ISE Cyber Security Industry Classification
|
|
|
- Basil Freeman
- 8 years ago
- Views:
Transcription
1 Industry Classification Methodology Guide ISE Cyber Security Industry Classification Issue 1.0 Issue date: August 26, 2015 Produced by: International Securities Exchange, LLC 60 Broad Street, New York NY
2 Table of Contents Chapter 1. Introduction... 3 Chapter 2. Industry Classification Structure and Changes Classification Guidelines Infrastructure Provider Service Provider... 5 Chapter 3. Classification Committee... 6 Chapter 4. Contact... 7
3 Chapter 1. Introduction Given the lack of an existing generally accepted equity classification scheme identifying and cataloging equity securities of companies involved in the cyber security industry, the ISE Cyber Security Industry Classification was developed by ISE. The ISE Cyber Security Industry Classification provides a framework for investment research, portfolio management and asset allocation. Eligible companies are publicly listed on exchanges globally and derive all or a material proportion of their revenues from cyber security or cyber security-related activities. ISE is responsible for the classification of companies within the ISE Cyber Security Industry Classification, maintenance of the database of companies comprising the ISE Cyber Security Industry Classification, including the history of changes, and the timely communication of any updates to licensees of the data. 3
4 Chapter 2. Industry Classification 2.1. Structure and Changes The Classification Committee will rely primarily on published audited annual reports and discussions with company investor relations groups, industry participants and experts to vet companies for inclusion and determine their classification. Companies are allocated into a category based on the focus of their business. In cases where a company s business straddles two or more segments, a final category determination will be made based on audited reported revenue segments as well as discussions with that company s investor relations group. Qualified and newly listed companies are assessed and approved by the Classification Committee for inclusion in the ISE Cyber Security Industry Classification. As the cyber security industry continues to evolve, the framework of the ISE Cyber Security Industry Classification will evolve in order to accurately reflect the thencurrent state of the cyber security industry. Any adjustments to the framework of the ISE Cyber Security Industry Classification will be based on long-term trends driving the cyber security industry and will be announced in advance of implementation. In the event of a significant change to a company s structure or business, its classification may be reviewed on an ad hoc basis. Events triggering a review include, but are not limited to: mergers, acquisitions, bankruptcy and delisting. Companies will also undergo a quarterly review. Companies may not apply, and may not be nominated for inclusion in the ISE Cyber Security Industry Classification. Additions and deletions to the list of companies eligible for classification may occur on an ad hoc basis and is dependent wholly on the reported activities of those companies. No changes in the ISE Cyber Security Index Classification will be based on nonpublic information Classification Guidelines All equities listed on exchanges globally are eligible for review. Companies are classified quantitatively and qualitatively. Each company is assigned to a single category according to its principal business activity based on audited financial reporting including the director s report. ISE uses revenues as a key factor in determining a company s principal business activity. Earnings and market perception are also recognized as important and relevant information for categorization purposes and are taken into account during the review process. The scope of the definition of cyber security can be quite broad. For the purposes of the ISE Cyber Security Index Classification, we consider cyber security to be concerned with enabling the protection of and secure communication between unique nodes of the internet from both external and internal threats. The basic eligibility determinant for inclusion in the ISE Cyber Security Index Classification is that prospective companies are either those which work to develop hardware and/or software that safeguards access to files, websites and networks from external origins or those that utilize these tools to provide consulting and/or secure cyber based services to their clients. 4
5 These two categorizations have been labeled as: i) Infrastructure Provider a company that is a direct provider of hardware or software for cyber security and for which cyber security business activities are the key driver of the business or, ii) Service Provider a company whose business model is defined by its role in providing secure cyber based services and for which those business activities are a key driver of the business Infrastructure Provider These companies provide hardware and/or software that help route and regulate message traffic in and out of networks. Anti-Virus - Companies providing anti-virus solutions fall into the definition of Infrastructure Provider as they provide protection against threats originating from external sources. Network Security - Examples of the type of network hardware products these companies produce include gateways, routers, bridges and switches. The set of operating instructions and security, referred to as a firewall, is usually bundled with the specific hardware element by the manufacturer although third party software can often be adapted to work outside of its native environment. In the case of firewalls, often times, third-party solutions can provide more robust solutions than those packaged with network hardware Service Provider These companies provide services that fall outside the narrow definition of Infrastructure Provider. Service Providers allow for their clients to conduct business securely while Infrastructure Providers are providing security itself. For example, a company may be engaged in domain name management or managing the efficient routing of internet traffic but do not have the responsibility for the security of the domains themselves or the nature of the traffic they are routing. Another example would be companies involved in the manufacture of secure credit cards, network authentication devices and/or electronic identity documents. 5
6 Chapter 3. Classification Committee The Classification Committee is comprised of employees of ISE. Additional resources include direct contact with companies engaged in cyber security and industry associations supporting the cyber security industry. The Classification Committee will meet on a quarterly basis to discuss any proposed changes to the ISE Cyber Security Industry Classification. Ad hoc meetings may be convened at the discretion of the Classification Committee. Meetings will typically consist of discussion and review of the framework and company classifications to ensure that the ISE Cyber Security Industry Classification continues to reflect the then-current state of the cyber security industry. 6
7 Chapter 4. Contact For any questions regarding the policies and procedures outlined in this document or for information regarding data licensing opportunities, please contact the ISE ETF Ventures Group by mail at: ISE ETF Ventures 60 Broad Street New York, NY U.S.A. Or by at: 7
