Customers Trust. Whitepaper
|
|
|
- Lewis Hunt
- 8 years ago
- Views:
Transcription
1 Steps to improve your Data Security and ensure your Customers Trust intimus consulting is a division of the MARTIN YALE GROUP Bergheimer Strasse Markdorf / Germany Steps to improve your Data Security and ensure your Customers Trust Whitepaper
2 Steps to improve your Data Security and ensure your Customers Trust Summary Information security is not just a marginal activity for today s companies; it is central to a company s daily operations, brand image and customer relationships. The way that a company handles its information security procedures reflects on every other aspect of how the company is run and what the company stands for. If a company has conscientious, thorough information security practices, its customers can feel confident that their information will be protected. On the other hand, if a company has disorganized, erratic information security practices that company is more likely to end up in the news as the latest example of corporate information assurance gone wrong. Steps to improve your Data Security and ensure your Customers Trust 2
3 Content Increasing Threats to Data Security 4 Recommendations 5 Conclusion 11 Company Profile 13 Contact Details 13 Steps to improve your Data Security and ensure your Customers Trust 3
4 Increasing Threats to Data Security Even the best-laid information security plans can still fail to prevent data breaches. To some extent, many senior executives are starting to take the position that data breaches are bound to occur; it s not a matter of if but when. According to a recent survey of CEOs and senior executives, 82% reported that their organization had experienced a data breach, and most were not confident that they would be able to prevent a data breach during the next 12 months. 1 One challenge for every information security officer is that the threats to data security are multiplying fast; every day, billions of bytes of information are created, stored, shared and disseminated to millions of people all over the world. Organized networks of cyber criminals lurk online, checking for weaknesses in corporate firewalls, looking for ways to steal credit card numbers, identity information and other sensitive data. In addition to the newly created information and the ever-evolving threats of cybercrime, many companies are vulnerable to old-fashioned threats posed by improperly handled paper records, or by years-old archives of information stored on obsolete formats of data storage devices. Any of these magnetic data storage devices or optical storage media could expose a company to lawsuits and embarrassing publicity if they were to fall into the wrong hands. Confidential customer information, trade secrets, and other sensitive information need to be protected. This is one of the major challenges for business leaders in our time. The full scope of information that could potentially pose a risk, and the full range of threats, is unprecedented in human history. But does that mean that data breaches are inevitable? Are companies forced to just stand by, and hope to mitigate the worst effects of data theft? 1 Ponemon Institute, The Business Case for Data Protection (July 2009), pg. 17. Steps to improve your Data Security and ensure your Customers Trust 4
5 Recommendations Just because data security is increasingly complex, costly and risky does not mean that companies are helpless to prevent data breaches. There are many steps that companies can take in order to better manage their risks, maintain the trust of their customers, and preserve their reputations. Develop an information security strategy: Data protection is not a matter just for the Legal department, Compliance team or Information Technology staff; it is a matter of strategic importance to the company and must be addressed at the highest levels of the company by creating a comprehensive strategy. The company needs to establish overarching goals, best practices and key principles for how its information is going to be managed, including record retention schedules, designated contact persons for information security questions, and compliance teams to monitor and enforce the information security policy. Enforce the overall information security strategy: Senior management needs to create a reporting structure for information security to ensure that people are held accountable for complying with the strategy. Errors and failures to comply need to be noted, reported and followed up information security is an ongoing process, and whenever a weakness is discovered, it needs to be investigated and corrected so that the overall information security system continues to strengthen and evolve. Connect the information security strategy to the overall vision and values of the organization make sure that people understand on a fundamental level that information security is an important part of the company s mission. Provide training for employees (including temporary employees and contractors): All employees need to receive thorough training in how to safeguard sensitive information, how long to retain various types of information, and how to properly dispose of sensitive documents and data storage devices. The company s top leaders need to continually communicate the information security policy and strategy to all levels of the organization; people need to be regularly reminded of the importance of sound practices and diligent attention to detail. Even the smallest mistake or oversight can lead to damaging consequences. Steps to improve your Data Security and ensure your Customers Trust 5
6 Put data security controls in place: According to a 2008 study from the Verizon Business Risk Team, 87% of data breaches could have been avoided if reasonable data security controls had been in place. The study says, Traditionally, organizations have aligned their focus on building security controls around the network perimeter, and in many cases, have turned a blind eye toward data within the network. While a strong network perimeter is important, it cannot be the only or even the main layer of protection around sensitive information assets. Information itself wherever it flows must be the focus of security efforts. 2 Many companies focus on building strong firewalls and other external security measures, but they fail to monitor their internal data security measures which are often the ones that are more important in preventing data breaches. Back up company policy with actual processes: Also according to the Verizon 2008 study, in 59% of data breaches, the victim organizations had formal policies in place, but did not enact the policies with actual processes. 3 This means that these companies did not keep their promises to themselves; they knew what needed to be done, but they failed to do it. It s not enough to write detailed policies and grand visions of what the company is going to do about information security; the work also has to be implemented and brought to life in everyday operations. Test, test, test: Companies also need to include compliance checks and testing as part of their information security operations it s not high-tech or glamorous, but it s one of the best ways to reliably ensure that a company s data security plans are actually being carried out. 2 Verizon Business Risk Team, 2008 Data Breach Investigations Report, pg Ibid. Steps to improve your Data Security and ensure your Customers Trust 6
7 Data thieves look for weaknesses plan accordingly: According to the Verizon study, the overwhelming majority of data breaches were achieved by attacks that were not considered difficult (83%) or by opportunistic attacks (85%). 4 This illustrates a point that is well-known to many police detectives: most criminals are lazy and unimaginative. Given the choice between picking the lock of a complex network firewall, or picking up a box of improperly discarded documents and data storage devices, most data thieves will take the easy way out every time. Companies are more likely to have their data security compromised by the small stuff (improperly disposed documents and storage devices) rather than be vanquished in a technological wizard s duel by a sophisticated cyber criminal. 4 Ibid. Steps to improve your Data Security and ensure your Customers Trust 7
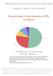
8 Take care of storage media: In the Ponemon Institute s survey of CEOs, 22% of respondents said that incorrect disposal of storage media was the greatest risk to sensitive data at their organizations this was the third highest rated response. 5 There are many steps that companies can take to properly dispose of their storage media, ranging from shredding (paper), to Secure Erase (hard disk drives), to grinding (optical storage media CDs and DVDs), degaussing (hard disk drives and other magnetic storage media) and disintegration (other solid state media). Companies that are serious about information security have more weapons at their disposal than ever before there s no excuse for improper disposal of storage media; if it contains information that might potentially pose a risk, it s worth making an investment in the equipment to properly dispose of the media. Bar Chart 1: from Ponemon Institute, The Business Case for Data Protection (July 2009), pg Ponemon Institute, The Business Case for Data Protection (July 2009), pg. 8. Steps to improve your Data Security and ensure your Customers Trust 8
