Security Aspects on the Signaling and Data-Plane in 2G/3G Networks
|
|
|
- Brett Townsend
- 7 years ago
- Views:
Transcription
1 Diplomarbeit Security Aspects on the Signaling and Data-Plane in 2G/3G Networks ausgeführt zum Zwecke der Erlangung des akademischen Grades eines Diplom Ingenieurs unter der Leitung von Univ.Prof. Dipl.-Ing. Dr.techn Markus Rupp Dipl.-Ing. Dr.techn. Philipp Svoboda Institute of Telecommunications eingereicht an der Technischen Universität Wien Fakultät für Elektrotechnik und Informationstechnik von Elena Recas de Buen Wien, November 2011
2
3 Abstract In this work we present a deep analysis in nowadays security threads over mobile digital networks. The goal is to answer the question if there are any technical feasible implementations possible for these attacks. We base our study in 2G (GSM) and 3G (UMTS) networks. Therefore, as a first step we present the basics of 2G/3G networks, as well as their architectures, procedures and protocols. It is well known that GSM present different vulnerabilities, as standard xxx describes. UMTS overcomes some of these vulnerabilities, but new ones appear. In order to study the state of the art in 2G/3G security, we conduct a literature research on any form of known and published security threads. In general, all of the attacks analyzed make use of strong assumptions, like possession of a Base Station, which makes them less feasible to be implemented. There is though, some procedures utilizing non-authenticated messages that are more vulnerable to be used maliciously. One of them is the remote IMSI attack. This attack makes use of the detach procedure, which sends a single message to the Base Station. In order to prove the feasibility and impact of this attack, we make use of the OsmocomBB open source project which implements the GSM protocol stack on the air interface from physical layer to transport layer. Furthermore, to analyze the impact of the attack on a real network we design a simple model that allows us to simulate the attack. Due to the different results obtained from the tests done with the OsmocomBB code, we tweak our model with different parameters ii
4 iii in order to approach it to a real world scenario. Our simulations demonstrate indeed that there is a vulnerability of the network against this attack.
5 Acknowledgements It would not have been possible to write this Master Thesis without the help and support of the kind people around me, to some of whom it is possible to give particular mention here. First of all, I would like to thank Professor Markus Rupp for offering me the opportunity to work directly in a research environment. I really enjoyed these four years at the Institute of Telecommunications. Thanks to all my colleagues for making of this time a great experience. I am extremely grateful to my supervisor Dr Philipp Svoboda who gave me great advice and support. It was a great pleasure to have him by my side, academically and personally. I would also like to thank and recognize our industry partners Mobilkom Austria and ftw - Forschungszentrum Telekommunikation Wien, without whom this thesis would have not been possible to realize. In a more personal plane, I would like to thank my parents Rafael and Antonia, my sister Cristina and my friends in Spain, who even being far away always believed in me, and supported me. I cannot of course forget my second family, Miriam, Javi, Josep and Carolina, who helped me to feel at home. And last, but by no means least, I want to thank my boyfriend Erich who stayed by my side in all the moments, encouraged me and never let me to give up. It would have not been easy without his help. A todos, gracias! iv
6
7 Contents 1 Cellular mobile networks Global System for Mobile Communications (GSM) Radio Access Network Core network GPRS core network extension GSM protocol stack Universal Mobile Telecommunications System (UMTS) New devices: UMTS extension UMTS protocol stack Security aspects in cellular mobile networks Vulnerabilities of 2G/3G networks Classification of threads Target: user Target: core network Target: access network Measurement Setup: enabling access to GSM OsmocomBB project Compiling and running OsmocomBB Setup of the main scenario vi
8 CONTENTS vii 4 Verification and analysis of the remote IMSI drop attack Remote IMSI drop attack Implementation of the attack In-deep testing including core network protocol analysis Single MSC scenario Multiple MSC scenario Impact of the attack Modeling the impact of the attack Modeling with real user mobility Analysis of a real world scenario Summary and conclusions 53 A Motorola C List of Acronyms 65 List of Figures 66 List of Tables 68 Bibliography 73
9 Chapter 1 Cellular mobile networks In the late 1940s, the United States started offering mobile telephone service, i.e., car phone and it arrived to Europe in the early 1950s. These systems were highly constrained by low capacity, limited service and poor speech quality. These facts were the reason of a low number of subscribers. In the 1970s though, the number of subscribers increased due to the introduction of cellular systems. The development of Second Generation (2G) networks was driven by the need to increase transmission quality, system capacity and coverage. Nowadays, different standards exist which offer different applications with different levels of mobility, capability and service area. GSM is the most successful group of cellular networks standards, supporting some hundreds of millions of the world s 450 million cellular subscribers with international roaming. The first phase of the GSM900 standardisation was finished by the European Telecommunications Standards Institute (ETSI) in 1990, and it included all the definitions of GSM network procedures 1. In 1996, ETSI decided to enhance the standard and incorporated 3G capabilities. Some of these features are high-data services, General Packet Radio Service (GPRS) and Enhanced Data rates for GSM Evolution (EDGE). The 1 1
10 1.1. GSM 2 UMTS standard is the evolution of GSM, and is GSM-compatible using the enhanced GPRS core network. 1.1 GSM GSM [1] is an open standard, developed by ETSI for transmitting voice and data over digital cellular networks. It is part of the so called 2G networks and it consists on three parts, radio, access and core network. GSM radio technology is defined in the TS 45 series of the 3GPP, the network architecture in 3GPP TS [2], and there is a list of technical specifications in 3GPP TS [3]. As an evolution of the 2G networks, technologies like EDGE or UMTS appear, forming the well-known group of Third Generation (3G) networks. Equally as GSM, UMTS also consists of three parts. While UMTS shares some of the elements of the network with GSM, it also adds new elements (see Figure 1.1). In order to a gain of better understanding of the vulnerabilities that these networks present and to know which elements take part on each procedure, it is important to introduce the protocols and interfaces involved, as well as the main elements of the network Radio Access Network Radio Access Network (RAN) (Radio and Access network of Figure 1.1) is the part of the network enabling the radio link access. This subsystem consists of the following elements: Mobile Equipment (ME), Base Station Controller (BSC), Base Transceiver Station (BTS), Serving GPRS Support Node (SGSN), Visitor Location Register (VLR), Mobile Switching Center (MSC), Home Location Register (HLR), Gateway GPRS Support Node (GGSN), and the Gateway MSC (GMSC). The interfaces interconnecting these elements are: Abis, A and Gb. The main function of the Radio Access
11 1.1. GSM 3 SIM RNC Iub NodeB RNC IuPS Gn SGSN GGSN PS Domain Gs HLR/AuC CS Domain PS/IP PSTN Gc Gr C D E CORE NETWORK IuCS IuR Gb ME USIM UE ME UE Uu Abis RADIO NETWORK BTS BSC A ACCESS NETWORK MSC/VLR GMSC GSM UMTS Figure 1.1: Network architecture.
12 1.1. GSM 4 Network (RAN) is the transmission of the data over a wireless link. Mobile Equipment (ME) or Mobile Station (MS) The Mobile Station (MS) is the physical equipment (also called Mobile Equipment ME) used by a subscriber to connect to a GSM Public Land Mobile Network (PLMN) and access to the offered services by this network [1]. The features that a ME may implement are listed in the Table 1.1 included in [4]. The ME is formed by the Subscriber Identity Module (SIM), which contains the user identity, and the User Equipment (UE), that corresponds to the physical device, i.e. the hardware that should implement all the standards. A mobile station has several identities. The whole equipment is identified by an International Mobile Equipment Identity (IMEI) [5]. The IMEI is composed in such a way that every equipment is uniquely identified. The information included on the IMEI is used by the GSM PLMN to decide if the calls made by this equipment will be accepted or not. The structure of the IMEI is described in [6] and it is depicted in Figure 1.2. It is composed by four elements: 6 digits TAC 2 digits 6 digits 1 digit FAC SNR Spare 15 digits Figure 1.2: Structure of IMEI. Type Approval Code (TAC) Final Assembly Code (FAC): identification of the place of manufacture or assembly. Serial Number (SNR): individual serial number uniquely identifying each equipment within each TAC and FAC.
13 1.1. GSM 5 Name Display of Called Number Indication of Call Progress Signal Country/PLMN Indication Country/PLMN Selection Keypad IMEI Short Message Short Message Overflow Indication DTE/DCE Interface ISDN S Interface International Access Function ( + key) Service Indicator Autocalling restriction capabilities Emergency Calls capabilities Dual Tone Multi Frequency function (DMTF) Subscription Identity Management On/Off Switch Subaddress Support of Encryption A5/1 and A5/2 Short Message Service Cell Broadcast Short Message Service Cell Broadcast DRX Service Provider Indication Support of the extended SMS CB channel Support of Additional Call Set-up MMI Procedures Network Identity and Timezone Ciphering Indicator Network s indication of alerting in the MS Network initiated Mobile Originated connection Support of Localized Service Area Enhanced circuit switched data (ECSD) Enhanced general packet radio service (EGPRS) Mandatory (M) or Optional (O) M M M M O M M M O O O M M M M M O O M M O O O O O M O O O O O Table 1.1: Basic MS features [4].
14 1.1. GSM 6 Spare digit: it shall be zero, when transmitted by the MS. When referring to the subscriber, the identifier is the International Mobile Subscriber Identity (IMSI) [6] embedded in the SIM [7]. The structure of the IMSI is shown in Figure 1.3. It is composed by three parts: The Mobile Country Code (MCC) identifies uniquely the country of the mobile subscriber. The Mobile Network Code (MNC) identifies the home GSM PLMN of the mobile subscriber. The Mobile Subscriber Identification Number (MSIN) identifies the mobile subscriber within a GSM PLMN. The National Mobile Subscriber Identity (NMSI) consists of the MNC and the MSIN. No more than15 digits 3 digits MCC 2 digits MNC MSIN IMSI NMSI Figure 1.3: Structure of IMSI. Another identifier is the Temporal IMSI (TMSI). It has only local significance, as it is only valid withint a VLR and its area, or an SGSN and its area. The TMSI consists of four octets [8]. The SIM is a removable module part of the MS. The SIM is storage device for subscriber related information. The data stored can be of three different types: data fixed during administrative phase; e.g., IMSI, subscriber authentication key, access control class;
15 1.1. GSM 7 temproary network data; e.g., TMSI, Kc, Forbidden PLMNs; service related data; e.g., Language Preference, Advice of Charge. To provide protection against unauthorized use, it also contains Card Holder Verification Information. Base Station System (BSS) The Base Station System (BSS) is the physical equipment that gives radio coverage to a specific geographical zone named cell, and it communicates with the MS [1]. The BSS carries out functions like transcoding of speech channels, allocation of radio channels to mobile phones, paging, transmission and reception over the air interface and other tasks. These functions can be subdivided in two groups: controlling functions, and radio transmitting functions, they are respectively carried out by the Base Station Controller (BSC) and the Base Transceiver Station (BTS). The RAN consists basically of many BSSs, each of which holds a number of BTSs managed by the respective BSCs Core network The core network includes the GGSN, SGSN, MSC, VLR and HLR. These elements allow 2G and 3G access networks to transmit IP packets to external networks. It is part of the GSM switching network. The interfaces interconnecting the core network devices are: Gs, Gr, Gn, Gc, D, C, and E. The main functions are: providing mobility management, session management and transport for Internet Protocol (IP) packet services in GSM and UMTS networks.
