... view 1 view 2 view n. implementation
|
|
|
- Magnus Carr
- 7 years ago
- Views:
Transcription
1 1 MULTIPLE VIEWS IN SOFTWARE ARCHITECTURE: CONSISTENCY AND CONFORMANCE POSITION PAPER D. Le Metayer and M. Perin MULTIPLE VIEWS: SIGNIFICANCE AND PROBLEMS The study of software architectures has grown as an autonomous discipline recently. A widely accepted, and very general, characterisation of software architectures can be sketched as follows [Shaw and Garlan, 1995]: \Software architecture is the level of software design that addresses the overall structure and properties of software systems". The success of this trend of work is based on two major assumptions: Much benet has to be gained from the description of software systems at a high level of abstraction: pay-os are expected in terms of quality of design, maintenance, analysis, verication, testing, communication between developers, etc. Software architectures involve specic concepts which require specic languages, techniques and tools. Irisa/Inria, Campus de Beaulieu, Rennes, France. lemetayer/mperin@irisa.fr 1
2 2 The rst assumption is hardly arguable in principle even if better tools and architecture development environments are still needed to really assess the practical signicance of the whole approach. The second assumption is sometimes questioned outside the emerging \software architecture community" because a number of issues related to software architectures have been studied in dierent contexts in the past. Abstract (and even nite state) models of real systems have been used for a long time and the notions of abstract interpretation [Cousot and Cousot, 1979] and property preserving abstraction [Loiseaux et al., 1995] have been formalised and studied extensively for various classes of programming languages (concurrent, sequential, functional, logic, etc.). Furthermore, as far as formalisms are concerned, process calculi such as CSP or the -calculus provide concurrency and synchronisation features that can also be used to specify the communication protocols between components in an architecture [Allen and Garlan, 1994, Radestock and Eisenbach, 1996]; sophisticated facilities for modularity are oered by functional languages of the ML family (SML, CAML, etc.) [MacQueen, 1985]; also synchronous languages provide formal semantics of box and line drawings used for describing real-time systems [Benveniste and Berry, 1991]. So it is legitimate at this stage to put the specicity of software architectures under scrutiny and discuss whether it justies the development of a new research area. First, as far as abstract interpretation is concerned, it should be noticed that it has mainly been used in a bottom-up rather than a top-down fashion so far. In other words, it has mostly been concerned with (a posteriori) analysis rather than design and renement. So one interesting issue in the context of software architecture would be the application of the abstract interpretation framework to the renement of global properties. This would lead, strictly speaking, to a \concrete interpretation" process. Second, and more importantly, we believe that the doubts mentioned above have been fuelled by the fact that the range of works published in this area so far does not reect the generality of the approach. It turns out that most of them are concerned with communication and synchronisation which is just one of the aspects of a software architecture. In particular, non functional properties such as security, performance, reliability and extensibility have not received enough attention. But the study of each of these properties may require a dierent kind of decomposition of the software. For this reason, we believe that the notion of \view" is crucial and deserves more consideration in the context of software architectures. A number of variants of the notion of view have been proposed in dierent areas of computer science: In development methods: for example RM-ODP descriptions [Bourgois et al., 1998] include ve viewpoints (enterprise, information, computational, engineering and technology); [Finkelstein et al., 1992] proposes a framework supporting the denition and use of multiple viewpoints in system development; UML also promotes the use of multiple views (as collections of diagrams such as static structure, statechart, component and deployment diagrams) to describe complex systems.
3 MULTIPLE VIEWS IN SOFTWARE ARCHITECTURE 3 In programming languages: Aspect Oriented Programming [Kiczales, 1996] puts forward a technique for the development of programs as collections of aspects (such as synchronisation, communication, failure handling, memory allocation) which isolate important design decisions that would otherwise be scattered throughout the code. In programming language semantics: the \action semantics" framework [Mosses, 1996] denes the meaning of a program using a number of \facets" (such as control ow, functional, declarative, imperative, communicative, etc.), each of them focussing on one specic kind of information (control ow, data ow, scoping, memory, communications, etc.). In database systems: most database management systems provide a facility for dening and querying views which can be seen as abstractions of the actual database [Ullman, 1988]. Views are typically used to ensure that specic elds of the database are not accessible to certain classes of users or to provide information that is not explicit in the actual database (but can be derived from it). The relevance of the notion of view for software architectures has already been advocated in [Kruchten, 1995] but, to our best knowledge, no existing ADL really supports the notion of multiple views. A major issue that must be addressed before introducing multiple views in an ADL is the specication of the correspondences between the dierent views. Ideally, a form of consistency should be dened and automatic tools should be provided to help in the design of an overall consistent architecture. The conformance of a system with respect to a given architecture is another signicant issue. Although not specic to the notion of view, this problem is compounded by the introduction of multiple views. There may bea great diversity of views and it is unlikely that one single technique can be appropriate to ensure conformance with respect to each of them. None of the works on the variants of views mentioned above provides solutions to the consistency and the conformance problems for software architecture views, either because they do not rely on rm theoretical foundations or because they cannot be transposed to the general notion of view that is required in the context of software architectures. We believe that the study of these problems is a research direction of prime importance for software architectures. In the rest of this position paper, we mainly focus on consistency and summarise a preliminary approach that we are currently experimenting through two case studies: the specication of security properties of an information system and the design of a train control system. CONSISTENCY AND HETEROGENEITY OF MULTIPLE VIEWS In order to get the greatest benets of the approach, the decomposition into multiple views should be chosen in such a way that it minimises the dependencies between views (otherwise little has to be gained from their separation). However all the views ultimately relate to the implemented system and they
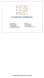
4 4 can rarely be completely independent. For example, the distribution view can have some impact on the security view and the fault-tolerance view. Dierent views may even correspond to conicting requirements: for instance adding a communication link can improve fault tolerance but also have a negative eect on security (because it may give rise to unwanted information ows). The consistency problem is compounded by the inherent heterogeneity of multiple view architectures: since there can be a great diversity of views, each of them should be expressed in the framework (model, specication language, notation, etc.) that is best suited to its specic purpose. It is dicult to imagine a general and semantics based solution to the consistency problem in this context. Previous work on consistency across specication languages [Zave and Jackson, 1993, Bowman et al., 1996] has considered either an intermediate language or a common underlying implementation. For example [Bowman et al., 1996] states that \n specications are consistent if and only if there exists a physical implementation which is a realisation of all the specications, ie. all the specications can be implemented in a single system". This implementation consistency is pictured in Figure view 1 view 2 view n implementation Figure 1.1 Implementation consistency So in all cases mappings have to be dened from each view specication language to a single formalism. This solution may be appropriate when the formalisms used to describe the views are not of a too dierent nature (like Z and LOTOS considered in [Bowman et al., 1996]), which is precisely not the case for software architectures. So we believe that this \single formalism mapping approach" would defeat the very purpose of the introduction of views in software architecture. In other words, little would be gained, in terms of verication, if, to decide upon their consistency, all the views had to be merged into a single all embracing specication. We believe that the issues of consistency and conformance should better be decoupled for a better separation of concerns and an increased tractability. The approach that we are currently experimenting can be sketched as follows: Consistency: each view is represented as an uninterpreted labelled graph. Graphs are widely used representations of software architectures and all the views that we have considered so far (functional, distribution, physical, security, etc.) can be expressed naturally in terms of graphs. The fact that a view dened in a specic framework has rst to be ex-
5 MULTIPLE VIEWS IN SOFTWARE ARCHITECTURE 5 pressed as a graph may be seen as a limitation of the approach. Note however that the versatile nature of graphs and the fact that they are uninterpreted makes this translation easier. The uninterpreted nature of our graphs is a major departure with respect to previous work on consistency across specication languages: even if all the views are expressed as graphs, each of these graphs may convey very dierent kind of semantic information. The only restrictions on graphs are expressed through a collection of structural constraints (also called internal consistency rules), which bear, for example on the number of nodes with a given label or the number of edges (or paths) from (and/or to) a given node, etc. We consider inter-view consistency as a local relation between two views 2. This relation is dened using a correspondence relation between the nodes (and edges) of the two views plus structural constraints similar to the internal consistency rules. Our approach, which introduces a clear separation between consistency and conformance, is depicted in Figure 1.2. The potential shortcoming of this local approach (as opposed to the \single formalism mapping approach") is that the number of correspondence relations may grow quadratically (in the worst case) with the number of views. We envision that the number of views will remain low though and the expected benet is a lower complexity and a better understandability of correspondence relations. inter-view concistency relations view 1 view 2... view n internal consistency conformance relations implementation Figure 1.2 Separation of local consistency and conformance Conformance: in our approach, heterogeneity issues are isolated from the denition of consistency for a better separation of concerns. We believe that heterogeneity is better handled as a conformance problem between each view and the actual system. By denition, there is no general solution to this problem since the set of possible frameworks for the denition of view is open-ended and potentially varied. Just to take an example, there is very little in common between the proof that a program satises a given data-ow property and the verication that the 2 Consistency relations involving more than two views can be dened as well, but they didn't turn out to be useful on the examples that we have treated so far.
