Architecture, Implementations, Integrations, and Technical Overview
|
|
|
- Neal Bishop
- 8 years ago
- Views:
Transcription
1 Architecture, Implementations, Integrations, and Technical Overview Introduction System Architecture & Infrastructure Implementation Parent Portal Medical Center Strategy Integrations SIS Immunization Registry Provider EMRs Security User authentication & authorization Roles & Permissions User Account Controls Auditing Technology Stack Data Model HIPAA & FERPA Introduction CareDox is a care coordination system for parents and schools. By facilitating an integrated conduit of health information between families, schools, and the healthcare ecosystem CareDox is increasing efficiencies and ensuring student safety. CareDox integrates with Student Information Systems (SIS), Immunization Registries (IIS), and Healthcare Provider Electronic Medical Record (EMR) systems. Ensuring high fidelity medical information flows betweens systems is CareDox s lifeblood. CareDox has been built from the ground up with security and infrastructure robustness in mind, as well as being a mobile optimized modern web application. Dealing with student data, personal health records, and clinical data in a safe and HIPAA & FERPA compliant 1
2 fashion is one of our top priorities. CareDox enables secure sharing of this information only to authorized personnel, which we believe will bring unilateral portability to the healthcare ecosystem, and therefore is a paramount goal of the company. This document will cover the following areas: System Architecture & Infrastructure Integrations SISs, IISs, and EMRs Security User authentication & authorization Technology Stack Data model Auditing HIPAA & FERPA compliance Any questions or concerns can be directed to our CTO Benjamin Maisano ben@caredox.com System Architecture & Infrastructure 2
3 3
4 CareDox s cloud infrastructure and web delivery means there is no hardware to provision for schools or software to install for users. Only select internal employees have access to our production system devices, and their access is audited and reviewed periodically. Our technical team has live system and application level monitoring in place so we know about any issue or build up of a potential issue before end users are impacted. We have real time back with a 30 second delay of all information and nightly snapshot backups of our entire database. We are hosted in AWS so we can scale quickly to meet the demands of large public districts. Our Business Associates Agreements (BAA) with schools provides piece of mind for data security and integrity, including our cloud infrastructure. 4
5 Implementation CareDox is very mindful of school staff s time and tries to be as responsive as possible. We can typically onboard your district within two weeks of a kickoff call with key stakeholders like Head of Student Services, Head of Health, and Head of Technology. Implementation plans can involve phased rollouts to select schools and staff first. We can load all existing student and medical information into CareDox from SIS and legacy health systems so your staff starts with a primed system, not a blank slate. Onboarding options typically include either a Parent Portal first strategy or a Medical Center first strategy. Parent Portal If your priority is getting parents engaged, ensuring you have the latest medical information, and completing medical registration we recommend the parent first option. We will digitize your paper forms, host other PDF templates, and setup all customizations and configurations. We then load any information you already have in your SIS and your state Immunization Registry so parents can just come in and fill in the blanks. Nurses will be able to review all submitted information 5
6 6
7 Medical Center Strategy Selecting nurses to try out the system first means they can start using CareDox to record visits, medications, screenings, and other staff events. Our state of the art Medical Center module is a full service clinical EMR. 7
8 Checkout our product screenshots for more visuals on the system here. Integrations CareDox can integrate with a variety of systems for student and medical information: SISs Student Information Systems IISs Immunization Registries EMRs Electronic Medical Record provider systems HIX State Health Information exchanges Integrations with these systems are covered under our typical three year contract for professional services at no additional cost. SIS CareDox integrates with SISs for the following pieces of information: Student Demographic and Enrollment information (ex. Student Id, grade, address) Parent information (ex. address, cell phone) Immunization Information Emergency Contact Information Medical Alerts, Conditions, and Allergies 8
9 Attendance Staff (ex. s, roles) CareDox can integrate in different ways: RealTime API integrations Event based (ex when a parent adds an allergy mid year) Schedule based every night or weekend syncup CareDox can integrate in many different methods: REST and SOAP Web Service APIs CSV files transferred via SFTP Single Sign On (SSO) for user info and authentication Custom CareDox supports as part of our standard contract expected professional services time to setup integrations. We will generally support and work with the district on what type of integration they desire and can support. Below is the recommended integration steps: 1. CareDox sets up a secure SFTP site solely for the district to transfer any CSV files. 2. Initial Student enrollment/roster file generated in CSV from district tech team. CareDox will provide the CSV specification to the team immediately. This gets the ball rolling while in parallel a more robust and integrated approach is planned with tech team. 9
10 3. If SIS has API available CareDox will provide a configuration file (plugin.xml, security token) for the district admin to authorize a one time setup for CareDox integration. CareDox will then perform connectivity and data tests with the SIS. a. API used to sync student/roster changes b. API used to capture medical information one time, afterwards CareDox becomes system of record for medical information c. API used to push medical information to SIS from CareDox 4. If SIS does not support API CareDox can setup monitoring jobs on the SFTP site for file transfers. a. CSV importers setup for student/roster sync b. CSV exporters setup for medical information Medical Information Exports CareDox can push the following medical information to SIS: Allergies Conditions Medications Medical Alerts Immunizations Diet Restrictions Provider / Physician info Insurance Info The details of the file formats CareDox providers for CSV exporters can be found here. Immunization Registry CareDox integrates with many state registries that support HL specification over a REST or SOAP web service. This allows us to automatically pull down immunization data an entire district at once. This includes vaccine groups, vaccine codes, administration dates, administered by provider details, lot numbers, and other exemption details. Provider EMRs CareDox Provider EMR integrations are custom and setup after a district has launched and CareDox analyzes the top providers in the area. Integrations include ACO care coordination systems, hospital systems, and doctor practice EMRs. The primary use cases to streamline include: Doctor signatures for medications Doctor signatures for IHPs, 504s, and IEPs Loading medical information from EMRs 10
11 Passing information in a HIPAA and FERPA compliant way to authorized EMRs on nurse request. Nurse and Doctor collaborations Parent and Doctor collaborations De identified reporting and analytics data for care coordination population health models. 11
