Configuration Management at Operating System Level. Module 4 Protection of Information Systems and Information Assets
|
|
|
- Myron Robbins
- 7 years ago
- Views:
Transcription
1 Configuration Management at Operating System Level Module 4 Protection of Information Systems and Information Assets 1
2 Table of Contents Introduction Password Policy Password Policy- How to Define? Audit Policy Audit Policy- How to Define? Users Rights Assignment User Rights Assignment- How to Define? Security Options Security Options- How to Define? Case Study 2
3 Introduction (1/2) Every organization defines it s IT Security policies and Security standards for network, servers, desktops, handheld devices etc. IT / Server Security Team needs to ensure that all servers (Windows, Unix, Linux etc.) have been configured in accordance with the organization's IT Security Policies and Security Standards. 3
4 Introduction (2/2) In MS Windows server, IT/Server Security team needs to configure the following parameters: Password Policy Audit Policy User Rights Assignment Security Options 4
5 Review Local Security Policy 5
6 Password Policy The security provided by a password depends on the passwords being kept secret at all times. Thus, a password is vulnerable to compromise whenever it is used or stored. Password policies can be set depending on the needs of the organization. For e.g. it is possible to specify minimum password length, maximum and minimum password age etc. It is also possible to prevent users from reusing passwords and ensure that they use specific characters in their passwords, making the passwords more difficult to crack. 6
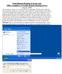
7 Password Policy- How to Define? (1/2) Start Control Panel Administrative tools Local Security Policy Run command prompt Type secedit.exe and press enter Expand Account Policies Double click on Password Policy. 7
8 Password Policy- How to Define? (2/2) Security Settings Account policies Password policy. On right pane, select Minimum password length (or any other setting which is required to be changed) Double click pop-up window will appear Change the setting to desired value Click OK 8
9 Create Password Go to Control Panel > User Accounts > Manage accounts 9
10 Audit Policy Before audit records are logged, an auditing policy must be established. The policy defines the types of events that will be audited for a specific user or group of users. An auditing policy specifies categories of security-related events that must be audited. When Windows server is first installed, all auditing categories are turned off. By turning on various auditing event categories, the administrator can implement an auditing policy that suits the security needs of the organization. 10
11 Audit Policy Go to Control Panel > System and Security> Administrative Tools> Local Security Policy 11
12 Audit Policy- How to Define? Run command prompt Type secedit.exe press enter Expand Local Policies Double click on Audit policy To change any of the Audit Policy, double click on the policies in the right pane Change the setting to desired value Click OK 12
13 Users Rights Assignment User Rights Assignment policies determines which users or groups have logon rights or privileges on the computer. User Rights Assignment govern the methods by which a user can log on to a system. User rights include logon rights and permissions. Logon rights control who is authorized to log on to a computer and how they can log on. User rights permissions control access to server and domain resources. 13
14 User Rights & Privileges User Rights apply to user accounts, and Permissions attached to objects Assigning User Rights Start> Control Panel>System and security>administrative Tools> Local Security Policy 14
15 User Rights Assigning User Rights Start> Control Panel>System and security>administrative Tools> Local Security Policy Click on User Rights assignment 15
16 Privileges Permissions are attached to objects Right Click on Properties > Security Tab > Advanced or Edit 16
17 User Rights Assignment- How to Define? Run command prompt Type secpol and press enter Expand Local Policies Double click on User Rights Assignment. Local policy 17 Domain Policy (Push by central server/wsus)
18 Security Options The Security Options section of Windows Server configures server s security settings for Administrator and Guest account names, digital data signatures, access to floppy disk and CD drives, driver installation behavior, logon prompts etc. 18
19 Security Options- How to Define? Run command prompt Type secpol and press enter Expand Local Policies Double click on Security Options. 19
20 Case Study Mr. Patel is IT Security Manager in ABC limited and is responsible for Windows Server Security. Some potential risks have been identified in the Windows Server security by Internal Audit team. You have been asked to update the Security settings and Password Policy on all Windows servers. How you will go about it? 20
Desktop Web Access Single Sign-On Configuration Guide
 Waypoint Global Suite Single Sign-On relies on establishing a relationship between a Windows network user identity and a Suite user (Windows Authentication). This is accomplished by assigning to each of
Waypoint Global Suite Single Sign-On relies on establishing a relationship between a Windows network user identity and a Suite user (Windows Authentication). This is accomplished by assigning to each of
Windows XP Exchange Client Installation Instructions
 WINDOWS XP with Outlook 2003 or Outlook 2007 1. Click the Start button and select Control Panel: 2. If your control panel looks like this: Click Switch to Classic View. 3. Double click Mail. 4. Click show
WINDOWS XP with Outlook 2003 or Outlook 2007 1. Click the Start button and select Control Panel: 2. If your control panel looks like this: Click Switch to Classic View. 3. Double click Mail. 4. Click show
Nexxis User Management
 User Manual Version 5.0 Nexxis User Management Nexxis User Management v5.0 User Manual Copyright 2011 Labtronics Inc. Printed in Canada. Windows is a registered trademark of Microsoft Corporation. Microsoft
User Manual Version 5.0 Nexxis User Management Nexxis User Management v5.0 User Manual Copyright 2011 Labtronics Inc. Printed in Canada. Windows is a registered trademark of Microsoft Corporation. Microsoft
Remote Desktop access via Faculty Terminal Server Using Internet Explorer (versions 5.x-7.x)
 Remote Desktop access via Faculty Terminal Server Using Internet Explorer (versions 5.x-7.x) Start your Internet Explorer browser and direct it to the faculty home page. Click on the link Remote Access,
Remote Desktop access via Faculty Terminal Server Using Internet Explorer (versions 5.x-7.x) Start your Internet Explorer browser and direct it to the faculty home page. Click on the link Remote Access,
Using Your Department Shared Folder
 Using Your Department Shared Folder What Is A Domain? A domain is an internal network of computers where the users can share space on a server for storing files and sharing access to printers. Sunysb.edu
Using Your Department Shared Folder What Is A Domain? A domain is an internal network of computers where the users can share space on a server for storing files and sharing access to printers. Sunysb.edu
ENABLE LOGON/LOGOFF AUDITING
 Lepide Software LepideAuditor Suite ENABLE LOGON/LOGOFF AUDITING This document explains the steps required to enable the auditing of logon and logoff events for a domain. Table of Contents 1. Introduction...
