Integrated trust, governance and access
|
|
|
- Curtis Bell
- 8 years ago
- Views:
Transcription
1 Introduction A major problem with many information infrastructures is the management and control of information sharing from within and beyond organisational boundaries. Traditionally this will be controlled through a security policy and implemented using either network controls and/or in-built software controls, defined and managed by each data access portal; but the scope of these policies are often just defined within that organisation. As more and more information crosses organisation and domain boundaries, it becomes increasingly difficult to manage the number of possible ways that information can be shared and aggregated. A key element of this is the increasing requirement for trust between organisations and units, especially with the move towards cloud-based services. The Symphonic product overcomes these problems by creating a formal structure for the abstraction, governance and implementation of trust relationships and security policies. It enables disparate systems and domains to open up access to their services in a highly governed and secure manner, confident in the knowledge that the services/data specified in their own managed can be accessed only by those with the necessary claims to gain permission. Symphonic can be used as a full end-to-end solution for policy abstraction, implementation and controlled access to services, or can integrate each of the elements as a Service to existing applications. Symphonic Suite The Symphonic Suite consists of three core components, each of which can operate as stand-alone products or can work with each other or existing systems to provide end-to-end integration. The core components are: Symphonic - This is a trust framework tool which enables the abstraction of roles, services, trust levels and defines their trust relationship. The export from this component provides the requirements for the information sharing/service aggregation policy. Symphonic - This takes, as an input, the abstraction of the trust framework, and provides a highly efficient rules engine to quickly and securely determine if an entity has the rights to access a given service based on their claims. This crosses domain boundaries and enables authentication and attribute provision from multiple identity and attribute providers. Symphonic Gateway - This takes the rules from the governance engine, and implements them within a real-time filtering system, which controls and audits all the accesses to services between the domains.
2 Features Figure 1 outlines some of the key features of Symphonic. These include: Extendable Policy. This allows for governance policies to be created which can define micro and macro relationships of individuals, roles and relationship to services. The data owner can have full rights to how data is then used within aggregated services. Overall, Symphonic abstracts trust relationships into domain boundaries where the relationship between each boundary is abstracted, and with the implementation of governance rules for the trust relationship. Integrated. This abstracts each of the accesses to data into well-managed services, which have defined exactly how the service can be used by other domains. Novel Modelling of Policy. Symphonic has patent pending technology which models the governance rules for their operation, including for rule shadowing, anomalies, and so on. Real-time Implementation and Control of Rules. The rules either run in a filtering engine or as-a- Service for other applications. This allows the governance of trust relationships to be changed in realtime, especially to add new services or to cope with security issues. Role, Relationship and. This involves the integration of a full use case of rights of trust, governance and access, including for role, consent, relationship and delegation. Integrated Federated Identity Provision. This allows for a range of identity/attribute providers to be built into the trust, governance and access relationships, and allocates levels of trust to each of the services. Static and dynamic rules. Symphonic implements both static rules which are defined for role-based trust and access, and can also implement dynamic rules which allow users to create their own trust relationship. Integration of full-rights infrastructure. Symphonic uses a data bucket concept where each element of data has an owner and the rights of access to the data as it is aggregated into other services is control by the data owner. This gives users complete control of their own data. Plug-in integration. Symphonic can be used as-a-service or can implement a full integration of trust, governance and access. Rules defined in a structured format. This provides trust relationships and governance rules in a structured English format, which can be easily interpreted by all the stakeholders, and can be easily audited. Foundation built on ontology. The complete infrastructure is built on a unique ontology built for the trust relationships, and which is then used to formally define the governance rules and filter between domains.
3 Pseudonyms used for rule definitions. The governance rules use pseudonyms in order to obfuscate the roles, and identities of the targets. Inter- and intra-domain rights. Symphonic can be used to define the rights of access within a domain and between domains, each defined in separate contracts. Extendable Policy - Micro to macro. - Cross domain. Integrated - Full service definition Health Care Social Care Novel Modelling of Policy - Rule Shadowing. - Anomolises. etc Real-time Implementation and Control of Rules Plug-in Integration - aas - As a Service or part/ full framework Static and Dynamic Rules - System creates rights as required Education Police Strong Infrastructure Integration of Full-rights Infrastructure - bucket integration supports end-to-end rights for service aggregation. Full use case rights - Integration of role, consent, relationship and delegation. Integrated Federated Identity Provision Rules defined in structure English format Foundation built on an Ontology of the Domain Interfaces Pseudonyms used for all rule defines Inter- and Intradomain rights - Full definition of rights Figure 1: Outline features of Symphonic
4 , and Access In modern service-oriented infrastructures a user must gather claims to consume a service. Too often the service is bound to a specific authentication infrastructure which limits the scalability of the provision of the service. For more dynamic infrastructures there is no direct communication between the service and the gathering of the claims around identity and the attributes required to consume a service. Figure 2 outlines this process, where there are Terms of Service (ToS) between a user and their identity and attribute provider, another ToS between them and the service, and so on. It is the focus of the and infrastructure to define a contract which binds these terms of service together. This contract pre-defines the requirements for the claims to the service, and then is trusted to actually issue the contract for the user to consume the service. Symphonic thus abstracts the trust relations from well-defined policies. A trusted broker will then pass the requirements for a user to consume a service, and the will provide back the claims that are required to be able to consume the service. The user will then gather the claims, and the broker then passes these to the for it to check its running rules for rights to the service. If these are acceptable it will issue a service token to consume the service, which can be given back to the user, via the broker (or the service can be invoked on their behalf, and the link to the service can be returned to the user). A key element of the is the concept of role, relationship, consent and delegation, where an access can claim rights of access to a referrer. In this way the owner of the data can have rights of access based on their role (such as whether they are a GP), their relationship (such as whether they are the GP of a specific patient), their consent (whether someone has given them rights), or their delegation (where they have given delegation of authority to another person). Terms of Service Terms of Service Service (RP) Portal Policy Policy Referrer ID Terms of Service ed Broker ed / Contract Personal Storage (Consent) ed Storage (Role,, Relationship) Gateway (SPoC) Figure 2:, and Access
5 and as a Service With the complex relationships that organisations have in rights of access to services, it is becoming increasing important to abstract and fully define the trust and the levels of access to services. Symphonic provides the ability to extract the trust relationship between two domains, and then implement this as a set of rules. These are then defined in the and the, which can be easily integrated into existing applications. Figure 3 outlines a basic use case, where a broker deals with the requests from a user. It will then use the to define the requirements of the claim to a service, and the to check these rights against the actual rules of access to a service. Dynamic trust relationships can be built up for identity and attribute providers, and how these map to the role, relationship, consent or delegation that an individual has to consume a service. The service itself can be invoked by the broker or a service token can be sent back to the user for them to give to the service. In this way both legacy services and new trusted services can be integrated into the infrastructure. Referrer ID 1. Service Access 6. Claims collection 5. Claim 7. Claims ed Broker 3. Service 4. Claims Requirement 2. base 8. Claims 9. Rights ed /Atrp 10. Service Invoke [ID,Items] Service (RP) Figure 3: and as a Service
6 Symphonic Gateway Symphonic can also implement a filtering gateway which takes the rules from the, and runs them with a Gateway, which then directly runs the rules, in a similar way that a network firewall will implement the filtering of network packets. Figure 4 outlines the full integration where the abstraction of the trust relationships are used to create the rules, which are then implemented within a gateway, which in turn provides securely controlled access to the services based on the trust relationships defined back in the trust framework. This type of architecture fully implements an end-toend solution for trust relationships, where the requirements can be audit and reviewed, with control of each stage. It can also integrate with a wide range of stakeholders, using trusted identity infrastructures. 1. Service Access 5. Claim 7. Claims Referrer ID 6. Claims collection ed Broker 2. base 3. Service 4. Claims Requirement ed /Atrp 8. Claims 9. Rights 10. Service Invoke [ID,Items] Domain Ontology Service Definition Service (RP) Referrer ID ed /Atrp Rules Policy Definition Services Domain A SPoC (Gateway) Domain B Figure 4: Full integration Symphonic technology is the culmination of over 5 years research and development within Edinburgh Napier University, through collaborations with both commercial and other academic partners, aimed at revolutionising the way organisations govern the sharing of information, allowing those that operate in highly-regulated environments such as health, social care, law and finance to securely share critical, timedependent and sensitive information. The innovative architecture created by ENU allows integration of complex trust and governance frameworks for information-sharing and legal policies to be integrated into the Symphonic solution, so that any information sharing which occurs meets compliance by design.
