Review of Hazard Analysis Methods and Their Basic Characteristics
|
|
|
- Laura Stafford
- 7 years ago
- Views:
Transcription
1 Review of Hazard Analysis Methods and Their Basic Characteristics Vladimir Popović Teaching and Research Assistant University of Belgrade Faculty of Mechanical Engineering Branko Vasić Associate Professor University of Belgrade Faculty of Mechanical Engineering We live in the world comprised of systems and risks. With systems and technology there also comes the exposure to mishaps because systems can fail or work improperly which results in damage, injury and deaths. The possibility that a system fails and results in death, injury, damage and the like is referred to as mishap risk. The key to system safety and effective risk management is the identification and mitigation of hazards. To successfully control hazards, it is necessary to understand hazards and know how to identify them. The purpose of this paper is to better understand hazards and the tools and techniques for identifying them, so that they can be effectively controlled during the development of a system. Keywords: hazard analysis methods, types and techniques. 1. INTRODUCTION Due to the fact that there are various definitions and interpretations for the same thing in the terminology used in the given area, it was necessary, especially in the introductory part, to provide clarification for specific terms that have been used, and consider the dilemmas each analyst, dealing with the given area, faces. The English language itself, on one hand, contains many synonyms, and on the other, different experts operate with different or even contradictory terms for the same concepts. Another problem arises when these terms are to be introduced into our language [1,2]. In order to resolve the above mentioned misgivings, we have provided a short review of terms and definitions, most frequently used. Fault: The state of an item characterized by inability to perform a required function, excluding the inability during preventive maintenance or other planned actions, or due to lack of external resources (JUS IEC 50). A fault is hence a state resulting from failure. Failure: The event when a required function is terminated (exceeding the acceptable limits) (JUS IEC 50). Error: A discrepancy between a computed, observed or measured value or condition and the true, specified or theoretically correct value or condition (JUS IEC 50). An error is (yet) not a failure because it is within the acceptable limits of deviation from the desired performance (target value). An error is sometimes referred to as an incipient failure. The term failure is sometimes confused with the terms fault and error. The distinction between failure (or fault) and error is essential in failure analysis, because this describes the borderline between what is a failure and what is not. The relationship between these terms is illustrated in Figure 1. Received: November 2008, Accepted: December 2008 Correspondence to: Dr Vladimir Popović Faculty of Mechanical Engineering, Kraljice Marije 16, Belgrade 35, Serbia vpopovic@mas.bg.ac.rs Figure 1. Illustration of the difference between failure, fault and error [3] Mishap: An unplanned event or series of event resulting in death, injury, occupational illness, or damage to or loss of equipment or property, or damage to the environment Accident (MIL-STD-882C). Note the last word accident in the definition. Hazard: Any real or potential condition that can cause injury, illness, or death to personnel; damage to or loss of a system, equipment or property; or damage to the environment (MIL-STD-882D). A hazard is a potential condition that can result in a mishap or accident, given that the hazard occurs. This means that mishaps can be predicted via hazard identification. And, mishaps can be prevented or controlled via hazard elimination, control, or mitigation measures. This viewpoint provides a sense of control over the systems we develop and utilize. We can also say that hazard is a condition that is a prerequisite for an accident. A hazard is comprised of the following three basic components [4]: Hazardous Element (HE) This is the basic hazardous resource creating the impetus for the hazard, such as a hazardous energy source such as explosives being used in the system. Initiating Mechanism (IM) This is the trigger or initiator event(s) causing the hazard to occur. The IM causes actualization or transformation of the hazard from a dormant state to an active mishap state. Target and Threat (T/T) This is the person or thing that is vulnerable to injury and/or damage, and it describes the severity of the mishap event. This is the mishap outcome and the expected consequential damage or loss. Faculty of Mechanical Engineering, Belgrade. All rights reserved FME Transactions (2008) 36,
2 The three components of a hazard form what is known in system safety as the hazard triangle. The hazard triangle illustrates that a hazard consists of three necessary and coupled components, each of which forms the side of a triangle. All three sides of the triangle are essential and required in order for a hazard to exist. Remove any one of the triangle sides and hazard is eliminated because it is no longer able to produce a mishap (i.e., the triangle is incomplete). Hazard is a deterministic entity with its own structure, components, characteristics and features. If the hazard cannot be eliminated, its risk can be limited (diminished or controlled), namely by reducing the probability of hazard occurrence and/or the severity of accident effects, through project techniques. When the hazard arises, its outcome is almost always fixed and unchangeable. For this reason, it is very hard to reduce the severity of effects (they usually remain the same even after dealing with the hazard); it is much easier though, to reduce the probability of hazard occurrence to a reasonable level. Risk: An expression of the impact and possibility of a mishap in terms of potential mishap severity and probability of occurrence (MIL-STD-882D). The possibility of incurring misfortune or loss danger, gamble, peril, hazard (Collins Dictionary and Thesaurus). To take a risk: to proceed without regard to the possibility of danger (Collins Dictionary and Thesaurus). The term risk is derived from the Greek word ριζα, which signifies the danger to be avoided at sea. Risk is a much misunderstood and sometimes misused word. This is not surprising; in its common usage in English, it can also mean chance or gamble. The meaning of the word can therefore change with the context, and with the background of the people using the word. The word risk has a negative connotation; you do not often hear of the risk of winning the jackpot, while you may run the risk of failing an examination. Risk has two aspects. The quantitative (or normative) aspect can be calculated if we know the probability and consequence of an event. The qualitative (or descriptive) aspect relates to people s perception and depends on the emotional state and feelings. Both aspects of risk are important, but their relative importance can differ from case to case. The following research is interesting: Faced with a situation where there is a 50 % chance of gaining 100 $, or a sure gain of 50 $, most people will go for the second option. As opposed to this, if there is a 50 % chance of losing 100 $ against a sure loss of 50 $, most people will opt for the first option. In all these cases the risked value of the loss is the same [5]. Safety: Freedom from those conditions that can cause death, injury, occupational illness, or damage to or loss of equipment or property (MIL-STD-882D). This definition has caused considerable controversy [3]. A number of alternative definitions have therefore been proposed. The main controversy is connected to the term freedom from. Most activities involve some sort of risk and are never totally free from risk. In most of the alternative definitions safety is defined as an acceptable level of risk. The concept safety is mainly used related to random hazards, while the concept security is used related to deliberate actions. 2. HAZARD CAUSAL FACTORS There is a difference between why hazards exist and how they exist. The basic reasons why hazards exist are: (1) They are unavoidable because hazardous elements must be used in the system, and/or (2) they are the result of inadequate design safety consideration. Inadequate design safety consideration results from poor or insufficient design or the incorrect implementation of a good design. This includes inadequate consideration given to the potential effect of hardware failures, sneak paths, software glitches, human error, and the like. HCFs are the specific items responsible for how a unique hazard exists in a system. Figure 2 depicts the overall HCF model [4]. This model correlates all of the factors involved in hazardmishap theory. The model illustrates that hazards create the potential for mishaps, and mishaps occur based on the level of risk involved (i.e., hazards and mishaps are linked by risk). The three basic hazard components define both the hazard and the mishap. The three basic hazard components can be further broken into major hazard causal factor categories, which are: (1) hardware, (2) software, (3) humans, (4) interfaces, (5) functions, and (6) the environment. Finally, the causal factor categories are refined even further into the actual specific detailed causes, such as a hardware component failure mode. Figure 2. Hazard causal factor model Figure 2 illustrates how hazard HCFs can be viewed at three different levels: Level 1 Top Layer: The three hazard components (HE, IM, T/T), Level 2 Midlevel: The HCF categories (hardware, software, human system integration (HSI), environment, functions, interfaces) and Level 3 Bottom Level: The detailed specific causes (failure modes, errors, etc.). 3. HAZARD ANALYSIS TYPES AND TECHNIQUES Hazard analyses are performed to identify hazards, hazard effects, and hazard causal factors. Hazard analyses are used to determine system risk and thereby 182 VOL. 36, No 4, 2008 FME Transactions
