Acommonvericationproblemforhardwaredesignsistodetermineifevery
|
|
|
- Amberly Robertson
- 8 years ago
- Views:
Transcription
1 OnCombiningFormalandInformalVerication JunYuan? bolicmethodsforthevericationofinvariants.themotivationistwo-fold. conjunctionwithtraditionalsimulationresultsinbetter\coverage"relativetothecomputationalresourcesused.additionally,evenondesigns First,therearedesignswhicharetoocomplextobeformallyveried Abstract.Weproposealgorithmswhichcombinesimulationwithsym- usingsymbolicmethods;howeverbytheuseofsymbolictechniquesin JianShen??JacobAbraham??AdnanAziz?? 1Introduction Inthispaperwewillbeconcernedwiththeproblemofdesignverication;specically,theproblemofinvariantcheckingovergate-leveldesigns.Traditionally, designshavebeenveriedbyextensivesimulation.whileoeringthebenetsof designs,thefractionofthedesignspacewhichcanbecoveredinthismethodo- passedextensivesimulation,butwerestillfoundtocontainbugs[4].thishasled simplicityandscalability,simulationoersnoguaranteesofcorrectness;forlarge simulation. whichcanbesymbolicallyveried,theuseofahybridmethodologyoftendetectsthepresenceofbugsfasterthaneitherformalvericationor totheproposalof\formalmethods"fordesignverication;theadjectiveformal logybecomesvanishinglysmall.indeed,therearemanyexamplesofdesignsthat structures"suchasbinarydecisiondiagrams(bdds)toecientlyrepresentand referstotheunambiguousspecicationofthesystemandthepropertiesbeing manipulatethestatespacesofdesigns[1].theprimarylimitationofbddbased cessfullyverifyalargenumberofcomplexdesignsistheuseof\symbolicdata checked,togetherwiththevalidationstepgeneratingamathematicallyrigorous approachestoinvariantcheckingisthatformanydesigns,thebddsconstructed wellonspecicclassesofdesigns.onemethodwhichhasbeenusedtosuc- proofofcorrectness. inthecourseofvericationcangrowextremelylarge,resultinginspace-outsor tured,andthiscanbeexploitedtodeviseheuristicprocedureswhichperform high;pspace-completetobeprecise.inpractise,manydesignsarewellstruc- severeperformancedegradationduetopaging[12]. ndingbugsinthemasearlyaspossible.ashenzingerhaspointedout,\falsi- Facedwiththetwindilemmasofdiminishedcoveragethroughsimulationand Practicingveriersarelessconcernedwithformallyverifyingdesignsthan
2 asquicklyaspossible. certicateofcorrectnessiftheinvariantpasses,oracounterexampleifitfails. bestressedthatneithermethodiscomplete,i.e.,guaranteedtoprovideaformal askhowbesttocombinesymbolicmethodswithsimulation,soastondbugs theinabilityofsymbolicmethodstoformallyverifylargedesigns,itisnaturalto However,allreportedviolationsoftheinvariantaretruebugs. performsapartialtraversalofthestatespace.ateachstep,symbolictechniques betheprogramcounterandstatusbitsinamicro-processor.theprocedure designatesasubsetofthelatchesasbeing\interesting";thesecould,forexample, Inthispaperweprovidetwoanswerstotheproblemposedabove.Itisto wealsodescribeanextensionthatvisitsallcontrolleredges.heuristically,the areusedtocomputethefullsetofcontrolstatesreachablefromthecurrentset; controlportionofthedesign,whilebeingmuchsmallerthanthedatapath,isthe mainsourceofdesignerrors.saturatedsimulationattemptstoexploreasmuch ofthecontrolstatespace,thusincreasingthelikelihoodofndingbugs. Werstdevelopthemethodofsaturatedsimulation,whereinthedesigner theentirestatespace.additionally,fastbddroutinesexistforgeneratingand coupledwiththefactthatthesetofcontrolstatesistypicallymuchsmallerthan manipulatingrepresentativeelementsofequivalenceclasses[8]. tocomputethesymbolicimageofasinglestateevenforverylargedesigns, Theeciencyofthisapproachcomesfromtheobservationthatitisfeasible somebngrowslargerinsizethana(user-specied)thresholdvalue.cyclesimulationisperformedfromaninitialstate;simulationishaltedifastatewhichlielysis[15].startingfromb,thecomplementoftheinvariant,successivepreimagesb;b1;b2;:::arecomputedsymbolically.thisisdonetillthebddfor Bn,sinceeverystateinBncanreachastateinB.Wedescribegreedysearch strategiesforndingpathstobnfromaninitialstatewhichusehammingdistanceasametrictobeminimized.theprimarybenetofretrogradeanalysisis thattheset[ibiistypicallymuchlarger(inthesenseofcardinality)thanb; Wethendescribeanorthogonalapproachreferredtoasretrogradeana- hence,inaheuristicsense,bnoersamuchlarger\target"forsimulation. givenabove. resultsunderlinetheeectivenessthatissuggestedbytheheuristicarguments rogradeanalysisarenoveltothispaper.wehavebeeninuencedbyanumberof relatedworks.thompson's[15]workonretrogradeanalysisprovidedtheinitial impetus.additionally,wewereinuencedbythedramaticimprovementsmade tocyclesimulationbytheuseofbddsbyasharandmalik[1],andmcgeeret TheseroutineshavebeencodedontopofthetoolVIS[2].Ourexperimental alargenumberofstates.thisisdistinctfromourapproach,whereinasubsetis setsencounteredduringreachabilityanalysiswhichhavesmallbddsbutcontain memoryavailableonthemachine.ravietal.[13]attempttopicksubsetsofstate al.[9],whomadecleartheimportanceofmakingmaximumuseofthephysical Tothebestofourknowledge,theprinciplesofsaturatedsimulationandret- chosenwhichattemptstomaximizethenumberofdistinctcontrollerstates.cho etal.[5]picknetstoabstractintoprimaryinputs,consequentlyobtainingsuper-
3 setsofthesetofreachablestates.theworkofhoetal.[6]andhoskoteetal.[7] oncreatingsimulationvectorswhichexcitealargenumberoftransitionsonthe thanstatestoobtaingoodcoverageofcontrollerbehavior.however,theyused controllerstatesofadesignsuggestedtheusefulnessofusingtransitionsrather designersupplied\translationfunctions",ortest-basedtechniquestogenerate simulationinputsequenceswhichexcitedasmuchofthecontrolaspossible;our 2Background InvariantVerication approachisrootedinsymbolicmethods. associatedbooleanfunction.anitestatemachinecanberepresentedbyan aninterconnectedsetofprimaryinputs,gates,andlatches.eachgatehasan atthebehaviorallevelusingnitestatemachines(fsms).anetlistconsistsof forcomputationalmodelsforhardware. Inordertobeabletoanalyticallyreasonabouthardware,werstneedtodevelop edge-labeleddirectedgraph,wheretheverticescorrespondtostates,andthe mathematicalmodelsfordigitalsystems.singhal[14]givesadetailedexposition labelsareinput-outputpairs. Hardwaredesignscanbemodeledatthestructurallevelusingnetlists,or implementedsymbolicallyusingreducedorderedbinarydecisiondiagram[3]. thesetofallstateswhichcanbereachedfromabyapplyinganinputsequenceof lengthone.similarly,thepre-imageofa(denotedbypreimg(a))isthesetoall stateswhichcanreachainonestep.theimgandpre-imageprocedurescanbe state/outputfunctionsarederivedbycomposingthegatefunctions. chinefromit;statesareevaluationstothesetoflatchvariables,andthenext- GivenadesignDandasetofstatesA,theimageofA(denotedbyImg(A))is Foragivenanetlist,thereisanaturalwayofderivinganitestatema- alllieintheinvariant.analternateapproachtocheckinginvariantsisbasedon icallycomputeallstatesreachablefromtheinitialstatesanddeterminethatthey backwardanalysis,whereinthesymbolicpreimgoperatorisiterativelyapplied todetermineallstateswhichcanreachthecomplementoftheinvariant;the asinvariantverication,orassertionchecking. of\goodstates"(referredtoastheinvariant).thisproblemisvariouslyknown statereachablefromadesignatedsetofinitialstateslieswithinaspeciedset Onestraightforwardsolutiontotheinvariantcheckingproblemistosymbol- Acommonvericationproblemforhardwaredesignsistodetermineifevery thecourseofimagecomputationscangrowverylarge. 3SaturatedSimulation Manydesignscanbeseparatedinto\control"and\datapath"asillustratedin Figure1;furthermore,thedesignerisawareofthisdichotomy.Formostsuch invariantfailsiftheinitialstateliesinthisset. TheprimarylimitationofbothapproachesisthattheBDDsencounteredin