ISE CLOUD COMPUTING TM INDEX
 Index Methodology Guide ISE CLOUD COMPUTING TM INDEX Issue 1.3 Issue date: August 28, 2015 Produced by:, LLC 60 Broad Street, New York NY 10004 www.ise.com The information contained in this document is
Index Methodology Guide ISE CLOUD COMPUTING TM INDEX Issue 1.3 Issue date: August 28, 2015 Produced by:, LLC 60 Broad Street, New York NY 10004 www.ise.com The information contained in this document is
ISE CYBER SECURITY TM INDEX
 Index Methodology Guide ISE CYBER SECURITY TM INDEX Issue 2.0 Issue date: August 28, 2015 Produced by:, LLC 60 Broad Street, New York NY 10004 www.ise.com The information contained in this document is
Index Methodology Guide ISE CYBER SECURITY TM INDEX Issue 2.0 Issue date: August 28, 2015 Produced by:, LLC 60 Broad Street, New York NY 10004 www.ise.com The information contained in this document is
Achieving SOX Compliance with Masergy Security Professional Services
 Achieving SOX Compliance with Masergy Security Professional Services The Sarbanes-Oxley (SOX) Act, also known as the Public Company Accounting Reform and Investor Protection Act of 2002 (and commonly called
Achieving SOX Compliance with Masergy Security Professional Services The Sarbanes-Oxley (SOX) Act, also known as the Public Company Accounting Reform and Investor Protection Act of 2002 (and commonly called
NETWORK AND CERTIFICATE SYSTEM SECURITY REQUIREMENTS
 NETWORK AND CERTIFICATE SYSTEM SECURITY REQUIREMENTS Scope and Applicability: These Network and Certificate System Security Requirements (Requirements) apply to all publicly trusted Certification Authorities
NETWORK AND CERTIFICATE SYSTEM SECURITY REQUIREMENTS Scope and Applicability: These Network and Certificate System Security Requirements (Requirements) apply to all publicly trusted Certification Authorities
Unified Security Anywhere SOX COMPLIANCE ACHIEVING SOX COMPLIANCE WITH MASERGY SECURITY PROFESSIONAL SERVICES
 Unified Security Anywhere SOX COMPLIANCE ACHIEVING SOX COMPLIANCE WITH MASERGY SECURITY PROFESSIONAL SERVICES SOX COMPLIANCE Achieving SOX Compliance with Professional Services The Sarbanes-Oxley (SOX)
Unified Security Anywhere SOX COMPLIANCE ACHIEVING SOX COMPLIANCE WITH MASERGY SECURITY PROFESSIONAL SERVICES SOX COMPLIANCE Achieving SOX Compliance with Professional Services The Sarbanes-Oxley (SOX)
Dow Jones Composite All REIT Indices Methodology
 Dow Jones Composite All REIT Indices Methodology August 2013 S&P Dow Jones Indices: Index Methodology Table of Contents Introduction 3 Highlights and Index Family 3 Eligibility Criteria 4 Index Eligibility
Dow Jones Composite All REIT Indices Methodology August 2013 S&P Dow Jones Indices: Index Methodology Table of Contents Introduction 3 Highlights and Index Family 3 Eligibility Criteria 4 Index Eligibility
Larry Wilson Version 1.0 November, 2013. University Cyber-security Program Critical Asset Mapping
 Larry Wilson Version 1.0 November, 2013 University Cyber-security Program Critical Asset Mapping Part 3 - Cyber-Security Controls Mapping Cyber-security Controls mapped to Critical Asset Groups CSC Control
Larry Wilson Version 1.0 November, 2013 University Cyber-security Program Critical Asset Mapping Part 3 - Cyber-Security Controls Mapping Cyber-security Controls mapped to Critical Asset Groups CSC Control
Individuals can nominate their own work and multiple individuals within one organization can be nominated, albeit from discrete business units.
 The FCS Financial Marketer of the Year Award honors the financial services organization whose strategy and execution delivered proven, high-impact results. Now in its 10 th year, this award will celebrate
The FCS Financial Marketer of the Year Award honors the financial services organization whose strategy and execution delivered proven, high-impact results. Now in its 10 th year, this award will celebrate
74% 96 Action Items. Compliance
 Compliance Report PCI DSS 2.0 Generated by Check Point Compliance Blade, on July 02, 2013 11:12 AM 1 74% Compliance 96 Action Items Upcoming 0 items About PCI DSS 2.0 PCI-DSS is a legal obligation mandated
Compliance Report PCI DSS 2.0 Generated by Check Point Compliance Blade, on July 02, 2013 11:12 AM 1 74% Compliance 96 Action Items Upcoming 0 items About PCI DSS 2.0 PCI-DSS is a legal obligation mandated
The Return on Disability Company
 The Return on Disability Company RoD Canada Index Methodology July 2012 Table of contents Introduction Introduction 3 Eligibility Criteria Additions RoD Canada 50 4 Deletions RoD Canada 50 5 Timing of
The Return on Disability Company RoD Canada Index Methodology July 2012 Table of contents Introduction Introduction 3 Eligibility Criteria Additions RoD Canada 50 4 Deletions RoD Canada 50 5 Timing of
Technical Accounting Alert
 TA ALERT 2009-12 JULY 2009 Technical Accounting Alert Impairment of available-for-sale equity investments Issue This alert provides guidance on the application of IAS 39's impairment rules to investments
TA ALERT 2009-12 JULY 2009 Technical Accounting Alert Impairment of available-for-sale equity investments Issue This alert provides guidance on the application of IAS 39's impairment rules to investments
LONDON STOCK EXCHANGE HIGH GROWTH SEGMENT RULEBOOK 27 March 2013
 LONDON STOCK EXCHANGE HIGH GROWTH SEGMENT RULEBOOK 27 March 2013 Contents INTRODUCTION... 2 SECTION A ADMISSION... 3 A1: Eligibility for admission... 3 A2: Procedure for admission... 4 SECTION B CONTINUING
LONDON STOCK EXCHANGE HIGH GROWTH SEGMENT RULEBOOK 27 March 2013 Contents INTRODUCTION... 2 SECTION A ADMISSION... 3 A1: Eligibility for admission... 3 A2: Procedure for admission... 4 SECTION B CONTINUING
Indxx SuperDividend U.S. Low Volatility Index
 www.indxx.com Indxx SuperDividend U.S. Low Volatility Index Methodology May 2015 INDXX, LLC has been granted a license by Global X Management Company LLC to use SuperDividend. SuperDividend is a trademark
www.indxx.com Indxx SuperDividend U.S. Low Volatility Index Methodology May 2015 INDXX, LLC has been granted a license by Global X Management Company LLC to use SuperDividend. SuperDividend is a trademark
Looking at the SANS 20 Critical Security Controls
 Looking at the SANS 20 Critical Security Controls Mapping the SANS 20 to NIST 800-53 to ISO 27002 by Brad C. Johnson The SANS 20 Overview SANS has created the 20 Critical Security Controls as a way of
Looking at the SANS 20 Critical Security Controls Mapping the SANS 20 to NIST 800-53 to ISO 27002 by Brad C. Johnson The SANS 20 Overview SANS has created the 20 Critical Security Controls as a way of
Consensus Policy Resource Community. Lab Security Policy
 Lab Security Policy Free Use Disclaimer: This policy was created by or for the SANS Institute for the Internet community. All or parts of this policy can be freely used for your organization. There is
Lab Security Policy Free Use Disclaimer: This policy was created by or for the SANS Institute for the Internet community. All or parts of this policy can be freely used for your organization. There is
MSCI Global Investable Market Indices Methodology
 MSCI Global Investable Market Indices Methodology Index Construction Objectives, Guiding Principles and Methodology for the MSCI Global Investable Market Indices Contents Outline of the Methodology Book...
MSCI Global Investable Market Indices Methodology Index Construction Objectives, Guiding Principles and Methodology for the MSCI Global Investable Market Indices Contents Outline of the Methodology Book...
