Perceptions of Cyberstalking Among College Students
|
|
|
- Magdalen King
- 8 years ago
- Views:
Transcription
1 Perceptions of Cyberstalking Among College Students Eileen M. Alexy, PhD, APRN, BC Ann W. Burgess, DNSc, APRN, BC, FAAN Timothy Baker, PhD Shirley A. Smoyak, PhD, RN, FAAN This article contributes to a growing body of research investigating the phenomenon of cyberstalking. Participants consisted of 100 students from a state university and 656 students from a large private university. Data were gathered from students about responses to a cyberstalking scenario and their use and experiences with the Internet. Furthermore, an analysis and comparison of students who reported having been stalked to those who had been cyberstalked was completed. An unexpected finding was that male students were statistically more likely than female students to have been cyberstalked, and Caucasian males had the highest correlation. The conclusion indicates that for those individuals who were cyberstalked, the stalking perpetrator was most likely to be a former intimate partner. Recommendations for mental health professionals are provided. [Brief Treatment and Crisis Intervention 5: (2005)] KEY WORDS: cyberstalking, stalking, Internet crime, online crime, harassment. Over the past decade, the phenomenon of stalking has emerged as a salient social and political issue. Stalking encompasses a range of behaviors initiated by an individual who engages in a pattern of harassing or threatening From the School of Nursing, The College of New Jersey (Alexy), Boston College (Burgess), Data Integrity, Inc. (Baker), and Rutgers, The State University of New Jersey (Smoyak). Contact author: Eileen M. Alexy, Assistant Professor, The College of New Jersey, School of Nursing, 2000 Pennington Road, PO Box 7718, Ewing, NJ alexy@tcnj.edu. doi: /brief-treatment/mhi020 Advance Access publication June 29, 2005 behavior (Ashcroft, 2001; Reno, 1999). The threatening behavior may manifest itself in direct or indirect acts, such as following a person, appearing at a person s home or place of business, making harassing phone calls, leaving written messages or objects, or vandalizing a person s property (Tjaden & Thoennes, 1998). The emergence of communication technologies, or new media, such as the Internet, has provided an additional conduit and method for stalkers to identify and target their victims. This evolution or transformation of stalking in common discourse is known as cyberstalking. ª The Author Published by Oxford University Press. All rights reserved. For permissions, please journals.permissions@oupjournals.org. 279
2 ALEXY ET AL. Background Researchers have only recently begun to investigate the phenomenon of cyberstalking (D Ovidio & Doyle, 2003; Finkelhor, Mitchell, & Wolak, 2000; Fisher, Cullen, & Turner, 2000, 2002; Lee, 1998; Pathé & Mullen, 1997; Spitzberg & Hoobler, 2002). Findings from these studies support the notion that the ability of an online stalker to instill fear and gain control over a victim reflects the modus operandi of an offline stalker. Although the prevalence and incidence of cyberstalking remain unknown, anecdotal reports suggest that cyberstalking appears to be expanding at a rapid pace, especially among the nation s youth. Lee (1998) reported the extent of cyberstalking behavior in a college context and posited that, to a certain extent, it was a sociallysanctioned behavior, instituted and encouraged by Western courtship mores and ideas of romance (pp ). To assess how college students view mutual romance compared to online and offline stalking, the investigator distributed a survey to 556 male and female college students at six universities. Six scenarios were presented to students, two of which addressed cyberstalking. In the first cyberstalking scenario, a stranger contacted a woman strictly through and chat rooms. In the second scenario, the stranger contacted the woman through and chat rooms, but he also began to employ conventional offline stalking behaviors, such as leaving messages on her answering machine and gifts on her doorstep. Slightly more than 50% of students responded that the woman was stalked in the first scenario. In the second scenario, 60.9% recognized the behavior as stalking. Lee (1998) found that romantic treatment obscured the issue of stalking and that stranger stalking was perceived as more dangerous than acquaintance stalking. In addition, behaviors that were characterized as stalking in an offline context were interpreted more like romance and less like stalking than in an online context. Students may have more readily identified both scenarios as cyberstalking because a stranger in both scenarios contacted the woman. Moreover, as the cyberstalker began to use conventional stalking methods, the physical proximity was increased; thus the second scenario may have appeared more foreboding. Lee concluded that the interpretation of cyberstalking as stalking was based on what other types of behavior accompanied electronic activities. Misperceptions and minimalization about stalking incidents abound are of significant concern and may be attributed to a lack of education and understanding of the crime. Victims, perpetrators, and authority figures (i.e., law enforcement officers, school administrators) often do not grasp the malicious nature of the crime until an individual is the victim of physical assault or personal property is damaged. Services for victims of offline stalking are often insufficient, and for victims of online stalking they are virtually nonexistent (Draucker, 1999; Fisher et al., 2000, 2002). Spitzberg and Hoobler (2002) reported on three pilot studies focused on developing and refining a measure of cyberstalking victimization and the incidence of such victimization. In the main study, they explored aspects of offline stalking that reciprocally cross into the electronic world. Based on responses from 235 undergraduate communication college students, the investigators found that almost one third reported some form of computer-based unwanted pursuit, most of which was relatively harmless but harassing. Spitzberg and Hoobler noted that this relatively innocuous type of hyperintimacy displayed over the Internet, in the guise of excessive and redundant messages of affection and disclosure, may elicit a range of relatively apparent coping responses. However, the more severe 280 Brief Treatment and Crisis Intervention / 5:3 August 2005
3 Cyberstalking Among College Students forms of computer-based unwanted pursuit showed little or no relationship to coping responses, suggesting that the victims of such computer-based actions and the shifting of pursuit from the Internet to the offline real world may desensitize victims of pursuit. D Ovidio and Doyle (2003) conducted a descriptive study on cyberstalking using official police records from the Computer Investigation & Technology Unit (CITU) of the New York City Police Department (NYPD). All closed cases of aggravated harassment in which the perpetrator used a computer or the Internet as the instrument to commit the offense were used as the basis for the data. As defined by New York Penal Law , a person is guilty of aggravated harassment when, he or she uses mechanical, electronic, or written communication with the purposeful intent to harass, annoy, threaten, or alarm another person. Approximately 43% of the cases reported to and investigated by the NYPD CITU during January 1996 through August 2000 involved the crime of cyberstalking. About 80% of the perpetrators were male, and the average age of the perpetrator was 24. In addition, approximately 26% of the perpetrators were juveniles under the age of 16. Nearly three quarters of the perpetrators were White, whereas 13% were Asian, 8% were Hispanic, and 5% were Black. The majority of victims were individuals, specifically, females who comprised 52% in comparison to males who comprised 35% of the victim population. The remaining targets of victimization were institutions: educational (8%), private corporations (5%), and public sector (1%). Approximately 85% of the victims were White, 6% were Asian, 5% were Black, and 4% were Hispanic. The average age of the victims was 32. In 92% of the cases, perpetrators used only one method to cyberstalk their victims. was the most prevalent method used in almost 79% of the cases. Instant messages were used in 13%, chat rooms were used in 8%, message boards were used in 4%, and Web sites were used in 2% of the cases. Finally, perpetrators used newsgroups and fake user profiles in approximately 1% of the cases. Unfortunately, the relationships between the victims and the perpetrators were not reported in the study. Three additional studies provide data on cyberstalking. As part of a large study on the sexual victimization of college women, Fisher et al. (2000) found that 581 women (13.1%) were stalked and reported a total of 696 stalking incidents. Of these incidents, 24.7% involved . Thus, 25% of the reported stalking incidents could be classified as cyberstalking. Pathé and Mullen (1997) examined the social and psychological impact of stalking on victims. The researchers included receiving unwanted communications through in their definition of stalking behaviors. Additionally, they reported that one victim received such voluminous and lengthy s from his/her stalker that it gravely disrupted any legitimate communications; this latter phenomenon illustrates the techniques of mail bombing and spam. Finally, the National Center for Missing and Exploited Children commissioned a study involving a national sample of children (ages 10 17) who regularly used the Internet (Finkelhor et al., 2000). In the study, the online victimization of youth was examined. In regard to cyberstalking, the researchers reported that 6% of the youth experienced online harassment in the last year; however, only 2% described the incident as distressing. Forty-eight percent of those who experienced online harassment were female, and 51% were male. Sixty-three percent of the perpetrators were other juveniles, and 24% lived within an hour s drive of the youth. Of the youth who found the episode distressing, 35% of the perpetrators lived within an hour s drive of the youth. Nearly one fourth of the youth Brief Treatment and Crisis Intervention / 5:3 August
4 ALEXY ET AL. reported that they did not disclose their experience. Additionally, only 1% of these incidents were reported to law enforcement agencies. Purpose The purpose of this descriptive study was threefold: (a) to ascertain the labels, feelings, and behavioral reactions of college students about cyberstalking, (b) to determine the prevalence and coping characteristics of cyberstalking victims, and (c) to compare the labels, feelings, and behavioral reactions of cyberstalked to stalked victims. Method Participants Participants of the current study were drawn from two universities in the Mid-Atlantic region of the United States, 100 students were from a public institution and 656 students were from a private institution. Students at the private institution were given nominal extra credit for their participation. Students at the public institution who participated in a focus group received $20, and those that completed the questionnaire received a nominal monetary compensation of $10. Participants ranged in age from 17 to 55 (M ¼ 20.7 years, SD ¼ 2.94). Four hundred and fourteen (54.8%) were male students, 342 (45.2%) were female, 107 (14.2%) were first-year students, 178 (23.5%) were sophomores, 190 (25.1%) were juniors, 247 (32.7%) were seniors, and 34 (4.5%) were in graduate school. The overwhelming majority of the students (72.9%) were Caucasian, 13.0% were Asian, 5.9% were African American, 3.9% were Hispanic, and 4.4% were biracial/ multiracial or other. Ninety-one (12.0%) of the students in the study were the first in their family to attend college. Three hundred and nine (41.1%) were affiliated with fraternities or sororities. One hundred and seventy-three (22.9%) participated in intercollegiate athletics. Three hundred and thirty-seven (44.6%) had previously attended a program focused on interpersonal violence. Procedure The participants were asked to anonymously complete a questionnaire in which information was asked about their Internet use and experience with cyberstalking. Additionally, responses to a set of scenarios about interactions between two people were presented. Students were asked to label and express their opinions about the scenarios. The following scenario concerned interaction in cyberspace and was constructed from the first cyberstalking case prosecuted in California (see Miller & Maharaj, 1999). Scenario You have been monitoring a live Internet friends chat room for several days when you decide to take the plunge and participate in the discussion. You engage in several online conversations and establish trust with a variety of individuals. One of your friends asks you to speak in a private chat room. Having established trust with this person, you engage in a private conversation. Your friend types I am very attracted to you and would like to meet you in person. You are flattered but respectfully decline to meet IRL (in real life), because you are concerned with how the person will perceive you in a face-toface situation. You say good-bye and logoff your computer. Over the next few days when you check your you receive several messages and solicitations which you consider to be obscene. On at least three occasions, 282 Brief Treatment and Crisis Intervention / 5:3 August 2005
