SecureIT Plus Firewall Features and Functionality
|
|
|
- Frederica Henderson
- 8 years ago
- Views:
Transcription
1 SecureIT Plus Firewall Features and Functionality Iowa Network Services SecureIT Plus Firewall Page 1 of 11
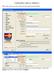
2 1.1 Enabling Firewall Main Settings Once you have installed the firewall and have rebooted your computer, right click on the padlock icon in the lower right hand corner and choose Open SecureIT Management Console. Once the management console opens, you will notice there is a new section on the left under Settings called Firewall Settings. Clicking Firewall Settings will open a screen that looks like the following (see figure 1-1). Figure 1-1 You will see that the Enable Firewall option is enabled (checked) and the High Security Mode Block All option is disabled (unchecked). The other three options Startup Protection, Enable Stealth Browsing, and Prevent Firewall Tampering are features that will be available for future releases of the firewall. However, for the beta version, these features will be unavailable and grayed out. You will also see three tabs on this screen called Main, Zones, and Traffic Management Zones Clicking on the Zones tab will open a screen that looks like the following (see figure 1-2). Iowa Network Services SecureIT Plus Firewall Page 2 of 11
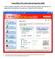
3 Figure 1-2 In the box where it states Firewall Zones, you will have all IP addresses listed for all network adapters on that machine, their connection type, and the zone that those adapters are in. By default, all network adapters that are detected get placed into the Internet zone. If you click on the dropdown menu next to where it states Change selected adapter to zone, you will see the following zones: Trusted, Internet and Blocked. An explanation of these zones follows: Trusted This is the safe zone. It contains all of the computers and networks that are trusted and that you want to share resources with (i.e. the other machines on your local or home network). By default, this is the zone that all network adapters will be in after installing the firewall. In this zone, all communication, both inbound and outbound, is allowed and the machine is fully visible to the outside world. Internet This is the unknown zone. All of the computers and networks in the world belong to this zone until they are moved either through the software or through manual rule creation. Here you will still have full access to the Internet, but you will be hidden from the outside world. In the Traffic Management tab, which we will talk about later, we can set custom rules to allow certain traffic from the Internet to be allowed by the firewall. Blocked This is a zone where all communication, both inbound and outbound, is blocked and the machine is completely hidden from the outside world. Another way to duplicate this is to enable High Security Mode. Once you change the zone, you will notice a message that appears in red in the upper right hand corner that states Settings have changed. This reminds you that that in order Iowa Network Services SecureIT Plus Firewall Page 3 of 11
4 for the changes that you just made to be saved, you will need to click on the Save Settings button before you click on Close. This message will appear throughout the firewall settings anytime you make a change in the configurations that require you to save the settings. Change the zone back to Trusted for now, and we will come back to the others later. Click on the Traffic Management tab, and you will see a screen that looks like the following (see figure 1-3) Traffic Management Figure 1-3 You will see two tabs here, Today s Blocked Traffic and Traffic Rules. Today s Blocked Traffic will show you the inbound and outbound communication that has been blocked by the firewall. Traffic Rules will show the rules that have been setup to allow or block certain traffic in communicating with this machine. Today s Blocked Traffic If you had your network adapter set in the Internet zone and went to another machine in the same network and tried to either ping or telnet to the IP address of the computer the firewall is installed on, the firewall would block that request. Let s say the IP address of computer1, which has the firewall enabled, was (as shown in figure 1-2). You have another computer, computer2, on the same network that has an IP address of Go to computer2 and type the following from a command prompt: telnet You will notice that this command will not work. If you go back to computer1 and click on the Today s Blocked Traffic tab and click the Refresh icon (the curved green Iowa Network Services SecureIT Plus Firewall Page 4 of 11
5 arrows in the lower right of that box), you will see the communication that was blocked from computer2 and will look similar to the next screen shown (see figure 1-4). Figure 1-4 Here, you will see the time the traffic was blocked, whether the communication was inbound or outbound, the protocol that was used, the IP address the traffic came from, and the port the traffic tried to communicate on. If you decided that you wanted this communication to happen, you would click the traffic listed that you wanted to allow, and then click the Add to Allowed Traffic button. Once this happens, a rule is automatically created to allow this traffic. You will see this by clicking on the Traffic Rules tab (see figure 1-5). Iowa Network Services SecureIT Plus Firewall Page 5 of 11
6 Figure 1-5 Here, you would see a rule was created to allow inbound TCP traffic from IP address on port 445. If you went back to computer2 and tried to run the telnet command again (telnet ), you will notice that the command would complete this time. Then if you went back to the computer1 and clicked Today s Blocked Traffic and clicked the refresh icon, there would be no new traffic that was blocked. Click on the Today s Blocked Traffic tab once again and you will notice there is a button at the bottom of the window called Clear Traffic. Due to the amount of communication that will be blocked and displayed in this window and how large this list will become, you can click on this button to clear the contents of this window. This would especially come in handy if you were trying to find out if a certain IP address or communication was being blocked by the firewall. Traffic Rules Another way to allow blocked traffic is to use the predefined rules that are included in the firewall. Let s say that you could not use your AOL Instant Messenger program because the traffic was being blocked, but you wanted to be able to use it. You would do the following: 1. Click on the Traffic Management tab 2. Click on the Traffic Rules tab 3. Click on the Add button You would see a screen that looks like the following (see figure 1-5) Iowa Network Services SecureIT Plus Firewall Page 6 of 11
7 Figure 1-5 You would pick AOL Instant Messenger from the dropdown list. You would then make sure that the Allow radial button is selected next to Define what action would you like to assign. Since all communication is already allowed outbound from the firewall due to the computer being in the Internet Zone, the only option for Direction for traffic is From and will already be selected for you. Next, set the IP range that you want to allow this traffic (by default this will be from to , which means all traffic will be able to communicate from this medium) and then click OK. You would now see a screen that looks similar to the following (see figure 1-6). Figure 1-6 Iowa Network Services SecureIT Plus Firewall Page 7 of 11