Complying with the Federal Information Security Management Act. Parallels with Sarbanes-Oxley Compliance
 WHITE paper Complying with the Federal Information Security Management Act How Tripwire Change Auditing Solutions Help page 2 page 3 page 3 page 3 page 4 page 4 page 5 page 5 page 6 page 6 page 7 Introduction
WHITE paper Complying with the Federal Information Security Management Act How Tripwire Change Auditing Solutions Help page 2 page 3 page 3 page 3 page 4 page 4 page 5 page 5 page 6 page 6 page 7 Introduction
INDEX METHODOLOGY MSCI REIT PREFERRED. Index Construction and Maintenance Methodology for the MSCI REIT Preferred Index.
 INDEX METHODOLOGY MSCI REIT PREFERRED INDEX METHODOLOGY Index Construction and Maintenance Methodology for the MSCI REIT Preferred Index December 2014 DECEMBER 2014 CONTENTS 1 Introduction... 3 2 Defining
INDEX METHODOLOGY MSCI REIT PREFERRED INDEX METHODOLOGY Index Construction and Maintenance Methodology for the MSCI REIT Preferred Index December 2014 DECEMBER 2014 CONTENTS 1 Introduction... 3 2 Defining
Ground Rules. FTSE/ATHEX Global Traders Index Series v1.5
 Ground Rules FTSE/ATHEX Global Traders Index Series v1.5 ftserussell.com November 2015 Contents 1.0 Introduction... 3 2.0 Management responsibilities... 5 3.0 Eligible securities... 7 4.0 Investability
Ground Rules FTSE/ATHEX Global Traders Index Series v1.5 ftserussell.com November 2015 Contents 1.0 Introduction... 3 2.0 Management responsibilities... 5 3.0 Eligible securities... 7 4.0 Investability
INVESTRAN DATA EXCHANGE
 INVESTRAN DATA EXCHANGE INVESTRAN DATA EXCHANGE AUTOMATING DATA CAPTURE AND REPORT DISTRIBUTION FOR ALTERNATIVE INVESTMENTS In today s alternative investment world, transparency of data is key, and the
INVESTRAN DATA EXCHANGE INVESTRAN DATA EXCHANGE AUTOMATING DATA CAPTURE AND REPORT DISTRIBUTION FOR ALTERNATIVE INVESTMENTS In today s alternative investment world, transparency of data is key, and the
Symphony Plus Cyber security for the power and water industries
 Symphony Plus Cyber security for the power and water industries Symphony Plus Cyber Security_3BUS095402_(Oct12)US Letter.indd 1 01/10/12 10:15 Symphony Plus Cyber security for the power and water industries
Symphony Plus Cyber security for the power and water industries Symphony Plus Cyber Security_3BUS095402_(Oct12)US Letter.indd 1 01/10/12 10:15 Symphony Plus Cyber security for the power and water industries
MSCI Global Investable Market Indices Methodology
 MSCI Global Investable Market Indices Methodology Index Construction Objectives, Guiding Principles and Methodology for the MSCI Global Investable Market Indices Contents Outline of the Methodology Book...
MSCI Global Investable Market Indices Methodology Index Construction Objectives, Guiding Principles and Methodology for the MSCI Global Investable Market Indices Contents Outline of the Methodology Book...
Summary Prospectus August 28, 2015, as revised September 21, 2015
 EXCHANGE TRADED CONCEPTS TRUST ROBO Global TM Robotics and Automation Index ETF Summary Prospectus August 28, 2015, as revised September 21, 2015 Principal Listing Exchange for the Fund: NASDAQ Stock Market
EXCHANGE TRADED CONCEPTS TRUST ROBO Global TM Robotics and Automation Index ETF Summary Prospectus August 28, 2015, as revised September 21, 2015 Principal Listing Exchange for the Fund: NASDAQ Stock Market
A host-based firewall can be used in addition to a network-based firewall to provide multiple layers of protection.
 A firewall is a software- or hardware-based network security system that allows or denies network traffic according to a set of rules. Firewalls can be categorized by their location on the network: A network-based
A firewall is a software- or hardware-based network security system that allows or denies network traffic according to a set of rules. Firewalls can be categorized by their location on the network: A network-based
STRATEGIC POLICY. Information Security Policy Documentation. Network Management Policy. 1. Introduction
 Policy: Title: Status: 1. Introduction ISP-S12 Network Management Policy Revised Information Security Policy Documentation STRATEGIC POLICY 1.1. This information security policy document covers management,
Policy: Title: Status: 1. Introduction ISP-S12 Network Management Policy Revised Information Security Policy Documentation STRATEGIC POLICY 1.1. This information security policy document covers management,
Harnessing Innovation and Growth Within Tech
 SPDR SPOTLIGHT Harnessing Innovation and Growth Within Tech by David B. Mazza, Head of ETF and Mutual Fund Research, Matthew Bartolini, CFA, Research Strategist, and Jared Rowley, CFA, Research Strategist,
SPDR SPOTLIGHT Harnessing Innovation and Growth Within Tech by David B. Mazza, Head of ETF and Mutual Fund Research, Matthew Bartolini, CFA, Research Strategist, and Jared Rowley, CFA, Research Strategist,
Network Architecture & Topology
 Network Architecture & Topology Coleman Kane Coleman.Kane@ge.com August 25, 2014 Cyber Defense Overview Network Architecture & Topology 1 / 12 For the sake of this course, we will focus on switched (or
Network Architecture & Topology Coleman Kane Coleman.Kane@ge.com August 25, 2014 Cyber Defense Overview Network Architecture & Topology 1 / 12 For the sake of this course, we will focus on switched (or
PureFunds ISE Cyber Security ETF (the Fund ) June 18, 2015. Supplement to the Summary Prospectus dated November 7, 2014
 PureFunds ISE Cyber Security ETF (the Fund ) June 18, 2015 Supplement to the Summary Prospectus dated November 7, 2014 Effective immediately, Ernesto Tong, CFA, Managing Director of Penserra Capital Management,
PureFunds ISE Cyber Security ETF (the Fund ) June 18, 2015 Supplement to the Summary Prospectus dated November 7, 2014 Effective immediately, Ernesto Tong, CFA, Managing Director of Penserra Capital Management,
EA-ISP-012-Network Management Policy
 Technology & Information Services EA-ISP-012-Network Management Policy Owner: Adrian Hollister Author: Paul Ferrier Date: 01/04/2015 Document Security Level: PUBLIC Document Version: 1.00 Document Ref:
Technology & Information Services EA-ISP-012-Network Management Policy Owner: Adrian Hollister Author: Paul Ferrier Date: 01/04/2015 Document Security Level: PUBLIC Document Version: 1.00 Document Ref:
Information Technology Policy
 Information Technology Policy Security Information and Event Management Policy ITP Number Effective Date ITP-SEC021 October 10, 2006 Category Supersedes Recommended Policy Contact Scheduled Review RA-ITCentral@pa.gov
Information Technology Policy Security Information and Event Management Policy ITP Number Effective Date ITP-SEC021 October 10, 2006 Category Supersedes Recommended Policy Contact Scheduled Review RA-ITCentral@pa.gov
RoD Canada 50 Tracking Index Methodology July 2014
 RoD Canada 50 Tracking Index Methodology July 2014 Table of contents Introduction Introduction 3 Eligibility Criteria Additions RoD Canada 50 4 Deletions RoD Canada 50 5 Timing of Changes 6 Index Construction
RoD Canada 50 Tracking Index Methodology July 2014 Table of contents Introduction Introduction 3 Eligibility Criteria Additions RoD Canada 50 4 Deletions RoD Canada 50 5 Timing of Changes 6 Index Construction
Guardian Digital Secure Mail Suite Quick Start Guide
 Guardian Digital Secure Mail Suite Quick Start Guide Copyright c 2004 Guardian Digital, Inc. Contents 1 Introduction 1 2 Contacting Guardian Digital 2 3 Purpose of This Document 3 3.1 Terminology...............................