5 Cyberstalking Among College Students sometimes in the middle of the night, people knock on your door saying that they want to make your fantasy come true. Upon further investigation, you find that your name, telephone number, and address have been posted on a pornographic Internet newsgroup, with the message, I fantasize about a stranger entering my house and forcing himself/herself upon me. Results Some interesting comparisons can be made between this study s findings and previous research. Although this scenario was derived from a case where the perpetrator was convicted of committing cyberstalking, only 29.9% of the college students labeled it as such in the current study. In fact, 7.6% of the sample did not even label it as harassment, let alone stalking. This occurred in spite of the fact that 69% of the participants felt that it was physically threatening or worse, and almost three quarters (73%) said that they would report it to the police. As Lee (1998) found, the behavioral and feeling responses of students to the cyberstalking scenario may have been more intense because there were elements of both online and offline stalking. The closer physical proximity between the target and the perpetrator may account for these intense reactions. Investigating the interaction of labeling, feeling, and behavioral reaction, all correlations were in the expected direction; specifically, the more intense the feeling, the stronger the reaction. An examination of the relationships with other variables in the study found that there were very high correlations with gender. Women were more likely than men to report more severe feelings and stronger reactions. It was also found that seniors were significantly less likely to express more severe feelings. Those who felt that sexually explicit material is a growing problem on the Internet and those who had known someone who had been raped were more likely to have significant positive correlations with their level of feeling. There were significant correlations in the opposite direction on the questions of whether students knew others who had received threats of physical violence via , for those who had been stalked, and for those who had received letters in the mail as part of their victimization. It is possible that this happened because those who had experienced these episodes were numbed by the experience (Burgess & Roberts, 2000). Additional research is needed to explore these dynamics. Concerning the strength of the response, there was a positive correlation between the person having experienced harassment and the severity of the response. As with the level of feeling, there were also a large number of negative correlations between other variables included in the study and severity. These included being a sophomore, belonging to a fraternity or sorority, and knowing others who had received violent s or who had been solicited to engage in sexually explicit conversations online. For those who had been stalked, there were negative correlations with length of the stalking, if victims were being stalked by a family member, if they were being threatened by a stalker, if they told their family, if they told their intimate partner, whether they got a pet or a gun, how other people would feel, if their intimate partner told them not to contact the police, and if the stalker had violated a restraining order. On the matter of labeling, those with membership in a fraternity or sorority were more likely to label the cyberstalking scenario as stalking and less likely to label it harassment. Those who were stalked at school were less likely to label the scenario as stalking and Brief Treatment and Crisis Intervention / 5:3 August
6 ALEXY ET AL. more likely to label it harassment. Surprisingly, those who attended a program focused on interpersonal violence were more likely to respond harassment and significantly less likely to respond stalking. Also, the longer victims experienced stalking, the less likely they were to label the scenario as stalking. These appear to be counterintuitive findings; however, prior evidence suggests that stalking victims might be hesitant to assume the identity of victim (Tjaden, Thoennes, & Allison, 2000). In addition, researchers have found that students who considered themselves stalked versus harassed experienced more intrusive and threatening behaviors (Westrup, Fremouw, Thompson, & Lewis, 1999). In the current study, those who were cyberstalked experienced additional intrusive behaviors offline in the real world. Thus, the choice of a specific label may be a self-protective coping mechanism for the victim. The rationale for these labeling decisions requires further investigation. Student Internet Use and Experiences With Cyberstalking Most of the students reported beginning to use the Internet before they were 16 years old. The average student used it 5 6 hr a week. About one third used chat rooms. Most participants reported having some negative experiences on the Internet and knowing others who had experienced such episodes. Three quarters agreed that sexually explicit materials were a growing problem on the Internet and felt that it was too easy to accidentally access sexually explicit materials. Only about a third of the participants thought that the government should regulate selected materials. The primary concern expressed by students was the abuse of their personal information on the Internet. Not surprisingly, the earlier the students began using the Internet, the more they currently used it, and the more likely they were to know of people who had experienced problems. The fact that first-year students were more likely to begin using the Internet at an earlier age indicates the direction this will go in the future. Research by Finkelhor et al. (2000) illustrated that both the perpetrators and victims of cyberstalking may be increasing among our youth at a drastic rate. Furthermore, the close proximity of the perpetrators to the victims suggests that the threat of violence offline in the real world has increased. Further research on cyberstalking will need to address the relationship between the victim and the perpetrator. Women in the sample began accessing the Internet later than men. Counter to the reported national trend, women also used the Internet significantly less than men. In this sample, African Americans started using the Internet earlier than others. Moreover, those in fraternities and sororities began using the Internet earlier than others. Asians used the Internet significantly more than others. In addition, the younger the participants, the more likely they were to use chat rooms, and men were more likely to use them than women. Caucasians were significantly less likely than other races to use chat rooms, with Hispanics having the highest usage. Fraternity and sorority members were less likely to be found in chat rooms. These data provide considerable insight into the potential risk from and interface with cyberstalkers. As expected, those who had a negative experience on the Internet and knew others who had such experiences were highly intercorrelated with having other negative experiences and knowing others who had had them. The older the participants, the less likely they were to have or know someone who had these experiences. Men were more likely than women to experience negative episodes. On the opinion 284 Brief Treatment and Crisis Intervention / 5:3 August 2005
7 Cyberstalking Among College Students questions, women were more likely to feel that sex was a growing problem on the Internet and the government should do something about it. Fraternity and sorority members generally felt the opposite to be true. Those who reported having negative experiences generally agreed more about the problems. Concerning the experience of being cyberstalked, 28 students (3.7% of the total sample and 31.5% of those who reported being stalked) reported such an experience. This is about the same as the 3.2% and 24.7% numbers reported by Fisher et al. (2000). Most of the cyberstalkers were either classmates or former intimate partners; thus, the perpetrator was known to the victim. Those who were cyberstalked were also likely to have experienced other forms of stalking behaviors including receiving telephone calls and letters, being harassed, being followed, being touched, being sexually threatened, and receiving physical injury threats. The majority of the victims (82%) were stalked at home or in the dorms, and 54% were stalked at school. In 79% of the cases, the race of the victim and the perpetrator was the same. The primary ways in which victims dealt with the situation were yell at the person, screen phone calls, try to reason with them, threaten them, and plead with them. The victim chose not to tell anyone in 11% of the cases, whereas 75% told close friends and 54% told a family member. Perhaps the most unexpected finding derived from the data was the fact that although females were significantly more likely to be stalked than men (r ¼.09, p ¼.011), comparing those who had been cyberstalked with the others who had been stalked, men were significantly more likely than women to have been cyberstalked (r ¼ÿ.25, p ¼.020). No significant differences were found regarding age or the other demographic variables, although Caucasian men had the highest correlation when the sex race groups were compared separately (r ¼.31, p ¼.003). Those who were cyberstalked were significantly more likely to have had this done by a former intimate partner and were less likely to have been stalked by a stranger when compared with the others who were stalked. Victims of cyberstalking were also more likely to have received threats. Regarding the perpetrators, those who were cyberstalked were significantly more likely to have the perpetrator threaten to kill themselves, to have personal items taken, and to screen phone calls. Finally, those who were cyberstalked were significantly more likely not to do something because they thought that the situation would stop. Discussion For the current study, a scenario was included in which the perpetrator posted messages on the Internet that said the victim had fantasies about being forced to have sex with a stranger. Although this scenario was derived from a case where the perpetrator was convicted of committing cyberstalking, only 29.9% of the participants labeled it as such in the current study. Those with membership in a fraternity or sorority were more likely to label the cyberstalking scenario as stalking and less likely to label it as harassment. This finding may be due to the recent trend of proactive and preventative education efforts directed toward high-risk groups for sex crimes on campus. Surprisingly, those who attended a program focused on interpersonal violence were more likely to respond harassment and significantly less likely to respond stalking. This suggests that programs focused on interpersonal violence need to illustrate more clearly the differences between stalking and harassment. In addition, the longer victims experienced stalking, the less likely they were to label the scenario as stalking. The latter appear to Brief Treatment and Crisis Intervention / 5:3 August