16 1.1. GSM 8 Visitor Location Register (VLR) The Visitor Location Register is a database of subscribers who moved into the area corresponding to the related MSC or SGSN. The relation between Base Station (BS) and VLR is unique, therefore a subscriber cannot appear in more than one VLR at the same time. The data stored is obtained from the HLR. It includes the IMSI, the authentication keys, the MSISDN (subscriber s phone number), GSM services that the subsrciber is allowed to access, the access point subscribed and the HLR address of the subscriber. The VLR is also in charge of the roaming functions [1]. When a roaming mobile enters an MSC area, this MSC communicates with the correspondent VLR; the mobile must then starts a registration procedure and it is assigned a Mobile Subscriber Roaming Number (MSRN). This MSRN it is used to route the incoming calls to this mobile. To handle incoming or outgoing calls, VLR also contains other information: Mobile Station Roaming Number, the Temporary Mobile Subscriber Identity (TMSI), if applicable, the location area in which the mobile has been registered, and the data related to supplementary service parameters. Mobile Switching Center (MSC) The Mobile Switching Center (MSC) is a switching center that is charge of all the switching functions needed for mobiles located in an associated geographical area [1].An MSC takes into account each kind of user and manages the necessary radio resources. It pays special attention to these procedures required to handle and update the location registration procedure (GSM 03.12) and procedures to carry out handover (GSM 03.09). In practice, VLR and MSC are integrated in the same device as they are closely linked.
17 1.1. GSM 9 Home Location Register (HLR) The Home Location Register is a central database containing information of each mobile phone subscriber that is allowed to use the GSM core network of the operator. The number of users in a PLMN varies according to the characteristics of the PLMN itself. Any administrative action by the Network Operator on subscriber data is carried out in the HLR. Two types of basic information are stored in the HLR s database: Subscriber Information, and some location information allowing incoming calls to be routed to the MSC for the desired mobile. Details of every SIM card are also stored, such as the IMSI, the Mobile Station ISDN Number (MSISDN) or the VLR address. The IMSI is used as the primary key to each HLR record. The data stored at the HLR is kept as long as the user stays with the same operator. Other important data stored in the database are: GSM services requested by or given to the subscriber, the GPRS settings for packet services access, and the location of subscriber (VLR and SGSN). Authentication Center (AuC) The Authentication Center (AuC) is in charge of authenticating every user SIM card that wants to connect to the GSM network. As Figure 1.1 shows, it is normally placed in the HLR. After the authentication procedure is performed, and if this is successful, the HLR will service the SIM. An encryption key is generated and will be used to encrypt all following wireless communications between the mobile phone and the GSM mobile
18 1.1. GSM 10 network. In case of authentication failure, the user is not allowed to use any of the services offered by the operator (only emergency calls). In order to avoid SIM cloning, a proper security mechanism has to be build in and around the AuC. The AuC does not execute directly the authentication procedure but generates some data, known as triplets, used by the MSC when authenticating the user. This process is secured via a secret shared by the SIM and the AuC called Ki. This secret ( see Figure 1.4 ) is burned into the SIM during manufacturing and securely replicated to the AuC. It is of course never transmitted between the AuC and the SIM, but is used in combination with the IMSI to generate a challenge for identification purposes and an encryption key called Kc used over the air communications. SIM IMSI Ki AuC IMSI - Ki... Figure 1.4: Shared secret Ki between SIM and AuC. Gateway MSC (GMSC) When a network requests a call to the PLMN and cannot identify the HLR then the call is forwarded to the MSC. This MSC knows which is the appropriate HLR to be interrogated. Aferwards the call is routed to the MSC where the mobile station is located. The MSC that performs the routing function to the real location of the MS is called GMSC.
19 1.1. GSM GPRS core network extension The GPRS implements packet oriented data services for the GSM network. It represents the first step towards UMTS. With this extension, it is possible to communicate directly PS-data with the internet. Two functional units extend the GSM network for GPRS services: the SGSN and the GGSN. Serving GPRS Support Node (SGSN) The Serving GPRS Support Node has the responsibility of delivering data packets within its geographical service area. The location register function stores two types of subscriber data needed to handle originating and terminating packet data transfer [2]: subscription and location information. Subscription information: the IMSI; one or more temporary identities; zero or more Packet Data Protocol (PDP) addresses. Location information: depending on the operating mode of the MS, the cell or the routing area where the MS is registered; the number of the associated VLR; the GGSN address of each GGSN for which an active PDP context exists. Its functions are: GPRS mobility management (attach/detach and location management), GPRS session management, ciphering, charging, and data compression. The procedures for information transfer between the SGSN, the GGSN, the VLR and the HLR are defined in [9] and [10].
20 1.1. GSM 12 Gateway GPRS Support Node (GGSN) The Gateway GPRS Support Node is a main component of the network. It is in charge of interconnection between the GPRS network and external packet switched networks, i.e. Internet. The GGSN forwards the data coming from the external network to the SGSN only if the mobile user is active. If the user is inactive, the data is discarded. The GGSN is the element in the network that enables mobility of users through the GPRS/UMTS networks. The location register function in the GGSN stores susbcriber data received from the HLR and the SGSN that can be subdivided in subscription and location information. Subscription information: the IMSI; zero or more PDP addresses. Location information: the SGSN address for the SGSN where the MS is registered GSM protocol stack Figure 1.5 displays the GSM protocol stack and its three layers: the Call Management (CM) layer, the Mobility Management (MM) layer, and the Radio Resource (RR) layer. The CM layer is divided in three parts: the Call Control (CC), the Suplementary Service (SS) and the Short Message Service (SMS). The next layer is the so called Mobility Management, which terminates at the MSC. The functions provided by this layer are threefold: the MM specific procedures, the MM common procedures and the MM connection-related procedures. The MM connection related procedures are used to establish, maintain, and release a MM connection between
21 1.1. GSM 13 Mobile Station Base Transceiver Station Base Station Controller Mobile Switching Center CM CM Call Management MM MM Mobility Management RR RR BTSM BTSM BSSAP RR BSSAP Application Part LAPDm LAPDm LAPD LAPD SCCP SCCP TDMA TDMA PCM PCM MTP MTP Um Abis A Figure 1.5: GSM protocol stack. the MS and the network. The MM specific procedures include the location update, and the IMSI attach. The MM common procedures consist of IMSI detach, TMSI reallocation, and authentication/identification. The third layer is the RR Management layer, which finishes at the BSS. Its functions are: establishing physical connections over the radio and traffic channels between a specific mobile user and the BSS. These functions are implemented in the BSS. Physical and logical channels GSM relies on a Time Division Multiple Access (TDMA) transmission system. It only has one physical channel, subdidived in time slots, used to transport different logical information (logical channels). In GSM there are control and traffic channels. The Traffic Channels (TCH) are used to transport user data. On the other hand, Control Channels (CCH) are divided in three different channel types, each of them subdivided in four different channels. The Broadcast Control Channel (BCCH) broadcasts all the important information the
22 1.1. GSM 14 ME needs to attach to the cell. The BCCH features channels for frequency correction (Frequency Correction Channel (FCCH)) and time synchronization (Synchronization Channel (SC)). The Dedicated Control Channel (DCCH) is a bidirectional channel that can be used by the mobile to interact with the cell. The TCH is allocated via the Stand- Alone DCCH (SDCCH). The ME exchanges system data through the Slow Associated DCCH (SACCH). If there is need for high signaling bitrate, then the mobile can book an additional signaling channel, the Fast Associated DCCH (FACCH). If a BTS receives a call for a user, it broadcasts this information on the Paging Channel (PCH). A MS answering to this paging employs the Random Access CHannel (RACH). A successful connection will receive a free TCH via the Access Grant Channel (AGCH). Interfaces There are different interfaces connecting the nodes of the network. For each connection exists a different interface. The most important are the following: Abis: interface between the ME and the BSS. Gb: interface between the BSS and the SGSN. A: interface between the BSS and the MSC/VLR. Gs: interface between the SGSN and the MSC/VLR. Gr: interface between the SGSN and the HLR/AuC. D: interface between the MSC/VLR and the HLR/AuC. Gn: IP interface between SGSN and internal GGSNs. E: interface between the MSC/VLR and the GMSC. Gc: interface between the HLR/AuC and the GGSN. C: interface between the HLR/AuC and the GMSC.
23 1.2. UMTS UMTS UMTS is seen as the successor of GSM. Both networks have to coexist with each other, therefore, as Figure 1.1 shows, most of the elements of the GSM network are reused. UMTS addresses the growing demand of mobile and internet applications, as well as the transmission speed increase New devices: UMTS extension Figure 1.1 shows how the basic GSM network is enhanced by the GPRS network extension and also merged with the UMTS network by adding some elements to it. Both networks share the GPRS core network. On the RAN side, two new network elements are introduced, the Radio Network Controller (RNC) and the NodeB. Each RNC is connected to a set of NodeB s, each of which can serve one or several cells. Mobile Station (MS) or Mobile Equipment (ME) The UMTS MS is based on the same principles as the GSM MS. There is as well a separation between the UE and, in this case, the UMTS SIM (USIM) card. The main difference between SIM and USIM is that, the USIM is not a physical entity but a logical application that is placed on a Universal Integrated Circuit Card (UICC). It only accepts 3G commands, and it is not compatible with 2G MEs. Optionally, the USIM may provide mechanisms to support 2G authentication and key agreement, in order to allow a 3G ME to connect to a 2G network [11]. The UICC is just the physical and logical platform for the USIM application, and additionally also for a SIM application.
24 1.2. UMTS 16 NodeB The NodeB is the physical unit in charge of radio transmission/reception of cells. A single NodeB can support FDD and TDD modes. It connects with the UE via the Uu interface and with the RNC via the Iub interface, based on Asynchronous Transfer Mode (ATM), and recently also on Ethernet. Its main task is the conversion of data to and from the Uu radio interface. This task includes Forward Error Protection (FEC), rate matching, WCDMA spreading/despreading, and Quadrature Phase Shift Keying (QPSK) modulation on the air interface. Radio Network Controller (RNC) The Radio Network Controller enables autonomous radio resource management and performs similar functions as the BSC. It is, therefore, the main element in the access network. It is responsible for controlling all the Base Stations connected to it and performing some mobility management functions. It is the network point where the user data is encrypted before it is sent or received by the mobile equipment. The RNC inter-connects access and core network. It connects to the access network via Iub interface (to the Base Stations), and to the core network, via the Gb interface (to the VLR/MSC or the SGSN). The RNC is also connected to the Packet Switched (PS) domain, and to the Circuit Switched (CS) domain. Due to the fact that the interfaces are ATM-based, the RNC switches cells between them. User data coming from Iu-CS and Iu-PS interfaces are multiplexed together for multimedia transmission via Iur, Iub and Uu interfaces to and from the UE.
25 1.2. UMTS UMTS protocol stack UMTS is presented as a network offering a variety of different connections. The protocol stack depicted on Figure 1.6 shows therefore a different structure than the GSM protocol stack (1.5), and presents many new protocols. Some of them are well known, i.e. ATM, IP, others are new. For our study, only the relevant ones will be described: GTP and BSSGP. Mobile Station NodeB RNC SGSN / MSC CS / SM MM AMR... IP IP IP IP Non Access Stratum Access Stratum RRC PDCP RRC PDCP RLC RLC RLC RLC RANAP UP-CS UP-PS RANAP UP-CS UP-PS PHY PHY NBAP FP SAAL AAL2 ATM NBAP FP SCCP MTP3 GTP-U UDP SAAL AAL2 SAAL AAL2 AAL5 ATM ATM SCCP MTP3 GTP-U UDP SAAL AAL2 AAL5 ATM PHY PHY PHY PHY Signaling Circuit Switched Packet Switched Uu Iub Iu Figure 1.6: UMTS protocol stack - all in one. GPRS Tunneling Protocol (GTP) GTP is a tunneling and management protocol through which the SGSN services GPRS network access to the users. We can divide the GTP protocol in two different planes control and user plane. GTP-C (control) provides signaling between GGSN and SGSN within the GPRS core network. The SGSN is then able to activate and deactivate user sessions, called PDP contexts, and adjust the connection parameters in order to improve the quality of service. GTP-U (user) carries user data packets between the core and the access network. This protocol is only implemented for SGSNs and GGSNs. The rest of the systems in the network do not need to be aware of it.