9 Take precautions with business partners: A company s information security is ultimately only as strong as the practices of that company s business partners vendors, suppliers, contractors, and other entities who might deal with the company. Business partners were implicated knowingly or unknowingly in 32% of all data breaches, according to the 2009 Verizon Data Breach Investigations Report. 6 To keep business partners from exposing a company to risk, it is important to measure business partners security controls, include clear language in contracts that refers to responsibilities and liabilities for data breaches, and avoid divulging any sensitive information to a business partner that is not on a need to know basis. According to the Ponemon Institute, while the average cost of a data breach (during 2008) was $6.65 million, the per victim cost of data breaches involving outsourced data was $52 higher. 7 This indicates that a lot of companies would benefit from implementing better vendor management programs to monitor their business partners data security practices after all, any time a company shares information beyond its walls, there is a chance that the information can be lost, stolen or mishandled. Create a data retention plan: According to the Verizon 2008 report, 66% of data breaches involved data that the victim organization did not know was there. 8 What a company doesn t know can definitely hurt. This is one reason why it is so important for every company to have a data retention plan/record retention schedule as part of its overall information security strategy. Companies need to know what kind of data they have and how much of it there is. They need to know where the information is stored, who has access to the information, and how long the information needs to be kept. Companies should also adopt a when in doubt, throw it out approach unless there is a compelling business need, companies should avoid creating additional copies of old data, or holding on to data storage devices longer than necessary. If the information is no longer sitting around in storage, it is no longer a threat. 6 Verizon Business Risk Team, 2009 Data Breach Investigations Report, pg CIO, Costs of a Data Breach: Can You Afford $6.65 Million? Dr. Larry Ponemon, Feb. 4, Verizon Business Risk Team, 2008 Data Breach Investigations Report, pg. 26 Steps to improve your Data Security and ensure your Customers Trust 9
10 Create an incident response plan: Hope for the best, plan for the worst this principle also applies to information security. Companies need to do what they can to prevent data breaches, but in the event that a data breach occurs, companies need to be prepared. An incident response plan will allow the company to assess the situation, collect evidence, determine the scope of the breach, contact affected customers, and work with law enforcement and regulatory agencies as needed. Data breaches are not inevitable, but if one occurs, the company must be ready to respond and move forward with confidence and a calm sense of direction. In the event of a data breach, act with all deliberate speed. Make sure you understand the applicable laws and reporting requirements for your location; depending on the situation, not every data breach needs to be publicly announced and reported, especially if no individual people s information was compromised. If you do have a data breach that requires reporting, be prepared to act fast. Make sure to notify the affected people as soon as reasonably possible; don t let the local news media spread the story before you ve had a chance to contact the people whose data has been compromised. Also be prepared to offer detailed information and assistance to customers or business partners affected by the data breach as Dr. Larry Ponemon says, Don't just give a script to the call agents -- give out a toll-free number where people can reach someone with enough internal knowledge to get them to the right person." 9 9 CIO, What, When and How to Respond to a Data Breach. Lamont Wood, April 27, Steps to improve your Data Security and ensure your Customers Trust 10
11 Conclusion Data breaches are not inevitable. Companies do not have to resign themselves to data theft, costly problems and embarrassing news headlines. There are many ways that companies can reduce their risk of data breaches while boosting their customers confidence and there is definitely a connection between these two goals; information security is not just a matter for IT and internal operations; it is also a matter that affects marketing and sales. 57% of CEOs surveyed said that information security increases the value of their companies by increasing customer loyalty and reducing customer turnover, and 80% said that information security helps to improve their overall brand image. 10 With customers more concerned than ever about identity theft and the various mysterious and complicated risks of doing business in an online, interconnected world, customers are more likely to turn to companies that can promise (and deliver) a robust, thorough and well-thought-out information security policy. By developing a comprehensive strategy for information security, putting good processes in place, training employees (and contractors), keeping control of digital storage media, understanding business partners information security practices, and creating good plans for data retention and emergency response in case of a data breach, companies can mitigate the biggest risks and enjoy the biggest benefits. A good information security strategy with the right training, the right equipment and the right advice is an investment, but it s an investment worth making. According to the CEOs surveyed by the Ponemon Institute, the average ROI of information security programs was 4.3 to 1 $4.30 in cost savings and revenue improvements for every $1 spent. 11 Preventing data breaches does not have to be a losing battle. In fact, it can even show positive gains for a company s bottom line! 10 Ponemon Institute, The Business Case for Data Protection (July 2009), pg Based on a median extrapolated value of $16 million in cost savings or revenue improvements from data protection efforts, divided by a median extrapolated value of $3.7 million annual budget dedicated to data protection. Ponemon Institute, The Business Case for Data Protection (July 2009), pgs Steps to improve your Data Security and ensure your Customers Trust 11
12 Most importantly, a company s information security efforts are a reflection of that company s strategic vision, core values and fundamental ability to execute. Customers are going to pay closer attention to companies records on information security as the world becomes more interconnected and more transactions and sensitive information move online, customers are going to be increasingly interested in working with companies who they can trust with their information. Despite the many amazing technologies available in the modern business world, so much of business is still based on simple trust. Companies that embrace this truth will be well positioned for future success. Steps to improve your Data Security and ensure your Customers Trust 12
13 Company Profile Data protection was something unheard of when the first shredders were introduced in the 1960 s. Starting with the "electronic wastepaper basket" INTIMUS Simplex in 1965 the product range nowadays meets all the requirements imposed with regard to information assurance. It does not only contain devices for the shredding of classical data media, such as print outs, computer lists or even complete folders, but also features machines to destroy information on modern endpoint devices like CDs, floppy disks, Hard Disk Drives and Solid State Media. intimus Security Consulting is a concept to assist organisations worldwide to define, implement and monitor procedures for information security beyond the endpoint. More information is available under The MARTIN YALE GROUP was formed in 2003 by the former individual organisations MARTIN YALE Industries (North America) and Schleicher International (Germany). Today the Group has got an extensive worldwide distribution network with 7 branch offices and over 150 distributors. Contact Details MARTIN YALE GROUP Bergheimer Strasse Markdorf / Germany Tel / (0) / Fax 0049 / (0) / mailto: strunz@martinyale.de Steps to improve your Data Security and ensure your Customers Trust 13
Stopping Leaks: How to Confront the Challenges of Endpoint Information Security from HDD. Whitepaper
 Stopping Leaks: How to Confront the Challenges of Endpoint Information Security from HDD intimus consulting is a division of the MARTIN YALE GROUP Bergheimer Strasse 6-12 88677 Markdorf / Germany www.intimusconsulting.com
Stopping Leaks: How to Confront the Challenges of Endpoint Information Security from HDD intimus consulting is a division of the MARTIN YALE GROUP Bergheimer Strasse 6-12 88677 Markdorf / Germany www.intimusconsulting.com
Trustworthy Mobile Security for Smartphones, Tablets, etc. Is there an App for that?
 Trustworthy Mobile Security for Smartphones, Tablets, etc. is there an App for that? intimus consulting is a division of the MARTIN YALE GROUP Bergheimer Strasse 6-12 88677 Markdorf / Germany www.intimusconsulting.com
Trustworthy Mobile Security for Smartphones, Tablets, etc. is there an App for that? intimus consulting is a division of the MARTIN YALE GROUP Bergheimer Strasse 6-12 88677 Markdorf / Germany www.intimusconsulting.com
Aftermath of a Data Breach Study
 Aftermath of a Data Breach Study Sponsored by Experian Data Breach Resolution Independently conducted by Ponemon Institute LLC Publication Date: January 2012 Ponemon Institute Research Report Aftermath
Aftermath of a Data Breach Study Sponsored by Experian Data Breach Resolution Independently conducted by Ponemon Institute LLC Publication Date: January 2012 Ponemon Institute Research Report Aftermath
PCI Compliance for Healthcare
 PCI Compliance for Healthcare Best practices for securing payment card data In just five years, criminal attacks on healthcare organizations are up by a stunning 125%. 1 Why are these data breaches happening?
PCI Compliance for Healthcare Best practices for securing payment card data In just five years, criminal attacks on healthcare organizations are up by a stunning 125%. 1 Why are these data breaches happening?