8 ALEXY ET AL. be counterintuitive findings; however, prior evidence suggests that stalking victims might be hesitant to assume the identity of victim (Tjaden et al., 2000). Lee (1998) suggested that either people cannot always objectively judge their own experiences, or that they do not easily see themselves as victims (p. 440). Additionally, researchers have found that students who considered themselves stalked versus harassed experienced more intrusive and threatening behaviors (Westrup et al., 1999). In the current study, those who were cyberstalked experienced additional intrusive behaviors offline in the real world. Thus, the choice of a specific label may be a selfprotective coping mechanism for the victim (Tjaden et al., 2000; Westrup et al., 1999). The rationale for these labeling decisions requires further investigation. As Lee (1998) found, the feeling and behavioral reaction of students to the cyberstalking scenario may have been more intense because there were elements of both online and offline stalking. The closer physical proximity between the victim and the perpetrator may account for these intense reactions. By the cyberstalker posting the victim s personal information online, he/she enlisted thirdparty participation. Students may not have interpreted the posting by the cyberstalker in the scenario as threatening, but the ensuing behaviors of third parties may account for the intensity of their reaction. Only 29.9% of the students in the present study labeled the scenario as cyberstalking. These findings contradict those reported by Lee (50% and 60.9%). This result may be due to a lack of knowledge about the legal differences between harassment and stalking and demonstrates the perceptions found in this college population. The primary difference between cyberstalking and cyberharassment is the intent to instill fear or dread in the victim and the repetitive nature of the perpetrator s actions. Differences between cyberstalking and cyberharassment require further elucidation, and future studies addressing the perception of cyberstalking in the general population are warranted. To ascertain more definitive characteristics about the victims and perpetrators of cyberstalking, future studies will need to include male participants and a more diverse population. Additionally, the age of victims and perpetrators of cyberstalking and their relationships are areas of inquiry that require further exploration. In the current study, younger students were more likely to begin using the Internet at an earlier age indicating the discernible trend that cyberstalking will take in the future. Both perpetrators and victims as young as 10 years of age were reported by D Ovidio and Doyle (2003). Moreover, research by Finkelhor et al. (2000) further illustrates the trend that both the perpetrators and victims of cyberstalking may be increasing among our youth at an increased rate. Further research on this particular phenomenon needs to address the age of victims and perpetrators as well as the relationship between the two. Those who were cyberstalked were significantly more likely to have had this done by a former intimate partner and were less likely to have been stalked by a stranger when compared with the others who were stalked. Victims of cyberstalking were also more likely to have received threats and to have personal items taken. In addition, the close physical proximity of the perpetrators to the victims reported by Finkelhor et al. (2000) suggests that the threat of violence offline in the real world has increased. Brewster (2000) found that threats of violence were significantly correlated with actual physical violence in a group of females that were stalked by former intimates. Overall, a finite amount of literature exists that focuses on the relationships between former intimate partners, threats, and violence. 286 Brief Treatment and Crisis Intervention / 5:3 August 2005
9 Cyberstalking Among College Students The role these dynamics play in cyberstalking requires additional attention. The perpetrators of cyberstalking were significantly more likely to threaten to kill themselves than the perpetrators of stalking. This suggests that the electronic medium may allow the cyberstalking perpetrator to express more dramatic or histrionic behavior. Furthermore, those who were cyberstalked were significantly more likely not to report the experience to law enforcement agencies because they thought that the situation would stop. Additional research of cyberstalking is needed to discover and understand the coping and reporting mechanisms employed by victims. Perhaps the most unexpected finding derived from the data was the fact that although females were significantly more likely to be stalked than men, men were significantly more likely to be cyberstalked than women. According to Finkelhor et al. (2000), 51% of the victims of online harassment were male; however, D Ovidio and Doyle (2003) reported a male victim population of only 35%. Traditionally, stalking studies have focused on female participants. The ever-changing emergence of communication technologies coupled with the evolution of stalking behaviors requires the inclusion of more male participants to understand the victims and perpetrators of cyberstalking as well as its nature. Implications for Mental Health Professionals In responding to victims of cyberstalking, particularly given the overarching typology of uncertainty, mental health professionals can offer principal strategies of intervention, including initial reassurance and debriefing, environmental assessment, education, referral, and family- and community-level partnership for positive and proactive change. Initial reassurance and debriefing comprise the first-line response to the disclosure of cyberstalking. It is essential to define and clarify what the experience of cyberstalking means to the individual. Is it a loss of safety? Is it a loss of control? Is it a sense of uncertainty? Is it a loss of trust? The answers to these questions, emanating from the individual, will guide the interventions. Environmental assessment, education, and referral follow the initial response to the disclosure. Appropriate risk assessments of individuals, families, homes, schools, and workplaces should be conducted. These risk assessments are critical to establish a baseline of understanding at the time the event is disclosed. Key questions to be asked during such assessments should include the following: What are the current and past experiences as told by the victim? What are the specific exposures to communications that might be considered cyberstalking or harassment? What is the relationship between these unsolicited and unwanted communications (at home, school, and workplace) and the subsequent intrapsychic or affective disruption? Finally, the mental health professional should help the victim to identify family- and community-level partnerships for the purpose of creating positive change. Although initial reassurance and environmental assessment are likely to occur immediately after the event, community partnership for change is a longterm solution. Mental health professionals can advocate on behalf of the affected persons who may lack the knowledge or social power to adaptively cope with the aftermath of cyberstalking. This includes identification of family members or other community-based support systems (employee assistance programs, human resources personnel, university/college counselors, etc.) to increase a sense of safety while also decreasing a sense of isolation. Brief Treatment and Crisis Intervention / 5:3 August
10 ALEXY ET AL. In general, it is critical for mental health professionals to be aware that victims often experience a heightened sense of fear that may overshadow every other emotion they are able to verbalize. Fear, as an intense emotion, especially in the immediate aftermath of acts of intrusion such as cyberstalking, is a normal reaction. In some instances, fear may last for months or even years, particularly if a pervasive fear of reoccurrence develops. When victims express fear, it is essential not to dismiss the emotion or refer to it as irrational or unnecessary. Mental health professionals can help victims to understand that fear can sometimes be a protective device that should never be denied. Rather, fear, properly identified and accepted, can promote safety and encourage an individual to proactively increase safety precautions. These data suggest that victims do not report incidents of stalking and cyberstalking to authorities. Often, victims do not think the behavior is a criminal offense or that school authorities or law enforcement officers will take them seriously (Ashcroft, 2001; Fisher et al., 2002; Reno, 1999). Victim advocates need to take a proactive role in identifying and instituting services for victims of online and offline stalking. Supportive services are essential for victims of online and offline stalking to maintain self-esteem. Educational services are needed for victims to navigate the Web sites of administrative and judicial systems. Finally, through supportive, educational, and psychotherapeutic measures victims will become empowered and enabled to recapture the control lost at the hands of their perpetrators. Conclusion The fact that little empirical research exists specifically addressing the phenomenon of cyberstalking is not surprising given the relatively recent adoption of antistalking statutes and widespread use of the Internet. In this article, we focuses on this phenomenon in a collegiate community. It examines responses to a scenario on cyberstalking to see how the students classify negative behavior on the Internet and how they feel about it; it presents the students experiences with the Internet; and finally it focuses on a subset of the sample victims who had been cyberstalked. Reno (1999, 75) recommended that law enforcement and mental health providers name the behavior as cyberstalking and validate that a crime is occurring when working with individual victims. Presently, not all states include specific guidelines to address stalking on the Internet in their antistalking statutes. This is an area in need of further investigation. References Ashcroft, J. (2001). Stalking and domestic violence: A report to Congress (No. NCJ ). Washington, DC: U.S. Department of Justice. Brewster, M. P. (2000). Stalking by former intimates: Verbal threats and other predictors of physical violence. Violence and Victims, 15, Burgess, A. W., & Roberts, A. R. (2000). Crisis intervention for persons diagnosed with clinical disorders based on the stress-crisis continuum. In A. R. Roberts (Ed.), Crisis intervention handbook: Assessment, treatment, and research (2nd ed., pp ). New York: Oxford University Press. D Ovidio, R., & Doyle, J. (2003). A study on cyberstalking: Understanding investigative hurdles. FBI Law Enforcement Bulletin, 72(3), Draucker, C. B. (1999). Living in hell: The experience of being stalked. Issues in Mental Health Nursing, 20, Finkelhor, D., Mitchell, K. J., & Wolak, J. (2000). Online victimization: A report on the nation s 288 Brief Treatment and Crisis Intervention / 5:3 August 2005
11 Cyberstalking Among College Students youth. Retrieved June 8, 2000, from Fisher, B. S., Cullen, F. T., & Turner, M. G. (2000). The sexual victimization of college women (No. NCJ ). Washington, DC: U.S. Department of Justice, Office of Justice Programs. Fisher, B. S., Cullen, F. T., & Turner, M. G. (2002). Being pursued: Stalking victimization in a national study of college women. Criminology & Public Policy, 1, Lee, R. K. (1998). Romantic and electronic stalking in a college context. William & Mary Journal of Women and the Law, 4, Miller, G., & Maharaj, D. (1999, January 22). N. Hollywood man charged in 1st cyber-stalking case; Internet: Spurned suitor allegedly forged lurid s, inviting would-be rapists to woman s home. Los Angeles Times. Retrieved June 23, 2005, from Pathé, M., & Mullen, P. E. (1997). The impact of stalkers on their victims. British Journal of Psychiatry, 170, Reno, J. (1999). Cyberstalking: A new challenge for law enforcement and industry: A report from the Attorney General to the Vice President, August, Retrieved February 13, 2000, from cybercrime/cyberstalking.htm Spitzberg, B. H., & Hoobler, G. (2002). Cyberstalking and the technologies of interpersonal terrorism. New Media & Society, 4, Tjaden, P., & Thoennes, N. (1998). Stalking in America: Findings from the National Violence Against Women Survey (No. NCJ ). Washington, DC: National Institute of Justice, Office of Justice Programs, U.S. Department of Justice, and the Centers for Disease Control and Prevention. Tjaden, P., Thoennes, N., & Allison, C. J. (2000). Comparing stalking victimization from legal and victim perspectives. Violence and Victims, 15, Westrup, D., Fremouw, W. J., Thompson, R. N., & Lewis, S. F. (1999). The psychological impact of stalking on female undergraduates. Journal of Forensic Science, 44, Brief Treatment and Crisis Intervention / 5:3 August
Stalking 101: Understanding the lethality of stalking in today s world
 Stalking 101: Understanding the lethality of stalking in today s world Objectives Participants will be able to recognize the dynamics of stalking and the its impact on victims Participants will understand
Stalking 101: Understanding the lethality of stalking in today s world Objectives Participants will be able to recognize the dynamics of stalking and the its impact on victims Participants will understand
Online Harassment and Victimization of College Students
 Online Harassment and Victimization of College Students M. Alexis Kennedy and Melanie A. Taylor* Volume 7 No. 1 Spring 2010 *M. Alexis Kennedy is an Assistant Professor in the Department of Criminal Justice
Online Harassment and Victimization of College Students M. Alexis Kennedy and Melanie A. Taylor* Volume 7 No. 1 Spring 2010 *M. Alexis Kennedy is an Assistant Professor in the Department of Criminal Justice
STALKING REALITIES AND RESPONSES
 State of New York h Office of the Attorney General STALKING REALITIES AND RESPONSES IF YOU BELIEVE YOU ARE IN IMMEDIATE DANGER, CALL 911 FOR EMERGENCY ASSISTANCE. IF YOU ARE IN AN ABUSIVE SITUATION, DO
State of New York h Office of the Attorney General STALKING REALITIES AND RESPONSES IF YOU BELIEVE YOU ARE IN IMMEDIATE DANGER, CALL 911 FOR EMERGENCY ASSISTANCE. IF YOU ARE IN AN ABUSIVE SITUATION, DO
Domestic Violence: Can the Legal System Help Protect Me?
