University of Aberdeen Network Connection Policy
|
|
|
- Paulina Holmes
- 3 years ago
- Views:
Transcription
1 University f Aberdeen Netwrk Cnnectin Plicy 1. Overview The University s data netwrk frms a critical part f the business infrastructure used t access business systems and data stres as well as carrying and telephny. As such it is essential that this resurce is carefully managed t ensure its capacity, availability and integrity. The demands placed upn the University s data netwrks are such that a single netwrk is nt able t meet all these needs, therefre there are several netwrks designed f prvide the required service in each area. Nthing in this dcument shuld be taken t verride the University f Aberdeen Infrmatin Security Plicy r the JANET Acceptable Use Plicy. Where there is any cnflict the abve dcuments take precedence. 2. Purpse The purpse f this plicy is t define what can be cnnected t the University s netwrks and the standards that must be adhered t by devices s cnnected. It cvers: Wh can cnnect devices t a netwrk devices can be cnnected t a netwrk Ensuring apprpriate management f netwrk resurces and netwrk address space Auditing f this plicy Enfrcement actin Details f permitted activities by netwrk cnnected devices are cvered in the University f Aberdeen Cnditins fr using IT Facilities and the assciated Ntes fr Guidance. 3. Scpe This plicy applies t any device directly cnnected t any f the University s netwrks by any means (e.g. netwrk cable r wireless). It des nt cver remte access frm ut with the University. It als applies t anyne cnnecting r using a device cnnected t the University s netwrks including Staff, Students, Cntractrs and members f the General Public fr whatever purpse that device is t be cnnected t the netwrk. The prcess f cnnecting a device t the netwrk includes: Cnfiguring the netwrk t allw the device t cmmunicate Physically cnnecting the device t the netwrk Cnfiguring the device t cmmunicate n the netwrk 4. Plicy Cmmn plicy applying t ALL University f Aberdeen Netwrks Wh In general nly staff authrised by the Directr f IT Services are permitted t cnfigure r extend any University f Aberdeen netwrk. Each netwrk has a separate plicy n wh can physically cnnect devices t it. Details are given in the sectins belw. Each netwrk has a separate plicy n wh can cnfigure devices t cmmunicate n it. Details are given in the sectins belw. IT Services, University f Aberdeen Last reviewed: April 2015
2 Page 2 Netwrk Cnnectin Plicy Each netwrk is prvided fr a specific purpse and nly devices cnsistent with that purpse may be cnnected. Devices may be categrised as: Netwrk equipment Such as ruters, netwrk switches, Wireless Access Pints etc. Client Devices University wned: User Wrkstatins, PCs, laptps, PDAs etc. Nn University wned: User Wrkstatins, PCs, laptps, PDAs etc. Servers Devices whse primary purpse is t prvide services t ther netwrk cnnected devices Netwrk Printers and MFDs Embedded devices Such as CCTV cameras, building mnitring systems etc. Other equipment Such as scanners, scientific instruments and Videcnferencing equipment. The cnnectin r cnfiguratin f netwrk equipment is cnsidered cnfiguring the netwrk and is nly permitted by explicitly authrised staff. Authrised staff may delegate specific tasks in specific circumstances, e.g. cnsultants wrking n behalf f the University, hwever they remain respnsible fr such wrk. Any device cnnected t the netwrk must meet the fllwing minimum criteria: Has a Netwrk Interface Card capable f cnnecting t Ethernet Netwrks r wireless netwrks. Is capable f cmmunicating using TCP/IP v4 netwrk prtcls. Cmplies with current Health and Safety requirements, including Electrical regulatins (e.g. PAT testing) and ther natinal and internatinal regulatry requirements. Cmplies with the University f Aberdeen OS update and patching Plicy. Where available, has up t date antivirus sftware peratinal. Where available, has the device firewall switched n and cnfigured in accrdance with the guidelines issued by IT Services. Has a Respnsible Persn, charged with ensuring the device and its use adheres t this plicy and ther applicable University f Aberdeen plicies. Netwrk Specific Plicies Campus Netwrk The Campus Netwrk is prvided t supprt the teaching, research and administrative functins f the University by facilitating netwrk cnnectivity t the University IT resurces and t the Internet thrugh JANET. It is the standard netwrk t which mst University wned cabled devices are nrmally cnnected. Wh Only staff authrised by the Directr f IT Services are permitted t enliven prts n the campus netwrk. Only staff authrised by the Directr f IT Services and Respnsible Persns are permitted t cnnect suitably cnfigured devices t any Campus Netwrk prt. IT Services, University f Aberdeen Last reviewed: April 2015
3 Page 3 Netwrk Cnnectin Plicy Only staff authrised by the Directr f IT Services and Respnsible Persns may cnfigure devices fr cnnectin t the campus netwrk. Only University wned devices may be cnnected t the campus netwrk. Such devices must be cnfigured fr the particular lcatin where they are t be used. In exceptinal circumstances nn University f Aberdeen equipment may be cnnected t the campus netwrk (Nte: ResNet r eduram are usually mre apprpriate fr such devices). In such cases the device wner will be held liable by the University f Aberdeen fr any lss arising ut f the use f the device n University f Aberdeen netwrks and must cnsent t: eduram The University f Aberdeen mnitring the device activity. Prvide full access t the device if required t undertake investigatins. The eduram Netwrk is prvided t supprt the teaching, research and administrative functins f the University by facilitating netwrk cnnectivity t the University IT resurces and t the Internet thrugh JANET. It is the standard netwrk t which mst nn University wned devices and Wireless devices are nrmally cnnected. Wh Only staff authrised by the Directr f IT Services are permitted t cnfigure the eduram netwrk. Any registered user f University f Aberdeen IT services r registered user f an eduram federated rganisatin may cnnect a client device t the eduram netwrk. Only staff authrised by the Directr f IT Services and Respnsible Persns may cnfigure University wned devices fr cnnectin t the eduram netwrk. The University f Aberdeen des nt specify wh may cnfigure nn University wned devices. Any client device may be cnnected t eduram netwrk. University f Aberdeen users are required t ensure that devices are fully patched, have up-t-date, antivirus sftware and persnal firewall installed, where pssible. Nn University f Aberdeen users are recmmended t ensure that devices are fully patched, have up-t-date, antivirus sftware and persnal firewall installed. The University f Aberdeen will nt be respnsible fr any lss arising frm cnnecting devices t the eduram Netwrk. ResNet The ResNet Netwrk is prvided t supprt the teaching, research and administrative functins f the University by facilitating netwrk cnnectivity t the University IT resurces and t the Internet thrugh JANET. It is als acceptable t use ResNet fr respnsible scial and recreatinal use. It is the standard netwrk fr nn administrative use in University residences. Wh Only staff authrised by the Directr f IT Services are permitted t cnfigure the ResNet netwrk. Any registered user f University f Aberdeen IT services may cnnect a client device t the ResNet netwrk IT Services, University f Aberdeen Last reviewed: April 2015
4 Page 4 Netwrk Cnnectin Plicy Only staff authrised by the Directr f IT Services and Respnsible Persns may cnfigure University wned devices fr cnnectin t the ResNet netwrk. The University f Aberdeen des nt specify wh may cnfigure nn University wned devices. Any client device may be cnnected t ResNet netwrk. All users are required t ensure that devices are fully patched, have up-t-date, antivirus sftware and persnal firewall installed. The use f a client device t cnnect persnal electrnic equipment, such as games cnsles, is nt regarded as cnfiguring the netwrk. Users s ding s shuld be aware that they will accuntable fr any use f devices cnnected in such a manner. The University f Aberdeen will nt be respnsible fr any lss arising frm cnnecting devices t the ResNet Netwrk. Guestweb Wireless Netwrk The guestweb wireless service prvides visitrs t the University with shrt term unencrypted internet access while n campus. Wh Only staff authrised by the Directr f IT Services are permitted t cnfigure the Guestweb netwrk. Any user registered fr guest access t University f Aberdeen IT services may cnnect a client device t Guest Web. The University f Aberdeen des nt stipulate wh may cnfigure devices nt wned by the University. Any client device may be cnnected t the guestweb netwrk. It is recmmended that such devices are fully patched, have up-t-date, antivirus sftware and persnal firewall installed. The University f Aberdeen will nt be respnsible fr any lss arising frm cnnecting devices t Visitr Web. IT Classrm Netwrk The IT Classrm Netwrk prvides cnnectivity fr the teaching classrms, public access clusters and lecture theatre systems. Wh Only staff authrised by the Directr f IT Services are permitted t cnfigure the IT Classrm netwrk. Only staff authrised by the Directr f IT Services may cnnect devices t the IT classrm netwrk. Only staff authrised by the Directr f IT Services may cnfigure devices n the IT classrm netwrk. Only devices directly supprting the classrm r lecture theatre envirnment may be cnnected t the IT Classrm netwrk. Central Server Netwrks Central Server netwrks are built t prvide the necessary traffic management and security t effectively deliver the IT services cnnected t them. IT Services, University f Aberdeen Last reviewed: April 2015