How To Create Trust Online
 Authors: Niall Burns (Symphonic), Professor Bill Buchanan (Edinburgh Napier University), Cassie Anderson (miicard) Overview There is a growing demand within governments, health sectors, social care, police,
Authors: Niall Burns (Symphonic), Professor Bill Buchanan (Edinburgh Napier University), Cassie Anderson (miicard) Overview There is a growing demand within governments, health sectors, social care, police,
Glossary of Key Terms
 and s Branch Glossary of Key Terms The terms and definitions listed in this glossary are used throughout the s Package to define key terms in the context of. Access Control Access The processes by which
and s Branch Glossary of Key Terms The terms and definitions listed in this glossary are used throughout the s Package to define key terms in the context of. Access Control Access The processes by which
Differentiated Services
 March 19, 1998 Gordon Chaffee Berkeley Multimedia Research Center University of California, Berkeley Email: chaffee@bmrc.berkeley.edu URL: http://bmrc.berkeley.edu/people/chaffee 1 Outline Architecture
March 19, 1998 Gordon Chaffee Berkeley Multimedia Research Center University of California, Berkeley Email: chaffee@bmrc.berkeley.edu URL: http://bmrc.berkeley.edu/people/chaffee 1 Outline Architecture
CLOUD BASED SEMANTIC EVENT PROCESSING FOR
 CLOUD BASED SEMANTIC EVENT PROCESSING FOR MONITORING AND MANAGEMENT OF SUPPLY CHAINS A VLTN White Paper Dr. Bill Karakostas Bill.karakostas@vltn.be Executive Summary Supply chain visibility is essential
CLOUD BASED SEMANTIC EVENT PROCESSING FOR MONITORING AND MANAGEMENT OF SUPPLY CHAINS A VLTN White Paper Dr. Bill Karakostas Bill.karakostas@vltn.be Executive Summary Supply chain visibility is essential
Breaking Down the Insurance Silos
 Breaking Down the Insurance Silos Improving Performance through Increased Collaboration Insurers that cannot model business scenarios quickly and accurately to allow them to plan effectively for the future
Breaking Down the Insurance Silos Improving Performance through Increased Collaboration Insurers that cannot model business scenarios quickly and accurately to allow them to plan effectively for the future
Cloud-Based Self Service Analytics
 Cloud-Based Self Service Analytics Andrew G Naish* Chief Technical Officer, Space-Time Research, Melbourne, Australia andrew.naish@spacetimeresearch.com Abstracts Traditionally, the means by which official
Cloud-Based Self Service Analytics Andrew G Naish* Chief Technical Officer, Space-Time Research, Melbourne, Australia andrew.naish@spacetimeresearch.com Abstracts Traditionally, the means by which official
Strengthen security with intelligent identity and access management
 Strengthen security with intelligent identity and access management IBM Security solutions help safeguard user access, boost compliance and mitigate insider threats Highlights Enable business managers
Strengthen security with intelligent identity and access management IBM Security solutions help safeguard user access, boost compliance and mitigate insider threats Highlights Enable business managers
Enterprise Security Architecture Concepts and Practice
 Enterprise Architecture Concepts and Practice Jim Whitmore whitmore@us.ibm.com Presentation to Open Group Oct 22, 2003 Enterprise Architecture Abstract In the early 90 s IBM Global Services created a Consultancy
Enterprise Architecture Concepts and Practice Jim Whitmore whitmore@us.ibm.com Presentation to Open Group Oct 22, 2003 Enterprise Architecture Abstract In the early 90 s IBM Global Services created a Consultancy
ParlaMI, Enterprise Instant Messaging
 ParlaMI, Enterprise Instant Messaging A step forward for the optimization and protection of corporate communications Why should you use instant messaging in your business environment? Optimize business
ParlaMI, Enterprise Instant Messaging A step forward for the optimization and protection of corporate communications Why should you use instant messaging in your business environment? Optimize business
Mitra Innovation Leverages WSO2's Open Source Middleware to Build BIM Exchange Platform
 Mitra Innovation Leverages WSO2's Open Source Middleware to Build BIM Exchange Platform May 2015 Contents 1. Introduction... 3 2. What is BIM... 3 2.1. History of BIM... 3 2.2. Why Implement BIM... 4 2.3.
Mitra Innovation Leverages WSO2's Open Source Middleware to Build BIM Exchange Platform May 2015 Contents 1. Introduction... 3 2. What is BIM... 3 2.1. History of BIM... 3 2.2. Why Implement BIM... 4 2.3.
