Distributed Proxy Server Management: A Self-Organized Approach
|
|
|
- Louise Mitchell
- 8 years ago
- Views:
Transcription
1 Distributed Proxy Server Management: A Self-Organized Approach K.C. Tsui (tsuikc@comp.hkbu.edu.hk) Department of Computer Science, Hong Kong Baptist University, Kowloon Tong, Kowloon, Hong Kong M.J. Kaiser (mjk@gmx.it) Department of Computer Science and Engineering, University of Connecticut, Storrs, CT , USA J. Liu (jiming@comp.hkbu.edu.hk) Department of Computer Science, Hong Kong Baptist University, Kowloon Tong, Kowloon, Hong Kong Abstract. Proxy servers are common solutions to relieve organizational networks from heavy traffic by storing the most frequently referenced web objects in their local cache. These proxies are commonly known as cooperative proxy systems and are usually organized in such a way as to optimize the utilization of their storage capacity. A self-organized approach to manage a distributed proxy system called Adaptive Distributed Caching (ADC) is proposed. We model each proxy as an autonomous agent that is equipped to decide how to deal with client requests using local information. Experimental results show that our ADC algorithm is able to compete with typical hashing-based approaches. This paper gives a full description of the self-organizing distributed algorithm, with a performance comparison based on hit rate and hop count. Additional evaluation of the performance with respect to the request routing table size is also presented. Keywords: autonomy oriented computation, self-organization, adaptive proxy server 1. Introduction The Internet is growing exponentially and web caches have been shown to be a feasible way to reduce the overall network traffic [3, 6, 18]. Web servers store web objects, which are requested by clients spread over the global network. A web cache, or proxy, is usually placed between clients making requests and web servers servicing the requests. It will try to resolve the needed object by its local cache. The Internet traffic is expected to reduce and the response to user request is expected to improve [1, 11]. Proxies that are not able to resolve an incoming request have to make a choice between either forwarding the request directly to the origin server or query a neighboring proxy. The idea that a proxy can forward requests to another peer leads to research in cooperative proxies and distributed proxy systems [8, 33]. Distributed proxy systems are based c 2003 Kluwer Academic Publishers. Printed in the Netherlands. so-adc.tex; 30/04/2003; 16:44; p.1
2 2 TSUI ET AL. on a set of proxies that when combined increase the overall storage space (cache) and, therefore, increase the chance of fulfilling incoming requests. Cooperative proxies try to combine their individual caches in such a way that maximum cache-usage is achieved while acting transparently as one single load-balanced proxy cache [10]. They lead to overhead problems like inter-proxy communication and the distribution of object storage location information. Previous research on cooperative proxies can be found in hierarchical [33] and hashing approaches [20, 29], adaptive web caching [37], CacheMesh [34], WebWave [15] and the straightforward approach with a central coordinator [25]. Additional research for distributed systems covers areas on consistency between multiple proxies [14], the theoretical description of the underlying processes [21, 35] and attempts to build the system on the idea of economical models [31]. Issues such as performance [28, 30] and effectiveness of replication schemes [23] were also studied and different schemes for the internal representation of URL lists have been analyzed [13, 24]. Research in distributed caching can also be found in distributed object replication schemes [32], resource allocation [9] and server load balancing [36]. Another way to relieve network congestion is to install an reverse proxy at the origin server end [5, 7]. This will speed up server response while balancing the load between multiple servers that might be mirrors of the main server. Various approaches have been suggested [4]. The advantage of this approach is transparency to user, no matter the server is located locally or distributed across the Internet. However, this solution does not bring the web objects closer to the clients. The load balancing problem can be tackled in many different ways. A knowledge-intensive approach relies heavily on the experience of network designers who understands the network traffic behavior and try to configure the proxy servers appropriately. This is an unreliable approach as the network traffic can be unpredictable. A slightly automated approach is to define certain heuristics in, say, an expert system that can react to the changes. This approach takes the human out of the loop but still suffers the same adaptability problem. A highly adaptive solution is needed that can react quickly to the change in traffic behavior, such as sudden burst of requests or break down of certain part of the Internet. It should also be able to learn the different modes of operation online so that the system does not need to be taken offline. The successful discovery of such an adaptive system will allow organizations to deliver better quality of service to local users. The same so-adc.tex; 30/04/2003; 16:44; p.2
3 DISTRIBUTED PROXY SERVER MANAGEMENT 3 benefit also applies to subscribers of Internet service providers if such an adaptive load balancing strategy is adopted. The proposed method emphasize the self-organization of autonomous proxy servers. The basic idea is to allow the elements of a system to make decisions based on some simple local behavior model that only need limited information about the system a notion central to the computational paradigm known as autonomy oriented computation [22]. Unlike common hashing algorithms, routing of requests are not pre-defined. In this sense, central control unit is absent in the proposed methods. Moreover, proxy systems using the proposed methods do not require any prior knowledge about any hardware differences between the proxy server, nor do they need to know in advance the client traffic pattern. This article will first describe some work related to proxy servers. Details of the Adaptive Distributed Caching (ADC) algorithm will then be described together with experimental results on their performance. The article concludes with discussions on some interesting observations and future research directions. 2. Related Work Proxy servers help to lower the demand on bandwidth and improve request turnaround time by storing up the frequently referenced web objects in their local cache. However, the cache still has a physical capacity limit and objects in the cache need to be replaced so as to make room for the new object that need to be stored in the cache. Commonly used strategy is least recently used (LRU) where the oldest object in the cache is replaced first. There are a lot of work on improving this base strategy. Existing cooperative proxy systems can be organized in hierarchical and distributed manners [12, 26]. The hierarchical approach is based on the Internet Caching Protocol (ICP) with a fixed hierarchy. A page not in the local cache of a proxy server is first requested from neighboring proxies on the same hierarchy level. Root proxy in the hierarchy will be queried if requests are not resolved locally and they continue to climb the hierarchy until the request objects are found. This often lead to a bottleneck situation at the main root server. The distributed approach is usually based on a hashing algorithm like the Cache Array Routing Protocol (CARP) [10]. Each requested page is mapped to exactly one proxy in the proxy array in a hashing system and will either be resolved by the local cache or requested from the origin server. Hashing-based allocations can be widely seen so-adc.tex; 30/04/2003; 16:44; p.3
4 4 TSUI ET AL. as the ideal way to find cached web pages, due to the fact that their location is pre-defined. Their major drawback is inflexibility and poor adaptability. Adaptive Web Caching [37] and CacheMesh [34] try to overcome specific performance bottlenecks. For example, Adaptive Web Caching dynamically creates proxy groups combined with data multicasting, while CacheMesh computes the routing protocol based on exchanged routing information. Both approaches can still be considered experimental. Yet other approaches like pre-fetching, reverse proxies and active proxies can usually be seen as further improvements to speed up the performance of a general hierarchical or distributed infrastructure and go hand in hand with our proposed self-organizing approach. See [16] for a more detailed discussion on the limitations of the pre-fetching approach. Others have work on structuring the proxy servers so as to improve the chance of locating the required object in one of the proxy servers. Common technique is to arrange a host of proxy servers in a hierarchical manner so that some proxy server, not necessarily on the same local area network, is the proxy of many other proxy servers while serving as the proxy of some local users [27]. This approach shortens the distance between the web server and the user who requests the object. However, some work has to be done on the design of the proxy hierarchy. Wu and Yu [36] have done some work on load balancing at the client side using proxy servers. They emphasized on tuning the commonly used hashing algorithm for load distribution. Researchers from MIT, on the other hand, have proposed a new hashing algorithm called consistent hashing to improve caching performance when resources are added from time to time [20]. 3. Adaptive Distributed Caching In this section, we will introduce the core components of the adaptive distributed caching (ADC) algorithm. In essence, the algorithm combines the advantages of hierarchical distributed caching (allowing multiple copies of the same object) and of hashing based distributed caching. ADC was developed out of the ideas behind the hashing based allocation and during our research we redefined specific components to reach the desired emergent behaviors. In short, our proxies maintain minimal number of duplicate copies of the frequently requested objects to balance the user request load between the cooperative proxies. ADC allows the distributed proxies so-adc.tex; 30/04/2003; 16:44; p.4
5 DISTRIBUTED PROXY SERVER MANAGEMENT 5 Figure 1. Different ways to deal with a client request where a cache miss occurs at the first point of inception by CARP and ADC to agree on the specific location of one object without the need for a central coordinator or a broadcasting protocol. All proxies in the widely used CARP algorithm use the same hashing algorithm to find out which proxy is responsible for a particular request based on the URL of the needed object [10]. If a proxy that first encountered the request (p 1 in Figure 1a) is responsible for the object, it will fulfill the request either from its cache or fetch the object the server. Otherwise, it will forward the request to another proxy (p 2 in Figure 1b), which will act like p 1 except forwarding a reqest. The benefits of CARP are efficient request handling and no redundant data. However, it is susceptible to data loss due to infrastructure change in the proxy system, and potential uneven distribution of load due to exceptional high demand on certain sites. The ADC proxies do not have a pre-defined request routing function and try to learn the routing table (mapping tables) by observing the experienced traffic. Any proxy that cannot fulfill the incoming request (p 1 in Figure 1b) will forward the request to another proxy, which in turn may continue to forward the request until a proxy (p n )eitherhas the requested objects in its cache or decides to fetch the objects from the origin server. The requested object will then travel in reverse direction along the path that the request has originally traversed and each proxy on the path will decide whether to cache the object (selective caching). Therefore, it is likely that there are duplicate copies of the web object. The following subsections will first describe the mapping tables that is used as request routing tables and index to the cache content. Details of the core functions of ADC, namely, request forwarding, backtracking, and selective caching, will be then given. so-adc.tex; 30/04/2003; 16:44; p.5
