A Multiple Bit Upset Tolerant SRAM Memory
|
|
|
- Hubert Jones
- 7 years ago
- Views:
Transcription
1 A Multiple Bit Upset Tolerant SRAM Memory Gustavo Neuberger, Fernanda de Lima, Luigi Carro, Ricardo Reis Universidade Federal do Rio Grande do Sul PPGC - Instituto de Informática - DELET Av. Bento Goncalves 9500, Bloco IV, Porto Alegre, RS, Brazil <neuberg, fglima, carro, reis>@inf.ufrgs.br ABSTRACT This paper presents a high level technique to protect SRAM memories against multiple upsets based on correcting codes. The proposed technique combines Reed Solomon code and Hamming code to assure reliability in presence of multiple bit flips with reduced area and performance penalties. Multiple upsets were randomly injected in various combinations of memory cells to evaluate the robustness of the method. The experiment was emulated in a Virtex FPGA platform. Results show that 100% of the injected double faults and a large amount of multiple faults were corrected by the method. 1: Introduction The constant technology process improvement, has remarkably reduced the transistor geometry and power supply levels in the integrated circuits. In high-density circuits operating in low voltage, the memory cells are able to store information with less capacitance, which means that less charge or current is required to store the data. Unfortunately, a direct consequence is the increase in the device vulnerability to radiation, as charged particles that were once negligible are now much more likely to produce upsets [1]. When a single charged particle strikes the silicon, it loses its energy, resulting in a dense ionized track in the local region. The ionization causes a transient current pulse. This effect is called Single Event Upset (SEU). Although SEU is the major concern in space application, multiple bit upsets (MBU) start to be also a matter to be addressed nowadays because of the nanometric technologies. When a single high-energy ion pass through the silicon it can energize two or more adjacent memory cells [2]. MBUs can be induced by direct ionization or nuclear recoil. The energy of the particle is more likely to provoke double bit upsets while multiple bit upsets are caused by an increase of the particle incident angle. In [3, 4, 5], experiments in memories under proton and heavy ions fluxes have shown the probability of multiple upsets provoked by a single ion. Several techniques are used nowadays to mitigate upsets in memory components. They are based on specific technology process such as Silicon on Insulator (SOI), or based on design, such as replacing each memory cell by hardened memory cells and using error detection and correction codes (EDAC) [6]. Each technique has some advantages and drawbacks, and there is always a compromise between cost, area, performance, power and fault tolerance efficiency. EDAC is an attractive technique because it can be implemented in a high level design step, without changes in the mask process (no NRE cost). There are examples of SEU mitigation techniques using EDAC performed by software [7] and by hardware [8]. Hamming code is largely used to protect memories against SEU because of its efficient ability to correct single upsets with a reduced area and performance overhead [9]. However, multiple upsets caused by a single charged particle can provoke errors in the system protected by the single-error correcting Hamming code, since it assumes a single upset corrected per coded word. In the other hand, Reed-Solomon [6] is a block-based error correcting code, able to cope with multiple upsets. It has a wide range of applications in digital communications and storage. Reed-Solomon codes are used to correct errors in many systems including: storage devices, wireless or mobile communications, high-speed modems and others. Reed-Solomon encoding and decoding is commonly carried out in software, for this reason the RS algorithms normally found in literature do not take into account area and performance effects for hardware implementation. We have developed an efficient Reed-Solomon encoding and decoding description with single block correction capability designed for hardware implementation to protect embedded system memories against multiple upsets. Although the designed RS code copes with multiple upsets, it does not correct double faults located in two adjacent blocks; which requires the use of RS code with double block correction capability. The cost of double block correction code is too high compared to the single block correction code, which makes this alternative inappropriate for hardware implementation. This paper presents a technique that solves the problem of how to achieve 100% of double faults correction without using the high costly double block correction capability RS code. This new technique to protect memories against single and multiple upsets combines Hamming and Reed-Solomon codes with a reduced area overhead compared to more complex codes able to correct multiple upsets. The robustness of the
2 technique was evaluated by fault injection emulated in a Virtex board. Results show that 100% of the single and double faults were corrected by the technique, as well a large amount of multiple faults. To the author s knowledge, no references were published about a highlevel technique able to correct all double faults and a large number of multiple faults in embedded memories, as presented in this paper. 2: Previous Work Hamming code is an error-detecting and errorcorrecting binary code that satisfies the equation, d+p+1? 2 p, where d is the number of data bits and p is the number of parity bits. Following this equation the Hamming code can correct all single-bit errors on d-bit words and detect double-bit errors when an overall parity check bit is used (SEC-DED) [6]. The hamming code implementation is composed by a combinational block responsible to code the data (encoder block), inclusion of extra bits in the word that indicate the parity (extra latches or flip-flops) and another combinational block responsible to decode the data (decoder block). The encoder block calculates the parity bit and it can be implemented by a set of 2-input XOR gates. The decoder block is more complex than the encoder block, because it needs not only to detect the fault, but it must also correct it. It is basically composed by the same logic used to compose the parity bits plus a decoder, that will indicate the bit address that contains the upset. The decoder block can also be composed of a set of 2-input XOR gates and some AND and INVERTER gates. In [9], studies show the area efficiency of using Hamming code to protect memories. However, it does not cope with multiple upsets. Consequently, more complex correcting codes must be investigated. Reed Solomon [6] is an error-correcting coding system that was devised to address the issue of correcting multiple errors. A Reed-Solomon code is specified as RS (n,k) with s-bit symbols, where n is the total number of symbols per code word and k is the number of data bytes. The number of parity bytes is equal to n k, where n is 2 raised to the power of s minus one (2 s 1). A Reed- Solomon decoder can correct up to t number of bytes, where 2t = n k. So, a Reed-Solomon code with t = 1 can correct all single-bit errors and up to s errors in the same symbol (block), but can not correct a double bit error if these bits are located in two adjacent symbols. To implement a Reed-Solomon code with t = 1, two parity symbols are needed, commonly named R and S. For example, a RS code with 5-bit symbols has a maximum of 31 symbols (155 bits). In order to has single symbol correction, it must has 2 parity symbols and 29 data symbols. The encoding process has to divide the data bits in s- bit symbols; to multiply each symbol by appropriate constants; to perform XOR operations between the multiplication results in order to find R and S symbols. The RS code algorithm needs a high number of tables for conversion proposes. But for hardware implementation, tables have a large area overhead, and to perform the operation in only one cycle, is needed one table for each conversion. In the developed implementation, the conversion tables were replaced logical and arithmetical operations. Consequently, the encoder block is basically implemented by XOR gates. The decoding process is to divide the received bits in R, S and the data symbols, to multiply the RS constants by the symbols and to perform XOR operations of the last results in order to find S0 and S1. If S0 and S1 are 0, no errors are found, otherwise, S1/S0 is the location of the error and S0 is the pattern. In a decoder that only detects if there are errors, with no correction, the steps are basically the same of the encoder. So, the full decoder block is more complex because of the logic needed to locate and correct the error. Reed-Solomon codes with symbols of 5, 6, 7 and 8 bits, all with correction capability of one symbol, were designed in VHDL. Encoding and decoding are performed in a single cycle [10]. This description was optimized for area and performance by using multiplication that do not use tables for this operation. The Reed-Solomon and Hamming designed cores were synthesized in VirtexE FPGA (V600EHQ240) from Xilinx [11] and simulated using ModelSim from Mentor. Results of area, extra flipflops and delay of encoding and decoding were compared to a Hamming code with same word width. The design area occupied in the FPGA is measured in number of 4- input Look-up Table (4-LUT) used to implement the logic. Table 1 shows the results of the RS(155, 145) compared to a 145-bit Hamming code. Reed Solomon Hamming Encoder Decoder Encoder Decoder # 4-LUTs # flip-flops 10 8 Delay (ns) Tab.1 Area and performance comparison between hamming code (145-bit) and Reed-Solomon (145-bit) Based on table 1, we can see that the Hamming code has less area overhead than the Reed-Solomon, but the advantage of the Reed-Solomon is that it can correct 1 to 5 bits of errors, if they are in the same symbol, versus only 1 bit corrected between all 145 bits of the Hamming code. In most cases, the errors are consecutive, and the Reed- Solomon can correct them if they are in the same symbol while Hamming code can not. Another important result is that in both codes, the decoding process has more overhead in area and delay than the encoding process. 3: New MBU Fault-tolerant Memory Architecture A n-bit data memory can be protected against faults by using correcting code techniques based on encoder and
3 decoder blocks and extra bits to store the data parities, as represented in figure 1. The encoder and the decoder can use any error detection and correction code. A limitation of this approach is that the data is only coded in write operations, and decoded in read operations. So, the accumulation of upsets is likely to occur and it is dependable of the reading and writing application request frequency. In order to avoid accumulation of upsets, it is necessary an extra logic able to constantly detect and correct upsets in all coded data. This logic represents area cost and it may interfere in the normal operation of the memory if dual port memory is not used. For example, in the case of using Hamming code, the memory can only support single bit upsets. The problem is that multiple upsets are likely to occur in current and in future technologies. In addition, upsets can accumulate in the memory if the correction process is not fast enough comparing to the upset flux. Fig. 1 General schematic of a fault tolerant memory In order to be able to correct multiple bit upsets, RS code must be used. The data word is divided in symbols, and each data word is a different RS coded word. For example, in a 256-rows memory, the data word uses the entire row, and each data word is divided in m symbols according to the symbol size and to the memory data size. Multiple upsets may occur in any portion of the matrix, but they are more likely to occur as double bit flips that are in the same symbol (upset type a), in vertical adjacent symbols, (upset type b), or in horizontal adjacent symbols, (upset type c) (figure 2). The RS code can easily correct upsets of type a, because it is the essential property of this code: multiple error correction in a same symbol. The second type of double upsets that can occur (type b) will also be corrected because each row is a different RS code, so this is equivalent to two single errors in distinct rows. But the third type of upsets (type c) will not be corrected, because it is equivalent to errors in two different symbols of the same coded word, and the implemented RS is not capable to correcting this type of error. Fig. 2 Examples of double bit flips in a memory where each row is protected by RS So, a new code is needed to correct all possible double errors. The first option is the use of a Reed-Solomon code with capability to correct two different symbols. But this RS code has more than twice the area and delay overhead of the single symbol correction RS [6], which makes this solution inappropriate for memory architectures. The second alternative is the use of bit protected by Hamming code between the RS symbols. The number of bits protected by Hamming will be the same of the number of symbols protected by Reed-Solomon, so this option does not significantly increases the area overhead. Figure 3 presents the insertion of Hamming code in row already coded by RS code. Fig. 3 Schematic of a memory row protected by Reed-Solomon and Hamming code This new approach was analyzed to all possible single, double and greater multiplicity errors, as shown in figure 4 and table 2. All single upsets are corrected by the code. Double bit upsets occurring horizontally or vertically are corrected by the code because each row is a different coded word and there is Hamming code protection in the RS symbols interface. Some multiple bit upsets such as the numbers 7, 8 and 9 are also corrected by the proposed method. The only type of multiple upsets that are not corrected by the method is number 10. However, special placement of the RS coded word symbols may solve this problem. Fig. 4 Representation of single, double and multiple upset types in a memory 3.1: The Memory Case Study Once defined the codes to be used, the next step is to determine the specifications of the memory and the Reed- Solomon and Hamming codes sizes. The first memory study case is a 128-bit data memory, where a 128-bit code is needed. Based on the previously compared tradeoffs of RS code [10], a 7-bit symbol RS code presents an efficient area and performance overhead compared to the number of protected bits. Consequently, a 7-bit symbol RS code was chosen to protect 112 bits of the data memory and a 16-bit Hamming code was chosen to protect the bits between each RS symbol, as it was presented in figure 3. The extra bits to be stored are 14 bits due to Reed- Solomon and 5 bits due to Hamming code, totalizing 19 parity bits for each row. Note that in this first memory study case, the size of the stored data is the same of the matrix physical row. In next section, we discuss the use of this method for any size of data memory in a 128-bit matrix row. Table 3 shows the area and delay of the 112- bit Reed-Solomon code and the 16-bit Hamming code.