3 ascertain the significance of hazards so that safety design measures can be established to eliminate or mitigate the hazard. Analyses are performed to systematically examine the system, subsystem, facility, components, software, personnel, and their interrelationships. There are two categories of hazard analyses: types and techniques. Hazard analysis type defines an analysis category (e.g., detailed design analysis), and technique defines a unique analysis methodology (e.g., fault tree analysis). The type establishes analysis timing, depth of detail, and system coverage. The technique refers to a specific and unique analysis methodology that provides specific results. System safety is built upon seven basic types, while there are well over 100 different techniques available. In general, there are several different techniques available for achieving each of the various types. The overarching distinctions between type and technique are summarized in Table 1. Table 1. Hazard analysis type vs. technique Type Establishes where, when, and what to analyze Establishes a specific analysis task at specific time in program life cycle Establishes what is desired from the analysis Provides a specific design focus Technique Establishes how to perform the analysis Establishes a specific and unique analysis methodology Provides the information to satisfy the intent of the analysis type Hazard analysis type describes the scope, coverage, detail, and life-cycle phase timing of the particular hazard analysis. Each type of analysis is intended to provide a time- or phase-dependent analysis that readily identifies hazards for a particular design phase in the system development life cycle. Since more detailed design and operation information is available as the development program progresses, so in turn more detailed information is available for a particular type of hazard analysis. The depth of detail for the analysis type increases as the level of design detail progresses. Each of these analysis types defines a point in time when the analysis should begin, the level of detail of the analysis, the type of information available, and the analysis output. The goals of each analysis type can be achieved by various analysis techniques. The analyst needs to carefully select the appropriate techniques to achieve the goals of each of the analysis types. There are seven hazard analysis types in the system safety discipline [4]: Conceptual design hazard analysis type (CD- HAT); Preliminary design hazard analysis type (PD- HAT); Detailed design hazard analysis type (); System design hazard analysis type (); Operations design hazard analysis type (OD- HAT); Health design hazard analysis type (HD-HAT) and Requirements design hazard analysis type (RD- HAT). An important principle about hazard analysis is that one particular hazard analysis type does not necessarily identify all the hazards within a system; identification of hazards may take more than one analysis type (hence the seven types). A corollary to this principle is that one particular hazard analysis type does not necessarily identify all of the hazard causal factors; more than one analysis type may be required. After performing all seven of the hazard analysis types, all hazards and causal factors should have been identified; however, additional hazards may be discovered during the test program. Figure 3 conveys the filter concept behind the seven hazard analysis types. In this concept, each hazard analysis type acts like a filter that identifies certain types of hazards. Each successive filter serves to identify hazards missed by the previous filter. The thick dark arrows at the top of the filter signify hazards existing in the system design. When all of the hazard analysis types have been applied, the only known hazards remaining have been reduced to an acceptable level of risk, denoted by the smaller thin arrows. Use of all seven hazards analysis types is critical in identifying and mitigating all hazards and reducing system residual risk. Figure 3. Hazard filters Each hazard analysis type serves a unique function or purpose. For a best practice system safety program (SSP), it is recommended that all seven of these hazard analysis types be applied; however, tailoring is permissible. If tailoring is utilized, the specifics should be spelled out in the system safety management plan (SSMP) and/or the system safety program plan (SSPP). Figure 4 depicts the relationship between hazard types and techniques. In this relationship, the seven hazard analysis types form the central focus for SSP hazard analysis. There are many different analysis techniques to select from when performing the analysis types, and there are many different factors that must go into the hazard analysis, such as the system life-cycle stages of concept, design, test, manufacture, operation, and disposal. The system modes, phases, and functions must be considered. The system hardware, software, firmware, human interfaces, and environmental aspects must also be considered. 3.1 Timing of hazard analysis types Figure 5 contains a consolidated view of the time period over which the hazard analysis types are typically performed [4]. This schedule shows the most typical FME Transactions VOL. 36, No 4,
4 Figure 4. Type-technique relationship Figure 5. Overall timing of hazard analysis types timing that has been found practical through many years of trial and error. The system development phases shown are from the standard engineering development life-cycle model. Note how each of the hazard analysis types correlates very closely to its associated development phase. Also, note that some of the analysis types should be performed in a later development phase if that phase was not specifically covered by the original analysis. The time period for performing the hazard analysis is not rigidly fixed but is dependent on many variables, such as size of the system and project, safety criticality of the system, personal experience, common sense, and so forth. The time period is shown as a bar because the analysis can be performed at nay time during the period shown. Specifying the time period for a hazard analysis is part of the safety program tailoring process and should be documented in the SSPP. Each of the hazard analysis types has a functional time period when it is most effectively applied to achieve the desired intent and goals. 3.2 Hazard analysis techniques Hazard analysis technique defines a unique analysis methodology (e.g., fault tree analysis). The technique refers to a specific and unique analysis methodology that is performed following a specific set of rules and provides specific result. As previously mentioned, there are over 100 different hazard analysis techniques in existence, and the number continues to slowly grow. Many of the techniques are minor variations of other techniques. And, many of the techniques are not widely practiced. We have pointed out to 22 techniques most commonly used by system safety practitioners. Each of these hazard analysis techniques is important enough to justify the fact it is mentioned in this paper. The system safety engineer/analyst should be thoroughly familiar with each of the analysis techniques considered in this paper. They form the basic building blocks for performing hazard and safety analysis on any type of system. 184 VOL. 36, No 4, 2008 FME Transactions
5 Technique attributes. Hazard analysis techniques can have many different inherent attributes, which makes their utility different. The appropriate technique to use can often be determined from the inherent attributes of the technique. Table 2 contains a list of the most significant attributes for a hazard analysis methodology. Table 3 summarizes some of the select attributes for the analysis techniques presented in this paper. Table 2. Major attributes of analysis techniques Attribute Description 1. qualitative/ quantitative analysis assessment is performed qualitatively or quantitatively 2. level of detail level of design detail that can be evaluated by the technique 3. data required type and level of design data required for the technique 4. program timing effective time during system development for the technique 5. time required relative amount of time required for the analysis 6. inductive/ deductive technique uses inductive or deductive reasoning 7. complexity relative complexity of the technique 8. difficulty relative difficulty of the technique 9. technical expertise relative technical expertise and experience required 10. tools required technique is standalone or additional tools are necessary 11. cost relative cost of the technique 12. primary safety tool technique is a primary or secondary safety tool Table 3: Summary of select attributes for analysis techniques Technique Type Identify hazards Identify root causes Life-cycle phase Qualitative/q uantitative Skill Level of detail PHL CD-HAT yes no CD-PD qual. SS min. I PHA PD-HAT yes partially CD-PD qual. SS Mod. I/D SSHA yes yes DD qual. SS, Eng, M&S in-depth I/D SHA yes yes PD-DD-T qual. SS, Eng, M&S in-depth I/D O&SHA OD-HAT yes yes PD-DD-T qual. SS, Eng, M&S in-depth I/D HHA HD-HAT yes yes PD-DD-T qual. SS, Eng, M&S in-depth I/D SRCA RD-HAT partially no PD-DD qual. SS in-depth FTA partially yes PD-DD qual./quant. SS, Eng, M&S Mod. D ETA partially partially PD-DD qual./quant. SS, Eng, M&S Mod. D FMEA partially partially PD-DD qual./quant. SS, Eng, M&S in-depth I FaHA yes partially PD-DD qual. SS, Eng, M&S in-depth I FuHA SCA PNA MA yes partially CD-PD-DD qual. SS, Eng, M&S Mod. I partially yes DD qual. SS, Eng, M&S Mod. D partially no PD-DD qual./quant. SS, Eng, M&S in-depth D partially no PD-DD qual./quant. SS, Eng, M&S Mod. D BA yes partially PD-DD qual. SS, Eng Mod. I BPA yes partially PD-DD qual. SS, Eng, M&S in-depth D HAZOP CCA CCFA MORT SWSA yes partially PD-DD qual. SS, Eng, M&S Mod. I yes partially PD-DD qual./quant. SS, Eng, M&S Mod. D yes partially PD-DD qual. SS, Eng, M&S Mod. D yes partially PD-DD qual./quant. SS, M&S Mod. D yes partially CD-PD qual. SS, Eng, M&S Mod. CD conceptual design; PD preliminary design; DD detailed design; T testing; SS system safety; Eng engineering electrical/mechanical/software; M&S math & statistics; Mod. moderate to in-depth. I/D FME Transactions VOL. 36, No 4,
