Understanding and Building HA/LB Clusters
|
|
|
- Dale Norris
- 10 years ago
- Views:
Transcription
1 Understanding and Building HA/LB Clusters mod_backhand, wackamole and other such freedoms Theo Schlossnagle Principal Consultant OmniTI Computer Consulting, Inc.
2 Defining Cluster, HA, and LB Cluster - (n.) a bunch; a number of things of the same kind gathered together. in computers, a set of like machines providing a particular service united to increase robustness and/or performance. HA - High Availability. (adj.) remaining available despite the failure of one s components. usually used to describe a system or a service. above and beyond fault tolerant. LB - Load Balanced. (adj.) providing a service from multiple separate systems where resources are effectively combined by distributing requests across these systems.
3 Building Clusters Why Bother? 1. Online applications used for internal productivity (Business Continuity) 2. Online applications used for revenue generation (Financial Continuity) 3. Strict service-level agreements for availability (Availability) 4. Strict service-level agreements for performance (Performance) 5. Services used by more concurrent users (Scalability)
4 Clustering problems Fault tolerance and high availability wackamole Effective resource allocation mod_backhand Content replication custom solution (NFS, rsync, etc.) Server proximity optimizations DNS shared IP or smarter DNS Manageability mod_backhand Resource monitoring mod_backhand Seamless scalability mod_backhand, mod_log_spread Unified log collection mod_log_spread
5 Pros: High Availability " Taking down components of your architecture for maintenance or upgrades is simple " Architectures often lend themselves to higher capacity " After tackling the 3 node cluster, scaling to n nodes is more a process than an experiment Cons: " More equipment, services, etc. to maintain " Troubleshooting issues becomes dramatically more difficult " Making your application and content synchronization get along " The mere fact that you need an HA solution speaks to the attention required to properly manage the cluster
6 High Availability Two Approaches Front-end high-availability distribution system Peer-based high-availability system
7 High Availability First Approach Front-end high-availability distribution system HA device is a single point of failure HA device costs money and isn t doing anything Application servers are not a single point of failure
8 High Availability First Approach (more robust) Single point of failure can be eliminated Two or more devices must be used and they must support some mechanism of failover All commercial solutions provide such built-in failover mechanics Some open source solutions for this machine-to-machine failover exist Thought: You have to use an HA solution to make your HA solution HA!
9 Implementations Pair-based systems (master/slave): Veritas Cluster Server Linux-HA Pirahna Front-end distribution systems: LVS F5 BIG/ip Cisco LocalDirector Cisco Arrowpoint Foundry ServerIron Alteon ACESwitch Coyote Point Equalizer
10 High Availability A New Paradigm Goals: How? No specialized or dedicated hardware Every party involved is responsible for the availability of the service As long as one machine in the cluster is functioning it is able to survive the service Wackamole
11 Wackamole: N-way IP failover Allows n machines to provide service from m IP address with n-1 faults. Good things: n > m, n = m, or n < m as long as n > 0 and m > 0. Limitations: A publicized IP address can only be managed by one machine at a time.
12 Spread: The Concept (.1) A daemon on each machine. Groups with guaranteed delivery semantics and membership views across the cluster.
13 Wackamole: The Concept (.1) 3 machines hosting 6 virtual IP addresses
14 Wackamole: The Concept (.2) 1 machine failed 2 machines hosting 6 virtual IP addresses
15 Wackamole: Installation and Configuration No steps can be taken to install Wackamole until we first satisfy its requirements: A supported operating system: Solaris FreeBSD Linux Mac OS X It s Open Source, PORT IT! Underlying system requirements: Spread (
16 STEP 1: Installing Spread The Spread Group Communication System is an integral toolkit used by Wackamole to make decisions: 1. Download Spread: Configure/Compile/Install: gzip -dc spread-src tar.gz tar xvf - cd spread /configure make make install (due to a bug in Spread , you must manually install the header files) cp sp.h sp_*.h /usr/local/include/
17 STEP 2: Configuring Spread spread.conf: Spread configuration for 2 machines using IP Broadcast DebugFlags = { EXIT CONFIGURATION } EventLogFile = /var/log/spread/mainlog EventTimeStamp DangerousMonitor = false Spread_Segment :3777 { moria moria }
18 STEP 2 continued: Configuring Spread Bigger spread.conf: Spread configuration for 10 machines using IP Multicast DebugFlags = { EXIT CONFIGURATION } EventLogFile = /var/log/spread/mainlog EventTimeStamp DangerousMonitor = false Spread_Segment :4803 { samwise peregrine meriadoc www-s www-s www-s stage-s rsync sslproxy-s sslproxy-s }
19 STEP 3: Installing Wackamole 1. Download Wackamole: Configure/Compile/Install: gzip -dc wackamole tar.gz tar xvf - cd spread-wackamole./configure make make install
20 Wackamole Configuration Basics (.1) Spread = <string> Specifies the location of the Spread daemon. A number like 4803 should be specified to connect to the locally running Spread daemon is the default port that Spread uses; if you have installed it differently the Spread daemon should be reflected here. Group = <string> Specifies the Spread group that should be joined. This group should only be used by Wackamole instances in the same cluster. SpreadRetryInterval = <time> Specifies the amount of time between attempted but failed reconnects.
21 Wackamole Configuration Basics (.2) Control = <filename> Specifies the location of the Wackamole control socket. Wackamole creates and listens on a unix domain socket. The program wackatrl connects via this socket. Mature = <time> Specifies the time interval required for the instance to mature. Maturation describes the change from a joined member to a member capable of assuming VIFs. This can be specified in order to prevent machine flapping causing service flapping. A time interval of 5 seconds (5s) is a reasonable value.
22 Wackamole Configuration Basics (.3) Address Resolution Protocol Is the protocol employed to resolve a given IP address on a local subnet to a hardware address for use on the datalink layer. The answer is cached. That cache is your enemy. Why? Machine A performs ARP to find Machine A finds at MAC 00:60:08:bf:4c:3e (machine B) Machine A caches this answer in its ARP cache Machine B crashes Machine C takes Machine A has machine B s MAC in its ARP cache. Machine A can t talk to
23 Wackamole Configuration Basics (.4) How do we fix other machines ARP caches? Arp-spoofing. This is technically easy. It involves answering unsolicited ARP requests. Wackamole manufactures fake ARP response packets and sends them to important hosts. Which hosts are important? Routers? Peers in the cluster? Can we be smarter than this? YES!
24 Wackamole Configuration Basics (.5) How do we know who is important? Any machine that has this particular IP address in its ARP cache. Problem: We cannot go look in every machine s ARP cache without special client installed code -- it is infeasible and unmanageable. Solution: If they have this IP address in their ARP cache, the previous owner of this IP address had their IP addresses in its ARP cache. Maintain a shared, aggregate ARP cache and notify everyone in it.
25 Wackamole Configuration Basics (.6) Arp-cache = <time> Specifies the time interval between recurrent ARP cache updates. Every n seconds, Wackamole will peruse the system's ARP cache and announce all the IP addresses contained therein to the Spread group. All members of the group will receive this list and integrate it into the shared ARP pool that can be used as a source for the Notify list.
26 Wackamole Configuration Basics (.7) Notify { <network> <network> throttle <number/second> arp-cache } The notification section describes which machines should be sent arp-spoofs when an IP address is acquired. <network>: <ifname>:<ip>/<mask> eth0: /23 fxp0: /32
27 Wackamole Configuration Basics (.8) What is this /n thing? Wackmole understands IP addresses CIDR form. (Classless Inter Domain Routing) The n refers to the number of set (1) bits in the netmask. /8 : /16 : /23 : /24 : /27 : /30 : /32 :
28 Wackamole Configuration Basics (.9) VirtualInterfaces { <interface> { <interface> <interface> } } Lists all virtual interfaces for which wackamole is responsible. All wackamole instances in the cluster must have all of the same interfaces in the same order. <interface>: <ifname>:<ip>/<netmask> (CIDR form) eth0: /32 fxp1: /32
29 Wackamole Configuration Basics (.10) Why do the examples use /32 as the netmask? The first IP address configured on a machine in a given subnet should have the netmask and broadcast address representing that subnet. All subsequent IP addresses in the same subnet on that machine are virtual and should be designated a netmask of or 0xffffffff or /32. This is clearly documented on FreeBSD and seems to hold true for all other OSs.
30 Wackamole Configuration Basics (.11) Balance { Interval = <time> AcquisitionsPerRound = <number> } Interval = <time> Specifies the length of a balancing round. AcquisitionsPerRound = <number> Specifies the number of IP addresses that can be assumed in a single round of balancing.
31 Wackamole: Example Uses (.1.1) Goals: Static image and document server for intranet 1500 concurrent connections 120 Mbs of sustained traffic Solution: 4 commodity machines 1 x 100Mbs interface card 4 x Ultra2 SCSI drives in RAID 0 Linux Apache (lean and mean) Wackamole
32 Wackamole: Example Uses (.1.2) 4 Linux machines running Apache and Wackamole, advertising 4 virtual IP (VIP) addresses through DNS. If all 4 machines are up, each will acquire and provide service on a single VIP. If one machine (A) crashes, one of the 3 remaining will acquire and provide service on the VIP previously managed by A. If only one machine remains, it will have acquired and be providing service on all 4 VIPs.