Lepide Software LepideAuditor Suite ENABLE LOGON/LOGOFF AUDITING This document explains the steps required to enable the auditing of logon and logoff events for a domain. Table of Contents 1. Introduction...
Use the below instructions to configure your wireless settings to connect to the secure wireless network using Microsoft Windows Vista/7.
 Use the below instructions to configure your wireless settings to connect to the secure wireless network using Microsoft Windows Vista/7. 1. Click the Windows Start button, then Control Panel How-To-WCC-Secure-Windows-7-11/4/2010-4:09
Use the below instructions to configure your wireless settings to connect to the secure wireless network using Microsoft Windows Vista/7. 1. Click the Windows Start button, then Control Panel How-To-WCC-Secure-Windows-7-11/4/2010-4:09
Tufts VPN Client User Guide for Windows
 Tufts VPN Client User Guide for Windows Introduction The Tufts Virtual Private Network (VPN) implementation is a service that is provided to the faculty and staff of Tufts University to enable secure access
Tufts VPN Client User Guide for Windows Introduction The Tufts Virtual Private Network (VPN) implementation is a service that is provided to the faculty and staff of Tufts University to enable secure access
Lab A: Deploying and Managing Software by Using Group Policy Answer Key
 Lab A: Deploying and Managing Software by Using Group Policy Answer Key Exercise 1 Assigning Software This Answer Key provides the detailed steps for completing Lab A: Deploying and Managing Software by
Lab A: Deploying and Managing Software by Using Group Policy Answer Key Exercise 1 Assigning Software This Answer Key provides the detailed steps for completing Lab A: Deploying and Managing Software by
WIRELESS SETUP FOR WINDOWS 7
 Computing & Communications WIRELESS SETUP FOR WINDOWS 7 For assistance during the configuration process please call the Computing and Communications Help Desk at 639-2049, avdesk@swgc.mun.ca Who should
Computing & Communications WIRELESS SETUP FOR WINDOWS 7 For assistance during the configuration process please call the Computing and Communications Help Desk at 639-2049, avdesk@swgc.mun.ca Who should
How to connect to the diamonds wireless network with Vista.
 How to connect to the diamonds wireless network with Vista. This configuration guide requires the use of Windows to configure the wireless settings. 1. Click on the START menu and click the Control Panel.
How to connect to the diamonds wireless network with Vista. This configuration guide requires the use of Windows to configure the wireless settings. 1. Click on the START menu and click the Control Panel.
BioDiscovery Product Activation Group Floating Windows
 BioDiscovery Product Activation Group Floating Windows Contents Group Floating License Activation... 3 Manual Activation... 11 License Transfer... 12 Group Floating License Activation Note: The activation
BioDiscovery Product Activation Group Floating Windows Contents Group Floating License Activation... 3 Manual Activation... 11 License Transfer... 12 Group Floating License Activation Note: The activation
Using Remote Desktop to access your Office Computer or Faculty Remote Desktop Server August, 2005 This document consists of two main parts and an
 Using Remote Desktop to access your Office Computer or Faculty Remote Desktop Server August, 2005 This document consists of two main parts and an addendum. The first part will be the steps required to
Using Remote Desktop to access your Office Computer or Faculty Remote Desktop Server August, 2005 This document consists of two main parts and an addendum. The first part will be the steps required to
To configure Outlook Express for your InfoMetrics E-mail address:
 To configure Outlook Express for your InfoMetrics E-mail address: 1. Open Outlook Express 2. Click the Tools menu, and select Accounts... 3. Internet Accounts window will open, click Add and menu will
To configure Outlook Express for your InfoMetrics E-mail address: 1. Open Outlook Express 2. Click the Tools menu, and select Accounts... 3. Internet Accounts window will open, click Add and menu will
Suite. How to Use GrandMaster Suite. Exporting with ODBC
 Suite How to Use GrandMaster Suite Exporting with ODBC This page intentionally left blank ODBC Export 3 Table of Contents: HOW TO USE GRANDMASTER SUITE - EXPORTING WITH ODBC...4 OVERVIEW...4 WHAT IS ODBC?...
Suite How to Use GrandMaster Suite Exporting with ODBC This page intentionally left blank ODBC Export 3 Table of Contents: HOW TO USE GRANDMASTER SUITE - EXPORTING WITH ODBC...4 OVERVIEW...4 WHAT IS ODBC?...
Non-ThinManager Components
 Non-ThinManager Components Microsoft Terminal Servers play an important role in the ThinManager system. It is recommended that you become familiar with the documentation provided by Microsoft about their
Non-ThinManager Components Microsoft Terminal Servers play an important role in the ThinManager system. It is recommended that you become familiar with the documentation provided by Microsoft about their
How to Configure Outlook 2010 E-mail Client for Exchange
 LAUSD IT Help Desk How to Configure Outlook 2010 E-mail Client for Exchange (03/04/2012) LAUSD IT Help Desk 333 S. Beaudry Ave. 9 th Floor Phone 213.241.5200 Table of Contents Configure Outlook 2010 for
LAUSD IT Help Desk How to Configure Outlook 2010 E-mail Client for Exchange (03/04/2012) LAUSD IT Help Desk 333 S. Beaudry Ave. 9 th Floor Phone 213.241.5200 Table of Contents Configure Outlook 2010 for
NeoMail Guide. Neotel (Pty) Ltd
 NeoMail Guide Neotel (Pty) Ltd NeoMail Connect Guide... 1 1. POP and IMAP Client access... 3 2. Outlook Web Access... 4 3. Outlook (IMAP and POP)... 6 4. Outlook 2007... 16 5. Outlook Express... 24 1.
NeoMail Guide Neotel (Pty) Ltd NeoMail Connect Guide... 1 1. POP and IMAP Client access... 3 2. Outlook Web Access... 4 3. Outlook (IMAP and POP)... 6 4. Outlook 2007... 16 5. Outlook Express... 24 1.
