Chapter 6 IPv4 Addresses
|
|
|
- Letitia Gilmore
- 7 years ago
- Views:
Transcription
1 Chapter 6 IPv4 Addresses
2 Network Math 2
3 Base 10 (Decimal) Number System Digits (10): 0, 1, 2, 3, 4, 5, 6, 7, 8, 9 Number of: ,000 s 1,000 s 100 s 10 s 1 s 1,
4 Number System Rules 1. All digits start with 0 2. A Base-n number system has n number of digits: Decimal: Base-10 has 10 digits Binary: Base-2 has 2 digits Hexadecimal: Base-16 has 16 digits 3. The first column is always the number of 1 s Each of the following columns is n times the previous column (n = Base-n) Base 10: 10,000 1, Base 2: Base 16: 65,536 4,
5 Digits (2): 0, 1 Number of: Dec s 8 s 4 s 2 s 1 s
6 Digits (2): 0, 1 Number of: Dec s 64 s 32 s 16 s 8 s 4 s 2 s 1 s
7 Digits (2): 0, 1 Number of: Dec s 64 s 32 s 16 s 8 s 4 s 2 s 1 s
8 Digits (2): 0, 1 Number of: Dec s 64 s 32 s 16 s 8 s 4 s 2 s 1 s
9 IPv4 Addresses
10 IPv4 Addresses IPv4 addresses are 32 bit addresses 10
11 IPv4 Addresses IPv4 Addresses are 32 bit addresses: We use dotted notation (or dotted decimal notation) to represent the value of each byte (octet) of the IP address in decimal
12 IPv4 Addresses An IP address has two parts: network number host number Which bits refer to the network number? Which bits refer to the host number? 12
13 IPv4 Addresses Answer: Newer technology - Classless IP Addressing The subnet mask determines the network portion and the host portion. Value of first octet does NOT matter (older classful IP addressing) Hosts and Classless Inter-Domain Routing (CIDR). Classless IP Addressing is what is used within the Internet and in most internal networks. Older technology - Classful IP Addressing (later) Value of first octet determines the network portion and the host portion. Used with classful routing protocols like RIPv1. The Cisco IP Routing Table is structured in a classful manner We shall see this on the CCNA Routing part 13
14 Types of Addresses Network Addresses have all 0 s in the host portion. Subnet Mask: Network address - The address by which we refer to the network Broadcast address - A special address used to send data to all hosts in the network Host addresses - The addresses assigned to the end devices in the network 14
15 Types of Addresses Broadcast Addresses have all 1 s in the host portion. Subnet Mask: Network address - The address by which we refer to the network Broadcast address - A special address used to send data to all hosts in the network Host addresses - The addresses assigned to the end devices in the network 15
16 Types of Addresses Host Addresses can not have all 0 s or all 1 s in the host portion. Subnet Mask: Network address - The address by which we refer to the network Broadcast address - A special address used to send data to all hosts in the network Host addresses - The addresses assigned to the end devices in the network 16
17 Dividing the Network and Host Portions Subnet Mask Used to define the: Network portion Host portion 32 bits Contiguous set of 1 s followed by a contiguous set of 0 s 1 s: Network portion 0 s: Host portion 17
18 Dividing the Network and Host Portions Expressed as: Dotted decimal Ex: Slash notation or prefix length /16 (the number of one bits) Dotted decimal: Slash notation: /16 18
19 Network Addresses Subnet Mask: Network address - The address by which we refer to the network All binary 0 s in the host portion of the address (more later) 19
20 Example 1 Network Address: Subnet Mask: Network Host Network Address in binary: Subnet Mask in binary: Prefix Length: /24 20
21 Example 2 Network Address: Subnet Mask: Network Host Network Address in binary: Subnet Mask in binary: Prefix Length : /8 21
22 Example 3 Network Address: Subnet Mask: Network Host Network Address in binary: Subnet Mask in binary: Prefix Length: /16 22
23 Why the mask matters: Number of hosts! Subnet Mask: or / or /16 1st octet 2nd octet 3rd octet 4th octet Network Host Host Host Network Network Host Host or /24 Network Network Network Host The more host bits in the subnet mask means the more hosts in the network. Subnet masks do not have to end on natural octet boundaries 23
24 Subnet: (/8) Network Host Host Host 8 bits 8 bits 8 bits With 24 bits available for hosts, there a 2 24 possible addresses. That s 16,777,216 nodes! Only large organizations such as the military, government agencies, universities, and large corporations have networks with these many addresses. Example: A certain cable modem ISP has and a DSL ISP has
25 Subnet: (/16) Network Network Host Host 8 bits 8 bits With 16 bits available for hosts, there a 2 16 possible addresses. That s 65,536 nodes! 65,534 host addresses, one for network address and one for broadcast address. 25
26 Subnet: (/24) Network Network Network Host 8 bits With 8 bits available for hosts, there a 2 8 possible addresses. That s 256 nodes! 254 host addresses, one for network address and one for broadcast address. 26
27 IP Addresses There is a tradeoff between: The number of network bits and the number of networks (subnets) you can have AND The number of HOST bits and the number of hosts for each network you can have. This will be examined more closely, later. 27
28 Broadcast Addresses Broadcast address - A special address used to send data to all hosts in the network All binary 1 s in the host portion of the address (more later) 28
29 Bringing it all together Subnet Mask divides Network portion and Host portion: 1 s: Network portion 0 s: Host portion Network address: All 0 s in the host portion of the address Broadcast address: All 1 s in the host portion of the address 29
30 Host IP Addresses /24 Host IP Addresses contain: Network portion of the address Unique combination of 0 s and 1 s in the host portion of the address Cannot be all 0 s (network address) Cannot be all 1 s (broadcast address) Hosts have subnet masks to determine network portion (later) 30
31 Subnet Masks: Non-Natural Boundaries Subnet masks do not have to end on natural octet boundaries Convert these to binary: Network Address Subnet Mask
32 Subnet Masks: Non-Natural Boundaries Subnet masks do not have to end on natural octet boundaries What is the range of host addresses in dotted-decimal and binary? What is the broadcast address? How many host addresses? 32
33 Subnet Masks: Non-Natural Boundaries Subnet masks do not have to end on natural octet boundaries
34 Subnet Masks: Non-Natural Boundaries Subnet masks do not have to end on natural octet boundaries (broadcast) Number of hosts: = 4,096 2 = 4,094 hosts 34
35 Subnet Masks: Non-Natural Boundaries Subnet masks do not have to end on natural octet boundaries (broadcast) 35
36 Subnet Masks: Non-Natural Boundaries Subnet masks do not have to end on natural octet boundaries (broadcast) Number of hosts: = 32 2 = 30 hosts 36
37 Regional Internet Registries (RIR) The 5 RIR s are: AfriNIC (African Network Information Centre) - Africa Region APNIC (Asia Pacific Network Information Centre) - Asia/Pacific Region ARIN (American Registry for Internet Numbers) - North America Region LACNIC (Regional Latin-American and Caribbean IP Address Registry) - Latin America and some Caribbean Islands RIPE NCC (Reseaux IP Europeans) - Europe, the Middle East, and Central Asia
38 ISP (Internet Service Providers) Most companies or organizations obtain their IPv4 address blocks from an ISP. Tier 1 ISP: Large national or international ISPs that are directly connected to the Internet backbone. Customers of Tier 1 ISPs: lower-tiered ISPs large companies and organizations. Offer reliability and speed AOL, SPRINT, Global Crossing, AT&T, Level 3, Verizon, NTT, Quest, SAVVIS 38
39 ISP (Internet Service Providers) Most companies or organizations obtain their IPv4 address blocks from an ISP. Tier 2 ISP: Acquire their Internet service from Tier 1 ISPs. Tier 2 ISPs generally focus on business customers. Examples: Allstream, AboveNet, British Telecom, Cogent Communications, France Telecom, Teleglobe TeliaSonera International Carrier Time Warner Telecom, Tiscali International Network, XO Communications 39
40 ISP (Internet Service Providers) Most companies or organizations obtain their IPv4 address blocks from an ISP. Tier 3 ISP: Purchase their Internet service from Tier 2 ISPs. The focus of these ISPs is the retail and home markets in a specific locale. Examples: Local ISPs 40
41 Special Unicast IPv4 Addresses Default Route Loopback Address Special address that hosts use to direct traffic to themselves to Link-Local Addresses to ( /16) Can be automatically assigned to the local host by the operating system in environments where no IP configuration is available. TEST-NET Addresses to ( /24) Set aside for teaching and learning purposes. These addresses can be used in documentation and network examples. 41
42 Private IP Addresses RFC to ( /8) to ( /12) to ( /16) The addresses will not be routed in the Internet Need NAT/PAT (next) Should be blocked by your ISP Allows for any network to have up to 16,777,216 hosts (/8) 42
43 Introducing NAT and PAT NAT is designed to conserve IP addresses and enable networks to use private IP addresses on internal networks. These private, internal addresses are translated to routable, public addresses. IPv4 addresses are almost depleted. NAT/PAT has allowed IPv4 to be the predominant network protocol, keeping IPv6 at-bay (for now). 43
44 NAT Example The translation from Private source IP address to Public source IP address. 44
45 4 NAT Example 3 4 Translation back, from Public destination IP address to Private destination IP address. 3 45
46 PAT Example NAT/PAT table maintains translation of: DA, SA, SP
47 PAT Example NAT/PAT table maintains translation of: SA (DA), DA (SA), DP (SP)
48 The Subnet Mask and the AND Operation
49 Subnet Mask Host: I m a host on the /24 network. The subnet mask is used to separate the network portion from the host portion of the address. On a host, the subnet mask tells the host what network it belongs to. Why does a host need to know what network it belongs to? 49
50 Subnet Mask Host: I m a host on the /24 network. Why does a host need to know what network it belongs to? So, it knows whether to encapsulate the IP packet into an Ethernet frame with: The Destination MAC Address of the default gateway Must know the default gateway s IP address The Destination MAC Address of the host with the Destination IP address of the packet Later when we discuss Ethernet 50
51 Subnet Mask Network Host Host IP: Mask: Net Add: Devices such as hosts use the bit-wise AND operation on the: Host IP address Subnet mask AND operation: 1 AND 1 = 1 0 AND anything = 0 51
52 Subnet Mask Network Host Host IP: Mask: Net Add: AND operation: 1 AND 1 = 1 0 AND anything = 0 52
53 Subnet Mask Network Host Host IP: Mask: Net Add: AND operation: 1 AND 1 = 1 0 AND anything = 0 53
54 Subnet Masks: Non-Natural Boundaries Subnet masks do not have to end on natural octet boundaries (broadcast) Number of hosts: = 4,096 2 = 4,094 hosts 54
55 Subnetting: First Look