 Domestic Violence: Can the Legal System Help Protect Me? What is domestic violence? Domestic violence is a pattern of physically and/or emotionally abusive behavior used to control another person with
Domestic Violence: Can the Legal System Help Protect Me? What is domestic violence? Domestic violence is a pattern of physically and/or emotionally abusive behavior used to control another person with
BERKELEY COLLEGE Equal Opportunity Policy
 BERKELEY COLLEGE Equal Opportunity Policy Purpose Recognizing that its diversity greatly enhances the workplace and opportunities for learning, Berkeley is firmly committed to providing all associates,
BERKELEY COLLEGE Equal Opportunity Policy Purpose Recognizing that its diversity greatly enhances the workplace and opportunities for learning, Berkeley is firmly committed to providing all associates,
CYBERSTALKING: AN EXPLORATORY STUDY OF LAW ENFORCEMENT IN ALLEGHENY COUNTY, PENNSYLVANIA
 CYBERSTALKING: AN EXPLORATORY STUDY OF LAW ENFORCEMENT IN ALLEGHENY COUNTY, PENNSYLVANIA Karen L. Paullet, Robert Morris University, paullet@rmu.edu Daniel R. Rota, Robert Morris University, rota@rmu.edu
CYBERSTALKING: AN EXPLORATORY STUDY OF LAW ENFORCEMENT IN ALLEGHENY COUNTY, PENNSYLVANIA Karen L. Paullet, Robert Morris University, paullet@rmu.edu Daniel R. Rota, Robert Morris University, rota@rmu.edu
Violence against women: key statistics
 Violence against women: key statistics Research from the 2012 ABS Personal Safety Survey and Australian Institute of Criminology shows that both men and women in Australia experience substantial levels
Violence against women: key statistics Research from the 2012 ABS Personal Safety Survey and Australian Institute of Criminology shows that both men and women in Australia experience substantial levels
Intimate Partner Violence and Firearms
 Intimate Partner Violence and Firearms According to the Centers for Disease Control and Prevention (CDC), intimate partner violence (IPV) is actual or threatened physical or sexual violence or psychological
Intimate Partner Violence and Firearms According to the Centers for Disease Control and Prevention (CDC), intimate partner violence (IPV) is actual or threatened physical or sexual violence or psychological
Cyberstalking: Dangers on the Information Superhighway By: Trudy M. Gregorie, Director of Training National Center for Victims of Crime, 2001
 Cyberstalking: Dangers on the Information Superhighway By: Trudy M. Gregorie, Director of Training National Center for Victims of Crime, 2001 Although there is no universally accepted definition of cyberstalking,
Cyberstalking: Dangers on the Information Superhighway By: Trudy M. Gregorie, Director of Training National Center for Victims of Crime, 2001 Although there is no universally accepted definition of cyberstalking,
Indiana Report. 2011 Action Plan Domestic Violence and Sexual Assault Services
 Indiana Report 2011 Action Plan Domestic Violence and Sexual Assault Services Introduction Every five years a committee of domestic and sexual violence victim service providers, coalitions, and vested
Indiana Report 2011 Action Plan Domestic Violence and Sexual Assault Services Introduction Every five years a committee of domestic and sexual violence victim service providers, coalitions, and vested
Table A. Characteristics of Respondents that completed the survey
 Table A. Characteristics of Respondents that completed the survey Characteristic Category Weighted Un- weighted Number % Number % Age 18 years old 4,111 8.8 700 8.4 19 years old 8,605 18.3 1,421 17.0 20
Table A. Characteristics of Respondents that completed the survey Characteristic Category Weighted Un- weighted Number % Number % Age 18 years old 4,111 8.8 700 8.4 19 years old 8,605 18.3 1,421 17.0 20
INTIMATE PARTNER VIOLENCE
 INTIMATE PARTNER VIOLENCE 28 Injury Prevention Plan of Alabama INTIMATE PARTNER VIOLENCE THE PROBLEM: In a national survey, 25% of female participants reported being raped or physically assaulted by an
INTIMATE PARTNER VIOLENCE 28 Injury Prevention Plan of Alabama INTIMATE PARTNER VIOLENCE THE PROBLEM: In a national survey, 25% of female participants reported being raped or physically assaulted by an
SOUTH DAKOTA BOARD OF REGENTS. Policy Manual
 Prevention of Sexual Assault, Domestic Violence, and Stalking Page 1 of 5 SOUTH DAKOTA BOARD OF REGENTS Policy Manual SUBJECT: Prevention of, Dating Violence, Domestic Violence Sexual Assault and Stalking
Prevention of Sexual Assault, Domestic Violence, and Stalking Page 1 of 5 SOUTH DAKOTA BOARD OF REGENTS Policy Manual SUBJECT: Prevention of, Dating Violence, Domestic Violence Sexual Assault and Stalking
STALKING and VIOLENCE
 U.S. Department of Justice Office of Justice Programs Violence Against Women Office STALKING and DOMESTIC VIOLENCE Report to Congress U.S. Department of Justice Office of Justice Programs 810 Seventh Street
U.S. Department of Justice Office of Justice Programs Violence Against Women Office STALKING and DOMESTIC VIOLENCE Report to Congress U.S. Department of Justice Office of Justice Programs 810 Seventh Street
SOUTH DAKOTA STATE UNIVERSITY Policy and Procedure Manual
 Office/Contact: Office of Human Resources Source: SDBOR Policy 1:17.1 and 1:18 Link: http://www.sdbor.edu/policy/1-governance/documents/1-17-1.pdf http://www.sdbor.edu/policy/1-governance/documents/1-18.pdf
Office/Contact: Office of Human Resources Source: SDBOR Policy 1:17.1 and 1:18 Link: http://www.sdbor.edu/policy/1-governance/documents/1-17-1.pdf http://www.sdbor.edu/policy/1-governance/documents/1-18.pdf
DOMESTIC VIOLENCE IN FLORIDA
 DOMESTIC VIOLENCE IN FLORIDA The Petitioner may go to court on his/her own (without an attorney) to petition for an injunction to protect him/her against domestic violence (assault or battery by your spouse
DOMESTIC VIOLENCE IN FLORIDA The Petitioner may go to court on his/her own (without an attorney) to petition for an injunction to protect him/her against domestic violence (assault or battery by your spouse
What is Domestic Violence?
 Reentry in the State of Connecticut: Partners in Progress February 24-26, 2009 Rachelle Giguere and Becki Ney What is Domestic Violence? The Centers for Disease Control (CDC) defines intimate partner violence
Reentry in the State of Connecticut: Partners in Progress February 24-26, 2009 Rachelle Giguere and Becki Ney What is Domestic Violence? The Centers for Disease Control (CDC) defines intimate partner violence
Abuse in Same-Sex Relationships
 1 Abuse in Same-Sex Relationships Abuse in relationships is any behavior or pattern of behavior used to coerce, dominate or isolate the other partner. It is the use of any form of power that is imposed
1 Abuse in Same-Sex Relationships Abuse in relationships is any behavior or pattern of behavior used to coerce, dominate or isolate the other partner. It is the use of any form of power that is imposed
What is DOMESTIC VIOLENCE?