33 Wackamole: Example Uses (.1.3) Spread = 4803 SpreadRetryInterval = 5s Group = wack1 Control = /var/run/wack.it Mature = 5s Balance { interval = 4s AcquisitionsPerRound = all } Arp-Cache = 90s Prefer None VirtualInterfaces { { eth0: /32 } { eth0: /32 } { eth0: /32 } { eth0: /32 } } Notify { eth0: /32 arp-cache }
34 Wackamole: Example Uses (.1.3.1) Spread = 4803 SpreadRetryInterval = 5s Group = wack1 Control = /var/run/wack.it Spread is running on port 4803 and Wackamole will connect over a local socket. Wackamole will retry every 5 seconds in the event of a Spread failure. Once connected to Spread, Wackamole will use the group called wack1 as a control group. Wackamole will listen on the local socket called /var/run/ wack.it for control commands from wackatrl.
35 Wackamole: Example Uses (.1.3.2) Wackamole is eligible to assume virtual interfaces after 5 seconds. Balancing rounds are 4 seconds long. Mature = 5s Balance { interval = 4s AcquisitionsPerRound = all } Arp-Cache = 90s Upon a new group membership, Wackamole will acquire all the virtual interfaces in the final configuration at once. Every 90 seconds Wackamole will examine the system s local ARP cache and announce all IP addresses found to the cluster through Spread.
36 Wackamole: Example Uses (.1.3.3) Wackamole will not prefer any virtual interface. Wackamole will attempt to balance the virtual interfaces across the currently available machines. These 4 virtual interfaces are the IP addresses exposed in DNS for the service in question. These are the addresses clients connect to. Prefer None VirtualInterfaces { { eth0: /32 } { eth0: /32 } { eth0: /32 } { eth0: /32 } }
37 Wackamole: Example Uses (.1.3.4) Notify our router We have to notify our router as it needs to direct traffic to the IP addresses that are brought up by Wackamole. If we effectively notify our router, then all traffic originating from outside the subnet will be able to establish connections to these IP addresses. Notify the contents of the shared ARP-cache. This helps all the machines on the local subnet notice the change. Notify { eth0: /32 arp-cache }
38 Wackamole: Example Uses (.2.1) Goals: Mission-critical router IPSEC tunnels for secure VPN Firewall rulesets NAT for attached private networks Solution: 2 commodity machines 3 x 100Mbs interface card FreeBSD Racoon/IPSEC ipfw Wackamole
39 Wackamole: Example Uses (.2.2) 2 machines running FreeBSD, routing between subnets and running ipfw. As there is only a single IP address advertised/used as a default route on each subnet, only one machine will own the address at any given time. Wackamole manages groupings of VIPs as single VirtualInterface which guarantees that a single machine will acquire all of the routing VIPs in an inseparable group. Arp-spoofing to a shared arp-cache of addresses ensures that all machines that use this virtual route will be notified (arp-spoofed) to the change over in the event of a failure.
40 Wackamole: Example Uses (.2.3) Spread = 3777 SpreadRetryInterval = 5s Group = wack1 Control = /var/run/wack.it mature = 5s balance { Interval = 4s AcquisitionsPerRound = all } arp-cache = 90s # There is no "master" Prefer None # Only one virtual interface VirtualInterfaces { { fxp2: /32 fxp1: /32 fxp0: /32 } } Notify { # Let's notify our upstream router: fxp0: /32 fxp0: /32 fxp0: /32 fxp0: /32 fxp0: /32 # And out DNS servers fxp1: /32 fxp1: /32 fxp2: /32 fxp2: /32 # And the ARP cache arp-cache # The networks we are attached to. fxp0: /28 fxp1: /24 throttle 16 fxp2: /23 throttle 16 }
41 Wackamole: Example Uses (.2.3.1) Spread = 3777 SpreadRetryInterval = 5s Group = wack1 Control = /var/run/wack.it Spread is running on port 3777 and Wackamole will connect over a local socket. Wackamole will retry every 5 seconds in the event of a Spread failure. Once connected to Spread, Wackamole will use the group called wack1 as a control group. Wackamole will listen on the local socket called /var/run/ wack.it for control commands from wackatrl.
42 Wackamole: Example Uses (.2.3.2) Wackamole is eligible to assume virtual interfaces after 5 seconds. Balancing rounds are 4 seconds long. mature = 5s balance { Interval = 4s AcquisitionsPerRound = all } arp-cache = 90s Upon a new group membership, Wackamole will acquire all the virtual interfaces in the final configuration at once. Every 90 seconds Wackamole will examine the system s local ARP cache and announce all IP addresses found to the cluster through Spread.
43 Wackamole: Example Uses (.2.3.3) Wackamole will not prefer any virtual interface. In this configuration that means that no instance wants to be master. This means that when a new Wackamole instance comes online and matures, it will not steal the VIF that is already being controlled by another machine. There is a single virtual interface with three IP addresses. These IP addresses are the default routes on all the respective attached networks. # There is no "master" Prefer None # Only one virtual interface VirtualInterfaces { { fxp2: /32 fxp1: /32 fxp0: /32 } }
44 Wackamole: Example Uses (.2.3.4) Notification of routers is tricky at times. Many routers do not react the same way to ARPspoofing. Notify { # Let's notify our upstream router: fxp0: /32 fxp0: /32 fxp0: /32 fxp0: /32 fxp0: /32 The static default route (the uplink) is , but that is a virtual router interface of two Cisco Catalysts running HSRP whose real IPs are and is a universal network address and is a universal broadcast address -- both can be used for ARP requests. Some machines will listen to those for ARP responses. }
45 Wackamole: Example Uses (.2.3.5) Notify { Perhaps the most important machines that we have on our network are our DNS servers. Any interruption in their availability can cause cascading effects on other caching name servers. } # And out DNS servers fxp1: /32 fxp1: /32 fxp2: /32 fxp2: / and are the virtual IP addresses advertised by a hardware load balancer and are their real static IP addresses.
46 Wackamole: Example Uses (.2.3.6) Notify { Notify the contents of the shared ARP-cache. Every time this Wackamole and peer Wackamole instances announce the IP addresses in their respective systems local ARP-caches, their IP addresses are placed in an aggregate pool. Each IP in this aggregate pool is used as a destination for ARP-spoofing. In theory, this should notify every machine that needs its ARP-cache refreshed. # And the ARP cache arp-cache }
47 Wackamole: Example Uses (.2.3.7) Notify { The addresses specified here are actually IP blocks /28 notifies the 16 addresses in that IP block /24 notifies the class C (256 addresses) /23 notifies the 512 addresses ( through ) } # The networks we are attached to. fxp0: /28 fxp1: /24 throttle 16 fxp2: /23 throttle 16
48 Wackamole: Cool Uses When pushing out new perl modules and configuration changes, we must restart Apache. These restarts can cause momentary interruption in service. How can wackamole help? #!/bin/sh wackatrl -f apachectl stop # sync content rsync -a stage::webroot/ /web/ apachectl start wackatrl -s
49 Wackamole: It works Wackamole is an effective HA tool It has been used in production for 24/7 services Wackamole can make any service highly available: Routers Firewalls Web servers FTP servers DNS servers
50 HA. Now what? Now that we have dissected HA we can approach LB without the itching question: What if it crashes? The approach of load balancing is not to make a system available in spite of failures. Load balancing is used to effectively combine the resources of several machines contributing to a single service. To increase performance To increase capacity
51 Load balancing: Practiced Solutions Standalone Server " Vanilla Apache server DNS Round Robin " Multiple A records in DNS Single point proxies " BIG/ip " Alteon, Foundry, Arrowpoint, and Extreme content aware Peer-based proxies " mod_backhand
52 Load balancing: or not Apache, plain and simple: One server One IP Single point of failure
53 Load balancing: DNS RR The most simple load balanced configuration: Multiple web servers with identical services and content. There is an A record in DNS for that web server for each IP. If a server fails, a portion of the service is unavailable. Sample BIND configuration: www 300 IN A IN A IN A IN A IN A
54 Load balancing: Single Point Proxy The most common load balanced configuration: A singular entity represents the cluster as a whole and traffic is allocated by that entity. Most commercial solutions conform to this paradigm. Single point of failure unless an HA solution is applied.
55 Load balancing: Peer-based Proxy Each node in the cluster is privileged to proxy requests to other nodes within the cluster. Extensive resource utilization information is available to each node allowing for more intelligent reallocation decisions. Like DNS RR, a single failure will cause a service availability issue. This can be solved with Wackamole.
56 What is mod_backhand? Effective utilization of resources in a web cluster. Handling heterogeneous environments: Resources (Memory, Processing Power, I/O) Hardware (Intel, Alpha, Sun) Platforms (Linux, BSD, Solaris) Flexible architecture allowing increased manageability. Seamless cluster scaling. A convenient means for resource monitoring. Open source solution that integrates with Apache. Wide area and local area support.
57 mod_backhand: configuration (.1) UnixSocketDir <directory> The directory which will house the moderator and children unix domain sockets over which file descriptors are passed (for connection pooling). BackhandModeratorPIDFile <filename> Specifies a filename in which to store the process ID of the currently running moderator process. This is useful for a start script that renices the moderator after Apache startup.