6 6 TSUI ET AL. Table Ia. A sample single-table OBJ-ID PROXY LAST AVG HITS [5] [4] [1] [2] [1] Mapping Tables The mapping table is a local data structure within a proxy that is used to resolve the object location by the forwarding process (see section 3.2). In a more abstract sense we see the mapping table as a direct replacement of the static hashing function used in hashing approaches to map object IDs (URLs) onto a unique location. It is the main objective of our algorithm to allow all existing mapping tables to agree on a unique location for each object without a broadcasting protocol or central coordinator. In our first attempt of the algorithm allowed the table to grow infinitely, keeping track of all previously experienced objects, which usually leads to out of memory problems and performance issues [17]. In our latest extension we introduced a way to limit the mapping table while still keeping the performance at the previously attained level [18] Single-Table The single-table is used to simply keep track of the current flow of requests. Each unknown object will become a new entry on the top of the table, displacing the oldest entry at the bottom of the table - the well-known LRU algorithm. It is a requirement of the single-table that it is large enough so that requests with at least two hits can occur. Table Ia shows a simple example of a single-mapping table. The first column contains the general object ID - object URLs in our case. The second column contains the current assigned location for the specific object. This information is local and might vary between different proxies. Objects for which a particular proxy is responsible will have the value THIS in this column of its single-table. The third column takes a marker, which stores the time when this object was last requested. The fourth column keeps track of the average time between two requests of this object and the last column simply keeps track of the number of times a specific object has been requested. so-adc.tex; 30/04/2003; 16:44; p.6
7 DISTRIBUTED PROXY SERVER MANAGEMENT 7 Table Ib. A sample multiple-table OBJ-ID PROXY LAST AVG HITS [8] THIS [1] THIS [4] Table Ic. A sample cache-table OBJ-ID PROXY LAST AVG HITS [3] THIS [2] THIS THIS It should be pointed out that we intentionally do not use the HITS value to compute the average request time but focus solely on the time difference between the last two requests. In any adaptive system, changes in the recent past need to be considered and the HITS value would allow objects that were highly requested in the past but within a very short time span to remain unnecessarily long in the local cache. When an existing entry in the single-table experiences another hit, migration from the single-table to the multiple may occur depending on two factors: the time difference between the latest two requests - a reasonable first approximation of the average object request frequency; and the request frequency of the objects in the multiple-table Multiple-Table The multiple-table (Table Ib) is restricted in size and contains only objects that were requested more than once. The organization of the multiple-table is the same as the single table and is ordered by the average request time of the objects. This order allows the simple identification of the object with the worst average time and quick insertions/deletions based using binary search. Once the multiple-table is filled, newly arrived objects from the single-table need to have an average request time lower than the worst so-adc.tex; 30/04/2003; 16:44; p.7
8 8 TSUI ET AL. case currently residing in the table before it will be placed at the appropriate position. Objects removed from the multiple-table will be put back into the single-table as a regular entry; giving it the chance to be hit again later. An object will be considered for migrating from the multiple-table to the caching-table when it is requested again after an entry has been created in the multiple-table Caching-Table The caching table (Table Ic) in an ADC proxy keeps track of all currently cached objects. This table is very similar to the multipletable, with the exception that the table entries represent actually stored objects. Similar to the multiple-table, this table is also ordered by the average request value in column four and new objects have to outperform at least the worst case in (the last row) the table and will be placed in the appropriate position within it. Elements that drop out of the bottom of this table move back to the multiple-table which gives them the chance to be hit again in the near future or to drop out completely over time. Notice that some entries in the caching-table has the PROXY entry set to another proxy ID. These objects are cached (i.e. a duplicate copy is made) during the selective caching process (see section 3.4) and the ID corresponds to the proxy that actually supplied the requested object, either from its cache or from the origin server Request Forwarding Every proxy in ADC has its own mapping table and each request comes with a global unique ID (usually based on the clients IP address and an internal request counter). ADC proxies handle a request by first look into its cache. Ideally, the requested object is found and returned to the requester (i.e. a client or another proxy). Otherwise, it triggers the request forwarding mechanism. Upon receipt of a reply, either from another proxy or the origin sever, further processing is required. The complete pseudocode is depicted in Figure 2. Request forwarding describes the idea that during the search process, unresolved requests will be forwarded to a more suitable proxy object or the origin server. In general, the decision for a forwarding location is based upon either previously learned data stored in the local mapping tables or a random selection over the set of known proxies. In cases where the same proxy got selected twice during the forwarding process, the doubly-hit proxy will always forward the request to the origin server to prevent a loop from happening. Similarly, a maximum number of forwarding can be set to avoid endless forwarding. so-adc.tex; 30/04/2003; 16:44; p.8
9 DISTRIBUTED PROXY SERVER MANAGEMENT 9 Request Handling: begin if (object in cache) update caching-table return object else // forward request store request info if (hop count > max hop count) or (seen request twice) send request to origin server else if (object in single-table or multiple table) retrieve proxy id else host randomly select a proxy id or origin server endif send request to host endif // process reply perform selective caching if else if endif endif endif end (responsible proxy is THIS) return object to client (object obtained from origin server) mark object with proxy id return object to requester (upstream proxy or client) Figure 2. The pseudocode for handling a request in a ADC proxy server The retrieved object will then traverse the same path back to the requesting client and all proxies on the way have the option to cache the data.wecallthisprocessbacktracking. In regard to the internal data structure, it is important that every proxy stores information about every forwarded request as long as the backtracking process is not completed Multicasting by Backtracking Backtracking is the process a retrieved object travels back from the downstream proxy. This is the method by which all ADC proxies agree so-adc.tex; 30/04/2003; 16:44; p.9
10 10 TSUI ET AL. on the location for a specific web object in the absence of a central coordinator or a broadcasting protocol. The assumption is that the proxy which retrieves the web object concerned will mark the package with its ID and all other proxies on the return path will receive and accept this information. Once the mapping tables are updated, subsequent requests for the same object can be directed to the right location Selective Caching and Aging Selective caching was introduced in our previous work to allow each proxy to autonomously specialize on a specific set of cached data [17]. In hierarchical and hashing systems, every proxy stores all passing objects regardless of its future significance and usually uses the LRU algorithm as the cache replacement strategy. This approach has the drawback that it creates a high cache fluctuation rate with minimal reliability in regard to the cached content. Proxy agents based on ADC keep track of the average request frequency of all requested objects based on the last two requests experienced. The learned data, in the form of time gap between two requests, will be used to decide whether the new data should be cached or not. A newly arrived object will only be cached if its average request time is smaller than the worst case currently residing in the cache. As mentioned before, we introduced selective caching as a mean to focus on the frequently requested objects, and preliminary work has shown that our ADC algorithm works better with selective caching and an ordered table than a table based on a typical LRU algorithm [19]. An object will only be cached if it is able to move from the multipletable into the caching-table by having an average request time shorter than the worst case. To make sure that old objects will expire, we introduced a simple object aging strategy by computing the object average time with a focus on the passed time since the last request. T age = T average +(T last T now ) (1) 2 The advantage of this equation is that it is simple and incurs minimal computational cost. It gives the currently requested objects a lower age (allowing them to stay longer in the table) and represents the actual average value for the next request. Essentially it can be seen as a moving average with a focus on the current time. It should be noted that all object age at the same pace and that an established table order remains the same during the aging process. New objects use the current age of the existing objects to place itself into the appropriate position. so-adc.tex; 30/04/2003; 16:44; p.10
