USING ULTRALIGHT C VERSION
|
|
|
- Thomas Woods
- 7 years ago
- Views:
Transcription
1 USING ULTRALIGHT C VERSION
2 TABLE OF CONTENTS 1 Overview Required Reading Document Scope Memory Structure Lock Bytes Authentication Using Write Lock Features for Ultralight C Details Write Lock Bytes using Write Command Lock Bytes at Address 0x Example 1 Lock Block 0x05 and 0x0A From Writing Example 2 Locking Lock bits for Blocks Lock Bytes at Address 0x Example 3 Lock Block 0x24 to 0x27 and AUTH1 From Writing Get Lock Status Command Example Get lock status of block 0x Using Authentication Features for Ultralight C Details Write Authentication Key with Write Command Example Write Authentication Password 0x A0B0C0D0E0F Write Authentication Configuration with Write Command Example Write AUTH0 to 0x10 to restrict tag access beyond address 0x Authenticate Command Example Authenticate tag with key 0x A0B0C0D0E0F References Revision History:...14
3 1 Overview 1.1 Required Reading This document assumes you have read and are familiar with the SkyeTek Protocol V3 Reference Guide and the SkyeTek Protocol V3 Basic Examples application note. 1.2 Document Scope This application note describes how to use special features of Ultralight C (ULC) tags with the M2 and M4 modules. ULC tags have 2 special features that can be accessed using SkyeTek Protocol v3 without requiring familiarity with detailed ULC tag operations. 1.3 Memory Structure There are 192 total bytes of memory, of which 144 bytes are user memory. The memory organization of ULC tags is illustrated below: 1.4 Lock Bytes Figure 1 ULC Memory Organization [1] The write locking feature is an extension of the write locking feature also available in the Ultralight tags. There is more memory in the ULC tag, so additional lock bytes were added. The lock bytes are located at bytes 2/3 of block 0x02 and bytes 0/1 of block 0x28. These bytes control which blocks of memory are locked from being written. Bits in the lock bytes are one time settable and cannot be returned to zeros. This means that ONCE A BLOCK IS SET TO READ-ONLY IT CAN NEVER BE RETURNED TO A WRITABLE STATE. The use
4 of lock bytes is described in detail in next section of this application note. The functions described in detail are: Write Lock Bytes Get Lock Status 1.5 Authentication The authentication feature is a new security capability added to the ULC tag and not supported by standard Ultralight tags. ULC authentication gives users the ability to secure sections of user memory from write or read/write with a 128-bit key. The ULC tag uses 3DES authentication to verify that both the reader and tag have the same key before granting access to secure sections. The authentication features described in detail are: Write Authentication Configuration Write Authentication Key Authenticate
5 2 Using Write Lock Features for Ultralight C 2.1 Details Locking blocks of memory from write access is achieved through normal write tag commands to specific blocks of memory. The ULC tag contains 2 lock bytes located at block address 0x02 and 0x28. The lock byte at 0x02 controls write access to memory blocks 0x03 0x0F. The lock byte at 0x28 controls write access to memory blocks 0x10 0x2F. Once a bit is set in any of the lock bytes it cannot be unset, so changes to these bytes are IRREVERSIBLE. Full detailed information about these lock bytes can be found in the Ultralight C datasheet[1]. A short description of the lock bytes and how to use the SkyeTek Protocol v3 to set them is described in the following sections. 2.2 Write Lock Bytes using Write Command Lock Bytes at Address 0x02 The layout of lock bytes at address 0x02 are shown below: Figure 2 Lock bytes 0 and 1 [1] Setting a 1 to lock bits labeled Lock Page X corresponds to locking the specified Page (equivalent to a block) for read-only access. Setting a 1 to the Block Locking Lockbits X makes the corresponding Lock Page bits uneditable. These bits essentially lock the read/write access for the selected pages.
6 2.2.2 Example 1 Lock Block 0x05 and 0x0A From Writing Request in ASCII: Len Addr # of Blocks <CR> A8589A <CR> Sets bit 5 of lock byte 0 and bit 2 of lock byte 1 as illustrated in figure 2 Italicized section is the ID Bold section is the lock bytes for success: <LF> 0103 <CR> <LF> Example 2 Locking Lock bits for Blocks 4-9 Request in ASCII: Len Addr # of Blocks <CR> A8589A <CR> Sets bit 2 of lock byte 0 as illustrated in figure 2 Italicized section is the ID Bold section is the lock bytes for success: <LF> 0103 <CR> <LF>
7 2.2.4 Lock Bytes at Address 0x28 The layout of lock bytes at address 0x28 are shown below: Figure 3 Lock bytes 2 and 3 [1] Setting a 1 to lock bits labeled Lock Page X-X corresponds to locking the specified Pages (equivalent to blocks) for read-only access. Setting a 1 to the Block Locking Lockbits X makes the corresponding Lock Page bits uneditable. These bits essentially lock the read/write access for the selected pages. Note that figure 3 above also references the Key, Auth0 and Auth1. These correspond to sections of memory 0x2A- 0x2F, which are used for the authentication feature described in detail in later sections of this application note Example 3 Lock Block 0x24 to 0x27 and AUTH1 From Writing Request in ASCII: Len Addr # of Blocks <CR> A8589A <CR> Sets bit 7 of lock byte 2 and bit 6 of lock byte 3 as illustrated in figure 3 Italicized section is the ID Bold section is the lock bytes for success: <LF> 0103 <CR> <LF>
8 2.3 Get Lock Status Command The Get Lock Status command is a simple SkyeTek Protocol v3 command that checks whether a specified block is locked and returns the status Example Get lock status of block 0x05 Request in ASCII: Len <CR> A8589A <CR> Requests lock status of block 0x05 Italicized section is the ID Bold section is the block address in question : <LF> <CR> <LF> Bold section is the lock status o 0x00 for not locked o 0x01 for locked
9 3 Using Authentication Features for Ultralight C 3.1 Details The security feature of the ULC tag allows the user to lock some or all of the tag memory from reading or writing. The amount of memory locked and whether the memory is locked only from writing or from reading and writing is set by writing specific values to the AUTH0 and AUTH1 bytes of tag memory. This is detailed in the section below titled Write Authentication Configuration with Write Command. Typical ULC tags come from the manufacturer with no memory restricted, allowing the user access to write their own authentication key and change the authentication configuration freely. The 128-bit 3DES authentication key can be set on a tag as described in the following section. Once access to secure memory is restricted, it can only be accessed by sending the authentication key as described in the Authenticate Command section below. 3.2 Write Authentication Key with Write Command The authentication key is stored in address 0x2C-0x2F. Note that this area of tag memory is not readable. It can only be written to if the value of AUTH0 is 0x30, which is the typical default value from the tag manufacturer. The authentication key is stored in memory as shown below: Figure 4 Authentication Key Memory Configuration [1] The authentication key is stored in tag memory in little-endian format while it is sent in big-endian format for authentication. This can cause some confusion. Basically when you write the key to memory, it is written backwards. The data is sent to the reader in the order shown below: Key1 [K0][K1][K2][K3][K4][K5][K6][K7], Key2 [K0][K1][K2][K3][K4][K5][K6][K7]
10 3.2.1 Example Write Authentication Password 0x A0B0C0D0E0F Request in ASCII: Len Addr # of Blocks <CR> A8589A C F0E0D0C0B0A0908 <CR> Sets authentication key (Starting address 0x2C) Italicized section is the ID Bold section is the key value sent in the order described in the previous section for success: <LF> 0103 <CR> <LF> 3.3 Write Authentication Configuration with Write Command The configuration of the authentication feature on ULC tags is stored in the last blocks of the tag, 0x2A 0x2F. The configuration is stored as follows: Address 0x2A o Byte 0 is AUTH0 o AUTH0 sets the block address from which authentication is required o EX: If AUTH0 is 0x10, Authentication is required for access to all data from address 0x10 to the end of the tag memory 0x2F o Typical default value is 0x30 (no authentication required) Address 0x2B o Byte 0 is AUTH1 o AUTH1 sets the write access for all memory defined in AUTH0 o Value of 0x80 means only write access is restricted o Value of 0x00 means read and write access is restricted o Typical default value is 0x80 (write restrictions) Address 0x2C 0x2F 16 bytes makes up 128 bit Authentication Key Writing authentication configuration is done with a write tag command at the correct address. This is illustrated in the following example.
