Ensuring Compliance to Sarbanes-Oxley through Privileged Identity & Information Management. White Paper. V Balasubramanian. ZOHO Corp.
|
|
|
- Pearl Hunt
- 8 years ago
- Views:
Transcription
1 Ensuring Compliance to Sarbanes-Oxley through Privileged Identity & Information Management White Paper V Balasubramanian ZOHO Corp. Disclaimer: This document is not intended to be a complete guide or legal advice to Sarbanes-Oxley. This is just to propose a solution for SOX-compliance. If you have a real-situation, satisfy yourself about the effectiveness of the solution through proper evaluation.
2 2 Ensuring Compliance to Sarbanes-Oxley through Privileged Identity & Information Management Abstract Enterprises dealing with public funds are required to comply to Sarbanes-Oxley (SOX) Act. Organizations are looking for a single, complete, low-cost, enterprisewide solution that could take care of all their SOX-compliance needs. This White Paper discusses the SOX compliance challenges and the problems faced by the IT administrators, who are mandated with the task of ensuring compliance to SOX. It explains how Privileged Identity and Information Management (PIIM) solutions could ensure effective internal controls and serve the enterprise-wide SOXcompliance needs. The vital ingredients that one should expect in a PIIM solution and the factors to ponder before zeroing-in on a PIIM solution, have also been dealt with.
3 3 Ensuring Compliance to Sarbanes-Oxley through Privileged Identity & Information Management Contents Ensuring Compliance to SOX Act The Challenge 4 Scenario Today. 5 The Way out... 6 What to look for in a PIIM Solution. 7 A Typical Business Environment.. 11 Conclusion
4 4 Ensuring Compliance to Sarbanes-Oxley through Privileged Identity & Information Management Ensuring Compliance to SOX The Challenge The Public Company Accounting Reform and Investor Protection Act of 2002, popularly known as the Sarbanes-Oxley Act, enacted in the U.S in the wake of unprecedented, large-scale financial scandals, mandates the top management of public finance companies to incorporate strong internal controls and ensure accuracy and transparency in public financial disclosures. Perhaps, the biggest challenge with SOX Act is that it just asks the companies to ensure accuracy and transparency in financial disclosure and establish internal controls without prescribing anything like best practices or other specific details. The objective of SOX Act is straight-forward: Assuring that the information, which the investing public rely on to make investment decisions are trustworthy, accurate and complete. But, ensuring compliance to this objective is indeed a daunting task as there are numerous factors that could lead to inaccurate financial reporting. Auditors and analysts have listed out some of the prime factors that dampen the accuracy of financial disclosure: As laid down in SOX Act itself, lack of proper internal control specifically, lack of an effective mechanism to restrict access to sensitive financial information, is often the key for malpractices in organizations The internal control mechanism should be capable of detecting and preventing the malpractices/frauds in organizations. If there are rooms for fraud, the financial disclosures will be inaccurate The biggest challenge with SOX Act is that it just asks the companies to ensure accuracy and transparency in financial disclosure and establish internal controls without prescribing anything like best practices or other specific details. Lack of informative reports that depict information on who has access to what information in the organization Each and every activity of a privileged user should be monitored in the organization. Lack of such a monitoring capability is a potential cause for mis-appropriation of funds Whenever a security breach occurs, the organization should be capable of detecting that quickly. Lack of such a mechanism will lead to holes in fraud prevention From the foregoing, it is clear that effective internal control forms the backbone of SOX.
5 5 Ensuring Compliance to Sarbanes-Oxley through Privileged Identity & Information Management Though SOX Act targets the top-brass like the CEOs, CFOs and Board of Directors of the organizations by holding them directly responsible for mal-practices, the implementation part for compliance largely rests with the staff at the lower level. The administrators and IT Managers, in particular, are responsible for defining SOX compliance policies and also demonstrate that the organization complies to the policies defined. The administrators mandated with the task of ensuring compliance to SOX are bogged by several questions: How to select an IT solution that can help in ensuring compliance to SOX? What to look for in the solution? Our financial data are spread across diverse systems, applications, databases and servers. How to generate a unified, enterprise-wide SOX compliance report? What are all the reports that SOX auditors expect? When the data pertaining to several clients are being managed, how to generate separate SOX compliance reports for each client separately? Where to store the audit trails related to SOX? How to generate reports for SOX compliance from the audit trails? How to detect and prevent misuse of data by privileged users? Scenario Today Today, organizations are looking for a complete solution that could take care of all their SOX-compliance headaches. But, such solutions are prohibitively expensive. Industry researchers have estimated that SOX and other financial governance spending in the U.S will reach $6.2B in 2008, up by nearly 2 per cent from What does SOX Mandate? Of the 11 sections of SOX, section 404 lays the foundation on how IT can aid SOX compliance. Section 302 and 802 are also relevant to some extent. Section Management Assessment of Internal Controls This section pertains to the guidelines laid down by the Securities and Exchange Commission on what SOX demands. According to the SEC, companies must: "Include in their annual reports a report of management on the company's internal control over financial reporting". The control report must include: 1. "A statement of management's responsibility for establishing and maintaining adequate internal control over financial reporting." 2. "Management's assessment of the effectiveness of the company's internal control over financial reporting." 3. "A statement identifying the framework used by management to evaluate the effectiveness of the company's internal control over financial reporting." 4. "A statement that the registered public accounting firm that audited the company's financial statements The SOX compliance costs for smaller organizations, in particular is very disproportionate. The U.S. Securities and Exchange
6 6 Ensuring Compliance to Sarbanes-Oxley through Privileged Identity & Information Management Commission has predicted compliance costs of $91,000 for smaller public companies, technically those with less than $75 million in market capitalization. Therefore, organizations are caught in a fix. They are required to comply to SOX, but not in a position to spend huge money. It is equally difficult to find a single solution that could take care of all their SOX compliance needs. The Way out SOX lays stress on internal controls on access to privileged information, resources and applications. Deploying a Privileged Identity and Information Management (PIIM) Solution is one of the ways to achieve effective internal control in organizations. All the documents, spreadsheets and reports containing sensitive financial data could be stored in a repository, which would serve as a secure, central vault. Ownership for the documents/data could be clearly-defined and the documents could be shared with the privileged users on need basis. Similarly, the privileged identities, whose passwords are typically shared to gain access to databases, servers and other IT resources containing financial data, could be stored in the
7 7 Ensuring Compliance to Sarbanes-Oxley through Privileged Identity & Information Management central vault. This would help in restricting access to these resources to a few privileged users alone. Thus, PIIM solution will become the centralized repository for all sensitive data. It will act as the centralized control point for the entire organization from the standpoint of SOX. The reports generated by the PIIM solution, with special emphasis on SOX related details, will provide a unified view of the happenings in the organization. A single PIIM solution could serve almost the entire SOX compliance requirements of organizations. With the availability of affordable PIIM solutions in the market, the cost of deploying and maintaining such a solution would be very less, in fact, just a fraction of the cost involved in deploying many compliance management solutions. What to look for in the Privileged Identity & Information Management (PIIM) Solution from SOX Compliance Perspective? Document Vault The solution should be capable of securely storing documents containing sensitive financial data, in addition to storing privileged identities / passwords. This is a pre-requisite for SOX compliance. Ownership & Sharing Model There should be provision for establishing clear-cut ownership for the passwords and documents. Only the owner should have exclusive privileges to access, view and change the document/password. Optionally, there should be provision to share the documents/passwords with other users on need basis, with fine-grained access restrictions. SOX emphasizes on segregation of duties. The ownership and sharing model is essential to achieve segregation with respect to SOX related information in the organization. Section Corporate Responsibility for Financial Reports For each company filing periodic statutory financial reports under section 13(a) or 15(d) of the Securities Exchange Act of 1934 it is required to include certifications that: 1. The signing officers have reviewed the report. 2. The report does not contain any material untrue statements or material omission to make the statements considered misleading. 3. The financial statements and other related financial information fairly present the financial condition and the results of operations in all material respects. 4. The signing officers are (a) responsible for internal controls (b) designed such internal controls (c) have evaluated these internal controls within the previous ninety days and (d) have reported on their findings. 5. The signing officers have disclosed (a) all deficiencies in the design or operation of internal controls and (b) any information on any fraud that involves employees who are involved with internal activities. 6. The signing officers have indicated any significant changes in internal controls or related factors that could have a negative impact on the internal controls. Section 802: Corporate and Criminal Fraud Accountability 1. This section mandates that records be maintained for seven years after the auditor concludes the audit 2. Also, specifies the criminal penalties for altering records