WHAT YOU NEED TO KNOW ABOUT CYBER SECURITY
 SMALL BUSINESSES WHAT YOU NEED TO KNOW ABOUT CYBER SECURITY ONE CLICK CAN CHANGE EVERYTHING SMALL BUSINESSES My reputation was ruined by malicious emails ONE CLICK CAN CHANGE EVERYTHING Cybercrime comes
SMALL BUSINESSES WHAT YOU NEED TO KNOW ABOUT CYBER SECURITY ONE CLICK CAN CHANGE EVERYTHING SMALL BUSINESSES My reputation was ruined by malicious emails ONE CLICK CAN CHANGE EVERYTHING Cybercrime comes
Whitepaper. Best Practices for Securing Your Backup Data. BOSaNOVA Phone: 866-865-5250 Email: info@theq3.com Web: www.theq3.com
 Whitepaper Best Practices for Securing Your Backup Data BOSaNOVA Phone: 866-865-5250 Email: info@theq3.com Web: www.theq3.com DATA PROTECTION CHALLENGE Encryption, the process of scrambling information
Whitepaper Best Practices for Securing Your Backup Data BOSaNOVA Phone: 866-865-5250 Email: info@theq3.com Web: www.theq3.com DATA PROTECTION CHALLENGE Encryption, the process of scrambling information
Security of Paper Records & Document Shredding. Sponsored by Cintas. Independently conducted by Ponemon Institute LLC Publication Date: January 2014
 Security of Paper Records & Document Shredding Sponsored by Cintas Independently conducted by Ponemon Institute LLC Publication Date: January 2014 Ponemon Institute Research Report Part 1. Introduction
Security of Paper Records & Document Shredding Sponsored by Cintas Independently conducted by Ponemon Institute LLC Publication Date: January 2014 Ponemon Institute Research Report Part 1. Introduction
Small businesses: What you need to know about cyber security
 Small businesses: What you need to know about cyber security March 2015 Contents page What you need to know about cyber security... 3 Why you need to know about cyber security... 4 Getting the basics right...
Small businesses: What you need to know about cyber security March 2015 Contents page What you need to know about cyber security... 3 Why you need to know about cyber security... 4 Getting the basics right...
Information Security
 Information Security A staff guide to the University's Information Systems Security Policy Issued by the IT Security Group on behalf of the University. Information Systems Security Guidelines for Staff
Information Security A staff guide to the University's Information Systems Security Policy Issued by the IT Security Group on behalf of the University. Information Systems Security Guidelines for Staff
S22 - Employee and Customer Awareness Turning Vulnerabilities Into Sentries John Sapp
 S22 - Employee and Customer Awareness Turning Vulnerabilities Into Sentries John Sapp Employee and Customer Awareness Turning Vulnerabilities Into Sentries What You Will Learn Data Breaches + employees
S22 - Employee and Customer Awareness Turning Vulnerabilities Into Sentries John Sapp Employee and Customer Awareness Turning Vulnerabilities Into Sentries What You Will Learn Data Breaches + employees
FINAL May 2005. Guideline on Security Systems for Safeguarding Customer Information
 FINAL May 2005 Guideline on Security Systems for Safeguarding Customer Information Table of Contents 1 Introduction 1 1.1 Purpose of Guideline 1 2 Definitions 2 3 Internal Controls and Procedures 2 3.1
FINAL May 2005 Guideline on Security Systems for Safeguarding Customer Information Table of Contents 1 Introduction 1 1.1 Purpose of Guideline 1 2 Definitions 2 3 Internal Controls and Procedures 2 3.1
Cybersecurity and the Threat to Your Company
 Why is BIG Data Important? March 2012 1 Cybersecurity and the Threat to Your Company A Navint Partners White Paper September 2014 www.navint.com Cyber Security and the threat to your company September
Why is BIG Data Important? March 2012 1 Cybersecurity and the Threat to Your Company A Navint Partners White Paper September 2014 www.navint.com Cyber Security and the threat to your company September
Small businesses: What you need to know about cyber security
 Small businesses: What you need to know about cyber security Contents Why you need to know about cyber security... 3 Understanding the risks to your business... 4 How you can manage the risks... 5 Planning
Small businesses: What you need to know about cyber security Contents Why you need to know about cyber security... 3 Understanding the risks to your business... 4 How you can manage the risks... 5 Planning
DATA BREACHES: WHEN COMPLIANCE IS NOT ENOUGH
 DATA BREACHES: WHEN COMPLIANCE IS NOT ENOUGH Andy Watson Grant Thornton LLP. All rights reserved. CYBERSECURITY 2 SURVEY OF CHIEF AUDIT EXECUTIVES (CAEs) GRANT THORNTON'S 2014 CAE SURVEY Data privacy and
DATA BREACHES: WHEN COMPLIANCE IS NOT ENOUGH Andy Watson Grant Thornton LLP. All rights reserved. CYBERSECURITY 2 SURVEY OF CHIEF AUDIT EXECUTIVES (CAEs) GRANT THORNTON'S 2014 CAE SURVEY Data privacy and
Nine recommendations for alternative funds battling cyber crime. kpmg.ca/cybersecurity
 Nine recommendations for alternative funds battling cyber crime kpmg.ca/cybersecurity Cyber criminals steal user names and passwords and use it to conduct financial trading activity illicitly. Hackers
Nine recommendations for alternative funds battling cyber crime kpmg.ca/cybersecurity Cyber criminals steal user names and passwords and use it to conduct financial trading activity illicitly. Hackers
Malware isn t The only Threat on Your Endpoints
 Malware isn t The only Threat on Your Endpoints Key Themes The cyber-threat landscape has Overview Cybersecurity has gained a much higher profile over the changed, and so have the past few years, thanks
Malware isn t The only Threat on Your Endpoints Key Themes The cyber-threat landscape has Overview Cybersecurity has gained a much higher profile over the changed, and so have the past few years, thanks
Data Breaches, Identity Theft, and Employees
 Data Breaches, Identity Theft, and Employees Joining the Dots and Dispelling the Myths What you ll learn Data Breaches + identity theft + employees Data Breaches or Data Donations? Data Breaches + Identity
Data Breaches, Identity Theft, and Employees Joining the Dots and Dispelling the Myths What you ll learn Data Breaches + identity theft + employees Data Breaches or Data Donations? Data Breaches + Identity
Mitigating and managing cyber risk: ten issues to consider
 Mitigating and managing cyber risk: ten issues to consider The board of directors is responsible for managing and mitigating risk exposure. A recent study conducted by the Ponemon Institute 1 revealed
Mitigating and managing cyber risk: ten issues to consider The board of directors is responsible for managing and mitigating risk exposure. A recent study conducted by the Ponemon Institute 1 revealed
Cyber Self Assessment
 Cyber Self Assessment According to Protecting Personal Information A Guide for Business 1 a sound data security plan is built on five key principles: 1. Take stock. Know what personal information you have
Cyber Self Assessment According to Protecting Personal Information A Guide for Business 1 a sound data security plan is built on five key principles: 1. Take stock. Know what personal information you have
Cybercrime: risks, penalties and prevention
 Cybercrime: risks, penalties and prevention Cyber attacks have been appearing in the news with increased frequency and recent victims of cybercrime have included well-known companies such as Sony, LinkedIn,
Cybercrime: risks, penalties and prevention Cyber attacks have been appearing in the news with increased frequency and recent victims of cybercrime have included well-known companies such as Sony, LinkedIn,
GUIDE TO IMPROVING INFORMATION SECURITY IDENTIFYING WEAKNESSES & STRENGTHENING SECURITY
 Penetration Testing: What You Need to Know Now GUIDE TO IMPROVING INFORMATION SECURITY IDENTIFYING WEAKNESSES & STRENGTHENING SECURITY PENETRATION TESTING: GUIDE TO IMPROVING INFORMATION SECURITY Contact
Penetration Testing: What You Need to Know Now GUIDE TO IMPROVING INFORMATION SECURITY IDENTIFYING WEAKNESSES & STRENGTHENING SECURITY PENETRATION TESTING: GUIDE TO IMPROVING INFORMATION SECURITY Contact
CYBERSECURITY: Is Your Business Ready?
