Archiving Technical Overview. A Technical Overview Paper Describing Key Functions And Capabilities Of The Managed Archiving Service
|
|
|
- Godfrey Sutton
- 8 years ago
- Views:
Transcription
1 A Technical Overview Paper Describing Key Functions And Capabilities Of The Managed Archiving Service
2 Contents Introduction Feature Overview The Archiving Process Archiving Boundary using the Filtering Service Archived Audit Trails (meta-data extensions) Archiving Internal Blind Carbon Copy (Bcc) Routing Journaling Routing Messages to the Managed Archiving Service Securing Connectivity Infrastructure Redundant Infrastructure Data Availability Mirrored Storage Availability of Data Access Data Security Data Store Management Retention Periods Storage Management Aspects of Scalability User Types Compliance Interface End User Interface Summary About Webroot Webroot, Inc th Street, Boulder, CO U.S.A. Tel:
3 Webroot s Archiving Service is designed as a mission critical service, offering organizations the option to quickly and easily deploy an archiving solution requiring no additional hardware or software. Driven through compliance requirements, business continuity and the need to continually manage storage costs, the Archiving Service offers a fully featured offering that is able to meet the requirements of all organizations, both large and small. Although simple to deploy, prospective purchasers will wish to better understand solutions that are handling their sensitive data. This paper provides a high level technical overview of the offering which aims to address the key technical concerns that any organization may have. Feature Overview The Managed Archiving Service is able to archive messages passing through the Webroot Managed filtering Service, as well as capturing internal mail traffic sent through mail servers such as Exchange, Sendmail, Postfix, etc. If using Exchange as the internal mail server, the solution takes advantage of Exchange extensions to preserve Bcc recipients and also record the authoritative sender and recipient envelope addresses. A fully compliant data storage and access solution is provided supporting the three key criteria for Data Protection: data protection through encryption, restricted access and audited access. All data is encrypted when stored within the service, ensuring that the privacy of the data is both retained and protected from malicious attack. Restricted access to the data is provided through a secure Web interface which authenticates individuals within the context of service-defined user credentials. Finally, any search requests made to the system are audited. If a user has permission to search within accounts other than their own, they must quote a reason for the search and acknowledge the terms and conditions of the search. Data Custodians can be notified by to ensure that any and all search requests are proactively monitored. An audit event log is provided with a search tool that allows authorised individuals to review recorded audit actions. The service provides a comprehensive set of search tools designed to assist the user in finding the required information in a fast and efficient manner. In addition to searches based on addresses, dates, subjects, etc, enhanced indexing facilities enable users to perform full text searches on messages bodies and attachments. When messages are indexed, common compression types, such as zip files, are decompressed whilst all enclosed contents (Word, Excel, PDF, RTF files) are indexed. A tiered search interface enables the user to approach the search task from a simple interface which ranges from a single intelligent entry box to an advanced interface which allows detailed search criteria to be constructed over a multitude of indexed fields. Webroot, Inc th Street, Boulder, CO U.S.A. Tel:
4 The search results interface provides a message based view, allowing the user to view all items at a message level, along with a document view which enables the user to view the search results according to the sought document type, revealing the actual attachment or message body that was found by the search. Tools are provided to restrict search results to those that are relevant to the user, e.g. by document type, relevance, sort order, etc. Archive capability is also provided for the End-User, which is able to query and view his or her messages in exactly the same way as the compliance administrator can. Access is provided via a Web Interface the only difference being that End-User access is not audited. End-Users may view messages and, if required, can release messages back for delivery to their inbox. The same archive store is used for both compliance and End-User access, thus minimizing storage overheads. Much of an organizations data will be stored within local PST folders. The service provides the capability to import PST folders into the archive. This is achieved by enabling the End-User or organization to upload PST files to the Managed Service, where it will be imported. All messages are stored on mirrored disk farms across two data centres, thus protecting against loss of data in the event of a disaster at either one of the data centres. Each disk farm is RAID enabled to provide maximum up-time. Messages are distributed to the disk farms in real-time. Search engine technology more commonly associated with internet search engines is used to implement a highly scalable and distributed indexing system, which is able to support searches over many terabytes of data at lighting speed. The Archiving Process The Managed Archiving Service has been designed to operate transparently with no hardware or software required on-site. Archiving can take place in two locations; either on the boundary of the organization or internally. INTERNET YOUR NETWORK FILTERING AND MANAGEMENT SYSTEMS ARCHIVE QUEUE TLS JOURNAL SERVER SEARCH HTTPS STORAGE ARCHIVE DIRECTOR INDEX STORAGE ARCHIVE DIRECTOR MIRRORED DATA STORE INDEX Figure 1 - Archiving Process Webroot, Inc th Street, Boulder, CO U.S.A. Tel:
5 If an organization has subscribed to the Managed Filtering Service for virus, spam, etc, then both inbound and outbound messages can be archived as they pass through the mail filters. Alternatively, if users haven t subscribed to the filtering service, or if they wish to archive internal as well as boundary , the system can be configured to capture generated through journaling or Blind Carbon Copy (Bcc) Routing. Archiving Boundary using the Filtering Service Archiving boundary that enters and leaves the organization is, for most, a fundamental requirement. In light of this, the function to archive boundary is a built-in component of the Managed Filtering Service. By simply enabling the archiving facility for each domain, all messages passing through the filters, in either direction, are also routed to the archive service. Rules can be defined for each domain, enabling policy decisions to be applied to certain classes of information. For example, messages detected as spam may or may not be archived and, if archived, it is possible to specify for how long. The flexibility to make such decisions enables a stricter compliance model to be adopted which balances the need to retain information with the need to efficiently manage storage space. Archived Audit Trails (meta-data extensions) Much of the time, the filter service is deleting or modifying mails as they pass through the filters. However, just because a message is filtered out, doesn t necessarily mean that it shouldn t be archived. Moreover, once a message is archived, it is important to record what actually happened to the message. The filtering service therefore offers a number of critical extensions that form the basis of an archived audit trail. Specifically, attributes are stored with the archived message that indicate what type of content was detected, e.g. spam, virus, etc, what the delivery outcome for each recipient was, including an indication of any additional recipients that were added to the message by the content rules, and retention policies. This information is available to the Compliance Officer when the message is pre-viewed, and assists in supporting claims relating to nonrepudiation of mail for example. Archiving Internal Intra-organizational mail generated between mailboxes within an organization can be captured and archived by the Managed Archiving Service. The process to archive internal is, in fact, very simple. Firstly, mail messages must be captured using one of two techniques; either Journaling or Blind Carbon Copy (Bcc) Routing. Secondly the captured messages are then routed via the organization s infrastructure to a virtual mailbox located within the Managed Archiving Service data centres, using standard SMTP protocols. The approach was selected to comply with the core design ethos of being able to provide a managed service that requires no additional hardware/software on site, thus reducing risk, complexity and cost. Furthermore, the approaches that have been taken allow a wider set of mail systems to be targeted. Webroot, Inc th Street, Boulder, CO U.S.A. Tel:
6 Blind Carbon Copy (Bcc) Routing The most basic form of capture is to use Blind Carbon Copy (Bcc) Routing. Effective use of this mechanism will be dependant upon the facilities provided by the organization s internal mail servers. Bcc Routing works by configuring the mail server to automatically add an additional delivery recipient to every routed . The additional delivery recipient is an address that is hosted on the Managed Archiving Service, thus causing a copy of the message to be routed to the service via standard SMTP. Journaling Journaling is a capability that is commonly associated with Microsoft Exchange. Provided as a built-in capability of Exchange, it was specifically designed to capture a copy of every message that is exchanged between individuals located in an Exchange Server environment. In its most basic form, it is simply a Blind Carbon Copy Routing solution, which makes another copy of the message which is routed to a mailbox for servicing by an archiving product. However, recent compliance pressures from the US Financial Services market have forced a number of extensions to the core journaling service, which resulted in an enhanced Envelope Journaling solution. Similar to the Bcc solution, Envelope Journaling delivers a copy of the original message to a mailbox, to which additional meta-data is added. This has two key advantages over the Bcc Routing mechanism: > The real envelope senders and recipients are retained. Using Bcc Routing, the best guess on who sent and received the message is based on the headers of the message which can be spoofed, non-existent, or different to the envelope. > bcc recipients specified by the original sender of the message (not to be confused with Bcc Routing) are also retained. The Managed Archiving Service supports the Envelope Journaling extensions and is therefore able to extract the relevant meta-data in order to correctly re-create, store and index the messages. As far as capacity planned is concerned, Microsoft estimate that journaling may introduce up to a 20% overhead on the Exchange Server. Routing Messages to the Managed Archiving Service In both cases of Bcc Routing and Journaling, captured internal is routed to the Managed Archiving Service using the same approach. As each message is captured, it is routed to a virtual mailbox which is located on the Managed Archiving Service using standard SMTP protocols. Dedicated Archive Servers within the service are designated for this purpose and, as such, special routing rules may be required in the organization s edge servers to ensure that messages are routed to the correct server within the service. Webroot, Inc th Street, Boulder, CO U.S.A. Tel:
7 Securing Connectivity contains material of a sensitive nature. A natural concern relates to the confidentiality of internal as it is transferred from the organization s infrastructure to the Managed Archiving Service. To counter these concerns, TLS (Transport Layer Security) is used to secure the messages from the organization s edge mail server to the Managed Archiving Service s mail server. TLS is supported as standard by the majority of main stream Mail Servers and allows an encrypted pipe to be setup between two MTAs. At the most secure level, the encryption can be mandated at the Managed Archiving Service level to ensure that only TLS connections are accepted for mail upload. Infrastructure The Webroot Managed Archiving Service is hosted over two data centres that are physically separated, providing a full Disaster Recovery architecture. As already discussed, can be captured for archiving either directly from the filter mail servers as they are relayed on behalf of the organization, or by routing internal mail from the organization to dedicated mail journaling servers hosted in the data centres. Redundant Infrastructure The Webroot architecture is a fully redundant N+1 grade solution at data centre level. Two data centres operating in an Active-Active mode are backed up by a third buffer data centre. The N+1 redundancy model means that an entire primary entire data centre can be lost and service will continue without interruption. In keeping with the core architecture, the Archiving Service has been designed to work within this N+1 model, meaning that all archiving infrastructure, including storage devices are duplicated over both the primary data centres. Redundancy is a key element of the entire service, and as well as providing a fully redundant N+1 dual data centre solution, the majority of the systems within each data centre also operate at this level. This includes redundant environmental controls, dual power feeds with battery and diesel generator UPS elements and redundant internet connectivity. Redundancy is also applied at the server level which includes redundant power supplies, RAID support for storage arrays and in certain cases, redundant NICs. Data Availability Organizations require access to their stored data on a 24 x 7 basis. In order to provide this level of availability, the Managed Archive Service has been designed to utilise the architecture to store data in a redundant fashion using mirrored storage. Webroot, Inc th Street, Boulder, CO U.S.A. Tel:
8 Mirrored Storage Data mirroring is a core design feature of the entire Webroot service, which uniquely ensures that all mail in transit, or logged to a message area, is replicated in real-time. This concept has been fully extended to encompass the Message Archiving element of the service as follows. All messages received by the service s journal or filter mail servers are immediately replicated in real-time to a mirrored peer in the opposing data centre on reception of the message. Such an action ensures that the message is protected in case of primary server failure or complete data centre outage. The data centres operate in an Active-Active mode, thus allowing data to enter either site, but with full bi-directional replication. Once a decision has been taken to commit the message to archive storage, the primary centre will again split the message, causing a copy to be sent to the primary site and a copy to the secondary site. At this point, the messages are essentially processed as two separate entities by separated archiving servers, using dual separated storage technology. The result is two copies of the stored message, and two updated indexes in physically separated centres. The dual separated storage approach ensures action will not be mirrored to the secondary site if a data store or index become polluted through corruption, thus preserving the integrity of the data. This is in contrast to technologies that rely on real-time disk level replication, which run a higher risk of data corruptions affecting the redundant stores. All data is stored directly onto spinning disks, as opposed to backing off to tape. This gives near instant access to s held in the archiving system. Availability of Data Access With stored in multiple locations, the architecture enables High Availability user access. In the event that a data centre or server suffers an outage, or planned maintenance is required, availability is maintained by re-directing the access request to the data stored in the secondary location. In any archiving solution, the Index tends to be the window into the data store. Loss of an Index means downtime whilst it is re-built - if indeed it can be re-built. The Webroot Managed Archiving Service mitigates the impact risk of Index corruption by maintaining a mirrored index in addition to the mirrored storage of . Data Security Security of the data is a key requirement for any organization. The integrity of the archive is maintained by recording each message with the key meta-data items. The loss of an index means that it can be totally re-constructed from the message and its associated meta-data. The data centers are also continually monitored to ensure that the integrity of the data stores are maintained, using each store as a reference to the other. In the event of any integrity issues, network engineers are immediately alerted. All messages are encrypted upon storage with a 128-bit symmetric key. This level of encryption protects the data against data theft and prying-eyes. Each customer s data is stored in a logically separated data store (Figure 2 - Segregated Customer Data), which is identified by a unique business identity that is allocated by Webroot when the archiving system is provisioned. Every message has the Business Identity built into its naming and storage scheme. Prior to presenting a message or a search result containing a message reference to a user, the Business Identity of the message is correlated with the identity of the user to ensure that he/ she is authorized to access it. As already discussed, encrypted channels using TLS are used to protect the message on transit from the organization to the Data Centers, to ensure that sensitive internal is transferred in a secure manner. Access to data is protected through user authentication to the service over an HTTPS links to the Control Panel. Webroot, Inc th Street, Boulder, CO U.S.A. Tel:
9 ARCHIVE DIRECTOR CUSTOMER A CUSTOMER A CUSTOMER B CUSTOMER B CUSTOMER C CUSTOMER C STORAGE MIRRORED STORAGE Figure 2 - Segregated Customer Data Data Store Management It is a continual balancing act to determine how much to delete versus how much to store in order to comply with relevant legislation. Data Store Management functions are critical to ensure that archives don t become bloated, yet the letter of the law, whether it is legislative or corporate policy, is maintained Retention Periods The key to Data Store Management is the retention policy. Many archiving solutions only enable a single retention period to be set, which determines how long a message is to be kept before it is deleted. However, for increasing amounts of legislation this is not sufficient. The Webroot Archive Service is able to define both a minimum amount of time a message must be stored for and the maximum amount of time after which it must be deleted. These retention periods are set at storage time and cannot be post-modified, thus preventing the deletion of data that may be regarded as evidence within an impending enquiry. An automatic purge process runs daily to delete all that has reached its maximum purge period. Data may be stored for as long as the organization requires. Most legislation features clauses that require certain data to be stored for as long as seven years. Storage Management To ensure compliance, messages are stored in their original form. Consumption of storage space is minimized by enabling the archiving solution to use the same message for both the End-User and compliance system. All data is compressed before storing, which gives an average compression ratio of about 50%, however on a per message basis this is dependant upon content. Unlike many solutions which only index and display the HTML component, the solution indexes and displays the text parts as well. Since text and HTML can be very different in content, this is essential to preserve the integrity of the system from a compliance perspective, ensuring that data cannot be hidden. Webroot, Inc th Street, Boulder, CO U.S.A. Tel:
10 Aspects of Scalability Techniques employed by high-end Internet search engines are used to ensure that the system is highly performant and scalable. The system has been designed to scale over many petabytes of data without introduction of delays in search performance. When a search request is issued by a user through the Web interface, the search criteria are submitted to a high performance distributed search cluster in the currently active data centre. To ensure optimum performance, both in terms of data insertion and query response times, indexes are constrained in the size they may grow to. Once an index reaches its designated capacity, a new index is created. Multiple search processors are then employed to query these distributed indexes in parallel. Results from each search processor are collated by a master processor and returned to the user, which allows results to be typically returned within seconds. Based on the search results, the user may require access to one or more of the messages. Messages are stored in storage locations, designated by a unique storage allocator. Access requests are passed to a Storage Director, which is responsible for accessing the correct storage location, finding the stored message, decrypting the message and then passing it through to the user. The solution is highly efficient in that the message is exploded before being passed out, allowing the user to access key elements of the message in a quick and efficient manner, rather than requiring a complete download of the message. HTTPS RETRIEVAL SEARCH & RESULTS SEARCH PROCESSOR SEARCH PROCESSOR SEARCH PROCESSOR STORAGE INDEX INDEX INDEX Figure 3 - Scalable Search Architecture Webroot, Inc th Street, Boulder, CO U.S.A. Tel:
11 User Types The Archiving Service supports two key user types: the Compliance user and the End-User. The Compliance User accesses the messages through the main Control Panel and has the ability to access the entire archive if suitably privileged. The End-User accesses messages from the End-User site, which already provides access to the End-User spam logs, etc. As already discussed, both the Compliance Administrator and End-User have access to the same physical messages to maximize storage utilisation. However, message access is managed in a very different way for each, relative to the user s login credentials. Compliance Interface The compliance interface provided through the standard Web Control Panel, supports a strict compliance model. Only authorised users are granted access to the archive system, which is fully audited. Every search request must be accompanied with a quoted reason, which is stored in the audit log before the search is actually applied. In fact, if for any reason the audit system cannot generate an audit activity, the activity will be denied. Optionally, a set of Data Custodians can be defined, which cause an notification to be automatically sent to the Custodians when a search request is performed. The security of the Custodian system is such that when the system is first provisioned, Webroot will configure the Custodian list for the organization. Thereafter any changes to that list will result in a notification sent to the Custodians, informing them that they may have been deleted. Coupled with the audit logging, the system is protected against unauthorized use. As in keeping with the redundancy of the rest of the service, all audit logs are replicated in real-time between data centres to mitigate risk of loss. The compliance interface also provides full view of the stored meta-data parameters associated with a message - including retention periods and information regarding the original message filtering decisions. End User Interface End-Users neither have any visibility of the meta-data options such as retention periods, filter message modifications, nor do they have access to the audit data associated with a message. The message is logically regarded as belonging to the End-User who is therefore allowed to search and view as required. Ownership of a message is established by the logged in End-User having either been a sender or a recipient of the message. Note that in the case of internal messages that have been captured through Blind Carbon Copy Routing, End-User access will not be possible, as the original sender and recipient information is no longer available. Webroot, Inc th Street, Boulder, CO U.S.A. Tel:
12 Summary Messaging is a mission critical environment. It is estimated that up to 60% of critical business information is conveyed via , and with estimates placing the growth of at as much as 80% year on year 1, the case for an archiving system is clear. Effective solutions to meet compliance legislation, minimise risk through business continuity solutions and manage storage in a cost effective manner are three key drivers pushing archiving up the organization s IT priority list. As demonstrated in this technical paper, the Webroot Managed Archiving Service is more than capable of meeting these needs. Redundancy and scalability are two of the key building blocks for the system, ensuring that when your data is stored with us, it is safe and available on a 24 x 7 basis, using a full N+1 redundant infrastructure. Comprehensive search and analysis ensure that individuals can quickly and easily find the data that they need, whilst working in the knowledge that the fail safe auditing system is protecting the organization from abuse of the data. Finally, the entire solution can be deployed with no hardware or software required on site, thus simplifying the entire proposition, mitigating risk and removing what can be a very real headache from the IT Manager. About Webroot Webroot Software, Inc. provides industry-leading security software and services to consumers, enterprises and small to medium-sized businesses worldwide. The Boulder, Colorado based company s newest software-as-a-service (SaaS) offerings, Webroot Security SaaS and Webroot Web Security SaaS provide better manageability, better value and better protection than any other or web security solutions. Webroot s award-winning endpoint products, Webroot AntiSpyware Corporate Edition and Webroot AntiSpyware Corporate Edition with AntiVirus are comprehensive, centrally managed solutions that aggressively block, detect and eradicate malware on desktops across the network. To find out more, visit or call Messaging Technology Report 2003 [Radicati] 2008 All rights reserved. Webroot Software, Inc. Webroot, the Webroot icon, and the Webroot tagline are trademarks or registered trademarks of Webroot Software, Inc. in the United States and other countries. All other trademarks are properties of their respective owners. NO WARRANTY. Analysis based on research conducted by Webroot Software, Inc. The information is provided AS-IS and Webroot makes no warranty as to its accuracy or use. Any use of the technical documentation or the information contained herein is at your own risk. Documentation may include technical or other inaccuracies or typographical errors. Webroot reserves the right to make changes without prior notice. Certain data is available upon request. Webroot, Inc th Street, Boulder, CO U.S.A. Tel:
exchange@pam email archiving at its best
 exchange@pam email archiving at its best Whitepaper exchange@pam and Microsoft Exchange Server 2007 C O N T E N T exchange@pam and Microsoft Exchange Server 2007 What s new in the latest Microsoft Exchange
exchange@pam email archiving at its best Whitepaper exchange@pam and Microsoft Exchange Server 2007 C O N T E N T exchange@pam and Microsoft Exchange Server 2007 What s new in the latest Microsoft Exchange
Guideline for E-mail Services
 Guideline for E-mail Services Under the Policy on Information Technology, the Vice-President and Provost is authorized to establish guidelines for information technology services at the University of Toronto.
Guideline for E-mail Services Under the Policy on Information Technology, the Vice-President and Provost is authorized to establish guidelines for information technology services at the University of Toronto.
V1.4. Spambrella Email Continuity SaaS. August 2
 V1.4 August 2 Spambrella Email Continuity SaaS Easy to implement, manage and use, Message Continuity is a scalable, reliable and secure service with no set-up fees. Built on a highly reliable and scalable
V1.4 August 2 Spambrella Email Continuity SaaS Easy to implement, manage and use, Message Continuity is a scalable, reliable and secure service with no set-up fees. Built on a highly reliable and scalable
THE SECURITY OF HOSTED EXCHANGE FOR SMBs
 THE SECURITY OF HOSTED EXCHANGE FOR SMBs In the interest of security and cost-efficiency, many businesses are turning to hosted Microsoft Exchange for the scalability, ease of use and accessibility available
THE SECURITY OF HOSTED EXCHANGE FOR SMBs In the interest of security and cost-efficiency, many businesses are turning to hosted Microsoft Exchange for the scalability, ease of use and accessibility available
BUILT FOR YOU. Contents. Cloudmore Exchange
 BUILT FOR YOU Introduction is designed so it is as cost effective as possible for you to configure, provision and manage to a specification to suit your organisation. With a proven history of delivering
BUILT FOR YOU Introduction is designed so it is as cost effective as possible for you to configure, provision and manage to a specification to suit your organisation. With a proven history of delivering
Mailwall Remote Features Tour Datasheet
 Management Portal & Dashboard Mailwall Remote Features Tour Datasheet Feature Benefit Learn More Screenshot Cloud based portal Securely manage your web filtering policy wherever you are without need for
Management Portal & Dashboard Mailwall Remote Features Tour Datasheet Feature Benefit Learn More Screenshot Cloud based portal Securely manage your web filtering policy wherever you are without need for
Top 10 Features: Clearswift SECURE Email Gateway
 Top 10 Features: Clearswift SECURE Email Gateway Top 10 Features: Clearswift SECURE Email Gateway Modern business simply couldn t function without email. However, both incoming and outgoing messages can
Top 10 Features: Clearswift SECURE Email Gateway Top 10 Features: Clearswift SECURE Email Gateway Modern business simply couldn t function without email. However, both incoming and outgoing messages can
WHITE PAPER Email Archiving and Continuity
 WHITE PAPER Email Archiving and Continuity Roaring Penguin Software Inc. June 2011 Email Archiving and Continuity Introduction Email archiving is becoming important for many organizations for several reasons:
WHITE PAPER Email Archiving and Continuity Roaring Penguin Software Inc. June 2011 Email Archiving and Continuity Introduction Email archiving is becoming important for many organizations for several reasons:
TEAL: Transparent Email Archiving Library
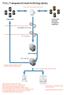 TEAL: Transparent Email Archiving Library 1. Users send & receive email as per normal 2. Existing customer filters remove spam & viruses Filters (Spam, Anti-Virus) 3. Interceptor agent takes a copy of
TEAL: Transparent Email Archiving Library 1. Users send & receive email as per normal 2. Existing customer filters remove spam & viruses Filters (Spam, Anti-Virus) 3. Interceptor agent takes a copy of
Projectplace: A Secure Project Collaboration Solution
 Solution brief Projectplace: A Secure Project Collaboration Solution The security of your information is as critical as your business is dynamic. That s why we built Projectplace on a foundation of the
Solution brief Projectplace: A Secure Project Collaboration Solution The security of your information is as critical as your business is dynamic. That s why we built Projectplace on a foundation of the
itg CloudBase is a suite of fully managed Hybrid & Private Cloud Services ready to support your business onwards and upwards into the future.