6 6 bandwidth of a hardware bus is greater than a given threshold. Furthermore, it should be noted that this conformance process can either be bottom-up (recovering aspects of the architecture from the actual code) or top-down and prescriptive (when a view can be compiled into executable code, thus ensuring, by construction, that the actual system conforms to the view). We have followed the latter approach in the work described in [Holzbacher et al., 1997], which shows how the communication view can be implemented as an eective coordinator. The ideas put forward in this paper are still preliminary and we are currently experimenting them on two case studies: The specication of the security aspects (condentiality, integrity) of the information system of a research center: the dierent views in this case correspond to the services provided by the system: web server, rlogin server, ftp server, etc. The consistency constraints are used to ensure a global coherency of the security policy: for example, \if there is an edge with security level l between two nodes (or sites) n 1 and n 2, there should not exist any path between n 1 and n 2 in which all the edges have a security level strictly less than l". The design of a train control system: the relevant views are the functional view, the distribution view and the physical view. An example of consistency constraint is that the distribution view preserves the data ow of the functional view (which is a path property between the related nodes). It is too early to draw any conclusion from these ongoing experiences but we feel that the approach sketched here is suciently practical to provide useful help in the design of multiple view architectures. Further interesting issues have emerged from these studies; among them let us just mention briey software architecture analysis. The analysis of a software architecture gets more complicated when the properties of interest are non functional. The reason is that they can usually not be characterised by a predicate (they may even be subjective). Instead of providing a yes/no answer, we must return a concise and understandable piece of information that the user can estimate by himself. For example, in the case of a security property, the output of the analysis can be \for such a security breach to be possible, the intruder must be able to spy network N and have access to machine M". References [Allen and Garlan, 1994] Allen, R. and Garlan, D. (1994). Formalizing architectural connection. In Proceedings of the 16th International Conference on Software Engineering, pages 71{80. IEEE Computer Society Press. [Benveniste and Berry, 1991] Benveniste, A. and Berry, G. (1991). The synchronous approach to reactive and real{time systems. IEEE Trans. Autom. Control, 9(79):1270{1282.
7 MULTIPLE VIEWS IN SOFTWARE ARCHITECTURE 7 [Bourgois et al., 1998] Bourgois, M., Franklin, D., and Robinson, P. (1998). Applying RM-ODP to the Air Trac Management Domain. EATCHiP Technical Document (CSD/architecture), Eurocontrol, Brussels. [Bowman et al., 1996] Bowman, H., Boiten, E., Derrick, J., and Steen, M. (1996). Viewpoint consistency in ODP, a general interpretation. In Najm, E. and Stefani, J.-B., editors, First IFIP International Workshop on Formal Methods for Open Object-Based Distributed Systems, pages 189{204. Chapman & Hall. [Cousot and Cousot, 1979] Cousot, P. and Cousot, R. (1979). Systematic design of program analysis frameworks. In Conference Record of the Sixth Annual ACM Symposium on Principles of Programming Languages, pages 269{282. [Finkelstein et al., 1992] Finkelstein, A., Kramer, J., Nuseibeh, B., Finkelstein, L., and Goedicke, M. (1992). Viewpoints: A framework for integrating multiple perspectives in systems development. International Journal of Software Engineering and Knowledge Engineering, 1(2):31{58. [Holzbacher et al., 1997] Holzbacher, A. A., Perin, M., and Sudholt, M. (1997). Modeling railway control systems using graph grammars: a case study. In Proceedings of the Second Conference on Coordination Models, Languages and Applications, volume 1282 of LNCS, pages 172{186, Berlin. [Kiczales, 1996] Kiczales, G. (1996). Aspect-oriented programming. ACM Computing Surveys, 28(4es):154{154. [Kruchten, 1995] Kruchten, P. B. (1995). The view model of architecture. IEEE Software, 12(6):42{50. [Loiseaux et al., 1995] Loiseaux, C., Graf, S., Sifakis, J., Bouajjani, A., and Bensale, S. (1995). Property preserving abstractions for the verication of concurrent systems. Formal Methods in System Design, 6(1):1{35. [MacQueen, 1985] MacQueen, D. (1985). Modules for standard ML. Dept. Computer Science, University of Edinburgh. [Mosses, 1996] Mosses, P. D. (1996). A tutorial on action semantics. Technical report, BRICS. Tutorial notes for FME'94 and FME'96. [Radestock and Eisenbach, 1996] Radestock, M. and Eisenbach, S. (1996). Semantics of a Higher-Order Coordination Language. In Ciancarini, P. and Hankin, C., editors, Proceedings of the Conference oncoordination Models, Languages and Applications, volume 1061 of LNCS, pages 339{356. [Shaw and Garlan, 1995] Shaw, M. and Garlan, D. (1995). Formulations and Formalisms in Software Architecture. In Computer Science Today, Recent Trends and Developments, volume 1000 of LNCS, pages 307{323. [Ullman, 1988] Ullman, J. D. (1988). Principles of database and knowledge-base systems, Vol. I. Computer Science Press, Inc., Rockville, MD, USA. [Zave and Jackson, 1993] Zave, P. and Jackson, M. (1993). Conjunction as composition. ACM Transactions of Software Engineering and Methodology, 2(4):379{411.
