THE FORMER YUGOSLAV REPUBLIC OF MACEDONIA
|
|
|
- Mervyn Barrett
- 8 years ago
- Views:
Transcription
1 INSTRUMENT FOR PRE-ACCESSION ASSISTANCE (IPA II) THE FORMER YUGOSLAV REPUBLIC OF MACEDONIA Implementation of business continuity and disaster recovery system phase 2 Action Summary The overall objective of the action is infrastructure development and procedures necessary for complying with criteria for accession to Schengen Area. The expected results are establishment of fully functional Business Continuity and Disaster recovery data centre which will enable business continuity of the ICT systems that support business functions of the Ministry of Interior, development of Disaster recovery process, policies and procedures and training of staff for usage and maintenance of the system.
2 Action Identification Programme Title Annual Action programme for the former Yugoslav Republic of Macedonia for 2014 Action Title Implementation of business continuity and disaster recovery system - phase 2 Action Reference IPA/2014/ IPA II Sector(s) DAC Sector Total cost EUR 7,000,000 (VAT excluded) 1 EU contribution EUR 5,950,000 Method of implementation Sector Information Rule of Law and Fundamental Rights - sub sector Home affairs Information and communication technology (ICT) Budget Management and Implementation Indirect management with the beneficiary country Indirect management: Responsible Unit or National Authority/Implementing Agency The Central Financing and Contracting Department (CFCD) will be the Contracting Authority and will be responsible for all administrative and procedural aspects of the tendering process, contracting matters and financial management including payment of action activities. The Head of CFCD will act as the Programme Authorising Officer (PAO) of the action. Ms. Radica Koceva (PAO) Central Financing and Contracting Department Ministry of Finance Tel: Fax: radica.koceva@finance.gov.mk Implementation responsibilities Ministry of Interior Mr. Sasko Kocev, Head of Section for IPA implementation and Senior Programme Officer) sasko_kocev@moi.gov.mk Zone benefiting from the action Specific implementation area(s) Location The former Yugoslav Republic of Macedonia Nation-wide activities Deadline for conclusion of 2015 (n+1) the Financing Agreement Contracting deadline d+3 End of operational d+6 implementation period Timeline 1 The total action cost should be net of VAT and/or of other taxes. Should this not be the case, clearly indicate the amount of VAT and the reasons why it is considered eligible.
3 1. RATIONALE The Ministry of Interior (MOI) together with other relevant authorities is in charge for managing the flow of persons and goods over state border including border control (border checks and border surveillance). The MOI has developed its own information system for border control. The system keeps data in accordance with the Law on border control related to persons to whom thorough check was performed (Article 64) as well as data with regards to the evidence about security and preventive measures taken against a foreigner in accordance with the Law on Foreigners (Article 143). In addition, the system is directly or indirectly connected to other information systems of the MOI which contain data kept in accordance with article 69 from the Law on police, related to persons for whom there are grounds for suspicion that they are perpetrators of criminal acts or misdemeanours, persons and objects being subject of a warrant, as well as persons to whom the entry to the country is prohibited, and data about registration of vehicles in accordance with the Law on vehicles (Article 73). With the new requirements for EU accession and the introduction of the Schengen Border Code in mind, the main task of the Ministry of Interior is the gradual harmonisation of legislation, standards and practices for border guarding in compliance with EU requirements, and modernisation of the IT infrastructure and in the field of border management. Therefore the MOI will be the principal responsible authority for setting up the Schengen Information System (SIS), and this system will be built on the basis of information stored at the Information Centre of the MOI. Candidate countries have to be ready to integrate into the SIS when it will be possible. The MOI should develop the national information system so that integrity of data and their lawful use is ensured and the system would be ready to join SIS. Development and establishment of national centre of the SIS (N.SIS) is one of the necessary actions to be undertaken in order to fulfil the requirements of Schengen Acquis. In this regard the aforementioned information system for border control will become the bases for development of the future National Schengen information system. Getting ready for using the SIS presumes building-up of such a national structure that enables data input and direct and continuous access of authorised bodies to the data. It entails the establishment of the N.SIS, of the Supplementary Information Request at the National Entries (SIRENE) office, set-up the transmission network of the MOI for data input and using the data contained in the SIS. It also involves harmonisation of national databases with the Schengen standards and development of necessary software etc. The MOI does not have a Disaster Recovery Data Centre for the aforementioned information system for border control which would enable back-up of data and the business continuity of the system. That means that in case of unavailability of the system or loss of data due to natural or man-made disaster there would be no continued operation of the system or its rapid recovery with possible catastrophic consequences to the overall functionality of MOI border control, business processes related to the fight against crime, exchange of intelligence data etc. Generally, it means that information system availability and reliability is crucial for all relevant processes in the Sector related to free movement of people, national border control, police authorities, etc. Therefore it is required to provide a backup data centre for complete disaster recovery purposes as well as to develop policies, plans and procedures to support recovery of the system such as developing the contingency planning policy statement, conducting the business impact analysis, identifying preventive controls, creation of contingency strategies, developing an information system contingency plan etc. In order to assess the current situation, a Framework contract for Preparation of Feasibility study for establishment of Business Continuity and Disaster recovery data centre was implemented (April 15, October 14, 2013). Based on the results of document analysis (building plans, network topology etc.) and the off-site visits, experts identified optimal scenarios and potential locations for the Disaster Recovery Data Centre taking into account first of all European Directives and European Norms and industry best practices and financial aspects (establishment of the data centre and the running costs in the long term). Summary of the Feasibility study is presented in Annex 2. 3
4 The process of the establishment of Business Continuity and Disaster recovery data centre as a complex process will be implemented in three phases. The first phase would be implemented under IPA 2013 programme. The construction or refurbishment, depending of the available budget, of a building, including preparation of tender for works contract and supervision of works (framework contracts): All work related to the preparation of land for investment, All work related to adaptation or erection of the building for needs of DC, Power supply for the building, Cooling system * Full size server room, Security systems (Access Control (AC) Intrusion Detection System (IDS) Closed Circuit Television (CCTV) Security Management System (SMS)) The second phase (under this action) would include: Preparation of tender dossier for supply of equipment Purchasing and installation of the equipment Development of policies, plans and procedures Training of the end users The third phase (under this action) would include: Perimeter security Additional RACK cabinets in the server room Additional InLine units for the needs of cooling of new RACK cabinets, Additional chiller to ensure redundancy n+1 in chillers PROBLEM AND STAKEHOLDER ANALYSIS The IT infrastructure in the MOI can be described as highly complex. Its complexity stems from following facts: There is no unified IT platform (Operating system/application server/database/storage) for Ministry of Interior IT systems, so IT infrastructure is heterogeneous and contains many different hardware and software platforms; There is a mix of in-house developed and third-party developed systems; There is divided responsibility for operations and maintenance of IT systems between three different sectors; Some of the operations and maintenance work on IT systems is conducted by third-parties (contractors). With such complex IT infrastructure it is very difficult to establish and implement an efficient and sustainable disaster recovery strategy. There are also operations and disaster recovery-related risks that are a result of the above-mentioned facts. The diversity of platforms that host different systems poses a big burden on the IT sector and creates additional overhead for employees involved in the support and maintenance of systems. Some of the platforms used in the MoI IT system are based on rather old technologies and despite the fact that vendors still provide full support for them and that there are no problems related to pure functioning of the systems, there are definitive drawbacks in using them namely a lack of skilled, qualified * Depending on the budget the cooling and security system might be purchased under second or third phase. 4
5 workforce, very difficult maintenance, lack of inter-connectivity options with newer technologies, and vendor lock-in. Furthermore, besides the lack of specialised Disaster Recovery Data Centre, there is no developed Disaster recovery process, policies and procedures which would enable business continuity of the ICT systems that support business functions of the MOI. More precisely the current situation is as follows: 1. There is no information continuity plan in place, just procedure for incident handling; 2. Disaster recovery is not included; 3. There is no training on disaster recovery in place; 4. Critical information technology resources are not identified. RELEVANCE WITH THE IPA II STRATEGY PAPER AND OTHER KEY REFERENCES To accomplish the strategic goal of becoming a member of the EU, and in order to meet the obligations deriving from the Stabilisation and Association Agreement (SAA) and the Accession Partnership (AP), the MOI has to undertake a series of complex adjustments which should bring about a comprehensive and successive adoption of EU standards in all areas relevant for border management. The ultimate objective envisaged is full alignment with the Schengen acquis and its accurate implementation. The main documents and the core strategic framework of the MOI for its further alignment towards the Schengen acquis are the Schengen Action Plan, National Strategy on development of the established system for integrated border management and the derived Action Plan. The Action Plan determines the following strategic goals: upgrading the legal framework in line with the European standards, strengthening the capacities and enhancement of the inter-agency cooperation between the organizational structures, ministries and institutions competent in the system for insert full name (IBM), building and reconstruction of insert full name (BCP)s, upgrading the IT support and of the established systems and projects, development of the cross-border and international co-operation The Strategic Plan of the MoI pins down the following key objectives: Prevention and detection of organized crime and corruption; Strengthening the trust of all communities in the Police, Completing the Police Reform process, Improving the public security and Improving the efficiency in the fight against terrorism and protection of the national security. Furthermore under the chapter IT system upgrading, the Strategic plan envisages Implementation of business continuity and disaster recovery system. The Indicative Strategy Paper , under the Sector Rule of Law and Fundamental Rights, clearly indicates that the human and material capacity of the border police should be further strengthened in accordance with the Schengen acquis. It also underlines that improved surveillance and detection capacity of the border police regarding all forms of cross-border crime as well as setting up a base for the future Schengen information system is needed. With regards to the fight against organised crime, NPAA stipulates that: On a medium term basis the strengthening of the law enforcement bodies is envisaged. SECTOR APPROACH ASSESSMENT Although this is a stand-alone action, it is anticipated that during the preparation of the tender dossier for civil works (phase 1) involvement of other governmental institutions (Customs, Public prosecution office, Ministry of information society and administration etc) as users of the centre will be taken into consideration. LESSONS LEARNED AND LINK TO PREVIOUS FINANCIAL ASSISTANCE 5