58 mod_backhand: configuration (.2) MulticastStats <broadcast IP:port> MulticastStats <multicast IP:port,ttl> The IP address and port to which the moderator will announce local resource information. AcceptStats <CIDR-form IP block> Describes aa IP block that the moderator will trust. Accepting and incorporating resource information from these IPs. All participating machines in the cluster should fall inside this block. Multiple AcceptStats lines are allowed.
59 mod_backhand: configuration (.3) MulticastStats <myip: port> <broadcast IP:port> MulticastStats <myname:port> <multicast IP:port,ttl> The IP address and port to which the moderator will announce local resource information. However, local information will be announces as if from myip:port or myname:port. BackhandSelfRedirect <On Off> Tells mob_backhand to use proxying even if it find itself to be the best host to service a request. This is useful for running two Apache instances and using the two argument MulticastStats directive.
60 mod_backhand: configuration (.4) BackhandConnectionPools <On Off> Tells mod_backhand that it should allow the moderator to manage connection to the other machines in the cluster and reuse them from client request to client request. If set to Off, the Apache child will not contact the moderator and the connection will be initiated from the child and terminated immediately after use. This requires more time per connection, but allows for more concurrency. It should be On for low traffic sites and Off for high traffic sites.
61 mod_backhand: configuration (.5) BackhandLogLevel <(+ -)(dcsn net mbcs)(all )> This is an advanced feature for troubleshooting problems with the underlying plumbing of mod_backhand. It enables verbose logging from all the different subsystems of mod_backhand: dcsn The decision making subsystem net The networking subsystem mbcs The mod_backhand control system used for child-moderator communications By default, all logging is disabled.
62 mod_backhand: configuration (.6) Backhand <function> [args] Passes the current list of eligible servers (candidates) through the candidacy function function which can examine the request and the available resources in the cluster and change that list accordingly. BackhandFromSO <file> <function> [args] Same as above, except that function is dynamically loaded from the shared object file. This allows candidacy functions to be written completely outside of mod_backhand. More than one Backhand directive can be specified, providing a cascading effect.
63 mod_backhand: configuration (.7) Directives can pertain only to a specific VirtualHost, Directory, or Location clause. Allows for decisions based on: Document location Virtual host File extension Example: <Files ~ (\.php)$ > Backhand byage Backhand bybusychildren </Files> Machines in cluster: www1.intel.domain.com www2.intel.domain.com www3.intel.domain.com www1.sun4u.domain.com www2.sun4u.domain.com www3.sun4u.domain.com www1.alpha.domain.com www2.alpha.domain.com www3.alpha.domain.com <Directory /www/64bitapps/> Backhand byage BackhandFromSO libexec/byhostname.so byhostname (alpha sun4u) Backhand bycost </Directory>
64 mod_backhand: configuration (.8) Loading the module: LoadModule backhand_module libexec/mod_backhand.so AddModule mod_backhand.c Main module configuration: <IfModule mod_backhand.c> UnixSocketDir /var/apache/backhand BackhandModeratorPIDFile /var/apache/backhand/moderator.pid MulticastStats :5445 AcceptStats /23 BackhandConnectionPools Off </IfModule> Status URL: <IfModule mod_backhand.c> <Location "/backhand/"> SetHandler backhand-handler Backhand off </Location> </IfModule>
65 mod_backhand: configuration (.9) Balancing a directory: <IfModule mod_backhand.c> <Directory /path/to/directory> Backhand byage Backhand byrandom Backhand bylogwindow Backhand bybusychildren </Directory> </IfModule> Balancing specific file types: <IfModule mod_backhand.c> <Files ~ (\.jsp \.do)$ > Backhand byage Backhand libexec/byhostname.so byhostname java </Files> </IfModule>
66 Flexible Framework: making decisions (.1) byage [# seconds] remove all servers from whom we have not heard resource information byrandom reorder the existing server list randomly bylogwindow reduce the list of n servers to the first log 2 (n) bycpu reorder the existing server list from most idle CPU to least idle CPU byload [# bias] reorder the existing server list from least loaded to most loaded biased toward yourself bycost reorder the existing server list from least costly to most costly bybusychildren reorder the existing server list based on the number of occupied Apache children from least to most.
67 Flexible Framework: making decisions (.2) Candidacy functions that cause mod_backhand to redirect: HTTPRedirectToIP change the proxying mechanism for the candidates to HTTP redirect and redirect to a server's IP address HTTPRedirectToName "format" change the mechanism for the candidates to HTTP redirect and build the name from the format string
68 Flexible Framework: making decisions (.3) How these candidacy functions do their job: 1 A list of candidacy functions is specified in the Apache configuration file 2 For each request, a complete server list is passed into the first function. 3 This function optionally modifies the list of servers and the resulting list is passed to the next function. The Apache request structure can be modified. The method (proxying/redirection) can be selected. 4 Repeat step 3 for next function until no more candidacy functions remain. 5 The first server in the resulting list is chosen for proxying or redirection.
69 Flexible Framework: making decisions (.4) The API for a decision function: int Foo(request_rec *r, ServerSlot *s, int *n, char *arg); r is the Apache request record structure s is the server list as a list ServerSlot structures. Each ServerSlot contains an id that in an index into the resource information table called serverstats and redirect and hosttype that describe how mod_backhand will direct traffic to that machine. n is the number of valid servers in the server list arg is the optional argument that can be passed in at run time from the Apache configuration file
70 Flexible Framework: making decisions (.6) The byhostname candidacy function #include "httpd.h" #include "http_log.h" #include "mod_backhand.h" static char *lastarg = NULL; static regex_t re_matching; int byhostname(request_rec r, int *s, int *n, char *a) { int ret, i, mycount; if(!a) return -1; if(!lastarg strcmp(arg, lastarg)) { if((ret = regcomp(&re_matching, arg, REG_EXTENDED))!=0) return -1; if(lastarg) free(lastarg); lastarg = strdup(lastarg); } for(i=0;i<*n;i++) if(!regexec(&re_matching, serverstats[s[i].id].hostname, 0, NULL, 0)) s[mycount++] = s[i]; *n = mycount; return mycount; }
71 Flexible Framework: internals (.5) Resource information includes: Hostname IP:port for service Total/Available memory System load CPU utilization Number of CPUs Speed of machine Age of more recent information Number of available/total Apache children Average turnaround time for remote requests
72 Flexible Framework: internals (.6) Resource information is collected from the local system every second. That information is multicasted to all peers. An event loop is used to collect information from peers and it is consolidated in the serverstats structure. That event loop is used to manage persistent connection pools assuming BackhandConnectionPools is on.
73 Flexible Framework: internals (.7) Connection pooling Reuse of connections to other servers reduces the overhead of TCP/IP establishment and possible Apache forking. Keepalive exploiting Keepalives allow reuse of an existing TCP/IP sessions by pipelining HTTP requests. If keepalives are unconditionally enabled internally to the cluster (Apache source patch available), sites that wish to disable keepalives can still exploit connection pooling.
74 Flexible Framework: internals (.8)
75 HA. LB. Now what? Now that we have dissected HA and LB, what remains to be tackled? Outstanding problems: Content distribution Logging Production pushes of code Efficiently placing static content in production Unifying/consolidating simple web logging on a cluster of machines Error logging and job logging on a cluster of machines
76 Content Distribution Most content distributions are based on: A combination of CVS export and rsync Front-end file system-based caches Can be smarter with intelligent cache placement and mod_rewrite The details of content distribution systems are out of the scope of this talk.
77 Distributed logging Distributed logging systems are in their infancy Some systems employ a passive network sniffing approach. This is flawed as packets can be dropped, and this behaviour is difficult to diagnose and fix. Some systems use TCP/IP to connect to a logging server. This has a high overhead, can hang in the event of a systems failure, and has inherent scalability limitations. Using a multicast message bus is the right approach. mod_log_spread is such an implementation.
78 Distributed logging: what we need What we need: Apache integration and a flexible and easy API Reliable and ordered delivery of logs Efficient network utilization Efficient handling of thousands of concurrent publishers Multiple subscribers with minimal overhead What we use: A group communication system (Spread) A log journaling program (spreadlogd) Spread client API (C, python, ruby, PHP, Perl) An Apache module (mod_log_spread using C API) mod_perl logging handler (Apache::Log::Spread)
79 Distributed logging: what we get Unified logging for local area clusters No drop semantics Ultra-convenient integration into an existing configuration Multiple subscribers with little overhead Fault-tolerant log writers Process real-time cross-cluster clickstreams Real-time per server and cluster-wide hit analysis Real-time individualized mass vhost logging ALL AT THE SAME TIME!
80 Distributed logging: concept (.1) Apache publishes logs to groups Loggers subscribe to those groups Monitor subscribes to groups With Spread: almost 0 overhead for multiple subscribers
81 Distributed logging: how its done Spread is installed on every web server and every log server Download and install mod_log_spread Compile/Install mod_log_spread Add to httpd.conf: LoadModule log_spread_module libexec/mod_log_spread.so AddModule mod_log_spread.c SpreadDaemon 4803 CustomLog $site1 combined Install spreadlogd (comes with mod_log_spread) Configure spreadlogd and let er rip!