4 Inthissection,wedescribeanapproachwerefertoas\saturatesimulation";this totalnumberoflatches;however,thecontrolportioniswherebugsusuallyoccur. designs,thenumberoflatchesinthecontrollerisusuallyasmallfractionofthe PC approachattemptsheuristicallytoexploreasmuchofthecontrolportionofthe Mem Out designaspossible. Fig.1.PartitioningadesignintoControlandDatapath. Mem Logic ALU OP canbenaturallydesignatedcontroland21whicharedata.hence,thereareno R ALU Registers verylargedesignstocomputetheimageofasmall(inthesenseofcardinality) morethan512dierentpossiblevaluesforthecontrolstate.itisfeasibleevenfor Asanexample,considerthevipermicroprocessor.Itcontains9latcheswhich ALU out M setofstates.inpart,thisfollowsfromthefactthattheconstructionofthebdd forthenext-statelogiccanberestrictedtothecurrentsetofstates.thissuggests Mem Addr thatitmaybepossibletoperforma\partial"reachabilityanalysis,inwhichall distinctcontrolstatesarepreservedateachstep. givenbyanevaluationtoxc[xd. respecttoaif(8c:8d)[(c;d)2a!(9d)[(c;d)2a]] thevariablesassociatedwiththedatapathbexd.thusthestateofthedesignis Denition1.LetAbeasetofstates.AsubsetAofAiscontrol-saturatedwith LetthevariablesassociatedwiththecontrolportionofthedesignbeXcand ationsina,andisassmallaspossible(inthesenseofcardinality).anexample ofaisagoodrepresentativeset itincludesallthedistinctcontrollercongur- ofacontrol-saturatedsubsetisgiveninfigure2(a). ofa.letfbeabooleanfunctiononvariablesx=fx1;x2;:::;xng.linet curringinaoccursina.thuscontrol-saturatedsubsetsofapreserveallthe controllerstatespresentina.heuristically,aminimalcontrol-saturatedsubset Intuitively,Aisacontrol-saturatedsubsetofAifeverycontrolstateoc- whichtakesabddforfandasubsetxxofthevariables,andreturnsa BDDforafunctionfwhichhasthepropertythat al.[8]presentedanecientalgorithm(referredtoasthecprojectoperator) Wenowaddresstheproblemofcomputingminimalcontrol-saturatedsubsets Status Bits
5 BDDtfunctionCntrlSatSim(A,CntrlVars,G)f /*AinitializedtotheBDDfortheresetstates.*/ /*GistheBDDfortheinvariant.*/ Fig.2.Minimalcontrolsaturatedsubsets. cproject cproject Data value First two bits are control, last three are data 11 A ={(111),(1),(1111), (1),(11),(1)} 1 1 A ={(1),(1),(1)} State Space = 16 (a) Ex. Control saturated gif(bddequal(r,a)) if(bddintersects(a,g))/*invariantfails!!*/ ImgA:=BDDImg(A); R:=BDDOr(A,ImgA); returncntrlsatsim(r,cntrlvars,g); R:=BDDCproject(R,CntrlVars); assertfail; returnr; subset (b) Ex. Control reachability Sincesetscanbethoughtofintermsofcharacteristicfunctions,wewillfreely 1.foranyassignmentvtothevariablesinX,sothatf(v)=1,thereisexactly 2.forallu,f(u)=1)f(u)=1. onevaluationvwhichagreeswiththevaluationvoverthevariablesinx sothatf(v)=1,andfurthermore Fig.3.Control-saturatedsimulation. cprojectoperator.thisinturnisusedasthecurrentreachedstateset.the ReachablestatesareiterativelycomputedusingtheImgoperator;ateachstep, controlsaturatedsubsetofa. rstfewstepsareillustratedinfigure2.theprocedureisincomplete,sinceitis acontrol-saturatedsubsetofthecurrentreachedstateiscomputedusingthe greedy:minimalcontrol-saturatedsubsetsofthesetscomputedbythecproject applythecprojectoperatortosets.observethatcproject(a;xc)isaminimal operatorwillnotnecessarilybesucienttocoverallpossiblecontrollerstates. InFigure3wesketchasimplesymbolicprocedureforinvariantverication. Onesimplewayoffurtherenhancingthecoverageachievedbycontrol-saturated Control value
6 simulationistogenerateseveral\representative"controlstates.therearesimple modicationstothecprojectoperatorwhichcanachievethiseect.another iteration. Afundamentalextensiontoobtainenhancedcoverageistoperformapartial 3.1Control-edgeSaturatedSimulation approachistoapplycprojectonlytothefrontierofthereachedstatesateach reachabilityanalysisandateachsteppickasubsetoftheimagewhichpreserves all\controllertransitions"totheimagefromthecurrentset.hoetal.[6]and Abrahametal.[7]createdsimulationvectorswhichexcitealargenumberof bugswiththesevectorsunderlinestheusefulnessofusingtransitionsratherthan statestoobtaingoodcoverage.asanexample,consideramicroprocessorwhere controltransitionsindesigns;thehighqualityoftheirresultsintermsofnding thecontrolstateisthevalueoftheprogramcounter.twostateswhichcorrespond withdierentdatavalues;inthiscase,itisnaturaltokeeptheresultingstates todierentlinesintheprogrammaybothtransitionthesameprogramline Denition2.LetAbeasetofstates.AsubsetBofImg(A)issaidtobe dierent. control-edgesaturatedwithrespecttoaif (8c:8d:8c:8d)[(c;d)2A^(c;d)2Img(f(c;d)g)]! (9d:9d)[(c;d)2B^(c;d)2A^(c;d)2Img(f(c;d)g)] Wenowdescribehowtoexploreedgesinthecontrolstatespace. inbandastate(c;d)inasothat(c;d)!(c;d). everytransition(c;d)!(c;d)fromatoimga,thereisastate(c;d) InEnglish,theabovedenitionsaysthatBiscontrol-edgesaturatedwhenfor foreverycontrollatchxc,addanewlatchxswhich\shadows"xc,thatis, subsetisgiveninfigure4. thenextstateofxsisthepresentstateofxc.denotethesetofshadowstate andisassmallaspossible.anexampleofaminimalcontrol-edgesaturated distinctcontrollercongurationsresultinginimg(a)fromtransitionsfroma, thecontrollertransitionsoriginatingata.heuristically,aminimalcontrol-edge saturatedsubsetofimg(a)isagoodrepresentativeset itincludesallthe Minimalcontrol-edgesaturatedsetscanbecomputedaugmentingthedesign: Thusinsomesense,control-edgesaturatedsubsetsofImg(A)preserveall variablesthusintroducedbyxs.clearlythenext-stateofthelatchesindexed byxc[xdisindependentofthatoftheshadowlatches.thefollowinglemma demonstratesthatminimalcontrol-edgesaturatedsetscanbecomputedfrom theaugmenteddesign. Lemma3.LetAbeAliftedfromXc[XdtoXc[Xd[Xs.DeneBtobe minimalcontrol-edgesaturatedwithrespecttoa. theexistentialquanticationofcproject(img(a);xc[xs)byxs.thenbis
7 Proof.Observingthatcproject(?;)isalwayssubsetof?,itfollowsthat non-shadowlatchesdoesnotdependontheshadowlatches,itfollowsthatthe subsetofimg(a). existentialquanticationofimg(a)byxsisequaltoimg(a),andsobisa cproject(img(a);xc[xs)isasubsetofimg(a).sincethenextstateof (namelyb)willcontain(c;d).since(c;d)liesintheimageof(c;d), tifyingthexsvariablesfromcproject(img(a);xc[xs),theresultingset Img(A);letitlieintheimageof((C;S);D).Hence,onexistentiallyquan- Xs)containsastateoftheform((C;C);D).Note((C;C);D)liesin foranarbitraryassignmentstotheshadowlatches.hencecproject(img(a);xc[ Fromtheconstructionoftheaugmenteddesign,((C;C);D)isinImg((C;S);D) atransitionfrom(c;d)2ato(c;d),i.e.,(c;d)2img(f(c;d)g). (C;D)satisfythe\if"portionoftheimplicationinDenition2.Thenthereis WenowshowBiscontrol-edgesaturatedwithrespecttoA.Let(C;D)and previoussection. indenition2. DandDareexistentialwitnessesforthe\then"portionoftheimplication WecodedtheroutinesdescribedintheprevioussectionaspartoftheVISprogram[2].Resultsareprovidedontwobenchmarks{the885,andvipermicroprocessors.The885isapproximately4gateequivalents,andcontains242 MinimalityofBfollowsfromthepropertiesofcprojectdescribedinthe 3.2ExperimentalResults{SaturatedSimulation latches,ofwhich33wereidentiedasbeingcontrol.theviperisalso4gate 128MBytesofmainmemory.Atimeoutof2secondswasusedforallviperexperiments,and1secondsfor885experiments.Sifting-baseddynamic reorderingwasenabledthroughouttheexperiments. perimentswereconductedonanultrasparc1,witha17mhzprocessor,and equivalents,andcontains218latchesofwhich9werefromthecontrol.allex- theuseofacontrol-statesaturatedsimulation(asgiveninfigure3).for885,we fourreachabiltysteps,whichwereeasilyperformed.)table2presentsresultson forviperintable1stemsfromthefactthattheprogramtimedoutaftertherst anorderofmagnitudemore.table3presentsresultsontheuseofcontrol-edge BDDencounteredduringreachabilityanalysis.(TheabnormallylowpeakBDD computealmosttwiceasmanyreachablecontrolstatesandtransitions;forviper, saturatedsimulation.inthesametime,moreedgesarevisited;thiscomesatthe analysisonthetwobenchmarks.peakbddisthenumberofnodesinthelargest Table1presentsresultsontheuseofacompleteBDD-basedreachability expenseofhighermemoryconsumptionwithrespecttocontrol-statesaturated simulation.interestingly,fewercontrolstatesarevisited;weascribethistothe factthatthecontrol-statesaturatedsimulationisfaster,andsomanagestogo deeperintothestatespaceinthesameamountoftime;thisisseeninthedepth column. 9]inTable4.Forviper,weperformed1setsofsimulations,eachcomprising Wecomparesaturatedsimulationwithfastlookupbasedcyclesimulation[1,