 Web Filtering Email Filtering Mail Archiving Cloud Backup Disaster Recovery Virtual Machines Private Cloud itg CloudBase is a suite of fully managed Hybrid & Private Cloud Services ready to support your
Web Filtering Email Filtering Mail Archiving Cloud Backup Disaster Recovery Virtual Machines Private Cloud itg CloudBase is a suite of fully managed Hybrid & Private Cloud Services ready to support your
nwstor Storage Security Solution 1. Executive Summary 2. Need for Data Security 3. Solution: nwstor isav Storage Security Appliances 4.
 CONTENTS 1. Executive Summary 2. Need for Data Security 3. Solution: nwstor isav Storage Security Appliances 4. Conclusion 1. EXECUTIVE SUMMARY The advantages of networked data storage technologies such
CONTENTS 1. Executive Summary 2. Need for Data Security 3. Solution: nwstor isav Storage Security Appliances 4. Conclusion 1. EXECUTIVE SUMMARY The advantages of networked data storage technologies such
Features and benefits guide for partners and their customers
 and benefits guide for partners and their customers Version 3.0 and Guide for Partners and their customers Security Anti Virus Proofpoint s own threat detection technology enables our email Anti-Virus
and benefits guide for partners and their customers Version 3.0 and Guide for Partners and their customers Security Anti Virus Proofpoint s own threat detection technology enables our email Anti-Virus
Mod 08: Exchange Online FOPE
 Office 365 for SMB Jump Start Mod 08: Exchange Online FOPE Chris Oakman Managing Partner Infrastructure Team Eastridge Technology Stephen Hall Owner & IT Consultant District Computers 1 Jump Start Schedule
Office 365 for SMB Jump Start Mod 08: Exchange Online FOPE Chris Oakman Managing Partner Infrastructure Team Eastridge Technology Stephen Hall Owner & IT Consultant District Computers 1 Jump Start Schedule
ARCHITECTURAL OVERVIEW E-mail Availability Service (EAS) with ActiveMailbox
 ARCHITECTURAL OVERVIEW E-mail Availability Service () with ActiveMailbox E-mail Availability Service () with ActiveMailbox For Microsoft Exchange -Centric Environments The Market Need for Through direct
ARCHITECTURAL OVERVIEW E-mail Availability Service () with ActiveMailbox E-mail Availability Service () with ActiveMailbox For Microsoft Exchange -Centric Environments The Market Need for Through direct
THIS SERVICE LEVEL AGREEMENT DEFINES THE SERVICE LEVELS PROVIDED TO YOU BY THE COMPANY.
 THIS SERVICE LEVEL AGREEMENT DEFINES THE SERVICE LEVELS PROVIDED TO YOU BY THE COMPANY. Capitalized terms used herein but not otherwise defined shall have their respective meanings set forth in the End
THIS SERVICE LEVEL AGREEMENT DEFINES THE SERVICE LEVELS PROVIDED TO YOU BY THE COMPANY. Capitalized terms used herein but not otherwise defined shall have their respective meanings set forth in the End
WHAT S NEW IN WEBSENSE TRITON RELEASE 7.8
 WHAT S NEW IN WEBSENSE TRITON RELEASE 7.8 Overview Global organizations are constantly battling with advanced persistent threats (APTs) and targeted attacks focused on extracting intellectual property
WHAT S NEW IN WEBSENSE TRITON RELEASE 7.8 Overview Global organizations are constantly battling with advanced persistent threats (APTs) and targeted attacks focused on extracting intellectual property
GiftWrap 4.0 Security FAQ
 GiftWrap 4.0 Security FAQ The information presented here is current as of the date of this document, and may change from time-to-time, in order to reflect s ongoing efforts to maintain the highest levels
GiftWrap 4.0 Security FAQ The information presented here is current as of the date of this document, and may change from time-to-time, in order to reflect s ongoing efforts to maintain the highest levels
Configuration Information
 This chapter describes some basic Email Security Gateway configuration settings, some of which can be set in the first-time Configuration Wizard. Other topics covered include Email Security interface navigation,
This chapter describes some basic Email Security Gateway configuration settings, some of which can be set in the first-time Configuration Wizard. Other topics covered include Email Security interface navigation,
Microsoft SQL Server 2008 R2 Enterprise Edition and Microsoft SharePoint Server 2010
 Microsoft SQL Server 2008 R2 Enterprise Edition and Microsoft SharePoint Server 2010 Better Together Writer: Bill Baer, Technical Product Manager, SharePoint Product Group Technical Reviewers: Steve Peschka,
Microsoft SQL Server 2008 R2 Enterprise Edition and Microsoft SharePoint Server 2010 Better Together Writer: Bill Baer, Technical Product Manager, SharePoint Product Group Technical Reviewers: Steve Peschka,
Reform PDC Document Workflow Solution Streamline capture and distribution. intuitive. lexible. mobile
 Reform PDC Document Workflow Solution Streamline capture and distribution intuitive lexible mobile Reform PDC Innovation and convenience to maximize efficiency. Your organization is unique so is its document
Reform PDC Document Workflow Solution Streamline capture and distribution intuitive lexible mobile Reform PDC Innovation and convenience to maximize efficiency. Your organization is unique so is its document
Account Restrictions Agreement [ARA] - Required by LuxSci HIPAA Accounts
![Account Restrictions Agreement [ARA] - Required by LuxSci HIPAA Accounts Account Restrictions Agreement [ARA] - Required by LuxSci HIPAA Accounts](/thumbs/24/3095735.jpg) Medical Privacy Version 2015.04.13 Account Restrictions Agreement [ARA] - Required by LuxSci HIPAA Accounts In order for Lux Scientiae, Incorporated (LuxSci) to ensure the security and privacy of all Electronic
Medical Privacy Version 2015.04.13 Account Restrictions Agreement [ARA] - Required by LuxSci HIPAA Accounts In order for Lux Scientiae, Incorporated (LuxSci) to ensure the security and privacy of all Electronic
GFI MailEssentials Online Archive Configuration and usage
 GFI MailEssentials Online Archive Configuration and usage Contents Retention policies 3 Message tagging 4 Access rights 5 Journaling 5 Accessing archived messages 7 Archive search / Viewing archived messages
GFI MailEssentials Online Archive Configuration and usage Contents Retention policies 3 Message tagging 4 Access rights 5 Journaling 5 Accessing archived messages 7 Archive search / Viewing archived messages
redcoal EmailSMS for MS Outlook and Lotus Notes
 redcoal EmailSMS for MS Outlook and Lotus Notes Technical Support: support@redcoal.com Or visit http://www.redcoal.com/ All Documents prepared or furnished by redcoal Pty Ltd remains the property of redcoal
redcoal EmailSMS for MS Outlook and Lotus Notes Technical Support: support@redcoal.com Or visit http://www.redcoal.com/ All Documents prepared or furnished by redcoal Pty Ltd remains the property of redcoal
Five essential considerations for your Exchange 2010 implementation
 Five essential considerations for your Exchange 2010 implementation Whitepaper Dell IT Management Software as a Service THIS WHITE PAPER IS FOR INFORMATIONAL PURPOSES ONLY, AND MAY CONTAIN TYPOGRAPHICAL
Five essential considerations for your Exchange 2010 implementation Whitepaper Dell IT Management Software as a Service THIS WHITE PAPER IS FOR INFORMATIONAL PURPOSES ONLY, AND MAY CONTAIN TYPOGRAPHICAL
Eiteasy s Enterprise Email Filter
 Eiteasy s Enterprise Email Filter Eiteasy s Enterprise Email Filter acts as a shield for companies, small and large, who are being inundated with Spam, viruses and other malevolent outside threats. Spammer
Eiteasy s Enterprise Email Filter Eiteasy s Enterprise Email Filter acts as a shield for companies, small and large, who are being inundated with Spam, viruses and other malevolent outside threats. Spammer
Dean Bank Primary and Nursery School. Secure Storage of Data and Cloud Storage
 Dean Bank Primary and Nursery School Secure Storage of Data and Cloud Storage January 2015 All school e-mail is disclosable under Freedom of Information and Data Protection legislation. Be aware that anything
Dean Bank Primary and Nursery School Secure Storage of Data and Cloud Storage January 2015 All school e-mail is disclosable under Freedom of Information and Data Protection legislation. Be aware that anything
Using EMC SourceOne Email Management in IBM Lotus Notes/Domino Environments
 Using EMC SourceOne Email Management in IBM Lotus Notes/Domino Environments Technology Concepts and Business Considerations Abstract EMC SourceOne Email Management enables customers to mitigate risk, reduce
Using EMC SourceOne Email Management in IBM Lotus Notes/Domino Environments Technology Concepts and Business Considerations Abstract EMC SourceOne Email Management enables customers to mitigate risk, reduce
BOWMAN SYSTEMS SECURING CLIENT DATA
 BOWMAN SYSTEMS SECURING CLIENT DATA 2012 Bowman Systems L.L.C. All Rights Reserved. This document and the information contained herein are the property of Bowman Systems L.L.C. and should be considered
BOWMAN SYSTEMS SECURING CLIENT DATA 2012 Bowman Systems L.L.C. All Rights Reserved. This document and the information contained herein are the property of Bowman Systems L.L.C. and should be considered
Injazat s Managed Services Portfolio
 Injazat s Managed Services Portfolio Overview Premium Managed Services to Transform Your IT Environment Injazat s Premier Tier IV Data Center is built to offer the highest level of security and reliability.