11 3.3.1 Example Write AUTH0 to 0x10 to restrict tag access beyond address 0x10 Request in ASCII: Len Addr # of Blocks <CR> A8589A A <CR> Sets AUTH0 to 0x10 Italicized section is the ID First Bold section is the address (0x2A for AUTH0) Second Bold section in the AUTH0 value for success: <LF> 0103 <CR> <LF> 3.4 Authenticate Command The authenticate tag command is used to send the authentication key to a tag to gain access to restricted sections of tag memory. A series of commands is needed to select the tag, create a session with the tag, and then authenticate the tag. All commands during authentication and once authenticated must be sent with the RF flag on, because as soon as the tag loses power it will lose its authentication state. The RF flag ensures that the tag maintains power as long as it is within the field of the reader antenna. The example below will show how to get a ULC tag into the authenticated state with the authentication key written in the previous section. Note that the authentication key is now sent big endian as illustrated below: Key1 [K7][K6][K5][K4][K3][K2][K1][K0], Key2 [K7][K6][K5][K4][K3][K2][K1][K0]
12 3.4.1 Example Authenticate tag with key 0x A0B0C0D0E0F First Request in ASCII: Len <CR> A8589A72780 <CR> Selects the tag with the specified tag in the field and creates a session (RF and flags set) Italicized section is the ID for success: <LF> XX <CR> <LF> Bold section is the session number used in the next command Second Request in ASCII: Session Addr <CR> 0C XX A0B0C0DE0F <CR> Authenticate tag command (With RF,, and Session flags) First bold section is the session number noted in the previous step Second bold section is the authentication key sent big-endian for success: <LF > 0201 <CR> <LF>
13 4 References [1] MF0ICU2 - MIFARE Ultralight C (v.3.2) Product short data sheet NXP
14 5 Revision History: Revision Author Change Brad Alcorn Initial Release Brad Alcorn Fixed errors in Lock bits examples Ryan Smith Updated Overview Section
USING MIFARE CLASSIC TAGS VERSION 100212
 USING MIFARE CLASSIC TAGS VERSION 100212 U s i n g M I F A R E C l a s s i c T a g s P a g e 2 TABLE OF CONTENTS 1 Overview... 4 1.1 Required Reading... 4 1.2 Document Scope... 4 1.3 MIFARE Features...
USING MIFARE CLASSIC TAGS VERSION 100212 U s i n g M I F A R E C l a s s i c T a g s P a g e 2 TABLE OF CONTENTS 1 Overview... 4 1.1 Required Reading... 4 1.2 Document Scope... 4 1.3 MIFARE Features...
RFID MODULE Mifare Reader / Writer SL030 User Manual Version 2.6 Nov 2012 StrongLink
 RFID MODULE Mifare Reader / Writer User Manual Version 2.6 Nov 2012 StrongLink CONTENT 1. MAIN FEATURES... 3 2. PINNING INFORMATION... 4 3. DEVICE OPERATION... 5 3-1. Clock and Data Transitions:... 5 3-2.
RFID MODULE Mifare Reader / Writer User Manual Version 2.6 Nov 2012 StrongLink CONTENT 1. MAIN FEATURES... 3 2. PINNING INFORMATION... 4 3. DEVICE OPERATION... 5 3-1. Clock and Data Transitions:... 5 3-2.
RFID MODULE Mifare Reader / Writer SL025B User Manual Version 1.4 Nov 2012 StrongLink
 RFID MODULE Mifare Reader / Writer User Manual Version 1.4 Nov 2012 StrongLink CONTENT 1. MAIN FEATURES... 3 2. PINNING INFORMATION... 4 3. BAUD RATE SETTING... 5 4. COMMUNICATION PROTOCOL... 5 4-1. COMMUNICATION
RFID MODULE Mifare Reader / Writer User Manual Version 1.4 Nov 2012 StrongLink CONTENT 1. MAIN FEATURES... 3 2. PINNING INFORMATION... 4 3. BAUD RATE SETTING... 5 4. COMMUNICATION PROTOCOL... 5 4-1. COMMUNICATION
Exercise 1: Set up the Environment
 RFID Lab Gildas Avoine, 2014 Contact: gildas.avoine@irisa.fr Objective: Learn how much it is easy to read contactless tags, possibly simulate/clone. Requirement: Hardware: Reader SCL3711 or ACR122, Reader
RFID Lab Gildas Avoine, 2014 Contact: gildas.avoine@irisa.fr Objective: Learn how much it is easy to read contactless tags, possibly simulate/clone. Requirement: Hardware: Reader SCL3711 or ACR122, Reader
USB Card Reader Configuration Utility. User Manual. Draft!
 USB Card Reader Configuration Utility User Manual Draft! SB Research 2009 The Configuration Utility for USB card reader family: Concept: To allow for field programming of the USB card readers a configuration
USB Card Reader Configuration Utility User Manual Draft! SB Research 2009 The Configuration Utility for USB card reader family: Concept: To allow for field programming of the USB card readers a configuration
RFID MODULE Mifare Reader / Writer SL031 User Manual Version 2.7 Nov 2012 StrongLink
 RFID MODULE Mifare Reader / Writer User Manual Version 2.7 Nov 2012 StrongLink CONTENT 1. MAIN FEATURES... 3 2. PINNING INFORMATION... 4 3. BAUD RATE SETTING... 5 4. COMMUNICATION PROTOCOL... 5 4-1. Communication
RFID MODULE Mifare Reader / Writer User Manual Version 2.7 Nov 2012 StrongLink CONTENT 1. MAIN FEATURES... 3 2. PINNING INFORMATION... 4 3. BAUD RATE SETTING... 5 4. COMMUNICATION PROTOCOL... 5 4-1. Communication
RFID MODULE Mifare Reader / Writer SL032 User Manual Version 1.5 Nov 2012 StrongLink
 RFID MODULE Mifare Reader / Writer User Manual Version 1.5 Nov 2012 StrongLink CONTENT 1. MAIN FEATURES... 3 2. PINNING INFORMATION... 4 3. BAUD RATE SETTING... 5 4. COMMUNICATION PROTOCOL... 5 4-1. Communication
RFID MODULE Mifare Reader / Writer User Manual Version 1.5 Nov 2012 StrongLink CONTENT 1. MAIN FEATURES... 3 2. PINNING INFORMATION... 4 3. BAUD RATE SETTING... 5 4. COMMUNICATION PROTOCOL... 5 4-1. Communication
Gemalto Mifare 1K Datasheet
 Gemalto Mifare 1K Datasheet Contents 1. Overview...3 1.1 User convenience and speed...3 1.2 Security...3 1.3 Anticollision...3 2. Gemalto Mifare Features...4 2.1 Compatibility with norms...4 2.2 Electrical...4
Gemalto Mifare 1K Datasheet Contents 1. Overview...3 1.1 User convenience and speed...3 1.2 Security...3 1.3 Anticollision...3 2. Gemalto Mifare Features...4 2.1 Compatibility with norms...4 2.2 Electrical...4
AN1305. MIFARE Classic as NFC Type MIFARE Classic Tag. Application note COMPANY PUBLIC. Rev. 1.3 2 October 2012 130513. Document information
 MIFARE Classic as NFC Type MIFARE Classic Tag Document information Info Content Keywords NFC Forum, NFC data mapping, MIFARE Classic 1K/4K, MIFARE Classic 1K, MIFARE Classic 4K, MIFARE Plus X/S, NFC Type
MIFARE Classic as NFC Type MIFARE Classic Tag Document information Info Content Keywords NFC Forum, NFC data mapping, MIFARE Classic 1K/4K, MIFARE Classic 1K, MIFARE Classic 4K, MIFARE Plus X/S, NFC Type
Smart Card Application Standard Draft
 Smart Card Application Standard Draft Contents 1 SCOPE... 6 1.1 DEFINITIONS / DOCUMENT CONVENTIONS... 6 2 KEY DATA ELEMENTS AND CONCEPTS... 7 2.1 STATIC CARD INFORMATION... 7 2.1.1 Card ID (CdID)... 7
Smart Card Application Standard Draft Contents 1 SCOPE... 6 1.1 DEFINITIONS / DOCUMENT CONVENTIONS... 6 2 KEY DATA ELEMENTS AND CONCEPTS... 7 2.1 STATIC CARD INFORMATION... 7 2.1.1 Card ID (CdID)... 7