11 DISTRIBUTED PROXY SERVER MANAGEMENT Experimentation To validate and verify the Adaptive Distributed Caching algorithm described above, we ran multiple simulations over two sets of artificially created client requests using the polygraph benchmarking tool 1,which is mostly used for the real-time evaluation of hardware proxy systems for and it allows us the specific settings of different parameters to create an artificial request pattern which is supposed to be close to that in real-life Experimental Setup In the first set of tests, we compare the performance of the ADC algorithm to the widely-used hashing-based CARP [35] using cache hit rate and hop count. The second set of tests aim to test the sensitivity of the ADC algorithm according to the size of the mapping tables and performance is evaluated according to cache hit rate, hop count and execution time. In all the tests, object size is ignored and are assumed to be uniform. The number of ADC or HASH proxies is 5 and there are 525 servers providing web objects to 250 clients. The maximum number of requests per second is set at 100. Therefore, the maximum possible number of requests in the generated data files is million Request Patterns Both created files come with a set of almost 4 million requests, which is equivalent to around 12 hours of traffic from the 250 clients, and is divided into three main phases. The load in each phase gradually increases from 10% to 100% at the initial 20 minutes and wise vera at the last 20 minutes. Figure 4 shows the request throughput in each phase 2. Phase 1 (fill), with around 864k requests, covers a simple fill phase with only 9% request repetitions. Phase 2 (top1) with around 1.5 million requests offers requests and repeats itself in Phase 3 (top2). There is an idle time covering 108k requests where the workload is kept at only 10% of the maximum workload. For performance assessment of industrial strength proxy servers using the polygraph tool, only the middle section of top2 is used. The two request patterns differ only in the document popularity model. For scenario 1 data file (Figure 3a), it has a set of popular documents (the hot set), which is equal to 1% of the total number of requested documents at any instant (the working set). The probability of requesting an object from the hot set is 10%. Scenario 2 data file (Figure 3b) has the same hot set size but the probability of accessing so-adc.tex; 30/04/2003; 16:44; p.11
12 12 TSUI ET AL Number of Requests Server ID Figure 3a. Number of requests per server for Scenario 1 request pattern Number of Requests Server ID Figure 3b. Number of requests per server for Scenario 2 request pattern the hot set is 90%. This result of this variation is a difference in the maximum achievable hit rate Performance Metrics We used cache hit rate and hop count to measure the performance of the algorithms. When we study the parameter sensitivity in relation to table size, we also included simulated execution time. Cache hit rate refers to the percentage of time a request can be located in the local cache of any proxy server in the proxy system. It can serve as an indicator as how much network traffic can be saved by employing a proxy. The maximum achievable hit rate depends on the cache size and the traffic pattern. Therefore, unless exact hardware/software is used, direct comparison with published results is not useful. However, for our purposes, relative performance can be measured. Hop count measures the number of inter-machine communication, i.e. client/proxy, proxy/proxy, and proxy/server communication. For the hashing algorithm, the possible combination sequence of communications are (shown graphically in Figure 1a & b): so-adc.tex; 30/04/2003; 16:44; p.12
13 DISTRIBUTED PROXY SERVER MANAGEMENT 13 Figure 4. Throughput of the polygraph generated traffic pattern over time client/proxy/client (local cache lookup) client/proxy/-server/proxy/client (origin server lookup) client/proxy1/proxy2/client (cache lookup from non-directly connected proxy) client/proxy1/-proxy2/server/proxy2/client (origin server lookup from non-directly connected proxy) Therefore, the average hop count should be bounded between 2 and 5, and an ideal hop count will be between 2 and 3. As for ADC, the number of hops is always an even number because the route will be traversed twice. The lower bound for ADC s hop count is two, and the ideal hop count is between 2 and ADC versus Hashing We compare the performance of our ADC algorithm to the performance of a common hashing algorithm by hit rate - the percentage of reuse, and hop count - the number of intervening proxies/server before the requested object reaches the requester. The system runs with 20k entries for the single- and the multiple-table and 10k entries for the caching-table in each of the 5 running proxies Hit Rate Figure 5a and 5b show the average hit rate as a moving average over 5,000 request intervals for scenario 1 and 2 traffic patterns respectively. The general observation is that during the fill and top1 phases, ADC takes longer time to achieve the hit rate hashing achieved. However, in the measurement taking phase (top2), ADC performs as well as the hashing algorithm. so-adc.tex; 30/04/2003; 16:44; p.13
14 14 TSUI ET AL ADC HASH 10 Hit Rate (%) Requests (x1000) Figure 5a. Hit rates achieved by ADC and hashing for scenario 1 traffic pattern ADC HASH 40 Hit Rate (%) Requests (x1000) Figure 5b. Hit rates achieved by ADC and hashing for scenario 2 traffic pattern Hop Count While ADC and hashing achieve similar cache hit rate, it is necessary to see if ADC is doing so at the expense of increased latency. Figure 6a and 6b show the comparison of the average number of hops needed to resolve a request. For scenario 1 traffic, hashing requires on average close to 5 hops to resolve a request. That means hashing needs to contact the origin server via the second proxy most of the time. On the other hand, ADC needs on average 2 additional hops than hashing. That means ADC needs to consult one more proxy than hashing about half of the time. This result, on one hand, allows the ADC algorithm to search for a specific object more flexibly than the hashing algorithm. On the other hand, ADC has longer systems response than the hashing algorithm. Scenario 2 traffic is generated such that a high cach hit rate can be achieved. The reduction in hop count also reflects this fact. Hashing so-adc.tex; 30/04/2003; 16:44; p.14
15 DISTRIBUTED PROXY SERVER MANAGEMENT ADC HASH 7.5 Hop Count Requests (x1000) Figure 6a. Hop counts of ADC and hashing for scenario 1 traffic pattern ADC HASH Hop Count Requests (x1000) Figure 6b. Hop counts of ADC and hashing for scenario 2 traffic pattern require on average only 4 hops. That means the second proxy only need to contact the origin server about half of the time. ADC needs only one additional hop than hashing during the top2 phase, which can be accounted for by the additional proxy/proxy transfer before reaching the client. There is no need for ADC to employ more than two proxies to resolve a request. It is clear that ADC can optimally duplicate the frequently requested objects and cut down on the need to contact the origin server for the required web objects Changing Table Size This section reports our experiments that focused on varying the size for the caching-, multiple- and single-table between 5k and 30k, and we varying the size of one table at a time. The default table sizes for all simulations were 10k for the caching table and 20k for the single and multiple-table. We used average hit rate, hop count and simulation so-adc.tex; 30/04/2003; 16:44; p.15
16 16 TSUI ET AL Single Multiple Cache 10 Hit Rate (%) Table Size Figure 7a. Hit rate and Hop count by various table size combinations (using scenario 1 traffic) Single Multiple Cache 7.2 Hop Count Table Size Figure 7b. Hit rate and Hop count by various table size combinations (using scenario 1 traffic) time needed for the 4 million requests in scenario 1 as our evaluation criteria Hits by Table Size In the first part of the evaluation we changed each table size from 5k to 30k in the steps of 5k and observe the overall cache hit rate. We can identify from Figure 7b that the size of the caching table is mostly responsible for the overall hit rate. Naturally, the more cache is available in the system, the more hits are experienced in the test-run. Increasing both the single and the multiple-table beyond 10k did not improve the hit rate above 7%. Interestingly, even a single-table size of 5k was still able to capture enough requests to allow the system to reach the same so-adc.tex; 30/04/2003; 16:44; p.16
17 DISTRIBUTED PROXY SERVER MANAGEMENT Single Multiple Cache 8000 Time Table Size Figure 8. Execution time (in seconds) of the simulations for various table size number of hits as a single-table size of 30k. A multiple-table of under 10k has a negative impact on the overall hit rate Hops by Table Size Figure 7a depicts the average number of hops needed to resolve a request for various table sizes. The general trend is that larger table sizes results in less hops. However, the difference is actually less than 0.15 hops for the single- and multiple-table. The biggest difference resulted in increasing the caching-table size is still just hop, and can be regarded as not significant in comparison of the average number of around 7 hops. The least radical decline can be observed from the changes in the singletable size. This result is consistent with the hit rate results above: the bigger the caching-table the better. If the size of the single-table is big enough to handle the amount of requests a proxy encounters plus those entries demoted from the multiple-table, further increase in size will be benefit the system, as these objects are not cached Time by Table Size Figure 8 shows the simulation time in seconds. It can be observed that increasing the single- and multiple-table slows down the overall execution time while increasing caching-table has no significant impact. It seems the most time consuming part of ADC lies with the access mechanism of the single- and multiple-table. While the single-table is based on the LRU algorithm, locating a candidate for removal during replacement requires ADC to search a linked list element by element. Insertion and deletion at the ordered multiple-table is mostly operated by binary search algorithms. Both access schemes are extremely time consuming and a better data structure is needed to provide speed-ups in the future versions of this algorithm. so-adc.tex; 30/04/2003; 16:44; p.17
18 18 TSUI ET AL. Constant paging and context switches occur frequently during the experiments due to limited amount of memory and causes significant delay. Algorithms like MD5 [24] could be used in future to reduce the amount of memory required for storing the URLs in the mapping tables. 5. Conclusions We have presented in the article the new design of the algorithm called Adaptive Distributed Caching, which aims to allow a system of proxy servers to self-organize without the need for central coordination or complicated communication protocol. Based on the experiments we conducted using two artificial (but quite realistic) data files, it is confident that ADC is able to achieve the same level of performance as a well-known hashing algorithm. The extra effort required is just one to two more hops, which can be considered small amount of network latency comparing to the latency incurred on the Internet. We also presented evaluation results regarding various parameters like caching-, multiple- and single-table sizes. We can conclude that a threetable setup only requires a small storage overhead, as small single- and multi-table are required. The results further show that ADC requires a learning period before it can match the performance of the common hashing algorithm. The strength of ADC should be further studied in the situations where changes both in the proxy system infrastructure and different traffic pattern such as the Wisconsin proxy benchmark [2]. Additionally, we plan to implement the ADC algorithm in a real proxy system such as the freely available Squid server 3. Acknowledgements This project is partially funded by grants from the Hong Kong Baptist University (FRG/01-02/I-37 & FRG/02-03/II-39). Notes 1 Polygraph website: 2 source: phases.png 3 Squid website: so-adc.tex; 30/04/2003; 16:44; p.18