8 ExamplejRchd.StatesjPeakBDDjControlStatesjjControlEdgesjdepth viper1: : ExamplePeakBDDjControlStatesjjControlEdgesjdepth viper1618 Table1.CompleteBDDbasedreachabilityanalysis worsethansaturatedsimulation. of2vectors;for885weperformed4setsoflength2.eventhoughwe gavecyclesimulationtwoordersofmagnitudemoretime,itstillperformedfar Table2.Partialreachabilityanalysisusingcontrol-statesaturatedsubsets RetrogradeAnalysis RetrogradeAnalysis(RA)isanimportantsearchtechniquedevelopedwithin theeldofarticialintelligence.initssimplestform,rarstmarksallend determiningthegametheoreticvaluesofallpositionsinthesearchspace. positions(e.g.,checkmate),andthenbymakingunmovesfromtheendpositions worksitswaybacktothepositionsfarthestfromtheendposition,ontheway B;B1;:::whereBisthecomplementoftheinvariantandBi+1=PreImg(Bi). Bl,searchforaninputsequencewhichtakesaninitialstatetoastateinBl. AnalogouslytotheWi'sabove,theBi'sareeectivelybadstates.TheB'scan themcompactly.finally,whenmainmemoryisnearlyexhausted,sayattheset growverylargeintermsofcardinality;itisnaturaltousebddstorepresent RAcannaturallybeappliedtoinvariantchecking:constructthesetsofstates tothenumberofbitsinthestate,andisindependentofthesizeofthebdd. ifastateliesinthesetdenedbyabddisveryfast ittaketimeproportional fashionliesinbl.thisapproachisillustratedinfigure5(a).notethatchecking ingfromarandominitialstate;thesearchhaltsifsomestatereachedinthis Thesimplestsearchstrategyisthesimulationofrandominputvectorsstart- Table3.Partialreachabilityanalysisusingcontrol-edgesaturatedsubsets. ExamplePeakBDDjControlStatesjjControlEdgesjdepth viper
9 ExampleSaturatedSimulation viper Time(sec)jCtlStatesjjCtlEdgesjTimeSizejCtlStatesjjCtlEdgesj Table4.Comparingsaturatedsimulationwithcyclesimulation CycleSimulation tothetargetstates,i.e.,tobl.weproposetheuseofhammingdistanceasa measureofcloseness. isthenumberofpositionsinwhichtheandvectorsdier.considertherelationsh;h1;h2;:::;hnf;1g2nwhere(;)2hki,(;)k.the RecallthattheHammingdistancebetween;2f;1gn(denotedby(;)) Amoresophisticatedsearchstrategyistopickaninitialstatewhichis\close" Fig.4.Aminimalcontrol-edgesaturatedsubset. thefollowingidentity: relationh1canbeconstructeddirectlyusingbdds.therelationhi+1satises thresholdsize.fromtheoutermostring,pickastate(say)whichisclosest reachabilityfromtheinitialstatestillthebddforreachedstatesreachesa Hence,theBDDsforH;H1;H2;:::;Hnf;1g2ncanbeeasilyconstructed; smallfortheinterleavedvariableordering. furthermoreasimpleargumentbasedoncountingcofactorsshowsthattheyare ThesearchforstatesinBlcanbeenhancedbybyrstperformingforward Hi+1=Hi[(9)[(;)2Hi^(;)2H1] tobl,andthenperformrandomcyclesimulationfrom.thisisillustrated recursivelyapplied.thisillustratedinfigure5(c). infigure5(b).insteadofcyclesimulationfrom,acombinationofsymbolic forwardreachabilityanalysiscoupledwiththethehammingheuristiccanbe A (1) (1111) (11) Input Img(A) (1) (111) (1111) (11) (111) (1) (1) (111) (1111) (11) (111) First two bits are control, last three are data Same control values, but correspond to different controller transitions => keep both
10 4.1ExperimentalResults{RetrogradeAnalysis areprovidedontwobenchmarks{mesh4isaroutingalgorithmona4by4mesh WecodedtheroutinesdescribedintheprevioussectionaspartoftheVISprogram[2],andexperimentedwithanumberofexamples.Representativeresults ofnodes,andcube4ishypercubebasedroutingprotocol.forbothexamples,we Fig.5.RetrogradesearchforInvariantchecking A init A1 A2 Ai A1 A2 A Ai A1 A2 A Bl Ai B4 choseaninvariantwhichfails. B3 Bl B2 B1 B B2 B1 B B2 B1 B State Space State Space State Space plotthenumberofsimulationtrialsneededtoreachapre-image,startingfrom aftersuccessivepre-imagesinfigure6(a);bothgrowquickly.infigure6(b)we theinitialstateagainstthenumberofpreimagestepstaken;eachtrialconsists ResultsonMesh4arereportedinFigure6.WeplotBDDsizeandcardinality Vanilla RA (b) RA Hamming; closest states hatched (c) Enhanced RA Hamming decreasesrapidly. Figures7(a)and7(b)areasbefore.InFigure7(c),weshowtheeectoftaking ofapplying1randomvectors.itisclearfromthepicturethatthisnumber oneforwardstep,andthenpickingastateintheimagewhichisclosetothetarget asopposedtoarandomstateintheimage;infigure7(d)wetaketwoforward distanceisused.interestingly,whenastateintheimageispickedatrandom, appreciabledecreaseinthenumberofsimulationtrialsneededwhenhamming steps,andthenpickastatewhichisclosetothetarget.inbothcases,thereisan theperformanceisactuallyworsethatsimplystartingattheinitialstate. TheeectofHammingdistanceisgiveninFigure7fortheCube4example. 5Conclusion Weinvestigatedwaysinwhichtocombinesymbolicvericationwithsimulation. Specically,wegaveheuristicjusticationforsaturatedsimulationandretrogradeanalysis.Experimentalevidencecorroboratesthattheseapproachesyield enhancedcoverageandrobustness.thusthecombinationofformalandinformal vericationoersbenetsnotavailableineachindependently. controllers. formalmethods,particularlytheproblemofvalidatingsoftwareforembedded Inthefutureweintendtobuilduponthethemeofrelatingformalandin-
11 BDD size Number of target states Simulation steps BDD size References P.AsharandS.Malik.FastFunctionalSimulationUsingBranchingPrograms.In Fig.6.RetrogradeAnalysisappliedtoMesh No. of backward steps No. of backward steps 4.B.Chen,M.Yamazaki,andM.Fujita.BugIdenticationofaRealChipDesign 2.R.K.Brayton,G.D.Hachtel,A.Sangiovanni-Vincentelli,F.Somenzi,A.Aziz,S.- 3.R.Bryant.Graph-basedAlgorithmsforBooleanFunctionManipulation.IEEE TransactionsonComputers,C-35:677{691,August1986. jan,s.sarwary,t.r.shiple,g.swamy,andt.villa.vis:asystemforveri- cationandsynthesis.inproc.ofthecomputeraidedvericationconf.,july T.Cheng,S.Edwards,S.Khatri,Y.Kukimoto,A.Pardo,S.Qadeer,R.K.Ran Proc.Intl.Conf.onComputer-AidedDesign,November1995. (a) (b) 5.H.Cho,G.D.Hachtel,E.Macii,M.Poncino,andF.Somenzi.AStructuralApproachtoStateSpaceDecompositionforApproximateReachabilityAnalysis.In FlowMachineandApplicationtoEvaluatingCoverageofVericationVectors.In Proc.Intl.Conf.onComputerDesign,Austin,TX,October1995. turalvalidationforprocessors.inproceedingsoftheinternationalsymposiumon DecisionDiagrams.InProc.Intl.Conf.onComputerDesign,Cambridge,MA, ComputerArchitecture,June RichardC.Ho,C.HanYang,MarkA.Horowitz,andDavidL.Dill.Architec- 7.Y.Hoskote,D.Moundanos,andJ.Abraham.AutomaticExtractionoftheControl bysymbolicmodelchecking.inproc.europeanconf.ondesignautomation, Proc.Intl.Conf.onComputerDesign,October1994. pages132{136,march B.LinandR.Newton.ImplicitManipulationofEquivalenceClassesUsingBinary 1.KennethL.McMillan.SymbolicModelChecking.KluwerAcademicPublishers, 9.P.McGeer,K.McMillan,A.Saldanha,A.Sangiovanni-Vincentelli,andP.Scaglia. November1995. October1991. FastDiscreteFunctionEvaluation.InProc.Intl.Conf.onComputer-AidedDesign, 1993.
12 1 Target state number Simulation steps without Hamming 8 BDD size 4 BDD size Fig.7.EectofHammingDistanceonCube No. of backward steps No. of backward steps (a) (b) BDD size Simulation steps Simulation steps 4 BDD size without Hamming 4 without Hamming Simulation steps Simulation steps with Hamming with Hamming R.Ranjan,J.Sanghavi,R.K.Brayton,andA.L.Sangiovanni-Vincentelli.High 11.R.MotwaniandP.Raghavan.RandomizedAlgorithms.CambridgeUniversity K.RaviandF.Somenzi.HighDensityReachabilityAnalysis.InProc.Intl.Conf VigyanSinghal.DesignReplacementsforSequentialCircuits.PhDthesis,Uni- Press, K.Thompson.Retrogradeanalysisofcertainendgames.ICCAJournal,9(3):131{ PerformanceBDDPackageBasedonExploitingMemoryHierarchy.InProc.of thedesignautomationconf.,lasvegas,nv,june1996. oncomputer-aideddesign,santaclara,ca,november1995. eering,universityofcalifornia,berkeley,ca9472,1996. versityofcaliforniaberkeley,electronicsresearchlaboratory,collegeofengin ,1986. No. backward steps No. backward steps (c) (d) ThisarticlewasprocessedusingtheLATEXmacropackagewithLLNCSstyle
WAR: Write After Read
 WAR: Write After Read write-after-read (WAR) = artificial (name) dependence add R1, R2, R3 sub R2, R4, R1 or R1, R6, R3 problem: add could use wrong value for R2 can t happen in vanilla pipeline (reads
WAR: Write After Read write-after-read (WAR) = artificial (name) dependence add R1, R2, R3 sub R2, R4, R1 or R1, R6, R3 problem: add could use wrong value for R2 can t happen in vanilla pipeline (reads
l C-Programming l A real computer language l Data Representation l Everything goes down to bits and bytes l Machine representation Language
 198:211 Computer Architecture Topics: Processor Design Where are we now? C-Programming A real computer language Data Representation Everything goes down to bits and bytes Machine representation Language
198:211 Computer Architecture Topics: Processor Design Where are we now? C-Programming A real computer language Data Representation Everything goes down to bits and bytes Machine representation Language
Data Dependences. A data dependence occurs whenever one instruction needs a value produced by another.