26 1.2. UMTS 18 BSS GPRS Protocol (BSSGP) BSSGP is a protocol used between BSS and SGSN, via the Gb interface. Primary functions of BSSGP are [12]: in the downlink, the provision by an SGSN to a BSS of radio related information used by the RLC/MAC function, in the uplink, the provision by a BSS to an SGSN of radio related information derived from the RLC/MAC function, and the provision of functionality to enable two physically distinct nodes, an SGSN and a BSS, to operate node management control functions. The peer-to-peer communication over the Gb interface is done over virtual connections. BSSGP is responsible for the management of the virtual connections between SGSN and BSS. Logical and transport channels There are four different logical channels: the BCCH for spreading cell information, the Paging Control Channel (PCCH) for paging purposes, the DCCH for establishing pointto-point connections and Radio Resource Control (RRC) procedures, and the Common Control Channel (CCCH) for exchanging control information. UMTS supports two kinds of data channels: the Dedicated Traffic Channel (DTCH), a point-to-point channel, assigned to a single UE, and the Common Traffic Channel (CTCH), similar to DTCH for multicast transmissions. The transport channels can be divided in two types: dedicated and common channels. Dedicated channels are for specific users, and common channels can be used by all the users in one cell. There is just one dedicated channel, the Dedicated Channel (DCH).
27 1.2. UMTS 19 There are six types of common channels. The function of these channels differs from its function on GSM as they can be used also for the transport of PS data. The BroadCast Channel (BCH) is utilized to transmit cell information broadcasted by the RNC. The Forward Access Channel (FACH) carries user control information. Paging procedures are done via the PCH. The RACH can be used together with the FACH to setup a radio link. The common packet channel is an extended version of the RACH that enables PS services. User and control data that should be accessed by several mobile stations is transmitted over the Downlink Shared Channel (DSCH). Interfaces UMTS defines five new open interfaces: Uu: UE to NodeB IuPS: RNC to SGSN for packet switched data. IuCS: RNC to VLR/MSC for circuit switched data Iub: RNC to NodeB interface Iur: RNC to RNC interface The Iu, Iub, and Iur interfaces are based on ATM transmission principles.
28
29 Chapter 2 Security aspects in cellular mobile networks In the last 20 years, mobile phone subscriptions grew to 4,6 billions worldwide. A device that was thought of in a first stage as a simple means of communication, is now a very important element in everybody s lives. Nowadays communication is not understood only as calling and messaging, but , browsing, etc. Therefore, many new technologies and standards appeared in order to offer data connection, and allow browsing, , and other internet services. The question is if it is as reliable to use our phone as to use a computer for this kind of operations. In Europe the most common mobile technologies, GSM and UMTS, which are inside the so called 2G and 3G networks, are known to have vulnerabilities [13]. Current research studies these weaknesses at different layers making a deep theoretical analysis. First of all we have to define what kind of security are we talking about and in which layer we are interested. In [14] the security threats are classified as follow: Denial of Service (DoS): based on the temporary or permanent interruption of the service, which for the user means that no calls can be made. Different kinds 21
30 2.1. Vulnerabilities of 2G/3G networks 22 of denial of service attacks on 2G/3G networks are user deregistration request spoofing, location update request spoofing, or camping on false BS/MS. Identity catching: interception of user identities by unauthorized parties. There are two kinds, passive and active. Impersonation of the network and thereby eavesdropping: it can be done by suppressing encryption between two parties, target and intruder, or target and the true network. It can also be performed by forcing the use of a compromised cipher key. Impersonation of the user ID: there are different ways to do that, using a compromised Authentication Vector (AV), an eavesdropped authentication response, or hijacking ougoing or incoming calls in networks with encryption disabled or enabled. Therefore, in order to be able to carry out these attacks, the intruder needs different capabilities, namely: eavesdropping, be able to impersonate a user or a network, perform man-in-the-middle attacks, and compromising authentication vector in the network. It has to be considered that some of those capabilities are complex to gain in a mobile network. 2.1 Vulnerabilities of 2G/3G networks It is widely known that 2G/3G networks present different vulnerabilities [15]. In the recent history of telecommunications there are important examples showing off these weaknesses, like the Greek wiretapping case in 2004 [16]. More than 100 mobile phones of the Vodafone Greece network were involved on an illegal tapping 1. The 3GPP TS standard states several security issues in 2G networks: 1
31 2.2. Classification of threads 23 There are active attacks as false BTS. Cipher keys and authentication data are transmitted in clear within networks, which is a clear weak point. Encryption is not used far enough towards the core network, which implies that user and signaling data is transmitted in clear text across microwave links. Encryption is not used in all the networks. This is a problem in cases where for example user authentication is done using a previously generated cipher key and the protection against channel hijack relies on the use of this encryption. In these networks data integrity is not provided. In case of 3G networks (i.e., UMTS) these issues are solved, but other have appeared. In [17], the authors tackle with these new weaknesses. The most important are: Integrity keys used between UE and RNC generated in VLR/SGSN are transmitted unencrypted to the RNC (and sometimes between RNCs). Integrity of user data is not defined. For a short time during signaling procedures, signaling is unprotected and hence exposed to tampering. 2.2 Classification of threads In this section we give an overview of the related work ( [14], [18], [19], [20], [21], [22], [23]) focused on 2G/3G vulnerabilities. The attacks can be classified depending on the interception point and the target, i.e. the user or the network. In [24], security in UMTS architecture is studied. Here, some procedures imply a vulnerability since they can be used to perform a DoS attack. To
32 2.2. Classification of threads 24 simplify the classification, attacks will be divided in three groups depending on which is their final target: user, access network, or core network Target: user In user-targeted attacks, the end user is the victim. However, this does not exclude that other elements in the network are not compromised or do not suffer side effects from the attack Black hole attack The Black Hole attack is presented as a very straight forward attack in [24]. The attacker presents himself as a valid BS, and places himself close to the victims. The users perceiving the attacker s broadcasting signal stronger than the real BS signal connect to the fake base station. Afterwards, the attacker simply drops the packets coming from or going to any user, and therefore the user has no connection. UMTS security architecture is not able to counteract these kinds of attacks. On the other hand, it is difficult that a malicious user choses this method to perform an attack because of the following reasons: the attack only works when the user is in idle mode (see Figure 2.1), it affects a reduced numbers of users, therefore its impact is not very high, and it cannot be focused on desired targets without affecting others Dropping ACK signal In a UMTS network every user has a unique identifier, the so called IMSI. This has to be protected against interception or other kind of malicious access, and transmitted
33 2.2. Classification of threads 25 GPRS attach READY timer expired or forced STANDBY IDLE READY STANDBY GPRS detach STANDBY timer expired Transmission of a packet Figure 2.1: GPRS states. only over the network. There is a second identifier known as the TMSI, which is assigned every time a user changes area, implying a change of the monitoring SGSN. The SGSN does not relates IMSI and TMSI, unless it receives a TMSI Allocation Complete message from the MS. If the TMSI Allocation Complete message does not reach the SGSN, then both relations [IMSI, TMSI old] and [IMSI, TMSI new] are considered valid by the SGSN and can be arbitrarily employed by the user in the uplink case. For the downlink case, the network needs to employ the IMSI, otherwise it has no knowledge of the valid TMSI (old or new). Afterwards, the SGSN asks the MS to delete any TMSI kept in the mobile. For both cases, the network is allowed to initiate the TMSI Allocation procedure. UE SGSN [TMSI Allocation Command] [TMSI Allocation Complete] Figure 2.2: TMSI Allocation Procedure [24]. In the following, the dropping ACK signal attack described in [24] is introduced. Here, the attacker positions its equipment in a strategic location. He tracks all the TMSI Allocation Command messages and drops any following TMSI Allocation Complete
34 2.2. Classification of threads 26 message. This implies that new TMSIs have to be created at a rate higher than normal, which would then mean a DoS to all users entering the router area of this specific SGSN. The creation of a new TMSI is a multi-step procedure and cannot be considered resource consuming. Moreover, the extension of this attack to a flooding attack is considered to be a difficult task [24]. Nevertheless, the observed weakness can be used to expose and collect an important number of IMSIs, as well as launching more dangerous attacks Modifying unprotected RRC messages The RRC messages are considered an important part of the system as they handle the control plane of Layer 3 between the UEs and the core network. Signalling information messages are protected by integrity mechanisms. This is almost always true, which means that some messages are not integrity protected and hence susceptible to be misused. Unprotected messages are: Handover to UTRAN Complete, Paging Type 1, Push Capacity Request, Physical Shared Channel Allocation, RRC Connection Request, Setup, Setup Complete, Reject and Release, System Information (Broadcast Information), System Information Change Indication, Transport Format Combination Control (TM DCCH Only).
35 2.2. Classification of threads 27 These messages are susceptible to be intercepted and therefore, modified, dropped, or substitued, which may cause either low QoS or a DoS situation [24]. This interception can be more or less dangerous depending on which message is chosen for the attack. The most susceptible messages to be accessed are the RRC Connection Request, Setup, Setup Complete, Reject and Release as the modification of any implies a change in the connection without the user realizing. A user attempting to connect, may not be able to do so, without getting any kind of information about the reason. Therefore, the dangerousness of this attack depends on which is the message intercepted, and the action performed on it afterwards, i.e modification, dropping, or substitution Reveal of subscriber s identity There are various situations where the identity of the user (IMSI) is sent in clear text, such as in the first rrcconnectionrequest, or in case of VLR database crash. In these cases, the low protection against identity catching is obvious. The first message in such a communication is sent over the RACH which is known to be easily intercepted. The idea of this attack is simple. To obtain a subscriber s IMSI the attacker presents itself as a UMTS VLR/SGSN. During rrcconnectionrequest the user uses the TMSI as unique identifier. The attacker acting as the real VLR claims not to be able to resolve this TMSI which forces the user to sent its IMSI in clear text. After receiving it, the attacker disconnects from the network. GSM based IMSI catcher devices are available on the market but their prices are as high as $500,000 and are sold only to government agencies. This fact makes this attack not plausible because of money and legal aspects.