6 Although impact realised through the previous assistance overall is satisfactory, a number of challenges remain. Project implementation is often hampered by either insufficient staff and resources allocated to (newly established) institutions or insufficient operational funds available in the government budget to allow for appropriate implementation of the mandate of the concerned department, or by late approval of relevant legislation etc. Clear co-operation and communication will be established with the all involved stakeholder agencies. Experience / Lessons learnt from during previous projects indicate that specific attention should be given to this aspect. Even though country accession to the Schengen area is at the moment a long term goal, experience from previous EU enlargements shows that some activities should start at a very early stage, notably the updated Catalogue of recommendations for the correct application of the Schengen acquis and best practices gives recommendations related to security such as: there should be a separate back-up system, with regular checks of the switch between the back-up and operational system; there must be emergency plans and escalation procedures to be used for remedying incidents that may potentially interrupt the operation of the system and make the Schengen IT systems fully or partly inaccessible; backup data must be subject to the required physical protection and kept in separate geographical locations; each Schengen State must establish and implement suitable emergency planning measures; the emergency plans have to be based on a risk assessment of the threats that may lead to inability to access the system and the impact of the threats on the other Schengen States. Another important lesson learned during the implementation of the other projects to support the MoI is that it is essential that a strong technical assistance team prepares the supply tender dossier and assists the Ministry of Interior to follow-up on project implementation. The same could be said for the need to ensure project sustainability and budgetary funds for maintenance of the previously achieved results. 6
7 2. INTERVENTION LOGIC LOGICAL FRAMEWORK MATRIX OVERALL OBJECTIVE OBJECTIVELY VERIFIABLE INDICATORS (OVI) SOURCES OF VERIFICATION To establish a base for the future Schengen system. The country has developed a base for the future Schengen system EU Progress Report SPECIFIC OBJECTIVE OBJECTIVELY VERIFIABLE INDICATORS (OVI) SOURCES OF VERIFICATION To implement business continuity and disaster recovery system. The business continuity and disaster recovery system is fully functional. EU Progress Report Reports from the system testing ASSUMPTIONS EU integration remains a country priority Political commitment RESULTS OBJECTIVELY VERIFIABLE INDICATORS (OVI) SOURCES OF VERIFICATION 1. Detailed report on the current situation and need assessment report related to the Monthly and quarterly reports establishment of Business Continuity and Disaster recovery data centre, prepared 2. ICT infrastructure of Business Continuity and Disaster recovery data centre including upgrade of existing ICT infrastructure of Primary Data Centre, implemented 3. Disaster recovery process, policies and procedures prepared 4. Trained personal of MoI The Business Continuity and Disaster recovery data centre is functional Disaster recovery process, policies and procedures are tested and adopted Number of employees trained Report on Provisional acceptance signing Timetables for staff training, Official reports from the competent services Official report from the Human Resources Section within the Ministry of Interior and received certificates from the trainings ASSUMPTIONS EU integration remains a country priority Professional and political commitment ACTIVITIES MEANS OVERALL COST ASSUMPTIONS Activities to achieve Result 1: Analysis of all relevant information related to the establishment of Business Continuity and Disaster recovery data centre Preparation of need assessment report Activities to achieve Result 2 Two procurement procedures ( supply and service) EUR 1. National budget resources available; 2. Presence of qualified personnel; 7
8 Preparation of the Tender dossier for supply of equipment and services Procurement of the ICT infrastructure and services for primary and secondary locations Installation and configuration of software and hardware for Business Continuity and Disaster recovery functions. Activities to achieve Result 3: Developing the contingency planning policy statement. Conducting the business impact analysis (BIA). Identifying preventive controls. Creation of contingency strategies. Developing an information system contingency plan. Ensuring plan testing, training, and exercises. Ensuring plan maintenance. Activities to achieve Result 4: Preparation of Curricula for the usage and maintenance of the system Training the MoI personal for operation, use and maintenance of the ICT infrastructure for BC&DR. 3. Sufficient financing of the activities from the state budget 8
9 ADDITIONAL DESCRIPTION The following components are envisaged: Component 1: Survey, conceptual design and estimation of quantities Component 2: Preparation of Technical Specifications and full Supply Tender Dossier Component 3: Supply Tender launch and evaluation Component 4: Implementation of the supply contract Component 5: Monitoring and supervising of the installation process Component 6: Preparation of policies, plans and procedures The following activities are expected to be implemented: Conducting survey taking into consideration existing ITC infrastructure of the Beneficiary and third parties; Preparation of technical Specifications for the equipment and related installation services for the Business Continuity and Disaster recovery data centre for primary and secondary locations based upon the conceptual design (Conceptual project) including cost estimation for equipment quantities, associated installation and commissioning services, the terms for any guarantee and after-sales maintenance for the Operation, Administration & Maintenance (OAM) of the system; Preparation of Tender Dossier for supply contract for the Business Continuity and Disaster recovery data centre for primary and secondary locations including provision of technical support to the Contracting Authority throughout the clarification and evaluation phases of the tender as needed; Implementation of Supply contract; Provision of technical and procedural advice throughout the implementation (supervision of the installation process) of the supply contract, including stages of the detailed survey and design, delivery, installation and commissioning; Assisting the Contracting Authority with Provisional Acceptance procedures for the supply contract; Preparation of training needs assessment for training for system management and maintenance, and specific training for final users to be performed under the supply contract and conducting of trainings; Developing contingency planning policy statement. A formal policy provides the authority and guidance necessary to develop an effective contingency plan; Conducting the business impact analysis (BIA). The BIA helps identify and prioritize information systems and components critical to supporting the organization s mission/business processes. A template for developing the BIA is provided to assist the user; Identifying preventive controls. Measures taken to reduce the effects of system disruptions can increase system availability and reduce contingency life cycle costs; Creation of contingency strategies. Thorough recovery strategies ensure that the system may be recovered quickly and effectively following a disruption; Developing an information system contingency plan. The contingency plan should contain detailed guidance and procedures for restoring a damaged system unique to the system s security impact level and recovery requirements; Ensuring plan testing, training, and exercises. Testing validates recovery capabilities, whereas training prepares recovery personnel for plan activation and exercising the plan identifies planning gaps; combined, the activities improve plan effectiveness and overall organization preparedness; Ensuring plan maintenance. The plan should be a living document that is updated regularly to remain current with system enhancements and organizational changes. 9
10 Plans to be considered as applicable for MoI contingency planning are as follows: 1. Business Continuity Plan (BCP) 2. Continuity of Operations (COOP) Plan 3. Crisis Communications Plan 4. Critical Infrastructure Protection (CIP) Plan 5. Cyber Incident Response Plan 6. Disaster Recovery Plan (DRP) 7. Information System Contingency Plan (ISCP) Assumptions: Professional and political commitment; National budget resources available; Presence of qualified personnel; Necessary time limits are respected pursuant to the EU legal regulative Continuous courses and trainings are provided for the personnel The system functions properly and is regularly maintained and used by the users Preconditions: Appointment of counterpart personnel by the beneficiary before the launch of the tender process; Allocation of working space and facilities by the beneficiary for technical assistance before the launch of the tender process; Participation by the beneficiary in the tender process as per EU regulations; Organisation, selection and appointment of members of working groups, steering and coordination committees, seminars by the beneficiary as per work plan; Necessary legislation in force; Appointment and availability of the relevant staff of the beneficiaries to participate in implementing activities (especially training activities) as per the work plan; The beneficiary ensures appropriate and timely handling of all legal and regulatory arrangements necessary to enable implementation of the works and supplies (e.g. land and property ownership, building permits, import arrangements, etc.) Risks: Better links between actions/projects belonging to the same sector should be ensured (at both design and implementation levels). External coordination with other international donors has to be also ensured; Communication between project management, contractor and beneficiaries: it is sometimes unsatisfactory and results in partners not having a clear understanding of the objectives/content of the project as well as the nature/level of the commitment expected from them; Absorption capacity is often over-estimated; partners are often unable or unwilling to provide the necessary human and material resources. The availability and permanence of adequate resources is an issue that should be addressed up-front before implementation of some action s components. The above mentioned risks will be mitigated with appropriate measures and appropriate actions such as: establishing good communication channels between all involved stakeholders in the implementation of the action, risk assessment of the contracts to be undertaken prior to the start of implementation and corrective measures during individual projects implementation, regular meetings initiated by relevant stakeholder to be organised, regular monitoring to be conducted and, last but not the least, the MOI to establish an employment policy. 10
11 3. IMPLEMENTATION ARRANGEMENTS The project will be implemented under Indirect Management mode. The Central Financing and Contracting Department (CFCD) will be the Contracting Authority and will be responsible for all administrative and procedural aspects of the tendering process, contracting matters and financial management including payment of project activities. The SPO in the Ministry of Interior will act according to the signed Operational Agreements. ROLES AND RESPONSIBILITIES The Contracting Authority is responsible for launching the tender, organising the evaluation, preparing and signing the contract and making the payments under the contract. The Contracting Authority will, after review and endorsement by the Steering Committee, formally approve reports (inception, quarterly, interim, final and provisional acceptance) submitted by the Consultant for contractual management purposes, and give guidance where appropriate. The Contracting Authority is also responsible for the monitoring the implementation of the contract which shall be carried out by way of appropriate meetings, on-the-spot checks, assessment of reports and verification of financial documentation. The Beneficiary will be represented by the Senior Programme Officer (SPO) within the MOI who will be responsible for monitoring the implementation of the action and a action Co-ordinator from the IT Department responsible for the technical implementation of the action. The Beneficiary will designate one or more representative(s) to be the permanent focus point for co-operation, including management of communications and resource allocation, and to monitor the action implementation. The Beneficiary will establish a Working Group comprising of representatives from the administrative, technical and operational branches of the MOI. This Working Group would function as a forum for consultation, exchange of ideas and formulation of questions/recommendations for consideration by the Steering Committee. During the inception phase and for the purpose of this action, the Beneficiary will establish and chair a Steering Committee, which will include at least one representative of the main sub-beneficiary services. The Contracting Authority, the EU Delegation and a representative of the Consultant s Expert Team shall be invited to participate with Observer status. Other bodies, agencies or institutions may be proposed by the Beneficiary as committee members. The final composition of the Steering Committee has to be agreed with the Contracting Authority. The Consultant will serve as the Secretariat to the Steering Committee. The Steering Committee will have quarterly meetings to oversee the implementation of the planning and implementation process of the project as a whole. Extraordinary meetings shall take place whenever necessary in response to specific requirements. IMPLEMENTATION METHOD(S) AND TYPE(S) OF FINANCING The Action would be implemented with two procurement procedures (supply and service), with an overall amount of EUR 7 million, where the IPA amount is EUR 5,950, and the co-financing is EUR 1,050,
