBM i to the Web Real Vision Software, Inc. P.O. Box 12958 Alexandria, LA 71315-2958 3700 Jackson Street
January 2013 YOUR DOCUMENT MANAGEMENT SOLUTION Real Vision Imaging Use a Proxy Server to Connect Your IBM i to the Web Real Vision Software, Inc. P.O. Box 12958 Alexandria, LA 71315-2958 3700 Jackson Street
Secure Email User Guide
 Secure Email User Guide Transport Layer Security (TLS) Pretty Good Privacy (PGP) PDF Messenger 1 Contents 1 Introduction... 3 2 Transport Layer Security (TLS).4 3 Pretty Good Privacy (PGP).5 4 PDF Messenger...
Secure Email User Guide Transport Layer Security (TLS) Pretty Good Privacy (PGP) PDF Messenger 1 Contents 1 Introduction... 3 2 Transport Layer Security (TLS).4 3 Pretty Good Privacy (PGP).5 4 PDF Messenger...
GUIDELINES. Electronic Reporting for Ozone-Depleting Substances. Part 3: Submitting ODS Data to EPA via CDX: Initial Setup and Submission
 GUIDELINES Electronic Reporting for Ozone-Depleting Substances Part 3: Submitting ODS Data to EPA via CDX: Initial Setup and Submission March 2008 If you need assistance with these guidelines, please contact:
GUIDELINES Electronic Reporting for Ozone-Depleting Substances Part 3: Submitting ODS Data to EPA via CDX: Initial Setup and Submission March 2008 If you need assistance with these guidelines, please contact:
How to Setup Privacy Guard Encryption.
 How to Setup Privacy Guard Encryption. Contents Setting up for the first time.... 1 Installing the Software (free)... 1 Generating your own key... 2 Share your key with your friends so they can send you
How to Setup Privacy Guard Encryption. Contents Setting up for the first time.... 1 Installing the Software (free)... 1 Generating your own key... 2 Share your key with your friends so they can send you
Law College Computer and Technology Information
 Law College Computer and Technology Information Account Creation All law students, faculty and staff must have a University of Toledo authentication domain (UTAD) computer account. This account will allow
Law College Computer and Technology Information Account Creation All law students, faculty and staff must have a University of Toledo authentication domain (UTAD) computer account. This account will allow
IBackup Drive User Guide
 IBackup Drive User Guide TABLE OF CONTENTS Introduction... 3 Features... 4 Install IBackup Drive... 5 Login to IBackup Drive... 5 About Main Screen... 7 Settings... 8 Toolbar Options... 11 IBackup Drive
IBackup Drive User Guide TABLE OF CONTENTS Introduction... 3 Features... 4 Install IBackup Drive... 5 Login to IBackup Drive... 5 About Main Screen... 7 Settings... 8 Toolbar Options... 11 IBackup Drive
NETWRIX IDENTITY MANAGEMENT SUITE
 NETWRIX IDENTITY MANAGEMENT SUITE FEATURES AND REQUIREMENTS Product Version: 3.3 February 2013. Legal Notice The information in this publication is furnished for information use only, and does not constitute
NETWRIX IDENTITY MANAGEMENT SUITE FEATURES AND REQUIREMENTS Product Version: 3.3 February 2013. Legal Notice The information in this publication is furnished for information use only, and does not constitute
Step by step guide how to password protect your USB flash drive
 Step by step guide how to password protect your USB flash drive 1 Content 1. How to create encrypted partition on USB flash drive 2. How to work with encrypted partition on the USB flash drive - Rohos
Step by step guide how to password protect your USB flash drive 1 Content 1. How to create encrypted partition on USB flash drive 2. How to work with encrypted partition on the USB flash drive - Rohos
Remote Network Accelerator
 Remote Network Accelerator Evaluation Guide LapLink Software 10210 NE Points Drive Kirkland, WA 98033 Tel: (425) 952-6000 www.laplink.com LapLink Remote Network Accelerator Evaluation Guide Page 1 of 19
Remote Network Accelerator Evaluation Guide LapLink Software 10210 NE Points Drive Kirkland, WA 98033 Tel: (425) 952-6000 www.laplink.com LapLink Remote Network Accelerator Evaluation Guide Page 1 of 19
PGP Zip Self-Decrypting Archive (SDA) 5/29/2012 Version 1.1
 PGP Zip Self-Decrypting Archive (SDA) 5/29/2012 Version 1.1 Table of Contents 1 Self Decrypting Archives (SDA)... 1-2 2 Setting Windows to Display File Extensions... 2-3 3 Creating PGP Zip SDA... 3-4