12 Security - User authentication & authorization CareDox is a care coordination system for parents and schools. This means we have a large number of different types of users, including Parents Nurses Teachers District Admins School staff Cafeteria staff Sports / Athletic team coaches Physicians (partial/future) Users access the system after registering their address from an invitation. Passwords are one way hashed and stored encrypted in the database. Single Sign On (SSO) options are also available for authentication. Each user is setup in different security roles, and therefore see a varying degree of features, actions, and data based on that roles permission set. 12
13 Roles & Permissions CareDox users are put into one or more roles, which have a list of permissions: 13
14 Each Role Permission has a qualifier, one of: Read Only Can only view the information, excluding health data marked private Edit can create, update, delete all information in the given permission category and see/edit private items 14
15 15
16 Users are added to the system self service by an admin or auto loaded from SIS: 16
17 Users can be assigned to certain sessions (Grade, Sports Team), schools, or a combination. User Account Controls CareDox requires every user to login to the system, which issues them a security token in a browser cookie. This token expires after 30 minutes of inactivity. The user will be prompted 1 minute before and then automatically logged out. 17
18 User accounts will be locked if 10 invalid attempts to login happen within a short time frame. Users can recover forgotten passwords through . 18
19 Auditing CareDox tracks all changes to health record data, including: Who which user What which child item of health record When exact time Where via IP Address Before & After comparison list of all changes made to given item 19
20 Technology Stack CareDox uses modern open source technologies to build our applications. Our team of professionally skilled engineers constantly evaluates new technologies, important upgrades, and broad trends going on in the industry. We have an aggressive patch maintenance schedule for all our systems and software to ensure we are always running with the latest security and bug fixes for any frameworks and libraries we depend on. Supported Browsers CareDox is fully delivered through HTML5 compliant web browsers. We test and support the latest browser versions and latest 1 versions for: Chrome FireFox Safari Internet Explorer Mobile Android & ios 20
21 21
22 Data Model This diagram shows at a high level how all our data entities relate to each other. All a student s key medical information is bucketed into a master health record. Each detailed item has a full audit history for every change made. Users (i.e. Parents or Nurses) are given access to health records. Health records are portable entities that a family owns, therefore they are not directly bucketed under schools. A health record s relationship to an organization is established through an enrollment or clinical visit. All configuration and custom forms for the district are linked through an enrollment as well, so other organizations (ie another district or camp) will never see each others notes, forms, or district owned data. 22
23 HIPAA & FERPA CareDox security and auditing go beyond what is required by HIPAA & FERPA law. Below is a summary of how CareDox is compliant, this does not cover all aspects of the law. CareDox with enter into Business Associate Agreements (BAA) with any 3rd parties and schools that it shares data with or that host HIPAA covered data. HIPAA has three main rules 1. Privacy Rule 2. Security Rule 3. Breach Notification Rule The Privacy Rule is concerned with the protection of Personal Health Information (PHI). This generally means anything that is specific and private to a given patient, including: Name, Address, Date of Birth, SSN Phone numbers & addresses Device or other ids used to track the person A full face photo of the person Medical profile information like allergies, conditions, medications, etc Claims, provider, or other discharge or medical process documentation. The Security Rule rule is concerned with the below, and how it related to CareDox: Technical Authentication & Access Control User s, passwords, roles, and permissions Audit Controls audit history of changes and logs of actions Integrity Data alterations only by who is authenticated and authorized Transmission Security https encrypted Physical Facility Access Controls office and data centers locked Workstation Use internal employees have password on devices, firewalls Device and Media Controls encrypted hard drives, no sharing USB sticks Administrative Security Management Process process for who has and gives out access Information Access Management production information cannot be shared Security Awareness and Training employee training Security Incident Procedures monitoring & response protocols Business Associate Contracts and Other Arrangements 3rd parties must also be HIPAA compliant and agree to such. FERPA law gives parents rights to their child s data, students rights to review their data, and requires schools to obtain consent when sharing student information. Generally the same technical and privacy concepts apply. 23
A Nemaris Company. Formal Privacy & Security Assessment For Surgimap version 2.2.6 and higher
 A Nemaris Company Formal Privacy & Security Assessment For Surgimap version 2.2.6 and higher 306 East 15 th Street Suite 1R, New York, New York 10003 Application Name Surgimap Vendor Nemaris Inc. Version
A Nemaris Company Formal Privacy & Security Assessment For Surgimap version 2.2.6 and higher 306 East 15 th Street Suite 1R, New York, New York 10003 Application Name Surgimap Vendor Nemaris Inc. Version
Healthcare Compliance Solutions
 Privacy Compliance Healthcare Compliance Solutions Trust and privacy are essential for building meaningful human relationships. Let Protected Trust be your Safe Harbor The U.S. Department of Health and
Privacy Compliance Healthcare Compliance Solutions Trust and privacy are essential for building meaningful human relationships. Let Protected Trust be your Safe Harbor The U.S. Department of Health and
ITAR Compliant Data Exchange
 ITAR Compliant Data Exchange Managing ITAR Data Across Collaborative Project Teams WebSpace Customers Aerospace & Defense Manufacturing High Tech & Contract Manufacturing Automotive Manufacturing Medical/
ITAR Compliant Data Exchange Managing ITAR Data Across Collaborative Project Teams WebSpace Customers Aerospace & Defense Manufacturing High Tech & Contract Manufacturing Automotive Manufacturing Medical/
NOTE: New directions for accessing the Parent Portal using Single Sign On
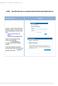 NOTE: New directions for accessing the Parent Portal using Single Sign On PROCESS STEPS SCREEN SHOTS Launch a web browser (Internet Explorer, Safari, or FireFox) and go to PowerSchool Parent Portal URL:
NOTE: New directions for accessing the Parent Portal using Single Sign On PROCESS STEPS SCREEN SHOTS Launch a web browser (Internet Explorer, Safari, or FireFox) and go to PowerSchool Parent Portal URL:
Vodafone Secure Device Manager Administration User Guide
 Vodafone Secure Device Manager Administration User Guide Vodafone New Zealand Limited. Correct as of September 2014. Do business better Contents Introduction 3 Help 4 How to find help in the Vodafone Secure
Vodafone Secure Device Manager Administration User Guide Vodafone New Zealand Limited. Correct as of September 2014. Do business better Contents Introduction 3 Help 4 How to find help in the Vodafone Secure
Secure Data Hosting. Your data is our top priority.
