What do I need to do to use an authentication app on my smartphone? What do I need to do to use an authentication app on my PC or laptop?
|
|
|
- Hilary Greene
- 7 years ago
- Views:
Transcription
1
2 What is two-factor authentication? Why has SIDN introduced two-factor authentication? When do we have to start using two-factor authentication? How is the log-in procedure changing? What second authentication methods are available? Which authentication apps does SIDN support? How do I log in the first time? What is the best authentication method for me to use? How does authentication by app work? What do I need to do to use an authentication app on my smartphone? What is the best authentication app to use on my smartphone? What do I need to do to use an authentication app on my PC or laptop? What is the best authentication app to use on my PC or laptop? How does SMS authentication work? What if I don't have a (business) mobile or we don't give our personnel (business) mobiles that can be used for authentication? What if I don't have (or the user doesn't have) a smartphone? What if my smartphone doesn't have a camera, or the camera doesn't work? What if I lose my mobile or if my mobile number changes? What if I forget my user name or password? What if I'm denied access? What if I enter the authentication code, but the DRS takes me back to the log-in screen? What if the DRS stops accepting the verification codes generated by the authentication app?
3 Two-factor authentication is an extended log-in procedure. We are introducing it for the web interface of DRS5. Whereas accessing the web interface used to involve entering a user name and password, it now also involves a second authentication step. After you have entered your details on the familiar log-in screen, you meet a second authentication screen. On the 'Additional authentication' screen, you have to enter a verification code sent to you by SMS ('text message') or generated by an authentication app before you reach the web interface.
4 Two-factor authentication increases the security of the web application. It stops an unauthorised person who has got hold of a user's password from gaining access to the application. The introduction of two-factor authentication follows on naturally from the recent switch from a single user account for each registrar to individual accounts for each person who uses the DRS. Both changes are part of a general strategy of making the web application more accessible and more secure. Two-factor authentication comes into effect at the end of September 2015.
5 After you have entered your details on the familiar log-in screen, you meet a second authentication screen. On the 'Additional authentication' screen, you have to enter a verification code sent to you by How does SMS authentication work? ('text message') or generated by an Which authentication apps does SIDN support? before you reach the web interface. We recommend using a What do I need to do to use an authentication app on my smartphone?. That does, however, require the user to have a What do I need to do to use an authentication app on my PC or laptop? installed on a smartphone or computer, whereas SMS authentication is possible with any mobile phone. We recognise that the introduction of two-factor authentication will make logging in to the DRS less straightforward than it used to be. However, we believe that the change is needed to ensure the security of the web application, which is in your interest too. To minimise the inconvenience, the system offers a choice of second authentication method: If you have a smartphone, the easiest approach is to install an What do I need to do to use an authentication app on my smartphone?. Then, after your How do I log in the first time?, the app will generate the verification codes. If you want to use a mobile phone that isn't a smartphone, you can click the 'SMS' button on the How does SMS authentication work? to have a verification code sent to the mobile phone number linked to your user account, in the form of an SMS message ('text message'). If you don't have a smartphone or a simple mobile available for logging in, you can also use an authentication app installed on a What do I need to do to use an authentication app on my PC or laptop? to generate verification codes. In principle, computer apps work in the same way as mobile apps.
6 Our two-factor authentication system uses the open OATH standard (RFC 6238). You can therefore use any authentication app that supports the OATH standard. Click What is the best authentication app to use on my smartphone? for more information about available mobile apps. Click What is the best authentication app to use on my PC or laptop? for more information about available apps for PC/laptop. The first time you log in under the new system, you have to use How does SMS authentication work? for authentication. That is because an How does authentication by app work? requires a private key, which can't be displayed until you have completed the log-in process. To register your authentication-app, you need to tick the checkbox on the 'Additional authentication' screen before clicking the 'Log in' button. You will then be given a key, both in QR code form and in text form. Once you have entered the key into an authentication app, you can use the app to generate verification codes.
7 We believe that a What do I need to do to use an authentication app on my smartphone? is the best option for most users. You only have to scan in the private key once, after which the app generates a sixdigit verification code each time you log in, providing quick access to DRS5's web interface. Authentication by SMS for which you are reliant on a mobile phone network is therefore necessary only once. SMS authentication is always available as an option, however.
8 If you use an authentication app, the app generates a six-digit verification code, which remains valid for thirty seconds. You enter the code in the relevant field on the DRS authentication screen and then click the 'Log in' button. After that, the familiar web interface will open. Before you can use an authentication app on your smartphone, a private key has to be passed between SIDN's system and the app. To obtain a private key, you need to tick the checkbox on the 'Additional authentication' screen before clicking the 'Log in' button. Then, when you log in, you will be presented with a new key in the form of a QR code. Your mobile authentication app will be able to read the key straight from your computer screen if you simply hold your smartphone up to the screen. As shown in the screen grab below, the private key also appears in text form above the QR code. So you have the option of entering the key into the app manually.