8 Here you will see the rule that you created would allow inbound traffic over a TCP connection from any IP address on port If at anytime you make a typo or need to edit the rule, you can simply click on the Edit button, which will open the screen in figure 1-5, and make your changes. Then click the OK button to save those changes. If you went back and launched your AOL Instant Messenger program, you will notice that it now works without a problem. In the cases where you would have a program that was not included in the list of predefined rules that accessed the Internet that you need to work, you would create a custom rule. You would do this by clicking on the Add button shown in figure 1-6 and clicking Custom. This would open a screen that would look like the following (see figure 1-7). Figure 1-7 Here you would give the custom rule a name, specify whether the program needs to communicate via a TCP or UDP protocol or both, and what the port range is that the program will need to communicate on. Once you are done, you would click the OK button. You will now see the custom protocol that you just created has been added to the dropdown list and is now highlighted. You would then also notice that the Delete button is now enabled, giving you the opportunity to delete custom protocols if they are no longer needed. This button can only be used to delete customized protocols, not the predefined protocols. Once your rules have been created, the arrows in the lower left of the window (shown in figure 1-6) are used to change the priority of the rule. The first rule that appears always takes precedence over the other rules even if the other rules are related. To change the priority, you would just click the rule that you wanted to move, and then click either the up or down arrow to move it up or down the priority list. Iowa Network Services SecureIT Plus Firewall Page 8 of 11
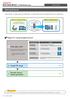
9 1.2 High Security Mode By clicking on the checkbox next to High Security Mode Block All, you will see the following box (see figure 1-8). Figure 1-8 Once you click OK on this box, you will set the firewall in High Security mode. When the firewall is set in High Security Mode, no traffic will be allowed outbound or inbound and the machine will be fully hidden from the outside world. All applications that need to communicate across the Internet will also no longer work. The only way for an application in this mode to communicate across the Internet, is for that application to be specifically allowed to access the Internet. NOTE: All SecureIT related services/processes and third party programs will still be allowed to communicate across the Internet and receive updates even in High Security mode. Program Control As you will notice in figure 1-9, a new tab appears once you put the firewall in High Security mode called Program Control. Clicking on this tab will open a screen that looks like the following (see figure 1-9). Iowa Network Services SecureIT Plus Firewall Page 9 of 11
10 Figure 1-9 You will notice two tabs, Today s Blocked Programs and Allowed Programs. Today s Blocked Programs will show a list of applications that were blocked that tried to communicate across the Internet while the firewall was in High Security Mode. Allowed Programs will show you a list of applications you have specifically added that you want to communicate across the Internet. Today s Blocked Programs For example, if you launch Internet Explorer while you are in High Security mode, you will notice the screen will open stating The page cannot be displayed. If you click the refresh icon in the lower right of the window (looks like two circulating green arrows and is shown in figure 1-9), you will see that there is now an application that shows up called iexplore.exe (see figure 1-10). Figure 1-10 This is the process name for Internet Explorer. If you wanted to set it up so you could use Internet Explorer and be able to view web pages, you would simply click on the iexplore.exe process that is listed in that window and click the Add to Programs button. Now if you launch Internet Explorer again, you will notice that your home page will open without a problem. You would repeat this process for all applications that you wanted to be able to access the Internet. If at any time you wanted to take all programs that appeared in Today s Blocked Programs and allow them to communicate across the Internet, you can click the Clear Programs button to do this. This may come in handy if the process being blocked is something you don t recognize but all of the sudden one of your applications stop functioning like it should. Allowed Programs Iowa Network Services SecureIT Plus Firewall Page 10 of 11
11 Clicking on the Allowed Programs tab will bring up a screen that looks like the following (see figure 1-11). Figure 1-11 This is a list of allowed programs that you have specified to allow communication across the Internet in High Security mode. If you completed the above steps, you would see iexplore.exe in the Allowed Programs list. There is also a Remove button that you can click on to remove a program that you no longer want to allow to communicate across the Internet. Iowa Network Services SecureIT Plus Firewall Page 11 of 11
Windows Firewall Configuration with Group Policy for SyAM System Client Installation
 with Group Policy for SyAM System Client Installation SyAM System Client can be deployed to systems on your network using SyAM Management Utilities. If Windows Firewall is enabled on target systems, it
with Group Policy for SyAM System Client Installation SyAM System Client can be deployed to systems on your network using SyAM Management Utilities. If Windows Firewall is enabled on target systems, it
How To: Configure a Cisco ASA 5505 for Video Conferencing
 How To: Configure a Cisco ASA 5505 for Video Conferencing There are five main items which will need to be addressed in order to successfully permit H.323 video conferencing traffic through the Cisco ASA.
How To: Configure a Cisco ASA 5505 for Video Conferencing There are five main items which will need to be addressed in order to successfully permit H.323 video conferencing traffic through the Cisco ASA.
10.3.1.8 Lab - Configure a Windows 7 Firewall
 5.0 10.3.1.8 Lab - Configure a Windows 7 Firewall Print and complete this lab. In this lab, you will explore the Windows 7 Firewall and configure some advanced settings. Recommended Equipment Step 1 Two
5.0 10.3.1.8 Lab - Configure a Windows 7 Firewall Print and complete this lab. In this lab, you will explore the Windows 7 Firewall and configure some advanced settings. Recommended Equipment Step 1 Two
10.3.1.9 Lab - Configure a Windows Vista Firewall
 5.0 10.3.1.9 Lab - Configure a Windows Vista Firewall Print and complete this lab. In this lab, you will explore the Windows Vista Firewall and configure some advanced settings. Recommended Equipment Step
5.0 10.3.1.9 Lab - Configure a Windows Vista Firewall Print and complete this lab. In this lab, you will explore the Windows Vista Firewall and configure some advanced settings. Recommended Equipment Step
How to Program a Commander or Scout to Connect to Pilot Software
 How to Program a Commander or Scout to Connect to Pilot Software Commander and Scout are monitoring and control products that can transfer physical environmental conditions and alarm sensor electrical
How to Program a Commander or Scout to Connect to Pilot Software Commander and Scout are monitoring and control products that can transfer physical environmental conditions and alarm sensor electrical
A-AUTO 50 for Windows Setup Guide
 A-AUTO 50 for Windows Setup Guide 1st Edition 1 A-AUTO is a registered trade mark of UNIRITA Inc. "This product includes software developed by the Apache Software Foundation (http://www.apache.org/)."
A-AUTO 50 for Windows Setup Guide 1st Edition 1 A-AUTO is a registered trade mark of UNIRITA Inc. "This product includes software developed by the Apache Software Foundation (http://www.apache.org/)."
ILTA HANDS ON Securing Windows 7
 Securing Windows 7 8/23/2011 Table of Contents About this lab... 3 About the Laboratory Environment... 4 Lab 1: Restricting Users... 5 Exercise 1. Verify the default rights of users... 5 Exercise 2. Adding
Securing Windows 7 8/23/2011 Table of Contents About this lab... 3 About the Laboratory Environment... 4 Lab 1: Restricting Users... 5 Exercise 1. Verify the default rights of users... 5 Exercise 2. Adding
How To Create An Easybelle History Database On A Microsoft Powerbook 2.5.2 (Windows)
 Introduction EASYLABEL 6 has several new features for saving the history of label formats. This history can include information about when label formats were edited and printed. In order to save this history,
Introduction EASYLABEL 6 has several new features for saving the history of label formats. This history can include information about when label formats were edited and printed. In order to save this history,
Note: With v3.2, the DocuSign Fetch application was renamed DocuSign Retrieve.
 Quick Start Guide DocuSign Retrieve 3.2.2 Published April 2015 Overview DocuSign Retrieve is a windows-based tool that "retrieves" envelopes, documents, and data from DocuSign for use in external systems.
Quick Start Guide DocuSign Retrieve 3.2.2 Published April 2015 Overview DocuSign Retrieve is a windows-based tool that "retrieves" envelopes, documents, and data from DocuSign for use in external systems.