 What is DOMESTIC VIOLENCE? Domestic violence is a pattern of control used by one person to exert power over another. Verbal abuse, threats, physical, and sexual abuse are the methods used to maintain power
What is DOMESTIC VIOLENCE? Domestic violence is a pattern of control used by one person to exert power over another. Verbal abuse, threats, physical, and sexual abuse are the methods used to maintain power
SEXUAL ASSAULT POLICY
 SEXUAL ASSAULT POLICY California State University, Stanislaus is strongly committed to the establishment of an educational environment in which students, faculty, and staff can work together in an atmosphere
SEXUAL ASSAULT POLICY California State University, Stanislaus is strongly committed to the establishment of an educational environment in which students, faculty, and staff can work together in an atmosphere
In 2014, U.S. residents age 12 or older experienced
 U.S. Department of Justice Office of Justice Programs Bureau of Justice Statistics Revised September 29, 2015 Criminal Victimization, 2014 Jennifer L. Truman, Ph.D., and Lynn Langton, Ph.D., BJS Statisticians
U.S. Department of Justice Office of Justice Programs Bureau of Justice Statistics Revised September 29, 2015 Criminal Victimization, 2014 Jennifer L. Truman, Ph.D., and Lynn Langton, Ph.D., BJS Statisticians
Policy on Sexual Assault, Stalking, Dating Violence, and Domestic Violence
 Administrative Regulation 6:2 Responsible Office: Title IX Coordinator / VP Student Affairs Date Effective: 12/3/2014 Supersedes Version: 9/30/2014 (Interim) Policy on Sexual Assault, Stalking, Dating
Administrative Regulation 6:2 Responsible Office: Title IX Coordinator / VP Student Affairs Date Effective: 12/3/2014 Supersedes Version: 9/30/2014 (Interim) Policy on Sexual Assault, Stalking, Dating
Trends in Arrests for Child Pornography Possession: The Third National Juvenile Online Victimization Study (NJOV 3)
 April 2012 Trends in Arrests for Child Pornography Possession: The Third National Juvenile Online Victimization Study (NJOV 3) Abstract Arrests for the possession of child pornography (CP) increased between
April 2012 Trends in Arrests for Child Pornography Possession: The Third National Juvenile Online Victimization Study (NJOV 3) Abstract Arrests for the possession of child pornography (CP) increased between
PATHWAYS TO JUSTICE: Introduction. The Movement of Adult Female Sexual Assault Cases Across the New Hampshire Criminal Justice System
 The Movement of Adult Female Sexual Assault Cases Across the New Hampshire Criminal Justice System PRIOR RESEARCH IN NH: Introduction The movement of adult female sexual assault cases across the justice
The Movement of Adult Female Sexual Assault Cases Across the New Hampshire Criminal Justice System PRIOR RESEARCH IN NH: Introduction The movement of adult female sexual assault cases across the justice
CHILDHOOD SEXUAL ABUSE FACT SHEET
 CHILDHOOD SEXUAL ABUSE FACT SHEET Emily M. Douglas and David Finkelhor PART 1: HOW MANY CHILDREN ARE THE VICTIMS OF CHILD SEXUAL ABUSE? There are many estimates of the number of children who are the victims
CHILDHOOD SEXUAL ABUSE FACT SHEET Emily M. Douglas and David Finkelhor PART 1: HOW MANY CHILDREN ARE THE VICTIMS OF CHILD SEXUAL ABUSE? There are many estimates of the number of children who are the victims
UNIVERSITY OF CALIFORNIA, MERCED POLICY REGARDING WORKPLACE VIOLENCE, BIAS INCIDENTS, HATE CRIMES AND DISRUPTIVE BEHAVIORS POLICY NUMBER: 757
 UNIVERSITY OF CALIFORNIA, MERCED POLICY REGARDING WORKPLACE VIOLENCE, BIAS INCIDENTS, HATE CRIMES AND DISRUPTIVE BEHAVIORS POLICY NUMBER: 757 RESPONSIBLE OFFICIAL: Vice Chancellor Administration EFFECTIVE
UNIVERSITY OF CALIFORNIA, MERCED POLICY REGARDING WORKPLACE VIOLENCE, BIAS INCIDENTS, HATE CRIMES AND DISRUPTIVE BEHAVIORS POLICY NUMBER: 757 RESPONSIBLE OFFICIAL: Vice Chancellor Administration EFFECTIVE
California State University, Northridge Campus Plan to Address Sexual Assault
 California State University, Northridge Campus Plan to Address Sexual Assault PREPARED BY CHIEF ANNE P. GLAVIN, CHAIR on behalf of THE CSUN SEXUAL ASSAULT COMMITTEE JUNE, 2009 2 California State University,
California State University, Northridge Campus Plan to Address Sexual Assault PREPARED BY CHIEF ANNE P. GLAVIN, CHAIR on behalf of THE CSUN SEXUAL ASSAULT COMMITTEE JUNE, 2009 2 California State University,
Understanding Nebraska's Protection Orders
 Understanding Nebraska's Protection Orders A guide for victims, law enforcement and service providers. What is a Protection Order? A protection order is a special type of order issued by a Judge which
Understanding Nebraska's Protection Orders A guide for victims, law enforcement and service providers. What is a Protection Order? A protection order is a special type of order issued by a Judge which
CAMPUS SECURITY INFORMATION ANNUAL CAMPUS SECURITY REPORT-TULSA
 CAMPUS SECURITY INFORMATION ANNUAL CAMPUS SECURITY REPORT-TULSA The following statistics are provided as part of the requirement under the Student Right- To Know and Campus Security Act, Public Law 101-542,
CAMPUS SECURITY INFORMATION ANNUAL CAMPUS SECURITY REPORT-TULSA The following statistics are provided as part of the requirement under the Student Right- To Know and Campus Security Act, Public Law 101-542,
Domestic Assaults by Juvenile Offenders
 U.S. Department of Justice Office of Justice Programs Office of Juvenile Justice and Delinquency Prevention J. Robert Flores, Administrator November 2008 Office of Justice Programs Innovation Partnerships
U.S. Department of Justice Office of Justice Programs Office of Juvenile Justice and Delinquency Prevention J. Robert Flores, Administrator November 2008 Office of Justice Programs Innovation Partnerships
University of Illinois at Chicago Student Sexual Misconduct and Sexual Violence Interim Policy
 University of Illinois at Chicago Student Sexual Misconduct and Sexual Violence Interim Policy Introduction The University of Illinois at Chicago is committed to creating a safe and secure community for
University of Illinois at Chicago Student Sexual Misconduct and Sexual Violence Interim Policy Introduction The University of Illinois at Chicago is committed to creating a safe and secure community for
Table A. Characteristics of Respondents that completed the survey
 Table A. Characteristics of Respondents that completed the survey Characteristic Category Weighted Un-weighted Number % Number % Age 18 years old 759 3.0 228 3.4 19 years old 1,462 5.7 400 6.0 20 years
Table A. Characteristics of Respondents that completed the survey Characteristic Category Weighted Un-weighted Number % Number % Age 18 years old 759 3.0 228 3.4 19 years old 1,462 5.7 400 6.0 20 years
Adolescent Sexual Offenders
 Adolescent Sexual Offenders Information from... The National Clearinghouse on Family Violence Who Are Adolescent Sexual Offenders? The adolescent sexual offender is defined as a youth, from 12 to 17 years
Adolescent Sexual Offenders Information from... The National Clearinghouse on Family Violence Who Are Adolescent Sexual Offenders? The adolescent sexual offender is defined as a youth, from 12 to 17 years
SEXUAL ASSAULT. REPORTING A SEXUAL ASSAULT If you are a victim of sexual assault:
 SEXUAL ASSAULT SEXUAL ASSAULT SEXUAL ASSAULT AND HARASSMENT Pratt Institute s mission is to educate men and women to become creative, responsible professionals who will contribute fully to society. The
SEXUAL ASSAULT SEXUAL ASSAULT SEXUAL ASSAULT AND HARASSMENT Pratt Institute s mission is to educate men and women to become creative, responsible professionals who will contribute fully to society. The
Sexual Assault Prevalence in Texas 1
 Sexual Assault Prevalence in Texas 1 Extent of the Problem Gender & Age 6.3 million Texans have experienced some form of sexual assault in their lifetime. 4.2 million adult women 2.1 million adult men
Sexual Assault Prevalence in Texas 1 Extent of the Problem Gender & Age 6.3 million Texans have experienced some form of sexual assault in their lifetime. 4.2 million adult women 2.1 million adult men
INSIGHT REPORT Winter 2015. Sexual Victimization and Social Norms on the College Campus
 INSIGHT REPORT Winter 2015 Sexual Victimization and Social Norms on the College Campus Sexual Victimization and Social Norms on the College Campus SUMMARY OF RESEARCH WINTER 2015 At the start of the 2014-2015
INSIGHT REPORT Winter 2015 Sexual Victimization and Social Norms on the College Campus Sexual Victimization and Social Norms on the College Campus SUMMARY OF RESEARCH WINTER 2015 At the start of the 2014-2015
I N F O R M A T I O N B U L L E T I N. Considerations for Sexual Assault Coordination
 I N F O R M A T I O N B U L L E T I N Considerations for Sexual Assault Coordination This information bulletin is based on the information available at April 4, 2002. In addition to the sources cited,
I N F O R M A T I O N B U L L E T I N Considerations for Sexual Assault Coordination This information bulletin is based on the information available at April 4, 2002. In addition to the sources cited,
Domestic Violence Case Management Plan
 Domestic Violence Case Management Plan From the commencement of litigation to its resolution, whether by trial or settlement, it is the goal of this Court to reduce delay and enable just and efficient
Domestic Violence Case Management Plan From the commencement of litigation to its resolution, whether by trial or settlement, it is the goal of this Court to reduce delay and enable just and efficient
School of Social Work University of Missouri Columbia
 Summary Report On Participant Characteristics at Entry Into the Missouri Drug Court Programs Included in the Multi-jurisdictional Enhancement for Evaluation of Drug Courts School of Social Work University
Summary Report On Participant Characteristics at Entry Into the Missouri Drug Court Programs Included in the Multi-jurisdictional Enhancement for Evaluation of Drug Courts School of Social Work University
The Nuts & Bolts of Orders of Protection and other relief for Victims of Domestic Violence
 The Nuts & Bolts of Orders of Protection and other relief for Victims of Domestic Violence Training for Victim Advocates Sponsored by South Carolina Legal Services Orders of Protection: The Basics What?
The Nuts & Bolts of Orders of Protection and other relief for Victims of Domestic Violence Training for Victim Advocates Sponsored by South Carolina Legal Services Orders of Protection: The Basics What?