6 Inductive and deductive techniques. System safety hazard analysis techniques are quite often labelled as being either an inductive or deductive methodology. For example, a failure mode and effects analysis (FMEA) is usually referred to as an inductive approach, while an FTA is referred to as a deductive approach [6]. Understanding how to correctly use the terms inductive and deductive is often confusing and even sometimes incorrectly applied. The question is: What do these terms really mean, how should they be used, and does their use provide any value to the safety analyst? The terms deductive or inductive refer to forms of logic and reasoning [2,6]. Deductive reasoning is a logical process in which a conclusion is drawn from a set of premises and contains no more information than the premises taken collectively. The truth of the conclusion is dependent upon the premises; the conclusion cannot be false if the premises on which it is based are true. Inductive reasoning is a logical process in which a conclusion is proposed that contains more information than the observation or experience on which it is based. The truth of the conclusion is verifiable only in terms of future experience, and certainty is attainable only if all possible instances have been examined. Two additional terms that are confusing to system safety analysts are top-down analysis and bottom-up Table 4. Inductive and deductive analysis characteristics analysis. In general, top-down analysis means starting the analysis from a high-level system viewpoint, for example, a missile navigation system, and continually burrowing into deeper levels of detail until the discrete component level is reached, such as a resistor or diode. A bottom-up analysis moves in the opposite direction. It begins at a low system level, such as the resistor or diode component, and moves upward until the system top level is reached. These definitions are illustrated in Figure 6. Some system safety practitioners advocate that a deductive analysis is always a top-down approach and that an inductive analysis is always a bottom-up approach. This may be a good generalization but is likely not always the case. Table 4 summarizes some of the characteristics of inductive and deductive analysis techniques [7]. The bottom line is that in the long run it does not really matter to the safety analyst if a hazard analysis technique is inductive or deductive. An analyst does not select an analysis technique based on whether its methodology is inductive, deductive, top-down, or bottom-up. What is important is that there are various techniques available for identifying hazards and hazard causal factors and that the safety analyst knows how to correctly use and apply the appropriate techniques. An analyst is more concerned with the actual task of identifying and mitigating hazards. Methodology General characteristics Applicability Potential pitfalls Examples Inductive What if Going from specific to the general System is broken down into individual components Potential failures for each component are considered (what can go wrong?) Effects of each failure are defined (what happens if it goes wrong?) Systems with few components Systems where single-point failure (SPFs) are predominant Preliminary or overview analysis Difficult to apply to complex systems Large number of components to consider Consideration of failure combinations becomes difficult Failure mode and effects analysis (FMEA) Hazard and operability (HAZOP) analysis Deductive How can Going from general to the specific General nature of the hazard has already been identified (fire, inadvertent launch, etc.) System is reviewed to define the cause of each hazard (how can it happen?) All sizes of systems Developed for complex systems Designed to identify hazards caused by multiple failures Detailed system documentation required Large amount of data involved Time consuming Fault tree analysis (FTA) Event tree analysis (ETA) Common cause failure analysis (CCFA) Figure 6. Inductive and deductive analysis relationship 186 VOL. 36, No 4, 2008 FME Transactions
7 Qualitative and quantitative techniques. System safety analysts are often in a quandary as whether to use a qualitative analysis technique or a quantitative analysis technique. Understanding which analysis type to use, and when, often seems more of an art than a science. The qualitative-quantitative factor is one of the basic attributes of a hazard analysis technique. Table 5 identifies some of the attributes that can be used to judge the strengths and weaknesses of qualitative and quantitative approaches. The system safety discipline primarily uses the qualitative risk characterization approach for a majority of safety work. Table 5. Differences between qualitative and quantitative techniques Attribute Qualitative Quantitative 1. numerical results no yes 2. cost lower higher 3. subjective/objective subjective objective 4. difficulty lower higher 5. complexity lower higher 6. data less detailed more detailed 7. technical expertise lower higher 8. time required lower higher 9. tools required seldom usually 10. accuracy lower higher 4. CONCLUSION Taking into account the previous considerations, we have come to the following conclusion: A hazard analysis type defines the analysis purpose, timing, scope, level of detail, and system coverage; it does not specify how to perform the analysis; A hazard analysis technique defines a specific and unique analysis methodology that provides a specific methodology and results; There are seven hazard analysis types in the system safety discipline that, together, help ensure identification and resolution of system hazards. There are over 100 different analysis techniques that can be used to satisfy the analysis type requirements and One particular hazard analysis type does not necessarily identify all the hazards within a system; it may take more than one type, and usually all seven types. REFERENCES [1] Popovic, V., Vasic, B. and Curovic, D.: Failure modes, effects and risks analysis FMERA, Journal of Institute for Research and Design in Commerce & Industry, Vol. 6, No. 20, pp , 2008, (in Serbian). [2] Todorovic, J.: Maintenance Engineering of Technical Systems, Institute for Research and Design in Commerce & Industry and Faculty of Mechanical Engineering, Belgrade, 2006, (in Serbian). [3] Rausand, M. and Høyland, A.: System Reliability Theory Models, Statistical Methods and Applications, John Wiley & Sons, New Jersey, [4] Ericson, A.C.: Hazard Analysis Techniques for System Safety, John Wiley & Sons, New Jersey, [5] Narayan, V.: Effective Maintenance Management: Risk and Reliability Strategies for Optimizing Performance, Industrial Press, New York, [6] Zelenovic, D. and Todorovic, J.: Effectiveness of Mechanical Systems, Science Book, Belgrade, 1990, (in Serbian). [7] Popovic, V., Vasic, B. and Stanojevic, N.: Contribution to development of new failure analysis methods, in: Proceedings of the 18 th EuroMaintenance Congress/3 rd World Congress of Maintenance, , Basel, Switzerland, pp ПРЕГЛЕД МЕТОДА АНАЛИЗЕ ОПАСНОСТИ И ЊИХОВИХ ОСНОВНИХ КАРАКТЕРИСТИКА Владимир Поповић, Бранко Васић Живимо у свету који чине системи и ризици. Уз системе и технологију, неизбежно долази и до изложености несрећама, пошто системи могу отказати или радити непрописно, што доводи до штете, повреда и смрти. Вероватноћа да систем откаже и доведе до смрти, повреда, штете и слично, зове се ризиком од несреће. Кључни моменат када је реч о безбедности система и ефикасном управљању ризиком, је уочавање и умањење опасности. Да би се успешно контролисала опасност, потребно ју је размотрити, као и знати како је уочити. Циљ овог рада је боље разумевање опасности, као и алата и техника за њено уочавање, да би се иста могла успешно контролисати током развоја система. FME Transactions VOL. 36, No 4,
3.0 Risk Assessment and Analysis Techniques and Tools
 3.0 Risk Assessment and Analysis Techniques and Tools Risks are determined in terms of the likelihood that an uncontrolled event will occur and the consequences of that event occurring. Risk = Likelihood
3.0 Risk Assessment and Analysis Techniques and Tools Risks are determined in terms of the likelihood that an uncontrolled event will occur and the consequences of that event occurring. Risk = Likelihood
Controlling Risks Risk Assessment
 Controlling Risks Risk Assessment Hazard/Risk Assessment Having identified the hazards, one must assess the risks by considering the severity and likelihood of bad outcomes. If the risks are not sufficiently
Controlling Risks Risk Assessment Hazard/Risk Assessment Having identified the hazards, one must assess the risks by considering the severity and likelihood of bad outcomes. If the risks are not sufficiently
Software-based medical devices from defibrillators
 C O V E R F E A T U R E Coping with Defective Software in Medical Devices Steven R. Rakitin Software Quality Consulting Inc. Embedding defective software in medical devices increases safety risks. Given
C O V E R F E A T U R E Coping with Defective Software in Medical Devices Steven R. Rakitin Software Quality Consulting Inc. Embedding defective software in medical devices increases safety risks. Given
University of Paderborn Software Engineering Group II-25. Dr. Holger Giese. University of Paderborn Software Engineering Group. External facilities
 II.2 Life Cycle and Safety Safety Life Cycle: The necessary activities involving safety-related systems, occurring during a period of time that starts at the concept phase of a project and finishes when
II.2 Life Cycle and Safety Safety Life Cycle: The necessary activities involving safety-related systems, occurring during a period of time that starts at the concept phase of a project and finishes when
How to achieve excellent enterprise risk management Why risk assessments fail
 How to achieve excellent enterprise risk management Why risk assessments fail Overview Risk assessments are a common tool for understanding business issues and potential consequences from uncertainties.
How to achieve excellent enterprise risk management Why risk assessments fail Overview Risk assessments are a common tool for understanding business issues and potential consequences from uncertainties.
Quality Risk Management Tools Quality Risk Management Tool Selection When to Select FMEA: QRM Tool Selection Matrix
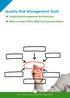 Quality Risk Management Tools Quality Risk Management Tool Selection When to Select FMEA: QRM Tool Selection Matrix 26 Quality Risk Management Tools The ICH Q9 guideline, Quality Risk Management, provides
Quality Risk Management Tools Quality Risk Management Tool Selection When to Select FMEA: QRM Tool Selection Matrix 26 Quality Risk Management Tools The ICH Q9 guideline, Quality Risk Management, provides
LSST Hazard Analysis Plan
 LSST Hazard Analysis Plan Large Synoptic Survey Telescope 950 N. Cherry Avenue Tucson, AZ 85719 www.lsst.org 1. REVISION SUMMARY: Contents 1 Introduction... 5 2 Definition of Terms... 5 2.1 System... 5
LSST Hazard Analysis Plan Large Synoptic Survey Telescope 950 N. Cherry Avenue Tucson, AZ 85719 www.lsst.org 1. REVISION SUMMARY: Contents 1 Introduction... 5 2 Definition of Terms... 5 2.1 System... 5
Designing an Effective Risk Matrix
 Designing an Effective Risk Matrix HENRY OZOG INTRODUCTION Risk assessment is an effective means of identifying process safety risks and determining the most cost-effective means to reduce risk. Many organizations
Designing an Effective Risk Matrix HENRY OZOG INTRODUCTION Risk assessment is an effective means of identifying process safety risks and determining the most cost-effective means to reduce risk. Many organizations
Identifying and Understanding Relevant System Safety Standards for use in the Automotive Industry
 SAE TECHNICAL PAPER SERIES 2003-01-1293 Identifying and Understanding Relevant System Standards for use in the Automotive Industry Barbara J. Czerny, Joseph G. D Ambrosio, Paravila O. Jacob and Brian T.