How to set up popular firewalls to work with Web CEO
 How to set up popular firewalls to work with Web CEO Contents How to set up popular firewalls to work with Web CEO... 1 Setting up Agnitum Outpost Firewall 2.5... 2 Setting up Black ICE 3... 6 Setting
How to set up popular firewalls to work with Web CEO Contents How to set up popular firewalls to work with Web CEO... 1 Setting up Agnitum Outpost Firewall 2.5... 2 Setting up Black ICE 3... 6 Setting
USER CONFERENCE 2011 SAN FRANCISCO APRIL 26 29. Running MarkLogic in the Cloud DEVELOPER LOUNGE LAB
 USER CONFERENCE 2011 SAN FRANCISCO APRIL 26 29 Running MarkLogic in the Cloud DEVELOPER LOUNGE LAB Table of Contents UNIT 1: Lab description... 3 Pre-requisites:... 3 UNIT 2: Launching an instance on EC2...
USER CONFERENCE 2011 SAN FRANCISCO APRIL 26 29 Running MarkLogic in the Cloud DEVELOPER LOUNGE LAB Table of Contents UNIT 1: Lab description... 3 Pre-requisites:... 3 UNIT 2: Launching an instance on EC2...
ShadowControl ShadowStream
 ShadowControl ShadowStream Revision 1.3 4/12/2012 Table of Contents Introduction... 3 Download ShadowStream Server... 3 Installation... 4 Configuration... 5 Creating Users... 6 Testing the User Rights...
ShadowControl ShadowStream Revision 1.3 4/12/2012 Table of Contents Introduction... 3 Download ShadowStream Server... 3 Installation... 4 Configuration... 5 Creating Users... 6 Testing the User Rights...
XStream Remote Control: Configuring DCOM Connectivity
 XStream Remote Control: Configuring DCOM Connectivity APPLICATION BRIEF March 2009 Summary The application running the graphical user interface of LeCroy Windows-based oscilloscopes is a COM Automation
XStream Remote Control: Configuring DCOM Connectivity APPLICATION BRIEF March 2009 Summary The application running the graphical user interface of LeCroy Windows-based oscilloscopes is a COM Automation
Immotec Systems, Inc. SQL Server 2005 Installation Document
 SQL Server Installation Guide 1. From the Visor 360 installation CD\USB Key, open the Access folder and install the Access Database Engine. 2. Open Visor 360 V2.0 folder and double click on Setup. Visor
SQL Server Installation Guide 1. From the Visor 360 installation CD\USB Key, open the Access folder and install the Access Database Engine. 2. Open Visor 360 V2.0 folder and double click on Setup. Visor
Time Stamp. Instruction Booklet
 Time Stamp Instruction Booklet Time Stamp Introductions Time stamp is a useful solution for backing up and restoring system, it backs up the entire computer system to the Backup Zone. Time Stamp is used
Time Stamp Instruction Booklet Time Stamp Introductions Time stamp is a useful solution for backing up and restoring system, it backs up the entire computer system to the Backup Zone. Time Stamp is used
UCO_SECURE Wireless Connection Guide: Windows 8
 1 The UCO_SECURE wireless network uses 802.1x encryption to ensure that your data is secure when it is transmitted wirelessly. This security is not enabled by default on Windows computers. In order to
1 The UCO_SECURE wireless network uses 802.1x encryption to ensure that your data is secure when it is transmitted wirelessly. This security is not enabled by default on Windows computers. In order to
Avaya IP Office SIP Configuration Guide
 Valcom Session Initiation Protocol (SIP) VIP devices are compatible with SIP-enabled versions of Avaya IP Office (5.0 and higher). The Valcom device is added to the IP Office system as a SIP Extension.
Valcom Session Initiation Protocol (SIP) VIP devices are compatible with SIP-enabled versions of Avaya IP Office (5.0 and higher). The Valcom device is added to the IP Office system as a SIP Extension.
CLEARONE DOCUMENT 801-000-002 (REVISION 1.0) October, 2008. with Converge Pro Units
 APPLICATION NOTES Converge Pro Products CLEARONE DOCUMENT 801-000-002 (REVISION 1.0) October, 2008. Troubleshooting USB Connections with Converge Pro Units Description This document explains how to connect
APPLICATION NOTES Converge Pro Products CLEARONE DOCUMENT 801-000-002 (REVISION 1.0) October, 2008. Troubleshooting USB Connections with Converge Pro Units Description This document explains how to connect
Windows Server 2008 R2 Initial Configuration Tasks
 Windows Server 2008 R2 Initial Configuration Tasks I am not responsible for your actions or their outcomes, in any way, while reading and/or implementing this tutorial. I will not provide support for the
Windows Server 2008 R2 Initial Configuration Tasks I am not responsible for your actions or their outcomes, in any way, while reading and/or implementing this tutorial. I will not provide support for the
CONFIGURING VIRTUAL TERMINAL: This is the screen you will see when you first open Virtual Terminal
 CONFIGURING VIRTUAL TERMINAL: This is the screen you will see when you first open Virtual Terminal Before you begin you must configure the Options for Virtual Terminal. Click on the Options drop down menu
CONFIGURING VIRTUAL TERMINAL: This is the screen you will see when you first open Virtual Terminal Before you begin you must configure the Options for Virtual Terminal. Click on the Options drop down menu
1:1 NAT in ZeroShell. Requirements. Overview. Network Setup
 1:1 NAT in ZeroShell Requirements The version of ZeroShell used for writing this document is Release 1.0.beta11. This document does not describe installing ZeroShell, it is assumed that the user already
1:1 NAT in ZeroShell Requirements The version of ZeroShell used for writing this document is Release 1.0.beta11. This document does not describe installing ZeroShell, it is assumed that the user already
Scan to E-mail Quick Setup Guide
 Xerox WorkCentre M118i Scan to E-mail Quick Setup Guide 701P42574 This guide provides a quick reference for setting up the Scan to E-mail feature on the Xerox WorkCentre M118i. It includes procedures for:
Xerox WorkCentre M118i Scan to E-mail Quick Setup Guide 701P42574 This guide provides a quick reference for setting up the Scan to E-mail feature on the Xerox WorkCentre M118i. It includes procedures for:
Verizon Firewall. 1 Introduction. 2 Firewall Home Page
 Verizon Firewall 1 Introduction Verizon Firewall monitors all traffic to and from a computer to block unauthorized access and protect personal information. It provides users with control over all outgoing
Verizon Firewall 1 Introduction Verizon Firewall monitors all traffic to and from a computer to block unauthorized access and protect personal information. It provides users with control over all outgoing
Plesk 11 Manual. Fasthosts Customer Support
 Fasthosts Customer Support Plesk 11 Manual This guide covers everything you need to know in order to get started with the Parallels Plesk 11 control panel. Contents Introduction... 3 Before you begin...
Fasthosts Customer Support Plesk 11 Manual This guide covers everything you need to know in order to get started with the Parallels Plesk 11 control panel. Contents Introduction... 3 Before you begin...