 Secure Data Hosting Your data is our top priority. ESO s world-class security infrastructure is designed to provide data redundancy, security and availability while keeping sensitive HIPAA and PHI information
Secure Data Hosting Your data is our top priority. ESO s world-class security infrastructure is designed to provide data redundancy, security and availability while keeping sensitive HIPAA and PHI information
Optum ID Migration for Provider Express Users
 Introducing Optum ID FREQUENTLY ASKED QUESTIONS Optum ID Migration for Provider Express Users 1. What is Optum ID? A1. Optum ID is a centralized, secure identity management solution that enables a single
Introducing Optum ID FREQUENTLY ASKED QUESTIONS Optum ID Migration for Provider Express Users 1. What is Optum ID? A1. Optum ID is a centralized, secure identity management solution that enables a single
Mobile Iron User Guide
 2015 Mobile Iron User Guide Information technology Sparrow Health System 9/1/2015 Contents...0 Introduction...2 Changes to your Mobile Device...2 Self Service Portal...3 Registering your new device...4
2015 Mobile Iron User Guide Information technology Sparrow Health System 9/1/2015 Contents...0 Introduction...2 Changes to your Mobile Device...2 Self Service Portal...3 Registering your new device...4
Feature List for Kaspersky Password Manager
 Feature List for Kaspersky Password Manager Overview... Features by Platform...3 Feature Descriptions...4 Glossary...7 PAGE Feature List for Kaspersky Password Manager Overview Kaspersky Password Manager
Feature List for Kaspersky Password Manager Overview... Features by Platform...3 Feature Descriptions...4 Glossary...7 PAGE Feature List for Kaspersky Password Manager Overview Kaspersky Password Manager
The CIO s Guide to HIPAA Compliant Text Messaging
 The CIO s Guide to HIPAA Compliant Text Messaging Executive Summary The risks associated with sending Electronic Protected Health Information (ephi) via unencrypted text messaging are significant, especially
The CIO s Guide to HIPAA Compliant Text Messaging Executive Summary The risks associated with sending Electronic Protected Health Information (ephi) via unencrypted text messaging are significant, especially
Georgia Immunization Registry (GRITS)
 Georgia Immunization Registry (GRITS) Frequently Asked Questions How do I... Obtain a copy of my immunization records? To request an immunization record from GRITS: Please use the Immunization Record Request
Georgia Immunization Registry (GRITS) Frequently Asked Questions How do I... Obtain a copy of my immunization records? To request an immunization record from GRITS: Please use the Immunization Record Request
Research Information Security Guideline
 Research Information Security Guideline Introduction This document provides general information security guidelines when working with research data. The items in this guideline are divided into two different
Research Information Security Guideline Introduction This document provides general information security guidelines when working with research data. The items in this guideline are divided into two different
AD Self-Service Suite for Active Directory
 The Dot Net Factory AD Self-Service Suite for Active Directory Version 3.6 The Dot Net Factory, LLC. 2005-2011. All rights reserved. This guide contains proprietary information, which is protected by copyright.
The Dot Net Factory AD Self-Service Suite for Active Directory Version 3.6 The Dot Net Factory, LLC. 2005-2011. All rights reserved. This guide contains proprietary information, which is protected by copyright.
Table of Contents. FME Cloud Architecture Overview. Secure Operations. Application Security. Shared Responsibility.
 FME Cloud Security Table of Contents FME Cloud Architecture Overview Secure Operations I. Backup II. Data Governance and Privacy III. Destruction of Data IV. Incident Reporting V. Development VI. Customer
FME Cloud Security Table of Contents FME Cloud Architecture Overview Secure Operations I. Backup II. Data Governance and Privacy III. Destruction of Data IV. Incident Reporting V. Development VI. Customer
Frequently Asked Questions
 Frequently Asked Questions What is an electronic health record? Borgess has transitioned from paper-based medical records to electronic health records (EHRs). An EHR is an electronic version of your medical
Frequently Asked Questions What is an electronic health record? Borgess has transitioned from paper-based medical records to electronic health records (EHRs). An EHR is an electronic version of your medical
HIPAA Privacy & Security White Paper
 HIPAA Privacy & Security White Paper Sabrina Patel, JD +1.718.683.6577 sabrina@captureproof.com Compliance TABLE OF CONTENTS Overview 2 Security Frameworks & Standards 3 Key Security & Privacy Elements
HIPAA Privacy & Security White Paper Sabrina Patel, JD +1.718.683.6577 sabrina@captureproof.com Compliance TABLE OF CONTENTS Overview 2 Security Frameworks & Standards 3 Key Security & Privacy Elements
HIPAA: MANAGING ACCESS TO SYSTEMS STORING ephi WITH SECRET SERVER
 HIPAA: MANAGING ACCESS TO SYSTEMS STORING ephi WITH SECRET SERVER With technology everywhere we look, the technical safeguards required by HIPAA are extremely important in ensuring that our information
HIPAA: MANAGING ACCESS TO SYSTEMS STORING ephi WITH SECRET SERVER With technology everywhere we look, the technical safeguards required by HIPAA are extremely important in ensuring that our information
How Managed File Transfer Addresses HIPAA Requirements for ephi
 How Managed File Transfer Addresses HIPAA Requirements for ephi 1 A White Paper by Linoma Software INTRODUCTION As the healthcare industry transitions from primarily using paper documents and patient charts
How Managed File Transfer Addresses HIPAA Requirements for ephi 1 A White Paper by Linoma Software INTRODUCTION As the healthcare industry transitions from primarily using paper documents and patient charts
Healthcare Compliance Solutions
 Healthcare Compliance Solutions Let Protected Trust be your Safe Harbor In the Health Information Technology for Economic and Clinical Health Act of 2009 (HITECH), the U.S. Department of Health and Human
Healthcare Compliance Solutions Let Protected Trust be your Safe Harbor In the Health Information Technology for Economic and Clinical Health Act of 2009 (HITECH), the U.S. Department of Health and Human
ILHIE Direct Secure Messaging Solution
 ILHIE Direct Secure Messaging Solution How Secure Messaging Can Improve Patient Care and Help You Achieve Stage 1 Meaningful Use January 2012 1 What is Secure Messaging? Secure Messaging is an encrypted
ILHIE Direct Secure Messaging Solution How Secure Messaging Can Improve Patient Care and Help You Achieve Stage 1 Meaningful Use January 2012 1 What is Secure Messaging? Secure Messaging is an encrypted
New Uses for ROCKET: HIPAA Compliant Workspaces and Other Developments. Tara Helmer Research Services Consultant July 12, 2013
 New Uses for ROCKET: HIPAA Compliant Workspaces and Other Developments Tara Helmer Research Services Consultant July 12, 2013 What is ROCKET(Research, Organization, and Collaboration Knowledge Exchange
New Uses for ROCKET: HIPAA Compliant Workspaces and Other Developments Tara Helmer Research Services Consultant July 12, 2013 What is ROCKET(Research, Organization, and Collaboration Knowledge Exchange
Service Description for Avaya Messaging Service Release 1.0 A hosted Software-as-a-service offering
 Service Description for Avaya Messaging Service Release 1.0 A hosted Software-as-a-service offering Effective Date: October 2013 1 Table of Contents 1 SERVICE TERMS... 5 1.1 Term of Service... 5 1.2 Service
Service Description for Avaya Messaging Service Release 1.0 A hosted Software-as-a-service offering Effective Date: October 2013 1 Table of Contents 1 SERVICE TERMS... 5 1.1 Term of Service... 5 1.2 Service
into HIPAA Ian Campbell and The information a service to Short Act, HIPAA "Administrative use to host contract with an Documentation regulations.
 7 Things all Law Firms (and their IT staff) ) need to know about HIPAA Ian Campbell and Gavin W. Manes, Ph.D. The information contained herein is for informational purposes only as the public, and is not
7 Things all Law Firms (and their IT staff) ) need to know about HIPAA Ian Campbell and Gavin W. Manes, Ph.D. The information contained herein is for informational purposes only as the public, and is not
Cloud Store & Share Frequently Ask Questions
 Cloud Store & Share Frequently Ask Questions Where can I find information about the offer, e.g. the price list? How can I order the service? What is the Cloud Store & Share Client? Where can I download
Cloud Store & Share Frequently Ask Questions Where can I find information about the offer, e.g. the price list? How can I order the service? What is the Cloud Store & Share Client? Where can I download
Emerging Trends in Health Information Technology: Personal Health Record(PHR) uphr. Nazir Ahmed Vaid ehealth Services (Pvt) Ltd.
