Owner of the content within this article is Written by Marc Grote
|
|
|
- Meryl Banks
- 8 years ago
- Views:
Transcription
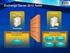
1 Owner of the content within this article is Written by Marc Grote Microsoft Forefront TMG Using the BranchCache feature in Forefront TMG SP1 Abstract In this article I will show you one of the new features in Forefront TMG Service Pack 1 called BranchCache in Hosted Mode. Let s begin Forefront TMG SP1 supports configuring the Server as a BranchCache Server in Hosted Mode. BranchCache is not used exclusively with Forefront TMG. BranchCache is a feature first introduced in Windows Server 2008 R2 and Windows 7 which use techniques to reduce the amount of data transferred from the Headquarter to the Branch Office through a WAN link. BranchCache provides two operation modes: Distributed Cache Hosted Cache Distributed Cache The Distributed Cache feature is great for small Branch Office without a dedicated Server. The BranchCache will be distributed between several Windows 7 clients, where every Windows 7 client hosts part of the BranchCache content. Hosted Cache In the Hosted Cache Mode there is a dedicated Server which hosts the cached content of the BranchCache. Every Windows 7 client in the BranchOffice can participate from the central cache in Hosted Cache mode. The Hosted Cache mode operates by deploying a computer that is running Windows Server 2008 R2 as a host in the Branch Office. If the content is not available in the Hosted Cache, it is retrieved from the content server by using the WAN. The Hosted Cache Mode server stores the content locally so that subsequent client computers can benefit from the Hosted cache again. To deploy BranchCache in Hosted Cache mode, you must install and configure content servers in your main office, and install and configure a Hosted Cache server and client computers in your branch office. Note: Forefront TMG SP1 can only be configured to operate in Hosted Cache Mode.
2 Activating BranchCache on Forefront TMG SP1 BranchCache in Hosted Cache mode can be activated in the Forefront TMG Management console. Navigate to the Firewall policy node and on the Task pane click Configure BranchCache and enable BranchCache in Hosted Cache mode. Figure 1: Configuring BranchCache Hosted Cache authentication The Hosted Cache is trusted by client computers to cache and distribute data that may be under access control to prevent executing and reading the data. To enhance the security, Windows 7 client computers use Transport Layer Security (TLS) when communicating with the Hosted Cache server. To support a TLS connection, Forefront TMG must have a certificate that is trusted by clients and the Extended Key Usage (EKU) must be server authentication. So the next step is to issue a Computer certificate from an internal certification authority (CA) which is trusted by all domain members. For the certificate in this article we are using the MMC on the Forefront TMG Server to request a certificate with the Computer certificate template. The Common Name (CN) of the certificate is the FQDN of the Forefront TMG Server.
3 Figure 2: Requesting a certificate for BranchCache After the certificate is issued and stored in the certificate store of the local computer, we can use the certificate to encrypt the data transfer from the Hosted Cache. Selected the certificate and if you only want to allow clients from the same Windows domain to access the Hosted Cache, activate the checkbox, as shown in the following picture. Figure 3: Select the certificate for BranchCache
4 BranchCache in Hosted Mode store the content of the Hosted Cache on the disk of Forefront TMG. I recommend using a dedicated volume or disk for Hosted Cache content and not the default folder. If you use a dedicated volume or disk you can also increase the percentage storage used for the Hosted Cache. The default value is 5 percent and I increased the percentage to 90 percent to keep 10 percent as a reserve. Figure 4: Select the location for BranchCache content and the Percentage of disk space used for Hosted Cache. NIS Inspection and BranchCache The next step is optional but very important in my opinion if you use the Network Inspection System (NIS) feature in Forefront TMG. TMG is a vulnerability-based Intrusion Prevention System (IPS). An IPS should protect your internal network from known and unknown vulnerabilities if TMG is being used directly on the edge of the internal network on the Internet. All network traffic must flow through TMG, so TMG is the first line of defense to protect against different vulnerabilities. TMG NIS IPS features block un/known attacks at the network level to fight against vulnerabilities. TMG uses a signature based IPS. A signature based IPS protects your hosts against exploitation of vulnerabilities which are found. A signature based IPS is used to close the time window between an announcement of vulnerability and the patch deployment of all possible vulnerable hosts. When NIS is enabled all traffic gets inspected, including traffic destined explicitly to the host or originating from the host. As a result, it may be possible that users may experience an increased latency when retrieving objects from the Hosted Cache server. To improve the performance it is possible to disable NIS for traffic from or to the Host to disable NIS for traffic to the host or originating from the host. Attention: Disabling NIS in Forefront TMG decrease the protection mechanism of Forefront
5 TMG. You will find more information about possible security impacts in the guide for implementing BranchCache with Forefront TMG. You will find a link to this guide at the end of this article. With the following registry key it is possible to disable the NIS traffic inspection of the Localhost: HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\RAT\Stingray\Debug\IPS\IPS_LO CALHOST_INSPECTION_MODE Set the value to 0. After that you must reapply the Forefront TMG policy. Next we have to change the BranchCache protocols default port numbers (from port 80 and 443) to custom port numbers. By default NIS inspects only HTTP and HTTPS on Localhost traffic. To retain inspection for non-related Branchcache traffic without impacting BranchCache performance it is required that the BranchCache default ports are changed to another available port. Firewall Rules for BranchCache By default, Forefront TMG blocks most traffic that is destined explicitly to the Forefront TMG Server or originating from the TMG Server, so we have to modify the Forefront TMG Firewall rules to allow BranchCache traffic because BranchCache is operating in Hosted Mode on the Forefront TMG Server. A BranchCache client initiates a connection to the Forefront TMG Server with the Hosted Cache Protocol (PCHC Port 443). The Hosted cache Server will initiate a new connection using the Retrieval protocol (PCCRR Port 80) to retrieve the data from the client. After that the data is now cached on the Hosted Cache Server. Another BranchCache client that needs to retrieve data from the Hosted Cache will initiate the Retrieval protocol (PCCRR) and retrieve content from the Hosted Cache. To allow this communication you must define two Forefront TMG policy rules: Allow Hosted Cache Inbound Connections Allow Hosted Cache Outbound Connections Allow Hosted Cache Inbound Connections This Firewall rule allows BranchCache clients to advertise new content to the Hosted Cache Server and retrieve data from the Hosted Cache Server. Allow Hosted Cache Outbound Connections This Firewall rule allows the Hosted Cache Server to retrieve advertised content from the BranchCache client. The actual ports that are used by the BranchCache clients are stored in the Registry of the client. The Registry keys are located here: For the Retrieval port (Default is Port 80) HKEY_LOCAL_MACHINE\Software\Microsoft\WindowsNT\CurrentVersion\PeerDist\ DownloadManager\Peers\Connection For the Hosted Cache port (Default is 443)
6 HKEY_LOCAL_MACHINE\Software\Microsoft\Windows NT\CurrentVersion\PeerDist\HostedCache\Connection Next we have to create the Firewall rules on Forefront TMG. You will see the Firewall protocol defintions in the following picture. After the new Protocol definitions have been created we must create two new Firewall rules which allows traffic for these protocol definitions from the internal network to the Localhost Network and vice versa. Figure 5: Firewall Protocol rules for BranchCache Figure 6: firewall rules for BranchCache Click Apply to save the configuration changes to the Forefront TMG storage. Monitoring BranchCache There are many ways to monitor the BranchCache efficiency. One way is to use a new monitoring option in the Forefront TMG dashboard as shown in the following picture. Another way is to use the built-in Performance Monitor counters for BranchCache of Windows Server 2008 R2.