A Conceptual Model of Practitioner Authentication Prior to Providing Telemedicine Services in Developing Countries
 A Conceptual Model of Practitioner Authentication Prior to Providing Telemedicine Services in Developing Countries Leonie Spoerer, Yashik Singh and Maurice Mars Dept of TeleHealth, University of KwaZulu-Natal
A Conceptual Model of Practitioner Authentication Prior to Providing Telemedicine Services in Developing Countries Leonie Spoerer, Yashik Singh and Maurice Mars Dept of TeleHealth, University of KwaZulu-Natal
Digital Marketplace - G-Cloud
 Digital Marketplace - G-Cloud SharePoint Services Core offer 22 services in this area: 1. SharePoint Forms SharePoint comes with out-of-the-box web-based forms that allow for data to be captured for your
Digital Marketplace - G-Cloud SharePoint Services Core offer 22 services in this area: 1. SharePoint Forms SharePoint comes with out-of-the-box web-based forms that allow for data to be captured for your
Onegini Token server / Web API Platform
 Onegini Token server / Web API Platform Companies and users interact securely by sharing data between different applications The Onegini Token server is a complete solution for managing your customer s
Onegini Token server / Web API Platform Companies and users interact securely by sharing data between different applications The Onegini Token server is a complete solution for managing your customer s
White Paper Delivering Web Services Security: The Entrust Secure Transaction Platform
 White Paper Delivering Web Services Security: September 2003 Copyright 2003 Entrust. All rights reserved. Entrust is a registered trademark of Entrust, Inc. in the United States and certain other countries.
White Paper Delivering Web Services Security: September 2003 Copyright 2003 Entrust. All rights reserved. Entrust is a registered trademark of Entrust, Inc. in the United States and certain other countries.
Identity management [TSA]
![Identity management [TSA] Identity management [TSA]](/thumbs/27/12447406.jpg) [TSA] INDEX 1. Introduction.3 2. Terminologies.3 3. Overview of Identity Management...4 4. Identity Management Models.....6 5. Identity management framework.8 6. Authentication Methods 12 7. Identity Management
[TSA] INDEX 1. Introduction.3 2. Terminologies.3 3. Overview of Identity Management...4 4. Identity Management Models.....6 5. Identity management framework.8 6. Authentication Methods 12 7. Identity Management
JOURNAL OF OBJECT TECHNOLOGY
 JOURNAL OF OBJECT TECHNOLOGY Online at www.jot.fm. Published by ETH Zurich, Chair of Software Engineering JOT, 2008 Vol. 7 No. 7, September-October 2008 Applications At Your Service Mahesh H. Dodani, IBM,
JOURNAL OF OBJECT TECHNOLOGY Online at www.jot.fm. Published by ETH Zurich, Chair of Software Engineering JOT, 2008 Vol. 7 No. 7, September-October 2008 Applications At Your Service Mahesh H. Dodani, IBM,
Broker Portal Tutorial Broker Portal Basics
 Broker Portal Tutorial Broker Portal Basics Create Agent Connect Link Forgotten Password Change Your Broker Portal Password Delegate View Application Status Create Agent Connect Link Log in to your Producer
Broker Portal Tutorial Broker Portal Basics Create Agent Connect Link Forgotten Password Change Your Broker Portal Password Delegate View Application Status Create Agent Connect Link Log in to your Producer
Cyber Essentials Questionnaire
 Cyber Essentials Questionnaire Introduction The Cyber Essentials scheme is recommended for organisations looking for a base level Cyber security test where IT is a business enabler rather than a core deliverable.
Cyber Essentials Questionnaire Introduction The Cyber Essentials scheme is recommended for organisations looking for a base level Cyber security test where IT is a business enabler rather than a core deliverable.
ICE econfirm. FAQs April 2012
 ICE econfirm FAQs April 2012 This material may not be reproduced or redistributed in whole or in part without the express, prior written consent of IntercontinentalExchange, Inc. Copyright Intercontinental
ICE econfirm FAQs April 2012 This material may not be reproduced or redistributed in whole or in part without the express, prior written consent of IntercontinentalExchange, Inc. Copyright Intercontinental
3Si Managed Authentication Services Service Description
 3Si Managed Authentication Services Service Description [Pick the date] 3Si Managed Authentication Services Service Description [Type the document subtitle] JT www.3sicloud.com www.3sicloud.com enquiry@3sicloud.com
3Si Managed Authentication Services Service Description [Pick the date] 3Si Managed Authentication Services Service Description [Type the document subtitle] JT www.3sicloud.com www.3sicloud.com enquiry@3sicloud.com
An Enterprise Architecture and Data quality framework
 An Enterprise Architecture and quality framework Jerome Capirossi - NATEA-Consulting jerome@capirossi.org http://capirossi.org, Pascal Rabier La Mutuelle Generale prabier@lamutuellegeneral.fr Abstract:
An Enterprise Architecture and quality framework Jerome Capirossi - NATEA-Consulting jerome@capirossi.org http://capirossi.org, Pascal Rabier La Mutuelle Generale prabier@lamutuellegeneral.fr Abstract:
Service Virtualization: Managing Change in a Service-Oriented Architecture
 Service Virtualization: Managing Change in a Service-Oriented Architecture Abstract Load balancers, name servers (for example, Domain Name System [DNS]), and stock brokerage services are examples of virtual
Service Virtualization: Managing Change in a Service-Oriented Architecture Abstract Load balancers, name servers (for example, Domain Name System [DNS]), and stock brokerage services are examples of virtual
How To Understand The Needs Of The Network
 White Paper The Modern Network Monitoring Mandate By Bob Laliberte, Senior Analyst April 2014 This ESG White Paper was commissioned by Emulex and is distributed under license from ESG. White Paper: The
White Paper The Modern Network Monitoring Mandate By Bob Laliberte, Senior Analyst April 2014 This ESG White Paper was commissioned by Emulex and is distributed under license from ESG. White Paper: The
Cisco ASA Adaptive Security Appliance Single Sign-On: Solution Brief
 Guide Cisco ASA Adaptive Security Appliance Single Sign-On: Solution Brief October 2012 2012 Cisco and/or its affiliates. All rights reserved. This document is Cisco Public Information. Page 1 of 21 Contents
Guide Cisco ASA Adaptive Security Appliance Single Sign-On: Solution Brief October 2012 2012 Cisco and/or its affiliates. All rights reserved. This document is Cisco Public Information. Page 1 of 21 Contents
Oracle Access Manager. An Oracle White Paper