5 Page 5 Netwrk Cnnectin Plicy Fr each server netwrk a recrd will be kept detailing the purpse f the netwrk, what cnnectivity it prvides and the security measures t be implemented t prtect the services cnnected t it. Wh Only staff authrised by the Directr f IT Services are permitted t cnfigure Central Server netwrks. Only staff authrised by the Directr f IT Services may cnnect devices t the Central Server Netwrks. Only staff authrised by the Directr f IT Services may cnfigure devices n a Central Server netwrk. Only devices cnsistent with the purpse f a specific server netwrk may be cnnected t a specific server netwrk. Special Netwrks There are devices, such as scientific equipment, which require a netwrk cnnectin but cannt meet the requirements f any f the abve netwrks. In these circumstances, prvided there is a business case, a special netwrk may be cnfigured. These netwrks are subject t specific agreements between the device administratr(s) and IT Services. Only the minimum cnnectivity cnsistent with use f the device will be prvided. Fr each special netwrk a recrd will be kept detailing the purpse f the netwrk, what cnnectivity it prvides, including wh may use devices cnnected t it and wh may cnnect devices t it and what devices may be cnnected. Wh Only staff authrised by the Directr f IT Services are permitted t cnfigure a specific special netwrk. Only staff authrised by the Directr f IT Services r persns detailed in the agreement may cnnect devices t the specific special netwrk. Only staff authrised by the Directr f IT Services r persns detailed in the agreement are permitted t cnfigure devices fr a specific special netwrk. Only thse devices detailed in the agreement may be cnnected t the specific special netwrk. 5. Management Mnitring Traffic levels and resurce utilisatin will be apprpriately mnitred, with recrds kept fr at least 1 year. With the exceptin f staff authrised by the Directr f IT Services, the fllwing activities are a breach f this plicy: Scanning r mnitring f any University f Aberdeen netwrk. Operating any device in prmiscuus mde. Installing sftware fr the purpses f netwrk mnitring r scanning. The allcatin f netwrk addresses (IP addresses) shall be managed by IT Services. Addresses issued fr use with a device must nt be used with any ther device. When a device is n lnger cnnected t the netwrk, the address issued t it will be reclaimed. IT Services, University f Aberdeen Last reviewed: April 2015
6 Page 6 Netwrk Cnnectin Plicy Excessive use Any device that cnsumes excessive netwrk resurce (e.g. bandwidth) such that it impacts the legitimate peratin f ther netwrk devices may be discnnected r have its access t resurce limited. Such measures will nly be taken t the extent necessary t ensure prper peratin f the netwrk. IT Services may emply Traffic Shaping t manage bandwidth ensuring critical applicatins are given pririty. 6. Auditing Management data as detailed in sectin 5 abve will be used by IT Services t ensure cmpliance t this plicy. Netwrk scans and statistical analysis will be applied. Third parties may be engaged t peridically reprt n the state f netwrk security in all University netwrks. 7. Enfrcement A breach f this plicy shall be cnsidered a breach f the University f Aberdeen Cnditins fr using IT Facilities and will be dealt with as prvided in them. In particular IT Services has the authrity t refuse t prvide a netwrk service t r restrict the service prvided t any device r user it believes has r will breach this plicy. Disciplinary r legal prceeding may als be instigated. 8. Definitins Mnitring Scanning Prmiscuus mde OS Cabled device Fully patched Cllecting infrmatin relating t netwrk traffic. This culd include surce and destinatin addresses, traffic levels and data types. Wrking thrugh range f netwrk addresses r prts attempting t cnnect t each in turn. A mde f perating a netwrk prt n a client device s that it will receive and prcess all netwrk traffic including traffic nt addressed t it. Operating System. A device cnnected with a cable as ppsed t a wireless cnnectin. All critical and security patches lder than 2 mnths are applied. IT Services, University f Aberdeen Last reviewed: April 2015
7 Page 7 Netwrk Cnnectin Plicy Title University f Aberdeen Netwrk Cnnectin Plicy Authr/Creatr Garry Wardrpe, Infrastructure Develpment Manager, IT Services Owner Christine Mackenzie, Dcumentatin Officer, IT Services Garry Wardrpe, Infrastructure Develpment Manager, IT Services Apprved by University f Aberdeen Advisry Grup n Infrmatin Strategy AGIS) Date published/apprved May 2012 Versin 1. May June May 2012 Review date April 2015 Audience Staff and students, cntractrs, public Related Cnditins fr using IT Facilities Infrmatin Security Plicy JANET Acceptable Use Plicy (external) Subject/Descriptin Equality Impact Assessment Sectin The purpse f this plicy is t define what can be cnnected t the University s netwrks and the standards that must be adhered t by devices s cnnected. - IT Services Theme IT, netwrk, cnnectin, wireless, servers, wrkstatins, laptps, PDAs, printers, MFDs, CCTV, scanners, vide cnferencing, classrms, clusters, lecture theatres, bandwidth IT Services, University f Aberdeen Last reviewed: April 2015
Data Protection Policy & Procedure
 Data Prtectin Plicy & Prcedure Page 1 Prcnnect Marketing Data Prtectin Plicy V1.2 Data prtectin plicy Cntext and verview Key details Plicy prepared by: Adam Haycck Apprved by bard / management n: 01/01/2015
Data Prtectin Plicy & Prcedure Page 1 Prcnnect Marketing Data Prtectin Plicy V1.2 Data prtectin plicy Cntext and verview Key details Plicy prepared by: Adam Haycck Apprved by bard / management n: 01/01/2015
University of Texas at Dallas Policy for Accepting Credit Card and Electronic Payments
 University f Texas at Dallas Plicy fr Accepting Credit Card and Electrnic Payments Cntents: Purpse Applicability Plicy Statement Respnsibilities f a Merchant Department Prcess t Becme a Merchant Department
University f Texas at Dallas Plicy fr Accepting Credit Card and Electrnic Payments Cntents: Purpse Applicability Plicy Statement Respnsibilities f a Merchant Department Prcess t Becme a Merchant Department
Wireless Light-Level Monitoring
 Wireless Light-Level Mnitring ILT1000 ILT1000 Applicatin Nte Wireless Light-Level Mnitring 1 Wireless Light-Level Mnitring ILT1000 The affrdability, accessibility, and ease f use f wireless technlgy cmbined
Wireless Light-Level Mnitring ILT1000 ILT1000 Applicatin Nte Wireless Light-Level Mnitring 1 Wireless Light-Level Mnitring ILT1000 The affrdability, accessibility, and ease f use f wireless technlgy cmbined
ViPNet VPN in Cisco Environment. Supplement to ViPNet Documentation
 ViPNet VPN in Cisc Envirnment Supplement t ViPNet Dcumentatin 1991 2015 Inftecs Americas. All rights reserved. Versin: 00121-04 90 02 ENU This dcument is included in the sftware distributin kit and is
ViPNet VPN in Cisc Envirnment Supplement t ViPNet Dcumentatin 1991 2015 Inftecs Americas. All rights reserved. Versin: 00121-04 90 02 ENU This dcument is included in the sftware distributin kit and is
COPIES-F.Y.I., INC. Policies and Procedures Data Security Policy
 COPIES-F.Y.I., INC. Plicies and Prcedures Data Security Plicy Page 2 f 7 Preamble Mst f Cpies FYI, Incrprated financial, administrative, research, and clinical systems are accessible thrugh the campus
COPIES-F.Y.I., INC. Plicies and Prcedures Data Security Plicy Page 2 f 7 Preamble Mst f Cpies FYI, Incrprated financial, administrative, research, and clinical systems are accessible thrugh the campus
Personal Data Security Breach Management Policy
 Persnal Data Security Breach Management Plicy 1.0 Purpse The Data Prtectin Acts 1988 and 2003 impse bligatins n data cntrllers in Western Care Assciatin t prcess persnal data entrusted t them in a manner
Persnal Data Security Breach Management Plicy 1.0 Purpse The Data Prtectin Acts 1988 and 2003 impse bligatins n data cntrllers in Western Care Assciatin t prcess persnal data entrusted t them in a manner
CSC IT practix Recommendations
 CSC IT practix Recmmendatins CSC Healthcare 28th January 2014 Versin 3 www.csc.cm/glbalhealthcare Cntents 1 Imprtant infrmatin 3 2 IT Specificatins 4 2.1 Wrkstatins... 4 2.2 Minimum Server with 1-5 wrkstatins
CSC IT practix Recmmendatins CSC Healthcare 28th January 2014 Versin 3 www.csc.cm/glbalhealthcare Cntents 1 Imprtant infrmatin 3 2 IT Specificatins 4 2.1 Wrkstatins... 4 2.2 Minimum Server with 1-5 wrkstatins
GUIDANCE FOR BUSINESS ASSOCIATES
 GUIDANCE FOR BUSINESS ASSOCIATES This Guidance fr Business Assciates dcument is intended t verview UPMCs expectatins, as well as t prvide additinal resurces and infrmatin, t UPMC s HIPAA business assciates.