 Data Hazards 1 Hazards: Key Points Hazards cause imperfect pipelining They prevent us from achieving CPI = 1 They are generally causes by counter flow data pennces in the pipeline Three kinds Structural
Data Hazards 1 Hazards: Key Points Hazards cause imperfect pipelining They prevent us from achieving CPI = 1 They are generally causes by counter flow data pennces in the pipeline Three kinds Structural
Computer Organization and Architecture
 Computer Organization and Architecture Chapter 11 Instruction Sets: Addressing Modes and Formats Instruction Set Design One goal of instruction set design is to minimize instruction length Another goal
Computer Organization and Architecture Chapter 11 Instruction Sets: Addressing Modes and Formats Instruction Set Design One goal of instruction set design is to minimize instruction length Another goal
Chapter 01: Introduction. Lesson 02 Evolution of Computers Part 2 First generation Computers
 Chapter 01: Introduction Lesson 02 Evolution of Computers Part 2 First generation Computers Objective Understand how electronic computers evolved during the first generation of computers First Generation
Chapter 01: Introduction Lesson 02 Evolution of Computers Part 2 First generation Computers Objective Understand how electronic computers evolved during the first generation of computers First Generation
Design of Pipelined MIPS Processor. Sept. 24 & 26, 1997
 Design of Pipelined MIPS Processor Sept. 24 & 26, 1997 Topics Instruction processing Principles of pipelining Inserting pipe registers Data Hazards Control Hazards Exceptions MIPS architecture subset R-type
Design of Pipelined MIPS Processor Sept. 24 & 26, 1997 Topics Instruction processing Principles of pipelining Inserting pipe registers Data Hazards Control Hazards Exceptions MIPS architecture subset R-type
The 104 Duke_ACC Machine
 The 104 Duke_ACC Machine The goal of the next two lessons is to design and simulate a simple accumulator-based processor. The specifications for this processor and some of the QuartusII design components
The 104 Duke_ACC Machine The goal of the next two lessons is to design and simulate a simple accumulator-based processor. The specifications for this processor and some of the QuartusII design components
Solution: start more than one instruction in the same clock cycle CPI < 1 (or IPC > 1, Instructions per Cycle) Two approaches:
 Multiple-Issue Processors Pipelining can achieve CPI close to 1 Mechanisms for handling hazards Static or dynamic scheduling Static or dynamic branch handling Increase in transistor counts (Moore s Law):
Multiple-Issue Processors Pipelining can achieve CPI close to 1 Mechanisms for handling hazards Static or dynamic scheduling Static or dynamic branch handling Increase in transistor counts (Moore s Law):
CS352H: Computer Systems Architecture
 CS352H: Computer Systems Architecture Topic 9: MIPS Pipeline - Hazards October 1, 2009 University of Texas at Austin CS352H - Computer Systems Architecture Fall 2009 Don Fussell Data Hazards in ALU Instructions
CS352H: Computer Systems Architecture Topic 9: MIPS Pipeline - Hazards October 1, 2009 University of Texas at Austin CS352H - Computer Systems Architecture Fall 2009 Don Fussell Data Hazards in ALU Instructions
Instruction Set Design
 Instruction Set Design Instruction Set Architecture: to what purpose? ISA provides the level of abstraction between the software and the hardware One of the most important abstraction in CS It s narrow,
Instruction Set Design Instruction Set Architecture: to what purpose? ISA provides the level of abstraction between the software and the hardware One of the most important abstraction in CS It s narrow,
ARM. Architecture and Assembly. Modest Goal: Turn on an LED
 ARM Architecture and Assembly Modest Goal: Turn on an LED Package on Package Broadcom 2865 ARM Processor Samsung 2Gb SDRAM (John) von Neumann Architecture Instructions and data stored in the same memory
ARM Architecture and Assembly Modest Goal: Turn on an LED Package on Package Broadcom 2865 ARM Processor Samsung 2Gb SDRAM (John) von Neumann Architecture Instructions and data stored in the same memory
Chapter 2 Topics. 2.1 Classification of Computers & Instructions 2.2 Classes of Instruction Sets 2.3 Informal Description of Simple RISC Computer, SRC
 Chapter 2 Topics 2.1 Classification of Computers & Instructions 2.2 Classes of Instruction Sets 2.3 Informal Description of Simple RISC Computer, SRC See Appendix C for Assembly language information. 2.4
Chapter 2 Topics 2.1 Classification of Computers & Instructions 2.2 Classes of Instruction Sets 2.3 Informal Description of Simple RISC Computer, SRC See Appendix C for Assembly language information. 2.4
Pipeline Hazards. Structure hazard Data hazard. ComputerArchitecture_PipelineHazard1
 Pipeline Hazards Structure hazard Data hazard Pipeline hazard: the major hurdle A hazard is a condition that prevents an instruction in the pipe from executing its next scheduled pipe stage Taxonomy of
Pipeline Hazards Structure hazard Data hazard Pipeline hazard: the major hurdle A hazard is a condition that prevents an instruction in the pipe from executing its next scheduled pipe stage Taxonomy of
Computer organization
 Computer organization Computer design an application of digital logic design procedures Computer = processing unit + memory system Processing unit = control + datapath Control = finite state machine inputs
Computer organization Computer design an application of digital logic design procedures Computer = processing unit + memory system Processing unit = control + datapath Control = finite state machine inputs
VLIW Processors. VLIW Processors
 1 VLIW Processors VLIW ( very long instruction word ) processors instructions are scheduled by the compiler a fixed number of operations are formatted as one big instruction (called a bundle) usually LIW
1 VLIW Processors VLIW ( very long instruction word ) processors instructions are scheduled by the compiler a fixed number of operations are formatted as one big instruction (called a bundle) usually LIW
CPU Organisation and Operation
 CPU Organisation and Operation The Fetch-Execute Cycle The operation of the CPU 1 is usually described in terms of the Fetch-Execute cycle. 2 Fetch-Execute Cycle Fetch the Instruction Increment the Program
CPU Organisation and Operation The Fetch-Execute Cycle The operation of the CPU 1 is usually described in terms of the Fetch-Execute cycle. 2 Fetch-Execute Cycle Fetch the Instruction Increment the Program
CPU Organization and Assembly Language
 COS 140 Foundations of Computer Science School of Computing and Information Science University of Maine October 2, 2015 Outline 1 2 3 4 5 6 7 8 Homework and announcements Reading: Chapter 12 Homework:
COS 140 Foundations of Computer Science School of Computing and Information Science University of Maine October 2, 2015 Outline 1 2 3 4 5 6 7 8 Homework and announcements Reading: Chapter 12 Homework:
Incorporating Evidence in Bayesian networks with the Select Operator
 Incorporating Evidence in Bayesian networks with the Select Operator C.J. Butz and F. Fang Department of Computer Science, University of Regina Regina, Saskatchewan, Canada SAS 0A2 {butz, fang11fa}@cs.uregina.ca
Incorporating Evidence in Bayesian networks with the Select Operator C.J. Butz and F. Fang Department of Computer Science, University of Regina Regina, Saskatchewan, Canada SAS 0A2 {butz, fang11fa}@cs.uregina.ca
CS:APP Chapter 4 Computer Architecture. Wrap-Up. William J. Taffe Plymouth State University. using the slides of
 CS:APP Chapter 4 Computer Architecture Wrap-Up William J. Taffe Plymouth State University using the slides of Randal E. Bryant Carnegie Mellon University Overview Wrap-Up of PIPE Design Performance analysis
CS:APP Chapter 4 Computer Architecture Wrap-Up William J. Taffe Plymouth State University using the slides of Randal E. Bryant Carnegie Mellon University Overview Wrap-Up of PIPE Design Performance analysis
To appear in the Conference on Computer-Aided Verification, June 21-23, 1994. Automatic Verication of. Pipelined Microprocessor Control
 To appear in the Conference on Computer-Aided Verification, June 21-23, 1994 (this version has an appendix not present in the conference version) Automatic Verication of Pipelined Microprocessor Control
To appear in the Conference on Computer-Aided Verification, June 21-23, 1994 (this version has an appendix not present in the conference version) Automatic Verication of Pipelined Microprocessor Control
Solutions. Solution 4.1. 4.1.1 The values of the signals are as follows:
 4 Solutions Solution 4.1 4.1.1 The values of the signals are as follows: RegWrite MemRead ALUMux MemWrite ALUOp RegMux Branch a. 1 0 0 (Reg) 0 Add 1 (ALU) 0 b. 1 1 1 (Imm) 0 Add 1 (Mem) 0 ALUMux is the
4 Solutions Solution 4.1 4.1.1 The values of the signals are as follows: RegWrite MemRead ALUMux MemWrite ALUOp RegMux Branch a. 1 0 0 (Reg) 0 Add 1 (ALU) 0 b. 1 1 1 (Imm) 0 Add 1 (Mem) 0 ALUMux is the
CPU Performance Equation
 CPU Performance Equation C T I T ime for task = C T I =Average # Cycles per instruction =Time per cycle =Instructions per task Pipelining e.g. 3-5 pipeline steps (ARM, SA, R3000) Attempt to get C down
