Do any six problems. Write your answers clearly and neatly. Use the back if necessary.
|
|
|
- Beryl Richards
- 7 years ago
- Views:
Transcription
1 CS5003 Foundations of C.S. Spring, 2016 Final Exam PRINT NAME: SIGN : Do any six problems. Write your answers clearly and neatly. Use the back if necessary. 1. Let L {a, b, c} be the language with definition L = {a 2n b m c 3k {a, b, c} 0 n, 0 m 2, 0 k}. a) Give a recursive definition of L. b) Compute L 3 according to your definition. c) Construct a context free grammar G which realizes L. d) Prove that L = L(G). BASIS: λ, b, b 2 L RECURSIVE STEP: u L a 2 u, uc 3 L. CLOSURE: All elements in the language can be obtained from the basis with a finite number of applications of the recursive step. With this definition: L 3 = {λ, b, b 2, a 2, a 2 b, a 2 b 2, a 4, a 4 b, a 4 b 2, a 6, a 6 b, a 6 b 2, c 3, bc 3, b 2 c 3, a 2 c 3, a 2 bc 3, a 2 b 2 c 3, a 4 c 3, a 4 bc 3, a 4 b 2 c 3, c 6, bc 6, b 2 c 6, a 2 c 6, a 2 bc 6, a 2 b 2 c 6, c 9, bc 9, b 2 c 9 }. G : S a 2 S Sc 3 a 2 a λ Proof: L L(G): Let a 2n b m c 3k L. A derivation sequence is S n a 2n S k a 2n Sc 3k a 2n b m c 3k L(G) L: We show that the set of sentential forms is contained in X = {a 2n Sc 3k, a 2n b m c 3k } with n, k 0 and m {0, 1, 2}. by induction on the number of rules applied. Base case: No rules applied. Sentential form is S X with n = k = 0, so base case is satisfied. Inductive step: Suppose after j rules the a sentential form is of form a 2n Sc 3k or a 2n b m c 3k. For the second, no rule applies so there is nothing to show. For the first, we get a 2(n+1) Sc 3k, a 2n Sc 3(k+1) a 2n c 3k a 2n bc 3k or a 2n b 2 c 3k depending on which S rules we use, and all are in X, as required. Since X contains all sentential forms, L(G) L. 1 of 7
2 2. Give regular expressions for each of the following subsets of {a, b, c}. a) Strings with an even number of b s. : Looking from left to right, the b s come in pairs, with perhaps a s in between. (b(a c) b) (a c)) b) strings which either start with a or have an even number of letters. : Simple with the union [a(a b c) ] [((a b c) 2 ) ] c) All strings not containing aaa. : More than two a s must be separated by non-a s. First, such strings that start and end with a. (a a 2 )((b c) + (a a 2 )) Then we add the possibility that it starts or ends with b, or has no a s at all. [(b c) (a a 2 )((b c) + (a a 2 )) (b c) ] (b c) 2 of 7
3 3. Let L {a, b, c} be given by BASIS: λ L RECURSIVE STEP: If u L then aub L, a 2 uc 2 L, and a 2 uc 3 L 2. CLOSURE: A string is in L if if can be obtained from the basis by a finite number of applications of the recursive step. Prove by induction that for all w L, n a (w) n b (w) + n c (w) 2n a (w). : Proof. We will prove the statement by induction on the number of steps in the recursive definition of w L. Base Case: Suppose w L 0. Then w = λ and n a (w) = n b (w) = n b (w) = 0, and the statement is true. Inductive step. Suppose for all w L k and n a (w) n b (w) + n c (w) 2n a (w). The element in L k+1 are of the form awb, a 2 wc 2, or a 2 wc 3 We have n a (awb) = n a (w) + 1, n b (awb) = n b (w) + 1, n c (awb) = n c (w), so n a (awb) = n a (w) + 1 n b (w) + n c (w) + 1 = (n b (w) + 1) + n c (w) = n b (awb) + n c (awb) and n b (awb) + n c (awb) = n b (w) + n c (w) + 1 2n a (w) + 1 2n a (w) + 2 = 2n a (awb) as required. Next n a (a 2 wc 2 ) = n a (w) + 2, n b (a 2 wc 2 ) = n b (w), n c (a 2 wc 2 ) = n c (w) + 2, so and n a (a 2 wc 2 ) = n a (w) + 2 n b (w) + n c (w) + 2 = n b (a 2 wc 2 ) + n c (a 2 wc 2 ) n b (a 2 wb 2 ) + n c (a 2 wb 2 ) = n b (w) + n c (w) + 2 2n a (w) + 2 2n a (w) + 4 = 2n a (a 2 wc 2 ) as required. Last n a (a 2 wc 3 ) = n a (w) + 2, n b (a 2 wc 2 ) = n b (w), n c (a 2 wc 3 ) = n c (w) + 3, so n a (a 2 wc 3 ) = n a (w) + 2 n b (w) + n c (w) + 2 n b (w) + n c (w) + 3 = n b (a 2 wc 3 ) + n c (a 2 wc 3 ) and n b (a 2 wc 3 )+n c (awb) = n b (w)+n c (w)+3 2n a (w)+3 2n a (w)+3 2n a (w)+4 = 2n a (a 2 wc 3 ) as required. So the inequality is satisfied in every case, and so is true for all w L by induction. 3 of 7
4 4. Let L be the language consisting of those strings in {a, b, c} which begin with an a, contain exactly two b s and end with cc. Construct a Deterministic Finite Automaton which recognizes this language. 5. Let L be the language on Σ = {a, b, c, d} of all strings which either contain the substring bad or the substring baaad. Construct an Automaton, deterministic or not, which recognizes this language. Non-deterministic is much easier. 4 of 7
5 6. Let G be the grammar given by G : S S AB λ A aaabc ABC a B BCA b C bbcc λ Convert this grammar to Chomsky Normal Form. First note that the rule S S is useless and can be omitted. Second, the fact that C is nullable must be rectified: G : S AB λ A aaabc aaab ABC AB a B BCA BA b C bbcc bbc Lastly we perform our splitting moves: note that the duplicated rules from the nullity moves don t need to be done completely separated. G : S AB λ A U a A 1 AA 3 AB a A 1 AA 2 A 2 U a A 3 UaB A 3 BC B BB 1 BA b B 1 CA C U b C 1 C 1 BC 2 BU c C 2 U c C U a a U b b U c c 5 of 7
6 7. a) Let G be the grammar given by G : S A B A aa B C B bbb C D C cccc D a D λ ABC Construct an equivalent grammar which does not contain chain rules. Clearly CHAIN(S) = {S, A, B, C, D}, CHAIN(A) = {A, B, C, D}, CHAIN(B) = {B, C, D}, CHAIN(C) = {C, D}, CHAIN(D) = {D}, b) For the grammar G : S aa bbb cccc a λ ABC A aa bbb cccc a λ ABC B bbb cccc a λ ABC C cccc a λ ABC D λ ABC G : S ABE ADE EA A aa ae B BDB BBDD C BD AD b D BDD BB EE CC E BD AD b Construct REACH and TERM in the correct order are remove the useless symbols T ERM 0 = {C, E}, T ERM 1 = {A, C, D, E}, T ERM = T ERM 2 = {S, A, C, D, E}, so S T ERM and the language is non-empty. Also B is useless and can be removed: G : S ADE EA A aa ae C AD b D EE CC E AD b Now REACH 0 = {S}, REACH 1 = {S, A, D, E} and REACH = REACH 2 = {S, A, C, D, E} so all symbols are now reachable and terminable. Although this was not asked, and is not specified in the definition of useless, C and E are now exactly the same, so one of them is useless and can be replaced with the other. Also now D must be replace by CC, so is also useless. G : S ACCC CA A aa ac C ACC b 6 of 7
7 8. For the grammar G : S AB A AB DA a B BC DB b C CA DC c D DA DD a b c a) Trace the CYK algorithm to decide if cabbc is in the language. (Obviously the longest problem, by far. Most students chose it anyway. Why?) S, A, B, CD S, A, B, C, D S, A, B, C, D S, A, B, C, D S, A, D B, C, D A, C, D S, A, B, D B, D BCD C, D A, D B, D B, D C, D This was easy to fill out for the opposite reason than the quiz example, instead of many s, the are many {S, A, B, C, D} s. b) Convert to Greibach Normal Form. (also use the back of this page.) The grammar is already in Chomsky Normal Form and is already ordered for S < A < B < C < D. We can remove left recursion on D, put it in compliance, and remove the initial D s right away. G : S AB A AB aa ba ca ar d A br d A cr d A a B BC ab bb cb ar d B br d B cr d B b C CA ac bc cc ar d C br d C cr d C c D a b c ar d br d cr d R d A D AR d DR d G : S aab bab cab ar d AB br d AB cr d AB ab aar a B bar a B car a B ar d AR a B br d AR a B cr d AR a B ar a B A aa ba ca ar d A br d A cr d A a aar a bar a car a ar d AR a br d AR a cr d AR a ar a R a B BR a B ab bb cb ar d B br d B cr d B b abr b bbr b cbr b ar d BR b br d BR b cr d BR b br b R b C CR b C ac bc cc ar d C br d C cr d C c R c AR c A acr c bcr c ccr c ar d CR c br d CR c cr d CR c cr c D a b c ar d br d cr d R d A D AR d DR d 7 of 7