56 Subnets and Subnet Masks Formalized in 1985, the subnet mask breaks a single network in to smaller pieces. Allows network administrators to divide their network into small networks or subnets. Advantages will be discussed later. 56
57 What is subnetting? Network Network Host Host Network Network Subnet Host Subnetting is the process of borrowing bits from the HOST bits, in order to divide the larger network into small subnets. Subnetting does NOT give you more hosts, but actually costs you hosts. You lose two host IP Addresses for each subnet, one for the subnet IP address and one for the subnet broadcast IP address. You lose the last subnet and all of it s hosts IP addresses as the broadcast for that subnet is the same as the broadcast for the network. In older technology, you would have lost the first subnet, as the subnet IP address is the same as the network IP address. (This subnet can be used in most networks.) 57
58 Analogy 98 Apples (100 2) Before subnetting: In any network (or subnet) we can not use all the IP addresses for host addresses. We lose two addresses for every network or subnet. 1. Network Address - One address is reserved to that of the network. For Example: /16 2. Broadcast Address One address is reserved to address all hosts in that network or subnet. For Example: This gives us a total of 65,534 usable hosts 58
59 Analogy 10 barrels x 10 apples = 100 apples Apples (100 2) It is the same as taking a barrel of 100 apples and dividing it into 10 barrels of 10 apples each. 59
60 10 barrels x 8 apples = 80 apples (less 2) (less 2) (less 2) 98 Apples (100 2) 2 = 1 network address + 1 broadcast address (less 2) (less 2) (less 2) (less 2) (less 2) (less 2) However, in subnetting we will see that we lose two apples per subnet: one for the network address one for the broadcast address (less 2) 8 60
61 8 barrels x 8 apples = 64 apples 98 Apples (100 2) X (less 2) (less 2) (less 2) = 1 network address + 1 broadcast address (less 2) (less 2) (less 2) In legacy networks, we also lost: The first basket (subnet) The network address of the first subnet is the network address of the entire network The last basket (subnet) The broadcast address for the last subnet is the same as for the entire network. (less 2) (less 2) (less 2) X (less 2) 8 61
62 Subnet Example Network address with /16 Base Network Mask Using Subnets: Subnet Mask or /24 Network Network Subnet Host Subnet addresses: All 0 s in host portion Etc Subnets Addresses 256 Subnets
63 Subnet Example Network address with /16 Base Network Mask Using Subnets: Subnet Mask or /24 Network Network Subnet Hosts Etc Each subnet has 254 hosts, Broadcast
64 With NO subnetting: Host IP Address: A host of the /24 network Network First Host Last Host Broadcast ,534 host addresses, one for network address and one for broadcast address. Host IP Address: A host of the /16 network 64
65 With subnetting: Host IP Address: A host of the /24 network Network First Host Last Host Broadcast
66 With subnetting: Network First Host Last Host Broadcast Hosts ,024 Total address = 256 subnets * (256 hosts 2) = 256 * 254 = 65,024 NOTE: It is common for some network administrator to not use the last subnet. 66
67 With subnetting: Network First Host Last Host Broadcast Major Network Address: Major Network Mask: Major Network Broadcast Address: Subnet Mask: First Subnet: Subnet Address: Subnet Broadcast Address: Last Subnet: Subnet Address: Subnet Broadcast Address:
68 Calculating the number subnets/hosts needed
69 Calculating the number subnets/hosts needed Network Host Network /24 Need: As many subnets as possible, 60 hosts per subnet 69
70 Calculating the number subnets/hosts needed Number of hosts per subnet Network Host 6 host bits Network /24 Need: As many subnets as possible, 60 hosts per subnet 70
71 Calculating the number subnets/hosts needed Number of subnets Network Host 6 host bits Network /24 Need: As many subnets as possible, 60 hosts per subnet New Subnet Mask: (/26) Number of Hosts per subnet: 6 bits, 64-2 hosts, 62 hosts Number of Subnets: 2 bits or 4 subnets 71
72 Calculating the number subnets/hosts needed Network Host Network /24 Need: As many subnets as possible, 12 hosts per subnet 72
73 Calculating the number subnets/hosts needed Number of hosts per subnet Network Host 4 host bits Network /24 Need: As many subnets as possible, 12 hosts per subnet 73
74 Calculating the number subnets/hosts needed Number of hosts per subnet Number of subnets Network Host 4 host bits Network /24 Need: As many subnets as possible, 12 hosts per subnet New Subnet Mask: (/28) Number of Hosts per subnet: 4 bits, 16-2 hosts, 14 hosts Number of Subnets: 4 bits or 16 subnets 74
75 Calculating the number subnets/hosts needed Network Host Network /24 Need: Need 6 subnets, as many hosts per subnet as possible 75
76 Calculating the number subnets/hosts needed Number of subnets subnet bits Network Host Network /24 Need: Need 6 subnets, as many hosts per subnet as possible 76
77 Calculating the number subnets/hosts needed Number of hosts per subnet subnet bits Network Host Number of subnets Network /24 Need: Need 6 subnets, as many hosts per subnet as possible New Subnet Mask: (/27) Number of Hosts per subnet: 5 bits, 32-2 hosts, 30 hosts Number of Subnets: 3 bits or 8 subnets 77
78 VLSM (Variable Length Subnet Masks)
79 VLSM If you know how to subnet, you can do VLSM. Example: /8 Subnet in /16 subnets: / / / /16 Etc. Subnet one of the subnets ( /16) / / / /24 etc 79
80 VLSM Host can only be a member of the subnet. Host can NOT be a member of the network that was subnetted. YES! / /16 All other /16 subnets are still available for use as /16 networks or to be subnetted. NO! 80
81 VLSM Using the chart This chart can be used to help determine subnet addresses. This can any octet. We ll keep it simple and make it the fourth octet. Network: /24 What if we needed 10 subnets with a minimum of 12 hosts? What would the Mask be? What would the addresses of each subnet be? What would the range of hosts be for each subnet? 81
82 VLSM Using the chart Network: /24 What if we needed 5 subnets? What would the Mask be? (/28) What would the addresses of each subnet be? / / / / / / / /28 What would the range of valid hosts for each subnet? /26: /26: /26: /26: Etc. 82
83 16 /30 subnets VLSM Using the chart What if we needed several (four) /30 subnets for our serial links? Take one of the /27 subnets and subnet it again into /30 subnets. Still have 7 / 27 subnets 16 /30 subnets 83
84 Apply the information to this topology Using the worksheet provided apply the subnetting scheme to the topology. 84
85 Classful Subnetting
86 Classful IP Addressing In the early days of the Internet, IP addresses were allocated to organizations based on request rather than actual need. When an organization received an IP network address, that address was associated with a Class, A, B, or C. This is known as Classful IP Addressing The first octet of the address determined what class the network belonged to and which bits were the network bits and which bits were the host bits. There were no subnet masks. It was not until 1992 when the IETF introduced CIDR (Classless Interdomain Routing), making the address class meaning less. This is known as Classless IP Addressing. For now, all you need to know is that today s networks are classless, except for some things like the structure of Cisco s IP routing table and for those networks that still use Classful routing protocols. 86
87 IPv4 Address Classes 87
88 Address Classes Class A Class B 1st octet 2nd octet 3rd octet 4th octet Network Host Host Host Network Network Host Host Class C Network Network Network Host N = Network number assigned by ARIN (American Registry for Internet Numbers) H = Host number assigned by administrator 88
89 Class A addresses Default Mask: (/8) First octet is between 0 127, begins with 0 Network Host Host Host Number between bits 8 bits 8 bits With 24 bits available for hosts, there a 2 24 possible addresses. That s 16,777,216 nodes! There are 126 class A addresses. 0 and 127 have special meaning and are not used. 16,777,214 host addresses, one for network address and one for broadcast address. Only large organizations such as the military, government agencies, universities, and large corporations have class A addresses. For example ISPs have and Class A addresses account for 2,147,483,648 of the possible IPv4 addresses. That s 50 % of the total unicast address space, if classful was still used in the Internet! 89
90 Class B addresses Default Mask: (/16) First octet is between , begins with 10 Network Network Host Host Number between There are 16,384 (2 14 ) class B networks. 8 bits 8 bits With 16 bits available for hosts, there a 2 16 possible addresses. That s 65,536 nodes! 65,534 host addresses, one for network address and one for broadcast address. Class B addresses represent 25% of the total IPv4 unicast address space. Class B addresses are assigned to large organizations including corporations (such as Cisco, government agencies, and school districts). 90
91 Class C addresses Default Mask: (/24) First octet is between , begins with 110 Network Network Network Host Number between bits With 8 bits available for hosts, there a 2 8 possible addresses. That s 256 nodes! There are 2,097,152 possible class C networks. 254 host addresses, one for network address and one for broadcast address. Class C addresses represent 12.5% of the total IPv4 unicast address space. 91
92 IPv4 Address Classes No medium size host networks In the early days of the Internet, IP addresses were allocated to organizations based on request rather than actual need. 92
93 Network based on first octet The network portion of the IP address was dependent upon the first octet. There was no Base Network Mask provided by the ISP. The network mask was inherent in the address itself. 93
94 IPv4 Address Classes Class D Addresses A Class D address begins with binary 1110 in the first octet. First octet range 224 to 239. Class D address can be used to represent a group of hosts called a host group, or multicast group. Class E Addresses First octet of an IP address begins with 1111 Class E addresses are reserved for experimental purposes and should not be used for addressing hosts or multicast groups. 94
95 Fill in the information Class Default Mask: Network: Broadcast: Hosts: through Class Default Mask: Network: Broadcast: Hosts: through Class Default Mask: Network: Broadcast: Hosts: through 95
96 Fill in the information Class C Default Mask: Network: Broadcast: Hosts: through Class A Default Mask: Network: Broadcast: Hosts: through Class B Default Mask: Network: Broadcast: Hosts: through
97 Class separates network from host bits The Class determines the Base Network Mask! Class C Default Mask: Network: Class A Default Mask: Network: Class B Default Mask: Network:
98 Know the classes! First First Network Host Class Bits Octet Bits Bits A B C D E
99 IP addressing crisis Address Depletion Internet Routing Table Explosion 99