7 Figure 7: Monitoring BranchCache BranchCache Performance Counter Windows Server 2008 R2 comes with a lot of built-in Performance Counters to monitor the efficiency of the BranchCache feature on Forefront TMG. You will need to monitor these Performance Counters from time to time to make changes when the efficiency of the BranchCache doesn t fulfill your needs. To monitor the BranchCache performance start the Windows Server 2008 R2 Performance Monitor and select the BranchCache counters and add the Performance Counters to be monitored. Figure 8: Performance Counters for BranchCache Conclusion
8 In this article I tried to show you how to configure Microsoft Forefront TMG SP1 as a Hosted Server for BranchCache. With the help of the BranchCache feature you can use Forefront TMG without an additional Server or Server feature to fulfill the requests for Branch Office to get the most updated content directly from the Forefront TMG Server without overloading the WAN link. With the help of Forefront TMG it is easy to implement an integrated BranchCache solution which is also easy to monitor with the built-in Forefront TMG dashboard or the integrated Performance Monitor counters from Windows Server 2008 R2. Related links Planning for BranchCache (SP1) Performance Counters Explaining and configuring NIS (Network Inspection Service) Service.html
Owner of the content within this article is www.isaserver.org Written by Marc Grote www.it-training-grote.de
 Owner of the content within this article is www.isaserver.org Written by Marc Grote www.it-training-grote.de Overview about the Microsoft Reputation Service (MRS), Microsoft Malware Protection Center (MMPC)
Owner of the content within this article is www.isaserver.org Written by Marc Grote www.it-training-grote.de Overview about the Microsoft Reputation Service (MRS), Microsoft Malware Protection Center (MMPC)
Owner of the content within this article is www.isaserver.org Written by Marc Grote www.it-training-grote.de
 Owner of the content within this article is www.isaserver.org Written by Marc Grote www.it-training-grote.de Microsoft Forefront TMG How to use SQL Server 2008 Express Reporting Services Abstract In this
Owner of the content within this article is www.isaserver.org Written by Marc Grote www.it-training-grote.de Microsoft Forefront TMG How to use SQL Server 2008 Express Reporting Services Abstract In this
Owner of the content within this article is www.isaserver.org Written by Marc Grote www.it-training-grote.de
 Owner of the content within this article is www.isaserver.org Written by Marc Grote www.it-training-grote.de Microsoft Forefront TMG Role based Administration Abstract In this article I will show you how
Owner of the content within this article is www.isaserver.org Written by Marc Grote www.it-training-grote.de Microsoft Forefront TMG Role based Administration Abstract In this article I will show you how
Owner of the content within this article is www.isaserver.org Written by Marc Grote www.it-training-grote.de
 Owner of the content within this article is www.isaserver.org Written by Marc Grote www.it-training-grote.de Microsoft Forefront TMG Publishing RD Web Access with RD Gateway Part II Abstract In this short
Owner of the content within this article is www.isaserver.org Written by Marc Grote www.it-training-grote.de Microsoft Forefront TMG Publishing RD Web Access with RD Gateway Part II Abstract In this short
Owner of the content within this article is www.isaserver.org Written by Marc Grote www.it-training-grote.de
 Owner of the content within this article is www.isaserver.org Written by Marc Grote www.it-training-grote.de Microsoft Forefront TMG Webserver Load Balancing Abstract In this article I will show you how
Owner of the content within this article is www.isaserver.org Written by Marc Grote www.it-training-grote.de Microsoft Forefront TMG Webserver Load Balancing Abstract In this article I will show you how
Owner of the content within this article is www.isaserver.org Written by Marc Grote www.it-training-grote.de
 Owner of the content within this article is www.isaserver.org Written by Marc Grote www.it-training-grote.de Microsoft Forefront TMG Logging options in Forefront TMG Abstract In this article I will show
Owner of the content within this article is www.isaserver.org Written by Marc Grote www.it-training-grote.de Microsoft Forefront TMG Logging options in Forefront TMG Abstract In this article I will show
How To Configure Forefront Threat Management Gateway (Forefront) For An Email Server
 Owner of the content within this article is www.isaserver.org Written by Marc Grote www.it-training-grote.de Configuring and using the E-Mail protection feature in Microsoft Forefront Threat Management
Owner of the content within this article is www.isaserver.org Written by Marc Grote www.it-training-grote.de Configuring and using the E-Mail protection feature in Microsoft Forefront Threat Management
How to Create a Forefront UAG Portport
 Owner of the content within this article is www.isaserver.org Written by Marc Grote www.it-training-grote.de Publish Remote Desktop Services RemoteApp with Forefront UAG Abstract In this article we will
Owner of the content within this article is www.isaserver.org Written by Marc Grote www.it-training-grote.de Publish Remote Desktop Services RemoteApp with Forefront UAG Abstract In this article we will
Configuring Security for FTP Traffic
 2 Configuring Security for FTP Traffic Securing FTP traffic Creating a security profile for FTP traffic Configuring a local traffic FTP profile Assigning an FTP security profile to a local traffic FTP
2 Configuring Security for FTP Traffic Securing FTP traffic Creating a security profile for FTP traffic Configuring a local traffic FTP profile Assigning an FTP security profile to a local traffic FTP
Owner of the content within this article is www.isaserver.org Written by Marc Grote www.it-training-grote.de
 Owner of the content within this article is www.isaserver.org Written by Marc Grote www.it-training-grote.de Microsoft Forefront TMG How to use TMG network templates Abstract In this article I will show
Owner of the content within this article is www.isaserver.org Written by Marc Grote www.it-training-grote.de Microsoft Forefront TMG How to use TMG network templates Abstract In this article I will show
the client omits the BranchCache identifier from the request message.
 Office Clients Distributed Cache Mode Step 3. Multicast with Metadata Step 4. No Replies Office Client Remote Server Hosted Cache Mode Step 3. Forwarded Metadata Step 4. Negative Reply Office Server 5.
Office Clients Distributed Cache Mode Step 3. Multicast with Metadata Step 4. No Replies Office Client Remote Server Hosted Cache Mode Step 3. Forwarded Metadata Step 4. Negative Reply Office Server 5.