CPU Performance Equation C T I T ime for task = C T I =Average # Cycles per instruction =Time per cycle =Instructions per task Pipelining e.g. 3-5 pipeline steps (ARM, SA, R3000) Attempt to get C down
Reduced Instruction Set Computer (RISC)
 Reduced Instruction Set Computer (RISC) Focuses on reducing the number and complexity of instructions of the ISA. RISC Goals RISC: Simplify ISA Simplify CPU Design Better CPU Performance Motivated by simplifying
Reduced Instruction Set Computer (RISC) Focuses on reducing the number and complexity of instructions of the ISA. RISC Goals RISC: Simplify ISA Simplify CPU Design Better CPU Performance Motivated by simplifying
IBCM: The Itty Bitty Computing Machine
 Chapter 1 IBCM: The Itty Bitty Computing Machine The child receives data through the sense organs; the child also has some inborn processing capacities otherwise it would not be able to learn but in addition,
Chapter 1 IBCM: The Itty Bitty Computing Machine The child receives data through the sense organs; the child also has some inborn processing capacities otherwise it would not be able to learn but in addition,
UNIVERSITY OF CALIFORNIA, DAVIS Department of Electrical and Computer Engineering. EEC180B Lab 7: MISP Processor Design Spring 1995
 UNIVERSITY OF CALIFORNIA, DAVIS Department of Electrical and Computer Engineering EEC180B Lab 7: MISP Processor Design Spring 1995 Objective: In this lab, you will complete the design of the MISP processor,
UNIVERSITY OF CALIFORNIA, DAVIS Department of Electrical and Computer Engineering EEC180B Lab 7: MISP Processor Design Spring 1995 Objective: In this lab, you will complete the design of the MISP processor,
Approximation Algorithms
 Approximation Algorithms or: How I Learned to Stop Worrying and Deal with NP-Completeness Ong Jit Sheng, Jonathan (A0073924B) March, 2012 Overview Key Results (I) General techniques: Greedy algorithms
Approximation Algorithms or: How I Learned to Stop Worrying and Deal with NP-Completeness Ong Jit Sheng, Jonathan (A0073924B) March, 2012 Overview Key Results (I) General techniques: Greedy algorithms
ELECTENG702 Advanced Embedded Systems. Improving AES128 software for Altera Nios II processor using custom instructions
 Assignment ELECTENG702 Advanced Embedded Systems Improving AES128 software for Altera Nios II processor using custom instructions October 1. 2005 Professor Zoran Salcic by Kilian Foerster 10-8 Claybrook
Assignment ELECTENG702 Advanced Embedded Systems Improving AES128 software for Altera Nios II processor using custom instructions October 1. 2005 Professor Zoran Salcic by Kilian Foerster 10-8 Claybrook
CS 1301 Homework 6 Scribbler Line Sensing Due: Friday March 13th, before 11:55pm PM EST. Out of 130 points Files to submit:
 CS 1301 Homework 6 Scribbler Line Sensing Due: Friday March 13th, before 11:55pm PM EST. Out of 130 points Files to submit: hw6.py For Help: - TA Helpdesk Schedule posted on class website. - Email TAs
CS 1301 Homework 6 Scribbler Line Sensing Due: Friday March 13th, before 11:55pm PM EST. Out of 130 points Files to submit: hw6.py For Help: - TA Helpdesk Schedule posted on class website. - Email TAs
Overview. CISC Developments. RISC Designs. CISC Designs. VAX: Addressing Modes. Digital VAX
 Overview CISC Developments Over Twenty Years Classic CISC design: Digital VAX VAXÕs RISC successor: PRISM/Alpha IntelÕs ubiquitous 80x86 architecture Ð 8086 through the Pentium Pro (P6) RJS 2/3/97 Philosophy
Overview CISC Developments Over Twenty Years Classic CISC design: Digital VAX VAXÕs RISC successor: PRISM/Alpha IntelÕs ubiquitous 80x86 architecture Ð 8086 through the Pentium Pro (P6) RJS 2/3/97 Philosophy
A Hybrid Model of the Akamai Adaptive Streaming Control System
 A Hybrid Model of the Akamai Adaptive Streaming Control System Cape Town, South Africa 26 August 2014 L. De Cicco, G. Cofano and S. Mascolo Politecnico di Bari, Dipartimento di Ingegneria Elettrica e dell'informazione
A Hybrid Model of the Akamai Adaptive Streaming Control System Cape Town, South Africa 26 August 2014 L. De Cicco, G. Cofano and S. Mascolo Politecnico di Bari, Dipartimento di Ingegneria Elettrica e dell'informazione
Architectures and Platforms
 Hardware/Software Codesign Arch&Platf. - 1 Architectures and Platforms 1. Architecture Selection: The Basic Trade-Offs 2. General Purpose vs. Application-Specific Processors 3. Processor Specialisation
Hardware/Software Codesign Arch&Platf. - 1 Architectures and Platforms 1. Architecture Selection: The Basic Trade-Offs 2. General Purpose vs. Application-Specific Processors 3. Processor Specialisation
Assembly Language Programming
 Assembly Language Programming Assemblers were the first programs to assist in programming. The idea of the assembler is simple: represent each computer instruction with an acronym (group of letters). Eg:
Assembly Language Programming Assemblers were the first programs to assist in programming. The idea of the assembler is simple: represent each computer instruction with an acronym (group of letters). Eg:
How To Validate Synchronous Reactivesystems
 fromformalvericationtoautomatictesting? ValidationofSynchronousReactiveSystems: fnicolas.halbwachs,pascal.raymondg@imag.fr NicolasHalbwachs,PascalRaymond thevalidationofreactivesystemsdescribedinthesynchronousdata-ow
fromformalvericationtoautomatictesting? ValidationofSynchronousReactiveSystems: fnicolas.halbwachs,pascal.raymondg@imag.fr NicolasHalbwachs,PascalRaymond thevalidationofreactivesystemsdescribedinthesynchronousdata-ow
Central Processing Unit (CPU)
 Central Processing Unit (CPU) CPU is the heart and brain It interprets and executes machine level instructions Controls data transfer from/to Main Memory (MM) and CPU Detects any errors In the following
Central Processing Unit (CPU) CPU is the heart and brain It interprets and executes machine level instructions Controls data transfer from/to Main Memory (MM) and CPU Detects any errors In the following
Computer Architecture Lecture 2: Instruction Set Principles (Appendix A) Chih Wei Liu 劉 志 尉 National Chiao Tung University cwliu@twins.ee.nctu.edu.
 Computer Architecture Lecture 2: Instruction Set Principles (Appendix A) Chih Wei Liu 劉 志 尉 National Chiao Tung University cwliu@twins.ee.nctu.edu.tw Review Computers in mid 50 s Hardware was expensive
Computer Architecture Lecture 2: Instruction Set Principles (Appendix A) Chih Wei Liu 劉 志 尉 National Chiao Tung University cwliu@twins.ee.nctu.edu.tw Review Computers in mid 50 s Hardware was expensive
COMPUTERS ORGANIZATION 2ND YEAR COMPUTE SCIENCE MANAGEMENT ENGINEERING JOSÉ GARCÍA RODRÍGUEZ JOSÉ ANTONIO SERRA PÉREZ
 COMPUTERS ORGANIZATION 2ND YEAR COMPUTE SCIENCE MANAGEMENT ENGINEERING UNIT 1 - INTRODUCTION JOSÉ GARCÍA RODRÍGUEZ JOSÉ ANTONIO SERRA PÉREZ Unit 1.MaNoTaS 1 Definitions (I) Description A computer is: A
COMPUTERS ORGANIZATION 2ND YEAR COMPUTE SCIENCE MANAGEMENT ENGINEERING UNIT 1 - INTRODUCTION JOSÉ GARCÍA RODRÍGUEZ JOSÉ ANTONIO SERRA PÉREZ Unit 1.MaNoTaS 1 Definitions (I) Description A computer is: A
Content Delivery Network (CDN) and P2P Model
 A multi-agent algorithm to improve content management in CDN networks Agostino Forestiero, forestiero@icar.cnr.it Carlo Mastroianni, mastroianni@icar.cnr.it ICAR-CNR Institute for High Performance Computing
A multi-agent algorithm to improve content management in CDN networks Agostino Forestiero, forestiero@icar.cnr.it Carlo Mastroianni, mastroianni@icar.cnr.it ICAR-CNR Institute for High Performance Computing
Course on Advanced Computer Architectures
 Course on Advanced Computer Architectures Surname (Cognome) Name (Nome) POLIMI ID Number Signature (Firma) SOLUTION Politecnico di Milano, September 3rd, 2015 Prof. C. Silvano EX1A ( 2 points) EX1B ( 2
Course on Advanced Computer Architectures Surname (Cognome) Name (Nome) POLIMI ID Number Signature (Firma) SOLUTION Politecnico di Milano, September 3rd, 2015 Prof. C. Silvano EX1A ( 2 points) EX1B ( 2
4511 MODBUS RTU. Configuration Manual. HART transparent driver. No. 9107MCM100(1328)
 4511 MODBUS RTU Configuration Manual HART transparent driver No. 9107MCM100(1328) 9107 CONTENTS Introduction... 3 Modbus basics... 3 Modbus RTU... 3 Supported Function Codes... 3 Modbus Parameters and
4511 MODBUS RTU Configuration Manual HART transparent driver No. 9107MCM100(1328) 9107 CONTENTS Introduction... 3 Modbus basics... 3 Modbus RTU... 3 Supported Function Codes... 3 Modbus Parameters and
ECE 451 Verilog Exercises. Sept 14, 2007. James Barnes (James.Barnes@colostate.edu)
 ECE 451 Verilog Exercises Sept 14, 2007 James Barnes (James.Barnes@colostate.edu) Organization These slides give a series of self-paced exercises. Read the specification of each exercise and write your
ECE 451 Verilog Exercises Sept 14, 2007 James Barnes (James.Barnes@colostate.edu) Organization These slides give a series of self-paced exercises. Read the specification of each exercise and write your
OUTILS DE DÉMONSTRATION
 OUTILS DE DÉMONSTRATION AUTOMATIQUE ET PREUVE DE CIRCUITS ÉLECTRONIQUES Laurence Pierre Laboratoire TIMA, Grenoble PREAMBLE Design/validation of embedded applications: Design/validation for the system