8 8 Ensuring Compliance to Sarbanes-Oxley through Privileged Identity & Information Management Secure Data Storage & Communication All sensitive data stored in the PIIM application such as passwords, files, digital keys, account names, IP addresses etc should be encrypted using government approved and industry standard encryption algorithms like AES and stored in the database. All data communication between the user interface and database should be encrypted. In the case of web interfaces, the communication should be through secure http. Account Activity Monitoring Maintaining the passwords of sensitive resources in the centralized control point alone may not be sufficient for completely tracking the activities performed by the privileged users on the resources. In such cases, the PIIM application should have the provision for monitoring the user activities in resources through detailed access logs. Periodic Password Rotation One of the important ways to protect IT resources from unauthorized access is to rotate the passwords of the resources at periodic intervals. Manually carrying out the password rotation would prove to be cumbersome. The PIIM solution should have provision to carry out periodic, automatic password rotation. Also, the solution should provide reports showing the frequency of password rotation as part of SOX compliance reports to be submitted to the auditors. Comprehensive Audit Trails All activities happening in the system should be accurately captured as audit trails. Comprehensive auditing is, in fact, the cornerstone of SOX. When SOX-related information is stored in the PIIM application, all activities performed by the privileged user should be audited. Document/password access, changes done, login/logout events, failed login attempts, changes to user privileges and all other operations performed should be audited. Details on who, what and when of user actions recorded chronologically would help in fixing accountability issues. Tamper-proof Audit Trails Audit trails recorded by the central vault should not only be accurate, but also tamper-proof. Otherwise, malicious users would delete the records to conceal their actions. Audit trails will then be of no use to fix accountability issues. There should be no provision to delete the audit trails as Section 802 of SOX mandates that audit records be maintained for seven years after
9 9 Ensuring Compliance to Sarbanes-Oxley through Privileged Identity & Information Management the auditor concludes the audit. Besides, alarms should be generated when an attempt is made to delete the trails. Request-Release Mechanism The application should have provision for some sort of dual control when it comes to providing access to sensitive documents/passwords stored in the central vault. When a user needs access to the document/password, a request for authorization would be sent to the administrator, who would validate the request and authorize access. Risk Analysis and Management Despite all the policies, standards, controls and precautions, the organizations might have to face innumerable threats to security. SOX mandates the presence of a sound risk analysis and management system in the organization to protect the financial data. Therefore, the application should have provisions for analyzing and managing various risks to the data. For example, inactive users/resources are vulnerable to hacking and attacks. The application should provide a report on the inactive users/resources. Such users and resources need to be isolated and monitored. Failed login attempts are another indication of potential hacking attempts and they also need to be monitored. Frequently accessed data, passwords and resources and records should be isolated and monitored. Out-of-the-box SOX Compliance Reports SOX mandates the presence of a sound risk analysis and management system in the organization to protect the financial data. When the very purpose of deploying a PIIM solution is for managing the SOX-related information, it should have provision for generating out-of-the-box reports depicting compliance to SOX. Particularly, the report should clearly depict who has access to what resources in the organization. This is the most basic requirement of SOX and automatic generation of such report would save a great deal of time for the administrators. SOX auditors are required to certify the assessment of the effectiveness of internal controls established in the organization. So, apart from showing who has access to what, there must be provision for proving other security measures such as periodic password rotation, enforcement of strong password policies, ensuring access is removed when an employee leaves the organization, eliminating need to share passwords to access systems and automating password reset process to eliminate human error.
10 10 Ensuring Compliance to Sarbanes-Oxley through Privileged Identity & Information Management Custom Reports Apart from the ready-to-use reports, the application should have provision for generating custom reports to prove compliance to SOX. For example, financial organization may be dealing with the data pertaining to different clients. Some of the clients may be big companies and would require SOX compliance report pertaining to their data alone. In that case, the administrators in the financial company will have the need to generate multiple SOX compliance reports. The PIIM solution should essentially have provision for easily filtering out the required data and generate SOX compliance reports based on that. Real-time Alerts & Notifications For detecting and preventing frauds in organizations, SOX lays stress on real-time notifications on access to sensitive data. To facilitate this, the application should have provision for sending alerts to the owners of documents/resources on various actions such as data/password access, change in access permissions, change in user roles, password expiry, automatic password reset etc. Backup & Disaster Recovery For detecting and preventing frauds in organizations, SOX lays stress on real-time notifications on access to sensitive data. SOX mandates organizations to have provision for disaster recovery. When all sensitive financial data are stored in the application, it should have a robust disaster recovery mechanism. The data should be backedup as and when there occurs a change in the data. There should also be provision for recovering the data quickly after a disaster. Continuous Availability of Information Financial data stored in the application should be available for access at anytime as desired by the users. Once the application is deployed in production with all data, administrators would be heavily dependent on the application availability for retrieving documents/passwords. Continuous availability of the PIIM solution would be crucial in such scenarios. Otherwise, at the most wanted time, users would end up in not getting the required document/password and it may lead to problems, including security issues. Affordable Price Though PIIM applications would provide high value for your buck by simplifying the compliance initiatives, the cost of the solution should not be too high to damage your pockets. The price of the solution should suit your IT budget and should be capable of providing rapid Return On Investment (ROI).
11 11 Ensuring Compliance to Sarbanes-Oxley through Privileged Identity & Information Management A typical business environment requiring ways to ensure SOX Compliance Consider a financial enterprise having critical financial data stored in 500 documents and 300 spreadsheets in diverse systems. Besides, other sensitive data are maintained in 100 file servers and databases. About 200 users, with different roles would require access to specific data. Information pertaining to different clients is stored. This is how the PIIM Solution will help: All the 200 users will get accounts in PIIM solution with well-defined access permissions and roles. The users will be grouped based on departments/divisions. The 500 documents and 300 spreadsheets will be stored in the PIIM application and specific ownership will be defined. The passwords of 100 file servers and databases will be stored in the PIIM solution and access permissions will be defined. The resources will be grouped for carrying out operations in bulk. The resources/resource groups would be shared with users/usergroups on need basis. PIIM solution will become the central control point and all the users will have to access it first to get the data / access other resources. Reports on user activities can be generated based on different user roles. Thus, a centralized management environment will be in place.