SAE TECHNICAL PAPER SERIES 2003-01-1293 Identifying and Understanding Relevant System Standards for use in the Automotive Industry Barbara J. Czerny, Joseph G. D Ambrosio, Paravila O. Jacob and Brian T.
FMEA and FTA Analysis
 FMEA and FTA Analysis Why it is Coming to Your Hospital and Your Laboratory Tina A. Krenc Director, R&D Phase Systems Abbott Laboratories 1 Agenda Background on requirements for risk management Tools to
FMEA and FTA Analysis Why it is Coming to Your Hospital and Your Laboratory Tina A. Krenc Director, R&D Phase Systems Abbott Laboratories 1 Agenda Background on requirements for risk management Tools to
Software Safety Hazard Analysis
 UCRL-ID-122514 Software Safety Hazard Analysis Version 2.0 Prepared by J. Dennis Lawrence Prepared for U.S. Nuclear Regulatory Commission Disclaimer This document was prepared as an account of work sponsored
UCRL-ID-122514 Software Safety Hazard Analysis Version 2.0 Prepared by J. Dennis Lawrence Prepared for U.S. Nuclear Regulatory Commission Disclaimer This document was prepared as an account of work sponsored
Risk Assessment Tools for Identifying Hazards and Evaluating Risks Associated with IVD Assays
 Risk Assessment Tools for Identifying Hazards and Evaluating Risks Associated with IVD Assays Robert C. Menson, PhD AACC Annual Meeting Philadelphia, PA 22 July 2003 What Risks Must Be Managed? Risk to
Risk Assessment Tools for Identifying Hazards and Evaluating Risks Associated with IVD Assays Robert C. Menson, PhD AACC Annual Meeting Philadelphia, PA 22 July 2003 What Risks Must Be Managed? Risk to
Accurate Risk Assessment Using Multi-Relational Hazard/Mishap Pairings
 Accurate Using Multi-Relational Hazard/Mishap Pairings Regina A. Eller, BA; Department of the Navy, Naval Surface Warfare Center, Dahlgren Division; Dahlgren, Virginia, USA Michael G. Zemore, MS Sys Eng;
Accurate Using Multi-Relational Hazard/Mishap Pairings Regina A. Eller, BA; Department of the Navy, Naval Surface Warfare Center, Dahlgren Division; Dahlgren, Virginia, USA Michael G. Zemore, MS Sys Eng;
Quality Risk Management in Pharmaceutical Industry: A Review
 International Journal of PharmTech Research CODEN (USA): IJPRIF ISSN : 0974-4304 Vol.6, No.3, pp 908-914, July-Aug 2014 Quality Risk Management in Pharmaceutical Industry: A Review V Vijayakumar Reddy*,
International Journal of PharmTech Research CODEN (USA): IJPRIF ISSN : 0974-4304 Vol.6, No.3, pp 908-914, July-Aug 2014 Quality Risk Management in Pharmaceutical Industry: A Review V Vijayakumar Reddy*,
Failure Analysis Methods What, Why and How. MEEG 466 Special Topics in Design Jim Glancey Spring, 2006
 Failure Analysis Methods What, Why and How MEEG 466 Special Topics in Design Jim Glancey Spring, 2006 Failure Analysis Methods Every product or process has modes of failure. An analysis of potential failures
Failure Analysis Methods What, Why and How MEEG 466 Special Topics in Design Jim Glancey Spring, 2006 Failure Analysis Methods Every product or process has modes of failure. An analysis of potential failures
A System-safety process for by-wire automotive systems
 A System-safety process for by-wire automotive systems Steer-by-wire and other by-wire systems (as defined in this article) offer many passive and active safety advantages. To help ensure these advantages
A System-safety process for by-wire automotive systems Steer-by-wire and other by-wire systems (as defined in this article) offer many passive and active safety advantages. To help ensure these advantages
QUALITY RISK MANAGEMENT (QRM): A REVIEW
 Lotlikar et al Journal of Drug Delivery & Therapeutics; 2013, 3(2), 149-154 149 Available online at http://jddtonline.info REVIEW ARTICLE QUALITY RISK MANAGEMENT (QRM): A REVIEW Lotlikar MV Head Corporate
Lotlikar et al Journal of Drug Delivery & Therapeutics; 2013, 3(2), 149-154 149 Available online at http://jddtonline.info REVIEW ARTICLE QUALITY RISK MANAGEMENT (QRM): A REVIEW Lotlikar MV Head Corporate
THE RELIABILITY ENGINEER SOLUTIONS TEXT
 THE RELIABILITY ENGINEER SOLUTIONS TEXT 2009 by QCI - All rights reserved 2.1. Which of the following is required to establish a reliability specification? a. The usage environment b. The system quality
THE RELIABILITY ENGINEER SOLUTIONS TEXT 2009 by QCI - All rights reserved 2.1. Which of the following is required to establish a reliability specification? a. The usage environment b. The system quality
www.transition-support.com
 Can we include all products and services in the QMS but limit the scope of registration? According to ISO/TC 176/SC 2/N 524, organizations are not obliged to include all the products that it provides within
Can we include all products and services in the QMS but limit the scope of registration? According to ISO/TC 176/SC 2/N 524, organizations are not obliged to include all the products that it provides within
Motivations. spm - 2014 adolfo villafiorita - introduction to software project management
 Risk Management Motivations When we looked at project selection we just took into account financial data In the scope management document we emphasized the importance of making our goals achievable, i.e.
Risk Management Motivations When we looked at project selection we just took into account financial data In the scope management document we emphasized the importance of making our goals achievable, i.e.
Advanced Risk Analysis for High-Performing Organizations
 Pittsburgh, PA 15213-3890 Advanced Risk Analysis for High-Performing Organizations Christopher Alberts Audrey Dorofee Sponsored by the U.S. Department of Defense 2006 by Carnegie Mellon University page
Pittsburgh, PA 15213-3890 Advanced Risk Analysis for High-Performing Organizations Christopher Alberts Audrey Dorofee Sponsored by the U.S. Department of Defense 2006 by Carnegie Mellon University page
Controlling Risks Safety Lifecycle
 Controlling Risks Safety Lifecycle Objective Introduce the concept of a safety lifecycle and the applicability and context in safety systems. Lifecycle Management A risk based management plan for a system
Controlling Risks Safety Lifecycle Objective Introduce the concept of a safety lifecycle and the applicability and context in safety systems. Lifecycle Management A risk based management plan for a system
Module 3: Correlation and Covariance
 Using Statistical Data to Make Decisions Module 3: Correlation and Covariance Tom Ilvento Dr. Mugdim Pašiƒ University of Delaware Sarajevo Graduate School of Business O ften our interest in data analysis
Using Statistical Data to Make Decisions Module 3: Correlation and Covariance Tom Ilvento Dr. Mugdim Pašiƒ University of Delaware Sarajevo Graduate School of Business O ften our interest in data analysis
Integrating System Safety and Software Assurance
 Integrating System Safety and Software Assurance Systems Certification and Integrity Directorate of Aviation Engineering Directorate General Technical Airworthiness 1 Overview Integration of software assurance
Integrating System Safety and Software Assurance Systems Certification and Integrity Directorate of Aviation Engineering Directorate General Technical Airworthiness 1 Overview Integration of software assurance
Developing software which should never compromise the overall safety of a system
 Safety-critical software Developing software which should never compromise the overall safety of a system Ian Sommerville 1995 Software Engineering, 5th edition. Chapter 21 Slide 1 Objectives To introduce
Safety-critical software Developing software which should never compromise the overall safety of a system Ian Sommerville 1995 Software Engineering, 5th edition. Chapter 21 Slide 1 Objectives To introduce
Risk Assessment for Medical Devices. Linda Braddon, Ph.D. Bring your medical device to market faster 1
 Risk Assessment for Medical Devices Linda Braddon, Ph.D. Bring your medical device to market faster 1 My Perspective Work with start up medical device companies Goal: Making great ideas into profitable
Risk Assessment for Medical Devices Linda Braddon, Ph.D. Bring your medical device to market faster 1 My Perspective Work with start up medical device companies Goal: Making great ideas into profitable
6-1. Process Modeling
 6-1 Process Modeling Key Definitions Process model A formal way of representing how a business system operates Illustrates the activities that are performed and how data moves among them Data flow diagramming
6-1 Process Modeling Key Definitions Process model A formal way of representing how a business system operates Illustrates the activities that are performed and how data moves among them Data flow diagramming
Analyzing and interpreting data Evaluation resources from Wilder Research