100 IPv4 Addressing Subnet Mask One solution to the IP address shortage was thought to be the subnet mask. Formalized in 1985 (RFC 950), the subnet mask breaks a single class A, B or C network in to smaller pieces. This does allow a network administrator to divide their network into subnets. Routers still associated an network address with the first octet of the IP address. 100
101 All Zeros and All Ones Subnets Using the All Ones Subnet There is no command to enable or disable the use of the all-ones subnet, it is enabled by default. Router(config)#ip subnet-zero The use of the all-ones subnet has always been explicitly allowed and the use of subnet zero is explicitly allowed since Cisco IOS version RFC 1878 states, "This practice (of excluding all-zeros and all-ones subnets) is obsolete! Modern software will be able to utilize all definable networks." Today, the use of subnet zero and the all-ones subnet is generally accepted and most vendors support their use, though, on certain networks, particularly the ones using legacy software, the use of subnet zero and the all-ones subnet can lead to problems. CCO: Subnet Zero and the All-Ones Subnet tech/tk648/tk361/technologies_tech_note09186a f18.shtml 101
102 Long Term Solution: IPv6 (coming) IPv6, or IPng (IP the Next Generation) uses a 128-bit address space, yielding 340,282,366,920,938,463,463,374,607,431,768,211,456 possible addresses. IPv6 has been slow to arrive IPv6 requires new software; IT staffs must be retrained IPv6 will most likely coexist with IPv4 for years to come. Some experts believe IPv4 will remain for more than 10 years. 102
103 Short Term Solutions: IPv4 Enhancements Discussed in CIS 83 and CIS 185 CIDR (Classless Inter-Domain Routing) RFCs 1517, 1518, 1519, 1520 VLSM (Variable Length Subnet Mask) RFC 1009 Private Addressing - RFC 1918 NAT/PAT (Network Address Translation / Port Address Translation) RFC More later when we discuss TCP 103
104 ICMP: Ping and Trace
105 Partial list ICMP (Internet Control Message Protocol) ICMP: A Layer 3 protocol Used for sending messages Encapsulated in a Layer 3, IP packet Uses Type and Code fields for various messages 105
106 ICMP Unreachable Destination or Service Used to notify a host that the destination or service is unreachable. When a host or router receives a packet that it cannot deliver, it may send an ICMP Destination Unreachable packet to the host originating the packet. The Destination Unreachable packet will contain codes that indicate why the packet could not be delivered. From a router: 0 = network unreachable Does not have a route in the routing table 1 = host unreachable Has a route but can t find host. (end router) From a host: 2 = protocol unreachable 3 = port unreachable Service is not available because no daemon is running providing the service or because security on the host is not allowing access to the service. 106
107
108 Ping Uses ICMP message encapsulated within an IP Packet Protocol field = 1 Does not use TCP or UDP Format ping ip address (or ping <cr> for extended ping) ping
109 Echo Request The sender of the ping, transmits an ICMP message, Echo Request Echo Request - Within ICMP Message Type = 8 Code = 0 109
110 Echo Reply The IP address (destination) of the ping, receives the ICMP message, Echo Request The ip address (destination) of the ping, returns the ICMP message, Echo Reply Echo Reply - Within ICMP Message Type = 0 Code = 0 110
111 Ping example 111
112 Pings may fail Q: Are pings forwarded by routers? A: Yes! This is why you can ping devices all over the Internet. Q: Do all devices forward or respond to pings? A: No, this is up to the network administrator of the device. Devices, including routers, can be configured not to reply to pings (ICMP echo requests). This is why you may not always be able to ping a device. Also, routers can be configured not to forward pings destined for other devices. 112
113 Traceroute Traceroute is a utility that records the route (router IP addresses) between two devices on different networks. 113
114 Traceroute On modern Unix and Linux-based operating systems, the traceroute utility by default uses UDP datagrams with a destination port number starting at The traceroute utility usually has an option to specify use of ICMP echo request (type 8) instead. The Windows utility uses ICMP echo request, better known as ping packets. Some firewalls on the path being investigated may block UDP probes but allow the ICMP echo request traffic to pass through. There are also traceroute implementations sending out TCP packets, such as tcptraceroute or Layer Four Trace. In Microsoft Windows, traceroute is named tracert. A new utility, pathping, was introduced with Windows NT, combining ping and traceroute functionality. All these traceroutes rely on ICMP (type 11) packets coming back. 114
115 Trace (Traceroute) Trace ( Cisco = traceroute, tracert, ) is used to trace the probable path a packet takes between source and destination. Probable, because IP is a connectionless protocol, and different packets may take different paths between the same source and destination networks, although this is not usually the case. Trace will show the path the packet takes to the destination, but the return path may be different. This is more likely the case in the Internet, and less likely within your own autonomous system. Linux/Unix Systems Uses ICMP message within an IP Packet Both are layer 3 protocols. Uses UDP as a the transport layer. We will see why this is important in a moment. 115
116 Trace Format (trace, traceroute, tracert) RTA# traceroute ip address RTA# traceroute
117 Trace How it works (using UDP) - Fooling the routers & host! Traceroute uses ping (echo requests) Traceroute sets the TTL (Time To Live) field in the IP Header, initially to 1 117
118 Trace RTB - TTL: When a router receives an IP Packet, it decrements the TTL by 1. If the TTL is 0, it will not forward the IP Packet, and send back to the source an ICMP time exceeded message. ICMP Message: Type = 11, Code = 0 118
119 RTB After the traceroute is received by the first router, it decrements the TTL by 1 to 0. Noticing the TTL is 0, it sends back a ICMP Time Exceeded message back to the source, using its IP address for the source IP address. Router B s IP header includes its own IP address (source IP) and the sending host s IP address (dest. IP). 119
120 RTA, Sending Host The traceroute program of the sending host (RTA) will use the source IP address of this ICMP Time Exceeded packet to display at the first hop. RTA# traceroute Type escape sequence to abort. Tracing the route to msec 4 msec 4 msec 120
121 RTA The traceroute program increments the TTL by 1 (now 2 ) and resends the ICMP Echo Request packet. 121
122 RTB This time RTB decrements the TTL by 1 and it is NOT 0. (It is 1.) So it looks up the destination ip address in its routing table and forwards it on to the next router. RTC RTC however decrements the TTL by 1 and it is 0. RTC notices the TTL is 0 and sends back the ICMP Time Exceeded message back to the source. RTC s IP header includes its own IP address (source IP) and the sending host s IP address (destination IP address of RTA). The sending host, RTA, will use the source IP address of this ICMP Time Exceeded message to display at the second hop. 122
123 RTA to RTB RTB to RTC. 123
124 The sending host, RTA: The traceroute program uses this information (Source IP Address) and displays the second hop. RTA# traceroute Type escape sequence to abort. Tracing the route to msec 4 msec 4 msec msec 16 msec 16 msec 124
125 The sending host, RTA: The traceroute program increments the TTL by 1 (now 3 ) and resends the Packet. 125
126 RTA to RTB RTB to RTC. RTC to RTD 126
127 RTB This time RTB decrements the TTL by 1 and it is NOT 0. (It is 2.) So it looks up the destination ip address in its routing table and forwards it on to the next router. RTC This time RTC decrements the TTL by 1 and it is NOT 0. (It is 1.) So it looks up the destination ip address in its routing table and forwards it on to the next router. RTD RTD however decrements the TTL by 1 and it is 0. However, RTD notices that the Destination IP Address of is it s own interface. Since it does not need to forward the packet, the TTL of 0 has no affect. 127
128 RTD RTD sends the packet to the UDP process. UDP examines the unrecognizable port number of 35,000 and sends back an ICMP Port Unreachable message to the sender, RTA, using Type 3 and Code
129 Sending host, RTA RTA receives the ICMP Port Unreachable message. The traceroute program uses this information (Source IP Address) and displays the third hop. The traceroute program also recognizes this Port Unreachable message as meaning this is the destination it was tracing. 129
130 Sending host, RTA RTA, the sending host, now displays the third hop. Getting the ICMP Port Unreachable message, it knows this is the final hop and does not send any more traces (echo requests). RTA# traceroute Type escape sequence to abort. Tracing the route to msec 4 msec 4 msec msec 16 msec 16 msec msec 16 msec 16 msec 130
Ref: A. Leon Garcia and I. Widjaja, Communication Networks, 2 nd Ed. McGraw Hill, 2006 Latest update of this lecture was on 16 10 2010
 IPv4 Addressing There are several non-profit organizations in the world that have the authority for assigning IP addresses to institutions that need access to the Internet. These organizations are (for
IPv4 Addressing There are several non-profit organizations in the world that have the authority for assigning IP addresses to institutions that need access to the Internet. These organizations are (for
IP Addressing A Simplified Tutorial
 Application Note IP Addressing A Simplified Tutorial July 2002 COMPAS ID 92962 Avaya Labs 1 All information in this document is subject to change without notice. Although the information is believed to
Application Note IP Addressing A Simplified Tutorial July 2002 COMPAS ID 92962 Avaya Labs 1 All information in this document is subject to change without notice. Although the information is believed to
Guide to Network Defense and Countermeasures Third Edition. Chapter 2 TCP/IP
 Guide to Network Defense and Countermeasures Third Edition Chapter 2 TCP/IP Objectives Explain the fundamentals of TCP/IP networking Describe IPv4 packet structure and explain packet fragmentation Describe
Guide to Network Defense and Countermeasures Third Edition Chapter 2 TCP/IP Objectives Explain the fundamentals of TCP/IP networking Describe IPv4 packet structure and explain packet fragmentation Describe
- IPv4 Addressing and Subnetting -
 1 Hardware Addressing - IPv4 Addressing and Subnetting - A hardware address is used to uniquely identify a host within a local network. Hardware addressing is a function of the Data-Link layer of the OSI
1 Hardware Addressing - IPv4 Addressing and Subnetting - A hardware address is used to uniquely identify a host within a local network. Hardware addressing is a function of the Data-Link layer of the OSI
You can probably work with decimal. binary numbers needed by the. Working with binary numbers is time- consuming & error-prone.