9 NB: Regardless of how you normally intend to log-in using an authentication app or with SMS authentication your very How do I log in the first time? must be How does SMS authentication work?. You have to complete the log-in process once (and tick the 'Request key' option) in order to obtain the private key that you need to subsequently use an authentication app. Any authentication app that supports the open OATH standard (RFC 6238) can be used to log in to DRS5's web interface. Suitable apps include the following: Google Authenticator: now closed-source FreeOTP: available for Android and ios; based on the open-source code of Google Authenticator, supported by Red Hat Before you can use an authentication app on your PC or laptop, a private key has to be passed between SIDN's system and the app. To obtain a private key, you need to tick the checkbox on the 'Additional authentication' screen before clicking the 'Log in' button.
10 Then, when you log in, you will be presented with a new key in the form of a QR code with text above. The key text needs to be entered into your authentication app. NB: Regardless of how you normally intend to log-in using an authentication app or with SMS authentication your very How do I log in the first time? must be How does SMS authentication work?. You have to complete the log-in process once (and tick the 'Request key' option) in order to obtain the private key that you need to subsequently use an authentication app. Any authentication app that supports the open OATH standard (RFC 6238) can be used to log in to DRS5's web interface. Suitable apps include the following: GAuth: open source Authy: commercial
11 If you use a web app for authentication, we recommend that, for security reasons, you do not run it on the same machine that you use to access DRS5's web interface. With SMS authentication, you can log in using a mobile phone that isn't a smartphone. To use this authentication method, click the 'SMS' button on the 'Additional authentication' screen. An eight-digit verification code will then be sent by SMS ('text message') to the mobile number linked to your user account. Confirmation that the code has been sent will appear on screen. Enter the code in the relevant field on the DRS authentication screen and then click the 'Log in' button. After that, the familiar web interface will open. The verification code sent by SMS remains valid for one minute. You must use How does SMS authentication work? ('text message') authentication the How do I log in the first time? under the new system. When you do so, you can tick the checkbox, so that after that you can use an authentication app instead of SMS. You will be given a key, both in QR code form and in text form. Once you have entered the key into an authentication app installed on a PC or laptop, you can use the app to generate verification codes.
12 We believe that a What do I need to do to use an authentication app on my smartphone? is the best option for most users. However, authentication apps are also available for PCs and laptops. You are only obliged to use How does SMS authentication work? the How do I log in the first time? under the new system. However, SMS ('text message') authentication is always available as an option that you can use if you prefer. Another option is to use an authentication app installed on a What do I need to do to use an authentication app on my PC or laptop?. The private key that you need to enter into your How does authentication by app work? is made available both in the form of a QR code and in the form of text that you can simply type into your app. The text is shown above the QR code.
13
14 If you are not your organisation's admin user, you'll need his or her help. If you are the admin user, you'll need to contact our support department. If you call support for help, you'll be asked to provide your SIDN identification code (SID). If you are not your organisation's admin user, you'll need his or her help. If you are the admin user, you'll need to contact our support department. If you call support for help, you'll be asked to provide your SIDN identification code (SID). Once your password has been reset, you'll need a new private key to continue using an authentication app. To get one, you'll need How do I log in the first time? using How does SMS authentication work?, and request a new private key. You will be denied access if the status of your organisation's registrar account is 'Inactive', or if your personal user account has been deactivated by SIDN or deleted by your admin user. If that happens, contact your organisation's admin user. The session times for the log-in screen and the authentication screen are short. So you need to complete the whole procedure without a significant pause. Otherwise, your session will time out and you'll be taken back to the start. If you are not your organisation's admin user, you'll need his or her help. It might be that your admin user has reset your password. If you are the admin user and SIDN has reset your password, you'll need a new private key to continue using an authentication app. To get one, you'll need How do I log in the first time? using How does SMS authentication work?, and request a new private key.
Two Factor Authentication - USER GUIDE
 Two Factor Authentication - USER GUIDE Two Factor Authentication (or 2FA) is a two step verification process that provides an extra layer of security for you when accessing your account within Online Services.
Two Factor Authentication - USER GUIDE Two Factor Authentication (or 2FA) is a two step verification process that provides an extra layer of security for you when accessing your account within Online Services.