 Emerging Trends in Health Information Technology: Personal Health Record(PHR) uphr Nazir Ahmed Vaid ehealth Services (Pvt) Ltd. April 26 2012 PROJECT GOALS Design universal health data accessibility on
Emerging Trends in Health Information Technology: Personal Health Record(PHR) uphr Nazir Ahmed Vaid ehealth Services (Pvt) Ltd. April 26 2012 PROJECT GOALS Design universal health data accessibility on
Securing Adobe PDFs. Adobe - Certified Document Services Registration Authority (RA) Training. Enterprise Security. ID Verification Services
 Web Security Enterprise Security ID Verification Services Signing Services Securing Adobe PDFs Adobe - Certified Document Services Registration Authority (RA) Training Introduction to CDS Certified Document
Web Security Enterprise Security ID Verification Services Signing Services Securing Adobe PDFs Adobe - Certified Document Services Registration Authority (RA) Training Introduction to CDS Certified Document
Central Desktop Enterprise Edition (Security Pack)
 Central Desktop Enterprise Edition (Security Pack) The Central Desktop Security Pack is included in the Enterprise Edition of Central Desktop. The Enterprise Edition is for companies and organizations
Central Desktop Enterprise Edition (Security Pack) The Central Desktop Security Pack is included in the Enterprise Edition of Central Desktop. The Enterprise Edition is for companies and organizations
Integrating Cisco ISE with GO!Enterprise MDM Quick Start
 Integrating Cisco ISE with GO!Enterprise MDM Quick Start GO!Enterprise MDM Version 3.x Overview 1 Table of Contents Overview 3 Getting GO!Enterprise MDM Ready for ISE 5 Grant ISE Access to the GO!Enterprise
Integrating Cisco ISE with GO!Enterprise MDM Quick Start GO!Enterprise MDM Version 3.x Overview 1 Table of Contents Overview 3 Getting GO!Enterprise MDM Ready for ISE 5 Grant ISE Access to the GO!Enterprise
Product Manual. MDM On Premise Installation Version 8.1. Last Updated: 06/07/15
 Product Manual MDM On Premise Installation Version 8.1 Last Updated: 06/07/15 Parallels IP Holdings GmbH Vordergasse 59 8200 Schaffhausen Switzerland Tel: + 41 52 632 0411 Fax: + 41 52 672 2010 www.parallels.com
Product Manual MDM On Premise Installation Version 8.1 Last Updated: 06/07/15 Parallels IP Holdings GmbH Vordergasse 59 8200 Schaffhausen Switzerland Tel: + 41 52 632 0411 Fax: + 41 52 672 2010 www.parallels.com
Introduction. Editions
 Introduction TRAIN TRACK Employee Training Management Software gives you the tools you need to make sure employee training requirements are met. Assign required training for groups or individuals. Easily
Introduction TRAIN TRACK Employee Training Management Software gives you the tools you need to make sure employee training requirements are met. Assign required training for groups or individuals. Easily
Cloud Services MDM. ios User Guide
 Cloud Services MDM ios User Guide 10/24/2014 CONTENTS Overview... 3 Supported Devices... 3 System Capabilities... 3 Enrollment and Activation... 4 Download the Agent... 4 Enroll Your Device Using the Agent...
Cloud Services MDM ios User Guide 10/24/2014 CONTENTS Overview... 3 Supported Devices... 3 System Capabilities... 3 Enrollment and Activation... 4 Download the Agent... 4 Enroll Your Device Using the Agent...
Security Tool Kit System Checklist Departmental Servers and Enterprise Systems
 Security Tool Kit System Checklist Departmental Servers and Enterprise Systems INSTRUCTIONS System documentation specifically related to security controls of departmental servers and enterprise systems
Security Tool Kit System Checklist Departmental Servers and Enterprise Systems INSTRUCTIONS System documentation specifically related to security controls of departmental servers and enterprise systems
WHITEPAPER. SECUREAUTH 2-FACTOR AS A SERVICE 2FaaS
 WHITEPAPER SECUREAUTH 2-FACTOR AS A SERVICE 2FaaS EXECUTIVE OVERVIEW 2-Factor as a Service (2FaaS) is a 100% cloud-hosted authentication solution that offers flexible security without compromising user
WHITEPAPER SECUREAUTH 2-FACTOR AS A SERVICE 2FaaS EXECUTIVE OVERVIEW 2-Factor as a Service (2FaaS) is a 100% cloud-hosted authentication solution that offers flexible security without compromising user
FileDrawer An Enterprise File Sharing and Synchronization (EFSS) solution.
 FileDrawer An Enterprise File Sharing and Synchronization (EFSS) solution. In today s world the potential for ready access to data from virtually any device over any type of network connection creates
FileDrawer An Enterprise File Sharing and Synchronization (EFSS) solution. In today s world the potential for ready access to data from virtually any device over any type of network connection creates
Managing policies. Chapter 7
 Chapter 7 Managing policies You use the Policies tab in Admin Portal to create policy sets for roles. A policy set lets you configure the following categories of policies: Mobile Device Policies Use to
Chapter 7 Managing policies You use the Policies tab in Admin Portal to create policy sets for roles. A policy set lets you configure the following categories of policies: Mobile Device Policies Use to
CTERA Portal Datacenter Edition
 Administrator Guide CTERA Portal Datacenter Edition November 2013 Version 4.0 Copyright 2009-2013 CTERA Networks Ltd. All rights reserved. No part of this document may be reproduced in any form or by any
Administrator Guide CTERA Portal Datacenter Edition November 2013 Version 4.0 Copyright 2009-2013 CTERA Networks Ltd. All rights reserved. No part of this document may be reproduced in any form or by any
SchoolBooking SSO Integration Guide
 SchoolBooking SSO Integration Guide Before you start This guide has been written to help you configure SchoolBooking to operate with SSO (Single Sign on) Please treat this document as a reference guide,
SchoolBooking SSO Integration Guide Before you start This guide has been written to help you configure SchoolBooking to operate with SSO (Single Sign on) Please treat this document as a reference guide,
SpringCM Troubleshooting Guide for Salesforce
 SpringCM Troubleshooting Guide for Salesforce July 2013 TABLE OF CONTENTS FAQS:... 3 WHY DID I NOT RECEIVE A SPRINGCM ACTIVATION EMAIL?... 3 WHY DON T MY SALESFORCE USERS HAVE ACCESS TO SPRINGCM?... 3