36 2.2. Classification of threads DoS by modifying initial security capabilities of ME The modification of ME s capabilities involves the use of the aforementioned attack in order to obtain the IMSI of the victim. Then, the attacker waits for this specific user to connect to the network. When the user makes a rrcconnectionrequest, the attacker modifies the message 1 (see Figure 2.3) that includes the initial security capabilities of the ME. In , we recognize that this message is unprotected, and as a consequence a malicious user can modify the ME capabilities. This issue is not detected until the security mode command reaches the ME (message 8 of Figure 2.3). Uu Iub Iu-CS/PS ME NodeB RNC VLR/ SGSN [Initial rrcconnection with ME security] [UEA,UIA, START_PS-CS] Initial L3 message with UE identity [User identity interrogation] Storage of UE security capabilities [Authentication and Key Agreement] Decide 4 5 allowed UEAs and [Security Mode Command] UIAs 6 [UEA, CK, UIA, IK, etc] Select UEAs and UIAs. 7 Generate FRESH, start integrity Verify message Start integrity [Security Mode Command] [UEA, UIA, MAC-I, Security capabilities of UE] [Security Mode Complete MAC-I] [Encryption/Decryption started] 11 [Security Mode Complete] [Selected UIA, UEA] Figure 2.3: UMTS Security Mode Setup Procedure [25]. When the ME receives a misleading message 8, the procedure is interrupted. Up to this point, the ME, the NodeB, the RNC, and the VLR/SGSN have exchanged information for setting up the connection, which in this case means unnecessary use of bandwidth and
37 2.2. Classification of threads 29 computing resources. As a result of this interruption, the user experiments a DoS. Khan et al. conclude in [25] that the modification of any of the authentication parameters may also result in DoS. These messages are neither encrypted nor integrity protected, therefore, any change results in non-authentication of the network and/or the user DoS using rrcconnectionreject message After obtaining the IMSI of the user, the attacker waits for the rrcconnectionrequest message. The identifier of the user is usually the TMSI, the P-TMSI (P-TMSI), or the IMEI. Though, the identifier in this message is the IMSI of the user. The attacker answers the user with a rrcconnectionreject message for closing the conenction. In [25] it is stated that the only way to check the authenticity of this message is to compare the INITIAL UE IDENTITY value at the rrcconnectionreject message, with the same parameter available at the UE. Therefore, an intruder possessing an IMSI can generate a valid rrcconnectionreject message and cause DoS to the user Integrity protection of user data Cryptographic integrity is not implemented all over the UMTS system. Even though signaling data is protected, user data is not. The network assumption is based on the fact that if the data is correctly decrypted, the data is intact [25]. However, this assumption is milded when other kind of user data is evaluated, such as web pages Target: core network This section is focused on attacks whose goal is to maliciously affect elements of the core network, i.e., SGSN, VLR, HLR, etc.
38 2.2. Classification of threads Modification of the initial security capabilities of MS This attack is an extension of the attack explained in Section and proposed by [25]. In this case, as exposed by [24], the modification is made in the rrcconnection- Request message, in the field that defines the UE security capabilities. This modification is not perceived until the Authentication and Key Agreement (AKA) procedure is complete and the Security Mode Command is sent to the MS. As in the example shown in Section , in case of security capabilities mismatching, the connection terminates. Nevertheless, during all the phases of the attack, resources are consumed. The goal of this kind of attacks is to overload the system with a procedure that is continuously being repeated. In case of being successful, the system will be unresponsive. In the worst case, when the attacker is in possession of a large list of stolen IMSIs, then this attack has higher impact SQN synchronization Resynchronization procedure is done for synchronizing the SeQueNce (SQN) value of the MS and HLR. This process implies the generation of new AV and its transmission from the HLR to the SGSN, therefore it is considered as a procedure requiring computational power and network resources. The goal of the attacker in this case is that this procedure is executed as many times as possible for different users at the same time, in order to overload the HLR. However, as mentioned by [24], the modification of the SQN HN value cannot be done easily, as it is contained in the AUTN part of the Authentication Request message. This message may be concealed with the Authentication Key (AK). Moreover, it is anyhow protected by Media Access Control (MAC). Additionally, the attacker is not able to spoof the whole {RAND-AUTN} hoping to subsequently modify this value in order to make it size variable and then trigger resynchronization. Every attempt to spoof the
39 2.2. Classification of threads 31 SQN value would initiate a MAC verification failure in the MS and the procedure will be stopped. The user will still perceive this as a DoS, but it is limited and it is not suitable for massive exhaustion of resources DoS by flooding the HLR/AuC The following attack is considered dangerous as it affects the HLR/AuC and is mobile operator specific. This means that some operator services can be blocked. The attack develops in two phases. First of all, the attacker builds a list of IMSIs, all of them from the same operator. This is easy to identify as the digits four and five (MNC) represent the operator (see Figure 1.3). Secondly, the attacker generates rrcconnectionrequest messages including each of the IMSIs of his list. For each request, the VLR sends the IMSI to the HLR/AuC. A check for the validation of the IMSI is done in the HLR/AuC. As they are valid IMSIs, all of them pass this check. The next step that the HLR takes is computing five AVs for each IMSI received. The process of generating these five AVs implies the calculation of RAND, MAC, XRES, CK, IK, and AK for each IMSI. These AVs are sent back to the VLR. For each IMSI, the VLR choses one, and sends the RAND and the AUTN for authentication. At this point, the attacker will not be authenticated and the procedure will terminate. The goal of this attack is not being authenticated as a valid user, but to exhaust the computing resources of the HLR/AuC. The flooding of the HLR by rrcconnectionrequest messages may cause also a high demand of bandwidth. A side effect will be a DoS to the users that are trying to connect but cannot do it due to the high load on the HLR.
40 2.2. Classification of threads Impersonation of the network In the beginning, the attacker impersonates as a valid GSM BS to the UMTS user and to the network. A UMTS user sends security capabilities which can be modified by the intruder. The AKA procedure is carried out between MS, VLR/SGSN and HLR/AuC. The fake GSM BS forwards these messages. GSM cipher key Kc is derived from the UMTS cipher/integrity keys and sent to the impersonated BS [26]. The network starts the security mode command according to the BS, which does not include the security capabilities previously forwarded by the ME. Since the ME assumes itself to be connected to a reliable GSM BS, it will accept this command. As a result, the attacker succeeds in obtaining the encryption algorithms. A5/1, and A5/2 can be compromised. Nevertheless, take over a BS is considered a difficult task Target: access network On the access network, we find different known attacks. Previously described attacks, like or although focused on the core network, they also affect the access network. The most clear problem presented on the access network is that the radio channel is open and can be monitored. Nevertheless it is not trivial to record due to the features in place, like i.e. frequency hopping in GSM. A well-known attack that targets the access network is the GSM network jammers. Cellular phones use two bands to communicate with the Base Station, one for sending, the other one for receiving. Jamming devices interrupt these signals transmitting on the same frequency as the cell phones at a high enough power so that both signals collide and cancel each other. Therefore, communication between Base Station and phone is disrupted. Jamming can also be focused to UMTS phones. In this case, though, it is more difficult
41 2.2. Classification of threads 33 to jamm a UMTS phone because of the use of WCDMA. In this case the attacker will need additionally the spreading codes used. Another problem found in the GSM access network is the encryption. It is widely known that GSM encryption is weak and there are several studies showing the different vulnerabilities [19]. This allows to malicious users to sniff the data transmitted and decrypt it.
42
43 Chapter 3 Measurement Setup: enabling access to GSM OsmocomBB 1 is an open source project which implements the GSM protocol stack from scratch on top of an existing chipset. It presents itself as a valuable tool for the study and analysis of the GSM network and the access to the radio link at very low price. We use this tool to proof some of the theoretical assumptions taken in some of the attacks introduced in the previous chapter, and analyze the attach model. This project allows to access the radio link at very low cost. 3.1 OsmocomBB project Open Source MObile COMmunication BaseBand (OsmocomBB) is an open source project that implements a GSM baseband software. It includes the GSM Mobile Station side protocol stack from layer 1 to layer 3, the drivers for GSM Baseband chipset, and a verbose User interface on the PC. It runs as a little software in the phone. Hardware drivers and layer 1 run directly in the phone. Layer 2 and 3 and the phone application
GSM GPRS. Course requirements: Understanding Telecommunications book by Ericsson (Part D PLMN) + supporting material (= these slides)
 GSM Example of a PLMN (Public Land Mobile Network) At present most successful cellular mobile system (over 200 million subscribers worldwide) Digital (2 nd Generation) cellular mobile system operating
GSM Example of a PLMN (Public Land Mobile Network) At present most successful cellular mobile system (over 200 million subscribers worldwide) Digital (2 nd Generation) cellular mobile system operating
2G/3G Mobile Communication Systems
 2G/3G Mobile Communication Systems Winter 2012/13 Integrated Communication Systems Group Ilmenau University of Technology Outline 2G Review: GSM Services Architecture Protocols Call setup Mobility management
2G/3G Mobile Communication Systems Winter 2012/13 Integrated Communication Systems Group Ilmenau University of Technology Outline 2G Review: GSM Services Architecture Protocols Call setup Mobility management
PDF vytvořeno zkušební verzí pdffactory www.fineprint.cz UMTS
 UMTS Generations of mobile systems Generation 1 (1980-1995) 2 (1992-2000) 2,5 (1999-2010) 3 (2004-20?) Names NMT (Nordic Mobile Telephone); 450 MHz, 900 MHz AMPS (Advance Mobile Telephone System); USA
UMTS Generations of mobile systems Generation 1 (1980-1995) 2 (1992-2000) 2,5 (1999-2010) 3 (2004-20?) Names NMT (Nordic Mobile Telephone); 450 MHz, 900 MHz AMPS (Advance Mobile Telephone System); USA
Global System for Mobile Communications (GSM)
 Global System for Mobile Communications (GSM) Nguyen Thi Mai Trang LIP6/PHARE Thi-Mai-Trang.Nguyen@lip6.fr UPMC/PUF - M2 Networks - PTEL 1 Outline Principles of cellular networks GSM architecture Security
Global System for Mobile Communications (GSM) Nguyen Thi Mai Trang LIP6/PHARE Thi-Mai-Trang.Nguyen@lip6.fr UPMC/PUF - M2 Networks - PTEL 1 Outline Principles of cellular networks GSM architecture Security
Chapter 2 Mobility Management for GPRS and UMTS
 Chapter 2 Mobility Management for GPRS and UMTS Prof. Yuh-Shyan Chen Department of Computer Science and Information Engineering National Taipei University Outline 2.1 Network Architectures 2.2 Concepts
Chapter 2 Mobility Management for GPRS and UMTS Prof. Yuh-Shyan Chen Department of Computer Science and Information Engineering National Taipei University Outline 2.1 Network Architectures 2.2 Concepts
UMTS/GPRS system overview from an IP addressing perspective. David Kessens Jonne Soininen
 UMTS/GPRS system overview from an IP addressing perspective David Kessens Jonne Soininen Introduction 1) Introduction to 3GPP networks (GPRS, UMTS) Technical overview and concepts for 3GPP networks Mobility
UMTS/GPRS system overview from an IP addressing perspective David Kessens Jonne Soininen Introduction 1) Introduction to 3GPP networks (GPRS, UMTS) Technical overview and concepts for 3GPP networks Mobility