82 Distributed logging: configure spreadlogd # This is a sample spreadlogd.conf file BufferSize = Spread { Port = 4903 Log { RewriteTimestamp = CommonLogFormat Group = site1" File = /data/logs/apache/ } Log { RewriteTimestamp = CommonLogFormat Group = site2" File = /data/logs/apache/ } }
83 Distributed logging: other cool things You can run 1, 2 or 10 spreadlogd instances on separate logging servers without incurring more network traffic. Writing other applications that listen to the logging stream for real-time statistics: Hit rates Click-thru rates Who s online lists
84 Summary LB is complicated and very specific to your application. If someone claims to offer the best solution, they are lying -- or misrepresenting the truth. HA clustering solutions are often combined with LB solutions. This isn t bad, but can confuse the topics. Peer-based HA solutions are powerful alternatives to the classic front-end device. They may be better for many applications. Distributed logging is not a truly complicated problem, but mod_log_spread is the best solution available. Period. Content distribution is complicated -- good luck.
85 Conclusion The Backhand Project provides solid, tested solutions for many of the complications found when building clusters to serve today s Internet Applications. As open source technologies, they all lend themselves to further extension, robustification and multi-platform support. The tools presented provide solutions that have been used successfully to build enterprise, mission-critical architectures.
86 Credits The Johns Hopkins Center for Networking and Distributed Systems who funds the core development of tools such as: Spread, mod_backhand and wackamole. OmniTI Computer Consulting, Inc. who funds development of: mod_log_spread, spreadlogd, wackamole, mod_backhand, tons of cool Perl and PHP stuff and countless other open source projects. and for providing an excellent work environment with a constant stream of challenging and exciting problems.
UNDERSTANDING AND BUILDING HA/LB CLUSTERS
 UNDERSTANDING AND BUILDING HA/LB CLUSTERS MOD BACKHAND, WACKAMOLE AND OTHER SUCH FREEDOMS THEO SCHLOSSNAGLE SEPTEMBER 12TH, 2002 Abstract Today s web applications are more demanding
UNDERSTANDING AND BUILDING HA/LB CLUSTERS MOD BACKHAND, WACKAMOLE AND OTHER SUCH FREEDOMS THEO SCHLOSSNAGLE SEPTEMBER 12TH, 2002 Abstract Today s web applications are more demanding
Scalable Linux Clusters with LVS
 Scalable Linux Clusters with LVS Considerations and Implementation, Part II Eric Searcy Tag1 Consulting, Inc. [email protected] May 2008 Abstract Whether you are perusing mailing lists or reading
Scalable Linux Clusters with LVS Considerations and Implementation, Part II Eric Searcy Tag1 Consulting, Inc. [email protected] May 2008 Abstract Whether you are perusing mailing lists or reading
Availability Digest. www.availabilitydigest.com. Redundant Load Balancing for High Availability July 2013
 the Availability Digest Redundant Load Balancing for High Availability July 2013 A large data center can comprise hundreds or thousands of servers. These servers must not only be interconnected, but they
the Availability Digest Redundant Load Balancing for High Availability July 2013 A large data center can comprise hundreds or thousands of servers. These servers must not only be interconnected, but they
Scalable Linux Clusters with LVS
 Scalable Linux Clusters with LVS Considerations and Implementation, Part I Eric Searcy Tag1 Consulting, Inc. [email protected] April 2008 Abstract Whether you are perusing mailing lists or reading
Scalable Linux Clusters with LVS Considerations and Implementation, Part I Eric Searcy Tag1 Consulting, Inc. [email protected] April 2008 Abstract Whether you are perusing mailing lists or reading
Creating Web Farms with Linux (Linux High Availability and Scalability)
 Creating Web Farms with Linux (Linux High Availability and Scalability) Horms (Simon Horman) [email protected] December 2001 For Presentation in Tokyo, Japan http://verge.net.au/linux/has/ http://ultramonkey.org/
Creating Web Farms with Linux (Linux High Availability and Scalability) Horms (Simon Horman) [email protected] December 2001 For Presentation in Tokyo, Japan http://verge.net.au/linux/has/ http://ultramonkey.org/
WebGUI Load Balancing
 WebGUI Load Balancing WebGUI User Conference October 5, 2005 Presented by: Len Kranendonk [email protected] Course Contents Introduction Example: The Royal Netherlands Football Association Scaling WebGUI
WebGUI Load Balancing WebGUI User Conference October 5, 2005 Presented by: Len Kranendonk [email protected] Course Contents Introduction Example: The Royal Netherlands Football Association Scaling WebGUI
High Performance Cluster Support for NLB on Window
 High Performance Cluster Support for NLB on Window [1]Arvind Rathi, [2] Kirti, [3] Neelam [1]M.Tech Student, Department of CSE, GITM, Gurgaon Haryana (India) [email protected] [2]Asst. Professor,
High Performance Cluster Support for NLB on Window [1]Arvind Rathi, [2] Kirti, [3] Neelam [1]M.Tech Student, Department of CSE, GITM, Gurgaon Haryana (India) [email protected] [2]Asst. Professor,
Purpose-Built Load Balancing The Advantages of Coyote Point Equalizer over Software-based Solutions
 Purpose-Built Load Balancing The Advantages of Coyote Point Equalizer over Software-based Solutions Abstract Coyote Point Equalizer appliances deliver traffic management solutions that provide high availability,
Purpose-Built Load Balancing The Advantages of Coyote Point Equalizer over Software-based Solutions Abstract Coyote Point Equalizer appliances deliver traffic management solutions that provide high availability,
DNS ROUND ROBIN HIGH-AVAILABILITY LOAD SHARING
 PolyServe High-Availability Server Clustering for E-Business 918 Parker Street Berkeley, California 94710 (510) 665-2929 wwwpolyservecom Number 990903 WHITE PAPER DNS ROUND ROBIN HIGH-AVAILABILITY LOAD
PolyServe High-Availability Server Clustering for E-Business 918 Parker Street Berkeley, California 94710 (510) 665-2929 wwwpolyservecom Number 990903 WHITE PAPER DNS ROUND ROBIN HIGH-AVAILABILITY LOAD
Network Defense Tools
 Network Defense Tools Prepared by Vanjara Ravikant Thakkarbhai Engineering College, Godhra-Tuwa +91-94291-77234 www.cebirds.in, www.facebook.com/cebirds [email protected] What is Firewall? A firewall
Network Defense Tools Prepared by Vanjara Ravikant Thakkarbhai Engineering College, Godhra-Tuwa +91-94291-77234 www.cebirds.in, www.facebook.com/cebirds [email protected] What is Firewall? A firewall
ClusterLoad ESX Virtual Appliance quick start guide v6.3
 ClusterLoad ESX Virtual Appliance quick start guide v6.3 ClusterLoad terminology...2 What are your objectives?...3 What is the difference between a one-arm and a two-arm configuration?...3 What are the
ClusterLoad ESX Virtual Appliance quick start guide v6.3 ClusterLoad terminology...2 What are your objectives?...3 What is the difference between a one-arm and a two-arm configuration?...3 What are the
How To Run A Web Farm On Linux (Ahem) On A Single Computer (For Free) On Your Computer (With A Freebie) On An Ipv4 (For Cheap) Or Ipv2 (For A Free) (For
 Creating Web Farms with Linux (Linux High Availability and Scalability) Horms (Simon Horman) [email protected] October 2000 http://verge.net.au/linux/has/ http://ultramonkey.sourceforge.net/ Introduction:
Creating Web Farms with Linux (Linux High Availability and Scalability) Horms (Simon Horman) [email protected] October 2000 http://verge.net.au/linux/has/ http://ultramonkey.sourceforge.net/ Introduction:
ELIXIR LOAD BALANCER 2
 ELIXIR LOAD BALANCER 2 Overview Elixir Load Balancer for Elixir Repertoire Server 7.2.2 or greater provides software solution for load balancing of Elixir Repertoire Servers. As a pure Java based software
ELIXIR LOAD BALANCER 2 Overview Elixir Load Balancer for Elixir Repertoire Server 7.2.2 or greater provides software solution for load balancing of Elixir Repertoire Servers. As a pure Java based software
DEPLOYMENT GUIDE Version 1.0. Deploying the BIG-IP LTM with Apache Tomcat and Apache HTTP Server
 DEPLOYMENT GUIDE Version 1.0 Deploying the BIG-IP LTM with Apache Tomcat and Apache HTTP Server Table of Contents Table of Contents Deploying the BIG-IP LTM with Tomcat application servers and Apache web
DEPLOYMENT GUIDE Version 1.0 Deploying the BIG-IP LTM with Apache Tomcat and Apache HTTP Server Table of Contents Table of Contents Deploying the BIG-IP LTM with Tomcat application servers and Apache web
Lab 5 Explicit Proxy Performance, Load Balancing & Redundancy
 Lab 5 Explicit Proxy Performance, Load Balancing & Redundancy Objectives The purpose of this lab is to demonstrate both high availability and performance using virtual IPs coupled with DNS round robin
Lab 5 Explicit Proxy Performance, Load Balancing & Redundancy Objectives The purpose of this lab is to demonstrate both high availability and performance using virtual IPs coupled with DNS round robin
Chapter 1 - Web Server Management and Cluster Topology
 Objectives At the end of this chapter, participants will be able to understand: Web server management options provided by Network Deployment Clustered Application Servers Cluster creation and management
Objectives At the end of this chapter, participants will be able to understand: Web server management options provided by Network Deployment Clustered Application Servers Cluster creation and management
Quick Start for Network Agent. 5-Step Quick Start. What is Network Agent?