12 12 Ensuring Compliance to Sarbanes-Oxley through Privileged Identity & Information Management Conclusion Protection of sensitive financial data by establishing robust internal control processes and demonstrating the effectiveness of the controls through reports, form the crux of the SOX. Deployment of a PIIM solution to manage critical financial data would prove to be cost effective and highly productive as it could act as the centralized control point for information access. For ensuring SOX compliance, the application would act as an enterprise-wide solution. With a central vault, most of your SOX-related information protection activities could be automated. Highly-skilled IT Managers and administrators need not have to spend their time generating SOX compliance reports. They can cash-in on the automation capabilities of PIIM application and meet the SOX Compliance requirements with ease and face the SOX audits with comfort. Introducing ManageEngine Password Manager Pro Password Manager Pro (PMP) is a web-based Privileged Identity and Information Management Solution for enterprises to control the access to shared administrative / privileged passwords of any 'enterprise resource' such as servers, databases, network devices, applications etc. PMP enables IT managers to enforce standard password management practices such as maintaining a central repository of all passwords, usage of strong passwords, frequent changing of sensitive passwords and controlling user access to shared passwords across the enterprise. PMP could ensure effective internal controls and prove as a potential solution for SOX compliance. It is available at costs affordable to SMBs. For more details on PMP, visit ZOHO Corp. (formerly AdventNet Inc.) 4900 Hopyard Rd., Suite 310, Pleasanton, CA 94588, USA Phone: Fax: Website: For Queries: passwordmanagerpro-support@manageengine.com
How IT Can Aid Sarbanes Oxley Compliance
 ZOHO Corp. How IT Can Aid Sarbanes Oxley Compliance Whitepaper Notice: This document represents the current view of ZOHO Corp. and makes no representations or warranties with respect to the contents as
ZOHO Corp. How IT Can Aid Sarbanes Oxley Compliance Whitepaper Notice: This document represents the current view of ZOHO Corp. and makes no representations or warranties with respect to the contents as
Privileged. Account Management. Accounts Discovery, Password Protection & Management. Overview. Privileged. Accounts Discovery
 Overview Password Manager Pro offers a complete solution to control, manage, monitor and audit the entire life-cycle of privileged access. In a single package it offers three solutions - privileged account
Overview Password Manager Pro offers a complete solution to control, manage, monitor and audit the entire life-cycle of privileged access. In a single package it offers three solutions - privileged account
The Role of Password Management in Achieving Compliance
 White Paper The Role of Password Management in Achieving Compliance PortalGuard PO Box 1226 Amherst, NH 03031 USA Phone: 603.547.1200 Fax: 617.674.2727 E-mail: sales@portalguard.com Website: www.portalguard.com
White Paper The Role of Password Management in Achieving Compliance PortalGuard PO Box 1226 Amherst, NH 03031 USA Phone: 603.547.1200 Fax: 617.674.2727 E-mail: sales@portalguard.com Website: www.portalguard.com
Sarbanes-Oxley Compliance for Cloud Applications
 Sarbanes-Oxley Compliance for Cloud Applications What Is Sarbanes-Oxley? Sarbanes-Oxley Act (SOX) aims to protect investors and the general public from accounting errors and fraudulent practices. For this
Sarbanes-Oxley Compliance for Cloud Applications What Is Sarbanes-Oxley? Sarbanes-Oxley Act (SOX) aims to protect investors and the general public from accounting errors and fraudulent practices. For this
HIPAA: MANAGING ACCESS TO SYSTEMS STORING ephi WITH SECRET SERVER
 HIPAA: MANAGING ACCESS TO SYSTEMS STORING ephi WITH SECRET SERVER With technology everywhere we look, the technical safeguards required by HIPAA are extremely important in ensuring that our information
HIPAA: MANAGING ACCESS TO SYSTEMS STORING ephi WITH SECRET SERVER With technology everywhere we look, the technical safeguards required by HIPAA are extremely important in ensuring that our information
MASSIVE NETWORKS Online Backup Compliance Guidelines... 1. Sarbanes-Oxley (SOX)... 2. SOX Requirements... 2
 MASSIVE NETWORKS Online Backup Compliance Guidelines Last updated: Sunday, November 13 th, 2011 Contents MASSIVE NETWORKS Online Backup Compliance Guidelines... 1 Sarbanes-Oxley (SOX)... 2 SOX Requirements...
MASSIVE NETWORKS Online Backup Compliance Guidelines Last updated: Sunday, November 13 th, 2011 Contents MASSIVE NETWORKS Online Backup Compliance Guidelines... 1 Sarbanes-Oxley (SOX)... 2 SOX Requirements...
Combating Cyber Security Threats
 Threat, Threat Everywhere; Cyber-Criminals on the Prowl Combating Cyber Security Threats V Balasubramanian, ManageEngine ManageEngine (A Division of ZOHO Corp.) 2 Abstract Of late, cyber-criminal activities
Threat, Threat Everywhere; Cyber-Criminals on the Prowl Combating Cyber Security Threats V Balasubramanian, ManageEngine ManageEngine (A Division of ZOHO Corp.) 2 Abstract Of late, cyber-criminal activities
Active Directory Auditing The Need and Result
 Jai hanumaan www.lepide.com Active Directory Auditing The Need and Result Whitepaper 2013 What are IT Audits? Increasing number of cases of malpractices and lackadaisical approach towards handling sensitive
Jai hanumaan www.lepide.com Active Directory Auditing The Need and Result Whitepaper 2013 What are IT Audits? Increasing number of cases of malpractices and lackadaisical approach towards handling sensitive
MANAGED FILE TRANSFER: 10 STEPS TO SOX COMPLIANCE
 WHITE PAPER MANAGED FILE TRANSFER: 10 STEPS TO SOX COMPLIANCE 1. OVERVIEW Do you want to design a file transfer process that is secure? Or one that is compliant? Of course, the answer is both. But it s
WHITE PAPER MANAGED FILE TRANSFER: 10 STEPS TO SOX COMPLIANCE 1. OVERVIEW Do you want to design a file transfer process that is secure? Or one that is compliant? Of course, the answer is both. But it s
Privileged User Monitoring for SOX Compliance
 White Paper Privileged User Monitoring for SOX Compliance Failed login, 6:45 a.m. Privilege escalation, 12:28 p.m. Financial data breach, 11:32 p.m. Financial data access, 5:48 p.m. 1 Privileged User Monitoring
White Paper Privileged User Monitoring for SOX Compliance Failed login, 6:45 a.m. Privilege escalation, 12:28 p.m. Financial data breach, 11:32 p.m. Financial data access, 5:48 p.m. 1 Privileged User Monitoring
Security Survey 2009: Privileged User Management It s Time to Take Control Frequently Asked Questions and Background
 Security Survey 2009: Privileged User Management It s Time to Take Control Frequently Asked Questions and Background What is a privileged user? A privileged user is an individual who, by virtue of function,
Security Survey 2009: Privileged User Management It s Time to Take Control Frequently Asked Questions and Background What is a privileged user? A privileged user is an individual who, by virtue of function,
Compliance and Industry Regulations
 Compliance and Industry Regulations Table of Contents Introduction...1 Executive Summary...1 General Federal Regulations and Oversight Agencies...1 Agency or Industry Specific Regulations...2 Hierarchy
Compliance and Industry Regulations Table of Contents Introduction...1 Executive Summary...1 General Federal Regulations and Oversight Agencies...1 Agency or Industry Specific Regulations...2 Hierarchy
Rackspace Archiving Compliance Overview
 Rackspace Archiving Compliance Overview Freedom Information Act Sunshine Laws The federal government and nearly all state governments have established Open Records laws. The purpose of these laws is to
Rackspace Archiving Compliance Overview Freedom Information Act Sunshine Laws The federal government and nearly all state governments have established Open Records laws. The purpose of these laws is to
CONTENTS. Abstract... 2. Need for Desktop Management... 2. What should typical Desktop Management Software do?... 2. Securing Desktops...
 CONTENTS Abstract... 2 Need for Desktop Management... 2 What should typical Desktop Management Software do?... 2 Securing Desktops... 3 Standardization... 4 Troubleshooting... 4 Auditing IT Assets... 5
CONTENTS Abstract... 2 Need for Desktop Management... 2 What should typical Desktop Management Software do?... 2 Securing Desktops... 3 Standardization... 4 Troubleshooting... 4 Auditing IT Assets... 5
Compliance Management, made easy
 Compliance Management, made easy LOGPOINT SECURING BUSINESS ASSETS SECURING BUSINESS ASSETS LogPoint 5.1: Protecting your data, intellectual property and your company Log and Compliance Management in one
Compliance Management, made easy LOGPOINT SECURING BUSINESS ASSETS SECURING BUSINESS ASSETS LogPoint 5.1: Protecting your data, intellectual property and your company Log and Compliance Management in one
Security Trends and Client Approaches
 Security Trends and Client Approaches May 2010 Bob Bocchino, CISA ERM Security and Compliance Business Advisor IBU Technology Sales Support Industries Business Unit, Technology Sales Support 1 Mark Dixon
Security Trends and Client Approaches May 2010 Bob Bocchino, CISA ERM Security and Compliance Business Advisor IBU Technology Sales Support Industries Business Unit, Technology Sales Support 1 Mark Dixon
White Paper. Imperva Data Security and Compliance Lifecycle
 White Paper Today s highly regulated business environment is forcing corporations to comply with a multitude of different regulatory mandates, including data governance, data protection and industry regulations.