Global System for Mobile Communication (GSM)
 Global System for Mobile Communication (GSM) Li-Hsing Yen National University of Kaohsiung GSM System Architecture Um (ME/SIM) C E C PSTN, ISDN, PSPDN, CSPDN A-bis A F A-bis C B BTS BSS BSC HLR VLR EIR
Global System for Mobile Communication (GSM) Li-Hsing Yen National University of Kaohsiung GSM System Architecture Um (ME/SIM) C E C PSTN, ISDN, PSPDN, CSPDN A-bis A F A-bis C B BTS BSS BSC HLR VLR EIR
How To Understand The Gsm And Mts Mobile Network Evolution
 Mobile Network Evolution Part 1 GSM and UMTS GSM Cell layout Architecture Call setup Mobility management Security GPRS Architecture Protocols QoS EDGE UMTS Architecture Integrated Communication Systems
Mobile Network Evolution Part 1 GSM and UMTS GSM Cell layout Architecture Call setup Mobility management Security GPRS Architecture Protocols QoS EDGE UMTS Architecture Integrated Communication Systems
UMTS security. Helsinki University of Technology S-38.153 Security of Communication Protocols k-p.perttula@hut.fi 15.4.2003
 UMTS security Helsinki University of Technology S-38.153 Security of Communication Protocols k-p.perttula@hut.fi 15.4.2003 Contents UMTS Security objectives Problems with GSM security UMTS security mechanisms
UMTS security Helsinki University of Technology S-38.153 Security of Communication Protocols k-p.perttula@hut.fi 15.4.2003 Contents UMTS Security objectives Problems with GSM security UMTS security mechanisms
GSM Network and Services
 GSM Network and Services GPRS - sharing of resources 1 What is the problem? Many data applications are very bursty in its traffic pattern: http, smtp, pop, telnet,... Why reserve physical resources at
GSM Network and Services GPRS - sharing of resources 1 What is the problem? Many data applications are very bursty in its traffic pattern: http, smtp, pop, telnet,... Why reserve physical resources at
The GSM and GPRS network T-110.300/301
 The GSM and GPRS network T-110.300/301 History The successful analog 1:st generation mobile telephone systems proved that there is a market for mobile telephones ARP (AutoRadioPuhelin) in Finland NMT (Nordic
The GSM and GPRS network T-110.300/301 History The successful analog 1:st generation mobile telephone systems proved that there is a market for mobile telephones ARP (AutoRadioPuhelin) in Finland NMT (Nordic
Mobile Wireless Overview
 Mobile Wireless Overview A fast-paced technological transition is occurring today in the world of internetworking. This transition is marked by the convergence of the telecommunications infrastructure
Mobile Wireless Overview A fast-paced technological transition is occurring today in the world of internetworking. This transition is marked by the convergence of the telecommunications infrastructure
Mobile Communications
 October 21, 2009 Agenda Topic 2: Case Study: The GSM Network 1 GSM System General Architecture 2 GSM Access network. 3 Traffic Models for the Air interface 4 Models for the BSS design. 5 UMTS and the path
October 21, 2009 Agenda Topic 2: Case Study: The GSM Network 1 GSM System General Architecture 2 GSM Access network. 3 Traffic Models for the Air interface 4 Models for the BSS design. 5 UMTS and the path
192620010 Mobile & Wireless Networking. Lecture 5: Cellular Systems (UMTS / LTE) (1/2) [Schiller, Section 4.4]
![192620010 Mobile & Wireless Networking. Lecture 5: Cellular Systems (UMTS / LTE) (1/2) [Schiller, Section 4.4] 192620010 Mobile & Wireless Networking. Lecture 5: Cellular Systems (UMTS / LTE) (1/2) [Schiller, Section 4.4]](/thumbs/18/698539.jpg) 192620010 Mobile & Wireless Networking Lecture 5: Cellular Systems (UMTS / LTE) (1/2) [Schiller, Section 4.4] Geert Heijenk Outline of Lecture 5 Cellular Systems (UMTS / LTE) (1/2) q Evolution of cellular
192620010 Mobile & Wireless Networking Lecture 5: Cellular Systems (UMTS / LTE) (1/2) [Schiller, Section 4.4] Geert Heijenk Outline of Lecture 5 Cellular Systems (UMTS / LTE) (1/2) q Evolution of cellular
CS 8803 - Cellular and Mobile Network Security: GSM - In Detail
 CS 8803 - Cellular and Mobile Network Security: GSM - In Detail Professor Patrick Traynor 9/27/12 Cellular Telecommunications Architecture Background Air Interfaces Network Protocols Application: Messaging
CS 8803 - Cellular and Mobile Network Security: GSM - In Detail Professor Patrick Traynor 9/27/12 Cellular Telecommunications Architecture Background Air Interfaces Network Protocols Application: Messaging
GSM BASICS GSM HISTORY:
 GSM BASICS GSM HISTORY: In 1982 the Nordic PTTs sent a proposal to CEPT (Conference of European Postal & telegraph Administration) to study and to improve digital cellular technology by forming a team
GSM BASICS GSM HISTORY: In 1982 the Nordic PTTs sent a proposal to CEPT (Conference of European Postal & telegraph Administration) to study and to improve digital cellular technology by forming a team
Mobile Application Part protocol implementation in OPNET
 Mobile Application Part protocol implementation in OPNET Vladimir Vukadinovic and Ljiljana Trajkovic School of Engineering Science Simon Fraser University Vancouver, BC, Canada E-mail: {vladimir, ljilja}@cs.sfu.ca
Mobile Application Part protocol implementation in OPNET Vladimir Vukadinovic and Ljiljana Trajkovic School of Engineering Science Simon Fraser University Vancouver, BC, Canada E-mail: {vladimir, ljilja}@cs.sfu.ca
Ch 2.3.3 GSM PENN. Magda El Zarki - Tcom 510 - Spring 98
 Ch 2.3.3 GSM In the early 80 s the European community decided to work together to define a cellular system that would permit full roaming in all countries and give the network providers freedom to provide
Ch 2.3.3 GSM In the early 80 s the European community decided to work together to define a cellular system that would permit full roaming in all countries and give the network providers freedom to provide
GSM Architecture and Interfaces
 GSM.05 Page 71 Monday, November 30, 1998 2:07 PM C H A P T E R 5 GSM Architecture and Interfaces 5.1 INTRODUCTION In this chapter we present an overview of the GSM as described in ETSI s recommendations.
GSM.05 Page 71 Monday, November 30, 1998 2:07 PM C H A P T E R 5 GSM Architecture and Interfaces 5.1 INTRODUCTION In this chapter we present an overview of the GSM as described in ETSI s recommendations.
TSG-RAN Meeting #7 Madrid, Spain, 13 15 March 2000 RP-000034. Title: Agreed CRs to TS 25.301. Agenda item: 6.3.3
 TSG-RAN Meeting #7 Madrid, Spain, 13 15 March 2000 RP-000034 Title: Agreed CRs to TS 25.301 Source: TSG-RAN WG2 Agenda item: 6.3.3 Doc-1st- Spec CR Rev Subject Cat Version Versio R2-000213 25.301 032 Correction
TSG-RAN Meeting #7 Madrid, Spain, 13 15 March 2000 RP-000034 Title: Agreed CRs to TS 25.301 Source: TSG-RAN WG2 Agenda item: 6.3.3 Doc-1st- Spec CR Rev Subject Cat Version Versio R2-000213 25.301 032 Correction
Mobile Communications Chapter 4: Wireless Telecommunication Systems slides by Jochen Schiller with modifications by Emmanuel Agu
 Mobile Communications Chapter 4: Wireless Telecommunication Systems slides by Jochen Schiller with modifications by Emmanuel Agu Market GSM Overview Services Sub-systems Components Prof. Dr.-Ing. Jochen
Mobile Communications Chapter 4: Wireless Telecommunication Systems slides by Jochen Schiller with modifications by Emmanuel Agu Market GSM Overview Services Sub-systems Components Prof. Dr.-Ing. Jochen
Global System for Mobile Communication Technology
 Global System for Mobile Communication Technology Mobile Device Investigations Program Technical Operations Division DHS - FLETC GSM Technology Global System for Mobile Communication or Groupe Special
Global System for Mobile Communication Technology Mobile Device Investigations Program Technical Operations Division DHS - FLETC GSM Technology Global System for Mobile Communication or Groupe Special
CS 8803 - Cellular and Mobile Network Security: CDMA/UMTS Air Interface
 CS 8803 - Cellular and Mobile Network Security: CDMA/UMTS Air Interface Hank Carter Professor Patrick Traynor 10/4/2012 UMTS and CDMA 3G technology - major change from GSM (TDMA) Based on techniques originally
CS 8803 - Cellular and Mobile Network Security: CDMA/UMTS Air Interface Hank Carter Professor Patrick Traynor 10/4/2012 UMTS and CDMA 3G technology - major change from GSM (TDMA) Based on techniques originally
Authentication and Secure Communication in GSM, GPRS, and UMTS Using Asymmetric Cryptography
 ISSN (Online): 1694-0784 ISSN (Print): 1694-0814 10 Authentication and Secure Communication in GSM, GPRS, and UMTS Using Asymmetric Cryptography Wilayat Khan 1 and Habib Ullah 2 1 Department of Electrical
ISSN (Online): 1694-0784 ISSN (Print): 1694-0814 10 Authentication and Secure Communication in GSM, GPRS, and UMTS Using Asymmetric Cryptography Wilayat Khan 1 and Habib Ullah 2 1 Department of Electrical
Mobile Office Security Requirements for the Mobile Office
 Mobile Office Security Requirements for the Mobile Office S.Rupp@alcatel.de Alcatel SEL AG 20./21.06.2001 Overview Security Concepts in Mobile Networks Applications in Mobile Networks Mobile Terminal used
Mobile Office Security Requirements for the Mobile Office S.Rupp@alcatel.de Alcatel SEL AG 20./21.06.2001 Overview Security Concepts in Mobile Networks Applications in Mobile Networks Mobile Terminal used
Role and Evolution of Radio Network Controllers
 01001000100000110000001000001100 010010001000 Role and Evolution of Radio Network Controllers Pekka Varis SPRP501 Senior R&D Manager / Senior Specialist Nokia pekka.ju.varis@nokia.com Agenda Radio Network
01001000100000110000001000001100 010010001000 Role and Evolution of Radio Network Controllers Pekka Varis SPRP501 Senior R&D Manager / Senior Specialist Nokia pekka.ju.varis@nokia.com Agenda Radio Network
On the Security of 3GPP Networks
 On the Security of 3GPP Networks Michael Walker Vodafone AirTouch & Royal Holloway, University of London Chairman 3GPP SA3 - Security Eurocrypt 2000 Security of 3GPP networks 1 Acknowledgements This presentation
On the Security of 3GPP Networks Michael Walker Vodafone AirTouch & Royal Holloway, University of London Chairman 3GPP SA3 - Security Eurocrypt 2000 Security of 3GPP networks 1 Acknowledgements This presentation
Chapter 3: WLAN-GPRS Integration for Next-Generation Mobile Data Networks
 Chapter 3: WLAN-GPRS Integration for Next-Generation Mobile Data Networks IEEE Wireless Communication, Oct. 2002 Prof. Yuh-Shyan Chen Department of Computer Science and Information Engineering National
Chapter 3: WLAN-GPRS Integration for Next-Generation Mobile Data Networks IEEE Wireless Communication, Oct. 2002 Prof. Yuh-Shyan Chen Department of Computer Science and Information Engineering National
!!! "# $ % & & # ' (! ) * +, -!!. / " 0! 1 (!!! ' &! & & & ' ( 2 3 0-4 ' 3 ' Giuseppe Bianchi
 !!! "# $ % & & # ' (! ) * +, -!!. / " 0! 1 (!!! ' &! & & & ' ( 2 3 0-4 ' 3 ' "#$!!% "&'! #&'!%! () *+,, 3 & 5 &,! #-!*! ' & '.! #%!* //!! & (0)/!&/, 6 5 /, "! First system: NMT-450 (Nordic Mobile Telephone)
!!! "# $ % & & # ' (! ) * +, -!!. / " 0! 1 (!!! ' &! & & & ' ( 2 3 0-4 ' 3 ' "#$!!% "&'! #&'!%! () *+,, 3 & 5 &,! #-!*! ' & '.! #%!* //!! & (0)/!&/, 6 5 /, "! First system: NMT-450 (Nordic Mobile Telephone)
Mobile Security. Practical attacks using cheap equipment. Business France. Presented the 07/06/2016. For. By Sébastien Dudek
 Mobile Security Practical attacks using cheap equipment Presented the 07/06/2016 Business France By Sébastien Dudek For Content Security measures Recent publications in the hacking community Practical
Mobile Security Practical attacks using cheap equipment Presented the 07/06/2016 Business France By Sébastien Dudek For Content Security measures Recent publications in the hacking community Practical
9.1 Introduction. 9.2 Roaming
 9 Location Updating Objectives After this chapter the student will: be able to define the concepts of roaming and location updating. be able to name the different types of location updating and why they
9 Location Updating Objectives After this chapter the student will: be able to define the concepts of roaming and location updating. be able to name the different types of location updating and why they
Teknillinen Korkeakoulu Teletekniikan laboratorio S-38.128 Teletekniikan erikoistyö. General Packet Radio Service
 Teknillinen Korkeakoulu Teletekniikan laboratorio S-38.128 Teletekniikan erikoistyö General Packet Radio Service Tekijä: Jani Kokkonen 42916s jkokkone@cc.hut.fi Ohjaaja: Vesa Kosonen Jätetty: 31.1.2000
Teknillinen Korkeakoulu Teletekniikan laboratorio S-38.128 Teletekniikan erikoistyö General Packet Radio Service Tekijä: Jani Kokkonen 42916s jkokkone@cc.hut.fi Ohjaaja: Vesa Kosonen Jätetty: 31.1.2000
GSM Architecture Training Document
 Training Document TC Finland Nokia Networks Oy 1 (20) The information in this document is subject to change without notice and describes only the product defined in the introduction of this documentation.