 What is Network Agent? The Websense Network Agent software component uses sniffer technology to monitor all of the internet traffic on the network machines that you assign to it. Network Agent filters
What is Network Agent? The Websense Network Agent software component uses sniffer technology to monitor all of the internet traffic on the network machines that you assign to it. Network Agent filters
Configuring MassTransit Server to listen on ports less than 1024 using WaterRoof on Macintosh Workstations
 Configuring MassTransit Server to listen on ports less than 1024 using WaterRoof on Macintosh Workstations Summary This article explains how to configure MassTransit to listen on ports less than 1024 without
Configuring MassTransit Server to listen on ports less than 1024 using WaterRoof on Macintosh Workstations Summary This article explains how to configure MassTransit to listen on ports less than 1024 without
Load Balancing using Pramati Web Load Balancer
 Load Balancing using Pramati Web Load Balancer Satyajit Chetri, Product Engineering Pramati Web Load Balancer is a software based web traffic management interceptor. Pramati Web Load Balancer offers much
Load Balancing using Pramati Web Load Balancer Satyajit Chetri, Product Engineering Pramati Web Load Balancer is a software based web traffic management interceptor. Pramati Web Load Balancer offers much
IM and Presence Service Network Setup
 Configuration changes and service restart notifications, page 1 DNS Domain Configuration, page 2 IM and Presence Service Default Domain Configuration, page 6 IM Address Configuration, page 7 Domain Management
Configuration changes and service restart notifications, page 1 DNS Domain Configuration, page 2 IM and Presence Service Default Domain Configuration, page 6 IM Address Configuration, page 7 Domain Management
Configuring Apache HTTP Server With Pramati
 Configuring Apache HTTP Server With Pramati 45 A general practice often seen in development environments is to have a web server to cater to the static pages and use the application server to deal with
Configuring Apache HTTP Server With Pramati 45 A general practice often seen in development environments is to have a web server to cater to the static pages and use the application server to deal with
Building a Highly Available and Scalable Web Farm
 Page 1 of 10 MSDN Home > MSDN Library > Deployment Rate this page: 10 users 4.9 out of 5 Building a Highly Available and Scalable Web Farm Duwamish Online Paul Johns and Aaron Ching Microsoft Developer
Page 1 of 10 MSDN Home > MSDN Library > Deployment Rate this page: 10 users 4.9 out of 5 Building a Highly Available and Scalable Web Farm Duwamish Online Paul Johns and Aaron Ching Microsoft Developer
Apache Tomcat. Load-balancing and Clustering. Mark Thomas, 20 November 2014. 2014 Pivotal Software, Inc. All rights reserved.
 2 Apache Tomcat Load-balancing and Clustering Mark Thomas, 20 November 2014 Introduction Apache Tomcat committer since December 2003 [email protected] Tomcat 8 release manager Member of the Servlet, WebSocket
2 Apache Tomcat Load-balancing and Clustering Mark Thomas, 20 November 2014 Introduction Apache Tomcat committer since December 2003 [email protected] Tomcat 8 release manager Member of the Servlet, WebSocket
Chapter 2 TOPOLOGY SELECTION. SYS-ED/ Computer Education Techniques, Inc.
 Chapter 2 TOPOLOGY SELECTION SYS-ED/ Computer Education Techniques, Inc. Objectives You will learn: Topology selection criteria. Perform a comparison of topology selection criteria. WebSphere component
Chapter 2 TOPOLOGY SELECTION SYS-ED/ Computer Education Techniques, Inc. Objectives You will learn: Topology selection criteria. Perform a comparison of topology selection criteria. WebSphere component
Configuring VIP and Virtual IP Interface Redundancy
 CHAPTER 6 Configuring VIP and Virtual IP Interface Redundancy This chapter describes how to plan for and configure Virtual IP (VIP) and Virtual IP Interface Redundancy on the CSS. Information in this chapter
CHAPTER 6 Configuring VIP and Virtual IP Interface Redundancy This chapter describes how to plan for and configure Virtual IP (VIP) and Virtual IP Interface Redundancy on the CSS. Information in this chapter
HP Load Balancing Module
 HP Load Balancing Module Load Balancing Configuration Guide Part number: 5998-2685 Document version: 6PW101-20120217 Legal and notice information Copyright 2012 Hewlett-Packard Development Company, L.P.
HP Load Balancing Module Load Balancing Configuration Guide Part number: 5998-2685 Document version: 6PW101-20120217 Legal and notice information Copyright 2012 Hewlett-Packard Development Company, L.P.
Implementing, Managing, and Maintaining a Microsoft Windows Server 2003 Network Infrastructure
 Question Number (ID) : 1 (jaamsp_mngnwi-025) Lisa would like to configure five of her 15 Web servers, which are running Microsoft Windows Server 2003, Web Edition, to always receive specific IP addresses
Question Number (ID) : 1 (jaamsp_mngnwi-025) Lisa would like to configure five of her 15 Web servers, which are running Microsoft Windows Server 2003, Web Edition, to always receive specific IP addresses
Oracle Collaboration Suite
 Oracle Collaboration Suite Firewall and Load Balancer Architecture Release 2 (9.0.4) Part No. B15609-01 November 2004 This document discusses the use of firewall and load balancer components with Oracle
Oracle Collaboration Suite Firewall and Load Balancer Architecture Release 2 (9.0.4) Part No. B15609-01 November 2004 This document discusses the use of firewall and load balancer components with Oracle
Virtualization Technologies and Blackboard: The Future of Blackboard Software on Multi-Core Technologies
 Virtualization Technologies and Blackboard: The Future of Blackboard Software on Multi-Core Technologies Kurt Klemperer, Principal System Performance Engineer [email protected] Agenda Session Length:
Virtualization Technologies and Blackboard: The Future of Blackboard Software on Multi-Core Technologies Kurt Klemperer, Principal System Performance Engineer [email protected] Agenda Session Length:
Load Balancing and Sessions. C. Kopparapu, Load Balancing Servers, Firewalls and Caches. Wiley, 2002.
 Load Balancing and Sessions C. Kopparapu, Load Balancing Servers, Firewalls and Caches. Wiley, 2002. Scalability multiple servers Availability server fails Manageability Goals do not route to it take servers
Load Balancing and Sessions C. Kopparapu, Load Balancing Servers, Firewalls and Caches. Wiley, 2002. Scalability multiple servers Availability server fails Manageability Goals do not route to it take servers
Content Switching Module for the Catalyst 6500 and Cisco 7600 Internet Router
 Content Switching Module for the Catalyst 6500 and Cisco 7600 Internet Router Product Overview The Cisco Content Switching Module (CSM) is a Catalyst 6500 line card that balances client traffic to farms
Content Switching Module for the Catalyst 6500 and Cisco 7600 Internet Router Product Overview The Cisco Content Switching Module (CSM) is a Catalyst 6500 line card that balances client traffic to farms
CS514: Intermediate Course in Computer Systems
 : Intermediate Course in Computer Systems Lecture 7: Sept. 19, 2003 Load Balancing Options Sources Lots of graphics and product description courtesy F5 website (www.f5.com) I believe F5 is market leader
: Intermediate Course in Computer Systems Lecture 7: Sept. 19, 2003 Load Balancing Options Sources Lots of graphics and product description courtesy F5 website (www.f5.com) I believe F5 is market leader
Fundamentals of Windows Server 2008 Network and Applications Infrastructure
 Fundamentals of Windows Server 2008 Network and Applications Infrastructure MOC6420 About this Course This five-day instructor-led course introduces students to network and applications infrastructure
Fundamentals of Windows Server 2008 Network and Applications Infrastructure MOC6420 About this Course This five-day instructor-led course introduces students to network and applications infrastructure
Internetworking Microsoft TCP/IP on Microsoft Windows NT 4.0
 Internetworking Microsoft TCP/IP on Microsoft Windows NT 4.0 Course length: 5 Days Course No. 688 - Five days - Instructor-led Introduction This course provides students with the knowledge and skills required
Internetworking Microsoft TCP/IP on Microsoft Windows NT 4.0 Course length: 5 Days Course No. 688 - Five days - Instructor-led Introduction This course provides students with the knowledge and skills required
Configuring the BIG-IP and Check Point VPN-1 /FireWall-1
 Configuring the BIG-IP and Check Point VPN-1 /FireWall-1 Introducing the BIG-IP and Check Point VPN-1/FireWall-1 LB, HALB, VPN, and ELA configurations Configuring the BIG-IP and Check Point FireWall-1
Configuring the BIG-IP and Check Point VPN-1 /FireWall-1 Introducing the BIG-IP and Check Point VPN-1/FireWall-1 LB, HALB, VPN, and ELA configurations Configuring the BIG-IP and Check Point FireWall-1
ZEN LOAD BALANCER EE v3.04 DATASHEET The Load Balancing made easy
 ZEN LOAD BALANCER EE v3.04 DATASHEET The Load Balancing made easy OVERVIEW The global communication and the continuous growth of services provided through the Internet or local infrastructure require to
ZEN LOAD BALANCER EE v3.04 DATASHEET The Load Balancing made easy OVERVIEW The global communication and the continuous growth of services provided through the Internet or local infrastructure require to
Understanding Slow Start
 Chapter 1 Load Balancing 57 Understanding Slow Start When you configure a NetScaler to use a metric-based LB method such as Least Connections, Least Response Time, Least Bandwidth, Least Packets, or Custom
Chapter 1 Load Balancing 57 Understanding Slow Start When you configure a NetScaler to use a metric-based LB method such as Least Connections, Least Response Time, Least Bandwidth, Least Packets, or Custom
INUVIKA TECHNICAL GUIDE
 --------------------------------------------------------------------------------------------------- INUVIKA TECHNICAL GUIDE FILE SERVER HIGH AVAILABILITY OVD Enterprise External Document Version 1.0 Published