File and Printer Sharing with Microsoft Windows
 Operating System File and Printer Sharing with Microsoft Windows Microsoft Corporation Published: November 2003 Abstract File and printer sharing in Microsoft Windows allows you to share the contents of
Operating System File and Printer Sharing with Microsoft Windows Microsoft Corporation Published: November 2003 Abstract File and printer sharing in Microsoft Windows allows you to share the contents of
Windows Vista: Connecting to the fastnsecure@hood wireless network at Hood College
 Windows Vista: Connecting to the fastnsecure@hood wireless network at Hood College Please ensure your computer meets the following criteria in order to successfully make a connection to this network: 802.11n
Windows Vista: Connecting to the fastnsecure@hood wireless network at Hood College Please ensure your computer meets the following criteria in order to successfully make a connection to this network: 802.11n
NAS 109 Using NAS with Linux
 NAS 109 Using NAS with Linux Access the files on your NAS using Linux A S U S T O R C O L L E G E COURSE OBJECTIVES Upon completion of this course you should be able to: 1. Use Linux to access files on
NAS 109 Using NAS with Linux Access the files on your NAS using Linux A S U S T O R C O L L E G E COURSE OBJECTIVES Upon completion of this course you should be able to: 1. Use Linux to access files on
PC Security and Maintenance
 PC Security and Maintenance by IMRAN GHANI PC Maintenance and Security-Forecast. Major sources of danger. Important steps to protect your PC. PC Security Tools. PC Maintenance Tools. Tips. PC Security-
PC Security and Maintenance by IMRAN GHANI PC Maintenance and Security-Forecast. Major sources of danger. Important steps to protect your PC. PC Security Tools. PC Maintenance Tools. Tips. PC Security-
Introduction. Activating the CFR Module License. CFR Configuration
 Introduction Effective August 20, 1997, the United States Food and Drug Administration released its Code of Federal Regulations (CFR) Title 21 Part 11: Electronic Records; Electronic Signatures (21 CFR
Introduction Effective August 20, 1997, the United States Food and Drug Administration released its Code of Federal Regulations (CFR) Title 21 Part 11: Electronic Records; Electronic Signatures (21 CFR
Setting Up Monthly Reporter
 Setting Up Monthly Reporter April 11, 2014 I. HOW IT WORKS A QUICK OVERVIEW A. AuditWare Development Company maintains a powerful, sophisticated server on which a portion of memory is assigned to each
Setting Up Monthly Reporter April 11, 2014 I. HOW IT WORKS A QUICK OVERVIEW A. AuditWare Development Company maintains a powerful, sophisticated server on which a portion of memory is assigned to each
extranet.airproducts.com Windows XP Client Configuration
 extranet.airproducts.com Windows XP Client Configuration To successfully connect to the Air Products extranet.airproducts.com website and have full functionality, the client computer needs to have the
extranet.airproducts.com Windows XP Client Configuration To successfully connect to the Air Products extranet.airproducts.com website and have full functionality, the client computer needs to have the
CANON FAX L360 SOFTWARE MANUAL
 CANON FAX L360 SOFTWARE MANUAL Before You Begin the Installation: a Checklist 2 To ensure a smooth and successful installation, take some time before you begin to plan and prepare for the installation
CANON FAX L360 SOFTWARE MANUAL Before You Begin the Installation: a Checklist 2 To ensure a smooth and successful installation, take some time before you begin to plan and prepare for the installation
Operating System Installation Guide
 Operating System Installation Guide This guide provides instructions on the following: Installing the Windows Server 2008 operating systems on page 1 Installing the Windows Small Business Server 2011 operating
Operating System Installation Guide This guide provides instructions on the following: Installing the Windows Server 2008 operating systems on page 1 Installing the Windows Small Business Server 2011 operating
Mapping ITS s File Server Folder to Mosaic Windows to Publish a Website
 Mapping ITS s File Server Folder to Mosaic Windows to Publish a Website April 16 2012 The following instructions are to show you how to map your Home drive using ITS s Network in order to publish a website
Mapping ITS s File Server Folder to Mosaic Windows to Publish a Website April 16 2012 The following instructions are to show you how to map your Home drive using ITS s Network in order to publish a website
Changing Passwords in Cisco Unity 8.x
 CHAPTER 9 Changing Passwords in Cisco Unity 8.x This chapter contains the following sections: Changing Passwords for the Cisco Unity 8.x Service Accounts (Without Failover), page 9-1 Changing Passwords
CHAPTER 9 Changing Passwords in Cisco Unity 8.x This chapter contains the following sections: Changing Passwords for the Cisco Unity 8.x Service Accounts (Without Failover), page 9-1 Changing Passwords
How to Use the Yellow Machine Appliance in a Windows 2000/2003 Server Environment
 How to Use the Yellow Machine Appliance in a Windows 2000/2003 Server Environment This procedure is for software versions 2.91 and 2.92 Overview This document will help you to configure the Yellow Machine
How to Use the Yellow Machine Appliance in a Windows 2000/2003 Server Environment This procedure is for software versions 2.91 and 2.92 Overview This document will help you to configure the Yellow Machine
How to Connect to Berkeley College Virtual Lab Using Windows
 How to Connect to Berkeley College Virtual Lab Using Windows Minimum Requirements Create and Save a Remote Desktop Services Connection Connecting to a Remote Desktop Services session Copy Files between
How to Connect to Berkeley College Virtual Lab Using Windows Minimum Requirements Create and Save a Remote Desktop Services Connection Connecting to a Remote Desktop Services session Copy Files between
Configure and enable remote access for windows operating system
 Configure and enable remote access for windows operating system There can be several reasons on why you cannot access a remote computer in your network. In this guide we will focus on troubleshooting the
Configure and enable remote access for windows operating system There can be several reasons on why you cannot access a remote computer in your network. In this guide we will focus on troubleshooting the
SYMANTEC BACKUPEXEC2010 WITH StorTrends
 SYMANTEC BACKUPEXEC2010 WITH StorTrends 1 Index 1. Introduction 3 2. Test Environment 3 3. System Requirement 4 4. Storage Requirement 4 5. Installation of Symantec Backup EXEC 2010 4 6. Installing Backup
SYMANTEC BACKUPEXEC2010 WITH StorTrends 1 Index 1. Introduction 3 2. Test Environment 3 3. System Requirement 4 4. Storage Requirement 4 5. Installation of Symantec Backup EXEC 2010 4 6. Installing Backup