Training Document TC Finland Nokia Networks Oy 1 (20) The information in this document is subject to change without notice and describes only the product defined in the introduction of this documentation.
GSM - Global System for Mobile Communications
 GSM - Global System for Mobile Communications VLR BTS BSC GMSC PSTN MS HLR 1) Overview of GSM architecture 2) GSM channel structure 05-1 GSM - Global System for Mobile Communications VLR BTS BSC GMSC PSTN
GSM - Global System for Mobile Communications VLR BTS BSC GMSC PSTN MS HLR 1) Overview of GSM architecture 2) GSM channel structure 05-1 GSM - Global System for Mobile Communications VLR BTS BSC GMSC PSTN
Lecture overview. History of cellular systems (1G) GSM introduction. Basic architecture of GSM system. Basic radio transmission parameters of GSM
 Lecture overview History of cellular systems (1G) GSM introduction Basic architecture of GSM system Basic radio transmission parameters of GSM Analogue cellular systems 70 s In the early 70 s radio frequencies
Lecture overview History of cellular systems (1G) GSM introduction Basic architecture of GSM system Basic radio transmission parameters of GSM Analogue cellular systems 70 s In the early 70 s radio frequencies
General Packet Radio Service (GPRS)
 General Packet Radio Service (GPRS) What is GPRS? GPRS (General Packet Radio Service) a packet oriented data service for IP and X.25 over GSM networks enables packet-switched services on the resources
General Packet Radio Service (GPRS) What is GPRS? GPRS (General Packet Radio Service) a packet oriented data service for IP and X.25 over GSM networks enables packet-switched services on the resources
GSM System. Global System for Mobile Communications
 GSM System Global System for Mobile Communications Introduced in 1991. Settings of standards under ETSI (European Telecommunication Standards Institute) Services - Telephone services - Data services -
GSM System Global System for Mobile Communications Introduced in 1991. Settings of standards under ETSI (European Telecommunication Standards Institute) Services - Telephone services - Data services -
Mobile Computing. Basic Call Calling terminal Network Called terminal 10/25/14. Public Switched Telephone Network - PSTN. CSE 40814/60814 Fall 2014
 Mobile Computing CSE 40814/60814 Fall 2014 Public Switched Telephone Network - PSTN Transit switch Transit switch Long distance network Transit switch Local switch Outgoing call Incoming call Local switch
Mobile Computing CSE 40814/60814 Fall 2014 Public Switched Telephone Network - PSTN Transit switch Transit switch Long distance network Transit switch Local switch Outgoing call Incoming call Local switch
Pradipta Biswas Roll No. 04IT6007 M. Tech. (IT) School of Information Technology Indian Institute of Technology, Kharagpur
 Pradipta Biswas Roll No. 04IT6007 M. Tech. (IT) School of Information Technology Indian Institute of Technology, Kharagpur ABSTRACT W-CDMA (Wideband Code-Division Multiple Access), an ITU standard derived
Pradipta Biswas Roll No. 04IT6007 M. Tech. (IT) School of Information Technology Indian Institute of Technology, Kharagpur ABSTRACT W-CDMA (Wideband Code-Division Multiple Access), an ITU standard derived
Delivery of Voice and Text Messages over LTE
 Delivery of Voice and Text Messages over LTE 1. The Market for Voice and SMS! 2. Third Party Voice over IP! 3. The IP Multimedia Subsystem! 4. Circuit Switched Fallback! 5. VoLGA LTE was designed as a
Delivery of Voice and Text Messages over LTE 1. The Market for Voice and SMS! 2. Third Party Voice over IP! 3. The IP Multimedia Subsystem! 4. Circuit Switched Fallback! 5. VoLGA LTE was designed as a
EETS 8316 Wireless Networks Fall 2013
 EETS 8316 Wireless Networks Fall 2013 Lecture: Cellular Overview: 3G and 4G http://lyle.smu.edu/~skangude/eets8316.html Dr. Shantanu Kangude skangude@lyle.smu.edu Third Generation Systems High-speed wireless
EETS 8316 Wireless Networks Fall 2013 Lecture: Cellular Overview: 3G and 4G http://lyle.smu.edu/~skangude/eets8316.html Dr. Shantanu Kangude skangude@lyle.smu.edu Third Generation Systems High-speed wireless
Provides a communication link between MS and MSC; Manages DB for MS location. Controls user connection. Transmission.
 Provides a communication link between MS and MSC; Manages DB for MS location Controls user connection CM MM RR Transmission Several RR functions considered in previous part!"# Surprise! handover is part
Provides a communication link between MS and MSC; Manages DB for MS location Controls user connection CM MM RR Transmission Several RR functions considered in previous part!"# Surprise! handover is part
Index. Common Packet Channel (CPCH) 25 Compression 265, 279 82, 288 header compression 284
 bindex.fm Page 296 Tuesday, March 22, 2005 7:17 AM Index 2G, 2.5G, 3G 13 3GPP 118 Release 5 (Rel 5) 124 Release 6 (Rel 6) 125 Release 97/98 (Rel 97/98) 119 Release 99 (Rel 99) 120 4 3GPP2 129 4G 13, 44
bindex.fm Page 296 Tuesday, March 22, 2005 7:17 AM Index 2G, 2.5G, 3G 13 3GPP 118 Release 5 (Rel 5) 124 Release 6 (Rel 6) 125 Release 97/98 (Rel 97/98) 119 Release 99 (Rel 99) 120 4 3GPP2 129 4G 13, 44
Security Architecture in UMTS Third Generation Cellular Networks Tomás Balderas-Contreras René A. Cumplido-Parra
 Security Architecture in UMTS Third Generation Cellular Networks Tomás Balderas-Contreras René A. Cumplido-Parra Reporte Técnico No. CCC-04-002 27 de febrero de 2004 Coordinación de Ciencias Computacionales
Security Architecture in UMTS Third Generation Cellular Networks Tomás Balderas-Contreras René A. Cumplido-Parra Reporte Técnico No. CCC-04-002 27 de febrero de 2004 Coordinación de Ciencias Computacionales
MAP/C SEND ROUTING INFO FOR SM. Destination Mobile Number. Obtain the SS7 address of the MSC VLR currently serving the specified Mobile Number
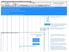 In this call flow we will look at how a terminating SMS is handled in GSM. Setting up a terminating SMS session is a multi-step process. (1) Interrogate the MSC to locate the subscriber (2)Setting SMS
In this call flow we will look at how a terminating SMS is handled in GSM. Setting up a terminating SMS session is a multi-step process. (1) Interrogate the MSC to locate the subscriber (2)Setting SMS
2 System introduction
 2 System introduction Objectives After this chapter the student will: be able to describe the different nodes in a GSM network. be able to describe geographical subdivision of a GSM network. be able to
2 System introduction Objectives After this chapter the student will: be able to describe the different nodes in a GSM network. be able to describe geographical subdivision of a GSM network. be able to
Handoff in GSM/GPRS Cellular Systems. Avi Freedman Hexagon System Engineering
 Handoff in GSM/GPRS Cellular Systems Avi Freedman Hexagon System Engineering Outline GSM and GSM referemce model GPRS basics Handoffs GSM GPRS Location and Mobility Management Re-selection and routing
Handoff in GSM/GPRS Cellular Systems Avi Freedman Hexagon System Engineering Outline GSM and GSM referemce model GPRS basics Handoffs GSM GPRS Location and Mobility Management Re-selection and routing
GPRS Overview. GPRS = General Packet Radio Service. GPRS Network
 GPRS - Overview GPRS Overview GPRS = General Packet Radio Service INTERNET/ INTRANET GPRS Network abcde X.25 Disclaimer: These overview slides are intended for informational purposes only. They have not
GPRS - Overview GPRS Overview GPRS = General Packet Radio Service INTERNET/ INTRANET GPRS Network abcde X.25 Disclaimer: These overview slides are intended for informational purposes only. They have not
Wireless Access of GSM
 Wireless Access of GSM Project Report FALL, 1999 Wireless Access of GSM Abstract: Global System for Mobile communications (GSM) started to be developed by Europeans when the removal of many European trade
Wireless Access of GSM Project Report FALL, 1999 Wireless Access of GSM Abstract: Global System for Mobile communications (GSM) started to be developed by Europeans when the removal of many European trade
GSM Channels. Physical & Logical Channels. Traffic and Control Mutltiframing. Frame Structure
 GSM Channels Physical & Logical Channels Traffic and Control Mutltiframing Frame Structure Engr. Mian Shahzad Iqbal Lecturer Department of Telecommunication Engineering Radio Interface The radio interface
GSM Channels Physical & Logical Channels Traffic and Control Mutltiframing Frame Structure Engr. Mian Shahzad Iqbal Lecturer Department of Telecommunication Engineering Radio Interface The radio interface
1 Introduction. 2 Assumptions. Implementing roaming for OpenBTS
 Implementing roaming for OpenBTS 1 Introduction One of the main advantages of OpenBTS TM system architecture is absence of a legacy GSM core network. SIP is used for registering, call control and messaging.
Implementing roaming for OpenBTS 1 Introduction One of the main advantages of OpenBTS TM system architecture is absence of a legacy GSM core network. SIP is used for registering, call control and messaging.