Thesis work and research project
 Thesis work and research project Hélia Pouyllau, INRIA of Rennes, Campus Beaulieu 35042 Rennes, helia.pouyllau@irisa.fr July 16, 2007 1 Thesis work on Distributed algorithms for endto-end QoS contract
Thesis work and research project Hélia Pouyllau, INRIA of Rennes, Campus Beaulieu 35042 Rennes, helia.pouyllau@irisa.fr July 16, 2007 1 Thesis work on Distributed algorithms for endto-end QoS contract
Verifying Semantic of System Composition for an Aspect-Oriented Approach
 2012 International Conference on System Engineering and Modeling (ICSEM 2012) IPCSIT vol. 34 (2012) (2012) IACSIT Press, Singapore Verifying Semantic of System Composition for an Aspect-Oriented Approach
2012 International Conference on System Engineering and Modeling (ICSEM 2012) IPCSIT vol. 34 (2012) (2012) IACSIT Press, Singapore Verifying Semantic of System Composition for an Aspect-Oriented Approach
Quotes from Object-Oriented Software Construction
 Quotes from Object-Oriented Software Construction Bertrand Meyer Prentice-Hall, 1988 Preface, p. xiv We study the object-oriented approach as a set of principles, methods and tools which can be instrumental
Quotes from Object-Oriented Software Construction Bertrand Meyer Prentice-Hall, 1988 Preface, p. xiv We study the object-oriented approach as a set of principles, methods and tools which can be instrumental
programming languages, programming language standards and compiler validation
 Software Quality Issues when choosing a Programming Language C.J.Burgess Department of Computer Science, University of Bristol, Bristol, BS8 1TR, England Abstract For high quality software, an important
Software Quality Issues when choosing a Programming Language C.J.Burgess Department of Computer Science, University of Bristol, Bristol, BS8 1TR, England Abstract For high quality software, an important
Chap 1. Introduction to Software Architecture
 Chap 1. Introduction to Software Architecture 1. Introduction 2. IEEE Recommended Practice for Architecture Modeling 3. Architecture Description Language: the UML 4. The Rational Unified Process (RUP)
Chap 1. Introduction to Software Architecture 1. Introduction 2. IEEE Recommended Practice for Architecture Modeling 3. Architecture Description Language: the UML 4. The Rational Unified Process (RUP)
Aerospace Software Engineering
 16.35 Aerospace Software Engineering Software Architecture The 4+1 view Patterns Prof. Kristina Lundqvist Dept. of Aero/Astro, MIT Why Care About Software Architecture? An architecture provides a vehicle
16.35 Aerospace Software Engineering Software Architecture The 4+1 view Patterns Prof. Kristina Lundqvist Dept. of Aero/Astro, MIT Why Care About Software Architecture? An architecture provides a vehicle
Questions? Assignment. Techniques for Gathering Requirements. Gathering and Analysing Requirements
 Questions? Assignment Why is proper project management important? What is goal of domain analysis? What is the difference between functional and non- functional requirements? Why is it important for requirements
Questions? Assignment Why is proper project management important? What is goal of domain analysis? What is the difference between functional and non- functional requirements? Why is it important for requirements
Component visualization methods for large legacy software in C/C++
 Annales Mathematicae et Informaticae 44 (2015) pp. 23 33 http://ami.ektf.hu Component visualization methods for large legacy software in C/C++ Máté Cserép a, Dániel Krupp b a Eötvös Loránd University mcserep@caesar.elte.hu
Annales Mathematicae et Informaticae 44 (2015) pp. 23 33 http://ami.ektf.hu Component visualization methods for large legacy software in C/C++ Máté Cserép a, Dániel Krupp b a Eötvös Loránd University mcserep@caesar.elte.hu
 Graph Visualization U. Dogrusoz and G. Sander Tom Sawyer Software, 804 Hearst Avenue, Berkeley, CA 94710, USA info@tomsawyer.com Graph drawing, or layout, is the positioning of nodes (objects) and the
Graph Visualization U. Dogrusoz and G. Sander Tom Sawyer Software, 804 Hearst Avenue, Berkeley, CA 94710, USA info@tomsawyer.com Graph drawing, or layout, is the positioning of nodes (objects) and the
Modular Communication Infrastructure Design with Quality of Service
 Modular Communication Infrastructure Design with Quality of Service Pawel Wojciechowski and Péter Urbán Distributed Systems Laboratory School of Computer and Communication Sciences Swiss Federal Institute
Modular Communication Infrastructure Design with Quality of Service Pawel Wojciechowski and Péter Urbán Distributed Systems Laboratory School of Computer and Communication Sciences Swiss Federal Institute
A B C. Decomposition I Y
 Software Development byevolution 3 Shaoying Liu Department of Computer Science Faculty of Information Sciences Hiroshima City University, Japan Email: shaoying@cs.hiroshima-cu.ac.jp Introduction Software
Software Development byevolution 3 Shaoying Liu Department of Computer Science Faculty of Information Sciences Hiroshima City University, Japan Email: shaoying@cs.hiroshima-cu.ac.jp Introduction Software
Applying 4+1 View Architecture with UML 2. White Paper
 Applying 4+1 View Architecture with UML 2 White Paper Copyright 2007 FCGSS, all rights reserved. www.fcgss.com Introduction Unified Modeling Language (UML) has been available since 1997, and UML 2 was
Applying 4+1 View Architecture with UML 2 White Paper Copyright 2007 FCGSS, all rights reserved. www.fcgss.com Introduction Unified Modeling Language (UML) has been available since 1997, and UML 2 was
Cedalion A Language Oriented Programming Language (Extended Abstract)
 Cedalion A Language Oriented Programming Language (Extended Abstract) David H. Lorenz Boaz Rosenan The Open University of Israel Abstract Implementations of language oriented programming (LOP) are typically
Cedalion A Language Oriented Programming Language (Extended Abstract) David H. Lorenz Boaz Rosenan The Open University of Israel Abstract Implementations of language oriented programming (LOP) are typically
Managing Variability in Software Architectures 1 Felix Bachmann*
 Managing Variability in Software Architectures Felix Bachmann* Carnegie Bosch Institute Carnegie Mellon University Pittsburgh, Pa 523, USA fb@sei.cmu.edu Len Bass Software Engineering Institute Carnegie
Managing Variability in Software Architectures Felix Bachmann* Carnegie Bosch Institute Carnegie Mellon University Pittsburgh, Pa 523, USA fb@sei.cmu.edu Len Bass Software Engineering Institute Carnegie
The Consequences of Process Modeling For Compliance
 Standards Compliant Software Development Wolfgang Emmerich, Anthony Finkelstein Interoperable Systems Research Centre City University London EC1V 0HB, UK femmerich j acwfg@cs.city.ac.uk Carlo Montangero
Standards Compliant Software Development Wolfgang Emmerich, Anthony Finkelstein Interoperable Systems Research Centre City University London EC1V 0HB, UK femmerich j acwfg@cs.city.ac.uk Carlo Montangero
Common Criteria For Information Technology Security Evaluation
 Security Characterisation and Integrity Assurance for Software Components and Component-Based Systems Jun Han and Yuliang Zheng Peninsula School of Computing and Information Technology Monash University,
Security Characterisation and Integrity Assurance for Software Components and Component-Based Systems Jun Han and Yuliang Zheng Peninsula School of Computing and Information Technology Monash University,
Aspect-Oriented Programming
 Aspect-Oriented Programming An Introduction to Aspect-Oriented Programming and AspectJ Niklas Påhlsson Department of Technology University of Kalmar S 391 82 Kalmar SWEDEN Topic Report for Software Engineering
Aspect-Oriented Programming An Introduction to Aspect-Oriented Programming and AspectJ Niklas Påhlsson Department of Technology University of Kalmar S 391 82 Kalmar SWEDEN Topic Report for Software Engineering
Handbook for the Computer Security Certification of Trusted Systems
 Handbook for the Computer Security Certification of Trusted Systems Chapter 1: Overview Chapter 2: Development Plan Chapter 3: Formal Model of the Security Policy Chapter 4: Descriptive Top-Level Specification
Handbook for the Computer Security Certification of Trusted Systems Chapter 1: Overview Chapter 2: Development Plan Chapter 3: Formal Model of the Security Policy Chapter 4: Descriptive Top-Level Specification
 Verication by Finitary Abstraction Weizmann Institute of Sciences and Universite Joseph Fourier, Grenoble Fourth International Spin Workshop (SPIN'98) Paris 2.11.98 Joint work with: Y. Kesten Ben Gurion