AN1304. NFC Type MIFARE Classic Tag Operation. Application note PUBLIC. Rev. 1.3 2 October 2012 130413. Document information
 NFC Type MIFARE Classic Tag Operation Document information Info Content Keywords NDEF, NDEF data mapping, NDEF Data Exchange Format MIFARE Classic 1K, MIFARE Classic 4K, MIFARE Classic 1K/4K, MIFARE Plus
NFC Type MIFARE Classic Tag Operation Document information Info Content Keywords NDEF, NDEF data mapping, NDEF Data Exchange Format MIFARE Classic 1K, MIFARE Classic 4K, MIFARE Classic 1K/4K, MIFARE Plus
Application Programming Interface
 Application Programming Interface Advanced Card Systems Ltd. Website: www.acs.com.hk Email: info@acs.com.hk CONTENTS Introduction 4 Features 4 USB interface 4 Contact and Contactless interface handling
Application Programming Interface Advanced Card Systems Ltd. Website: www.acs.com.hk Email: info@acs.com.hk CONTENTS Introduction 4 Features 4 USB interface 4 Contact and Contactless interface handling
ACR122 NFC Contactless Smart Card Reader
 Datenblatt / Specifications ACR122 NFC Contactless Smart Card Reader Table of Contents 1. Introduction... 3 1.1. USB Interface... 3 2. Implementation... 4 2.1. Smart Card Reader Interface Overview... 5
Datenblatt / Specifications ACR122 NFC Contactless Smart Card Reader Table of Contents 1. Introduction... 3 1.1. USB Interface... 3 2. Implementation... 4 2.1. Smart Card Reader Interface Overview... 5
SKYEMODULE GEMINI DATASHEET VERSION 040913
 SKYEMODULE GEMINI DATASHEET VERSION 040913 SkyeModule Gemini Datasheet Page 2 COPYRIGHT INFORMATION: Copyright 2013 SkyeTek, Inc., 1525 Market St. Suite 200, Denver, Colorado 80202, U.S.A. All rights reserved.
SKYEMODULE GEMINI DATASHEET VERSION 040913 SkyeModule Gemini Datasheet Page 2 COPYRIGHT INFORMATION: Copyright 2013 SkyeTek, Inc., 1525 Market St. Suite 200, Denver, Colorado 80202, U.S.A. All rights reserved.
Application Note. Introduction AN2471/D 3/2003. PC Master Software Communication Protocol Specification
 Application Note 3/2003 PC Master Software Communication Protocol Specification By Pavel Kania and Michal Hanak S 3 L Applications Engineerings MCSL Roznov pod Radhostem Introduction The purpose of this
Application Note 3/2003 PC Master Software Communication Protocol Specification By Pavel Kania and Michal Hanak S 3 L Applications Engineerings MCSL Roznov pod Radhostem Introduction The purpose of this
MF1 IC S50. 1. General description. Functional specification. 1.1 Contactless Energy and Data Transfer. 1.2 Anticollision. Energy
 Rev. 5.2 15 January 2007 Product data sheet 001052 PUBLIC 1. General description NXP has developed the Mifare to be used in contactess smart cards according to ISO/IEC 14443A. The communication layer (
Rev. 5.2 15 January 2007 Product data sheet 001052 PUBLIC 1. General description NXP has developed the Mifare to be used in contactess smart cards according to ISO/IEC 14443A. The communication layer (
Exam 1 Review Questions
 CSE 473 Introduction to Computer Networks Exam 1 Review Questions Jon Turner 10/2013 1. A user in St. Louis, connected to the internet via a 20 Mb/s (b=bits) connection retrieves a 250 KB (B=bytes) web
CSE 473 Introduction to Computer Networks Exam 1 Review Questions Jon Turner 10/2013 1. A user in St. Louis, connected to the internet via a 20 Mb/s (b=bits) connection retrieves a 250 KB (B=bytes) web
Technical Support Bulletin Nr.18 Modbus Tips
 Technical Support Bulletin Nr.18 Modbus Tips Contents! Definitions! Implemented commands! Examples of commands or frames! Calculating the logical area! Reading a signed variable! Example of commands supported
Technical Support Bulletin Nr.18 Modbus Tips Contents! Definitions! Implemented commands! Examples of commands or frames! Calculating the logical area! Reading a signed variable! Example of commands supported
Command Param1 Param2 Return1 Return2 Description. 0xE9 0..0x7F (id) speed pos_high pos_low Set servo #id speed & read position
 set Description 0..0x7F (id) Set servo #id target position 0xE1 Read EEPROM 0xE2 Write EEPROM 0xE3 Read memory 0xE4 Write memory 0xE5 Read position 0xE6 Set target position 0xE7 version id Read version
set Description 0..0x7F (id) Set servo #id target position 0xE1 Read EEPROM 0xE2 Write EEPROM 0xE3 Read memory 0xE4 Write memory 0xE5 Read position 0xE6 Set target position 0xE7 version id Read version
SL2 ICS53/SL2 ICS54. 1. General description I CODE SLI-S/I CODE SLI-S HC. 1.1 Anticollision. 1.2 Contactless energy and data transfer
 Rev. 3.0 14 March 2007 Product data sheet 113730 1. General description The IC is a dedicated chip for smart label applications with the need for a higher security level, larger memory and/or a product
Rev. 3.0 14 March 2007 Product data sheet 113730 1. General description The IC is a dedicated chip for smart label applications with the need for a higher security level, larger memory and/or a product
PCI IDE Controller. Specification. Revision 1.0
 PCI IDE Controller Specification Revision 1.0 3/4/94 1.0. Introduction This document defines the necessary characteristics of a PCI-based IDE controller so that device independent software (i.e.; BIOSes)
PCI IDE Controller Specification Revision 1.0 3/4/94 1.0. Introduction This document defines the necessary characteristics of a PCI-based IDE controller so that device independent software (i.e.; BIOSes)
Field Software Updates Using TPMS LF An example using the Low Frequency radio (LFR) for wireless software updating
 Freescale Semiconductor Document Number: AN5149 Application Note Rev. 1.0, 8/2015 Field Software Updates Using TPMS LF An example using the Low Frequency radio (LFR) for wireless software updating 1 Introduction
Freescale Semiconductor Document Number: AN5149 Application Note Rev. 1.0, 8/2015 Field Software Updates Using TPMS LF An example using the Low Frequency radio (LFR) for wireless software updating 1 Introduction
Supporting ZDOs with the XBee API
 Supporting ZDOs with the XBee API The ZigBee Device Profile is a management and discovery service layer supported on all ZigBee devices. Like all other profiles, the ZigBee Device Profile defines a set
Supporting ZDOs with the XBee API The ZigBee Device Profile is a management and discovery service layer supported on all ZigBee devices. Like all other profiles, the ZigBee Device Profile defines a set
2015/02/07 05:41 1/23 WIZ550WEB Users' Guide
 2015/02/07 05:41 1/23 WIZ550WEB Users' Guide WIZ550WEB Users' Guide Overview WIZ550web provides the lightweight webserver operating. It controls digital output or monitors digital and analogue input through
2015/02/07 05:41 1/23 WIZ550WEB Users' Guide WIZ550WEB Users' Guide Overview WIZ550web provides the lightweight webserver operating. It controls digital output or monitors digital and analogue input through
AN11004. MIFARE DESFire as Type 4 Tag. Rev. 2.4 22 May 2013 130224. Application note COMPANY PUBLIC. Document information.