Firewall Defaults and Some Basic Rules
 Firewall Defaults and Some Basic Rules ProSecure UTM Quick Start Guide This quick start guide provides the firewall defaults and explains how to configure some basic firewall rules for the ProSecure Unified
Firewall Defaults and Some Basic Rules ProSecure UTM Quick Start Guide This quick start guide provides the firewall defaults and explains how to configure some basic firewall rules for the ProSecure Unified
GlobeSurfer III Port Forwarding
 GlobeSurfer III Port Forwarding nv, Gaston Geenslaan 14, 3001 Leuven - Belgium - Tel +32 16 317 411 - Fax +32 16 207 164 About this document Overview and Purpose This document provides a description of
GlobeSurfer III Port Forwarding nv, Gaston Geenslaan 14, 3001 Leuven - Belgium - Tel +32 16 317 411 - Fax +32 16 207 164 About this document Overview and Purpose This document provides a description of
freesshd SFTP Server on Windows
 freesshd SFTP Server on Windows Configuration Steps: Setting up the Bridgestone User ID... 2 Setup the freesshd Server... 3 Login as the Bridgestone User ID using WinSCP... 5 Create Default Bridgestone
freesshd SFTP Server on Windows Configuration Steps: Setting up the Bridgestone User ID... 2 Setup the freesshd Server... 3 Login as the Bridgestone User ID using WinSCP... 5 Create Default Bridgestone
About Firewall Protection
 1. This guide describes how to configure basic firewall rules in the UTM to protect your network. The firewall then can provide secure, encrypted communications between your local network and a remote
1. This guide describes how to configure basic firewall rules in the UTM to protect your network. The firewall then can provide secure, encrypted communications between your local network and a remote
Steps for using MagicConnect
 Getting Started Getting Started MagicConnect is a remote access service that allows you safe remote access to a target device from your remote device. What is a remote device? It is a Windows device, iphone/ipad,
Getting Started Getting Started MagicConnect is a remote access service that allows you safe remote access to a target device from your remote device. What is a remote device? It is a Windows device, iphone/ipad,
XenApp/Citrix Program Neighborhood Installation
 1. Download the XenApp Plugin (Citrix Presentation Server) Client Package Version 11.0 for Hosted Apps. Click on this LINK to obtain it. Once prompted, click RUN 2. 3. Save the file to your desktop. Once
1. Download the XenApp Plugin (Citrix Presentation Server) Client Package Version 11.0 for Hosted Apps. Click on this LINK to obtain it. Once prompted, click RUN 2. 3. Save the file to your desktop. Once
REMEDY 7.5 INCIDENT MANAGEMENT AND CHANGE MANAGEMENT USER MANUAL
 INCIDENT MANAGEMENT AND CHANGE MANAGEMENT USER MANUAL 08/17/2009 Contents OVERVIEW... 3 CREATING INCIDENT TICKETS... 13 WORKING AND RESOLVING INCIDENTS AS SUPPORT STAFF... 28 CHANGE MANAGEMENT... 33 SEARCHING
INCIDENT MANAGEMENT AND CHANGE MANAGEMENT USER MANUAL 08/17/2009 Contents OVERVIEW... 3 CREATING INCIDENT TICKETS... 13 WORKING AND RESOLVING INCIDENTS AS SUPPORT STAFF... 28 CHANGE MANAGEMENT... 33 SEARCHING
Home Station ADSL. You may also use the following address (regardless of whether you have changed the primary address or not):
 TABLE OF CONTENTS 1 Introduction 1 2 User interface overview 2 3 LAN and WLAN settings 8 4 Setting the Internet connection 11 5 Settings and status of devices connected to your router 13 6 Configure applications
TABLE OF CONTENTS 1 Introduction 1 2 User interface overview 2 3 LAN and WLAN settings 8 4 Setting the Internet connection 11 5 Settings and status of devices connected to your router 13 6 Configure applications
Special Note Ethernet Connection Problems and Handling Methods (CS203 / CS468 / CS469)
 Special Note Connection Problems and Handling Methods (CS203 / CS468 / CS469) Sometimes user cannot find the RFID device after installing the CSL Demo App and the RFID reader is connected. If user cannot
Special Note Connection Problems and Handling Methods (CS203 / CS468 / CS469) Sometimes user cannot find the RFID device after installing the CSL Demo App and the RFID reader is connected. If user cannot
Trend Micro PC-cillin Internet Security 2006
 Trend Micro PC-cillin Internet Security 2006 I. How to modify Trend Micro PC-cillin Internet Security 2006 to prompt you for applications attempting to access your network and the internet. 1) Right-click
Trend Micro PC-cillin Internet Security 2006 I. How to modify Trend Micro PC-cillin Internet Security 2006 to prompt you for applications attempting to access your network and the internet. 1) Right-click
Support Guide: Managing the Subject machine s Firewall.
 Support Guide: Managing the Subject machine s Firewall. Note: This guide assumes you have successfully deployed F-Response to the subject/target machine. If not, then we recommend you look at one of the
Support Guide: Managing the Subject machine s Firewall. Note: This guide assumes you have successfully deployed F-Response to the subject/target machine. If not, then we recommend you look at one of the
Cisco Unified Communications Manager SIP Trunk Configuration Guide
 Valcom PagePro SIP (Session Initiation Protocol) Paging Servers, models VIP-201 and VIP-204, are compatible with Cisco Unified Communications Manager as either a Third-party SIP Device (Basic or Advanced)
Valcom PagePro SIP (Session Initiation Protocol) Paging Servers, models VIP-201 and VIP-204, are compatible with Cisco Unified Communications Manager as either a Third-party SIP Device (Basic or Advanced)
pcanywhere Advanced Configuration Guide
 Introduction The pcanywhere Solution Advanced Configuration Guide is provided to assist customers with advanced features once they have the Symantec Management Platform with pcanywhere Solution installed.
Introduction The pcanywhere Solution Advanced Configuration Guide is provided to assist customers with advanced features once they have the Symantec Management Platform with pcanywhere Solution installed.
Avaya IP Office SIP Trunk Configuration Guide
 Valcom Session Initiation Protocol (SIP) VIP devices are compatible with SIP-enabled versions of Avaya IP Office (5.0 and higher). The Valcom device can be added to the IP Office system as a SIP Trunk.
Valcom Session Initiation Protocol (SIP) VIP devices are compatible with SIP-enabled versions of Avaya IP Office (5.0 and higher). The Valcom device can be added to the IP Office system as a SIP Trunk.