Guardian Digital Secure Mail Suite Quick Start Guide Copyright c 2004 Guardian Digital, Inc. Contents 1 Introduction 1 2 Contacting Guardian Digital 2 3 Purpose of This Document 3 3.1 Terminology...............................
Company Co. Inc. LLC. LAN Domain Network Security Best Practices. An integrated approach to securing Company Co. Inc.
 Company Co. Inc. LLC Multiple Minds, Singular Results LAN Domain Network Security Best Practices An integrated approach to securing Company Co. Inc. LLC s network Written and Approved By: Geoff Lacy, Tim
Company Co. Inc. LLC Multiple Minds, Singular Results LAN Domain Network Security Best Practices An integrated approach to securing Company Co. Inc. LLC s network Written and Approved By: Geoff Lacy, Tim
INDEX RULE BOOK NYSE Diversified High Income Index
 INDEX RULE BOOK NYSE Diversified High Income Index Version 1-1 Effective from 31 July 2013 www.nyx.com/indices Index 1. INDEX SUMMARY... 1 2. GOVERNANCE AND DISCLAIMER... 3 2.1 INDICES... 3 2.2 INDEX GOVERNANCE...
INDEX RULE BOOK NYSE Diversified High Income Index Version 1-1 Effective from 31 July 2013 www.nyx.com/indices Index 1. INDEX SUMMARY... 1 2. GOVERNANCE AND DISCLAIMER... 3 2.1 INDICES... 3 2.2 INDEX GOVERNANCE...
TICSA. Telecommunications (Interception Capability and Security) Act 2013. Guidance for Network Operators. www.gcsb.govt.nz www.ncsc.govt.
 TICSA Telecommunications (Interception Capability and Security) Act 2013 Guidance for Network Operators www.gcsb.govt.nz www.ncsc.govt.nz Contents Introduction...2 Overview of the Guidance...3 Focus of
TICSA Telecommunications (Interception Capability and Security) Act 2013 Guidance for Network Operators www.gcsb.govt.nz www.ncsc.govt.nz Contents Introduction...2 Overview of the Guidance...3 Focus of
Enterprise Security Architecture
 Enterprise Architecture -driven security April 2012 Agenda Facilities and safety information Introduction Overview of the problem Introducing security architecture The SABSA approach A worked example architecture
Enterprise Architecture -driven security April 2012 Agenda Facilities and safety information Introduction Overview of the problem Introducing security architecture The SABSA approach A worked example architecture
Oracle Maps Cloud Service Enterprise Hosting and Delivery Policies Effective Date: October 1, 2015 Version 1.0
 Oracle Maps Cloud Service Enterprise Hosting and Delivery Policies Effective Date: October 1, 2015 Version 1.0 Unless otherwise stated, these Oracle Maps Cloud Service Enterprise Hosting and Delivery Policies
Oracle Maps Cloud Service Enterprise Hosting and Delivery Policies Effective Date: October 1, 2015 Version 1.0 Unless otherwise stated, these Oracle Maps Cloud Service Enterprise Hosting and Delivery Policies
How To Configure Forefront Threat Management Gateway (Forefront) For An Email Server
 Owner of the content within this article is www.isaserver.org Written by Marc Grote www.it-training-grote.de Configuring and using the E-Mail protection feature in Microsoft Forefront Threat Management
Owner of the content within this article is www.isaserver.org Written by Marc Grote www.it-training-grote.de Configuring and using the E-Mail protection feature in Microsoft Forefront Threat Management
INFORMATION TECHNOLOGY ENGINEER V
 1464 INFORMATION TECHNOLOGY ENGINEER V NATURE AND VARIETY OF WORK This is senior level lead administrative, professional and technical engineering work creating, implementing, and maintaining the County
1464 INFORMATION TECHNOLOGY ENGINEER V NATURE AND VARIETY OF WORK This is senior level lead administrative, professional and technical engineering work creating, implementing, and maintaining the County
MANAGED SECURITY SERVICES
 MANAGED SECURITY SERVICES Security first Safety first! Security is becoming increasingly important for companies, especially for the extension of networking to mission-critical environments, with new intranet
MANAGED SECURITY SERVICES Security first Safety first! Security is becoming increasingly important for companies, especially for the extension of networking to mission-critical environments, with new intranet
DISCLOSURE BROCHURE (FORM ADV, PART 2A) AMERIVEST INVESTMENT MANAGEMENT, LLC SEC File No. 801-55501. Main: 888-310-7921 Fax: 866-468-6268
 DISCLOSURE BROCHURE (FORM ADV, PART 2A) AMERIVEST INVESTMENT MANAGEMENT, LLC SEC File No. 801-55501 4211 S 102nd Street Omaha, NE 68127 Main: 888-310-7921 Fax: 866-468-6268 WWW.TDAMERITRADE.COM October
DISCLOSURE BROCHURE (FORM ADV, PART 2A) AMERIVEST INVESTMENT MANAGEMENT, LLC SEC File No. 801-55501 4211 S 102nd Street Omaha, NE 68127 Main: 888-310-7921 Fax: 866-468-6268 WWW.TDAMERITRADE.COM October
Online Lead Generation: Data Security Best Practices
 Online Lead Generation: Data Security Best Practices Released September 2009 The IAB Online Lead Generation Committee has developed these Best Practices. About the IAB Online Lead Generation Committee:
Online Lead Generation: Data Security Best Practices Released September 2009 The IAB Online Lead Generation Committee has developed these Best Practices. About the IAB Online Lead Generation Committee:
SECURING YOUR SMALL BUSINESS. Principles of information security and risk management
 SECURING YOUR SMALL BUSINESS Principles of information security and risk management The challenge Information is one of the most valuable assets of any organization public or private, large or small and
SECURING YOUR SMALL BUSINESS Principles of information security and risk management The challenge Information is one of the most valuable assets of any organization public or private, large or small and
How To Ensure The C.E.A.S.A
 APPENDI 3 TO SCHEDULE 3.3 TO THE COMPREHENSIVE INFRASTRUCTURE AGREEMENT APPENDI 3 TO SCHEDULE 3.3 TO THE COMPREHENSIVE INFRASTRUCTURE AGREEMENT TUGeneral TUSecurity TURequirements TUDesign TUIntegration
APPENDI 3 TO SCHEDULE 3.3 TO THE COMPREHENSIVE INFRASTRUCTURE AGREEMENT APPENDI 3 TO SCHEDULE 3.3 TO THE COMPREHENSIVE INFRASTRUCTURE AGREEMENT TUGeneral TUSecurity TURequirements TUDesign TUIntegration
BMO Global Asset Management (Asia) Limited 11 February 2016
 Product Key Facts BMO NASDAQ 100 ETF BMO Global Asset Management (Asia) Limited 11 February 2016 Quick facts This is an exchange traded fund. This statement provides you with key information about this