Google 2 factor authentication User Guide
 Information Technology Services Centre Google 2 factor authentication User Guide Description: This guide describes how to setup Two factor authentication for your Google account. Version: 1.0 Link: Effective
Information Technology Services Centre Google 2 factor authentication User Guide Description: This guide describes how to setup Two factor authentication for your Google account. Version: 1.0 Link: Effective
Two-Factor Authentication
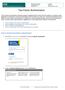 Two-Factor Authentication The two-factor authentication system provides an additional level of security when signing in to Ryerson web applications via Ryerson s Central Authentication Service. When you
Two-Factor Authentication The two-factor authentication system provides an additional level of security when signing in to Ryerson web applications via Ryerson s Central Authentication Service. When you
Two-Factor Authentication
 Two-Factor Authentication Two-Factor Authentication is an enhanced security feature for Payentry. It adds an extra layer of protection to ensure only authorized users can gain access to your data. In addition
Two-Factor Authentication Two-Factor Authentication is an enhanced security feature for Payentry. It adds an extra layer of protection to ensure only authorized users can gain access to your data. In addition
2-FACTOR AUTHENTICATION WITH
 2-FACTOR AUTHENTICATION WITH 2X JUNE 2014 Two-Factor Authentication and Authy What is Two-Factor Authentication? Two-Factor Authentication is a process involving two stages to verify the identity of someone
2-FACTOR AUTHENTICATION WITH 2X JUNE 2014 Two-Factor Authentication and Authy What is Two-Factor Authentication? Two-Factor Authentication is a process involving two stages to verify the identity of someone
Registration for My Profile & Administration
 Registration for My Profile & Administration Table Of Contents User Registration... 1 Registering as a New User... 1 About the IDcipherTM Card... 7 How Do I Get An IDcipher TM Card?... 8 Two-Factor Authentication...
Registration for My Profile & Administration Table Of Contents User Registration... 1 Registering as a New User... 1 About the IDcipherTM Card... 7 How Do I Get An IDcipher TM Card?... 8 Two-Factor Authentication...
NetIQ Advanced Authentication Framework - Smartphone Applications
 NetIQ Advanced Authentication Framework - Smartphone Applications User Guide Version 3.0 1 Table of Contents 1 Table of Contents 2 Introduction 3 About This Document 3 System Requirements 4 Install Smartphone
NetIQ Advanced Authentication Framework - Smartphone Applications User Guide Version 3.0 1 Table of Contents 1 Table of Contents 2 Introduction 3 About This Document 3 System Requirements 4 Install Smartphone
Electronic Questionnaires for Investigations Processing (e-qip)
 January 2016 Electronic Questionnaires for Investigations Processing (e-qip) Login Instructions for first-time users OR users that have had their accounts reset Step 1 Access the e-qip Login screen at
January 2016 Electronic Questionnaires for Investigations Processing (e-qip) Login Instructions for first-time users OR users that have had their accounts reset Step 1 Access the e-qip Login screen at
Two-Step Authentication FAQ
 Two-Step Authentication FAQ General Questions Q: Why is Stanford requiring this additional step? A: Hackers, including foreign state-sponsored entities, are attacking university computer systems with ever-increasing
Two-Step Authentication FAQ General Questions Q: Why is Stanford requiring this additional step? A: Hackers, including foreign state-sponsored entities, are attacking university computer systems with ever-increasing
Guide for Setting Up Your Multi-Factor Authentication Account and Using Multi-Factor Authentication. Mobile App Activation
 Guide for Setting Up Your Multi-Factor Authentication Account and Using Multi-Factor Authentication Mobile App Activation Before you can activate the mobile app you must download it. You can have up to
Guide for Setting Up Your Multi-Factor Authentication Account and Using Multi-Factor Authentication Mobile App Activation Before you can activate the mobile app you must download it. You can have up to
Sophos Mobile Control User guide for Android
 Sophos Mobile Control User guide for Android Product version: 2.5 Document date: July 2012 Contents 1 About Sophos Mobile Control... 3 2 Login to the Self Service Portal... 4 3 Set up Sophos Mobile Control
Sophos Mobile Control User guide for Android Product version: 2.5 Document date: July 2012 Contents 1 About Sophos Mobile Control... 3 2 Login to the Self Service Portal... 4 3 Set up Sophos Mobile Control
Student Quick Start Guide
 Student Quick Start Guide Welcome to Top Hat! This guide will help you register a student account and understand how to use Top Hat for your class. Creating an Account 1. If you don t already have a previous
Student Quick Start Guide Welcome to Top Hat! This guide will help you register a student account and understand how to use Top Hat for your class. Creating an Account 1. If you don t already have a previous
Multi-Factor Authentication Job Aide
 To start your account configuration and begin using Multi-Factor Authentication, log in to the CCHMC Multi-Factor Authentication User Portal at https://mfa.cchmc.org/multifactorauth. For assistance, please
To start your account configuration and begin using Multi-Factor Authentication, log in to the CCHMC Multi-Factor Authentication User Portal at https://mfa.cchmc.org/multifactorauth. For assistance, please
APPENDIX 8 EAZY NETWORKING
 APPENDIX 8 EAZY NETWORKING EaZy Networking is a cloud service to connect your devices to the Internet automatically through our free mobile app, EagleEyes, in a few steps without going through the complicated
APPENDIX 8 EAZY NETWORKING EaZy Networking is a cloud service to connect your devices to the Internet automatically through our free mobile app, EagleEyes, in a few steps without going through the complicated
Step 1. Step 2. Open your browser and go to https://accounts.bestcare.org and you will be presented a logon screen show below.