TechNote. Configuring SonicOS for MS Windows Azure
 Network Security SonicOS Contents Overview...1 Deployment Considerations...2 Supported Platforms...2 Configuring a Policy-Based VPN...2 Configuring a Route-Based VPN...17 Overview This TechNote details
Network Security SonicOS Contents Overview...1 Deployment Considerations...2 Supported Platforms...2 Configuring a Policy-Based VPN...2 Configuring a Route-Based VPN...17 Overview This TechNote details
TM SysAid Chat Guide Document Updated: 10 November 2009
 SysAidTM Chat Guide Document Updated: 10 November 2009 Introduction 2 Quick Access to SysAid Chat 3 Enable / Disable the SysAid Chat from the End User Portal. 4 Edit the Chat Settings 5 Chat Automatic
SysAidTM Chat Guide Document Updated: 10 November 2009 Introduction 2 Quick Access to SysAid Chat 3 Enable / Disable the SysAid Chat from the End User Portal. 4 Edit the Chat Settings 5 Chat Automatic
WORKING WITH WINDOWS FIREWALL IN WINDOWS 7
 WORKING WITH WINDOWS FIREWALL IN WINDOWS 7 Firewall in Windows 7 Windows 7 comes with two firewalls that work together. One is the Windows Firewall, and the other is Windows Firewall with Advanced Security
WORKING WITH WINDOWS FIREWALL IN WINDOWS 7 Firewall in Windows 7 Windows 7 comes with two firewalls that work together. One is the Windows Firewall, and the other is Windows Firewall with Advanced Security
523 Non-ThinManager Components
 28 Non-ThinManager Components Microsoft Terminal Servers play an important role in the ThinManager system. It is recommended that you become familiar with the documentation provided by Microsoft about
28 Non-ThinManager Components Microsoft Terminal Servers play an important role in the ThinManager system. It is recommended that you become familiar with the documentation provided by Microsoft about
Firewall Firewall August, 2003
 Firewall August, 2003 1 Firewall and Access Control This product also serves as an Internet firewall, not only does it provide a natural firewall function (Network Address Translation, NAT), but it also
Firewall August, 2003 1 Firewall and Access Control This product also serves as an Internet firewall, not only does it provide a natural firewall function (Network Address Translation, NAT), but it also
Chapter 4 Firewall Protection and Content Filtering
 Chapter 4 Firewall Protection and Content Filtering This chapter describes how to use the content filtering features of the ProSafe Dual WAN Gigabit Firewall with SSL & IPsec VPN to protect your network.
Chapter 4 Firewall Protection and Content Filtering This chapter describes how to use the content filtering features of the ProSafe Dual WAN Gigabit Firewall with SSL & IPsec VPN to protect your network.
ONE POS User Manual. A brief hand guide for ONE ERP POS SYSTEM MYIT SOLUTION. Latest update on: 03/09/12
 ONE POS User Manual A brief hand guide for ONE ERP POS SYSTEM MYIT SOLUTION Latest update on: 03/09/12 TABLE OF CONTENTS CHAPTER 1 - SETTINGS Database Setup... 3 Printer Configuration... 5 Cash Drawer
ONE POS User Manual A brief hand guide for ONE ERP POS SYSTEM MYIT SOLUTION Latest update on: 03/09/12 TABLE OF CONTENTS CHAPTER 1 - SETTINGS Database Setup... 3 Printer Configuration... 5 Cash Drawer
Connecting to a Soundweb TM. London Network
 This guide will step you through the process of configuring your laptop and HiQnet TM London Architect TM to communicate with a network of Soundweb London devices. 1 Install London Architect Install the
This guide will step you through the process of configuring your laptop and HiQnet TM London Architect TM to communicate with a network of Soundweb London devices. 1 Install London Architect Install the
How To Industrial Networking
 How To Industrial Networking Prepared by: Matt Crites Product: Date: April 2014 Any RAM or SN 6xxx series router Legacy firmware 3.14/4.14 or lower Subject: This document provides a step by step procedure
How To Industrial Networking Prepared by: Matt Crites Product: Date: April 2014 Any RAM or SN 6xxx series router Legacy firmware 3.14/4.14 or lower Subject: This document provides a step by step procedure
Document Revision Date: August 14, 2014. Create a New Data Protection Policy in the Symantec.cloud Management Portal
 Document Revision Date: August 14, 2014 Create a New Data Protection Policy in the Symantec.cloud Management Portal Create a New Data Protection Policy i Contents Configure Data Protection Settings in
Document Revision Date: August 14, 2014 Create a New Data Protection Policy in the Symantec.cloud Management Portal Create a New Data Protection Policy i Contents Configure Data Protection Settings in
LifeSize UVC Manager TM Deployment Guide
 LifeSize UVC Manager TM Deployment Guide May 2014 LifeSize UVC Manager Deployment Guide 2 LifeSize UVC Manager Network administrators who use UVC Manager to manage video and voice communications systems
LifeSize UVC Manager TM Deployment Guide May 2014 LifeSize UVC Manager Deployment Guide 2 LifeSize UVC Manager Network administrators who use UVC Manager to manage video and voice communications systems
OneLogin Integration User Guide
 OneLogin Integration User Guide Table of Contents OneLogin Account Setup... 2 Create Account with OneLogin... 2 Setup Application with OneLogin... 2 Setup Required in OneLogin: SSO and AD Connector...
OneLogin Integration User Guide Table of Contents OneLogin Account Setup... 2 Create Account with OneLogin... 2 Setup Application with OneLogin... 2 Setup Required in OneLogin: SSO and AD Connector...
Galileo Print Manager
 Galileo Print Manager Troubleshooting Guide December 2003 Contents General Application... 3 Printer does not auto wake... 3 Preliminary checks... 3 Firewall issues... 4 Changes in Configuration dialog
Galileo Print Manager Troubleshooting Guide December 2003 Contents General Application... 3 Printer does not auto wake... 3 Preliminary checks... 3 Firewall issues... 4 Changes in Configuration dialog
Network/Floating License Installation Instructions
 Network/Floating License Installation Instructions Installation steps: On the Windows PC that will act as License Manager (SERVER): 1. Install HASP Run-time environment, SERVER 2. Plug in the red USB hardware
Network/Floating License Installation Instructions Installation steps: On the Windows PC that will act as License Manager (SERVER): 1. Install HASP Run-time environment, SERVER 2. Plug in the red USB hardware
Safe internet for business use: Getting Started Guide
 Safe internet for business use: Getting Started Guide Table of Contents 1. Preface 1 2. Before You Install 2 2.1 Disabling Firewalls 2 2.2 About Accelerators 3 3. About Profiles 4 4. Installation and Initial
Safe internet for business use: Getting Started Guide Table of Contents 1. Preface 1 2. Before You Install 2 2.1 Disabling Firewalls 2 2.2 About Accelerators 3 3. About Profiles 4 4. Installation and Initial
Velocity Web Services Client 1.0 Installation Guide and Release Notes
 Velocity Web Services Client 1.0 Installation Guide and Release Notes Copyright 2014-2015, Identiv. Last updated June 24, 2015. Overview This document provides the only information about version 1.0 of
Velocity Web Services Client 1.0 Installation Guide and Release Notes Copyright 2014-2015, Identiv. Last updated June 24, 2015. Overview This document provides the only information about version 1.0 of