Verication by Finitary Abstraction Weizmann Institute of Sciences and Universite Joseph Fourier, Grenoble Fourth International Spin Workshop (SPIN'98) Paris 2.11.98 Joint work with: Y. Kesten Ben Gurion
Algorithms, Flowcharts & Program Design. ComPro
 Algorithms, Flowcharts & Program Design ComPro Definition Algorithm: o sequence of steps to be performed in order to solve a problem by the computer. Flowchart: o graphical or symbolic representation of
Algorithms, Flowcharts & Program Design ComPro Definition Algorithm: o sequence of steps to be performed in order to solve a problem by the computer. Flowchart: o graphical or symbolic representation of
Software Quality Factors OOA, OOD, and OOP Object-oriented techniques enhance key external and internal software quality factors, e.g., 1. External (v
 Object-Oriented Design and Programming Deja Vu? In the past: Structured = Good Overview of Object-Oriented Design Principles and Techniques Today: Object-Oriented = Good e.g., Douglas C. Schmidt www.cs.wustl.edu/schmidt/
Object-Oriented Design and Programming Deja Vu? In the past: Structured = Good Overview of Object-Oriented Design Principles and Techniques Today: Object-Oriented = Good e.g., Douglas C. Schmidt www.cs.wustl.edu/schmidt/
Decomposition into Parts. Software Engineering, Lecture 4. Data and Function Cohesion. Allocation of Functions and Data. Component Interfaces
 Software Engineering, Lecture 4 Decomposition into suitable parts Cross cutting concerns Design patterns I will also give an example scenario that you are supposed to analyse and make synthesis from The
Software Engineering, Lecture 4 Decomposition into suitable parts Cross cutting concerns Design patterns I will also give an example scenario that you are supposed to analyse and make synthesis from The
IAI : Expert Systems
 IAI : Expert Systems John A. Bullinaria, 2005 1. What is an Expert System? 2. The Architecture of Expert Systems 3. Knowledge Acquisition 4. Representing the Knowledge 5. The Inference Engine 6. The Rete-Algorithm
IAI : Expert Systems John A. Bullinaria, 2005 1. What is an Expert System? 2. The Architecture of Expert Systems 3. Knowledge Acquisition 4. Representing the Knowledge 5. The Inference Engine 6. The Rete-Algorithm
French Scheme CSPN to CC Evaluation
 French Scheme CSPN to CC Evaluation Antoine COUTANT ITSEF AMOSSYS 4 bis allée du bâtiment 35000 Rennes antoine.coutant@amossys.fr Abstract. Since 2008, French certication body created a new scheme for
French Scheme CSPN to CC Evaluation Antoine COUTANT ITSEF AMOSSYS 4 bis allée du bâtiment 35000 Rennes antoine.coutant@amossys.fr Abstract. Since 2008, French certication body created a new scheme for
ISF: A Visual Formalism for Specifying Interconnection Styles. for Software Design. Drexel University. 3141 Chestnut Street,
 ISF: A Visual Formalism for Specifying Interconnection Styles for Software Design Spiros Mancoridis Department of Mathematics & Computer Science Drexel University 3141 Chestnut Street, Philadelphia, PA,
ISF: A Visual Formalism for Specifying Interconnection Styles for Software Design Spiros Mancoridis Department of Mathematics & Computer Science Drexel University 3141 Chestnut Street, Philadelphia, PA,
 Chapter 4 Multi-Stage Interconnection Networks The general concept of the multi-stage interconnection network, together with its routing properties, have been used in the preceding chapter to describe
Chapter 4 Multi-Stage Interconnection Networks The general concept of the multi-stage interconnection network, together with its routing properties, have been used in the preceding chapter to describe
An Approach to Software Architecture Description Using UML
 An Approach to Software Architecture Description Using UML Henrik Bærbak Christensen, Aino Corry, and Klaus Marius Hansen Department of Computer Science, University of Aarhus Aabogade 34, 8200 Århus N,
An Approach to Software Architecture Description Using UML Henrik Bærbak Christensen, Aino Corry, and Klaus Marius Hansen Department of Computer Science, University of Aarhus Aabogade 34, 8200 Århus N,
Data Flow-based Validation of Web Services Compositions: Perspectives and Examples
 Data Flow-based Validation of Web Services Compositions: Perspectives and Examples Cesare Bartolini 1, Antonia Bertolino 1, Eda Marchetti 1, Ioannis Parissis 1,2 1 ISTI - CNR Via Moruzzi 1-56124 Pisa 2
Data Flow-based Validation of Web Services Compositions: Perspectives and Examples Cesare Bartolini 1, Antonia Bertolino 1, Eda Marchetti 1, Ioannis Parissis 1,2 1 ISTI - CNR Via Moruzzi 1-56124 Pisa 2
PS engine. Execution
 A Model-Based Approach to the Verication of Program Supervision Systems Mar Marcos 1 y, Sabine Moisan z and Angel P. del Pobil y y Universitat Jaume I, Dept. of Computer Science Campus de Penyeta Roja,
A Model-Based Approach to the Verication of Program Supervision Systems Mar Marcos 1 y, Sabine Moisan z and Angel P. del Pobil y y Universitat Jaume I, Dept. of Computer Science Campus de Penyeta Roja,
UML TUTORIALS THE COMPONENT MODEL
 UML TUTORIALS THE COMPONENT MODEL www.sparxsystems.com.au Sparx Systems 2004 Page 1/5 The component model illustrates the software components that will be used to build the system. These may be built up
UML TUTORIALS THE COMPONENT MODEL www.sparxsystems.com.au Sparx Systems 2004 Page 1/5 The component model illustrates the software components that will be used to build the system. These may be built up
Email: m.uschold@ed.ac.uk mudcat@ie.utoronto.ca
 Ontologies: Principles, Methods and Applications Mike Uschold & Michael Gruninger AIAI-TR-191 February 1996 To appear in Knowledge Engineering Review Volume 11 Number 2, June 1996 Mike Uschold Michael
Ontologies: Principles, Methods and Applications Mike Uschold & Michael Gruninger AIAI-TR-191 February 1996 To appear in Knowledge Engineering Review Volume 11 Number 2, June 1996 Mike Uschold Michael
The CVS-Server Case Study: A Formalized Security Architecture
 The CVS-Server Case Study: A Formalized Security Architecture Extended Abstract Achim D. Brucker, Frank Rittinger, and Burkhart Wolff {brucker,rittinge,wolff}@informatik.uni-freiburg.de 1 Introduction
The CVS-Server Case Study: A Formalized Security Architecture Extended Abstract Achim D. Brucker, Frank Rittinger, and Burkhart Wolff {brucker,rittinge,wolff}@informatik.uni-freiburg.de 1 Introduction
Project VIDE Challenges of Executable Modelling of Business Applications
 Project VIDE Challenges of Executable Modelling of Business Applications Radoslaw Adamus *, Grzegorz Falda *, Piotr Habela *, Krzysztof Kaczmarski #*, Krzysztof Stencel *+, Kazimierz Subieta * * Polish-Japanese
Project VIDE Challenges of Executable Modelling of Business Applications Radoslaw Adamus *, Grzegorz Falda *, Piotr Habela *, Krzysztof Kaczmarski #*, Krzysztof Stencel *+, Kazimierz Subieta * * Polish-Japanese
Challenges and Opportunities for formal specifications in Service Oriented Architectures
 ACSD ATPN Xi an China June 2008 Challenges and Opportunities for formal specifications in Service Oriented Architectures Gustavo Alonso Systems Group Department of Computer Science Swiss Federal Institute
ACSD ATPN Xi an China June 2008 Challenges and Opportunities for formal specifications in Service Oriented Architectures Gustavo Alonso Systems Group Department of Computer Science Swiss Federal Institute
CHAPTER 2 MODELLING FOR DISTRIBUTED NETWORK SYSTEMS: THE CLIENT- SERVER MODEL
 CHAPTER 2 MODELLING FOR DISTRIBUTED NETWORK SYSTEMS: THE CLIENT- SERVER MODEL This chapter is to introduce the client-server model and its role in the development of distributed network systems. The chapter
CHAPTER 2 MODELLING FOR DISTRIBUTED NETWORK SYSTEMS: THE CLIENT- SERVER MODEL This chapter is to introduce the client-server model and its role in the development of distributed network systems. The chapter
From Control Loops to Software
 CNRS-VERIMAG Grenoble, France October 2006 Executive Summary Embedded systems realization of control systems by computers Computers are the major medium for realizing controllers There is a gap between
CNRS-VERIMAG Grenoble, France October 2006 Executive Summary Embedded systems realization of control systems by computers Computers are the major medium for realizing controllers There is a gap between
Transforming security audit requirements into a software architecture
 Transforming security audit requirements into a software architecture Koen Yskout, Bart De Win, and Wouter Joosen IBBT-DistriNet, Katholieke Universiteit Leuven, Belgium first.last@cs.kuleuven.be Abstract.
Transforming security audit requirements into a software architecture Koen Yskout, Bart De Win, and Wouter Joosen IBBT-DistriNet, Katholieke Universiteit Leuven, Belgium first.last@cs.kuleuven.be Abstract.