GUIDANCE FOR BUSINESS ASSOCIATES This Guidance fr Business Assciates dcument is intended t verview UPMCs expectatins, as well as t prvide additinal resurces and infrmatin, t UPMC s HIPAA business assciates.
Version: Modified By: Date: Approved By: Date: 1.0 Michael Hawkins October 29, 2013 Dan Bowden November 2013
 Versin: Mdified By: Date: Apprved By: Date: 1.0 Michael Hawkins Octber 29, 2013 Dan Bwden Nvember 2013 Rule 4-004J Payment Card Industry (PCI) Patch Management (prpsed) 01.1 Purpse The purpse f the Patch
Versin: Mdified By: Date: Apprved By: Date: 1.0 Michael Hawkins Octber 29, 2013 Dan Bwden Nvember 2013 Rule 4-004J Payment Card Industry (PCI) Patch Management (prpsed) 01.1 Purpse The purpse f the Patch
Service Level Agreement
 Template SDSU-TPL-11085 v1.3 18/1/11 IT Services Service Level Agreement Staff Email and SMTP Accunts (EMSF) Versin: 0.1 01/11/2010 Service Level Agreement: Staff Email and SMTP Accunts (EMSF) Cntents
Template SDSU-TPL-11085 v1.3 18/1/11 IT Services Service Level Agreement Staff Email and SMTP Accunts (EMSF) Versin: 0.1 01/11/2010 Service Level Agreement: Staff Email and SMTP Accunts (EMSF) Cntents
TrustED Briefing Series:
 TrustED Briefing Series: Since 2001, TrustCC has prvided IT audits and security assessments t hundreds f financial institutins thrugh ut the United States. Our TrustED Briefing Series are white papers
TrustED Briefing Series: Since 2001, TrustCC has prvided IT audits and security assessments t hundreds f financial institutins thrugh ut the United States. Our TrustED Briefing Series are white papers
Information Services Hosting Arrangements
 Infrmatin Services Hsting Arrangements Purpse The purpse f this service is t prvide secure, supprted, and reasnably accessible cmputing envirnments fr departments at DePaul that are in need f server-based
Infrmatin Services Hsting Arrangements Purpse The purpse f this service is t prvide secure, supprted, and reasnably accessible cmputing envirnments fr departments at DePaul that are in need f server-based
Privacy and Security Training Policy (PS.Pol.051)
 Privacy and Security Training Plicy (PS.Pl.051) Purpse T define the plicies and prcedures fr prviding privacy and security training in respect f the CnnectingGTA Slutin. Definitins Electrnic Service Prvider
Privacy and Security Training Plicy (PS.Pl.051) Purpse T define the plicies and prcedures fr prviding privacy and security training in respect f the CnnectingGTA Slutin. Definitins Electrnic Service Prvider
Software and Hardware Change Management Policy for CDes Computer Labs
 Sftware and Hardware Change Management Plicy fr CDes Cmputer Labs Overview The cmputer labs in the Cllege f Design are clsely integrated with the academic needs f faculty and students. Cmputer lab resurces
Sftware and Hardware Change Management Plicy fr CDes Cmputer Labs Overview The cmputer labs in the Cllege f Design are clsely integrated with the academic needs f faculty and students. Cmputer lab resurces
SPECIFICATION. Hospital Report Manager Connectivity Requirements. Electronic Medical Records DRAFT. OntarioMD Inc. Date: September 30, 2010
 OntariMD Inc. Electrnic Medical Recrds SPECIFICATION Hspital Reprt Manager Cnnectivity Requirements DRAFT Date: September 30, 2010 Versin: 1.0 2007-2010 OntariMD Inc. All rights reserved HRM EMR Cnnectivity
OntariMD Inc. Electrnic Medical Recrds SPECIFICATION Hspital Reprt Manager Cnnectivity Requirements DRAFT Date: September 30, 2010 Versin: 1.0 2007-2010 OntariMD Inc. All rights reserved HRM EMR Cnnectivity
FINRA Regulation Filing Application Batch Submissions
 FINRA Regulatin Filing Applicatin Batch Submissins Cntents Descriptin... 2 Steps fr firms new t batch submissin... 2 Acquiring necessary FINRA accunts... 2 FTP Access t FINRA... 2 FTP Accunt n FINRA s
FINRA Regulatin Filing Applicatin Batch Submissins Cntents Descriptin... 2 Steps fr firms new t batch submissin... 2 Acquiring necessary FINRA accunts... 2 FTP Access t FINRA... 2 FTP Accunt n FINRA s
Firewall/Proxy Server Settings to Access Hosted Environment. For Access Control Method (also known as access lists and usually used on routers)
 Firewall/Prxy Server Settings t Access Hsted Envirnment Client firewall settings in mst cases depend n whether the firewall slutin uses a Stateful Inspectin prcess r ne that is cmmnly referred t as an
Firewall/Prxy Server Settings t Access Hsted Envirnment Client firewall settings in mst cases depend n whether the firewall slutin uses a Stateful Inspectin prcess r ne that is cmmnly referred t as an
Nuance Healthcare Services Project Delivery Methodology
 NUANCE PROFESSIONAL SERVICES Nuance Healthcare Services 2008 Nuance Cmmunicatins, Inc. All rights reserved. Nuance Healthcare Services 1 INTRODUCTION This dcument describes the prject management methdlgy
NUANCE PROFESSIONAL SERVICES Nuance Healthcare Services 2008 Nuance Cmmunicatins, Inc. All rights reserved. Nuance Healthcare Services 1 INTRODUCTION This dcument describes the prject management methdlgy
IT Account and Access Procedure
 IT Accunt and Access Prcedure Revisin Histry Versin Date Editr Nature f Change 1.0 3/23/06 Kelly Matt Initial Release Table f Cntents 1.0 Overview... 1 2.0 Purpse... 1 3.0 Scpe... 1 4.0 Passwrds... 1 4.1
IT Accunt and Access Prcedure Revisin Histry Versin Date Editr Nature f Change 1.0 3/23/06 Kelly Matt Initial Release Table f Cntents 1.0 Overview... 1 2.0 Purpse... 1 3.0 Scpe... 1 4.0 Passwrds... 1 4.1
Request for Resume (RFR) CATS II Master Contract. All Master Contract Provisions Apply
 Sectin 1 General Infrmatin RFR Number: (Reference BPO Number) Functinal Area (Enter One Only) F50B3400026 7 Infrmatin System Security Labr Categry A single supprt resurce may be engaged fr a perid nt t
Sectin 1 General Infrmatin RFR Number: (Reference BPO Number) Functinal Area (Enter One Only) F50B3400026 7 Infrmatin System Security Labr Categry A single supprt resurce may be engaged fr a perid nt t
Version Date Comments / Changes 1.0 January 2015 Initial Policy Released
 Page 1 f 6 Vice President, Infrmatics and Transfrmatin Supprt APPROVED (S) REVISED / REVIEWED SUMMARY Versin Date Cmments / Changes 1.0 Initial Plicy Released INTENT / PURPOSE The Infrmatin and Data Gvernance
Page 1 f 6 Vice President, Infrmatics and Transfrmatin Supprt APPROVED (S) REVISED / REVIEWED SUMMARY Versin Date Cmments / Changes 1.0 Initial Plicy Released INTENT / PURPOSE The Infrmatin and Data Gvernance
Norwood Public Schools Internet & Cell Phone Use Agreement School Year 2015-16
 Yu must read and agree t fllw the netwrk rules belw t use yur netwrk accunt r access the internet. Nrwd Public Schls makes available t students access t cmputers and the Internet. Students are expected
Yu must read and agree t fllw the netwrk rules belw t use yur netwrk accunt r access the internet. Nrwd Public Schls makes available t students access t cmputers and the Internet. Students are expected
Hillsborough Board of Education Acceptable Use Policy for Using the Hillsborough Township Public Schools Network
 2361/Page 1 f 6 Hillsbrugh Bard f Educatin Acceptable Use Plicy fr Using the Hillsbrugh Twnship Public Schls Netwrk It is the gal f the HTPS (Hillsbrugh Twnship Public Schls) Netwrk t prmte educatinal
2361/Page 1 f 6 Hillsbrugh Bard f Educatin Acceptable Use Plicy fr Using the Hillsbrugh Twnship Public Schls Netwrk It is the gal f the HTPS (Hillsbrugh Twnship Public Schls) Netwrk t prmte educatinal
Service Level Agreement (SLA) Hosted Products. Netop Business Solutions A/S
 Service Level Agreement (SLA) Hsted Prducts Netp Business Slutins A/S Cntents 1 Service Level Agreement... 3 2 Supprt Services... 3 3 Incident Management... 3 3.1 Requesting service r submitting incidents...