 Manage your two-factor options through the accounts.bestcare.org website. This website is available internally and externally of the organization. Like other services, if you connect while external of
Manage your two-factor options through the accounts.bestcare.org website. This website is available internally and externally of the organization. Like other services, if you connect while external of
AWS Account Management Guidance
 AWS Account Management Guidance Introduction Security is a top priority at AWS. Every service that is offered is tightly controlled and adheres to a strict security standard. This is evident in the security
AWS Account Management Guidance Introduction Security is a top priority at AWS. Every service that is offered is tightly controlled and adheres to a strict security standard. This is evident in the security
Merchant Portal Guide. TradeRoute Copyright 2014. All Rights Reserved.
 Merchant Portal Guide TradeRoute Copyright 2014. All Rights Reserved. TradeRoute Merchant Portal User Manual Table of Contents TradeRoute Merchant Account Portal Login Instructions... 3-4 Recovering your
Merchant Portal Guide TradeRoute Copyright 2014. All Rights Reserved. TradeRoute Merchant Portal User Manual Table of Contents TradeRoute Merchant Account Portal Login Instructions... 3-4 Recovering your
Brainloop Secure Dataroom Version 8.30. QR Code Scanner Apps for ios Version 1.1 and for Android
 Brainloop Secure Dataroom Version 8.30 QR Code Scanner Apps for ios Version 1.1 and for Android Quick Guide Brainloop Secure Dataroom Version 8.30 Copyright Brainloop AG, 2004-2015. All rights reserved.
Brainloop Secure Dataroom Version 8.30 QR Code Scanner Apps for ios Version 1.1 and for Android Quick Guide Brainloop Secure Dataroom Version 8.30 Copyright Brainloop AG, 2004-2015. All rights reserved.
Mobile Online Banking
 Mobile Online Banking User Guide Table of Contents Enrolling Through Traditional Online Banking, pg. 2 Enrolling Using Your Mobile Device, pg. 4 Login Screen, pg. 7 Locations, pg. 7 Mobile Browser View,
Mobile Online Banking User Guide Table of Contents Enrolling Through Traditional Online Banking, pg. 2 Enrolling Using Your Mobile Device, pg. 4 Login Screen, pg. 7 Locations, pg. 7 Mobile Browser View,
Sophos Mobile Control User guide for Android. Product version: 4
 Sophos Mobile Control User guide for Android Product version: 4 Document date: May 2014 Contents 1 About Sophos Mobile Control...3 2 About this guide...4 3 Login to the Self Service Portal...5 4 Set up
Sophos Mobile Control User guide for Android Product version: 4 Document date: May 2014 Contents 1 About Sophos Mobile Control...3 2 About this guide...4 3 Login to the Self Service Portal...5 4 Set up
Guidelines to setup mobile devices to a UOITnet account Google Apps for Education. Information Technology Services
 Guidelines to setup mobile devices to a UOITnet account Google Apps for Education Information Technology Services Contents Support for UOITnet email set up on a Mobile Device... 2 Generate Google Token...
Guidelines to setup mobile devices to a UOITnet account Google Apps for Education Information Technology Services Contents Support for UOITnet email set up on a Mobile Device... 2 Generate Google Token...
Using GhostPorts Two-Factor Authentication
 Using GhostPorts Two-Factor Authentication With CloudPassage Halo GhostPorts is a powerful two-factor authentication feature available with the Halo NetSec and Halo Professional subscription plans. GhostPorts
Using GhostPorts Two-Factor Authentication With CloudPassage Halo GhostPorts is a powerful two-factor authentication feature available with the Halo NetSec and Halo Professional subscription plans. GhostPorts
Remote Desktop Solution, (RDS), replacing CITRIX Home Access
 Remote Desktop Solution, (RDS), replacing CITRIX Home Access RDS Applications on a Computer Overview RDS has replaced citrix for remote access at home for College staff and pupils. This does not replace
Remote Desktop Solution, (RDS), replacing CITRIX Home Access RDS Applications on a Computer Overview RDS has replaced citrix for remote access at home for College staff and pupils. This does not replace
Downloading Electro Scan Smartphone App From Google Play* * Previously known as The Android Market
 Downloading Electro Scan Smartphone App From Google Play* * Previously known as The Android Market Hello and Welcome to Electro Scan s Next Generation in Leak Detection Before you begin, please make sure
Downloading Electro Scan Smartphone App From Google Play* * Previously known as The Android Market Hello and Welcome to Electro Scan s Next Generation in Leak Detection Before you begin, please make sure
User s manual for Android Application
 Motorised IP Video surveillance camera for smartphones, tablets and PC / MAC. Protect your home and family remotely! User s manual for Android Application Thanks We thank you for choosing Aquila Vizion.