SpringCM Troubleshooting Guide for Salesforce July 2013 TABLE OF CONTENTS FAQS:... 3 WHY DID I NOT RECEIVE A SPRINGCM ACTIVATION EMAIL?... 3 WHY DON T MY SALESFORCE USERS HAVE ACCESS TO SPRINGCM?... 3
Guide to setting up IRIS AE Suite TM & IRIS OpenSpace online
 18/02/2014 Guide to setting up IRIS AE Suite TM & IRIS OpenSpace online IRIS Payroll Professional 30/04/2015 Contents What is IRIS OpenEnrol?... 4 Steps to setting up and using IRIS OpenEnrol... 5 How
18/02/2014 Guide to setting up IRIS AE Suite TM & IRIS OpenSpace online IRIS Payroll Professional 30/04/2015 Contents What is IRIS OpenEnrol?... 4 Steps to setting up and using IRIS OpenEnrol... 5 How
THE COMPLETE GUIDE TO GOOGLE APPS SECURITY. Building a comprehensive Google Apps security plan
 THE COMPLETE GUIDE TO GOOGLE APPS SECURITY Building a comprehensive Google Apps security plan Contents Introduction................................ 3 1. Secure the core.............................4 Google
THE COMPLETE GUIDE TO GOOGLE APPS SECURITY Building a comprehensive Google Apps security plan Contents Introduction................................ 3 1. Secure the core.............................4 Google
Configuration Guide. BES12 Cloud
 Configuration Guide BES12 Cloud Published: 2016-04-08 SWD-20160408113328879 Contents About this guide... 6 Getting started... 7 Configuring BES12 for the first time...7 Administrator permissions you need
Configuration Guide BES12 Cloud Published: 2016-04-08 SWD-20160408113328879 Contents About this guide... 6 Getting started... 7 Configuring BES12 for the first time...7 Administrator permissions you need
Security FAQs (Frequently Asked Questions) for Xerox Remote Print Services
 Security FAQs (Frequently Asked Questions) for Xerox Remote Print Services February 30, 2012 2012 Xerox Corporation. All rights reserved. Xerox and Xerox and Design are trademarks of Xerox Corporation
Security FAQs (Frequently Asked Questions) for Xerox Remote Print Services February 30, 2012 2012 Xerox Corporation. All rights reserved. Xerox and Xerox and Design are trademarks of Xerox Corporation
Five Ways to Improve Electronic Patient Record Handling for HIPAA/HITECH with Managed File Transfer
 Five Ways to Improve Electronic Patient Record Handling for HIPAA/HITECH with Managed File Transfer 1 A White Paper by Linoma Software INTRODUCTION The healthcare industry is under increasing pressure
Five Ways to Improve Electronic Patient Record Handling for HIPAA/HITECH with Managed File Transfer 1 A White Paper by Linoma Software INTRODUCTION The healthcare industry is under increasing pressure
HIPAA Compliance Guide
 HIPAA Compliance Guide Important Terms Covered Entities (CAs) The HIPAA Privacy Rule refers to three specific groups as covered entities, including health plans, healthcare clearinghouses, and health care
HIPAA Compliance Guide Important Terms Covered Entities (CAs) The HIPAA Privacy Rule refers to three specific groups as covered entities, including health plans, healthcare clearinghouses, and health care
Administrator Quick Start Guide
 This guide is designed to provide Administrators with a quick overview of the features and functionalities provided to them in LEARN360 s Administration section. Login Figures 1-4 feature different components
This guide is designed to provide Administrators with a quick overview of the features and functionalities provided to them in LEARN360 s Administration section. Login Figures 1-4 feature different components
Bell Mobile Device Management (MDM)
 Bell MDM Technical FAQs 1 Bell Mobile Device Management (MDM) Frequently Asked Questions INTRODUCTION Bell Mobile Device Management provides business customers an all in one device administration tool
Bell MDM Technical FAQs 1 Bell Mobile Device Management (MDM) Frequently Asked Questions INTRODUCTION Bell Mobile Device Management provides business customers an all in one device administration tool
Single Sign On Guide. Table of Contents
 Single Sign On Guide Table of Contents I. Overview II. Benefits III. How SSO Works IV. Set-up Requirements and Recommendations V. Set-up Instructions a. Required Parameters b. Optional Parameters c. Error
Single Sign On Guide Table of Contents I. Overview II. Benefits III. How SSO Works IV. Set-up Requirements and Recommendations V. Set-up Instructions a. Required Parameters b. Optional Parameters c. Error
ESA EO Identify Management
 ESA EO Identify Management The ESA EO IM Infrastructure & Services A. Baldi ESA: Andrea.Baldi@esa.int M. Leonardi ESA: m.leonardi@rheagroup.com 1 Issues @ ESA with legacy user management Users had multiple
ESA EO Identify Management The ESA EO IM Infrastructure & Services A. Baldi ESA: Andrea.Baldi@esa.int M. Leonardi ESA: m.leonardi@rheagroup.com 1 Issues @ ESA with legacy user management Users had multiple
Tableau Online Security in the Cloud
 Tableau Online Security in the Cloud Author: Ellie Fields Senior Director, Product Marketing, Tableau Software June 2013 p2 Tableau Software understands that data is among the most strategic and important
Tableau Online Security in the Cloud Author: Ellie Fields Senior Director, Product Marketing, Tableau Software June 2013 p2 Tableau Software understands that data is among the most strategic and important
HIPAA for HIT and EHRs. Latest on Meaningful Use and EHR Certification: For Privacy and Security Professionals
 HIPAA for HIT and EHRs Latest on Meaningful Use and EHR Certification: For Privacy and Security Professionals Donald Bechtel, CHP Siemens Health Services Patient Privacy Officer Fair Information Practices
HIPAA for HIT and EHRs Latest on Meaningful Use and EHR Certification: For Privacy and Security Professionals Donald Bechtel, CHP Siemens Health Services Patient Privacy Officer Fair Information Practices
Internet Banking User Guide
 Internet Banking User Guide Jack Henry & Associates, Inc. 2011.11 Contents Login... 1 Login Screen... 1 Password Change... 2 Watermark Selection... 2 Multi-Factor Authentication Security Question Selection...
Internet Banking User Guide Jack Henry & Associates, Inc. 2011.11 Contents Login... 1 Login Screen... 1 Password Change... 2 Watermark Selection... 2 Multi-Factor Authentication Security Question Selection...