Active Directory Integration for Greentree
 App Number: 010044 Active Directory Integration for Greentree Last Updated 14 th February 2013 Powered by: AppsForGreentree.com 2013 1 Table of Contents Features... 3 Options... 3 Important Notes... 3
App Number: 010044 Active Directory Integration for Greentree Last Updated 14 th February 2013 Powered by: AppsForGreentree.com 2013 1 Table of Contents Features... 3 Options... 3 Important Notes... 3
Objectives. At the end of this chapter students should be able to:
 NTFS PERMISSIONS AND SECURITY SETTING.1 Introduction to NTFS Permissions.1.1 File Permissions and Folder Permission.2 Assigning NTFS Permissions and Special Permission.2.1 Planning NTFS Permissions.2.2
NTFS PERMISSIONS AND SECURITY SETTING.1 Introduction to NTFS Permissions.1.1 File Permissions and Folder Permission.2 Assigning NTFS Permissions and Special Permission.2.1 Planning NTFS Permissions.2.2
Instructions: Configuring Outlook 2003 with Exchange 2010 on the FIUMail
 Instructions: Configuring Outlook 2003 with Exchange 2010 on the FIUMail Environment Some users have been using Outlook 2003 with their IMAP or POP account, and already have a profile set up. For those
Instructions: Configuring Outlook 2003 with Exchange 2010 on the FIUMail Environment Some users have been using Outlook 2003 with their IMAP or POP account, and already have a profile set up. For those
Implementing a SAS Metadata Server Configuration for Use with SAS Enterprise Guide
 Implementing a SAS Metadata Server Configuration for Use with SAS Enterprise Guide Step 1: Setting Up Required Users and Groups o Windows Operating Systems Only Step 2: Installing Software Using the SAS
Implementing a SAS Metadata Server Configuration for Use with SAS Enterprise Guide Step 1: Setting Up Required Users and Groups o Windows Operating Systems Only Step 2: Installing Software Using the SAS
For paid computer support call 604-518-6695 http://www.netdigix.com contact@netdigix.com
 Setting up your vpn connection on windows 2000 or XP in continuation from installing x.509 certificate on windows (please do not continue if you have not installed your x.509 certificate): Instructions
Setting up your vpn connection on windows 2000 or XP in continuation from installing x.509 certificate on windows (please do not continue if you have not installed your x.509 certificate): Instructions
Test Note Phone Manager Deployment Windows Group Policy Sever 2003 and XP SPII Clients
 Test Note Phone Manager Deployment Windows Group Policy Sever 2003 and XP SPII Clients Note: I have only tested these procedures on Server 2003 SP1 (DC) and XP SPII client, in a controlled lab environment,
Test Note Phone Manager Deployment Windows Group Policy Sever 2003 and XP SPII Clients Note: I have only tested these procedures on Server 2003 SP1 (DC) and XP SPII client, in a controlled lab environment,
VERITAS Backup Exec 9.1 for Windows Servers Quick Installation Guide
 VERITAS Backup Exec 9.1 for Windows Servers Quick Installation Guide N109548 Disclaimer The information contained in this publication is subject to change without notice. VERITAS Software Corporation makes
VERITAS Backup Exec 9.1 for Windows Servers Quick Installation Guide N109548 Disclaimer The information contained in this publication is subject to change without notice. VERITAS Software Corporation makes
Secure Agent Quick Start for Windows
 Secure Agent Quick Start for Windows 1993-2015 Informatica Corporation. No part of this document may be reproduced or transmitted in any form, by any means (electronic, photocopying, recording or otherwise)
Secure Agent Quick Start for Windows 1993-2015 Informatica Corporation. No part of this document may be reproduced or transmitted in any form, by any means (electronic, photocopying, recording or otherwise)
Windows Operating Systems. Basic Security
 Windows Operating Systems Basic Security Objectives Explain Windows Operating System (OS) common configurations Recognize OS related threats Apply major steps in securing the OS Windows Operating System
Windows Operating Systems Basic Security Objectives Explain Windows Operating System (OS) common configurations Recognize OS related threats Apply major steps in securing the OS Windows Operating System
Installation Instruction STATISTICA Enterprise Small Business
 Installation Instruction STATISTICA Enterprise Small Business Notes: ❶ The installation of STATISTICA Enterprise Small Business entails two parts: a) a server installation, and b) workstation installations
Installation Instruction STATISTICA Enterprise Small Business Notes: ❶ The installation of STATISTICA Enterprise Small Business entails two parts: a) a server installation, and b) workstation installations
Most of your tasks in Windows XP will involve working with information
 OFFICE 1 File Management Files and Folders Most of your tasks in Windows XP will involve working with information stored on your computer. This material briefly explains how information is stored in Windows
OFFICE 1 File Management Files and Folders Most of your tasks in Windows XP will involve working with information stored on your computer. This material briefly explains how information is stored in Windows
Yale Software Library http://www.yale.edu/software/
 e/ Yale Software Library http://www.yale.edu/software/ For assistance contact the ITS Help Desk 785-3200, 432-9000, helpdesk@yale.edu Remote Desktop General overview With Remote Desktop, you get full access
e/ Yale Software Library http://www.yale.edu/software/ For assistance contact the ITS Help Desk 785-3200, 432-9000, helpdesk@yale.edu Remote Desktop General overview With Remote Desktop, you get full access
How to configure the DBxtra Report Web Service on IIS (Internet Information Server)
 How to configure the DBxtra Report Web Service on IIS (Internet Information Server) Table of Contents Install the DBxtra Report Web Service automatically... 2 Access the Report Web Service... 4 Verify
How to configure the DBxtra Report Web Service on IIS (Internet Information Server) Table of Contents Install the DBxtra Report Web Service automatically... 2 Access the Report Web Service... 4 Verify
STATISTICA VERSION 9 STATISTICA ENTERPRISE INSTALLATION INSTRUCTIONS FOR USE WITH TERMINAL SERVER
 Notes: STATISTICA VERSION 9 STATISTICA ENTERPRISE INSTALLATION INSTRUCTIONS FOR USE WITH TERMINAL SERVER 1. These instructions focus on installation on Windows Terminal Server (WTS), but are applicable
Notes: STATISTICA VERSION 9 STATISTICA ENTERPRISE INSTALLATION INSTRUCTIONS FOR USE WITH TERMINAL SERVER 1. These instructions focus on installation on Windows Terminal Server (WTS), but are applicable
This is a training module for Maximo Asset Management V7.1. In this module, you learn to use the E-Signature user authentication feature.