 CYBERSECURITY: Is Your Business Ready? Cybersecurity: Is your business ready? Cyber risk is just like any other corporate risk and it must be managed from the top. An organization will spend time monitoring
CYBERSECURITY: Is Your Business Ready? Cybersecurity: Is your business ready? Cyber risk is just like any other corporate risk and it must be managed from the top. An organization will spend time monitoring
Remarks by. Thomas J. Curry. Comptroller of the Currency. Before the. Chicago. November 7, 2014
 Remarks by Thomas J. Curry Comptroller of the Currency Before the 10 th Annual Community Bankers Symposium Chicago November 7, 2014 Good morning, it s a pleasure to be here today and to have this opportunity
Remarks by Thomas J. Curry Comptroller of the Currency Before the 10 th Annual Community Bankers Symposium Chicago November 7, 2014 Good morning, it s a pleasure to be here today and to have this opportunity
Corporate Spying An Overview
 Corporate Spying An Overview With the boom in informational and technological advancements in recent years, there comes the good and the bad the bad being more susceptibility to the theft of confidential
Corporate Spying An Overview With the boom in informational and technological advancements in recent years, there comes the good and the bad the bad being more susceptibility to the theft of confidential
A practical guide to IT security
 Data protection A practical guide to IT security Ideal for the small business The Data Protection Act states that appropriate technical and organisational measures shall be taken against unauthorised or
Data protection A practical guide to IT security Ideal for the small business The Data Protection Act states that appropriate technical and organisational measures shall be taken against unauthorised or
WHAT EVERY CEO, CIO AND CFO NEEDS TO KNOW ABOUT CYBER SECURITY.
 WHAT EVERY CEO, CIO AND CFO NEEDS TO KNOW ABOUT CYBER SECURITY. A guide for IT security from BIOS The Problem SME s, Enterprises and government agencies are under virtually constant attack today. There
WHAT EVERY CEO, CIO AND CFO NEEDS TO KNOW ABOUT CYBER SECURITY. A guide for IT security from BIOS The Problem SME s, Enterprises and government agencies are under virtually constant attack today. There
Hope for the best, prepare for the worst:
 Hope for the best, prepare for the worst: Why your customers will demand self-service back-up Presented by Ridley Ruth, COO Breaking News Yahoo email Accounts were hacked in Jan 2014 (Washington Post)
Hope for the best, prepare for the worst: Why your customers will demand self-service back-up Presented by Ridley Ruth, COO Breaking News Yahoo email Accounts were hacked in Jan 2014 (Washington Post)
FIVE PRACTICAL STEPS
 WHITEPAPER FIVE PRACTICAL STEPS To Protecting Your Organization Against Breach How Security Intelligence & Reducing Information Risk Play Strategic Roles in Driving Your Business CEOs, CIOs, CTOs, AND
WHITEPAPER FIVE PRACTICAL STEPS To Protecting Your Organization Against Breach How Security Intelligence & Reducing Information Risk Play Strategic Roles in Driving Your Business CEOs, CIOs, CTOs, AND
The Merchant. Skimming is No Laughing Matter. A hand held skimming device. These devices can easily be purchased online.
 1 February 2010 Volume 2, Issue 1 The Merchant Serving Florida State University s Payment Card Community Individual Highlights: Skimming Scam 1 Skimming at Work 2 Safe at Home 3 Read your Statement 4 Useful
1 February 2010 Volume 2, Issue 1 The Merchant Serving Florida State University s Payment Card Community Individual Highlights: Skimming Scam 1 Skimming at Work 2 Safe at Home 3 Read your Statement 4 Useful
How Your Current IT Security System Might Be Leaving You Exposed TAKEAWAYS CHALLENGES WHITE PAPER
 WHITE PAPER CHALLENGES Protecting company systems and data from costly hacker intrusions Finding tools and training to affordably and effectively enhance IT security Building More Secure Companies (and
WHITE PAPER CHALLENGES Protecting company systems and data from costly hacker intrusions Finding tools and training to affordably and effectively enhance IT security Building More Secure Companies (and
WHITE PAPER KEEPING CLIENT AND EMPLOYEE DATA SECURE DRIVES REVENUE AND BUILDS TRUST PROTECTING THE PROTECTOR
 KEEPING CLIENT AND EMPLOYEE DATA SECURE DRIVES REVENUE AND BUILDS TRUST Protecting Identities. Enhancing Reputations. IDT911 1 DATA BREACHES AND SUBSEQUENT IDENTITY THEFT AND FRAUD THREATEN YOUR ORGANIZATION
KEEPING CLIENT AND EMPLOYEE DATA SECURE DRIVES REVENUE AND BUILDS TRUST Protecting Identities. Enhancing Reputations. IDT911 1 DATA BREACHES AND SUBSEQUENT IDENTITY THEFT AND FRAUD THREATEN YOUR ORGANIZATION
Cyber Security - What Would a Breach Really Mean for your Business?
 Cyber Security - What Would a Breach Really Mean for your Business? August 2014 v1.0 As the internet has become increasingly important across every aspect of business, the risks posed by breaches to cyber
Cyber Security - What Would a Breach Really Mean for your Business? August 2014 v1.0 As the internet has become increasingly important across every aspect of business, the risks posed by breaches to cyber
Cybersecurity Workshop
 Cybersecurity Workshop February 10, 2015 E. Andrew Keeney, Esq. Kaufman & Canoles, P.C. E. Andrew Keeney, Esq. Kaufman & Canoles, P.C. 150 West Main Street, Suite 2100 Norfolk, VA 23510 (757) 624-3153
Cybersecurity Workshop February 10, 2015 E. Andrew Keeney, Esq. Kaufman & Canoles, P.C. E. Andrew Keeney, Esq. Kaufman & Canoles, P.C. 150 West Main Street, Suite 2100 Norfolk, VA 23510 (757) 624-3153
10 Smart Ideas for. Keeping Data Safe. From Hackers
 0100101001001010010001010010101001010101001000000100101001010101010010101010010100 0100101001001010010001010010101001010101001000000100101001010101010010101010010100000 0100101001001010010001010010101001010101001000000100101001010101010010101010010100000
0100101001001010010001010010101001010101001000000100101001010101010010101010010100 0100101001001010010001010010101001010101001000000100101001010101010010101010010100000 0100101001001010010001010010101001010101001000000100101001010101010010101010010100000
Network Security: Policies and Guidelines for Effective Network Management
 Network Security: Policies and Guidelines for Effective Network Management Department of Electrical and Computer Engineering, Federal University of Technology, Minna, Nigeria. jgkolo@gmail.com, usdauda@gmail.com
Network Security: Policies and Guidelines for Effective Network Management Department of Electrical and Computer Engineering, Federal University of Technology, Minna, Nigeria. jgkolo@gmail.com, usdauda@gmail.com
Leveraging a Maturity Model to Achieve Proactive Compliance
 Leveraging a Maturity Model to Achieve Proactive Compliance White Paper: Proactive Compliance Leveraging a Maturity Model to Achieve Proactive Compliance Contents Introduction............................................................................................
Leveraging a Maturity Model to Achieve Proactive Compliance White Paper: Proactive Compliance Leveraging a Maturity Model to Achieve Proactive Compliance Contents Introduction............................................................................................