 Document information Info Content Keywords NFC Forum, NFC Forum data mapping, NFC Forum Type 4 Tag Operation version 2.0, Type 4 Tag version 2.0, MIFARE DESFire EV1, NDEF Tag Application Abstract The NFC
Document information Info Content Keywords NFC Forum, NFC Forum data mapping, NFC Forum Type 4 Tag Operation version 2.0, Type 4 Tag version 2.0, MIFARE DESFire EV1, NDEF Tag Application Abstract The NFC
Table 1 below is a complete list of MPTH commands with descriptions. Table 1 : MPTH Commands. Command Name Code Setting Value Description
 MPTH: Commands Table 1 below is a complete list of MPTH commands with descriptions. Note: Commands are three bytes long, Command Start Byte (default is 128), Command Code, Setting value. Table 1 : MPTH
MPTH: Commands Table 1 below is a complete list of MPTH commands with descriptions. Note: Commands are three bytes long, Command Start Byte (default is 128), Command Code, Setting value. Table 1 : MPTH
How to use KEPServerEX OPC Server (Kepware) with iologik 4000 (Modbus TCP/IP NA-4010 and Modbus Serial NA-4020/NA-4021)
 with iologik 4000 (Modbus TCP/IP NA-4010 and Modbus Serial NA-4020/NA-4021) Alex Chen, Senior Engineer, Moxa Technical Support Dept. In this Technical Note, we cover the following topics: 1. How to export
with iologik 4000 (Modbus TCP/IP NA-4010 and Modbus Serial NA-4020/NA-4021) Alex Chen, Senior Engineer, Moxa Technical Support Dept. In this Technical Note, we cover the following topics: 1. How to export
Bluetooth HID Profile
 RN-WIFLYCR-UM-.01 RN-HID-UM Bluetooth HID Profile 2012 Roving Networks. All rights reserved. Version 1.0r 1/17/2012 USER MANUAL www.rovingnetworks.com 1 OVERVIEW Roving Networks Bluetooth modules support
RN-WIFLYCR-UM-.01 RN-HID-UM Bluetooth HID Profile 2012 Roving Networks. All rights reserved. Version 1.0r 1/17/2012 USER MANUAL www.rovingnetworks.com 1 OVERVIEW Roving Networks Bluetooth modules support
Connecting AMD Flash Memory to a System Address Bus
 Connecting AMD Memory to a System Address Bus Application Note This document is intended to clarify how memories may be connected to a system address bus and how software should issue device commands to
Connecting AMD Memory to a System Address Bus Application Note This document is intended to clarify how memories may be connected to a system address bus and how software should issue device commands to
NFC TagWriter by NXP
 Rev. 1.6 27 April 2016 User manual Document information Info Content Keywords User manual Abstract This document describes the features of the TagWriter and steps to setup TagWriter application in smart
Rev. 1.6 27 April 2016 User manual Document information Info Content Keywords User manual Abstract This document describes the features of the TagWriter and steps to setup TagWriter application in smart
Secure Automatic Ticketing System
 Secure Automatic Ticketing System MARIUS POPA, CRISTIAN TOMA Department of Computer Science in Economics Academy of Economic Studies Bucharest Romana Square, No. 6, Bucharest ROMANIA marius.popa@ase.ro
Secure Automatic Ticketing System MARIUS POPA, CRISTIAN TOMA Department of Computer Science in Economics Academy of Economic Studies Bucharest Romana Square, No. 6, Bucharest ROMANIA marius.popa@ase.ro
Xbox 360 File Specifications Reference
 Xbox 360 File Specifications Reference Introduction This reference attempts to document the specifications of the custom data formats in use by the Xbox 360 console. This data has either been discovered
Xbox 360 File Specifications Reference Introduction This reference attempts to document the specifications of the custom data formats in use by the Xbox 360 console. This data has either been discovered
NFCulT. An easy a nice tool that will make you have fun, or... make profit!
 NFCulT An easy a nice tool that will make you have fun, or... make profit Matteo Beccaro ( aka bughardy ) Student at Politecnico di Torino Computer Engineering Security Engineer and researcher at Secure
NFCulT An easy a nice tool that will make you have fun, or... make profit Matteo Beccaro ( aka bughardy ) Student at Politecnico di Torino Computer Engineering Security Engineer and researcher at Secure
New Attacks against RFID-Systems. Lukas Grunwald DN-Systems GmbH Germany
 New Attacks against RFID-Systems Lukas Grunwald DN-Systems GmbH Germany Agenda What is RFID? How to exploit and attack RFID systems Attacks against the middleware Reader-emulation, soft-tags Unexpected
New Attacks against RFID-Systems Lukas Grunwald DN-Systems GmbH Germany Agenda What is RFID? How to exploit and attack RFID systems Attacks against the middleware Reader-emulation, soft-tags Unexpected
NTAG213/215/216. The mechanical and electrical specifications of NTAG21x are tailored to meet the requirements of inlay and tag manufacturers.
 NFC Forum Type 2 Tag compliant IC with 144/504/888 bytes user memory 265332 1. General description NTAG213, NTAG215 and NTAG216 have been developed by NXP Semiconductors as standard NFC tag ICs to be used
NFC Forum Type 2 Tag compliant IC with 144/504/888 bytes user memory 265332 1. General description NTAG213, NTAG215 and NTAG216 have been developed by NXP Semiconductors as standard NFC tag ICs to be used
Caml Virtual Machine File & data formats Document version: 1.4 http://cadmium.x9c.fr
 Caml Virtual Machine File & data formats Document version: 1.4 http://cadmium.x9c.fr Copyright c 2007-2010 Xavier Clerc cadmium@x9c.fr Released under the LGPL version 3 February 6, 2010 Abstract: This
Caml Virtual Machine File & data formats Document version: 1.4 http://cadmium.x9c.fr Copyright c 2007-2010 Xavier Clerc cadmium@x9c.fr Released under the LGPL version 3 February 6, 2010 Abstract: This
Development Kit EM4095 User s Manual
 EM MICROELECTRONIC - MARIN SA Appte 405 Title: Product Family: Application te 405 Development Kit EM4095 User s Manual RFID Part Number: EMDB40 Keywords: RFID Design Tools Date: 5 September 00 TABLE OF
EM MICROELECTRONIC - MARIN SA Appte 405 Title: Product Family: Application te 405 Development Kit EM4095 User s Manual RFID Part Number: EMDB40 Keywords: RFID Design Tools Date: 5 September 00 TABLE OF
AN601 I2C 2.8 Communication Protocol. SM130 SM130 - Mini APPLICATION NOTE
 AN601 I2C 2.8 Communication Protocol SM130 SM130 - Mini APPLICATION NOTE 2 1. INTRODUCTION This application note explains I2C communication protocol with SM130 or SM130-Mini Mifare module based on the
AN601 I2C 2.8 Communication Protocol SM130 SM130 - Mini APPLICATION NOTE 2 1. INTRODUCTION This application note explains I2C communication protocol with SM130 or SM130-Mini Mifare module based on the
MODBUS APPLICATION PROTOCOL SPECIFICATION V1.1b3 CONTENTS
 MODBUS APPLICATION PROTOCOL SPECIFICATION V1.1b3 CONTENTS 1 Introduction... 2 1.1 Scope of this document... 2 2 Abbreviations... 2 3 Context... 3 4 General description... 3 4.1 Protocol description...