 This is a training module for Maximo Asset Management V7.1. In this module, you learn to use the E-Signature user authentication feature. Page 1 of 16 When you complete this module, you can perform these
This is a training module for Maximo Asset Management V7.1. In this module, you learn to use the E-Signature user authentication feature. Page 1 of 16 When you complete this module, you can perform these
Activity 1: Scanning with Windows Defender
 Activity 1: Scanning with Windows Defender 1. Click on Start > All Programs > Windows Defender 2. Click on the arrow next to Scan 3. Choose Custom Scan Page 1 4. Choose Scan selected drives and folders
Activity 1: Scanning with Windows Defender 1. Click on Start > All Programs > Windows Defender 2. Click on the arrow next to Scan 3. Choose Custom Scan Page 1 4. Choose Scan selected drives and folders
Information to configure your Windows 7 office computer is described below.
 The Remote Desktop feature in Windows allows you to control your computer from another office or from home. Remote Desktop allows you to use the applications on your office computer, and access your data
The Remote Desktop feature in Windows allows you to control your computer from another office or from home. Remote Desktop allows you to use the applications on your office computer, and access your data
ExhIBIT 1 User Manager and Users Group
 51-30-26 DATA COMMUNICATIONS MANAGEMENT SECURITY IN A WINDOWS NT ENVIRONMENT Gilbert Held INSIDE The User Manager, Creating a User Account, Comparing NT and NetWare Groups, Assigning Users to Groups, Working
51-30-26 DATA COMMUNICATIONS MANAGEMENT SECURITY IN A WINDOWS NT ENVIRONMENT Gilbert Held INSIDE The User Manager, Creating a User Account, Comparing NT and NetWare Groups, Assigning Users to Groups, Working
Installing IDEA v8 Client Software on Citrix Server Environment
 CASEWARE IDEA INC. Installing IDEA v8 Client Software on Citrix Server Environment Quick How to Guide This document describes the process of Installing Caseware IDEA v8 Client software on Citrix Server
CASEWARE IDEA INC. Installing IDEA v8 Client Software on Citrix Server Environment Quick How to Guide This document describes the process of Installing Caseware IDEA v8 Client software on Citrix Server
AeroLab Wireless Network Code of Conduct. Connecting to the AeroLab Wireless Network
 AeroLab Wireless Network Code of Conduct The AeroLab wireless network is intended for academic use only. Any use of the wireless network for BitTorrent or other Peer-to-Peer file sharing is strictly prohibited.
AeroLab Wireless Network Code of Conduct The AeroLab wireless network is intended for academic use only. Any use of the wireless network for BitTorrent or other Peer-to-Peer file sharing is strictly prohibited.
Setting up Your Acusis Email Address. Microsoft Outlook
 Setting up Your Acusis Email Address in Microsoft Outlook Click on your Microsoft Outlook Version you are using: Microsoft Outlook 2002/XP Microsoft Outlook 2003 Microsoft Outlook 2007 Microsoft Outlook
Setting up Your Acusis Email Address in Microsoft Outlook Click on your Microsoft Outlook Version you are using: Microsoft Outlook 2002/XP Microsoft Outlook 2003 Microsoft Outlook 2007 Microsoft Outlook
ODBC Driver Version 4 Manual
 ODBC Driver Version 4 Manual Revision Date 12/05/2007 HanDBase is a Registered Trademark of DDH Software, Inc. All information contained in this manual and all software applications mentioned in this manual
ODBC Driver Version 4 Manual Revision Date 12/05/2007 HanDBase is a Registered Trademark of DDH Software, Inc. All information contained in this manual and all software applications mentioned in this manual
Job Aid: Creating Additional Remote Access Logins
 This job aid describes the steps required to add an additional remote access login to the Avaya S8300, S8500, and S8700 Series Media Servers. These logins may be used to establish a Point to Point Protocol
This job aid describes the steps required to add an additional remote access login to the Avaya S8300, S8500, and S8700 Series Media Servers. These logins may be used to establish a Point to Point Protocol
Setting Up a Backup Domain Controller
 Setting Up a Backup Domain Controller June 27, 2012 Copyright 2012 by World Class CAD, LLC. All Rights Reserved. A Backup Domain Controller After setting up a primary domain controller, we will want to
Setting Up a Backup Domain Controller June 27, 2012 Copyright 2012 by World Class CAD, LLC. All Rights Reserved. A Backup Domain Controller After setting up a primary domain controller, we will want to
Configuring Windows 7 to Use Encrypted (WPA-E) Wireless Services a...