How One Smart Phone Picture Can Take Down Your Company
 SESSION ID: HUM-R04 How One Smart Phone Picture Can Take Down Your Company Dr. Larry Ponemon Chairman and Founder Ponemon Institute @Ponemon Have You Ever Felt Wandering Eyes Over Your Shoulder? Username:
SESSION ID: HUM-R04 How One Smart Phone Picture Can Take Down Your Company Dr. Larry Ponemon Chairman and Founder Ponemon Institute @Ponemon Have You Ever Felt Wandering Eyes Over Your Shoulder? Username:
How to Protect Sensitive Corporate Data against Security Vulnerabilities of Your Vendors
 How to Protect Sensitive Corporate Data against Security Vulnerabilities of Your Vendors July 2014 Executive Summary Data breaches cost organizations millions and sometimes even billions of dollars in
How to Protect Sensitive Corporate Data against Security Vulnerabilities of Your Vendors July 2014 Executive Summary Data breaches cost organizations millions and sometimes even billions of dollars in
Protecting. Personal Information A Business Guide. Division of Finance and Corporate Securities
 Protecting Personal Information A Business Guide Division of Finance and Corporate Securities Oregon Identity Theft Protection Act Collecting, keeping, and sharing personal data is essential to all types
Protecting Personal Information A Business Guide Division of Finance and Corporate Securities Oregon Identity Theft Protection Act Collecting, keeping, and sharing personal data is essential to all types
CORPORATE IDENTITY FRAUD: A PRIMER
 CORPORATE IDENTITY FRAUD: A PRIMER Hanim Norza Baba, Head of Graduate Studies Center, Universiti Teknologi MARA, Melaka, Malaysia. drhanimnorzababa@gmail.com ABSTRACT Corporate identity fraud occurs when
CORPORATE IDENTITY FRAUD: A PRIMER Hanim Norza Baba, Head of Graduate Studies Center, Universiti Teknologi MARA, Melaka, Malaysia. drhanimnorzababa@gmail.com ABSTRACT Corporate identity fraud occurs when
Data Breaches: Expectation and Reality
 White Paper: Data Security Sharon Frost Faronics UK +44 (0) 1344 741057 sfrost@faronics.com Introduction In November 2012, The Ponemon Institute released the State of Cyber Security Readiness: UK Study
White Paper: Data Security Sharon Frost Faronics UK +44 (0) 1344 741057 sfrost@faronics.com Introduction In November 2012, The Ponemon Institute released the State of Cyber Security Readiness: UK Study
What the Biggest Data Breaches in Retail Have Taught Us about Cyber Security
 What the Biggest Data Breaches in Retail Have Taught Us about Cyber Security With the holiday season upon us, much attention turns to the retail sector, which is expected to see unprecedented activity
What the Biggest Data Breaches in Retail Have Taught Us about Cyber Security With the holiday season upon us, much attention turns to the retail sector, which is expected to see unprecedented activity
Data Security Breaches: Learn more about two new regulations and how to help reduce your risks
 Data Security Breaches: Learn more about two new regulations and how to help reduce your risks By Susan Salpeter, Vice President, Zurich Healthcare Risk Management News stories about data security breaches
Data Security Breaches: Learn more about two new regulations and how to help reduce your risks By Susan Salpeter, Vice President, Zurich Healthcare Risk Management News stories about data security breaches
NNIT Cybersecurity. A new threat landscape requires a new approach
 NNIT Cybersecurity A new threat landscape requires a new approach Effective cybersecurity is not about spending more money. It s about aligning your security initiatives with the threats and priorities
NNIT Cybersecurity A new threat landscape requires a new approach Effective cybersecurity is not about spending more money. It s about aligning your security initiatives with the threats and priorities
The Importance of Senior Executive Involvement in Breach Response
 The Importance of Senior Executive Involvement in Breach Response Sponsored by HP Enterprise Security Services Independently conducted by Ponemon Institute LLC Publication Date: October 2014 The Importance
The Importance of Senior Executive Involvement in Breach Response Sponsored by HP Enterprise Security Services Independently conducted by Ponemon Institute LLC Publication Date: October 2014 The Importance
To all GRSB debit and credit card customers:
 To all GRSB debit and credit card customers: A data breach at the Target Corporation may have exposed 40 million credit/debit cards to potential fraudulent activity. If you made purchases in a Target store
To all GRSB debit and credit card customers: A data breach at the Target Corporation may have exposed 40 million credit/debit cards to potential fraudulent activity. If you made purchases in a Target store
Seamless Mobile Security for Network Operators. Build a secure foundation for winning new wireless services revenue.
 Seamless Mobile Security for Network Operators Build a secure foundation for winning new wireless services revenue. New wireless services drive revenues. Faced with the dual challenges of increasing revenues
Seamless Mobile Security for Network Operators Build a secure foundation for winning new wireless services revenue. New wireless services drive revenues. Faced with the dual challenges of increasing revenues
Hope for the best, prepare for the worst:
 Hope for the best, prepare for the worst: Why your customers will demand self-service back-up Presented by Ridley Ruth, COO 2014 a record year for hacking! 100K+ WordPress sites infected by mysterious
Hope for the best, prepare for the worst: Why your customers will demand self-service back-up Presented by Ridley Ruth, COO 2014 a record year for hacking! 100K+ WordPress sites infected by mysterious
Teradata and Protegrity High-Value Protection for High-Value Data
 Teradata and Protegrity High-Value Protection for High-Value Data 03.16 EB7178 DATA SECURITY Table of Contents 2 Data-Centric Security: Providing High-Value Protection for High-Value Data 3 Visibility:
Teradata and Protegrity High-Value Protection for High-Value Data 03.16 EB7178 DATA SECURITY Table of Contents 2 Data-Centric Security: Providing High-Value Protection for High-Value Data 3 Visibility:
TechTarget Enterprise Applications Media. Pocket E-Guide
 TechTarget Enterprise Applications Media Pocket E-Guide Data Breach Dangers: Learn to How to Protect Data and Lower Security Spending While most organizations today acknowledge the importance of information
TechTarget Enterprise Applications Media Pocket E-Guide Data Breach Dangers: Learn to How to Protect Data and Lower Security Spending While most organizations today acknowledge the importance of information
Global security intelligence. YoUR DAtA UnDeR siege: DeFenD it with encryption. #enterprisesec kaspersky.com/enterprise
 Global security intelligence YoUR DAtA UnDeR siege: DeFenD it with encryption #enterprisesec kaspersky.com/enterprise Contents Your Data Under Siege: Defend it with Encryption 3 Steps Taken to Minimise
Global security intelligence YoUR DAtA UnDeR siege: DeFenD it with encryption #enterprisesec kaspersky.com/enterprise Contents Your Data Under Siege: Defend it with Encryption 3 Steps Taken to Minimise
1. For each of the 25 questions, multiply each question response risk value (1-5) by the number of times it was chosen by the survey takers.