National Statistics. Domestic Violence/Sexual Assault Fact Sheet: Oklahoma Department of Mental Health and Substance Abuse Services
 National Statistics Domestic Violence/Sexual Assault Fact Sheet: Oklahoma Department of Mental Health and Substance Abuse Services The National Domestic Violence Hotline has received more than 700,000
National Statistics Domestic Violence/Sexual Assault Fact Sheet: Oklahoma Department of Mental Health and Substance Abuse Services The National Domestic Violence Hotline has received more than 700,000
Domestic Violence Law Reform The Victim s Voice Survey: Victim s Experience of Domestic Violence and the Criminal Justice System
 Domestic Violence Law Reform The Victim s Voice Survey: Victim s Experience of Domestic Violence and the Criminal Justice System FOREWORD We would like to thank all those who took the time to share their
Domestic Violence Law Reform The Victim s Voice Survey: Victim s Experience of Domestic Violence and the Criminal Justice System FOREWORD We would like to thank all those who took the time to share their
4 Criminal and Family Law
 4 Criminal and Family Law ENG 004/2010 FAMILY LAW FOR WOMEN IN ONTARIO All Women. One Family Law. Know your Rights. Criminal and Family Law This booklet is meant to give you a basic understanding of legal
4 Criminal and Family Law ENG 004/2010 FAMILY LAW FOR WOMEN IN ONTARIO All Women. One Family Law. Know your Rights. Criminal and Family Law This booklet is meant to give you a basic understanding of legal
FROM CHARGE TO TRIAL: A GUIDE TO CRIMINAL PROCEEDINGS
 FROM CHARGE TO TRIAL: A GUIDE TO CRIMINAL PROCEEDINGS If you are experiencing, or have experienced, domestic violence and/or sexual violence there are a number of ways the law can protect you. This includes
FROM CHARGE TO TRIAL: A GUIDE TO CRIMINAL PROCEEDINGS If you are experiencing, or have experienced, domestic violence and/or sexual violence there are a number of ways the law can protect you. This includes
Results. Contact sexual crimes based on PSI and self-report after SOTP participation
 Self-Reported Contact Sexual Offenses by Participants in the Federal Bureau of Prisons Sex Offender Treatment Program: Implications for Internet Sex Offenders Andres E. Hernandez, Psy.D. Director, Sex
Self-Reported Contact Sexual Offenses by Participants in the Federal Bureau of Prisons Sex Offender Treatment Program: Implications for Internet Sex Offenders Andres E. Hernandez, Psy.D. Director, Sex
National Institute of Justice. Centers for Disease Control and Prevention
 U.S. Department of Justice Office of Justice Programs National Institute of Justice National Institute of Justice Centers for Disease Control and Prevention R e s e a r c h i n B r i e f April 1998 Stalking
U.S. Department of Justice Office of Justice Programs National Institute of Justice National Institute of Justice Centers for Disease Control and Prevention R e s e a r c h i n B r i e f April 1998 Stalking
Advocates and Officers: Working Together to Address Campus Sexual Violence. www.umn.edu/aurora www.umn.edu/police 612.626.9111 612.624.
 Advocates and Officers: Working Together to Address Campus Sexual Violence www.umn.edu/aurora www.umn.edu/police 612.626.9111 612.624.2677 Introductions Kevin Randolph: Investigator, University of Minnesota
Advocates and Officers: Working Together to Address Campus Sexual Violence www.umn.edu/aurora www.umn.edu/police 612.626.9111 612.624.2677 Introductions Kevin Randolph: Investigator, University of Minnesota
Internet Safety Fact Sheet Facts about Social Networking:
 Internet Safety Fact Sheet Facts about Social Networking: 96% of students ages 9 to 17 who have access to the Internet have used social networking technologies (Grunwald Associates, "Creating & Connecting
Internet Safety Fact Sheet Facts about Social Networking: 96% of students ages 9 to 17 who have access to the Internet have used social networking technologies (Grunwald Associates, "Creating & Connecting
This report provides the executive summary for Indicators of School Crime and Safety: 2014.
 1 Liability Report Number: LB-10-66 Release Date: August 6, 2015 Section Title: General Information Abstract School violence not only has a direct impact on students, but also on educators, parents, and
1 Liability Report Number: LB-10-66 Release Date: August 6, 2015 Section Title: General Information Abstract School violence not only has a direct impact on students, but also on educators, parents, and
Spring 2015 Sexual Harassment Survey Results
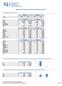 Spring 2015 Sexual Harassment Survey Results Response Rates by Demographic Variable Overall 23048 1724 7.48% Gender Male 11530 50.03% 620 35.96% Female 11517 49.97% 1039 60.27% t Specified 1 0.0 0 0.0
Spring 2015 Sexual Harassment Survey Results Response Rates by Demographic Variable Overall 23048 1724 7.48% Gender Male 11530 50.03% 620 35.96% Female 11517 49.97% 1039 60.27% t Specified 1 0.0 0 0.0
Sexual Assault & Domestic Violence: Common Goals, Distinct Differences (Winter 2006) Last Updated Wednesday, August 26, 2009 at 04:01 pm
 The work of the anti-sexual assault and domestic violence movements is clearly interconnected. The pervasive problems of sexual assault and domestic violence are firmly embedded in our society, allowing
The work of the anti-sexual assault and domestic violence movements is clearly interconnected. The pervasive problems of sexual assault and domestic violence are firmly embedded in our society, allowing
Are you living in fear? Is someone stalking you? STALKING is a crime in Minnesota! From the Office of Lori Swanson MINNESOTA ATTORNEY GENERAL
 Are you living in fear? Is someone stalking you? STALKING is a crime in Minnesota! From the Office of Lori Swanson MINNESOTA ATTORNEY GENERAL WHAT IS STALKING? Stalking is intentionally following or harassing
Are you living in fear? Is someone stalking you? STALKING is a crime in Minnesota! From the Office of Lori Swanson MINNESOTA ATTORNEY GENERAL WHAT IS STALKING? Stalking is intentionally following or harassing
In 2013, U.S. residents age 12 or older experienced
 U.S. Department of Justice Office of Justice Programs Bureau of Justice Statistics Revised 9/19/2014 Criminal Victimization, 2013 Jennifer L. Truman, Ph.D., and Lynn Langton, Ph.D., BJS Statisticians In
U.S. Department of Justice Office of Justice Programs Bureau of Justice Statistics Revised 9/19/2014 Criminal Victimization, 2013 Jennifer L. Truman, Ph.D., and Lynn Langton, Ph.D., BJS Statisticians In
Idaho. Coalition Against Sexual & Domestic Violence Engaging Voices, Creating Change. Table of Contents
 stalking Most victims are stalked by someone they know. Stalking is serious, often violent, and can escalate over time. This handbook provides information on stalking and available resources. Idaho Coalition
stalking Most victims are stalked by someone they know. Stalking is serious, often violent, and can escalate over time. This handbook provides information on stalking and available resources. Idaho Coalition
Intersection of Title IX and the Clery Act. What types of incidents must be reported to school officials under Title IX and the Clery Act?
 Intersection of Title IX and the Clery Act The purpose of this chart is to clarify the reporting requirements of Title IX and the Clery Act in cases of sexual violence and to resolve any concerns about
Intersection of Title IX and the Clery Act The purpose of this chart is to clarify the reporting requirements of Title IX and the Clery Act in cases of sexual violence and to resolve any concerns about
State University of New York College at Old Westbury. Domestic Violence and the Workplace Policy
 State University of New York College at Old Westbury Domestic Violence and the Workplace Policy Policy Statement The persons covered by this policy are: employees of SUNY College at Old Westbury (the College
State University of New York College at Old Westbury Domestic Violence and the Workplace Policy Policy Statement The persons covered by this policy are: employees of SUNY College at Old Westbury (the College
There is help. Take action. Sexual Violence Survival Guide. Options available to victims of sexual assault crimes.
 There is help. Take action. Sexual Violence Survival Guide Options available to victims of sexual assault crimes. You are not alone. Help is available. Call 1-888-956-7273 (RAPE) or go to www.fcasv.org
There is help. Take action. Sexual Violence Survival Guide Options available to victims of sexual assault crimes. You are not alone. Help is available. Call 1-888-956-7273 (RAPE) or go to www.fcasv.org
How to Protect Students from Sexual Harassment: A Primer for Schools
 How to Protect Students from Sexual Harassment: A Primer for Schools This fact sheet is part of a series of tools designed by the National Women s Law Center to help schools address the dropout crisis.
How to Protect Students from Sexual Harassment: A Primer for Schools This fact sheet is part of a series of tools designed by the National Women s Law Center to help schools address the dropout crisis.
Know Your Rights NEW YORK STATE: WELFARE TO-WORK
 Know Your Rights NEW YORK STATE: WELFARE TO-WORK 395 Hudson Street New York, NY 10014-3684 t: 212.925.6635 f: 212.226.1066 www.legalmomentum.org Under federal welfare law, New York State receives a block
Know Your Rights NEW YORK STATE: WELFARE TO-WORK 395 Hudson Street New York, NY 10014-3684 t: 212.925.6635 f: 212.226.1066 www.legalmomentum.org Under federal welfare law, New York State receives a block
Landlords Prey on Poor Women by Extorting Sexual Favors in Lieu of Rent
 March 9, 2007 Landlords Prey on Poor Women by Extorting Sexual Favors in Lieu of Rent By Russell Goldman March 8, 2007 For four years Mary lived in fear of her landlord, describing herself as a prisoner
March 9, 2007 Landlords Prey on Poor Women by Extorting Sexual Favors in Lieu of Rent By Russell Goldman March 8, 2007 For four years Mary lived in fear of her landlord, describing herself as a prisoner
The Second Responders Program: A Coordinated Police and Social Service Response to Domestic Violence
 The Second Responders Program: A Coordinated Police and Social Service Response to Domestic Violence By Erin Lane, Rosann Greenspan, and David Weisburd 2004 NCJ 199717 Erin Lane, M.P.H., is with the Police
The Second Responders Program: A Coordinated Police and Social Service Response to Domestic Violence By Erin Lane, Rosann Greenspan, and David Weisburd 2004 NCJ 199717 Erin Lane, M.P.H., is with the Police
Abuse of elderly victims age 65 or older can take
 U.S. Department of Justice Office of Justice Programs Bureau of Justice Statistics Special Report JUNE 2012, NCJ 238546 National Incident-Based Reporting System Violent Crime against the Elderly Reported
U.S. Department of Justice Office of Justice Programs Bureau of Justice Statistics Special Report JUNE 2012, NCJ 238546 National Incident-Based Reporting System Violent Crime against the Elderly Reported
REPORTING AN OFFENCE TO THE POLICE: A GUIDE TO CRIMINAL INVESTIGATIONS
 REPORTING AN OFFENCE TO THE POLICE: A GUIDE TO CRIMINAL INVESTIGATIONS If you are experiencing or have experienced domestic volence and/or sexual violence there are a number of ways the law can protect
REPORTING AN OFFENCE TO THE POLICE: A GUIDE TO CRIMINAL INVESTIGATIONS If you are experiencing or have experienced domestic volence and/or sexual violence there are a number of ways the law can protect
How To Protect Women From Domestic Violence
 U.S. Department of Justice Executive Office for United States Attorneys Office of the Director RFK Main Justice Building, Room 2263 950 Pennsylvania Avenue, NW Washington, DC 20530 (202) 252-1000 MEMORANDUM-
U.S. Department of Justice Executive Office for United States Attorneys Office of the Director RFK Main Justice Building, Room 2263 950 Pennsylvania Avenue, NW Washington, DC 20530 (202) 252-1000 MEMORANDUM-
SEXUAL PREDATORS ON MYSPACE:
 SEXUAL PREDATORS ON MYSPACE: A DEEPER LOOK AT TEENS BEING STALKED OR APPROACHED FOR SEXUAL LIAISONS Short Report 2006-01 Larry D. Rosen, Ph.D. California State University, Dominguez Hills July 2006 I recently
SEXUAL PREDATORS ON MYSPACE: A DEEPER LOOK AT TEENS BEING STALKED OR APPROACHED FOR SEXUAL LIAISONS Short Report 2006-01 Larry D. Rosen, Ph.D. California State University, Dominguez Hills July 2006 I recently
Comments made online may be misinterpreted by both receivers and third-parties, which may affect the determination of prevalence of cyberbullying.