12 4. PERFORMANCE MEASUREMENT METHODOLOGY FOR MONITORING (AND EVALUATION) A Steering Committee will be established to oversee the implementation process of the action activities. The Steering Committee will be chaired by the MOI and will include at least one representative of the primarily involved beneficiary services. The Delegation of the European Union, and the Secretariat for European affairs shall be invited to participate with an observer status. The Steering Committee shall meet not less than once per every three months. The core action team consisting of the team leader and other expertise will be placed within the Ministry of Interior. The team leader will be responsible for the overall management, representation (co-ordination with the EU and other international bodies) as well as reporting. The co-ordination of activity development in the different components of the activity is significantly important. The team leader is responsible for an appropriate management of resources. During the inception phase of the action, a detailed deployment plan will be developed under the coordination of a Steering Committee, in which each co-operating national institution will be represented to ensure appropriate inclusion. The role and main functions of the Steering Committee will be: 1. Assess the action progress and monitor all activities of the action, as agreed in the contract; 2. Assess the performance of the Consultant, review and endorse the Consultant s Inception Report and other Reports, and make recommendations as appropriate to the Contracting Authority which will formally approve these reports; 3. Jointly discuss any critical points or bottlenecks for further project implementation and propose and discuss remedial actions to be taken in order to tackle problems. The contracting authority in coordination with the Senior Programme Officer will monitor the implementation of the action through the project reports, minutes from the Steering Committee meetings, quality check of the produced documents (Assessment report, Tender dossier etc.), on the spot visits, reports from the Provisional acceptance procedure, etc. The overall implementation of the action in line with the sector will be monitored by the relevant Sector Monitoring Committees. 12
13 INDICATOR MEASUREMENT Indicator Description Baseline (2010) Last (year) Milestone 2017 CSP indicator(s) if applicable n/a Action output indicator 1 The Business Continuity and Disaster recovery data centre is functional Action output indicator 2 Action output indicator 3 Disaster recovery process, policies and procedures are tested and adopted Number of employees trained The MOI does not have a Disaster Recovery Data Centre which would enable back-up of data and the business continuity of the system There is no developed Disaster recovery process, policies and procedures which would enable business continuity of the ICT systems that support business functions of the MOI There is no training neither trianed personal on disaster recovery in place Target 2020 Source of information 25% 100% Monitoring Report Project Report Progress Report 80% 100% Monitoring Report Project Report Progress Report 40% 60% Monitoring Report Project Report Progress Report 13
14 5. CROSS-CUTTING ISSUES ENVIRONMENT AND CLIMATE CHANGE (AND IF RELEVANT DISASTER RESILIENCE) The European Community has a longstanding commitment to address environmental concerns in its assistance programmes. The support to institutions will include a specific component to assist the beneficiary to implement an internal environment assessment to identify areas where it could improve its internal performance vis-à-vis environmental aspects. Beneficiaries shall ensure that during the implementation shall take into consideration national and EU policies related to environmental management and they would be included in all materials/project outputs that may occur. ENGAGEMENT WITH CIVIL SOCIETY (AND IF RELEVANT OTHER NON-STATE STAKEHOLDERS) n/a EQUAL OPPORTUNITIES AND GENDER MAINSTREAMING The MOI is committed to equal gender treatment throughout its human resource management. The present action however, is not expected to have an additional impact on gender treatment. MINORITIES AND VULNERABLE GROUPS The MOI is committed to an equal treatment of minorities throughout its human resource management. The present action however, is not expected to have an additional impact on the treatment of minorities and vulnerable groups. 6. SUSTAINABILITY After the implementation period of the action MOI would continue maintaining the achieved results. Trained technical staff from the MOI would have the capacity to manage the IT and telecommunication system, to deal with any failure and to train end users. Every year the MOI budget foresees sufficient financial means for maintenance of the IT system and telecommunication network. 7. COMMUNICATION AND VISIBILITY EU-funded projects should achieve a high and consistent level of visibility. A sufficient level of awareness can only be achieved through coherent branding of all EU projects. The role of contractors and implementing authorities in raising public awareness is thereby crucial. The Consultant shall comply with the provisions of the attached document 'Communications guidelines: visual and written identity for contractors and implementing partners', which is also set out at The EU Delegation will use reasonable efforts to assist the Consultant in complying with this obligation, but without incurring expenditure by the EU Delegation. Therefore, the cost of visibility activities has to be included in the incidental budget. The following indicative set of communication and visibility activities may be covered by the budget for incidental expenditure: Press releases on specific project activities Organisation of press conferences, when necessary All visibility items and activities must receive prior approval by the Contracting Authority The equipment delivered will be marked in compliance with the EU visibility manual. 14
15 LIST OF ANNEXES (to be shared between Beneficiary Countries and the EC/EU Delegation only) Indicative list of documents to be annexed to the Action Document: 1. Executive Summary of the Feasibility Study 15
16 ANNEX 1 - EXECUTIVE SUMMARY OF THE FEASIBILITY STUDY Bearing in mind security considerations (man-made hazards, natural disasters), applicable standards and industry best practices, the experts identified five possible scenarios for both data-centre establishment and hardware/software deployment, which results in the financial considerations ranging from to for the Data-centre and for hardware, software and communication. Scenarios S1 to S4 are recommended due to the fact that the proper construction of the building is addressed as well as perimeter security with the required stand-off distance. S1 and S4 are designed to handle both the Disaster Recovery activities and anti-terrorism protection. S1 and S4 have the same level of protection and security; however S1 is capable of handling 120 Standard RACKs (1000x800) and S4 handling 300 RACKs. It is important to mention that none of the Scenarios is designed for protection against foreign military intervention with the use of the military grade rockets/bombs or ground forces however locations S1 and S4, if adequately staffed with armed personnel, are designed to withstand a high profile terrorist attack or limited military intervention with the use of grenades or hand rocket propelled grenades. The Beneficiary may consider adding additional security measurements for perimeter protection including double anti-ram K12 gates for checkpoints or X-ray machines at the entries. Scenario S2 provides basic protections in terms of anti-terrorism, however is susceptible to a more sophisticated terrorist attack due to the stand-off distance and lower grade walls with minimal distance between outer walls and Server Room (IT Chamber). Scenari o S1 S2 S3 S4 Scenarios S3 and S5 are not recommended however they can serve as a solution only if the Primary Datacenter location is tailored to meet Tier III standards and hardened to withstand terrorist attack. Description New building (Recommended Scenario) Adaptation of a building Minimalistic adaptation New building To serve as DRDC (300 RACKs) for the Government of the former Yugoslav Republic of Macedonia Location Stage 1 Datacenter (Tier II, 60 RACKs*) Stage 1 (hardware and software for primary and secondary locations) Stage 2 Datacenter (Tier III and 120 RACKs*) + Perimeter Security Total Strumica Kavadarci Kavadarci Strumica (300 RACKs, Tier III) S5 Very risky Kavadarci NO TIER III capabilities
17 *) Number of RACKs for S2, S3, S5 refer to Standard RACKs (1000x800) S1 and S4 refer to Standard RACKs (1000x600) Scenario Protection against Protection against man-made disasters natural disasters Earthquakes, fires, Low profile terroristattack High-profile Foreign flooding terrorist attack intervention S1 YES YES YES NO S2 YES YES NO NO S3 YES NO NO NO S4 YES YES YES NO S5 NO NO NO NO military 1.1. Scenario S1 (recommended, optimal) 1. The new building of medium protection level and 600 square meters is erected in Strumica or any other location with available stand-off distance from the anti-ram fence to the outline of the building 100 meters or more and no hills or high rise building in the nearby vicinity 2. Building Management System with Access Control System, Intrusion Detection System and CCTV is installed 3. K12 fence with anti-ram gate and the fully equipped guards post is erected in Phase 2 4. Tier III datacenter facility of the capacity of max. 120 RACKS is established in the building 5. CBR threats not addressed 1.2. Scenario S2 (realistic) 5. The existing building in Kavadarci is adapted 6. Building Management System with Access Control System, Intrusion Detection System and CCTV is installed 7. K12 fence with anti-ram gate is erected in Phase 2 8. Tier III datacenter facility with proper Server Room (IT Chamber) of the capacity of max. 120 RACKS is established in the building, without Power Quality Systems 9. Phase 1 will cover one track for power (1xGen/UPS) and one track for HVAC 10. CBR threats not addressed 1.3. Scenario S3 (minimalistic) 1. Server Room (IT Chamber), single UPS/Generator and minimal necessary electrical equipment and single HVAC system is installed for 60 RACKS maximum 2. No adaptations to the existing building except necessary works for installation of the Server Room (IT Chamber), cabling etc. 3. CBR threats not addressed 1.4. Scenario S4 (to serve as disaster recovery and business continuity solution for the Government of the former Yugoslav Republic of Macedonia) 1. The new building of medium protection level is erected in Strumica or any other location (for example Prilep) with available stand-off distance from the antiram fence to the outline of the building 100 meters or more and no hills or high rise building in the nearby vicinity 2. Building Management System with Access Control System, Intrusion Detection System and CCTV is installed 3. K12 fence with single antiram gate and the fully equipped guards post (single) is erected in Phase 1 4. Tier III datacenter facility of the capacity of max. 300 RACKS is established in the building 5. CBR threats not addressed 17
18 1.5. Scenario S5 (risky) - Single UPS/Generator and necessary electrical equipment (ELC 1, 2, 3, 5, 7) and single HVAC (HVC-1) system is installed for 60 RACKS maximum - No Server Room (IT Chamber) installed, only concrete walls and ceiling is provided - Basic adaptations of the building 18
THE FORMER YUGOSLAV REPUBLIC OF MACEDONIA FURTHER DEVELOPMENT OF
 INSTRUMENT FOR PRE-ACCESSION ASSISTANCE (IPA II) 2014-2020 THE FORMER YUGOSLAV REPUBLIC OF MACEDONIA FURTHER DEVELOPMENT OF THE CAPACITIES FOR CRIME SCENE INVESTIGATION Action Summary The overall objective
INSTRUMENT FOR PRE-ACCESSION ASSISTANCE (IPA II) 2014-2020 THE FORMER YUGOSLAV REPUBLIC OF MACEDONIA FURTHER DEVELOPMENT OF THE CAPACITIES FOR CRIME SCENE INVESTIGATION Action Summary The overall objective
PROJECT FICHE 3.2.1.2
 PROJECT FICHE 3.2.1.2 TO ACTION PROGRAMME 2005 FOR THE FORMER YUGOSLAV REPUBLIC OF MACEDONIA Title Combating money laundering (phase II) Total cost EC contribution: 1.5 million (approx) Aid Method Project
PROJECT FICHE 3.2.1.2 TO ACTION PROGRAMME 2005 FOR THE FORMER YUGOSLAV REPUBLIC OF MACEDONIA Title Combating money laundering (phase II) Total cost EC contribution: 1.5 million (approx) Aid Method Project
Official Journal of the European Union
 L 132/32 COMMISSION IMPLEMTING REGULATION (EU) No 447/2014 of 2 May 2014 on the specific rules for implementing Regulation (EU) No 231/2014 of the European Parliament and of the Council establishing an
L 132/32 COMMISSION IMPLEMTING REGULATION (EU) No 447/2014 of 2 May 2014 on the specific rules for implementing Regulation (EU) No 231/2014 of the European Parliament and of the Council establishing an
Regulation on the implementation of the Norwegian Financial Mechanism 2009-2014
 Regulation on the implementation of the Norwegian Financial Mechanism 2009-2014 adopted by the Norwegian Ministry of Foreign Affairs pursuant to Article 8.8 of the Agreement between the Kingdom of Norway
Regulation on the implementation of the Norwegian Financial Mechanism 2009-2014 adopted by the Norwegian Ministry of Foreign Affairs pursuant to Article 8.8 of the Agreement between the Kingdom of Norway
COMMISSION OF THE EUROPEAN COMMUNITIES. COMMISSION REGULATION (EC) No /..