19 DISTRIBUTED PROXY SERVER MANAGEMENT 19 References 1. G. Abdulla. Analysis and Modeling of World Wide Web Traffic. PhD thesis, Virginia Polytechnic Institute and State University, May J. Almeida and P. Cao. Measuring proxy performance with the wisconsin proxy benchmark. Technical report, University of Wisconsin Department of Computer Science, April G. Barish and K. Obraczka. World wide web caching: Trends and techniques. IEEE Communications Magazine, May H. Bryhni, E. Klovning, and O. Kure. A comparison of load balancing techniques for scalable web servers. IEEE Network, 14(4):58 64, July/August R. B. Bunt, D. L. Eager, G. M. Oster, and C. L. Williamson. Achieving load balance and effective caching in clustered web servers. In Proceedings of the Fourth International WWWCaching Workshop, R. Caceres, F. Douglis, A. Feldmann, G. Glass, and M. Rabinovich. Web proxy caching: The devil is in the details. Performance Evaluation Review, 26(3):11 15, December V. Cardellini, M. Colajanni, and P. S. Yu. Load balancing on web-server systems. IEEE Internet Computing, 3(3):28 39, May/June C.-Y.Chiang,Y.Li,M.T.Liu,andM.E.Muller. Onrequestforwarding for dynamic web caching hierarchies. In Proceedings of the 20th International Conference on Distributed Computing Systems, J. Chuang. Resource allocation for stor-serv: Network storage services with QOF guarantee. In Proceedings of the Nework Storage Symposium, J. Cohen, N. Phadnis, V. Valloppillil, and K. W. Ross. Cache array routing protocol v.1.1. September B. M. Duska, D. Marwood, and M. J. Feeley. The measured access characteristics of world-wide-web client proxy caches. In Proceedings of USENIX Symposium on Internet Technology and Systems, December S. G. Dykes, C. L. Jeffery, and S. Das. Taxonomy and design for distributed web caching. In Proceedings of the Hawaii International Conference on System Science, L. Fan, P. Cao, J. Almeida, and A. Broder. Summary cache: A sacable widearea web caching sharing pool. In Proceedings of ACM SIGCOMM Conference, J. Gwertzman and M. Seltzer. World-wide web cache consistency. In Proceedings of USENIX Symposium on Internetworking Technologies and Systems, pages , A. Heddaya and S. Mirdad. WebWave: Globally load balanced fully distributed caching of hot published documents. In Proceedings of 17th IEEE Conference on Distributed Computing Systems, Q. Jacobson and P. Cao. Potential and limits of web prefetching between low-bandwidth clients and proxies. In Proceedings of Third International WWWCaching Workshop, M. J. Kaiser, K. C. Tsui, and J. Liu. Adaptive distributed caching. In Proceedings of the 2002 Congress on Evolutionary Computation, pages , May M. J. Kaiser, K. C. Tsui, and J. Liu. Adaptive distributed caching with minimal memory usage. In Proceedings of Simulated Evolution and Automated Learning Conference, pages , September so-adc.tex; 30/04/2003; 16:44; p.19
20 20 TSUI ET AL. 19. M. J. Kaiser, K. C. Tsui, and J. Liu. Self-organized autonomous web proxies. In Proceedings of the First International Joint Conference on Autonomous Agents and Multiagent Systems, pages , July D. Karger, T. Leighton, D. Lewin, and A. Sherman. Web caching with consistent hashing. In Proceedings of the WWW8 Conference, C. Lindemann and A. Reuys. Modeling Web Proxy Cache Architectures. Addison-Wesley, J. Liu and K. C. Tsui. Introduction to autonomy oriented computation. In Proceedings of 1st International Workshop on Autonomy Oriented Computation, pages 1 11, J.-M. Menaud, V. Issarny, and M. Banatre. Improving effiectiveness of web caching. In Recent Advances in Distributed Systems, volume LNCS Springer Verlag, A. J. Menezes, P. C. V. Oorscht, and S. A. Vanstone. In Handbook of Applied Crytography, page 816. CRC Press, S. Paul and Z. Fei. Distributed caching with centralized control. In Proceedings of the Fifth International Web Caching and Content Delivery Workshop, M. S. Raunak. A survey of cooperative caching. Technical report, December P. Rodriguez, C. Spanner, and E. W. Biersack. Web caching architectures: Hierarchical and distributed caching. In Proceedings of the Fourth International WWWCaching Workshop, P. Rodriguez, C. Spanner, and E. W. Biersack. Web caching architectures: Hierarchical and distributed caching K. W. Ross. Hash-routing for collections of shared web caches. IEEE Network Magazine, 11(7):37 44, Nov-Dec A. Rousskov and V. Soloviev. On performance of caching proxies. In Proceedings of the ACM SIGMETRICS Conference, M. Sinnwell and G. Weikum. A cost model-based online method for distributed caching. In Proceedings of IEEE Conference on Data Engineering, R. Tweari, M. Dahlin, H. Vin, and J. Kay. Design considerations for distributed caching on the internet. In Proceedings of the 19th IEEE Conference on Distributed Computing Systems, J. Wang. A survey of web caching schemes for the internet. ACM Computer Communication Review, 29(5):36 46, October Z. Wang and J. Crowcroft. CacheMesh: A distributed cache system for world wide web. In Proceedings of NLANR Web Cache Workshop, June A. Wolman, G. M. Voelker, N. Sharman, N. Cardwell, A. Karlin, and H. M. Levy. On the scale and performance of cooperative web proxy caching. In Proceedings of the 17th ACM Symposium on Operating Systems Principles, pages 16 31, K.-L. Wu and P. S. Yu. Load balancing and hot spot relief for hash routing among a collection of proxy caches. In Proceedings of the 19th International Conference on Distributed Computing Systems, L. Zhang, S. Michel, K. Nguyen, and A. Rosenstein. Adaptive web caching: Towards a new global caching architecture. In Proceedings of the Third International WWWCaching Workshop, so-adc.tex; 30/04/2003; 16:44; p.20
ADAPTIVE DISTRIBUTED CACHING WITH MINIMAL MEMORY USAGE
 ADAPTIVE DISTRIBUTED CACHING WITH MINIMAL MEMORY USAGE Markus J. Kaiser, Kwok Ching Tsui and Jiming Liu Department of Computer Science Hong Kong Baptist University Kowloon Tong, Kowloon, Hong Kong ABSTRACT
ADAPTIVE DISTRIBUTED CACHING WITH MINIMAL MEMORY USAGE Markus J. Kaiser, Kwok Ching Tsui and Jiming Liu Department of Computer Science Hong Kong Baptist University Kowloon Tong, Kowloon, Hong Kong ABSTRACT
Self-Organized Load Balancing in Proxy Servers: Algorithms and Performance
 Self-Organized Load Balancing in Proxy Servers: Algorithms and Performance Kwok Ching Tsui (tsuikc@comp.hkbu.edu.hk) Department of Computer Science, Hong Kong Baptist University Jiming Liu (jiming@comp.hkbu.edu.hk)
Self-Organized Load Balancing in Proxy Servers: Algorithms and Performance Kwok Ching Tsui (tsuikc@comp.hkbu.edu.hk) Department of Computer Science, Hong Kong Baptist University Jiming Liu (jiming@comp.hkbu.edu.hk)
International Journal of Scientific & Engineering Research, Volume 4, Issue 11, November-2013 349 ISSN 2229-5518
 International Journal of Scientific & Engineering Research, Volume 4, Issue 11, November-2013 349 Load Balancing Heterogeneous Request in DHT-based P2P Systems Mrs. Yogita A. Dalvi Dr. R. Shankar Mr. Atesh
International Journal of Scientific & Engineering Research, Volume 4, Issue 11, November-2013 349 Load Balancing Heterogeneous Request in DHT-based P2P Systems Mrs. Yogita A. Dalvi Dr. R. Shankar Mr. Atesh
2. DESIGN OF SCALABLE DYNAMIC WEB SERVER ARCHITECTURE
 PARALLEL CACHE MANAGEMENT PROTOCOL FOR STATIC AND DYNAMIC WEB CONTENTS * Jaeyong Lim Dept. of Computer and Information Science and Engineering University of Florida, Gainesville, FL 32611 jlim@cise.ufl.edu
PARALLEL CACHE MANAGEMENT PROTOCOL FOR STATIC AND DYNAMIC WEB CONTENTS * Jaeyong Lim Dept. of Computer and Information Science and Engineering University of Florida, Gainesville, FL 32611 jlim@cise.ufl.edu
Hierarchical Content Routing in Large-Scale Multimedia Content Delivery Network
 Hierarchical Content Routing in Large-Scale Multimedia Content Delivery Network Jian Ni, Danny H. K. Tsang, Ivan S. H. Yeung, Xiaojun Hei Department of Electrical & Electronic Engineering Hong Kong University
Hierarchical Content Routing in Large-Scale Multimedia Content Delivery Network Jian Ni, Danny H. K. Tsang, Ivan S. H. Yeung, Xiaojun Hei Department of Electrical & Electronic Engineering Hong Kong University
Fault-Tolerant Framework for Load Balancing System
 Fault-Tolerant Framework for Load Balancing System Y. K. LIU, L.M. CHENG, L.L.CHENG Department of Electronic Engineering City University of Hong Kong Tat Chee Avenue, Kowloon, Hong Kong SAR HONG KONG Abstract:
Fault-Tolerant Framework for Load Balancing System Y. K. LIU, L.M. CHENG, L.L.CHENG Department of Electronic Engineering City University of Hong Kong Tat Chee Avenue, Kowloon, Hong Kong SAR HONG KONG Abstract:
1. Comments on reviews a. Need to avoid just summarizing web page asks you for:
 1. Comments on reviews a. Need to avoid just summarizing web page asks you for: i. A one or two sentence summary of the paper ii. A description of the problem they were trying to solve iii. A summary of
1. Comments on reviews a. Need to avoid just summarizing web page asks you for: i. A one or two sentence summary of the paper ii. A description of the problem they were trying to solve iii. A summary of
A Content-Based Load Balancing Algorithm for Metadata Servers in Cluster File Systems*
 A Content-Based Load Balancing Algorithm for Metadata Servers in Cluster File Systems* Junho Jang, Saeyoung Han, Sungyong Park, and Jihoon Yang Department of Computer Science and Interdisciplinary Program
A Content-Based Load Balancing Algorithm for Metadata Servers in Cluster File Systems* Junho Jang, Saeyoung Han, Sungyong Park, and Jihoon Yang Department of Computer Science and Interdisciplinary Program
Efficient DNS based Load Balancing for Bursty Web Application Traffic
 ISSN Volume 1, No.1, September October 2012 International Journal of Science the and Internet. Applied However, Information this trend leads Technology to sudden burst of Available Online at http://warse.org/pdfs/ijmcis01112012.pdf
ISSN Volume 1, No.1, September October 2012 International Journal of Science the and Internet. Applied However, Information this trend leads Technology to sudden burst of Available Online at http://warse.org/pdfs/ijmcis01112012.pdf
Measuring the Performance of Prefetching Proxy Caches
 Measuring the Performance of Prefetching Proxy Caches Brian D. Davison davison@cs.rutgers.edu Department of Computer Science Rutgers, The State University of New Jersey The Problem Traffic Growth User
Measuring the Performance of Prefetching Proxy Caches Brian D. Davison davison@cs.rutgers.edu Department of Computer Science Rutgers, The State University of New Jersey The Problem Traffic Growth User
Concept of Cache in web proxies
 Concept of Cache in web proxies Chan Kit Wai and Somasundaram Meiyappan 1. Introduction Caching is an effective performance enhancing technique that has been used in computer systems for decades. However,
Concept of Cache in web proxies Chan Kit Wai and Somasundaram Meiyappan 1. Introduction Caching is an effective performance enhancing technique that has been used in computer systems for decades. However,
Storage Systems Autumn 2009. Chapter 6: Distributed Hash Tables and their Applications André Brinkmann
 Storage Systems Autumn 2009 Chapter 6: Distributed Hash Tables and their Applications André Brinkmann Scaling RAID architectures Using traditional RAID architecture does not scale Adding news disk implies
Storage Systems Autumn 2009 Chapter 6: Distributed Hash Tables and their Applications André Brinkmann Scaling RAID architectures Using traditional RAID architecture does not scale Adding news disk implies
Evaluating Cooperative Web Caching Protocols for Emerging Network Technologies 1
 Evaluating Cooperative Web Caching Protocols for Emerging Network Technologies 1 Christoph Lindemann and Oliver P. Waldhorst University of Dortmund Department of Computer Science August-Schmidt-Str. 12