Motorised IP Video surveillance camera for smartphones, tablets and PC / MAC. Protect your home and family remotely! User s manual for Android Application Thanks We thank you for choosing Aquila Vizion.
Mobile Device Management: Deployment
 Mobile Device Management: Deployment MOBILE DEVICE MANAGEMENT: DEPLOYMENT... 1 Overview... 1 Give Access to Enroll Mobile Devices... 1 Via Web Link on the Web Control Center... 1 Via Android Market...
Mobile Device Management: Deployment MOBILE DEVICE MANAGEMENT: DEPLOYMENT... 1 Overview... 1 Give Access to Enroll Mobile Devices... 1 Via Web Link on the Web Control Center... 1 Via Android Market...
Acano solution. Acano Clients v1.7 Getting Started Guide. June 2015 76-1047-03-D
 Acano solution Acano Clients v1.7 Getting Started Guide June 2015 76-1047-03-D Contents Contents 1 Introduction... 4 1.1 cospaces... 4 1.2 cospace Users... 4 1.3 The Acano Client... 5 2 Overview... 6 2.1
Acano solution Acano Clients v1.7 Getting Started Guide June 2015 76-1047-03-D Contents Contents 1 Introduction... 4 1.1 cospaces... 4 1.2 cospace Users... 4 1.3 The Acano Client... 5 2 Overview... 6 2.1
Management Website User Guide. SecureAnywhere AntiVirus SecureAnywhere Internet Security Plus SecureAnywhere Complete
 Management Website User Guide SecureAnywhere AntiVirus SecureAnywhere Internet Security Plus SecureAnywhere Complete Copyright Management Website User Guide July, 2013 2012-2013 Webroot Software, Inc.
Management Website User Guide SecureAnywhere AntiVirus SecureAnywhere Internet Security Plus SecureAnywhere Complete Copyright Management Website User Guide July, 2013 2012-2013 Webroot Software, Inc.
MOBILE BANKING. Why should I use Mobile Banking?
 MOBILE BANKING What is Mobile Banking? With Mobile Banking, you can access your account, conduct transfers, and pay and manage bills from any mobile device that has web browsing capabilities and a data
MOBILE BANKING What is Mobile Banking? With Mobile Banking, you can access your account, conduct transfers, and pay and manage bills from any mobile device that has web browsing capabilities and a data
DUO SECURITY CISCO VPN USER GUIDE 1/27/2016
 DUO SECURITY CISCO VPN USER GUIDE 1/27/2016 CONTENTS Enrolling Your Devices... 2 Install Cisco AnyConnect VPN Client... 6 Connecting to a PC with Microsoft Remote Desktop... 8 Disconnecting the AnyConnect
DUO SECURITY CISCO VPN USER GUIDE 1/27/2016 CONTENTS Enrolling Your Devices... 2 Install Cisco AnyConnect VPN Client... 6 Connecting to a PC with Microsoft Remote Desktop... 8 Disconnecting the AnyConnect
Using Devices. Chapter 3
 Chapter 3 Using Devices es The Devices page lists all the devices you have enrolled in the Centrify identity platform and lets you send commands to the devices. Device related tasks that you can perform
Chapter 3 Using Devices es The Devices page lists all the devices you have enrolled in the Centrify identity platform and lets you send commands to the devices. Device related tasks that you can perform
TeamViewer & DynGate Manual V 2.0
 TeamViewer & DynGate Manual V 2.0 i Table Of Contents 1. OVERVIEW... 1 1.1. INTRODUCTION... 1 1.2. TEAMVIEWER RELATED DOWNLOADS... 2 1.3. ABOUT THIS MANUAL... 4 2. INSTALLATION... 5 2.1. CLIENT- AND HOST
TeamViewer & DynGate Manual V 2.0 i Table Of Contents 1. OVERVIEW... 1 1.1. INTRODUCTION... 1 1.2. TEAMVIEWER RELATED DOWNLOADS... 2 1.3. ABOUT THIS MANUAL... 4 2. INSTALLATION... 5 2.1. CLIENT- AND HOST
Central Commissioning Facility Research Management Systems (RMS): User Guidance
 Central Commissioning Facility Research Management Systems (RMS): User Guidance Contents 1. How to login and register a new account... 2 2. How to accept an invitation to review... 8 3. How to submit a
Central Commissioning Facility Research Management Systems (RMS): User Guidance Contents 1. How to login and register a new account... 2 2. How to accept an invitation to review... 8 3. How to submit a
Photo library user guide
 Photo library user guide Section 1: Getting started What is asset bank? Asset bank is the Council s photo library. The system allows the Council to organise photos in one place. What are the benefits of
Photo library user guide Section 1: Getting started What is asset bank? Asset bank is the Council s photo library. The system allows the Council to organise photos in one place. What are the benefits of
HE Gateway User guide for colleges and universities
 HE Gateway User guide for colleges and universities HE Gateway 1 Student Loans Company Ltd Contents Section 1 Definitions & Related Documents...3 Definitions... 3 Related Documents... 3 Section 2 Purpose