 Employee Security Awareness Survey Trenton Bond trent.bond@gmail.com Admin - Version 1.3 Security Awareness One of the most significant security risks that organizations and corporations face today is
Employee Security Awareness Survey Trenton Bond trent.bond@gmail.com Admin - Version 1.3 Security Awareness One of the most significant security risks that organizations and corporations face today is
Ten Questions Your Board Should be asking about Cyber Security. Eric M. Wright, Shareholder
 Ten Questions Your Board Should be asking about Cyber Security Eric M. Wright, Shareholder Eric Wright, CPA, CITP Started my career with Schneider Downs in 1983. Responsible for all IT audit and system
Ten Questions Your Board Should be asking about Cyber Security Eric M. Wright, Shareholder Eric Wright, CPA, CITP Started my career with Schneider Downs in 1983. Responsible for all IT audit and system
VENDOR MANAGEMENT. General Overview
 VENDOR MANAGEMENT General Overview With many organizations outsourcing services to other third-party entities, the issue of vendor management has become a noted topic in today s business world. Vendor
VENDOR MANAGEMENT General Overview With many organizations outsourcing services to other third-party entities, the issue of vendor management has become a noted topic in today s business world. Vendor
MONTSERRAT COLLEGE OF ART WRITTEN INFORMATION SECURITY POLICY (WISP)
 MONTSERRAT COLLEGE OF ART WRITTEN INFORMATION SECURITY POLICY (WISP) 201 CMR 17.00 Standards for the Protection of Personal Information Of Residents of the Commonwealth of Massachusetts Revised April 28,
MONTSERRAT COLLEGE OF ART WRITTEN INFORMATION SECURITY POLICY (WISP) 201 CMR 17.00 Standards for the Protection of Personal Information Of Residents of the Commonwealth of Massachusetts Revised April 28,
Cyber threat reality check GLOBAL TECHNOLOGY S RISK ADVISOR SERIES TURN RISK INTO ADVANTAGE THE THREAT IS GROWING IGNORING IT CAN BE COSTLY
 GLOBAL TECHNOLOGY S RISK ADVISOR SERIES TURN RISK INTO ADVANTAGE WHY COMPLACENCY IS UNWARRANTED > WHERE CYBER THREATS COME FROM > THREE STEPS TO MANAGING CYBER THREATS > Cyber threat reality check THE
GLOBAL TECHNOLOGY S RISK ADVISOR SERIES TURN RISK INTO ADVANTAGE WHY COMPLACENCY IS UNWARRANTED > WHERE CYBER THREATS COME FROM > THREE STEPS TO MANAGING CYBER THREATS > Cyber threat reality check THE
www.pwc.co.uk Cyber security Building confidence in your digital future
 www.pwc.co.uk Cyber security Building confidence in your digital future November 2013 Contents 1 Confidence in your digital future 2 Our point of view 3 Building confidence 4 Our services Confidence in
www.pwc.co.uk Cyber security Building confidence in your digital future November 2013 Contents 1 Confidence in your digital future 2 Our point of view 3 Building confidence 4 Our services Confidence in
BIG SHIFT TO CLOUD-BASED SECURITY
 GUIDE THE BIG SHIFT TO CLOUD-BASED SECURITY How mid-sized and smaller organizations can manage their IT risks and meet regulatory compliance with minimal staff and budget. CONTINUOUS SECURITY TABLE OF
GUIDE THE BIG SHIFT TO CLOUD-BASED SECURITY How mid-sized and smaller organizations can manage their IT risks and meet regulatory compliance with minimal staff and budget. CONTINUOUS SECURITY TABLE OF
Proactive Credential Monitoring as a Method of Fraud Prevention and Risk Mitigation. By Marc Ostryniec, vice president, CSID
 Proactive Credential Monitoring as a Method of Fraud Prevention and Risk Mitigation By Marc Ostryniec, vice president, CSID The increase in volume, severity, publicity and fallout of recent data breaches
Proactive Credential Monitoring as a Method of Fraud Prevention and Risk Mitigation By Marc Ostryniec, vice president, CSID The increase in volume, severity, publicity and fallout of recent data breaches
Matthew Howes Senior Vice President, Strategic Services inventiv Digital+Innovation Matthew.Howes@inVentivHealth.com
 WHITE PAPER Global Digital Security: The Human Element March 2014 Written by: Matthew Howes Senior Vice President, Strategic Services inventiv Digital+Innovation Matthew.Howes@inVentivHealth.com TABLE
WHITE PAPER Global Digital Security: The Human Element March 2014 Written by: Matthew Howes Senior Vice President, Strategic Services inventiv Digital+Innovation Matthew.Howes@inVentivHealth.com TABLE
Data Security in the Evolving Payments Ecosystem
 Data Security in the Evolving Payments Ecosystem Sponsored by Experian Data Breach Resolution Independently conducted by Ponemon Institute LLC Publication Date: April 2015 Ponemon Institute Research Report
Data Security in the Evolving Payments Ecosystem Sponsored by Experian Data Breach Resolution Independently conducted by Ponemon Institute LLC Publication Date: April 2015 Ponemon Institute Research Report
Cybersecurity: Safeguarding Your Business in the Digital Age
 Cybersecurity: Safeguarding Your Business in the Digital Age Introduction The digitization of our society has had a powerful impact on the ways in which organizations work and relate to their customers
Cybersecurity: Safeguarding Your Business in the Digital Age Introduction The digitization of our society has had a powerful impact on the ways in which organizations work and relate to their customers
Experience the commitment WHITE PAPER. Information Security Continuous Monitoring. Charting the Right Course. cgi.com 2014 CGI GROUP INC.
 Experience the commitment WHITE PAPER Information Security Continuous Monitoring Charting the Right Course May 2014 cgi.com 2014 CGI GROUP INC. During the last few months of 2013, six federal agencies
Experience the commitment WHITE PAPER Information Security Continuous Monitoring Charting the Right Course May 2014 cgi.com 2014 CGI GROUP INC. During the last few months of 2013, six federal agencies
WHITE PAPER THE TOP 5 MYTHS OF DATA BREACHES
 WHITE PAPER THE TOP 5 MYTHS OF DATA BREACHES Table of Contents Introduction...3 Who and what is at risk?...3 Myth #1...4 Myth #2...4 Myth #3...5 Myth #4...6 Myth #5...6 Conclusion...7 The Top 5 Myths of
WHITE PAPER THE TOP 5 MYTHS OF DATA BREACHES Table of Contents Introduction...3 Who and what is at risk?...3 Myth #1...4 Myth #2...4 Myth #3...5 Myth #4...6 Myth #5...6 Conclusion...7 The Top 5 Myths of
Nine Steps to Smart Security for Small Businesses
 Nine Steps to Smart Security for Small Businesses by David Lacey Co-Founder, Jericho Forum Courtesy of TABLE OF CONTENTS INTRODUCTION... 1 WHY SHOULD I BOTHER?... 1 AREN T FIREWALLS AND ANTI-VIRUS ENOUGH?...
Nine Steps to Smart Security for Small Businesses by David Lacey Co-Founder, Jericho Forum Courtesy of TABLE OF CONTENTS INTRODUCTION... 1 WHY SHOULD I BOTHER?... 1 AREN T FIREWALLS AND ANTI-VIRUS ENOUGH?...
Cybersecurity. Are you prepared?