RSA SecurID Ready Implementation Guide
 RSA SecurID Ready Implementation Guide Partner Information Last Modified: December 18, 2006 Product Information Partner Name Microsoft Web Site http://www.microsoft.com/isaserver Product Name Internet
RSA SecurID Ready Implementation Guide Partner Information Last Modified: December 18, 2006 Product Information Partner Name Microsoft Web Site http://www.microsoft.com/isaserver Product Name Internet
How to use mobilecho with Microsoft Forefront Threat Management Gateway (TMG)
 How to use mobilecho with Microsoft Forefront Threat Management Gateway (TMG) Introduction Understanding Forefront Threat Management Gateway (TMG) Network Topology Understanding Forefront Threat Management
How to use mobilecho with Microsoft Forefront Threat Management Gateway (TMG) Introduction Understanding Forefront Threat Management Gateway (TMG) Network Topology Understanding Forefront Threat Management
RSA SecurID Ready Implementation Guide
 RSA SecurID Ready Implementation Guide Partner Information Last Modified: December 18, 2006 Product Information Partner Name Microsoft Web Site http://www.microsoft.com/isaserver Product Name Internet
RSA SecurID Ready Implementation Guide Partner Information Last Modified: December 18, 2006 Product Information Partner Name Microsoft Web Site http://www.microsoft.com/isaserver Product Name Internet
Owner of the content within this article is www.isaserver.org Written by Marc Grote www.it-training-grote.de
 Owner of the content within this article is www.isaserver.org Written by Marc Grote www.it-training-grote.de Advanced Forefront TMG debugging Abstract This article will show you how to collect advanced
Owner of the content within this article is www.isaserver.org Written by Marc Grote www.it-training-grote.de Advanced Forefront TMG debugging Abstract This article will show you how to collect advanced
Forefront UAG Monitoring and Network Traffic Control
 Owner of the content within this article is www.isaserver.org Written by Marc Grote www.it-training-grote.de Microsoft Forefront UAG Forefront UAG monitoring and debugging part I Abstract This is a two
Owner of the content within this article is www.isaserver.org Written by Marc Grote www.it-training-grote.de Microsoft Forefront UAG Forefront UAG monitoring and debugging part I Abstract This is a two
RSA Security Analytics
 RSA Security Analytics Event Source Log Configuration Guide Microsoft Windows using Eventing Collection Last Modified: Thursday, July 30, 2015 Event Source Product Information: Vendor: Microsoft Event
RSA Security Analytics Event Source Log Configuration Guide Microsoft Windows using Eventing Collection Last Modified: Thursday, July 30, 2015 Event Source Product Information: Vendor: Microsoft Event
Configuring Personal Firewalls and Understanding IDS. Securing Networks Chapter 3 Part 2 of 4 CA M S Mehta, FCA
 Configuring Personal Firewalls and Understanding IDS Securing Networks Chapter 3 Part 2 of 4 CA M S Mehta, FCA 1 Configuring Personal Firewalls and IDS Learning Objectives Task Statements 1.4 Analyze baseline
Configuring Personal Firewalls and Understanding IDS Securing Networks Chapter 3 Part 2 of 4 CA M S Mehta, FCA 1 Configuring Personal Firewalls and IDS Learning Objectives Task Statements 1.4 Analyze baseline
Windows Server on WAAS: Reduce Branch-Office Cost and Complexity with WAN Optimization and Secure, Reliable Local IT Services
 Windows Server on WAAS: Reduce Branch-Office Cost and Complexity with WAN Optimization and Secure, Reliable Local IT Services What You Will Learn Windows Server on WAAS reduces the cost and complexity
Windows Server on WAAS: Reduce Branch-Office Cost and Complexity with WAN Optimization and Secure, Reliable Local IT Services What You Will Learn Windows Server on WAAS reduces the cost and complexity
Configuring Security for SMTP Traffic
 4 Configuring Security for SMTP Traffic Securing SMTP traffic Creating a security profile for SMTP traffic Configuring a local traffic SMTP profile Assigning an SMTP security profile to a local traffic
4 Configuring Security for SMTP Traffic Securing SMTP traffic Creating a security profile for SMTP traffic Configuring a local traffic SMTP profile Assigning an SMTP security profile to a local traffic
Owner of the content within this article is www.isaserver.org Written by Marc Grote www.it-training-grote.de
 Owner of the content within this article is www.isaserver.org Written by Marc Grote www.it-training-grote.de Configuring the Forefront TMG HTTP Filter Abstract In this article I will show you how to configure
Owner of the content within this article is www.isaserver.org Written by Marc Grote www.it-training-grote.de Configuring the Forefront TMG HTTP Filter Abstract In this article I will show you how to configure
Enabling Users for Lync services
 Enabling Users for Lync services 1) Login to collaborate.widevoice Server as admin user 2) Open Lync Server control Panel as Run As Administrator 3) Click on Users option and click Enable Users option
Enabling Users for Lync services 1) Login to collaborate.widevoice Server as admin user 2) Open Lync Server control Panel as Run As Administrator 3) Click on Users option and click Enable Users option
Many network and firewall administrators consider the network firewall at the network edge as their primary defense against all network woes.
 RimApp RoadBLOCK goes beyond simple filtering! Many network and firewall administrators consider the network firewall at the network edge as their primary defense against all network woes. However, traditional
RimApp RoadBLOCK goes beyond simple filtering! Many network and firewall administrators consider the network firewall at the network edge as their primary defense against all network woes. However, traditional
Owner of the content within this article is www.isaserver.org Written by Marc Grote www.it-training-grote.de
 Owner of the content within this article is www.isaserver.org Written by Marc Grote www.it-training-grote.de Troubleshooting Forefront TMG Abstract In this article I will show you some helpful Forefront
Owner of the content within this article is www.isaserver.org Written by Marc Grote www.it-training-grote.de Troubleshooting Forefront TMG Abstract In this article I will show you some helpful Forefront
Decryption. Palo Alto Networks. PAN-OS Administrator s Guide Version 6.0. Copyright 2007-2015 Palo Alto Networks
 Decryption Palo Alto Networks PAN-OS Administrator s Guide Version 6.0 Contact Information Corporate Headquarters: Palo Alto Networks 4401 Great America Parkway Santa Clara, CA 95054 www.paloaltonetworks.com/company/contact-us
Decryption Palo Alto Networks PAN-OS Administrator s Guide Version 6.0 Contact Information Corporate Headquarters: Palo Alto Networks 4401 Great America Parkway Santa Clara, CA 95054 www.paloaltonetworks.com/company/contact-us
NSi Mobile Installation Guide. Version 6.2
 NSi Mobile Installation Guide Version 6.2 Revision History Version Date 1.0 October 2, 2012 2.0 September 18, 2013 2 CONTENTS TABLE OF CONTENTS PREFACE... 5 Purpose of this Document... 5 Version Compatibility...
NSi Mobile Installation Guide Version 6.2 Revision History Version Date 1.0 October 2, 2012 2.0 September 18, 2013 2 CONTENTS TABLE OF CONTENTS PREFACE... 5 Purpose of this Document... 5 Version Compatibility...