Evaluating Cooperative Web Caching Protocols for Emerging Network Technologies 1 Christoph Lindemann and Oliver P. Waldhorst University of Dortmund Department of Computer Science August-Schmidt-Str. 12
Lecture 3: Scaling by Load Balancing 1. Comments on reviews i. 2. Topic 1: Scalability a. QUESTION: What are problems? i. These papers look at
 Lecture 3: Scaling by Load Balancing 1. Comments on reviews i. 2. Topic 1: Scalability a. QUESTION: What are problems? i. These papers look at distributing load b. QUESTION: What is the context? i. How
Lecture 3: Scaling by Load Balancing 1. Comments on reviews i. 2. Topic 1: Scalability a. QUESTION: What are problems? i. These papers look at distributing load b. QUESTION: What is the context? i. How
DUP: Dynamic-tree Based Update Propagation in Peer-to-Peer Networks
 : Dynamic-tree Based Update Propagation in Peer-to-Peer Networks Liangzhong Yin and Guohong Cao Department of Computer Science & Engineering The Pennsylvania State University University Park, PA 16802
: Dynamic-tree Based Update Propagation in Peer-to-Peer Networks Liangzhong Yin and Guohong Cao Department of Computer Science & Engineering The Pennsylvania State University University Park, PA 16802
D1.1 Service Discovery system: Load balancing mechanisms
 D1.1 Service Discovery system: Load balancing mechanisms VERSION 1.0 DATE 2011 EDITORIAL MANAGER Eddy Caron AUTHORS STAFF Eddy Caron, Cédric Tedeschi Copyright ANR SPADES. 08-ANR-SEGI-025. Contents Introduction
D1.1 Service Discovery system: Load balancing mechanisms VERSION 1.0 DATE 2011 EDITORIAL MANAGER Eddy Caron AUTHORS STAFF Eddy Caron, Cédric Tedeschi Copyright ANR SPADES. 08-ANR-SEGI-025. Contents Introduction
Copyright www.agileload.com 1
 Copyright www.agileload.com 1 INTRODUCTION Performance testing is a complex activity where dozens of factors contribute to its success and effective usage of all those factors is necessary to get the accurate
Copyright www.agileload.com 1 INTRODUCTION Performance testing is a complex activity where dozens of factors contribute to its success and effective usage of all those factors is necessary to get the accurate
Recommendations for Performance Benchmarking
 Recommendations for Performance Benchmarking Shikhar Puri Abstract Performance benchmarking of applications is increasingly becoming essential before deployment. This paper covers recommendations and best
Recommendations for Performance Benchmarking Shikhar Puri Abstract Performance benchmarking of applications is increasingly becoming essential before deployment. This paper covers recommendations and best
Path Selection Methods for Localized Quality of Service Routing
 Path Selection Methods for Localized Quality of Service Routing Xin Yuan and Arif Saifee Department of Computer Science, Florida State University, Tallahassee, FL Abstract Localized Quality of Service
Path Selection Methods for Localized Quality of Service Routing Xin Yuan and Arif Saifee Department of Computer Science, Florida State University, Tallahassee, FL Abstract Localized Quality of Service
Dynamic Adaptive Feedback of Load Balancing Strategy
 Journal of Information & Computational Science 8: 10 (2011) 1901 1908 Available at http://www.joics.com Dynamic Adaptive Feedback of Load Balancing Strategy Hongbin Wang a,b, Zhiyi Fang a,, Shuang Cui
Journal of Information & Computational Science 8: 10 (2011) 1901 1908 Available at http://www.joics.com Dynamic Adaptive Feedback of Load Balancing Strategy Hongbin Wang a,b, Zhiyi Fang a,, Shuang Cui
Simple Solution for a Location Service. Naming vs. Locating Entities. Forwarding Pointers (2) Forwarding Pointers (1)
 Naming vs. Locating Entities Till now: resources with fixed locations (hierarchical, caching,...) Problem: some entity may change its location frequently Simple solution: record aliases for the new address
Naming vs. Locating Entities Till now: resources with fixed locations (hierarchical, caching,...) Problem: some entity may change its location frequently Simple solution: record aliases for the new address
Guiding Web Proxy and Server Placement for High Performance Internet Content Delivery 1
 Guiding Web Proxy and Server Placement for High Performance Internet Content Delivery 1 Peter Triantafillou (contact author) Department of Computer Engineering and Informatics, University of Patras Rio
Guiding Web Proxy and Server Placement for High Performance Internet Content Delivery 1 Peter Triantafillou (contact author) Department of Computer Engineering and Informatics, University of Patras Rio
LOAD BALANCING AS A STRATEGY LEARNING TASK
 LOAD BALANCING AS A STRATEGY LEARNING TASK 1 K.KUNGUMARAJ, 2 T.RAVICHANDRAN 1 Research Scholar, Karpagam University, Coimbatore 21. 2 Principal, Hindusthan Institute of Technology, Coimbatore 32. ABSTRACT
LOAD BALANCING AS A STRATEGY LEARNING TASK 1 K.KUNGUMARAJ, 2 T.RAVICHANDRAN 1 Research Scholar, Karpagam University, Coimbatore 21. 2 Principal, Hindusthan Institute of Technology, Coimbatore 32. ABSTRACT
Back-End Forwarding Scheme in Server Load Balancing using Client Virtualization
 Back-End Forwarding Scheme in Server Load Balancing using Client Virtualization Shreyansh Kumar School of Computing Science and Engineering VIT University Chennai Campus Parvathi.R, Ph.D Associate Professor-
Back-End Forwarding Scheme in Server Load Balancing using Client Virtualization Shreyansh Kumar School of Computing Science and Engineering VIT University Chennai Campus Parvathi.R, Ph.D Associate Professor-
Dependency Free Distributed Database Caching for Web Applications and Web Services
 Dependency Free Distributed Database Caching for Web Applications and Web Services Hemant Kumar Mehta School of Computer Science and IT, Devi Ahilya University Indore, India Priyesh Kanungo Patel College
Dependency Free Distributed Database Caching for Web Applications and Web Services Hemant Kumar Mehta School of Computer Science and IT, Devi Ahilya University Indore, India Priyesh Kanungo Patel College
Locality Based Protocol for MultiWriter Replication systems
 Locality Based Protocol for MultiWriter Replication systems Lei Gao Department of Computer Science The University of Texas at Austin lgao@cs.utexas.edu One of the challenging problems in building replication
Locality Based Protocol for MultiWriter Replication systems Lei Gao Department of Computer Science The University of Texas at Austin lgao@cs.utexas.edu One of the challenging problems in building replication
Globule: a Platform for Self-Replicating Web Documents
 Globule: a Platform for Self-Replicating Web Documents Guillaume Pierre Maarten van Steen Vrije Universiteit, Amsterdam Internal report IR-483 January 2001 Abstract Replicating Web documents at a worldwide
Globule: a Platform for Self-Replicating Web Documents Guillaume Pierre Maarten van Steen Vrije Universiteit, Amsterdam Internal report IR-483 January 2001 Abstract Replicating Web documents at a worldwide
Load balancing as a strategy learning task
 Scholarly Journal of Scientific Research and Essay (SJSRE) Vol. 1(2), pp. 30-34, April 2012 Available online at http:// www.scholarly-journals.com/sjsre ISSN 2315-6163 2012 Scholarly-Journals Review Load
Scholarly Journal of Scientific Research and Essay (SJSRE) Vol. 1(2), pp. 30-34, April 2012 Available online at http:// www.scholarly-journals.com/sjsre ISSN 2315-6163 2012 Scholarly-Journals Review Load
Rapid Bottleneck Identification A Better Way to do Load Testing. An Oracle White Paper June 2009
 Rapid Bottleneck Identification A Better Way to do Load Testing An Oracle White Paper June 2009 Rapid Bottleneck Identification A Better Way to do Load Testing. RBI combines a comprehensive understanding
Rapid Bottleneck Identification A Better Way to do Load Testing An Oracle White Paper June 2009 Rapid Bottleneck Identification A Better Way to do Load Testing. RBI combines a comprehensive understanding
A Reputation Management System in Structured Peer-to-Peer Networks
 A Reputation Management System in Structured Peer-to-Peer Networks So Young Lee, O-Hoon Kwon, Jong Kim and Sung Je Hong Dept. of Computer Science & Engineering, Pohang University of Science and Technology
A Reputation Management System in Structured Peer-to-Peer Networks So Young Lee, O-Hoon Kwon, Jong Kim and Sung Je Hong Dept. of Computer Science & Engineering, Pohang University of Science and Technology
A Novel Caching Scheme for Internet based Mobile Ad Hoc Networks
 A Novel Caching Scheme for Internet based Mobile Ad Hoc Networks Sunho Lim, Wang-Chien Lee, Guohong Cao, and Chita R. Das Department of Computer Science & Engineering The Pennsylvania State University
A Novel Caching Scheme for Internet based Mobile Ad Hoc Networks Sunho Lim, Wang-Chien Lee, Guohong Cao, and Chita R. Das Department of Computer Science & Engineering The Pennsylvania State University
Monitoring Large Flows in Network
 Monitoring Large Flows in Network Jing Li, Chengchen Hu, Bin Liu Department of Computer Science and Technology, Tsinghua University Beijing, P. R. China, 100084 { l-j02, hucc03 }@mails.tsinghua.edu.cn,
Monitoring Large Flows in Network Jing Li, Chengchen Hu, Bin Liu Department of Computer Science and Technology, Tsinghua University Beijing, P. R. China, 100084 { l-j02, hucc03 }@mails.tsinghua.edu.cn,
CHAPTER 7 SUMMARY AND CONCLUSION
 179 CHAPTER 7 SUMMARY AND CONCLUSION This chapter summarizes our research achievements and conclude this thesis with discussions and interesting avenues for future exploration. The thesis describes a novel
179 CHAPTER 7 SUMMARY AND CONCLUSION This chapter summarizes our research achievements and conclude this thesis with discussions and interesting avenues for future exploration. The thesis describes a novel
A Cloud Data Center Optimization Approach Using Dynamic Data Interchanges
 A Cloud Data Center Optimization Approach Using Dynamic Data Interchanges Efstratios Rappos Institute for Information and Communication Technologies, Haute Ecole d Ingénierie et de Geston du Canton de
A Cloud Data Center Optimization Approach Using Dynamic Data Interchanges Efstratios Rappos Institute for Information and Communication Technologies, Haute Ecole d Ingénierie et de Geston du Canton de
An Active Packet can be classified as
 Mobile Agents for Active Network Management By Rumeel Kazi and Patricia Morreale Stevens Institute of Technology Contact: rkazi,pat@ati.stevens-tech.edu Abstract-Traditionally, network management systems
Mobile Agents for Active Network Management By Rumeel Kazi and Patricia Morreale Stevens Institute of Technology Contact: rkazi,pat@ati.stevens-tech.edu Abstract-Traditionally, network management systems
Web Application Hosting Cloud Architecture
 Web Application Hosting Cloud Architecture Executive Overview This paper describes vendor neutral best practices for hosting web applications using cloud computing. The architectural elements described
Web Application Hosting Cloud Architecture Executive Overview This paper describes vendor neutral best practices for hosting web applications using cloud computing. The architectural elements described
How To Balance A Web Server With Remaining Capacity
 Remaining Capacity Based Load Balancing Architecture for Heterogeneous Web Server System Tsang-Long Pao Dept. Computer Science and Engineering Tatung University Taipei, ROC Jian-Bo Chen Dept. Computer
Remaining Capacity Based Load Balancing Architecture for Heterogeneous Web Server System Tsang-Long Pao Dept. Computer Science and Engineering Tatung University Taipei, ROC Jian-Bo Chen Dept. Computer
Towards Streaming Media Traffic Monitoring and Analysis. Hun-Jeong Kang, Hong-Taek Ju, Myung-Sup Kim and James W. Hong. DP&NM Lab.