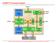
4 Upset Location Fault type Reed-Solomon combined with Hamming Code Effect Single Reed-Solomon symbol 1 Corrected, single error in only one RS symbol Hamming bit 2 Corrected, single error in the Hamming data bits Double RS symbol 3 Corrected, multiple error in only one RS symbol Vertical RS adjacent symbols 4 Corrected, single error in different RS codes Vertical Hamming adjacent bits 5 Corrected, single error in different Hamming codes Horizontal RS and Hamming adjacent bits 6 Corrected, single error in RS symbol and single error in Hamming data bits Multiple Vertical RS symbols 7 Corrected, single error in different RS codes Vertical Hamming bits 8 Corrected, single error in different Hamming codes Horizontal RS symbol and Hamming bit 9 Corrected, single error in RS symbol and single error in Hamming data bits Horizontal RS symbol, Hamming bit and RS symbol 10 Detected but not corrected, single error in Hamming data bits but error in two different RS symbols in the same row Tab. 2 Upset Analysis in Space Environment 16-bit Hamming 112-bit RS Encoder Decoder Encoder Decoder # 4-LUTs # extra ffs 5 x # of row 14 x # of rows Delay (ns) Tab.3 Area and Delay of Reed-Solomon and Hamming codes used to protect a memory Figure 5 shows the final architecture of the double error tolerant memory. There are two encoder and decoder blocks, one for Hamming code and other for RS code. The parity bits are also stored in the memory in a reserved area. The placement of each RS parity symbols and Hamming parity bits must be also taken into account to avoid double upsets in the same Hamming coded parity word or in two parity symbols of the same RS coded word. However, because the method is robust to a large number of upsets in a memory, it is necessary a very high flux of charged particles to provoke an accumulation of upsets able to overcome the technique. In order to refresh the data, correcting the faults, a dual-port memory can be used. During read operations, thief any error is detected during decoding, the correct value is written in the memory using the second port, without interruptions in the normal memory operation. The data memory now is error-free. This approach is shown in figure 6. No protected Fault Tolerant Memory Memory # 4-LUTs # BlockRAMs Speed (MHz) Tab.4 Area and performance comparison between a noprotected 128-bit memory and a full fault tolerant 128-bit memory based on RS and Hamming code. Fig. 5 Final schematic of the fault tolerant memory The memory study case was described in VHDL and synthesized in a Virtex-E FPGA using BlockRAMs and CLBs. The simulation was performed using ModelSim from Mentor [11]. Results are presented in table 4. In the results, it is noticed that the fault tolerant memory has an area overhead that is basically the area used by the encoder and decoder blocks. Only two more BlockRAMs are needed, one to store the RS redundancy symbols and other to store the Hamming extra bits. The performance penalty in the fault tolerant memory synthesized in the FPGA is around 50%. Note that in this new mitigation technique, we still cope with the feature of performing encoding only in the write operations and decoding only in read operations. Fig. 6 Fault tolerant memory implemented using a two-port memory 4: GENERALIZING THE MEMORY SIZE The MBU mitigation technique proposed in this paper was presented for a case study memory of 128-bit data words. But not all processors could work with 128-bit memory. One possible solution is to design a new code for each data width. But it is not good because we need to design a completely new library of encoding functions corresponding to the new data width. And for common words of 8-bits, Reed-Solomon and Hamming need too many extra bits and the area occupied will be significantly
5 larger compared to the original area. So, it is better to adapt the memory without changing the used code. This section shows the necessary steps to adapt the previously designed memory to an interface with the 8 bit processor, but the process can be easily modified for other data widths. In the output, it is easy to change from 128 bits to 8 bits. It only needs a multiplexer to choose the correct 8 bits address. The signal of selection of the multiplexer is the least significant bits from the address signal. The input data of the memory needs more modifications than the output, because now we have only 8 bits of the data that must be encoded, and the others 120 bits remains the same. Looking more closely to the Reed- Solomon and Hamming codes encoding process, one will see that they are basically exclusive or (XOR) operations. The encoding step of the Reed-Solomon code is composed by: divide the input data bits between the symbols, multiply each symbol by an appropriate constant, and the parity bits are XOR operations of these multiplications. The XOR operation has two important properties: A xor 0 = A, A xor 1 = not A. Knowing these properties, we can see that it is easily to subtract the part of a symbol that is contributing to the parity bits. It is only a XOR of the parity bits with a multiplication of the appropriated constant by the old symbol. To get the new parity bits, we use XOR gates again, but with a multiplication of the new symbol with the same constant. So, we need to design a new Reed-Solomon and Hamming encoders, but the inputs of these new encoders are the old parity bits, the old data, the new data and the address of the data; the output is the new parity data. For example, now the steps of Reed-Solomon encoding process are: use the address to get the appropriate constant, multiply the old symbol and the new symbol by the constant, and do a XOR between the old parity and the two multiplications. More than to adapt the encoder to the new memory, we can see that the encoder will have a significantly reduction in area, because now need only two multiplications, compared to 16 multipliers in the full encoding version shown before. The comparison between the new and the old encoders are presented in table 5. Standard RS Enc Dedicated RS Enc # 4-LUTs Delay (ns) Tab.5 Area and performance comparison between the standard RS and the RS dedicated for 8-bit memories Now we have a new encoder that can works with a data input of 8 bits. But the problem is that the new encoder needs the data previously stored in the same address. Usually, in a write operation the new data is stored in the specified address, and it is not necessary to know the old data. But for this memory, we need it. So, the solution is to read the memory in the clock rising edge, and to write only in the falling edge of the clock. The user s data and address input are stored in two auxiliary registers while the old data is read from the memory. The write enable signal is also stored in a latch to be used in the clock falling edge. Note that there is no clock phase latency, just a delay in the write cycle that is transparent for the user. One drawback of this solution is the necessity of using extra SEU mitigation techniques for the two registers (data and address) and the write signal latch. The final schematic of the 8 bits memory is shown in Fig 8. Fig. 8 MBU tolerant 8-bit memory schematic The comparison between the original 128 bits memory and this adapted 8 bits memory is presented in table 6. Analysing these results, the performed changes increases the area overhead in approximately 60%. But the speed has a bigger overhead, caused by the utilization of both rising and falling edges of the clock for the write process. Fault Tolerant 128-bit Memory Fault Tolerant 8-bit Memory # 4-LUTs # BlockRAMs Speed (MHz) Tab.6 Area and performance comparison between fault tolerant 128 bits and 8 bits fault tolerant memory 5: Fault Injection Emulation Experiment Fault injection is an attractive technique for design evaluation due to its high flexibility in terms of spatial and temporal information. The process involves the insertion of faults into particular targets of a system at a determined time in the process and monitoring of results to define its behavior in response of a fault. It has also a reduced turnaround time and an evaluation cost compared to traditional radiation ground testing. Moreover, it has been shown that injecting fault in a programmable logic platform, after synthesizing the full system in a Field Programmable Gate Array (FPGA) can speed up the process in many orders of magnitude [13]. The case study memory evaluated in the experiment is a MBU tolerant 128-bit memory protected by the proposed method based on RS and Hamming code. The fault injection test platform is composed by one AFX V600HQ daughter card, a JTAG cable used as an interface to a host PC, and a control panel. The system operates in conjunction with a host PC in order to collect the data in the Chipscope analyzer tool [14]. In order to evaluate the robustness of the protected memory, static and dynamic test were performed by fault injection. During the static test, the protected memory