 Wilder Research Analyzing and interpreting data Evaluation resources from Wilder Research Once data are collected, the next step is to analyze the data. A plan for analyzing your data should be developed
Wilder Research Analyzing and interpreting data Evaluation resources from Wilder Research Once data are collected, the next step is to analyze the data. A plan for analyzing your data should be developed
The use of statistical problem solving methods for Risk Assessment
 The use of statistical problem solving methods for Risk Assessment Citti P., Delogu M., Giorgetti A. University of Florence. DMTI, Department of Mechanics and Industrial Technology Via Santa Marta, 3 50121
The use of statistical problem solving methods for Risk Assessment Citti P., Delogu M., Giorgetti A. University of Florence. DMTI, Department of Mechanics and Industrial Technology Via Santa Marta, 3 50121
Sample Size and Power in Clinical Trials
 Sample Size and Power in Clinical Trials Version 1.0 May 011 1. Power of a Test. Factors affecting Power 3. Required Sample Size RELATED ISSUES 1. Effect Size. Test Statistics 3. Variation 4. Significance
Sample Size and Power in Clinical Trials Version 1.0 May 011 1. Power of a Test. Factors affecting Power 3. Required Sample Size RELATED ISSUES 1. Effect Size. Test Statistics 3. Variation 4. Significance
2005-01-0785. Effective Application of Software Safety Techniques for Automotive Embedded Control Systems SAE TECHNICAL PAPER SERIES
 2005-01-0785 SAE TECHNICAL PAPER SERIES Effective Application of Software Safety Techniques for Automotive Embedded Control Systems Barbara J. Czerny, Joseph G. D Ambrosio, Brian T. Murray and Padma Sundaram
2005-01-0785 SAE TECHNICAL PAPER SERIES Effective Application of Software Safety Techniques for Automotive Embedded Control Systems Barbara J. Czerny, Joseph G. D Ambrosio, Brian T. Murray and Padma Sundaram
An Introduction to Fault Tree Analysis (FTA)
 An Introduction to Fault Tree Analysis (FTA) Dr Jane Marshall Product Excellence using 6 Sigma Module PEUSS 2011/2012 FTA Page 1 Objectives Understand purpose of FTA Understand & apply rules of FTA Analyse
An Introduction to Fault Tree Analysis (FTA) Dr Jane Marshall Product Excellence using 6 Sigma Module PEUSS 2011/2012 FTA Page 1 Objectives Understand purpose of FTA Understand & apply rules of FTA Analyse
INTERNATIONAL STANDARD ON ASSURANCE ENGAGEMENTS 3000 ASSURANCE ENGAGEMENTS OTHER THAN AUDITS OR REVIEWS OF HISTORICAL FINANCIAL INFORMATION CONTENTS
 INTERNATIONAL STANDARD ON ASSURANCE ENGAGEMENTS 3000 ASSURANCE ENGAGEMENTS OTHER THAN AUDITS OR REVIEWS OF HISTORICAL FINANCIAL INFORMATION (Effective for assurance reports dated on or after January 1,
INTERNATIONAL STANDARD ON ASSURANCE ENGAGEMENTS 3000 ASSURANCE ENGAGEMENTS OTHER THAN AUDITS OR REVIEWS OF HISTORICAL FINANCIAL INFORMATION (Effective for assurance reports dated on or after January 1,
Chapter 6 Experiment Process
 Chapter 6 Process ation is not simple; we have to prepare, conduct and analyze experiments properly. One of the main advantages of an experiment is the control of, for example, subjects, objects and instrumentation.
Chapter 6 Process ation is not simple; we have to prepare, conduct and analyze experiments properly. One of the main advantages of an experiment is the control of, for example, subjects, objects and instrumentation.
A System-Safety Process For By-Wire Automotive Systems
 SAE TECHNICAL PAPER SERIES 2000-01-1056 A System-Safety Process For By-Wire Automotive Systems Sanket Amberkar, Joseph G. D Ambrosio and Brian T. Murray Delphi Automotive Systems Joseph Wysocki HRL Laboratories
SAE TECHNICAL PAPER SERIES 2000-01-1056 A System-Safety Process For By-Wire Automotive Systems Sanket Amberkar, Joseph G. D Ambrosio and Brian T. Murray Delphi Automotive Systems Joseph Wysocki HRL Laboratories
Design Verification The Case for Verification, Not Validation
 Overview: The FDA requires medical device companies to verify that all the design outputs meet the design inputs. The FDA also requires that the final medical device must be validated to the user needs.
Overview: The FDA requires medical device companies to verify that all the design outputs meet the design inputs. The FDA also requires that the final medical device must be validated to the user needs.
The Supports Coordinator s Role in Incident Management
 The SC s Role in Incident Management 1 The Supports Coordinator s Role in Incident Management Title Slide (music playing) This webcast is one in a series about incident management and risk management in
The SC s Role in Incident Management 1 The Supports Coordinator s Role in Incident Management Title Slide (music playing) This webcast is one in a series about incident management and risk management in
Risk Management Primer
 Risk Management Primer Purpose: To obtain strong project outcomes by implementing an appropriate risk management process Audience: Project managers, project sponsors, team members and other key stakeholders
Risk Management Primer Purpose: To obtain strong project outcomes by implementing an appropriate risk management process Audience: Project managers, project sponsors, team members and other key stakeholders
Title: Basic Principles of Risk Management for Medical Device Design
 Title: Basic Principles of Risk Management for Medical Device Design WHITE PAPER Author: Ganeshkumar Palanichamy Abstract Medical devices developed for human application are used for diagnostic or treatment
Title: Basic Principles of Risk Management for Medical Device Design WHITE PAPER Author: Ganeshkumar Palanichamy Abstract Medical devices developed for human application are used for diagnostic or treatment
Improved Utilization of Self-Inspection Programs within the GMP Environment A Quality Risk Management Approach
 Improved Utilization of Self-Inspection Programs within the GMP Environment A Quality Risk Management Approach Barbara Jeroncic Self-inspection is a well-established and vital part of the pharmaceutical
Improved Utilization of Self-Inspection Programs within the GMP Environment A Quality Risk Management Approach Barbara Jeroncic Self-inspection is a well-established and vital part of the pharmaceutical
Planning Your Safety Instrumented System
 Planning Your Safety Instrumented System Executive Summary Industrial processes today involve innate risks due to the presence of gases, chemicals and other dangerous materials. Each year catastrophes
Planning Your Safety Instrumented System Executive Summary Industrial processes today involve innate risks due to the presence of gases, chemicals and other dangerous materials. Each year catastrophes
Q1. The graph below shows how a sinusoidal alternating voltage varies with time when connected across a resistor, R.
 Q1. The graph below shows how a sinusoidal alternating voltage varies with time when connected across a resistor, R. (a) (i) State the peak-to-peak voltage. peak-to-peak voltage...v (1) (ii) State the
Q1. The graph below shows how a sinusoidal alternating voltage varies with time when connected across a resistor, R. (a) (i) State the peak-to-peak voltage. peak-to-peak voltage...v (1) (ii) State the
Chapter 10. System Software Safety
 Chapter 10 System Software Safety 10.0 SYSTEM SOFTWARE SAFETY...2 10.1 INTRODUCTION...2 10.2 THE IMPORTANCE OF SYSTEM SAFETY...3 10.3 SOFTWARE SAFETY DEVELOPMENT PROCESS...5 10.4 SYSTEM SAFETY ASSESSMENT
Chapter 10 System Software Safety 10.0 SYSTEM SOFTWARE SAFETY...2 10.1 INTRODUCTION...2 10.2 THE IMPORTANCE OF SYSTEM SAFETY...3 10.3 SOFTWARE SAFETY DEVELOPMENT PROCESS...5 10.4 SYSTEM SAFETY ASSESSMENT
System Specification. Objectives
 System Specification cmsc435-1 Objectives To explain how dependability requirements may be identified by analyzing the risks faced by critical systems To explain how safety requirements are generated from
System Specification cmsc435-1 Objectives To explain how dependability requirements may be identified by analyzing the risks faced by critical systems To explain how safety requirements are generated from
Five High Order Thinking Skills
 Five High Order Introduction The high technology like computers and calculators has profoundly changed the world of mathematics education. It is not only what aspects of mathematics are essential for learning,
Five High Order Introduction The high technology like computers and calculators has profoundly changed the world of mathematics education. It is not only what aspects of mathematics are essential for learning,
Risk Assessment and Management. Allen L. Burgenson Manager, Regulatory Affairs Lonza Walkersville Inc.