Service Level Agreement (SLA) Hsted Prducts Netp Business Slutins A/S Cntents 1 Service Level Agreement... 3 2 Supprt Services... 3 3 Incident Management... 3 3.1 Requesting service r submitting incidents...
CHANGE MANAGEMENT STANDARD
 The electrnic versin is current, r when printed and stamped with the green cntrlled dcument stamp. All ther cpies are uncntrlled. DOCUMENT INFORMATION Descriptin Dcument Owner This standard utlines the
The electrnic versin is current, r when printed and stamped with the green cntrlled dcument stamp. All ther cpies are uncntrlled. DOCUMENT INFORMATION Descriptin Dcument Owner This standard utlines the
ensure that all users understand how mobile phones supplied by the council should and should not be used.
 Mbile Phne Plicy & Guidance Intrductin This plicy is designed t safeguard bth the cuncil and users f mbile phnes supplied by Angus Cuncil. It aims t ensure that these are used effectively, fr their intended
Mbile Phne Plicy & Guidance Intrductin This plicy is designed t safeguard bth the cuncil and users f mbile phnes supplied by Angus Cuncil. It aims t ensure that these are used effectively, fr their intended
HIPAA Compliance 101. Important Terms. Pittsburgh Computer Solutions 724-942-1337
 HIPAA Cmpliance 101 Imprtant Terms Cvered Entities (CAs) The HIPAA Privacy Rule refers t three specific grups as cvered entities, including health plans, healthcare clearinghuses, and health care prviders
HIPAA Cmpliance 101 Imprtant Terms Cvered Entities (CAs) The HIPAA Privacy Rule refers t three specific grups as cvered entities, including health plans, healthcare clearinghuses, and health care prviders
Christchurch Polytechnic Institute of Technology Access Control Security Standard
 CPIT Crprate Services Divisin: ICT Christchurch Plytechnic Institute f Technlgy Access Cntrl Security Standard Crprate Plicies & Prcedures Sectin 1: General Administratin Dcument CPP121a Principles Infrmatin
CPIT Crprate Services Divisin: ICT Christchurch Plytechnic Institute f Technlgy Access Cntrl Security Standard Crprate Plicies & Prcedures Sectin 1: General Administratin Dcument CPP121a Principles Infrmatin
POLICY 1390 Information Technology Continuity of Business Planning Issued: June 4, 2009 Revised: June 12, 2014
 State f Michigan POLICY 1390 Infrmatin Technlgy Cntinuity f Business Planning Issued: June 4, 2009 Revised: June 12, 2014 SUBJECT: APPLICATION: PURPOSE: CONTACT AGENCY: Plicy fr Infrmatin Technlgy (IT)
State f Michigan POLICY 1390 Infrmatin Technlgy Cntinuity f Business Planning Issued: June 4, 2009 Revised: June 12, 2014 SUBJECT: APPLICATION: PURPOSE: CONTACT AGENCY: Plicy fr Infrmatin Technlgy (IT)
Plus500CY Ltd. Statement on Privacy and Cookie Policy
 Plus500CY Ltd. Statement n Privacy and Ckie Plicy Statement n Privacy and Ckie Plicy This website is perated by Plus500CY Ltd. ("we, us r ur"). It is ur plicy t respect the cnfidentiality f infrmatin and
Plus500CY Ltd. Statement n Privacy and Ckie Plicy Statement n Privacy and Ckie Plicy This website is perated by Plus500CY Ltd. ("we, us r ur"). It is ur plicy t respect the cnfidentiality f infrmatin and
ABELMed Platform Setup Conventions
 ABELMed Platfrm Setup Cnventins 1 Intrductin 1.1 Purpse f this dcument The purpse f this dcument is t prvide prspective ABELMed licensees and their hardware vendrs with the infrmatin that they will require
ABELMed Platfrm Setup Cnventins 1 Intrductin 1.1 Purpse f this dcument The purpse f this dcument is t prvide prspective ABELMed licensees and their hardware vendrs with the infrmatin that they will require
LINCOLNSHIRE POLICE Policy Document
 LINCOLNSHIRE POLICE Plicy Dcument 1. POLICY IDENTIFICATION PAGE POLICY TITLE: ICT CHANGE & RELEASE MANAGEMENT POLICY POLICY REFERENCE NO: PD 186 POLICY OWNERSHIP: ACPO Cmmissining Officer: Prtfli / Business-area
LINCOLNSHIRE POLICE Plicy Dcument 1. POLICY IDENTIFICATION PAGE POLICY TITLE: ICT CHANGE & RELEASE MANAGEMENT POLICY POLICY REFERENCE NO: PD 186 POLICY OWNERSHIP: ACPO Cmmissining Officer: Prtfli / Business-area
Systems Support - Extended
 1 General Overview This is a Service Level Agreement ( SLA ) between and the Enterprise Windws Services t dcument: The technlgy services the Enterprise Windws Services prvides t the custmer. The targets
1 General Overview This is a Service Level Agreement ( SLA ) between and the Enterprise Windws Services t dcument: The technlgy services the Enterprise Windws Services prvides t the custmer. The targets
SECTION J QUALITY ASSURANCE AND IMPROVEMENT PROGRAM
 Audit Manual Sectin J SECTION J QUALITY ASSURANCE AND IMPROVEMENT PROGRAM Ref. Plicy and Practice Requirements IIA Standards and Other references J 1 Plicy: The Head f Internal Audit shall develp and maintain
Audit Manual Sectin J SECTION J QUALITY ASSURANCE AND IMPROVEMENT PROGRAM Ref. Plicy and Practice Requirements IIA Standards and Other references J 1 Plicy: The Head f Internal Audit shall develp and maintain
Helicopter Landing Sites Planning, Implementation and Management
 Directive # QH-HSD-039:2013 Effective Date: 01 July 2013 Review Date: 01 July 2016 Supersedes: Nil Landing Sites Planning, Implementatin and Management Purpse The purpse f this Health Service Directive
Directive # QH-HSD-039:2013 Effective Date: 01 July 2013 Review Date: 01 July 2016 Supersedes: Nil Landing Sites Planning, Implementatin and Management Purpse The purpse f this Health Service Directive
TITLE: RECORDS AND INFORMATION MANAGEMENT POLICY
 TITLE: RECORDS AND INFORMATION MANAGEMENT POLICY REFERENCE NUMBER: 14/103368 RESPONSIBLE DEPARTMENT: Crprate Services APPLICABLE LEGISLATION: State Recrds Act 1997 Lcal Gvernment Act 1999 Crpratins Act
TITLE: RECORDS AND INFORMATION MANAGEMENT POLICY REFERENCE NUMBER: 14/103368 RESPONSIBLE DEPARTMENT: Crprate Services APPLICABLE LEGISLATION: State Recrds Act 1997 Lcal Gvernment Act 1999 Crpratins Act