Product Key Facts BMO NASDAQ 100 ETF BMO Global Asset Management (Asia) Limited 11 February 2016 Quick facts This is an exchange traded fund. This statement provides you with key information about this
Compliance series Guide to meeting requirements of the UK Government Cyber Essentials Scheme
 Compliance series Guide to meeting requirements of the UK Government Cyber Essentials Scheme avecto.com Contents Introduction to the scheme 2 Boundary firewalls and internet gateways 3 Secure configuration
Compliance series Guide to meeting requirements of the UK Government Cyber Essentials Scheme avecto.com Contents Introduction to the scheme 2 Boundary firewalls and internet gateways 3 Secure configuration
Information Technology Branch Access Control Technical Standard
 Information Technology Branch Access Control Technical Standard Information Management, Administrative Directive A1461 Cyber Security Technical Standard # 5 November 20, 2014 Approved: Date: November 20,
Information Technology Branch Access Control Technical Standard Information Management, Administrative Directive A1461 Cyber Security Technical Standard # 5 November 20, 2014 Approved: Date: November 20,
Case 2:13-cv-01887-ES-JAD Document 282-2 Filed 12/09/15 Page 1 of 116 PageID: 4879. Appendix A
 Case 2:13-cv-01887-ES-JAD Document 282-2 Filed 12/09/15 Page 1 of 116 PageID: 4879 Appendix A Case 2:13-cv-01887-ES-JAD Document 282-2 Filed 12/09/15 Page 2 of 116 PageID: 4880 Payment Card Industry (PCI)
Case 2:13-cv-01887-ES-JAD Document 282-2 Filed 12/09/15 Page 1 of 116 PageID: 4879 Appendix A Case 2:13-cv-01887-ES-JAD Document 282-2 Filed 12/09/15 Page 2 of 116 PageID: 4880 Payment Card Industry (PCI)
IP Telephony Management
 IP Telephony Management How Cisco IT Manages Global IP Telephony A Cisco on Cisco Case Study: Inside Cisco IT 1 Overview Challenge Design, implement, and maintain a highly available, reliable, and resilient
IP Telephony Management How Cisco IT Manages Global IP Telephony A Cisco on Cisco Case Study: Inside Cisco IT 1 Overview Challenge Design, implement, and maintain a highly available, reliable, and resilient
A Practical Approach to Threat Modeling
 A Practical Approach to Threat Modeling Tom Olzak March 2006 Today s security management efforts are based on risk management principles. In other words, security resources are applied to vulnerabilities
A Practical Approach to Threat Modeling Tom Olzak March 2006 Today s security management efforts are based on risk management principles. In other words, security resources are applied to vulnerabilities
Your Guide to E*TRADE s Platinum Independent Advisor Platform
 1 Your Guide to E*TRADE s Platinum Independent Advisor Platform As an independent advisor, you can rely on E*TRADE s state-of-the-art, advisor-only system to help you better serve your clients, while making
1 Your Guide to E*TRADE s Platinum Independent Advisor Platform As an independent advisor, you can rely on E*TRADE s state-of-the-art, advisor-only system to help you better serve your clients, while making
Best Practices in ICS Security for System Operators. A Wurldtech White Paper
 Best Practices in ICS Security for System Operators A Wurldtech White Paper No part of this document may be distributed, reproduced or posted without the express written permission of Wurldtech Security
Best Practices in ICS Security for System Operators A Wurldtech White Paper No part of this document may be distributed, reproduced or posted without the express written permission of Wurldtech Security
Lecture 23: Firewalls
 Lecture 23: Firewalls Introduce several types of firewalls Discuss their advantages and disadvantages Compare their performances Demonstrate their applications C. Ding -- COMP581 -- L23 What is a Digital
Lecture 23: Firewalls Introduce several types of firewalls Discuss their advantages and disadvantages Compare their performances Demonstrate their applications C. Ding -- COMP581 -- L23 What is a Digital
TABLE OF CONTENTS. Section 5 IPv6... 5-1 5.1 Introduction... 5-1 5.2 Definitions... 5-1 5.3 DoD IPv6 Profile... 5-3 5.3.1 Product Requirements...
 , Table of Contents TABLE OF CONTENTS SECTION PAGE IPv6... 5-1 5.1 Introduction... 5-1 5.2 Definitions... 5-1 5.3 DoD IPv6 Profile... 5-3 5.3.1 Product Requirements... 5-4 i , List of Figures LIST OF FIGURES
, Table of Contents TABLE OF CONTENTS SECTION PAGE IPv6... 5-1 5.1 Introduction... 5-1 5.2 Definitions... 5-1 5.3 DoD IPv6 Profile... 5-3 5.3.1 Product Requirements... 5-4 i , List of Figures LIST OF FIGURES
Continuous Disclosure and Market Communication Policy
 Continuous Disclosure and Market Communication Policy 1. CONTINUOUS DISCLOSURE 1.1 Principle In accordance with legislative and regulatory requirements, we will immediately disclose information if either:
Continuous Disclosure and Market Communication Policy 1. CONTINUOUS DISCLOSURE 1.1 Principle In accordance with legislative and regulatory requirements, we will immediately disclose information if either:
PCN Cyber-security Considerations for Manufacturers. Based on Chevron Phillips Chemical Company PCN Architecture Design and Philosophy
 PCN Cyber-security Considerations for Manufacturers Based on Chevron Phillips Chemical Company PCN Architecture Design and Philosophy Contents CPChem PCN Philosophy and Policy Remote Access Considerations
PCN Cyber-security Considerations for Manufacturers Based on Chevron Phillips Chemical Company PCN Architecture Design and Philosophy Contents CPChem PCN Philosophy and Policy Remote Access Considerations
Anthony J. Albanese, Acting Superintendent of Financial Services. Financial and Banking Information Infrastructure Committee (FBIIC) Members:
 Andrew M. Cuomo Governor Anthony J. Albanese Acting Superintendent FROM: TO: Anthony J. Albanese, Acting Superintendent of Financial Services Financial and Banking Information Infrastructure Committee
Andrew M. Cuomo Governor Anthony J. Albanese Acting Superintendent FROM: TO: Anthony J. Albanese, Acting Superintendent of Financial Services Financial and Banking Information Infrastructure Committee
Supplier Security Assessment Questionnaire
 HALKYN CONSULTING LTD Supplier Security Assessment Questionnaire Security Self-Assessment and Reporting This questionnaire is provided to assist organisations in conducting supplier security assessments.