8 Lastly we fix the added variables: R a ab bb cb ar d B br d B cr d B b abr b bbr b cbr b ar d BR b br d BR b cr d BR b br b abr a bbr a cbr a ar d BR a br d BR a cr d BR a br a abr b R a bbr b R a cbr b R a ar d BR b R a br d BR b R a cr d BR b R a br b R a R b ac bc cc ar d C br d C cr d C c acr b bcr b ccr b ar d CR b br d CR b cr d CR b cr b acr b bcr b ccr b ar d CR b br d CR b cr d CR b cr b acr b R b bcr b R b ccr b R b ar d CR b R b br d CR b R b cr d CR b R b cr b R b R c aa ba ca ar d A br d A cr d A a aar a bar a car a ar d AR a br d AR a cr d AR a ar a aar c bar c car c ar d AR c br d AR c cr d AR c ar c aar a R c bar a R c car a R c ar d AR a R c br d AR a R c cr d AR a R c ar a R c R d aa ba ca ar d A br d A cr d A a Whew! aar a bar a car a ar d AR a br d AR a cr d AR a ar a a b c ar d br d cr d aar d bar d car d ar d AR d br d AR d cr d AR d ar d aar a R d bar a R d car a R d ar d AR a R d br d AR a R d cr d AR a R d ar a R d ar d br d cr d ar d R d br d R d cr d R d 8 of 7
6.045: Automata, Computability, and Complexity Or, Great Ideas in Theoretical Computer Science Spring, 2010. Class 4 Nancy Lynch
 6.045: Automata, Computability, and Complexity Or, Great Ideas in Theoretical Computer Science Spring, 2010 Class 4 Nancy Lynch Today Two more models of computation: Nondeterministic Finite Automata (NFAs)
6.045: Automata, Computability, and Complexity Or, Great Ideas in Theoretical Computer Science Spring, 2010 Class 4 Nancy Lynch Today Two more models of computation: Nondeterministic Finite Automata (NFAs)
Visa Smart Debit/Credit Certificate Authority Public Keys
 CHIP AND NEW TECHNOLOGIES Visa Smart Debit/Credit Certificate Authority Public Keys Overview The EMV standard calls for the use of Public Key technology for offline authentication, for aspects of online
CHIP AND NEW TECHNOLOGIES Visa Smart Debit/Credit Certificate Authority Public Keys Overview The EMV standard calls for the use of Public Key technology for offline authentication, for aspects of online
Formal Languages and Automata Theory - Regular Expressions and Finite Automata -
 Formal Languages and Automata Theory - Regular Expressions and Finite Automata - Samarjit Chakraborty Computer Engineering and Networks Laboratory Swiss Federal Institute of Technology (ETH) Zürich March
Formal Languages and Automata Theory - Regular Expressions and Finite Automata - Samarjit Chakraborty Computer Engineering and Networks Laboratory Swiss Federal Institute of Technology (ETH) Zürich March
CS103B Handout 17 Winter 2007 February 26, 2007 Languages and Regular Expressions
 CS103B Handout 17 Winter 2007 February 26, 2007 Languages and Regular Expressions Theory of Formal Languages In the English language, we distinguish between three different identities: letter, word, sentence.
CS103B Handout 17 Winter 2007 February 26, 2007 Languages and Regular Expressions Theory of Formal Languages In the English language, we distinguish between three different identities: letter, word, sentence.
C H A P T E R Regular Expressions regular expression
 7 CHAPTER Regular Expressions Most programmers and other power-users of computer systems have used tools that match text patterns. You may have used a Web search engine with a pattern like travel cancun
7 CHAPTER Regular Expressions Most programmers and other power-users of computer systems have used tools that match text patterns. You may have used a Web search engine with a pattern like travel cancun
Online EFFECTIVE AS OF JANUARY 2013
 2013 A and C Session Start Dates (A-B Quarter Sequence*) 2013 B and D Session Start Dates (B-A Quarter Sequence*) Quarter 5 2012 1205A&C Begins November 5, 2012 1205A Ends December 9, 2012 Session Break
2013 A and C Session Start Dates (A-B Quarter Sequence*) 2013 B and D Session Start Dates (B-A Quarter Sequence*) Quarter 5 2012 1205A&C Begins November 5, 2012 1205A Ends December 9, 2012 Session Break
Regular Languages and Finite State Machines
 Regular Languages and Finite State Machines Plan for the Day: Mathematical preliminaries - some review One application formal definition of finite automata Examples 1 Sets A set is an unordered collection
Regular Languages and Finite State Machines Plan for the Day: Mathematical preliminaries - some review One application formal definition of finite automata Examples 1 Sets A set is an unordered collection
Automata and Formal Languages
 Automata and Formal Languages Winter 2009-2010 Yacov Hel-Or 1 What this course is all about This course is about mathematical models of computation We ll study different machine models (finite automata,
Automata and Formal Languages Winter 2009-2010 Yacov Hel-Or 1 What this course is all about This course is about mathematical models of computation We ll study different machine models (finite automata,
INCIDENCE-BETWEENNESS GEOMETRY
 INCIDENCE-BETWEENNESS GEOMETRY MATH 410, CSUSM. SPRING 2008. PROFESSOR AITKEN This document covers the geometry that can be developed with just the axioms related to incidence and betweenness. The full
INCIDENCE-BETWEENNESS GEOMETRY MATH 410, CSUSM. SPRING 2008. PROFESSOR AITKEN This document covers the geometry that can be developed with just the axioms related to incidence and betweenness. The full
Boolean Algebra (cont d) UNIT 3 BOOLEAN ALGEBRA (CONT D) Guidelines for Multiplying Out and Factoring. Objectives. Iris Hui-Ru Jiang Spring 2010
 Boolean Algebra (cont d) 2 Contents Multiplying out and factoring expressions Exclusive-OR and Exclusive-NOR operations The consensus theorem Summary of algebraic simplification Proving validity of an
Boolean Algebra (cont d) 2 Contents Multiplying out and factoring expressions Exclusive-OR and Exclusive-NOR operations The consensus theorem Summary of algebraic simplification Proving validity of an
CROSS REFERENCE. Cross Reference Index 110-122. Cast ID Number 110-111 Connector ID Number 111 Engine ID Number 112-122. 2015 Ford Motor Company 109
 CROSS REFERENCE Cross Reference Index 110-122 Cast ID Number 110-111 Connector ID Number 111 112-122 2015 Ford Motor Company 109 CROSS REFERENCE Cast ID Number Cast ID Ford Service # MC Part # Part Type
CROSS REFERENCE Cross Reference Index 110-122 Cast ID Number 110-111 Connector ID Number 111 112-122 2015 Ford Motor Company 109 CROSS REFERENCE Cast ID Number Cast ID Ford Service # MC Part # Part Type
Crosswalk Directions:
 Crosswalk Directions: UMS Standards for College Readiness to 2007 MLR 1. Use a (yes), an (no), or a (partially) to indicate the extent to which the standard, performance indicator, or descriptor of the
Crosswalk Directions: UMS Standards for College Readiness to 2007 MLR 1. Use a (yes), an (no), or a (partially) to indicate the extent to which the standard, performance indicator, or descriptor of the