6 under test (DUT) and a gold memory (fault free) were initialized with random values in the first 16 row positions (2048 total bits per memory). Then in the next cycles, all types of faults discussed in table 2 were injected in the DUT memory. Just one fault was inserted per analysis. The two memories were read and their values were compared. If they are different the fault was not tolerated. As predicted, only the fault type 10 was not tolerated. After that, the faults were injected dynamically as follows. In the initialization, 16 pairs of 128-bit random numbers were stored in two memories under test, and their sums were stored in a gold memory, used to further comparison. Random types of faults were injected at a random instant of time in a random position. The two memories under test were continuously read and the sum of their outputs was compared to the sum stored in the gold memory. After all positions were read, the memories were reinitialized and other random type of fault was injected. The injected faults are the same fault types discussed in table 2. Each fault type has a different probability to occur according to the application environment. Single upsets were projected to have more probability to occur in the fault injection experiment 2:1. While double and multiple upsets are more unlikely to occur but are also tested by the fault injection. These parameters of fault probability can be customized by the user in the VHDL code consistent with the target application. There were injected 1,002 faults, classified in the 10 different types of faults. As predicted, all single and double faults were tolerated. In the case of multiple faults, the method does not tolerate faults upsetting two adjacent RS symbols and the Hamming bit between these two symbols (fault type number 10). For the used application, 21% of the injected multiple faults, type number 10, were tolerated by the application. Although this type of fault is not expected to be corrected by the method, it can be tolerated according to the application. 6: Conclusion This paper presented a high level technique to protect SRAM memories against single and multiple upsets based on correcting codes. The proposed technique combines Reed Solomon code and Hamming code to assure reliability in presence of multiple bit flips with reduced area overhead, needs only 19 parity bits per 128-bit row and performance penalty around 50%. Multiple upsets were randomly injected in all memory cells to evaluate the robustness of the method. The experiment was emulated in a Virtex FPGA platform. Results show the efficiency of the proposed method in presence of all single and double upsets and many types of multiple upsets. All double faults and a large combination of multiple faults were corrected by the method. The only type of multiple faults that was only detected but not corrected by the method is where multiple upsets (three or more) affect two different RS code symbol (example fault type 10). Future work involves the implementation of the method in an ASIC approach in order to have a more precise area and performance overhead evaluation comparing to a no-protected memory component, and make a design embedding this memory and several others to compare in terms of area and performance penalties. ACKNOWLEDGMENTS The authors would like to thank CNPq Brazilian Agency for their support to this work. REFERENCE [1] JOHNSTON, A. Scaling and Technology Issues for Soft Error Rates, 4th Annual Research Conference on Reliability, Stanford University, Oct [2] REED, R.; et al, Heavy Ion and Proton Induced Single Event Multiple Upsets, IEEE Nuclear and Space Radiation Effects Conference (NSREC), July [3] WROBEL, F., PALAU, J., CALVET, M., BERSILLON, O., DUARTE, H., Simulation of Nucleon-Induced Nuclear Reactions in a Simplified SRAM Structure: Scaling Effects on SEU and MBU Cross Sections IEEE Transactions on Nuclear Science, December 2001 [4] JOHANSSON, K., OHLSSON, M., OLSSON, N., BLOMGREN, J., RENBERG, P., Neutron Induced Single- Word Multiple-bit Upset in SRAM IEEE Transactions on Nuclear Science, December 1999 [5] BUCHNER, S., CAMPBELL, A., MEEHAN, T., CLARK, K., McMORROW, D., DYER, C., SANDERSON, C., COMBER, C., KUBOYAMA, S., Investigation of Single- Ion Multiple-Bit Upsets in Memories on Board a Space Experiment IEEE Trans. on Nuclear Science, June 2000 [6] HOUGHTON, A. D., The Engineer s Error Coding Handbook, Chapman & Hall : London, [7] SHIRVANI, P., SAXENA, N., McCLUSKEY, E., Software Implemented EDAC Protection Agains SEUs, IEEE Transactions on Reliability, Special Section on Fault-Tolerant VLSI Systems, Vol. 49, No. 3, pp , Sep [8] REDINBO, G., NAPOLITANO, L., ANDALEON, D., Multibit Correcting Data Interface for Fault-Tolerant Systems IEEE Transactions on Nuclear Science, April 1993 [9] HENTSCHKE, R., MARQUES, F, LIMA, F., CARRO, L., SUSIN, A., REIS, R., Analyzing Area and Performance Penalty of Protecting Different Digital Modules with Hamming Code and Triple Modular Redundancy, In: Symposium on Integrated Circuits and Systems Design (SBCCI), [10] NEUBERGER, G., LIMA, F., REIS, R., Designing a Reed-Solomon Core Optimized for Area and Performance XVII South Symposium on Microelectronics, June [11] Xilinx Inc. Virtex 2.5 V Field Programmable Gate Arrays, Xilinx Datasheet DS003, v2.4, Oct [12] Mentor, ModelSim SE User's Manual. Sep [13] LIMA, F., CARRO, L., VELAZCO, R., REIS, R., Injecting Multiple Upsets in a SEU tolerant 8051 Microcontroller, In: Latin-American Test Workshop, [14] XILINX, INC. Chipscope Software and ILA Cores User Manual, Xilinx User Manual, (v2.0) Dec., 2000.
How To Fix A 3 Bit Error In Data From A Data Point To A Bit Code (Data Point) With A Power Source (Data Source) And A Power Cell (Power Source)
 FPGA IMPLEMENTATION OF 4D-PARITY BASED DATA CODING TECHNIQUE Vijay Tawar 1, Rajani Gupta 2 1 Student, KNPCST, Hoshangabad Road, Misrod, Bhopal, Pin no.462047 2 Head of Department (EC), KNPCST, Hoshangabad
FPGA IMPLEMENTATION OF 4D-PARITY BASED DATA CODING TECHNIQUE Vijay Tawar 1, Rajani Gupta 2 1 Student, KNPCST, Hoshangabad Road, Misrod, Bhopal, Pin no.462047 2 Head of Department (EC), KNPCST, Hoshangabad
Chapter 4 Register Transfer and Microoperations. Section 4.1 Register Transfer Language
 Chapter 4 Register Transfer and Microoperations Section 4.1 Register Transfer Language Digital systems are composed of modules that are constructed from digital components, such as registers, decoders,
Chapter 4 Register Transfer and Microoperations Section 4.1 Register Transfer Language Digital systems are composed of modules that are constructed from digital components, such as registers, decoders,
ERROR DETECTION AND CORRECTION
 Supplement to Logic and Computer Design Fundamentals 3rd Edition 1 ERROR DETECTION AND CORRECTION Selected topics not covered in the third edition of Logic and Computer Design Fundamentals are provided
Supplement to Logic and Computer Design Fundamentals 3rd Edition 1 ERROR DETECTION AND CORRECTION Selected topics not covered in the third edition of Logic and Computer Design Fundamentals are provided
CHAPTER 3 Boolean Algebra and Digital Logic
 CHAPTER 3 Boolean Algebra and Digital Logic 3.1 Introduction 121 3.2 Boolean Algebra 122 3.2.1 Boolean Expressions 123 3.2.2 Boolean Identities 124 3.2.3 Simplification of Boolean Expressions 126 3.2.4
CHAPTER 3 Boolean Algebra and Digital Logic 3.1 Introduction 121 3.2 Boolean Algebra 122 3.2.1 Boolean Expressions 123 3.2.2 Boolean Identities 124 3.2.3 Simplification of Boolean Expressions 126 3.2.4
Computer Systems Structure Main Memory Organization
 Computer Systems Structure Main Memory Organization Peripherals Computer Central Processing Unit Main Memory Computer Systems Interconnection Communication lines Input Output Ward 1 Ward 2 Storage/Memory
Computer Systems Structure Main Memory Organization Peripherals Computer Central Processing Unit Main Memory Computer Systems Interconnection Communication lines Input Output Ward 1 Ward 2 Storage/Memory
Verification of Triple Modular Redundancy (TMR) Insertion for Reliable and Trusted Systems
 Verification of Triple Modular Redundancy (TMR) Insertion for Reliable and Trusted Systems Melanie Berg 1, Kenneth LaBel 2 1.AS&D in support of NASA/GSFC Melanie.D.Berg@NASA.gov 2. NASA/GSFC Kenneth.A.LaBel@NASA.gov
Verification of Triple Modular Redundancy (TMR) Insertion for Reliable and Trusted Systems Melanie Berg 1, Kenneth LaBel 2 1.AS&D in support of NASA/GSFC Melanie.D.Berg@NASA.gov 2. NASA/GSFC Kenneth.A.LaBel@NASA.gov
FPGA Implementation of System-on-chip (SOC) Architecture for Spacecraft Application
 The International Journal Of Engineering And Science (IJES) Volume 3 Issue 6 Pages 17-24 2014 ISSN (e): 2319 1813 ISSN (p): 2319 1805 FPGA Implementation of System-on-chip (SOC) Architecture for Spacecraft
The International Journal Of Engineering And Science (IJES) Volume 3 Issue 6 Pages 17-24 2014 ISSN (e): 2319 1813 ISSN (p): 2319 1805 FPGA Implementation of System-on-chip (SOC) Architecture for Spacecraft
Nonlinear Multi-Error Correction Codes for Reliable NAND Flash Memories
 1 Nonlinear Multi-Error Correction Codes for Reliable NAND Flash Memories Zhen Wang, Student Member, IEEE, Mark Karpovsky, Fellow, IEEE, and Ajay Joshi, Member, IEEE Abstract Multi-level cell (MLC NAND
1 Nonlinear Multi-Error Correction Codes for Reliable NAND Flash Memories Zhen Wang, Student Member, IEEE, Mark Karpovsky, Fellow, IEEE, and Ajay Joshi, Member, IEEE Abstract Multi-level cell (MLC NAND
LA-UR- Title: Author(s): Intended for: Approved for public release; distribution is unlimited.