 Chapter 7 summaries Cyberbullying definitions and prevalence Many definitions have been offered for cyberbullying. Several of these definitions explicitly or implicitly indicate that the bullying behaviour
Chapter 7 summaries Cyberbullying definitions and prevalence Many definitions have been offered for cyberbullying. Several of these definitions explicitly or implicitly indicate that the bullying behaviour
Capstone Project Minnesota State University Crime and Victimization Survey
 Capstone Project Minnesota State University Crime and Victimization Survey Sherrise Truesdale, PhD Department of Sociology and Corrections Minnesota State University April 28, 2005 1 Alan Hughes (2005)
Capstone Project Minnesota State University Crime and Victimization Survey Sherrise Truesdale, PhD Department of Sociology and Corrections Minnesota State University April 28, 2005 1 Alan Hughes (2005)
ONLINE PREDATORS & PREDATORS
 the myths and realities of ONLINE PREDATORS & PREDATORS Center For Child Advocacy Sixth Annual National Conference Crimes Against Children: The Multiple Faces of Child Victimization Joseph Hanley B.A.
the myths and realities of ONLINE PREDATORS & PREDATORS Center For Child Advocacy Sixth Annual National Conference Crimes Against Children: The Multiple Faces of Child Victimization Joseph Hanley B.A.
PREAMBLE TO GUIDELINES FOR MEDIATION IN CASES INVOLVING ISSUES OF DOMESTIC VIOLENCE
 PREAMBLE TO GUIDELINES FOR MEDIATION IN CASES INVOLVING ISSUES OF DOMESTIC VIOLENCE The Committee on Ethics of the Georgia Commission on Dispute Resolution studied the issue of mediation in cases involving
PREAMBLE TO GUIDELINES FOR MEDIATION IN CASES INVOLVING ISSUES OF DOMESTIC VIOLENCE The Committee on Ethics of the Georgia Commission on Dispute Resolution studied the issue of mediation in cases involving
*****THIS FORM IS NOT A PROTECTIVE ORDER APPLICATION OR A PROTECTIVE ORDER*****
 SHAREN WILSON CRIMINAL DISTRICT ATTORNEY OF TARRANT COUNTY, TEXAS PROTECTIVE ORDER UNIT Family Law Center Phone Number 817-884-1623 200 East Weatherford Street # 3040 Fax Number 817-212-7393 Fort Worth,
SHAREN WILSON CRIMINAL DISTRICT ATTORNEY OF TARRANT COUNTY, TEXAS PROTECTIVE ORDER UNIT Family Law Center Phone Number 817-884-1623 200 East Weatherford Street # 3040 Fax Number 817-212-7393 Fort Worth,
4 What is Sexual Assault? 5 Why Me? 6 Common Reactions Following an Assault. 7 What Next? 10 Civil Legal Remedies. 13 Idaho Crime Victims Rights Act
 sexual assault No one deserves to be sexually assaulted. Most victims are sexually assaulted by someone they know. This handbook provides information on sexual assault and available resources. This handbook
sexual assault No one deserves to be sexually assaulted. Most victims are sexually assaulted by someone they know. This handbook provides information on sexual assault and available resources. This handbook
Peace Bond Process. What is a Peace Bond? Contents
 Peace Bond Process October 2010 Contents Peace Bond Basics 2 The Process 3 Protecting Privacy 5 Joint Peace Bonds 9 The purpose of this brochure is to help guide you through the process of acquiring a
Peace Bond Process October 2010 Contents Peace Bond Basics 2 The Process 3 Protecting Privacy 5 Joint Peace Bonds 9 The purpose of this brochure is to help guide you through the process of acquiring a
SOCIAL WORK PRACTICE AND DOMESTIC VIOLENCE
 SOCIAL WORK PRACTICE AND DOMESTIC VIOLENCE Working with Children and Families Mary Kate Barry, IASW 2015 How are you? Grand Ask me In the hospital Please ask me In the clinic In the church Ask me, ask
SOCIAL WORK PRACTICE AND DOMESTIC VIOLENCE Working with Children and Families Mary Kate Barry, IASW 2015 How are you? Grand Ask me In the hospital Please ask me In the clinic In the church Ask me, ask
Violent Victimization of College Students, 1995-2002
 U.S. Department of Justice Office of Justice Programs Bureau of Justice Statistics Special Report National Crime Victimization Survey January 25, NCJ 26836 Violent Victimization of College Students, By
U.S. Department of Justice Office of Justice Programs Bureau of Justice Statistics Special Report National Crime Victimization Survey January 25, NCJ 26836 Violent Victimization of College Students, By
BULLYING/ANTI-HARASSMENT
 BULLYING/ANTI-HARASSMENT The state of Mississippi has established legislation requiring Bullying Prevention to be taught in schools. Executive Summary The purpose of this policy is to assist the Mississippi
BULLYING/ANTI-HARASSMENT The state of Mississippi has established legislation requiring Bullying Prevention to be taught in schools. Executive Summary The purpose of this policy is to assist the Mississippi
Guidelines for Setting up Security Measures to Stop Domestic Violence in the Workplace
 Guidelines for Setting up Security Measures to Stop Domestic Violence in the Workplace As of June 15, 2010, all employers in Ontario are responsible for protecting workers when domestic violence follows
Guidelines for Setting up Security Measures to Stop Domestic Violence in the Workplace As of June 15, 2010, all employers in Ontario are responsible for protecting workers when domestic violence follows
PREA COMPLIANCE AUDIT TOOL QUESTIONS FOR INMATES. Prisons and Jails 05/03/2013
 Prisons and Jails 05/03/2013 RANDOM SAMPLE OF INMATES... 2 YOUTHFUL INMATES... 4 DISABLED AND LIMITED ENGLISH PROFICIENT INMATES... 5 TRANSGENDER AND INTERSEX INMATES; GAY, LESBIAN, AND BISEXUAL INMATES...
Prisons and Jails 05/03/2013 RANDOM SAMPLE OF INMATES... 2 YOUTHFUL INMATES... 4 DISABLED AND LIMITED ENGLISH PROFICIENT INMATES... 5 TRANSGENDER AND INTERSEX INMATES; GAY, LESBIAN, AND BISEXUAL INMATES...
DOMESTIC VIOLENCE AND THE WORKPLACE A TUC SURVEY REPORT
 DOMESTIC VIOLENCE AND THE WORKPLACE A TUC SURVEY REPORT THE BACKGROUND TO THE SURVEY Domestic violence may happen behind closed doors but it has far reaching consequences and is known to have an impact
DOMESTIC VIOLENCE AND THE WORKPLACE A TUC SURVEY REPORT THE BACKGROUND TO THE SURVEY Domestic violence may happen behind closed doors but it has far reaching consequences and is known to have an impact
14 September 2012. The Director Criminal Law Review NSW Department of Attorney-General and Justice GPO Box 6 SYDNEY NSW 2001
 14 September 2012 The Director Criminal Law Review NSW Department of Attorney-General and Justice GPO Box 6 SYDNEY NSW 2001 By email: lpclrd@agd.nsw.gov.au Dear Director, RE: INQUIRY INTO THE CONSENT PROVISIONS
14 September 2012 The Director Criminal Law Review NSW Department of Attorney-General and Justice GPO Box 6 SYDNEY NSW 2001 By email: lpclrd@agd.nsw.gov.au Dear Director, RE: INQUIRY INTO THE CONSENT PROVISIONS
Stalking. Office for Student Affairs
 Stalking The Aurora Center for Advocacy & Education 117 Appleby Hall*128 Pleasant St. SE*Minneapolis, MN 55455 Business Line: (612) 626-2929 Email: aurora.center@umn.edu*website: www.umn.edu/aurora Office
Stalking The Aurora Center for Advocacy & Education 117 Appleby Hall*128 Pleasant St. SE*Minneapolis, MN 55455 Business Line: (612) 626-2929 Email: aurora.center@umn.edu*website: www.umn.edu/aurora Office
*****THIS FORM IS NOT A PROTECTIVE ORDER APPLICATION OR A PROTECTIVE ORDER*****
 SHAREN WILSON CRIMINAL DISTRICT ATTORNEY OF TARRANT COUNTY, TEXAS PROTECTIVE ORDERS Family Law Center Phone Number 817-884-1623 200 East Weatherford Street # 3040 Fax Number 817-212-7393 Fort Worth, Texas
SHAREN WILSON CRIMINAL DISTRICT ATTORNEY OF TARRANT COUNTY, TEXAS PROTECTIVE ORDERS Family Law Center Phone Number 817-884-1623 200 East Weatherford Street # 3040 Fax Number 817-212-7393 Fort Worth, Texas
For purposes of this policy, the following terms will be defined as follows.