Telemedicine HIPAA/HITECH Privacy and Security
 Telemedicine HIPAA/HITECH Privacy and Security 1 Access Control Role Based Access The organization shall provide secure rolebased account management. Privileges granted utilizing the principle of least
Telemedicine HIPAA/HITECH Privacy and Security 1 Access Control Role Based Access The organization shall provide secure rolebased account management. Privileges granted utilizing the principle of least
Last Updated July, 2014
 MyHealth Patient Portal Last Updated July, 2014 Frequently Asked Questions General What is MyHealth Portal? Is there a fee to use MyHealth Portal? What do I need to use MyHealth Portal? Who do I contact
MyHealth Patient Portal Last Updated July, 2014 Frequently Asked Questions General What is MyHealth Portal? Is there a fee to use MyHealth Portal? What do I need to use MyHealth Portal? Who do I contact
How to use the Alertsec Service to Achieve HIPAA Compliance for Your Organization
 How to use the Alertsec Service to Achieve HIPAA Compliance for Your Organization Alertsec offers Cloud Managed - Policy Controlled - Security Modules for Ensuring Compliance at the Endpoints Contents
How to use the Alertsec Service to Achieve HIPAA Compliance for Your Organization Alertsec offers Cloud Managed - Policy Controlled - Security Modules for Ensuring Compliance at the Endpoints Contents
Athletic Trainer System
 The Athletic Trainer System ATS is the industr y leading electronic medical records software for athletic trainers. ATS is a comprehensive multi-level system used by the medical staff in high schools,
The Athletic Trainer System ATS is the industr y leading electronic medical records software for athletic trainers. ATS is a comprehensive multi-level system used by the medical staff in high schools,
A Workflow for Patient Electronic Signatures and Document Storage
 A Workflow for Patient Electronic Signatures and Document Storage Presented by: Margery Beck System Analyst Jennifer Boldin Application Support Analyst MIMA: Independent 125-provider multi-specialty group
A Workflow for Patient Electronic Signatures and Document Storage Presented by: Margery Beck System Analyst Jennifer Boldin Application Support Analyst MIMA: Independent 125-provider multi-specialty group
itrust Medical Records System: Requirements for Technical Safeguards
 itrust Medical Records System: Requirements for Technical Safeguards Physicians and healthcare practitioners use Electronic Health Records (EHR) systems to obtain, manage, and share patient information.
itrust Medical Records System: Requirements for Technical Safeguards Physicians and healthcare practitioners use Electronic Health Records (EHR) systems to obtain, manage, and share patient information.
Sophos Mobile Control SaaS startup guide. Product version: 6
 Sophos Mobile Control SaaS startup guide Product version: 6 Document date: January 2016 Contents 1 About this guide...4 2 About Sophos Mobile Control...5 3 What are the key steps?...7 4 Change your password...8
Sophos Mobile Control SaaS startup guide Product version: 6 Document date: January 2016 Contents 1 About this guide...4 2 About Sophos Mobile Control...5 3 What are the key steps?...7 4 Change your password...8
Advantage for Windows Copyright 2012 by The Advantage Software Company, Inc. All rights reserved. Client Portal blue Installation Guide v1.
 Advantage for Windows Copyright 2012 by The Advantage Software Company, Inc. All rights reserved Client Portal blue Installation Guide v1.1 Overview This document will walk you through the process of installing
Advantage for Windows Copyright 2012 by The Advantage Software Company, Inc. All rights reserved Client Portal blue Installation Guide v1.1 Overview This document will walk you through the process of installing
Mobile Radiography Radiology Information System with Google GPS by AMTEMD
 2014 Mobile Radiography Radiology Information System with Google GPS by AMTEMD Mobile RIS is specifically designed for the mobile radiography industry Distributed by Powered by ISM Information System Management
2014 Mobile Radiography Radiology Information System with Google GPS by AMTEMD Mobile RIS is specifically designed for the mobile radiography industry Distributed by Powered by ISM Information System Management
Administering Jive Mobile Apps
 Administering Jive Mobile Apps Contents 2 Contents Administering Jive Mobile Apps...3 Configuring Jive for Android and ios... 3 Native Apps and Push Notifications...4 Custom App Wrapping for ios... 5 Native
Administering Jive Mobile Apps Contents 2 Contents Administering Jive Mobile Apps...3 Configuring Jive for Android and ios... 3 Native Apps and Push Notifications...4 Custom App Wrapping for ios... 5 Native
Client Security Risk Assessment Questionnaire
 Select the appropriate answer from the drop down in the column, and provide a brief description in the section. 1 Do you have a member of your organization with dedicated information security duties? 2
Select the appropriate answer from the drop down in the column, and provide a brief description in the section. 1 Do you have a member of your organization with dedicated information security duties? 2
plantemoran.com What School Personnel Administrators Need to know
 plantemoran.com Data Security and Privacy What School Personnel Administrators Need to know Tomorrow s Headline Let s hope not District posts confidential data online (Tech News, May 18, 2007) In one of
plantemoran.com Data Security and Privacy What School Personnel Administrators Need to know Tomorrow s Headline Let s hope not District posts confidential data online (Tech News, May 18, 2007) In one of
AVG Business SSO Partner Getting Started Guide
 AVG Business SSO Partner Getting Started Guide Table of Contents Overview... 2 Getting Started... 3 Web and OS requirements... 3 Supported web and device browsers... 3 Initial Login... 4 Navigation in
AVG Business SSO Partner Getting Started Guide Table of Contents Overview... 2 Getting Started... 3 Web and OS requirements... 3 Supported web and device browsers... 3 Initial Login... 4 Navigation in
Volunteer Software Feature Comparison
 Thank you for your interest in our Better software! This document has been prepared to list the functions of Better software and, if helpful, to assist you in comparing it to other software you might be
Thank you for your interest in our Better software! This document has been prepared to list the functions of Better software and, if helpful, to assist you in comparing it to other software you might be
System Administration Training Guide. S100 Installation and Site Management
 System Administration Training Guide S100 Installation and Site Management Table of contents System Requirements for Acumatica ERP 4.2... 5 Learning Objects:... 5 Web Browser... 5 Server Software... 5
System Administration Training Guide S100 Installation and Site Management Table of contents System Requirements for Acumatica ERP 4.2... 5 Learning Objects:... 5 Web Browser... 5 Server Software... 5
1. What are the System Requirements for using the MaaS360 for Exchange ActiveSync solution?
 MaaS360 FAQs This guide is meant to help answer some of the initial frequently asked questions businesses ask as they try to figure out the who, what, when, why and how of managing their smartphone devices,
MaaS360 FAQs This guide is meant to help answer some of the initial frequently asked questions businesses ask as they try to figure out the who, what, when, why and how of managing their smartphone devices,
HIPAA Privacy and Security Risk Assessment and Action Planning
 HIPAA Privacy and Security Risk Assessment and Action Planning Practice Name: Participants: Date: MU Stage: EHR Vendor: Access Control Unique ID and PW for Users (TVS016) Role Based Access (TVS023) Account
HIPAA Privacy and Security Risk Assessment and Action Planning Practice Name: Participants: Date: MU Stage: EHR Vendor: Access Control Unique ID and PW for Users (TVS016) Role Based Access (TVS023) Account
Welcome to part 2 of the HIPAA Security Administrative Safeguards presentation. This presentation covers information access management, security
 Welcome to part 2 of the HIPAA Security Administrative Safeguards presentation. This presentation covers information access management, security awareness training, and security incident procedures. The
Welcome to part 2 of the HIPAA Security Administrative Safeguards presentation. This presentation covers information access management, security awareness training, and security incident procedures. The
Features of AnyShare
 of AnyShare of AnyShare CONTENT Brief Introduction of AnyShare... 3 Chapter 1 Centralized Management... 5 1.1 Operation Management... 5 1.2 User Management... 5 1.3 User Authentication... 6 1.4 Roles...
of AnyShare of AnyShare CONTENT Brief Introduction of AnyShare... 3 Chapter 1 Centralized Management... 5 1.1 Operation Management... 5 1.2 User Management... 5 1.3 User Authentication... 6 1.4 Roles...