 Oracle Access Manager An Oracle White Paper NOTE: The following is intended to outline our general product direction. It is intended for information purposes only, and may not be incorporated into any
Oracle Access Manager An Oracle White Paper NOTE: The following is intended to outline our general product direction. It is intended for information purposes only, and may not be incorporated into any
Attribute-Based Access Control Solutions: Federating Authoritative User Data to Support Relying Party Authorization Decisions and Requirements
 Joint White Paper: Attribute-Based Access Control Solutions: Federating Authoritative User Data to Support Relying Party Authorization Decisions and Requirements Submitted Date: April 10, 2013 Submitted
Joint White Paper: Attribute-Based Access Control Solutions: Federating Authoritative User Data to Support Relying Party Authorization Decisions and Requirements Submitted Date: April 10, 2013 Submitted
The University of Information Technology Management System
 IT Monitoring Code of Practice 1.4 University of Ulster Code of Practice Cover Sheet Document Title IT Monitoring Code of Practice 1.4 Custodian Approving Committee Deputy Director of Finance and Information
IT Monitoring Code of Practice 1.4 University of Ulster Code of Practice Cover Sheet Document Title IT Monitoring Code of Practice 1.4 Custodian Approving Committee Deputy Director of Finance and Information
Stateful Inspection Technology
 Stateful Inspection Technology Security Requirements TECH NOTE In order to provide robust security, a firewall must track and control the flow of communication passing through it. To reach control decisions
Stateful Inspection Technology Security Requirements TECH NOTE In order to provide robust security, a firewall must track and control the flow of communication passing through it. To reach control decisions
BRISSkit: Biomedical Research Infrastructure Software Service kit. Jonathan Tedds. http://www.le.ac.uk/brisskit #brisskit #umfcloud
 BRISSkit: Biomedical Research Infrastructure Software Service kit http://www.le.ac.uk/brisskit #brisskit #umfcloud Jonathan Tedds University of Leicester jat26@le.ac.uk @jtedds JISC University Modernisation
BRISSkit: Biomedical Research Infrastructure Software Service kit http://www.le.ac.uk/brisskit #brisskit #umfcloud Jonathan Tedds University of Leicester jat26@le.ac.uk @jtedds JISC University Modernisation
FileRunner Security Overview. An overview of the security protocols associated with the FileRunner file delivery application
 FileRunner Security Overview An overview of the security protocols associated with the FileRunner file delivery application Overview Sohonet FileRunner is a secure high-speed transfer application that
FileRunner Security Overview An overview of the security protocols associated with the FileRunner file delivery application Overview Sohonet FileRunner is a secure high-speed transfer application that
Integrating SharePoint Sites within WebSphere Portal
 Integrating SharePoint Sites within WebSphere Portal November 2007 Contents Executive Summary 2 Proliferation of SharePoint Sites 2 Silos of Information 2 Security and Compliance 3 Overview: Mainsoft SharePoint
Integrating SharePoint Sites within WebSphere Portal November 2007 Contents Executive Summary 2 Proliferation of SharePoint Sites 2 Silos of Information 2 Security and Compliance 3 Overview: Mainsoft SharePoint
NCS. EMS/NMS Platforms for Network Equipment Providers
 NCS EMS/NMS Platforms for Network Equipment Providers NCS Overview Tail-f s Network Control System (NCS) is a powerful solution for developing centralized management platforms that configure and element
NCS EMS/NMS Platforms for Network Equipment Providers NCS Overview Tail-f s Network Control System (NCS) is a powerful solution for developing centralized management platforms that configure and element
Migrating an Identity Resolution software to open source
 Migrating an Identity Resolution software to open source www.xoriant.com Client Overview Our client is a leading developer and provider of identity resolution (entity analytics) software for government
Migrating an Identity Resolution software to open source www.xoriant.com Client Overview Our client is a leading developer and provider of identity resolution (entity analytics) software for government
Migrating your custom settings to version 7.6
 Migrating your custom settings to version 7.6 Webinar July 2011 web security data security email security 2009, Inc. All rights reserved. Webinar Presenter Greg Didier Title: Support Specialist Accomplishments:
Migrating your custom settings to version 7.6 Webinar July 2011 web security data security email security 2009, Inc. All rights reserved. Webinar Presenter Greg Didier Title: Support Specialist Accomplishments:
BUSINESSOBJECTS DATA INTEGRATOR
 PRODUCTS BUSINESSOBJECTS DATA INTEGRATOR IT Benefits Correlate and integrate data from any source Efficiently design a bulletproof data integration process Improve data quality Move data in real time and
PRODUCTS BUSINESSOBJECTS DATA INTEGRATOR IT Benefits Correlate and integrate data from any source Efficiently design a bulletproof data integration process Improve data quality Move data in real time and
Internet Quality of Service
 Internet Quality of Service Weibin Zhao zwb@cs.columbia.edu 1 Outline 1. Background 2. Basic concepts 3. Supporting mechanisms 4. Frameworks 5. Policy & resource management 6. Conclusion 2 Background:
Internet Quality of Service Weibin Zhao zwb@cs.columbia.edu 1 Outline 1. Background 2. Basic concepts 3. Supporting mechanisms 4. Frameworks 5. Policy & resource management 6. Conclusion 2 Background:
Jitterbit Technical Overview : Microsoft Dynamics CRM
 Jitterbit allows you to easily integrate Microsoft Dynamics CRM with any cloud, mobile or on premise application. Jitterbit s intuitive Studio delivers the easiest way of designing and running modern integrations
Jitterbit allows you to easily integrate Microsoft Dynamics CRM with any cloud, mobile or on premise application. Jitterbit s intuitive Studio delivers the easiest way of designing and running modern integrations
How To Create A Network Monitoring System (Flowmon) In Avea-Tech (For Free)
 Network Traffic Performance & Security Monitoring Project proposal minimal project Orsenna;Invea-Tech FLOWMON PROBES 1000 & 100 Contents 1. Introduction... 2 1.1. General System Requirements... 2 1.2.
Network Traffic Performance & Security Monitoring Project proposal minimal project Orsenna;Invea-Tech FLOWMON PROBES 1000 & 100 Contents 1. Introduction... 2 1.1. General System Requirements... 2 1.2.