PGP Zip Self-Decrypting Archive (SDA) 5/29/2012 Version 1.1 Table of Contents 1 Self Decrypting Archives (SDA)... 1-2 2 Setting Windows to Display File Extensions... 2-3 3 Creating PGP Zip SDA... 3-4
SECURE EMAIL USER GUIDE OUTLOOK 2000
 WELLS FARGO AUTHENTICATION SERVICES DATED: MAY 2003 TABLE OF CONTENTS GENERAL INFORMATION... 1 INSTALLING THE WELLS FARGO ROOT CERTIFICATE CHAIN.. 2 INSTALLING THE CERTIFICATES INTO IE... 3 SETTING UP
WELLS FARGO AUTHENTICATION SERVICES DATED: MAY 2003 TABLE OF CONTENTS GENERAL INFORMATION... 1 INSTALLING THE WELLS FARGO ROOT CERTIFICATE CHAIN.. 2 INSTALLING THE CERTIFICATES INTO IE... 3 SETTING UP
RMFT Web Client User Guide
 RMFT Web Client User Guide Software Version 2.5 Supported Browsers: Browser Internet Explorer Firefox Safari Google Chrome Version 7.0 and above 3 and above 3.2 and above 1.0 and above August 7, 2011 RepliWeb,
RMFT Web Client User Guide Software Version 2.5 Supported Browsers: Browser Internet Explorer Firefox Safari Google Chrome Version 7.0 and above 3 and above 3.2 and above 1.0 and above August 7, 2011 RepliWeb,
Overview Keys. Overview
 Overview Keys Overview The PGPmail program performs fast, high-security, public-key encrypting (with optional compression), decrypting, and authenticating of electronic messages and files. The program
Overview Keys Overview The PGPmail program performs fast, high-security, public-key encrypting (with optional compression), decrypting, and authenticating of electronic messages and files. The program
MICR Check Printing with Digital Signatures
 Table of Contents Table of Contents... 1 Overview... 2 Ordering Supplies... 3 Loading the Software... 4 TOPS 2000 MICR Disk... 4 Before you install... 4 Installing the MICR Check Printing Interface...
Table of Contents Table of Contents... 1 Overview... 2 Ordering Supplies... 3 Loading the Software... 4 TOPS 2000 MICR Disk... 4 Before you install... 4 Installing the MICR Check Printing Interface...
For all other applications, including new applications, please visit www.apvma.gov.au
 This content only applies to transition applications that were received before 1 July 2014. The content will be relevant for these applications until 30 June 2015. For all other applications, including
This content only applies to transition applications that were received before 1 July 2014. The content will be relevant for these applications until 30 June 2015. For all other applications, including
USER MANUAL. v. 11.4.1 ---------------------- December 2015 ----------------------
 USER MANUAL v. 11.4.1 ---------------------- December 2015 ---------------------- Contents At a Glance Miscellaneous 3 About EncryptDisc 14 Product info 4 About this manual 15 Copyright & trademark 15
USER MANUAL v. 11.4.1 ---------------------- December 2015 ---------------------- Contents At a Glance Miscellaneous 3 About EncryptDisc 14 Product info 4 About this manual 15 Copyright & trademark 15
Your Archiving Service
 It s as simple as 1, 2, 3 This email archiving setup guide provides you with easy to follow instructions on how to setup your new archiving service as well as how to create archiving users and assign archiving
It s as simple as 1, 2, 3 This email archiving setup guide provides you with easy to follow instructions on how to setup your new archiving service as well as how to create archiving users and assign archiving
Configuring the WT-4 for ftp (Infrastructure Mode)
 Introduction En Configuring the WT-4 for ftp (Infrastructure Mode) This document provides basic instructions on configuring the WT-4 wireless transmitter and a ftp server for transmission over an infrastructure
Introduction En Configuring the WT-4 for ftp (Infrastructure Mode) This document provides basic instructions on configuring the WT-4 wireless transmitter and a ftp server for transmission over an infrastructure
B. KTT Web-based File Transfer
 B. KTT Web-based File Transfer The Key Total Treasury Internet File Transfer module allows clients to upload or download data files to/from KeyBank s transmission platform using a PC and Internet browser.