HALKYN CONSULTING LTD Supplier Security Assessment Questionnaire Security Self-Assessment and Reporting This questionnaire is provided to assist organisations in conducting supplier security assessments.
Information Technology Cyber Security Policy
 Information Technology Cyber Security Policy (Insert Name of Organization) SAMPLE TEMPLATE Organizations are encouraged to develop their own policy and procedures from the information enclosed. Please
Information Technology Cyber Security Policy (Insert Name of Organization) SAMPLE TEMPLATE Organizations are encouraged to develop their own policy and procedures from the information enclosed. Please
Privacy Policy EMA Online
 Privacy Policy EMA Online Thank you for visiting our Privacy Policy. We are committed to respecting the privacy rights of the users of www.emaonline.com ( Website ). We created this privacy policy (the
Privacy Policy EMA Online Thank you for visiting our Privacy Policy. We are committed to respecting the privacy rights of the users of www.emaonline.com ( Website ). We created this privacy policy (the
UNCLASSIFIED (U) U.S. Department of State Foreign Affairs Manual Volume 5 Information Management 5 FAM 870 NETWORKS
 5 FAM 870 NETWORKS (Office of Origin: IRM/BMP/GRP/GP) 5 FAM 871 ENTERPRISE NETWORKS (CT:IM-138; 01-18-2013) The Department currently has two enterprise networks: ClassNet and OpenNet. Only Department-issued
5 FAM 870 NETWORKS (Office of Origin: IRM/BMP/GRP/GP) 5 FAM 871 ENTERPRISE NETWORKS (CT:IM-138; 01-18-2013) The Department currently has two enterprise networks: ClassNet and OpenNet. Only Department-issued
Computer Networking. Definitions. Introduction
 Computer Networking Definitions DHCP Dynamic Host Configuration Protocol It assigns IP addresses to client devices, such as desktop computers, laptops, and phones, when they are plugged into Ethernet or
Computer Networking Definitions DHCP Dynamic Host Configuration Protocol It assigns IP addresses to client devices, such as desktop computers, laptops, and phones, when they are plugged into Ethernet or
Computer and Network Security Policy
 Coffeyville Community College Computer and Network Security Policy Created By: Jeremy Robertson Network Administrator Created on: 6/15/2012 Computer and Network Security Page 1 Introduction: The Coffeyville
Coffeyville Community College Computer and Network Security Policy Created By: Jeremy Robertson Network Administrator Created on: 6/15/2012 Computer and Network Security Page 1 Introduction: The Coffeyville
An Overview of Information Security Frameworks. Presented to TIF September 25, 2013
 An Overview of Information Security Frameworks Presented to TIF September 25, 2013 What is a framework? A framework helps define an approach to implementing, maintaining, monitoring, and improving information
An Overview of Information Security Frameworks Presented to TIF September 25, 2013 What is a framework? A framework helps define an approach to implementing, maintaining, monitoring, and improving information
BEFORE THE BOARD OF COUNTY COMMISSIONERS FOR MULTNOMAH COUNTY, OREGON RESOLUTION NO. 05-050
 BEFORE THE BOARD OF COUNTY COMMISSIONERS FOR MULTNOMAH COUNTY, OREGON RESOLUTION NO. 05-050 Adopting Multnomah County HIPAA Security Policies and Directing the Appointment of Information System Security
BEFORE THE BOARD OF COUNTY COMMISSIONERS FOR MULTNOMAH COUNTY, OREGON RESOLUTION NO. 05-050 Adopting Multnomah County HIPAA Security Policies and Directing the Appointment of Information System Security
The Protection Mission a constant endeavor
 a constant endeavor The IT Protection Mission a constant endeavor As businesses become more and more dependent on IT, IT must face a higher bar for preparedness Cyber preparedness is the process of ensuring
a constant endeavor The IT Protection Mission a constant endeavor As businesses become more and more dependent on IT, IT must face a higher bar for preparedness Cyber preparedness is the process of ensuring
SUPPLIER SECURITY STANDARD
 SUPPLIER SECURITY STANDARD OWNER: LEVEL 3 COMMUNICATIONS AUTHOR: LEVEL 3 GLOBAL SECURITY AUTHORIZER: DALE DREW, CSO CURRENT RELEASE: 12/09/2014 Purpose: The purpose of this Level 3 Supplier Security Standard
SUPPLIER SECURITY STANDARD OWNER: LEVEL 3 COMMUNICATIONS AUTHOR: LEVEL 3 GLOBAL SECURITY AUTHORIZER: DALE DREW, CSO CURRENT RELEASE: 12/09/2014 Purpose: The purpose of this Level 3 Supplier Security Standard
TEAL: Transparent Email Archiving Library
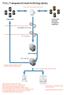 TEAL: Transparent Email Archiving Library 1. Users send & receive email as per normal 2. Existing customer filters remove spam & viruses Filters (Spam, Anti-Virus) 3. Interceptor agent takes a copy of
TEAL: Transparent Email Archiving Library 1. Users send & receive email as per normal 2. Existing customer filters remove spam & viruses Filters (Spam, Anti-Virus) 3. Interceptor agent takes a copy of
Cyber security. ETFS ISE Cyber Security GO UCITS ETF. Investing in a safer digital future
 Cyber security Investing in a safer digital future About the index The ISE Cyber Security UCITS Index Net Total Return utilises a rules-based investment methodology to select a diverse group of companies
Cyber security Investing in a safer digital future About the index The ISE Cyber Security UCITS Index Net Total Return utilises a rules-based investment methodology to select a diverse group of companies
WildFire Reporting. WildFire Administrator s Guide 55. Copyright 2007-2015 Palo Alto Networks
 WildFire Reporting When malware is discovered on your network, it is important to take quick action to prevent spread of the malware to other systems. To ensure immediate alerts to malware discovered on
WildFire Reporting When malware is discovered on your network, it is important to take quick action to prevent spread of the malware to other systems. To ensure immediate alerts to malware discovered on
How a Company s IT Systems Can Be Breached Despite Strict Security Protocols
 How a Company s IT Systems Can Be Breached Despite Strict Security Protocols Brian D. Huntley, CISSP, PMP, CBCP, CISA Senior Information Security Advisor Information Security Officer, IDT911 Overview Good
How a Company s IT Systems Can Be Breached Despite Strict Security Protocols Brian D. Huntley, CISSP, PMP, CBCP, CISA Senior Information Security Advisor Information Security Officer, IDT911 Overview Good
Virtual LAN Configuration Guide Version 9
 Virtual LAN Configuration Guide Version 9 Document version 96-1.0-12/05/2009 2 IMPORTANT NOTICE Elitecore has supplied this Information believing it to be accurate and reliable at the time of printing,