Introduction to SAML
 Introduction to THE LEADER IN API AND CLOUD GATEWAY TECHNOLOGY Introduction to Introduction In today s world of rapidly expanding and growing software development; organizations, enterprises and governments
Introduction to THE LEADER IN API AND CLOUD GATEWAY TECHNOLOGY Introduction to Introduction In today s world of rapidly expanding and growing software development; organizations, enterprises and governments
Proxy Server, Network Address Translator, Firewall. Proxy Server
 Proxy Server, Network Address Translator, Firewall 1 Proxy Server 2 1 Introduction What is a proxy server? Acts on behalf of other clients, and presents requests from other clients to a server. Acts as
Proxy Server, Network Address Translator, Firewall 1 Proxy Server 2 1 Introduction What is a proxy server? Acts on behalf of other clients, and presents requests from other clients to a server. Acts as
LSF HEALTH SYSTEMS Information Technology Plan
 LSF HEALTH SYSTEMS Information Technology Plan I. INTRODUCTION The LSF Health Systems software is a web-enabled, secure website providing access to LSF, the Provider Network and DCF. At this time, the
LSF HEALTH SYSTEMS Information Technology Plan I. INTRODUCTION The LSF Health Systems software is a web-enabled, secure website providing access to LSF, the Provider Network and DCF. At this time, the
Securing Physician and Patient Portals for HIPAA Compliance
 Securing Physician and Patient Portals for HIPAA Compliance HIPAA Summit VIII Session 2.04 1:00 2:00 pm March 8 1 Agenda Identity and Access Management Technology and HIPAA Requirements Bob Tahmaseb, Principal
Securing Physician and Patient Portals for HIPAA Compliance HIPAA Summit VIII Session 2.04 1:00 2:00 pm March 8 1 Agenda Identity and Access Management Technology and HIPAA Requirements Bob Tahmaseb, Principal
Policy Management: The Avenda Approach To An Essential Network Service
 End-to-End Trust and Identity Platform White Paper Policy Management: The Avenda Approach To An Essential Network Service http://www.avendasys.com email: info@avendasys.com email: sales@avendasys.com Avenda
End-to-End Trust and Identity Platform White Paper Policy Management: The Avenda Approach To An Essential Network Service http://www.avendasys.com email: info@avendasys.com email: sales@avendasys.com Avenda
nexus Hybrid Access Gateway
 Product Sheet nexus Hybrid Access Gateway nexus Hybrid Access Gateway nexus Hybrid Access Gateway uses the inherent simplicity of virtual appliances to create matchless security, even beyond the boundaries
Product Sheet nexus Hybrid Access Gateway nexus Hybrid Access Gateway nexus Hybrid Access Gateway uses the inherent simplicity of virtual appliances to create matchless security, even beyond the boundaries
LUCENT S ENTRY INTO NETWORK SECURITY
 LUCENT S ENTRY INTO NETWORK SECURITY and Distributed System Security Symposium March 12, 1998 H. M. Gittleson Director, Internet Security Products Group 1 Traffic Growth In Voice And Data Services 250
LUCENT S ENTRY INTO NETWORK SECURITY and Distributed System Security Symposium March 12, 1998 H. M. Gittleson Director, Internet Security Products Group 1 Traffic Growth In Voice And Data Services 250
RealMe. Technology Solution Overview. Version 1.0 Final September 2012. Authors: Mick Clarke & Steffen Sorensen
 RealMe Technology Solution Overview Version 1.0 Final September 2012 Authors: Mick Clarke & Steffen Sorensen 1 What is RealMe? RealMe is a product that offers identity services for people to use and manage
RealMe Technology Solution Overview Version 1.0 Final September 2012 Authors: Mick Clarke & Steffen Sorensen 1 What is RealMe? RealMe is a product that offers identity services for people to use and manage
Online Identity Attribute Exchange 2013-2014 Initiatives
 Online Identity Attribute Exchange 2013-2014 Initiatives Agenda Overview AXN Services Framework Demonstration NSTIC Pilots Summary ABAC Services Attribute Exchange Network Page 2 AXN - Enabling IT & Other
Online Identity Attribute Exchange 2013-2014 Initiatives Agenda Overview AXN Services Framework Demonstration NSTIC Pilots Summary ABAC Services Attribute Exchange Network Page 2 AXN - Enabling IT & Other
E-Health: Chances and Challenges of Distributed Service oriented Architectures
 E-Health: Chances and Challenges of Distributed Service oriented Architectures Prof. Christoph Thuemmler, PhD Centre for Applied E-Health Edinburgh Napier University C.Thuemmler@napier.ac.uk 2011 Dr. Lu
E-Health: Chances and Challenges of Distributed Service oriented Architectures Prof. Christoph Thuemmler, PhD Centre for Applied E-Health Edinburgh Napier University C.Thuemmler@napier.ac.uk 2011 Dr. Lu
Oracle Real Time Decisions
 A Product Review James Taylor CEO CONTENTS Introducing Decision Management Systems Oracle Real Time Decisions Product Architecture Key Features Availability Conclusion Oracle Real Time Decisions (RTD)
A Product Review James Taylor CEO CONTENTS Introducing Decision Management Systems Oracle Real Time Decisions Product Architecture Key Features Availability Conclusion Oracle Real Time Decisions (RTD)
An Oracle White Paper Dec 2013. Oracle Access Management Security Token Service
 An Oracle White Paper Dec 2013 Oracle Access Management Security Token Service Disclaimer The following is intended to outline our general product direction. It is intended for information purposes only,
An Oracle White Paper Dec 2013 Oracle Access Management Security Token Service Disclaimer The following is intended to outline our general product direction. It is intended for information purposes only,
Using Entrust certificates with VPN
 Entrust Managed Services PKI Using Entrust certificates with VPN Document issue: 1.0 Date of issue: May 2009 Copyright 2009 Entrust. All rights reserved. Entrust is a trademark or a registered trademark
Entrust Managed Services PKI Using Entrust certificates with VPN Document issue: 1.0 Date of issue: May 2009 Copyright 2009 Entrust. All rights reserved. Entrust is a trademark or a registered trademark
Centrify Cloud Connector Deployment Guide
 C E N T R I F Y D E P L O Y M E N T G U I D E Centrify Cloud Connector Deployment Guide Abstract Centrify provides mobile device management and single sign-on services that you can trust and count on as
C E N T R I F Y D E P L O Y M E N T G U I D E Centrify Cloud Connector Deployment Guide Abstract Centrify provides mobile device management and single sign-on services that you can trust and count on as
SOA FOUNDATION DEFINITIONS
 SOA FOUNDATION DEFINITIONS SOA Blueprint A structured blog by Yogish Pai The SOA foundation components are illustrated in the figure below. Figure 1: SOA Foundation Business Architecture Business architecture
SOA FOUNDATION DEFINITIONS SOA Blueprint A structured blog by Yogish Pai The SOA foundation components are illustrated in the figure below. Figure 1: SOA Foundation Business Architecture Business architecture
IBM Tivoli Federated Identity Manager
 IBM Tivoli Federated Identity Manager Employ user-centric federated access management to enable secure online business collaboration Highlights Enhance business-to-business and business-to-consumer collaborations
IBM Tivoli Federated Identity Manager Employ user-centric federated access management to enable secure online business collaboration Highlights Enhance business-to-business and business-to-consumer collaborations
A Step-by-Step Guide to Defining Your Cloud Services Catalog
 A Step-by-Step Guide to Defining Your Cloud Services Catalog Table of Contents Introduction Chapter 1 Defining the Services Catalog Chapter 2 Building a Services Catalog Chapter 3 Choosing the Right Solution
A Step-by-Step Guide to Defining Your Cloud Services Catalog Table of Contents Introduction Chapter 1 Defining the Services Catalog Chapter 2 Building a Services Catalog Chapter 3 Choosing the Right Solution
360 Application Performance Management
 White Paper 360 Application Performance Management Best Practices for Gaining Comprehensive Visibility Into Enterprise Application Performance Publication Date: December 2008 Abstract: APM focuses on monitoring
White Paper 360 Application Performance Management Best Practices for Gaining Comprehensive Visibility Into Enterprise Application Performance Publication Date: December 2008 Abstract: APM focuses on monitoring
PROPALMS TSE 6.0 March 2008
 PROPALMS March 2008 An Analysis of and Terminal Services: Contents System Administration... 2 Server Management... 3 Application Management... 5 Security... 7 End User Experience... 8 Monitoring and Reporting...