--------------------------------------------------------------------------------------------------- INUVIKA TECHNICAL GUIDE FILE SERVER HIGH AVAILABILITY OVD Enterprise External Document Version 1.0 Published
PolyServe Understudy QuickStart Guide
 PolyServe Understudy QuickStart Guide PolyServe Understudy QuickStart Guide POLYSERVE UNDERSTUDY QUICKSTART GUIDE... 3 UNDERSTUDY SOFTWARE DISTRIBUTION & REGISTRATION... 3 Downloading an Evaluation Copy
PolyServe Understudy QuickStart Guide PolyServe Understudy QuickStart Guide POLYSERVE UNDERSTUDY QUICKSTART GUIDE... 3 UNDERSTUDY SOFTWARE DISTRIBUTION & REGISTRATION... 3 Downloading an Evaluation Copy
SiteCelerate white paper
 SiteCelerate white paper Arahe Solutions SITECELERATE OVERVIEW As enterprises increases their investment in Web applications, Portal and websites and as usage of these applications increase, performance
SiteCelerate white paper Arahe Solutions SITECELERATE OVERVIEW As enterprises increases their investment in Web applications, Portal and websites and as usage of these applications increase, performance
vcloud Director User's Guide
 vcloud Director 5.5 This document supports the version of each product listed and supports all subsequent versions until the document is replaced by a new edition. To check for more recent editions of
vcloud Director 5.5 This document supports the version of each product listed and supports all subsequent versions until the document is replaced by a new edition. To check for more recent editions of
S y s t e m A r c h i t e c t u r e
 S y s t e m A r c h i t e c t u r e V e r s i o n 5. 0 Page 1 Enterprise etime automates and streamlines the management, collection, and distribution of employee hours, and eliminates the use of manual
S y s t e m A r c h i t e c t u r e V e r s i o n 5. 0 Page 1 Enterprise etime automates and streamlines the management, collection, and distribution of employee hours, and eliminates the use of manual
Configuring Nex-Gen Web Load Balancer
 Configuring Nex-Gen Web Load Balancer Table of Contents Load Balancing Scenarios & Concepts Creating Load Balancer Node using Administration Service Creating Load Balancer Node using NodeCreator Connecting
Configuring Nex-Gen Web Load Balancer Table of Contents Load Balancing Scenarios & Concepts Creating Load Balancer Node using Administration Service Creating Load Balancer Node using NodeCreator Connecting
Implementing a Weblogic Architecture with High Availability
 Implementing a Weblogic Architecture with High Availability Contents 1. Introduction... 3 2. Topology... 3 2.1. Limitations... 3 2.2. Servers diagram... 4 2.3. Weblogic diagram... 4 3. Components... 6
Implementing a Weblogic Architecture with High Availability Contents 1. Introduction... 3 2. Topology... 3 2.1. Limitations... 3 2.2. Servers diagram... 4 2.3. Weblogic diagram... 4 3. Components... 6
Chapter 3. Internet Applications and Network Programming
 Chapter 3 Internet Applications and Network Programming 1 Introduction The Internet offers users a rich diversity of services none of the services is part of the underlying communication infrastructure
Chapter 3 Internet Applications and Network Programming 1 Introduction The Internet offers users a rich diversity of services none of the services is part of the underlying communication infrastructure
IM and Presence Service Network Setup
 Configuration changes and service restart notifications, page 1 Domain Value Configuration, page 2 Routing Information Configuration on IM and Presence Service, page 3 Configure Proxy Server Settings,
Configuration changes and service restart notifications, page 1 Domain Value Configuration, page 2 Routing Information Configuration on IM and Presence Service, page 3 Configure Proxy Server Settings,
Aqua Connect Load Balancer User Manual (Mac)
 Aqua Connect Load Balancer User Manual (Mac) Table of Contents About Aqua Connect Load Balancer... 3 System Requirements... 4 Hardware... 4 Software... 4 Installing the Load Balancer... 5 Configuration...
Aqua Connect Load Balancer User Manual (Mac) Table of Contents About Aqua Connect Load Balancer... 3 System Requirements... 4 Hardware... 4 Software... 4 Installing the Load Balancer... 5 Configuration...
LOAD BALANCING TECHNIQUES FOR RELEASE 11i AND RELEASE 12 E-BUSINESS ENVIRONMENTS
 LOAD BALANCING TECHNIQUES FOR RELEASE 11i AND RELEASE 12 E-BUSINESS ENVIRONMENTS Venkat Perumal IT Convergence Introduction Any application server based on a certain CPU, memory and other configurations
LOAD BALANCING TECHNIQUES FOR RELEASE 11i AND RELEASE 12 E-BUSINESS ENVIRONMENTS Venkat Perumal IT Convergence Introduction Any application server based on a certain CPU, memory and other configurations
PATROL Console Server and RTserver Getting Started
 PATROL Console Server and RTserver Getting Started Supporting PATROL Console Server 7.5.00 RTserver 6.6.00 February 14, 2005 Contacting BMC Software You can access the BMC Software website at http://www.bmc.com.
PATROL Console Server and RTserver Getting Started Supporting PATROL Console Server 7.5.00 RTserver 6.6.00 February 14, 2005 Contacting BMC Software You can access the BMC Software website at http://www.bmc.com.
Installing and Using the vnios Trial
 Installing and Using the vnios Trial The vnios Trial is a software package designed for efficient evaluation of the Infoblox vnios appliance platform. Providing the complete suite of DNS, DHCP and IPAM
Installing and Using the vnios Trial The vnios Trial is a software package designed for efficient evaluation of the Infoblox vnios appliance platform. Providing the complete suite of DNS, DHCP and IPAM
Exploring Oracle E-Business Suite Load Balancing Options. Venkat Perumal IT Convergence
 Exploring Oracle E-Business Suite Load Balancing Options Venkat Perumal IT Convergence Objectives Overview of 11i load balancing techniques Load balancing architecture Scenarios to implement Load Balancing
Exploring Oracle E-Business Suite Load Balancing Options Venkat Perumal IT Convergence Objectives Overview of 11i load balancing techniques Load balancing architecture Scenarios to implement Load Balancing
Oracle EXAM - 1Z0-102. Oracle Weblogic Server 11g: System Administration I. Buy Full Product. http://www.examskey.com/1z0-102.html
 Oracle EXAM - 1Z0-102 Oracle Weblogic Server 11g: System Administration I Buy Full Product http://www.examskey.com/1z0-102.html Examskey Oracle 1Z0-102 exam demo product is here for you to test the quality
Oracle EXAM - 1Z0-102 Oracle Weblogic Server 11g: System Administration I Buy Full Product http://www.examskey.com/1z0-102.html Examskey Oracle 1Z0-102 exam demo product is here for you to test the quality
Detecting rogue systems
 Product Guide Revision A McAfee Rogue System Detection 4.7.1 For use with epolicy Orchestrator 4.6.3-5.0.0 Software Detecting rogue systems Unprotected systems, referred to as rogue systems, are often
Product Guide Revision A McAfee Rogue System Detection 4.7.1 For use with epolicy Orchestrator 4.6.3-5.0.0 Software Detecting rogue systems Unprotected systems, referred to as rogue systems, are often
CS312 Solutions #6. March 13, 2015
 CS312 Solutions #6 March 13, 2015 Solutions 1. (1pt) Define in detail what a load balancer is and what problem it s trying to solve. Give at least two examples of where using a load balancer might be useful,
CS312 Solutions #6 March 13, 2015 Solutions 1. (1pt) Define in detail what a load balancer is and what problem it s trying to solve. Give at least two examples of where using a load balancer might be useful,
TECHNICAL NOTE. Technical Note P/N 300-999-649 REV 03. EMC NetWorker Simplifying firewall port requirements with NSR tunnel Release 8.
 TECHNICAL NOTE EMC NetWorker Simplifying firewall port requirements with NSR tunnel Release 8.0 and later Technical Note P/N 300-999-649 REV 03 February 6, 2014 This technical note describes how to configure
TECHNICAL NOTE EMC NetWorker Simplifying firewall port requirements with NSR tunnel Release 8.0 and later Technical Note P/N 300-999-649 REV 03 February 6, 2014 This technical note describes how to configure
> Technical Configuration Guide for Microsoft Network Load Balancing. Ethernet Switch and Ethernet Routing Switch Engineering
 Ethernet Switch and Ethernet Routing Switch Engineering > Technical Configuration Guide for Microsoft Network Load Balancing Enterprise Solutions Engineering Document Date: March 9, 2006 Document Version:
Ethernet Switch and Ethernet Routing Switch Engineering > Technical Configuration Guide for Microsoft Network Load Balancing Enterprise Solutions Engineering Document Date: March 9, 2006 Document Version:
Creating a DUO MFA Service in AWS
 Amazon AWS is a cloud based development environment with a goal to provide many options to companies wishing to leverage the power and convenience of cloud computing within their organisation. In 2013
Amazon AWS is a cloud based development environment with a goal to provide many options to companies wishing to leverage the power and convenience of cloud computing within their organisation. In 2013
Guideline for setting up a functional VPN
 Guideline for setting up a functional VPN Why do I want a VPN? VPN by definition creates a private, trusted network across an untrusted medium. It allows you to connect offices and people from around the
Guideline for setting up a functional VPN Why do I want a VPN? VPN by definition creates a private, trusted network across an untrusted medium. It allows you to connect offices and people from around the
Configuring HAproxy as a SwiftStack Load Balancer
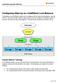 Configuring HAproxy as a SwiftStack Load Balancer To illustrate how a SwiftStack cluster can be configured with an external load balancer, such as HAProxy, let s walk through a step-by-step example of
Configuring HAproxy as a SwiftStack Load Balancer To illustrate how a SwiftStack cluster can be configured with an external load balancer, such as HAProxy, let s walk through a step-by-step example of
ExamPDF. Higher Quality,Better service!