HE Gateway User guide for colleges and universities HE Gateway 1 Student Loans Company Ltd Contents Section 1 Definitions & Related Documents...3 Definitions... 3 Related Documents... 3 Section 2 Purpose
FREQUENTLY ASKED QUESTIONS Capital City Bank Mobile Deposit
 FREQUENTLY ASKED QUESTIONS Capital City Bank offers CCBMobile Deposit and Mobile Deposit Plus to accommodate varying deposit needs. Consider your typical monthly deposit needs when determining which service
FREQUENTLY ASKED QUESTIONS Capital City Bank offers CCBMobile Deposit and Mobile Deposit Plus to accommodate varying deposit needs. Consider your typical monthly deposit needs when determining which service
MyPrint instructions; printing, scanning and copying. version 1.3 EN march 2015
 MyPrint instructions; printing, scanning and copying version 1.3 EN march 2015 TOC 1 Introduction to myprint 3 1.1 Print credit and payments 3 1.2 Accepting the terms 3 2 Upgrading credit (students only)
MyPrint instructions; printing, scanning and copying version 1.3 EN march 2015 TOC 1 Introduction to myprint 3 1.1 Print credit and payments 3 1.2 Accepting the terms 3 2 Upgrading credit (students only)
Multi-Factor Authentication for first time users
 Multi-Factor Authentication for first time users **Multi-Factor Authentication will be required for all Duke University accounts on July 1 st, 2016.** What is Multi-Factor Authentication (MFA)?? Multi-factor
Multi-Factor Authentication for first time users **Multi-Factor Authentication will be required for all Duke University accounts on July 1 st, 2016.** What is Multi-Factor Authentication (MFA)?? Multi-factor
EXTERNAL GUIDE GUIDE FOR TAX PRACTITIONERS ON EFILING
 GUIDE FOR TAX PRACTITIONERS ON TABLE OF CONTENTS 1 PURPOSE 3 2 INTRODUCTION 3 3 LEGISLATION BACKGROUND 3 4 OFFENCES 3 5 REGISTRATION PROCESS 4 6 TAX PRACTITIONER USER FUNCTIONALITY 10 6.1 REGISTER NEW
GUIDE FOR TAX PRACTITIONERS ON TABLE OF CONTENTS 1 PURPOSE 3 2 INTRODUCTION 3 3 LEGISLATION BACKGROUND 3 4 OFFENCES 3 5 REGISTRATION PROCESS 4 6 TAX PRACTITIONER USER FUNCTIONALITY 10 6.1 REGISTER NEW
Help. myprint introduction myprint website. Create account. Forgot your password? Home. Printing using upload (WebPrint)
 myprint Help myprint introduction myprint website Create account Forgot your password? Home Printing using upload (WebPrint) Printing using email (EmailPrint) Printing using Right Mouse Click (Sent To
myprint Help myprint introduction myprint website Create account Forgot your password? Home Printing using upload (WebPrint) Printing using email (EmailPrint) Printing using Right Mouse Click (Sent To
Axis 360 Administrator User Manual. May 2015
 Axis 360 Administrator User Manual May 2015 Table of Contents 1 Introduction... 4 1.1 Site Access and Home Page... 4 2 Settings... 5 2.1 Library Settings... 5 2.1.1 Library Site Settings...5 2.1.2 Lending
Axis 360 Administrator User Manual May 2015 Table of Contents 1 Introduction... 4 1.1 Site Access and Home Page... 4 2 Settings... 5 2.1 Library Settings... 5 2.1.1 Library Site Settings...5 2.1.2 Lending
Two-Factor Authentication Basics for Linux. Pat Barron (pat@lectroid.com) Western PA Linux Users Group
 Two-Factor Authentication Basics for Linux Pat Barron (pat@lectroid.com) Western PA Linux Users Group Some Basic Security Terminology Two of the most common things we discuss related to security are Authentication
Two-Factor Authentication Basics for Linux Pat Barron (pat@lectroid.com) Western PA Linux Users Group Some Basic Security Terminology Two of the most common things we discuss related to security are Authentication
Guidelines for new users of the Union Registry ECAS account, registration and enrolment
 Guidelines for new users of the Union Registry ECAS account, registration and enrolment An ECAS account and registration are required for a new user to be added as an account representative Before a new
Guidelines for new users of the Union Registry ECAS account, registration and enrolment An ECAS account and registration are required for a new user to be added as an account representative Before a new
Faith Lutheran College, Redlands. Install and Setup Office 365
 Faith Lutheran College, Redlands Install and Setup Office 365 Table of Contents Install Office 365... 3 Set up my current Office desktop programs to work with Office 365 for business... 4 Connect your