Injazat s Managed Services Portfolio Overview Premium Managed Services to Transform Your IT Environment Injazat s Premier Tier IV Data Center is built to offer the highest level of security and reliability.
Netwrix Auditor for Windows Server
 Netwrix Auditor for Windows Server Quick-Start Guide Version: 7.0 7/7/2015 Legal Notice The information in this publication is furnished for information use only, and does not constitute a commitment from
Netwrix Auditor for Windows Server Quick-Start Guide Version: 7.0 7/7/2015 Legal Notice The information in this publication is furnished for information use only, and does not constitute a commitment from
Spambrella Email Archiving Service Guide Service Guide
 April 4, 2013 Spambrella Email Archiving Service Guide Service Guide Spambrella and/or other noted Spambrella related products contained herein are registered trademarks or trademarks of Spambrella and/or
April 4, 2013 Spambrella Email Archiving Service Guide Service Guide Spambrella and/or other noted Spambrella related products contained herein are registered trademarks or trademarks of Spambrella and/or
Netwrix Auditor for Exchange
 Netwrix Auditor for Exchange Quick-Start Guide Version: 8.0 4/22/2016 Legal Notice The information in this publication is furnished for information use only, and does not constitute a commitment from Netwrix
Netwrix Auditor for Exchange Quick-Start Guide Version: 8.0 4/22/2016 Legal Notice The information in this publication is furnished for information use only, and does not constitute a commitment from Netwrix
Netwrix Auditor for SQL Server
 Netwrix Auditor for SQL Server Quick-Start Guide Version: 7.1 10/26/2015 Legal Notice The information in this publication is furnished for information use only, and does not constitute a commitment from
Netwrix Auditor for SQL Server Quick-Start Guide Version: 7.1 10/26/2015 Legal Notice The information in this publication is furnished for information use only, and does not constitute a commitment from
CALNET 3 Category 7 Network Based Management Security. Table of Contents
 State of California IFB STPD 12-001-B CALNET 3 Category 7 Network Based Security Table of Contents 7.2.1.4.a DDoS Detection and Mitigation Features... 1 7.2.2.3 Email Monitoring Service Features... 2 7.2.3.2
State of California IFB STPD 12-001-B CALNET 3 Category 7 Network Based Security Table of Contents 7.2.1.4.a DDoS Detection and Mitigation Features... 1 7.2.2.3 Email Monitoring Service Features... 2 7.2.3.2
Netwrix Auditor for Active Directory
 Netwrix Auditor for Active Directory Quick-Start Guide Version: 7.1 10/26/2015 Legal Notice The information in this publication is furnished for information use only, and does not constitute a commitment
Netwrix Auditor for Active Directory Quick-Start Guide Version: 7.1 10/26/2015 Legal Notice The information in this publication is furnished for information use only, and does not constitute a commitment
At a Glance. Key Benefits. Data sheet. A la carte User Module. Administration. Integrations. Enterprise SaaS
 HP Application Lifecycle Management on Software-as-a-Service Dedicated HP ALM/QC Offering Data sheet At a Glance The Dedicated HP ALM/QC offering is an on-demand Software-as-a-Service (SaaS) solution for
HP Application Lifecycle Management on Software-as-a-Service Dedicated HP ALM/QC Offering Data sheet At a Glance The Dedicated HP ALM/QC offering is an on-demand Software-as-a-Service (SaaS) solution for
Selecting Your Essential Cloud Services
 DATASHEET Selecting Your Essential Cloud Services Mimecast s flexible and scalable suite of essential cloud services for Microsoft Exchange removes the risks and complexities of business email management
DATASHEET Selecting Your Essential Cloud Services Mimecast s flexible and scalable suite of essential cloud services for Microsoft Exchange removes the risks and complexities of business email management
Technical White Paper BlackBerry Enterprise Server
 Technical White Paper BlackBerry Enterprise Server BlackBerry Enterprise Edition for Microsoft Exchange For GPRS Networks Research In Motion 1999-2001, Research In Motion Limited. All Rights Reserved Table
Technical White Paper BlackBerry Enterprise Server BlackBerry Enterprise Edition for Microsoft Exchange For GPRS Networks Research In Motion 1999-2001, Research In Motion Limited. All Rights Reserved Table
Netwrix Auditor for File Servers
 Netwrix Auditor for File Servers Quick-Start Guide Version: 7.0 7/7/2015 Legal Notice The information in this publication is furnished for information use only, and does not constitute a commitment from
Netwrix Auditor for File Servers Quick-Start Guide Version: 7.0 7/7/2015 Legal Notice The information in this publication is furnished for information use only, and does not constitute a commitment from
Simple Storage Service (S3)
 Simple Storage Service (S3) Amazon S3 is storage for the Internet. It is designed to make web-scale computing easier for developers. Amazon S3 provides a simple web services interface that can be used
Simple Storage Service (S3) Amazon S3 is storage for the Internet. It is designed to make web-scale computing easier for developers. Amazon S3 provides a simple web services interface that can be used
Hosted Exchange. Security Overview. Learn More: Call us at 877.634.2728. www.megapath.com
 Security Overview Learn More: Call us at 877.634.2728. www.megapath.com Secure and Reliable Hosted Exchange Our Hosted Exchange service is delivered across an advanced network infrastructure, built on
Security Overview Learn More: Call us at 877.634.2728. www.megapath.com Secure and Reliable Hosted Exchange Our Hosted Exchange service is delivered across an advanced network infrastructure, built on
XGENPLUS SECURITY FEATURES...
 Security Features Table of Contents TABLE OF CONTENTS... 2 1. INTRODUCTION... 3 2. XGENPLUS SECURITY FEATURES... 3 3. SERVER LEVEL FEATURES... 5 4. DOMAIN LEVEL FEATURES... 8 5. USER LEVEL FEATURES...
Security Features Table of Contents TABLE OF CONTENTS... 2 1. INTRODUCTION... 3 2. XGENPLUS SECURITY FEATURES... 3 3. SERVER LEVEL FEATURES... 5 4. DOMAIN LEVEL FEATURES... 8 5. USER LEVEL FEATURES...
Barracuda Message Archiver Administrator s Guide
 Barracuda Message Archiver Administrator s Guide Version 1.x Barracuda Networks Inc. 3175 S. Winchester Blvd. Campbell, CA 95008 http://www.barracuda.com Copyright Notice Copyright 2004-2008, Barracuda
Barracuda Message Archiver Administrator s Guide Version 1.x Barracuda Networks Inc. 3175 S. Winchester Blvd. Campbell, CA 95008 http://www.barracuda.com Copyright Notice Copyright 2004-2008, Barracuda
THIS SERVICE LEVEL AGREEMENT DEFINES THE SERVICE LEVELS PROVIDED TO YOU BY THE COMPANY ( Exchange My Mail ).
 THIS SERVICE LEVEL AGREEMENT DEFINES THE SERVICE LEVELS PROVIDED TO YOU BY THE COMPANY ( Exchange My Mail ). I. Service Definition. Exchange My Mail will provide Hosted Exchange and other Application Services
THIS SERVICE LEVEL AGREEMENT DEFINES THE SERVICE LEVELS PROVIDED TO YOU BY THE COMPANY ( Exchange My Mail ). I. Service Definition. Exchange My Mail will provide Hosted Exchange and other Application Services
MAILGUARD LIVE. Email Continuity. Trust the innovator to simplify cloud security
 MAILGUARD LIVE Email Continuity Trust the innovator to simplify cloud security One in five organisations experiences more than one hour of unplanned downtime each month. Osterman Research 2007 MAILGUARD
MAILGUARD LIVE Email Continuity Trust the innovator to simplify cloud security One in five organisations experiences more than one hour of unplanned downtime each month. Osterman Research 2007 MAILGUARD
Addressing Legal Discovery & Compliance Requirements
 Addressing Legal Discovery & Compliance Requirements A Comparison of and Archiving In today s digital landscape, the legal, regulatory and business requirements for email archiving continue to grow in
Addressing Legal Discovery & Compliance Requirements A Comparison of and Archiving In today s digital landscape, the legal, regulatory and business requirements for email archiving continue to grow in
Basic Email Funneling MX Verify and Redundancy. Why E-Mail Sorting Solutions? Why Vircom?