PROPALMS March 2008 An Analysis of and Terminal Services: Contents System Administration... 2 Server Management... 3 Application Management... 5 Security... 7 End User Experience... 8 Monitoring and Reporting...
1.0 VOLUME 2, SECTION 2.13
 1.0 VOLUME 2, SECTION 2.13 (CONTINUED): Networx Operational Support Systems 1.1 2.13.1.4.5 Respond to technical support. The (3)Enterprise portal will provide a link to respond to technical support questions
1.0 VOLUME 2, SECTION 2.13 (CONTINUED): Networx Operational Support Systems 1.1 2.13.1.4.5 Respond to technical support. The (3)Enterprise portal will provide a link to respond to technical support questions
PRIVACY AWARE ACCESS CONTROL FOR CLOUD-BASED DATA PLATFORMS
 www.openi-ict.eu Open-Source, Web-Based, Framework for Integrating Applications with Social Media Services and Personal Cloudlets PRIVACY AWARE ACCESS CONTROL FOR CLOUD-BASED DATA PLATFORMS Open-Source,
www.openi-ict.eu Open-Source, Web-Based, Framework for Integrating Applications with Social Media Services and Personal Cloudlets PRIVACY AWARE ACCESS CONTROL FOR CLOUD-BASED DATA PLATFORMS Open-Source,
NetworkingPS Federated Identity Solution Solutions Overview
 NetworkingPS Federated Identity Solution Solutions Overview OVERVIEW As the global marketplace continues to expand, new and innovating ways of conducting business are becoming a necessity in order for
NetworkingPS Federated Identity Solution Solutions Overview OVERVIEW As the global marketplace continues to expand, new and innovating ways of conducting business are becoming a necessity in order for
VividApps Limited Service Definition Document
 VividApps Limited Service Definition Document Page 1 of 10 Overview Reap the Benefits of multiple services from a single application, keeping you proactively connected with your clients. Assurity is a
VividApps Limited Service Definition Document Page 1 of 10 Overview Reap the Benefits of multiple services from a single application, keeping you proactively connected with your clients. Assurity is a
OPENIAM ACCESS MANAGER. Web Access Management made Easy
 OPENIAM ACCESS MANAGER Web Access Management made Easy TABLE OF CONTENTS Introduction... 3 OpenIAM Access Manager Overview... 4 Access Gateway... 4 Authentication... 5 Authorization... 5 Role Based Access
OPENIAM ACCESS MANAGER Web Access Management made Easy TABLE OF CONTENTS Introduction... 3 OpenIAM Access Manager Overview... 4 Access Gateway... 4 Authentication... 5 Authorization... 5 Role Based Access
Current and Future Research into Network Security Prof. Madjid Merabti
 Current and Future Research into Network Security Prof. Madjid Merabti School of Computing & Mathematical Sciences Liverpool John Moores University UK Overview Introduction Secure component composition
Current and Future Research into Network Security Prof. Madjid Merabti School of Computing & Mathematical Sciences Liverpool John Moores University UK Overview Introduction Secure component composition
Reconciliation Best Practice
 INTRODUCTION This paper provides an outline statement of what we consider to be best practice with respect to the use of reconciliation software used by asset managers. It is not a description of any particular
INTRODUCTION This paper provides an outline statement of what we consider to be best practice with respect to the use of reconciliation software used by asset managers. It is not a description of any particular
Web Applications Access Control Single Sign On
 Web Applications Access Control Single Sign On Anitha Chepuru, Assocaite Professor IT Dept, G.Narayanamma Institute of Technology and Science (for women), Shaikpet, Hyderabad - 500008, Andhra Pradesh,
Web Applications Access Control Single Sign On Anitha Chepuru, Assocaite Professor IT Dept, G.Narayanamma Institute of Technology and Science (for women), Shaikpet, Hyderabad - 500008, Andhra Pradesh,
PRIME IDENTITY MANAGEMENT CORE
 PRIME IDENTITY MANAGEMENT CORE For secure enrollment applications processing and workflow management. PRIME Identity Management Core provides the foundation for any biometric identification platform. It
PRIME IDENTITY MANAGEMENT CORE For secure enrollment applications processing and workflow management. PRIME Identity Management Core provides the foundation for any biometric identification platform. It
The Essentials Series: Enterprise Identity and Access Management. Authorization. sponsored by. by Richard Siddaway
 The Essentials Series: Enterprise Identity and Access Management Authorization sponsored by by Richard Siddaway Authorization...1 What Needs to Be Protected?...1 Groups...2 Role-Based Access...2 Heterogeneous
The Essentials Series: Enterprise Identity and Access Management Authorization sponsored by by Richard Siddaway Authorization...1 What Needs to Be Protected?...1 Groups...2 Role-Based Access...2 Heterogeneous
Updated 03/09/15 JKB 08:58 pm. Coats Employee Payment History Portal
 Updated 03/09/15 JKB 08:58 pm Coats Employee Payment History Portal Overview 2 Employee User access to the Portal allows an Employee to update their Personal information, opt into Online W2 s, modify their
Updated 03/09/15 JKB 08:58 pm Coats Employee Payment History Portal Overview 2 Employee User access to the Portal allows an Employee to update their Personal information, opt into Online W2 s, modify their
CounterACT Plugin Configuration Guide for ForeScout Mobile Integration Module MaaS360 Version 1.0.1. ForeScout Mobile
 CounterACT Plugin Configuration Guide for ForeScout Mobile Integration Module Version 1.0.1 ForeScout Mobile Table of Contents About the Integration... 3 ForeScout MDM... 3 Additional Documentation...
CounterACT Plugin Configuration Guide for ForeScout Mobile Integration Module Version 1.0.1 ForeScout Mobile Table of Contents About the Integration... 3 ForeScout MDM... 3 Additional Documentation...