 IP Addressing & Subnetting Made Easy Working with IP Addresses Introduction You can probably work with decimal numbers much easier than with the binary numbers needed by the computer. Working with binary
IP Addressing & Subnetting Made Easy Working with IP Addresses Introduction You can probably work with decimal numbers much easier than with the binary numbers needed by the computer. Working with binary
8.2 The Internet Protocol
 TCP/IP Protocol Suite HTTP SMTP DNS RTP Distributed applications Reliable stream service TCP UDP User datagram service Best-effort connectionless packet transfer Network Interface 1 IP Network Interface
TCP/IP Protocol Suite HTTP SMTP DNS RTP Distributed applications Reliable stream service TCP UDP User datagram service Best-effort connectionless packet transfer Network Interface 1 IP Network Interface
TCP/IP Basis. OSI Model
 TCP/IP Basis 高 雄 大 學 資 訊 工 程 學 系 嚴 力 行 Source OSI Model Destination Application Presentation Session Transport Network Data-Link Physical ENCAPSULATION DATA SEGMENT PACKET FRAME BITS 0101010101010101010
TCP/IP Basis 高 雄 大 學 資 訊 工 程 學 系 嚴 力 行 Source OSI Model Destination Application Presentation Session Transport Network Data-Link Physical ENCAPSULATION DATA SEGMENT PACKET FRAME BITS 0101010101010101010
Internet Addresses (You should read Chapter 4 in Forouzan)
 Internet Addresses (You should read Chapter 4 in Forouzan) IP Address is 32 Bits Long Conceptually the address is the pair (NETID, HOSTID) Addresses are assigned by the internet company for assignment
Internet Addresses (You should read Chapter 4 in Forouzan) IP Address is 32 Bits Long Conceptually the address is the pair (NETID, HOSTID) Addresses are assigned by the internet company for assignment
256 4 = 4,294,967,296 ten billion. 256 16 = 18,446,744,073,709,551,616 ten quintillion. IP Addressing. IPv4 Address Classes
 IP Addressing With the exception of multicast addresses, Internet addresses consist of a network portion and a host portion. The network portion identifies a logical network to which the address refers,
IP Addressing With the exception of multicast addresses, Internet addresses consist of a network portion and a host portion. The network portion identifies a logical network to which the address refers,
Lecture Computer Networks
 Prof. Dr. H. P. Großmann mit M. Rabel sowie H. Hutschenreiter und T. Nau Sommersemester 2012 Institut für Organisation und Management von Informationssystemen Thomas Nau, kiz Lecture Computer Networks
Prof. Dr. H. P. Großmann mit M. Rabel sowie H. Hutschenreiter und T. Nau Sommersemester 2012 Institut für Organisation und Management von Informationssystemen Thomas Nau, kiz Lecture Computer Networks
Procedure: You can find the problem sheet on Drive D: of the lab PCs. 1. IP address for this host computer 2. Subnet mask 3. Default gateway address
 Objectives University of Jordan Faculty of Engineering & Technology Computer Engineering Department Computer Networks Laboratory 907528 Lab.4 Basic Network Operation and Troubleshooting 1. To become familiar
Objectives University of Jordan Faculty of Engineering & Technology Computer Engineering Department Computer Networks Laboratory 907528 Lab.4 Basic Network Operation and Troubleshooting 1. To become familiar
Internet Protocol version 4 Part I
 Internet Protocol version 4 Part I Claudio Cicconetti International Master on Information Technology International Master on Communication Networks Engineering Table of Contents
Internet Protocol version 4 Part I Claudio Cicconetti International Master on Information Technology International Master on Communication Networks Engineering Table of Contents
Technical Support Information Belkin internal use only
 The fundamentals of TCP/IP networking TCP/IP (Transmission Control Protocol / Internet Protocols) is a set of networking protocols that is used for communication on the Internet and on many other networks.
The fundamentals of TCP/IP networking TCP/IP (Transmission Control Protocol / Internet Protocols) is a set of networking protocols that is used for communication on the Internet and on many other networks.
Computer Networks. Lecture 3: IP Protocol. Marcin Bieńkowski. Institute of Computer Science University of Wrocław
 Computer Networks Lecture 3: IP Protocol Marcin Bieńkowski Institute of Computer Science University of Wrocław Computer networks (II UWr) Lecture 3 1 / 24 In previous lectures We learned about layer 1
Computer Networks Lecture 3: IP Protocol Marcin Bieńkowski Institute of Computer Science University of Wrocław Computer networks (II UWr) Lecture 3 1 / 24 In previous lectures We learned about layer 1
Network layer: Overview. Network layer functions IP Routing and forwarding
 Network layer: Overview Network layer functions IP Routing and forwarding 1 Network layer functions Transport packet from sending to receiving hosts Network layer protocols in every host, router application
Network layer: Overview Network layer functions IP Routing and forwarding 1 Network layer functions Transport packet from sending to receiving hosts Network layer protocols in every host, router application
Internet Protocol Address
 SFWR 4C03: Computer Networks & Computer Security Jan 17-21, 2005 Lecturer: Kartik Krishnan Lecture 7-9 Internet Protocol Address Addressing is a critical component of the internet abstraction. To give
SFWR 4C03: Computer Networks & Computer Security Jan 17-21, 2005 Lecturer: Kartik Krishnan Lecture 7-9 Internet Protocol Address Addressing is a critical component of the internet abstraction. To give
Network and Host Addresses 1.3. 2003, Cisco Systems, Inc. All rights reserved. INTRO v1.0a 6-4
 IP Addressing To facilitate the routing of packets over a network, the TCP/IP protocol suite uses a 32-bit logical address known as an IP address. This topic introduces the components of an IP address.
IP Addressing To facilitate the routing of packets over a network, the TCP/IP protocol suite uses a 32-bit logical address known as an IP address. This topic introduces the components of an IP address.