Step-By-Step Guide to Deploying Lync Server 2010 Enterprise Edition
 Step-By-Step Guide to Deploying Lync Server 2010 Enterprise Edition The installation of Lync Server 2010 is a fairly task-intensive process. In this article, I will walk you through each of the tasks,
Step-By-Step Guide to Deploying Lync Server 2010 Enterprise Edition The installation of Lync Server 2010 is a fairly task-intensive process. In this article, I will walk you through each of the tasks,
Owner of the content within this article is www.isaserver.org Written by Marc Grote www.it-training-grote.de
 Owner of the content within this article is www.isaserver.org Written by Marc Grote www.it-training-grote.de Microsoft Forefront TMG Publishing RD Web Access with RD Gateway Part one Abstract In this short
Owner of the content within this article is www.isaserver.org Written by Marc Grote www.it-training-grote.de Microsoft Forefront TMG Publishing RD Web Access with RD Gateway Part one Abstract In this short
GFI Product Manual. Administration and Configuration Manual
 GFI Product Manual Administration and Configuration Manual http://www.gfi.com info@gfi.com The information and content in this document is provided for informational purposes only and is provided "as is"
GFI Product Manual Administration and Configuration Manual http://www.gfi.com info@gfi.com The information and content in this document is provided for informational purposes only and is provided "as is"
Installation and configuration guide
 Installation and Configuration Guide Installation and configuration guide Adding X-Forwarded-For support to Forward and Reverse Proxy TMG Servers Published: May 2010 Applies to: Winfrasoft X-Forwarded-For
Installation and Configuration Guide Installation and configuration guide Adding X-Forwarded-For support to Forward and Reverse Proxy TMG Servers Published: May 2010 Applies to: Winfrasoft X-Forwarded-For
Hyper-V Replica Essentials
 Hyper-V Replica Essentials Vangel Krstevski Chapter No. 3 "Configuring Hyper-V Replica" In this package, you will find: A Biography of the author of the book A preview chapter from the book, Chapter NO.3
Hyper-V Replica Essentials Vangel Krstevski Chapter No. 3 "Configuring Hyper-V Replica" In this package, you will find: A Biography of the author of the book A preview chapter from the book, Chapter NO.3
User Manual. Onsight Management Suite Version 5.1. Another Innovation by Librestream
 User Manual Onsight Management Suite Version 5.1 Another Innovation by Librestream Doc #: 400075-06 May 2012 Information in this document is subject to change without notice. Reproduction in any manner
User Manual Onsight Management Suite Version 5.1 Another Innovation by Librestream Doc #: 400075-06 May 2012 Information in this document is subject to change without notice. Reproduction in any manner
ISA 2006 Array Step by step configuration guide
 ISA 2006 Array Step by step configuration guide Index Preface... 2 Step 1, Install Configuration Storage Server... 3 Step 2, Create an array... 5 Step 3, Install your ISA servers... 9 Step 4, Configure
ISA 2006 Array Step by step configuration guide Index Preface... 2 Step 1, Install Configuration Storage Server... 3 Step 2, Create an array... 5 Step 3, Install your ISA servers... 9 Step 4, Configure
Setting Up SSL on IIS6 for MEGA Advisor
 Setting Up SSL on IIS6 for MEGA Advisor Revised: July 5, 2012 Created: February 1, 2008 Author: Melinda BODROGI CONTENTS Contents... 2 Principle... 3 Requirements... 4 Install the certification authority
Setting Up SSL on IIS6 for MEGA Advisor Revised: July 5, 2012 Created: February 1, 2008 Author: Melinda BODROGI CONTENTS Contents... 2 Principle... 3 Requirements... 4 Install the certification authority
Monitoring SharePoint 2007/2010/2013 Server Using Event Tracker
 Monitoring SharePoint 2007/2010/2013 Server Using Event Tracker White Paper Publication Date: June 2012 EventTracker 8815 Centre Park Drive Columbia MD 21045 www.eventtracker.com Overview EventTracker
Monitoring SharePoint 2007/2010/2013 Server Using Event Tracker White Paper Publication Date: June 2012 EventTracker 8815 Centre Park Drive Columbia MD 21045 www.eventtracker.com Overview EventTracker
Network Configuration Settings
 Network Configuration Settings Many small businesses already have an existing firewall device for their local network when they purchase Microsoft Windows Small Business Server 2003. Often, these devices
Network Configuration Settings Many small businesses already have an existing firewall device for their local network when they purchase Microsoft Windows Small Business Server 2003. Often, these devices
Grandstream Networks, Inc. UCM6100 Security Manual
 Grandstream Networks, Inc. UCM6100 Security Manual Index Table of Contents OVERVIEW... 3 WEB UI ACCESS... 4 UCM6100 HTTP SERVER ACCESS... 4 PROTOCOL TYPE... 4 USER LOGIN... 4 LOGIN TIMEOUT... 5 TWO-LEVEL
Grandstream Networks, Inc. UCM6100 Security Manual Index Table of Contents OVERVIEW... 3 WEB UI ACCESS... 4 UCM6100 HTTP SERVER ACCESS... 4 PROTOCOL TYPE... 4 USER LOGIN... 4 LOGIN TIMEOUT... 5 TWO-LEVEL
Best Practice Configurations for OfficeScan (OSCE) 10.6
 Best Practice Configurations for OfficeScan (OSCE) 10.6 Applying Latest Patch(es) for OSCE 10.6 To find out the latest patches for OfficeScan, click here. Enable Smart Clients 1. Ensure that Officescan
Best Practice Configurations for OfficeScan (OSCE) 10.6 Applying Latest Patch(es) for OSCE 10.6 To find out the latest patches for OfficeScan, click here. Enable Smart Clients 1. Ensure that Officescan
Application Notes for Microsoft Office Communicator Clients with Avaya Communication Manager Phones - Issue 1.1
 Avaya Solution & Interoperability Test Lab Application Notes for Microsoft Office Communicator Clients with Avaya Communication Manager Phones - Issue 1.1 Abstract These Application Notes describe the
Avaya Solution & Interoperability Test Lab Application Notes for Microsoft Office Communicator Clients with Avaya Communication Manager Phones - Issue 1.1 Abstract These Application Notes describe the
How To Load balance traffic of Mail server hosted in the Internal network and redirect traffic over preferred Interface
 How To Load balance traffic of Mail server hosted in the Internal network and redirect traffic over preferred Interface How To Configure load sharing and redirect mail server traffic over preferred Gateway
How To Load balance traffic of Mail server hosted in the Internal network and redirect traffic over preferred Interface How To Configure load sharing and redirect mail server traffic over preferred Gateway
This article describes a detailed configuration example that demonstrates how to configure Cyberoam to provide the access of internal resources.