 EN EN EN COMMISSION OF THE EUROPEAN COMMUNITIES Brussels, XX/XX/2007 COM(2006) XXX COMMISSION REGULATION (EC) No /.. of [ ] implementing Council Regulation (EC) No 1085/2006 establishing an instrument
EN EN EN COMMISSION OF THE EUROPEAN COMMUNITIES Brussels, XX/XX/2007 COM(2006) XXX COMMISSION REGULATION (EC) No /.. of [ ] implementing Council Regulation (EC) No 1085/2006 establishing an instrument
Regulation on the implementation of the European Economic Area (EEA) Financial Mechanism 2009-2014
 the European Economic Area (EEA) Financial Mechanism 2009-2014 adopted by the EEA Financial Mechanism Committee pursuant to Article 8.8 of Protocol 38b to the EEA Agreement on 13 January 2011 and confirmed
the European Economic Area (EEA) Financial Mechanism 2009-2014 adopted by the EEA Financial Mechanism Committee pursuant to Article 8.8 of Protocol 38b to the EEA Agreement on 13 January 2011 and confirmed
DESIGNATED CONTRACT MARKET OPERATIONAL CAPABILITY TECHNOLOGY QUESTIONNAIRE
 DESIGNATED CONTRACT MARKET OPERATIONAL CAPABILITY TECHNOLOGY QUESTIONNAIRE Please provide all relevant documents responsive to the information requests listed within each area below. In addition to the
DESIGNATED CONTRACT MARKET OPERATIONAL CAPABILITY TECHNOLOGY QUESTIONNAIRE Please provide all relevant documents responsive to the information requests listed within each area below. In addition to the
1.1 Publication reference: EuropeAid/ 135-061/M/ACT/MK
 1. Basic Information TWINNING PROJECT FICHE Improving of the Public Revenue Office (PRO) taxpayers services Project Fiche 3.4, No. 2010/022-264 1.1 Publication reference: EuropeAid/ 135-061/M/ACT/MK 1.2
1. Basic Information TWINNING PROJECT FICHE Improving of the Public Revenue Office (PRO) taxpayers services Project Fiche 3.4, No. 2010/022-264 1.1 Publication reference: EuropeAid/ 135-061/M/ACT/MK 1.2
Creating a Business Continuity Plan for your Health Center
 Creating a Business Continuity Plan for your Health Center 1 Page Left Intentionally Blank 2 About This Manual This tool is the result of collaboration between the Primary Care Development Corporation
Creating a Business Continuity Plan for your Health Center 1 Page Left Intentionally Blank 2 About This Manual This tool is the result of collaboration between the Primary Care Development Corporation
Standard Summary Project Fiche IPA decentralised National programmes. Project number: TR 07 02 22
 Standard Summary Project Fiche IPA decentralised National programmes Project number: TR 07 02 22 1. Basic information 1.1 CRIS Number: 1.2 Title: Capacity Building of Social Security Institution 1.3 Sector:
Standard Summary Project Fiche IPA decentralised National programmes Project number: TR 07 02 22 1. Basic information 1.1 CRIS Number: 1.2 Title: Capacity Building of Social Security Institution 1.3 Sector:
Advanced training for tax auditors in the field of computer audit. 1.1 CRIS Number: 2006/018-180.01-03 Twinning No: PL/06/IB/FI/01/TL
 1. Basic Information Advanced training for tax auditors in the field of computer audit 1.1 CRIS Number: 2006/018-180.01-03 Twinning No: PL/06/IB/FI/01/TL 1.2 Title: Advanced training for tax auditors in
1. Basic Information Advanced training for tax auditors in the field of computer audit 1.1 CRIS Number: 2006/018-180.01-03 Twinning No: PL/06/IB/FI/01/TL 1.2 Title: Advanced training for tax auditors in
Summary Project Fiche
 Summary Project Fiche 1. Basic Information 1.1. Désirée Number: BG 0203.13 1.2. Title: Development and Implementation of VIES requirements and EU interoperability standards in the field of VAT within the
Summary Project Fiche 1. Basic Information 1.1. Désirée Number: BG 0203.13 1.2. Title: Development and Implementation of VIES requirements and EU interoperability standards in the field of VAT within the
NEEDS BASED PLANNING FOR IT DISASTER RECOVERY
 The Define/Align/Approve Reference Series NEEDS BASED PLANNING FOR IT DISASTER RECOVERY Disaster recovery planning is essential it s also expensive. That s why every step taken and dollar spent must be
The Define/Align/Approve Reference Series NEEDS BASED PLANNING FOR IT DISASTER RECOVERY Disaster recovery planning is essential it s also expensive. That s why every step taken and dollar spent must be
BOSNIA AND HERZEGOVINA
 INSTRUMENT FOR PRE-ACCESSION ASSISTANCE (IPA II) 2014-2020 BOSNIA AND HERZEGOVINA Support to participation in EU Programmes Action Summary The Action provides support to the participation of Bosnia and
INSTRUMENT FOR PRE-ACCESSION ASSISTANCE (IPA II) 2014-2020 BOSNIA AND HERZEGOVINA Support to participation in EU Programmes Action Summary The Action provides support to the participation of Bosnia and
(Mr. Krirk Vanikkul) Assistant Governor, Financial Institutions Policy Group Governor For
 Unofficial Translation by the courtesy of The Foreign Banks' Association This translation is for the convenience of those unfamiliar with the Thai language. Please refer to the Thai text for the official
Unofficial Translation by the courtesy of The Foreign Banks' Association This translation is for the convenience of those unfamiliar with the Thai language. Please refer to the Thai text for the official
CENTRAL BANK OF KENYA (CBK) PRUDENTIAL GUIDELINE ON BUSINESS CONTINUITY MANAGEMENT (BCM) FOR INSTITUTIONS LICENSED UNDER THE BANKING ACT
 CENTRAL BANK OF KENYA (CBK) PRUDENTIAL GUIDELINE ON BUSINESS CONTINUITY MANAGEMENT (BCM) FOR INSTITUTIONS LICENSED UNDER THE BANKING ACT JANUARY 2008 GUIDELINE ON BUSINESS CONTINUITY GUIDELINE CBK/PG/14
CENTRAL BANK OF KENYA (CBK) PRUDENTIAL GUIDELINE ON BUSINESS CONTINUITY MANAGEMENT (BCM) FOR INSTITUTIONS LICENSED UNDER THE BANKING ACT JANUARY 2008 GUIDELINE ON BUSINESS CONTINUITY GUIDELINE CBK/PG/14
Why Should Companies Take a Closer Look at Business Continuity Planning?