GSM and UMTS security
 2007 Levente Buttyán Why is security more of a concern in wireless? no inherent physical protection physical connections between devices are replaced by logical associations sending and receiving messages
2007 Levente Buttyán Why is security more of a concern in wireless? no inherent physical protection physical connections between devices are replaced by logical associations sending and receiving messages
IP-based Mobility Management for a Distributed Radio Access Network Architecture. helmut.becker@siemens.com
 IP-based Mobility Management for a Distributed Radio Access Network Architecture helmut.becker@siemens.com Outline - Definition IP-based Mobility Management for a Distributed RAN Architecture Page 2 Siemens
IP-based Mobility Management for a Distributed Radio Access Network Architecture helmut.becker@siemens.com Outline - Definition IP-based Mobility Management for a Distributed RAN Architecture Page 2 Siemens
Security and Authentication Concepts
 Security and Authentication Concepts for UMTS/WLAN Convergence F. Fitzek M. Munari V. Pastesini S. Rossi L. Badia Dipartimento di Ingegneria, Università di Ferrara, via Saragat 1, 44100 Ferrara, Italy
Security and Authentication Concepts for UMTS/WLAN Convergence F. Fitzek M. Munari V. Pastesini S. Rossi L. Badia Dipartimento di Ingegneria, Università di Ferrara, via Saragat 1, 44100 Ferrara, Italy
Global Roadmap for SMG and SA plenary WIs Document for: Information Agenda Item: 7
 Technical Specification Group Services and System Aspects Meeting #4, Miami, USA, 21-23 June 1999 TSGS#4(99)330 Source: MCC Title: Global Roadmap for SMG and SA plenary WIs Document for: Information Agenda
Technical Specification Group Services and System Aspects Meeting #4, Miami, USA, 21-23 June 1999 TSGS#4(99)330 Source: MCC Title: Global Roadmap for SMG and SA plenary WIs Document for: Information Agenda
Contents VULNERABILITIES OF MOBILE INTERNET (GPRS), 2014
 VULNERABILITIES OF MOBILE INTERNET (GPRS) Dmitry Kurbatov Sergey Puzankov Pavel Novikov 2014 Contents 1. Introduction 2. Summary 3. Mobile network scheme 4. GTP protocol 5. Searching for mobile operator
VULNERABILITIES OF MOBILE INTERNET (GPRS) Dmitry Kurbatov Sergey Puzankov Pavel Novikov 2014 Contents 1. Introduction 2. Summary 3. Mobile network scheme 4. GTP protocol 5. Searching for mobile operator
Long-Term Evolution. Mobile Telecommunications Networks WMNet Lab
 Long-Term Evolution Mobile Telecommunications Networks WMNet Lab Background Long-Term Evolution Define a new packet-only wideband radio with flat architecture as part of 3GPP radio technology family 2004:
Long-Term Evolution Mobile Telecommunications Networks WMNet Lab Background Long-Term Evolution Define a new packet-only wideband radio with flat architecture as part of 3GPP radio technology family 2004:
MRN 6 GSM part 1. Politecnico di Milano Facoltà di Ingegneria dell Informazione. Mobile Radio Networks Prof. Antonio Capone
 Politecnico di Milano Facoltà di Ingegneria dell Informazione MRN 6 GSM part 1 Mobile Radio Networks Prof. Antonio Capone A. Capone: Mobile Radio Networks 1 General characteristics of the system A. Capone:
Politecnico di Milano Facoltà di Ingegneria dell Informazione MRN 6 GSM part 1 Mobile Radio Networks Prof. Antonio Capone A. Capone: Mobile Radio Networks 1 General characteristics of the system A. Capone:
LTE Security How Good Is It?
 LTE Security How Good Is It? Michael Bartock IT Specialist (Security) National Institute of Standards & Technology Jeffrey Cichonski IT Specialist (Security) National Institute of Standards & Technology
LTE Security How Good Is It? Michael Bartock IT Specialist (Security) National Institute of Standards & Technology Jeffrey Cichonski IT Specialist (Security) National Institute of Standards & Technology
IMT-2000 Network Architecture
 IMT-2000 Network Architecture vtoshio Shimoe vtakamichi Sano (Manuscript received May 31, 2002) International Mobile Telecommunication-2000 (IMT-2000) is a third-generation mobile communication system.
IMT-2000 Network Architecture vtoshio Shimoe vtakamichi Sano (Manuscript received May 31, 2002) International Mobile Telecommunication-2000 (IMT-2000) is a third-generation mobile communication system.
GSM GSM 08.52 TECHNICAL December 1996 SPECIFICATION Version 5.0.0
 GSM GSM 08.52 TECHNICAL December 1996 SPECIFICATION Version 5.0.0 Source: ETSI TC-SMG Reference: TS/SMG-030852Q ICS: 33.020 Key words: Digital cellular telecommunications system, Global System for Mobile
GSM GSM 08.52 TECHNICAL December 1996 SPECIFICATION Version 5.0.0 Source: ETSI TC-SMG Reference: TS/SMG-030852Q ICS: 33.020 Key words: Digital cellular telecommunications system, Global System for Mobile
2G Mobile Communication Systems
 2G Mobile Communication Systems 2G Review: GSM Services Architecture Protocols Call setup Mobility management Security HSCSD GPRS EDGE References Jochen Schiller: Mobile Communications (German and English),
2G Mobile Communication Systems 2G Review: GSM Services Architecture Protocols Call setup Mobility management Security HSCSD GPRS EDGE References Jochen Schiller: Mobile Communications (German and English),
Mobility Management in UMTS
 Rheinisch-Westfälische Technische Hochschule Aachen Lehrstuhl für Informatik IV Prof. Dr. rer. nat. Otto Spaniol Mobility Management in UMTS Seminar: Datacommunication & Distributed Systems WS 2003/2004
Rheinisch-Westfälische Technische Hochschule Aachen Lehrstuhl für Informatik IV Prof. Dr. rer. nat. Otto Spaniol Mobility Management in UMTS Seminar: Datacommunication & Distributed Systems WS 2003/2004
Mobile Communications Chapter 4: Wireless Telecommunication Systems
 Mobile Communications Chapter 4: Wireless Telecommunication Systems Market GSM Overview Services Sub-systems Components GPRS DECT Not a part if this course! TETRA Not a part if this course! w-cdma (rel
Mobile Communications Chapter 4: Wireless Telecommunication Systems Market GSM Overview Services Sub-systems Components GPRS DECT Not a part if this course! TETRA Not a part if this course! w-cdma (rel
Performance Issues of TCP and MPEG-4 4 over UMTS
 Performance Issues of TCP and MPEG-4 4 over UMTS Anthony Lo A.Lo@ewi.tudelft.nl 1 Wiskunde end Informatica Outline UMTS Overview TCP and MPEG-4 Performance Summary 2 1 Universal Mobile Telecommunications
Performance Issues of TCP and MPEG-4 4 over UMTS Anthony Lo A.Lo@ewi.tudelft.nl 1 Wiskunde end Informatica Outline UMTS Overview TCP and MPEG-4 Performance Summary 2 1 Universal Mobile Telecommunications
Mobile network security report: Greece
 Mobile network security report: Greece GSM Map Project gsmmap@srlabs.de Security Research Labs, Berlin October 2012 Abstract. Mobile networks differ widely in their protection capabilities against common
Mobile network security report: Greece GSM Map Project gsmmap@srlabs.de Security Research Labs, Berlin October 2012 Abstract. Mobile networks differ widely in their protection capabilities against common
The Network Layer Layer 3
 CHAPTER 7 The Network Layer Layer 3 Now it is time to hijack the GSM freight train, to see what is inside, to break into the time-slotted boxcars and spill the drums of unknown acids and solvents on the
CHAPTER 7 The Network Layer Layer 3 Now it is time to hijack the GSM freight train, to see what is inside, to break into the time-slotted boxcars and spill the drums of unknown acids and solvents on the
Cellular Networks: Background and Classical Vulnerabilities
 Cellular Networks: Background and Classical Vulnerabilities Patrick Traynor CSE 545 1 Cellular Networks Provide communications infrastructure for an estimated 2.6 billion users daily. The Internet connects
Cellular Networks: Background and Classical Vulnerabilities Patrick Traynor CSE 545 1 Cellular Networks Provide communications infrastructure for an estimated 2.6 billion users daily. The Internet connects
-The equipment was limited to operate only within the boundaries of each country. -The market for each mo bile equipment was limited.
 1 History of GSM During the early 1980s, analog cellular telephone systems were experienced a very fast growth in Europe, particularly in Scandinavia and the United Kingdom, but also in France and Germany.
1 History of GSM During the early 1980s, analog cellular telephone systems were experienced a very fast growth in Europe, particularly in Scandinavia and the United Kingdom, but also in France and Germany.
Telesystem Innovations. LTE in a Nutshell: Protocol Architecture WHITE PAPER
 Telesystem Innovations LTE in a Nutshell: Protocol Architecture WHITE PAPER PROTOCOL OVERVIEW This whitepaper presents an overview of the protocol stack for LTE with the intent to describe where important
Telesystem Innovations LTE in a Nutshell: Protocol Architecture WHITE PAPER PROTOCOL OVERVIEW This whitepaper presents an overview of the protocol stack for LTE with the intent to describe where important
ETSI TS 123 251 V6.5.0 (2005-09)
 TS 123 251 V6.5.0 (2005-09) Technical Specification Universal Mobile Telecommunications System (UMTS); Network sharing; Architecture and functional description (3GPP TS 23.251 version 6.5.0 Release 6)
TS 123 251 V6.5.0 (2005-09) Technical Specification Universal Mobile Telecommunications System (UMTS); Network sharing; Architecture and functional description (3GPP TS 23.251 version 6.5.0 Release 6)
Wireless Mobile Telephony
 Wireless Mobile Telephony The Ohio State University Columbus, OH 43210 Durresi@cis.ohio-state.edu http://www.cis.ohio-state.edu/~durresi/ 1 Overview Why wireless mobile telephony? First Generation, Analog
Wireless Mobile Telephony The Ohio State University Columbus, OH 43210 Durresi@cis.ohio-state.edu http://www.cis.ohio-state.edu/~durresi/ 1 Overview Why wireless mobile telephony? First Generation, Analog
ETSI TS 133 102 V3.6.0 (2000-10)
 TS 133 102 V3.6.0 (2000-10) Technical Specification Universal Mobile Telecommunications System (UMTS); 3G Security; Security Architecture (3GPP TS 33.102 version 3.6.0 Release 1999) 1 TS 133 102 V3.6.0
TS 133 102 V3.6.0 (2000-10) Technical Specification Universal Mobile Telecommunications System (UMTS); 3G Security; Security Architecture (3GPP TS 33.102 version 3.6.0 Release 1999) 1 TS 133 102 V3.6.0
3GPP TR 23.912 V3.1.0 (2001-12)
 TR 23.912 V3.1.0 (2001-12) Technical Specification 3rd Generation Partnership Project; Technical Specification Group Core Network; Technical report on Super-Charger (Release 1999) The present document
TR 23.912 V3.1.0 (2001-12) Technical Specification 3rd Generation Partnership Project; Technical Specification Group Core Network; Technical report on Super-Charger (Release 1999) The present document
Theory and Practice. IT-Security: GSM Location System Syslog XP 3.7. Mobile Communication. December 18, 2001. GSM Location System Syslog XP 3.