 LA-UR- Approved for public release; distribution is unlimited. Title: Author(s): Intended for: Los Alamos National Laboratory, an affirmative action/equal opportunity employer, is operated by the Los Alamos
LA-UR- Approved for public release; distribution is unlimited. Title: Author(s): Intended for: Los Alamos National Laboratory, an affirmative action/equal opportunity employer, is operated by the Los Alamos
Digital Logic Design. Basics Combinational Circuits Sequential Circuits. Pu-Jen Cheng
 Digital Logic Design Basics Combinational Circuits Sequential Circuits Pu-Jen Cheng Adapted from the slides prepared by S. Dandamudi for the book, Fundamentals of Computer Organization and Design. Introduction
Digital Logic Design Basics Combinational Circuits Sequential Circuits Pu-Jen Cheng Adapted from the slides prepared by S. Dandamudi for the book, Fundamentals of Computer Organization and Design. Introduction
ON SUITABILITY OF FPGA BASED EVOLVABLE HARDWARE SYSTEMS TO INTEGRATE RECONFIGURABLE CIRCUITS WITH HOST PROCESSING UNIT
 216 ON SUITABILITY OF FPGA BASED EVOLVABLE HARDWARE SYSTEMS TO INTEGRATE RECONFIGURABLE CIRCUITS WITH HOST PROCESSING UNIT *P.Nirmalkumar, **J.Raja Paul Perinbam, @S.Ravi and #B.Rajan *Research Scholar,
216 ON SUITABILITY OF FPGA BASED EVOLVABLE HARDWARE SYSTEMS TO INTEGRATE RECONFIGURABLE CIRCUITS WITH HOST PROCESSING UNIT *P.Nirmalkumar, **J.Raja Paul Perinbam, @S.Ravi and #B.Rajan *Research Scholar,
Data Storage Time Sensitive ECC Schemes for MLC NAND Flash Memories
 Data Storage Time Sensitive ECC Schemes for MLC NAND Flash Memories C. Yang, D. Muckatira, A. Kulkarni, C. Chakrabarti School of Electrical, Computer and Energy Engineering, Arizona State University, Tempe,
Data Storage Time Sensitive ECC Schemes for MLC NAND Flash Memories C. Yang, D. Muckatira, A. Kulkarni, C. Chakrabarti School of Electrical, Computer and Energy Engineering, Arizona State University, Tempe,
1. Memory technology & Hierarchy
 1. Memory technology & Hierarchy RAM types Advances in Computer Architecture Andy D. Pimentel Memory wall Memory wall = divergence between CPU and RAM speed We can increase bandwidth by introducing concurrency
1. Memory technology & Hierarchy RAM types Advances in Computer Architecture Andy D. Pimentel Memory wall Memory wall = divergence between CPU and RAM speed We can increase bandwidth by introducing concurrency
Implementation of Modified Booth Algorithm (Radix 4) and its Comparison with Booth Algorithm (Radix-2)
 Advance in Electronic and Electric Engineering. ISSN 2231-1297, Volume 3, Number 6 (2013), pp. 683-690 Research India Publications http://www.ripublication.com/aeee.htm Implementation of Modified Booth
Advance in Electronic and Electric Engineering. ISSN 2231-1297, Volume 3, Number 6 (2013), pp. 683-690 Research India Publications http://www.ripublication.com/aeee.htm Implementation of Modified Booth
Open Flow Controller and Switch Datasheet
 Open Flow Controller and Switch Datasheet California State University Chico Alan Braithwaite Spring 2013 Block Diagram Figure 1. High Level Block Diagram The project will consist of a network development
Open Flow Controller and Switch Datasheet California State University Chico Alan Braithwaite Spring 2013 Block Diagram Figure 1. High Level Block Diagram The project will consist of a network development
Radiation effects on space electronics. Jan Kenneth Bekkeng, University of Oslo - Department of Physics
 Radiation effects on space electronics Jan Kenneth Bekkeng, University of Oslo - Department of Physics Background The presence of radiation in space causes effects in electronic devices. The effects range
Radiation effects on space electronics Jan Kenneth Bekkeng, University of Oslo - Department of Physics Background The presence of radiation in space causes effects in electronic devices. The effects range
7a. System-on-chip design and prototyping platforms
 7a. System-on-chip design and prototyping platforms Labros Bisdounis, Ph.D. Department of Computer and Communication Engineering 1 What is System-on-Chip (SoC)? System-on-chip is an integrated circuit
7a. System-on-chip design and prototyping platforms Labros Bisdounis, Ph.D. Department of Computer and Communication Engineering 1 What is System-on-Chip (SoC)? System-on-chip is an integrated circuit
Introduction to Digital System Design
 Introduction to Digital System Design Chapter 1 1 Outline 1. Why Digital? 2. Device Technologies 3. System Representation 4. Abstraction 5. Development Tasks 6. Development Flow Chapter 1 2 1. Why Digital
Introduction to Digital System Design Chapter 1 1 Outline 1. Why Digital? 2. Device Technologies 3. System Representation 4. Abstraction 5. Development Tasks 6. Development Flow Chapter 1 2 1. Why Digital
Modeling Latches and Flip-flops
 Lab Workbook Introduction Sequential circuits are digital circuits in which the output depends not only on the present input (like combinatorial circuits), but also on the past sequence of inputs. In effect,
Lab Workbook Introduction Sequential circuits are digital circuits in which the output depends not only on the present input (like combinatorial circuits), but also on the past sequence of inputs. In effect,
RAM & ROM Based Digital Design. ECE 152A Winter 2012
 RAM & ROM Based Digital Design ECE 152A Winter 212 Reading Assignment Brown and Vranesic 1 Digital System Design 1.1 Building Block Circuits 1.1.3 Static Random Access Memory (SRAM) 1.1.4 SRAM Blocks in
RAM & ROM Based Digital Design ECE 152A Winter 212 Reading Assignment Brown and Vranesic 1 Digital System Design 1.1 Building Block Circuits 1.1.3 Static Random Access Memory (SRAM) 1.1.4 SRAM Blocks in
Fault Tolerance & Reliability CDA 5140. Chapter 3 RAID & Sample Commercial FT Systems
 Fault Tolerance & Reliability CDA 5140 Chapter 3 RAID & Sample Commercial FT Systems - basic concept in these, as with codes, is redundancy to allow system to continue operation even if some components
Fault Tolerance & Reliability CDA 5140 Chapter 3 RAID & Sample Commercial FT Systems - basic concept in these, as with codes, is redundancy to allow system to continue operation even if some components
Chapter 7 Memory and Programmable Logic
 NCNU_2013_DD_7_1 Chapter 7 Memory and Programmable Logic 71I 7.1 Introduction ti 7.2 Random Access Memory 7.3 Memory Decoding 7.5 Read Only Memory 7.6 Programmable Logic Array 77P 7.7 Programmable Array
NCNU_2013_DD_7_1 Chapter 7 Memory and Programmable Logic 71I 7.1 Introduction ti 7.2 Random Access Memory 7.3 Memory Decoding 7.5 Read Only Memory 7.6 Programmable Logic Array 77P 7.7 Programmable Array
ESP-CV Custom Design Formal Equivalence Checking Based on Symbolic Simulation
 Datasheet -CV Custom Design Formal Equivalence Checking Based on Symbolic Simulation Overview -CV is an equivalence checker for full custom designs. It enables efficient comparison of a reference design
Datasheet -CV Custom Design Formal Equivalence Checking Based on Symbolic Simulation Overview -CV is an equivalence checker for full custom designs. It enables efficient comparison of a reference design
Floating Point Fused Add-Subtract and Fused Dot-Product Units
 Floating Point Fused Add-Subtract and Fused Dot-Product Units S. Kishor [1], S. P. Prakash [2] PG Scholar (VLSI DESIGN), Department of ECE Bannari Amman Institute of Technology, Sathyamangalam, Tamil Nadu,
Floating Point Fused Add-Subtract and Fused Dot-Product Units S. Kishor [1], S. P. Prakash [2] PG Scholar (VLSI DESIGN), Department of ECE Bannari Amman Institute of Technology, Sathyamangalam, Tamil Nadu,
Hardware and Software
 Hardware and Software 1 Hardware and Software: A complete design Hardware and software support each other Sometimes it is necessary to shift functions from software to hardware or the other way around
Hardware and Software 1 Hardware and Software: A complete design Hardware and software support each other Sometimes it is necessary to shift functions from software to hardware or the other way around
Memory Elements. Combinational logic cannot remember