Virtual LAN Configuration Guide Version 9 Document version 96-1.0-12/05/2009 2 IMPORTANT NOTICE Elitecore has supplied this Information believing it to be accurate and reliable at the time of printing,
THE U.S. INFRASTRUCTURE EFFECT INTERVIEW BY CAROL CAMERON
 This interview originally appeared in the Summer 24 edition of InSIGHTS, a quarterly publication from S&P Dow Jones Indices. THE U.S. INFRASTRUCTURE EFFECT INTERVIEW BY CAROL CAMERON Every four years,
This interview originally appeared in the Summer 24 edition of InSIGHTS, a quarterly publication from S&P Dow Jones Indices. THE U.S. INFRASTRUCTURE EFFECT INTERVIEW BY CAROL CAMERON Every four years,
Borderless Services Node (BSN) Delivers Integrated Wired, Wireless Policies
 Q&A with... Borderless Services Node (BSN) Delivers Integrated Wired, Wireless Policies Cisco is bundling several modular components into a package for the company s Catalyst 6500 switching platform that
Q&A with... Borderless Services Node (BSN) Delivers Integrated Wired, Wireless Policies Cisco is bundling several modular components into a package for the company s Catalyst 6500 switching platform that
Physical Protection Policy Sample (Required Written Policy)
 Physical Protection Policy Sample (Required Written Policy) 1.0 Purpose: The purpose of this policy is to provide guidance for agency personnel, support personnel, and private contractors/vendors for the
Physical Protection Policy Sample (Required Written Policy) 1.0 Purpose: The purpose of this policy is to provide guidance for agency personnel, support personnel, and private contractors/vendors for the
Logical Operations CyberSec First Responder: Threat Detection and Response (CFR) Exam CFR-110
 Logical Operations CyberSec First Responder: Threat Detection and Response (CFR) Exam CFR-110 Exam Information Candidate Eligibility: The CyberSec First Responder: Threat Detection and Response (CFR) exam
Logical Operations CyberSec First Responder: Threat Detection and Response (CFR) Exam CFR-110 Exam Information Candidate Eligibility: The CyberSec First Responder: Threat Detection and Response (CFR) exam
Security Controls What Works. Southside Virginia Community College: Security Awareness
 Security Controls What Works Southside Virginia Community College: Security Awareness Session Overview Identification of Information Security Drivers Identification of Regulations and Acts Introduction
Security Controls What Works Southside Virginia Community College: Security Awareness Session Overview Identification of Information Security Drivers Identification of Regulations and Acts Introduction
Routing Security Server failure detection and recovery Protocol support Redundancy
 Cisco IOS SLB and Exchange Director Server Load Balancing for Cisco Mobile SEF The Cisco IOS SLB and Exchange Director software features provide a rich set of server load balancing (SLB) functions supporting
Cisco IOS SLB and Exchange Director Server Load Balancing for Cisco Mobile SEF The Cisco IOS SLB and Exchange Director software features provide a rich set of server load balancing (SLB) functions supporting
VMware vcloud Air. Enterprise IT Hybrid Data Center TECHNICAL MARKETING DOCUMENTATION
 TECHNICAL MARKETING DOCUMENTATION October 2014 Table of Contents Purpose and Overview.... 3 1.1 Background............................................................... 3 1.2 Target Audience...........................................................
TECHNICAL MARKETING DOCUMENTATION October 2014 Table of Contents Purpose and Overview.... 3 1.1 Background............................................................... 3 1.2 Target Audience...........................................................
Defined contribution workplace pensions: The audit of charges and benefits in legacy schemes
 Defined contribution workplace pensions: The audit of charges and benefits in legacy schemes A PROGRESS UPDATE FROM THE INDEPENDENT PROJECT BOARD July 2014 July 2014 i The audit of charges and benefits
Defined contribution workplace pensions: The audit of charges and benefits in legacy schemes A PROGRESS UPDATE FROM THE INDEPENDENT PROJECT BOARD July 2014 July 2014 i The audit of charges and benefits
APPENDIX 3 TO SCHEDULE 3.3 SECURITY SERVICES SOW
 EHIBIT H to Amendment No. 60 APPENDI 3 TO SCHEDULE 3.3 TO THE COMPREHENSIVE INFRASTRUCTURE AGREEMENT SECURITY SERVICES SOW EHIBIT H to Amendment No. 60 Table of Contents 1.0 Security Services Overview
EHIBIT H to Amendment No. 60 APPENDI 3 TO SCHEDULE 3.3 TO THE COMPREHENSIVE INFRASTRUCTURE AGREEMENT SECURITY SERVICES SOW EHIBIT H to Amendment No. 60 Table of Contents 1.0 Security Services Overview
Investment Objective
 BlueStar TA-BIGITech Israel Technology ETF Trading Symbol: ITEQ Listed on NASDAQ Summary Prospectus October 21, 2015 www.iteqetf.com Before you invest, you may want to review the BlueStar TA-BIGITech Israel
BlueStar TA-BIGITech Israel Technology ETF Trading Symbol: ITEQ Listed on NASDAQ Summary Prospectus October 21, 2015 www.iteqetf.com Before you invest, you may want to review the BlueStar TA-BIGITech Israel
How To Protect Your Data From Being Stolen
 DATA SECURITY & PCI DSS COMPLIANCE PROTECTING CUSTOMER DATA WHAT IS PCI DSS? PAYMENT CARD INDUSTRY DATA SECURITY STANDARD A SET OF REQUIREMENTS FOR ANY ORGANIZATION OR MERCHANT THAT ACCEPTS, TRANSMITS
DATA SECURITY & PCI DSS COMPLIANCE PROTECTING CUSTOMER DATA WHAT IS PCI DSS? PAYMENT CARD INDUSTRY DATA SECURITY STANDARD A SET OF REQUIREMENTS FOR ANY ORGANIZATION OR MERCHANT THAT ACCEPTS, TRANSMITS
This is a preview - click here to buy the full publication
 TECHNICAL REPORT IEC/TR 62443-3-1 Edition 1.0 2009-07 colour inside Industrial communication networks Network and system security Part 3 1: Security technologies for industrial automation and control systems
TECHNICAL REPORT IEC/TR 62443-3-1 Edition 1.0 2009-07 colour inside Industrial communication networks Network and system security Part 3 1: Security technologies for industrial automation and control systems
Rule 4-004M Payment Card Industry (PCI) Monitoring, Logging and Audit (proposed)
 Version: Modified By: Date: Approved By: Date: 1.0 Michael Hawkins October 29, 2013 Dan Bowden November 2013 Rule 4-004M Payment Card Industry (PCI) Monitoring, Logging and Audit (proposed) 01.1 Purpose
Version: Modified By: Date: Approved By: Date: 1.0 Michael Hawkins October 29, 2013 Dan Bowden November 2013 Rule 4-004M Payment Card Industry (PCI) Monitoring, Logging and Audit (proposed) 01.1 Purpose
Securing Virtualization with Check Point and Consolidation with Virtualized Security
 Securing Virtualization with Check Point and Consolidation with Virtualized Security consolidate security gateways with full power of Software Blades with Check Point Virtual Systems (VSX) secure virtualized