MODBUS APPLICATION PROTOCOL SPECIFICATION V1.1b3 CONTENTS 1 Introduction... 2 1.1 Scope of this document... 2 2 Abbreviations... 2 3 Context... 3 4 General description... 3 4.1 Protocol description...
UM0853 User manual. 1 Introduction. M24LRxx application software user guide
 User manual M24LRxx application software user guide 1 Introduction The purpose of this user manual is to teach how to use the M24LRxx tool kit with the M24LRxx_Application_Software. It describes the M24LRxx_Application_Software
User manual M24LRxx application software user guide 1 Introduction The purpose of this user manual is to teach how to use the M24LRxx tool kit with the M24LRxx_Application_Software. It describes the M24LRxx_Application_Software
Technical Data Sheet UM-005. UM005-doc-01.04 In reference to UM005-c-01.04
 Technical Data Sheet UM-005 UM005-doc-01.04 In reference to UM005-c-01.04 Contents Contents... 2 Introductions... 3 Specifications... 3 Pin description... 4 Connection diagram... 4 Module PCB dimensions...
Technical Data Sheet UM-005 UM005-doc-01.04 In reference to UM005-c-01.04 Contents Contents... 2 Introductions... 3 Specifications... 3 Pin description... 4 Connection diagram... 4 Module PCB dimensions...
Business Portal for Microsoft Dynamics GP 2010. Field Service Suite
 Business Portal for Microsoft Dynamics GP 2010 Field Service Suite Copyright Copyright 2010 Microsoft. All rights reserved. Limitation of liability This document is provided as-is. Information and views
Business Portal for Microsoft Dynamics GP 2010 Field Service Suite Copyright Copyright 2010 Microsoft. All rights reserved. Limitation of liability This document is provided as-is. Information and views
Byte Ordering of Multibyte Data Items
 Byte Ordering of Multibyte Data Items Most Significant Byte (MSB) Least Significant Byte (LSB) Big Endian Byte Addresses +0 +1 +2 +3 +4 +5 +6 +7 VALUE (8-byte) Least Significant Byte (LSB) Most Significant
Byte Ordering of Multibyte Data Items Most Significant Byte (MSB) Least Significant Byte (LSB) Big Endian Byte Addresses +0 +1 +2 +3 +4 +5 +6 +7 VALUE (8-byte) Least Significant Byte (LSB) Most Significant
Nemo 96HD/HD+ MODBUS
 18/12/12 Pagina 1 di 28 MULTIFUNCTION FIRMWARE 2.30 Nemo 96HD/HD+ MODBUS COMMUNICATION PROTOCOL CONTENTS 1.0 ABSTRACT 2.0 DATA MESSAGE DESCRIPTION 2.1 Parameters description 2.2 Data format 2.3 Description
18/12/12 Pagina 1 di 28 MULTIFUNCTION FIRMWARE 2.30 Nemo 96HD/HD+ MODBUS COMMUNICATION PROTOCOL CONTENTS 1.0 ABSTRACT 2.0 DATA MESSAGE DESCRIPTION 2.1 Parameters description 2.2 Data format 2.3 Description
NFC Tag Type 5 Specification
 Document Type: Software Technical Specification Reference: STS_NFC_0707-001 Version 1.8 (14516) Release Date: Nov. 18, 2011 File Name: STS_NFC_0707-001 NFC Tag Type 5 Specification.pdf Security Level:
Document Type: Software Technical Specification Reference: STS_NFC_0707-001 Version 1.8 (14516) Release Date: Nov. 18, 2011 File Name: STS_NFC_0707-001 NFC Tag Type 5 Specification.pdf Security Level:
Advanced Encryption Standard (AES) User's Guide
 Advanced Encryption Standard (AES) User's Guide Version 1.00 BETA For use with AES versions 1.6 and above Date: 11-Feb-2015 11:23 All rights reserved. This document and the associated software are the
Advanced Encryption Standard (AES) User's Guide Version 1.00 BETA For use with AES versions 1.6 and above Date: 11-Feb-2015 11:23 All rights reserved. This document and the associated software are the
Type 2 Tag Operation Specification. Technical Specification T2TOP 1.1 NFC Forum TM NFCForum-TS-Type-2-Tag_1.1 2011-05-31
 Type 2 Tag Operation Specification Technical Specification T2TOP 1.1 NFC Forum TM NFCForum-TS-Type-2-Tag_1.1 2011-05-31 RESTRICTIONS ON USE This specification is copyright 2005-2011 by the NFC Forum, and
Type 2 Tag Operation Specification Technical Specification T2TOP 1.1 NFC Forum TM NFCForum-TS-Type-2-Tag_1.1 2011-05-31 RESTRICTIONS ON USE This specification is copyright 2005-2011 by the NFC Forum, and
Self-Check-In Hotels Using RFID. Technology
 Self-Check-In Hotels Using RFID Technology David H. Miller December 5, 2007 MAE 295C, Professor R. Gadh Contents I. The Need. 2 II. The Solution 2 III. The RFID Tag. 3 IV. The RFID Reader.... 5 V. Middleware.
Self-Check-In Hotels Using RFID Technology David H. Miller December 5, 2007 MAE 295C, Professor R. Gadh Contents I. The Need. 2 II. The Solution 2 III. The RFID Tag. 3 IV. The RFID Reader.... 5 V. Middleware.
MF0ICU2. 1. General description. MIFARE Ultralight C. 1.1 Contactless energy and data transfer. 1.2 Anticollision. Rev. 3.2 19 May 2009 171432
 Rev. 3.2 19 May 2009 171432 1. General description NXP Semiconductors has developed MIFARE - - to be used with Proximity Coupling Devices (PCD) according to ISO/IEC 14443A (see Ref. 1 ISO/IEC ). The communication
Rev. 3.2 19 May 2009 171432 1. General description NXP Semiconductors has developed MIFARE - - to be used with Proximity Coupling Devices (PCD) according to ISO/IEC 14443A (see Ref. 1 ISO/IEC ). The communication
Data sheet Wireless UART firmware version 4.02
 Data sheet Wireless UART firmware version 4.02 BLUETOOTH is a trademark owned by Bluetooth SIG, Inc., U.S.A. and licensed to Free2move Rev: 22 December 2008 Table of contents 1 GENERAL INFORMATION...4
Data sheet Wireless UART firmware version 4.02 BLUETOOTH is a trademark owned by Bluetooth SIG, Inc., U.S.A. and licensed to Free2move Rev: 22 December 2008 Table of contents 1 GENERAL INFORMATION...4
IP Card Reader Interface User Manual
 IP Card Reader Interface User Manual SB Research 2009-2011 The IP Reader Interface family: Concept: The IP Card Reader Interface allows access control card readers to be connected to a network device,
IP Card Reader Interface User Manual SB Research 2009-2011 The IP Reader Interface family: Concept: The IP Card Reader Interface allows access control card readers to be connected to a network device,
Application Note AN0008. Data Logging Extension. For. Venus 8 GPS Receiver
 Application Note AN0008 Data Logging Extension For Venus 8 GPS Receiver Ver 1.4.17 July 25, 2014 Introduction The data logging option for the SkyTraq GPS receiver firmware allows storage of position, velocity,
Application Note AN0008 Data Logging Extension For Venus 8 GPS Receiver Ver 1.4.17 July 25, 2014 Introduction The data logging option for the SkyTraq GPS receiver firmware allows storage of position, velocity,
Secure recharge of disposable RFID tickets
 Secure recharge of disposable RFID tickets Riccardo Focardi Flaminia Luccio Università Ca Foscari, Venezia {focardi,luccio}@unive.it FAST 2011 15-16 September 2011, Leuven FAST 2011 ()Secure recharge of
Secure recharge of disposable RFID tickets Riccardo Focardi Flaminia Luccio Università Ca Foscari, Venezia {focardi,luccio}@unive.it FAST 2011 15-16 September 2011, Leuven FAST 2011 ()Secure recharge of
20 Using Scripts. (Programming without Parts) 20-1
 20 Using Scripts (Programming without Parts) This chapter explains the basics of creating and using programming scripts in GP-Pro EX. Please start by reading 20.1 Settings Menu (page 20-2) and then turn
20 Using Scripts (Programming without Parts) This chapter explains the basics of creating and using programming scripts in GP-Pro EX. Please start by reading 20.1 Settings Menu (page 20-2) and then turn
Authorize.net modules for oscommerce Online Merchant.