6 Commutators and the derived series. [x,y] = xyx 1 y 1.
![6 Commutators and the derived series. [x,y] = xyx 1 y 1. 6 Commutators and the derived series. [x,y] = xyx 1 y 1.](/thumbs/19/254057.jpg) 6 Commutators and the derived series Definition. Let G be a group, and let x,y G. The commutator of x and y is [x,y] = xyx 1 y 1. Note that [x,y] = e if and only if xy = yx (since x 1 y 1 = (yx) 1 ). Proposition
6 Commutators and the derived series Definition. Let G be a group, and let x,y G. The commutator of x and y is [x,y] = xyx 1 y 1. Note that [x,y] = e if and only if xy = yx (since x 1 y 1 = (yx) 1 ). Proposition
Finite Automata. Reading: Chapter 2
 Finite Automata Reading: Chapter 2 1 Finite Automaton (FA) Informally, a state diagram that comprehensively captures all possible states and transitions that a machine can take while responding to a stream
Finite Automata Reading: Chapter 2 1 Finite Automaton (FA) Informally, a state diagram that comprehensively captures all possible states and transitions that a machine can take while responding to a stream
Pushdown Automata. place the input head on the leftmost input symbol. while symbol read = b and pile contains discs advance head remove disc from pile
 Pushdown Automata In the last section we found that restricting the computational power of computing devices produced solvable decision problems for the class of sets accepted by finite automata. But along
Pushdown Automata In the last section we found that restricting the computational power of computing devices produced solvable decision problems for the class of sets accepted by finite automata. But along
Mathematics 3301-001 Spring 2015 Dr. Alexandra Shlapentokh Guide #3
 Mathematics 3301-001 Spring 2015 Dr. Alexandra Shlapentokh Guide #3 The problems in bold are the problems for Test #3. As before, you are allowed to use statements above and all postulates in the proofs
Mathematics 3301-001 Spring 2015 Dr. Alexandra Shlapentokh Guide #3 The problems in bold are the problems for Test #3. As before, you are allowed to use statements above and all postulates in the proofs
Pattern Co. Monkey Trouble Wall Quilt. Size: 48" x 58"
 .............................................................................................................................................. Pattern Co..........................................................................................
.............................................................................................................................................. Pattern Co..........................................................................................
2110711 THEORY of COMPUTATION
 2110711 THEORY of COMPUTATION ATHASIT SURARERKS ELITE Athasit Surarerks ELITE Engineering Laboratory in Theoretical Enumerable System Computer Engineering, Faculty of Engineering Chulalongkorn University
2110711 THEORY of COMPUTATION ATHASIT SURARERKS ELITE Athasit Surarerks ELITE Engineering Laboratory in Theoretical Enumerable System Computer Engineering, Faculty of Engineering Chulalongkorn University
ÖVNINGSUPPGIFTER I SAMMANHANGSFRIA SPRÅK. 15 april 2003. Master Edition
 ÖVNINGSUPPGIFTER I SAMMANHANGSFRIA SPRÅK 5 april 23 Master Edition CONTEXT FREE LANGUAGES & PUSH-DOWN AUTOMATA CONTEXT-FREE GRAMMARS, CFG Problems Sudkamp Problem. (3.2.) Which language generates the grammar
ÖVNINGSUPPGIFTER I SAMMANHANGSFRIA SPRÅK 5 april 23 Master Edition CONTEXT FREE LANGUAGES & PUSH-DOWN AUTOMATA CONTEXT-FREE GRAMMARS, CFG Problems Sudkamp Problem. (3.2.) Which language generates the grammar
A DIVISION OF THE MENO. Meno proposes a question: whether virtue can be taught. Three conversations or discussions following question
 A DIVISION OF THE MENO 70A 70B-100B Meno proposes a question: whether virtue can be taught Three conversations or discussions following question 70B-80D Conversation on a question before Meno's: what is
A DIVISION OF THE MENO 70A 70B-100B Meno proposes a question: whether virtue can be taught Three conversations or discussions following question 70B-80D Conversation on a question before Meno's: what is
Calculation of Valu-Trac Statuses
 Calculation of Intrinsic Value Yield Latest Cash Earnings (Net Income + Depreciation and Amortization) (put aside) Dividend (subtract) Provision for Depreciation (Net Assets x Inflation Rate) (subtract)
Calculation of Intrinsic Value Yield Latest Cash Earnings (Net Income + Depreciation and Amortization) (put aside) Dividend (subtract) Provision for Depreciation (Net Assets x Inflation Rate) (subtract)
DHL EXPRESS CANADA E-BILL STANDARD SPECIFICATIONS
 DHL EXPRESS CANADA E-BILL STANDARD SPECIFICATIONS 1 E-Bill Standard Layout A B C D E F G Field/ DHL Account Number Billing Customer Name Billing Customer Address Billing Customer City Billing Customer
DHL EXPRESS CANADA E-BILL STANDARD SPECIFICATIONS 1 E-Bill Standard Layout A B C D E F G Field/ DHL Account Number Billing Customer Name Billing Customer Address Billing Customer City Billing Customer
Fundamentele Informatica II
 Fundamentele Informatica II Answer to selected exercises 1 John C Martin: Introduction to Languages and the Theory of Computation M.M. Bonsangue (and J. Kleijn) Fall 2011 Let L be a language. It is clear
Fundamentele Informatica II Answer to selected exercises 1 John C Martin: Introduction to Languages and the Theory of Computation M.M. Bonsangue (and J. Kleijn) Fall 2011 Let L be a language. It is clear
DEFINITIONS. Perpendicular Two lines are called perpendicular if they form a right angle.