 Risk Assessment and Management Allen L. Burgenson Manager, Regulatory Affairs Lonza Walkersville Inc. Standard Disclaimer Standard Disclaimer: This presentation is the opinion of the presenter, and does
Risk Assessment and Management Allen L. Burgenson Manager, Regulatory Affairs Lonza Walkersville Inc. Standard Disclaimer Standard Disclaimer: This presentation is the opinion of the presenter, and does
Proposal: A Vendor Approach to a Business Problem
 Gopala Krishna Behara & Madhusudhana Rao Abstract Presenting a proposal is the best way to address the business problems of customers. In a proposal, you offer solutions to customer problems both from
Gopala Krishna Behara & Madhusudhana Rao Abstract Presenting a proposal is the best way to address the business problems of customers. In a proposal, you offer solutions to customer problems both from
University of Ljubljana. Faculty of Computer and Information Science
 University of Ljubljana Faculty of Computer and Information Science Failure Mode and Effects (and Criticality) Analysis Fault Tree Analysis Report Computer Reliability and Diagnostics Ľuboš Slovák Assoc.
University of Ljubljana Faculty of Computer and Information Science Failure Mode and Effects (and Criticality) Analysis Fault Tree Analysis Report Computer Reliability and Diagnostics Ľuboš Slovák Assoc.
Failure Modes & Effects Analysis
 The Failure Modes and Effects Analysis (FMEA), also known as Failure Modes, Effects, and Criticality Analysis (FMECA), is a systematic method by which potential failures of a product or process design
The Failure Modes and Effects Analysis (FMEA), also known as Failure Modes, Effects, and Criticality Analysis (FMECA), is a systematic method by which potential failures of a product or process design
Occupational safety risk management in Australian mining
 IN-DEPTH REVIEW Occupational Medicine 2004;54:311 315 doi:10.1093/occmed/kqh074 Occupational safety risk management in Australian mining J. Joy Abstract Key words In the past 15 years, there has been a
IN-DEPTH REVIEW Occupational Medicine 2004;54:311 315 doi:10.1093/occmed/kqh074 Occupational safety risk management in Australian mining J. Joy Abstract Key words In the past 15 years, there has been a
Systems Assurance Management in Railway through the Project Life Cycle
 Systems Assurance Management in Railway through the Project Life Cycle Vivian Papen Ronald Harvey Hamid Qaasim Peregrin Spielholz ABSTRACT Systems assurance management is essential for transit agencies
Systems Assurance Management in Railway through the Project Life Cycle Vivian Papen Ronald Harvey Hamid Qaasim Peregrin Spielholz ABSTRACT Systems assurance management is essential for transit agencies
ASSESSMENT OF THE ISO 26262 STANDARD, ROAD VEHICLES FUNCTIONAL SAFETY
 ASSESSMENT OF THE ISO 26262 STANDARD, ROAD VEHICLES FUNCTIONAL SAFETY Dr. Qi Van Eikema Hommes SAE 2012 Government/Industry Meeting January 25, 2012 1 Outline ISO 26262 Overview Scope of the Assessment
ASSESSMENT OF THE ISO 26262 STANDARD, ROAD VEHICLES FUNCTIONAL SAFETY Dr. Qi Van Eikema Hommes SAE 2012 Government/Industry Meeting January 25, 2012 1 Outline ISO 26262 Overview Scope of the Assessment
Basic Fundamentals Of Safety Instrumented Systems
 September 2005 DVC6000 SIS Training Course 1 Basic Fundamentals Of Safety Instrumented Systems Overview Definitions of basic terms Basics of safety and layers of protection Basics of Safety Instrumented
September 2005 DVC6000 SIS Training Course 1 Basic Fundamentals Of Safety Instrumented Systems Overview Definitions of basic terms Basics of safety and layers of protection Basics of Safety Instrumented
QUANTITATIVE RISK ASSESSMENT FOR ACCIDENTS AT WORK IN THE CHEMICAL INDUSTRY AND THE SEVESO II DIRECTIVE
 QUANTITATIVE RISK ASSESSMENT FOR ACCIDENTS AT WORK IN THE CHEMICAL INDUSTRY AND THE SEVESO II DIRECTIVE I. A. PAPAZOGLOU System Reliability and Industrial Safety Laboratory National Center for Scientific
QUANTITATIVE RISK ASSESSMENT FOR ACCIDENTS AT WORK IN THE CHEMICAL INDUSTRY AND THE SEVESO II DIRECTIVE I. A. PAPAZOGLOU System Reliability and Industrial Safety Laboratory National Center for Scientific
3.4.4 Description of risk management plan Unofficial Translation Only the Thai version of the text is legally binding.
 - 1 - Regulation of Department of Industrial Works Re: Criteria for hazard identification, risk assessment, and establishment of risk management plan B.E. 2543 (2000) ---------------------------- Pursuant
- 1 - Regulation of Department of Industrial Works Re: Criteria for hazard identification, risk assessment, and establishment of risk management plan B.E. 2543 (2000) ---------------------------- Pursuant
Outline Intrusion Detection CS 239 Security for Networks and System Software June 3, 2002
 Outline Intrusion Detection CS 239 Security for Networks and System Software June 3, 2002 Introduction Characteristics of intrusion detection systems Some sample intrusion detection systems Page 1 Page
Outline Intrusion Detection CS 239 Security for Networks and System Software June 3, 2002 Introduction Characteristics of intrusion detection systems Some sample intrusion detection systems Page 1 Page
Guide to CQI Qualifications for learners
 Guide to CQI Qualifications for learners CQI Qualifications and Professional Recognition Quality management is about improving organisational performance in delivering product and service that meet customer
Guide to CQI Qualifications for learners CQI Qualifications and Professional Recognition Quality management is about improving organisational performance in delivering product and service that meet customer
A Risk Management System Framework for New Product Development (NPD)
 2011 International Conference on Economics and Finance Research IPEDR vol.4 (2011) (2011) IACSIT Press, Singapore A Risk Management System Framework for New Product Development (NPD) Seonmuk Park, Jongseong
2011 International Conference on Economics and Finance Research IPEDR vol.4 (2011) (2011) IACSIT Press, Singapore A Risk Management System Framework for New Product Development (NPD) Seonmuk Park, Jongseong
Practical Research. Paul D. Leedy Jeanne Ellis Ormrod. Planning and Design. Tenth Edition
 Practical Research Planning and Design Tenth Edition Paul D. Leedy Jeanne Ellis Ormrod 2013, 2010, 2005, 2001, 1997 Pearson Education, Inc. All rights reserved. Chapter 1 The Nature and Tools of Research
Practical Research Planning and Design Tenth Edition Paul D. Leedy Jeanne Ellis Ormrod 2013, 2010, 2005, 2001, 1997 Pearson Education, Inc. All rights reserved. Chapter 1 The Nature and Tools of Research
Design Verification. Introduction
 Design verification is an essential step in the development of any product. Also referred to as qualification testing, design verification ensures that the product as designed is the same as the product
Design verification is an essential step in the development of any product. Also referred to as qualification testing, design verification ensures that the product as designed is the same as the product
SUCCESSFUL INTERFACE RISK MANAGEMENT FROM BLAME CULTURE TO JOINT ACTION
 SUCCESSFUL INTERFACE RISK MANAGEMENT FROM BLAME CULTURE TO JOINT ACTION SUMMARY Axel Kappeler, Principal James Catmur, Director Interfaces are important because they are everywhere. However, interfaces
SUCCESSFUL INTERFACE RISK MANAGEMENT FROM BLAME CULTURE TO JOINT ACTION SUMMARY Axel Kappeler, Principal James Catmur, Director Interfaces are important because they are everywhere. However, interfaces
Comparing Methods to Identify Defect Reports in a Change Management Database
 Comparing Methods to Identify Defect Reports in a Change Management Database Elaine J. Weyuker, Thomas J. Ostrand AT&T Labs - Research 180 Park Avenue Florham Park, NJ 07932 (weyuker,ostrand)@research.att.com
Comparing Methods to Identify Defect Reports in a Change Management Database Elaine J. Weyuker, Thomas J. Ostrand AT&T Labs - Research 180 Park Avenue Florham Park, NJ 07932 (weyuker,ostrand)@research.att.com
4. Critical success factors/objectives of the activity/proposal/project being risk assessed
 ARTC Risk Management Work Instruction 2: 1. Conduct Risk Assessment Workshop This Work Instruction provides general guidelines for conducting a generic Risk Assessment workshop. The instructions supplement
ARTC Risk Management Work Instruction 2: 1. Conduct Risk Assessment Workshop This Work Instruction provides general guidelines for conducting a generic Risk Assessment workshop. The instructions supplement
California State University, Los Angeles Department of Sociology. Guide to Preparing a Masters Thesis Proposal
 California State University, Los Angeles Department of Sociology Guide to Preparing a Masters Thesis Proposal Overview The following few pages provide you with guidelines for writing a Masters thesis proposal.
