Static versus Dynamic Data Information Fusion analysis using DDDAS for Cyber Security Trust
|
|
|
- Carmel York
- 8 years ago
- Views:
Transcription
1 Static versus Dynamic Data Information Fusion analysis using DDDAS for Cyber Security Trust Erik Blasch AFRL/RIEA Rome, NY e erik.blasch@gmail.com Youssif Al-Nashif, Salim Hariri NSF Center for Cloud and Autonomic Computing, The University of Arizona Sponsor AFRL/AFOSR ICCS 2014 June 2014
2 PRESENTATION OUTLINE Motivation Information Fusion for Decision Making (Trust) Understand the flow of information in Man and Machines Information Fusion and DDDAS Information Management Flow Managers and QoS Flow SOA-based DDDAS - DaaS End to End Trust Metrics Summary of metrics Calculations Potential Use Case Scenarios for DaaS DDDAS-based Crisis Management
3 High Level Information Fusion Low-level Information Fusion High-level Information Fusion Human Level 0 SAW SENSATION Level 1 SAW PERCEPTION Level 2 SAW COMPREHENSION Level 3 SAW PROJECTION Situation Awareness (SAW) Interface Visualization (Evaluation) Observables (dots on maps) Objects (lines on maps) Situations (storytelling) Scenarios (forecasting) Machine Level 0 MIF SUB-OBJECT ASSESSMENT Level 1 MIF OBJECT ASSESSMENT Level 2 MIF SITUATION ASSESSMENT Level 3 MIF IMPACT ASSESSMENT Machine Information Fusion (MIF) Decompose problem into elements of LLIF and HLIF Determine the user (situation awareness) and machine (computation) Discussion on evaluation/visualization and projection 3
4 Blasch s book: HLIF Information/Resource Management Scenario Situation Object Observable Assessment High-Level Information Fusion Projection Comprehension TRUST Perception Sensation Awareness Low-Level Information Fusion Situation Analysis Evaluation Human - Machine Interface Machine Systems Design Human 4
5 Information Fusion and DDDAS 5
6 IF-DDDAS Design Challenges How do you handle, manage, and analyze Big amount of data, results, and users that are heterogeneous, dynamic, and continuously changing? How do you trust, quantify trust of users, data, results, etc.? How do you adopt, design, QoS, Quality of Protection (QoP) of such DDDAS environments? How can you integrate design stage and runtime stage to achieve continous integration of design and runtime? 6
7 OUTLINE Motivation Information Fusion for Decision Making (Trust) Understand the flow of information in Man and Machines Information Fusion and DDDAS Information Management Flow Managers and QoS Flow SOA-based DDDAS - DaaS End to End Trust Metrics Summary of metrics Calculations Potential Use Case Scenarios for DaaS DDDAS-based Crisis Management
8 Information Management Model 8
9 IF-DDDAS Environments Adapt DDDAS QoS, QoP at rutnime - DDDAS Analytics - Resilient DDDAS - Trustworthy DDDAS Managed Information Object MIO comprises a payload and metadata that characterize the object such as topic, time, and location. Manage Types Security Policy Resource Allocation Data Mediation Monitor & Audit Maintain Federations Maintain Currency Publish Advertise Get Feedback Receive RFIs Retract Managers Producers Actors Federates Consumer s Seamless Access Restrictions Mediation Integrity Information SLAs Search/Browse Subscribe Query Transform Assess 9
10 Distributed Information Management Coalition Issues Acquisition cannot be standardized or synchronized. Universal data standards are unrealistic. Data standards version skew is the norm not the exception. Coalition information spaces must adapt quickly to new partners and processes. Information Management Best Practices 1. Information Sharing - Package information for sharing. - Adopt common syntax and semantics for common information attributes such as location, time, and subject. 2. Reduce Complexity - Adopt dedicated IM infrastructure - Create simple ubiquitous common services 3. Control and Flexibility - Common Information Space 10
11 Proposed Solution: DDDAS as a Service (DaaS) Producer Information Brokering Service? Producer Submission Service Repository Service Dissemination Service = Query Service? Subscribing Consumer Query Consumer Online Storage 11
12 OUTLINE Motivation Information Fusion for Decision Making (Trust) Understand the flow of information in Man and Machines Information Fusion and DDDAS Information Management Flow Managers and QoS Flow (trust is a QoS service) Polices for Information Flow End to End Trust Metrics Summary of metrics Calculations Potential Use Case Scenarios DDDAS-based Crisis Management
13 Trust in Action Trust (Multidiscipline) - Users - Systems Jin-Hee Cho, Member, IEEE, Ananthram Swami, Fellow, IEEE, and Ing-Ray Chen, Member, IEEE, A Survey on Trust Management for Mobile Ad Hoc Networks, IEEE COMMUNICATIONS SURVEYS & TUTORIALS, VOL. 13, NO. 4, FOURTH QUARTER
14 Human Trust Blasch, 2001, SPIE Rempel s stages, (Muir & Moray, 1996) postulated that Trust = Predictability + Dependability + Faith + Competence + Responsibility + Reliability Trust Dimensions Operator s trust & allocation of function Trusts and uses the automation Distrusts and rejects the automation Appropriate Trust (optimize system performance) False Distrust (lose benefits of automation, inc. workload) Quality of the automation Good Poor False Trust (risk automated disaster) Appropriate Distrust (optimize system performance) 14
15 Trust in Action Jin-Hee Cho, Member, IEEE, Ananthram Swami, Fellow, IEEE, and Ing-Ray Chen, Member, IEEE, A Survey on Trust Management for Mobile Ad Hoc Networks, IEEE COMMUNICATIONS SURVEYS & TUTORIALS, VOL. 13, NO. 4, FOURTH QUARTER
16 Trust and Risk Management Trust (Communication) - Networks - Message Passing Jin-Hee Cho, Member, IEEE, Ananthram Swami, Fellow, IEEE, and Ing-Ray Chen, Member, IEEE, A Survey on Trust Management for Mobile Ad Hoc Networks, IEEE COMMUNICATIONS SURVEYS & TUTORIALS, VOL. 13, NO. 4, FOURTH QUARTER
17 Proposed Approach: Trust Analysis and Quantification 4 Trust can be defined as a state of mind consisting of 0 Expectancy of what the trustee will do 0 Believe expected behavior will be performed 0 Willingness to take risk in trustee 4 Trust can be based on reputation 0 Collect from collaborating and interacting entities 4 Trust a factor of technology and computations End-to-end trust = f (Trust in infrastructure, Trust in entities) Which can be as simple as: End-to-end trust = (Trust in infrastructure) * (Trust in entities)
18 Trust Stack Brokerage Policies Enforcement Domain Trust Authority QoS, QoP Collecting Raw Metrics Behavior Analysis Analysis (Situation Awareness) Workflow Authentication and Authorization Security Secure Communication
19 Domainless Trust Evaluation Architecture
20 Domain Based Trust Evaluation Cross-Domain Trust
21 ATM Functionalities Trust Metrics between analysis and filtering Environment Entity Activity User Context Monitoring Collected Information Situation Analysis Vulnerability Analysis Anomaly Analysis Security Policy Analysis Directly Collected Context-Based Filtering Trust Metrics Quantification Trust Evaluation Trust Database Self-Trust Evaluation Machine-Trust Evaluation Peer-Trust Evaluation Data Decision Dissemination
22 TrustFlow Voltage Frequency Temperature I/O Paging Fan Privilege Level Behavior Logs User Hardware Software # of Cores CPU Utilization Memory Read/Write Manager Developer Application TRUST Network Number of Connection Correct Signature Logs Location Protection Apps Machines Middleware Bandwidth Packet Rate Machine Manager OS Firmware Logs
23 Trust Flow
24 Trust Metrics 24
25 Trust Metrics 25
26 Trust The trust of an entity is a function of its CIA: Confidentiality, Integrity, and Availability: CIA And since trust metrics are used to determine the values of the CIA components, we can use a function h that will map the trust metrics to the CIA components to get the trust: T (E) = f (Confidentiality, Integrity, Availability) T (E) = f (h(trust Metrics)) 4 Directly collected 4 Trust Measured outputs
27 Determining Initial Trust for a system Using NIST CVSS can determine the risk in a system. CVSS uses the following metrics to evaluate the score: - Base Metrics - Temporal Metrics - Environmental Metrics
28 Determining Initial Trust for a system Base Metrics: 4 Exploitability Metrics 0 Access Vector 0 Access Complexity 0 Authentication 4 Impact Metrics: 0 Confidentiality 0 Integrity 0 Availability Temporal Metrics: 4 Exploitability 4 Remediation Level 4 Report Confidence Environmental Metrics: 4 Collateral Damage Potential 4 Target Distribution 4 Security Requirements
29 User Trust 4 The initial user trust is a function based on the user rank and reputation at the time of adding it to the system. T (E,C) = T (User) T (Machine based on CVSS) 4 Trust measurement takes the value from 0 to 1 0 represents the distrust and 1 represent the blind or full trust. 4 We adopt the NIST standard SP 800 four levels of trust: 0 Distrust: 0 0 Low trust: Moderate Trust: High Trust: 1
30 Adaptive Trust 4 Trust Flow 0 The trust value assigned to each component is not static and will be updated continuously. 0 The Trust Authority module is the one responsible for re-evaluating the trust at runtime. 0 The trust is measured per entity and the trust levels are between 0 and 1. 4 The trust of an entity E is given by: T (E) [ 0,1] 4 Interaction between entities is defined by a context C. And the trust for entities will be computed per context:. T (E,C) [0,1]
31 Adaptive Trust (continue) 4 M i denotes the collected Trust Flow metric, where i is the metric identifier. The function m i () is a quantifying function that returns a measurement between 0 and 1 for the metric M i- 4 The trust for an entity will be computed using two types of trust: 0 Self-measured trust and 0 Reputation-measured trust.