 whitepaper Why Should Companies Take a Closer Look at Business Continuity Planning? How Datalink s business continuity and disaster recovery solutions can help organizations lessen the impact of disasters
whitepaper Why Should Companies Take a Closer Look at Business Continuity Planning? How Datalink s business continuity and disaster recovery solutions can help organizations lessen the impact of disasters
Islamic Republic of Afghanistan, Post Disaster Need Assessment (PDNA) Training Manual
 Islamic Republic of Afghanistan, Ministry of Rural Rehabilitation and Development (MRRD) Ministry of Rural Rehabilitation & Development Post Disaster Need Assessment (PDNA) Training Manual Social Protection
Islamic Republic of Afghanistan, Ministry of Rural Rehabilitation and Development (MRRD) Ministry of Rural Rehabilitation & Development Post Disaster Need Assessment (PDNA) Training Manual Social Protection
Oracle Maps Cloud Service Enterprise Hosting and Delivery Policies Effective Date: October 1, 2015 Version 1.0
 Oracle Maps Cloud Service Enterprise Hosting and Delivery Policies Effective Date: October 1, 2015 Version 1.0 Unless otherwise stated, these Oracle Maps Cloud Service Enterprise Hosting and Delivery Policies
Oracle Maps Cloud Service Enterprise Hosting and Delivery Policies Effective Date: October 1, 2015 Version 1.0 Unless otherwise stated, these Oracle Maps Cloud Service Enterprise Hosting and Delivery Policies
BCP and DR. P K Patel AGM, MoF
 BCP and DR P K Patel AGM, MoF Key difference between BS 25999 and ISO 22301 ISO 22301 puts a much greater emphasis on setting the objectives, monitoring performance and metrics aligning BC to top management
BCP and DR P K Patel AGM, MoF Key difference between BS 25999 and ISO 22301 ISO 22301 puts a much greater emphasis on setting the objectives, monitoring performance and metrics aligning BC to top management
Overview of how to test a. Business Continuity Plan
 Overview of how to test a Business Continuity Plan Prepared by: Thomas Bronack Phone: (718) 591-5553 Email: bronackt@dcag.com BRP/DRP Test Plan Creation and Exercise Page: 1 Table of Contents BCP/DRP Test
Overview of how to test a Business Continuity Plan Prepared by: Thomas Bronack Phone: (718) 591-5553 Email: bronackt@dcag.com BRP/DRP Test Plan Creation and Exercise Page: 1 Table of Contents BCP/DRP Test
ISO27001 Controls and Objectives
 Introduction This reference document for the University of Birmingham lists the control objectives, specific controls and background information, as given in Annex A to ISO/IEC 27001:2005. As such, the
Introduction This reference document for the University of Birmingham lists the control objectives, specific controls and background information, as given in Annex A to ISO/IEC 27001:2005. As such, the
Annex 2: Rules and Procedures for the Swiss-Polish Cooperation Programme
 Annex 2: Rules and Procedures for the Swiss-Polish Cooperation Programme Annex 2 is an integral part of the Framework Agreement between the Swiss Federal Council and the Government of the Republic of Poland
Annex 2: Rules and Procedures for the Swiss-Polish Cooperation Programme Annex 2 is an integral part of the Framework Agreement between the Swiss Federal Council and the Government of the Republic of Poland
Request for Proposals from non-for-profit organizations
 Request for Proposals from non-for-profit organizations Request to submit a written and financial proposal for a work assignment with UNESCO on Support and development of journalism entry education in
Request for Proposals from non-for-profit organizations Request to submit a written and financial proposal for a work assignment with UNESCO on Support and development of journalism entry education in
Federal Financial Institutions Examination Council FFIEC. Business Continuity Planning BCP MARCH 2003 MARCH 2008 IT EXAMINATION
 Federal Financial Institutions Examination Council FFIEC Business Continuity Planning MARCH 2003 MARCH 2008 BCP IT EXAMINATION H ANDBOOK TABLE OF CONTENTS INTRODUCTION... 1 BOARD AND SENIOR MANAGEMENT
Federal Financial Institutions Examination Council FFIEC Business Continuity Planning MARCH 2003 MARCH 2008 BCP IT EXAMINATION H ANDBOOK TABLE OF CONTENTS INTRODUCTION... 1 BOARD AND SENIOR MANAGEMENT
Ohio Supercomputer Center
 Ohio Supercomputer Center IT Business Continuity Planning No: Effective: OSC-13 06/02/2009 Issued By: Kevin Wohlever Director of Supercomputer Operations Published By: Ohio Supercomputer Center Original
Ohio Supercomputer Center IT Business Continuity Planning No: Effective: OSC-13 06/02/2009 Issued By: Kevin Wohlever Director of Supercomputer Operations Published By: Ohio Supercomputer Center Original
How To Manage A Business Continuity Strategy
 Business continuity strategy 2009 2012 Table of contents 1 Why this strategy is needed 3 2 Aim of the strategy 4 3 Our approach to business continuity 4 PROCESS 4 STRUCTURE 5 DOCUMENTATION 6 DISRUPTION
Business continuity strategy 2009 2012 Table of contents 1 Why this strategy is needed 3 2 Aim of the strategy 4 3 Our approach to business continuity 4 PROCESS 4 STRUCTURE 5 DOCUMENTATION 6 DISRUPTION
EMERGENCY PREPAREDNESS PLAN Business Continuity Plan
 EMERGENCY PREPAREDNESS PLAN Business Continuity Plan GIS Bankers Insurance Group Powered by DISASTER PREPAREDNESS Implementation Small Business Guide to Business Continuity Planning Surviving a Catastrophic
EMERGENCY PREPAREDNESS PLAN Business Continuity Plan GIS Bankers Insurance Group Powered by DISASTER PREPAREDNESS Implementation Small Business Guide to Business Continuity Planning Surviving a Catastrophic
National Cyber Security Policy -2013
 National Cyber Security Policy -2013 Preamble 1. Cyberspace 1 is a complex environment consisting of interactions between people, software and services, supported by worldwide distribution of information
National Cyber Security Policy -2013 Preamble 1. Cyberspace 1 is a complex environment consisting of interactions between people, software and services, supported by worldwide distribution of information
Standard Summary Project Fiche IPA centralised programmes
 Standard Summary Project Fiche IPA centralised programmes Project number 15: Implementation of Hospital Information System (HIS) 1 BASIC INFORMATION 1.1 CRIS Number: 2008/020-406 1.2 Title: Implementation
Standard Summary Project Fiche IPA centralised programmes Project number 15: Implementation of Hospital Information System (HIS) 1 BASIC INFORMATION 1.1 CRIS Number: 2008/020-406 1.2 Title: Implementation
Section A: Introduction, Definitions and Principles of Infrastructure Resilience
 Section A: Introduction, Definitions and Principles of Infrastructure Resilience A1. This section introduces infrastructure resilience, sets out the background and provides definitions. Introduction Purpose
Section A: Introduction, Definitions and Principles of Infrastructure Resilience A1. This section introduces infrastructure resilience, sets out the background and provides definitions. Introduction Purpose
BUSINESS CONTINUITY PLAN
 How to Develop a BUSINESS CONTINUITY PLAN To print to A4, print at 75%. TABLE OF CONTENTS SUMMARY SUMMARY WHAT IS A BUSINESS CONTINUITY PLAN? CHAPTER PREPARING TO WRITE YOUR BUSINESS CONTINUITY PLAN CHAPTER
How to Develop a BUSINESS CONTINUITY PLAN To print to A4, print at 75%. TABLE OF CONTENTS SUMMARY SUMMARY WHAT IS A BUSINESS CONTINUITY PLAN? CHAPTER PREPARING TO WRITE YOUR BUSINESS CONTINUITY PLAN CHAPTER
BUSINESS CONTINUITY POLICY
 BUSINESS CONTINUITY POLICY Last Review Date Approving Body n/a Audit Committee Date of Approval 9 th January 2014 Date of Implementation 1 st February 2014 Next Review Date February 2017 Review Responsibility
BUSINESS CONTINUITY POLICY Last Review Date Approving Body n/a Audit Committee Date of Approval 9 th January 2014 Date of Implementation 1 st February 2014 Next Review Date February 2017 Review Responsibility
Business Continuity Planning and Disaster Recovery Planning
 4 Business Continuity Planning and Disaster Recovery Planning Basic Concepts 1. Business Continuity Management: Business Continuity means maintaining the uninterrupted availability of all key business
4 Business Continuity Planning and Disaster Recovery Planning Basic Concepts 1. Business Continuity Management: Business Continuity means maintaining the uninterrupted availability of all key business
Business Continuity Plan
 Business Continuity Plan October 2007 Agenda Business continuity plan definition Evolution of the business continuity plan Business continuity plan life cycle FFIEC & Business continuity plan Questions
Business Continuity Plan October 2007 Agenda Business continuity plan definition Evolution of the business continuity plan Business continuity plan life cycle FFIEC & Business continuity plan Questions
STANDARD TWINNING LIGHT PROJECT FICHE
 STANDARD TWINNING LIGHT PROJECT FICHE 1. Basic Information 1.1 Programme: IPA 2011 1.2 Twinning Number: HR/2011/IB/OT/01 TWL 1.3 Title: Capacity Building of the National School for Public Administration
STANDARD TWINNING LIGHT PROJECT FICHE 1. Basic Information 1.1 Programme: IPA 2011 1.2 Twinning Number: HR/2011/IB/OT/01 TWL 1.3 Title: Capacity Building of the National School for Public Administration
Cloud Computing and Records Management
 GPO Box 2343 Adelaide SA 5001 Tel (+61 8) 8204 8773 Fax (+61 8) 8204 8777 DX:336 srsarecordsmanagement@sa.gov.au www.archives.sa.gov.au Cloud Computing and Records Management June 2015 Version 1 Version
GPO Box 2343 Adelaide SA 5001 Tel (+61 8) 8204 8773 Fax (+61 8) 8204 8777 DX:336 srsarecordsmanagement@sa.gov.au www.archives.sa.gov.au Cloud Computing and Records Management June 2015 Version 1 Version
SUBJECT: REPLACEMENT OF CORPORATE ELECTRONIC DATA STORAGE, BACKUP AND DISASTER RECOVERY SOLUTIONS
 REPORT TO CABINET TO BE HELD ON 15 SEPTEMBER 2015 Key Decision No Forward Plan Ref No 23K Corporate Priority The proposals in this report contribute to the delivery of all the Council s priorities Cabinet
REPORT TO CABINET TO BE HELD ON 15 SEPTEMBER 2015 Key Decision No Forward Plan Ref No 23K Corporate Priority The proposals in this report contribute to the delivery of all the Council s priorities Cabinet
AUSTRACLEAR REGULATIONS Guidance Note 10
 BUSINESS CONTINUITY AND DISASTER RECOVERY The purpose of this Guidance Note The main points it covers To assist participants to understand the disaster recovery and business continuity arrangements they
BUSINESS CONTINUITY AND DISASTER RECOVERY The purpose of this Guidance Note The main points it covers To assist participants to understand the disaster recovery and business continuity arrangements they
ISO 27001 Controls and Objectives
 ISO 27001 s and Objectives A.5 Security policy A.5.1 Information security policy Objective: To provide management direction and support for information security in accordance with business requirements