California State University, Los Angeles Department of Sociology Guide to Preparing a Masters Thesis Proposal Overview The following few pages provide you with guidelines for writing a Masters thesis proposal.
RISK ASSESSMENT BASED UPON FUZZY SET THEORY
 RISK ASSESSMENT BASED UPON FUZZY SET THEORY László POKORÁDI, professor, University of Debrecen pokoradi@mfk.unideb.hu KEYWORDS: risk management; risk assessment; fuzzy set theory; reliability. Abstract:
RISK ASSESSMENT BASED UPON FUZZY SET THEORY László POKORÁDI, professor, University of Debrecen pokoradi@mfk.unideb.hu KEYWORDS: risk management; risk assessment; fuzzy set theory; reliability. Abstract:
REVIEW OF HAZARD IDENTIFICATION TECHNIQUES
 Broad Lane, Sheffield, S3 7HQ Telephone: +44 (0)114 289 2000 Facsimile: +44 (0)114 289 2500 REVIEW OF HAZARD IDENTIFICATION TECHNIQUES HSL/2005/58 Project Leader: John Gould Michael Glossop Agamemnon Ioannides
Broad Lane, Sheffield, S3 7HQ Telephone: +44 (0)114 289 2000 Facsimile: +44 (0)114 289 2500 REVIEW OF HAZARD IDENTIFICATION TECHNIQUES HSL/2005/58 Project Leader: John Gould Michael Glossop Agamemnon Ioannides
DEVELOPING HYPOTHESIS AND
 Shalini Prasad Ajith Rao Eeshoo Rehani DEVELOPING 500 METHODS SEPTEMBER 18 TH 2001 DEVELOPING HYPOTHESIS AND Introduction Processes involved before formulating the hypotheses. Definition Nature of Hypothesis
Shalini Prasad Ajith Rao Eeshoo Rehani DEVELOPING 500 METHODS SEPTEMBER 18 TH 2001 DEVELOPING HYPOTHESIS AND Introduction Processes involved before formulating the hypotheses. Definition Nature of Hypothesis
An Introduction to. Metrics. used during. Software Development
 An Introduction to Metrics used during Software Development Life Cycle www.softwaretestinggenius.com Page 1 of 10 Define the Metric Objectives You can t control what you can t measure. This is a quote
An Introduction to Metrics used during Software Development Life Cycle www.softwaretestinggenius.com Page 1 of 10 Define the Metric Objectives You can t control what you can t measure. This is a quote
LOCAL GOVERNMENT SERVICES JOB EVALUATION SCHEME:
 LOCAL GOVERNMENT SERVICES JOB EVALUATION SCHEME: TECHNICAL NOTE NO. 14: CONSISTENCY CHECKING OF JE OUTCOMES (formerly issued as Quality Assurance NJC circular dated 14Apr03) 1. Introduction 1.1 The NJC
LOCAL GOVERNMENT SERVICES JOB EVALUATION SCHEME: TECHNICAL NOTE NO. 14: CONSISTENCY CHECKING OF JE OUTCOMES (formerly issued as Quality Assurance NJC circular dated 14Apr03) 1. Introduction 1.1 The NJC
Independent Validation of Software Safety Requirements for System of Systems by S. Driskell, J. Murphy, J.B. Michael, M. Shing
 Independent Validation of Software Safety Requirements for System of Systems by S. Driskell, J. Murphy, J.B. Michael, M. Shing Presented by Stephen Driskell Stephen.Driskell@TASC.com Judy Murphy jmurphy@mpl.com
Independent Validation of Software Safety Requirements for System of Systems by S. Driskell, J. Murphy, J.B. Michael, M. Shing Presented by Stephen Driskell Stephen.Driskell@TASC.com Judy Murphy jmurphy@mpl.com
Optimal Replacement of Underground Distribution Cables
 1 Optimal Replacement of Underground Distribution Cables Jeremy A. Bloom, Member, IEEE, Charles Feinstein, and Peter Morris Abstract This paper presents a general decision model that enables utilities
1 Optimal Replacement of Underground Distribution Cables Jeremy A. Bloom, Member, IEEE, Charles Feinstein, and Peter Morris Abstract This paper presents a general decision model that enables utilities
WRITING A CRITICAL ARTICLE REVIEW
 WRITING A CRITICAL ARTICLE REVIEW A critical article review briefly describes the content of an article and, more importantly, provides an in-depth analysis and evaluation of its ideas and purpose. The
WRITING A CRITICAL ARTICLE REVIEW A critical article review briefly describes the content of an article and, more importantly, provides an in-depth analysis and evaluation of its ideas and purpose. The
Space project management
 ECSS-M-ST-80C Space project management Risk management ECSS Secretariat ESA-ESTEC Requirements & Standards Division Noordwijk, The Netherlands Foreword This Standard is one of the series of ECSS Standards
ECSS-M-ST-80C Space project management Risk management ECSS Secretariat ESA-ESTEC Requirements & Standards Division Noordwijk, The Netherlands Foreword This Standard is one of the series of ECSS Standards
Safety of Nuclear Power Plant : Human Reliability Analysis (HRA) Prof. Wolfgang Kröger
 Safety of Nuclear Power Plant : Human Reliability Analysis (HRA) Prof. Wolfgang Kröger (http://www.riskcenter.ethz.ch, kroeger@ethz.ch) Human influence on operation and safety of a system such as anpp
Safety of Nuclear Power Plant : Human Reliability Analysis (HRA) Prof. Wolfgang Kröger (http://www.riskcenter.ethz.ch, kroeger@ethz.ch) Human influence on operation and safety of a system such as anpp
Risk Management and the Impact of EN ISO 14971:2012 Annex Z
 Risk Management and the Impact of EN ISO 14971:2012 Annex Z BSI 2014 Medical Device Mini-Roadshow Ibim Tariah Ph.D Technical Director, Healthcare Solutions Copyright 2014 BSI. All rights reserved. 1 Risk
Risk Management and the Impact of EN ISO 14971:2012 Annex Z BSI 2014 Medical Device Mini-Roadshow Ibim Tariah Ph.D Technical Director, Healthcare Solutions Copyright 2014 BSI. All rights reserved. 1 Risk
ThinkReliability. Six Common Errors when Solving Problems. Solve Problems. Prevent Problems.
 Six Common Errors when Solving Problems Mark Galley Organizations apply a variety of tools to solve problems, improve operations and increase reliability many times without success. Why? More than likely,
Six Common Errors when Solving Problems Mark Galley Organizations apply a variety of tools to solve problems, improve operations and increase reliability many times without success. Why? More than likely,
White paper. Corrective action: The closed-loop system
 White paper Corrective action: The closed-loop system Contents Summary How corrective action works The steps 1 - Identify non-conformities - Opening a corrective action 6 - Responding to a corrective action
White paper Corrective action: The closed-loop system Contents Summary How corrective action works The steps 1 - Identify non-conformities - Opening a corrective action 6 - Responding to a corrective action
Chapter 10. Key Ideas Correlation, Correlation Coefficient (r),
 Chapter 0 Key Ideas Correlation, Correlation Coefficient (r), Section 0-: Overview We have already explored the basics of describing single variable data sets. However, when two quantitative variables
Chapter 0 Key Ideas Correlation, Correlation Coefficient (r), Section 0-: Overview We have already explored the basics of describing single variable data sets. However, when two quantitative variables
Audit Readiness Lessons Learned
 Audit Readiness Lessons Learned Four Tips for Achieving a Smooth Audit It seems obvious: Prepare well and prepare ahead of time and the year-end audit does not have to be the painful experience most organizations
Audit Readiness Lessons Learned Four Tips for Achieving a Smooth Audit It seems obvious: Prepare well and prepare ahead of time and the year-end audit does not have to be the painful experience most organizations
Conn Valuation Services Ltd.
 CAPITALIZED EARNINGS VS. DISCOUNTED CASH FLOW: Which is the more accurate business valuation tool? By Richard R. Conn CMA, MBA, CPA, ABV, ERP Is the capitalized earnings 1 method or discounted cash flow
CAPITALIZED EARNINGS VS. DISCOUNTED CASH FLOW: Which is the more accurate business valuation tool? By Richard R. Conn CMA, MBA, CPA, ABV, ERP Is the capitalized earnings 1 method or discounted cash flow
Teaching & Learning Plans. Plan 1: Introduction to Probability. Junior Certificate Syllabus Leaving Certificate Syllabus
 Teaching & Learning Plans Plan 1: Introduction to Probability Junior Certificate Syllabus Leaving Certificate Syllabus The Teaching & Learning Plans are structured as follows: Aims outline what the lesson,
Teaching & Learning Plans Plan 1: Introduction to Probability Junior Certificate Syllabus Leaving Certificate Syllabus The Teaching & Learning Plans are structured as follows: Aims outline what the lesson,
3. Logical Reasoning in Mathematics
 3. Logical Reasoning in Mathematics Many state standards emphasize the importance of reasoning. We agree disciplined mathematical reasoning is crucial to understanding and to properly using mathematics.