 1 di 9 31/05/2011 14.48 Search This Site All UCSD Sites Blink Home > Technology > Network Services > Connections > Wireless > Windows 7 Configuring Windows 7 to Use Encrypted (WPA-E) Wireless Services
1 di 9 31/05/2011 14.48 Search This Site All UCSD Sites Blink Home > Technology > Network Services > Connections > Wireless > Windows 7 Configuring Windows 7 to Use Encrypted (WPA-E) Wireless Services
MBC WiFi wireless logon: Windows 7 (laptop)
 Connecting to the MBC Guest wireless network requires: FAQ s at end of document A. A connection to the wireless network SSID (identifier for a wireless LAN) from your laptop. B. Authentication to the MBC
Connecting to the MBC Guest wireless network requires: FAQ s at end of document A. A connection to the wireless network SSID (identifier for a wireless LAN) from your laptop. B. Authentication to the MBC
Configuring VPN Using Windows XP
 Configuring VPN Using Windows XP How to Create a VPN Connection What is VPN? Connecting to VPN Create a VPN Connection Connect to Your Work Computer Copying Files What is VPN? Virtual Private Networks
Configuring VPN Using Windows XP How to Create a VPN Connection What is VPN? Connecting to VPN Create a VPN Connection Connect to Your Work Computer Copying Files What is VPN? Virtual Private Networks
Known Issues and Work Around
 Known s and Work Around During Compass 2.0 installation, sometimes you may get a popup message.net framework/sqlexpress could not be installed. Install.Net framework/sqlexpress manually. Sometimes, migration
Known s and Work Around During Compass 2.0 installation, sometimes you may get a popup message.net framework/sqlexpress could not be installed. Install.Net framework/sqlexpress manually. Sometimes, migration
Remote Terminal Service (RTS) User Guide (Version 2.1)
 Remote Terminal Service (RTS) User Guide (Version 2.1) Page 1 Table of Content Content Page 1 Introduction 3 2 Prerequisite 3 3 Logon Corporate Network via Internet 4 4 Download and Install RTS Client
Remote Terminal Service (RTS) User Guide (Version 2.1) Page 1 Table of Content Content Page 1 Introduction 3 2 Prerequisite 3 3 Logon Corporate Network via Internet 4 4 Download and Install RTS Client
Client for Macintosh
 Client for Macintosh Installation Instructions Sequencher Server Network Overview Page 2 Installing the KeyAccess Client Page 3 Logging on to the Server on OSX Page 4 Logging on to the Server in Classic
Client for Macintosh Installation Instructions Sequencher Server Network Overview Page 2 Installing the KeyAccess Client Page 3 Logging on to the Server on OSX Page 4 Logging on to the Server in Classic
Secrets of Event Viewer for Active Directory Security Auditing Lepide Software
 Secrets of Event Viewer for Active Directory Security Auditing Windows Event Viewer doesn t need any introduction to the IT Administrators. However, some of its hidden secrets, especially those related
Secrets of Event Viewer for Active Directory Security Auditing Windows Event Viewer doesn t need any introduction to the IT Administrators. However, some of its hidden secrets, especially those related
MyNetFone Virtual Fax. Virtual Fax Installation
 Table of Contents MyNetFone Virtual Fax MyNetFone Virtual Fax Installation... 1 Changing the SIP endpoint details for the fax driver... 11 Uninstalling Virtual Fax... 13 Virtual Fax Installation Follow
Table of Contents MyNetFone Virtual Fax MyNetFone Virtual Fax Installation... 1 Changing the SIP endpoint details for the fax driver... 11 Uninstalling Virtual Fax... 13 Virtual Fax Installation Follow
Secure Messaging Service
 Human Resources Secure Messaging Service Receiving Secure Emails from West Berkshire Council Table of Contents What are Secure Messaging notifications?... 3 How do I set up my Secure Messaging account?...
Human Resources Secure Messaging Service Receiving Secure Emails from West Berkshire Council Table of Contents What are Secure Messaging notifications?... 3 How do I set up my Secure Messaging account?...
Network Services One Washington Square, San Jose, CA 95192-0209 408-924-1530
 SJSU Premier Wi-Fi Service Network Services One Washington Square, San Jose, CA 95192-0209 408-924-1530 The SJSU Premier Wi-Fi service transmits your data across a secure, encrypted connection. This ensures
SJSU Premier Wi-Fi Service Network Services One Washington Square, San Jose, CA 95192-0209 408-924-1530 The SJSU Premier Wi-Fi service transmits your data across a secure, encrypted connection. This ensures
MacScan. MacScan User Guide. Detect, Isolate and Remove Spyware
 MacScan MacScan User Guide Detect, Isolate and Remove Spyware Part 1 1.1 Introduction MacScan is a spyware detection utility for Macintosh OS X that finds and removes spyware and other Internet files
MacScan MacScan User Guide Detect, Isolate and Remove Spyware Part 1 1.1 Introduction MacScan is a spyware detection utility for Macintosh OS X that finds and removes spyware and other Internet files
3 Setting up Databases on a Microsoft SQL 7.0 Server
 3 Setting up Databases on a Microsoft SQL 7.0 Server Overview of the Installation Process To set up GoldMine properly, you must follow a sequence of steps to install GoldMine s program files, and the other
3 Setting up Databases on a Microsoft SQL 7.0 Server Overview of the Installation Process To set up GoldMine properly, you must follow a sequence of steps to install GoldMine s program files, and the other
ecstudent-ts Terminal Server How to Use
 ecstudent-ts Terminal Server How to Use Connect to Cisco Any Connect Connect to Terminal Server, Set Options to Use Home Computer Files, Printers, Clipboard Use Network Folders Copy Files from Network
ecstudent-ts Terminal Server How to Use Connect to Cisco Any Connect Connect to Terminal Server, Set Options to Use Home Computer Files, Printers, Clipboard Use Network Folders Copy Files from Network
Changing Your Cameleon Server IP
 1.1 Overview Technical Note Cameleon requires that you have a static IP address defined for the server PC the Cameleon server application runs on. Even if the server PC has a static IP address, you may
1.1 Overview Technical Note Cameleon requires that you have a static IP address defined for the server PC the Cameleon server application runs on. Even if the server PC has a static IP address, you may
To install the SMTP service:
 To install the SMTP service: From the Start menu, click Control Panel. 2. Double-click Add or Remove Programs. 3. From the left pane, click Add/Remove Windows Components. 4. From the Components list, click
To install the SMTP service: From the Start menu, click Control Panel. 2. Double-click Add or Remove Programs. 3. From the left pane, click Add/Remove Windows Components. 4. From the Components list, click
Shellshock Security Patch for X86
 Shellshock Security Patch for X86 Guide for Using the FFPS Update Manager October 2014 Version 1.0. Page 1 Page 2 This page is intentionally blank Table of Contents 1.0 OVERVIEW - SHELLSHOCK/BASH SHELL
Shellshock Security Patch for X86 Guide for Using the FFPS Update Manager October 2014 Version 1.0. Page 1 Page 2 This page is intentionally blank Table of Contents 1.0 OVERVIEW - SHELLSHOCK/BASH SHELL
Converting InfoPlus.21 Data to a Microsoft SQL Server 2000 Database
 Technical Bulletin Issue Date August 14, 2003 Converting InfoPlus.21 Data to a Microsoft SQL Server 2000 Database Converting InfoPlus.21 Data to a Microsoft SQL Server 2000 Database...2 Introduction...