ISO 27001 s and Objectives A.5 Security policy A.5.1 Information security policy Objective: To provide management direction and support for information security in accordance with business requirements
De Nederlandsche Bank N.V. May 2011. Assessment Framework for Financial Core Infrastructure Business Continuity Management
 De Nederlandsche Bank N.V. May 2011 Assessment Framework for Financial Core Infrastructure Business Continuity Management Contents INTRODUCTION... 3 BUSINESS CONTINUITY MANAGEMENT STANDARDS... 5 1. STRATEGY
De Nederlandsche Bank N.V. May 2011 Assessment Framework for Financial Core Infrastructure Business Continuity Management Contents INTRODUCTION... 3 BUSINESS CONTINUITY MANAGEMENT STANDARDS... 5 1. STRATEGY
Business Continuity Management
 Business Continuity Management Standard Operating Procedure Notice: This document has been made available through the Police Service of Scotland Freedom of Information Publication Scheme. It should not
Business Continuity Management Standard Operating Procedure Notice: This document has been made available through the Police Service of Scotland Freedom of Information Publication Scheme. It should not
OPERATIONAL CAPABILITY TECHNOLOGY QUESTIONNAIRE
 OPERATIONAL CAPABILITY TECHNOLOGY QUESTIONNAIRE Please provide all relevant documents responsive to the information requests listed within each area below. In addition to the specific documents requested,
OPERATIONAL CAPABILITY TECHNOLOGY QUESTIONNAIRE Please provide all relevant documents responsive to the information requests listed within each area below. In addition to the specific documents requested,
Company Management System. Business Continuity in SIA
 Company Management System Business Continuity in SIA Document code: Classification: Company Project/Service Year Document No. Version Public INDEX 1. INTRODUCTION... 3 2. SIA S BUSINESS CONTINUITY MANAGEMENT
Company Management System Business Continuity in SIA Document code: Classification: Company Project/Service Year Document No. Version Public INDEX 1. INTRODUCTION... 3 2. SIA S BUSINESS CONTINUITY MANAGEMENT
ASX CLEAR (FUTURES) OPERATING RULES Guidance Note 10
 BUSINESS CONTINUITY AND DISASTER RECOVERY The purpose of this Guidance Note The main points it covers To assist participants to understand the disaster recovery and business continuity arrangements they
BUSINESS CONTINUITY AND DISASTER RECOVERY The purpose of this Guidance Note The main points it covers To assist participants to understand the disaster recovery and business continuity arrangements they
Project Fiche No. 8 Implementation and follow-up of the Small Business Act (SBA)
 1. Basic information Project Fiche No. 8 Implementation and follow-up of the Small Business Act (SBA) 1.1 CRIS Number: 2010/XXXX 1.2 Title: Implementation and follow-up of the Small Business Act (SBA)
1. Basic information Project Fiche No. 8 Implementation and follow-up of the Small Business Act (SBA) 1.1 CRIS Number: 2010/XXXX 1.2 Title: Implementation and follow-up of the Small Business Act (SBA)
GUIDELINES FOR BUSINESS CONTINUITY IN WHOLESALE MARKETS AND SUPPORT SYSTEMS MARKET SUPERVISION OFFICE. October 2004
 GUIDELINES FOR BUSINESS CONTINUITY IN WHOLESALE MARKETS AND SUPPORT SYSTEMS MARKET SUPERVISION OFFICE October 2004 1 1. Introduction Guaranteeing the efficiency and correct operation of money and financial
GUIDELINES FOR BUSINESS CONTINUITY IN WHOLESALE MARKETS AND SUPPORT SYSTEMS MARKET SUPERVISION OFFICE October 2004 1 1. Introduction Guaranteeing the efficiency and correct operation of money and financial
Shankar Gawade VP IT INFRASTRUCTURE ENAM SECURITIES PVT. LTD.
 Business Continuity Management & Disaster Recovery Planning Presented by: Shankar Gawade VP IT INFRASTRUCTURE ENAM SECURITIES PVT. LTD. 1 What is Business Continuity Management? Is a holistic management
Business Continuity Management & Disaster Recovery Planning Presented by: Shankar Gawade VP IT INFRASTRUCTURE ENAM SECURITIES PVT. LTD. 1 What is Business Continuity Management? Is a holistic management
EVALUATION OF THE INVESTMENT COMPENSATION SCHEME DIRECTIVE DG INTERNAL MARKET AND SERVICES EXECUTIVE REPORT AND RECOMMENDATIONS
 EVALUATION OF THE INVESTMENT COMPENSATION SCHEME DIRECTIVE DG INTERNAL MARKET AND SERVICES EXECUTIVE REPORT AND RECOMMENDATIONS 1. BACKGROUND Directive 97/9/EC, known as the Investment Compensation Scheme
EVALUATION OF THE INVESTMENT COMPENSATION SCHEME DIRECTIVE DG INTERNAL MARKET AND SERVICES EXECUTIVE REPORT AND RECOMMENDATIONS 1. BACKGROUND Directive 97/9/EC, known as the Investment Compensation Scheme
BUSINESS CONTINUITY PLAN OVERVIEW
 BUSINESS CONTINUITY PLAN OVERVIEW INTRODUCTION The purpose of this document is to provide Loomis customers with an overview of the company s Business Continuity Plan (BCP). Because of the specific and
BUSINESS CONTINUITY PLAN OVERVIEW INTRODUCTION The purpose of this document is to provide Loomis customers with an overview of the company s Business Continuity Plan (BCP). Because of the specific and
Q uick Guide to Disaster Recovery Planning An ITtoolkit.com White Paper
 This quick reference guide provides an introductory overview of the key principles and issues involved in IT related disaster recovery planning, including needs evaluation, goals, objectives and related
This quick reference guide provides an introductory overview of the key principles and issues involved in IT related disaster recovery planning, including needs evaluation, goals, objectives and related
[Insert Company Logo]
![[Insert Company Logo] [Insert Company Logo]](/thumbs/30/14202230.jpg) [Insert Company Logo] Business Continuity and Disaster Recovery Planning (BCDRP) Manual 1 Table of Contents Critical Business Information 4 Business Continuity and Disaster Recover Planning (BCDRP) Personnel
[Insert Company Logo] Business Continuity and Disaster Recovery Planning (BCDRP) Manual 1 Table of Contents Critical Business Information 4 Business Continuity and Disaster Recover Planning (BCDRP) Personnel
IT Disaster Recovery Plan Template
 HOPONE INTERNET CORP IT Disaster Recovery Plan Template Compliments of: Tim Sexton 1/1/2015 An information technology (IT) disaster recovery (DR) plan provides a structured approach for responding to unplanned
HOPONE INTERNET CORP IT Disaster Recovery Plan Template Compliments of: Tim Sexton 1/1/2015 An information technology (IT) disaster recovery (DR) plan provides a structured approach for responding to unplanned
THE WESTERN BALKANS LEGAL BASIS OBJECTIVES BACKGROUND INSTRUMENTS
 THE WESTERN BALKANS The EU has developed a policy to support the gradual integration of the Western Balkan countries with the Union. On 1 July 2013, Croatia became the first of the seven countries to join,
THE WESTERN BALKANS The EU has developed a policy to support the gradual integration of the Western Balkan countries with the Union. On 1 July 2013, Croatia became the first of the seven countries to join,
Operational Risk Publication Date: May 2015. 1. Operational Risk... 3
 OPERATIONAL RISK Contents 1. Operational Risk... 3 1.1 Legislation... 3 1.2 Guidance... 3 1.3 Risk management process... 4 1.4 Risk register... 7 1.5 EBA Guidelines on the Security of Internet Payments...
OPERATIONAL RISK Contents 1. Operational Risk... 3 1.1 Legislation... 3 1.2 Guidance... 3 1.3 Risk management process... 4 1.4 Risk register... 7 1.5 EBA Guidelines on the Security of Internet Payments...
<Client Name> IT Disaster Recovery Plan Template. By Paul Kirvan, CISA, CISSP, FBCI, CBCP
 IT Disaster Recovery Plan Template By Paul Kirvan, CISA, CISSP, FBCI, CBCP Revision History REVISION DATE NAME DESCRIPTION Original 1.0 2 Table of Contents Information Technology Statement
IT Disaster Recovery Plan Template By Paul Kirvan, CISA, CISSP, FBCI, CBCP Revision History REVISION DATE NAME DESCRIPTION Original 1.0 2 Table of Contents Information Technology Statement
HIPAA Security Alert
 Shipman & Goodwin LLP HIPAA Security Alert July 2008 EXECUTIVE GUIDANCE HIPAA SECURITY COMPLIANCE How would your organization s senior management respond to CMS or OIG inquiries about health information
Shipman & Goodwin LLP HIPAA Security Alert July 2008 EXECUTIVE GUIDANCE HIPAA SECURITY COMPLIANCE How would your organization s senior management respond to CMS or OIG inquiries about health information
Development, Acquisition, Implementation, and Maintenance of Application Systems
 Development, Acquisition, Implementation, and Maintenance of Application Systems Part of a series of notes to help Centers review their own Center internal management processes from the point of view of
Development, Acquisition, Implementation, and Maintenance of Application Systems Part of a series of notes to help Centers review their own Center internal management processes from the point of view of
INFORMATION TECHNOLOGY SECURITY STANDARDS
 INFORMATION TECHNOLOGY SECURITY STANDARDS Version 2.0 December 2013 Table of Contents 1 OVERVIEW 3 2 SCOPE 4 3 STRUCTURE 5 4 ASSET MANAGEMENT 6 5 HUMAN RESOURCES SECURITY 7 6 PHYSICAL AND ENVIRONMENTAL
INFORMATION TECHNOLOGY SECURITY STANDARDS Version 2.0 December 2013 Table of Contents 1 OVERVIEW 3 2 SCOPE 4 3 STRUCTURE 5 4 ASSET MANAGEMENT 6 5 HUMAN RESOURCES SECURITY 7 6 PHYSICAL AND ENVIRONMENTAL
ANNEX. to the COMMISSION IMPLEMENTING DECISION
 EUROPEAN COMMISSION Brussels, 8.8.2014 C(2014) 5650 final ANNEX 1 ANNEX to the COMMISSION IMPLEMENTING DECISION concerning the adoption of the work programme for 2014 and the financing for Union actions
EUROPEAN COMMISSION Brussels, 8.8.2014 C(2014) 5650 final ANNEX 1 ANNEX to the COMMISSION IMPLEMENTING DECISION concerning the adoption of the work programme for 2014 and the financing for Union actions
DISASTER RECOVERY PLANNING FOR CITY COMPUTER FACILITIES
 APPENDIX 1 DISASTER RECOVERY PLANNING FOR CITY COMPUTER FACILITIES March 2008 Auditor General s Office Jeffrey Griffiths, C.A., C.F.E. Auditor General City of Toronto TABLE OF CONTENTS EXECUTIVE SUMMARY...1
APPENDIX 1 DISASTER RECOVERY PLANNING FOR CITY COMPUTER FACILITIES March 2008 Auditor General s Office Jeffrey Griffiths, C.A., C.F.E. Auditor General City of Toronto TABLE OF CONTENTS EXECUTIVE SUMMARY...1
SWAP EXECUTION FACILITY OPERATIONAL CAPABILITY TECHNOLOGY QUESTIONNAIRE
 SWAP EXECUTION FACILITY OPERATIONAL CAPABILITY TECHNOLOGY QUESTIONNAIRE Please provide all relevant documents responsive to the information requests listed within each area below. In addition to the specific
SWAP EXECUTION FACILITY OPERATIONAL CAPABILITY TECHNOLOGY QUESTIONNAIRE Please provide all relevant documents responsive to the information requests listed within each area below. In addition to the specific
DG ENLARGEMENT SECTOR BUDGET SUPPORT GUIDELINES
 Ref. Ares(2014)571140-04/03/2014 DG ENLARGEMENT SECTOR BUDGET SUPPORT GUIDELINES EXECUTIVE SUMMARY January 2014 TABLE OF CONTENTS Introduction 1. RATIONALE FOR BUDGET SUPPORT 1.1 What is Budget Support?