 How To Configure Port Forwarding using Virtual Host to access devices on Internal network Applicable to versions 9.5.3 build 14 or above This article describes a detailed configuration example that demonstrates
How To Configure Port Forwarding using Virtual Host to access devices on Internal network Applicable to versions 9.5.3 build 14 or above This article describes a detailed configuration example that demonstrates
Deploying the BIG-IP LTM with. Citrix XenApp. Deployment Guide Version 1.2. What s inside: 2 Prerequisites and configuration notes
 Deployment Guide Version 1.2 Deploying the BIG-IP LTM with What s inside: 2 Prerequisites and configuration notes 3 Configuration Worksheet 4 Using the BIG-IP LTM Application Template for 8 Modifying the
Deployment Guide Version 1.2 Deploying the BIG-IP LTM with What s inside: 2 Prerequisites and configuration notes 3 Configuration Worksheet 4 Using the BIG-IP LTM Application Template for 8 Modifying the
Caching SMB Data for Offline Access and an Improved Online Experience
 Caching SMB Data for Offline Access and an Improved Online Experience Agenda What is Offline Files How does Offline Files interact with SMB Offline Files enhancements for Windows 7 Questions 2 What is
Caching SMB Data for Offline Access and an Improved Online Experience Agenda What is Offline Files How does Offline Files interact with SMB Offline Files enhancements for Windows 7 Questions 2 What is
Edge Configuration Series Reporting Overview
 Reporting Edge Configuration Series Reporting Overview The Reporting portion of the Edge appliance provides a number of enhanced network monitoring and reporting capabilities. WAN Reporting Provides detailed
Reporting Edge Configuration Series Reporting Overview The Reporting portion of the Edge appliance provides a number of enhanced network monitoring and reporting capabilities. WAN Reporting Provides detailed
Desktop Surveillance Help
 Desktop Surveillance Help Table of Contents About... 9 What s New... 10 System Requirements... 11 Updating from Desktop Surveillance 2.6 to Desktop Surveillance 3.2... 13 Program Structure... 14 Getting
Desktop Surveillance Help Table of Contents About... 9 What s New... 10 System Requirements... 11 Updating from Desktop Surveillance 2.6 to Desktop Surveillance 3.2... 13 Program Structure... 14 Getting
OVERVIEW OF TYPICAL WINDOWS SERVER ROLES
 OVERVIEW OF TYPICAL WINDOWS SERVER ROLES Before you start Objectives: learn about common server roles which can be used in Windows environment. Prerequisites: no prerequisites. Key terms: network, server,
OVERVIEW OF TYPICAL WINDOWS SERVER ROLES Before you start Objectives: learn about common server roles which can be used in Windows environment. Prerequisites: no prerequisites. Key terms: network, server,
Configuring Security Features of Session Recording
 Configuring Security Features of Session Recording Summary This article provides information about the security features of Citrix Session Recording and outlines the process of configuring Session Recording
Configuring Security Features of Session Recording Summary This article provides information about the security features of Citrix Session Recording and outlines the process of configuring Session Recording
F-Secure Messaging Security Gateway. Deployment Guide
 F-Secure Messaging Security Gateway Deployment Guide TOC F-Secure Messaging Security Gateway Contents Chapter 1: Deploying F-Secure Messaging Security Gateway...3 1.1 The typical product deployment model...4
F-Secure Messaging Security Gateway Deployment Guide TOC F-Secure Messaging Security Gateway Contents Chapter 1: Deploying F-Secure Messaging Security Gateway...3 1.1 The typical product deployment model...4
Deploy Remote Desktop Gateway on the AWS Cloud
 Deploy Remote Desktop Gateway on the AWS Cloud Mike Pfeiffer April 2014 Last updated: May 2015 (revisions) Table of Contents Abstract... 3 Before You Get Started... 3 Three Ways to Use this Guide... 4
Deploy Remote Desktop Gateway on the AWS Cloud Mike Pfeiffer April 2014 Last updated: May 2015 (revisions) Table of Contents Abstract... 3 Before You Get Started... 3 Three Ways to Use this Guide... 4
7.1. Remote Access Connection
 7.1. Remote Access Connection When a client uses a dial up connection, it connects to the remote access server across the telephone system. Windows client and server operating systems use the Point to
7.1. Remote Access Connection When a client uses a dial up connection, it connects to the remote access server across the telephone system. Windows client and server operating systems use the Point to
How to configure SSL proxying in Zorp 3 F5
 How to configure SSL proxying in Zorp 3 F5 June 14, 2013 This tutorial describes how to configure Zorp to proxy SSL traffic Copyright 1996-2013 BalaBit IT Security Ltd. Table of Contents 1. Preface...
How to configure SSL proxying in Zorp 3 F5 June 14, 2013 This tutorial describes how to configure Zorp to proxy SSL traffic Copyright 1996-2013 BalaBit IT Security Ltd. Table of Contents 1. Preface...
Networking for Caribbean Development
 Networking for Caribbean Development BELIZE NOV 2 NOV 6, 2015 w w w. c a r i b n o g. o r g N E T W O R K I N G F O R C A R I B B E A N D E V E L O P M E N T BELIZE NOV 2 NOV 6, 2015 w w w. c a r i b n
Networking for Caribbean Development BELIZE NOV 2 NOV 6, 2015 w w w. c a r i b n o g. o r g N E T W O R K I N G F O R C A R I B B E A N D E V E L O P M E N T BELIZE NOV 2 NOV 6, 2015 w w w. c a r i b n
Deploying F5 to Replace Microsoft TMG or ISA Server
 Deploying F5 to Replace Microsoft TMG or ISA Server Welcome to the F5 deployment guide for configuring the BIG-IP system as a forward and reverse proxy, enabling you to remove or relocate gateway security
Deploying F5 to Replace Microsoft TMG or ISA Server Welcome to the F5 deployment guide for configuring the BIG-IP system as a forward and reverse proxy, enabling you to remove or relocate gateway security
SAFE-T RSACCESS REPLACEMENT FOR MICROSOFT FOREFRONT UNIFIED ACCESS GATEWAY (UAG)
 SAFE-T RSACCESS REPLACEMENT FOR MICROSOFT FOREFRONT UNIFIED ACCESS GATEWAY (UAG) A RSACCESS WHITE PAPER 1 Microsoft Forefront Unified Access Gateway Overview 2 Safe-T RSAccess Secure Front-end Overview
SAFE-T RSACCESS REPLACEMENT FOR MICROSOFT FOREFRONT UNIFIED ACCESS GATEWAY (UAG) A RSACCESS WHITE PAPER 1 Microsoft Forefront Unified Access Gateway Overview 2 Safe-T RSAccess Secure Front-end Overview
Installation Guide. . All right reserved. For more information about Specops Deploy and other Specops products, visit www.specopssoft.