32 Adaptive Trust (continue) Trust is evaluated by the Trust Authority Self-Trust Evaluation : T s (E,C) = T(ATM E,C) I i (C) m i (M i ) Peer-Trust Evaluation: T p (E,C) = 1 K K j=1 L i=1 T(ATM j,c) T p,e j (E j,c) C = Context (Mandatory Fields: Federal ID#; Optional Fields) E = Evaluation Strategies / Enforcement (Rules e.g.; Space, Time Policies). 4 The values of the metric weight I i for metric i is determined based on the feature selection technique, where: L i=1 I i (C) = 1
33 Adaptive Trust (continue) 4 Determining the peer trust is based on the gain or lose in the measured self-trust. 4 Assume that E 1 is communicating with E 2. We have the following facts after the communication: T s (E 1,C Before),T s (E 1,C After), T (E 2,C Before) 4 Then: T p,e1 (E 2,C After) = T s (E 1,C After) T s (E 1,C Before) > 1, Increase Trust(T(E 2,C Before)) T s (E 1,C After) T s (E 1,C Before) = 1, T(E 2,C Before) T s (E 1,C After) T s (E 1,C Before) < 1, Decrease Trust(T(E 2,C Before))
34 Adaptive Trust (continue) Based on the context and the type of operations, the end-to-end trust can be evaluated using three trust evaluation strategies: Optimistic, Pessimistic, and Average. The end-to-end trust for each strategy can be evaluated as follows: 4 Optimistic Trust Evaluation Strategy: T (E,C) = max(t s (E,C),T p (E,C)) 4 Pessimistic Trust Evaluation Strategy: T (E,C) = min(t s (E,C),T p (E,C)) 4 Average Trust Evaluation Strategy: T (E,C) = average(t s (E,C),T p (E,C)).
35 Context Context ID: The context ID consists of a mandatory part which is the application protocol that is used in establishing the connection and an optional part which consists of additional information such as location and objectives. Note: Optional Context ID doesn t mean it is not required for connections, it only means that not all connections require this field. 4 EX: A fighter is trying to download Targets map. 0 Context ID: Mandatory Fields: Federal ID#, Affiliation, Agency, Rank, Protocol: SFTP Optional: Location, Operation Context Enforcement: The context enforcement is the process of enforcing security policies based on the context of the communication. It is handled by the ATM. 4 The context enforcement could have the following as inputs: 0 Context ID 0 Entity ID: in cased of the domain based trust, this is a combination of the entity ID, group, domain. 0 Location 0 Trust Level
36 Example of Context Enforcement 4 Assume E 1 is communicating with E 2, the following is a possible policy for the context enforcement on ATM 1 which is responsible for handling E 1 communications: if ( E 2 Rome Labs) then Deny if ( Context Acceptable Air Force Contexts) then Deny if ( T (E 2,C) < Moderate Trust ) then Deny if ( Location(E 2 ) not in US) then Deny Accept
37 Trust Metrics Trust (T), Context (C), Metric (M) CYBER Example, ICCS2014 (ATM specific to Communications) Trust Confidence Optimistic Average Pessimistic Trust Evaluation Strategy T(E, C) = max {T S (E, C), T P (E, C)} T(E, C) = ave {T S (E, C), T P (E, C)} T(E, C) = min {T S (E, C), T P (E, C)}
38 OUTLINE Motivation Information Fusion for Decision Making (Trust) Understand the flow of information in Man and Machines Information Fusion and DDDAS Information Management Flow Managers and QoS Flow (trust is a QoS service) SOA-based DDDAS - DaaS End to End Trust Metrics Summary of metrics Calculations Potential Use Case Scenarios for DaaS DDDAS-based Crisis Management
39 DDDAS-based Crisis Management Battle Management Nuclear Disaster Management Terrorist/Accident Management Decision Makers Management Domain Domain Experts DDAS Analytics for Cybersecurity Actions Operations Domain Sensors Measurements Air Force Police Firemen First Medical Responders 39
40 DDDAS Components as a Service (DaaS) Producer Information Brokering Service? Producer Submission Service Repository Service Dissemination Service = Query Service? Subscribing Consumer Query Consumer Online Storage 40
41 SOA-based DDDAS Environment We are collaborating with:! Youakim Badr, LIRIS Lab, INSA- Lyon, France! Ilkay Altintas, UCSD!! Information Trust Infrastructure Business Process Service Providers S 1 S 2 Design time S 3 S 4 S 5 Runtime (ESB) Environment 41
42 SOA-based DDDAS Environment We are collaborating, with Ilkay Altintas, UCSD to use Kepler to implement DDDAS workflows that can meet any QoS, QoP or trust requirements for mission critical DDDAS environments 42
43 Resilient DDAS-based Models 4 Resilient models are based on (DDDAS) Info-Symbiotic Systems 4 Unify computing and measurements S n E n D n S n f(d n ) E n S n+1 S D 1 Time S 2 5 D 2 E n S n - D n Model evolution 6 S D 3 43
44 Generalized DaaS Business Requirements Model Design time Endogenous Changes QoS Model Tolerance Model Security Model generate affect Contextual Information Business Logic Security Model Exogenous Changes Ad-hoc Composition Approach affect runtime Running processes Infrastructure 44
45 Generalized Resilient DaaS Business Requirement Endogenous Changes Service Model Exogenous Changes Security Policy Context Model feedback generate Business Domain Security Objective Context Model. affect Risk Model affect Annotation Model Web Service Composition 45
46 DDDAS-based Crisis Management Youakim Badr, Frederique Biennier, and Samir Tata, IEEE Transaction on Services Computing, Vol4,
47 USE CASE SCENARIO Crisis Management Youakim Badr, Frederique Biennier, and Samir Tata, IEEE Transaction on Services Computing, Vol4,
48 Access Control Policies Youakim Badr, Frederique Biennier, and Samir Tata, IEEE Transaction on Services Computing, Vol4,
49 Concluding Remarks How to continuously adapt DDDAS environments to changes, occurring within/outside the DDDAS composition process and satisfying a wide range of security/trust constraints in dynamic environments Solution : Resilient SOA- DDDAS Architecture (DaaS) (Continuous integration of runtime and design time) 49
50 Back Up Slides
51 Continuous Behavior Analysis
52 User Cyber DNA
53 User Cyber DNA
54 User Cyber DNA
IaaS Federation. Contrail project. IaaS Federation! Objectives and Challenges! & SLA management in Federations 5/23/11
 Cloud Computing (IV) s and SPD Course 19-20/05/2011 Massimo Coppola IaaS! Objectives and Challenges! & management in s Adapted from two presentations! by Massimo Coppola (CNR) and Lorenzo Blasi (HP) Italy)!