Adobe Digital Publishing Security FAQ
 Adobe Digital Publishing Suite Security FAQ Adobe Digital Publishing Security FAQ Table of contents DPS Security Overview Network Service Topology Folio ProducerService Network Diagram Fulfillment Server
Adobe Digital Publishing Suite Security FAQ Adobe Digital Publishing Security FAQ Table of contents DPS Security Overview Network Service Topology Folio ProducerService Network Diagram Fulfillment Server
MOVEIT: SECURE, GUARANTEED FILE DELIVERY BY JONATHAN LAMPE, GCIA, GSNA
 MOVEIT: SECURE, GUARANTEED FILE DELIVERY BY JONATHAN LAMPE, GCIA, GSNA The MOVEit line of secure managed file transfer software products by Ipswitch File Transfer consists of two flagship products, the
MOVEIT: SECURE, GUARANTEED FILE DELIVERY BY JONATHAN LAMPE, GCIA, GSNA The MOVEit line of secure managed file transfer software products by Ipswitch File Transfer consists of two flagship products, the
Optum Patient Portal. 70 Royal Little Drive. Providence, RI 02904. Copyright 2002-2013 Optum. All rights reserved. Updated: 3/7/13
 Optum Patient Portal 70 Royal Little Drive Providence, RI 02904 Copyright 2002-2013 Optum. All rights reserved. Updated: 3/7/13 Table of Contents 1 Patient Portal Activation...1 1.1 Pre-register a Patient...1
Optum Patient Portal 70 Royal Little Drive Providence, RI 02904 Copyright 2002-2013 Optum. All rights reserved. Updated: 3/7/13 Table of Contents 1 Patient Portal Activation...1 1.1 Pre-register a Patient...1
BlackBerry Enterprise Service 10. Universal Device Service Version: 10.2. Administration Guide
 BlackBerry Enterprise Service 10 Universal Service Version: 10.2 Administration Guide Published: 2015-02-24 SWD-20150223125016631 Contents 1 Introduction...9 About this guide...10 What is BlackBerry
BlackBerry Enterprise Service 10 Universal Service Version: 10.2 Administration Guide Published: 2015-02-24 SWD-20150223125016631 Contents 1 Introduction...9 About this guide...10 What is BlackBerry
Software as a Service (SaaS) Requirements
 Introduction Software as a Service (SaaS) Requirements Software as a Service (SaaS) is a software service model where an application is hosted as a service provided to customers across the Internet. By
Introduction Software as a Service (SaaS) Requirements Software as a Service (SaaS) is a software service model where an application is hosted as a service provided to customers across the Internet. By
Certified Secure Computer User
 Certified Secure Computer User Exam Info Exam Name CSCU (112-12) Exam Credit Towards Certification Certified Secure Computer User (CSCU). Students need to pass the online EC-Council exam to receive the
Certified Secure Computer User Exam Info Exam Name CSCU (112-12) Exam Credit Towards Certification Certified Secure Computer User (CSCU). Students need to pass the online EC-Council exam to receive the
TestNav 8 User Guide for PARCC
 TestNav 8 User Guide for PARCC Copyright 2014, Pearson Education, Inc. Published March 6, 2014 TestNav 8 User Guide for PARCC 1 TestNav 8 User Guide for PARCC Revision History What is TestNav? Technical
TestNav 8 User Guide for PARCC Copyright 2014, Pearson Education, Inc. Published March 6, 2014 TestNav 8 User Guide for PARCC 1 TestNav 8 User Guide for PARCC Revision History What is TestNav? Technical
Interwise Connect. Working with Reverse Proxy Version 7.x
 Working with Reverse Proxy Version 7.x Table of Contents BACKGROUND...3 Single Sign On (SSO)... 3 Interwise Connect... 3 INTERWISE CONNECT WORKING WITH REVERSE PROXY...4 Architecture... 4 Interwise Web
Working with Reverse Proxy Version 7.x Table of Contents BACKGROUND...3 Single Sign On (SSO)... 3 Interwise Connect... 3 INTERWISE CONNECT WORKING WITH REVERSE PROXY...4 Architecture... 4 Interwise Web
A Guide to New Features in Propalms OneGate 4.0
 A Guide to New Features in Propalms OneGate 4.0 Propalms Ltd. Published April 2013 Overview This document covers the new features, enhancements and changes introduced in Propalms OneGate 4.0 Server (previously
A Guide to New Features in Propalms OneGate 4.0 Propalms Ltd. Published April 2013 Overview This document covers the new features, enhancements and changes introduced in Propalms OneGate 4.0 Server (previously
Administration Guide. WatchDox Server. Version 4.8.0
 Administration Guide WatchDox Server Version 4.8.0 Published: 2015-11-01 SWD-20151101091846278 Contents Introduction... 7 Getting started... 11 Signing in to WatchDox... 11 Signing in with username and
Administration Guide WatchDox Server Version 4.8.0 Published: 2015-11-01 SWD-20151101091846278 Contents Introduction... 7 Getting started... 11 Signing in to WatchDox... 11 Signing in with username and
Introduction to Mobile Application Management (MAM)
 Introduction to Mobile Application Management (MAM) Overview This guide details how your organization can manage mobile applications using AirWatch's Mobile Application Management (MAM) functionality.
Introduction to Mobile Application Management (MAM) Overview This guide details how your organization can manage mobile applications using AirWatch's Mobile Application Management (MAM) functionality.
EmpLive Technical Overview
 Version 1.6 Updated 27/08/2015 Support: +61 2 8399 1688 Email: support@wfsaustralia.com Website: wfsaustralia.com Legal Notice Copyright WFS: A WorkForce Software Company. All Rights Reserved. By receiving
Version 1.6 Updated 27/08/2015 Support: +61 2 8399 1688 Email: support@wfsaustralia.com Website: wfsaustralia.com Legal Notice Copyright WFS: A WorkForce Software Company. All Rights Reserved. By receiving
Password Reset PRO INSTALLATION GUIDE
 Password Reset PRO INSTALLATION GUIDE This guide covers the new features and settings available in Password Reset PRO. Please read this guide completely to ensure a trouble-free installation. March 2009
Password Reset PRO INSTALLATION GUIDE This guide covers the new features and settings available in Password Reset PRO. Please read this guide completely to ensure a trouble-free installation. March 2009
MaaS360 Mobile Enterprise Gateway
 MaaS360 Mobile Enterprise Gateway Administrator Guide Copyright 2013 Fiberlink Communications Corporation. All rights reserved. Information in this document is subject to change without notice. The software
MaaS360 Mobile Enterprise Gateway Administrator Guide Copyright 2013 Fiberlink Communications Corporation. All rights reserved. Information in this document is subject to change without notice. The software
Sophos Mobile Control Installation guide
 Sophos Mobile Control Installation guide Product version: 2.5 Document date: July 2012 Contents 1 Introduction... 3 2 The Sophos Mobile Control server... 4 3 Set up Sophos Mobile Control... 13 4 Running
Sophos Mobile Control Installation guide Product version: 2.5 Document date: July 2012 Contents 1 Introduction... 3 2 The Sophos Mobile Control server... 4 3 Set up Sophos Mobile Control... 13 4 Running
Directory Integration with Okta. An Architectural Overview. Okta Inc. 301 Brannan Street San Francisco, CA 94107. info@okta.