Securing Virtualization with Check Point and Consolidation with Virtualized Security consolidate security gateways with full power of Software Blades with Check Point Virtual Systems (VSX) secure virtualized
db x-trackers MSCI World Telecom Services Index UCITS ETF (Prospective DR) 1 Supplement to the Prospectus
 db x-trackers MSCI World Telecom Services Index UCITS ETF (Prospective DR) 1 Supplement to the Prospectus This Supplement contains information in relation to the db x-trackers MSCI World Telecom Services
db x-trackers MSCI World Telecom Services Index UCITS ETF (Prospective DR) 1 Supplement to the Prospectus This Supplement contains information in relation to the db x-trackers MSCI World Telecom Services
Nuclear Plant Information Security A Management Overview
 Nuclear Plant Information Security A Management Overview The diagram above is a typical (simplified) Infosec Architecture Model for a nuclear power plant. The fully-developed model would, for example,
Nuclear Plant Information Security A Management Overview The diagram above is a typical (simplified) Infosec Architecture Model for a nuclear power plant. The fully-developed model would, for example,
BME CLEARING s Business Continuity Policy
 BME CLEARING s Business Continuity Policy Contents 1. Introduction 1 2. General goals of the Continuity Policy 1 3. Scope of BME CLEARING s Business Continuity Policy 1 4. Recovery strategies 2 5. Distribution
BME CLEARING s Business Continuity Policy Contents 1. Introduction 1 2. General goals of the Continuity Policy 1 3. Scope of BME CLEARING s Business Continuity Policy 1 4. Recovery strategies 2 5. Distribution
Pricelist Template Form
 SSB-DAM-V25-FAM-1001U-2SL0 Hardware Business Security Bundle, V2500 Database each Imperva SSB-DAM-V25-FAM-1001U-2SL0 1001 Users, 2-Year Standard SSB-DAM-V25-FAM-1001U-2SL1 Hardware Business Security Bundle,
SSB-DAM-V25-FAM-1001U-2SL0 Hardware Business Security Bundle, V2500 Database each Imperva SSB-DAM-V25-FAM-1001U-2SL0 1001 Users, 2-Year Standard SSB-DAM-V25-FAM-1001U-2SL1 Hardware Business Security Bundle,
HP ProtectTools Email Release Manager
 HP ProtectTools Email Release Manager White Paper Introduction... 2 User Interface... 3 Configuration... 3 Message Properties... 3 Message Classification Prompt... 3 Labels... 5 Destinations... 5 Users...
HP ProtectTools Email Release Manager White Paper Introduction... 2 User Interface... 3 Configuration... 3 Message Properties... 3 Message Classification Prompt... 3 Labels... 5 Destinations... 5 Users...
Payment Card Industry (PCI) Data Security Standard. Summary of Changes from PCI DSS Version 2.0 to 3.0
 Payment Card Industry (PCI) Data Security Standard Summary of s from Version 2.0 to 3.0 November 2013 Introduction This document provides a summary of changes from v2.0 to v3.0. Table 1 provides an overview
Payment Card Industry (PCI) Data Security Standard Summary of s from Version 2.0 to 3.0 November 2013 Introduction This document provides a summary of changes from v2.0 to v3.0. Table 1 provides an overview
Chapter 15: Advanced Networks
 Chapter 15: Advanced Networks IT Essentials: PC Hardware and Software v4.0 1 Determine a Network Topology A site survey is a physical inspection of the building that will help determine a basic logical
Chapter 15: Advanced Networks IT Essentials: PC Hardware and Software v4.0 1 Determine a Network Topology A site survey is a physical inspection of the building that will help determine a basic logical
Business resilience: The best defense is a good offense
 IBM Business Continuity and Resiliency Services January 2009 Business resilience: The best defense is a good offense Develop a best practices strategy using a tiered approach Page 2 Contents 2 Introduction
IBM Business Continuity and Resiliency Services January 2009 Business resilience: The best defense is a good offense Develop a best practices strategy using a tiered approach Page 2 Contents 2 Introduction
E-Commerce Security Perimeter (ESP) Identification and Access Control Process
 Electronic Security Perimeter (ESP) Identification and Access Control Process 1. Introduction. A. This document outlines a multi-step process for identifying and protecting ESPs pursuant to the North American
Electronic Security Perimeter (ESP) Identification and Access Control Process 1. Introduction. A. This document outlines a multi-step process for identifying and protecting ESPs pursuant to the North American
Network Services Internet VPN
 Contents 1. 2. Network Services Customer Responsibilities 3. Network Services General 4. Service Management Boundary 5. Defined Terms Network Services Where the Customer selects as detailed in the Order
Contents 1. 2. Network Services Customer Responsibilities 3. Network Services General 4. Service Management Boundary 5. Defined Terms Network Services Where the Customer selects as detailed in the Order
Continuous compliance through good governance
 PCI DSS Compliance: A step into the payment ecosystem and Nets compliance program Continuous compliance through good governance Who are the PCI SSC? The Payment Card Industry Security Standard Council
PCI DSS Compliance: A step into the payment ecosystem and Nets compliance program Continuous compliance through good governance Who are the PCI SSC? The Payment Card Industry Security Standard Council
Information Technology Security Guideline. Network Security Zoning
 Information Technology Security Guideline Network Security Zoning Design Considerations for Placement of s within Zones ITSG-38 This page intentionally left blank. Foreword The Network Security Zoning
Information Technology Security Guideline Network Security Zoning Design Considerations for Placement of s within Zones ITSG-38 This page intentionally left blank. Foreword The Network Security Zoning
Document process management solutions for MiFID compliance
 Adobe Technical White Paper produced in conjunction with Equiduct Document process management solutions for MiFID compliance Adobe technology provides document process management solutions, enabling investment
Adobe Technical White Paper produced in conjunction with Equiduct Document process management solutions for MiFID compliance Adobe technology provides document process management solutions, enabling investment
can you simplify your infrastructure?
 SOLUTION BRIEF CA Virtual Desktop Automation for Vblock Platforms can you simplify your infrastructure? agility made possible You Can. With services that increase the speed of virtual provisioning on Vblock
SOLUTION BRIEF CA Virtual Desktop Automation for Vblock Platforms can you simplify your infrastructure? agility made possible You Can. With services that increase the speed of virtual provisioning on Vblock