EVALUATION BY PARTS OF TRUSTED. Ravi S. Sandhu. George Mason University, Fairfax, VA 22030-4444
 Proc. 4th RADC Workshop on Multilevel Database Security, Rhode Island, April 1991, pages 122-126. EVALUATION BY PARTS OF TRUSTED DATABASE MANAGEMENT SYSTEMS Ravi S. Sandhu Center for Secure Information
Proc. 4th RADC Workshop on Multilevel Database Security, Rhode Island, April 1991, pages 122-126. EVALUATION BY PARTS OF TRUSTED DATABASE MANAGEMENT SYSTEMS Ravi S. Sandhu Center for Secure Information
Minimizing technical complexities in emerging cloud computing platforms
 Minimizing technical complexities in emerging cloud computing platforms Andreas Menychtas 1, George Kousiouris 1, Dimosthenis Kyriazis 1, Theodora Varvarigou 1 National Technical University of Athens,
Minimizing technical complexities in emerging cloud computing platforms Andreas Menychtas 1, George Kousiouris 1, Dimosthenis Kyriazis 1, Theodora Varvarigou 1 National Technical University of Athens,
Appendix B Data Quality Dimensions
 Appendix B Data Quality Dimensions Purpose Dimensions of data quality are fundamental to understanding how to improve data. This appendix summarizes, in chronological order of publication, three foundational
Appendix B Data Quality Dimensions Purpose Dimensions of data quality are fundamental to understanding how to improve data. This appendix summarizes, in chronological order of publication, three foundational
ACM SIGSOFT SOFTWARE ENGINEERING NOTES vol 17 no 4 Oct 1992 Page 40. Foundations for the Study of Software Architecture
 ACM SIGSOFT SOFTWARE ENGINEERING NOTES vol 17 no 4 Oct 1992 Page 40 Foundations for the Study of Software Architecture Dewayne E. Perry AT&T Bell Laboratories 600 Mountain Avenue Murray Hill, New Jersey
ACM SIGSOFT SOFTWARE ENGINEERING NOTES vol 17 no 4 Oct 1992 Page 40 Foundations for the Study of Software Architecture Dewayne E. Perry AT&T Bell Laboratories 600 Mountain Avenue Murray Hill, New Jersey
A Framework of Model-Driven Web Application Testing
 A Framework of Model-Driven Web Application Testing Nuo Li, Qin-qin Ma, Ji Wu, Mao-zhong Jin, Chao Liu Software Engineering Institute, School of Computer Science and Engineering, Beihang University, China
A Framework of Model-Driven Web Application Testing Nuo Li, Qin-qin Ma, Ji Wu, Mao-zhong Jin, Chao Liu Software Engineering Institute, School of Computer Science and Engineering, Beihang University, China
Managing large sound databases using Mpeg7
 Max Jacob 1 1 Institut de Recherche et Coordination Acoustique/Musique (IRCAM), place Igor Stravinsky 1, 75003, Paris, France Correspondence should be addressed to Max Jacob (max.jacob@ircam.fr) ABSTRACT
Max Jacob 1 1 Institut de Recherche et Coordination Acoustique/Musique (IRCAM), place Igor Stravinsky 1, 75003, Paris, France Correspondence should be addressed to Max Jacob (max.jacob@ircam.fr) ABSTRACT
An Algebra for Feature-Oriented Software Development
 An Algebra for Feature-Oriented Software Development Sven Apel 1, Christian Lengauer 1, Don Batory 2, Bernhard Möller 3, and Christian Kästner 4 1 Department of Informatics and Mathematics, University
An Algebra for Feature-Oriented Software Development Sven Apel 1, Christian Lengauer 1, Don Batory 2, Bernhard Möller 3, and Christian Kästner 4 1 Department of Informatics and Mathematics, University
CONDIS. IT Service Management and CMDB
 CONDIS IT Service and CMDB 2/17 Table of contents 1. Executive Summary... 3 2. ITIL Overview... 4 2.1 How CONDIS supports ITIL processes... 5 2.1.1 Incident... 5 2.1.2 Problem... 5 2.1.3 Configuration...
CONDIS IT Service and CMDB 2/17 Table of contents 1. Executive Summary... 3 2. ITIL Overview... 4 2.1 How CONDIS supports ITIL processes... 5 2.1.1 Incident... 5 2.1.2 Problem... 5 2.1.3 Configuration...
New Generation of Software Development
 New Generation of Software Development Terry Hon University of British Columbia 201-2366 Main Mall Vancouver B.C. V6T 1Z4 tyehon@cs.ubc.ca ABSTRACT In this paper, I present a picture of what software development
New Generation of Software Development Terry Hon University of British Columbia 201-2366 Main Mall Vancouver B.C. V6T 1Z4 tyehon@cs.ubc.ca ABSTRACT In this paper, I present a picture of what software development
Spécication et analyse formelle des politiques de sécurité dans le cloud computing
 Spécication et analyse formelle des politiques de sécurité dans le cloud computing Asma GUESMI, Patrice CLEMENTE, Frédéric LOULERGUE, Pascal BERTHOMÉ Laboratoire d'informatique Fondamentale d'orléans (LIFO)
Spécication et analyse formelle des politiques de sécurité dans le cloud computing Asma GUESMI, Patrice CLEMENTE, Frédéric LOULERGUE, Pascal BERTHOMÉ Laboratoire d'informatique Fondamentale d'orléans (LIFO)
How to Design and Maintain a Secure ICS Network
 Whitepaper How to Design and Maintain a Secure ICS Network Support IEC 62443 Compliance with SilentDefense ICS Authors Daniel Trivellato, PhD - Product Manager Industrial Line Dennis Murphy, MSc - Senior
Whitepaper How to Design and Maintain a Secure ICS Network Support IEC 62443 Compliance with SilentDefense ICS Authors Daniel Trivellato, PhD - Product Manager Industrial Line Dennis Murphy, MSc - Senior
A Tool for Enterprise Architecture Analysis using the PRM formalism
 A Tool for Enterprise Architecture Analysis using the PRM formalism Markus Buschle, Johan Ullberg, Ulrik Franke, Robert Lagerström, and Teodor Sommestad Industrial Information and Control Systems, KTH
A Tool for Enterprise Architecture Analysis using the PRM formalism Markus Buschle, Johan Ullberg, Ulrik Franke, Robert Lagerström, and Teodor Sommestad Industrial Information and Control Systems, KTH
Requirements Analysis through Viewpoints Oriented Requirements Model (VORD)
 Requirements Analysis through Viewpoints Oriented Requirements Model (VORD) Ahmed M. Salem Computer Science Department California State University, Sacramento Sacramento, CA 95819 USA Email: salema@ecs.csus.edu
Requirements Analysis through Viewpoints Oriented Requirements Model (VORD) Ahmed M. Salem Computer Science Department California State University, Sacramento Sacramento, CA 95819 USA Email: salema@ecs.csus.edu
Example EET: request(car, from, to) offer(price) confirmation(card_no)
 Exemplary and Complete Object Interaction Descriptions Ruth Breu, Radu Grosu, Christoph Hofmann, Franz Huber, Ingolf Kruger, Bernhard Rumpe, Monika Schmidt, Wolfgang Schwerin email: fbreur,grosu,hofmannc,huberf,kruegeri,rumpe,schmidtm,schwering
Exemplary and Complete Object Interaction Descriptions Ruth Breu, Radu Grosu, Christoph Hofmann, Franz Huber, Ingolf Kruger, Bernhard Rumpe, Monika Schmidt, Wolfgang Schwerin email: fbreur,grosu,hofmannc,huberf,kruegeri,rumpe,schmidtm,schwering
Automated Test Approach for Web Based Software
 Automated Test Approach for Web Based Software Indrajit Pan 1, Subhamita Mukherjee 2 1 Dept. of Information Technology, RCCIIT, Kolkata 700 015, W.B., India 2 Dept. of Information Technology, Techno India,
Automated Test Approach for Web Based Software Indrajit Pan 1, Subhamita Mukherjee 2 1 Dept. of Information Technology, RCCIIT, Kolkata 700 015, W.B., India 2 Dept. of Information Technology, Techno India,
Karunya University Dept. of Information Technology
 PART A Questions 1. Mention any two software process models. 2. Define risk management. 3. What is a module? 4. What do you mean by requirement process? 5. Define integration testing. 6. State the main
PART A Questions 1. Mention any two software process models. 2. Define risk management. 3. What is a module? 4. What do you mean by requirement process? 5. Define integration testing. 6. State the main
Keywords Aspect-Oriented Modeling, Rule-based graph transformations, Aspect, pointcuts, crosscutting concerns.