B. KTT Web-based File Transfer The Key Total Treasury Internet File Transfer module allows clients to upload or download data files to/from KeyBank s transmission platform using a PC and Internet browser.
Configuring Windows 7 to Use Encrypted (WPA-E) Wireless Services a...
 1 di 9 31/05/2011 14.48 Search This Site All UCSD Sites Blink Home > Technology > Network Services > Connections > Wireless > Windows 7 Configuring Windows 7 to Use Encrypted (WPA-E) Wireless Services
1 di 9 31/05/2011 14.48 Search This Site All UCSD Sites Blink Home > Technology > Network Services > Connections > Wireless > Windows 7 Configuring Windows 7 to Use Encrypted (WPA-E) Wireless Services
Email Archiving User Guide Outlook Plugin. Manual version 3.1
 Email Archiving User Guide Outlook Plugin Manual version 3.1 Copyright 2012 Omniquad Ltd. All rights reserved. Omniquad Ltd Crown House 72 Hammersmith Road Hammersmith London W14 8TH United Kingdom Omniquad
Email Archiving User Guide Outlook Plugin Manual version 3.1 Copyright 2012 Omniquad Ltd. All rights reserved. Omniquad Ltd Crown House 72 Hammersmith Road Hammersmith London W14 8TH United Kingdom Omniquad
Honeywell Secure Email External User Guide August 2013
 Honeywell Secure Email External User Guide August 2013 PAGE: 1 of 14 Chapter No Table of Content Page No 1 Introduction 3 2 Using the Honeywell Secure Email Interface 3 3 Sending an Encrypted Email to
Honeywell Secure Email External User Guide August 2013 PAGE: 1 of 14 Chapter No Table of Content Page No 1 Introduction 3 2 Using the Honeywell Secure Email Interface 3 3 Sending an Encrypted Email to
7-zip Encryption Instructions
 1. In a simple text editor (Notepad, Notepad++, jedit, etc.) create a text file (SendToTAP) that contains your sensitive data information. [Note the location where the file is stored on your computer.]
1. In a simple text editor (Notepad, Notepad++, jedit, etc.) create a text file (SendToTAP) that contains your sensitive data information. [Note the location where the file is stored on your computer.]
CCH Axcess Portal Client User Guide
 CCH Axcess Portal Client User Guide Keys Quick reference to the key aspects of a particular function Icon Legend Tip Notes Best practice tips and shortcuts Informational notes about functions Warning Important
CCH Axcess Portal Client User Guide Keys Quick reference to the key aspects of a particular function Icon Legend Tip Notes Best practice tips and shortcuts Informational notes about functions Warning Important
The LRS File Transfer Service offers a way to send and receive files in a secured environment
 File Transfer Service The LRS File Transfer Service offers a way to send and receive files in a secured environment using HTTPS or FTPS. It also supports unsecured standard FTP transfers. The service supports
File Transfer Service The LRS File Transfer Service offers a way to send and receive files in a secured environment using HTTPS or FTPS. It also supports unsecured standard FTP transfers. The service supports
CISCO SECURE MAIL. External User Guide. 1/15/15 Samson V.
 1/15/15 Samson V. 1. These instructions are for users who reside outside the University of Colorado Denver that receive encrypted emails from faculty or staff of UC Denver. As a part of our HIPAA compliance
1/15/15 Samson V. 1. These instructions are for users who reside outside the University of Colorado Denver that receive encrypted emails from faculty or staff of UC Denver. As a part of our HIPAA compliance
USER MANUAL. v. 11.3 ------------------------ January 2014 ------------------------
 USER MANUAL v. 11.3 ------------------------ January 2014 ------------------------ 1 Contents At a Glance Miscellaneous 3 About EncryptDisc 14 Product info 4 About this manual 15 Copyright & trademark
USER MANUAL v. 11.3 ------------------------ January 2014 ------------------------ 1 Contents At a Glance Miscellaneous 3 About EncryptDisc 14 Product info 4 About this manual 15 Copyright & trademark
Figure 1: Restore Tab
 Apptix Online Backup by Mozy Restore How do I restore my data? There are five ways of restoring your data: 1) Performing a Restore Using the Restore Tab You can restore files from the Apptix Online Backup
Apptix Online Backup by Mozy Restore How do I restore my data? There are five ways of restoring your data: 1) Performing a Restore Using the Restore Tab You can restore files from the Apptix Online Backup
AxCrypt File Encryption Software for Windows. Quick Installation and Users Guide. Version 1.7 or later. July 2012
 AxCrypt File Encryption Software for Windows Quick Installation and Users Guide Version 1.7 or later July 2012 Copyright 2005-2012 Svante Seleborg, Axantum Software AB 2(18) This guide describes how to
AxCrypt File Encryption Software for Windows Quick Installation and Users Guide Version 1.7 or later July 2012 Copyright 2005-2012 Svante Seleborg, Axantum Software AB 2(18) This guide describes how to
OutDisk 4.0 FTP FTP for Email Users using Microsoft Windows and/or Microsoft Outlook. 5/1/2012 2012 Encryptomatic LLC www.encryptomatic.