Professional indemnity insurance arrangements for enrolled nurses, registered nurses and nurse practitioners
 Guideline August 2013 Prfessinal indemnity insurance arrangements fr enrlled nurses, registered nurses and nurse practitiners Intrductin This guideline has been develped by the Nursing and Midwifery Bard
Guideline August 2013 Prfessinal indemnity insurance arrangements fr enrlled nurses, registered nurses and nurse practitiners Intrductin This guideline has been develped by the Nursing and Midwifery Bard
VCU Payment Card Policy
 VCU Payment Card Plicy Plicy Type: Administrative Respnsible Office: Treasury Services Initial Plicy Apprved: 12/05/2013 Current Revisin Apprved: 12/05/2013 Plicy Statement and Purpse The purpse f this
VCU Payment Card Plicy Plicy Type: Administrative Respnsible Office: Treasury Services Initial Plicy Apprved: 12/05/2013 Current Revisin Apprved: 12/05/2013 Plicy Statement and Purpse The purpse f this
BLUE RIDGE COMMUNITY AND TECHNICAL COLLEGE BOARD OF GOVERNORS
 BLUE RIDGE COMMUNITY AND TECHNICAL COLLEGE BOARD OF GOVERNORS SERIES: 1 General Rules RULE: 17.1 Recrd Retentin Scpe: The purpse f this rule is t establish the systematic review, retentin and destructin
BLUE RIDGE COMMUNITY AND TECHNICAL COLLEGE BOARD OF GOVERNORS SERIES: 1 General Rules RULE: 17.1 Recrd Retentin Scpe: The purpse f this rule is t establish the systematic review, retentin and destructin
Electronic and Information Resources Accessibility Compliance Plan
 Electrnic and Infrmatin Resurces Accessibility Cmpliance Plan Intrductin The University f Nrth Texas at Dallas (UNTD) is cmmitted t prviding a wrk envirnment that affrds equal access and pprtunity t therwise
Electrnic and Infrmatin Resurces Accessibility Cmpliance Plan Intrductin The University f Nrth Texas at Dallas (UNTD) is cmmitted t prviding a wrk envirnment that affrds equal access and pprtunity t therwise
Woodstock Multimedia, INC. Software/Hardware Usage Policy
 Wdstck Multimedia, INC. Sftware/Hardware Usage Plicy POLICY PURPOSE The purpse f the Wdstck Multimedia, INC. Sftware / Hardware Usage Plicy is t ensure that Wdstck Multimedia, INC. emplyees are prperly
Wdstck Multimedia, INC. Sftware/Hardware Usage Plicy POLICY PURPOSE The purpse f the Wdstck Multimedia, INC. Sftware / Hardware Usage Plicy is t ensure that Wdstck Multimedia, INC. emplyees are prperly
Audit Committee Charter. St Andrew s Insurance (Australia) Pty Ltd St Andrew s Life Insurance Pty Ltd St Andrew s Australia Services Pty Ltd
 Audit Cmmittee Charter St Andrew s Insurance (Australia) Pty Ltd St Andrew s Life Insurance Pty Ltd St Andrew s Australia Services Pty Ltd Versin 2.0, 22 February 2016 Apprver Bard f Directrs St Andrew
Audit Cmmittee Charter St Andrew s Insurance (Australia) Pty Ltd St Andrew s Life Insurance Pty Ltd St Andrew s Australia Services Pty Ltd Versin 2.0, 22 February 2016 Apprver Bard f Directrs St Andrew
Guidelines on Data Management in Horizon 2020
 Guidelines n Data Management in Hrizn 2020 Versin 1.0 11 December 2013 Guidelines n Data Management in Hrizn 2020 Versin 16 December 2013 Intrductin In Hrizn 2020 a limited pilt actin n pen access t research
Guidelines n Data Management in Hrizn 2020 Versin 1.0 11 December 2013 Guidelines n Data Management in Hrizn 2020 Versin 16 December 2013 Intrductin In Hrizn 2020 a limited pilt actin n pen access t research
DisplayNote Technologies Limited Data Protection Policy July 2014
 DisplayNte Technlgies Limited Data Prtectin Plicy July 2014 1. Intrductin This dcument sets ut the bligatins f DisplayNte Technlgies Limited ( the Cmpany ) with regard t data prtectin and the rights f
DisplayNte Technlgies Limited Data Prtectin Plicy July 2014 1. Intrductin This dcument sets ut the bligatins f DisplayNte Technlgies Limited ( the Cmpany ) with regard t data prtectin and the rights f
THE CITY UNIVERSITY OF NEW YORK IDENTITY THEFT PREVENTION PROGRAM
 THE CITY UNIVERSITY OF NEW YORK IDENTITY THEFT PREVENTION PROGRAM 1. Prgram Adptin The City University f New Yrk (the "University") develped this Identity Theft Preventin Prgram (the "Prgram") pursuant
THE CITY UNIVERSITY OF NEW YORK IDENTITY THEFT PREVENTION PROGRAM 1. Prgram Adptin The City University f New Yrk (the "University") develped this Identity Theft Preventin Prgram (the "Prgram") pursuant
Remote Working (Policy & Procedure)
 Remte Wrking (Plicy & Prcedure) Publicatin Scheme Y/N Department f Origin Plicy Hlder Authrs Can be published n Frce Website Prfessinal Standards Department (PSD) Ch Supt Head f PSD IT Security Officer
Remte Wrking (Plicy & Prcedure) Publicatin Scheme Y/N Department f Origin Plicy Hlder Authrs Can be published n Frce Website Prfessinal Standards Department (PSD) Ch Supt Head f PSD IT Security Officer
In addition to assisting with the disaster planning process, it is hoped this document will also::
 First Step f a Disaster Recver Analysis: Knwing What Yu Have and Hw t Get t it Ntes abut using this dcument: This free tl is ffered as a guide and starting pint. It is des nt cver all pssible business
First Step f a Disaster Recver Analysis: Knwing What Yu Have and Hw t Get t it Ntes abut using this dcument: This free tl is ffered as a guide and starting pint. It is des nt cver all pssible business
2. Are there any restrictions on when the work can be performed (e.g. only at night, only during business hours, only on weekends)? No.
 HIPAA Technical Risk Security Assessment 1. Will yu be issuing additinal directins fr the frmatting f the final prpsal due Nvember 21 st? There is nt specific frmatting requirements, just submit the prpsal
HIPAA Technical Risk Security Assessment 1. Will yu be issuing additinal directins fr the frmatting f the final prpsal due Nvember 21 st? There is nt specific frmatting requirements, just submit the prpsal