 Basic Email Funneling MX Verify and Redundancy Why E-Mail Sorting Solutions? Why Vircom? Why? Focused on Managed Messaging SaaS Security Systems Own Superior-Architected Infrastructure DATACENTERS: Carrier-class
Basic Email Funneling MX Verify and Redundancy Why E-Mail Sorting Solutions? Why Vircom? Why? Focused on Managed Messaging SaaS Security Systems Own Superior-Architected Infrastructure DATACENTERS: Carrier-class
Mimecast Services for Outlook (MSO4)
 Mimecast Services for Outlook (MSO4) End User Quick Start Guide for Outlook 2010/2013 Mimecast Services for Outlook (MSO 4) is a software application that integrates with your Microsoft Outlook. Once installed,
Mimecast Services for Outlook (MSO4) End User Quick Start Guide for Outlook 2010/2013 Mimecast Services for Outlook (MSO 4) is a software application that integrates with your Microsoft Outlook. Once installed,
Technical specifications
 Technical specifications PhD Manager is built on the Haplo open source platform. The Haplo platform provides a flexible database tailored to storing information about the activities in complex organisations.
Technical specifications PhD Manager is built on the Haplo open source platform. The Haplo platform provides a flexible database tailored to storing information about the activities in complex organisations.
GFI Product Manual. Administration and Configuration Manual
 GFI Product Manual Administration and Configuration Manual http://www.gfi.com info@gfi.com The information and content in this document is provided for informational purposes only and is provided "as is"
GFI Product Manual Administration and Configuration Manual http://www.gfi.com info@gfi.com The information and content in this document is provided for informational purposes only and is provided "as is"
MEDIAROOM. Products Hosting Infrastructure Documentation. Introduction. Hosting Facility Overview
 MEDIAROOM Products Hosting Infrastructure Documentation Introduction The purpose of this document is to provide an overview of the hosting infrastructure used for our line of hosted Web products and provide
MEDIAROOM Products Hosting Infrastructure Documentation Introduction The purpose of this document is to provide an overview of the hosting infrastructure used for our line of hosted Web products and provide
Shared Services Email Project: Steering Committee Business Requirements Review - Technical Clarifications
 Shared Services Email Project: Steering Committee Business Requirements Review - Technical Clarifications Item Functional Area Business Requirement CAB Trace Team Questions and Notes Steering Committee
Shared Services Email Project: Steering Committee Business Requirements Review - Technical Clarifications Item Functional Area Business Requirement CAB Trace Team Questions and Notes Steering Committee
T E C H N I C A L S A L E S S O L U T I O N
 Trend Micro Email Encryption Gateway 5.0 Deployment Guide January 2009 Trend Micro, Inc. 10101 N. De Anza Blvd. Cupertino, CA 95014 USA T +1.800.228.5651 / +1.408.257.1500 F +1.408.257.2003 www.trendmicro.com
Trend Micro Email Encryption Gateway 5.0 Deployment Guide January 2009 Trend Micro, Inc. 10101 N. De Anza Blvd. Cupertino, CA 95014 USA T +1.800.228.5651 / +1.408.257.1500 F +1.408.257.2003 www.trendmicro.com
Lesson Plans Configuring Exchange Server 2007
 Lesson Plans Configuring Exchange Server 2007 (Exam 70-236) Version 2.1 Table of Contents Course Overview... 2 Section 1.1: Server-based Messaging... 4 Section 1.2: Exchange Versions... 5 Section 1.3:
Lesson Plans Configuring Exchange Server 2007 (Exam 70-236) Version 2.1 Table of Contents Course Overview... 2 Section 1.1: Server-based Messaging... 4 Section 1.2: Exchange Versions... 5 Section 1.3:
How To Use Gfi Mailarchiver On A Pc Or Macbook With Gfi Email From A Windows 7.5 (Windows 7) On A Microsoft Mail Server On A Gfi Server On An Ipod Or Gfi.Org (
 GFI MailArchiver for Exchange 4 Manual By GFI Software http://www.gfi.com Email: info@gfi.com Information in this document is subject to change without notice. Companies, names, and data used in examples
GFI MailArchiver for Exchange 4 Manual By GFI Software http://www.gfi.com Email: info@gfi.com Information in this document is subject to change without notice. Companies, names, and data used in examples
REDCENTRIC MANAGED ARCHIVE SERVICE SERVICE DEFINITION
 REDCENTRIC MANAGED ARCHIVE SERVICE SERVICE DEFINITION SD005 V2.0 Issue Date 02 July 2014 1) SERVICE OVERVIEW Redcentric's Managed Archive Service allows customers to regain control of their Microsoft Exchange
REDCENTRIC MANAGED ARCHIVE SERVICE SERVICE DEFINITION SD005 V2.0 Issue Date 02 July 2014 1) SERVICE OVERVIEW Redcentric's Managed Archive Service allows customers to regain control of their Microsoft Exchange
UNCLASSIFIED. UK Email Archiving powered by Mimecast Service Description
 UNCLASSIFIED 11/12/2015 v2.2 UK Email Archiving powered by Mimecast Service Description Cobweb s UK Email Archiving, powered by Mimecast, provides businesses with a secure, scalable cloud-based message
UNCLASSIFIED 11/12/2015 v2.2 UK Email Archiving powered by Mimecast Service Description Cobweb s UK Email Archiving, powered by Mimecast, provides businesses with a secure, scalable cloud-based message
ensure prompt restart of critical applications and business activities in a timely manner following an emergency or disaster
 Security Standards Symantec shall maintain administrative, technical, and physical safeguards for the Symantec Network designed to (i) protect the security and integrity of the Symantec Network, and (ii)
Security Standards Symantec shall maintain administrative, technical, and physical safeguards for the Symantec Network designed to (i) protect the security and integrity of the Symantec Network, and (ii)
Solution Brief FortiMail for Service Providers. Nathalie Rivat
 Solution Brief FortiMail for Service Providers Nathalie Rivat Agenda FortiMail for Internet Service Providers Outbound antispam to prevent blacklisting MMS routing for Mobile Operators Inbound antispam
Solution Brief FortiMail for Service Providers Nathalie Rivat Agenda FortiMail for Internet Service Providers Outbound antispam to prevent blacklisting MMS routing for Mobile Operators Inbound antispam
are some of the key drivers behind mandates from executives to move IT infrastructure from on-premises to the cloud.
 W H I T E PA P E R Public Network External Application MTA Moving to the Cloud Important Things to Consider Before Migrating Your Messaging Infrastructure to the Cloud Fallback MTA External Corporate MTAs
W H I T E PA P E R Public Network External Application MTA Moving to the Cloud Important Things to Consider Before Migrating Your Messaging Infrastructure to the Cloud Fallback MTA External Corporate MTAs
IBX Business Network Platform Information Security Controls. 2015-02- 20 Document Classification [Public]
![IBX Business Network Platform Information Security Controls. 2015-02- 20 Document Classification [Public] IBX Business Network Platform Information Security Controls. 2015-02- 20 Document Classification [Public]](/thumbs/26/7758795.jpg) IBX Business Network Platform Information Security Controls 2015-02- 20 Document Classification [Public] Table of Contents 1. General 2 2. Physical Security 2 3. Network Access Control 2 4. Operating System
IBX Business Network Platform Information Security Controls 2015-02- 20 Document Classification [Public] Table of Contents 1. General 2 2. Physical Security 2 3. Network Access Control 2 4. Operating System
The data which you put into our systems is yours, and we believe it should stay that way. We think that means three key things.
 Privacy and Security FAQ Privacy 1. Who owns the data that organizations put into Google Apps? 2. When can Google employees access my account? 3. Who can gain access to my Google Apps administrative account?