OUTILS DE DÉMONSTRATION AUTOMATIQUE ET PREUVE DE CIRCUITS ÉLECTRONIQUES Laurence Pierre Laboratoire TIMA, Grenoble PREAMBLE Design/validation of embedded applications: Design/validation for the system
A simple algorithm with no simple verication
 A simple algorithm with no simple verication Laszlo Csirmaz Central European University Abstract The correctness of a simple sorting algorithm is resented, which algorithm is \evidently wrong" at the rst
A simple algorithm with no simple verication Laszlo Csirmaz Central European University Abstract The correctness of a simple sorting algorithm is resented, which algorithm is \evidently wrong" at the rst
Interfacing With Microprocessor
 MICROPROCESSOR BASED SOLAR TRACKING SYSTEM USING STEPPER MOTOR Jyotirmay Gadewadikar B. E. Final Year (Electronics), S.G.S. Institute of Tech. & Science, Indore This project uses a stepper motor to control
MICROPROCESSOR BASED SOLAR TRACKING SYSTEM USING STEPPER MOTOR Jyotirmay Gadewadikar B. E. Final Year (Electronics), S.G.S. Institute of Tech. & Science, Indore This project uses a stepper motor to control
Memory Elements. Combinational logic cannot remember
 Memory Elements Combinational logic cannot remember Output logic values are function of inputs only Feedback is needed to be able to remember a logic value Memory elements are needed in most digital logic
Memory Elements Combinational logic cannot remember Output logic values are function of inputs only Feedback is needed to be able to remember a logic value Memory elements are needed in most digital logic
Instruction Set Architecture. or How to talk to computers if you aren t in Star Trek
 Instruction Set Architecture or How to talk to computers if you aren t in Star Trek The Instruction Set Architecture Application Compiler Instr. Set Proc. Operating System I/O system Instruction Set Architecture
Instruction Set Architecture or How to talk to computers if you aren t in Star Trek The Instruction Set Architecture Application Compiler Instr. Set Proc. Operating System I/O system Instruction Set Architecture
6.830 Lecture 3 9.16.2015 PS1 Due Next Time (Tuesday!) Lab 1 Out today start early! Relational Model Continued, and Schema Design and Normalization
 6.830 Lecture 3 9.16.2015 PS1 Due Next Time (Tuesday!) Lab 1 Out today start early! Relational Model Continued, and Schema Design and Normalization Animals(name,age,species,cageno,keptby,feedtime) Keeper(id,name)
6.830 Lecture 3 9.16.2015 PS1 Due Next Time (Tuesday!) Lab 1 Out today start early! Relational Model Continued, and Schema Design and Normalization Animals(name,age,species,cageno,keptby,feedtime) Keeper(id,name)
SAP PPM Portfolio Analysis Dashboard
 SAP PPM Portfolio Analysis Dashboard A PPM Consulting Solution SAP PPM Portfolio Analysis Dashboard A number of portfolio management process steps require in detail information to execute a reliable comparison
SAP PPM Portfolio Analysis Dashboard A PPM Consulting Solution SAP PPM Portfolio Analysis Dashboard A number of portfolio management process steps require in detail information to execute a reliable comparison
 More on Pipelining and Pipelines in Real Machines CS 333 Fall 2006 Main Ideas Data Hazards RAW WAR WAW More pipeline stall reduction techniques Branch prediction» static» dynamic bimodal branch prediction
More on Pipelining and Pipelines in Real Machines CS 333 Fall 2006 Main Ideas Data Hazards RAW WAR WAW More pipeline stall reduction techniques Branch prediction» static» dynamic bimodal branch prediction
NetFlow probe on NetFPGA
 Verze #1.00, 2008-12-12 NetFlow probe on NetFPGA Introduction With ever-growing volume of data being transferred over the Internet, the need for reliable monitoring becomes more urgent. Monitoring devices
Verze #1.00, 2008-12-12 NetFlow probe on NetFPGA Introduction With ever-growing volume of data being transferred over the Internet, the need for reliable monitoring becomes more urgent. Monitoring devices
16-bit ALU, Register File and Memory Write Interface
 CS M152B Fall 2002 Project 2 16-bit ALU, Register File and Memory Write Interface Suggested Due Date: Monday, October 21, 2002 Actual Due Date determined by your Lab TA This project will take much longer
CS M152B Fall 2002 Project 2 16-bit ALU, Register File and Memory Write Interface Suggested Due Date: Monday, October 21, 2002 Actual Due Date determined by your Lab TA This project will take much longer
The Big Picture. Cache Memory CSE 675.02. Memory Hierarchy (1/3) Disk
 The Big Picture Cache Memory CSE 5.2 Computer Processor Memory (active) (passive) Control (where ( brain ) programs, Datapath data live ( brawn ) when running) Devices Input Output Keyboard, Mouse Disk,
The Big Picture Cache Memory CSE 5.2 Computer Processor Memory (active) (passive) Control (where ( brain ) programs, Datapath data live ( brawn ) when running) Devices Input Output Keyboard, Mouse Disk,
Preface. Any questions from last time? A bit more motivation, information about me. A bit more about this class. Later: Will review 1st 22 slides
 Preface Any questions from last time? Will review 1st 22 slides A bit more motivation, information about me Research ND A bit more about this class Microsoft Later: HW 1 Review session MD McNally about
Preface Any questions from last time? Will review 1st 22 slides A bit more motivation, information about me Research ND A bit more about this class Microsoft Later: HW 1 Review session MD McNally about
Software Pipelining. for (i=1, i<100, i++) { x := A[i]; x := x+1; A[i] := x
![Software Pipelining. for (i=1, i<100, i++) { x := A[i]; x := x+1; A[i] := x Software Pipelining. for (i=1, i<100, i++) { x := A[i]; x := x+1; A[i] := x](/thumbs/25/6459870.jpg) Software Pipelining for (i=1, i
Software Pipelining for (i=1, i
Sistemas Digitais I LESI - 2º ano
 Sistemas Digitais I LESI - 2º ano Lesson 6 - Combinational Design Practices Prof. João Miguel Fernandes (miguel@di.uminho.pt) Dept. Informática UNIVERSIDADE DO MINHO ESCOLA DE ENGENHARIA - PLDs (1) - The
Sistemas Digitais I LESI - 2º ano Lesson 6 - Combinational Design Practices Prof. João Miguel Fernandes (miguel@di.uminho.pt) Dept. Informática UNIVERSIDADE DO MINHO ESCOLA DE ENGENHARIA - PLDs (1) - The
EECS 427 RISC PROCESSOR
 RISC PROCESSOR ISA FOR EECS 427 PROCESSOR ImmHi/ ImmLo/ OP Code Rdest OP Code Ext Rsrc Mnemonic Operands 15-12 11-8 7-4 3-0 Notes (* is Baseline) ADD Rsrc, Rdest 0000 Rdest 0101 Rsrc * ADDI Imm, Rdest
RISC PROCESSOR ISA FOR EECS 427 PROCESSOR ImmHi/ ImmLo/ OP Code Rdest OP Code Ext Rsrc Mnemonic Operands 15-12 11-8 7-4 3-0 Notes (* is Baseline) ADD Rsrc, Rdest 0000 Rdest 0101 Rsrc * ADDI Imm, Rdest
A new approach for dynamic optimization of water flooding problems
 A new approach for dynamic optimization of water flooding problems Rolf J. Lorentzen Aina M. Berg Geir Nævdal Erlend H. Vefring IRIS International Research Institute of Stavanger (formerly Rogaland Research)
A new approach for dynamic optimization of water flooding problems Rolf J. Lorentzen Aina M. Berg Geir Nævdal Erlend H. Vefring IRIS International Research Institute of Stavanger (formerly Rogaland Research)
1 Introduction to Matrices
 1 Introduction to Matrices In this section, important definitions and results from matrix algebra that are useful in regression analysis are introduced. While all statements below regarding the columns
1 Introduction to Matrices In this section, important definitions and results from matrix algebra that are useful in regression analysis are introduced. While all statements below regarding the columns
Automata-based Verification - I
 CS3172: Advanced Algorithms Automata-based Verification - I Howard Barringer Room KB2.20: email: howard.barringer@manchester.ac.uk March 2006 Supporting and Background Material Copies of key slides (already
CS3172: Advanced Algorithms Automata-based Verification - I Howard Barringer Room KB2.20: email: howard.barringer@manchester.ac.uk March 2006 Supporting and Background Material Copies of key slides (already
Coding techniques for failure recovery in a distributive modular memory organization
 Coding techniques for failure recovery in a distributive modular memory organization by S. A. SZYGENDA Southern M ethodist University Dallas, Texas and M. J. FLYNN T
Coding techniques for failure recovery in a distributive modular memory organization by S. A. SZYGENDA Southern M ethodist University Dallas, Texas and M. J. FLYNN T
IEEE 802.11 frame format
 IEEE 802.11 frame format Pietro Nicoletti www.studioreti.it 802-11-Frame - 1 P. Nicoletti: see note pag. 2 Copyright note These slides are protected by copyright and international treaties. The title and
IEEE 802.11 frame format Pietro Nicoletti www.studioreti.it 802-11-Frame - 1 P. Nicoletti: see note pag. 2 Copyright note These slides are protected by copyright and international treaties. The title and
Exceptions in MIPS. know the exception mechanism in MIPS be able to write a simple exception handler for a MIPS machine
 7 Objectives After completing this lab you will: know the exception mechanism in MIPS be able to write a simple exception handler for a MIPS machine Introduction Branches and jumps provide ways to change
7 Objectives After completing this lab you will: know the exception mechanism in MIPS be able to write a simple exception handler for a MIPS machine Introduction Branches and jumps provide ways to change