Cloud Computing (IV) s and SPD Course 19-20/05/2011 Massimo Coppola IaaS! Objectives and Challenges! & management in s Adapted from two presentations! by Massimo Coppola (CNR) and Lorenzo Blasi (HP) Italy)!
How To Secure Cloud Computing
 Resilient Cloud Services By Hemayamini Kurra, Glynis Dsouza, Youssif Al Nasshif, Salim Hariri University of Arizona First Franco-American Workshop on Cybersecurity 18 th October, 2013 Presentation Outline
Resilient Cloud Services By Hemayamini Kurra, Glynis Dsouza, Youssif Al Nasshif, Salim Hariri University of Arizona First Franco-American Workshop on Cybersecurity 18 th October, 2013 Presentation Outline
Challenges of Security Risks in Service-Oriented Architectures
 UMR 5205 Challenges of Security Risks in Service-Oriented Architectures Youakim Badr 1, Frederique Biennier 1, Pascal Bou Nassar 3, Soumya Banerjee 2!! 1 LIRIS Lab, INSA-Lyon, France! 2 Agence Universitaire
UMR 5205 Challenges of Security Risks in Service-Oriented Architectures Youakim Badr 1, Frederique Biennier 1, Pascal Bou Nassar 3, Soumya Banerjee 2!! 1 LIRIS Lab, INSA-Lyon, France! 2 Agence Universitaire
Oracle SOA Suite: The Evaluation from 10g to 11g
 KATTA Durga Reddy TATA Consultancy Services. Oracle SOA Suite: The Evaluation from 10g to 11g Introduction Oracle SOA Suite is an essential middleware layer of Oracle Fusion Middleware. It provides a complete
KATTA Durga Reddy TATA Consultancy Services. Oracle SOA Suite: The Evaluation from 10g to 11g Introduction Oracle SOA Suite is an essential middleware layer of Oracle Fusion Middleware. It provides a complete
Risk, security, and legal analysis for migration to cloud. PART 2: Organising a secured cloud architecture
 Project acronym: Project name: Project code: NEBULA A novel vocational training programme on cloud computing skills 540226-LLP-1-2013-1-GR-LEONARDO-LMP Document Information Document ID name: Nebula_WP4_D4.3.1_Learning_Material_and_Content_2015_30_04
Project acronym: Project name: Project code: NEBULA A novel vocational training programme on cloud computing skills 540226-LLP-1-2013-1-GR-LEONARDO-LMP Document Information Document ID name: Nebula_WP4_D4.3.1_Learning_Material_and_Content_2015_30_04
NIST CYBERSECURITY FRAMEWORK COMPLIANCE WITH OBSERVEIT
 NIST CYBERSECURITY FRAMEWORK COMPLIANCE WITH OBSERVEIT OVERVIEW The National Institute of Standards of Technology Framework for Improving Critical Infrastructure Cybersecurity (The NIST Framework) is a
NIST CYBERSECURITY FRAMEWORK COMPLIANCE WITH OBSERVEIT OVERVIEW The National Institute of Standards of Technology Framework for Improving Critical Infrastructure Cybersecurity (The NIST Framework) is a
2011 Cyber Security and the Advanced Persistent Threat A Holistic View
 2011 Cyber and the Advanced Persistent Threat A Holistic View Thomas Varney Cybersecurity & Privacy BM Global Business Services 1 31/10/11 Agenda The Threat We Face A View to Addressing the Four Big Problem
2011 Cyber and the Advanced Persistent Threat A Holistic View Thomas Varney Cybersecurity & Privacy BM Global Business Services 1 31/10/11 Agenda The Threat We Face A View to Addressing the Four Big Problem
Augmented Search for Web Applications. New frontier in big log data analysis and application intelligence
 Augmented Search for Web Applications New frontier in big log data analysis and application intelligence Business white paper May 2015 Web applications are the most common business applications today.
Augmented Search for Web Applications New frontier in big log data analysis and application intelligence Business white paper May 2015 Web applications are the most common business applications today.
NIST s Guide to Secure Web Services
 NIST s Guide to Secure Web Services Presented by Gaspar Modelo-Howard and Ratsameetip Wita Secure and Dependable Web Services National Institute of Standards and Technology. Special Publication 800-95:
NIST s Guide to Secure Web Services Presented by Gaspar Modelo-Howard and Ratsameetip Wita Secure and Dependable Web Services National Institute of Standards and Technology. Special Publication 800-95:
White Paper: Enhancing Functionality and Security of Enterprise Data Holdings
 White Paper: Enhancing Functionality and Security of Enterprise Data Holdings Examining New Mission- Enabling Design Patterns Made Possible by the Cloudera- Intel Partnership Inside: Improving Return on
White Paper: Enhancing Functionality and Security of Enterprise Data Holdings Examining New Mission- Enabling Design Patterns Made Possible by the Cloudera- Intel Partnership Inside: Improving Return on
The Cisco Powered Network Cloud: An Exciting Managed Services Opportunity
 . White Paper The Cisco Powered Network Cloud: An Exciting Managed Services Opportunity The cloud computing phenomenon is generating a lot of interest worldwide because of its potential to offer services
. White Paper The Cisco Powered Network Cloud: An Exciting Managed Services Opportunity The cloud computing phenomenon is generating a lot of interest worldwide because of its potential to offer services
Report on the Dagstuhl Seminar Data Quality on the Web
 Report on the Dagstuhl Seminar Data Quality on the Web Michael Gertz M. Tamer Özsu Gunter Saake Kai-Uwe Sattler U of California at Davis, U.S.A. U of Waterloo, Canada U of Magdeburg, Germany TU Ilmenau,
Report on the Dagstuhl Seminar Data Quality on the Web Michael Gertz M. Tamer Özsu Gunter Saake Kai-Uwe Sattler U of California at Davis, U.S.A. U of Waterloo, Canada U of Magdeburg, Germany TU Ilmenau,
Internet of Things (IoT): A vision, architectural elements, and future directions
 SeoulTech UCS Lab 2014-2 st Internet of Things (IoT): A vision, architectural elements, and future directions 2014. 11. 18 Won Min Kang Email: wkaqhsk0@seoultech.ac.kr Table of contents Open challenges
SeoulTech UCS Lab 2014-2 st Internet of Things (IoT): A vision, architectural elements, and future directions 2014. 11. 18 Won Min Kang Email: wkaqhsk0@seoultech.ac.kr Table of contents Open challenges
Preface Introduction
 Preface Introduction Cloud computing is revolutionizing all aspects of technologies to provide scalability, flexibility and cost-effectiveness. It has become a challenge to ensure the security of cloud
Preface Introduction Cloud computing is revolutionizing all aspects of technologies to provide scalability, flexibility and cost-effectiveness. It has become a challenge to ensure the security of cloud
The Impact of PaaS on Business Transformation
 The Impact of PaaS on Business Transformation September 2014 Chris McCarthy Sr. Vice President Information Technology 1 Legacy Technology Silos Opportunities Business units Infrastructure Provisioning
The Impact of PaaS on Business Transformation September 2014 Chris McCarthy Sr. Vice President Information Technology 1 Legacy Technology Silos Opportunities Business units Infrastructure Provisioning
San Diego Supercomputer Center, UCSD. Institute for Digital Research and Education, UCLA
 Facilitate Parallel Computation Using Kepler Workflow System on Virtual Resources Jianwu Wang 1, Prakashan Korambath 2, Ilkay Altintas 1 1 San Diego Supercomputer Center, UCSD 2 Institute for Digital Research
Facilitate Parallel Computation Using Kepler Workflow System on Virtual Resources Jianwu Wang 1, Prakashan Korambath 2, Ilkay Altintas 1 1 San Diego Supercomputer Center, UCSD 2 Institute for Digital Research
Cyber Security. BDS PhantomWorks. Boeing Energy. Copyright 2011 Boeing. All rights reserved.