 Volume 4, Issue 5, May 2014 ISSN: 2277 128X International Journal of Advanced Research in Computer Science and Software Engineering Research Paper Available online at: www.ijarcsse.com Functional and Non-Functional
Volume 4, Issue 5, May 2014 ISSN: 2277 128X International Journal of Advanced Research in Computer Science and Software Engineering Research Paper Available online at: www.ijarcsse.com Functional and Non-Functional
An Automatic Tool for Checking Consistency between Data Flow Diagrams (DFDs)
 An Automatic Tool for Checking Consistency between Data Flow Diagrams (DFDs) Rosziati Ibrahim, Siow Yen Yen Abstract System development life cycle (SDLC) is a process uses during the development of any
An Automatic Tool for Checking Consistency between Data Flow Diagrams (DFDs) Rosziati Ibrahim, Siow Yen Yen Abstract System development life cycle (SDLC) is a process uses during the development of any
Enterprise Architecture: Practical Guide to Logical Architecture
 Objecteering Practical Guides Enterprise Architecture: Practical Guide to Logical Architecture Author: Version: 1.0 Copyright: Softeam Softeam Consulting Team Supervised by Philippe Desfray Softeam 21
Objecteering Practical Guides Enterprise Architecture: Practical Guide to Logical Architecture Author: Version: 1.0 Copyright: Softeam Softeam Consulting Team Supervised by Philippe Desfray Softeam 21
A UML Introduction Tutorial
 A UML Introduction Tutorial 1/27/08 9:55 PM A UML Introduction Tutorial In this tutorial you will learn about the fundamentals of object oriented modelling, the Unified Modelling Language and the software
A UML Introduction Tutorial 1/27/08 9:55 PM A UML Introduction Tutorial In this tutorial you will learn about the fundamentals of object oriented modelling, the Unified Modelling Language and the software
Software Development in the Fields of Embedded Systems, Safety, and Security
 Software in the Fields of Embedded Systems, Safety, and Security, Erlangen, May 2007 Maritta Heisel Joint work with Denis Hatebur and Holger Schmidt University Duisburg-Essen, Faculty of Engineering, Department
Software in the Fields of Embedded Systems, Safety, and Security, Erlangen, May 2007 Maritta Heisel Joint work with Denis Hatebur and Holger Schmidt University Duisburg-Essen, Faculty of Engineering, Department
Introduction to Service Oriented Architectures (SOA)
 Introduction to Service Oriented Architectures (SOA) Responsible Institutions: ETHZ (Concept) ETHZ (Overall) ETHZ (Revision) http://www.eu-orchestra.org - Version from: 26.10.2007 1 Content 1. Introduction
Introduction to Service Oriented Architectures (SOA) Responsible Institutions: ETHZ (Concept) ETHZ (Overall) ETHZ (Revision) http://www.eu-orchestra.org - Version from: 26.10.2007 1 Content 1. Introduction
Discussing Implicit Parallelism and Its Applications
 OpenStax-CNX module: m19529 1 Discussing Implicit Parallelism and Its Applications Hong Lin This work is produced by OpenStax-CNX and licensed under the Creative Commons Attribution License 2.0 Abstract
OpenStax-CNX module: m19529 1 Discussing Implicit Parallelism and Its Applications Hong Lin This work is produced by OpenStax-CNX and licensed under the Creative Commons Attribution License 2.0 Abstract
Consistency Management for Multiple Perspective Software Development
 Consistency Management for Multiple Perspective Software Development Wai Leung Poon Anthony Finkelstein Dept. of Computing, Dept. of Computer Science, Imperial College, City University, 180 Queen's Gate,
Consistency Management for Multiple Perspective Software Development Wai Leung Poon Anthony Finkelstein Dept. of Computing, Dept. of Computer Science, Imperial College, City University, 180 Queen's Gate,
Architecture Definitions
 Architecture Definitions Dana Bredemeyer Bredemeyer Consulting Tel: (812) 335-1653 Fax: (812) 335-1652 Email: dana@bredemeyer.com Web: Ruth Malan Bredemeyer Consulting Tel: (812) 335-1653 Fax: (812) 335-1652
Architecture Definitions Dana Bredemeyer Bredemeyer Consulting Tel: (812) 335-1653 Fax: (812) 335-1652 Email: dana@bredemeyer.com Web: Ruth Malan Bredemeyer Consulting Tel: (812) 335-1653 Fax: (812) 335-1652
The Service Revolution software engineering without programming languages
 The Service Revolution software engineering without programming languages Gustavo Alonso Institute for Pervasive Computing Department of Computer Science Swiss Federal Institute of Technology (ETH Zurich)
The Service Revolution software engineering without programming languages Gustavo Alonso Institute for Pervasive Computing Department of Computer Science Swiss Federal Institute of Technology (ETH Zurich)
Edited by: Juan Bicarregui. With contributions from: Sten Agerholm. Bart Van Assche. John Fitzgerald. Jacob Frost. Albert Hoogewijs.
 Proof in VDM: case studies Edited by: Juan Bicarregui With contributions from: Sten Agerholm Bart Van Assche John Fitzgerald Jacob Frost Albert Hoogewijs Cli Jones Peter Lindsay Savi Maharaj Brian Matthews
Proof in VDM: case studies Edited by: Juan Bicarregui With contributions from: Sten Agerholm Bart Van Assche John Fitzgerald Jacob Frost Albert Hoogewijs Cli Jones Peter Lindsay Savi Maharaj Brian Matthews
Software Engineering. System Models. Based on Software Engineering, 7 th Edition by Ian Sommerville
 Software Engineering System Models Based on Software Engineering, 7 th Edition by Ian Sommerville Objectives To explain why the context of a system should be modeled as part of the RE process To describe
Software Engineering System Models Based on Software Engineering, 7 th Edition by Ian Sommerville Objectives To explain why the context of a system should be modeled as part of the RE process To describe
How To Develop Software
 Software Engineering Prof. N.L. Sarda Computer Science & Engineering Indian Institute of Technology, Bombay Lecture-4 Overview of Phases (Part - II) We studied the problem definition phase, with which
Software Engineering Prof. N.L. Sarda Computer Science & Engineering Indian Institute of Technology, Bombay Lecture-4 Overview of Phases (Part - II) We studied the problem definition phase, with which
INTEROPERABILITY IN DATA WAREHOUSES
 INTEROPERABILITY IN DATA WAREHOUSES Riccardo Torlone Roma Tre University http://torlone.dia.uniroma3.it/ SYNONYMS Data warehouse integration DEFINITION The term refers to the ability of combining the content
INTEROPERABILITY IN DATA WAREHOUSES Riccardo Torlone Roma Tre University http://torlone.dia.uniroma3.it/ SYNONYMS Data warehouse integration DEFINITION The term refers to the ability of combining the content
The Role of the Software Architect
 IBM Software Group The Role of the Software Architect Peter Eeles peter.eeles@uk.ibm.com 2004 IBM Corporation Agenda Architecture Architect Architecting Requirements Analysis and design Implementation
IBM Software Group The Role of the Software Architect Peter Eeles peter.eeles@uk.ibm.com 2004 IBM Corporation Agenda Architecture Architect Architecting Requirements Analysis and design Implementation
Viewpoint Modeling. Agenda. 1. Viewpoint Modeling 2. ODS, Enterprise Architecture, Viewpoints, Models 3. Modeling approaches and standards
 Viewpoint Modeling Antonio Vallecillo Universidad de Málaga Dpto. Lenguajes y Ciencias de la Computación av@lcc.uma.es http://www.lcc.uma.es/~av Master en Ingeniería del Software e Inteligencia Artificial
Viewpoint Modeling Antonio Vallecillo Universidad de Málaga Dpto. Lenguajes y Ciencias de la Computación av@lcc.uma.es http://www.lcc.uma.es/~av Master en Ingeniería del Software e Inteligencia Artificial
A Systematic Approach. to Parallel Program Verication. Tadao TAKAOKA. Department of Computer Science. Ibaraki University. Hitachi, Ibaraki 316, JAPAN