 Cybersecurity Are you prepared? First Cash, then your customer, now YOU! What is Cybersecurity? The body of technologies, processes, practices designed to protect networks, computers, programs, and data
Cybersecurity Are you prepared? First Cash, then your customer, now YOU! What is Cybersecurity? The body of technologies, processes, practices designed to protect networks, computers, programs, and data
2012 Endpoint Security Best Practices Survey
 WHITE PAPER: 2012 ENDPOINT SECURITY BEST PRACTICES SURVEY........................................ 2012 Endpoint Security Best Practices Survey Who should read this paper Small and medium business owners
WHITE PAPER: 2012 ENDPOINT SECURITY BEST PRACTICES SURVEY........................................ 2012 Endpoint Security Best Practices Survey Who should read this paper Small and medium business owners
Reputation Impact of a Data Breach Executive Summary
 Reputation Impact of a Data Breach Executive Summary Sponsored by Experian Data Breach Resolution Independently conducted by Ponemon Institute LLC Publication Date: October 2011 Ponemon Institute Research
Reputation Impact of a Data Breach Executive Summary Sponsored by Experian Data Breach Resolution Independently conducted by Ponemon Institute LLC Publication Date: October 2011 Ponemon Institute Research
THE CYBER SECURITY PLAYBOOK WHAT EVERY BOARD OF DIRECTORS SHOULD KNOW BEFORE, DURING, AND AFTER AN ATTACK SECURITY REIMAGINED
 THE CYBER SECURITY PLAYBOOK WHAT EVERY BOARD OF DIRECTORS SHOULD KNOW BEFORE, DURING, AND AFTER AN ATTACK SECURITY REIMAGINED THE CYBER SECURITY PLAYBOOK 2 03 Introduction 04 Changing Roles, Changing Threat
THE CYBER SECURITY PLAYBOOK WHAT EVERY BOARD OF DIRECTORS SHOULD KNOW BEFORE, DURING, AND AFTER AN ATTACK SECURITY REIMAGINED THE CYBER SECURITY PLAYBOOK 2 03 Introduction 04 Changing Roles, Changing Threat
Cyber Security Management
 Cyber Security Management Focusing on managing your IT Security effectively. By Anthony Goodeill With the news cycles regularly announcing a recurrently theme of targets of hacker attacks and companies
Cyber Security Management Focusing on managing your IT Security effectively. By Anthony Goodeill With the news cycles regularly announcing a recurrently theme of targets of hacker attacks and companies
Assessing the strength of your security operating model
 www.pwc.com Assessing the strength of your security operating model May 2014 Assessing the strength of your security operating model Retail stores, software companies, the U.S. Federal Reserve it seems
www.pwc.com Assessing the strength of your security operating model May 2014 Assessing the strength of your security operating model Retail stores, software companies, the U.S. Federal Reserve it seems
How To Protect Your Restaurant From A Data Security Breach
 NAVIGATING THE PAYMENTS AND SECURITY LANDSCAPE Payment disruptions impacting restaurant owners today An NCR Hospitality white paper Almost every month we hear a news story about another data breach that
NAVIGATING THE PAYMENTS AND SECURITY LANDSCAPE Payment disruptions impacting restaurant owners today An NCR Hospitality white paper Almost every month we hear a news story about another data breach that
Security and Privacy Trends 2014
 2014 Agenda Today s cyber threats 3 You could be under cyber attack now! Improve 6 Awareness of cyber threats propels improvements Expand 11 Leading practices to combat cyber threats Innovate 20 To survive,
2014 Agenda Today s cyber threats 3 You could be under cyber attack now! Improve 6 Awareness of cyber threats propels improvements Expand 11 Leading practices to combat cyber threats Innovate 20 To survive,
Kaseya White Paper. Endpoint Security. Fighting Cyber Crime with Automated, Centralized Management. www.kaseya.com
 Kaseya White Paper Endpoint Security Fighting Cyber Crime with Automated, Centralized Management www.kaseya.com To win the ongoing war against hackers and cyber criminals, IT professionals must do two
Kaseya White Paper Endpoint Security Fighting Cyber Crime with Automated, Centralized Management www.kaseya.com To win the ongoing war against hackers and cyber criminals, IT professionals must do two
How-To Guide: Cyber Security. Content Provided by
 How-To Guide: Cyber Security Content Provided by Who needs cyber security? Businesses that have, use, or support computers, smartphones, email, websites, social media, or cloudbased services. Businesses
How-To Guide: Cyber Security Content Provided by Who needs cyber security? Businesses that have, use, or support computers, smartphones, email, websites, social media, or cloudbased services. Businesses
Sytorus Information Security Assessment Overview
 Sytorus Information Assessment Overview Contents Contents 2 Section 1: Our Understanding of the challenge 3 1 The Challenge 4 Section 2: IT-CMF 5 2 The IT-CMF 6 Section 3: Information Management (ISM)
Sytorus Information Assessment Overview Contents Contents 2 Section 1: Our Understanding of the challenge 3 1 The Challenge 4 Section 2: IT-CMF 5 2 The IT-CMF 6 Section 3: Information Management (ISM)
How Companies and Consumers Can Protect Themselves
 Identity Theft How Companies and Consumers Can Protect Themselves Identity theft has become one of the fastest-growing white collar crimes in the world. Just as infectious diseases can today spread faster
Identity Theft How Companies and Consumers Can Protect Themselves Identity theft has become one of the fastest-growing white collar crimes in the world. Just as infectious diseases can today spread faster
Remarks by Thomas J. Curry Comptroller of the Currency Before the New England Council Boston, Massachusetts May 16, 2014
 Remarks by Thomas J. Curry Comptroller of the Currency Before the New England Council Boston, Massachusetts May 16, 2014 It s a pleasure to be with you back home in Boston. I was here just six weeks ago
Remarks by Thomas J. Curry Comptroller of the Currency Before the New England Council Boston, Massachusetts May 16, 2014 It s a pleasure to be with you back home in Boston. I was here just six weeks ago
LAMAR STATE COLLEGE - ORANGE INFORMATION RESOURCES SECURITY MANUAL. for INFORMATION RESOURCES
 LAMAR STATE COLLEGE - ORANGE INFORMATION RESOURCES SECURITY MANUAL for INFORMATION RESOURCES Updated: June 2007 Information Resources Security Manual 1. Purpose of Security Manual 2. Audience 3. Acceptable
LAMAR STATE COLLEGE - ORANGE INFORMATION RESOURCES SECURITY MANUAL for INFORMATION RESOURCES Updated: June 2007 Information Resources Security Manual 1. Purpose of Security Manual 2. Audience 3. Acceptable
$194 per record lost* 3/15/2013. Global Economic Crime Survey. Data Breach Costs. David Childers, CEO Compli Vivek Krishnamurthy, Foley Hoag LLP
 David Childers, CEO Compli Vivek Krishnamurthy, Foley Hoag LLP Global Economic Crime Survey Global Cyber Crime is the fastest growing economic crime Cyber Crime is more lucrative than trafficking drugs!
David Childers, CEO Compli Vivek Krishnamurthy, Foley Hoag LLP Global Economic Crime Survey Global Cyber Crime is the fastest growing economic crime Cyber Crime is more lucrative than trafficking drugs!
4 Steps to Better Security In The BYOD Era For Your Company.
 4 Steps to Better Security In The BYOD Era For Your Company. Research & Analysis by: Q Kensington Security Survey 2014 Our 2014 survey of more than 500 IT Managers found that: 44% of organizations suffered
4 Steps to Better Security In The BYOD Era For Your Company. Research & Analysis by: Q Kensington Security Survey 2014 Our 2014 survey of more than 500 IT Managers found that: 44% of organizations suffered
Data Security: Fight Insider Threats & Protect Your Sensitive Data
 Data Security: Fight Insider Threats & Protect Your Sensitive Data Marco Ercolani Agenda Data is challenging to secure A look at security incidents Cost of a Data Breach Data Governance and Security Understand
Data Security: Fight Insider Threats & Protect Your Sensitive Data Marco Ercolani Agenda Data is challenging to secure A look at security incidents Cost of a Data Breach Data Governance and Security Understand
Network Security & Privacy Landscape
 Network Security & Privacy Landscape Presented By: Greg Garijanian Senior Underwriter Professional Liability 1 Agenda Network Security Overview -Latest Threats - Exposure Trends - Regulations Case Studies
Network Security & Privacy Landscape Presented By: Greg Garijanian Senior Underwriter Professional Liability 1 Agenda Network Security Overview -Latest Threats - Exposure Trends - Regulations Case Studies
AUTOMATED PENETRATION TESTING PRODUCTS
 AUTOMATED PENETRATION TESTING PRODUCTS Justification and Return on Investment (ROI) EXECUTIVE SUMMARY This paper will help you justify the need for an automated penetration testing product and demonstrate
AUTOMATED PENETRATION TESTING PRODUCTS Justification and Return on Investment (ROI) EXECUTIVE SUMMARY This paper will help you justify the need for an automated penetration testing product and demonstrate
Deciphering the Code: A Simple Guide to Encryption
 Deciphering the Code: A Simple Guide to Encryption By Anthony Merry, Director of Product Management - Data Protection A business s success is increasingly dependent on its ability to leverage its data.