Faith Lutheran College, Redlands Install and Setup Office 365 Table of Contents Install Office 365... 3 Set up my current Office desktop programs to work with Office 365 for business... 4 Connect your
SIEMENS. Operating Web Server. Opening program and changing message text properties
 With the new LOGO! 8 you can monitor and control your application via PC, smartphone or tablet via the integrated web server with all conventional browsers via the integrated web server. Opening program
With the new LOGO! 8 you can monitor and control your application via PC, smartphone or tablet via the integrated web server with all conventional browsers via the integrated web server. Opening program
Quick Installation Guide
 Quick Installation Guide Cloud Camera, 300Mbps Wi-Fi 7106505077 REV1.0.3 NC200 Configuring the Camera Via Smartphone: 9V=0.6A ETHERNET 1 Connecting the camera Connect the camera to the network your smartphone
Quick Installation Guide Cloud Camera, 300Mbps Wi-Fi 7106505077 REV1.0.3 NC200 Configuring the Camera Via Smartphone: 9V=0.6A ETHERNET 1 Connecting the camera Connect the camera to the network your smartphone
How to complete and submit an expert application
 How to complete and submit an expert application General information All applications must be completed and submitted online. The application form can only be completed in English, French or German. When
How to complete and submit an expert application General information All applications must be completed and submitted online. The application form can only be completed in English, French or German. When
DIGITAL CERTIFICATE INSTALLATION MANUAL
 DIGITAL CERTIFICATE INSTALLATION MANUAL TABLE OF CONTENTS BASIC CHECKS: INTERNET EXPLORER (IE)... 3 TROUBLESHOOTING TIPS (IE AND FIREFOX)... 9 INSTALLATION: WINDOWS XP, 7 OR 8 WITH IE 7,8 OR 9... 20 INSTALLATION:
DIGITAL CERTIFICATE INSTALLATION MANUAL TABLE OF CONTENTS BASIC CHECKS: INTERNET EXPLORER (IE)... 3 TROUBLESHOOTING TIPS (IE AND FIREFOX)... 9 INSTALLATION: WINDOWS XP, 7 OR 8 WITH IE 7,8 OR 9... 20 INSTALLATION:
Business Mobile Banking
 Business Mobile Banking Union Bank & Trust Business Mobile Application User Guide Contents Overview... 2 Security... 2 Requirements... 3 Downloading the App... 3 Logging In... 4 One-time Passcode Entry...
Business Mobile Banking Union Bank & Trust Business Mobile Application User Guide Contents Overview... 2 Security... 2 Requirements... 3 Downloading the App... 3 Logging In... 4 One-time Passcode Entry...
ASUS WebStorage Client-based for Windows [Advanced] User Manual
![ASUS WebStorage Client-based for Windows [Advanced] User Manual ASUS WebStorage Client-based for Windows [Advanced] User Manual](/thumbs/40/21159954.jpg) ASUS WebStorage Client-based for Windows [Advanced] User Manual 1 Welcome to ASUS WebStorage, your personal cloud space Our function panel will help you better understand ASUS WebStorage services. The
ASUS WebStorage Client-based for Windows [Advanced] User Manual 1 Welcome to ASUS WebStorage, your personal cloud space Our function panel will help you better understand ASUS WebStorage services. The
The Institute of Education Spam filter service allows you to take control of your spam filtering.
 CUSTOMISING THE IOE SPAM FILTER The Institute of Education Spam filter service allows you to take control of your spam filtering. The interface is very simple to access and use. Through a secure web page
CUSTOMISING THE IOE SPAM FILTER The Institute of Education Spam filter service allows you to take control of your spam filtering. The interface is very simple to access and use. Through a secure web page
Sophos Mobile Control user help. Product version: 6.1
 Sophos Mobile Control user help Product version: 6.1 Document date: May 2016 Contents 1 About this help...4 2 About Sophos Mobile Control...5 3 Login to the Self Service Portal...6 3.1 First login...6
Sophos Mobile Control user help Product version: 6.1 Document date: May 2016 Contents 1 About this help...4 2 About Sophos Mobile Control...5 3 Login to the Self Service Portal...6 3.1 First login...6
Citizens 1 st National Bank Mobile Banking FAQ
 Citizens 1 st National Bank Mobile Banking FAQ Citizens 1 st National Bank has an App for its customers available for Apple iphones, ipads and Android phones. SMARTPHONE DEVICE MINIMUM REQUIREMENTS APPLE
Citizens 1 st National Bank Mobile Banking FAQ Citizens 1 st National Bank has an App for its customers available for Apple iphones, ipads and Android phones. SMARTPHONE DEVICE MINIMUM REQUIREMENTS APPLE
Coillte IT has recently upgraded the Remote Access Solution to a new platform.