White Paper Today s highly regulated business environment is forcing corporations to comply with a multitude of different regulatory mandates, including data governance, data protection and industry regulations.
The PCI Dilemma. COPYRIGHT 2009. TecForte
 The PCI Dilemma Today, all service providers and retailers that process, store or transmit cardholder data have a legislated responsibility to protect that data. As such, they must comply with a diverse
The PCI Dilemma Today, all service providers and retailers that process, store or transmit cardholder data have a legislated responsibility to protect that data. As such, they must comply with a diverse
Securing Data in the Virtual Data Center and Cloud: Requirements for Effective Encryption
 THE DATA PROTECTIO TIO N COMPANY Securing Data in the Virtual Data Center and Cloud: Requirements for Effective Encryption whitepaper Executive Summary Long an important security measure, encryption has
THE DATA PROTECTIO TIO N COMPANY Securing Data in the Virtual Data Center and Cloud: Requirements for Effective Encryption whitepaper Executive Summary Long an important security measure, encryption has
The Impact of Sarbanes-Oxley on the Collections Process. A Decision Analytics briefing paper from Experian
 The Impact of Sarbanes-Oxley on the Collections Process A Decision Analytics briefing paper from Experian February 2007 Introduction This briefing paper reviews how the use of an automated debt management
The Impact of Sarbanes-Oxley on the Collections Process A Decision Analytics briefing paper from Experian February 2007 Introduction This briefing paper reviews how the use of an automated debt management
Log Management How to Develop the Right Strategy for Business and Compliance. Log Management
 Log Management How to Develop the Right Strategy for Business and Compliance An Allstream / Dell SecureWorks White Paper 1 Table of contents Executive Summary 1 Current State of Log Monitoring 2 Five Steps
Log Management How to Develop the Right Strategy for Business and Compliance An Allstream / Dell SecureWorks White Paper 1 Table of contents Executive Summary 1 Current State of Log Monitoring 2 Five Steps
Securing Privileges in the Cloud. A Clear View of Challenges, Solutions and Business Benefits
 A Clear View of Challenges, Solutions and Business Benefits Introduction Cloud environments are widely adopted because of the powerful, flexible infrastructure and efficient use of resources they provide
A Clear View of Challenges, Solutions and Business Benefits Introduction Cloud environments are widely adopted because of the powerful, flexible infrastructure and efficient use of resources they provide
White Paper Achieving SOX Compliance through Security Information Management. White Paper / SOX
 White Paper Achieving SOX Compliance through Security Information Management White Paper / SOX Contents Executive Summary... 1 Introduction: Brief Overview of SOX... 1 The SOX Challenge: Improving the
White Paper Achieving SOX Compliance through Security Information Management White Paper / SOX Contents Executive Summary... 1 Introduction: Brief Overview of SOX... 1 The SOX Challenge: Improving the
RESEARCH NOTE CYBER-ARK FOR PRIVILEGED ACCOUNT MANAGEMENT
 Document K23 RESEARCH NOTE CYBER-ARK FOR PRIVILEGED ACCOUNT MANAGEMENT THE BOTTOM LINE Managing privileged accounts requires balancing accessibility and control while ensuring audit capabilities. Cyber-Ark
Document K23 RESEARCH NOTE CYBER-ARK FOR PRIVILEGED ACCOUNT MANAGEMENT THE BOTTOM LINE Managing privileged accounts requires balancing accessibility and control while ensuring audit capabilities. Cyber-Ark
Reducing Sarbanes-Oxley Operational Risk. Using. A Document Management System
 Reducing Sarbanes-Oxley Operational Risk Using A Document Management System All rights reserved Prepared by: John V. Ashley, CEO, This white paper reviews the Sarbanes-Oxley Act and discusses the reduction
Reducing Sarbanes-Oxley Operational Risk Using A Document Management System All rights reserved Prepared by: John V. Ashley, CEO, This white paper reviews the Sarbanes-Oxley Act and discusses the reduction
Information Security: A Perspective for Higher Education
 Information Security: A Perspective for Higher Education A By Introduction On a well-known hacker website, individuals charged students $2,100 to hack into university and college computers for the purpose
Information Security: A Perspective for Higher Education A By Introduction On a well-known hacker website, individuals charged students $2,100 to hack into university and college computers for the purpose
nwstor Storage Security Solution 1. Executive Summary 2. Need for Data Security 3. Solution: nwstor isav Storage Security Appliances 4.
 CONTENTS 1. Executive Summary 2. Need for Data Security 3. Solution: nwstor isav Storage Security Appliances 4. Conclusion 1. EXECUTIVE SUMMARY The advantages of networked data storage technologies such
CONTENTS 1. Executive Summary 2. Need for Data Security 3. Solution: nwstor isav Storage Security Appliances 4. Conclusion 1. EXECUTIVE SUMMARY The advantages of networked data storage technologies such
2012 JiJi Technologies All rights reserved. Privacy Policy
 Page 02 INDEX Introduction:...3 Problem Definition:...3 1. Security Auditing:...3 2. Audit Logs:...3 3. Compliance...3 4. Adherence with Organization s security policy...4 Audit requirements for IT infrastructure:...4
Page 02 INDEX Introduction:...3 Problem Definition:...3 1. Security Auditing:...3 2. Audit Logs:...3 3. Compliance...3 4. Adherence with Organization s security policy...4 Audit requirements for IT infrastructure:...4
Implementing HIPAA Compliance with ScriptLogic
 Implementing HIPAA Compliance with ScriptLogic A ScriptLogic Product Positioning Paper By Nick Cavalancia 1.800.424.9411 www.scriptlogic.com Table of Contents INTRODUCTION... 3 HIPAA BACKGROUND... 3 ADMINISTRATIVE
Implementing HIPAA Compliance with ScriptLogic A ScriptLogic Product Positioning Paper By Nick Cavalancia 1.800.424.9411 www.scriptlogic.com Table of Contents INTRODUCTION... 3 HIPAA BACKGROUND... 3 ADMINISTRATIVE
The Casper Suite An ROI overview
 The Casper Suite An ROI overview Introduction Inside Read how the Casper Suite delivers significant ROI in the following areas: Imaging Inventory Software Distribution Patch Management Settings and Security
The Casper Suite An ROI overview Introduction Inside Read how the Casper Suite delivers significant ROI in the following areas: Imaging Inventory Software Distribution Patch Management Settings and Security
SECURELINK.COM COMPLIANCE AND INDUSTRY REGULATIONS
 COMPLIANCE AND INDUSTRY REGULATIONS INTRODUCTION Multiple federal regulations exist today requiring government organizations to implement effective controls that ensure the security of their information
COMPLIANCE AND INDUSTRY REGULATIONS INTRODUCTION Multiple federal regulations exist today requiring government organizations to implement effective controls that ensure the security of their information
787 Wye Road, Akron, Ohio 44333 P 330-666-6200 F 330-666-7801 www.keystonecorp.com
 Introduction Keystone White Paper: Regulations affecting IT This document describes specific sections of current U.S. regulations applicable to IT governance and data protection and maps those requirements
Introduction Keystone White Paper: Regulations affecting IT This document describes specific sections of current U.S. regulations applicable to IT governance and data protection and maps those requirements
IT General Controls Domain COBIT Domain Control Objective Control Activity Test Plan Test of Controls Results
 Acquire or develop application systems software Controls provide reasonable assurance that application and system software is acquired or developed that effectively supports financial reporting requirements.
Acquire or develop application systems software Controls provide reasonable assurance that application and system software is acquired or developed that effectively supports financial reporting requirements.