 Cyber Security Automation of energy systems provides attack surfaces that previously did not exist Cyber attacks have matured from teenage hackers to organized crime to nation states Centralized control
Cyber Security Automation of energy systems provides attack surfaces that previously did not exist Cyber attacks have matured from teenage hackers to organized crime to nation states Centralized control
Splunk Enterprise Log Management Role Supporting the ISO 27002 Framework EXECUTIVE BRIEF
 Splunk Enterprise Log Management Role Supporting the ISO 27002 Framework EXECUTIVE BRIEF Businesses around the world have adopted the information security standard ISO 27002 as part of their overall risk
Splunk Enterprise Log Management Role Supporting the ISO 27002 Framework EXECUTIVE BRIEF Businesses around the world have adopted the information security standard ISO 27002 as part of their overall risk
Patch and Vulnerability Management Program
 Patch and Vulnerability Management Program What is it? A security practice designed to proactively prevent the exploitation of IT vulnerabilities within an organization To reduce the time and money spent
Patch and Vulnerability Management Program What is it? A security practice designed to proactively prevent the exploitation of IT vulnerabilities within an organization To reduce the time and money spent
Current and Future Research into Network Security Prof. Madjid Merabti
 Current and Future Research into Network Security Prof. Madjid Merabti School of Computing & Mathematical Sciences Liverpool John Moores University UK Overview Introduction Secure component composition
Current and Future Research into Network Security Prof. Madjid Merabti School of Computing & Mathematical Sciences Liverpool John Moores University UK Overview Introduction Secure component composition
Plain English Guide To Common Criteria Requirements In The. Field Device Protection Profile Version 0.75
 Plain English Guide To Common Criteria Requirements In The Field Device Protection Profile Version 0.75 Prepared For: Process Control Security Requirements Forum (PCSRF) Prepared By: Digital Bond, Inc.
Plain English Guide To Common Criteria Requirements In The Field Device Protection Profile Version 0.75 Prepared For: Process Control Security Requirements Forum (PCSRF) Prepared By: Digital Bond, Inc.
LOGIIC Remote Access. Final Public Report. June 2015 1 LOGIIC - APPROVED FOR PUBLIC DISTRIBUTION
 LOGIIC Remote Access June 2015 Final Public Report Document Title LOGIIC Remote Monitoring Project Public Report Version Version 1.0 Primary Author A. McIntyre (SRI) Distribution Category LOGIIC Approved
LOGIIC Remote Access June 2015 Final Public Report Document Title LOGIIC Remote Monitoring Project Public Report Version Version 1.0 Primary Author A. McIntyre (SRI) Distribution Category LOGIIC Approved
Capacity Management PinkVERIFY
 CAP-11-G-001 General Criteria Does the tool use ITIL 2011 Edition process terms and align to ITIL 2011 Edition workflows and process integrations? CAP-11-G-002 Does the tool have security controls in place
CAP-11-G-001 General Criteria Does the tool use ITIL 2011 Edition process terms and align to ITIL 2011 Edition workflows and process integrations? CAP-11-G-002 Does the tool have security controls in place
Information Security. Rick Aldrich, JD, CISSP Booz Allen Hamilton Aldrich_Richard@bah.com
 Information Security Rick Aldrich, JD, CISSP Booz Allen Hamilton Aldrich_Richard@bah.com Overview (Fed Info Sys) From NIST SP 800-60, Vol 1, Guide for Mapping Types of Information Systems to Security Categories
Information Security Rick Aldrich, JD, CISSP Booz Allen Hamilton Aldrich_Richard@bah.com Overview (Fed Info Sys) From NIST SP 800-60, Vol 1, Guide for Mapping Types of Information Systems to Security Categories
WHITE PAPER. Enabling predictive analysis in service oriented BPM solutions.
 WHITE PAPER Enabling predictive analysis in service oriented BPM solutions. Summary Complex Event Processing (CEP) is a real time event analysis, correlation and processing mechanism that fits in seamlessly
WHITE PAPER Enabling predictive analysis in service oriented BPM solutions. Summary Complex Event Processing (CEP) is a real time event analysis, correlation and processing mechanism that fits in seamlessly
Consumption IT. Michael Shepherd Business Development Manager. Cisco Public Sector May 1 st 2014
 Consumption IT Michael Shepherd Business Development Manager Cisco Public Sector May 1 st 2014 Short Bio Cloud BDM in Public Sector (SLED + FED) Cisco for 14 + years Focused on cloud for 4 + years Awareness,
Consumption IT Michael Shepherd Business Development Manager Cisco Public Sector May 1 st 2014 Short Bio Cloud BDM in Public Sector (SLED + FED) Cisco for 14 + years Focused on cloud for 4 + years Awareness,
Seed4C: A Cloud Security Infrastructure validated on Grid 5000
 Seed4C: A Cloud Security Infrastructure validated on Grid 5000 E. Caron 1, A. Lefray 1, B. Marquet 2, and J. Rouzaud-Cornabas 1 1 Université de Lyon. LIP Laboratory. UMR CNRS - ENS Lyon - INRIA - UCBL
Seed4C: A Cloud Security Infrastructure validated on Grid 5000 E. Caron 1, A. Lefray 1, B. Marquet 2, and J. Rouzaud-Cornabas 1 1 Université de Lyon. LIP Laboratory. UMR CNRS - ENS Lyon - INRIA - UCBL
Development of High-Quality Secure Service-based Software Systems
 Development of High-Quality Secure Service-based Software Systems Stephen S. Yau Information Assurance Center, and School of Computing, Informatics, and Decision Sys. Eng. Arizona State University Tempe,
Development of High-Quality Secure Service-based Software Systems Stephen S. Yau Information Assurance Center, and School of Computing, Informatics, and Decision Sys. Eng. Arizona State University Tempe,
Security Challenges & Opportunities in Software Defined Networks (SDN)
 Security Challenges & Opportunities in Software Defined Networks (SDN) June 30 th, 2015 SEC2 2015 Premier atelier sur la sécurité dans les Clouds Nizar KHEIR Cyber Security Researcher Orange Labs Products
Security Challenges & Opportunities in Software Defined Networks (SDN) June 30 th, 2015 SEC2 2015 Premier atelier sur la sécurité dans les Clouds Nizar KHEIR Cyber Security Researcher Orange Labs Products
Security Analytics Topology
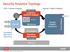 Security Analytics Topology CEP = Stream Analytics Hadoop = Batch Analytics Months to years LOGS PKTS Correlation with Live in Real Time Meta, logs, select payload Decoder Long-term, intensive analysis
Security Analytics Topology CEP = Stream Analytics Hadoop = Batch Analytics Months to years LOGS PKTS Correlation with Live in Real Time Meta, logs, select payload Decoder Long-term, intensive analysis
SPARKS Cybersecurity Technology and the NESCOR Failure Scenarios
 SPARKS Cybersecurity Technology and the NESCOR Failure Scenarios Lucie Langer and Paul Smith firstname.lastname@ait.ac.at AIT Austrian Institute of Technology ComForEn Workshop Monday 29 th September,
SPARKS Cybersecurity Technology and the NESCOR Failure Scenarios Lucie Langer and Paul Smith firstname.lastname@ait.ac.at AIT Austrian Institute of Technology ComForEn Workshop Monday 29 th September,
Cloud Resilient Architecture (CRA) -Design and Analysis. Hamid Alipour Salim Hariri Youssif-Al-Nashif
 Cloud Resilient Architecture (CRA) -Design and Analysis Glynis Dsouza Hamid Alipour Salim Hariri Youssif-Al-Nashif NSF Center for Autonomic Computing University of Arizona Mohamed Eltoweissy Pacific National
Cloud Resilient Architecture (CRA) -Design and Analysis Glynis Dsouza Hamid Alipour Salim Hariri Youssif-Al-Nashif NSF Center for Autonomic Computing University of Arizona Mohamed Eltoweissy Pacific National
How To Monitor Your Entire It Environment
 Preparing for FISMA 2.0 and Continuous Monitoring Requirements Symantec's Continuous Monitoring Solution White Paper: Preparing for FISMA 2.0 and Continuous Monitoring Requirements Contents Introduction............................................................................................
Preparing for FISMA 2.0 and Continuous Monitoring Requirements Symantec's Continuous Monitoring Solution White Paper: Preparing for FISMA 2.0 and Continuous Monitoring Requirements Contents Introduction............................................................................................