 Authorize.net Authorize.net modules for oscommerce Online Merchant. Chapters oscommerce Online Merchant v2.3 Copyright Copyright (c) 2014 oscommerce. All rights reserved. Content may be reproduced for
Authorize.net Authorize.net modules for oscommerce Online Merchant. Chapters oscommerce Online Merchant v2.3 Copyright Copyright (c) 2014 oscommerce. All rights reserved. Content may be reproduced for
Using KEPServerEX OPC Server (Kepware)with the iologik E2210
 Using KEPServerEX OPC Server (Kepware)with the iologik E2210 Alex Chen, Senior Engineer, Moxa Technical Support Dept. In this Technical Note, we cover the following topics: 1. Obtaining Modbus addresses
Using KEPServerEX OPC Server (Kepware)with the iologik E2210 Alex Chen, Senior Engineer, Moxa Technical Support Dept. In this Technical Note, we cover the following topics: 1. Obtaining Modbus addresses
WIZnet S2E (Serial-to-Ethernet) Device s Configuration Tool Programming Guide
 WIZnet S2E (Serial-to-Ethernet) Device s Configuration Tool Programming Guide Rev 0.2 This document describes how to make your own Configuration Tool for WIZ100SR, WIZ105SR and WIZ110SR of WIZnet. And
WIZnet S2E (Serial-to-Ethernet) Device s Configuration Tool Programming Guide Rev 0.2 This document describes how to make your own Configuration Tool for WIZ100SR, WIZ105SR and WIZ110SR of WIZnet. And
Active Directory Integration with Blue Coat
 The Web Security Authority. TM Active Directory Integration with Blue Coat NOTE: This techbrief is applicable when using NTLM under Windows 2000 Server. Introduction Windows 2000 server utilizes Active
The Web Security Authority. TM Active Directory Integration with Blue Coat NOTE: This techbrief is applicable when using NTLM under Windows 2000 Server. Introduction Windows 2000 server utilizes Active
Tamper protection with Bankgirot HMAC Technical Specification
 Mars 2014 Tamper protection with Bankgirot HMAC Technical Specification Bankgirocentralen BGC AB 2013. All rights reserved. www.bankgirot.se Innehåll 1 General...3 2 Tamper protection with HMAC-SHA256-128...3
Mars 2014 Tamper protection with Bankgirot HMAC Technical Specification Bankgirocentralen BGC AB 2013. All rights reserved. www.bankgirot.se Innehåll 1 General...3 2 Tamper protection with HMAC-SHA256-128...3
INTEGRATED CIRCUITS I CODE SLI. Smart Label IC SL2 ICS20. Functional Specification. Product Specification Revision 3.1 Public. Philips Semiconductors
 INTEGRATED CIRCUITS I CODE SLI Smart Label IC SL2 ICS20 Product Specification Revision 3.1 February July 2005 2001 Public Philips Semiconductors CONTENTS 1 FEATURES...4 1.1 I CODE SLI RF Interface (ISO/IEC
INTEGRATED CIRCUITS I CODE SLI Smart Label IC SL2 ICS20 Product Specification Revision 3.1 February July 2005 2001 Public Philips Semiconductors CONTENTS 1 FEATURES...4 1.1 I CODE SLI RF Interface (ISO/IEC
SYMETRIX SOLUTIONS: TECH TIP August 2015
 String Output Modules The purpose of this document is to provide an understanding of operation and configuration of the two different String Output modules available within SymNet Composer. The two different
String Output Modules The purpose of this document is to provide an understanding of operation and configuration of the two different String Output modules available within SymNet Composer. The two different
Secure My-d TM and Mifare TM RFID reader system by using a security access module Erich Englbrecht (info@eonline.de) V0.1draft
 Application Report Secure My-d TM and Mifare TM RFID reader system by using a security access module Erich Englbrecht (info@eonline.de) V0.1draft Embedded RF ABSTRACT This application report describes
Application Report Secure My-d TM and Mifare TM RFID reader system by using a security access module Erich Englbrecht (info@eonline.de) V0.1draft Embedded RF ABSTRACT This application report describes
Binary Representation
 Binary Representation The basis of all digital data is binary representation. Binary - means two 1, 0 True, False Hot, Cold On, Off We must tbe able to handle more than just values for real world problems
Binary Representation The basis of all digital data is binary representation. Binary - means two 1, 0 True, False Hot, Cold On, Off We must tbe able to handle more than just values for real world problems
MicroLogix 1400 Embedded Web Server
 MicroLogix 1400 Embedded Web Server Bulletin 1766 Controllers User Manual Important User Information Solid state equipment has operational characteristics differing from those of electromechanical equipment.
MicroLogix 1400 Embedded Web Server Bulletin 1766 Controllers User Manual Important User Information Solid state equipment has operational characteristics differing from those of electromechanical equipment.
MIFARE CONTACTLESS CARD TECHNOLOLGY AN HID WHITE PAPER
 MIFARE CONTACTLESS CARD TECHNOLOLGY AN HID WHITE PAPER GENERAL The MIFARE contactless smart card and MIFARE card reader/writer were developed to handle payment transactions for public transportation systems.
MIFARE CONTACTLESS CARD TECHNOLOLGY AN HID WHITE PAPER GENERAL The MIFARE contactless smart card and MIFARE card reader/writer were developed to handle payment transactions for public transportation systems.
Online Banking for Business Secure FTP with SSH (Secure Shell) USER GUIDE
 Online Banking for Business Secure FTP with SSH (Secure Shell) USER GUIDE Contents Secure FTP Setup... 1 Introduction... 1 Before You Set Up S/FTP... 1 Setting Up FTP with SSH... 2 Sending Files... 3 Address
Online Banking for Business Secure FTP with SSH (Secure Shell) USER GUIDE Contents Secure FTP Setup... 1 Introduction... 1 Before You Set Up S/FTP... 1 Setting Up FTP with SSH... 2 Sending Files... 3 Address
Sample EHG CL and EHG SL10 16-bit Modbus RTU Packet
 Sent to EHG - Read (16-bit) Process Value Controller 00000011 0x03 3 Function Code - Read Holding Registers 00000000 0x00 0 Read starting at register High byte (Process Value Controller is contained in
Sent to EHG - Read (16-bit) Process Value Controller 00000011 0x03 3 Function Code - Read Holding Registers 00000000 0x00 0 Read starting at register High byte (Process Value Controller is contained in
Syscall 5. Erik Jonsson School of Engineering and Computer Science. The University of Texas at Dallas
 Syscall 5 System call 5 allows input of numerical data from the keyboard while a program is running. Syscall 5 is a bit unusual, in that it requires the use of register $v0 twice. In syscall 5 (as for
Syscall 5 System call 5 allows input of numerical data from the keyboard while a program is running. Syscall 5 is a bit unusual, in that it requires the use of register $v0 twice. In syscall 5 (as for
ROM Monitor. Entering the ROM Monitor APPENDIX
 APPENDIX B This appendix describes the Cisco router ROM monitor (also called the bootstrap program). The ROM monitor firmware runs when the router is powered up or reset. The firmware helps to initialize
APPENDIX B This appendix describes the Cisco router ROM monitor (also called the bootstrap program). The ROM monitor firmware runs when the router is powered up or reset. The firmware helps to initialize
EtherNet/IP Modbus XPort, NET232, and NET485
 EtherNet/IP Modbus XPort, NET232, and NET485 xxx-xxx-xxx Document Version 1.08x May 26, 2010 Grid Connect, Inc. 1630 W Diehl Rd Naperville, IL 60563 (630) 245-1445 2010 Grid Connect All rights reserved.