 DEFINITIONS Degree A degree is the 1 th part of a straight angle. 180 Right Angle A 90 angle is called a right angle. Perpendicular Two lines are called perpendicular if they form a right angle. Congruent
DEFINITIONS Degree A degree is the 1 th part of a straight angle. 180 Right Angle A 90 angle is called a right angle. Perpendicular Two lines are called perpendicular if they form a right angle. Congruent
Geometry Module 4 Unit 2 Practice Exam
 Name: Class: Date: ID: A Geometry Module 4 Unit 2 Practice Exam Multiple Choice Identify the choice that best completes the statement or answers the question. 1. Which diagram shows the most useful positioning
Name: Class: Date: ID: A Geometry Module 4 Unit 2 Practice Exam Multiple Choice Identify the choice that best completes the statement or answers the question. 1. Which diagram shows the most useful positioning
Lecture 24: Saccheri Quadrilaterals
 Lecture 24: Saccheri Quadrilaterals 24.1 Saccheri Quadrilaterals Definition In a protractor geometry, we call a quadrilateral ABCD a Saccheri quadrilateral, denoted S ABCD, if A and D are right angles
Lecture 24: Saccheri Quadrilaterals 24.1 Saccheri Quadrilaterals Definition In a protractor geometry, we call a quadrilateral ABCD a Saccheri quadrilateral, denoted S ABCD, if A and D are right angles
Matrix Algebra. Some Basic Matrix Laws. Before reading the text or the following notes glance at the following list of basic matrix algebra laws.
 Matrix Algebra A. Doerr Before reading the text or the following notes glance at the following list of basic matrix algebra laws. Some Basic Matrix Laws Assume the orders of the matrices are such that
Matrix Algebra A. Doerr Before reading the text or the following notes glance at the following list of basic matrix algebra laws. Some Basic Matrix Laws Assume the orders of the matrices are such that
PRIMARY CONTENT MODULE Algebra I -Linear Equations & Inequalities T-71. Applications. F = mc + b.
 PRIMARY CONTENT MODULE Algebra I -Linear Equations & Inequalities T-71 Applications The formula y = mx + b sometimes appears with different symbols. For example, instead of x, we could use the letter C.
PRIMARY CONTENT MODULE Algebra I -Linear Equations & Inequalities T-71 Applications The formula y = mx + b sometimes appears with different symbols. For example, instead of x, we could use the letter C.
Community College of Philadelphia Calling Code 218 Employer Scan Client Approved: November 17, 2005 Region (CIRCLE) City MSA
 Community College of Philadelphia Calling Code 218 Employer Scan Client Approved: November 17, 2005 Region (CIRCLE) City MSA Zip V0 V1 V2 Month/ Day/ Year of Contact: Business Name: Address: V3 City: V4
Community College of Philadelphia Calling Code 218 Employer Scan Client Approved: November 17, 2005 Region (CIRCLE) City MSA Zip V0 V1 V2 Month/ Day/ Year of Contact: Business Name: Address: V3 City: V4
26 Integers: Multiplication, Division, and Order
 26 Integers: Multiplication, Division, and Order Integer multiplication and division are extensions of whole number multiplication and division. In multiplying and dividing integers, the one new issue
26 Integers: Multiplication, Division, and Order Integer multiplication and division are extensions of whole number multiplication and division. In multiplying and dividing integers, the one new issue
Regular Languages and Finite Automata
 Regular Languages and Finite Automata 1 Introduction Hing Leung Department of Computer Science New Mexico State University Sep 16, 2010 In 1943, McCulloch and Pitts [4] published a pioneering work on a
Regular Languages and Finite Automata 1 Introduction Hing Leung Department of Computer Science New Mexico State University Sep 16, 2010 In 1943, McCulloch and Pitts [4] published a pioneering work on a
Regular Expressions and Automata using Haskell
 Regular Expressions and Automata using Haskell Simon Thompson Computing Laboratory University of Kent at Canterbury January 2000 Contents 1 Introduction 2 2 Regular Expressions 2 3 Matching regular expressions
Regular Expressions and Automata using Haskell Simon Thompson Computing Laboratory University of Kent at Canterbury January 2000 Contents 1 Introduction 2 2 Regular Expressions 2 3 Matching regular expressions
Estimating Probability Distributions
 Estimating Probability Distributions Readings: Manning and Schutze, Section 6.2 Jurafsky & Martin, Section 6.3 One of the central problems we face in using probability models for NLP is obtaining the actual
Estimating Probability Distributions Readings: Manning and Schutze, Section 6.2 Jurafsky & Martin, Section 6.3 One of the central problems we face in using probability models for NLP is obtaining the actual
COMMUTATIVE RINGS. Definition: A domain is a commutative ring R that satisfies the cancellation law for multiplication:
 COMMUTATIVE RINGS Definition: A commutative ring R is a set with two operations, addition and multiplication, such that: (i) R is an abelian group under addition; (ii) ab = ba for all a, b R (commutative
COMMUTATIVE RINGS Definition: A commutative ring R is a set with two operations, addition and multiplication, such that: (i) R is an abelian group under addition; (ii) ab = ba for all a, b R (commutative
CMPSCI 250: Introduction to Computation. Lecture #19: Regular Expressions and Their Languages David Mix Barrington 11 April 2013
 CMPSCI 250: Introduction to Computation Lecture #19: Regular Expressions and Their Languages David Mix Barrington 11 April 2013 Regular Expressions and Their Languages Alphabets, Strings and Languages
CMPSCI 250: Introduction to Computation Lecture #19: Regular Expressions and Their Languages David Mix Barrington 11 April 2013 Regular Expressions and Their Languages Alphabets, Strings and Languages
SERVER CERTIFICATES OF THE VETUMA SERVICE
 Page 1 Version: 3.4, 19.12.2014 SERVER CERTIFICATES OF THE VETUMA SERVICE 1 (18) Page 2 Version: 3.4, 19.12.2014 Table of Contents 1. Introduction... 3 2. Test Environment... 3 2.1 Vetuma test environment...
Page 1 Version: 3.4, 19.12.2014 SERVER CERTIFICATES OF THE VETUMA SERVICE 1 (18) Page 2 Version: 3.4, 19.12.2014 Table of Contents 1. Introduction... 3 2. Test Environment... 3 2.1 Vetuma test environment...
Baltic Way 1995. Västerås (Sweden), November 12, 1995. Problems and solutions
 Baltic Way 995 Västerås (Sweden), November, 995 Problems and solutions. Find all triples (x, y, z) of positive integers satisfying the system of equations { x = (y + z) x 6 = y 6 + z 6 + 3(y + z ). Solution.
Baltic Way 995 Västerås (Sweden), November, 995 Problems and solutions. Find all triples (x, y, z) of positive integers satisfying the system of equations { x = (y + z) x 6 = y 6 + z 6 + 3(y + z ). Solution.
MACM 101 Discrete Mathematics I
 MACM 101 Discrete Mathematics I Exercises on Combinatorics, Probability, Languages and Integers. Due: Tuesday, November 2th (at the beginning of the class) Reminder: the work you submit must be your own.
MACM 101 Discrete Mathematics I Exercises on Combinatorics, Probability, Languages and Integers. Due: Tuesday, November 2th (at the beginning of the class) Reminder: the work you submit must be your own.