Host Installation on a Terminal Server
 TECHNICAL PAPER Host Installation on a Terminal Server Netop develops and sells software solutions that enable swift, secure and seamless transfer of video, screens, sounds and data between two or more
TECHNICAL PAPER Host Installation on a Terminal Server Netop develops and sells software solutions that enable swift, secure and seamless transfer of video, screens, sounds and data between two or more
Database Program Instructions
 Database Program Instructions 1) Start your Comparative Rating software by double-clicking the icon on your desktop. 2) Click on the button on the Comparative Rating Software Main Menu. 3) A message Loading
Database Program Instructions 1) Start your Comparative Rating software by double-clicking the icon on your desktop. 2) Click on the button on the Comparative Rating Software Main Menu. 3) A message Loading
Chapter 3 Security and Firewall Protection
 Chapter 3 Security and Firewall Protection This chapter describes how to use the basic firewall features of the ADSL2+ Modem Router to protect your network. Firewall Settings You can set up the ADSL2+
Chapter 3 Security and Firewall Protection This chapter describes how to use the basic firewall features of the ADSL2+ Modem Router to protect your network. Firewall Settings You can set up the ADSL2+
Troubleshooting Guide
 Enable WMI after applying SP2 for XP Company web site: Support email: support@ Support telephone: +44 20 3287-7651 +1 646 233-1163 2 This tutorial will guide you on enabling WMI after applying Service
Enable WMI after applying SP2 for XP Company web site: Support email: support@ Support telephone: +44 20 3287-7651 +1 646 233-1163 2 This tutorial will guide you on enabling WMI after applying Service
CREATING AN IKE IPSEC TUNNEL BETWEEN AN INTERNET SECURITY ROUTER AND A WINDOWS 2000/XP PC
 CREATING AN IKE IPSEC TUNNEL BETWEEN AN INTERNET SECURITY ROUTER AND A WINDOWS 2000/XP PC 1 Introduction Release date: 11/12/2003 This application note details the steps for creating an IKE IPSec VPN tunnel
CREATING AN IKE IPSEC TUNNEL BETWEEN AN INTERNET SECURITY ROUTER AND A WINDOWS 2000/XP PC 1 Introduction Release date: 11/12/2003 This application note details the steps for creating an IKE IPSec VPN tunnel
Mac OS VPN Set Up Guide
 Mac OS VPN Set Up Guide If internet traffic is not being sent over the VPN then go to System Preferences- >Network and click on your VPN connection. Click the "Advanced..." button, and in the "Options"
Mac OS VPN Set Up Guide If internet traffic is not being sent over the VPN then go to System Preferences- >Network and click on your VPN connection. Click the "Advanced..." button, and in the "Options"
isupplier PORTAL ACCESS SYSTEM REQUIREMENTS
 TABLE OF CONTENTS Recommended Browsers for isupplier Portal Recommended Microsoft Internet Explorer Browser Settings (MSIE) Recommended Firefox Browser Settings Recommended Safari Browser Settings SYSTEM
TABLE OF CONTENTS Recommended Browsers for isupplier Portal Recommended Microsoft Internet Explorer Browser Settings (MSIE) Recommended Firefox Browser Settings Recommended Safari Browser Settings SYSTEM
Wakanda Studio Features
 Wakanda Studio Features Discover the many features in Wakanda Studio. The main features each have their own chapters and other features are documented elsewhere: Wakanda Server Administration Data Browser
Wakanda Studio Features Discover the many features in Wakanda Studio. The main features each have their own chapters and other features are documented elsewhere: Wakanda Server Administration Data Browser
OneSourceFax Customer Guide
 OneSourceFax Customer Guide General Information Billing: OneSourceFax Plan Features Monthly Charge OneSourceFax 150 Unlimited Faxes to Numbers in your Local Calling Area $12.95 150 Nationwide Long Distance
OneSourceFax Customer Guide General Information Billing: OneSourceFax Plan Features Monthly Charge OneSourceFax 150 Unlimited Faxes to Numbers in your Local Calling Area $12.95 150 Nationwide Long Distance
Lab 4.4.8a Configure a Cisco GRE over IPSec Tunnel using SDM
 Lab 4.4.8a Configure a Cisco GRE over IPSec Tunnel using SDM Objective Scenario Topology In this lab, the students will complete the following tasks: Prepare to configure Virtual Private Network (VPN)
Lab 4.4.8a Configure a Cisco GRE over IPSec Tunnel using SDM Objective Scenario Topology In this lab, the students will complete the following tasks: Prepare to configure Virtual Private Network (VPN)
Setup Guide for Exchange Server
 Setup Guide for Exchange Server Table of Contents Overview... 1 A. Exchange Server 2007/2010 Inbound Mail... 2 B. Exchange Server 2007/2010 Outbound Mail (optional)... 8 C. Exchange Server 2003/2000 Inbound
Setup Guide for Exchange Server Table of Contents Overview... 1 A. Exchange Server 2007/2010 Inbound Mail... 2 B. Exchange Server 2007/2010 Outbound Mail (optional)... 8 C. Exchange Server 2003/2000 Inbound
In this lab you will explore the Windows XP Firewall and configure some advanced settings.
 16.3.2 Lab: Configure Windows XP Firewall Print and complete this lab. In this lab you will explore the Windows XP Firewall and configure some advanced settings. Recommended Equipment Two computers directly
16.3.2 Lab: Configure Windows XP Firewall Print and complete this lab. In this lab you will explore the Windows XP Firewall and configure some advanced settings. Recommended Equipment Two computers directly
Configure the idrac Remote Access Console
 Configure the idrac Remote Access Console If your ExtraHop system is deployed in a data center or other remote environment, you might need to remotely access the console and its power-management features.
Configure the idrac Remote Access Console If your ExtraHop system is deployed in a data center or other remote environment, you might need to remotely access the console and its power-management features.
enicq 5 System Administrator s Guide
 Vermont Oxford Network enicq 5 Documentation enicq 5 System Administrator s Guide Release 2.0 Published November 2014 2014 Vermont Oxford Network. All Rights Reserved. enicq 5 System Administrator s Guide
Vermont Oxford Network enicq 5 Documentation enicq 5 System Administrator s Guide Release 2.0 Published November 2014 2014 Vermont Oxford Network. All Rights Reserved. enicq 5 System Administrator s Guide
Installing NetSupport School for use with the NetSupport School Student extension for Google Chrome
 Installing NetSupport School for use with the NetSupport School Student extension for Google Chrome NetSupport School delivers the tools you need to help maximise the effectiveness of computer led teaching
Installing NetSupport School for use with the NetSupport School Student extension for Google Chrome NetSupport School delivers the tools you need to help maximise the effectiveness of computer led teaching
PIGCHAMP MOBILE. PigCHAMP Knowledge Software. Installation Guide for Mobile Units
 PIGCHAMP MOBILE PigCHAMP Knowledge Software Installation Guide for Mobile Units Table of Contents: Important Note:... 4 Chapter 1: PC Setup... 5 A. Install PigCHAMP Mobile Manager on Windows XP...5 B.
PIGCHAMP MOBILE PigCHAMP Knowledge Software Installation Guide for Mobile Units Table of Contents: Important Note:... 4 Chapter 1: PC Setup... 5 A. Install PigCHAMP Mobile Manager on Windows XP...5 B.