 OutDisk 4.0 FTP FTP for Email Users using Microsoft Windows and/or Microsoft Outlook 5/1/2012 2012 Encryptomatic LLC www.encryptomatic.com Contents What is OutDisk?... 3 OutDisk Requirements... 3 How Does
OutDisk 4.0 FTP FTP for Email Users using Microsoft Windows and/or Microsoft Outlook 5/1/2012 2012 Encryptomatic LLC www.encryptomatic.com Contents What is OutDisk?... 3 OutDisk Requirements... 3 How Does
How To Restore Your Data On A Backup By Mozy (Windows) On A Pc Or Macbook Or Macintosh (Windows 2) On Your Computer Or Mac) On An Pc Or Ipad (Windows 3) On Pc Or Pc Or Micro
 Online Backup by Mozy Restore Common Questions Document Revision Date: June 29, 2012 Online Backup by Mozy Common Questions 1 How do I restore my data? There are five ways of restoring your data: 1) Performing
Online Backup by Mozy Restore Common Questions Document Revision Date: June 29, 2012 Online Backup by Mozy Common Questions 1 How do I restore my data? There are five ways of restoring your data: 1) Performing
2007 Microsoft Office System Document Encryption
 2007 Microsoft Office System Document Encryption June 2007 Table of Contents Introduction 1 Benefits of Document Encryption 2 Microsoft 2007 Office system Document Encryption Improvements 5 End-User Microsoft
2007 Microsoft Office System Document Encryption June 2007 Table of Contents Introduction 1 Benefits of Document Encryption 2 Microsoft 2007 Office system Document Encryption Improvements 5 End-User Microsoft
ADSelfService Plus: 3rd party Winlogon Client Software Support
 ADSelfService Plus: 3rd party Winlogon Client Software Support 1 Contents ADSelfService Plus - Introduction:... 3 ADSelfService Plus Client Software:... 3 Support for 3rd party GINA/Credential Provider
ADSelfService Plus: 3rd party Winlogon Client Software Support 1 Contents ADSelfService Plus - Introduction:... 3 ADSelfService Plus Client Software:... 3 Support for 3rd party GINA/Credential Provider
Welcome. 4 Common Security Best Practices. to the. Online Training Course
 Welcome to the 4 Common Security Best Practices Online Training Course Disclaimer 2 Introduction Information Security means protecting information from unauthorized access, use, disclosure, inspection
Welcome to the 4 Common Security Best Practices Online Training Course Disclaimer 2 Introduction Information Security means protecting information from unauthorized access, use, disclosure, inspection
Outlook Data File navigate to the PST file that you want to open, select it and choose OK. The file will now appear as a folder in Outlook.
 Migrate Archived Outlook Items Outlook includes archiving functionality that is used to free up space on the mail server by moving older items from the mail server to PST files stored on your computer
Migrate Archived Outlook Items Outlook includes archiving functionality that is used to free up space on the mail server by moving older items from the mail server to PST files stored on your computer
DESLock+ Basic Setup Guide Version 1.20, rev: June 9th 2014
 DESLock+ Basic Setup Guide Version 1.20, rev: June 9th 2014 Contents Overview... 2 System requirements:... 2 Before installing... 3 Download and installation... 3 Configure DESLock+ Enterprise Server...
DESLock+ Basic Setup Guide Version 1.20, rev: June 9th 2014 Contents Overview... 2 System requirements:... 2 Before installing... 3 Download and installation... 3 Configure DESLock+ Enterprise Server...