 Towards Streaming Media Traffic Monitoring and Analysis Hun-Jeong Kang, Hong-Taek Ju, Myung-Sup Kim and James W. Hong Dept. of Computer Science and Engineering, Pohang Korea Email: {bluewind, juht, mount,
Towards Streaming Media Traffic Monitoring and Analysis Hun-Jeong Kang, Hong-Taek Ju, Myung-Sup Kim and James W. Hong Dept. of Computer Science and Engineering, Pohang Korea Email: {bluewind, juht, mount,
Naming vs. Locating Entities
 Naming vs. Locating Entities Till now: resources with fixed locations (hierarchical, caching,...) Problem: some entity may change its location frequently Simple solution: record aliases for the new address
Naming vs. Locating Entities Till now: resources with fixed locations (hierarchical, caching,...) Problem: some entity may change its location frequently Simple solution: record aliases for the new address
OpenFlow Based Load Balancing
 OpenFlow Based Load Balancing Hardeep Uppal and Dane Brandon University of Washington CSE561: Networking Project Report Abstract: In today s high-traffic internet, it is often desirable to have multiple
OpenFlow Based Load Balancing Hardeep Uppal and Dane Brandon University of Washington CSE561: Networking Project Report Abstract: In today s high-traffic internet, it is often desirable to have multiple
Server Traffic Management. Jeff Chase Duke University, Department of Computer Science CPS 212: Distributed Information Systems
 Server Traffic Management Jeff Chase Duke University, Department of Computer Science CPS 212: Distributed Information Systems The Server Selection Problem server array A server farm B Which server? Which
Server Traffic Management Jeff Chase Duke University, Department of Computer Science CPS 212: Distributed Information Systems The Server Selection Problem server array A server farm B Which server? Which
AN EFFICIENT LOAD BALANCING ALGORITHM FOR A DISTRIBUTED COMPUTER SYSTEM. Dr. T.Ravichandran, B.E (ECE), M.E(CSE), Ph.D., MISTE.,
 AN EFFICIENT LOAD BALANCING ALGORITHM FOR A DISTRIBUTED COMPUTER SYSTEM K.Kungumaraj, M.Sc., B.L.I.S., M.Phil., Research Scholar, Principal, Karpagam University, Hindusthan Institute of Technology, Coimbatore
AN EFFICIENT LOAD BALANCING ALGORITHM FOR A DISTRIBUTED COMPUTER SYSTEM K.Kungumaraj, M.Sc., B.L.I.S., M.Phil., Research Scholar, Principal, Karpagam University, Hindusthan Institute of Technology, Coimbatore
Dynamic Load Balancing for Cluster-based Publish/Subscribe System
 Dynamic Load Balancing for Cluster-based Publish/Subscribe System Hojjat Jafarpour, Sharad Mehrotra and Nalini Venkatasubramanian Department of Computer Science University of California, Irvine {hjafarpo,
Dynamic Load Balancing for Cluster-based Publish/Subscribe System Hojjat Jafarpour, Sharad Mehrotra and Nalini Venkatasubramanian Department of Computer Science University of California, Irvine {hjafarpo,
Keywords: Dynamic Load Balancing, Process Migration, Load Indices, Threshold Level, Response Time, Process Age.
 Volume 3, Issue 10, October 2013 ISSN: 2277 128X International Journal of Advanced Research in Computer Science and Software Engineering Research Paper Available online at: www.ijarcsse.com Load Measurement
Volume 3, Issue 10, October 2013 ISSN: 2277 128X International Journal of Advanced Research in Computer Science and Software Engineering Research Paper Available online at: www.ijarcsse.com Load Measurement
PART IV Performance oriented design, Performance testing, Performance tuning & Performance solutions. Outline. Performance oriented design
 PART IV Performance oriented design, Performance testing, Performance tuning & Performance solutions Slide 1 Outline Principles for performance oriented design Performance testing Performance tuning General
PART IV Performance oriented design, Performance testing, Performance tuning & Performance solutions Slide 1 Outline Principles for performance oriented design Performance testing Performance tuning General
Scaling 10Gb/s Clustering at Wire-Speed
 Scaling 10Gb/s Clustering at Wire-Speed InfiniBand offers cost-effective wire-speed scaling with deterministic performance Mellanox Technologies Inc. 2900 Stender Way, Santa Clara, CA 95054 Tel: 408-970-3400
Scaling 10Gb/s Clustering at Wire-Speed InfiniBand offers cost-effective wire-speed scaling with deterministic performance Mellanox Technologies Inc. 2900 Stender Way, Santa Clara, CA 95054 Tel: 408-970-3400
Performance Workload Design
 Performance Workload Design The goal of this paper is to show the basic principles involved in designing a workload for performance and scalability testing. We will understand how to achieve these principles
Performance Workload Design The goal of this paper is to show the basic principles involved in designing a workload for performance and scalability testing. We will understand how to achieve these principles
Low-rate TCP-targeted Denial of Service Attack Defense
 Low-rate TCP-targeted Denial of Service Attack Defense Johnny Tsao Petros Efstathopoulos University of California, Los Angeles, Computer Science Department Los Angeles, CA E-mail: {johnny5t, pefstath}@cs.ucla.edu
Low-rate TCP-targeted Denial of Service Attack Defense Johnny Tsao Petros Efstathopoulos University of California, Los Angeles, Computer Science Department Los Angeles, CA E-mail: {johnny5t, pefstath}@cs.ucla.edu
Study of Different Types of Attacks on Multicast in Mobile Ad Hoc Networks
 Study of Different Types of Attacks on Multicast in Mobile Ad Hoc Networks Hoang Lan Nguyen and Uyen Trang Nguyen Department of Computer Science and Engineering, York University 47 Keele Street, Toronto,
Study of Different Types of Attacks on Multicast in Mobile Ad Hoc Networks Hoang Lan Nguyen and Uyen Trang Nguyen Department of Computer Science and Engineering, York University 47 Keele Street, Toronto,
IMPROVED PROXIMITY AWARE LOAD BALANCING FOR HETEROGENEOUS NODES
 www.ijecs.in International Journal Of Engineering And Computer Science ISSN:2319-7242 Volume 2 Issue 6 June, 2013 Page No. 1914-1919 IMPROVED PROXIMITY AWARE LOAD BALANCING FOR HETEROGENEOUS NODES Ms.
www.ijecs.in International Journal Of Engineering And Computer Science ISSN:2319-7242 Volume 2 Issue 6 June, 2013 Page No. 1914-1919 IMPROVED PROXIMITY AWARE LOAD BALANCING FOR HETEROGENEOUS NODES Ms.
Object Request Reduction in Home Nodes and Load Balancing of Object Request in Hybrid Decentralized Web Caching
 2012 2 nd International Conference on Information Communication and Management (ICICM 2012) IPCSIT vol. 55 (2012) (2012) IACSIT Press, Singapore DOI: 10.7763/IPCSIT.2012.V55.5 Object Request Reduction
2012 2 nd International Conference on Information Communication and Management (ICICM 2012) IPCSIT vol. 55 (2012) (2012) IACSIT Press, Singapore DOI: 10.7763/IPCSIT.2012.V55.5 Object Request Reduction
Introduction to LAN/WAN. Network Layer
 Introduction to LAN/WAN Network Layer Topics Introduction (5-5.1) Routing (5.2) (The core) Internetworking (5.5) Congestion Control (5.3) Network Layer Design Isues Store-and-Forward Packet Switching Services
Introduction to LAN/WAN Network Layer Topics Introduction (5-5.1) Routing (5.2) (The core) Internetworking (5.5) Congestion Control (5.3) Network Layer Design Isues Store-and-Forward Packet Switching Services
An Energy Efficient Location Service for Mobile Ad Hoc Networks
 An Energ Efficient Location Service for Mobile Ad Hoc Networks Zijian Wang 1, Euphan Bulut 1 and Boleslaw K. Szmanski 1, 1 Department of Computer Science, Rensselaer Poltechnic Institute, Tro, NY 12180
An Energ Efficient Location Service for Mobile Ad Hoc Networks Zijian Wang 1, Euphan Bulut 1 and Boleslaw K. Szmanski 1, 1 Department of Computer Science, Rensselaer Poltechnic Institute, Tro, NY 12180
Performance Modeling and Analysis of a Database Server with Write-Heavy Workload
 Performance Modeling and Analysis of a Database Server with Write-Heavy Workload Manfred Dellkrantz, Maria Kihl 2, and Anders Robertsson Department of Automatic Control, Lund University 2 Department of
Performance Modeling and Analysis of a Database Server with Write-Heavy Workload Manfred Dellkrantz, Maria Kihl 2, and Anders Robertsson Department of Automatic Control, Lund University 2 Department of
Job Reference Guide. SLAMD Distributed Load Generation Engine. Version 1.8.2
 Job Reference Guide SLAMD Distributed Load Generation Engine Version 1.8.2 June 2004 Contents 1. Introduction...3 2. The Utility Jobs...4 3. The LDAP Search Jobs...11 4. The LDAP Authentication Jobs...22
Job Reference Guide SLAMD Distributed Load Generation Engine Version 1.8.2 June 2004 Contents 1. Introduction...3 2. The Utility Jobs...4 3. The LDAP Search Jobs...11 4. The LDAP Authentication Jobs...22
Internet Content Distribution
 Internet Content Distribution Chapter 2: Server-Side Techniques (TUD Student Use Only) Chapter Outline Server-side techniques for content distribution Goals Mirrors Server farms Surrogates DNS load balancing
Internet Content Distribution Chapter 2: Server-Side Techniques (TUD Student Use Only) Chapter Outline Server-side techniques for content distribution Goals Mirrors Server farms Surrogates DNS load balancing
A STUDY OF WORKLOAD CHARACTERIZATION IN WEB BENCHMARKING TOOLS FOR WEB SERVER CLUSTERS
 382 A STUDY OF WORKLOAD CHARACTERIZATION IN WEB BENCHMARKING TOOLS FOR WEB SERVER CLUSTERS Syed Mutahar Aaqib 1, Lalitsen Sharma 2 1 Research Scholar, 2 Associate Professor University of Jammu, India Abstract:
382 A STUDY OF WORKLOAD CHARACTERIZATION IN WEB BENCHMARKING TOOLS FOR WEB SERVER CLUSTERS Syed Mutahar Aaqib 1, Lalitsen Sharma 2 1 Research Scholar, 2 Associate Professor University of Jammu, India Abstract:
High Performance Cluster Support for NLB on Window
 High Performance Cluster Support for NLB on Window [1]Arvind Rathi, [2] Kirti, [3] Neelam [1]M.Tech Student, Department of CSE, GITM, Gurgaon Haryana (India) arvindrathi88@gmail.com [2]Asst. Professor,
High Performance Cluster Support for NLB on Window [1]Arvind Rathi, [2] Kirti, [3] Neelam [1]M.Tech Student, Department of CSE, GITM, Gurgaon Haryana (India) arvindrathi88@gmail.com [2]Asst. Professor,
An Oracle White Paper February 2010. Rapid Bottleneck Identification - A Better Way to do Load Testing
 An Oracle White Paper February 2010 Rapid Bottleneck Identification - A Better Way to do Load Testing Introduction You re ready to launch a critical Web application. Ensuring good application performance
An Oracle White Paper February 2010 Rapid Bottleneck Identification - A Better Way to do Load Testing Introduction You re ready to launch a critical Web application. Ensuring good application performance
SiteCelerate white paper
 SiteCelerate white paper Arahe Solutions SITECELERATE OVERVIEW As enterprises increases their investment in Web applications, Portal and websites and as usage of these applications increase, performance
SiteCelerate white paper Arahe Solutions SITECELERATE OVERVIEW As enterprises increases their investment in Web applications, Portal and websites and as usage of these applications increase, performance
CROSS LAYER BASED MULTIPATH ROUTING FOR LOAD BALANCING
 CHAPTER 6 CROSS LAYER BASED MULTIPATH ROUTING FOR LOAD BALANCING 6.1 INTRODUCTION The technical challenges in WMNs are load balancing, optimal routing, fairness, network auto-configuration and mobility
CHAPTER 6 CROSS LAYER BASED MULTIPATH ROUTING FOR LOAD BALANCING 6.1 INTRODUCTION The technical challenges in WMNs are load balancing, optimal routing, fairness, network auto-configuration and mobility
Improving Availability with Adaptive Roaming Replicas in Presence of Determined DoS Attacks
 Improving Availability with Adaptive Roaming Replicas in Presence of Determined DoS Attacks Chin-Tser Huang, Prasanth Kalakota, Alexander B. Alexandrov Department of Computer Science and Engineering University
Improving Availability with Adaptive Roaming Replicas in Presence of Determined DoS Attacks Chin-Tser Huang, Prasanth Kalakota, Alexander B. Alexandrov Department of Computer Science and Engineering University
Multilevel Load Balancing in NUMA Computers
 FACULDADE DE INFORMÁTICA PUCRS - Brazil http://www.pucrs.br/inf/pos/ Multilevel Load Balancing in NUMA Computers M. Corrêa, R. Chanin, A. Sales, R. Scheer, A. Zorzo Technical Report Series Number 049 July,
FACULDADE DE INFORMÁTICA PUCRS - Brazil http://www.pucrs.br/inf/pos/ Multilevel Load Balancing in NUMA Computers M. Corrêa, R. Chanin, A. Sales, R. Scheer, A. Zorzo Technical Report Series Number 049 July,
Web Load Stress Testing
 Web Load Stress Testing Overview A Web load stress test is a diagnostic tool that helps predict how a website will respond to various traffic levels. This test can answer critical questions such as: How
Web Load Stress Testing Overview A Web load stress test is a diagnostic tool that helps predict how a website will respond to various traffic levels. This test can answer critical questions such as: How
A Novel Way of Deduplication Approach for Cloud Backup Services Using Block Index Caching Technique
 A Novel Way of Deduplication Approach for Cloud Backup Services Using Block Index Caching Technique Jyoti Malhotra 1,Priya Ghyare 2 Associate Professor, Dept. of Information Technology, MIT College of
A Novel Way of Deduplication Approach for Cloud Backup Services Using Block Index Caching Technique Jyoti Malhotra 1,Priya Ghyare 2 Associate Professor, Dept. of Information Technology, MIT College of
Structure and Performance of Open Access Networks Case Lappeenranta Model
 Structure and Performance of Open Access Networks Case Lappeenranta Model M.Juutilainen, T.Lapinlampi, J.Ikonen and J.Porras Paper Title Laboratory of Communications Engineering, Lappeenranta University
Structure and Performance of Open Access Networks Case Lappeenranta Model M.Juutilainen, T.Lapinlampi, J.Ikonen and J.Porras Paper Title Laboratory of Communications Engineering, Lappeenranta University
The Role and uses of Peer-to-Peer in file-sharing. Computer Communication & Distributed Systems EDA 390
 The Role and uses of Peer-to-Peer in file-sharing Computer Communication & Distributed Systems EDA 390 Jenny Bengtsson Prarthanaa Khokar jenben@dtek.chalmers.se prarthan@dtek.chalmers.se Gothenburg, May
The Role and uses of Peer-to-Peer in file-sharing Computer Communication & Distributed Systems EDA 390 Jenny Bengtsson Prarthanaa Khokar jenben@dtek.chalmers.se prarthan@dtek.chalmers.se Gothenburg, May
BW-EML SAP Standard Application Benchmark
 BW-EML SAP Standard Application Benchmark Heiko Gerwens and Tobias Kutning (&) SAP SE, Walldorf, Germany tobas.kutning@sap.com Abstract. The focus of this presentation is on the latest addition to the
BW-EML SAP Standard Application Benchmark Heiko Gerwens and Tobias Kutning (&) SAP SE, Walldorf, Germany tobas.kutning@sap.com Abstract. The focus of this presentation is on the latest addition to the
Scalability of web applications. CSCI 470: Web Science Keith Vertanen
 Scalability of web applications CSCI 470: Web Science Keith Vertanen Scalability questions Overview What's important in order to build scalable web sites? High availability vs. load balancing Approaches
Scalability of web applications CSCI 470: Web Science Keith Vertanen Scalability questions Overview What's important in order to build scalable web sites? High availability vs. load balancing Approaches
A Topology-Aware Relay Lookup Scheme for P2P VoIP System
 Int. J. Communications, Network and System Sciences, 2010, 3, 119-125 doi:10.4236/ijcns.2010.32018 Published Online February 2010 (http://www.scirp.org/journal/ijcns/). A Topology-Aware Relay Lookup Scheme
Int. J. Communications, Network and System Sciences, 2010, 3, 119-125 doi:10.4236/ijcns.2010.32018 Published Online February 2010 (http://www.scirp.org/journal/ijcns/). A Topology-Aware Relay Lookup Scheme
Adding Advanced Caching and Replication Techniques to the Apache Web Server
 Adding Advanced Caching and Replication Techniques to the Apache Web Server Joachim Marder, Steffen Rothkugel, Peter Sturm University of Trier D-54286 Trier, Germany Email: marder@jam-software.com, sroth@uni-trier.de,
Adding Advanced Caching and Replication Techniques to the Apache Web Server Joachim Marder, Steffen Rothkugel, Peter Sturm University of Trier D-54286 Trier, Germany Email: marder@jam-software.com, sroth@uni-trier.de,
Multi-service Load Balancing in a Heterogeneous Network with Vertical Handover
 1 Multi-service Load Balancing in a Heterogeneous Network with Vertical Handover Jie Xu, Member, IEEE, Yuming Jiang, Member, IEEE, and Andrew Perkis, Member, IEEE Abstract In this paper we investigate
1 Multi-service Load Balancing in a Heterogeneous Network with Vertical Handover Jie Xu, Member, IEEE, Yuming Jiang, Member, IEEE, and Andrew Perkis, Member, IEEE Abstract In this paper we investigate
The Medusa Proxy. A Tool For Exploring User-Perceived Web Performance. Mimika Koletsou and Geoffrey M. Voelker
 The Medusa Proxy A Tool For Exploring User-Perceived Web Performance Mimika Koletsou and Geoffrey M. Voelker Department of Computer Science and Engineering University of California, San Diego 9500 Gilman
The Medusa Proxy A Tool For Exploring User-Perceived Web Performance Mimika Koletsou and Geoffrey M. Voelker Department of Computer Science and Engineering University of California, San Diego 9500 Gilman
Load Balancing on a Grid Using Data Characteristics
 Load Balancing on a Grid Using Data Characteristics Jonathan White and Dale R. Thompson Computer Science and Computer Engineering Department University of Arkansas Fayetteville, AR 72701, USA {jlw09, drt}@uark.edu
Load Balancing on a Grid Using Data Characteristics Jonathan White and Dale R. Thompson Computer Science and Computer Engineering Department University of Arkansas Fayetteville, AR 72701, USA {jlw09, drt}@uark.edu
Bloom Filter based Inter-domain Name Resolution: A Feasibility Study
 Bloom Filter based Inter-domain Name Resolution: A Feasibility Study Konstantinos V. Katsaros, Wei Koong Chai and George Pavlou University College London, UK Outline Inter-domain name resolution in ICN
Bloom Filter based Inter-domain Name Resolution: A Feasibility Study Konstantinos V. Katsaros, Wei Koong Chai and George Pavlou University College London, UK Outline Inter-domain name resolution in ICN
Performance Evaluation of Mobile Agent-based Dynamic Load Balancing Algorithm
 Performance Evaluation of Mobile -based Dynamic Load Balancing Algorithm MAGDY SAEB, CHERINE FATHY Computer Engineering Department Arab Academy for Science, Technology & Maritime Transport Alexandria,
Performance Evaluation of Mobile -based Dynamic Load Balancing Algorithm MAGDY SAEB, CHERINE FATHY Computer Engineering Department Arab Academy for Science, Technology & Maritime Transport Alexandria,
Quick Start for Network Agent. 5-Step Quick Start. What is Network Agent?