Privacy and Security FAQ Privacy 1. Who owns the data that organizations put into Google Apps? 2. When can Google employees access my account? 3. Who can gain access to my Google Apps administrative account?
anomaly, thus reported to our central servers.
 Cloud Email Firewall Maximum email availability and protection against phishing and advanced threats. If the company email is not protected then the information is not safe Cloud Email Firewall is a solution
Cloud Email Firewall Maximum email availability and protection against phishing and advanced threats. If the company email is not protected then the information is not safe Cloud Email Firewall is a solution
Netwrix Auditor. Administrator's Guide. Version: 7.1 10/30/2015
 Netwrix Auditor Administrator's Guide Version: 7.1 10/30/2015 Legal Notice The information in this publication is furnished for information use only, and does not constitute a commitment from Netwrix Corporation
Netwrix Auditor Administrator's Guide Version: 7.1 10/30/2015 Legal Notice The information in this publication is furnished for information use only, and does not constitute a commitment from Netwrix Corporation
ANTI-SPAM SOLUTIONS TECHNOLOGY REPORT FEBRUARY 2006. Email Systems Managed Service. www.westcoastlabs.org
 ANTI-SPAM SOLUTIONS TECHNOLOGY REPORT FEBRUARY 2006 Email Systems Managed Service 2 ANTI-SPAM SOLUTIONS TECHNOLOGY REPORT Contents Email Systems Managed Service Test objectives and scenario...3 Test network...4
ANTI-SPAM SOLUTIONS TECHNOLOGY REPORT FEBRUARY 2006 Email Systems Managed Service 2 ANTI-SPAM SOLUTIONS TECHNOLOGY REPORT Contents Email Systems Managed Service Test objectives and scenario...3 Test network...4
Secure Email Frequently Asked Questions
 Secure Email Frequently Asked Questions Frequently Asked Questions Contents General Secure Email Questions and Answers Forced TLS Questions and Answers SecureMail Questions and Answers Glossary Support
Secure Email Frequently Asked Questions Frequently Asked Questions Contents General Secure Email Questions and Answers Forced TLS Questions and Answers SecureMail Questions and Answers Glossary Support
Remote Services. Managing Open Systems with Remote Services
 Remote Services Managing Open Systems with Remote Services Reduce costs and mitigate risk with secure remote services As control systems move from proprietary technology to open systems, there is greater
Remote Services Managing Open Systems with Remote Services Reduce costs and mitigate risk with secure remote services As control systems move from proprietary technology to open systems, there is greater
Veritas AdvisorMail. Email archiving, compliance, and ediscovery solution designed specifically for U.S. financial services companies
 Veritas AdvisorMail Email archiving, compliance, and ediscovery solution designed specifically for U.S. financial services companies Email compliance redefined Our new and improved version of redefines
Veritas AdvisorMail Email archiving, compliance, and ediscovery solution designed specifically for U.S. financial services companies Email compliance redefined Our new and improved version of redefines
Archiving. Mimecast Training. Student Workbook V 2.3
 Archiving Mimecast Training Student Workbook V 2.3 2014 by Mimecast Services Ltd. The information posted in this guide is for use by Mimecast customers only. Use of the guide is governed by the terms contained
Archiving Mimecast Training Student Workbook V 2.3 2014 by Mimecast Services Ltd. The information posted in this guide is for use by Mimecast customers only. Use of the guide is governed by the terms contained
MAXIMUM DATA SECURITY with ideals TM Virtual Data Room
 MAXIMUM DATA SECURITY with ideals TM Virtual Data Room WWW.IDEALSCORP.COM ISO 27001 Certified Account Settings and Controls Administrators control users settings and can easily configure privileges for
MAXIMUM DATA SECURITY with ideals TM Virtual Data Room WWW.IDEALSCORP.COM ISO 27001 Certified Account Settings and Controls Administrators control users settings and can easily configure privileges for
Enterprise Email Archive Managed Archiving & ediscovery Services User Manual
 Enterprise Email Archive Managed Archiving & ediscovery Services User Manual Copyright (C) 2012 MessageSolution Inc. All Rights Reserved Table of Contents Chapter 1: Introduction... 3 1.1 About MessageSolution
Enterprise Email Archive Managed Archiving & ediscovery Services User Manual Copyright (C) 2012 MessageSolution Inc. All Rights Reserved Table of Contents Chapter 1: Introduction... 3 1.1 About MessageSolution
Email archiving, compliance, and ediscovery solution designed specifically for U.S. financial services companies.
 Email archiving, compliance, and ediscovery solution designed specifically for U.S. financial services companies. Data Sheet: Symantec.cloud Email Compliance Redefined Our new and improved version of redefines
Email archiving, compliance, and ediscovery solution designed specifically for U.S. financial services companies. Data Sheet: Symantec.cloud Email Compliance Redefined Our new and improved version of redefines
Cloud Relay Solution. Whitepaper
 Cloud Relay Solution Whitepaper Abstract Cloud-based email is an attractive solution for organizations looking to provide optimum email service for their users at predictable costs. However, cloud-based
Cloud Relay Solution Whitepaper Abstract Cloud-based email is an attractive solution for organizations looking to provide optimum email service for their users at predictable costs. However, cloud-based
Premium Email Filtering MX Verify, Redundancy, Virus & Spam. Why E-mail Sorting Solutions? Why Vircom?
 Premium Email Filtering MX Verify, Redundancy, Virus & Spam Why E-mail Sorting Solutions? Why Vircom? Why? Focused on Managed Messaging SaaS Security Systems Own Superior-Architected Infrastructure DATACENTERS:
Premium Email Filtering MX Verify, Redundancy, Virus & Spam Why E-mail Sorting Solutions? Why Vircom? Why? Focused on Managed Messaging SaaS Security Systems Own Superior-Architected Infrastructure DATACENTERS:
Web Security Update. A Radicati Group, Inc. Webconference. The Radicati Group, Inc. Copyright March 2010, Reproduction Prohibited
 The Radicati Group, Inc. www.radicati.com Web Security Update A Radicati Group, Inc. Webconference The Radicati Group, Inc. Copyright March 2010, Reproduction Prohibited 9:30 am, PT March 25, 2010 Speakers
The Radicati Group, Inc. www.radicati.com Web Security Update A Radicati Group, Inc. Webconference The Radicati Group, Inc. Copyright March 2010, Reproduction Prohibited 9:30 am, PT March 25, 2010 Speakers
EMC DATA DOMAIN OPERATING SYSTEM
 EMC DATA DOMAIN OPERATING SYSTEM Powering EMC Protection Storage ESSENTIALS High-Speed, Scalable Deduplication Up to 58.7 TB/hr performance Reduces requirements for backup storage by 10 to 30x and archive
EMC DATA DOMAIN OPERATING SYSTEM Powering EMC Protection Storage ESSENTIALS High-Speed, Scalable Deduplication Up to 58.7 TB/hr performance Reduces requirements for backup storage by 10 to 30x and archive
Firewalls Overview and Best Practices. White Paper
 Firewalls Overview and Best Practices White Paper Copyright Decipher Information Systems, 2005. All rights reserved. The information in this publication is furnished for information use only, does not
Firewalls Overview and Best Practices White Paper Copyright Decipher Information Systems, 2005. All rights reserved. The information in this publication is furnished for information use only, does not
Additional services are also available according to your specific plan configuration.