 ExamPDF Higher Quality,Better service! Q&A Exam : 1Y0-A21 Title : Basic Administration for Citrix NetScaler 9.2 Version : Demo 1 / 5 1.Scenario: An administrator is working with a Citrix consultant to
ExamPDF Higher Quality,Better service! Q&A Exam : 1Y0-A21 Title : Basic Administration for Citrix NetScaler 9.2 Version : Demo 1 / 5 1.Scenario: An administrator is working with a Citrix consultant to
Veritas Cluster Server
 APPENDIXE This module provides basic guidelines for the (VCS) configuration in a Subscriber Manager (SM) cluster installation. It assumes basic knowledge of the VCS environment; it does not replace the
APPENDIXE This module provides basic guidelines for the (VCS) configuration in a Subscriber Manager (SM) cluster installation. It assumes basic knowledge of the VCS environment; it does not replace the
AS/400e. TCP/IP routing and workload balancing
 AS/400e TCP/IP routing and workload balancing AS/400e TCP/IP routing and workload balancing Copyright International Business Machines Corporation 2000. All rights reserved. US Government Users Restricted
AS/400e TCP/IP routing and workload balancing AS/400e TCP/IP routing and workload balancing Copyright International Business Machines Corporation 2000. All rights reserved. US Government Users Restricted
Chapter 6 Configuring the SSL VPN Tunnel Client and Port Forwarding
 Chapter 6 Configuring the SSL VPN Tunnel Client and Port Forwarding This chapter describes the configuration for the SSL VPN Tunnel Client and for Port Forwarding. When a remote user accesses the SSL VPN
Chapter 6 Configuring the SSL VPN Tunnel Client and Port Forwarding This chapter describes the configuration for the SSL VPN Tunnel Client and for Port Forwarding. When a remote user accesses the SSL VPN
FioranoMQ 9. High Availability Guide
 FioranoMQ 9 High Availability Guide Copyright (c) 1999-2008, Fiorano Software Technologies Pvt. Ltd., Copyright (c) 2008-2009, Fiorano Software Pty. Ltd. All rights reserved. This software is the confidential
FioranoMQ 9 High Availability Guide Copyright (c) 1999-2008, Fiorano Software Technologies Pvt. Ltd., Copyright (c) 2008-2009, Fiorano Software Pty. Ltd. All rights reserved. This software is the confidential
2 Downloading Access Manager 3.1 SP4 IR1
 Novell Access Manager 3.1 SP4 IR1 Readme May 2012 Novell This Readme describes the Novell Access Manager 3.1 SP4 IR1 release. Section 1, Documentation, on page 1 Section 2, Downloading Access Manager 3.1
Novell Access Manager 3.1 SP4 IR1 Readme May 2012 Novell This Readme describes the Novell Access Manager 3.1 SP4 IR1 release. Section 1, Documentation, on page 1 Section 2, Downloading Access Manager 3.1
ERserver. iseries. TCP/IP routing and workload balancing
 ERserver iseries TCP/IP routing and workload balancing ERserver iseries TCP/IP routing and workload balancing Copyright International Business Machines Corporation 1998, 2001. All rights reserved. US
ERserver iseries TCP/IP routing and workload balancing ERserver iseries TCP/IP routing and workload balancing Copyright International Business Machines Corporation 1998, 2001. All rights reserved. US
Step-by-Step Guide. to configure Open-E DSS V7 Active-Active iscsi Failover on Intel Server Systems R2224GZ4GC4. Software Version: DSS ver. 7.
 Step-by-Step Guide to configure on Intel Server Systems R2224GZ4GC4 Software Version: DSS ver. 7.00 up01 Presentation updated: April 2013 www.open-e.com 1 www.open-e.com 2 TECHNICAL SPECIFICATIONS OF THE
Step-by-Step Guide to configure on Intel Server Systems R2224GZ4GC4 Software Version: DSS ver. 7.00 up01 Presentation updated: April 2013 www.open-e.com 1 www.open-e.com 2 TECHNICAL SPECIFICATIONS OF THE
CS 348: Computer Networks. - IP addressing; 21 st Aug 2012. Instructor: Sridhar Iyer IIT Bombay
 CS 348: Computer Networks - IP addressing; 21 st Aug 2012 Instructor: Sridhar Iyer IIT Bombay Think-Pair-Share: IP addressing What is the need for IP addresses? Why not have only MAC addresses? Given that
CS 348: Computer Networks - IP addressing; 21 st Aug 2012 Instructor: Sridhar Iyer IIT Bombay Think-Pair-Share: IP addressing What is the need for IP addresses? Why not have only MAC addresses? Given that
DB2 Connect for NT and the Microsoft Windows NT Load Balancing Service
 DB2 Connect for NT and the Microsoft Windows NT Load Balancing Service Achieving Scalability and High Availability Abstract DB2 Connect Enterprise Edition for Windows NT provides fast and robust connectivity
DB2 Connect for NT and the Microsoft Windows NT Load Balancing Service Achieving Scalability and High Availability Abstract DB2 Connect Enterprise Edition for Windows NT provides fast and robust connectivity
How To Configure Apa Web Server For High Performance
 DEPLOYMENT GUIDE Version 1.0 Deploying F5 with Apache Web Servers Table of Contents Table of Contents Deploying the BIG-IP LTM with the Apache web server Prerequisites and configuration notes... 1 Product
DEPLOYMENT GUIDE Version 1.0 Deploying F5 with Apache Web Servers Table of Contents Table of Contents Deploying the BIG-IP LTM with the Apache web server Prerequisites and configuration notes... 1 Product
BlackBerry Enterprise Server for Microsoft Exchange Version: 5.0 Service Pack: 2. Feature and Technical Overview
 BlackBerry Enterprise Server for Microsoft Exchange Version: 5.0 Service Pack: 2 Feature and Technical Overview Published: 2010-06-16 SWDT305802-1108946-0615123042-001 Contents 1 Overview: BlackBerry Enterprise
BlackBerry Enterprise Server for Microsoft Exchange Version: 5.0 Service Pack: 2 Feature and Technical Overview Published: 2010-06-16 SWDT305802-1108946-0615123042-001 Contents 1 Overview: BlackBerry Enterprise
BlackBerry Enterprise Service 10. Secure Work Space for ios and Android Version: 10.1.1. Security Note
 BlackBerry Enterprise Service 10 Secure Work Space for ios and Android Version: 10.1.1 Security Note Published: 2013-06-21 SWD-20130621110651069 Contents 1 About this guide...4 2 What is BlackBerry Enterprise
BlackBerry Enterprise Service 10 Secure Work Space for ios and Android Version: 10.1.1 Security Note Published: 2013-06-21 SWD-20130621110651069 Contents 1 About this guide...4 2 What is BlackBerry Enterprise
FAQs for Oracle iplanet Proxy Server 4.0
 FAQs for Oracle iplanet Proxy Server 4.0 Get answers to the questions most frequently asked about Oracle iplanet Proxy Server Q: What is Oracle iplanet Proxy Server (Java System Web Proxy Server)? A: Oracle
FAQs for Oracle iplanet Proxy Server 4.0 Get answers to the questions most frequently asked about Oracle iplanet Proxy Server Q: What is Oracle iplanet Proxy Server (Java System Web Proxy Server)? A: Oracle
cnds@napier Slide 1 Introduction cnds@napier 1 Lecture 6 (Network Layer)
 Slide 1 Introduction In today s and next week s lecture we will cover two of the most important areas in networking and the Internet: IP and TCP. These cover the network and transport layer of the OSI
Slide 1 Introduction In today s and next week s lecture we will cover two of the most important areas in networking and the Internet: IP and TCP. These cover the network and transport layer of the OSI
Network setup and troubleshooting
 ACTi Knowledge Base Category: Troubleshooting Note Sub-category: Network Model: All Firmware: All Software: NVR Author: Jane.Chen Published: 2009/12/21 Reviewed: 2010/10/11 Network setup and troubleshooting
ACTi Knowledge Base Category: Troubleshooting Note Sub-category: Network Model: All Firmware: All Software: NVR Author: Jane.Chen Published: 2009/12/21 Reviewed: 2010/10/11 Network setup and troubleshooting
VERITAS Cluster Server Traffic Director Option. Product Overview
 VERITAS Cluster Server Traffic Director Option Product Overview V E R I T A S W H I T E P A P E R Table of Contents Traffic Director Option for VERITAS Cluster Server Overview.............................................1
VERITAS Cluster Server Traffic Director Option Product Overview V E R I T A S W H I T E P A P E R Table of Contents Traffic Director Option for VERITAS Cluster Server Overview.............................................1
Course Syllabus. Fundamentals of Windows Server 2008 Network and Applications Infrastructure. Key Data. Audience. Prerequisites. At Course Completion
 Key Data Product #: 3380 Course #: 6420A Number of Days: 5 Format: Certification Exams: Instructor-Led None This course syllabus should be used to determine whether the course is appropriate for the students,
Key Data Product #: 3380 Course #: 6420A Number of Days: 5 Format: Certification Exams: Instructor-Led None This course syllabus should be used to determine whether the course is appropriate for the students,
1. LAB SNIFFING LAB ID: 10
 H E R A LAB ID: 10 SNIFFING Sniffing in a switched network ARP Poisoning Analyzing a network traffic Extracting files from a network trace Stealing credentials Mapping/exploring network resources 1. LAB
H E R A LAB ID: 10 SNIFFING Sniffing in a switched network ARP Poisoning Analyzing a network traffic Extracting files from a network trace Stealing credentials Mapping/exploring network resources 1. LAB
GlobalSCAPE DMZ Gateway, v1. User Guide
 GlobalSCAPE DMZ Gateway, v1 User Guide GlobalSCAPE, Inc. (GSB) Address: 4500 Lockhill-Selma Road, Suite 150 San Antonio, TX (USA) 78249 Sales: (210) 308-8267 Sales (Toll Free): (800) 290-5054 Technical
GlobalSCAPE DMZ Gateway, v1 User Guide GlobalSCAPE, Inc. (GSB) Address: 4500 Lockhill-Selma Road, Suite 150 San Antonio, TX (USA) 78249 Sales: (210) 308-8267 Sales (Toll Free): (800) 290-5054 Technical
Quick Start for Network Agent. 5-Step Quick Start. What is Network Agent?