Integrating IBM Cognos 8 BI with 3rd Party Auhtentication Proxies
 Guideline Integrating IBM Cognos 8 BI with 3rd Party Auhtentication Proxies Product(s): IBM Cognos 8 BI Area of Interest: Security Integrating IBM Cognos 8 BI with 3rd Party Auhtentication Proxies 2 Copyright
Guideline Integrating IBM Cognos 8 BI with 3rd Party Auhtentication Proxies Product(s): IBM Cognos 8 BI Area of Interest: Security Integrating IBM Cognos 8 BI with 3rd Party Auhtentication Proxies 2 Copyright
e-gateway SOLUTION OVERVIEW Financials HCM ERP e-gateway Web Applications Mobile Devices SharePoint Portal
 e-gateway SOLUTION OVERVIEW In an effort to manage mission critical information better, perform their daily tasks more efficiently, share information to key stakeholders more effectively, and ensure that
e-gateway SOLUTION OVERVIEW In an effort to manage mission critical information better, perform their daily tasks more efficiently, share information to key stakeholders more effectively, and ensure that
Orchestrate IT Process with an Integrated Workflow Management
 Orchestrate IT Process with an Integrated Workflow Management Table of Contents Introduction...3 What is Workload Automation?...4 Workflow...4 Workload...5 Combining Workflow and Workload...5 CA Workload
Orchestrate IT Process with an Integrated Workflow Management Table of Contents Introduction...3 What is Workload Automation?...4 Workflow...4 Workload...5 Combining Workflow and Workload...5 CA Workload
MANAGING OTT MESSAGING SERVICES FOR A GLOBAL TELECOM PROVIDER
 MANAGING OTT MESSAGING SERVICES FOR A GLOBAL TELECOM PROVIDER Sytel Reply was commissioned by a client (a large global telecom operator) to provide quality Service Assurance. Over a period of 12 months,
MANAGING OTT MESSAGING SERVICES FOR A GLOBAL TELECOM PROVIDER Sytel Reply was commissioned by a client (a large global telecom operator) to provide quality Service Assurance. Over a period of 12 months,
The XACML Enabled Gateway The Entrance to a New SOA Ecosystem
 The XACML Enabled Gateway The Entrance to a New SOA Ecosystem White Paper Intel SOA Expressway and Axiomatics Policy Server Solution Intel SOA Expressway and Axiomatics Policy Server combined provide a
The XACML Enabled Gateway The Entrance to a New SOA Ecosystem White Paper Intel SOA Expressway and Axiomatics Policy Server Solution Intel SOA Expressway and Axiomatics Policy Server combined provide a
QRadar Security Intelligence Platform Appliances
 DATASHEET Total Security Intelligence An IBM Company QRadar Security Intelligence Platform Appliances QRadar Security Intelligence Platform appliances combine typically disparate network and security management
DATASHEET Total Security Intelligence An IBM Company QRadar Security Intelligence Platform Appliances QRadar Security Intelligence Platform appliances combine typically disparate network and security management
Self-Service Active Directory Group Management
 Self-Service Active Directory Group Management 2015 Hitachi ID Systems, Inc. All rights reserved. Hitachi ID Group Manager is a self-service group membership request portal. It allows users to request
Self-Service Active Directory Group Management 2015 Hitachi ID Systems, Inc. All rights reserved. Hitachi ID Group Manager is a self-service group membership request portal. It allows users to request
Provide access control with innovative solutions from IBM.
 Security solutions To support your IT objectives Provide access control with innovative solutions from IBM. Highlights Help protect assets and information from unauthorized access and improve business
Security solutions To support your IT objectives Provide access control with innovative solutions from IBM. Highlights Help protect assets and information from unauthorized access and improve business
Compliance Guide: ASD ISM OVERVIEW
 Compliance Guide: ASD ISM OVERVIEW Australian Information Security Manual Mapping to the Principles using Huntsman INTRODUCTION In June 2010, The Australian Government Protective Security Policy Framework
Compliance Guide: ASD ISM OVERVIEW Australian Information Security Manual Mapping to the Principles using Huntsman INTRODUCTION In June 2010, The Australian Government Protective Security Policy Framework
Securing Enterprise: Employability and HR
 1 Securing Enterprise: Employability and HR Federation and XACML as Security and Access Control Layer Open Standards Forum 2 Employability and HR Vertical Multiple Players - Excellent case for federation
1 Securing Enterprise: Employability and HR Federation and XACML as Security and Access Control Layer Open Standards Forum 2 Employability and HR Vertical Multiple Players - Excellent case for federation
In this chapter, we will introduce works related to our research. First, we will
 Chapter 2 Related Works In this chapter, we will introduce works related to our research. First, we will present the basic concept of directory service and Lightweight Directory Access Protocol (LDAP).
Chapter 2 Related Works In this chapter, we will introduce works related to our research. First, we will present the basic concept of directory service and Lightweight Directory Access Protocol (LDAP).
Dynamism and Data Management in Distributed, Collaborative Working Environments
 Dynamism and Data Management in Distributed, Collaborative Working Environments Alexander Kipp 1, Lutz Schubert 1, Matthias Assel 1 and Terrence Fernando 2, 1 High Performance Computing Center Stuttgart,
Dynamism and Data Management in Distributed, Collaborative Working Environments Alexander Kipp 1, Lutz Schubert 1, Matthias Assel 1 and Terrence Fernando 2, 1 High Performance Computing Center Stuttgart,
Service-Oriented Architectures
 Architectures Computing & 2009-11-06 Architectures Computing & SERVICE-ORIENTED COMPUTING (SOC) A new computing paradigm revolving around the concept of software as a service Assumes that entire systems
Architectures Computing & 2009-11-06 Architectures Computing & SERVICE-ORIENTED COMPUTING (SOC) A new computing paradigm revolving around the concept of software as a service Assumes that entire systems
Real-Time Security Intelligence for Greater Visibility and Information-Asset Protection
 Real-Time Security Intelligence for Greater Visibility and Information-Asset Protection Take the Effort Out of Log Management and Gain the Actionable Information You Need to Improve Your Organisation s
Real-Time Security Intelligence for Greater Visibility and Information-Asset Protection Take the Effort Out of Log Management and Gain the Actionable Information You Need to Improve Your Organisation s
API Management: Powered by SOA Software Dedicated Cloud
 Software Dedicated Cloud The Challenge Smartphones, mobility and the IoT are changing the way users consume digital information. They re changing the expectations and experience of customers interacting
Software Dedicated Cloud The Challenge Smartphones, mobility and the IoT are changing the way users consume digital information. They re changing the expectations and experience of customers interacting
Corente Cloud Services Exchange
 Corente Cloud Services Exchange Oracle s Corente Cloud Services Exchange (Corente CSX) is a cloud-based software-defined networking (SDN) solution that enables distributed enterprises to deliver trusted
Corente Cloud Services Exchange Oracle s Corente Cloud Services Exchange (Corente CSX) is a cloud-based software-defined networking (SDN) solution that enables distributed enterprises to deliver trusted
Application Security Best Practices. Matt Tavis Principal Solutions Architect
 Application Security Best Practices Matt Tavis Principal Solutions Architect Application Security Best Practices is a Complex topic! Design scalable and fault tolerant applications See Architecting for
Application Security Best Practices Matt Tavis Principal Solutions Architect Application Security Best Practices is a Complex topic! Design scalable and fault tolerant applications See Architecting for
Data Sharing. Matching and Routing THOUGHT LEADERSHIP. Delivering Transformation. Together.