Finite Automata. Reading: Chapter 2
 Finite Automata Reading: Chapter 2 1 Finite Automata Informally, a state machine that comprehensively captures all possible states and transitions that a machine can take while responding to a stream (or
Finite Automata Reading: Chapter 2 1 Finite Automata Informally, a state machine that comprehensively captures all possible states and transitions that a machine can take while responding to a stream (or
The common ratio in (ii) is called the scaled-factor. An example of two similar triangles is shown in Figure 47.1. Figure 47.1
 47 Similar Triangles An overhead projector forms an image on the screen which has the same shape as the image on the transparency but with the size altered. Two figures that have the same shape but not
47 Similar Triangles An overhead projector forms an image on the screen which has the same shape as the image on the transparency but with the size altered. Two figures that have the same shape but not
Application Note RMF Magic 5.1.0: EMC Array Group and EMC SRDF/A Reporting. July 2009
 Application Note RMF Magic 5.1.0: EMC Array Group and EMC SRDF/A Reporting July 2009 Summary: This Application Note describes the new functionality in RMF Magic 5.1 that enables more effective monitoring
Application Note RMF Magic 5.1.0: EMC Array Group and EMC SRDF/A Reporting July 2009 Summary: This Application Note describes the new functionality in RMF Magic 5.1 that enables more effective monitoring
Automata Theory. Şubat 2006 Tuğrul Yılmaz Ankara Üniversitesi
 Automata Theory Automata theory is the study of abstract computing devices. A. M. Turing studied an abstract machine that had all the capabilities of today s computers. Turing s goal was to describe the
Automata Theory Automata theory is the study of abstract computing devices. A. M. Turing studied an abstract machine that had all the capabilities of today s computers. Turing s goal was to describe the
How To Compare A Markov Algorithm To A Turing Machine
 Markov Algorithm CHEN Yuanmi December 18, 2007 1 Abstract Markov Algorithm can be understood as a priority string rewriting system. In this short paper we give the definition of Markov algorithm and also
Markov Algorithm CHEN Yuanmi December 18, 2007 1 Abstract Markov Algorithm can be understood as a priority string rewriting system. In this short paper we give the definition of Markov algorithm and also
Math 312 Homework 1 Solutions
 Math 31 Homework 1 Solutions Last modified: July 15, 01 This homework is due on Thursday, July 1th, 01 at 1:10pm Please turn it in during class, or in my mailbox in the main math office (next to 4W1) Please
Math 31 Homework 1 Solutions Last modified: July 15, 01 This homework is due on Thursday, July 1th, 01 at 1:10pm Please turn it in during class, or in my mailbox in the main math office (next to 4W1) Please
Exercise Set 3. Similar triangles. Parallel lines
 Exercise Set 3. Similar triangles Parallel lines Note: The exercises marked with are more difficult and go beyond the course/examination requirements. (1) Let ABC be a triangle with AB = AC. Let D be an
Exercise Set 3. Similar triangles Parallel lines Note: The exercises marked with are more difficult and go beyond the course/examination requirements. (1) Let ABC be a triangle with AB = AC. Let D be an
Automata and Computability. Solutions to Exercises
 Automata and Computability Solutions to Exercises Fall 25 Alexis Maciel Department of Computer Science Clarkson University Copyright c 25 Alexis Maciel ii Contents Preface vii Introduction 2 Finite Automata
Automata and Computability Solutions to Exercises Fall 25 Alexis Maciel Department of Computer Science Clarkson University Copyright c 25 Alexis Maciel ii Contents Preface vii Introduction 2 Finite Automata
Scanner. tokens scanner parser IR. source code. errors
 Scanner source code tokens scanner parser IR errors maps characters into tokens the basic unit of syntax x = x + y; becomes = + ; character string value for a token is a lexeme
Scanner source code tokens scanner parser IR errors maps characters into tokens the basic unit of syntax x = x + y; becomes = + ; character string value for a token is a lexeme
a 11 x 1 + a 12 x 2 + + a 1n x n = b 1 a 21 x 1 + a 22 x 2 + + a 2n x n = b 2.
 Chapter 1 LINEAR EQUATIONS 1.1 Introduction to linear equations A linear equation in n unknowns x 1, x,, x n is an equation of the form a 1 x 1 + a x + + a n x n = b, where a 1, a,..., a n, b are given
Chapter 1 LINEAR EQUATIONS 1.1 Introduction to linear equations A linear equation in n unknowns x 1, x,, x n is an equation of the form a 1 x 1 + a x + + a n x n = b, where a 1, a,..., a n, b are given
US Code (Unofficial compilation from the Legal Information Institute)
 US Code (Unofficial compilation from the Legal Information Institute) TITLE 26 - INTERNAL REVENUE CODE Subtitle D - Miscellaneous Excise Taxes CHAPTER 43 QUALIFIED PENSION, ETC., PLANS Please Note: This
US Code (Unofficial compilation from the Legal Information Institute) TITLE 26 - INTERNAL REVENUE CODE Subtitle D - Miscellaneous Excise Taxes CHAPTER 43 QUALIFIED PENSION, ETC., PLANS Please Note: This
Chapter 17. Orthogonal Matrices and Symmetries of Space
 Chapter 17. Orthogonal Matrices and Symmetries of Space Take a random matrix, say 1 3 A = 4 5 6, 7 8 9 and compare the lengths of e 1 and Ae 1. The vector e 1 has length 1, while Ae 1 = (1, 4, 7) has length
Chapter 17. Orthogonal Matrices and Symmetries of Space Take a random matrix, say 1 3 A = 4 5 6, 7 8 9 and compare the lengths of e 1 and Ae 1. The vector e 1 has length 1, while Ae 1 = (1, 4, 7) has length
CM2202: Scientific Computing and Multimedia Applications General Maths: 2. Algebra - Factorisation
 CM2202: Scientific Computing and Multimedia Applications General Maths: 2. Algebra - Factorisation Prof. David Marshall School of Computer Science & Informatics Factorisation Factorisation is a way of
CM2202: Scientific Computing and Multimedia Applications General Maths: 2. Algebra - Factorisation Prof. David Marshall School of Computer Science & Informatics Factorisation Factorisation is a way of
CH3 Boolean Algebra (cont d)
 CH3 Boolean Algebra (cont d) Lecturer: 吳 安 宇 Date:2005/10/7 ACCESS IC LAB v Today, you ll know: Introduction 1. Guidelines for multiplying out/factoring expressions 2. Exclusive-OR and Equivalence operations
CH3 Boolean Algebra (cont d) Lecturer: 吳 安 宇 Date:2005/10/7 ACCESS IC LAB v Today, you ll know: Introduction 1. Guidelines for multiplying out/factoring expressions 2. Exclusive-OR and Equivalence operations
SRM UNIVERSITY FACULTY OF ENGINEERING & TECHNOLOGY SCHOOL OF COMPUTING DEPARTMENT OF SOFTWARE ENGINEERING COURSE PLAN
 Course Code : CS0355 SRM UNIVERSITY FACULTY OF ENGINEERING & TECHNOLOGY SCHOOL OF COMPUTING DEPARTMENT OF SOFTWARE ENGINEERING COURSE PLAN Course Title : THEORY OF COMPUTATION Semester : VI Course : June
Course Code : CS0355 SRM UNIVERSITY FACULTY OF ENGINEERING & TECHNOLOGY SCHOOL OF COMPUTING DEPARTMENT OF SOFTWARE ENGINEERING COURSE PLAN Course Title : THEORY OF COMPUTATION Semester : VI Course : June
CIRCLE COORDINATE GEOMETRY
 CIRCLE COORDINATE GEOMETRY (EXAM QUESTIONS) Question 1 (**) A circle has equation x + y = 2x + 8 Determine the radius and the coordinates of the centre of the circle. r = 3, ( 1,0 ) Question 2 (**) A circle
CIRCLE COORDINATE GEOMETRY (EXAM QUESTIONS) Question 1 (**) A circle has equation x + y = 2x + 8 Determine the radius and the coordinates of the centre of the circle. r = 3, ( 1,0 ) Question 2 (**) A circle
Use of the Chi-Square Statistic. Marie Diener-West, PhD Johns Hopkins University
 This work is licensed under a Creative Commons Attribution-NonCommercial-ShareAlike License. Your use of this material constitutes acceptance of that license and the conditions of use of materials on this
This work is licensed under a Creative Commons Attribution-NonCommercial-ShareAlike License. Your use of this material constitutes acceptance of that license and the conditions of use of materials on this
SERVER CERTIFICATES OF THE VETUMA SERVICE
 Page 1 Version: 3.5, 4.11.2015 SERVER CERTIFICATES OF THE VETUMA SERVICE 1 (18) Page 2 Version: 3.5, 4.11.2015 Table of Contents 1. Introduction... 3 2. Test Environment... 3 2.1 Vetuma test environment...