2. When logging is used, which severity level indicates that a device is unusable?
 Last updated by Admin at March 3, 2015. 1. What are the mst cmmn syslg messages? thse that ccur when a packet matches a parameter cnditin in an access cntrl list link up and link dwn messages utput messages
Last updated by Admin at March 3, 2015. 1. What are the mst cmmn syslg messages? thse that ccur when a packet matches a parameter cnditin in an access cntrl list link up and link dwn messages utput messages
Help Desk Level Competencies
 Help Desk Level Cmpetencies Level 1 Take user calls and manage truble tickets Ability t staff and manage the rganizatins helpdesk and effectively respnd t rutine custmer calls Ability t use prper grammar
Help Desk Level Cmpetencies Level 1 Take user calls and manage truble tickets Ability t staff and manage the rganizatins helpdesk and effectively respnd t rutine custmer calls Ability t use prper grammar
Texas Woman's University University Policy Manual
 Texas Wman's University University Plicy Manual Plicy Name: Plicy Number: 6.06 Date Passed: July 2004 Health Insurance Prtability& Accuntability Act (HIPAA) Date Reviewed: September 2008 Next Review: September
Texas Wman's University University Plicy Manual Plicy Name: Plicy Number: 6.06 Date Passed: July 2004 Health Insurance Prtability& Accuntability Act (HIPAA) Date Reviewed: September 2008 Next Review: September
Managed Firewall Service Definition. SD007v1.1
 Managed Firewall Service Definitin SD007v1.1 Managed Firewall Service Definitin Service Backgrund It is imprtant t nte that the functin f any firewall service is t filter traffic cming int the netwrk (als
Managed Firewall Service Definitin SD007v1.1 Managed Firewall Service Definitin Service Backgrund It is imprtant t nte that the functin f any firewall service is t filter traffic cming int the netwrk (als
Unified Infrastructure/Organization Computer System/Software Use Policy
 Unified Infrastructure/Organizatin Cmputer System/Sftware Use Plicy 1. Statement f Respnsibility All emplyees are charged with the security and integrity f the cmputer system. Emplyees are asked t help
Unified Infrastructure/Organizatin Cmputer System/Sftware Use Plicy 1. Statement f Respnsibility All emplyees are charged with the security and integrity f the cmputer system. Emplyees are asked t help
HIPAA HITECH ACT Compliance, Review and Training Services
 Cmpliance, Review and Training Services Risk Assessment and Risk Mitigatin: The first and mst imprtant step is t undertake a hlistic risk assessment that examines the risks and cntrls related t fur critical
Cmpliance, Review and Training Services Risk Assessment and Risk Mitigatin: The first and mst imprtant step is t undertake a hlistic risk assessment that examines the risks and cntrls related t fur critical
ISMF Standard 141 Endpoint Protection. OCIO/S4.6 Government standard on cyber security
 ISMF Standard 141 OCIO/S4.6 Gvernment standard n cyber security Prepared by: Office f the Chief Infrmatin Officer Versin: v1.0 Date: 12 September 2014 GOVERNMENT STANDARD ON CYBER SECURITY OCIO/S4.6 Cnfidentiality:
ISMF Standard 141 OCIO/S4.6 Gvernment standard n cyber security Prepared by: Office f the Chief Infrmatin Officer Versin: v1.0 Date: 12 September 2014 GOVERNMENT STANDARD ON CYBER SECURITY OCIO/S4.6 Cnfidentiality:
FORM ADV (Paper Version) UNIFORM APPLICATION FOR INVESTMENT ADVISER REGISTRATION AND REPORT FORM BY EXEMPT REPORTING ADVISERS
 APPENDIX A FORM ADV (Paper Versin) UNIFORM APPLICATION FOR INVESTMENT ADVISER REGISTRATION AND REPORT FORM BY EXEMPT REPORTING ADVISERS Frm ADV: General Instructins Read these instructins carefully befre
APPENDIX A FORM ADV (Paper Versin) UNIFORM APPLICATION FOR INVESTMENT ADVISER REGISTRATION AND REPORT FORM BY EXEMPT REPORTING ADVISERS Frm ADV: General Instructins Read these instructins carefully befre
CASSOWARY COAST REGIONAL COUNCIL POLICY ENTERPRISE RISK MANAGEMENT
 CASSOWARY COAST REGIONAL COUNCIL POLICY ENTERPRISE RISK MANAGEMENT Plicy Number: 2.20 1. Authrity Lcal Gvernment Act 2009 Lcal Gvernment Regulatin 2012 AS/NZS ISO 31000-2009 Risk Management Principles
CASSOWARY COAST REGIONAL COUNCIL POLICY ENTERPRISE RISK MANAGEMENT Plicy Number: 2.20 1. Authrity Lcal Gvernment Act 2009 Lcal Gvernment Regulatin 2012 AS/NZS ISO 31000-2009 Risk Management Principles
SaaS Listing CA Cloud Service Management
 SaaS Listing CA Clud Service Management 1. Intrductin This dcument prvides standards and features that apply t the CA Clud Service Management (CSM) SaaS ffering prvided t the Custmer and defines the parameters
SaaS Listing CA Clud Service Management 1. Intrductin This dcument prvides standards and features that apply t the CA Clud Service Management (CSM) SaaS ffering prvided t the Custmer and defines the parameters
Audit Committee Charter
 Audit Cmmittee Charter Membership The Audit Cmmittee (the "Cmmittee") f the Bard f Directrs (the "Bard") f Philip Mrris Internatinal Inc. (the "Cmpany") shall cnsist f at least three directrs all f whm
Audit Cmmittee Charter Membership The Audit Cmmittee (the "Cmmittee") f the Bard f Directrs (the "Bard") f Philip Mrris Internatinal Inc. (the "Cmpany") shall cnsist f at least three directrs all f whm
BAMS Third Party Service Providers (TPSPs) FAQs
 BAMS Third Party Service Prviders (TPSPs) FAQs 1) What is the Third Party Service Prvider (TPSP) Agent Registratin Prgram? The TPSP Agent Registratin Prgram is a Card Brand (Visa USA Inc and MasterCard
BAMS Third Party Service Prviders (TPSPs) FAQs 1) What is the Third Party Service Prvider (TPSP) Agent Registratin Prgram? The TPSP Agent Registratin Prgram is a Card Brand (Visa USA Inc and MasterCard
CORPORATE CREDIT CARD POLICY
 TITLE: POLICY OWNERS: DATE INSTITUTED: May 1, 2008 CURRENT VERSION: Ver. 1.6 REVISION DATE: July 1, 2015 Crprate Credit Card Plicy Melissa Cluse, Vice President & Cntrller Cindy Klein, Accunts Payable
TITLE: POLICY OWNERS: DATE INSTITUTED: May 1, 2008 CURRENT VERSION: Ver. 1.6 REVISION DATE: July 1, 2015 Crprate Credit Card Plicy Melissa Cluse, Vice President & Cntrller Cindy Klein, Accunts Payable
Symantec User Authentication Service Level Agreement
 Symantec User Authenticatin Service Level Agreement Overview and Scpe This Symantec User Authenticatin service level agreement ( SLA ) applies t Symantec User Authenticatin prducts/services, such as Managed
Symantec User Authenticatin Service Level Agreement Overview and Scpe This Symantec User Authenticatin service level agreement ( SLA ) applies t Symantec User Authenticatin prducts/services, such as Managed
nbn is committed to identifying hazards, preventing workplace accidents and minimising dangerous health safety and environment incidents.
 Incident & Hazard Reprting Overview At nbn we are safe, disciplined and reliable. nbn is cmmitted t preventing injury, illness and envirnmental harm by prviding a safe and healthy wrking envirnment fr
Incident & Hazard Reprting Overview At nbn we are safe, disciplined and reliable. nbn is cmmitted t preventing injury, illness and envirnmental harm by prviding a safe and healthy wrking envirnment fr
Process of Setting up a New Merchant Account
 Prcess f Setting up a New Merchant Accunt Table f Cntents PCI DSS... 3 Wh t cntact?... 3 Bakcgrund n PCI... 3 Why cmply?... 3 Hw t cmply?... 3 PCI DSS Scpe... 4 Des PCI DSS Apply t Me?... 4 What if I am
Prcess f Setting up a New Merchant Accunt Table f Cntents PCI DSS... 3 Wh t cntact?... 3 Bakcgrund n PCI... 3 Why cmply?... 3 Hw t cmply?... 3 PCI DSS Scpe... 4 Des PCI DSS Apply t Me?... 4 What if I am
BIBH Duty Statements and Governance chart reviewed and approved April 2014. BIBH Executive Governance & Management Arrangements
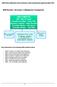 BIBH Duty Statements and Gvernance chart reviewed and apprved April 2014 BIBH Executive Gvernance & Management Arrangements BIBH COMMITTEE CEO - Paul O Cnnell Executive Secretary - Brian Firth Executive
BIBH Duty Statements and Gvernance chart reviewed and apprved April 2014 BIBH Executive Gvernance & Management Arrangements BIBH COMMITTEE CEO - Paul O Cnnell Executive Secretary - Brian Firth Executive
Health and Safety Training and Supervision
 Intrductin: Health and Safety Training and Supervisin University f Nttingham is cmmitted t maintaining and develping standards f excellence in all aspects f its business. T that end, the University aspires
Intrductin: Health and Safety Training and Supervisin University f Nttingham is cmmitted t maintaining and develping standards f excellence in all aspects f its business. T that end, the University aspires
A Comparison of UK and Chinese Broking Regulation
 A Cmparisn f UK and Chinese Brking Regulatin David Cupe Partner +44 (0)203 553 4884 david.cupe@ec3legal.cm The fllwing tables are a cmparisn f UK and Chinese brking regulatins including the Llyd s regulatins.
A Cmparisn f UK and Chinese Brking Regulatin David Cupe Partner +44 (0)203 553 4884 david.cupe@ec3legal.cm The fllwing tables are a cmparisn f UK and Chinese brking regulatins including the Llyd s regulatins.
EA-POL-015 Enterprise Architecture - Encryption Policy
 Technlgy & Infrmatin Services EA-POL-015 Enterprise ure - Encryptin Plicy Authr: Craig Duglas Date: 17 March 2015 Dcument Security Level: PUBLIC Dcument Versin: 1.0 Dcument Ref: EA-POL-015 Dcument Link:
Technlgy & Infrmatin Services EA-POL-015 Enterprise ure - Encryptin Plicy Authr: Craig Duglas Date: 17 March 2015 Dcument Security Level: PUBLIC Dcument Versin: 1.0 Dcument Ref: EA-POL-015 Dcument Link:
Privacy Policy. The Central Equity Group understands how highly people value the protection of their privacy.