CE363 Data Communications & Networking. Chapter 6 Network Layer: Logical Addressing
 CE363 Data Communications & Networking Chapter 6 Network Layer: Logical Addressing TCP/IP and OSI model APPLICATION APPLICATION PRESENTATION SESSION TRANSPORT NETWORK Host-Network TRANSPORT NETWORK DATA
CE363 Data Communications & Networking Chapter 6 Network Layer: Logical Addressing TCP/IP and OSI model APPLICATION APPLICATION PRESENTATION SESSION TRANSPORT NETWORK Host-Network TRANSPORT NETWORK DATA
Computer Networks. Introduc)on to Naming, Addressing, and Rou)ng. Week 09. College of Information Science and Engineering Ritsumeikan University
 Computer Networks Introduc)on to Naming, Addressing, and Rou)ng Week 09 College of Information Science and Engineering Ritsumeikan University MAC Addresses l MAC address is intended to be a unique identifier
Computer Networks Introduc)on to Naming, Addressing, and Rou)ng Week 09 College of Information Science and Engineering Ritsumeikan University MAC Addresses l MAC address is intended to be a unique identifier
IPv6 Addressing. John Rullan Cisco Certified Instructor Trainer Thomas A. Edison CTE HS
 IPv6 Addressing John Rullan Cisco Certified Instructor Trainer Thomas A. Edison CTE HS Stephen Lynch Network Architect, CCIE #36243 ABS Technology Architects 128-bit hexadecimal format (0-9, A-F) Uses
IPv6 Addressing John Rullan Cisco Certified Instructor Trainer Thomas A. Edison CTE HS Stephen Lynch Network Architect, CCIE #36243 ABS Technology Architects 128-bit hexadecimal format (0-9, A-F) Uses
Savera Tanwir. Internet Protocol
 Savera Tanwir Internet Protocol The IP Protocol The IPv4 (Internet Protocol) header. IP Packet Details Header and payload Header itself has a fixed part and variable part Version IPv4, IPv5 or IPv6 IHL,
Savera Tanwir Internet Protocol The IP Protocol The IPv4 (Internet Protocol) header. IP Packet Details Header and payload Header itself has a fixed part and variable part Version IPv4, IPv5 or IPv6 IHL,
ICS 351: Today's plan
 ICS 351: Today's plan Quiz, on overall Internet function, linux and IOS commands, network monitoring, protocols IPv4 addresses: network part and host part address masks IP interface configuration IPv6
ICS 351: Today's plan Quiz, on overall Internet function, linux and IOS commands, network monitoring, protocols IPv4 addresses: network part and host part address masks IP interface configuration IPv6
CCNA Tutorial Series SUBNETTING
 CCNA Tutorial Series This document contains the Course Map For The Interactive flash tutorial at: http://www.semsim.com/ccna/tutorial/subnetting/subnetting.html HOME PAGE Course Objectives Pre-test By
CCNA Tutorial Series This document contains the Course Map For The Interactive flash tutorial at: http://www.semsim.com/ccna/tutorial/subnetting/subnetting.html HOME PAGE Course Objectives Pre-test By
IP Addressing and Subnetting. 2002, Cisco Systems, Inc. All rights reserved.
 IP Addressing and Subnetting 2002, Cisco Systems, Inc. All rights reserved. 1 Objectives Upon completion, you will be able to: Discuss the Types of Network Addressing Explain the Form of an IP Address
IP Addressing and Subnetting 2002, Cisco Systems, Inc. All rights reserved. 1 Objectives Upon completion, you will be able to: Discuss the Types of Network Addressing Explain the Form of an IP Address
Chapter 5. IPv4 Addresses. TCP/IP Protocol Suite 1 Copyright The McGraw-Hill Companies, Inc. Permission required for reproduction or display.
 Chapter 5 IPv4 Addresses TCP/IP Protocol Suite 1 Copyright The McGraw-Hill Companies, Inc. Permission required for reproduction or display. Chapter Outline TCP/IP Protocol Suite 2 5-1 INTRODUCTION The
Chapter 5 IPv4 Addresses TCP/IP Protocol Suite 1 Copyright The McGraw-Hill Companies, Inc. Permission required for reproduction or display. Chapter Outline TCP/IP Protocol Suite 2 5-1 INTRODUCTION The
Internet Protocols. Addressing & Services. Updated: 9-29-2012
 Internet Protocols Addressing & Services Updated: 9-29-2012 Virtual vs. Physical Networks MAC is the part of the underlying network MAC is used on the LAN What is the addressing mechanism in WAN? WAN is
Internet Protocols Addressing & Services Updated: 9-29-2012 Virtual vs. Physical Networks MAC is the part of the underlying network MAC is used on the LAN What is the addressing mechanism in WAN? WAN is
Guide to TCP/IP, Third Edition. Chapter 2: IP Addressing and Related Topics
 Guide to TCP/IP, Third Edition Chapter 2: IP Addressing and Related Topics Objectives Understand IP addressing, anatomy and structures, and addresses from a computer s point of view Recognize and describe
Guide to TCP/IP, Third Edition Chapter 2: IP Addressing and Related Topics Objectives Understand IP addressing, anatomy and structures, and addresses from a computer s point of view Recognize and describe
IP Addressing Introductory material.
 IP Addressing Introductory material. A module devoted to IP addresses. Addresses & Names Hardware (Layer 2) Lowest level Ethernet (MAC), Serial point-to-point,.. Network (Layer 3) IP IPX, SNA, others Transport
IP Addressing Introductory material. A module devoted to IP addresses. Addresses & Names Hardware (Layer 2) Lowest level Ethernet (MAC), Serial point-to-point,.. Network (Layer 3) IP IPX, SNA, others Transport
04 Internet Protocol (IP)
 SE 4C03 Winter 2007 04 Internet Protocol (IP) William M. Farmer Department of Computing and Software McMaster University 29 January 2007 Internet Protocol (IP) IP provides a connectionless packet delivery
SE 4C03 Winter 2007 04 Internet Protocol (IP) William M. Farmer Department of Computing and Software McMaster University 29 January 2007 Internet Protocol (IP) IP provides a connectionless packet delivery
Future Internet Technologies
 Future Internet Technologies Traditional Internet Dr. Dennis Pfisterer Institut für Telematik, Universität zu Lübeck http://www.itm.uni-luebeck.de/people/pfisterer Internet Protocol v4 (IPv4) IPv4 Model
Future Internet Technologies Traditional Internet Dr. Dennis Pfisterer Institut für Telematik, Universität zu Lübeck http://www.itm.uni-luebeck.de/people/pfisterer Internet Protocol v4 (IPv4) IPv4 Model
IPv6 Fundamentals Ch t ap 1 er I : ntroducti ti t on I o P IPv6 Copyright Cisco Academy Yannis Xydas
 IPv6 Fundamentals Chapter 1: Introduction ti to IPv6 Copyright Cisco Academy Yannis Xydas The Network Today The Internet of today is much different that it was 30, 15 or 5 years ago. 2 Technology Tomorrow
IPv6 Fundamentals Chapter 1: Introduction ti to IPv6 Copyright Cisco Academy Yannis Xydas The Network Today The Internet of today is much different that it was 30, 15 or 5 years ago. 2 Technology Tomorrow
Chapter 19 Network Layer: Logical Addressing 19.1
 Chapter 19 Network Layer: Logical Addressing 19.1 Copyright The McGraw-Hill Companies, Inc. Permission required for reproduction or display. 19-1 IPv4 ADDRESSES An IPv4 address is a 32-bit address that
Chapter 19 Network Layer: Logical Addressing 19.1 Copyright The McGraw-Hill Companies, Inc. Permission required for reproduction or display. 19-1 IPv4 ADDRESSES An IPv4 address is a 32-bit address that
Chapter 3. TCP/IP Networks. 3.1 Internet Protocol version 4 (IPv4)
 Chapter 3 TCP/IP Networks 3.1 Internet Protocol version 4 (IPv4) Internet Protocol version 4 is the fourth iteration of the Internet Protocol (IP) and it is the first version of the protocol to be widely
Chapter 3 TCP/IP Networks 3.1 Internet Protocol version 4 (IPv4) Internet Protocol version 4 is the fourth iteration of the Internet Protocol (IP) and it is the first version of the protocol to be widely
Lecture 15. IP address space managed by Internet Assigned Numbers Authority (IANA)
 Lecture 15 IP Address Each host and router on the Internet has an IP address, which consist of a combination of network number and host number. The combination is unique; no two machines have the same
Lecture 15 IP Address Each host and router on the Internet has an IP address, which consist of a combination of network number and host number. The combination is unique; no two machines have the same
http://computernetworkingnotes.com/ccna-study-guide/basic-of-network-addressing.html
 Subnetting is a process of dividing large network into the smaller networks based on layer 3 IP address. Every computer on network has an IP address that represent its location on network. Two version
Subnetting is a process of dividing large network into the smaller networks based on layer 3 IP address. Every computer on network has an IP address that represent its location on network. Two version
2. IP Networks, IP Hosts and IP Ports
 1. Introduction to IP... 1 2. IP Networks, IP Hosts and IP Ports... 1 3. IP Packet Structure... 2 4. IP Address Structure... 2 Network Portion... 2 Host Portion... 3 Global vs. Private IP Addresses...3
1. Introduction to IP... 1 2. IP Networks, IP Hosts and IP Ports... 1 3. IP Packet Structure... 2 4. IP Address Structure... 2 Network Portion... 2 Host Portion... 3 Global vs. Private IP Addresses...3
Networking Test 4 Study Guide
 Networking Test 4 Study Guide True/False Indicate whether the statement is true or false. 1. IPX/SPX is considered the protocol suite of the Internet, and it is the most widely used protocol suite in LANs.
Networking Test 4 Study Guide True/False Indicate whether the statement is true or false. 1. IPX/SPX is considered the protocol suite of the Internet, and it is the most widely used protocol suite in LANs.
IP Subnetting and Addressing
 Indian Institute of Technology Kharagpur IP Subnetting and Addressing Prof Indranil Sengupta Computer Science and Engineering Indian Institute of Technology Kharagpur Lecture 6: IP Subnetting and Addressing
Indian Institute of Technology Kharagpur IP Subnetting and Addressing Prof Indranil Sengupta Computer Science and Engineering Indian Institute of Technology Kharagpur Lecture 6: IP Subnetting and Addressing
IP Addressing. IP Addresses. Introductory material.