XpoLog Center Suite Log Management & Analysis platform
 XpoLog Center Suite Log Management & Analysis platform Summary: 1. End to End data management collects and indexes data in any format from any machine / device in the environment. 2. Logs Monitoring -
XpoLog Center Suite Log Management & Analysis platform Summary: 1. End to End data management collects and indexes data in any format from any machine / device in the environment. 2. Logs Monitoring -
CONTINUOUS DIAGNOSTICS BEGINS WITH REDSEAL
 CONTINUOUS DIAGNOSTICS BEGINS WITH REDSEAL WHAT IS CDM? The continuous stream of high profile cybersecurity breaches demonstrates the need to move beyond purely periodic, compliance-based approaches to
CONTINUOUS DIAGNOSTICS BEGINS WITH REDSEAL WHAT IS CDM? The continuous stream of high profile cybersecurity breaches demonstrates the need to move beyond purely periodic, compliance-based approaches to
NETWORK ACCESS CONTROL AND CLOUD SECURITY. Tran Song Dat Phuc SeoulTech 2015
 NETWORK ACCESS CONTROL AND CLOUD SECURITY Tran Song Dat Phuc SeoulTech 2015 Table of Contents Network Access Control (NAC) Network Access Enforcement Methods Extensible Authentication Protocol IEEE 802.1X
NETWORK ACCESS CONTROL AND CLOUD SECURITY Tran Song Dat Phuc SeoulTech 2015 Table of Contents Network Access Control (NAC) Network Access Enforcement Methods Extensible Authentication Protocol IEEE 802.1X
JOURNAL OF OBJECT TECHNOLOGY
 JOURNAL OF OBJECT TECHNOLOGY Online at www.jot.fm. Published by ETH Zurich, Chair of Software Engineering JOT, 2008 Vol. 7 No. 7, September-October 2008 Applications At Your Service Mahesh H. Dodani, IBM,
JOURNAL OF OBJECT TECHNOLOGY Online at www.jot.fm. Published by ETH Zurich, Chair of Software Engineering JOT, 2008 Vol. 7 No. 7, September-October 2008 Applications At Your Service Mahesh H. Dodani, IBM,
Cloud Federations in Contrail
 Cloud Federations in Contrail Emanuele Carlini 1,3, Massimo Coppola 1, Patrizio Dazzi 1, Laura Ricci 1,2, GiacomoRighetti 1,2 " 1 - CNR - ISTI, Pisa, Italy" 2 - University of Pisa, C.S. Dept" 3 - IMT Lucca,
Cloud Federations in Contrail Emanuele Carlini 1,3, Massimo Coppola 1, Patrizio Dazzi 1, Laura Ricci 1,2, GiacomoRighetti 1,2 " 1 - CNR - ISTI, Pisa, Italy" 2 - University of Pisa, C.S. Dept" 3 - IMT Lucca,
SERVICE ORIENTED ARCHITECTURE
 SERVICE ORIENTED ARCHITECTURE Introduction SOA provides an enterprise architecture that supports building connected enterprise applications to provide solutions to business problems. SOA facilitates the
SERVICE ORIENTED ARCHITECTURE Introduction SOA provides an enterprise architecture that supports building connected enterprise applications to provide solutions to business problems. SOA facilitates the
Augmented Search for IT Data Analytics. New frontier in big log data analysis and application intelligence
 Augmented Search for IT Data Analytics New frontier in big log data analysis and application intelligence Business white paper May 2015 IT data is a general name to log data, IT metrics, application data,
Augmented Search for IT Data Analytics New frontier in big log data analysis and application intelligence Business white paper May 2015 IT data is a general name to log data, IT metrics, application data,
VMware's Cloud Management Platform Simplifies and Automates Operations of Heterogeneous Environments and Hybrid Clouds
 VMware's Cloud Platform Simplifies and Automates Operations of Heterogeneous Environments and Hybrid Clouds Ekkarat Klinbubpa Senior Business Development Manager, VMware 2009 VMware Inc. All rights reserved
VMware's Cloud Platform Simplifies and Automates Operations of Heterogeneous Environments and Hybrid Clouds Ekkarat Klinbubpa Senior Business Development Manager, VMware 2009 VMware Inc. All rights reserved
PALANTIR CYBER An End-to-End Cyber Intelligence Platform for Analysis & Knowledge Management
 PALANTIR CYBER An End-to-End Cyber Intelligence Platform for Analysis & Knowledge Management INTRODUCTION Traditional perimeter defense solutions fail against sophisticated adversaries who target their
PALANTIR CYBER An End-to-End Cyber Intelligence Platform for Analysis & Knowledge Management INTRODUCTION Traditional perimeter defense solutions fail against sophisticated adversaries who target their
IBM 000-281 EXAM QUESTIONS & ANSWERS
 IBM 000-281 EXAM QUESTIONS & ANSWERS Number: 000-281 Passing Score: 800 Time Limit: 120 min File Version: 58.8 http://www.gratisexam.com/ IBM 000-281 EXAM QUESTIONS & ANSWERS Exam Name: Foundations of
IBM 000-281 EXAM QUESTIONS & ANSWERS Number: 000-281 Passing Score: 800 Time Limit: 120 min File Version: 58.8 http://www.gratisexam.com/ IBM 000-281 EXAM QUESTIONS & ANSWERS Exam Name: Foundations of
MOBILE ARCHITECTURE FOR DYNAMIC GENERATION AND SCALABLE DISTRIBUTION OF SENSOR-BASED APPLICATIONS
 MOBILE ARCHITECTURE FOR DYNAMIC GENERATION AND SCALABLE DISTRIBUTION OF SENSOR-BASED APPLICATIONS Marco Picone, Marco Muro, Vincenzo Micelli, Michele Amoretti, Francesco Zanichelli Distributed Systems
MOBILE ARCHITECTURE FOR DYNAMIC GENERATION AND SCALABLE DISTRIBUTION OF SENSOR-BASED APPLICATIONS Marco Picone, Marco Muro, Vincenzo Micelli, Michele Amoretti, Francesco Zanichelli Distributed Systems
Good metrics aggregate both objective and quantitative
 Editors: John Steven, jsteven@cigital.com Gunnar Peterson, gunnar@arctecgroup.net Introduction to Identity Management Risk Metrics GUNNAR PETERSON Arctec Group Good metrics aggregate both objective and
Editors: John Steven, jsteven@cigital.com Gunnar Peterson, gunnar@arctecgroup.net Introduction to Identity Management Risk Metrics GUNNAR PETERSON Arctec Group Good metrics aggregate both objective and
Information Services for Smart Grids
 Smart Grid and Renewable Energy, 2009, 8 12 Published Online September 2009 (http://www.scirp.org/journal/sgre/). ABSTRACT Interconnected and integrated electrical power systems, by their very dynamic
Smart Grid and Renewable Energy, 2009, 8 12 Published Online September 2009 (http://www.scirp.org/journal/sgre/). ABSTRACT Interconnected and integrated electrical power systems, by their very dynamic
Oracle SOA Suite Then and Now:
 Oracle SOA Suite Then and Now: The Evolution from 10g to 11g Shane Goss Impac Services Agenda SOA Suite 11g New Features Highlight new features of SOA 11g Some products have added features and functionality
Oracle SOA Suite Then and Now: The Evolution from 10g to 11g Shane Goss Impac Services Agenda SOA Suite 11g New Features Highlight new features of SOA 11g Some products have added features and functionality
Gaming as a Service. Prof. Victor C.M. Leung. The University of British Columbia, Canada www.ece.ubc.ca/~vleung
 Gaming as a Service Prof. Victor C.M. Leung The University of British Columbia, Canada www.ece.ubc.ca/~vleung International Conference on Computing, Networking and Communications 4 February, 2014 Outline
Gaming as a Service Prof. Victor C.M. Leung The University of British Columbia, Canada www.ece.ubc.ca/~vleung International Conference on Computing, Networking and Communications 4 February, 2014 Outline
Critical Controls for Cyber Security. www.infogistic.com
 Critical Controls for Cyber Security www.infogistic.com Understanding Risk Asset Threat Vulnerability Managing Risks Systematic Approach for Managing Risks Identify, characterize threats Assess the vulnerability
Critical Controls for Cyber Security www.infogistic.com Understanding Risk Asset Threat Vulnerability Managing Risks Systematic Approach for Managing Risks Identify, characterize threats Assess the vulnerability
Dynamic Trust Management for the Internet of Things Applications
 Dynamic Trust Management for the Internet of Things Applications Fenye Bao and Ing-Ray Chen Department of Computer Science, Virginia Tech Self-IoT 2012 1 Sept. 17, 2012, San Jose, CA, USA Contents Introduction
Dynamic Trust Management for the Internet of Things Applications Fenye Bao and Ing-Ray Chen Department of Computer Science, Virginia Tech Self-IoT 2012 1 Sept. 17, 2012, San Jose, CA, USA Contents Introduction