 Memory Elements Combinational logic cannot remember Output logic values are function of inputs only Feedback is needed to be able to remember a logic value Memory elements are needed in most digital logic
Memory Elements Combinational logic cannot remember Output logic values are function of inputs only Feedback is needed to be able to remember a logic value Memory elements are needed in most digital logic
How To Encrypt Data With A Power Of N On A K Disk
 Towards High Security and Fault Tolerant Dispersed Storage System with Optimized Information Dispersal Algorithm I Hrishikesh Lahkar, II Manjunath C R I,II Jain University, School of Engineering and Technology,
Towards High Security and Fault Tolerant Dispersed Storage System with Optimized Information Dispersal Algorithm I Hrishikesh Lahkar, II Manjunath C R I,II Jain University, School of Engineering and Technology,
Attaining EDF Task Scheduling with O(1) Time Complexity
 Attaining EDF Task Scheduling with O(1) Time Complexity Verber Domen University of Maribor, Faculty of Electrical Engineering and Computer Sciences, Maribor, Slovenia (e-mail: domen.verber@uni-mb.si) Abstract:
Attaining EDF Task Scheduling with O(1) Time Complexity Verber Domen University of Maribor, Faculty of Electrical Engineering and Computer Sciences, Maribor, Slovenia (e-mail: domen.verber@uni-mb.si) Abstract:
Static-Noise-Margin Analysis of Conventional 6T SRAM Cell at 45nm Technology
 Static-Noise-Margin Analysis of Conventional 6T SRAM Cell at 45nm Technology Nahid Rahman Department of electronics and communication FET-MITS (Deemed university), Lakshmangarh, India B. P. Singh Department
Static-Noise-Margin Analysis of Conventional 6T SRAM Cell at 45nm Technology Nahid Rahman Department of electronics and communication FET-MITS (Deemed university), Lakshmangarh, India B. P. Singh Department
Module 2. Embedded Processors and Memory. Version 2 EE IIT, Kharagpur 1
 Module 2 Embedded Processors and Memory Version 2 EE IIT, Kharagpur 1 Lesson 5 Memory-I Version 2 EE IIT, Kharagpur 2 Instructional Objectives After going through this lesson the student would Pre-Requisite
Module 2 Embedded Processors and Memory Version 2 EE IIT, Kharagpur 1 Lesson 5 Memory-I Version 2 EE IIT, Kharagpur 2 Instructional Objectives After going through this lesson the student would Pre-Requisite
Implementation and Design of AES S-Box on FPGA
 International Journal of Research in Engineering and Science (IJRES) ISSN (Online): 232-9364, ISSN (Print): 232-9356 Volume 3 Issue ǁ Jan. 25 ǁ PP.9-4 Implementation and Design of AES S-Box on FPGA Chandrasekhar
International Journal of Research in Engineering and Science (IJRES) ISSN (Online): 232-9364, ISSN (Print): 232-9356 Volume 3 Issue ǁ Jan. 25 ǁ PP.9-4 Implementation and Design of AES S-Box on FPGA Chandrasekhar
9/14/2011 14.9.2011 8:38
 Algorithms and Implementation Platforms for Wireless Communications TLT-9706/ TKT-9636 (Seminar Course) BASICS OF FIELD PROGRAMMABLE GATE ARRAYS Waqar Hussain firstname.lastname@tut.fi Department of Computer
Algorithms and Implementation Platforms for Wireless Communications TLT-9706/ TKT-9636 (Seminar Course) BASICS OF FIELD PROGRAMMABLE GATE ARRAYS Waqar Hussain firstname.lastname@tut.fi Department of Computer
Chapter 2 Logic Gates and Introduction to Computer Architecture
 Chapter 2 Logic Gates and Introduction to Computer Architecture 2.1 Introduction The basic components of an Integrated Circuit (IC) is logic gates which made of transistors, in digital system there are
Chapter 2 Logic Gates and Introduction to Computer Architecture 2.1 Introduction The basic components of an Integrated Circuit (IC) is logic gates which made of transistors, in digital system there are
What Types of ECC Should Be Used on Flash Memory?
 What Types of ECC Should Be Used on Flash Memory? Application 1. Abstract NOR Flash normally does not need ECC (Error-Correcting Code). On the other hand, NAND requires ECC to ensure data integrity. NAND
What Types of ECC Should Be Used on Flash Memory? Application 1. Abstract NOR Flash normally does not need ECC (Error-Correcting Code). On the other hand, NAND requires ECC to ensure data integrity. NAND
Design and FPGA Implementation of a Novel Square Root Evaluator based on Vedic Mathematics
 International Journal of Information & Computation Technology. ISSN 0974-2239 Volume 4, Number 15 (2014), pp. 1531-1537 International Research Publications House http://www. irphouse.com Design and FPGA
International Journal of Information & Computation Technology. ISSN 0974-2239 Volume 4, Number 15 (2014), pp. 1531-1537 International Research Publications House http://www. irphouse.com Design and FPGA
NEW adder cells are useful for designing larger circuits despite increase in transistor count by four per cell.
 CHAPTER 4 THE ADDER The adder is one of the most critical components of a processor, as it is used in the Arithmetic Logic Unit (ALU), in the floating-point unit and for address generation in case of cache
CHAPTER 4 THE ADDER The adder is one of the most critical components of a processor, as it is used in the Arithmetic Logic Unit (ALU), in the floating-point unit and for address generation in case of cache
ETEC 2301 Programmable Logic Devices. Chapter 10 Counters. Shawnee State University Department of Industrial and Engineering Technologies
 ETEC 2301 Programmable Logic Devices Chapter 10 Counters Shawnee State University Department of Industrial and Engineering Technologies Copyright 2007 by Janna B. Gallaher Asynchronous Counter Operation
ETEC 2301 Programmable Logic Devices Chapter 10 Counters Shawnee State University Department of Industrial and Engineering Technologies Copyright 2007 by Janna B. Gallaher Asynchronous Counter Operation
1. True or False? A voltage level in the range 0 to 2 volts is interpreted as a binary 1.
 File: chap04, Chapter 04 1. True or False? A voltage level in the range 0 to 2 volts is interpreted as a binary 1. 2. True or False? A gate is a device that accepts a single input signal and produces one
File: chap04, Chapter 04 1. True or False? A voltage level in the range 0 to 2 volts is interpreted as a binary 1. 2. True or False? A gate is a device that accepts a single input signal and produces one
Improved NAND Flash Memories Storage Reliablity Using Nonlinear Multi Error Correction Codes
 Advance in Electronic and Electric Engineering. ISSN 2231-1297, Volume 3, Number 9 (2013), pp. 1121-1134 Research India Publications http://www.ripublication.com/aeee.htm Improved NAND Flash Memories Storage
Advance in Electronic and Electric Engineering. ISSN 2231-1297, Volume 3, Number 9 (2013), pp. 1121-1134 Research India Publications http://www.ripublication.com/aeee.htm Improved NAND Flash Memories Storage
FPGA Implementation of an Advanced Traffic Light Controller using Verilog HDL
 FPGA Implementation of an Advanced Traffic Light Controller using Verilog HDL B. Dilip, Y. Alekhya, P. Divya Bharathi Abstract Traffic lights are the signaling devices used to manage traffic on multi-way
FPGA Implementation of an Advanced Traffic Light Controller using Verilog HDL B. Dilip, Y. Alekhya, P. Divya Bharathi Abstract Traffic lights are the signaling devices used to manage traffic on multi-way
Implementation Details
 LEON3-FT Processor System Scan-I/F FT FT Add-on Add-on 2 2 kbyte kbyte I- I- Cache Cache Scan Scan Test Test UART UART 0 0 UART UART 1 1 Serial 0 Serial 1 EJTAG LEON_3FT LEON_3FT Core Core 8 Reg. Windows
LEON3-FT Processor System Scan-I/F FT FT Add-on Add-on 2 2 kbyte kbyte I- I- Cache Cache Scan Scan Test Test UART UART 0 0 UART UART 1 1 Serial 0 Serial 1 EJTAG LEON_3FT LEON_3FT Core Core 8 Reg. Windows
Lecture 5: Gate Logic Logic Optimization
 Lecture 5: Gate Logic Logic Optimization MAH, AEN EE271 Lecture 5 1 Overview Reading McCluskey, Logic Design Principles- or any text in boolean algebra Introduction We could design at the level of irsim
Lecture 5: Gate Logic Logic Optimization MAH, AEN EE271 Lecture 5 1 Overview Reading McCluskey, Logic Design Principles- or any text in boolean algebra Introduction We could design at the level of irsim
Use of Reprogrammable FPGA on EUCLID mission