Memeo C1 Secure File Transfer and Compliance
 Overview and analysis of Memeo C1 and SSAE16 & SOX Compliance Requirements Memeo C1 Secure File Transfer and Compliance Comply360, Inc Contents Executive Summary... 2 Overview... 2 Scope of Evaluation...
Overview and analysis of Memeo C1 and SSAE16 & SOX Compliance Requirements Memeo C1 Secure File Transfer and Compliance Comply360, Inc Contents Executive Summary... 2 Overview... 2 Scope of Evaluation...
The Challenges and Myths of Sarbanes-Oxley Compliance
 W H I T E P A P E R The Challenges and Myths of Sarbanes-Oxley Compliance Meeting the requirements of regulatory legislation on the iseries. SOX-001 REV1b FEBRUARY 2005 Bytware, Inc. All Rights Reserved.
W H I T E P A P E R The Challenges and Myths of Sarbanes-Oxley Compliance Meeting the requirements of regulatory legislation on the iseries. SOX-001 REV1b FEBRUARY 2005 Bytware, Inc. All Rights Reserved.
Design of Database Security Policy In Enterprise Systems
 Design of Database Security Policy In Enterprise Systems by Krishna R Singitam Database Architect Page 1 of 10 Table of Contents 1. Abstract... 3 2. Introduction... 3 2.1. Understanding the Necessity of
Design of Database Security Policy In Enterprise Systems by Krishna R Singitam Database Architect Page 1 of 10 Table of Contents 1. Abstract... 3 2. Introduction... 3 2.1. Understanding the Necessity of
MANAGED FILE TRANSFER: 10 STEPS TO PCI DSS COMPLIANCE
 WHITE PAPER MANAGED FILE TRANSFER: 10 STEPS TO PCI DSS COMPLIANCE 1. OVERVIEW Do you want to design a file transfer process that is secure? Or one that is compliant? Of course, the answer is both. But
WHITE PAPER MANAGED FILE TRANSFER: 10 STEPS TO PCI DSS COMPLIANCE 1. OVERVIEW Do you want to design a file transfer process that is secure? Or one that is compliant? Of course, the answer is both. But
Security Information Lifecycle
 Security Information Lifecycle By Eric Ogren Security Analyst, April 2006 Copyright 2006. The, Inc. All Rights Reserved. Table of Contents Executive Summary...2 Figure 1... 2 The Compliance Climate...4
Security Information Lifecycle By Eric Ogren Security Analyst, April 2006 Copyright 2006. The, Inc. All Rights Reserved. Table of Contents Executive Summary...2 Figure 1... 2 The Compliance Climate...4
How to Develop a Log Management Strategy
 Information Security Services Log Management: How to develop the right strategy for business and compliance The purpose of this whitepaper is to provide the reader with guidance on developing a strategic
Information Security Services Log Management: How to develop the right strategy for business and compliance The purpose of this whitepaper is to provide the reader with guidance on developing a strategic
ipatch System Manager - HIPAA Compliance
 SYSTIMAX Solutions ipatch System Manager - HIPAA Compliance White Paper July 2008 www.commscope.com Overview Health plans, healthcare clearinghouses, healthcare providers including Medicare/ Medicaid agencies
SYSTIMAX Solutions ipatch System Manager - HIPAA Compliance White Paper July 2008 www.commscope.com Overview Health plans, healthcare clearinghouses, healthcare providers including Medicare/ Medicaid agencies
MANAGED FILE TRANSFER: 10 STEPS TO HIPAA/HITECH COMPLIANCE
 WHITE PAPER MANAGED FILE TRANSFER: 10 STEPS TO HIPAA/HITECH COMPLIANCE 1. OVERVIEW Do you want to design a file transfer process that is secure? Or one that is compliant? Of course, the answer is both.
WHITE PAPER MANAGED FILE TRANSFER: 10 STEPS TO HIPAA/HITECH COMPLIANCE 1. OVERVIEW Do you want to design a file transfer process that is secure? Or one that is compliant? Of course, the answer is both.
ensure prompt restart of critical applications and business activities in a timely manner following an emergency or disaster
 Security Standards Symantec shall maintain administrative, technical, and physical safeguards for the Symantec Network designed to (i) protect the security and integrity of the Symantec Network, and (ii)
Security Standards Symantec shall maintain administrative, technical, and physical safeguards for the Symantec Network designed to (i) protect the security and integrity of the Symantec Network, and (ii)
MySQL Security: Best Practices
 MySQL Security: Best Practices Sastry Vedantam sastry.vedantam@oracle.com Safe Harbor Statement The following is intended to outline our general product direction. It is intended for information purposes
MySQL Security: Best Practices Sastry Vedantam sastry.vedantam@oracle.com Safe Harbor Statement The following is intended to outline our general product direction. It is intended for information purposes
Self-Service SOX Auditing With S3 Control
 Self-Service SOX Auditing With S3 Control The Sarbanes-Oxley Act (SOX), passed by the US Congress in 2002, represents a fundamental shift in corporate governance norms. As corporations come to terms with
Self-Service SOX Auditing With S3 Control The Sarbanes-Oxley Act (SOX), passed by the US Congress in 2002, represents a fundamental shift in corporate governance norms. As corporations come to terms with
PCI Compliance for Cloud Applications
 What Is It? The Payment Card Industry Data Security Standard (PCIDSS), in particular v3.0, aims to reduce credit card fraud by minimizing the risks associated with the transmission, processing, and storage
What Is It? The Payment Card Industry Data Security Standard (PCIDSS), in particular v3.0, aims to reduce credit card fraud by minimizing the risks associated with the transmission, processing, and storage
Sarbanes-Oxley Act. Solution Brief. Sarbanes-Oxley Act. Publication Date: March 17, 2015. EventTracker 8815 Centre Park Drive, Columbia MD 21045
 Publication Date: March 17, 2015 Solution Brief EventTracker 8815 Centre Park Drive, Columbia MD 21045 About EventTracker EventTracker delivers business critical software and services that transform high-volume
Publication Date: March 17, 2015 Solution Brief EventTracker 8815 Centre Park Drive, Columbia MD 21045 About EventTracker EventTracker delivers business critical software and services that transform high-volume
Achieving SOX Compliance with Masergy Security Professional Services
 Achieving SOX Compliance with Masergy Security Professional Services The Sarbanes-Oxley (SOX) Act, also known as the Public Company Accounting Reform and Investor Protection Act of 2002 (and commonly called
Achieving SOX Compliance with Masergy Security Professional Services The Sarbanes-Oxley (SOX) Act, also known as the Public Company Accounting Reform and Investor Protection Act of 2002 (and commonly called
Certification Practice Statement
 FernUniversität in Hagen: Certification Authority (CA) Certification Practice Statement VERSION 1.1 Ralph Knoche 18.12.2009 Contents 1. Introduction... 4 1.1. Overview... 4 1.2. Scope of the Certification
FernUniversität in Hagen: Certification Authority (CA) Certification Practice Statement VERSION 1.1 Ralph Knoche 18.12.2009 Contents 1. Introduction... 4 1.1. Overview... 4 1.2. Scope of the Certification
Solution Brief for HIPAA HIPAA. Publication Date: Jan 27, 2015. EventTracker 8815 Centre Park Drive, Columbia MD 21045
 Publication Date: Jan 27, 2015 8815 Centre Park Drive, Columbia MD 21045 HIPAA About delivers business critical software and services that transform high-volume cryptic log data into actionable, prioritized
Publication Date: Jan 27, 2015 8815 Centre Park Drive, Columbia MD 21045 HIPAA About delivers business critical software and services that transform high-volume cryptic log data into actionable, prioritized
ITECH Net Monitor. Standards Compliance
 If you rely on your IT infrastructure to maintain data integrity and protect your business from financial losses, it s a good idea to invest in a full fledged network monitoring program and achieve compliance