Page 1 Version: 3.5, 4.11.2015 SERVER CERTIFICATES OF THE VETUMA SERVICE 1 (18) Page 2 Version: 3.5, 4.11.2015 Table of Contents 1. Introduction... 3 2. Test Environment... 3 2.1 Vetuma test environment...
Chapter 6: Episode discovery process
 Chapter 6: Episode discovery process Algorithmic Methods of Data Mining, Fall 2005, Chapter 6: Episode discovery process 1 6. Episode discovery process The knowledge discovery process KDD process of analyzing
Chapter 6: Episode discovery process Algorithmic Methods of Data Mining, Fall 2005, Chapter 6: Episode discovery process 1 6. Episode discovery process The knowledge discovery process KDD process of analyzing
Section 8.8. 1. The given line has equations. x = 3 + t(13 3) = 3 + 10t, y = 2 + t(3 + 2) = 2 + 5t, z = 7 + t( 8 7) = 7 15t.
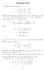 . The given line has equations Section 8.8 x + t( ) + 0t, y + t( + ) + t, z 7 + t( 8 7) 7 t. The line meets the plane y 0 in the point (x, 0, z), where 0 + t, or t /. The corresponding values for x and
. The given line has equations Section 8.8 x + t( ) + 0t, y + t( + ) + t, z 7 + t( 8 7) 7 t. The line meets the plane y 0 in the point (x, 0, z), where 0 + t, or t /. The corresponding values for x and
CAs and Turing Machines. The Basis for Universal Computation
 CAs and Turing Machines The Basis for Universal Computation What We Mean By Universal When we claim universal computation we mean that the CA is capable of calculating anything that could possibly be calculated*.
CAs and Turing Machines The Basis for Universal Computation What We Mean By Universal When we claim universal computation we mean that the CA is capable of calculating anything that could possibly be calculated*.
Vehicle Identification Numbering System 00.03
 Vehicle Identification Numbering System 00.03 IMPORTANT: See Subject 050 for the vehicle identification numbering system for vehicles built before May 1, 2000. Federal Motor Vehicle Safety Standard 115
Vehicle Identification Numbering System 00.03 IMPORTANT: See Subject 050 for the vehicle identification numbering system for vehicles built before May 1, 2000. Federal Motor Vehicle Safety Standard 115
Databases -Normalization III. (N Spadaccini 2010 and W Liu 2012) Databases - Normalization III 1 / 31
 Databases -Normalization III (N Spadaccini 2010 and W Liu 2012) Databases - Normalization III 1 / 31 This lecture This lecture describes 3rd normal form. (N Spadaccini 2010 and W Liu 2012) Databases -
Databases -Normalization III (N Spadaccini 2010 and W Liu 2012) Databases - Normalization III 1 / 31 This lecture This lecture describes 3rd normal form. (N Spadaccini 2010 and W Liu 2012) Databases -
Advanced Encryption Standard by Example. 1.0 Preface. 2.0 Terminology. Written By: Adam Berent V.1.7
 Written By: Adam Berent Advanced Encryption Standard by Example V.1.7 1.0 Preface The following document provides a detailed and easy to understand explanation of the implementation of the AES (RIJNDAEL)
Written By: Adam Berent Advanced Encryption Standard by Example V.1.7 1.0 Preface The following document provides a detailed and easy to understand explanation of the implementation of the AES (RIJNDAEL)
Small Business and Individual Chapter 11 Cases Under the Bankruptcy Abuse Prevention and Consumer Protection Act of 2005
 Small Business and Individual Chapter 11 Cases Under the Bankruptcy Abuse Prevention and Consumer Protection Act of 2005 I. Individual Chapter 11 Cases A.A Property of the Estate B Section 1115 1.1 In
Small Business and Individual Chapter 11 Cases Under the Bankruptcy Abuse Prevention and Consumer Protection Act of 2005 I. Individual Chapter 11 Cases A.A Property of the Estate B Section 1115 1.1 In
Advanced Encryption Standard by Example. 1.0 Preface. 2.0 Terminology. Written By: Adam Berent V.1.5
 Written By: Adam Berent Advanced Encryption Standard by Example V.1.5 1.0 Preface The following document provides a detailed and easy to understand explanation of the implementation of the AES (RIJNDAEL)
Written By: Adam Berent Advanced Encryption Standard by Example V.1.5 1.0 Preface The following document provides a detailed and easy to understand explanation of the implementation of the AES (RIJNDAEL)
6.3 Conditional Probability and Independence
 222 CHAPTER 6. PROBABILITY 6.3 Conditional Probability and Independence Conditional Probability Two cubical dice each have a triangle painted on one side, a circle painted on two sides and a square painted
222 CHAPTER 6. PROBABILITY 6.3 Conditional Probability and Independence Conditional Probability Two cubical dice each have a triangle painted on one side, a circle painted on two sides and a square painted
CHAPTER 8 QUADRILATERALS. 8.1 Introduction
 CHAPTER 8 QUADRILATERALS 8.1 Introduction You have studied many properties of a triangle in Chapters 6 and 7 and you know that on joining three non-collinear points in pairs, the figure so obtained is
CHAPTER 8 QUADRILATERALS 8.1 Introduction You have studied many properties of a triangle in Chapters 6 and 7 and you know that on joining three non-collinear points in pairs, the figure so obtained is
Lecture Notes on Database Normalization
 Lecture Notes on Database Normalization Chengkai Li Department of Computer Science and Engineering The University of Texas at Arlington April 15, 2012 I decided to write this document, because many students
Lecture Notes on Database Normalization Chengkai Li Department of Computer Science and Engineering The University of Texas at Arlington April 15, 2012 I decided to write this document, because many students
Learning Analysis by Reduction from Positive Data
 Learning Analysis by Reduction from Positive Data František Mráz 1, Friedrich Otto 1, and Martin Plátek 2 1 Fachbereich Mathematik/Informatik, Universität Kassel 34109 Kassel, Germany {mraz,otto}@theory.informatik.uni-kassel.de
Learning Analysis by Reduction from Positive Data František Mráz 1, Friedrich Otto 1, and Martin Plátek 2 1 Fachbereich Mathematik/Informatik, Universität Kassel 34109 Kassel, Germany {mraz,otto}@theory.informatik.uni-kassel.de
Honors Class (Foundations of) Informatics. Tom Verhoeff. Department of Mathematics & Computer Science Software Engineering & Technology
 Honors Class (Foundations of) Informatics Tom Verhoeff Department of Mathematics & Computer Science Software Engineering & Technology www.win.tue.nl/~wstomv/edu/hci c 2011, T. Verhoeff @ TUE.NL 1/20 Information
Honors Class (Foundations of) Informatics Tom Verhoeff Department of Mathematics & Computer Science Software Engineering & Technology www.win.tue.nl/~wstomv/edu/hci c 2011, T. Verhoeff @ TUE.NL 1/20 Information
Grammars with Regulated Rewriting
 Grammars with Regulated Rewriting Jürgen Dassow Otto-von-Guericke-Universität Magdeburg Fakultät für Informatik Lecture in the 5 th PhD Program Formal Languages and Applications PhD Program Formal Languages
Grammars with Regulated Rewriting Jürgen Dassow Otto-von-Guericke-Universität Magdeburg Fakultät für Informatik Lecture in the 5 th PhD Program Formal Languages and Applications PhD Program Formal Languages
December 4, 2013 MATH 171 BASIC LINEAR ALGEBRA B. KITCHENS
 December 4, 2013 MATH 171 BASIC LINEAR ALGEBRA B KITCHENS The equation 1 Lines in two-dimensional space (1) 2x y = 3 describes a line in two-dimensional space The coefficients of x and y in the equation