 THOUGHT LEADERSHIP Data Sharing Matching and Routing Delivering Transformation. Together. Introduction There are many reasons why data needs to be shared in the public sector, and in reality there are
THOUGHT LEADERSHIP Data Sharing Matching and Routing Delivering Transformation. Together. Introduction There are many reasons why data needs to be shared in the public sector, and in reality there are
WHAT ARE THE BENEFITS OF OUTSOURCING NETWORK SECURITY?
 WHAT ARE THE BENEFITS OF OUTSOURCING NETWORK SECURITY? Contents Introduction.... 3 What Types of Network Security Services are Available?... 4 Penetration Testing and Vulnerability Assessment... 4 Cyber
WHAT ARE THE BENEFITS OF OUTSOURCING NETWORK SECURITY? Contents Introduction.... 3 What Types of Network Security Services are Available?... 4 Penetration Testing and Vulnerability Assessment... 4 Cyber
An Oracle White Paper October 2013. Maximize the Benefits of Oracle SOA Suite 11g with Oracle Service Bus
 An Oracle White Paper October 2013 Maximize the Benefits of Oracle SOA Suite 11g with Oracle Service Bus Maximize the Benefits of Oracle SOA Suite 11g with Oracle Service Bus Table of Contents Introduction...
An Oracle White Paper October 2013 Maximize the Benefits of Oracle SOA Suite 11g with Oracle Service Bus Maximize the Benefits of Oracle SOA Suite 11g with Oracle Service Bus Table of Contents Introduction...
Oracle Role Manager. An Oracle White Paper Updated June 2009
 Oracle Role Manager An Oracle White Paper Updated June 2009 Oracle Role Manager Introduction... 3 Key Benefits... 3 Features... 5 Enterprise Role Lifecycle Management... 5 Organization and Relationship
Oracle Role Manager An Oracle White Paper Updated June 2009 Oracle Role Manager Introduction... 3 Key Benefits... 3 Features... 5 Enterprise Role Lifecycle Management... 5 Organization and Relationship
When millions need access: Identity management in an increasingly connected world
 IBM Software Thought Leadership White Paper January 2011 When millions need access: Identity management in an increasingly connected world Best practice solutions that scale to meet today s huge numbers
IBM Software Thought Leadership White Paper January 2011 When millions need access: Identity management in an increasingly connected world Best practice solutions that scale to meet today s huge numbers
CS/ECE 438: Communication Networks. Internet QoS. Syed Faisal Hasan, PhD (Research Scholar Information Trust Institute) Visiting Lecturer ECE
 CS/ECE 438: Communication Networks Internet QoS Syed Faisal Hasan, PhD (Research Scholar Information Trust Institute) Visiting Lecturer ECE Introduction The Internet only provides a best effort service
CS/ECE 438: Communication Networks Internet QoS Syed Faisal Hasan, PhD (Research Scholar Information Trust Institute) Visiting Lecturer ECE Introduction The Internet only provides a best effort service
Claims Management for the London Market
 for the London Market is a complete lifecycle claims solution, driving efficiencies and speed of handling claims. It guides claims handlers through the complex process of dealing with the progress of a
for the London Market is a complete lifecycle claims solution, driving efficiencies and speed of handling claims. It guides claims handlers through the complex process of dealing with the progress of a
Architecture, Implementations, Integrations, and Technical Overview
 Architecture, Implementations, Integrations, and Technical Overview Introduction System Architecture & Infrastructure Implementation Parent Portal Medical Center Strategy Integrations SIS Immunization
Architecture, Implementations, Integrations, and Technical Overview Introduction System Architecture & Infrastructure Implementation Parent Portal Medical Center Strategy Integrations SIS Immunization
TEAL: Transparent Email Archiving Library
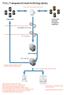 TEAL: Transparent Email Archiving Library 1. Users send & receive email as per normal 2. Existing customer filters remove spam & viruses Filters (Spam, Anti-Virus) 3. Interceptor agent takes a copy of
TEAL: Transparent Email Archiving Library 1. Users send & receive email as per normal 2. Existing customer filters remove spam & viruses Filters (Spam, Anti-Virus) 3. Interceptor agent takes a copy of
White Paper Cybercom & Axiomatics Joint Identity & Access Management (R)evolution
 White Paper Cybercom & Axiomatics Joint Identity & Access Management (R)evolution Federation and Attribute Based Access Control Page 2 Realization of the IAM (R)evolution Executive Summary Many organizations
White Paper Cybercom & Axiomatics Joint Identity & Access Management (R)evolution Federation and Attribute Based Access Control Page 2 Realization of the IAM (R)evolution Executive Summary Many organizations
Michigan Criminal Justice Information Network (MiCJIN) State of Michigan Department of Information Technology & Michigan State Police
 Michigan Criminal Justice Information Network (MiCJIN) State of Michigan Department of Information Technology & Michigan State Police NASCIO 2006 Recognition Awards Enterprise Architecture Category Executive
Michigan Criminal Justice Information Network (MiCJIN) State of Michigan Department of Information Technology & Michigan State Police NASCIO 2006 Recognition Awards Enterprise Architecture Category Executive
PRIVACY IMPLICATIONS FOR NEXT GENERATION SIEMs AND OTHER META-SYSTEMS
 PRIVACY IMPLICATIONS FOR NEXT GENERATION SIEMs AND OTHER META-SYSTEMS www.massif-project.eu Dr Andrew Hutchison T-Systems (andrew.hutchison@t-systems.com) MAanagement of Security information and events
PRIVACY IMPLICATIONS FOR NEXT GENERATION SIEMs AND OTHER META-SYSTEMS www.massif-project.eu Dr Andrew Hutchison T-Systems (andrew.hutchison@t-systems.com) MAanagement of Security information and events
Overview of Network Architecture Alternatives for 3GPP2 Femto Cells Jen M. Chen, et al. QUALCOMM Incorporated
 3GPP2 Workshop, Boston, MA Title: Source: Contact: Overview of Network Architecture Alternatives for 3GPP2 Femto Cells Jen M. Chen, et al. QUALCOMM Incorporated Jen M. Chen QUALCOMM Incorporated 858-658-2543
3GPP2 Workshop, Boston, MA Title: Source: Contact: Overview of Network Architecture Alternatives for 3GPP2 Femto Cells Jen M. Chen, et al. QUALCOMM Incorporated Jen M. Chen QUALCOMM Incorporated 858-658-2543
Enterprise Solution for Remote Desktop Services... 2. System Administration... 3. Server Management... 4. Server Management (Continued)...
 CONTENTS Enterprise Solution for Remote Desktop Services... 2 System Administration... 3 Server Management... 4 Server Management (Continued)... 5 Application Management... 6 Application Management (Continued)...
CONTENTS Enterprise Solution for Remote Desktop Services... 2 System Administration... 3 Server Management... 4 Server Management (Continued)... 5 Application Management... 6 Application Management (Continued)...