 19/05/2016 Workshop su Applicazioni FPGA in ambito Astrofisico Raoul Grimoldi Use of Reprogrammable FPGA on EUCLID mission Euclid mission overview EUCLID is a cosmology mission part of Cosmic Vision 2015-2025
19/05/2016 Workshop su Applicazioni FPGA in ambito Astrofisico Raoul Grimoldi Use of Reprogrammable FPGA on EUCLID mission Euclid mission overview EUCLID is a cosmology mission part of Cosmic Vision 2015-2025
Counters and Decoders
 Physics 3330 Experiment #10 Fall 1999 Purpose Counters and Decoders In this experiment, you will design and construct a 4-bit ripple-through decade counter with a decimal read-out display. Such a counter
Physics 3330 Experiment #10 Fall 1999 Purpose Counters and Decoders In this experiment, you will design and construct a 4-bit ripple-through decade counter with a decimal read-out display. Such a counter
Sequential 4-bit Adder Design Report
 UNIVERSITY OF WATERLOO Faculty of Engineering E&CE 438: Digital Integrated Circuits Sequential 4-bit Adder Design Report Prepared by: Ian Hung (ixxxxxx), 99XXXXXX Annette Lo (axxxxxx), 99XXXXXX Pamela
UNIVERSITY OF WATERLOO Faculty of Engineering E&CE 438: Digital Integrated Circuits Sequential 4-bit Adder Design Report Prepared by: Ian Hung (ixxxxxx), 99XXXXXX Annette Lo (axxxxxx), 99XXXXXX Pamela
Latch Timing Parameters. Flip-flop Timing Parameters. Typical Clock System. Clocking Overhead
 Clock - key to synchronous systems Topic 7 Clocking Strategies in VLSI Systems Peter Cheung Department of Electrical & Electronic Engineering Imperial College London Clocks help the design of FSM where
Clock - key to synchronous systems Topic 7 Clocking Strategies in VLSI Systems Peter Cheung Department of Electrical & Electronic Engineering Imperial College London Clocks help the design of FSM where
路 論 Chapter 15 System-Level Physical Design
 Introduction to VLSI Circuits and Systems 路 論 Chapter 15 System-Level Physical Design Dept. of Electronic Engineering National Chin-Yi University of Technology Fall 2007 Outline Clocked Flip-flops CMOS
Introduction to VLSI Circuits and Systems 路 論 Chapter 15 System-Level Physical Design Dept. of Electronic Engineering National Chin-Yi University of Technology Fall 2007 Outline Clocked Flip-flops CMOS
Enhancing High-Speed Telecommunications Networks with FEC
 White Paper Enhancing High-Speed Telecommunications Networks with FEC As the demand for high-bandwidth telecommunications channels increases, service providers and equipment manufacturers must deliver
White Paper Enhancing High-Speed Telecommunications Networks with FEC As the demand for high-bandwidth telecommunications channels increases, service providers and equipment manufacturers must deliver
International Journal of Electronics and Computer Science Engineering 1482
 International Journal of Electronics and Computer Science Engineering 1482 Available Online at www.ijecse.org ISSN- 2277-1956 Behavioral Analysis of Different ALU Architectures G.V.V.S.R.Krishna Assistant
International Journal of Electronics and Computer Science Engineering 1482 Available Online at www.ijecse.org ISSN- 2277-1956 Behavioral Analysis of Different ALU Architectures G.V.V.S.R.Krishna Assistant
150127-Microprocessor & Assembly Language
 Chapter 3 Z80 Microprocessor Architecture The Z 80 is one of the most talented 8 bit microprocessors, and many microprocessor-based systems are designed around the Z80. The Z80 microprocessor needs an
Chapter 3 Z80 Microprocessor Architecture The Z 80 is one of the most talented 8 bit microprocessors, and many microprocessor-based systems are designed around the Z80. The Z80 microprocessor needs an
Memory Basics. SRAM/DRAM Basics
 Memory Basics RAM: Random Access Memory historically defined as memory array with individual bit access refers to memory with both Read and Write capabilities ROM: Read Only Memory no capabilities for
Memory Basics RAM: Random Access Memory historically defined as memory array with individual bit access refers to memory with both Read and Write capabilities ROM: Read Only Memory no capabilities for
Modeling Sequential Elements with Verilog. Prof. Chien-Nan Liu TEL: 03-4227151 ext:34534 Email: jimmy@ee.ncu.edu.tw. Sequential Circuit
 Modeling Sequential Elements with Verilog Prof. Chien-Nan Liu TEL: 03-4227151 ext:34534 Email: jimmy@ee.ncu.edu.tw 4-1 Sequential Circuit Outputs are functions of inputs and present states of storage elements
Modeling Sequential Elements with Verilog Prof. Chien-Nan Liu TEL: 03-4227151 ext:34534 Email: jimmy@ee.ncu.edu.tw 4-1 Sequential Circuit Outputs are functions of inputs and present states of storage elements
DESIGN CHALLENGES OF TECHNOLOGY SCALING
 DESIGN CHALLENGES OF TECHNOLOGY SCALING IS PROCESS TECHNOLOGY MEETING THE GOALS PREDICTED BY SCALING THEORY? AN ANALYSIS OF MICROPROCESSOR PERFORMANCE, TRANSISTOR DENSITY, AND POWER TRENDS THROUGH SUCCESSIVE
DESIGN CHALLENGES OF TECHNOLOGY SCALING IS PROCESS TECHNOLOGY MEETING THE GOALS PREDICTED BY SCALING THEORY? AN ANALYSIS OF MICROPROCESSOR PERFORMANCE, TRANSISTOR DENSITY, AND POWER TRENDS THROUGH SUCCESSIVE
Digital Systems Based on Principles and Applications of Electrical Engineering/Rizzoni (McGraw Hill
 Digital Systems Based on Principles and Applications of Electrical Engineering/Rizzoni (McGraw Hill Objectives: Analyze the operation of sequential logic circuits. Understand the operation of digital counters.
Digital Systems Based on Principles and Applications of Electrical Engineering/Rizzoni (McGraw Hill Objectives: Analyze the operation of sequential logic circuits. Understand the operation of digital counters.
Spacecraft Computer Systems. Colonel John E. Keesee
 Spacecraft Computer Systems Colonel John E. Keesee Overview Spacecraft data processing requires microcomputers and interfaces that are functionally similar to desktop systems However, space systems require:
Spacecraft Computer Systems Colonel John E. Keesee Overview Spacecraft data processing requires microcomputers and interfaces that are functionally similar to desktop systems However, space systems require:
Optimising the resource utilisation in high-speed network intrusion detection systems.
 Optimising the resource utilisation in high-speed network intrusion detection systems. Gerald Tripp www.kent.ac.uk Network intrusion detection Network intrusion detection systems are provided to detect
Optimising the resource utilisation in high-speed network intrusion detection systems. Gerald Tripp www.kent.ac.uk Network intrusion detection Network intrusion detection systems are provided to detect
Homework # 2. Solutions. 4.1 What are the differences among sequential access, direct access, and random access?
 ECE337 / CS341, Fall 2005 Introduction to Computer Architecture and Organization Instructor: Victor Manuel Murray Herrera Date assigned: 09/19/05, 05:00 PM Due back: 09/30/05, 8:00 AM Homework # 2 Solutions
ECE337 / CS341, Fall 2005 Introduction to Computer Architecture and Organization Instructor: Victor Manuel Murray Herrera Date assigned: 09/19/05, 05:00 PM Due back: 09/30/05, 8:00 AM Homework # 2 Solutions
SOCWIRE: A SPACEWIRE INSPIRED FAULT TOLERANT NETWORK-ON-CHIP FOR RECONFIGURABLE SYSTEM-ON-CHIP DESIGNS
 SOCWIRE: A SPACEWIRE INSPIRED FAULT TOLERANT NETWORK-ON-CHIP FOR RECONFIGURABLE SYSTEM-ON-CHIP DESIGNS IN SPACE APPLICATIONS Session: Networks and Protocols Long Paper B. Osterloh, H. Michalik, B. Fiethe
SOCWIRE: A SPACEWIRE INSPIRED FAULT TOLERANT NETWORK-ON-CHIP FOR RECONFIGURABLE SYSTEM-ON-CHIP DESIGNS IN SPACE APPLICATIONS Session: Networks and Protocols Long Paper B. Osterloh, H. Michalik, B. Fiethe
FAULT TOLERANCE FOR MULTIPROCESSOR SYSTEMS VIA TIME REDUNDANT TASK SCHEDULING
 FAULT TOLERANCE FOR MULTIPROCESSOR SYSTEMS VIA TIME REDUNDANT TASK SCHEDULING Hussain Al-Asaad and Alireza Sarvi Department of Electrical & Computer Engineering University of California Davis, CA, U.S.A.
FAULT TOLERANCE FOR MULTIPROCESSOR SYSTEMS VIA TIME REDUNDANT TASK SCHEDULING Hussain Al-Asaad and Alireza Sarvi Department of Electrical & Computer Engineering University of California Davis, CA, U.S.A.