If you rely on your IT infrastructure to maintain data integrity and protect your business from financial losses, it s a good idea to invest in a full fledged network monitoring program and achieve compliance
What IT Auditors Need to Know About Secure Shell. SSH Communications Security
 What IT Auditors Need to Know About Secure Shell SSH Communications Security Agenda Secure Shell Basics Security Risks Compliance Requirements Methods, Tools, Resources What is Secure Shell? A cryptographic
What IT Auditors Need to Know About Secure Shell SSH Communications Security Agenda Secure Shell Basics Security Risks Compliance Requirements Methods, Tools, Resources What is Secure Shell? A cryptographic
IT Best Practices Audit TCS offers a wide range of IT Best Practices Audit content covering 15 subjects and over 2200 topics, including:
 IT Best Practices Audit TCS offers a wide range of IT Best Practices Audit content covering 15 subjects and over 2200 topics, including: 1. IT Cost Containment 84 topics 2. Cloud Computing Readiness 225
IT Best Practices Audit TCS offers a wide range of IT Best Practices Audit content covering 15 subjects and over 2200 topics, including: 1. IT Cost Containment 84 topics 2. Cloud Computing Readiness 225
Sarbanes-Oxley Control Transformation Through Automation
 Sarbanes-Oxley Control Transformation Through Automation An Executive White Paper By BLUE LANCE, Inc. Where have we been? Where are we going? BLUE LANCE INC. www.bluelance.com 713.255.4800 info@bluelance.com
Sarbanes-Oxley Control Transformation Through Automation An Executive White Paper By BLUE LANCE, Inc. Where have we been? Where are we going? BLUE LANCE INC. www.bluelance.com 713.255.4800 info@bluelance.com
Information Security Policy September 2009 Newman University IT Services. Information Security Policy
 Contents 1. Statement 1.1 Introduction 1.2 Objectives 1.3 Scope and Policy Structure 1.4 Risk Assessment and Management 1.5 Responsibilities for Information Security 2. Compliance 3. HR Security 3.1 Terms
Contents 1. Statement 1.1 Introduction 1.2 Objectives 1.3 Scope and Policy Structure 1.4 Risk Assessment and Management 1.5 Responsibilities for Information Security 2. Compliance 3. HR Security 3.1 Terms
White Paper. Protecting Databases from Unauthorized Activities Using Imperva SecureSphere
 Protecting Databases from Unauthorized Activities Using Imperva SecureSphere White Paper As the primary repository for the enterprise s most valuable information, the database is perhaps the most sensitive
Protecting Databases from Unauthorized Activities Using Imperva SecureSphere White Paper As the primary repository for the enterprise s most valuable information, the database is perhaps the most sensitive
March 2012 www.tufin.com
 SecureTrack Supporting Compliance with PCI DSS 2.0 March 2012 www.tufin.com Table of Contents Introduction... 3 The Importance of Network Security Operations... 3 Supporting PCI DSS with Automated Solutions...
SecureTrack Supporting Compliance with PCI DSS 2.0 March 2012 www.tufin.com Table of Contents Introduction... 3 The Importance of Network Security Operations... 3 Supporting PCI DSS with Automated Solutions...
HIPAA Privacy & Security White Paper
 HIPAA Privacy & Security White Paper Sabrina Patel, JD +1.718.683.6577 sabrina@captureproof.com Compliance TABLE OF CONTENTS Overview 2 Security Frameworks & Standards 3 Key Security & Privacy Elements
HIPAA Privacy & Security White Paper Sabrina Patel, JD +1.718.683.6577 sabrina@captureproof.com Compliance TABLE OF CONTENTS Overview 2 Security Frameworks & Standards 3 Key Security & Privacy Elements
Unified Security Anywhere SOX COMPLIANCE ACHIEVING SOX COMPLIANCE WITH MASERGY SECURITY PROFESSIONAL SERVICES
 Unified Security Anywhere SOX COMPLIANCE ACHIEVING SOX COMPLIANCE WITH MASERGY SECURITY PROFESSIONAL SERVICES SOX COMPLIANCE Achieving SOX Compliance with Professional Services The Sarbanes-Oxley (SOX)
Unified Security Anywhere SOX COMPLIANCE ACHIEVING SOX COMPLIANCE WITH MASERGY SECURITY PROFESSIONAL SERVICES SOX COMPLIANCE Achieving SOX Compliance with Professional Services The Sarbanes-Oxley (SOX)
TEMPLE UNIVERSITY POLICIES AND PROCEDURES MANUAL
 TEMPLE UNIVERSITY POLICIES AND PROCEDURES MANUAL Title: Computer and Network Security Policy Policy Number: 04.72.12 Effective Date: November 4, 2003 Issuing Authority: Office of the Vice President for
TEMPLE UNIVERSITY POLICIES AND PROCEDURES MANUAL Title: Computer and Network Security Policy Policy Number: 04.72.12 Effective Date: November 4, 2003 Issuing Authority: Office of the Vice President for
Setting up High Availability
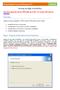 ManageEngine Password Manager Pro Tutorial Setting up High Availability (Procedure applicable only for PMP builds up to 6301. For versions 6302 and later, click here ) Overview Setting up high availability
ManageEngine Password Manager Pro Tutorial Setting up High Availability (Procedure applicable only for PMP builds up to 6301. For versions 6302 and later, click here ) Overview Setting up high availability
MICHIGAN AUDIT REPORT OFFICE OF THE AUDITOR GENERAL THOMAS H. MCTAVISH, C.P.A. AUDITOR GENERAL
 MICHIGAN OFFICE OF THE AUDITOR GENERAL AUDIT REPORT THOMAS H. MCTAVISH, C.P.A. AUDITOR GENERAL ...The auditor general shall conduct post audits of financial transactions and accounts of the state and of
MICHIGAN OFFICE OF THE AUDITOR GENERAL AUDIT REPORT THOMAS H. MCTAVISH, C.P.A. AUDITOR GENERAL ...The auditor general shall conduct post audits of financial transactions and accounts of the state and of
Seven Things To Consider When Evaluating Privileged Account Security Solutions
 Seven Things To Consider When Evaluating Privileged Account Security Solutions Contents Introduction 1 Seven questions to ask every privileged account security provider 4 1. Is the solution really secure?
Seven Things To Consider When Evaluating Privileged Account Security Solutions Contents Introduction 1 Seven questions to ask every privileged account security provider 4 1. Is the solution really secure?
HIPAA Security Rule Compliance and Health Care Information Protection
 HIPAA Security Rule Compliance and Health Care Information Protection How SEA s Solution Suite Ensures HIPAA Security Rule Compliance Legal Notice: This document reflects the understanding of Software
HIPAA Security Rule Compliance and Health Care Information Protection How SEA s Solution Suite Ensures HIPAA Security Rule Compliance Legal Notice: This document reflects the understanding of Software
BKDconnect Security Overview
 BKDconnect Security Overview 1 Introduction 1.1 What is BKDconnect 1.2 Site Creation 1.3 Client Authentication and Access 2 Security Design 2.1 Confidentiality 2.1.1 Least Privilege and Role Based Security
BKDconnect Security Overview 1 Introduction 1.1 What is BKDconnect 1.2 Site Creation 1.3 Client Authentication and Access 2 Security Design 2.1 Confidentiality 2.1.1 Least Privilege and Role Based Security
Secret Server Qualys Integration Guide
 Secret Server Qualys Integration Guide Table of Contents Secret Server and Qualys Cloud Platform... 2 Authenticated vs. Unauthenticated Scanning... 2 What are the Advantages?... 2 Integrating Secret Server
Secret Server Qualys Integration Guide Table of Contents Secret Server and Qualys Cloud Platform... 2 Authenticated vs. Unauthenticated Scanning... 2 What are the Advantages?... 2 Integrating Secret Server
Enabling SOX Compliance on DataStax Enterprise
 Enabling SOX Compliance on DataStax Enterprise Table of Contents Table of Contents... 2 Introduction... 3 SOX Compliance and Requirements... 3 Who Must Comply with SOX?... 3 SOX Goals and Objectives...