 Participant: Hack contacting... IT-Security: Theory and Practice Mobile Communication December 18, 2001 Uwe Jendricke uwe@iig.uni-freiburg.de Lecture Homepage: http://www.informatik.uni-freiburg.de/~softech/teaching/ws01/itsec/
Participant: Hack contacting... IT-Security: Theory and Practice Mobile Communication December 18, 2001 Uwe Jendricke uwe@iig.uni-freiburg.de Lecture Homepage: http://www.informatik.uni-freiburg.de/~softech/teaching/ws01/itsec/
The Global System for Mobile communications (GSM) Overview
 The Global System for Mobile communications (GSM) Overview GSM D-AMPS Japan Digital PCS 1900 DCS 1800 CDMA Digital Cellular Systems World-wide Multiple Access Techniques In the GSM/DCS mobile system each
The Global System for Mobile communications (GSM) Overview GSM D-AMPS Japan Digital PCS 1900 DCS 1800 CDMA Digital Cellular Systems World-wide Multiple Access Techniques In the GSM/DCS mobile system each
Telecommunication Systems (GSM) Mobile Communications (Ch 4) John Schiller, Addison-Wesley
 Telecommunication Systems (GSM) Mobile Communications (Ch 4) John Schiller, Addison-Wesley 1 Telecommunication System Wireless extension of traditional PSTN Telephony architecture (NOT computer net) Many
Telecommunication Systems (GSM) Mobile Communications (Ch 4) John Schiller, Addison-Wesley 1 Telecommunication System Wireless extension of traditional PSTN Telephony architecture (NOT computer net) Many
Security Evaluation of CDMA2000
 Security Evaluation of CDMA2000 L. Ertaul 1, S. Natte 2, and G. Saldamli 3 1 Mathematics and Computer Science, CSU East Bay, Hayward, CA, USA 2 Mathematics and Computer Science, CSU East Bay, Hayward,
Security Evaluation of CDMA2000 L. Ertaul 1, S. Natte 2, and G. Saldamli 3 1 Mathematics and Computer Science, CSU East Bay, Hayward, CA, USA 2 Mathematics and Computer Science, CSU East Bay, Hayward,
Worldwide attacks on SS7 network
 Worldwide attacks on SS7 network P1 Security Hackito Ergo Sum 26 th April 2014 Pierre-Olivier Vauboin (po@p1sec.com) Alexandre De Oliveira (alex@p1sec.com) Agenda Overall telecom architecture Architecture
Worldwide attacks on SS7 network P1 Security Hackito Ergo Sum 26 th April 2014 Pierre-Olivier Vauboin (po@p1sec.com) Alexandre De Oliveira (alex@p1sec.com) Agenda Overall telecom architecture Architecture
Wireless Cellular Networks: 1G and 2G
 Wireless Cellular Networks: 1G and 2G Raj Jain Professor of Computer Science and Engineering Washington University in Saint Louis Saint Louis, MO 63130 Audio/Video recordings of this lecture are available
Wireless Cellular Networks: 1G and 2G Raj Jain Professor of Computer Science and Engineering Washington University in Saint Louis Saint Louis, MO 63130 Audio/Video recordings of this lecture are available
Evolution of GSM in to 2.5G and 3G
 CMPE 477 Wireless and Mobile Networks Evolution of GSM in to 2.5G and 3G New Data Services for GSM CMPE 477 HSCSD GPRS 3G UMTS IMT2000 UMTS Architecture UTRAN Architecture Data services in GSM I Data transmission
CMPE 477 Wireless and Mobile Networks Evolution of GSM in to 2.5G and 3G New Data Services for GSM CMPE 477 HSCSD GPRS 3G UMTS IMT2000 UMTS Architecture UTRAN Architecture Data services in GSM I Data transmission
LTE Overview October 6, 2011
 LTE Overview October 6, 2011 Robert Barringer Enterprise Architect AT&T Proprietary (Internal Use Only) Not for use or disclosure outside the AT&T companies except under written agreement LTE Long Term
LTE Overview October 6, 2011 Robert Barringer Enterprise Architect AT&T Proprietary (Internal Use Only) Not for use or disclosure outside the AT&T companies except under written agreement LTE Long Term
International Journal of Computing and Business Research (IJCBR)
 AN INVESTIGATION OF GSM ARCHITECTURE AND OVERLAYING WITH EFFICIENT SECURITY PROTOCOL Karun Madan, Surya World Institute of Engg. & Technology, Rajpura, Punjab ABSTRACT The Global System for Mobile Communications
AN INVESTIGATION OF GSM ARCHITECTURE AND OVERLAYING WITH EFFICIENT SECURITY PROTOCOL Karun Madan, Surya World Institute of Engg. & Technology, Rajpura, Punjab ABSTRACT The Global System for Mobile Communications
Authentication and Security in IP based Multi Hop Networks
 7TH WWRF MEETING IN EINDHOVEN, THE NETHERLANDS 3RD - 4TH DECEMBER 2002 1 Authentication and Security in IP based Multi Hop Networks Frank Fitzek, Andreas Köpsel, Patrick Seeling Abstract Network security
7TH WWRF MEETING IN EINDHOVEN, THE NETHERLANDS 3RD - 4TH DECEMBER 2002 1 Authentication and Security in IP based Multi Hop Networks Frank Fitzek, Andreas Köpsel, Patrick Seeling Abstract Network security
Network Infrastructure Security in Cellular Data Networks: An Initial Investigation
 Network Infrastructure Security in Cellular Data Networks: An Initial Investigation Kavita Barapatre, Nirlesh Koshta, Vishal Sharma IIT Bombay, Mumbai, India and Fabio Ricciato Forschungszentrum Telekommunikation
Network Infrastructure Security in Cellular Data Networks: An Initial Investigation Kavita Barapatre, Nirlesh Koshta, Vishal Sharma IIT Bombay, Mumbai, India and Fabio Ricciato Forschungszentrum Telekommunikation
Product Description. HiLink E3531 HSPA+ USB Stick V100R001 HUAWEI TECHNOLOGIES CO., LTD. Issue 01. Date 2013-6-13
 HiLink E3531 HSPA+ USB Stick V100R001 Issue 01 Date 2013-6-13 HUAWEI TECHNOLOGIES CO., LTD. Huawei Technologies Co., Ltd. provides customers with comprehensive technical support and service. Please feel
HiLink E3531 HSPA+ USB Stick V100R001 Issue 01 Date 2013-6-13 HUAWEI TECHNOLOGIES CO., LTD. Huawei Technologies Co., Ltd. provides customers with comprehensive technical support and service. Please feel
1G to 4G. Overview. Presentation By Rajeev Bansal Director(Mobile-1) Telecommunication Engineering Centre
 1G to 4G Overview Presentation By Rajeev Bansal Director(Mobile-1) Telecommunication Engineering Centre Mobile Networks differentiated from each other by the word Generation 1G, 2G, 2.5G, 2.75G, 3G milestones
1G to 4G Overview Presentation By Rajeev Bansal Director(Mobile-1) Telecommunication Engineering Centre Mobile Networks differentiated from each other by the word Generation 1G, 2G, 2.5G, 2.75G, 3G milestones
Mobile Services (ST 2010)
 Mobile Services (ST 2010) Chapter 3: Mobility Management Axel Küpper Service-centric Networking Deutsche Telekom Laboratories, TU Berlin 1 Mobile Services Summer Term 2010 3 Mobility Management 3.1 Handover
Mobile Services (ST 2010) Chapter 3: Mobility Management Axel Küpper Service-centric Networking Deutsche Telekom Laboratories, TU Berlin 1 Mobile Services Summer Term 2010 3 Mobility Management 3.1 Handover
GSM Databases. Virginia Location Area HLR Vienna Cell Virginia BSC. Virginia MSC VLR
 Update ( Update Procedure) Network Mobiles Maryland Maryland Other Rockville Bethesda Maryland Mobile Mobile Cell Cell HLR Vienna Cell 12-Jun-14 22:48 (Page 1) This sequence diagram was generated with
Update ( Update Procedure) Network Mobiles Maryland Maryland Other Rockville Bethesda Maryland Mobile Mobile Cell Cell HLR Vienna Cell 12-Jun-14 22:48 (Page 1) This sequence diagram was generated with
GSM LOGICAL CHANNELS
 GSM LOGICAL CHANNELS There are two types of GSM logical channels 1. Traffic Channels (TCHs) 2. Control Channels (CCHs) Traffic channels carry digitally encoded user speech or user data and have identical
GSM LOGICAL CHANNELS There are two types of GSM logical channels 1. Traffic Channels (TCHs) 2. Control Channels (CCHs) Traffic channels carry digitally encoded user speech or user data and have identical
Global System for Mobile Communication (GSM)
 Global System for Mobile Communication (GSM) Definition Global system for mobile communication (GSM) is a globally accepted standard for digital cellular communication. GSM is the name of a standardization
Global System for Mobile Communication (GSM) Definition Global system for mobile communication (GSM) is a globally accepted standard for digital cellular communication. GSM is the name of a standardization
IMSI Catcher. Daehyun Strobel. 13.Juli 2007. Seminararbeit Ruhr-Universität Bochum. Chair for Communication Security Prof. Dr.-Ing.
 IMSI Catcher Daehyun Strobel 13.Juli 2007 Seminararbeit Ruhr-Universität Bochum Chair for Communication Security Prof. Dr.-Ing. Christof Paar Contents 1 Introduction 1 2 GSM (Global System for Mobile
IMSI Catcher Daehyun Strobel 13.Juli 2007 Seminararbeit Ruhr-Universität Bochum Chair for Communication Security Prof. Dr.-Ing. Christof Paar Contents 1 Introduction 1 2 GSM (Global System for Mobile
ASR 5x00 Series SGSN Authentication and PTMSI Reallocation Best Practices
 ASR 5x00 Series SGSN Authentication and PTMSI Reallocation Best Practices Document ID: 119148 Contributed by Krishna Kishore DV, Sujin Anagani, and Parthasarathy M, Cisco TAC Engineers. Jun 12, 2015 Contents
ASR 5x00 Series SGSN Authentication and PTMSI Reallocation Best Practices Document ID: 119148 Contributed by Krishna Kishore DV, Sujin Anagani, and Parthasarathy M, Cisco TAC Engineers. Jun 12, 2015 Contents
Mobile Phone Security. Hoang Vo Billy Ngo
 Mobile Phone Security Hoang Vo Billy Ngo Table of Content 1. Introduction Page 2 1.1 Analog Network Page 2 1.2 Digital Network Page 2 2. Security Protocols Page 4 2.1 Analog Page 4 2.2 Digital Page 5 3.
Mobile Phone Security Hoang Vo Billy Ngo Table of Content 1. Introduction Page 2 1.1 Analog Network Page 2 1.2 Digital Network Page 2 2. Security Protocols Page 4 2.1 Analog Page 4 2.2 Digital Page 5 3.
Mobile network security report: Poland
 Mobile network security report: Poland GSM Map Project gsmmap@srlabs.de Security Research Labs, Berlin February 2015 Abstract. Mobile networks differ widely in their protection capabilities against common
Mobile network security report: Poland GSM Map Project gsmmap@srlabs.de Security Research Labs, Berlin February 2015 Abstract. Mobile networks differ widely in their protection capabilities against common
(U)SimMonitor: A Mobile Application for Security Evaluation of Cellular Networks
 (U)SimMonitor: A Mobile Application for Security Evaluation of Cellular Networks Christos Xenakis, Christoforos Ntantogian, Orestis Panos Department of Digital Systems, University of Piraeus Piraeus, Greece
(U)SimMonitor: A Mobile Application for Security Evaluation of Cellular Networks Christos Xenakis, Christoforos Ntantogian, Orestis Panos Department of Digital Systems, University of Piraeus Piraeus, Greece
NTT DOCOMO Technical Journal. Core Network Infrastructure and Congestion Control Technology for M2M Communications
 M2M 3GPP Standardization Further Development of LTE/LTE-Advanced LTE Release 10/11 Standardization Trends Core Network Infrastructure and Congestion Control Technology for M2M Communications The number
M2M 3GPP Standardization Further Development of LTE/LTE-Advanced LTE Release 10/11 Standardization Trends Core Network Infrastructure and Congestion Control Technology for M2M Communications The number
How to secure an LTE-network: Just applying the 3GPP security standards and that's it?
 How to secure an LTE-network: Just applying the 3GPP security standards and that's it? Telco Security Day @ Troopers 2012 Peter Schneider Nokia Siemens Networks Research 1 Nokia Siemens Networks 2012 Intro
How to secure an LTE-network: Just applying the 3GPP security standards and that's it? Telco Security Day @ Troopers 2012 Peter Schneider Nokia Siemens Networks Research 1 Nokia Siemens Networks 2012 Intro
1 Introduction to mobile telecommunications
 1 Introduction to mobile telecommunications Mobile phones were first introduced in the early 1980s. In the succeeding years, the underlying technology has gone through three phases, known as generations.
1 Introduction to mobile telecommunications Mobile phones were first introduced in the early 1980s. In the succeeding years, the underlying technology has gone through three phases, known as generations.
Mobile network security report: Norway
 Mobile network security report: Norway GSM Map Project gsmmap@srlabs.de Security Research Labs, Berlin August 2014 Abstract. Mobile networks differ widely in their protection capabilities against common
Mobile network security report: Norway GSM Map Project gsmmap@srlabs.de Security Research Labs, Berlin August 2014 Abstract. Mobile networks differ widely in their protection capabilities against common