The Way to SOA Concept, Architectural Components and Organization
 The Way to SOA Concept, Architectural Components and Organization Eric Scholz Director Product Management Software AG Seite 1 Goals of business and IT Business Goals Increase business agility Support new
The Way to SOA Concept, Architectural Components and Organization Eric Scholz Director Product Management Software AG Seite 1 Goals of business and IT Business Goals Increase business agility Support new
Building Platform as a Service for Scientific Applications
 Building Platform as a Service for Scientific Applications Moustafa AbdelBaky moustafa@cac.rutgers.edu Rutgers Discovery Informa=cs Ins=tute (RDI 2 ) The NSF Cloud and Autonomic Compu=ng Center Department
Building Platform as a Service for Scientific Applications Moustafa AbdelBaky moustafa@cac.rutgers.edu Rutgers Discovery Informa=cs Ins=tute (RDI 2 ) The NSF Cloud and Autonomic Compu=ng Center Department
Framework for Improving Critical Infrastructure Cybersecurity
 Framework for Improving Critical Infrastructure Cybersecurity 18 November 2015 grance@nist.gov cyberframework@nist.gov National Institute of Standards and Technology About NIST NIST s mission is to develop
Framework for Improving Critical Infrastructure Cybersecurity 18 November 2015 grance@nist.gov cyberframework@nist.gov National Institute of Standards and Technology About NIST NIST s mission is to develop
SLA BASED SERVICE BROKERING IN INTERCLOUD ENVIRONMENTS
 SLA BASED SERVICE BROKERING IN INTERCLOUD ENVIRONMENTS Foued Jrad, Jie Tao and Achim Streit Steinbuch Centre for Computing, Karlsruhe Institute of Technology, Karlsruhe, Germany {foued.jrad, jie.tao, achim.streit}@kit.edu
SLA BASED SERVICE BROKERING IN INTERCLOUD ENVIRONMENTS Foued Jrad, Jie Tao and Achim Streit Steinbuch Centre for Computing, Karlsruhe Institute of Technology, Karlsruhe, Germany {foued.jrad, jie.tao, achim.streit}@kit.edu
EFFECTIVE VULNERABILITY SCANNING DEMYSTIFYING SCANNER OUTPUT DATA
 EFFECTIVE VULNERABILITY SCANNING DEMYSTIFYING SCANNER OUTPUT DATA Paul R. Lazarr, CISSP, CISA, CIPP, CRISK Sr. Managing Consultant, IBM Cybersecurity and Biometrics January 21, 2016 PERSONAL BACKGROUND
EFFECTIVE VULNERABILITY SCANNING DEMYSTIFYING SCANNER OUTPUT DATA Paul R. Lazarr, CISSP, CISA, CIPP, CRISK Sr. Managing Consultant, IBM Cybersecurity and Biometrics January 21, 2016 PERSONAL BACKGROUND
Cloud and Regulations: A match made in heaven, or the worst blind date ever?
 Cloud and Regulations: A match made in heaven, or the worst blind date ever? Vinod S Chavan Director Industry Cloud Solutions, IBM Cloud October 28, 2015 Customers are faced with challenge of balancing
Cloud and Regulations: A match made in heaven, or the worst blind date ever? Vinod S Chavan Director Industry Cloud Solutions, IBM Cloud October 28, 2015 Customers are faced with challenge of balancing
Service Oriented Networks Security. David Brossard, M.Eng, SCEA Senior Security Researcher, BT Innovate Globecom 2008
 Service Oriented Networks Security David Brossard, M.Eng, SCEA Senior Security Researcher, BT Innovate Globecom 2008 While empowering new business models, SON leads to a proliferation of application networks
Service Oriented Networks Security David Brossard, M.Eng, SCEA Senior Security Researcher, BT Innovate Globecom 2008 While empowering new business models, SON leads to a proliferation of application networks
journey to a hybrid cloud
 journey to a hybrid cloud Virtualization and Automation VI015SN journey to a hybrid cloud Jim Sweeney, CTO GTSI about the speaker Jim Sweeney GTSI, Chief Technology Officer 35 years of engineering experience
journey to a hybrid cloud Virtualization and Automation VI015SN journey to a hybrid cloud Jim Sweeney, CTO GTSI about the speaker Jim Sweeney GTSI, Chief Technology Officer 35 years of engineering experience
3rd International Symposium on Big Data and Cloud Computing Challenges (ISBCC-2016) March 10-11, 2016 VIT University, Chennai, India
 3rd International Symposium on Big Data and Cloud Computing Challenges (ISBCC-2016) March 10-11, 2016 VIT University, Chennai, India Call for Papers Cloud computing has emerged as a de facto computing
3rd International Symposium on Big Data and Cloud Computing Challenges (ISBCC-2016) March 10-11, 2016 VIT University, Chennai, India Call for Papers Cloud computing has emerged as a de facto computing
Establishing a business performance management ecosystem.
 IBM business performance management solutions White paper Establishing a business performance management ecosystem. IBM Software Group March 2004 Page 2 Contents 2 Executive summary 3 Business performance
IBM business performance management solutions White paper Establishing a business performance management ecosystem. IBM Software Group March 2004 Page 2 Contents 2 Executive summary 3 Business performance
Managed Virtualized Platforms: From Multicore Nodes to Distributed Cloud Infrastructures
 Managed Virtualized Platforms: From Multicore Nodes to Distributed Cloud Infrastructures Ada Gavrilovska Karsten Schwan, Mukil Kesavan Sanjay Kumar, Ripal Nathuji, Adit Ranadive Center for Experimental
Managed Virtualized Platforms: From Multicore Nodes to Distributed Cloud Infrastructures Ada Gavrilovska Karsten Schwan, Mukil Kesavan Sanjay Kumar, Ripal Nathuji, Adit Ranadive Center for Experimental
Service-Oriented Architecture and Software Engineering
 -Oriented Architecture and Software Engineering T-86.5165 Seminar on Enterprise Information Systems (2008) 1.4.2008 Characteristics of SOA The software resources in a SOA are represented as services based
-Oriented Architecture and Software Engineering T-86.5165 Seminar on Enterprise Information Systems (2008) 1.4.2008 Characteristics of SOA The software resources in a SOA are represented as services based
IEEE International Conference on Computing, Analytics and Security Trends CAST-2016 (19 21 December, 2016) Call for Paper
 IEEE International Conference on Computing, Analytics and Security Trends CAST-2016 (19 21 December, 2016) Call for Paper CAST-2015 provides an opportunity for researchers, academicians, scientists and
IEEE International Conference on Computing, Analytics and Security Trends CAST-2016 (19 21 December, 2016) Call for Paper CAST-2015 provides an opportunity for researchers, academicians, scientists and
The Storage Capacity Design Dilemma
 The Storage Capacity Design Dilemma an ITIL approach LeRoy Budnik Knowledge Transfer SNIA Legal Notice The material contained in this tutorial is copyrighted by the SNIA and portions are subject to other
The Storage Capacity Design Dilemma an ITIL approach LeRoy Budnik Knowledge Transfer SNIA Legal Notice The material contained in this tutorial is copyrighted by the SNIA and portions are subject to other
Brown County Information Technology Aberdeen, SD. Request for Proposals For Document Management Solution. Proposals Deadline: Submit proposals to:
 Brown County Information Technology Aberdeen, SD Request for Proposals For Document Management Solution Proposals Deadline: 9:10am, January 12, 2016 Submit proposals to: Brown County Auditor 25 Market
Brown County Information Technology Aberdeen, SD Request for Proposals For Document Management Solution Proposals Deadline: 9:10am, January 12, 2016 Submit proposals to: Brown County Auditor 25 Market
Creating a Strong Security Infrastructure for Exposing JBoss Services
 Creating a Strong Security Infrastructure for Exposing JBoss Services JBoss Enterprise SOA Platform Service Clients Service Gateway Enterprise Services Blake Dournaee, Product Management, Intel SOA Products
Creating a Strong Security Infrastructure for Exposing JBoss Services JBoss Enterprise SOA Platform Service Clients Service Gateway Enterprise Services Blake Dournaee, Product Management, Intel SOA Products
Cautela Labs Cloud Agile. Secured. Threat Management Security Solutions at Work