3. Logical Reasoning in Mathematics Many state standards emphasize the importance of reasoning. We agree disciplined mathematical reasoning is crucial to understanding and to properly using mathematics.
Viewpoint on ISA TR84.0.02 Simplified Methods and Fault Tree Analysis Angela E. Summers, Ph.D., P.E., President
 Viewpoint on ISA TR84.0.0 Simplified Methods and Fault Tree Analysis Angela E. Summers, Ph.D., P.E., President Presented at Interkama, Dusseldorf, Germany, October 1999, Published in ISA Transactions,
Viewpoint on ISA TR84.0.0 Simplified Methods and Fault Tree Analysis Angela E. Summers, Ph.D., P.E., President Presented at Interkama, Dusseldorf, Germany, October 1999, Published in ISA Transactions,
Interrelationship with other "Ability Engineering" and Logistics Groups
 Reliability and Maintainability Programs General This section introduces high level considerations associated with the implementation of Reliability, Availability, Maintainability, Safety (RAMS) and Logistics
Reliability and Maintainability Programs General This section introduces high level considerations associated with the implementation of Reliability, Availability, Maintainability, Safety (RAMS) and Logistics
Introduction: ITIL Version 3 and the ITIL Process Map V3
 Introduction: ITIL Version 3 and the ITIL Process Map V3 IT Process Maps www.it-processmaps.com IT Process Know-How out of a Box IT Process Maps GbR, 2009-2 - Contents HISTORY OF ITIL... 4 The Beginnings...
Introduction: ITIL Version 3 and the ITIL Process Map V3 IT Process Maps www.it-processmaps.com IT Process Know-How out of a Box IT Process Maps GbR, 2009-2 - Contents HISTORY OF ITIL... 4 The Beginnings...
Effective Techniques for Risk Measurement. Agenda
 Effective Techniques for Risk Measurement Steven Ross Executive Principal Risk Masters, Inc. Agenda The Failure of Current Techniques A Fresh Approach to Risk Measurement The Theory Behind the Techniques
Effective Techniques for Risk Measurement Steven Ross Executive Principal Risk Masters, Inc. Agenda The Failure of Current Techniques A Fresh Approach to Risk Measurement The Theory Behind the Techniques
QUALITY TOOLBOX. Understanding Processes with Hierarchical Process Mapping. Robert B. Pojasek. Why Process Mapping?
 QUALITY TOOLBOX Understanding Processes with Hierarchical Process Mapping In my work, I spend a lot of time talking to people about hierarchical process mapping. It strikes me as funny that whenever I
QUALITY TOOLBOX Understanding Processes with Hierarchical Process Mapping In my work, I spend a lot of time talking to people about hierarchical process mapping. It strikes me as funny that whenever I
Criticality Analysis for COTS Software Components. Fan Ye; University of York, York, UK Tim Kelly; University of York, York, UK
 Criticality Analysis for COTS Software Components Fan Ye; University of York, York, UK Tim Kelly; University of York, York, UK Keywords: COTS, Safety-Critical System, Criticality Analysis Abstract Understanding
Criticality Analysis for COTS Software Components Fan Ye; University of York, York, UK Tim Kelly; University of York, York, UK Keywords: COTS, Safety-Critical System, Criticality Analysis Abstract Understanding
Development of a Safety Knowledge Base
 Development of a Safety Knowledge Base Philip R. Lewis Chief Engineer J&P Technologies Abstract The salient features of the proposed Safety Knowledge Base, an integrated toolset for tying together Hazard
Development of a Safety Knowledge Base Philip R. Lewis Chief Engineer J&P Technologies Abstract The salient features of the proposed Safety Knowledge Base, an integrated toolset for tying together Hazard
Session 4. System Engineering Management. Session Speaker : Dr. Govind R. Kadambi. M S Ramaiah School of Advanced Studies 1
 Session 4 System Engineering Management Session Speaker : Dr. Govind R. Kadambi M S Ramaiah School of Advanced Studies 1 Session Objectives To learn and understand the tasks involved in system engineering
Session 4 System Engineering Management Session Speaker : Dr. Govind R. Kadambi M S Ramaiah School of Advanced Studies 1 Session Objectives To learn and understand the tasks involved in system engineering
Summary of assessment and checklist for the new GCE Health and Social Care Unit HSC08 (optional)
 Summary of assessment and checklist for the new GCE Health and Social Care Unit HSC08 (optional) The summary should be used in conjunction with the new specification available for teaching from September
Summary of assessment and checklist for the new GCE Health and Social Care Unit HSC08 (optional) The summary should be used in conjunction with the new specification available for teaching from September
DEPENDABILITY STUDY OF THE ERP SYSTEM
 Dependability, ERP system, availability Daniel GĄSKA *, Antoni ŚWIĆ ** DEPENDABILITY STUDY OF THE ERP SYSTEM Abstract The paper present the various aspects of the process of testing of the ERP system s
Dependability, ERP system, availability Daniel GĄSKA *, Antoni ŚWIĆ ** DEPENDABILITY STUDY OF THE ERP SYSTEM Abstract The paper present the various aspects of the process of testing of the ERP system s
META DATA QUALITY CONTROL ARCHITECTURE IN DATA WAREHOUSING
 META DATA QUALITY CONTROL ARCHITECTURE IN DATA WAREHOUSING Ramesh Babu Palepu 1, Dr K V Sambasiva Rao 2 Dept of IT, Amrita Sai Institute of Science & Technology 1 MVR College of Engineering 2 asistithod@gmail.com
META DATA QUALITY CONTROL ARCHITECTURE IN DATA WAREHOUSING Ramesh Babu Palepu 1, Dr K V Sambasiva Rao 2 Dept of IT, Amrita Sai Institute of Science & Technology 1 MVR College of Engineering 2 asistithod@gmail.com
With the introduction of GAMP 5, A
 Online Exclusive from PHARMACEUTICAL ENGINEERING The Official Magazine of ISPE January/February 2012, Vol. 32 No. 1 www.pharmaceuticalengineering.org Copyright ISPE 2012 This article presents the case
Online Exclusive from PHARMACEUTICAL ENGINEERING The Official Magazine of ISPE January/February 2012, Vol. 32 No. 1 www.pharmaceuticalengineering.org Copyright ISPE 2012 This article presents the case
6.3 Conditional Probability and Independence
 222 CHAPTER 6. PROBABILITY 6.3 Conditional Probability and Independence Conditional Probability Two cubical dice each have a triangle painted on one side, a circle painted on two sides and a square painted
222 CHAPTER 6. PROBABILITY 6.3 Conditional Probability and Independence Conditional Probability Two cubical dice each have a triangle painted on one side, a circle painted on two sides and a square painted
Accident Investigation
 Accident Investigation ACCIDENT INVESTIGATION/adentcvr.cdr/1-95 ThisdiscussionistakenfromtheU.S.Department oflabor,minesafetyandhealthadministration Safety Manual No. 10, Accident Investigation, Revised
Accident Investigation ACCIDENT INVESTIGATION/adentcvr.cdr/1-95 ThisdiscussionistakenfromtheU.S.Department oflabor,minesafetyandhealthadministration Safety Manual No. 10, Accident Investigation, Revised
Research Design and Research Methods
 CHAPTER 3 Research Design and Research Methods Overview This chapter uses an emphasis on research design to discuss qualitative, quantitative, and mixed methods research as three major approaches to research
CHAPTER 3 Research Design and Research Methods Overview This chapter uses an emphasis on research design to discuss qualitative, quantitative, and mixed methods research as three major approaches to research
Edwin Lindsay Principal Consultant. Compliance Solutions (Life Sciences) Ltd, Tel: + 44 (0) 7917134922 E-Mail: elindsay@blueyonder.co.
 Edwin Lindsay Principal Consultant, Tel: + 44 (0) 7917134922 E-Mail: elindsay@blueyonder.co.uk There were no guidelines/ regulations There was no training No Procedures No Inspectors Inform All staff of
Edwin Lindsay Principal Consultant, Tel: + 44 (0) 7917134922 E-Mail: elindsay@blueyonder.co.uk There were no guidelines/ regulations There was no training No Procedures No Inspectors Inform All staff of
Procurement Programmes & Projects P3M3 v2.1 Self-Assessment Instructions and Questionnaire. P3M3 Project Management Self-Assessment
 Procurement Programmes & Projects P3M3 v2.1 Self-Assessment Instructions and Questionnaire P3M3 Project Management Self-Assessment Contents Introduction 3 User Guidance 4 P3M3 Self-Assessment Questionnaire
Procurement Programmes & Projects P3M3 v2.1 Self-Assessment Instructions and Questionnaire P3M3 Project Management Self-Assessment Contents Introduction 3 User Guidance 4 P3M3 Self-Assessment Questionnaire