Deciphering the Code: A Simple Guide to Encryption By Anthony Merry, Director of Product Management - Data Protection A business s success is increasingly dependent on its ability to leverage its data.
Why Lawyers? Why Now?
 TODAY S PRESENTERS Why Lawyers? Why Now? New HIPAA regulations go into effect September 23, 2013 Expands HIPAA safeguarding and breach liabilities for business associates (BAs) Lawyer is considered a business
TODAY S PRESENTERS Why Lawyers? Why Now? New HIPAA regulations go into effect September 23, 2013 Expands HIPAA safeguarding and breach liabilities for business associates (BAs) Lawyer is considered a business
The Impact of Cybercrime on Business
 The Impact of Cybercrime on Business Studies of IT practitioners in the United States, United Kingdom, Germany, Hong Kong and Brazil Sponsored by Check Point Software Technologies Independently conducted
The Impact of Cybercrime on Business Studies of IT practitioners in the United States, United Kingdom, Germany, Hong Kong and Brazil Sponsored by Check Point Software Technologies Independently conducted
AUTOMATED PENETRATION TESTING PRODUCTS
 AUTOMATED PENETRATION TESTING PRODUCTS Justification and Return on Investment (ROI) EXECUTIVE SUMMARY This paper will help you justify the need for automated penetration testing software and demonstrate
AUTOMATED PENETRATION TESTING PRODUCTS Justification and Return on Investment (ROI) EXECUTIVE SUMMARY This paper will help you justify the need for automated penetration testing software and demonstrate
OVERVIEW. With just 10,000 customers in your database, the cost of a data breach averages more than $2 million.
 Security PLAYBOOK OVERVIEW Today, security threats to retail organizations leave little margin for error. Retailers face increasingly complex security challenges persistent threats that can undermine the
Security PLAYBOOK OVERVIEW Today, security threats to retail organizations leave little margin for error. Retailers face increasingly complex security challenges persistent threats that can undermine the
Employing Best Practices for Mainframe Tape Encryption
 WHITE PAPER: DATA ENCRYPTION BEST PRACTICES FOR MAINFRAME TAPE Employing Best Practices for Mainframe Tape Encryption JUNE 2008 Stefan Kochishan CA MAINFRAME PRODUCT MARKETING John Hill CA MAINFRAME PRODUCT
WHITE PAPER: DATA ENCRYPTION BEST PRACTICES FOR MAINFRAME TAPE Employing Best Practices for Mainframe Tape Encryption JUNE 2008 Stefan Kochishan CA MAINFRAME PRODUCT MARKETING John Hill CA MAINFRAME PRODUCT
October 24, 2014. Mitigating Legal and Business Risks of Cyber Breaches
 October 24, 2014 Mitigating Legal and Business Risks of Cyber Breaches AGENDA Introductions Cyber Threat Landscape Cyber Risk Mitigation Strategies 1 Introductions 2 Introductions To Be Confirmed Title
October 24, 2014 Mitigating Legal and Business Risks of Cyber Breaches AGENDA Introductions Cyber Threat Landscape Cyber Risk Mitigation Strategies 1 Introductions 2 Introductions To Be Confirmed Title
Collateral Effects of Cyberwar
 Your texte here. Collateral Effects of Cyberwar by Ilia Kolochenko for Geneva Information Security Day 9 th of October 2015 Quick Facts and Numbers About Cybersecurity In 2014 the annual cost of global
Your texte here. Collateral Effects of Cyberwar by Ilia Kolochenko for Geneva Information Security Day 9 th of October 2015 Quick Facts and Numbers About Cybersecurity In 2014 the annual cost of global
WRITTEN TESTIMONY BEFORE THE HEARING ON PROTECTING PERSONAL CONSUMER INFORMATION FROM CYBER ATTACKS AND DATA BREACHES MARCH 26, 2014 2:30 PM
 WRITTEN TESTIMONY BEFORE THE SENATE COMMITTEE ON COMMERCE, SCIENCE, & TRANSPORTATION HEARING ON PROTECTING PERSONAL CONSUMER INFORMATION FROM CYBER ATTACKS AND DATA BREACHES MARCH 26, 2014 2:30 PM TESTIMONY
WRITTEN TESTIMONY BEFORE THE SENATE COMMITTEE ON COMMERCE, SCIENCE, & TRANSPORTATION HEARING ON PROTECTING PERSONAL CONSUMER INFORMATION FROM CYBER ATTACKS AND DATA BREACHES MARCH 26, 2014 2:30 PM TESTIMONY
ERM Symposium April 2009. Moderator Nancy Bennett
 ERM Symposium April 2009 RI4-Implementing a Comprehensive Privacy Program John Kelly Joseph Nocera Moderator Nancy Bennett Data & Identity Theft: Keeping sensitive data out of the wrong hands Presented
ERM Symposium April 2009 RI4-Implementing a Comprehensive Privacy Program John Kelly Joseph Nocera Moderator Nancy Bennett Data & Identity Theft: Keeping sensitive data out of the wrong hands Presented
Data Security in Development & Testing
 Data Security in Development & Testing Sponsored by Micro Focus Independently conducted by Ponemon Institute LLC Publication Date: July 31, 2009 Ponemon Institute Research Report Data Security in Development
Data Security in Development & Testing Sponsored by Micro Focus Independently conducted by Ponemon Institute LLC Publication Date: July 31, 2009 Ponemon Institute Research Report Data Security in Development
A NEW APPROACH TO CYBER SECURITY
 A NEW APPROACH TO CYBER SECURITY We believe cyber security should be about what you can do not what you can t. DRIVEN BY BUSINESS ASPIRATIONS We work with you to move your business forward. Positively
A NEW APPROACH TO CYBER SECURITY We believe cyber security should be about what you can do not what you can t. DRIVEN BY BUSINESS ASPIRATIONS We work with you to move your business forward. Positively
Network Security and Data Privacy Insurance for Physician Groups
 Network Security and Data Privacy Insurance for Physician Groups February 2014 Lockton Companies While exposure to medical malpractice remains a principal risk MIKE EGAN, CPCU Senior Vice President Unit
Network Security and Data Privacy Insurance for Physician Groups February 2014 Lockton Companies While exposure to medical malpractice remains a principal risk MIKE EGAN, CPCU Senior Vice President Unit
Testing the Security of your Applications
 Home Safeguarding Business Critical Testing the of your Applications Safeguarding business critical systems and applications 2 Safeguarding business critical systems and applications Organizations are
Home Safeguarding Business Critical Testing the of your Applications Safeguarding business critical systems and applications 2 Safeguarding business critical systems and applications Organizations are
the evolving governance Model for CYBERSECURITY RISK By Gary owen, Director, Promontory Financial Group
 the evolving governance Model for CYBERSECURITY RISK By Gary owen, Director, Promontory Financial Group 54 Banking PersPective Quarter 2, 2014 Responsibility for the oversight of information security and
the evolving governance Model for CYBERSECURITY RISK By Gary owen, Director, Promontory Financial Group 54 Banking PersPective Quarter 2, 2014 Responsibility for the oversight of information security and
IN CASE OF EMERGENCY. A guide for managing a data breach quickly and confidently
 IN CASE OF EMERGENCY A guide for managing a data breach quickly and confidently The number of breaches increased 47% in 2008. Source: Identity Theft Resource Center. ITRC Breach Report 2008 Final. January
IN CASE OF EMERGENCY A guide for managing a data breach quickly and confidently The number of breaches increased 47% in 2008. Source: Identity Theft Resource Center. ITRC Breach Report 2008 Final. January