Technical Bulletin Issue Date August 14, 2003 Converting InfoPlus.21 Data to a Microsoft SQL Server 2000 Database Converting InfoPlus.21 Data to a Microsoft SQL Server 2000 Database...2 Introduction...
Download/Install IDENTD
 Download/Install IDENTD IDENTD is the small software program that must be installed on each user s computer if multiple filters are to be used in ComSifter. The program may be installed and executed locally
Download/Install IDENTD IDENTD is the small software program that must be installed on each user s computer if multiple filters are to be used in ComSifter. The program may be installed and executed locally
Joining an XP workstation to a domain Version 1.00
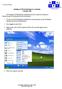 Joining an XP workstation to a domain Version 1.00 All Windows XP Professional workstations need to be joined to a domain to function as part of the domain security environment. Need to Know TM 1. To join
Joining an XP workstation to a domain Version 1.00 All Windows XP Professional workstations need to be joined to a domain to function as part of the domain security environment. Need to Know TM 1. To join
XenApp/Citrix Program Neighborhood Installation
 1. Download the XenApp Plugin (Citrix Presentation Server) Client Package Version 11.0 for Hosted Apps. Click on this LINK to obtain it. Once prompted, click RUN 2. 3. Save the file to your desktop. Once
1. Download the XenApp Plugin (Citrix Presentation Server) Client Package Version 11.0 for Hosted Apps. Click on this LINK to obtain it. Once prompted, click RUN 2. 3. Save the file to your desktop. Once
Identity and Access Management Integration with PowerBroker. Providing Complete Visibility and Auditing of Identities
 Identity and Access Management Integration with PowerBroker Providing Complete Visibility and Auditing of Identities Table of Contents Executive Summary... 3 Identity and Access Management... 4 BeyondTrust
Identity and Access Management Integration with PowerBroker Providing Complete Visibility and Auditing of Identities Table of Contents Executive Summary... 3 Identity and Access Management... 4 BeyondTrust
Installing Crystal Reports Runtime For use with the Human Resource Suite when using Progress version 9
 For use with the Human Resource Suite when using Progress version 9 Contents Introduction... 1 Step 1. Install Crystal Reports Runtime on the PC... 1 Step 2. Set Up ODBC Data Sources... 2 If using Windows
For use with the Human Resource Suite when using Progress version 9 Contents Introduction... 1 Step 1. Install Crystal Reports Runtime on the PC... 1 Step 2. Set Up ODBC Data Sources... 2 If using Windows
Instructions for connecting to the FDIBA Wireless Network. (Windows XP)
 Instructions for connecting to the FDIBA Wireless Network (Windows XP) In order to connect, you need your username and password, as well as the FDIBA Root Certificate which you need to install on your
Instructions for connecting to the FDIBA Wireless Network (Windows XP) In order to connect, you need your username and password, as well as the FDIBA Root Certificate which you need to install on your
About This Document 3. About the Migration Process 4. Requirements and Prerequisites 5. Requirements... 5 Prerequisites... 5
 Contents About This Document 3 About the Migration Process 4 Requirements and Prerequisites 5 Requirements... 5 Prerequisites... 5 Installing the Migration Tool and Enabling Migration 8 On Linux Servers...
Contents About This Document 3 About the Migration Process 4 Requirements and Prerequisites 5 Requirements... 5 Prerequisites... 5 Installing the Migration Tool and Enabling Migration 8 On Linux Servers...
Adding a User to Active Directory in Windows Server 2012
 Adding a User to Active Directory in Windows Server 2012 June 19, 2013 Copyright 2013 by World Class CAD, LLC. All Rights Reserved. Setup Security Policies To add a new user on a Domain Controller on the
Adding a User to Active Directory in Windows Server 2012 June 19, 2013 Copyright 2013 by World Class CAD, LLC. All Rights Reserved. Setup Security Policies To add a new user on a Domain Controller on the
Prepared by Mythtech Limited OFFICE 365 EMAIL MIGRATION MANUAL GUIDELINE
 Prepared by Mythtech Limited OFFICE 365 EMAIL MIGRATION MANUAL GUIDELINE Table of Contents Change Password... 1 Send New Email... 2 Forward E-mail... 3 Reply E-mail... 4 Archive old emails... 5 Office
Prepared by Mythtech Limited OFFICE 365 EMAIL MIGRATION MANUAL GUIDELINE Table of Contents Change Password... 1 Send New Email... 2 Forward E-mail... 3 Reply E-mail... 4 Archive old emails... 5 Office
Setting up an MS SQL Server for IGSS
 Setting up an MS SQL Server for IGSS Table of Contents Table of Contents...1 Introduction... 2 The Microsoft SQL Server database...2 Setting up an MS SQL Server...3 Installing the MS SQL Server software...3
Setting up an MS SQL Server for IGSS Table of Contents Table of Contents...1 Introduction... 2 The Microsoft SQL Server database...2 Setting up an MS SQL Server...3 Installing the MS SQL Server software...3
How to Access Coast Wi-Fi
 How to Access Coast Wi-Fi Below is a summary of the information required to configure your device to connect to the coast-wifi network. For further assistance in configuring your specific device, continue
How to Access Coast Wi-Fi Below is a summary of the information required to configure your device to connect to the coast-wifi network. For further assistance in configuring your specific device, continue
Scan to SMB(PC) Set up Guide
 Scan to SMB(PC) Set up Guide Regarding Trade Names Windows is a registered trademark of Microsoft Corporation in the U.S.A. and/or other countries. Windows XP and Windows Vista are trademarks of Microsoft
Scan to SMB(PC) Set up Guide Regarding Trade Names Windows is a registered trademark of Microsoft Corporation in the U.S.A. and/or other countries. Windows XP and Windows Vista are trademarks of Microsoft
Zanibal Plug-in For Microsoft Outlook Installation & User Guide Version 1.1
 Zanibal Plug-in For Microsoft Outlook Installation & User Guide Version 1.1 Zanibal LLC Phone: +1-408-887-0480, +234-1-813-1744 Email: support@zanibal.com www.zanibal.com Copyright 2012, Zanibal LLC. All