HertSFX. User Guide V2.04. Hertfordshire s Secure File Exchange Portal. (Jan 2014) HertSFX User Guide V2.04 Jan 2014 Page 1 of 17
 Hertfordshire s Secure File Exchange Portal User Guide V2.04 (Jan 2014) HertSFX User Guide V2.04 Jan 2014 Page 1 of 17 CONTENTS 1. About HertSFX... 3 2. HertSFX Limitations... 3 3. Getting Started... 3
Hertfordshire s Secure File Exchange Portal User Guide V2.04 (Jan 2014) HertSFX User Guide V2.04 Jan 2014 Page 1 of 17 CONTENTS 1. About HertSFX... 3 2. HertSFX Limitations... 3 3. Getting Started... 3
ACS Email Encryption Recipient Guide
 ACS Email Encryption Recipient Guide ACS ENCRYPTION SERVICES / TRAINING AND AWARENESS ACS Email Encryption Recipient Guide Email Encryption Recipient Guide ACS A Xerox Company 2828 North Haskell Dallas,
ACS Email Encryption Recipient Guide ACS ENCRYPTION SERVICES / TRAINING AND AWARENESS ACS Email Encryption Recipient Guide Email Encryption Recipient Guide ACS A Xerox Company 2828 North Haskell Dallas,
AxCrypt File Encryption Software for Windows. Quick Installation Guide. Version 1.6.3. January 2008
 AxCrypt File Encryption Software for Windows Quick Installation Guide Version 1.6.3 January 2008 Copyright 2005-2008 Svante Seleborg, Axantum Software AB 2(19) This guide describes how to install and quickly
AxCrypt File Encryption Software for Windows Quick Installation Guide Version 1.6.3 January 2008 Copyright 2005-2008 Svante Seleborg, Axantum Software AB 2(19) This guide describes how to install and quickly
Unipass Securemail Client FAQ Document v1.1. This document a summary of some of the most common questions asked about the Unipass Securemail client.
 Unipass Securemail Client FAQ Document v1.1 This document a summary of some of the most common questions asked about the Unipass Securemail client. UIdP Project Team 28/06/2014 Contents Section 1 - Unipass
Unipass Securemail Client FAQ Document v1.1 This document a summary of some of the most common questions asked about the Unipass Securemail client. UIdP Project Team 28/06/2014 Contents Section 1 - Unipass
Guidance for IA DMM: Connecting Your Computer to FSU Video File Server
 1 Guidance for IA DMM: Connecting Your Computer to FSU Video File Server This guide will walk you through the process of connecting your computer to the FSU Video File Server and then uploading video files
1 Guidance for IA DMM: Connecting Your Computer to FSU Video File Server This guide will walk you through the process of connecting your computer to the FSU Video File Server and then uploading video files
File Share Service User guide
 File Share Service User guide Version: 2.0 Written by: Sriram Rao Last Modified: 03/16/2012 1 Index Index... 2 Overview... 3 Change Log... 4 Login Instructions... 5 Searching files by name or content...
File Share Service User guide Version: 2.0 Written by: Sriram Rao Last Modified: 03/16/2012 1 Index Index... 2 Overview... 3 Change Log... 4 Login Instructions... 5 Searching files by name or content...
Accellion, Inc. 1900 Embarcadero Road Suite 207 Palo Alto, CA 94303 Tel +1 650 739-0095 Fax +1 650 739-0561. info@accellion.com
 Accellion, Inc. 1900 Embarcadero Road Suite 207 Palo Alto, CA 94303 Tel +1 650 739-0095 Fax +1 650 739-0561 info@accellion.com TABLE OF CONTENTS QUICK START... 4 Create an Account... 4 Send a file... 4
Accellion, Inc. 1900 Embarcadero Road Suite 207 Palo Alto, CA 94303 Tel +1 650 739-0095 Fax +1 650 739-0561 info@accellion.com TABLE OF CONTENTS QUICK START... 4 Create an Account... 4 Send a file... 4
How to backup important data
 How to backup important data How to backup important data Page 1 of 27 Contents Page: A. Backing up your emails into a Personal Folder (.pst file) 1 B. Backing up from My Documents folder. 6 C. Searching
How to backup important data How to backup important data Page 1 of 27 Contents Page: A. Backing up your emails into a Personal Folder (.pst file) 1 B. Backing up from My Documents folder. 6 C. Searching