Ref. Ares(2014)571140-04/03/2014 DG ENLARGEMENT SECTOR BUDGET SUPPORT GUIDELINES EXECUTIVE SUMMARY January 2014 TABLE OF CONTENTS Introduction 1. RATIONALE FOR BUDGET SUPPORT 1.1 What is Budget Support?
Protecting your Enterprise
 Understanding Disaster Recovery in California Protecting your Enterprise Session Overview Why do we Prepare What is? How do I analyze (measure) it? What to do with it? How do I communicate it? What does
Understanding Disaster Recovery in California Protecting your Enterprise Session Overview Why do we Prepare What is? How do I analyze (measure) it? What to do with it? How do I communicate it? What does
CONTINUITY OF OPERATIONS AUDIT PROGRAM EVALUATION AND AUDIT
 CONTINUITY OF OPERATIONS AUDIT PROGRAM EVALUATION AND AUDIT April 16, 2014 INTRODUCTION Purpose The purpose of the audit is to give assurance that the development of the Metropolitan Council s Continuity
CONTINUITY OF OPERATIONS AUDIT PROGRAM EVALUATION AND AUDIT April 16, 2014 INTRODUCTION Purpose The purpose of the audit is to give assurance that the development of the Metropolitan Council s Continuity
ANNEX C1 1 STANDARD TWINNING PROJECT FICHE
 ANNEX C1 1 STANDARD TWINNING PROJECT FICHE 1. Basic Information 1.1 Publication notice reference: EuropeAid/ 137-622/DH/ACT/XK 1.2 Programme: Annual Action Programme for Kosovo 1 for 2014 1.3 Twinning
ANNEX C1 1 STANDARD TWINNING PROJECT FICHE 1. Basic Information 1.1 Publication notice reference: EuropeAid/ 137-622/DH/ACT/XK 1.2 Programme: Annual Action Programme for Kosovo 1 for 2014 1.3 Twinning
D2-02_01 Disaster Recovery in the modern EPU
 CONSEIL INTERNATIONAL DES GRANDS RESEAUX ELECTRIQUES INTERNATIONAL COUNCIL ON LARGE ELECTRIC SYSTEMS http:d2cigre.org STUDY COMMITTEE D2 INFORMATION SYSTEMS AND TELECOMMUNICATION 2015 Colloquium October
CONSEIL INTERNATIONAL DES GRANDS RESEAUX ELECTRIQUES INTERNATIONAL COUNCIL ON LARGE ELECTRIC SYSTEMS http:d2cigre.org STUDY COMMITTEE D2 INFORMATION SYSTEMS AND TELECOMMUNICATION 2015 Colloquium October
Risk Management & Business Continuity Manual 2011-2014
 ANNEX C Risk Management & Business Continuity Manual 2011-2014 Produced by the Risk Produced and by the Business Risk and Business Continuity Continuity Team Team February 2011 April 2011 Draft V.10 Page
ANNEX C Risk Management & Business Continuity Manual 2011-2014 Produced by the Risk Produced and by the Business Risk and Business Continuity Continuity Team Team February 2011 April 2011 Draft V.10 Page
White Paper on Financial Institution Vendor Management
 White Paper on Financial Institution Vendor Management Virtually every organization in the modern economy relies to some extent on third-party vendors that facilitate business operations in a wide variety
White Paper on Financial Institution Vendor Management Virtually every organization in the modern economy relies to some extent on third-party vendors that facilitate business operations in a wide variety
CYBER SECURITY STRATEGY OF THE CZECH REPUBLIC FOR THE 2011 2015 PERIOD
 CYBER SECURITY STRATEGY OF THE CZECH REPUBLIC FOR THE 2011 2015 PERIOD The 2011 2015 Cyber Security Strategy of the Czech Republic is linked to the Security Strategy of the Czech Republic and reflects
CYBER SECURITY STRATEGY OF THE CZECH REPUBLIC FOR THE 2011 2015 PERIOD The 2011 2015 Cyber Security Strategy of the Czech Republic is linked to the Security Strategy of the Czech Republic and reflects
Disaster Recovery and Business Continuity Plan
 Disaster Recovery and Business Continuity Plan Table of Contents 1. Introduction... 3 2. Objectives... 3 3. Risks... 3 4. Steps of Disaster Recovery Plan formulation... 3 5. Audit Procedure.... 5 Appendix
Disaster Recovery and Business Continuity Plan Table of Contents 1. Introduction... 3 2. Objectives... 3 3. Risks... 3 4. Steps of Disaster Recovery Plan formulation... 3 5. Audit Procedure.... 5 Appendix
Federal Financial Institutions Examination Council FFIEC BCP. Business Continuity Planning FEBRUARY 2015 IT EXAMINATION H ANDBOOK
 Federal Financial Institutions Examination Council FFIEC Business Continuity Planning BCP FEBRUARY 2015 IT EXAMINATION H ANDBOOK Table of Contents Introduction 1 Board and Senior Management Responsibilities
Federal Financial Institutions Examination Council FFIEC Business Continuity Planning BCP FEBRUARY 2015 IT EXAMINATION H ANDBOOK Table of Contents Introduction 1 Board and Senior Management Responsibilities
Code of Conduct on Data Centre Energy Efficiency. Endorser Guidelines and Registration Form. Version 3.0.0
 1 EUROPEAN COMMISSION DIRECTORATE-GENERAL JRC JOINT RESEARCH CENTRE Institute for Energy Renewable Energies Unit Ispra, 1 st January 2015 Code of Conduct on Data Centre Energy Efficiency Endorser Guidelines
1 EUROPEAN COMMISSION DIRECTORATE-GENERAL JRC JOINT RESEARCH CENTRE Institute for Energy Renewable Energies Unit Ispra, 1 st January 2015 Code of Conduct on Data Centre Energy Efficiency Endorser Guidelines
HMG Security Policy Framework
 HMG Security Policy Framework Security Policy Framework 3 Foreword Sir Jeremy Heywood, Cabinet Secretary Chair of the Official Committee on Security (SO) As Cabinet Secretary, I have a good overview of
HMG Security Policy Framework Security Policy Framework 3 Foreword Sir Jeremy Heywood, Cabinet Secretary Chair of the Official Committee on Security (SO) As Cabinet Secretary, I have a good overview of
Business Continuity Planning for Schools, Departments & Support Units
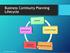 Business Continuity Planning for Schools, Departments & Support Units 1 What is Business Continuity Planning? Examples Planning for an adverse, major or catastrophic event that would cause a disruption
Business Continuity Planning for Schools, Departments & Support Units 1 What is Business Continuity Planning? Examples Planning for an adverse, major or catastrophic event that would cause a disruption
Frequently Asked Questions regarding European Innovation Partnerships
 May 2012 Frequently Asked Questions regarding European Innovation Partnerships 6 December 2010 FAQs 1. What are the objectives behind European innovation partnerships? 2. What concrete benefits can be
May 2012 Frequently Asked Questions regarding European Innovation Partnerships 6 December 2010 FAQs 1. What are the objectives behind European innovation partnerships? 2. What concrete benefits can be
FINANCIAL AND ADMINISTRATIVE FRAMEWORK AGREEMENT. between. the EUROPEAN UNION represented by the EUROPEAN COMMISSION. and. the UNITED NATIONS
 FINANCIAL AND ADMINISTRATIVE FRAMEWORK AGREEMENT between the EUROPEAN UNION represented by the EUROPEAN COMMISSION and the UNITED NATIONS Preamble The United Nations 1 (hereinafter referred to collectively
FINANCIAL AND ADMINISTRATIVE FRAMEWORK AGREEMENT between the EUROPEAN UNION represented by the EUROPEAN COMMISSION and the UNITED NATIONS Preamble The United Nations 1 (hereinafter referred to collectively
NHS 24 - Business Continuity Strategy
 NHS 24 - Strategy Version: 0.3 Issue Date: 20/09/2005 Status: Issued for Board Approval Status: draft Page 1 of 13 Table of Contents 1 INTRODUCTION...3 2 PURPOSE...3 3 SCOPE...3 4 ASSUMPTIONS...4 5 BUSINESS
NHS 24 - Strategy Version: 0.3 Issue Date: 20/09/2005 Status: Issued for Board Approval Status: draft Page 1 of 13 Table of Contents 1 INTRODUCTION...3 2 PURPOSE...3 3 SCOPE...3 4 ASSUMPTIONS...4 5 BUSINESS
Offsite Disaster Recovery Plan
 1 Offsite Disaster Recovery Plan Offsite Disaster Recovery Plan Presented By: Natan Verkhovsky President Disty Portal Inc. 2 Offsite Disaster Recovery Plan Introduction This document is a comprehensive
1 Offsite Disaster Recovery Plan Offsite Disaster Recovery Plan Presented By: Natan Verkhovsky President Disty Portal Inc. 2 Offsite Disaster Recovery Plan Introduction This document is a comprehensive
Guidance Note on Developing Terms of Reference (ToR) for Evaluations
 Evaluation Guidance Note Series UNIFEM Evaluation Unit October 2009 Guidance Note on Developing Terms of Reference (ToR) for Evaluations Terms of Reference (ToR) What? Why? And How? These guidelines aim
Evaluation Guidance Note Series UNIFEM Evaluation Unit October 2009 Guidance Note on Developing Terms of Reference (ToR) for Evaluations Terms of Reference (ToR) What? Why? And How? These guidelines aim
Cyber Security Strategy for Germany
 Cyber Security Strategy for Germany Contents Introduction 2 IT threat assessment 3 Framework conditions 4 Basic principles of the Cyber Security Strategy 4 Strategic objectives and measures 6 Sustainable
Cyber Security Strategy for Germany Contents Introduction 2 IT threat assessment 3 Framework conditions 4 Basic principles of the Cyber Security Strategy 4 Strategic objectives and measures 6 Sustainable
Service Children s Education
 Service Children s Education Data Handling and Security Information Security Audit Issued January 2009 2009 - An Agency of the Ministry of Defence Information Security Audit 2 Information handling and