 IP Addressing Introductory material. An entire module devoted to IP addresses. IP Addresses Structure of an IP address Classful IP addresses Limitations and problems with classful IP addresses Subnetting
IP Addressing Introductory material. An entire module devoted to IP addresses. IP Addresses Structure of an IP address Classful IP addresses Limitations and problems with classful IP addresses Subnetting
PART IV. Network Layer
 PART IV Network Layer Position of network layer Network layer duties Internetworking : heterogeneous Physical Networks To look Like a single network to he upper layers The address at Network layer must
PART IV Network Layer Position of network layer Network layer duties Internetworking : heterogeneous Physical Networks To look Like a single network to he upper layers The address at Network layer must
Computer Network Foundation. Chun-Jen (James) Chung. Arizona State University
 Computer Network Foundation Chun-Jen (James) Chung 1 Outline Network Addressing Subnetting Classless Inter-Domain Routing (CIDR) Route Aggregation Network Addressing How does the network decide where to
Computer Network Foundation Chun-Jen (James) Chung 1 Outline Network Addressing Subnetting Classless Inter-Domain Routing (CIDR) Route Aggregation Network Addressing How does the network decide where to
RARP: Reverse Address Resolution Protocol
 SFWR 4C03: Computer Networks and Computer Security January 19-22 2004 Lecturer: Kartik Krishnan Lectures 7-9 RARP: Reverse Address Resolution Protocol When a system with a local disk is bootstrapped it
SFWR 4C03: Computer Networks and Computer Security January 19-22 2004 Lecturer: Kartik Krishnan Lectures 7-9 RARP: Reverse Address Resolution Protocol When a system with a local disk is bootstrapped it
IP Address Classes (Some are Obsolete) 15-441 Computer Networking. Important Concepts. Subnetting 15-441 15-641. Lecture 8 IP Addressing & Packets
 Address Classes (Some are Obsolete) 15-441 15-441 Computer Networking 15-641 Class A 0 Network ID Network ID 8 16 Host ID Host ID 24 32 Lecture 8 Addressing & Packets Peter Steenkiste Fall 2013 www.cs.cmu.edu/~prs/15-441-f13
Address Classes (Some are Obsolete) 15-441 15-441 Computer Networking 15-641 Class A 0 Network ID Network ID 8 16 Host ID Host ID 24 32 Lecture 8 Addressing & Packets Peter Steenkiste Fall 2013 www.cs.cmu.edu/~prs/15-441-f13
Scaling the Network: Subnetting and Other Protocols. Networking CS 3470, Section 1
 Scaling the Network: Subnetting and Other Protocols Networking CS 3470, Section 1 Today CIDR Subnetting Private IP addresses ICMP, IMAP, and DHCP Protocols 2 Packet Encapsulation ** Creative Commons: http://en.wikipedia.org/wiki/file:udp_encapsulation.svg
Scaling the Network: Subnetting and Other Protocols Networking CS 3470, Section 1 Today CIDR Subnetting Private IP addresses ICMP, IMAP, and DHCP Protocols 2 Packet Encapsulation ** Creative Commons: http://en.wikipedia.org/wiki/file:udp_encapsulation.svg
What's inside the cloud?!
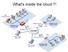 What's inside the cloud?! Initial Arpanet Initial Arpanet Interface Message Processors - DDP-516 mini-computers - 24 Kbyte of Core memory - Store-and-forward packet switching - Predecessors of present
What's inside the cloud?! Initial Arpanet Initial Arpanet Interface Message Processors - DDP-516 mini-computers - 24 Kbyte of Core memory - Store-and-forward packet switching - Predecessors of present
IP Networking Part 3- IP Address Management A webinar to help you prepare for the CBNE Certification
 IP Networking Part 3- IP Address Management A webinar to help you prepare for the CBNE Certification Wayne M. Pecena, CPBE, CBNE Texas A&M Information Technology Educational Broadcast Services IP Networking,
IP Networking Part 3- IP Address Management A webinar to help you prepare for the CBNE Certification Wayne M. Pecena, CPBE, CBNE Texas A&M Information Technology Educational Broadcast Services IP Networking,
Introduction to IP v6
 IP v 1-3: defined and replaced Introduction to IP v6 IP v4 - current version; 20 years old IP v5 - streams protocol IP v6 - replacement for IP v4 During developments it was called IPng - Next Generation
IP v 1-3: defined and replaced Introduction to IP v6 IP v4 - current version; 20 years old IP v5 - streams protocol IP v6 - replacement for IP v4 During developments it was called IPng - Next Generation
Subnetting and Network Management Omer F. Rana. Networks and Data Communications 1
 Subnetting and Network Management Omer F. Rana Networks and Data Communications 1 Subnetting Subnetting is an important concept in establishing TCP/IP based networks important in integrating small Local
Subnetting and Network Management Omer F. Rana Networks and Data Communications 1 Subnetting Subnetting is an important concept in establishing TCP/IP based networks important in integrating small Local
Course Overview: Learn the essential skills needed to set up, configure, support, and troubleshoot your TCP/IP-based network.
 Course Name: TCP/IP Networking Course Overview: Learn the essential skills needed to set up, configure, support, and troubleshoot your TCP/IP-based network. TCP/IP is the globally accepted group of protocols
Course Name: TCP/IP Networking Course Overview: Learn the essential skills needed to set up, configure, support, and troubleshoot your TCP/IP-based network. TCP/IP is the globally accepted group of protocols
APPENDIX B. Routers route based on the network number. The router that delivers the data packet to the correct destination host uses the host ID.
 APPENDIX B IP Subnetting IP Addressing Routers route based on the network number. The router that delivers the data packet to the correct destination host uses the host ID. IP Classes An IP address is
APPENDIX B IP Subnetting IP Addressing Routers route based on the network number. The router that delivers the data packet to the correct destination host uses the host ID. IP Classes An IP address is
Objectives. Upon completing this chapter, you will be able to
 1358_fmi.book Page 30 Thursday, May 27, 2004 2:21 PM Objectives Upon completing this chapter, you will be able to Create and configure IPv4 addresses Understand and resolve IP addressing crises Assign a
1358_fmi.book Page 30 Thursday, May 27, 2004 2:21 PM Objectives Upon completing this chapter, you will be able to Create and configure IPv4 addresses Understand and resolve IP addressing crises Assign a
IP addressing and forwarding Network layer
 The Internet Network layer Host, router network layer functions: IP addressing and forwarding Network layer Routing protocols path selection RIP, OSPF, BGP Transport layer: TCP, UDP forwarding table IP
The Internet Network layer Host, router network layer functions: IP addressing and forwarding Network layer Routing protocols path selection RIP, OSPF, BGP Transport layer: TCP, UDP forwarding table IP
Lab 10.3.5a Basic Subnetting
 Lab 10.3.5a Basic Subnetting Objective How to identify reasons to use a subnet mask How to distinguish between a default subnet mask and a custom subnet mask What given requirements determine the subnet
Lab 10.3.5a Basic Subnetting Objective How to identify reasons to use a subnet mask How to distinguish between a default subnet mask and a custom subnet mask What given requirements determine the subnet
Advanced IP Addressing
 Advanced IP Addressing CS-765 A Aspects Of Systems Administration Spring-2005 Instructure: Jan Schauman Stevens Institute Of Technology, NJ. Prepared By: Modh, Jay A. M.S. NIS SID: 999-14-0352 Date: 05/02/2005
Advanced IP Addressing CS-765 A Aspects Of Systems Administration Spring-2005 Instructure: Jan Schauman Stevens Institute Of Technology, NJ. Prepared By: Modh, Jay A. M.S. NIS SID: 999-14-0352 Date: 05/02/2005
2. What is the maximum value of each octet in an IP address? A. 28 B. 255 C. 256 D. None of the above
 CCNA1 V3.0 Mod 10 (Ch 8) 1. How many bits are in an IP C. 64 2. What is the maximum value of each octet in an IP A. 28 55 C. 256 3. The network number plays what part in an IP A. It specifies the network
CCNA1 V3.0 Mod 10 (Ch 8) 1. How many bits are in an IP C. 64 2. What is the maximum value of each octet in an IP A. 28 55 C. 256 3. The network number plays what part in an IP A. It specifies the network
Chapter 3: IP Addressing and VLSM
 Chapter 3: IP Addressing and VLSM QUESTION 54 What is the principle reason to use a private IP address on an internal network? A. Subnet strategy for private companies. B. Manage and scale the growth of
Chapter 3: IP Addressing and VLSM QUESTION 54 What is the principle reason to use a private IP address on an internal network? A. Subnet strategy for private companies. B. Manage and scale the growth of
WHITE PAPER. Understanding IP Addressing: Everything You Ever Wanted To Know
 WHITE PAPER Understanding IP Addressing: Everything You Ever Wanted To Know Understanding IP Addressing: Everything You Ever Wanted To Know CONTENTS Internet Scaling Problems 1 Classful IP Addressing 3
WHITE PAPER Understanding IP Addressing: Everything You Ever Wanted To Know Understanding IP Addressing: Everything You Ever Wanted To Know CONTENTS Internet Scaling Problems 1 Classful IP Addressing 3
Subnetting,Supernetting, VLSM & CIDR
 Subnetting,Supernetting, VLSM & CIDR WHAT - IP Address Unique 32 or 128 bit Binary, used to identify a system on a Network or Internet. Network Portion Host Portion CLASSFULL ADDRESSING IP address space
Subnetting,Supernetting, VLSM & CIDR WHAT - IP Address Unique 32 or 128 bit Binary, used to identify a system on a Network or Internet. Network Portion Host Portion CLASSFULL ADDRESSING IP address space
Source net: 200.1.1.0 Destination net: 200.1.2.0 Subnet mask: 255.255.255.0 Subnet mask: 255.255.255.0. Router Hub
 then to a router. Remember that with a Class C network address, the first 3 octets, or 24 bits, are assigned as the network address. So, these are two different Class C networks. This leaves one octet,