 DOMESTIC VIOLENCE AND THE WORKPLACE POLICY STATEMENT The City University of New York ( CUNY ) disapproves of violence against women, men, or children in any form, whether as an act of workplace violence
DOMESTIC VIOLENCE AND THE WORKPLACE POLICY STATEMENT The City University of New York ( CUNY ) disapproves of violence against women, men, or children in any form, whether as an act of workplace violence
Victim Services Program:
 Victim Services Program: Mission Statement: To provide crisis intervention, emotional and judicial support and critical services referrals to aid victims and their children, and to promote community awareness
Victim Services Program: Mission Statement: To provide crisis intervention, emotional and judicial support and critical services referrals to aid victims and their children, and to promote community awareness
College Safety Offices. www.ecc.edu 716-851-1ECC
 College Safety Offices North Campus Spring Student Center Room 5 Phone 85-4 South Campus Building 5 Room 5 Phone 85-6 City Campus Main Building Room Phone 85- For emergencies call 76-7-4545 or 9 www.ecc.edu
College Safety Offices North Campus Spring Student Center Room 5 Phone 85-4 South Campus Building 5 Room 5 Phone 85-6 City Campus Main Building Room Phone 85- For emergencies call 76-7-4545 or 9 www.ecc.edu
Stalking. Info Packet
 Stalking Info Packet The Aurora Center for Advocacy & Education 407 Boynton*410 Church St. SE*Minneapolis, MN 55455 Business Line: (612) 626-2929*TTY Line: (612) 626-4279 Email: aurora.center@umn.edu*website:
Stalking Info Packet The Aurora Center for Advocacy & Education 407 Boynton*410 Church St. SE*Minneapolis, MN 55455 Business Line: (612) 626-2929*TTY Line: (612) 626-4279 Email: aurora.center@umn.edu*website:
(b) It may order the Adverse Party to refrain from contacting, intimidating, threatening or otherwise interfering with
 NEVADA PROTECTION ORDER HANDBOOK describing Protection Orders against Stalking and Harassment; Protection Orders for Children; and Protection Orders -- Sexual Assault (1) What is a Protection Order? A
NEVADA PROTECTION ORDER HANDBOOK describing Protection Orders against Stalking and Harassment; Protection Orders for Children; and Protection Orders -- Sexual Assault (1) What is a Protection Order? A
Campus Crime Awareness
 1 of 5 2/24/2009 9:22 AM Campus Crime Awareness Title II of the Student Right to Know and Campus Security Act, know as the Campus Crime Awareness and Campus Security Act of 1990, requires that colleges
1 of 5 2/24/2009 9:22 AM Campus Crime Awareness Title II of the Student Right to Know and Campus Security Act, know as the Campus Crime Awareness and Campus Security Act of 1990, requires that colleges
How To Answer Those Tough Questions. About Elder Abuse NEGLECT FINANCIAL EXPLOITATION EMOTIONAL ABUSE PHYSICAL ABUSE
 How To Answer Those Tough Questions About Elder Abuse HOW TO ANSWER THOSE TOUGH QUESTIONS ABOUT ELDER ABUSE This booklet is designed as a reference for your organization when responding to inquiries about
How To Answer Those Tough Questions About Elder Abuse HOW TO ANSWER THOSE TOUGH QUESTIONS ABOUT ELDER ABUSE This booklet is designed as a reference for your organization when responding to inquiries about
U.S. Citizenship and Inurtigratioil,services
 U $. Depal'tJDent of IIcnnelami.Sec.urity U.S. Citizenship and Immigration. Services Administrative Appeals Office (AAO) 20 Massachusetts Ave., N.W., MS 2090 Washington, DC 20529-2090 U.S. Citizenship
U $. Depal'tJDent of IIcnnelami.Sec.urity U.S. Citizenship and Immigration. Services Administrative Appeals Office (AAO) 20 Massachusetts Ave., N.W., MS 2090 Washington, DC 20529-2090 U.S. Citizenship
Riverside Community College District Policy No. 3515 General Institution
 Riverside Community College District Policy No. 3515 General Institution BP 3515 REPORTING OF CRIMES Reference: Education Code Section 67380 34 Code of Federal Regulations Section 668.46(b)(7) The Chancellor
Riverside Community College District Policy No. 3515 General Institution BP 3515 REPORTING OF CRIMES Reference: Education Code Section 67380 34 Code of Federal Regulations Section 668.46(b)(7) The Chancellor
Rules for the use of the IT facilities. Effective August 2015 Present
 Rules for the use of the IT facilities Effective August 2015 Present INFORMATION MANAGEMENT GUIDE RULES FOR THE USE OF THE UNIVERSITY S IT FACILITIES ( The Rules ) 1. Introduction 2. Interpretation 3.
Rules for the use of the IT facilities Effective August 2015 Present INFORMATION MANAGEMENT GUIDE RULES FOR THE USE OF THE UNIVERSITY S IT FACILITIES ( The Rules ) 1. Introduction 2. Interpretation 3.
New Housing Rights for Victims of Domestic Violence, Rape, Sexual Assault and Stalking
 New Housing Rights for Victims of Domestic Violence, Rape, Sexual Assault and Stalking Victims of domestic violence, rape, sexual assault and stalking have increased rights and protections under a new
New Housing Rights for Victims of Domestic Violence, Rape, Sexual Assault and Stalking Victims of domestic violence, rape, sexual assault and stalking have increased rights and protections under a new
COMPUTER USAGE - EMAIL
 BASIC BELIEF This policy relates to the use of staff email at Mater Dei and is designed to provide guidelines for individual staff regarding their use. It encourages users to make responsible choices when
BASIC BELIEF This policy relates to the use of staff email at Mater Dei and is designed to provide guidelines for individual staff regarding their use. It encourages users to make responsible choices when
BARNARD COLLEGE SEXUAL VIOLENCE RESOURCES
 BARNARD COLLEGE SEXUAL VIOLENCE RESOURCES AMY ZAVADIL ASSOCIATE DEAN FOR EQUITY TITLE IX COORDINATOR 212 854 0037 STUDENT SERVICES FOR GENDER- BASED MISCONDUCT 212 854 1717 Barnard Policy and Procedures
BARNARD COLLEGE SEXUAL VIOLENCE RESOURCES AMY ZAVADIL ASSOCIATE DEAN FOR EQUITY TITLE IX COORDINATOR 212 854 0037 STUDENT SERVICES FOR GENDER- BASED MISCONDUCT 212 854 1717 Barnard Policy and Procedures
An estimated 17.6 million persons, or 7% of all
 U.S. Department of Justice Office of Justice Programs Bureau of Justice Statistics September 2015, NCJ 248991 Victims of Identity Theft, 2014 Erika Harrell, Ph.D., BJS Statistician An estimated 17.6 million
U.S. Department of Justice Office of Justice Programs Bureau of Justice Statistics September 2015, NCJ 248991 Victims of Identity Theft, 2014 Erika Harrell, Ph.D., BJS Statistician An estimated 17.6 million
395 HUDSON STREET, NEW YORK, NY 10014-3684 (212) 925-6635 FAX: (212) 226-1066. Legal Resource Kit. Stalking
 395 HUDSON STREET, NEW YORK, NY 10014-3684 (212) 925-6635 FAX: (212) 226-1066 Legal Resource Kit Stalking 395 HUDSON STREET, NEW YORK, NY 10014-3684 (212) 925-6635 FAX: (212) 226-1066 Please Note Copyright
395 HUDSON STREET, NEW YORK, NY 10014-3684 (212) 925-6635 FAX: (212) 226-1066 Legal Resource Kit Stalking 395 HUDSON STREET, NEW YORK, NY 10014-3684 (212) 925-6635 FAX: (212) 226-1066 Please Note Copyright
RESTRAINING ORDERS IN MASSACHUSETTS Your rights whether you are a Plaintiff or a Defendant
 RESTRAINING ORDERS IN MASSACHUSETTS Your rights whether you are a Plaintiff or a Defendant Prepared by the Mental Health Legal Advisors Committee October 2012 What is a restraining order? A restraining
RESTRAINING ORDERS IN MASSACHUSETTS Your rights whether you are a Plaintiff or a Defendant Prepared by the Mental Health Legal Advisors Committee October 2012 What is a restraining order? A restraining
Findings from the CPS/DV Caseworker Experience Survey
 Findings from the CPS/DV Caseworker Experience Survey January 2013 Background While it is well documented that child welfare services and domestic violence (DV) providers often serve the same families,
Findings from the CPS/DV Caseworker Experience Survey January 2013 Background While it is well documented that child welfare services and domestic violence (DV) providers often serve the same families,
Updated Guidance for Schools and Districts on Addressing Teen Dating Violence (2013)
 Updated Guidance for Schools and Districts on Addressing Teen Dating Violence (2013) G.L. c. 71, as amended by sections 60 and 61 of Chapter 256 of the Acts of 2010, requires public schools to include
Updated Guidance for Schools and Districts on Addressing Teen Dating Violence (2013) G.L. c. 71, as amended by sections 60 and 61 of Chapter 256 of the Acts of 2010, requires public schools to include
Violence Against Women
 Background Violence against women impacts the lives of countless women and their families across the United States. Women and girls of all ages, income levels, racial and ethnic communities, sexual orientations
Background Violence against women impacts the lives of countless women and their families across the United States. Women and girls of all ages, income levels, racial and ethnic communities, sexual orientations