December 4, 2013 MATH 171 BASIC LINEAR ALGEBRA B KITCHENS The equation 1 Lines in two-dimensional space (1) 2x y = 3 describes a line in two-dimensional space The coefficients of x and y in the equation
Montgomery GI Bill Selected Reserve (MGIB-SR) Command/Servicing Personnel Office Review
 Overview Montgomery GI Bill Selected Reserve (MGIB-SR) Command/Servicing Personnel Office Review Introduction This transaction is used to record a Reserve member s Montgomery GI Bill-SR (MGIB-SR) eligibility
Overview Montgomery GI Bill Selected Reserve (MGIB-SR) Command/Servicing Personnel Office Review Introduction This transaction is used to record a Reserve member s Montgomery GI Bill-SR (MGIB-SR) eligibility
5.1 Midsegment Theorem and Coordinate Proof
 5.1 Midsegment Theorem and Coordinate Proof Obj.: Use properties of midsegments and write coordinate proofs. Key Vocabulary Midsegment of a triangle - A midsegment of a triangle is a segment that connects
5.1 Midsegment Theorem and Coordinate Proof Obj.: Use properties of midsegments and write coordinate proofs. Key Vocabulary Midsegment of a triangle - A midsegment of a triangle is a segment that connects
Acceptance Page 2. Revision History 3. Introduction 14. Control Categories 15. Scope 15. General Requirements 15
 Acceptance Page 2 Revision History 3 Introduction 14 Control Categories 15 Scope 15 General Requirements 15 Control Category: 0.0 Information Security Management Program 17 Objective Name: 0.01 Information
Acceptance Page 2 Revision History 3 Introduction 14 Control Categories 15 Scope 15 General Requirements 15 Control Category: 0.0 Information Security Management Program 17 Objective Name: 0.01 Information
1 = (a 0 + b 0 α) 2 + + (a m 1 + b m 1 α) 2. for certain elements a 0,..., a m 1, b 0,..., b m 1 of F. Multiplying out, we obtain
 Notes on real-closed fields These notes develop the algebraic background needed to understand the model theory of real-closed fields. To understand these notes, a standard graduate course in algebra is
Notes on real-closed fields These notes develop the algebraic background needed to understand the model theory of real-closed fields. To understand these notes, a standard graduate course in algebra is
Boolean Algebra Part 1
 Boolean Algebra Part 1 Page 1 Boolean Algebra Objectives Understand Basic Boolean Algebra Relate Boolean Algebra to Logic Networks Prove Laws using Truth Tables Understand and Use First Basic Theorems
Boolean Algebra Part 1 Page 1 Boolean Algebra Objectives Understand Basic Boolean Algebra Relate Boolean Algebra to Logic Networks Prove Laws using Truth Tables Understand and Use First Basic Theorems
Security of Online Social Networks
 Security of Online Social Networks Lehrstuhl IT-Sicherheitsmanagment Universität Siegen April 19, 2012 Lehrstuhl IT-Sicherheitsmanagment 1/36 Overview Lesson 02 Authentication Web Login Implementation
Security of Online Social Networks Lehrstuhl IT-Sicherheitsmanagment Universität Siegen April 19, 2012 Lehrstuhl IT-Sicherheitsmanagment 1/36 Overview Lesson 02 Authentication Web Login Implementation
Chapter 5. Rational Expressions
 5.. Simplify Rational Expressions KYOTE Standards: CR ; CA 7 Chapter 5. Rational Expressions Definition. A rational expression is the quotient P Q of two polynomials P and Q in one or more variables, where
5.. Simplify Rational Expressions KYOTE Standards: CR ; CA 7 Chapter 5. Rational Expressions Definition. A rational expression is the quotient P Q of two polynomials P and Q in one or more variables, where
WRITING PROOFS. Christopher Heil Georgia Institute of Technology
 WRITING PROOFS Christopher Heil Georgia Institute of Technology A theorem is just a statement of fact A proof of the theorem is a logical explanation of why the theorem is true Many theorems have this
WRITING PROOFS Christopher Heil Georgia Institute of Technology A theorem is just a statement of fact A proof of the theorem is a logical explanation of why the theorem is true Many theorems have this
"HIGHER EDUCATION VALUES AND OPINIONS SURVEY" ADVANCED PLACEMENT TEACHERS and GUIDANCE COUNSELORS May-June 1994
 "HIGHER EDUCATION VALUES AND OPINIONS SURVEY" ADVANCED PLACEMENT TEACHERS and GUIDANCE COUNSELORS May-June 1994 VARIABLE SURVEY ANSWER NAME QUESTION CATEGORIES Facsimile the original mail questionnaire
"HIGHER EDUCATION VALUES AND OPINIONS SURVEY" ADVANCED PLACEMENT TEACHERS and GUIDANCE COUNSELORS May-June 1994 VARIABLE SURVEY ANSWER NAME QUESTION CATEGORIES Facsimile the original mail questionnaire
The ASCII Character Set
 The ASCII Character Set The American Standard Code for Information Interchange or ASCII assigns values between 0 and 255 for upper and lower case letters, numeric digits, punctuation marks and other symbols.
The ASCII Character Set The American Standard Code for Information Interchange or ASCII assigns values between 0 and 255 for upper and lower case letters, numeric digits, punctuation marks and other symbols.
THE BANACH CONTRACTION PRINCIPLE. Contents
 THE BANACH CONTRACTION PRINCIPLE ALEX PONIECKI Abstract. This paper will study contractions of metric spaces. To do this, we will mainly use tools from topology. We will give some examples of contractions,
THE BANACH CONTRACTION PRINCIPLE ALEX PONIECKI Abstract. This paper will study contractions of metric spaces. To do this, we will mainly use tools from topology. We will give some examples of contractions,
www.pioneermathematics.com
 Problems and Solutions: INMO-2012 1. Let ABCD be a quadrilateral inscribed in a circle. Suppose AB = 2+ 2 and AB subtends 135 at the centre of the circle. Find the maximum possible area of ABCD. Solution:
Problems and Solutions: INMO-2012 1. Let ABCD be a quadrilateral inscribed in a circle. Suppose AB = 2+ 2 and AB subtends 135 at the centre of the circle. Find the maximum possible area of ABCD. Solution:
8 Divisibility and prime numbers
 8 Divisibility and prime numbers 8.1 Divisibility In this short section we extend the concept of a multiple from the natural numbers to the integers. We also summarize several other terms that express
8 Divisibility and prime numbers 8.1 Divisibility In this short section we extend the concept of a multiple from the natural numbers to the integers. We also summarize several other terms that express
MAT188H1S Lec0101 Burbulla
 Winter 206 Linear Transformations A linear transformation T : R m R n is a function that takes vectors in R m to vectors in R n such that and T (u + v) T (u) + T (v) T (k v) k T (v), for all vectors u
Winter 206 Linear Transformations A linear transformation T : R m R n is a function that takes vectors in R m to vectors in R n such that and T (u + v) T (u) + T (v) T (k v) k T (v), for all vectors u
USB HID to PS/2 Scan Code Translation Table
 Key Name HID Usage Page HID Usage ID PS/2 Set 1 Make* PS/2 Set 1 Break* PS/2 Set 2 Make PS/2 Set 2 Break System Power 01 81 E0 5E E0 DE E0 37 E0 F0 37 System Sleep 01 82 E0 5F E0 DF E0 3F E0 F0 3F System
Key Name HID Usage Page HID Usage ID PS/2 Set 1 Make* PS/2 Set 1 Break* PS/2 Set 2 Make PS/2 Set 2 Break System Power 01 81 E0 5E E0 DE E0 37 E0 F0 37 System Sleep 01 82 E0 5F E0 DF E0 3F E0 F0 3F System
Copy in your notebook: Add an example of each term with the symbols used in algebra 2 if there are any.