then to a router. Remember that with a Class C network address, the first 3 octets, or 24 bits, are assigned as the network address. So, these are two different Class C networks. This leaves one octet,
Gary Hecht Computer Networking (IP Addressing, Subnet Masks, and Packets)
 Gary Hecht Computer Networking (IP Addressing, Subnet Masks, and Packets) The diagram below illustrates four routers on the Internet backbone along with two companies that have gateways for their internal
Gary Hecht Computer Networking (IP Addressing, Subnet Masks, and Packets) The diagram below illustrates four routers on the Internet backbone along with two companies that have gateways for their internal
IP - The Internet Protocol
 Orientation IP - The Internet Protocol IP (Internet Protocol) is a Network Layer Protocol. IP s current version is Version 4 (IPv4). It is specified in RFC 891. TCP UDP Transport Layer ICMP IP IGMP Network
Orientation IP - The Internet Protocol IP (Internet Protocol) is a Network Layer Protocol. IP s current version is Version 4 (IPv4). It is specified in RFC 891. TCP UDP Transport Layer ICMP IP IGMP Network
Troubleshooting IP Routing
 C H A P T E R 7 Troubleshooting IP Routing This troubleshooting chapter has several goals. First, it explains several tools and functions not covered in Chapters 4 through 6 specifically, tools that can
C H A P T E R 7 Troubleshooting IP Routing This troubleshooting chapter has several goals. First, it explains several tools and functions not covered in Chapters 4 through 6 specifically, tools that can
(Refer Slide Time: 02:17)
 Internet Technology Prof. Indranil Sengupta Department of Computer Science and Engineering Indian Institute of Technology, Kharagpur Lecture No #06 IP Subnetting and Addressing (Not audible: (00:46)) Now,
Internet Technology Prof. Indranil Sengupta Department of Computer Science and Engineering Indian Institute of Technology, Kharagpur Lecture No #06 IP Subnetting and Addressing (Not audible: (00:46)) Now,
Lab#2: IP Addressing and Subnetting
 IP Addressing Lab#2: IP Addressing and Subnetting Each Network Interface Card (NIC or Network card) present in a PC is assigned one Network address called as IP address. This IP address is assigned by
IP Addressing Lab#2: IP Addressing and Subnetting Each Network Interface Card (NIC or Network card) present in a PC is assigned one Network address called as IP address. This IP address is assigned by
Sample Configuration Using the ip nat outside source static
 Sample Configuration Using the ip nat outside source static Table of Contents Sample Configuration Using the ip nat outside source static Command...1 Introduction...1 Before You Begin...1 Conventions...1
Sample Configuration Using the ip nat outside source static Table of Contents Sample Configuration Using the ip nat outside source static Command...1 Introduction...1 Before You Begin...1 Conventions...1
IP Addressing. -Internetworking (with TCP/IP) -Classful addressing -Subnetting and Supernetting -Classless addressing
 IP Addressing -Internetworking (with TCP/IP) -Classful addressing -Subnetting and Supernetting -Classless addressing Internetworking The concept of internetworking: we need to make different networks communicate
IP Addressing -Internetworking (with TCP/IP) -Classful addressing -Subnetting and Supernetting -Classless addressing Internetworking The concept of internetworking: we need to make different networks communicate
This tutorial will help you in understanding IPv4 and its associated terminologies along with appropriate references and examples.
 About the Tutorial Internet Protocol version 4 (IPv4) is the fourth version in the development of the Internet Protocol (IP) and the first version of the protocol to be widely deployed. IPv4 is described
About the Tutorial Internet Protocol version 4 (IPv4) is the fourth version in the development of the Internet Protocol (IP) and the first version of the protocol to be widely deployed. IPv4 is described
Module 2: Assigning IP Addresses in a Multiple Subnet Network
 Module 2: Assigning IP Addresses in a Multiple Subnet Network Contents Overview 1 Lesson: Assigning IP Addresses 2 Lesson: Creating a Subnet 19 Lesson: Using IP Routing Tables 29 Lesson: Overcoming Limitations
Module 2: Assigning IP Addresses in a Multiple Subnet Network Contents Overview 1 Lesson: Assigning IP Addresses 2 Lesson: Creating a Subnet 19 Lesson: Using IP Routing Tables 29 Lesson: Overcoming Limitations
1 Data information is sent onto the network cable using which of the following? A Communication protocol B Data packet
 Review questions 1 Data information is sent onto the network cable using which of the following? A Communication protocol B Data packet C Media access method D Packages 2 To which TCP/IP architecture layer
Review questions 1 Data information is sent onto the network cable using which of the following? A Communication protocol B Data packet C Media access method D Packages 2 To which TCP/IP architecture layer
Overview. 15-441 Computer Networking. IP Address Classes (Some are Obsolete) Outline. Lecture 9 IP Packets. CIDR IP addressing. Forwarding examples
 Overview 15-441 Computer Networking Lecture 9 Packets Last lecture How does choice of address impact network architecture and scalability? What do addresses look like? This lecture Modern addresses How
Overview 15-441 Computer Networking Lecture 9 Packets Last lecture How does choice of address impact network architecture and scalability? What do addresses look like? This lecture Modern addresses How
Part A:Background/Preparation
 Lab no 1 PC Network TCP/IP Configuration In this lab we will learn about Computer Networks Configuration Introduction to IP addressing Identify tools used for discovering a computer s network configuration
Lab no 1 PC Network TCP/IP Configuration In this lab we will learn about Computer Networks Configuration Introduction to IP addressing Identify tools used for discovering a computer s network configuration
Classless Subnetting Explained
 Classless Subnetting Explained When given an IP Address, Major Network Mask, and a Subnet Mask, how can you determine other information such as: The subnet address of this subnet The broadcast address
Classless Subnetting Explained When given an IP Address, Major Network Mask, and a Subnet Mask, how can you determine other information such as: The subnet address of this subnet The broadcast address
Internet Control Protocols Reading: Chapter 3
 Internet Control Protocols Reading: Chapter 3 ARP - RFC 826, STD 37 DHCP - RFC 2131 ICMP - RFC 0792, STD 05 1 Goals of Today s Lecture Bootstrapping an end host Learning its own configuration parameters
Internet Control Protocols Reading: Chapter 3 ARP - RFC 826, STD 37 DHCP - RFC 2131 ICMP - RFC 0792, STD 05 1 Goals of Today s Lecture Bootstrapping an end host Learning its own configuration parameters
Activity 6.7.4: IPv4 Address Subnetting Part 2
 Activity 6.7.4: IPv4 Address Subnetting Part 2 Learning Objectives Upon completion of this activity, you will be able to determine subnet information for a given IP address and subnetwork mask. Background
Activity 6.7.4: IPv4 Address Subnetting Part 2 Learning Objectives Upon completion of this activity, you will be able to determine subnet information for a given IP address and subnetwork mask. Background
Ethernet and IP A slightly less introductory networking class. Drew Saunders Networking Systems Stanford University
 Ethernet and IP A slightly less introductory networking class Drew Saunders Networking Systems Stanford University Goals of Class Slightly more in-depth knowledge of Ethernet. Internet Protocol, TCP, UDP,
Ethernet and IP A slightly less introductory networking class Drew Saunders Networking Systems Stanford University Goals of Class Slightly more in-depth knowledge of Ethernet. Internet Protocol, TCP, UDP,
Instructor Notes for Lab 3
 Instructor Notes for Lab 3 Do not distribute instructor notes to students! Lab Preparation: Make sure that enough Ethernet hubs and cables are available in the lab. The following tools will be used in
Instructor Notes for Lab 3 Do not distribute instructor notes to students! Lab Preparation: Make sure that enough Ethernet hubs and cables are available in the lab. The following tools will be used in
TCP/IP Networking Terms you ll need to understand: Techniques you ll need to master:
 5 TCP/IP Networking Terms you ll need to understand: Subnet mask Subnetting Classless Interdomain Routing (CIDR) Transmission Control Protocol/Internet Protocol (TCP/IP) Address Resolution Protocol (ARP)
5 TCP/IP Networking Terms you ll need to understand: Subnet mask Subnetting Classless Interdomain Routing (CIDR) Transmission Control Protocol/Internet Protocol (TCP/IP) Address Resolution Protocol (ARP)
IPv6 Address Planning
 eip604_v1.0 APNIC elearning: IPv6 Address Planning Contact: training@apnic.net Overview Where to Get IPv6 Addresses Addressing Plans ISP Infrastructure Addressing Plans Customer Example Address Plan Addressing
eip604_v1.0 APNIC elearning: IPv6 Address Planning Contact: training@apnic.net Overview Where to Get IPv6 Addresses Addressing Plans ISP Infrastructure Addressing Plans Customer Example Address Plan Addressing
BGP Terminology, Concepts, and Operation. Chapter 6 2007 2010, Cisco Systems, Inc. All rights reserved. Cisco Public
 BGP Terminology, Concepts, and Operation 1 IGP versus EGP Interior gateway protocol (IGP) A routing protocol operating within an Autonomous System (AS). RIP, OSPF, and EIGRP are IGPs. Exterior gateway
BGP Terminology, Concepts, and Operation 1 IGP versus EGP Interior gateway protocol (IGP) A routing protocol operating within an Autonomous System (AS). RIP, OSPF, and EIGRP are IGPs. Exterior gateway
IP Routing Features. Contents
 7 IP Routing Features Contents Overview of IP Routing.......................................... 7-3 IP Interfaces................................................ 7-3 IP Tables and Caches........................................