 Directory Integration with Okta An Architectural Overview Okta Inc. 301 Brannan Street San Francisco, CA 94107 info@okta.com 1-888-722-7871 Contents 1 User Directories and the Cloud: An Overview 3 Okta
Directory Integration with Okta An Architectural Overview Okta Inc. 301 Brannan Street San Francisco, CA 94107 info@okta.com 1-888-722-7871 Contents 1 User Directories and the Cloud: An Overview 3 Okta
This release bulletin relates to Version 3.10.4 build 2701 of the Swivel Authentication Platform and other new capabilities.
 Swivel Authentication Version 3.10.4 Release Bulletin Introduction This release bulletin relates to Version 3.10.4 build 2701 of the Swivel Authentication Platform and other new capabilities. This latest
Swivel Authentication Version 3.10.4 Release Bulletin Introduction This release bulletin relates to Version 3.10.4 build 2701 of the Swivel Authentication Platform and other new capabilities. This latest
DiamondStream Data Security Policy Summary
 DiamondStream Data Security Policy Summary Overview This document describes DiamondStream s standard security policy for accessing and interacting with proprietary and third-party client data. This covers
DiamondStream Data Security Policy Summary Overview This document describes DiamondStream s standard security policy for accessing and interacting with proprietary and third-party client data. This covers
Single Sign-On Administrator s Guide
 Single Sign-On Administrator s Guide Released 11/22/2013 About this Guide This guide is designed for the people who handle software administrative duties for their agency or organization, and have the
Single Sign-On Administrator s Guide Released 11/22/2013 About this Guide This guide is designed for the people who handle software administrative duties for their agency or organization, and have the
Denver Public Schools - East High School
 Denver Public Schools - East High School Return this page to the Technology Department in room 230 Electronic Web Access Agreement for Viewing Student Information via DPS Infinite Campus Parent/Student
Denver Public Schools - East High School Return this page to the Technology Department in room 230 Electronic Web Access Agreement for Viewing Student Information via DPS Infinite Campus Parent/Student
Understanding PowerSchool Parent Portal with Single Sign-On
 nderstanding PowerSchool Parent Portal with Single Sign-On The Power of the application comes from understanding what it can do and how it can help you participate in your child s education. Introduction
nderstanding PowerSchool Parent Portal with Single Sign-On The Power of the application comes from understanding what it can do and how it can help you participate in your child s education. Introduction
MaaS360 Mobile Enterprise Gateway
 MaaS360 Mobile Enterprise Gateway Administrator Guide Copyright 2014 Fiberlink, an IBM Company. All rights reserved. Information in this document is subject to change without notice. The software described
MaaS360 Mobile Enterprise Gateway Administrator Guide Copyright 2014 Fiberlink, an IBM Company. All rights reserved. Information in this document is subject to change without notice. The software described
How To Secure Shareware Kiteworks By Accellion
 Top 10 Reasons Universities Select kiteworks by Accellion Top 10 Reasons Universities Select kiteworks kiteworks by Accellion provides higher education institutions with secure wherever, whenever access
Top 10 Reasons Universities Select kiteworks by Accellion Top 10 Reasons Universities Select kiteworks kiteworks by Accellion provides higher education institutions with secure wherever, whenever access
Sophos Mobile Control Startup guide. Product version: 3.5
 Sophos Mobile Control Startup guide Product version: 3.5 Document date: July 2013 Contents 1 About this guide...3 2 What are the key steps?...5 3 Log in as a super administrator...6 4 Activate Sophos Mobile
Sophos Mobile Control Startup guide Product version: 3.5 Document date: July 2013 Contents 1 About this guide...3 2 What are the key steps?...5 3 Log in as a super administrator...6 4 Activate Sophos Mobile
Soonr Workplace Enterprise Plan Overview
 This document is an overview of the features that are included in the Soonr Workplace Enterprise Plan. The Enterprise Plan is designed for the specific needs of IT departments in larger companies where
This document is an overview of the features that are included in the Soonr Workplace Enterprise Plan. The Enterprise Plan is designed for the specific needs of IT departments in larger companies where
Privacy Policy Version 1.0, 1 st of May 2016
 Privacy Policy Version 1.0, 1 st of May 2016 THIS PRIVACY POLICY APPLIES TO PERSONAL INFORMATION COLLECTED BY GOCIETY SOLUTIONS FROM USERS OF THE GOCIETY SOLUTIONS APPLICATIONS (GoLivePhone and GoLiveAssist)
Privacy Policy Version 1.0, 1 st of May 2016 THIS PRIVACY POLICY APPLIES TO PERSONAL INFORMATION COLLECTED BY GOCIETY SOLUTIONS FROM USERS OF THE GOCIETY SOLUTIONS APPLICATIONS (GoLivePhone and GoLiveAssist)
User Manual for Version 4.4.0.5. Mobile Device Management (MDM) User Manual
 User Manual for Version 4.4.0.5 Mobile Device Management (MDM) User Manual I Endpoint Protector Mobile Device Management User Manual Table of Contents 1. Introduction... 1 1.1. What is Endpoint Protector?...
User Manual for Version 4.4.0.5 Mobile Device Management (MDM) User Manual I Endpoint Protector Mobile Device Management User Manual Table of Contents 1. Introduction... 1 1.1. What is Endpoint Protector?...
Your Location Instant NOC using Kaseya. Administrator at Remote Location Secure access to Management Console from anywhere using only a browser
 Kaseya Product Brief The Kaseya Platform Making your systems more secure, your staff more productive, your services more reliable and your results easier to validate. No matter what part of Kaseya s integrated
Kaseya Product Brief The Kaseya Platform Making your systems more secure, your staff more productive, your services more reliable and your results easier to validate. No matter what part of Kaseya s integrated
Table of Contents. Page 1 of 6 (Last updated 30 July 2015)
 Table of Contents What is Connect?... 2 Physical Access Controls... 2 User Access Controls... 3 Systems Architecture... 4 Application Development... 5 Business Continuity Management... 5 Other Operational
Table of Contents What is Connect?... 2 Physical Access Controls... 2 User Access Controls... 3 Systems Architecture... 4 Application Development... 5 Business Continuity Management... 5 Other Operational