 . All right reserved. For more information about Specops Deploy and other Specops products, visit www.specopssoft.com Copyright and Trademarks Specops Deploy is a trademark owned by Specops Software. All
. All right reserved. For more information about Specops Deploy and other Specops products, visit www.specopssoft.com Copyright and Trademarks Specops Deploy is a trademark owned by Specops Software. All
Hosting more than one FortiOS instance on. VLANs. 1. Network topology
 Hosting more than one FortiOS instance on a single FortiGate unit using VDOMs and VLANs 1. Network topology Use Virtual domains (VDOMs) to divide the FortiGate unit into two or more virtual instances of
Hosting more than one FortiOS instance on a single FortiGate unit using VDOMs and VLANs 1. Network topology Use Virtual domains (VDOMs) to divide the FortiGate unit into two or more virtual instances of
Enable SSL for Apollo 2015
 Enable SSL for Apollo 2015 [1] Obtain proper SSL certificate *.pfx (contains both certificate and private keys) For example, the pfx file contains both certificate and private keys, also the ascii file
Enable SSL for Apollo 2015 [1] Obtain proper SSL certificate *.pfx (contains both certificate and private keys) For example, the pfx file contains both certificate and private keys, also the ascii file
Installation and configuration guide
 Installation and Configuration Guide Installation and configuration guide Adding X-Username support to Forward and Reverse Proxy TMG Servers Published: December 2010 Applies to: Winfrasoft X-Username for
Installation and Configuration Guide Installation and configuration guide Adding X-Username support to Forward and Reverse Proxy TMG Servers Published: December 2010 Applies to: Winfrasoft X-Username for
Introduction to Mobile Access Gateway Installation
 Introduction to Mobile Access Gateway Installation This document describes the installation process for the Mobile Access Gateway (MAG), which is an enterprise integration component that provides a secure
Introduction to Mobile Access Gateway Installation This document describes the installation process for the Mobile Access Gateway (MAG), which is an enterprise integration component that provides a secure
Optimal Network Connectivity Reliable Network Access Flexible Network Management
 The Intelligent WAN Load Balancer Aggregating Links For Maximum Performance Optimal Network Connectivity Reliable Network Access Flexible Network Management Enterprises are increasingly relying on the
The Intelligent WAN Load Balancer Aggregating Links For Maximum Performance Optimal Network Connectivity Reliable Network Access Flexible Network Management Enterprises are increasingly relying on the
GlobalSCAPE DMZ Gateway, v1. User Guide
 GlobalSCAPE DMZ Gateway, v1 User Guide GlobalSCAPE, Inc. (GSB) Address: 4500 Lockhill-Selma Road, Suite 150 San Antonio, TX (USA) 78249 Sales: (210) 308-8267 Sales (Toll Free): (800) 290-5054 Technical
GlobalSCAPE DMZ Gateway, v1 User Guide GlobalSCAPE, Inc. (GSB) Address: 4500 Lockhill-Selma Road, Suite 150 San Antonio, TX (USA) 78249 Sales: (210) 308-8267 Sales (Toll Free): (800) 290-5054 Technical
Getting Started. Symantec Client Security. About Symantec Client Security. How to get started
 Getting Started Symantec Client Security About Security Security provides scalable, cross-platform firewall, intrusion prevention, and antivirus protection for workstations and antivirus protection for
Getting Started Symantec Client Security About Security Security provides scalable, cross-platform firewall, intrusion prevention, and antivirus protection for workstations and antivirus protection for
Install and configure e-mail server
 IBM WEBSPHERE ADAPTER 6.0.2 LAB EXERCISE Copyright IBM Corporation 2007 All rights reserved Install and configure e-mail server What this exercise is about... 1 What you should be able to do... 1 Introduction...
IBM WEBSPHERE ADAPTER 6.0.2 LAB EXERCISE Copyright IBM Corporation 2007 All rights reserved Install and configure e-mail server What this exercise is about... 1 What you should be able to do... 1 Introduction...
Configuring Windows Server Clusters
 Configuring Windows Server Clusters In Enterprise network, group of servers are often used to provide a common set of services. For example, Different physical computers can be used to answer request directed
Configuring Windows Server Clusters In Enterprise network, group of servers are often used to provide a common set of services. For example, Different physical computers can be used to answer request directed
Kaspersky Anti-Virus 8.0 for Microsoft ISA Server and Forefront TMG Standard Edition
 Kaspersky Anti-Virus 8.0 for Microsoft ISA Server and Forefront TMG Standard Edition ADMINISTRATOR'S GUIDE PROGRAM VERSION: 8.0 Dear User! Thank you for choosing our product. We hope that this document
Kaspersky Anti-Virus 8.0 for Microsoft ISA Server and Forefront TMG Standard Edition ADMINISTRATOR'S GUIDE PROGRAM VERSION: 8.0 Dear User! Thank you for choosing our product. We hope that this document
Integrate Check Point Firewall
 Integrate Check Point Firewall EventTracker Enterprise Publication Date: Oct.26, 2015 EventTracker 8815 Centre Park Drive Columbia MD 21045 www.eventtracker.com Abstract The purpose of this document is
Integrate Check Point Firewall EventTracker Enterprise Publication Date: Oct.26, 2015 EventTracker 8815 Centre Park Drive Columbia MD 21045 www.eventtracker.com Abstract The purpose of this document is
INTERNET INFORMATION SERVICES (IIS) IMPLEMENTATION BEST PRACTICES: By: Terri Donahue, Microsoft IIS MVP
 INTERNET INFORMATION SERVICES (IIS) IMPLEMENTATION BEST PRACTICES: SECURITY, LOAD TESTING, SCALABILITY, LOAD BALANCING By: Terri Donahue, Microsoft IIS MVP Internet information services (iis) Implementation
INTERNET INFORMATION SERVICES (IIS) IMPLEMENTATION BEST PRACTICES: SECURITY, LOAD TESTING, SCALABILITY, LOAD BALANCING By: Terri Donahue, Microsoft IIS MVP Internet information services (iis) Implementation
Microsoft Lync Server Overview
 Organizations can use the to enhance the scalability and availability of their Microsoft Lync Server 2010 deployments (formerly known as Microsoft Office Communications Server). Barracuda Networks has
Organizations can use the to enhance the scalability and availability of their Microsoft Lync Server 2010 deployments (formerly known as Microsoft Office Communications Server). Barracuda Networks has
How to set up popular firewalls to work with Web CEO
 How to set up popular firewalls to work with Web CEO Contents How to set up popular firewalls to work with Web CEO... 1 Setting up Agnitum Outpost Firewall 2.5... 2 Setting up Black ICE 3... 6 Setting
How to set up popular firewalls to work with Web CEO Contents How to set up popular firewalls to work with Web CEO... 1 Setting up Agnitum Outpost Firewall 2.5... 2 Setting up Black ICE 3... 6 Setting
Setting up Microsoft Office 365