Service Children s Education Data Handling and Security Information Security Audit Issued January 2009 2009 - An Agency of the Ministry of Defence Information Security Audit 2 Information handling and
ASX SETTLEMENT OPERATING RULES Guidance Note 10
 BUSINESS CONTINUITY AND DISASTER RECOVERY The purpose of this Guidance Note The main points it covers To assist participants to understand the disaster recovery and business continuity arrangements they
BUSINESS CONTINUITY AND DISASTER RECOVERY The purpose of this Guidance Note The main points it covers To assist participants to understand the disaster recovery and business continuity arrangements they
Roles within ITIL V3. Contents
 Roles within ITIL V3 Roles are employed in order to define responsibilities. In particular, they are used to assign Process Owners to the various ITIL V3 processes, and to illustrate responsibilities for
Roles within ITIL V3 Roles are employed in order to define responsibilities. In particular, they are used to assign Process Owners to the various ITIL V3 processes, and to illustrate responsibilities for
Cyber Security Risk Management
 Our Ref.: B1/15C B9/29C 15 September 2015 The Chief Executive All Authorized Institutions Dear Sir/Madam, Cyber Security Risk Management I am writing to draw your attention to the growing importance of
Our Ref.: B1/15C B9/29C 15 September 2015 The Chief Executive All Authorized Institutions Dear Sir/Madam, Cyber Security Risk Management I am writing to draw your attention to the growing importance of
STANDARD TWINNING PROJECT FICHE Strengthening the medium term budgeting for effective public financial management
 STANDARD TWINNING PROJECT FICHE Strengthening the medium term budgeting for effective public financial management List of abbreviations BC BC PL BFD CV CFCD EC EPSO ESA EU EUD GFS IMF IPA IPA IR MIPD MoF
STANDARD TWINNING PROJECT FICHE Strengthening the medium term budgeting for effective public financial management List of abbreviations BC BC PL BFD CV CFCD EC EPSO ESA EU EUD GFS IMF IPA IPA IR MIPD MoF
El Camino College Homeland Security Spring 2016 Courses
 El Camino College Homeland Security Spring 2016 Courses With over 250,000 federal positions in Homeland Security and associated divisions, students may find good career opportunities in this field. Explore
El Camino College Homeland Security Spring 2016 Courses With over 250,000 federal positions in Homeland Security and associated divisions, students may find good career opportunities in this field. Explore
Security Risk Assessment Tool
 Security Risk Assessment Tool Version: (Draft) 24 April 2014 This tool was developed by the ACT Safety & Security Community of Practice (SSCP) for use by ACT Alliance members and partners. 1. Purpose of
Security Risk Assessment Tool Version: (Draft) 24 April 2014 This tool was developed by the ACT Safety & Security Community of Practice (SSCP) for use by ACT Alliance members and partners. 1. Purpose of
THE DOMESTIC SURVEY AND THE CONSEQUENT RECOMMENDATIONS
 OVERSIGHT RECOMMENDATIONS ON BUSINESS CONTINUITY BACKGROUND OF THE DOMESTIC SURVEY Unexpected incidents worldwide have focused the attention of the financial sector, including the participants of the domestic
OVERSIGHT RECOMMENDATIONS ON BUSINESS CONTINUITY BACKGROUND OF THE DOMESTIC SURVEY Unexpected incidents worldwide have focused the attention of the financial sector, including the participants of the domestic
Communication Plan. for the. ATLANTIC AREA 2007-2013 Transnational Cooperation Programme
 Communication Plan for the ATLANTIC AREA 2007-2013 Transnational Cooperation Programme Prepared by the Managing Authority 18 January 2008 Index 0. Introduction... 2 1. Communication Strategy... 2 1.1
Communication Plan for the ATLANTIC AREA 2007-2013 Transnational Cooperation Programme Prepared by the Managing Authority 18 January 2008 Index 0. Introduction... 2 1. Communication Strategy... 2 1.1
Law on Fire Safety of the Republic of Azerbaijan
 Chapter I. General provisions Law on Fire Safety of the Republic of Azerbaijan Article 1. Key definitions used in this Law Following definitions are applied for the purposes of this Law: 1) Fire- uncontrolled
Chapter I. General provisions Law on Fire Safety of the Republic of Azerbaijan Article 1. Key definitions used in this Law Following definitions are applied for the purposes of this Law: 1) Fire- uncontrolled
Business Continuity Planning at Financial Institutions
 Business Continuity Planning at Financial Institutions July 2003 Bank of Japan Table of Contents Introduction...2 1 The Bank s View of Business Continuity Planning 1) Significance of business continuity
Business Continuity Planning at Financial Institutions July 2003 Bank of Japan Table of Contents Introduction...2 1 The Bank s View of Business Continuity Planning 1) Significance of business continuity
Audit Report. Effectiveness of IT Controls at the Global Fund Follow-up report. GF-OIG-15-20b 26 November 2015 Geneva, Switzerland
 Audit Report Effectiveness of IT Controls at the Global Fund Follow-up report GF-OIG-15-20b Geneva, Switzerland Table of Contents I. Background and scope... 3 II. Executive Summary... 4 III. Status of
Audit Report Effectiveness of IT Controls at the Global Fund Follow-up report GF-OIG-15-20b Geneva, Switzerland Table of Contents I. Background and scope... 3 II. Executive Summary... 4 III. Status of
ASSOCIATION OF CARIBBEAN STATES (ACS) 19th MEETING OF THE SPECIAL COMMITTEE FOR DISASTER RISK REDUCTION. Bogotá, Colombia, August 2-3 2011
 ACS/2011/DRR.19/WP.002 Original: English Last update: 26 July 2011 ASSOCIATION OF CARIBBEAN STATES (ACS) 19th MEETING OF THE SPECIAL COMMITTEE FOR DISASTER RISK REDUCTION Bogotá, Colombia, August 2-3 2011
ACS/2011/DRR.19/WP.002 Original: English Last update: 26 July 2011 ASSOCIATION OF CARIBBEAN STATES (ACS) 19th MEETING OF THE SPECIAL COMMITTEE FOR DISASTER RISK REDUCTION Bogotá, Colombia, August 2-3 2011
FFIEC Cybersecurity Assessment Tool
 Overview In light of the increasing volume and sophistication of cyber threats, the Federal Financial Institutions Examination Council 1 (FFIEC) developed the Cybersecurity Tool (), on behalf of its members,
Overview In light of the increasing volume and sophistication of cyber threats, the Federal Financial Institutions Examination Council 1 (FFIEC) developed the Cybersecurity Tool (), on behalf of its members,
Advisory Guidelines of the Financial Supervisory Authority. Requirements regarding the arrangement of operational risk management
 Advisory Guidelines of the Financial Supervisory Authority Requirements regarding the arrangement of operational risk management These Advisory Guidelines have established by resolution no. 63 of the Management
Advisory Guidelines of the Financial Supervisory Authority Requirements regarding the arrangement of operational risk management These Advisory Guidelines have established by resolution no. 63 of the Management
By: Tracy Hall. Community Bank Auditors Group Taking Your Business Continuity Plan To The Next Level. June 9, 2015
 Community Bank Auditors Group Taking Your Business Continuity Plan To The Next Level June 9, 2015 By: Tracy Hall MEMBER OF PKF NORTH AMERICA, AN ASSOCIATION OF LEGALLY INDEPENDENT FIRMS 2015 Wolf & Company,
Community Bank Auditors Group Taking Your Business Continuity Plan To The Next Level June 9, 2015 By: Tracy Hall MEMBER OF PKF NORTH AMERICA, AN ASSOCIATION OF LEGALLY INDEPENDENT FIRMS 2015 Wolf & Company,
How To Manage A Financial Institution
 BUSINESS CONTINUITY MANAGEMENT GUIDELINE April 2010 Table of Contents Preamble...3 Introduction...4 Scope...5 Coming into effect and updating...6 1. Continuity and resumption of business...7 2. Sound and
BUSINESS CONTINUITY MANAGEMENT GUIDELINE April 2010 Table of Contents Preamble...3 Introduction...4 Scope...5 Coming into effect and updating...6 1. Continuity and resumption of business...7 2. Sound and
Risk Management Strategy EEA & Norway Grants 2009-2014. Adopted by the Financial Mechanism Committee on 27 February 2013.
 Risk Management Strategy EEA & Norway Grants 2009-2014 Adopted by the Financial Mechanism Committee on 27 February 2013. Contents 1 Purpose of the strategy... 3 2 Risk management as part of managing for
Risk Management Strategy EEA & Norway Grants 2009-2014 Adopted by the Financial Mechanism Committee on 27 February 2013. Contents 1 Purpose of the strategy... 3 2 Risk management as part of managing for
www.pwc.com Business Resiliency Business Continuity Management - January 14, 2014
 www.pwc.com Business Resiliency Business Continuity Management - January 14, 2014 Agenda Key Definitions Risks Business Continuity Management Program BCM Capability Assessment Process BCM Value Proposition
www.pwc.com Business Resiliency Business Continuity Management - January 14, 2014 Agenda Key Definitions Risks Business Continuity Management Program BCM Capability Assessment Process BCM Value Proposition