Lecture 4: Binary. CS442: Great Insights in Computer Science Michael L. Littman, Spring 2006. I-Before-E, Continued
 Lecture 4: Binary CS442: Great Insights in Computer Science Michael L. Littman, Spring 26 I-Before-E, Continued There are two ideas from last time that I d like to flesh out a bit more. This time, let
Lecture 4: Binary CS442: Great Insights in Computer Science Michael L. Littman, Spring 26 I-Before-E, Continued There are two ideas from last time that I d like to flesh out a bit more. This time, let
Programmer s Model = model of µc useful to view hardware during execution of software instructions
 HC12/S12 Programmer s Model Programmer s Model = model of µc useful to view hardware during execution of software instructions Recall: General Microcontroller/Computer Architecture note: Control Unit &
HC12/S12 Programmer s Model Programmer s Model = model of µc useful to view hardware during execution of software instructions Recall: General Microcontroller/Computer Architecture note: Control Unit &
(Unit) Testing ios Apps. Paweł Dudek
 (Unit) Testing ios Apps Paweł Dudek 1 Why do we want to write tests? 2 Reasons for testing Striving for better software Leads to better, more modularized codebase Faster development cycles Being confident
(Unit) Testing ios Apps Paweł Dudek 1 Why do we want to write tests? 2 Reasons for testing Striving for better software Leads to better, more modularized codebase Faster development cycles Being confident
DELL. Virtual Desktop Infrastructure Study END-TO-END COMPUTING. Dell Enterprise Solutions Engineering
 DELL Virtual Desktop Infrastructure Study END-TO-END COMPUTING Dell Enterprise Solutions Engineering 1 THIS WHITE PAPER IS FOR INFORMATIONAL PURPOSES ONLY, AND MAY CONTAIN TYPOGRAPHICAL ERRORS AND TECHNICAL
DELL Virtual Desktop Infrastructure Study END-TO-END COMPUTING Dell Enterprise Solutions Engineering 1 THIS WHITE PAPER IS FOR INFORMATIONAL PURPOSES ONLY, AND MAY CONTAIN TYPOGRAPHICAL ERRORS AND TECHNICAL
S / RA / EXT / HEFS / 35 EXTENT MAP FLOOD EXTENT TIDAL FLOODING RURAL AREA HIGH END FUTURE SCENARIO. Location Plan :
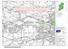 Government of Osi permit number EN-- NOTE : MORE DETAILED MAPS SHOWING COMBINED TIDAL AND FLUVIAL FLOOD HAZARD FOR THIS AREA HAVE BEEN PREPARED UNDER THE LEE CFRAM STUDY. PLEASE REFER TO WWW.LEECFRAMS.IE
Government of Osi permit number EN-- NOTE : MORE DETAILED MAPS SHOWING COMBINED TIDAL AND FLUVIAL FLOOD HAZARD FOR THIS AREA HAVE BEEN PREPARED UNDER THE LEE CFRAM STUDY. PLEASE REFER TO WWW.LEECFRAMS.IE
Memory Basics. SRAM/DRAM Basics
 Memory Basics RAM: Random Access Memory historically defined as memory array with individual bit access refers to memory with both Read and Write capabilities ROM: Read Only Memory no capabilities for
Memory Basics RAM: Random Access Memory historically defined as memory array with individual bit access refers to memory with both Read and Write capabilities ROM: Read Only Memory no capabilities for
Windows 7 XP Mode Application Note
 17741 Mitchell North, Irvine, CA 92614 USA Tel: 949-833-3355 Fax: 949-833-0322 http://www.genovation.com support@genovation.com Windows 7 XP Mode Application Note Using a MiniTerm with Legacy Software
17741 Mitchell North, Irvine, CA 92614 USA Tel: 949-833-3355 Fax: 949-833-0322 http://www.genovation.com support@genovation.com Windows 7 XP Mode Application Note Using a MiniTerm with Legacy Software
Application Note. Introduction AN2471/D 3/2003. PC Master Software Communication Protocol Specification
 Application Note 3/2003 PC Master Software Communication Protocol Specification By Pavel Kania and Michal Hanak S 3 L Applications Engineerings MCSL Roznov pod Radhostem Introduction The purpose of this
Application Note 3/2003 PC Master Software Communication Protocol Specification By Pavel Kania and Michal Hanak S 3 L Applications Engineerings MCSL Roznov pod Radhostem Introduction The purpose of this
Continuous Auditing in Big Data Computing Environments: Towards an Integrated Audit Approach by Using CAATTs
 Continuous Auditing in Big Data Computing Environments: Towards an Integrated Audit Approach by Using CAATTs Andreas Kiesow, Novica Zarvić, Oliver Thomas Stuttgart, 23.09.2014 Management komplexer IT-Systeme
Continuous Auditing in Big Data Computing Environments: Towards an Integrated Audit Approach by Using CAATTs Andreas Kiesow, Novica Zarvić, Oliver Thomas Stuttgart, 23.09.2014 Management komplexer IT-Systeme
Using Graphics and Animation to Visualize Instruction Pipelining and its Hazards
 Using Graphics and Animation to Visualize Instruction Pipelining and its Hazards Per Stenström, Håkan Nilsson, and Jonas Skeppstedt Department of Computer Engineering, Lund University P.O. Box 118, S-221
Using Graphics and Animation to Visualize Instruction Pipelining and its Hazards Per Stenström, Håkan Nilsson, and Jonas Skeppstedt Department of Computer Engineering, Lund University P.O. Box 118, S-221
ENHANCEMENTS TO SQL SERVER COLUMN STORES. Anuhya Mallempati #2610771
 ENHANCEMENTS TO SQL SERVER COLUMN STORES Anuhya Mallempati #2610771 CONTENTS Abstract Introduction Column store indexes Batch mode processing Other Enhancements Conclusion ABSTRACT SQL server introduced
ENHANCEMENTS TO SQL SERVER COLUMN STORES Anuhya Mallempati #2610771 CONTENTS Abstract Introduction Column store indexes Batch mode processing Other Enhancements Conclusion ABSTRACT SQL server introduced
Model Checking: An Introduction
 Announcements Model Checking: An Introduction Meeting 2 Office hours M 1:30pm-2:30pm W 5:30pm-6:30pm (after class) and by appointment ECOT 621 Moodle problems? Fundamentals of Programming Languages CSCI
Announcements Model Checking: An Introduction Meeting 2 Office hours M 1:30pm-2:30pm W 5:30pm-6:30pm (after class) and by appointment ECOT 621 Moodle problems? Fundamentals of Programming Languages CSCI
Lab Work 2. MIPS assembly and introduction to PCSpim
 Lab Work 2. MIPS assembly and introduction to PCSpim The goal of this work is for the student to become familiar with the data types and the programming in assembly (MIPS32). To realize this lab work you
Lab Work 2. MIPS assembly and introduction to PCSpim The goal of this work is for the student to become familiar with the data types and the programming in assembly (MIPS32). To realize this lab work you
A Static Analyzer for Large Safety-Critical Software. Considered Programs and Semantics. Automatic Program Verification by Abstract Interpretation
 PLDI 03 A Static Analyzer for Large Safety-Critical Software B. Blanchet, P. Cousot, R. Cousot, J. Feret L. Mauborgne, A. Miné, D. Monniaux,. Rival CNRS École normale supérieure École polytechnique Paris
PLDI 03 A Static Analyzer for Large Safety-Critical Software B. Blanchet, P. Cousot, R. Cousot, J. Feret L. Mauborgne, A. Miné, D. Monniaux,. Rival CNRS École normale supérieure École polytechnique Paris
Review: MIPS Addressing Modes/Instruction Formats
 Review: Addressing Modes Addressing mode Example Meaning Register Add R4,R3 R4 R4+R3 Immediate Add R4,#3 R4 R4+3 Displacement Add R4,1(R1) R4 R4+Mem[1+R1] Register indirect Add R4,(R1) R4 R4+Mem[R1] Indexed
Review: Addressing Modes Addressing mode Example Meaning Register Add R4,R3 R4 R4+R3 Immediate Add R4,#3 R4 R4+3 Displacement Add R4,1(R1) R4 R4+Mem[1+R1] Register indirect Add R4,(R1) R4 R4+Mem[R1] Indexed
Business Scenario Using GP/Web Dynpro with Back and Forth 3 Level Process and Dynamic Approvers in a Loop
 Business Scenario Using GP/Web Dynpro with Back and Forth 3 Level Process and Dynamic Approvers in a Loop Applies to This Article applies to Guided Procedures, Web Dynpro Java, Business Process Modeling
Business Scenario Using GP/Web Dynpro with Back and Forth 3 Level Process and Dynamic Approvers in a Loop Applies to This Article applies to Guided Procedures, Web Dynpro Java, Business Process Modeling
Robotstudio Offline Visual Programming & Simulation Tool
 Robotstudio Offline Visual Programming & Simulation Tool Akbar F. Moghaddam (Shahab) M.Sc. Of Robotics & Intelligent Systems ROBIN, UiO Robot Engineer, Norsk Titanium Components Chairman, Robotica Osloensis
Robotstudio Offline Visual Programming & Simulation Tool Akbar F. Moghaddam (Shahab) M.Sc. Of Robotics & Intelligent Systems ROBIN, UiO Robot Engineer, Norsk Titanium Components Chairman, Robotica Osloensis
Using Expert Systems for Simulation Modeling of Patient Scheduling
 Grand Valley State University ScholarWorks@GVSU Peer Reviewed Articles School of Engineering 9-1-2000 Using Expert Systems for Simulation Modeling of Patient Scheduling Charles R. Standridge Grand Valley
Grand Valley State University ScholarWorks@GVSU Peer Reviewed Articles School of Engineering 9-1-2000 Using Expert Systems for Simulation Modeling of Patient Scheduling Charles R. Standridge Grand Valley
Giving credit where credit is due
 CSCE 230J Computer Organization Processor Architecture VI: Wrap-Up Dr. Steve Goddard goddard@cse.unl.edu http://cse.unl.edu/~goddard/courses/csce230j Giving credit where credit is due ost of slides for
CSCE 230J Computer Organization Processor Architecture VI: Wrap-Up Dr. Steve Goddard goddard@cse.unl.edu http://cse.unl.edu/~goddard/courses/csce230j Giving credit where credit is due ost of slides for