 A Systematic Approach to Parallel Program Verication Tadao TAKAOKA Department of Computer Science Ibaraki University Hitachi, Ibaraki 316, JAPAN E-mail: takaoka@cis.ibaraki.ac.jp Phone: +81 94 38 5130
A Systematic Approach to Parallel Program Verication Tadao TAKAOKA Department of Computer Science Ibaraki University Hitachi, Ibaraki 316, JAPAN E-mail: takaoka@cis.ibaraki.ac.jp Phone: +81 94 38 5130
Composing Concerns with a Framework Approach
 Composing Concerns with a Framework Approach Constantinos A. Constantinides 1,2 and Tzilla Elrad 2 1 Mathematical and Computer Sciences Department Loyola University Chicago cac@cs.luc.edu 2 Concurrent
Composing Concerns with a Framework Approach Constantinos A. Constantinides 1,2 and Tzilla Elrad 2 1 Mathematical and Computer Sciences Department Loyola University Chicago cac@cs.luc.edu 2 Concurrent
CHAPTER 1: OPERATING SYSTEM FUNDAMENTALS
 CHAPTER 1: OPERATING SYSTEM FUNDAMENTALS What is an operating? A collection of software modules to assist programmers in enhancing efficiency, flexibility, and robustness An Extended Machine from the users
CHAPTER 1: OPERATING SYSTEM FUNDAMENTALS What is an operating? A collection of software modules to assist programmers in enhancing efficiency, flexibility, and robustness An Extended Machine from the users
Object Oriented Design
 Object Oriented Design Kenneth M. Anderson Lecture 20 CSCI 5828: Foundations of Software Engineering OO Design 1 Object-Oriented Design Traditional procedural systems separate data and procedures, and
Object Oriented Design Kenneth M. Anderson Lecture 20 CSCI 5828: Foundations of Software Engineering OO Design 1 Object-Oriented Design Traditional procedural systems separate data and procedures, and
 COMPILER CONSTRUCTION William M. Waite Department of Electrical Engineering University of Colorado Boulder, Colorado 80309 USA email: William.Waite@colorado.edu Gerhard Goos Institut Programmstrukturen
COMPILER CONSTRUCTION William M. Waite Department of Electrical Engineering University of Colorado Boulder, Colorado 80309 USA email: William.Waite@colorado.edu Gerhard Goos Institut Programmstrukturen
An eclipse-based Feature Models toolchain
 An eclipse-based Feature Models toolchain Luca Gherardi, Davide Brugali Dept. of Information Technology and Mathematics Methods, University of Bergamo luca.gherardi@unibg.it, brugali@unibg.it Abstract.
An eclipse-based Feature Models toolchain Luca Gherardi, Davide Brugali Dept. of Information Technology and Mathematics Methods, University of Bergamo luca.gherardi@unibg.it, brugali@unibg.it Abstract.
Object-Oriented Software Specification in Programming Language Design and Implementation
 Object-Oriented Software Specification in Programming Language Design and Implementation Barrett R. Bryant and Viswanathan Vaidyanathan Department of Computer and Information Sciences University of Alabama
Object-Oriented Software Specification in Programming Language Design and Implementation Barrett R. Bryant and Viswanathan Vaidyanathan Department of Computer and Information Sciences University of Alabama
 Trust Management and Network Layer Security Protocols Matt Blaze 1 and John Ioannidis 1 and Angelos D. Keromytis 2 1 AT&T Laboratories { Research fmab,jig@research.att.com 2 Distributed Systems Labs CIS
Trust Management and Network Layer Security Protocols Matt Blaze 1 and John Ioannidis 1 and Angelos D. Keromytis 2 1 AT&T Laboratories { Research fmab,jig@research.att.com 2 Distributed Systems Labs CIS
SYSTEMS AND SOFTWARE REQUIREMENTS SPECIFICATION (SSRS) TEMPLATE. Version A.4, January 2014 FOREWORD DOCUMENT CONVENTIONS
 SYSTEMS AND SOFTWARE REQUIREMENTS SPECIFICATION (SSRS) TEMPLATE Version A.4, January 2014 FOREWORD This document was written to provide software development projects with a template for generating a System
SYSTEMS AND SOFTWARE REQUIREMENTS SPECIFICATION (SSRS) TEMPLATE Version A.4, January 2014 FOREWORD This document was written to provide software development projects with a template for generating a System
Verication Techniques for LOTOS [ISO:8807] was a collaborative project, from 1989 to 1993, funded by the UK SERC/IED research program.
![Verication Techniques for LOTOS [ISO:8807] was a collaborative project, from 1989 to 1993, funded by the UK SERC/IED research program. Verication Techniques for LOTOS [ISO:8807] was a collaborative project, from 1989 to 1993, funded by the UK SERC/IED research program.](/thumbs/19/367556.jpg) Verication Techniques for LOTOS U. Martin, University of St. Andrews, Scotland, U.K. M. Thomas, University of Glasgow, Scotland, U.K. Abstract. We report on the results of a project which applied LOTOS
Verication Techniques for LOTOS U. Martin, University of St. Andrews, Scotland, U.K. M. Thomas, University of Glasgow, Scotland, U.K. Abstract. We report on the results of a project which applied LOTOS
SIMPLE NETWORKING QUESTIONS?
 DECODING SDN SIMPLE NETWORKING QUESTIONS? Can A talk to B? If so which what limitations? Is VLAN Y isolated from VLAN Z? Do I have loops on the topology? SO SDN is a recognition by the Networking industry
DECODING SDN SIMPLE NETWORKING QUESTIONS? Can A talk to B? If so which what limitations? Is VLAN Y isolated from VLAN Z? Do I have loops on the topology? SO SDN is a recognition by the Networking industry
A Foolish Consistency: Technical Challenges in Consistency Management
 A Foolish Consistency: Technical Challenges in Consistency Management Anthony Finkelstein University College London, Department of Computer Science, Gower St., London WC1E 6BT UK a.finkelstein@cs.ucl.ac.uk
A Foolish Consistency: Technical Challenges in Consistency Management Anthony Finkelstein University College London, Department of Computer Science, Gower St., London WC1E 6BT UK a.finkelstein@cs.ucl.ac.uk
Introduction to CORBA. 1. Introduction 2. Distributed Systems: Notions 3. Middleware 4. CORBA Architecture
 Introduction to CORBA 1. Introduction 2. Distributed Systems: Notions 3. Middleware 4. CORBA Architecture 1. Introduction CORBA is defined by the OMG The OMG: -Founded in 1989 by eight companies as a non-profit
Introduction to CORBA 1. Introduction 2. Distributed Systems: Notions 3. Middleware 4. CORBA Architecture 1. Introduction CORBA is defined by the OMG The OMG: -Founded in 1989 by eight companies as a non-profit
An Approach for Generating Concrete Test Cases Utilizing Formal Specifications of Web Applications
 An Approach for Generating Concrete Test Cases Utilizing Formal Specifications of Web Applications Khusbu Bubna RC Junit concrete test cases suitable for execution on the implementation. The remainder
An Approach for Generating Concrete Test Cases Utilizing Formal Specifications of Web Applications Khusbu Bubna RC Junit concrete test cases suitable for execution on the implementation. The remainder
Normative Ontologies to Define Regulations Over Roles in Open Multi- Agent Systems
 Normative Ontologies to Define Regulations Over Roles in Open Multi- Agent Systems Carolina Felicíssimo, Carlos Lucena, Gustavo Carvalho and Rodrigo Paes Departamento de Informática PUC Rio Rua Marquês
Normative Ontologies to Define Regulations Over Roles in Open Multi- Agent Systems Carolina Felicíssimo, Carlos Lucena, Gustavo Carvalho and Rodrigo Paes Departamento de Informática PUC Rio Rua Marquês
BUSINESS RULES AS PART OF INFORMATION SYSTEMS LIFE CYCLE: POSSIBLE SCENARIOS Kestutis Kapocius 1,2,3, Gintautas Garsva 1,2,4
 International Conference 20th EURO Mini Conference Continuous Optimization and Knowledge-Based Technologies (EurOPT-2008) May 20 23, 2008, Neringa, LITHUANIA ISBN 978-9955-28-283-9 L. Sakalauskas, G.W.