Procedure for updating Firmware of EZ4 W or ICC50 W
 Procedure for updating Firmware of EZ4 W or ICC50 W 1. Download the Firmware file for your camera to your PC 2. Download the Leica Camera Configuration program to your PC 3. Install Leica Camera Configuration
Procedure for updating Firmware of EZ4 W or ICC50 W 1. Download the Firmware file for your camera to your PC 2. Download the Leica Camera Configuration program to your PC 3. Install Leica Camera Configuration
Yale Software Library http://www.yale.edu/software/
 e/ Yale Software Library http://www.yale.edu/software/ For assistance contact the ITS Help Desk 785-3200, 432-9000, helpdesk@yale.edu Windows XP Firewall Windows XP SP2 includes the new Windows Firewall,
e/ Yale Software Library http://www.yale.edu/software/ For assistance contact the ITS Help Desk 785-3200, 432-9000, helpdesk@yale.edu Windows XP Firewall Windows XP SP2 includes the new Windows Firewall,
Lab 8.3.13 Configure Cisco IOS Firewall CBAC
 Lab 8.3.13 Configure Cisco IOS Firewall CBAC Objective Scenario Topology In this lab, the students will complete the following tasks: Configure a simple firewall including CBAC using the Security Device
Lab 8.3.13 Configure Cisco IOS Firewall CBAC Objective Scenario Topology In this lab, the students will complete the following tasks: Configure a simple firewall including CBAC using the Security Device
Registering with Cisco UCM
 FLX VoIP Registering with Cisco UCM Date: May 15 th, 2012 This technical note gives a detailed description on how to register a Revolabs FLX conference phone with a Cisco Unified Communications Manager
FLX VoIP Registering with Cisco UCM Date: May 15 th, 2012 This technical note gives a detailed description on how to register a Revolabs FLX conference phone with a Cisco Unified Communications Manager
How to install and use CrossTec Remote Control or SchoolVue in a Virtual and or Terminal Service environment
 How to install and use CrossTec Remote Control or SchoolVue in a Virtual and or Terminal Service environment 1 P a g e CrossTec Corporation 500 NE Spanish River Blvd. Suite 201 Phone 800.675.0729 Fax 561.391.5820
How to install and use CrossTec Remote Control or SchoolVue in a Virtual and or Terminal Service environment 1 P a g e CrossTec Corporation 500 NE Spanish River Blvd. Suite 201 Phone 800.675.0729 Fax 561.391.5820
Manual. 3CX Phone System integration with Microsoft Outlook and Salesforce Version 1.0
 Manual 3CX Phone System integration with Microsoft Outlook and Salesforce Version 1.0 Copyright 2006-2009, 3CX ltd. http:// E-mail: info@3cx.com Information in this document is subject to change without
Manual 3CX Phone System integration with Microsoft Outlook and Salesforce Version 1.0 Copyright 2006-2009, 3CX ltd. http:// E-mail: info@3cx.com Information in this document is subject to change without
Biznet GIO Cloud Connecting VM via Windows Remote Desktop
 Biznet GIO Cloud Connecting VM via Windows Remote Desktop Introduction Connecting to your newly created Windows Virtual Machine (VM) via the Windows Remote Desktop client is easy but you will need to make
Biznet GIO Cloud Connecting VM via Windows Remote Desktop Introduction Connecting to your newly created Windows Virtual Machine (VM) via the Windows Remote Desktop client is easy but you will need to make
Using Public IP Settings
 Using Public IP Settings Interoute Virtual Data Centre Peter Farmer VDC Appliance Development Manager Interoute 01 Using Public IP Settings The Interoute Virtual Data Centre (VDC) Public IP Settings allow
Using Public IP Settings Interoute Virtual Data Centre Peter Farmer VDC Appliance Development Manager Interoute 01 Using Public IP Settings The Interoute Virtual Data Centre (VDC) Public IP Settings allow
Vizit 4.1 Installation Guide
 Vizit 4.1 Installation Guide Contents Running the Solution Installer... 3 Installation Requirements... 3 The Solution Installer... 3 Activating your License... 7 Online Activation... 7 Offline Activation...
Vizit 4.1 Installation Guide Contents Running the Solution Installer... 3 Installation Requirements... 3 The Solution Installer... 3 Activating your License... 7 Online Activation... 7 Offline Activation...
Getting Started. A Getting Started Guide for Locum RealTime Monitor. Manual Version 2.1 LOCUM SOFTWARE SERVICES LIMITED
 Getting Started A Getting Started Guide for Locum RealTime Monitor Manual Version 2.1 LOCUM SOFTWARE SERVICES LIMITED Locum House, 84 Brown Street, Sheffield, S1 2BS, England Telephone: +44 (0) 114 252-1199
Getting Started A Getting Started Guide for Locum RealTime Monitor Manual Version 2.1 LOCUM SOFTWARE SERVICES LIMITED Locum House, 84 Brown Street, Sheffield, S1 2BS, England Telephone: +44 (0) 114 252-1199
User Guide. Version 3.2. Copyright 2002-2009 Snow Software AB. All rights reserved.
 Version 3.2 User Guide Copyright 2002-2009 Snow Software AB. All rights reserved. This manual and computer program is protected by copyright law and international treaties. Unauthorized reproduction or
Version 3.2 User Guide Copyright 2002-2009 Snow Software AB. All rights reserved. This manual and computer program is protected by copyright law and international treaties. Unauthorized reproduction or
Sophos Client Firewall version 1.5 user manual. For Windows
 Sophos Client Firewall version 1.5 user manual For Windows Document date: June 2007 Contents 1 Sophos... Client Firewall 4 2 How... do I get started? 5 3 How... do I configure the firewall? 15 4 How...
Sophos Client Firewall version 1.5 user manual For Windows Document date: June 2007 Contents 1 Sophos... Client Firewall 4 2 How... do I get started? 5 3 How... do I configure the firewall? 15 4 How...
Service Bulletin [2014 02]
![Service Bulletin [2014 02] Service Bulletin [2014 02]](/thumbs/27/10792456.jpg) How do you know if you have a PanelView Plus or a Panelview Plus 6? The quickest way is to look at the type of memory slot the unit has on the back. If it accepts and SD Card, it s a PanelView Plus 6.
How do you know if you have a PanelView Plus or a Panelview Plus 6? The quickest way is to look at the type of memory slot the unit has on the back. If it accepts and SD Card, it s a PanelView Plus 6.
Pearl Echo Installation Checklist
 Pearl Echo Installation Checklist Use this checklist to enter critical installation and setup information that will be required to install Pearl Echo in your network. For detailed deployment instructions
Pearl Echo Installation Checklist Use this checklist to enter critical installation and setup information that will be required to install Pearl Echo in your network. For detailed deployment instructions
Managing Identities and Admin Access
 CHAPTER 4 This chapter describes how Cisco Identity Services Engine (ISE) manages its network identities and access to its resources using role-based access control policies, permissions, and settings.
CHAPTER 4 This chapter describes how Cisco Identity Services Engine (ISE) manages its network identities and access to its resources using role-based access control policies, permissions, and settings.