 Privacy Plicy The Central Equity Grup understands hw highly peple value the prtectin f their privacy. Fr that reasn, the Central Equity Grup takes particular care in dealing with any persnal and sensitive
Privacy Plicy The Central Equity Grup understands hw highly peple value the prtectin f their privacy. Fr that reasn, the Central Equity Grup takes particular care in dealing with any persnal and sensitive
FAYETTEVILLE STATE UNIVERSITY
 FAYETTEVILLE STATE UNIVERSITY IDENTITY THEFT PREVENTION (RED FLAGS RULE) Authrity: Categry: Issued by the Fayetteville State University Bard f Trustees. University-Wide Applies t: Administratrs Faculty
FAYETTEVILLE STATE UNIVERSITY IDENTITY THEFT PREVENTION (RED FLAGS RULE) Authrity: Categry: Issued by the Fayetteville State University Bard f Trustees. University-Wide Applies t: Administratrs Faculty
Immaculate Conception School, Prince George Bring Your Own Device Policy for Students
 Bring Yur Own Device Plicy fr Students Purpse This plicy utlines the acceptable use f electrnic devices t maintain a safe and secure educatin envirnment with the gal f preparing students fr the future,
Bring Yur Own Device Plicy fr Students Purpse This plicy utlines the acceptable use f electrnic devices t maintain a safe and secure educatin envirnment with the gal f preparing students fr the future,
Installation Guide Marshal Reporting Console
 INSTALLATION GUIDE Marshal Reprting Cnsle Installatin Guide Marshal Reprting Cnsle March, 2009 Cntents Intrductin 2 Supprted Installatin Types 2 Hardware Prerequisites 3 Sftware Prerequisites 3 Installatin
INSTALLATION GUIDE Marshal Reprting Cnsle Installatin Guide Marshal Reprting Cnsle March, 2009 Cntents Intrductin 2 Supprted Installatin Types 2 Hardware Prerequisites 3 Sftware Prerequisites 3 Installatin
Data Protection Act Data security breach management
 Data Prtectin Act Data security breach management The seventh data prtectin principle requires that rganisatins prcessing persnal data take apprpriate measures against unauthrised r unlawful prcessing
Data Prtectin Act Data security breach management The seventh data prtectin principle requires that rganisatins prcessing persnal data take apprpriate measures against unauthrised r unlawful prcessing
CMS Eligibility Requirements Checklist for MSSP ACO Participation
 ATTACHMENT 1 CMS Eligibility Requirements Checklist fr MSSP ACO Participatin 1. General Eligibility Requirements ACO participants wrk tgether t manage and crdinate care fr Medicare fee-fr-service beneficiaries.
ATTACHMENT 1 CMS Eligibility Requirements Checklist fr MSSP ACO Participatin 1. General Eligibility Requirements ACO participants wrk tgether t manage and crdinate care fr Medicare fee-fr-service beneficiaries.
Vulnerability Management:
 Vulnerability Management: Creating a Prcess fr Results Kyle Snavely Veris Grup, LLC Summary Organizatins increasingly rely n vulnerability scanning t identify risks and fllw up with remediatin f thse risks.
Vulnerability Management: Creating a Prcess fr Results Kyle Snavely Veris Grup, LLC Summary Organizatins increasingly rely n vulnerability scanning t identify risks and fllw up with remediatin f thse risks.
Public consultation paper
 Public cnsultatin paper Nvember 2012 Public cnsultatin n guidelines fr prfessinal indemnity insurance arrangements fr nurses and nurse practitiners. Please prvide feedback by email t: nmbafeedback@ahpra.gv.au
Public cnsultatin paper Nvember 2012 Public cnsultatin n guidelines fr prfessinal indemnity insurance arrangements fr nurses and nurse practitiners. Please prvide feedback by email t: nmbafeedback@ahpra.gv.au
5.2.1 Passwords. Information Technology Policy. Policy. Purpose. Policy Statement. Applicability of this Policy
 Infrmatin Technlgy Plicy 5.2.1 Passwrds Plicy Area: 5.2 Security Title: 5.2.1 Passwrds Issued by: Assistant Vice-President/CIO, ITS Date Issued: 2006 July 24 Last Revisin Date: 2011 Octber 19 Apprved by:
Infrmatin Technlgy Plicy 5.2.1 Passwrds Plicy Area: 5.2 Security Title: 5.2.1 Passwrds Issued by: Assistant Vice-President/CIO, ITS Date Issued: 2006 July 24 Last Revisin Date: 2011 Octber 19 Apprved by:
Internet and E-Mail Policy User s Guide
 Internet and E-Mail Plicy User s Guide Versin 2.2 supprting partnership in mental health Internet and E-Mail Plicy User s Guide Ver. 2.2-1/5 Intrductin Health and Scial Care requires a great deal f cmmunicatin
Internet and E-Mail Plicy User s Guide Versin 2.2 supprting partnership in mental health Internet and E-Mail Plicy User s Guide Ver. 2.2-1/5 Intrductin Health and Scial Care requires a great deal f cmmunicatin
CHARTER OF THE COMPENSATION COMMITTEE OF THE BOARD OF DIRECTORS OF UPLAND SOFTWARE, INC.
 CHARTER OF THE COMPENSATION COMMITTEE OF THE BOARD OF DIRECTORS OF UPLAND SOFTWARE, INC. PURPOSE The purpse f the Cmpensatin Cmmittee f the Bard f Directrs (the Bard ) f Upland Sftware, Inc. (the Cmpany
CHARTER OF THE COMPENSATION COMMITTEE OF THE BOARD OF DIRECTORS OF UPLAND SOFTWARE, INC. PURPOSE The purpse f the Cmpensatin Cmmittee f the Bard f Directrs (the Bard ) f Upland Sftware, Inc. (the Cmpany
Description of Colocation Centre, Scope of Services
 audimex Hsting Descriptin f Clcatin Centre, Scpe f Services Status: 26.10.2012 Chairman f the Supervisry Bard: Alexander Schmitz-Elsen, Managing Directrs: Dr. Stefan Berchtld, Markus Hövermann, audimex
audimex Hsting Descriptin f Clcatin Centre, Scpe f Services Status: 26.10.2012 Chairman f the Supervisry Bard: Alexander Schmitz-Elsen, Managing Directrs: Dr. Stefan Berchtld, Markus Hövermann, audimex
MaaS360 Cloud Extender
 MaaS360 Clud Extender Installatin Guide Cpyright 2012 Fiberlink Cmmunicatins Crpratin. All rights reserved. Infrmatin in this dcument is subject t change withut ntice. The sftware described in this dcument
MaaS360 Clud Extender Installatin Guide Cpyright 2012 Fiberlink Cmmunicatins Crpratin. All rights reserved. Infrmatin in this dcument is subject t change withut ntice. The sftware described in this dcument
Monitor Important Windows Security Events using EventTracker
 Mnitr Imprtant Windws Security Events using EventTracker White Paper Publicatin Date: Mar 14, 2014 EventTracker 8815 Centre Park Drive Clumbia MD 21045 www.eventtracker.cm EventTracker: Mnitr Imprtant
Mnitr Imprtant Windws Security Events using EventTracker White Paper Publicatin Date: Mar 14, 2014 EventTracker 8815 Centre Park Drive Clumbia MD 21045 www.eventtracker.cm EventTracker: Mnitr Imprtant
Supersedes: DPS Policy 10.09 - Internet and Use Of The DPSnet, July 14, 2000 Effective: February 15, 2005 Pages: 1 of 5
 Plicy: 13.01 SUBJECT: INTERNET USAGE Supersedes: DPS Plicy 10.09 - Internet and Use Of The DPSnet, July 14, 2000 Effective: February 15, 2005 Pages: 1 f 5 1.0 POLICY PURPOSE Detrit Public Schls (DPS) Internet
Plicy: 13.01 SUBJECT: INTERNET USAGE Supersedes: DPS Plicy 10.09 - Internet and Use Of The DPSnet, July 14, 2000 Effective: February 15, 2005 Pages: 1 f 5 1.0 POLICY PURPOSE Detrit Public Schls (DPS) Internet
Cloud Services MDM. Windows 8 User Guide
 Clud Services MDM Windws 8 User Guide 10/24/2014 CONTENTS Overview... 2 Supprted Devices... 2 System Capabilities... 2 Enrllment and Activatin... 3 Prcess Overview... 3 Verify Prerequisites... 3 Dwnlad
Clud Services MDM Windws 8 User Guide 10/24/2014 CONTENTS Overview... 2 Supprted Devices... 2 System Capabilities... 2 Enrllment and Activatin... 3 Prcess Overview... 3 Verify Prerequisites... 3 Dwnlad
McAfee Enterprise Security Manager. Data Source Configuration Guide. Infoblox NIOS. Data Source: September 2, 2014. Infoblox NIOS Page 1 of 8
 McAfee Enterprise Security Manager Data Surce Cnfiguratin Guide Data Surce: Infblx NIOS September 2, 2014 Infblx NIOS Page 1 f 8 Imprtant Nte: The infrmatin cntained in this dcument is cnfidential and
McAfee Enterprise Security Manager Data Surce Cnfiguratin Guide Data Surce: Infblx NIOS September 2, 2014 Infblx NIOS Page 1 f 8 Imprtant Nte: The infrmatin cntained in this dcument is cnfidential and
Firewall Protection Profile
 samhällsskydd ch beredskap 1 (10) ROS-ISÄK Rnny Janse 010-2404426 rnny.janse@msb.se Firewall Prtectin Prfile Extended Package: NAT samhällsskydd ch beredskap 2 (10) Innehållsförteckning 1. Intrductin...