 Integration Guide Revision G McAfee SaaS Email Protection Securing Exchange Online in Microsoft Office 365 Setting up Microsoft Office 365 Use this guide to configure Microsoft Office 365 and Microsoft
Integration Guide Revision G McAfee SaaS Email Protection Securing Exchange Online in Microsoft Office 365 Setting up Microsoft Office 365 Use this guide to configure Microsoft Office 365 and Microsoft
Proxies. Chapter 4. Network & Security Gildas Avoine
 Proxies Chapter 4 Network & Security Gildas Avoine SUMMARY OF CHAPTER 4 Generalities Forward Proxies Reverse Proxies Open Proxies Conclusion GENERALITIES Generalities Forward Proxies Reverse Proxies Open
Proxies Chapter 4 Network & Security Gildas Avoine SUMMARY OF CHAPTER 4 Generalities Forward Proxies Reverse Proxies Open Proxies Conclusion GENERALITIES Generalities Forward Proxies Reverse Proxies Open
Sophos for Microsoft SharePoint startup guide
 Sophos for Microsoft SharePoint startup guide Product version: 2.0 Document date: March 2011 Contents 1 About this guide...3 2 About Sophos for Microsoft SharePoint...3 3 System requirements...3 4 Planning
Sophos for Microsoft SharePoint startup guide Product version: 2.0 Document date: March 2011 Contents 1 About this guide...3 2 About Sophos for Microsoft SharePoint...3 3 System requirements...3 4 Planning
Introduction to the EIS Guide
 Introduction to the EIS Guide The AirWatch Enterprise Integration Service (EIS) provides organizations the ability to securely integrate with back-end enterprise systems from either the AirWatch SaaS environment
Introduction to the EIS Guide The AirWatch Enterprise Integration Service (EIS) provides organizations the ability to securely integrate with back-end enterprise systems from either the AirWatch SaaS environment
Basic Exchange Setup Guide
 Basic Exchange Setup Guide The following document and screenshots are provided for a single Microsoft Exchange Small Business Server 2003 or Exchange Server 2007 setup. These instructions are not provided
Basic Exchange Setup Guide The following document and screenshots are provided for a single Microsoft Exchange Small Business Server 2003 or Exchange Server 2007 setup. These instructions are not provided
IIS Reverse Proxy Implementation
 IIS Reverse Proxy Implementation for OXI/OEDS Servers V E R S I O N : 1. 1 M A Y 2 9, 2 0 1 5 Table of Contents Intended Audience 3 About this Document 3 Advisories and Known Issues 3 Additional Considerations
IIS Reverse Proxy Implementation for OXI/OEDS Servers V E R S I O N : 1. 1 M A Y 2 9, 2 0 1 5 Table of Contents Intended Audience 3 About this Document 3 Advisories and Known Issues 3 Additional Considerations
Transport server data paths
 1 of 14 14/11/2011 2:45 PM Applies to: Exchange Server 2010 SP1 Topic Last Modified: 2011-04-22 This topic provides information about ports, authentication, and for all data paths used by Microsoft Exchange
1 of 14 14/11/2011 2:45 PM Applies to: Exchange Server 2010 SP1 Topic Last Modified: 2011-04-22 This topic provides information about ports, authentication, and for all data paths used by Microsoft Exchange
How to Logon with Domain Credentials to a Server in a Workgroup
 How to Logon with Domain Credentials to a Server in a Workgroup Johan Loos johan@accessdenied.be Version 1.0 Authentication Overview Basically when you logon to a Windows Server you can logon locally using
How to Logon with Domain Credentials to a Server in a Workgroup Johan Loos johan@accessdenied.be Version 1.0 Authentication Overview Basically when you logon to a Windows Server you can logon locally using
How To Install Powerpoint 6 On A Windows Server With A Powerpoint 2.5 (Powerpoint) And Powerpoint 3.5.5 On A Microsoft Powerpoint 4.5 Powerpoint (Powerpoints) And A Powerpoints 2
 DocAve 6 Service Pack 1 Installation Guide Revision C Issued September 2012 1 Table of Contents About the Installation Guide... 4 Submitting Documentation Feedback to AvePoint... 4 Before You Begin...
DocAve 6 Service Pack 1 Installation Guide Revision C Issued September 2012 1 Table of Contents About the Installation Guide... 4 Submitting Documentation Feedback to AvePoint... 4 Before You Begin...
Managing Qualys Scanners
 Q1 Labs Help Build 7.0 Maintenance Release 3 documentation@q1labs.com Managing Qualys Scanners Managing Qualys Scanners A QualysGuard vulnerability scanner runs on a remote web server. QRadar must access
Q1 Labs Help Build 7.0 Maintenance Release 3 documentation@q1labs.com Managing Qualys Scanners Managing Qualys Scanners A QualysGuard vulnerability scanner runs on a remote web server. QRadar must access
IBM Security QRadar Vulnerability Manager Version 7.2.1. User Guide
 IBM Security QRadar Vulnerability Manager Version 7.2.1 User Guide Note Before using this information and the product that it supports, read the information in Notices on page 61. Copyright IBM Corporation
IBM Security QRadar Vulnerability Manager Version 7.2.1 User Guide Note Before using this information and the product that it supports, read the information in Notices on page 61. Copyright IBM Corporation
Forward proxy server vs reverse proxy server
 Using a reverse proxy server for TAD4D/LMT Intended audience The intended recipient of this document is a TAD4D/LMT administrator and the staff responsible for the configuration of TAD4D/LMT agents. Purpose
Using a reverse proxy server for TAD4D/LMT Intended audience The intended recipient of this document is a TAD4D/LMT administrator and the staff responsible for the configuration of TAD4D/LMT agents. Purpose
Outpost Network Security
 Administrator Guide Reference Outpost Network Security Office Firewall Software from Agnitum Abstract This document provides information on deploying Outpost Network Security in a corporate network. It
Administrator Guide Reference Outpost Network Security Office Firewall Software from Agnitum Abstract This document provides information on deploying Outpost Network Security in a corporate network. It
Architecture and Data Flow Overview. BlackBerry Enterprise Service 10 721-08877-123 Version: 10.2. Quick Reference
 Architecture and Data Flow Overview BlackBerry Enterprise Service 10 721-08877-123 Version: Quick Reference Published: 2013-11-28 SWD-20131128130321045 Contents Key components of BlackBerry Enterprise
Architecture and Data Flow Overview BlackBerry Enterprise Service 10 721-08877-123 Version: Quick Reference Published: 2013-11-28 SWD-20131128130321045 Contents Key components of BlackBerry Enterprise
Firewall. User Manual
 Firewall User Manual 1 IX. Firewall This chapter introduces firewall general policy, access rule, and content filter settings to ensure network security. 9.1 General Policy The firewall is enabled by default.
Firewall User Manual 1 IX. Firewall This chapter introduces firewall general policy, access rule, and content filter settings to ensure network security. 9.1 General Policy The firewall is enabled by default.