7 IP Routing Features Contents Overview of IP Routing.......................................... 7-3 IP Interfaces................................................ 7-3 IP Tables and Caches........................................
Internet Protocol (IP) IP - Network Layer. IP Routing. Advantages of Connectionless. CSCE 515: Computer Network Programming ------ IP routing
 Process Process Process Layer CSCE 515: Computer Network Programming ------ IP routing Wenyuan Xu ICMP, AP & AP TCP IP UDP Transport Layer Network Layer Department of Computer Science and Engineering University
Process Process Process Layer CSCE 515: Computer Network Programming ------ IP routing Wenyuan Xu ICMP, AP & AP TCP IP UDP Transport Layer Network Layer Department of Computer Science and Engineering University
Lab 10.4.1 IP Addressing Overview
 Lab 10.4.1 IP ing Overview Estimated time: 30 min. Objectives: Background: This lab will focus on your ability to accomplish the following tasks: Name the five different classes of IP addresses Describe
Lab 10.4.1 IP ing Overview Estimated time: 30 min. Objectives: Background: This lab will focus on your ability to accomplish the following tasks: Name the five different classes of IP addresses Describe
Internet Protocols Fall 2005. Lectures 7-8 Andreas Terzis
 Internet Protocols Fall 2005 Lectures 7-8 Andreas Terzis Outline Internet Protocol Service Model Fragmentation Addressing Original addressing scheme Subnetting CIDR Forwarding ICMP ARP Address Shortage
Internet Protocols Fall 2005 Lectures 7-8 Andreas Terzis Outline Internet Protocol Service Model Fragmentation Addressing Original addressing scheme Subnetting CIDR Forwarding ICMP ARP Address Shortage
Interconnection of Heterogeneous Networks. Internetworking. Service model. Addressing Address mapping Automatic host configuration
 Interconnection of Heterogeneous Networks Internetworking Service model Addressing Address mapping Automatic host configuration Wireless LAN network@home outer Ethernet PPS Internet-Praktikum Internetworking
Interconnection of Heterogeneous Networks Internetworking Service model Addressing Address mapping Automatic host configuration Wireless LAN network@home outer Ethernet PPS Internet-Praktikum Internetworking
IP addressing. Interface: Connection between host, router and physical link. IP address: 32-bit identifier for host, router interface
 IP addressing IP address: 32-bit identifier for host, router interface Interface: Connection between host, router and physical link routers typically have multiple interfaces host may have multiple interfaces
IP addressing IP address: 32-bit identifier for host, router interface Interface: Connection between host, router and physical link routers typically have multiple interfaces host may have multiple interfaces
IPv6 Fundamentals: A Straightforward Approach
 IPv6 Fundamentals: A Straightforward Approach to Understanding IPv6 Rick Graziani Cisco Press 800 East 96th Street Indianapolis, IN 46240 IPv6 Fundamentals Contents Introduction xvi Part I: Background
IPv6 Fundamentals: A Straightforward Approach to Understanding IPv6 Rick Graziani Cisco Press 800 East 96th Street Indianapolis, IN 46240 IPv6 Fundamentals Contents Introduction xvi Part I: Background
2.3 IPv4 Address Subnetting Part 2
 .3 IPv4 Address Subnetting Part Objective Upon completion of this activity, you will be able to determine subnet information for a given IP address and subnetwork mask. When given an IP address, network
.3 IPv4 Address Subnetting Part Objective Upon completion of this activity, you will be able to determine subnet information for a given IP address and subnetwork mask. When given an IP address, network
Introduction to The Internet. ISP/IXP Workshops
 Introduction to The Internet ISP/IXP Workshops 1 Introduction to the Internet Topologies and Definitions IP Addressing Internet Hierarchy Gluing it all together 2 Topologies and Definitions What does all
Introduction to The Internet ISP/IXP Workshops 1 Introduction to the Internet Topologies and Definitions IP Addressing Internet Hierarchy Gluing it all together 2 Topologies and Definitions What does all
TCP/IP Fundamentals. OSI Seven Layer Model & Seminar Outline
 OSI Seven Layer Model & Seminar Outline TCP/IP Fundamentals This seminar will present TCP/IP communications starting from Layer 2 up to Layer 4 (TCP/IP applications cover Layers 5-7) IP Addresses Data
OSI Seven Layer Model & Seminar Outline TCP/IP Fundamentals This seminar will present TCP/IP communications starting from Layer 2 up to Layer 4 (TCP/IP applications cover Layers 5-7) IP Addresses Data
Introduction to The Internet
 Introduction to The Internet ISP Workshops Last updated 5 September 2014 1 Introduction to the Internet p Topologies and Definitions p IP Addressing p Internet Hierarchy p Gluing it all together 2 Topologies
Introduction to The Internet ISP Workshops Last updated 5 September 2014 1 Introduction to the Internet p Topologies and Definitions p IP Addressing p Internet Hierarchy p Gluing it all together 2 Topologies
Packet Tracer 3 Lab VLSM 2 Solution
 Packet Tracer 3 Lab VLSM 2 Solution Objective Create a simulated network topology using Packet Tracer Design an IP addressing scheme using a Class B subnetwork address and VLSM Apply IP addresses to the
Packet Tracer 3 Lab VLSM 2 Solution Objective Create a simulated network topology using Packet Tracer Design an IP addressing scheme using a Class B subnetwork address and VLSM Apply IP addresses to the
Chapter 3: Review of Important Networking Concepts. Magda El Zarki Dept. of CS UC Irvine elzarki@uci.edu http://www.ics.uci.
 Chapter 3: Review of Important Networking Concepts Magda El Zarki Dept. of CS UC Irvine elzarki@uci.edu http://www.ics.uci.edu/~magda 1 Networking Concepts Protocol Architecture Protocol Layers Encapsulation
Chapter 3: Review of Important Networking Concepts Magda El Zarki Dept. of CS UC Irvine elzarki@uci.edu http://www.ics.uci.edu/~magda 1 Networking Concepts Protocol Architecture Protocol Layers Encapsulation
DO NOT REPLICATE. Analyze IP. Given a Windows Server 2003 computer, you will use Network Monitor to view and analyze all the fields of IP.
 Advanced TCP/IP Overview There is one primary set of protocols that runs networks and the Internet today. In this lesson, you will work with those protocols: the Transmission Control Protocol (TCP) and
Advanced TCP/IP Overview There is one primary set of protocols that runs networks and the Internet today. In this lesson, you will work with those protocols: the Transmission Control Protocol (TCP) and
Network layer" 1DT066! Distributed Information Systems!! Chapter 4" Network Layer!! goals: "
 1DT066! Distributed Information Systems!! Chapter 4" Network Layer!! Network layer" goals: "! understand principles behind layer services:" " layer service models" " forwarding versus routing" " how a
1DT066! Distributed Information Systems!! Chapter 4" Network Layer!! Network layer" goals: "! understand principles behind layer services:" " layer service models" " forwarding versus routing" " how a
UNDERSTANDING IP ADDRESSING
 52-20-31 DATA COMMUNICATIONS MANAGEMENT UNDERSTANDING IP ADDRESSING Gilbert Held INSIDE The IP Addressing Scheme; Dotted Decimal Notation; Basic Workstation Configuration; Reserved Addresses; Subnetting;
52-20-31 DATA COMMUNICATIONS MANAGEMENT UNDERSTANDING IP ADDRESSING Gilbert Held INSIDE The IP Addressing Scheme; Dotted Decimal Notation; Basic Workstation Configuration; Reserved Addresses; Subnetting;
We Are HERE! Subne\ng
 TELE 302 Network Design Lecture 21 Addressing Strategies Source: McCabe 12.1 ~ 12.4 Jeremiah Deng TELE Programme, University of Otago, 2013 We Are HERE! Requirements analysis Flow Analysis Logical Design
TELE 302 Network Design Lecture 21 Addressing Strategies Source: McCabe 12.1 ~ 12.4 Jeremiah Deng TELE Programme, University of Otago, 2013 We Are HERE! Requirements analysis Flow Analysis Logical Design
2.1.2.2.2 Variable length subnetting
 2.1.2.2.2 Variable length subnetting Variable length subnetting or variable length subnet masks (VLSM) allocated subnets within the same network can use different subnet masks. Advantage: conserves the
2.1.2.2.2 Variable length subnetting Variable length subnetting or variable length subnet masks (VLSM) allocated subnets within the same network can use different subnet masks. Advantage: conserves the
IPv4 Supplement Tutorial - Job Aids and Subnetting
 Appendix B IPv4 Supplement This appendix contains job aids and supplementary information that cover the following topics: IPv4 Addresses and Subnetting Job Aid Decimal-to-Binary Conversion Chart IPv4 Addressing
Appendix B IPv4 Supplement This appendix contains job aids and supplementary information that cover the following topics: IPv4 Addresses and Subnetting Job Aid Decimal-to-Binary Conversion Chart IPv4 Addressing