 Cautela Labs Cloud Agile. Secured. Threat Management Security Solutions at Work Security concerns and dangers come both from internal means as well as external. In order to enhance your security posture
Cautela Labs Cloud Agile. Secured. Threat Management Security Solutions at Work Security concerns and dangers come both from internal means as well as external. In order to enhance your security posture
Developing SOA solutions using IBM SOA Foundation
 Developing SOA solutions using IBM SOA Foundation Course materials may not be reproduced in whole or in part without the prior written permission of IBM. 4.0.3 4.0.3 Unit objectives After completing this
Developing SOA solutions using IBM SOA Foundation Course materials may not be reproduced in whole or in part without the prior written permission of IBM. 4.0.3 4.0.3 Unit objectives After completing this
Oracle Maps Cloud Service Enterprise Hosting and Delivery Policies Effective Date: October 1, 2015 Version 1.0
 Oracle Maps Cloud Service Enterprise Hosting and Delivery Policies Effective Date: October 1, 2015 Version 1.0 Unless otherwise stated, these Oracle Maps Cloud Service Enterprise Hosting and Delivery Policies
Oracle Maps Cloud Service Enterprise Hosting and Delivery Policies Effective Date: October 1, 2015 Version 1.0 Unless otherwise stated, these Oracle Maps Cloud Service Enterprise Hosting and Delivery Policies
Augmented Search for Software Testing
 Augmented Search for Software Testing For Testers, Developers, and QA Managers New frontier in big log data analysis and application intelligence Business white paper May 2015 During software testing cycles,
Augmented Search for Software Testing For Testers, Developers, and QA Managers New frontier in big log data analysis and application intelligence Business white paper May 2015 During software testing cycles,
A Strawman Model. NIST Cloud Computing Reference Architecture and Taxonomy Working Group. January 3, 2011
 A Strawman Model NIST Cloud Computing Reference Architecture and Taxonomy Working Group January 3, 2011 Objective Our objective is to define a neutral architecture consistent with NIST definition of cloud
A Strawman Model NIST Cloud Computing Reference Architecture and Taxonomy Working Group January 3, 2011 Objective Our objective is to define a neutral architecture consistent with NIST definition of cloud
Italy. EY s Global Information Security Survey 2013
 Italy EY s Global Information Security Survey 2013 EY s Global Information Security Survey 2013 This year s survey our 16th edition captures the responses of 1,909 C-suite and senior level IT and information
Italy EY s Global Information Security Survey 2013 EY s Global Information Security Survey 2013 This year s survey our 16th edition captures the responses of 1,909 C-suite and senior level IT and information
INTRUSION DETECTION ON CLOUD APPLICATIONS
 Available Online at www.ijcsmc.com International Journal of Computer Science and Mobile Computing A Monthly Journal of Computer Science and Information Technology IJCSMC, Vol. 2, Issue. 9, September 2013,
Available Online at www.ijcsmc.com International Journal of Computer Science and Mobile Computing A Monthly Journal of Computer Science and Information Technology IJCSMC, Vol. 2, Issue. 9, September 2013,
EL Program: Smart Manufacturing Systems Design and Analysis
 EL Program: Smart Manufacturing Systems Design and Analysis Program Manager: Dr. Sudarsan Rachuri Associate Program Manager: K C Morris Strategic Goal: Smart Manufacturing, Construction, and Cyber-Physical
EL Program: Smart Manufacturing Systems Design and Analysis Program Manager: Dr. Sudarsan Rachuri Associate Program Manager: K C Morris Strategic Goal: Smart Manufacturing, Construction, and Cyber-Physical
CAREER TRACKS PHASE 1 UCSD Information Technology Family Function and Job Function Summary
 UCSD Applications Programming Involved in the development of server / OS / desktop / mobile applications and services including researching, designing, developing specifications for designing, writing,
UCSD Applications Programming Involved in the development of server / OS / desktop / mobile applications and services including researching, designing, developing specifications for designing, writing,
How To Manage Cloud Management
 WHITE PAPER Five Steps to Successful Integrated Cloud Management Sponsored by: HP Mary Johnston Turner May 2011 Robert P. Mahowald IDC OPINION Global Headquarters: 5 Speen Street Framingham, MA 01701 USA
WHITE PAPER Five Steps to Successful Integrated Cloud Management Sponsored by: HP Mary Johnston Turner May 2011 Robert P. Mahowald IDC OPINION Global Headquarters: 5 Speen Street Framingham, MA 01701 USA
Why Use OPTIMIS? Build and Run Services in the Most Suitable Cloud Venues. October 2012
 Why Use OPTIMIS? Build and Run Services in the Most Suitable Cloud Venues October 2012 Authors: Csilla Zsigri (451 Research), Ana Juan Ferrer and Oliver Barreto (Atos), Raül Sirvent and Jordi Guitart (BSC),
Why Use OPTIMIS? Build and Run Services in the Most Suitable Cloud Venues October 2012 Authors: Csilla Zsigri (451 Research), Ana Juan Ferrer and Oliver Barreto (Atos), Raül Sirvent and Jordi Guitart (BSC),
Vulnerability Management
 Vulnerability Management Buyer s Guide Buyer s Guide 01 Introduction 02 Key Components 03 Other Considerations About Rapid7 01 INTRODUCTION Exploiting weaknesses in browsers, operating systems and other
Vulnerability Management Buyer s Guide Buyer s Guide 01 Introduction 02 Key Components 03 Other Considerations About Rapid7 01 INTRODUCTION Exploiting weaknesses in browsers, operating systems and other
Instilling Confidence in Security and Risk Operations with Behavioral Analytics and Contextualization
 WHITEPAPER Instilling Confidence in Security and Risk Operations with Behavioral Analytics and Contextualization Understanding Why Automated Machine Learning Behavioral Analytics with Contextualization
WHITEPAPER Instilling Confidence in Security and Risk Operations with Behavioral Analytics and Contextualization Understanding Why Automated Machine Learning Behavioral Analytics with Contextualization
Federal CIO: Cloud Selection Toolkit. Georgetown University: Chris Radich Dana Christiansen Doyle Zhang India Donald
 Federal CIO: Cloud Selection Toolkit Georgetown University: Chris Radich Dana Christiansen Doyle Zhang India Donald Agenda Project Introduction Agency Cloud Challenges Toolkit Solution Overview Step 1:
Federal CIO: Cloud Selection Toolkit Georgetown University: Chris Radich Dana Christiansen Doyle Zhang India Donald Agenda Project Introduction Agency Cloud Challenges Toolkit Solution Overview Step 1:
Why Use OPTIMIS? Build and Run Services in the Most Suitable Cloud Venues. May 2013
 Why Use OPTIMIS? Build and Run Services in the Most Suitable Cloud Venues May 2013 Authors: Csilla Zsigri (451 Research), Ana Juan Ferrer and Oliver Barreto (Atos), Raül Sirvent and Jordi Guitart (BSC),
Why Use OPTIMIS? Build and Run Services in the Most Suitable Cloud Venues May 2013 Authors: Csilla Zsigri (451 Research), Ana Juan Ferrer and Oliver Barreto (Atos), Raül Sirvent and Jordi Guitart (BSC),
Network Virtualization
 . White Paper Network Services Virtualization What Is Network Virtualization? Business and IT leaders require a more responsive IT infrastructure that can help accelerate business initiatives and remove
. White Paper Network Services Virtualization What Is Network Virtualization? Business and IT leaders require a more responsive IT infrastructure that can help accelerate business initiatives and remove
International Journal of Computer & Organization Trends Volume21 Number1 June 2015 A Study on Load Balancing in Cloud Computing
 A Study on Load Balancing in Cloud Computing * Parveen Kumar * Er.Mandeep Kaur Guru kashi University,Talwandi Sabo Guru kashi University,Talwandi Sabo Abstract: Load Balancing is a computer networking