Upon completion of unit 1.1, students will be able to
 Upon completion of unit 1.1, students will be able to 1. Demonstrate safety of the individual, class, and overall environment of the classroom/laboratory, and understand that electricity, even at the nominal
Upon completion of unit 1.1, students will be able to 1. Demonstrate safety of the individual, class, and overall environment of the classroom/laboratory, and understand that electricity, even at the nominal
Let s put together a Manual Processor
 Lecture 14 Let s put together a Manual Processor Hardware Lecture 14 Slide 1 The processor Inside every computer there is at least one processor which can take an instruction, some operands and produce
Lecture 14 Let s put together a Manual Processor Hardware Lecture 14 Slide 1 The processor Inside every computer there is at least one processor which can take an instruction, some operands and produce
Chapter 1: Digital Systems and Binary Numbers
 Chapter 1: Digital Systems and Binary Numbers Digital age and information age Digital computers general purposes many scientific, industrial and commercial applications Digital systems telephone switching
Chapter 1: Digital Systems and Binary Numbers Digital age and information age Digital computers general purposes many scientific, industrial and commercial applications Digital systems telephone switching
Computer Architecture
 Computer Architecture Random Access Memory Technologies 2015. április 2. Budapest Gábor Horváth associate professor BUTE Dept. Of Networked Systems and Services ghorvath@hit.bme.hu 2 Storing data Possible
Computer Architecture Random Access Memory Technologies 2015. április 2. Budapest Gábor Horváth associate professor BUTE Dept. Of Networked Systems and Services ghorvath@hit.bme.hu 2 Storing data Possible
DEVELOPMENT OF DEVICES AND METHODS FOR PHASE AND AC LINEARITY MEASUREMENTS IN DIGITIZERS
 DEVELOPMENT OF DEVICES AND METHODS FOR PHASE AND AC LINEARITY MEASUREMENTS IN DIGITIZERS U. Pogliano, B. Trinchera, G.C. Bosco and D. Serazio INRIM Istituto Nazionale di Ricerca Metrologica Torino (Italia)
DEVELOPMENT OF DEVICES AND METHODS FOR PHASE AND AC LINEARITY MEASUREMENTS IN DIGITIZERS U. Pogliano, B. Trinchera, G.C. Bosco and D. Serazio INRIM Istituto Nazionale di Ricerca Metrologica Torino (Italia)
Lab 1: Introduction to Xilinx ISE Tutorial
 Lab 1: Introduction to Xilinx ISE Tutorial This tutorial will introduce the reader to the Xilinx ISE software. Stepby-step instructions will be given to guide the reader through generating a project, creating
Lab 1: Introduction to Xilinx ISE Tutorial This tutorial will introduce the reader to the Xilinx ISE software. Stepby-step instructions will be given to guide the reader through generating a project, creating
Programming Logic controllers
 Programming Logic controllers Programmable Logic Controller (PLC) is a microprocessor based system that uses programmable memory to store instructions and implement functions such as logic, sequencing,
Programming Logic controllers Programmable Logic Controller (PLC) is a microprocessor based system that uses programmable memory to store instructions and implement functions such as logic, sequencing,
DDR4 Memory Technology on HP Z Workstations
 Technical white paper DDR4 Memory Technology on HP Z Workstations DDR4 is the latest memory technology available for main memory on mobile, desktops, workstations, and server computers. DDR stands for
Technical white paper DDR4 Memory Technology on HP Z Workstations DDR4 is the latest memory technology available for main memory on mobile, desktops, workstations, and server computers. DDR stands for
Experiment # 9. Clock generator circuits & Counters. Eng. Waleed Y. Mousa
 Experiment # 9 Clock generator circuits & Counters Eng. Waleed Y. Mousa 1. Objectives: 1. Understanding the principles and construction of Clock generator. 2. To be familiar with clock pulse generation
Experiment # 9 Clock generator circuits & Counters Eng. Waleed Y. Mousa 1. Objectives: 1. Understanding the principles and construction of Clock generator. 2. To be familiar with clock pulse generation
ECE410 Design Project Spring 2008 Design and Characterization of a CMOS 8-bit Microprocessor Data Path
 ECE410 Design Project Spring 2008 Design and Characterization of a CMOS 8-bit Microprocessor Data Path Project Summary This project involves the schematic and layout design of an 8-bit microprocessor data
ECE410 Design Project Spring 2008 Design and Characterization of a CMOS 8-bit Microprocessor Data Path Project Summary This project involves the schematic and layout design of an 8-bit microprocessor data
Memory. The memory types currently in common usage are:
 ory ory is the third key component of a microprocessor-based system (besides the CPU and I/O devices). More specifically, the primary storage directly addressed by the CPU is referred to as main memory
ory ory is the third key component of a microprocessor-based system (besides the CPU and I/O devices). More specifically, the primary storage directly addressed by the CPU is referred to as main memory
Memory Systems. Static Random Access Memory (SRAM) Cell
 Memory Systems This chapter begins the discussion of memory systems from the implementation of a single bit. The architecture of memory chips is then constructed using arrays of bit implementations coupled
Memory Systems This chapter begins the discussion of memory systems from the implementation of a single bit. The architecture of memory chips is then constructed using arrays of bit implementations coupled
MICROPROCESSOR. Exclusive for IACE Students www.iace.co.in iacehyd.blogspot.in Ph: 9700077455/422 Page 1
 MICROPROCESSOR A microprocessor incorporates the functions of a computer s central processing unit (CPU) on a single Integrated (IC), or at most a few integrated circuit. It is a multipurpose, programmable
MICROPROCESSOR A microprocessor incorporates the functions of a computer s central processing unit (CPU) on a single Integrated (IC), or at most a few integrated circuit. It is a multipurpose, programmable
A Parallel Processor for Distributed Genetic Algorithm with Redundant Binary Number
 A Parallel Processor for Distributed Genetic Algorithm with Redundant Binary Number 1 Tomohiro KAMIMURA, 2 Akinori KANASUGI 1 Department of Electronics, Tokyo Denki University, 07ee055@ms.dendai.ac.jp
A Parallel Processor for Distributed Genetic Algorithm with Redundant Binary Number 1 Tomohiro KAMIMURA, 2 Akinori KANASUGI 1 Department of Electronics, Tokyo Denki University, 07ee055@ms.dendai.ac.jp
Technical Note. Micron NAND Flash Controller via Xilinx Spartan -3 FPGA. Overview. TN-29-06: NAND Flash Controller on Spartan-3 Overview
 Technical Note TN-29-06: NAND Flash Controller on Spartan-3 Overview Micron NAND Flash Controller via Xilinx Spartan -3 FPGA Overview As mobile product capabilities continue to expand, so does the demand
Technical Note TN-29-06: NAND Flash Controller on Spartan-3 Overview Micron NAND Flash Controller via Xilinx Spartan -3 FPGA Overview As mobile product capabilities continue to expand, so does the demand
Lecture-3 MEMORY: Development of Memory:
 Lecture-3 MEMORY: It is a storage device. It stores program data and the results. There are two kind of memories; semiconductor memories & magnetic memories. Semiconductor memories are faster, smaller,
Lecture-3 MEMORY: It is a storage device. It stores program data and the results. There are two kind of memories; semiconductor memories & magnetic memories. Semiconductor memories are faster, smaller,
Digital Electronics Detailed Outline
 Digital Electronics Detailed Outline Unit 1: Fundamentals of Analog and Digital Electronics (32 Total Days) Lesson 1.1: Foundations and the Board Game Counter (9 days) 1. Safety is an important concept
Digital Electronics Detailed Outline Unit 1: Fundamentals of Analog and Digital Electronics (32 Total Days) Lesson 1.1: Foundations and the Board Game Counter (9 days) 1. Safety is an important concept
Trends in NAND Flash Memory Error Correction
 Trends in NAND Flash Memory Error Correction June 2009 Eric Deal Cyclic Design Introduction NAND Flash is a popular storage media because of its ruggedness, power efficiency, and storage capacity. Flash
Trends in NAND Flash Memory Error Correction June 2009 Eric Deal Cyclic Design Introduction NAND Flash is a popular storage media because of its ruggedness, power efficiency, and storage capacity. Flash
RAPID PROTOTYPING OF DIGITAL SYSTEMS Second Edition
 RAPID PROTOTYPING OF DIGITAL SYSTEMS Second Edition A Tutorial Approach James O. Hamblen Georgia Institute of Technology Michael D. Furman Georgia Institute of Technology KLUWER ACADEMIC PUBLISHERS Boston
RAPID PROTOTYPING OF DIGITAL SYSTEMS Second Edition A Tutorial Approach James O. Hamblen Georgia Institute of Technology Michael D. Furman Georgia Institute of Technology KLUWER ACADEMIC PUBLISHERS Boston
COMBINATIONAL and SEQUENTIAL LOGIC CIRCUITS Hardware implementation and software design
 PH-315 COMINATIONAL and SEUENTIAL LOGIC CIRCUITS Hardware implementation and software design A La Rosa I PURPOSE: To familiarize with combinational and sequential logic circuits Combinational circuits
PH-315 COMINATIONAL and SEUENTIAL LOGIC CIRCUITS Hardware implementation and software design A La Rosa I PURPOSE: To familiarize with combinational and sequential logic circuits Combinational circuits
Manchester Encoder-Decoder for Xilinx CPLDs
 Application Note: CoolRunner CPLDs R XAPP339 (v.3) October, 22 Manchester Encoder-Decoder for Xilinx CPLDs Summary This application note provides a functional description of VHDL and Verilog source code