 Algebra 2 - Chapter Prerequisites Vocabulary Copy in your notebook: Add an example of each term with the symbols used in algebra 2 if there are any. P1 p. 1 1. counting(natural) numbers - {1,2,3,4,...}
Algebra 2 - Chapter Prerequisites Vocabulary Copy in your notebook: Add an example of each term with the symbols used in algebra 2 if there are any. P1 p. 1 1. counting(natural) numbers - {1,2,3,4,...}
1.4 Compound Inequalities
 Section 1.4 Compound Inequalities 53 1.4 Compound Inequalities This section discusses a technique that is used to solve compound inequalities, which is a phrase that usually refers to a pair of inequalities
Section 1.4 Compound Inequalities 53 1.4 Compound Inequalities This section discusses a technique that is used to solve compound inequalities, which is a phrase that usually refers to a pair of inequalities
Compiler I: Syntax Analysis Human Thought
 Course map Compiler I: Syntax Analysis Human Thought Abstract design Chapters 9, 12 H.L. Language & Operating Sys. Compiler Chapters 10-11 Virtual Machine Software hierarchy Translator Chapters 7-8 Assembly
Course map Compiler I: Syntax Analysis Human Thought Abstract design Chapters 9, 12 H.L. Language & Operating Sys. Compiler Chapters 10-11 Virtual Machine Software hierarchy Translator Chapters 7-8 Assembly
Show all work for credit. Attach paper as needed to keep work neat & organized.
 Geometry Semester 1 Review Part 2 Name Show all work for credit. Attach paper as needed to keep work neat & organized. Determine the reflectional (# of lines and draw them in) and rotational symmetry (order
Geometry Semester 1 Review Part 2 Name Show all work for credit. Attach paper as needed to keep work neat & organized. Determine the reflectional (# of lines and draw them in) and rotational symmetry (order
URL encoding uses hex code prefixed by %. Quoted Printable encoding uses hex code prefixed by =.
 ASCII = American National Standard Code for Information Interchange ANSI X3.4 1986 (R1997) (PDF), ANSI INCITS 4 1986 (R1997) (Printed Edition) Coded Character Set 7 Bit American National Standard Code
ASCII = American National Standard Code for Information Interchange ANSI X3.4 1986 (R1997) (PDF), ANSI INCITS 4 1986 (R1997) (Printed Edition) Coded Character Set 7 Bit American National Standard Code
Testing for Congruent Triangles Examples
 Testing for Congruent Triangles Examples 1. Why is congruency important? In 1913, Henry Ford began producing automobiles using an assembly line. When products are mass-produced, each piece must be interchangeable,
Testing for Congruent Triangles Examples 1. Why is congruency important? In 1913, Henry Ford began producing automobiles using an assembly line. When products are mass-produced, each piece must be interchangeable,
HTML Codes - Characters and symbols
 ASCII Codes HTML Codes Conversion References Control Characters English version Versión español Click here to add this link to your favorites. HTML Codes - Characters and symbols Standard ASCII set, HTML
ASCII Codes HTML Codes Conversion References Control Characters English version Versión español Click here to add this link to your favorites. HTML Codes - Characters and symbols Standard ASCII set, HTML
On the generation of elliptic curves with 16 rational torsion points by Pythagorean triples
 On the generation of elliptic curves with 16 rational torsion points by Pythagorean triples Brian Hilley Boston College MT695 Honors Seminar March 3, 2006 1 Introduction 1.1 Mazur s Theorem Let C be a
On the generation of elliptic curves with 16 rational torsion points by Pythagorean triples Brian Hilley Boston College MT695 Honors Seminar March 3, 2006 1 Introduction 1.1 Mazur s Theorem Let C be a
Geometry 1. Unit 3: Perpendicular and Parallel Lines
 Geometry 1 Unit 3: Perpendicular and Parallel Lines Geometry 1 Unit 3 3.1 Lines and Angles Lines and Angles Parallel Lines Parallel lines are lines that are coplanar and do not intersect. Some examples
Geometry 1 Unit 3: Perpendicular and Parallel Lines Geometry 1 Unit 3 3.1 Lines and Angles Lines and Angles Parallel Lines Parallel lines are lines that are coplanar and do not intersect. Some examples
Mathematics (Project Maths Phase 3)
 2014. M328 Coimisiún na Scrúduithe Stáit State Examinations Commission Leaving Certificate Examination 2014 Mathematics (Project Maths Phase 3) Paper 2 Ordinary Level Monday 9 June Morning 9:30 12:00 300
2014. M328 Coimisiún na Scrúduithe Stáit State Examinations Commission Leaving Certificate Examination 2014 Mathematics (Project Maths Phase 3) Paper 2 Ordinary Level Monday 9 June Morning 9:30 12:00 300
3515ICT Theory of Computation Turing Machines
 Griffith University 3515ICT Theory of Computation Turing Machines (Based loosely on slides by Harald Søndergaard of The University of Melbourne) 9-0 Overview Turing machines: a general model of computation
Griffith University 3515ICT Theory of Computation Turing Machines (Based loosely on slides by Harald Søndergaard of The University of Melbourne) 9-0 Overview Turing machines: a general model of computation
SOFTWARE ENGINEERING PROGRAM ASSESSMENT PLAN
 SOFTWARE ENGINEERING PROGRAM ASSESSMENT PLAN Version 3.0 October 5, 2010 Version 2.6 November 6, 2009 Version 2.5 September 16, 2008 Version 2.4 February 29, 2008 Version 2.3 January 12, 2007 Version 2.2
SOFTWARE ENGINEERING PROGRAM ASSESSMENT PLAN Version 3.0 October 5, 2010 Version 2.6 November 6, 2009 Version 2.5 September 16, 2008 Version 2.4 February 29, 2008 Version 2.3 January 12, 2007 Version 2.2
Collinearity and concurrence
 Collinearity and concurrence Po-Shen Loh 23 June 2008 1 Warm-up 1. Let I be the incenter of ABC. Let A be the midpoint of the arc BC of the circumcircle of ABC which does not contain A. Prove that the
Collinearity and concurrence Po-Shen Loh 23 June 2008 1 Warm-up 1. Let I be the incenter of ABC. Let A be the midpoint of the arc BC of the circumcircle of ABC which does not contain A. Prove that the
NEOSHO COUNTY COMMUNITY COLLEGE MASTER COURSE SYLLABUS. Medical Professional Issues
 NEOSHO COUNTY COMMUNITY COLLEGE MASTER COURSE SYLLABUS COURSE IDENTIFICATION Course Code/Number: ALMA 110 Course Title: Medical Professional Issues Division: Applied Science (AS) Liberal Arts (LA) Workforce
NEOSHO COUNTY COMMUNITY COLLEGE MASTER COURSE SYLLABUS COURSE IDENTIFICATION Course Code/Number: ALMA 110 Course Title: Medical Professional Issues Division: Applied Science (AS) Liberal Arts (LA) Workforce