Zanibal Plug-in For Microsoft Outlook Installation & User Guide Version 1.1 Zanibal LLC Phone: +1-408-887-0480, +234-1-813-1744 Email: support@zanibal.com www.zanibal.com Copyright 2012, Zanibal LLC. All
VPN clients configuration for Windows 98SE - for Library access
 VPN clients configuration for Windows 98SE - for Library access Requirements: 1. These instructions are only applicable for a computer that has Windows 98SE with a current Internet dialup connection. Note
VPN clients configuration for Windows 98SE - for Library access Requirements: 1. These instructions are only applicable for a computer that has Windows 98SE with a current Internet dialup connection. Note
CROSSPOINTE AT SABLE SUITE 150 3102 CHERRY PALM DRIVE TAMPA, FL 33619 UNITED STATES OF AMERICA TEL: (813) 621-8001 FAX:
 Network setup using MS Network Client 3.0 for DOS. You should have the MS Client install disks 1 and 2, available on the installation CD for Windows NT/2000 server, and the DOS driver disk supplied with
Network setup using MS Network Client 3.0 for DOS. You should have the MS Client install disks 1 and 2, available on the installation CD for Windows NT/2000 server, and the DOS driver disk supplied with
File Management and File Storage
 File Management and File Storage http://training.usask.ca Information Technology Services Division Table of Contents File Management at the University of Saskatchewan...3 Introduction...3 Creating Files
File Management and File Storage http://training.usask.ca Information Technology Services Division Table of Contents File Management at the University of Saskatchewan...3 Introduction...3 Creating Files
Avatier Identity Management Suite
 Avatier Identity Management Suite Migrating AIMS Configuration and Audit Log Data To Microsoft SQL Server Version 9 2603 Camino Ramon Suite 110 San Ramon, CA 94583 Phone: 800-609-8610 925-217-5170 FAX:
Avatier Identity Management Suite Migrating AIMS Configuration and Audit Log Data To Microsoft SQL Server Version 9 2603 Camino Ramon Suite 110 San Ramon, CA 94583 Phone: 800-609-8610 925-217-5170 FAX:
How to Enable the Audit of Active Directory Objects in Windows 2008 R2 Lepide Software
 How to Enable the Audit of Active Directory Objects in Windows 2008 R2 Windows 2008 R2 has much more and better features than its predecessors. It also wins in the native auditing part when it comes to
How to Enable the Audit of Active Directory Objects in Windows 2008 R2 Windows 2008 R2 has much more and better features than its predecessors. It also wins in the native auditing part when it comes to
Hosted Microsoft Exchange Client Setup & Guide Book
 Hosted Microsoft Exchange Client Setup & Guide Book Section 1 Microsoft Outlook Web Access (OWA) access directions Section 2 Windows Mobile Phone ActiveSync setup & configuration Section 3 - Apple iphone
Hosted Microsoft Exchange Client Setup & Guide Book Section 1 Microsoft Outlook Web Access (OWA) access directions Section 2 Windows Mobile Phone ActiveSync setup & configuration Section 3 - Apple iphone
PPUM icare SINGLE SIGN ON
 Double click the Single Sign On shortcut located in the desktop. Enter user PPUM icare ID in the User ID text box. Leave the Password text box as blank. Click Login button. You will be prompt about the
Double click the Single Sign On shortcut located in the desktop. Enter user PPUM icare ID in the User ID text box. Leave the Password text box as blank. Click Login button. You will be prompt about the
User Guide Microsoft Exchange Remote Test Instructions
 User Guide Microsoft Exchange Remote Test Instructions University of Louisville Information Technology 1.1 Who Should Use It This guide is intended for University of Louisville Faculty and Staff participating
User Guide Microsoft Exchange Remote Test Instructions University of Louisville Information Technology 1.1 Who Should Use It This guide is intended for University of Louisville Faculty and Staff participating
SARANGSoft WinBackup Business v2.5 Client Installation Guide
 SARANGSoft WinBackup Business v2.5 Client Installation Guide (November, 2015) WinBackup Business Client is a part of WinBackup Business application. It runs in the background on every client computer that
SARANGSoft WinBackup Business v2.5 Client Installation Guide (November, 2015) WinBackup Business Client is a part of WinBackup Business application. It runs in the background on every client computer that
Password Policy Enforcer
 Password Policy Enforcer Evaluator s Guide V7.6 Copyright 1998-2013 ANIXIS. All rights reserved. ANIXIS, ANIXIS Password Reset, Password Policy Enforcer, PPE/Web, Password Policy Client, Password Policy
Password Policy Enforcer Evaluator s Guide V7.6 Copyright 1998-2013 ANIXIS. All rights reserved. ANIXIS, ANIXIS Password Reset, Password Policy Enforcer, PPE/Web, Password Policy Client, Password Policy
EventTracker: Integrating Imperva SecureSphere
 EventTracker: Integrating Imperva SecureSphere Publication Date: June 14, 2012 EventTracker 8815 Centre Park Drive Columbia MD 21045 www.eventtracker.com About This Guide Abstract This guide provides instructions
EventTracker: Integrating Imperva SecureSphere Publication Date: June 14, 2012 EventTracker 8815 Centre Park Drive Columbia MD 21045 www.eventtracker.com About This Guide Abstract This guide provides instructions
Both MS Windows 2000 Server and MS System Management Server (SMS) support this type of network installation.
 Network Installation of OmniPage Pro 12 Office Introduction Network installation enables a system administrator to push applications out to client computers without the need to visit each client system.
Network Installation of OmniPage Pro 12 Office Introduction Network installation enables a system administrator to push applications out to client computers without the need to visit each client system.
4cast Client Specification and Installation
 4cast Client Specification and Installation Version 2015.00 10 November 2014 Innovative Solutions for Education Management www.drakelane.co.uk System requirements The client requires Administrative rights
4cast Client Specification and Installation Version 2015.00 10 November 2014 Innovative Solutions for Education Management www.drakelane.co.uk System requirements The client requires Administrative rights