Application Note: CoolRunner CPLDs R XAPP339 (v.3) October, 22 Manchester Encoder-Decoder for Xilinx CPLDs Summary This application note provides a functional description of VHDL and Verilog source code
Implementing a Digital Answering Machine with a High-Speed 8-Bit Microcontroller
 Implementing a Digital Answering Machine with a High-Speed 8-Bit Microcontroller Zafar Ullah Senior Application Engineer Scenix Semiconductor Inc. Leo Petropoulos Application Manager Invox TEchnology 1.0
Implementing a Digital Answering Machine with a High-Speed 8-Bit Microcontroller Zafar Ullah Senior Application Engineer Scenix Semiconductor Inc. Leo Petropoulos Application Manager Invox TEchnology 1.0
Aims and Objectives. E 3.05 Digital System Design. Course Syllabus. Course Syllabus (1) Programmable Logic
 Aims and Objectives E 3.05 Digital System Design Peter Cheung Department of Electrical & Electronic Engineering Imperial College London URL: www.ee.ic.ac.uk/pcheung/ E-mail: p.cheung@ic.ac.uk How to go
Aims and Objectives E 3.05 Digital System Design Peter Cheung Department of Electrical & Electronic Engineering Imperial College London URL: www.ee.ic.ac.uk/pcheung/ E-mail: p.cheung@ic.ac.uk How to go
Layout of Multiple Cells
 Layout of Multiple Cells Beyond the primitive tier primitives add instances of primitives add additional transistors if necessary add substrate/well contacts (plugs) add additional polygons where needed
Layout of Multiple Cells Beyond the primitive tier primitives add instances of primitives add additional transistors if necessary add substrate/well contacts (plugs) add additional polygons where needed
A Practical Parallel CRC Generation Method
 F EATURE ARTICLE by Evgeni Stavinov A Practical Parallel CRC Generation Method Do you understand the mechanics of the cyclic redundancy check (CRC) well enough to build a customized parallel CRC circuit
F EATURE ARTICLE by Evgeni Stavinov A Practical Parallel CRC Generation Method Do you understand the mechanics of the cyclic redundancy check (CRC) well enough to build a customized parallel CRC circuit
Latches, the D Flip-Flop & Counter Design. ECE 152A Winter 2012
 Latches, the D Flip-Flop & Counter Design ECE 52A Winter 22 Reading Assignment Brown and Vranesic 7 Flip-Flops, Registers, Counters and a Simple Processor 7. Basic Latch 7.2 Gated SR Latch 7.2. Gated SR
Latches, the D Flip-Flop & Counter Design ECE 52A Winter 22 Reading Assignment Brown and Vranesic 7 Flip-Flops, Registers, Counters and a Simple Processor 7. Basic Latch 7.2 Gated SR Latch 7.2. Gated SR
3.Basic Gate Combinations
 3.Basic Gate Combinations 3.1 TTL NAND Gate In logic circuits transistors play the role of switches. For those in the TTL gate the conducting state (on) occurs when the baseemmiter signal is high, and
3.Basic Gate Combinations 3.1 TTL NAND Gate In logic circuits transistors play the role of switches. For those in the TTL gate the conducting state (on) occurs when the baseemmiter signal is high, and
AC 2007-2485: PRACTICAL DESIGN PROJECTS UTILIZING COMPLEX PROGRAMMABLE LOGIC DEVICES (CPLD)
 AC 2007-2485: PRACTICAL DESIGN PROJECTS UTILIZING COMPLEX PROGRAMMABLE LOGIC DEVICES (CPLD) Samuel Lakeou, University of the District of Columbia Samuel Lakeou received a BSEE (1974) and a MSEE (1976)
AC 2007-2485: PRACTICAL DESIGN PROJECTS UTILIZING COMPLEX PROGRAMMABLE LOGIC DEVICES (CPLD) Samuel Lakeou, University of the District of Columbia Samuel Lakeou received a BSEE (1974) and a MSEE (1976)
Distributed Storage Networks and Computer Forensics
 Distributed Storage Networks 5 Raid-6 Encoding Technical Faculty Winter Semester 2011/12 RAID Redundant Array of Independent Disks Patterson, Gibson, Katz, A Case for Redundant Array of Inexpensive Disks,
Distributed Storage Networks 5 Raid-6 Encoding Technical Faculty Winter Semester 2011/12 RAID Redundant Array of Independent Disks Patterson, Gibson, Katz, A Case for Redundant Array of Inexpensive Disks,
Implementation of Full -Parallelism AES Encryption and Decryption
 Implementation of Full -Parallelism AES Encryption and Decryption M.Anto Merline M.E-Commuication Systems, ECE Department K.Ramakrishnan College of Engineering-Samayapuram, Trichy. Abstract-Advanced Encryption
Implementation of Full -Parallelism AES Encryption and Decryption M.Anto Merline M.E-Commuication Systems, ECE Department K.Ramakrishnan College of Engineering-Samayapuram, Trichy. Abstract-Advanced Encryption
Switch Fabric Implementation Using Shared Memory
 Order this document by /D Switch Fabric Implementation Using Shared Memory Prepared by: Lakshmi Mandyam and B. Kinney INTRODUCTION Whether it be for the World Wide Web or for an intra office network, today
Order this document by /D Switch Fabric Implementation Using Shared Memory Prepared by: Lakshmi Mandyam and B. Kinney INTRODUCTION Whether it be for the World Wide Web or for an intra office network, today
Selective SWIFT-R. A flexible software-based technique for soft error mitigation in low-cost embedded systems
 Journal of Electronic Testing manuscript No. (will be inserted by the editor) Selective SWIFT-R A flexible software-based technique for soft error mitigation in low-cost embedded systems Felipe Restrepo-Calle
Journal of Electronic Testing manuscript No. (will be inserted by the editor) Selective SWIFT-R A flexible software-based technique for soft error mitigation in low-cost embedded systems Felipe Restrepo-Calle
Algorithms and Methods for Distributed Storage Networks 5 Raid-6 Encoding Christian Schindelhauer
 Algorithms and Methods for Distributed Storage Networks 5 Raid-6 Encoding Institut für Informatik Wintersemester 2007/08 RAID Redundant Array of Independent Disks Patterson, Gibson, Katz, A Case for Redundant
Algorithms and Methods for Distributed Storage Networks 5 Raid-6 Encoding Institut für Informatik Wintersemester 2007/08 RAID Redundant Array of Independent Disks Patterson, Gibson, Katz, A Case for Redundant
A Novel Low Power Fault Tolerant Full Adder for Deep Submicron Technology
 International Journal of Computer Sciences and Engineering Open Access Research Paper Volume-4, Issue-1 E-ISSN: 2347-2693 A Novel Low Power Fault Tolerant Full Adder for Deep Submicron Technology Zahra
International Journal of Computer Sciences and Engineering Open Access Research Paper Volume-4, Issue-1 E-ISSN: 2347-2693 A Novel Low Power Fault Tolerant Full Adder for Deep Submicron Technology Zahra
A Computer Vision System on a Chip: a case study from the automotive domain
 A Computer Vision System on a Chip: a case study from the automotive domain Gideon P. Stein Elchanan Rushinek Gaby Hayun Amnon Shashua Mobileye Vision Technologies Ltd. Hebrew University Jerusalem, Israel
A Computer Vision System on a Chip: a case study from the automotive domain Gideon P. Stein Elchanan Rushinek Gaby Hayun Amnon Shashua Mobileye Vision Technologies Ltd. Hebrew University Jerusalem, Israel
ISSCC 2003 / SESSION 13 / 40Gb/s COMMUNICATION ICS / PAPER 13.7
 ISSCC 2003 / SESSION 13 / 40Gb/s COMMUNICATION ICS / PAPER 13.7 13.7 A 40Gb/s Clock and Data Recovery Circuit in 0.18µm CMOS Technology Jri Lee, Behzad Razavi University of California, Los Angeles, CA
ISSCC 2003 / SESSION 13 / 40Gb/s COMMUNICATION ICS / PAPER 13.7 13.7 A 40Gb/s Clock and Data Recovery Circuit in 0.18µm CMOS Technology Jri Lee, Behzad Razavi University of California, Los Angeles, CA
Lab 1: Full Adder 0.0
 Lab 1: Full Adder 0.0 Introduction In this lab you will design a simple digital circuit called a full adder. You will then use logic gates to draw a schematic for the circuit. Finally, you will verify
Lab 1: Full Adder 0.0 Introduction In this lab you will design a simple digital circuit called a full adder. You will then use logic gates to draw a schematic for the circuit. Finally, you will verify
Having read this workbook you should be able to: recognise the arrangement of NAND gates used to form an S-R flip-flop.
 Objectives Having read this workbook you should be able to: recognise the arrangement of NAND gates used to form an S-R flip-flop. describe how such a flip-flop can be SET and RESET. describe the disadvantage
Objectives Having read this workbook you should be able to: recognise the arrangement of NAND gates used to form an S-R flip-flop. describe how such a flip-flop can be SET and RESET. describe the disadvantage
what operations can it perform? how does it perform them? on what kind of data? where are instructions and data stored?
 Inside the CPU how does the CPU work? what operations can it perform? how does it perform them? on what kind of data? where are instructions and data stored? some short, boring programs to illustrate the
Inside the CPU how does the CPU work? what operations can it perform? how does it perform them? on what kind of data? where are instructions and data stored? some short, boring programs to illustrate the
A Novel Low Power, High Speed 14 Transistor CMOS Full Adder Cell with 50% Improvement in Threshold Loss Problem
 A Novel Low Power, High Speed 4 Transistor CMOS Full Adder Cell with 5% Improvement in Threshold Loss Problem T. Vigneswaran, B. Mukundhan, and P. Subbarami Reddy Abstract Full adders are important components
A Novel Low Power, High Speed 4 Transistor CMOS Full Adder Cell with 5% Improvement in Threshold Loss Problem T. Vigneswaran, B. Mukundhan, and P. Subbarami Reddy Abstract Full adders are important components
Computer Architecture
 Computer Architecture Slide Sets WS 2013/2014 Prof. Dr. Uwe Brinkschulte M.Sc. Benjamin Betting Part 11 Memory Management Computer Architecture Part 11 page 1 of 44 Prof. Dr. Uwe Brinkschulte, M.Sc. Benjamin
Computer Architecture Slide Sets WS 2013/2014 Prof. Dr. Uwe Brinkschulte M.Sc. Benjamin Betting Part 11 Memory Management Computer Architecture Part 11 page 1 of 44 Prof. Dr. Uwe Brinkschulte, M.Sc. Benjamin