Enabling SOX Compliance on DataStax Enterprise Table of Contents Table of Contents... 2 Introduction... 3 SOX Compliance and Requirements... 3 Who Must Comply with SOX?... 3 SOX Goals and Objectives...
10 Hidden IT Risks That Threaten Your Practice
 (Plus 1 Fast Way to Find Them) Your practice depends on intelligence. But can you count on your technology? You may not be in the intelligence technology business, but it s probably impossible to imagine
(Plus 1 Fast Way to Find Them) Your practice depends on intelligence. But can you count on your technology? You may not be in the intelligence technology business, but it s probably impossible to imagine
FINAL May 2005. Guideline on Security Systems for Safeguarding Customer Information
 FINAL May 2005 Guideline on Security Systems for Safeguarding Customer Information Table of Contents 1 Introduction 1 1.1 Purpose of Guideline 1 2 Definitions 2 3 Internal Controls and Procedures 2 3.1
FINAL May 2005 Guideline on Security Systems for Safeguarding Customer Information Table of Contents 1 Introduction 1 1.1 Purpose of Guideline 1 2 Definitions 2 3 Internal Controls and Procedures 2 3.1
IBM Security Privileged Identity Manager helps prevent insider threats
 IBM Security Privileged Identity Manager helps prevent insider threats Securely provision, manage, automate and track privileged access to critical enterprise resources Highlights Centrally manage privileged
IBM Security Privileged Identity Manager helps prevent insider threats Securely provision, manage, automate and track privileged access to critical enterprise resources Highlights Centrally manage privileged
Measuring Sarbanes-Oxley Compliance Requirements
 IGG-10012003-03 R. Mogull, D. Logan, L. Leskela Article 1 October 2003 CIO Alert: How You Should Prepare for Sarbanes-Oxley Sarbanes-Oxley is the most sweeping legislation to affect publicly traded companies
IGG-10012003-03 R. Mogull, D. Logan, L. Leskela Article 1 October 2003 CIO Alert: How You Should Prepare for Sarbanes-Oxley Sarbanes-Oxley is the most sweeping legislation to affect publicly traded companies
IBX Business Network Platform Information Security Controls. 2015-02- 20 Document Classification [Public]
![IBX Business Network Platform Information Security Controls. 2015-02- 20 Document Classification [Public] IBX Business Network Platform Information Security Controls. 2015-02- 20 Document Classification [Public]](/thumbs/26/7758795.jpg) IBX Business Network Platform Information Security Controls 2015-02- 20 Document Classification [Public] Table of Contents 1. General 2 2. Physical Security 2 3. Network Access Control 2 4. Operating System
IBX Business Network Platform Information Security Controls 2015-02- 20 Document Classification [Public] Table of Contents 1. General 2 2. Physical Security 2 3. Network Access Control 2 4. Operating System
IMPROVING AUDIT READINESS BY MANAGING YOUR DYNAMICS ERP
 IMPROVING AUDIT READINESS BY MANAGING YOUR DYNAMICS ERP Building Sustainable Control Accountability Contents 1 EXECUTIVE SUMMARY... 1 2 MANAGING YOUR DYNAMICS ERP SYSTEM: AUDIT READINESS... 1 2.1 Common
IMPROVING AUDIT READINESS BY MANAGING YOUR DYNAMICS ERP Building Sustainable Control Accountability Contents 1 EXECUTIVE SUMMARY... 1 2 MANAGING YOUR DYNAMICS ERP SYSTEM: AUDIT READINESS... 1 2.1 Common
White Paper. Sarbanes Oxley and iseries Security, Audit and Compliance
 White Paper Sarbanes Oxley and iseries Security, Audit and Compliance This White Paper was written by AH Technology Distributors of isecurity a suite of iseries security products developed by Raz-Lee Security
White Paper Sarbanes Oxley and iseries Security, Audit and Compliance This White Paper was written by AH Technology Distributors of isecurity a suite of iseries security products developed by Raz-Lee Security
Sarbanes-Oxley Compliance: Section 404-Past, Present, and Future
 Sarbanes-Oxley Compliance: Section 404-Past, Present, and Future BADM 590/395 IT Governance MS1 Professor Michael Shaw Submitted by: Amy Smith BA in MIS University of Illinois at Urbana-Champaign Smith
Sarbanes-Oxley Compliance: Section 404-Past, Present, and Future BADM 590/395 IT Governance MS1 Professor Michael Shaw Submitted by: Amy Smith BA in MIS University of Illinois at Urbana-Champaign Smith
Addressing SOX compliance with XaitPorter. Version 1.0 Sept. 2014
 Addressing SOX compliance with XaitPorter Version 1.0 Sept. 2014 Table of Contents 1 Addressing Compliance... 1 2 SOX Compliance... 2 3 Key Benefits... 5 4 Contact Information... 6 1 Addressing Compliance
Addressing SOX compliance with XaitPorter Version 1.0 Sept. 2014 Table of Contents 1 Addressing Compliance... 1 2 SOX Compliance... 2 3 Key Benefits... 5 4 Contact Information... 6 1 Addressing Compliance
Managing Privileged Identities in the Cloud. How Privileged Identity Management Evolved to a Service Platform
 Managing Privileged Identities in the Cloud How Privileged Identity Management Evolved to a Service Platform Managing Privileged Identities in the Cloud Contents Overview...3 Management Issues...3 Real-World
Managing Privileged Identities in the Cloud How Privileged Identity Management Evolved to a Service Platform Managing Privileged Identities in the Cloud Contents Overview...3 Management Issues...3 Real-World
Projectplace: A Secure Project Collaboration Solution
 Solution brief Projectplace: A Secure Project Collaboration Solution The security of your information is as critical as your business is dynamic. That s why we built Projectplace on a foundation of the
Solution brief Projectplace: A Secure Project Collaboration Solution The security of your information is as critical as your business is dynamic. That s why we built Projectplace on a foundation of the
Best Practices Report
 Overview As an IT leader within your organization, you face new challenges every day from managing user requirements and operational needs to the burden of IT Compliance. Developing a strong IT general
Overview As an IT leader within your organization, you face new challenges every day from managing user requirements and operational needs to the burden of IT Compliance. Developing a strong IT general
SOX Compliance & Your Database
 SOX Compliance & Your Database Achieving & Maintaining Database Compliance for SOX Complying with SOX data requirements can be confusing, especially with so many products providing protection on only a
SOX Compliance & Your Database Achieving & Maintaining Database Compliance for SOX Complying with SOX data requirements can be confusing, especially with so many products providing protection on only a
Regulatory Compliance: How Digital Data Protection Helps
 WHITE PAPER Regulatory Compliance: How Digital Data Protection Helps Executive Summary Organizations today face many compulsory regulatory requirements, among them: Gramm-Leach-Bliley (GLB) Act SEC Rule
WHITE PAPER Regulatory Compliance: How Digital Data Protection Helps Executive Summary Organizations today face many compulsory regulatory requirements, among them: Gramm-Leach-Bliley (GLB) Act SEC Rule
Stock Plan Administration in the Age of Sarbanes-Oxley. Compliance Considerations for Administrators
 White Paper Stock Plan Administration in the Age of Sarbanes-Oxley Compliance Considerations for Administrators The information published in this paper is of a general nature and is intended merely as
White Paper Stock Plan Administration in the Age of Sarbanes-Oxley Compliance Considerations for Administrators The information published in this paper is of a general nature and is intended merely as
HIPAA Compliance and the Protection of Patient Health Information
 HIPAA Compliance and the Protection of Patient Health Information WHITE PAPER By Swift Systems Inc. April 2015 Swift Systems Inc. 7340 Executive Way, Ste M Frederick MD 21704 1 Contents HIPAA Compliance
HIPAA Compliance and the Protection of Patient Health Information WHITE PAPER By Swift Systems Inc. April 2015 Swift Systems Inc. 7340 Executive Way, Ste M Frederick MD 21704 1 Contents HIPAA Compliance
Circular to All Licensed Corporations on Information Technology Management