GFI White Paper PCI-DSS compliance and GFI Software products
 White Paper PCI-DSS compliance and Software products The Payment Card Industry Data Standard () compliance is a set of specific security standards developed by the payment brands* to help promote the adoption
White Paper PCI-DSS compliance and Software products The Payment Card Industry Data Standard () compliance is a set of specific security standards developed by the payment brands* to help promote the adoption
Computer Security CS 426 Lecture 36. CS426 Fall 2010/Lecture 36 1
 Computer Security CS 426 Lecture 36 Perimeter Defense and Firewalls CS426 Fall 2010/Lecture 36 1 Announcements There will be a quiz on Wed There will be a guest lecture on Friday, by Prof. Chris Clifton
Computer Security CS 426 Lecture 36 Perimeter Defense and Firewalls CS426 Fall 2010/Lecture 36 1 Announcements There will be a quiz on Wed There will be a guest lecture on Friday, by Prof. Chris Clifton
Security IIS Service Lesson 6
 Security IIS Service Lesson 6 Skills Matrix Technology Skill Objective Domain Objective # Configuring Certificates Configure SSL security 3.6 Assigning Standard and Special NTFS Permissions Enabling and
Security IIS Service Lesson 6 Skills Matrix Technology Skill Objective Domain Objective # Configuring Certificates Configure SSL security 3.6 Assigning Standard and Special NTFS Permissions Enabling and
DEPLOYMENT GUIDE Version 2.1. Deploying F5 with Microsoft SharePoint 2010
 DEPLOYMENT GUIDE Version 2.1 Deploying F5 with Microsoft SharePoint 2010 Table of Contents Table of Contents Introducing the F5 Deployment Guide for Microsoft SharePoint 2010 Prerequisites and configuration
DEPLOYMENT GUIDE Version 2.1 Deploying F5 with Microsoft SharePoint 2010 Table of Contents Table of Contents Introducing the F5 Deployment Guide for Microsoft SharePoint 2010 Prerequisites and configuration
Application Notes for Configuring Microsoft Office Communications Server 2007 R2 and Avaya IP Office PSTN Call Routing - Issue 1.0
 Avaya Solution & Interoperability Test Lab Application Notes for Configuring Microsoft Office Communications Server 2007 R2 and Avaya IP Office PSTN Call Routing - Issue 1.0 Abstract These Application
Avaya Solution & Interoperability Test Lab Application Notes for Configuring Microsoft Office Communications Server 2007 R2 and Avaya IP Office PSTN Call Routing - Issue 1.0 Abstract These Application
nexvortex Setup Template
 nexvortex Setup Template ZULTYS, INC. April 2013 5 1 0 S P R I N G S T R E E T H E R N D O N V A 2 0 1 7 0 + 1 8 5 5. 6 3 9. 8 8 8 8 Introduction This document is intended only for nexvortex customers
nexvortex Setup Template ZULTYS, INC. April 2013 5 1 0 S P R I N G S T R E E T H E R N D O N V A 2 0 1 7 0 + 1 8 5 5. 6 3 9. 8 8 8 8 Introduction This document is intended only for nexvortex customers
Building the SAP Business One Cloud Landscape Part of the SAP Business One Cloud Landscape Workshop
 Building the SAP Business One Cloud Landscape Part of the SAP Business One Cloud Landscape Workshop TABLE OF CONTENTS 1 INTRODUCTION... 3 2 LANDSCAPE DETAILS... 3 2.1 Server Details... 3 2.2 Landscape
Building the SAP Business One Cloud Landscape Part of the SAP Business One Cloud Landscape Workshop TABLE OF CONTENTS 1 INTRODUCTION... 3 2 LANDSCAPE DETAILS... 3 2.1 Server Details... 3 2.2 Landscape
Kaseya Server Instal ation User Guide June 6, 2008
 Kaseya Server Installation User Guide June 6, 2008 About Kaseya Kaseya is a global provider of IT automation software for IT Solution Providers and Public and Private Sector IT organizations. Kaseya's
Kaseya Server Installation User Guide June 6, 2008 About Kaseya Kaseya is a global provider of IT automation software for IT Solution Providers and Public and Private Sector IT organizations. Kaseya's
Inspection of Encrypted HTTPS Traffic
 Technical Note Inspection of Encrypted HTTPS Traffic StoneGate version 5.0 SSL/TLS Inspection T e c h n i c a l N o t e I n s p e c t i o n o f E n c r y p t e d H T T P S T r a f f i c 1 Table of Contents
Technical Note Inspection of Encrypted HTTPS Traffic StoneGate version 5.0 SSL/TLS Inspection T e c h n i c a l N o t e I n s p e c t i o n o f E n c r y p t e d H T T P S T r a f f i c 1 Table of Contents
Monitoring Forefront TMG
 Monitoring Forefront TMG eg Enterprise v6 Restricted Rights Legend The information contained in this document is confidential and subject to change without notice. No part of this document may be reproduced
Monitoring Forefront TMG eg Enterprise v6 Restricted Rights Legend The information contained in this document is confidential and subject to change without notice. No part of this document may be reproduced
WHITE PAPER Citrix Secure Gateway Startup Guide
 WHITE PAPER Citrix Secure Gateway Startup Guide www.citrix.com Contents Introduction... 2 What you will need... 2 Preparing the environment for Secure Gateway... 2 Installing a CA using Windows Server
WHITE PAPER Citrix Secure Gateway Startup Guide www.citrix.com Contents Introduction... 2 What you will need... 2 Preparing the environment for Secure Gateway... 2 Installing a CA using Windows Server
Authentication in XenMobile 8.6 with a Focus on Client Certificate Authentication
 Authentication in XenMobile 8.6 with a Focus on Client Certificate Authentication Authentication is about security and user experience and balancing the two goals. This document describes the authentication
Authentication in XenMobile 8.6 with a Focus on Client Certificate Authentication Authentication is about security and user experience and balancing the two goals. This document describes the authentication
TECHNICAL NOTE Stormshield Network Firewall AUTOMATIC BACKUPS. Document version: 1.0 Reference: snentno_autobackup
 Stormshield Network Firewall Document version: 1.0 Reference: snentno_autobackup CONTENTS INTRODUCTION 3 OPERATION 3 Storing in the Mystormshield.eu client area 3 Storing on a customized server 3 FIREWALL
Stormshield Network Firewall Document version: 1.0 Reference: snentno_autobackup CONTENTS INTRODUCTION 3 OPERATION 3 Storing in the Mystormshield.eu client area 3 Storing on a customized server 3 FIREWALL
HP ProLiant Essentials Vulnerability and Patch Management Pack Server Security Recommendations
 HP ProLiant Essentials Vulnerability and Patch Management Pack Server Security Recommendations Security Considerations for VPM and HP SIM Servers Introduction... 3 External patch acquisition... 4 Comparing
HP ProLiant Essentials Vulnerability and Patch Management Pack Server Security Recommendations Security Considerations for VPM and HP SIM Servers Introduction... 3 External patch acquisition... 4 Comparing
How To - Configure Virtual Host using FQDN How To Configure Virtual Host using FQDN
 How To - Configure Virtual Host using FQDN How To Configure Virtual Host using FQDN Applicable Version: 10.6.2 onwards Overview Virtual host implementation is based on the Destination NAT concept. Virtual
How To - Configure Virtual Host using FQDN How To Configure Virtual Host using FQDN Applicable Version: 10.6.2 onwards Overview Virtual host implementation is based on the Destination NAT concept. Virtual