EtherNet/IP Modbus XPort, NET232, and NET485 xxx-xxx-xxx Document Version 1.08x May 26, 2010 Grid Connect, Inc. 1630 W Diehl Rd Naperville, IL 60563 (630) 245-1445 2010 Grid Connect All rights reserved.
Introduction: Implementation of the MVI56-MCM module for modbus communications:
 Introduction: Implementation of the MVI56-MCM module for modbus communications: Initial configuration of the module should be done using the sample ladder file for the mvi56mcm module. This can be obtained
Introduction: Implementation of the MVI56-MCM module for modbus communications: Initial configuration of the module should be done using the sample ladder file for the mvi56mcm module. This can be obtained
mypro Installation and Handling Manual Version: 7
 mypro Installation and Handling Manual Version: 7 Date: JAN 2016 Thank you for using mypro on your PC. myscada is a full featured HMI/SCADA system with advanced options such as vector graphics views, advanced
mypro Installation and Handling Manual Version: 7 Date: JAN 2016 Thank you for using mypro on your PC. myscada is a full featured HMI/SCADA system with advanced options such as vector graphics views, advanced
HP Service Virtualization
 HP Service Virtualization Fixed Length Protocol Virtualization SV Training September 2014 Fixed Length Protocol Virtualization Technology Description Use Cases Supported Message Structures SV Service Description
HP Service Virtualization Fixed Length Protocol Virtualization SV Training September 2014 Fixed Length Protocol Virtualization Technology Description Use Cases Supported Message Structures SV Service Description
BRMO 80 / ETH-IP. User Manual. Réf : MU-BRMO 80-ETH-IP-1.4-EN
 User Manual Réf : MU-BRMO 80-ETH-IP-1.4-EN BALOGH SA 189, rue d Aubervilliers - C.P. 97 75886 PARIS Cedex 18 France Tél : 33 (0)1 44 65 65 00 Fax : 33 (0)1 44 65 65 10 e-mail : balogh@balogh-group.com
User Manual Réf : MU-BRMO 80-ETH-IP-1.4-EN BALOGH SA 189, rue d Aubervilliers - C.P. 97 75886 PARIS Cedex 18 France Tél : 33 (0)1 44 65 65 00 Fax : 33 (0)1 44 65 65 10 e-mail : balogh@balogh-group.com
Training MIFARE SDK. Public. MobileKnowledge June 2015
 MIFARE SDK Public MobileKnowledge June 2015 Agenda Overview of MIFARE SDK related technologies NFC Technology (Read/Write mode) MIFARE, NTAG and ICODE products NFC in Android MIFARE SDK Introduction to
MIFARE SDK Public MobileKnowledge June 2015 Agenda Overview of MIFARE SDK related technologies NFC Technology (Read/Write mode) MIFARE, NTAG and ICODE products NFC in Android MIFARE SDK Introduction to
Security & Chip Card ICs SLE 44R35S / Mifare
 Security & Chip Card ICs SLE 44R35S / Mifare Intelligent 1 Kbyte EEPROM with Interface for Contactless Transmission, Security Logic and Anticollision according to the MIFARE -System Short Product Info
Security & Chip Card ICs SLE 44R35S / Mifare Intelligent 1 Kbyte EEPROM with Interface for Contactless Transmission, Security Logic and Anticollision according to the MIFARE -System Short Product Info
Implementation Guide. SAS Serial Protocol. for. Montana Department of Justice Gambling Control Division. October 22, 2012. Version 1.4.
 Implementation Guide for SAS Serial Protocol Montana Department of Justice Gambling Control Division October 22, 2012 Version 1.4.1 Montana SAS Implementation Guide Page 2 Table of Contents 1 Introduction...
Implementation Guide for SAS Serial Protocol Montana Department of Justice Gambling Control Division October 22, 2012 Version 1.4.1 Montana SAS Implementation Guide Page 2 Table of Contents 1 Introduction...
Mifare DESFire Specification
 Mifare DESFire Specification Version 1.0 29 th September 2009 Revision History Version Date Author Description of Changes 1.0 29/09/09 O McLaughlin Ratified by LASSeO 0.2 28/07/09 O McLaughlin Minor changes
Mifare DESFire Specification Version 1.0 29 th September 2009 Revision History Version Date Author Description of Changes 1.0 29/09/09 O McLaughlin Ratified by LASSeO 0.2 28/07/09 O McLaughlin Minor changes
NTAG213F/216F. 1. General description. NFC Forum Type 2 Tag compliant IC with 144/888 bytes user memory and field detection
 NFC Forum Type 2 Tag compliant IC with 144/888 bytes user memory and field detection 262236 1. General description The NTAG213F and NTAG216F are the new NFC forum compliant Type 2 Tag products developed
NFC Forum Type 2 Tag compliant IC with 144/888 bytes user memory and field detection 262236 1. General description The NTAG213F and NTAG216F are the new NFC forum compliant Type 2 Tag products developed
Using Logix5000 Controllers as Masters or Slaves on Modbus
 Application Solution Using Logix5000 Controllers as Masters or Slaves on Modbus Purpose of the Document This application solution, and the associated RSLogix 5000 project files, help you use Logix5000
Application Solution Using Logix5000 Controllers as Masters or Slaves on Modbus Purpose of the Document This application solution, and the associated RSLogix 5000 project files, help you use Logix5000
Memory Systems. Static Random Access Memory (SRAM) Cell
 Memory Systems This chapter begins the discussion of memory systems from the implementation of a single bit. The architecture of memory chips is then constructed using arrays of bit implementations coupled
Memory Systems This chapter begins the discussion of memory systems from the implementation of a single bit. The architecture of memory chips is then constructed using arrays of bit implementations coupled
IBM i Version 7.2. Security Service Tools
 IBM i Version 7.2 Security Service Tools IBM i Version 7.2 Security Service Tools Note Before using this information and the product it supports, read the information in Notices on page 37. This edition
IBM i Version 7.2 Security Service Tools IBM i Version 7.2 Security Service Tools Note Before using this information and the product it supports, read the information in Notices on page 37. This edition
Catalyst 3750 Switch Boot Loader Commands
 APPENDIX A This appendix describes the boot loader commands on the Catalyst 3750 switch. Unless otherwise noted, the term switch refers to a standalone switch and to a switch stack. During normal boot
APPENDIX A This appendix describes the boot loader commands on the Catalyst 3750 switch. Unless otherwise noted, the term switch refers to a standalone switch and to a switch stack. During normal boot
AKD EtherNet/IP Communication
 AKD EtherNet/IP Communication Edition August 2012, Revision C Valid for firmware version 1.7 Patents Pending Part Number 903-200008-00 Keep all manuals as a product component during the life span of the
AKD EtherNet/IP Communication Edition August 2012, Revision C Valid for firmware version 1.7 Patents Pending Part Number 903-200008-00 Keep all manuals as a product component during the life span of the
NTAG213/215/216. The mechanical and electrical specifications of NTAG21x are tailored to meet the requirements of inlay and tag manufacturers.