 Circular 16 March 2010 Circular to All Licensed Corporations on Information Technology Management In the course of our supervision, it has recently come to our attention that certain deficiencies in information
Circular 16 March 2010 Circular to All Licensed Corporations on Information Technology Management In the course of our supervision, it has recently come to our attention that certain deficiencies in information
SafeNet DataSecure vs. Native Oracle Encryption
 SafeNet vs. Native Encryption Executive Summary Given the vital records databases hold, these systems often represent one of the most critical areas of exposure for an enterprise. Consequently, as enterprises
SafeNet vs. Native Encryption Executive Summary Given the vital records databases hold, these systems often represent one of the most critical areas of exposure for an enterprise. Consequently, as enterprises
Analyzing Logs For Security Information Event Management Whitepaper
 ADVENTNET INC. Analyzing Logs For Security Information Event Management Whitepaper Notice: AdventNet shall have no liability for errors, omissions or inadequacies in the information contained herein or
ADVENTNET INC. Analyzing Logs For Security Information Event Management Whitepaper Notice: AdventNet shall have no liability for errors, omissions or inadequacies in the information contained herein or
Best Practices for PCI DSS V3.0 Network Security Compliance
 Best Practices for PCI DSS V3.0 Network Security Compliance January 2015 www.tufin.com Table of Contents Preparing for PCI DSS V3.0 Audit... 3 Protecting Cardholder Data with PCI DSS... 3 Complying with
Best Practices for PCI DSS V3.0 Network Security Compliance January 2015 www.tufin.com Table of Contents Preparing for PCI DSS V3.0 Audit... 3 Protecting Cardholder Data with PCI DSS... 3 Complying with
Basics of Internet Security
 Basics of Internet Security Premraj Jeyaprakash About Technowave, Inc. Technowave is a strategic and technical consulting group focused on bringing processes and technology into line with organizational
Basics of Internet Security Premraj Jeyaprakash About Technowave, Inc. Technowave is a strategic and technical consulting group focused on bringing processes and technology into line with organizational
How To Manage Security On A Networked Computer System
 Unified Security Reduce the Cost of Compliance Introduction In an effort to achieve a consistent and reliable security program, many organizations have adopted the standard as a key compliance strategy
Unified Security Reduce the Cost of Compliance Introduction In an effort to achieve a consistent and reliable security program, many organizations have adopted the standard as a key compliance strategy
Analyzing Logs For Security Information Event Management Whitepaper
 ADVENTNET INC. Analyzing Logs For Security Information Event Management Whitepaper Notice: AdventNet shall have no liability for errors, omissions or inadequacies in the information contained herein or
ADVENTNET INC. Analyzing Logs For Security Information Event Management Whitepaper Notice: AdventNet shall have no liability for errors, omissions or inadequacies in the information contained herein or
Drawbacks to Traditional Approaches When Securing Cloud Environments
 WHITE PAPER Drawbacks to Traditional Approaches When Securing Cloud Environments Drawbacks to Traditional Approaches When Securing Cloud Environments Exec Summary Exec Summary Securing the VMware vsphere
WHITE PAPER Drawbacks to Traditional Approaches When Securing Cloud Environments Drawbacks to Traditional Approaches When Securing Cloud Environments Exec Summary Exec Summary Securing the VMware vsphere
Network & Information Security Policy
 Policy Version: 2.1 Approved: 02/20/2015 Effective: 03/02/2015 Table of Contents I. Purpose................... 1 II. Scope.................... 1 III. Roles and Responsibilities............. 1 IV. Risk
Policy Version: 2.1 Approved: 02/20/2015 Effective: 03/02/2015 Table of Contents I. Purpose................... 1 II. Scope.................... 1 III. Roles and Responsibilities............. 1 IV. Risk
Understanding the Significance of SOX Compliance. www.cognoscape.com
 Understanding the Significance of SOX Compliance www.cognoscape.com Understanding the Significance of SOX Compliance The Sarbanes-Oxley Act (SOX) became effective in 2006 and was implemented to hold all
Understanding the Significance of SOX Compliance www.cognoscape.com Understanding the Significance of SOX Compliance The Sarbanes-Oxley Act (SOX) became effective in 2006 and was implemented to hold all
CallRail Healthcare Marketing. HIPAA and HITECH Compliance for Covered Entities using Call Analytics Software
 CallRail Healthcare Marketing HIPAA and HITECH Compliance for Covered Entities using Call Analytics Software Healthcare 2015 HIPAA and HITECH Compliance for Covered Entities using Call Analytics Software
CallRail Healthcare Marketing HIPAA and HITECH Compliance for Covered Entities using Call Analytics Software Healthcare 2015 HIPAA and HITECH Compliance for Covered Entities using Call Analytics Software
Solutions for Health Insurance Portability and Accountability Act (HIPAA) Compliance
 White Paper Solutions for Health Insurance Portability and Accountability Act (HIPAA) Compliance Troy Herrera Sr. Field Solutions Manager Juniper Networks, Inc. 1194 North Mathilda Avenue Sunnyvale, CA
White Paper Solutions for Health Insurance Portability and Accountability Act (HIPAA) Compliance Troy Herrera Sr. Field Solutions Manager Juniper Networks, Inc. 1194 North Mathilda Avenue Sunnyvale, CA
WHITEPAPER. Identity Management and Sarbanes-Oxley Compliance. T h i n k I D e n t i t y. September 2005
 Identity Management and Sarbanes-Oxley Compliance September 2005 T h i n k I D e n t i t y Table of Contents INTRODUCTION...3 THE SARBANES-OXLEY ACT OF 2002...3 HOW SARBANES-OXLEY AFFECTS IT PROCESSES...6
Identity Management and Sarbanes-Oxley Compliance September 2005 T h i n k I D e n t i t y Table of Contents INTRODUCTION...3 THE SARBANES-OXLEY ACT OF 2002...3 HOW SARBANES-OXLEY AFFECTS IT PROCESSES...6
whitepaper Ten Essential Steps for Achieving Continuous Compliance: A Complete Strategy for Compliance
 Ten Essential Steps for Achieving Continuous Compliance: A Complete Strategy for Compliance Table of Contents 3 10 Essential Steps 3 Understand the Requirements 4 Implement IT Controls that Affect your
Ten Essential Steps for Achieving Continuous Compliance: A Complete Strategy for Compliance Table of Contents 3 10 Essential Steps 3 Understand the Requirements 4 Implement IT Controls that Affect your
Department of Public Utilities Customer Information System (BANNER)
 REPORT # 2010-06 AUDIT of the Customer Information System (BANNER) January 2010 TABLE OF CONTENTS Executive Summary..... i Comprehensive List of Recommendations. iii Introduction, Objective, Methodology
REPORT # 2010-06 AUDIT of the Customer Information System (BANNER) January 2010 TABLE OF CONTENTS Executive Summary..... i Comprehensive List of Recommendations. iii Introduction, Objective, Methodology
LogRhythm and PCI Compliance
 LogRhythm and PCI Compliance The Payment Card Industry (PCI) Data Security Standard (DSS) was developed to encourage and enhance cardholder data security and facilitate the broad adoption of consistent
LogRhythm and PCI Compliance The Payment Card Industry (PCI) Data Security Standard (DSS) was developed to encourage and enhance cardholder data security and facilitate the broad adoption of consistent
How DataSunrise Helps to Comply with SOX, PCI DSS and HIPAA Requirements
 How DataSunrise Helps to Comply with SOX, PCI DSS and HIPAA Requirements DataSunrise, Inc. https://www.datasunrise.com Note: the latest copy of this document is available at https://www.datasunrise.com/documentation/resources/
How DataSunrise Helps to Comply with SOX, PCI DSS and HIPAA Requirements DataSunrise, Inc. https://www.datasunrise.com Note: the latest copy of this document is available at https://www.datasunrise.com/documentation/resources/