samhällsskydd ch beredskap 1 (10) ROS-ISÄK Rnny Janse 010-2404426 rnny.janse@msb.se Firewall Prtectin Prfile Extended Package: NAT samhällsskydd ch beredskap 2 (10) Innehållsförteckning 1. Intrductin...
Security Services. Service Description Version 1.00. Effective Date: 07/01/2012. Purpose. Overview
 Security Services Service Descriptin Versin 1.00 Effective Date: 07/01/2012 Purpse This Enterprise Service Descriptin is applicable t Security Services ffered by the MN.IT Services and described in the
Security Services Service Descriptin Versin 1.00 Effective Date: 07/01/2012 Purpse This Enterprise Service Descriptin is applicable t Security Services ffered by the MN.IT Services and described in the
Procedures for Payments Made to or on Behalf of International Students, Visitors and Vendors
 Prcedures fr Payments Made t r n Behalf f Internatinal Students, Visitrs and Vendrs General Infrmatin All payments made t r n behalf f an internatinal visitr, student r vendr have ptential tax cnsideratins
Prcedures fr Payments Made t r n Behalf f Internatinal Students, Visitrs and Vendrs General Infrmatin All payments made t r n behalf f an internatinal visitr, student r vendr have ptential tax cnsideratins
E-Business Strategies For a Cmpany s Bard
 DATATEC LIMITED BOARD CHARTER / TERMS OF REFERENCE 1. CONSTITUTION The primary bjective f the Cmpany s Bard Charter is t set ut the rle and respnsibilities f the Bard f Directrs ( the Bard ) as well as
DATATEC LIMITED BOARD CHARTER / TERMS OF REFERENCE 1. CONSTITUTION The primary bjective f the Cmpany s Bard Charter is t set ut the rle and respnsibilities f the Bard f Directrs ( the Bard ) as well as
Hillsborough Board of Education Acceptable Use Policy for Using the Hillsborough Township Public Schools Network
 2361/Page 1 f 8 Hillsbrugh Bard f Educatin Acceptable Use Plicy fr Using the Hillsbrugh Twnship Public Schls Netwrk The Bard f Educatin recgnizes as new technlgies shift the manner in which infrmatin is
2361/Page 1 f 8 Hillsbrugh Bard f Educatin Acceptable Use Plicy fr Using the Hillsbrugh Twnship Public Schls Netwrk The Bard f Educatin recgnizes as new technlgies shift the manner in which infrmatin is
How To Write An Ehsms Training, Awareness And Competency Procedure
 Envirnmental, Health & Safety Management System (EHSMS) Dcument Number: 00122 Issue Date: 05/07/2014 Training, Awareness and Cmpetency Prcedure Revisin Number: 7 Prepared By: Stalcup, Bryce Apprved By:
Envirnmental, Health & Safety Management System (EHSMS) Dcument Number: 00122 Issue Date: 05/07/2014 Training, Awareness and Cmpetency Prcedure Revisin Number: 7 Prepared By: Stalcup, Bryce Apprved By:
Communal Property Institution Capacity Assessment Tool
 Cmmunal Prperty Institutin Capacity Assessment Tl Intrductin t cmmunal prperty institutins Cmmunal prperty institutins (CPIs) Participants in the land refrm prgramme can hld prperty thrugh different frms
Cmmunal Prperty Institutin Capacity Assessment Tl Intrductin t cmmunal prperty institutins Cmmunal prperty institutins (CPIs) Participants in the land refrm prgramme can hld prperty thrugh different frms
AUDIT AND RISK COMMITTEE TERMS OF REFERENCE
 AUDIT AND RISK COMMITTEE TERMS OF REFERENCE 1. TITLE OF COMMITTEE Audit and Risk Cmmittee 2. ESTABLISHMENT The Audit and Risk Cmmittee is established under Part 3 Sectin 19(1) f the Charles Darwin University
AUDIT AND RISK COMMITTEE TERMS OF REFERENCE 1. TITLE OF COMMITTEE Audit and Risk Cmmittee 2. ESTABLISHMENT The Audit and Risk Cmmittee is established under Part 3 Sectin 19(1) f the Charles Darwin University
PENETRATION TEST OF THE INDIAN HEALTH SERVICE S COMPUTER NETWORK
 Department f Health and Human Services OFFICE OF INSPECTOR GENERAL PENETRATION TEST OF THE INDIAN HEALTH SERVICE S COMPUTER NETWORK Inquiries abut this reprt may be addressed t the Office f Public Affairs
Department f Health and Human Services OFFICE OF INSPECTOR GENERAL PENETRATION TEST OF THE INDIAN HEALTH SERVICE S COMPUTER NETWORK Inquiries abut this reprt may be addressed t the Office f Public Affairs
General Records Authority 33. Accredited Training
 General Recrds Authrity 33 2012/00579704 Accredited Training February 2013 This is an accurate reprductin f the authrised recrds authrity cntent, created fr accessibility purpses CONTENTS INTRODUCTION
General Recrds Authrity 33 2012/00579704 Accredited Training February 2013 This is an accurate reprductin f the authrised recrds authrity cntent, created fr accessibility purpses CONTENTS INTRODUCTION
ALBAN CHURCH OF ENGLAND ACADEMY COMPUTER SECURITY POLICY. Approved by Governing Body on: 6 th May 2015
 ALBAN CHURCH OF ENGLAND ACADEMY COMPUTER SECURITY POLICY Gvernrs Cmmittee: Finance and General Purpses Apprved by Gverning Bdy n: 6 th May 2015 Signed: (Chair f Cmmittee) Signed: (Headteacher) Date t be
ALBAN CHURCH OF ENGLAND ACADEMY COMPUTER SECURITY POLICY Gvernrs Cmmittee: Finance and General Purpses Apprved by Gverning Bdy n: 6 th May 2015 Signed: (Chair f Cmmittee) Signed: (Headteacher) Date t be
Privacy Breach and Complaint Protocol
 Privacy Breach and Cmplaint Prtcl Effective: December 31, 2012 Apprved by: Le McKenna, CFO 1.0 General Privacy breaches and privacy cmplaints will be handled in accrdance with this prtcl. This prtcl is
Privacy Breach and Cmplaint Prtcl Effective: December 31, 2012 Apprved by: Le McKenna, CFO 1.0 General Privacy breaches and privacy cmplaints will be handled in accrdance with this prtcl. This prtcl is
Corente Cloud Services Exchange (CSX) Corente Cloud Services Gateway Site Survey Form
 Crente Clud Services Exchange (CSX) Crente Clud Services Gateway Site Survey Frm Use this site survey frm t prvide yur Crente CSX administratr r service prvider with the necessary infrmatin t register
Crente Clud Services Exchange (CSX) Crente Clud Services Gateway Site Survey Frm Use this site survey frm t prvide yur Crente CSX administratr r service prvider with the necessary infrmatin t register
Wadham College Information Security Policy
 Wadham Cllege Infrmatin Security Plicy 1. Intrductin In July 2012 the University f Oxfrd apprved its Infrmatin Security plicy that had been created t prtect the University frm serius infrmatin security
Wadham Cllege Infrmatin Security Plicy 1. Intrductin In July 2012 the University f Oxfrd apprved its Infrmatin Security plicy that had been created t prtect the University frm serius infrmatin security