 NFC Forum Type 2 Tag compliant IC with 144/504/888 bytes user memory 265331 1. General description NTAG213, NTAG215 and NTAG216 have been developed by NXP Semiconductors as standard NFC tag ICs to be used
NFC Forum Type 2 Tag compliant IC with 144/504/888 bytes user memory 265331 1. General description NTAG213, NTAG215 and NTAG216 have been developed by NXP Semiconductors as standard NFC tag ICs to be used
4511 MODBUS RTU. Configuration Manual. HART transparent driver. No. 9107MCM100(1328)
 4511 MODBUS RTU Configuration Manual HART transparent driver No. 9107MCM100(1328) 9107 CONTENTS Introduction... 3 Modbus basics... 3 Modbus RTU... 3 Supported Function Codes... 3 Modbus Parameters and
4511 MODBUS RTU Configuration Manual HART transparent driver No. 9107MCM100(1328) 9107 CONTENTS Introduction... 3 Modbus basics... 3 Modbus RTU... 3 Supported Function Codes... 3 Modbus Parameters and
Note: A WebFOCUS Developer Studio license is required for each developer.
 WebFOCUS FAQ s Q. What is WebFOCUS? A. WebFOCUS was developed by Information Builders Incorporated and is a comprehensive and fully integrated enterprise business intelligence system. The WebFOCUShttp://www.informationbuilders.com/products/webfocus/architecture.html
WebFOCUS FAQ s Q. What is WebFOCUS? A. WebFOCUS was developed by Information Builders Incorporated and is a comprehensive and fully integrated enterprise business intelligence system. The WebFOCUShttp://www.informationbuilders.com/products/webfocus/architecture.html
ACR122U USB NFC Reader
 ACR122U USB NFC Reader Application Programming Interface V2.02 Subject to change without prior notice Table of Contents 1.0. Introduction... 4 1.1. Features... 4 1.2. USB Interface... 5 2.0. Implementation...
ACR122U USB NFC Reader Application Programming Interface V2.02 Subject to change without prior notice Table of Contents 1.0. Introduction... 4 1.1. Features... 4 1.2. USB Interface... 5 2.0. Implementation...
Automated Identification Technologies
 Spec 2000 ebusiness Forum Automated Identification Technologies Jon Andresen President Technology Solutions Jon@TechSoln.com Budapest, Hungry 23 October 2008 Agenda 1. AIT Chapter 9 Intro - Jon A. AIT
Spec 2000 ebusiness Forum Automated Identification Technologies Jon Andresen President Technology Solutions Jon@TechSoln.com Budapest, Hungry 23 October 2008 Agenda 1. AIT Chapter 9 Intro - Jon A. AIT
How to use Citect (SCADA) with iologik 4000 (Modbus TCP/IP NA-4010 and Modbus Serial NA-4020/NA-4021)
 with iologik 4000 (Modbus TCP/IP NA-4010 and Modbus Serial NA-4020/NA-4021) Alex Chen, Senior Engineer, Moxa Technical Support Dept. In this Technical Note, we cover the following topics: 1. How to export
with iologik 4000 (Modbus TCP/IP NA-4010 and Modbus Serial NA-4020/NA-4021) Alex Chen, Senior Engineer, Moxa Technical Support Dept. In this Technical Note, we cover the following topics: 1. How to export
Data Acquisition Module with I2C interface «I2C-FLEXEL» User s Guide
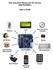 Data Acquisition Module with I2C interface «I2C-FLEXEL» User s Guide Sensors LCD Real Time Clock/ Calendar DC Motors Buzzer LED dimming Relay control I2C-FLEXEL PS2 Keyboards Servo Motors IR Remote Control
Data Acquisition Module with I2C interface «I2C-FLEXEL» User s Guide Sensors LCD Real Time Clock/ Calendar DC Motors Buzzer LED dimming Relay control I2C-FLEXEL PS2 Keyboards Servo Motors IR Remote Control
Delta Temperature Controller User Manual
 Delta Temperature Controller User Manual Foreword The user manual details the process of using Delta DT series temperature controllers step by step for beginners to easily set up all kinds of parameters
Delta Temperature Controller User Manual Foreword The user manual details the process of using Delta DT series temperature controllers step by step for beginners to easily set up all kinds of parameters
Administration: Users and Roles
 Last Update: September 2011 Release 7.5 Administration: Users and Roles This lesson is specifically designed for administrators responsible for user security settings in the Astra Schedule system. Astra
Last Update: September 2011 Release 7.5 Administration: Users and Roles This lesson is specifically designed for administrators responsible for user security settings in the Astra Schedule system. Astra
Online Banking for Business Secure FTP with SSL (Secure Socket Layer) USER GUIDE
 Online Banking for Business Secure FTP with SSL (Secure Socket Layer) USER GUIDE Contents Secure FTP Setup... 1 Introduction...1 Secure FTP Setup Diagram...1 Before You Set Up S/FTP...2 Setting Up S/FTP...2
Online Banking for Business Secure FTP with SSL (Secure Socket Layer) USER GUIDE Contents Secure FTP Setup... 1 Introduction...1 Secure FTP Setup Diagram...1 Before You Set Up S/FTP...2 Setting Up S/FTP...2
14443A ISO\IEC 14443B ISO\IEC
 RDM Tag Module RDM880 13.56MHz RFID Reader/Writer ISO\IEC 14443A ISO\IEC 14443B ISO\IEC 15693 PRODUCT REFERENCE GUIDE RDM880 April 2007 Shenzhen RDM Tag Master Co., Ltd. www.datarfid.com 1 / 28 Document
RDM Tag Module RDM880 13.56MHz RFID Reader/Writer ISO\IEC 14443A ISO\IEC 14443B ISO\IEC 15693 PRODUCT REFERENCE GUIDE RDM880 April 2007 Shenzhen RDM Tag Master Co., Ltd. www.datarfid.com 1 / 28 Document
Overview of the LTC2978 Configuration EEPROM (NVM) Revision 1.0
 Overview of the LTC2978 Configuration EEPROM (NVM) Revision 1.0 Author: Mike Holloway, Rob Chiacchia, Linear Technology Date: 11/11/2010 Revision History: 1.0 Added Arrow Contact Information 0.9 Added
Overview of the LTC2978 Configuration EEPROM (NVM) Revision 1.0 Author: Mike Holloway, Rob Chiacchia, Linear Technology Date: 11/11/2010 Revision History: 1.0 Added Arrow Contact Information 0.9 Added
Web Authentication Proxy on a Wireless LAN Controller Configuration Example
 Web Authentication Proxy on a Wireless LAN Controller Configuration Example Document ID: 113151 Contents Introduction Prerequisites Requirements Components Used Conventions Web Authentication Proxy on
Web Authentication Proxy on a Wireless LAN Controller Configuration Example Document ID: 113151 Contents Introduction Prerequisites Requirements Components Used Conventions Web Authentication Proxy on
APNT#1168 Modbus - Establishing Communications Hints
 Application Note #1168: Modbus - Establishing Communications Hints Introduction This document provides supplemental information about configuring Pro-face Device/PLC drivers to communicate with your device.
Application Note #1168: Modbus - Establishing Communications Hints Introduction This document provides supplemental information about configuring Pro-face Device/PLC drivers to communicate with your device.
AN 073120. mifare Ultralight Features and Hints. Document information. Multiple ticketing, secured data storage, implementation hints
 AN 073120 Rev. 2.0 18 December 2006 Application note Document information Info Keywords Abstract Content Multiple ticketing, secured data storage, implementation hints This document presents features and
AN 073120 Rev. 2.0 18 December 2006 Application note Document information Info Keywords Abstract Content Multiple ticketing, secured data storage, implementation hints This document presents features and
Configuration Variables For Digital Command Control, All Scales
 This document received approval from the NMRA Board of Trustees in July 1995, March 1997, July 2003, and July 2006. Changes since the last approved version are indicated by change bars on the left or right
This document received approval from the NMRA Board of Trustees in July 1995, March 1997, July 2003, and July 2006. Changes since the last approved version are indicated by change bars on the left or right