 What is Network Agent? The Websense Network Agent software component uses sniffer technology to monitor all of the internet traffic on the network machines that you assign to it. Network Agent filters
What is Network Agent? The Websense Network Agent software component uses sniffer technology to monitor all of the internet traffic on the network machines that you assign to it. Network Agent filters
HyLARD: A Hybrid Locality-Aware Request Distribution Policy in Cluster-based Web Servers
 TANET2007 臺 灣 網 際 網 路 研 討 會 論 文 集 二 HyLARD: A Hybrid Locality-Aware Request Distribution Policy in Cluster-based Web Servers Shang-Yi Zhuang, Mei-Ling Chiang Department of Information Management National
TANET2007 臺 灣 網 際 網 路 研 討 會 論 文 集 二 HyLARD: A Hybrid Locality-Aware Request Distribution Policy in Cluster-based Web Servers Shang-Yi Zhuang, Mei-Ling Chiang Department of Information Management National
High volume Internet data centers. MPLS-based Request Routing. Current dispatcher technology. MPLS-based architecture
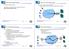 MPLS-based Request Routing High volume Internet data centers MPLS-based Request Routing Arup Acharya, Anees Shaikh, Renu Tewari, Dinesh Verma IBM TJ Watson Research Center Web server cluster + front-end
MPLS-based Request Routing High volume Internet data centers MPLS-based Request Routing Arup Acharya, Anees Shaikh, Renu Tewari, Dinesh Verma IBM TJ Watson Research Center Web server cluster + front-end
Load Balancing in Distributed Web Server Systems With Partial Document Replication
 Load Balancing in Distributed Web Server Systems With Partial Document Replication Ling Zhuo, Cho-Li Wang and Francis C. M. Lau Department of Computer Science and Information Systems The University of
Load Balancing in Distributed Web Server Systems With Partial Document Replication Ling Zhuo, Cho-Li Wang and Francis C. M. Lau Department of Computer Science and Information Systems The University of
2. Research and Development on the Autonomic Operation. Control Infrastructure Technologies in the Cloud Computing Environment
 R&D supporting future cloud computing infrastructure technologies Research and Development on Autonomic Operation Control Infrastructure Technologies in the Cloud Computing Environment DEMPO Hiroshi, KAMI
R&D supporting future cloud computing infrastructure technologies Research and Development on Autonomic Operation Control Infrastructure Technologies in the Cloud Computing Environment DEMPO Hiroshi, KAMI
Internet Content Distribution
 Internet Content Distribution Chapter 4: Content Distribution Networks (TUD Student Use Only) Chapter Outline Basics of content distribution networks (CDN) Why CDN? How do they work? Client redirection
Internet Content Distribution Chapter 4: Content Distribution Networks (TUD Student Use Only) Chapter Outline Basics of content distribution networks (CDN) Why CDN? How do they work? Client redirection
Dissertation Title: SOCKS5-based Firewall Support For UDP-based Application. Author: Fung, King Pong
 Dissertation Title: SOCKS5-based Firewall Support For UDP-based Application Author: Fung, King Pong MSc in Information Technology The Hong Kong Polytechnic University June 1999 i Abstract Abstract of dissertation
Dissertation Title: SOCKS5-based Firewall Support For UDP-based Application Author: Fung, King Pong MSc in Information Technology The Hong Kong Polytechnic University June 1999 i Abstract Abstract of dissertation
MAGENTO HOSTING Progressive Server Performance Improvements
 MAGENTO HOSTING Progressive Server Performance Improvements Simple Helix, LLC 4092 Memorial Parkway Ste 202 Huntsville, AL 35802 sales@simplehelix.com 1.866.963.0424 www.simplehelix.com 2 Table of Contents
MAGENTO HOSTING Progressive Server Performance Improvements Simple Helix, LLC 4092 Memorial Parkway Ste 202 Huntsville, AL 35802 sales@simplehelix.com 1.866.963.0424 www.simplehelix.com 2 Table of Contents
How To Create A P2P Network
 Peer-to-peer systems INF 5040 autumn 2007 lecturer: Roman Vitenberg INF5040, Frank Eliassen & Roman Vitenberg 1 Motivation for peer-to-peer Inherent restrictions of the standard client/server model Centralised
Peer-to-peer systems INF 5040 autumn 2007 lecturer: Roman Vitenberg INF5040, Frank Eliassen & Roman Vitenberg 1 Motivation for peer-to-peer Inherent restrictions of the standard client/server model Centralised
ICP. Cache Hierarchies. Squid. Squid Cache ICP Use. Squid. Squid
 Caching & CDN s 15-44: Computer Networking L-21: Caching and CDNs HTTP APIs Assigned reading [FCAB9] Summary Cache: A Scalable Wide- Area Cache Sharing Protocol [Cla00] Freenet: A Distributed Anonymous
Caching & CDN s 15-44: Computer Networking L-21: Caching and CDNs HTTP APIs Assigned reading [FCAB9] Summary Cache: A Scalable Wide- Area Cache Sharing Protocol [Cla00] Freenet: A Distributed Anonymous
Combining Client Knowledge and Resource Dependencies for Improved World Wide Web Performance
 Conferences INET NDSS Other Conferences Combining Client Knowledge and Resource Dependencies for Improved World Wide Web Performance John H. HINE Victoria University of Wellington
Conferences INET NDSS Other Conferences Combining Client Knowledge and Resource Dependencies for Improved World Wide Web Performance John H. HINE Victoria University of Wellington
Chapter 4. VoIP Metric based Traffic Engineering to Support the Service Quality over the Internet (Inter-domain IP network)
 Chapter 4 VoIP Metric based Traffic Engineering to Support the Service Quality over the Internet (Inter-domain IP network) 4.1 Introduction Traffic Engineering can be defined as a task of mapping traffic
Chapter 4 VoIP Metric based Traffic Engineering to Support the Service Quality over the Internet (Inter-domain IP network) 4.1 Introduction Traffic Engineering can be defined as a task of mapping traffic
Meeting Worldwide Demand for your Content
 Meeting Worldwide Demand for your Content Evolving to a Content Delivery Network A Lucent Technologies White Paper By L. R. Beaumont 4/25/01 Meeting Worldwide Demand for your Content White Paper Table
Meeting Worldwide Demand for your Content Evolving to a Content Delivery Network A Lucent Technologies White Paper By L. R. Beaumont 4/25/01 Meeting Worldwide Demand for your Content White Paper Table
The Effectiveness of Request Redirection on CDN Robustness
 The Effectiveness of Request Redirection on CDN Robustness Limin Wang, Vivek Pai and Larry Peterson Presented by: Eric Leshay Ian McBride Kai Rasmussen 1 Outline! Introduction! Redirection Strategies!
The Effectiveness of Request Redirection on CDN Robustness Limin Wang, Vivek Pai and Larry Peterson Presented by: Eric Leshay Ian McBride Kai Rasmussen 1 Outline! Introduction! Redirection Strategies!
Lecture 8b: Proxy Server Load Balancing
 Internet and Intranet Protocols and Applications Lecture 8b: Proxy Server Load Balancing March, 2004 Arthur Goldberg Computer Science Department New York University artg@cs.nyu.edu Load Balancing Problem:
Internet and Intranet Protocols and Applications Lecture 8b: Proxy Server Load Balancing March, 2004 Arthur Goldberg Computer Science Department New York University artg@cs.nyu.edu Load Balancing Problem:
Behavior Analysis of TCP Traffic in Mobile Ad Hoc Network using Reactive Routing Protocols
 Behavior Analysis of TCP Traffic in Mobile Ad Hoc Network using Reactive Routing Protocols Purvi N. Ramanuj Department of Computer Engineering L.D. College of Engineering Ahmedabad Hiteishi M. Diwanji
Behavior Analysis of TCP Traffic in Mobile Ad Hoc Network using Reactive Routing Protocols Purvi N. Ramanuj Department of Computer Engineering L.D. College of Engineering Ahmedabad Hiteishi M. Diwanji
Multi-Datacenter Replication
 www.basho.com Multi-Datacenter Replication A Technical Overview & Use Cases Table of Contents Table of Contents... 1 Introduction... 1 How It Works... 1 Default Mode...1 Advanced Mode...2 Architectural
www.basho.com Multi-Datacenter Replication A Technical Overview & Use Cases Table of Contents Table of Contents... 1 Introduction... 1 How It Works... 1 Default Mode...1 Advanced Mode...2 Architectural
VXLAN: Scaling Data Center Capacity. White Paper
 VXLAN: Scaling Data Center Capacity White Paper Virtual Extensible LAN (VXLAN) Overview This document provides an overview of how VXLAN works. It also provides criteria to help determine when and where
VXLAN: Scaling Data Center Capacity White Paper Virtual Extensible LAN (VXLAN) Overview This document provides an overview of how VXLAN works. It also provides criteria to help determine when and where
Tornado: A Capability-Aware Peer-to-Peer Storage Network
 Tornado: A Capability-Aware Peer-to-Peer Storage Network Hung-Chang Hsiao hsiao@pads1.cs.nthu.edu.tw Chung-Ta King* king@cs.nthu.edu.tw Department of Computer Science National Tsing Hua University Hsinchu,
Tornado: A Capability-Aware Peer-to-Peer Storage Network Hung-Chang Hsiao hsiao@pads1.cs.nthu.edu.tw Chung-Ta King* king@cs.nthu.edu.tw Department of Computer Science National Tsing Hua University Hsinchu,
Document distribution algorithm for load balancing on an extensible Web server architecture
 Title Document distribution algorithm for load balancing on an extensible Web server architecture Author(s) Ng, CP; Wang, CL Citation The 1st IEEE / ACM International Symposium on Cluster Computing and
Title Document distribution algorithm for load balancing on an extensible Web server architecture Author(s) Ng, CP; Wang, CL Citation The 1st IEEE / ACM International Symposium on Cluster Computing and
A Time Efficient Algorithm for Web Log Analysis
 A Time Efficient Algorithm for Web Log Analysis Santosh Shakya Anju Singh Divakar Singh Student [M.Tech.6 th sem (CSE)] Asst.Proff, Dept. of CSE BU HOD (CSE), BUIT, BUIT,BU Bhopal Barkatullah University,
A Time Efficient Algorithm for Web Log Analysis Santosh Shakya Anju Singh Divakar Singh Student [M.Tech.6 th sem (CSE)] Asst.Proff, Dept. of CSE BU HOD (CSE), BUIT, BUIT,BU Bhopal Barkatullah University,
A Study on the Application of Existing Load Balancing Algorithms for Large, Dynamic, Heterogeneous Distributed Systems
 A Study on the Application of Existing Load Balancing Algorithms for Large, Dynamic, Heterogeneous Distributed Systems RUPAM MUKHOPADHYAY, DIBYAJYOTI GHOSH AND NANDINI MUKHERJEE Department of Computer
A Study on the Application of Existing Load Balancing Algorithms for Large, Dynamic, Heterogeneous Distributed Systems RUPAM MUKHOPADHYAY, DIBYAJYOTI GHOSH AND NANDINI MUKHERJEE Department of Computer