 What is Network Agent? Websense Network Agent software monitors all internet traffic on the machines that you assign to it. Network Agent filters HTTP traffic and more than 70 other popular internet protocols,
What is Network Agent? Websense Network Agent software monitors all internet traffic on the machines that you assign to it. Network Agent filters HTTP traffic and more than 70 other popular internet protocols,
Break Internet Bandwidth Limits Higher Speed. Extreme Reliability. Reduced Cost.
 Break Internet Bandwidth Limits Higher Speed. Extreme Reliability. Reduced Cost. Peplink. All Rights Reserved. Unauthorized Reproduction Prohibited Presentation Agenda Peplink Balance Pepwave MAX Features
Break Internet Bandwidth Limits Higher Speed. Extreme Reliability. Reduced Cost. Peplink. All Rights Reserved. Unauthorized Reproduction Prohibited Presentation Agenda Peplink Balance Pepwave MAX Features
OVERVIEW OF TYPICAL WINDOWS SERVER ROLES
 OVERVIEW OF TYPICAL WINDOWS SERVER ROLES Before you start Objectives: learn about common server roles which can be used in Windows environment. Prerequisites: no prerequisites. Key terms: network, server,
OVERVIEW OF TYPICAL WINDOWS SERVER ROLES Before you start Objectives: learn about common server roles which can be used in Windows environment. Prerequisites: no prerequisites. Key terms: network, server,
Using WhatsUp IP Address Manager 1.0
 Using WhatsUp IP Address Manager 1.0 Contents Table of Contents Welcome to WhatsUp IP Address Manager Finding more information and updates... 1 Sending feedback... 2 Installing and Licensing IP Address
Using WhatsUp IP Address Manager 1.0 Contents Table of Contents Welcome to WhatsUp IP Address Manager Finding more information and updates... 1 Sending feedback... 2 Installing and Licensing IP Address
ilinc Web Conferencing
 system architecture overview introduction ilinc is a suite of Web conferencing products designed to allow participants to interact and collaborate online in a number of different types of sessions, including
system architecture overview introduction ilinc is a suite of Web conferencing products designed to allow participants to interact and collaborate online in a number of different types of sessions, including
DATA CENTER. Best Practices for High Availability Deployment for the Brocade ADX Switch
 DATA CENTER Best Practices for High Availability Deployment for the Brocade ADX Switch CONTENTS Contents... 2 Executive Summary... 3 Introduction... 3 Brocade ADX HA Overview... 3 Hot-Standby HA... 4 Active-Standby
DATA CENTER Best Practices for High Availability Deployment for the Brocade ADX Switch CONTENTS Contents... 2 Executive Summary... 3 Introduction... 3 Brocade ADX HA Overview... 3 Hot-Standby HA... 4 Active-Standby
Network Agent Quick Start
 Network Agent Quick Start Topic 50500 Network Agent Quick Start Updated 17-Sep-2013 Applies To: Web Filter, Web Security, Web Security Gateway, and Web Security Gateway Anywhere, v7.7 and 7.8 Websense
Network Agent Quick Start Topic 50500 Network Agent Quick Start Updated 17-Sep-2013 Applies To: Web Filter, Web Security, Web Security Gateway, and Web Security Gateway Anywhere, v7.7 and 7.8 Websense
Server Traffic Management. Jeff Chase Duke University, Department of Computer Science CPS 212: Distributed Information Systems
 Server Traffic Management Jeff Chase Duke University, Department of Computer Science CPS 212: Distributed Information Systems The Server Selection Problem server array A server farm B Which server? Which
Server Traffic Management Jeff Chase Duke University, Department of Computer Science CPS 212: Distributed Information Systems The Server Selection Problem server array A server farm B Which server? Which
WebAccelerator Administration Guide
 WebAccelerator version 5.1 MAN-0206-00 Service and Support Information Product Version This manual applies to product version 5.1 of the WebAccelerator. Legal Notices Copyright Copyright 2005, F5 Networks,
WebAccelerator version 5.1 MAN-0206-00 Service and Support Information Product Version This manual applies to product version 5.1 of the WebAccelerator. Legal Notices Copyright Copyright 2005, F5 Networks,
PLUMgrid Toolbox: Tools to Install, Operate and Monitor Your Virtual Network Infrastructure
 Toolbox: Tools to Install, Operate and Monitor Your Virtual Network Infrastructure Introduction The concept of Virtual Networking Infrastructure (VNI) is disrupting the networking space and is enabling
Toolbox: Tools to Install, Operate and Monitor Your Virtual Network Infrastructure Introduction The concept of Virtual Networking Infrastructure (VNI) is disrupting the networking space and is enabling
Cisco AnyConnect Secure Mobility Solution Guide
 Cisco AnyConnect Secure Mobility Solution Guide This document contains the following information: Cisco AnyConnect Secure Mobility Overview, page 1 Understanding How AnyConnect Secure Mobility Works, page
Cisco AnyConnect Secure Mobility Solution Guide This document contains the following information: Cisco AnyConnect Secure Mobility Overview, page 1 Understanding How AnyConnect Secure Mobility Works, page
CheckPoint Software Technologies LTD. How to Configure Firewall-1 With Connect Control
 CheckPoint Software Technologies LTD. How to Configure Firewall-1 With Connect Control (Load-Balance across multiple servers) Event: Partner Exchange Conference Date: October 10, 1999 Revision 1.0 Author:
CheckPoint Software Technologies LTD. How to Configure Firewall-1 With Connect Control (Load-Balance across multiple servers) Event: Partner Exchange Conference Date: October 10, 1999 Revision 1.0 Author:
VERITAS Cluster Server v2.0 Technical Overview
 VERITAS Cluster Server v2.0 Technical Overview V E R I T A S W H I T E P A P E R Table of Contents Executive Overview............................................................................1 Why VERITAS
VERITAS Cluster Server v2.0 Technical Overview V E R I T A S W H I T E P A P E R Table of Contents Executive Overview............................................................................1 Why VERITAS
Setting Up B2B Data Exchange for High Availability in an Active/Active Configuration
 Setting Up B2B Data Exchange for High Availability in an Active/Active Configuration 2010 Informatica Abstract This document explains how to install multiple copies of B2B Data Exchange on a single computer.
Setting Up B2B Data Exchange for High Availability in an Active/Active Configuration 2010 Informatica Abstract This document explains how to install multiple copies of B2B Data Exchange on a single computer.
The SSL device also supports the 64-bit Internet Explorer with new ActiveX loaders for Assessment, Abolishment, and the Access Client.
 WatchGuard SSL v3.2 Release Notes Supported Devices SSL 100 and 560 WatchGuard SSL OS Build 355419 Revision Date January 28, 2013 Introduction WatchGuard is pleased to announce the release of WatchGuard
WatchGuard SSL v3.2 Release Notes Supported Devices SSL 100 and 560 WatchGuard SSL OS Build 355419 Revision Date January 28, 2013 Introduction WatchGuard is pleased to announce the release of WatchGuard
High Availability Low Dollar Load Balancing
 High Availability Low Dollar Load Balancing Simon Karpen System Architect, VoiceThread [email protected] Via Karpen Internet Systems [email protected] These slides are licensed under the
High Availability Low Dollar Load Balancing Simon Karpen System Architect, VoiceThread [email protected] Via Karpen Internet Systems [email protected] These slides are licensed under the