20 Saving Device Data Backup
 20 Saving Device Data Backup 20.1 Try to Save Device Data Backup...20-2 20.2 Setting Guide...20-6 20-1 Try to Save Device Data Backup 20.1 Try to Save Device Data Backup The device data in Device/PLC can
20 Saving Device Data Backup 20.1 Try to Save Device Data Backup...20-2 20.2 Setting Guide...20-6 20-1 Try to Save Device Data Backup 20.1 Try to Save Device Data Backup The device data in Device/PLC can
Relational Databases
 Relational Databases Jan Chomicki University at Buffalo Jan Chomicki () Relational databases 1 / 18 Relational data model Domain domain: predefined set of atomic values: integers, strings,... every attribute
Relational Databases Jan Chomicki University at Buffalo Jan Chomicki () Relational databases 1 / 18 Relational data model Domain domain: predefined set of atomic values: integers, strings,... every attribute
Fairness in Routing and Load Balancing
 Fairness in Routing and Load Balancing Jon Kleinberg Yuval Rabani Éva Tardos Abstract We consider the issue of network routing subject to explicit fairness conditions. The optimization of fairness criteria
Fairness in Routing and Load Balancing Jon Kleinberg Yuval Rabani Éva Tardos Abstract We consider the issue of network routing subject to explicit fairness conditions. The optimization of fairness criteria
THUMB Instruction Set
 5 THUMB Instruction Set This chapter describes the THUMB instruction set. Format Summary 5-2 Opcode Summary 5-3 5. Format : move shifted register 5-5 5.2 Format 2: add/subtract 5-7 5.3 Format 3: move/compare/add/subtract
5 THUMB Instruction Set This chapter describes the THUMB instruction set. Format Summary 5-2 Opcode Summary 5-3 5. Format : move shifted register 5-5 5.2 Format 2: add/subtract 5-7 5.3 Format 3: move/compare/add/subtract
STATUS REPORT ON MAUDE-NPA TOOL
 STATUS REPORT ON MAUDE-NPA TOOL Catherine Meadows Santiago Escobar Jose Meseguer September 28, 2006 1 GOAL Extend standard free algebra model of crypto protocol analysis to deal with algebraic properties
STATUS REPORT ON MAUDE-NPA TOOL Catherine Meadows Santiago Escobar Jose Meseguer September 28, 2006 1 GOAL Extend standard free algebra model of crypto protocol analysis to deal with algebraic properties
Testing high-power hydraulic pumps with NI LabVIEW (RT) and the StateChart module. Jeffrey Habets & Roger Custers www.vi-tech.nl
 Testing high-power hydraulic pumps with NI LabVIEW (RT) and the StateChart module Jeffrey Habets & Roger Custers www.vi-tech.nl Agenda Introduction to the teststand The challenge New setup system overview
Testing high-power hydraulic pumps with NI LabVIEW (RT) and the StateChart module Jeffrey Habets & Roger Custers www.vi-tech.nl Agenda Introduction to the teststand The challenge New setup system overview
Data Link Layer(1) Principal service: Transferring data from the network layer of the source machine to the one of the destination machine
 Data Link Layer(1) Principal service: Transferring data from the network layer of the source machine to the one of the destination machine Virtual communication versus actual communication: Specific functions
Data Link Layer(1) Principal service: Transferring data from the network layer of the source machine to the one of the destination machine Virtual communication versus actual communication: Specific functions
Architecture bits. (Chromosome) (Evolved chromosome) Downloading. Downloading PLD. GA operation Architecture bits
 A Pattern Recognition System Using Evolvable Hardware Masaya Iwata 1 Isamu Kajitani 2 Hitoshi Yamada 2 Hitoshi Iba 1 Tetsuya Higuchi 1 1 1-1-4,Umezono,Tsukuba,Ibaraki,305,Japan Electrotechnical Laboratory
A Pattern Recognition System Using Evolvable Hardware Masaya Iwata 1 Isamu Kajitani 2 Hitoshi Yamada 2 Hitoshi Iba 1 Tetsuya Higuchi 1 1 1-1-4,Umezono,Tsukuba,Ibaraki,305,Japan Electrotechnical Laboratory
Switching Regulator IC Series Inductor Calculation for Buck Converter IC
 Switching Regulator C Series nductor Calculation for Buck Converter C No.107ECY01 This application note covers the steps required in choosing the inductor and to calculate the value used in buck regulator
Switching Regulator C Series nductor Calculation for Buck Converter C No.107ECY01 This application note covers the steps required in choosing the inductor and to calculate the value used in buck regulator
A Unified View of Virtual Machines
 A Unified View of Virtual Machines First ACM/USENIX Conference on Virtual Execution Environments J. E. Smith June 2005 Introduction Why are virtual machines interesting? They allow transcending of interfaces
A Unified View of Virtual Machines First ACM/USENIX Conference on Virtual Execution Environments J. E. Smith June 2005 Introduction Why are virtual machines interesting? They allow transcending of interfaces
CNES fault tolerant architectures intended for electronic COTS components in space applications
 4ème Atelier Thématique du RIS Nlles architectures & techno des processeurs et SdF Aix-en-Provence 20 novembre 2002 CNES fault tolerant architectures intended for electronic COTS components in space applications
4ème Atelier Thématique du RIS Nlles architectures & techno des processeurs et SdF Aix-en-Provence 20 novembre 2002 CNES fault tolerant architectures intended for electronic COTS components in space applications
Lua as a business logic language in high load application. Ilya Martynov ilya@iponweb.net CTO at IPONWEB
 Lua as a business logic language in high load application Ilya Martynov ilya@iponweb.net CTO at IPONWEB Company background Ad industry Custom development Technical platform with multiple components Custom
Lua as a business logic language in high load application Ilya Martynov ilya@iponweb.net CTO at IPONWEB Company background Ad industry Custom development Technical platform with multiple components Custom
Resource Dashboard. Portfolio and Project Management. A PLM Consulting Solution. Public
 Portfolio and Project Management A PLM Consulting Solution The PPM Consulting Solution allows you to manage you resources efficiently. It shows business partner availability, role demand and staffing,
Portfolio and Project Management A PLM Consulting Solution The PPM Consulting Solution allows you to manage you resources efficiently. It shows business partner availability, role demand and staffing,
An Architecture for Concurrent Future Networks
 An Architecture for Concurrent Future Networks Future Internet 2008 Karlsruhe, 11.11.2008 Lars Völker, Denis Martin, Ibtissam El Khayat, Christoph Werle, Martina Zitterbart (Universität Karlsruhe (TH)
An Architecture for Concurrent Future Networks Future Internet 2008 Karlsruhe, 11.11.2008 Lars Völker, Denis Martin, Ibtissam El Khayat, Christoph Werle, Martina Zitterbart (Universität Karlsruhe (TH)
types, but key declarations and constraints Similar CREATE X commands for other schema ëdrop X name" deletes the created element of beer VARCHARè20è,
 Dening a Database Schema CREATE TABLE name èlist of elementsè. Principal elements are attributes and their types, but key declarations and constraints also appear. Similar CREATE X commands for other schema
Dening a Database Schema CREATE TABLE name èlist of elementsè. Principal elements are attributes and their types, but key declarations and constraints also appear. Similar CREATE X commands for other schema
CSE 141L Computer Architecture Lab Fall 2003. Lecture 2
 CSE 141L Computer Architecture Lab Fall 2003 Lecture 2 Pramod V. Argade CSE141L: Computer Architecture Lab Instructor: TA: Readers: Pramod V. Argade (p2argade@cs.ucsd.edu) Office Hour: Tue./Thu. 9:30-10:30
CSE 141L Computer Architecture Lab Fall 2003 Lecture 2 Pramod V. Argade CSE141L: Computer Architecture Lab Instructor: TA: Readers: Pramod V. Argade (p2argade@cs.ucsd.edu) Office Hour: Tue./Thu. 9:30-10:30
Ericsson T18s Voice Dialing Simulator
 Ericsson T18s Voice Dialing Simulator Mauricio Aracena Kovacevic, Anna Dehlbom, Jakob Ekeberg, Guillaume Gariazzo, Eric Lästh and Vanessa Troncoso Dept. of Signals Sensors and Systems Royal Institute of
Ericsson T18s Voice Dialing Simulator Mauricio Aracena Kovacevic, Anna Dehlbom, Jakob Ekeberg, Guillaume Gariazzo, Eric Lästh and Vanessa Troncoso Dept. of Signals Sensors and Systems Royal Institute of
Lab 10.4.1 IP Addressing Overview
 Lab 10.4.1 IP ing Overview Estimated time: 30 min. Objectives: Background: This lab will focus on your ability to accomplish the following tasks: Name the five different classes of IP addresses Describe
Lab 10.4.1 IP ing Overview Estimated time: 30 min. Objectives: Background: This lab will focus on your ability to accomplish the following tasks: Name the five different classes of IP addresses Describe
Microprocessor and Microcontroller Architecture
 Microprocessor and Microcontroller Architecture 1 Von Neumann Architecture Stored-Program Digital Computer Digital computation in ALU Programmable via set of standard instructions input memory output Internal
Microprocessor and Microcontroller Architecture 1 Von Neumann Architecture Stored-Program Digital Computer Digital computation in ALU Programmable via set of standard instructions input memory output Internal