International Conference 20th EURO Mini Conference Continuous Optimization and Knowledge-Based Technologies (EurOPT-2008) May 20 23, 2008, Neringa, LITHUANIA ISBN 978-9955-28-283-9 L. Sakalauskas, G.W.
 Do Process-Centred Environments Deserve Process-Centred Tools? Wolfgang Emmerich and Anthony Finkelstein Dept. of Computer Science, The City University, Northampton Square, London EC1V 0HB, UK femmerich
Do Process-Centred Environments Deserve Process-Centred Tools? Wolfgang Emmerich and Anthony Finkelstein Dept. of Computer Science, The City University, Northampton Square, London EC1V 0HB, UK femmerich
UML-based Test Generation and Execution
 UML-based Test Generation and Execution Jean Hartmann, Marlon Vieira, Herb Foster, Axel Ruder Siemens Corporate Research, Inc. 755 College Road East Princeton NJ 08540, USA jeanhartmann@siemens.com ABSTRACT
UML-based Test Generation and Execution Jean Hartmann, Marlon Vieira, Herb Foster, Axel Ruder Siemens Corporate Research, Inc. 755 College Road East Princeton NJ 08540, USA jeanhartmann@siemens.com ABSTRACT
Software Testing Strategies and Techniques
 Software Testing Strategies and Techniques Sheetal Thakare 1, Savita Chavan 2, Prof. P. M. Chawan 3 1,2 MTech, Computer Engineering VJTI, Mumbai 3 Associate Professor, Computer Technology Department, VJTI,
Software Testing Strategies and Techniques Sheetal Thakare 1, Savita Chavan 2, Prof. P. M. Chawan 3 1,2 MTech, Computer Engineering VJTI, Mumbai 3 Associate Professor, Computer Technology Department, VJTI,
Software development process
 OpenStax-CNX module: m14619 1 Software development process Trung Hung VO This work is produced by OpenStax-CNX and licensed under the Creative Commons Attribution License 2.0 Abstract A software development
OpenStax-CNX module: m14619 1 Software development process Trung Hung VO This work is produced by OpenStax-CNX and licensed under the Creative Commons Attribution License 2.0 Abstract A software development
Development. Boston MA 02114 Murray Hill, NJ 07974 [CMU/SEI-95-SR-024]. A rational design process should address. software reuse.
![Development. Boston MA 02114 Murray Hill, NJ 07974 [CMU/SEI-95-SR-024]. A rational design process should address. software reuse. Development. Boston MA 02114 Murray Hill, NJ 07974 [CMU/SEI-95-SR-024]. A rational design process should address. software reuse.](/thumbs/25/6439874.jpg) Session 5: Key Techniques and Process Aspects for Product Line Development Nancy S. Staudenmayer Dewayne E. Perry Sloan School Software Production Research Massachusetts Institute of Technology Bell Laboratories
Session 5: Key Techniques and Process Aspects for Product Line Development Nancy S. Staudenmayer Dewayne E. Perry Sloan School Software Production Research Massachusetts Institute of Technology Bell Laboratories
A methodology for secure software design
 A methodology for secure software design Eduardo B. Fernandez Dept. of Computer Science and Eng. Florida Atlantic University Boca Raton, FL 33431 ed@cse.fau.edu 1. Introduction A good percentage of the
A methodology for secure software design Eduardo B. Fernandez Dept. of Computer Science and Eng. Florida Atlantic University Boca Raton, FL 33431 ed@cse.fau.edu 1. Introduction A good percentage of the
KWIC Exercise. 6/18/2007 2007, Spencer Rugaber 1
 KWIC Exercise On a subsequent slide, you will be given the description of a simple program for which you will be asked to devise two architectures. For the purposes of this exercise, you should imagine
KWIC Exercise On a subsequent slide, you will be given the description of a simple program for which you will be asked to devise two architectures. For the purposes of this exercise, you should imagine
An Overview of Distributed Databases
 International Journal of Information and Computation Technology. ISSN 0974-2239 Volume 4, Number 2 (2014), pp. 207-214 International Research Publications House http://www. irphouse.com /ijict.htm An Overview
International Journal of Information and Computation Technology. ISSN 0974-2239 Volume 4, Number 2 (2014), pp. 207-214 International Research Publications House http://www. irphouse.com /ijict.htm An Overview
Towards Verified Automotive Software
 Towards Verified Automotive Software J. Botaschanjan, L. Kof, C. Kühnel, M. Spichkova Institut für Informatik Bolzmannstr. 3 D-85748 Garching, Germany {botascha, kof, kuehnelc, spichkov}@in.tum.de ABSTRACT
Towards Verified Automotive Software J. Botaschanjan, L. Kof, C. Kühnel, M. Spichkova Institut für Informatik Bolzmannstr. 3 D-85748 Garching, Germany {botascha, kof, kuehnelc, spichkov}@in.tum.de ABSTRACT
Rose/Architect: a tool to visualize architecture
 Published in the Proceedings of the 32 nd Annual Hawaii International Conference on Systems Sciences (HICSS 99) Rose/Architect: a tool to visualize architecture Alexander Egyed University of Southern California
Published in the Proceedings of the 32 nd Annual Hawaii International Conference on Systems Sciences (HICSS 99) Rose/Architect: a tool to visualize architecture Alexander Egyed University of Southern California
Efficient Agent Based Testing Framework for Web Applications
 International Journal of Scientific & Engineering Research, Volume 3, Issue 2, February-2012 1 Efficient Agent Based Testing Framework for Web Applications Ms.Neha Saluja Prof.Amit Kanskar Abstract- Now
International Journal of Scientific & Engineering Research, Volume 3, Issue 2, February-2012 1 Efficient Agent Based Testing Framework for Web Applications Ms.Neha Saluja Prof.Amit Kanskar Abstract- Now
Teaching Methodology for 3D Animation
 Abstract The field of 3d animation has addressed design processes and work practices in the design disciplines for in recent years. There are good reasons for considering the development of systematic
Abstract The field of 3d animation has addressed design processes and work practices in the design disciplines for in recent years. There are good reasons for considering the development of systematic
Goal-Driven Adaptable Software Architecture for UAVs
 SEAS DTC Annual Technical Conference 2008 Goal-Driven Adaptable Software Architecture for UAVs William Heaven, Daniel Sykes, Jeff Magee, Jeff Kramer SER001 Imperial College London The Challenge Autonomous
SEAS DTC Annual Technical Conference 2008 Goal-Driven Adaptable Software Architecture for UAVs William Heaven, Daniel Sykes, Jeff Magee, Jeff Kramer SER001 Imperial College London The Challenge Autonomous
KNOWLEDGE ORGANIZATION
 KNOWLEDGE ORGANIZATION Gabi Reinmann Germany reinmann.gabi@googlemail.com Synonyms Information organization, information classification, knowledge representation, knowledge structuring Definition The term
KNOWLEDGE ORGANIZATION Gabi Reinmann Germany reinmann.gabi@googlemail.com Synonyms Information organization, information classification, knowledge representation, knowledge structuring Definition The term
TAOS: Testing with Analysis and Oracle Support. Debra J. Richardson. University of California. 714-856-7353 djr@ics.uci.edu.
 TAOS: Testing with Analysis and Oracle Support Debra J. Richardson Information and Computer Science University of California Irvine, California 92717-3425 714-856-7353 djr@ics.uci.edu Abstract Few would
TAOS: Testing with Analysis and Oracle Support Debra J. Richardson Information and Computer Science University of California Irvine, California 92717-3425 714-856-7353 djr@ics.uci.edu Abstract Few would