A Study on Load Balancing in Cloud Computing * Parveen Kumar * Er.Mandeep Kaur Guru kashi University,Talwandi Sabo Guru kashi University,Talwandi Sabo Abstract: Load Balancing is a computer networking
Rackspace Cloud Databases and Container-based Virtualization
 Rackspace Cloud Databases and Container-based Virtualization August 2012 J.R. Arredondo @jrarredondo Page 1 of 6 INTRODUCTION When Rackspace set out to build the Cloud Databases product, we asked many
Rackspace Cloud Databases and Container-based Virtualization August 2012 J.R. Arredondo @jrarredondo Page 1 of 6 INTRODUCTION When Rackspace set out to build the Cloud Databases product, we asked many
Thales Communications Perspectives to the Future Internet 2 nd June 2010 - Luxembourg
 Thales Communications Perspectives to the Future Internet 2 nd June 2010 - Luxembourg Challenges of Future Internet Internet as a starting point Was defined for asynchronous services (web pages, file transfer
Thales Communications Perspectives to the Future Internet 2 nd June 2010 - Luxembourg Challenges of Future Internet Internet as a starting point Was defined for asynchronous services (web pages, file transfer
Air Force SOA Enterprise Service Bus Study Using Business Process Management Workflow Orchestration for C4I Systems Integration
 Air Force SOA Enterprise Service Bus Study Using Business Process Management Workflow Orchestration for C4I s Integration Dr. Timothy D. Kehoe, Irene Chang, Dave Czulada, Howard Kong, Dr. Dino Konstantopoulos
Air Force SOA Enterprise Service Bus Study Using Business Process Management Workflow Orchestration for C4I s Integration Dr. Timothy D. Kehoe, Irene Chang, Dave Czulada, Howard Kong, Dr. Dino Konstantopoulos
Proximity Marketing Privacy Considerations
 Proximity Marketing Privacy Considerations Proximity Marketing Commercial in confidence HOP Commercial Ubiquitous in confidence S.L. 2015 www.hopu.eu HOP Ubiquitous Page S.L. 1 2015 Dr. Antonio J. Jara
Proximity Marketing Privacy Considerations Proximity Marketing Commercial in confidence HOP Commercial Ubiquitous in confidence S.L. 2015 www.hopu.eu HOP Ubiquitous Page S.L. 1 2015 Dr. Antonio J. Jara
ORACLE HYPERION DATA RELATIONSHIP MANAGEMENT
 Oracle Fusion editions of Oracle's Hyperion performance management products are currently available only on Microsoft Windows server platforms. The following is intended to outline our general product
Oracle Fusion editions of Oracle's Hyperion performance management products are currently available only on Microsoft Windows server platforms. The following is intended to outline our general product
Beyond Provisioning. Ongoing operations of an efficient cloud environment SOLUTION WHITE PAPER
 Beyond Provisioning Ongoing operations of an efficient cloud environment SOLUTION WHITE PAPER Table of Contents EXECUTIVE SUMMARY............................................... 1 THE ROLE OF OPERATIONS
Beyond Provisioning Ongoing operations of an efficient cloud environment SOLUTION WHITE PAPER Table of Contents EXECUTIVE SUMMARY............................................... 1 THE ROLE OF OPERATIONS
Contents. 1010 Huntcliff, Suite 1350, Atlanta, Georgia, 30350, USA http://www.nevatech.com
 Sentinet Overview Contents Overview... 3 Architecture... 3 Technology Stack... 4 Features Summary... 6 Repository... 6 Runtime Management... 6 Services Virtualization and Mediation... 9 Communication and
Sentinet Overview Contents Overview... 3 Architecture... 3 Technology Stack... 4 Features Summary... 6 Repository... 6 Runtime Management... 6 Services Virtualization and Mediation... 9 Communication and
Ashok Kumar Gonela MTech Department of CSE Miracle Educational Group Of Institutions Bhogapuram.
 Protection of Vulnerable Virtual machines from being compromised as zombies during DDoS attacks using a multi-phase distributed vulnerability detection & counter-attack framework Ashok Kumar Gonela MTech
Protection of Vulnerable Virtual machines from being compromised as zombies during DDoS attacks using a multi-phase distributed vulnerability detection & counter-attack framework Ashok Kumar Gonela MTech
A Broker Based Trust Model for Cloud Computing Environment
 A Broker Based Trust Model for Cloud Computing Environment Chaitali Uikey 1, Dr. D. S. Bhilare 2 1 School of Computer Science & IT, DAVV, Indore, MP. India 2 Computer Center, DAVV, Indore, MP. India Abstract
A Broker Based Trust Model for Cloud Computing Environment Chaitali Uikey 1, Dr. D. S. Bhilare 2 1 School of Computer Science & IT, DAVV, Indore, MP. India 2 Computer Center, DAVV, Indore, MP. India Abstract
VMware Virtualization and Cloud Management Overview. 2010 VMware Inc. All rights reserved
 VMware Virtualization and Cloud Management Overview 2010 VMware Inc. All rights reserved Automating Operations Management Why? What? How? Why is Operations Management different in the virtual world? What
VMware Virtualization and Cloud Management Overview 2010 VMware Inc. All rights reserved Automating Operations Management Why? What? How? Why is Operations Management different in the virtual world? What
Integration using IBM Solutions
 With special reference to integration with SAP XI Email: keithprabhu@hotmail.com Table of contents Integration using IBM Solutions Executive Summary...3 1. Introduction...4 2. IBM Business Integration
With special reference to integration with SAP XI Email: keithprabhu@hotmail.com Table of contents Integration using IBM Solutions Executive Summary...3 1. Introduction...4 2. IBM Business Integration
Resource Provisioning in Clouds via Non-Functional Requirements
 Resource Provisioning in Clouds via Non-Functional Requirements By Diana Carolina Barreto Arias Under the supervision of Professor Rajkumar Buyya and Dr. Rodrigo N. Calheiros A minor project thesis submitted
Resource Provisioning in Clouds via Non-Functional Requirements By Diana Carolina Barreto Arias Under the supervision of Professor Rajkumar Buyya and Dr. Rodrigo N. Calheiros A minor project thesis submitted
Data Mining Governance for Service Oriented Architecture
 Data Mining Governance for Service Oriented Architecture Ali Beklen Software Group IBM Turkey Istanbul, TURKEY alibek@tr.ibm.com Turgay Tugay Bilgin Dept. of Computer Engineering Maltepe University Istanbul,
Data Mining Governance for Service Oriented Architecture Ali Beklen Software Group IBM Turkey Istanbul, TURKEY alibek@tr.ibm.com Turgay Tugay Bilgin Dept. of Computer Engineering Maltepe University Istanbul,
Charith Pereral, Arkady Zaslavsky, Peter Christen, Ali Salehi and Dimitrios Georgakopoulos (IEEE 2012) Presented By- Anusha Sekar
 Charith Pereral, Arkady Zaslavsky, Peter Christen, Ali Salehi and Dimitrios Georgakopoulos (IEEE 2012) Presented By- Anusha Sekar Introduction Terms and Concepts Mobile Sensors Global Sensor Networks DAM4GSN
Charith Pereral, Arkady Zaslavsky, Peter Christen, Ali Salehi and Dimitrios Georgakopoulos (IEEE 2012) Presented By- Anusha Sekar Introduction Terms and Concepts Mobile Sensors Global Sensor Networks DAM4GSN
The DEMONS Integrated Access Control Model for Collaborative Network Monitoring
 The DEMONS Integrated Access Control Model for Collaborative Network Monitoring Eugenia I. Papagiannakopoulou Maria N. Koukovini Georgios V. Lioudakis Dimitra I. Kaklamani Iakovos S. Venieris The 4 th
The DEMONS Integrated Access Control Model for Collaborative Network Monitoring Eugenia I. Papagiannakopoulou Maria N. Koukovini Georgios V. Lioudakis Dimitra I. Kaklamani Iakovos S. Venieris The 4 th
BMC Client Management - SCAP Implementation Statement. Version 12.0
 BMC Client Management - SCAP Implementation Statement Version 12.0 BMC Client Management - SCAP Implementation Statement TOC 3 Contents SCAP Implementation Statement... 4 4 BMC Client Management - SCAP
BMC Client Management - SCAP Implementation Statement Version 12.0 BMC Client Management - SCAP Implementation Statement TOC 3 Contents SCAP Implementation Statement... 4 4 BMC Client Management - SCAP