 THIS SERVICE LEVEL AGREEMENT (SLA) DEFINES GUARANTEED SERVICE LEVELS PROVIDED TO YOU BY THE COMPANY. I. Service Definition SMS (Company) will provide You with Hosted Exchange and other Application Services
THIS SERVICE LEVEL AGREEMENT (SLA) DEFINES GUARANTEED SERVICE LEVELS PROVIDED TO YOU BY THE COMPANY. I. Service Definition SMS (Company) will provide You with Hosted Exchange and other Application Services
FTA Computer Security Workshop. Secure Email
 FTA Computer Security Workshop Secure Email March 8, 2007 Stan Wiechert, KDOR IS Security Officer Outline of Presentation The Risks associated with Email Business Constraints Secure Email Features Some
FTA Computer Security Workshop Secure Email March 8, 2007 Stan Wiechert, KDOR IS Security Officer Outline of Presentation The Risks associated with Email Business Constraints Secure Email Features Some
SERVICE LEVEL AGREEMENT
 SERVICE LEVEL AGREEMENT This Service Level Agreement (SLA) is provided by ECS and is intended to define services and responsibilities between ECS and customer. ECS along with contracted 3 rd party partners
SERVICE LEVEL AGREEMENT This Service Level Agreement (SLA) is provided by ECS and is intended to define services and responsibilities between ECS and customer. ECS along with contracted 3 rd party partners
Strengthen Microsoft Office 365 with Sophos Cloud and Reflexion
 Strengthen Microsoft Office 365 with Sophos Cloud and Reflexion Many organizations are embracing cloud technology and moving from complex, rigid on-premise infrastructure and software to the simplicity
Strengthen Microsoft Office 365 with Sophos Cloud and Reflexion Many organizations are embracing cloud technology and moving from complex, rigid on-premise infrastructure and software to the simplicity
EMC DATA DOMAIN OPERATING SYSTEM
 ESSENTIALS HIGH-SPEED, SCALABLE DEDUPLICATION Up to 58.7 TB/hr performance Reduces protection storage requirements by 10 to 30x CPU-centric scalability DATA INVULNERABILITY ARCHITECTURE Inline write/read
ESSENTIALS HIGH-SPEED, SCALABLE DEDUPLICATION Up to 58.7 TB/hr performance Reduces protection storage requirements by 10 to 30x CPU-centric scalability DATA INVULNERABILITY ARCHITECTURE Inline write/read
InsightCloud. www.insightcloud.com. Hosted Desktop Service. What is InsightCloud? What is SaaS? What are the benefits of SaaS?
 What is InsightCloud? InsightCloud is a web portal enabling Insight customers to purchase and provision a wide range of Cloud services in a straightforward and convenient manner. What is SaaS? Software
What is InsightCloud? InsightCloud is a web portal enabling Insight customers to purchase and provision a wide range of Cloud services in a straightforward and convenient manner. What is SaaS? Software
Technical Proposition. Security
 Technical Proposition ADAM Software NV The global provider of media workflow and marketing technology software ADAM Software NV adamsoftware.net info@adamsoftware.net Why Read this Technical Proposition?
Technical Proposition ADAM Software NV The global provider of media workflow and marketing technology software ADAM Software NV adamsoftware.net info@adamsoftware.net Why Read this Technical Proposition?
Chapter 8: Security Measures Test your knowledge
 Security Equipment Chapter 8: Security Measures Test your knowledge 1. How does biometric security differ from using password security? Biometric security is the use of human physical characteristics (such
Security Equipment Chapter 8: Security Measures Test your knowledge 1. How does biometric security differ from using password security? Biometric security is the use of human physical characteristics (such
MailEnable Connector for Microsoft Outlook
 MailEnable Connector for Microsoft Outlook Version 2.23 This guide describes the installation and functionality of the MailEnable Connector for Microsoft Outlook. Features The MailEnable Connector for
MailEnable Connector for Microsoft Outlook Version 2.23 This guide describes the installation and functionality of the MailEnable Connector for Microsoft Outlook. Features The MailEnable Connector for
Omniquad Exchange Archiving
 Omniquad Exchange Archiving Deployment and Administrator Guide Manual version 3.1.2 Revision Date: 20 May 2013 Copyright 2012 Omniquad Ltd. All rights reserved. Omniquad Ltd Crown House 72 Hammersmith
Omniquad Exchange Archiving Deployment and Administrator Guide Manual version 3.1.2 Revision Date: 20 May 2013 Copyright 2012 Omniquad Ltd. All rights reserved. Omniquad Ltd Crown House 72 Hammersmith
Securing enterprise collaboration through email and file sharing on a unified platform
 Axway MailGate SC Securing enterprise collaboration through email and file sharing on a unified platform Email is the primary collaboration tool employees use to share information and send large files.
Axway MailGate SC Securing enterprise collaboration through email and file sharing on a unified platform Email is the primary collaboration tool employees use to share information and send large files.
FortiMail Email Filtering. Course 221 (for FortiMail v5.0) Course Overview
 FortiMail Email Filtering Course 221 (for FortiMail v5.0) Course Overview FortiMail Email Filtering is a 2-day instructor-led course with comprehensive hands-on labs to provide you with the skills needed
FortiMail Email Filtering Course 221 (for FortiMail v5.0) Course Overview FortiMail Email Filtering is a 2-day instructor-led course with comprehensive hands-on labs to provide you with the skills needed
Using email over FleetBroadband
 Using email over FleetBroadband Version 01 20 October 2007 inmarsat.com/fleetbroadband Whilst the information has been prepared by Inmarsat in good faith, and all reasonable efforts have been made to ensure
Using email over FleetBroadband Version 01 20 October 2007 inmarsat.com/fleetbroadband Whilst the information has been prepared by Inmarsat in good faith, and all reasonable efforts have been made to ensure
Email Archiving, Retrieval and Analysis The Key Issues
 Email Archiving, Retrieval and Analysis The "If you are going to find a smoking gun, you will find it in email." Abstract Organisations are increasingly dependent on email for conducting business, internally
Email Archiving, Retrieval and Analysis The "If you are going to find a smoking gun, you will find it in email." Abstract Organisations are increasingly dependent on email for conducting business, internally
IBM System Storage DR550
 An innovative information-retention solution IBM System Storage DR550 Highlights Repository for all kinds of Offers low TCO by using multiple content structured and storage tiers (disk, tape, unstructured
An innovative information-retention solution IBM System Storage DR550 Highlights Repository for all kinds of Offers low TCO by using multiple content structured and storage tiers (disk, tape, unstructured
Content Teaching Academy at James Madison University
 Content Teaching Academy at James Madison University 1 2 The Battle Field: Computers, LANs & Internetworks 3 Definitions Computer Security - generic name for the collection of tools designed to protect
Content Teaching Academy at James Madison University 1 2 The Battle Field: Computers, LANs & Internetworks 3 Definitions Computer Security - generic name for the collection of tools designed to protect
Information Security Policy September 2009 Newman University IT Services. Information Security Policy
 Contents 1. Statement 1.1 Introduction 1.2 Objectives 1.3 Scope and Policy Structure 1.4 Risk Assessment and Management 1.5 Responsibilities for Information Security 2. Compliance 3. HR Security 3.1 Terms
Contents 1. Statement 1.1 Introduction 1.2 Objectives 1.3 Scope and Policy Structure 1.4 Risk Assessment and Management 1.5 Responsibilities for Information Security 2. Compliance 3. HR Security 3.1 Terms
Hosted Email Managed by Email Specialists
 Hosted Email Managed by Email Specialists The Mailtrust email system is the premium hosted email platform that provides your business with powerful, secure, and reliable email with absolutely no maintenance
Hosted Email Managed by Email Specialists The Mailtrust email system is the premium hosted email platform that provides your business with powerful, secure, and reliable email with absolutely no maintenance
Setting up Microsoft Office 365
 Integration Guide Revision G McAfee SaaS Email Protection Securing Exchange Online in Microsoft Office 365 Setting up Microsoft Office 365 Use this guide to configure Microsoft Office 365 and Microsoft
Integration Guide Revision G McAfee SaaS Email Protection Securing Exchange Online in Microsoft Office 365 Setting up Microsoft Office 365 Use this guide to configure Microsoft Office 365 and Microsoft
ILM et Archivage Les solutions IBM
 Information Management ILM et Archivage Les solutions IBM Dr. Christian ARNOUX Consultant Information Management IBM Suisse, Software Group 2007 IBM Corporation IBM Strategy for Enterprise Content Compliance
Information Management ILM et Archivage Les solutions IBM Dr. Christian ARNOUX Consultant Information Management IBM Suisse, Software Group 2007 IBM Corporation IBM Strategy for Enterprise Content Compliance
Cloud Computing: Legal Risks and Best Practices
 Cloud Computing: Legal Risks and Best Practices A Bennett Jones Presentation Toronto, Ontario Lisa Abe-Oldenburg, Partner Bennett Jones LLP November 7, 2012 Introduction Security and Data Privacy Recent
Cloud Computing: Legal Risks and Best Practices A Bennett Jones Presentation Toronto, Ontario Lisa Abe-Oldenburg, Partner Bennett Jones LLP November 7, 2012 Introduction Security and Data Privacy Recent
Copyright 2012 Trend Micro Incorporated. All rights reserved.
 Trend Micro Incorporated reserves the right to make changes to this document and to the products described herein without notice. Before installing and using the software, please review the readme files,
Trend Micro Incorporated reserves the right to make changes to this document and to the products described herein without notice. Before installing and using the software, please review the readme files,