How to Open HTTP or HTTPS traffic to a webserver behind the NetVanta 2000 Series unit (Enhanced OS)
 NetVanta 2000 Series Technical Note How to Open HTTP or HTTPS traffic to a webserver behind the NetVanta 2000 Series unit (Enhanced OS) This document is applicable to NetVanta 2600 series, 2700 series,
NetVanta 2000 Series Technical Note How to Open HTTP or HTTPS traffic to a webserver behind the NetVanta 2000 Series unit (Enhanced OS) This document is applicable to NetVanta 2600 series, 2700 series,
10.3.1.10 Lab - Configure a Windows XP Firewall
 5.0 10.3.1.10 Lab - Configure a Windows XP Firewall Print and complete this lab. In this lab, you will explore the Windows XP Firewall and configure some advanced settings. Recommended Equipment Step 1
5.0 10.3.1.10 Lab - Configure a Windows XP Firewall Print and complete this lab. In this lab, you will explore the Windows XP Firewall and configure some advanced settings. Recommended Equipment Step 1
Non-ThinManager Components
 Non-ThinManager Components Microsoft Terminal Servers play an important role in the ThinManager system. It is recommended that you become familiar with the documentation provided by Microsoft about their
Non-ThinManager Components Microsoft Terminal Servers play an important role in the ThinManager system. It is recommended that you become familiar with the documentation provided by Microsoft about their
Intel Unite Solution. Standalone User Guide
 Intel Unite Solution Standalone User Guide Legal Disclaimers & Copyrights All information provided here is subject to change without notice. Contact your Intel representative to obtain the latest Intel
Intel Unite Solution Standalone User Guide Legal Disclaimers & Copyrights All information provided here is subject to change without notice. Contact your Intel representative to obtain the latest Intel
1. Set Daylight Savings Time... 3. 2. Create Migrator Account... 3. 3. Assign Migrator Account to Administrator group... 4
 1. Set Daylight Savings Time... 3 a. Have client log into Novell/Local Machine with Administrator Account...3 b. Access Adjust Date/Time...3 c. Make sure the time zone is set to Central Time...3 2. Create
1. Set Daylight Savings Time... 3 a. Have client log into Novell/Local Machine with Administrator Account...3 b. Access Adjust Date/Time...3 c. Make sure the time zone is set to Central Time...3 2. Create
Configuring PA Firewalls for a Layer 3 Deployment
 Configuring PA Firewalls for a Layer 3 Deployment Configuring PAN Firewalls for a Layer 3 Deployment Configuration Guide January 2009 Introduction The following document provides detailed step-by-step
Configuring PA Firewalls for a Layer 3 Deployment Configuring PAN Firewalls for a Layer 3 Deployment Configuration Guide January 2009 Introduction The following document provides detailed step-by-step
Sharp Remote Device Manager (SRDM) Server Software Setup Guide
 Sharp Remote Device Manager (SRDM) Server Software Setup Guide This Guide explains how to install the software which is required in order to use Sharp Remote Device Manager (SRDM). SRDM is a web-based
Sharp Remote Device Manager (SRDM) Server Software Setup Guide This Guide explains how to install the software which is required in order to use Sharp Remote Device Manager (SRDM). SRDM is a web-based
Office 2013 Settings Customization Created 7/29/2014 by ICIT Training (training@uww.edu)
 Office 2013 Settings Customization Created 7/29/2014 by ICIT Training (training@uww.edu) This guide helps you quickly restore any default preferences or settings in Office programs (Word, Excel, PowerPoint,
Office 2013 Settings Customization Created 7/29/2014 by ICIT Training (training@uww.edu) This guide helps you quickly restore any default preferences or settings in Office programs (Word, Excel, PowerPoint,
WhatsUpGold. v12.3.1. NetFlow Monitor User Guide
 WhatsUpGold v12.3.1 NetFlow Monitor User Guide Contents CHAPTER 1 WhatsUp Gold NetFlow Monitor Overview What is NetFlow?... 1 How does NetFlow Monitor work?... 2 Supported versions... 2 System requirements...
WhatsUpGold v12.3.1 NetFlow Monitor User Guide Contents CHAPTER 1 WhatsUp Gold NetFlow Monitor Overview What is NetFlow?... 1 How does NetFlow Monitor work?... 2 Supported versions... 2 System requirements...
8x8 Click2Pop User Guide
 USER GUIDE 8x8 User Guide Getting Started with April 2014 Contents Introduction... 3 What s new.... 3 8x8.... 3 Here is how works...4 8x8 Click2Connect.... 4 Requirements.... 4 Installation on Microsoft
USER GUIDE 8x8 User Guide Getting Started with April 2014 Contents Introduction... 3 What s new.... 3 8x8.... 3 Here is how works...4 8x8 Click2Connect.... 4 Requirements.... 4 Installation on Microsoft
For keyboard and touchscreen BlackBerry devices User manual
 TSMobiles Terminal Service client for Mobiles For keyboard and touchscreen BlackBerry devices User manual Introduction... 3 System Requirements... 3 1. Configuring Remote Desktop on computer... 4 2. Installation...
TSMobiles Terminal Service client for Mobiles For keyboard and touchscreen BlackBerry devices User manual Introduction... 3 System Requirements... 3 1. Configuring Remote Desktop on computer... 4 2. Installation...
Infinity Web Viewer Reference Guide
 Infinity Web Viewer Reference Guide Table of Contents Overview... 1 Security Considerations... 1 System Setup... 1 Infinity Configuration... 1 Workstation Prerequisites... 2 Configuring Internet Security...
Infinity Web Viewer Reference Guide Table of Contents Overview... 1 Security Considerations... 1 System Setup... 1 Infinity Configuration... 1 Workstation Prerequisites... 2 Configuring Internet Security...
Getting Started. Symantec Client Security. About Symantec Client Security. How to get started
 Getting Started Symantec Client Security About Security Security provides scalable, cross-platform firewall, intrusion prevention, and antivirus protection for workstations and antivirus protection for
Getting Started Symantec Client Security About Security Security provides scalable, cross-platform firewall, intrusion prevention, and antivirus protection for workstations and antivirus protection for
Chapter 4 Firewall Protection and Content Filtering
 Chapter 4 Firewall Protection and Content Filtering The ProSafe VPN Firewall 50 provides you with Web content filtering options such as Block Sites and Keyword Blocking. Parents and network administrators
Chapter 4 Firewall Protection and Content Filtering The ProSafe VPN Firewall 50 provides you with Web content filtering options such as Block Sites and Keyword Blocking. Parents and network administrators
To add Citrix XenApp Client Setup for home PC/Office using the 32bit Windows client.
 I. PURPOSE To add Citrix XenApp Client Setup for home PC/Office using the 32bit Windows client. II. POLICY: Network Request form must be sent from MIS staff to HCN Hardware Support requesting Citrix XenApp
I. PURPOSE To add Citrix XenApp Client Setup for home PC/Office using the 32bit Windows client. II. POLICY: Network Request form must be sent from MIS staff to HCN Hardware Support requesting Citrix XenApp