 Overview Coillte IT has recently upgraded the Remote Access Solution to a new platform. This document explains how to gain access to the Coillte network using your home computer through the new Remote
Overview Coillte IT has recently upgraded the Remote Access Solution to a new platform. This document explains how to gain access to the Coillte network using your home computer through the new Remote
T his feature is add-on service available to Enterprise accounts.
 SAML Single Sign-On T his feature is add-on service available to Enterprise accounts. Are you already using an Identity Provider (IdP) to manage logins and access to the various systems your users need
SAML Single Sign-On T his feature is add-on service available to Enterprise accounts. Are you already using an Identity Provider (IdP) to manage logins and access to the various systems your users need
Cloud Services. Lync. IM/ Web Conferencing Admin Quick Start Guide
 Cloud Services Lync IM/ Web Conferencing Admin Quick Start Guide 10/14/2014 ACTIVATION LETTER An activation letter will be sent to the email account of your administrator contact. Please look for the following
Cloud Services Lync IM/ Web Conferencing Admin Quick Start Guide 10/14/2014 ACTIVATION LETTER An activation letter will be sent to the email account of your administrator contact. Please look for the following
Single Sign-On Portal User Reference (Okta Cloud SSO)
 Single Sign-On Portal User Reference (Okta Cloud SSO) Contents Okta Single Sign-on Portal... 3 Initial account creation and configuration... 3 First time manual login to the Okta Single Sign-on Portal...
Single Sign-On Portal User Reference (Okta Cloud SSO) Contents Okta Single Sign-on Portal... 3 Initial account creation and configuration... 3 First time manual login to the Okta Single Sign-on Portal...
Guide for Setting Up Your Multi-Factor Authentication Account and Using Multi-Factor Authentication
 Guide for Setting Up Your Multi-Factor Authentication Account and Using Multi-Factor Authentication This document serves as a How To reference guide for employees to execute the following MFA tasks: 1.
Guide for Setting Up Your Multi-Factor Authentication Account and Using Multi-Factor Authentication This document serves as a How To reference guide for employees to execute the following MFA tasks: 1.
AVDC Document Management System Getting Started
 Page 1 of 7 AVDC Document Management System Getting Started Login Upon entering the AVDC document management system (http://www.avdc-dms.org/dms/ or via the link on the AVDC web site Home page), the initial
Page 1 of 7 AVDC Document Management System Getting Started Login Upon entering the AVDC document management system (http://www.avdc-dms.org/dms/ or via the link on the AVDC web site Home page), the initial
Microsoft Office 365 Exchange Online Cloud
 5-9-2014 A.Bueter Set up an Exchange connection to your email in Outlook 2010 or Outlook 2013 Note: Outlook 2007 is not supported with Office 365/Exchange Online- only Outlook 2010 & 2013 will work. 1.
5-9-2014 A.Bueter Set up an Exchange connection to your email in Outlook 2010 or Outlook 2013 Note: Outlook 2007 is not supported with Office 365/Exchange Online- only Outlook 2010 & 2013 will work. 1.
Setup guide for ebanking
 Setup guide for ebanking SETUP GUIDE This setup guide will take you through your initial logon to ebanking with Access ID. At the end of the setup guide, you will also find detailed contact information
Setup guide for ebanking SETUP GUIDE This setup guide will take you through your initial logon to ebanking with Access ID. At the end of the setup guide, you will also find detailed contact information
NetIQ Advanced Authentication Framework
 NetIQ Advanced Authentication Framework Security Officer Guide Version 5.2.0 1 Table of Contents 1 Table of Contents 2 Introduction 3 About This Document 3 Authenticators Management 4 Card 8 Email OTP
NetIQ Advanced Authentication Framework Security Officer Guide Version 5.2.0 1 Table of Contents 1 Table of Contents 2 Introduction 3 About This Document 3 Authenticators Management 4 Card 8 Email OTP
Conducting Virtual Meetings
 Page 1 oovoo Chat & Video Conferencing Information gathered by, International Faculty 2013 Faculty Training General Information What can I do with oovoo? oovoo offers free high quality video chat and instant
Page 1 oovoo Chat & Video Conferencing Information gathered by, International Faculty 2013 Faculty Training General Information What can I do with oovoo? oovoo offers free high quality video chat and instant
Introduction to Google Apps for Business Integration
 Introduction to Google Apps for Business Integration Overview Providing employees with mobile email access can introduce a number of security concerns not addressed by most standard email security infrastructures.
Introduction to Google Apps for Business Integration Overview Providing employees with mobile email access can introduce a number of security concerns not addressed by most standard email security infrastructures.
Getting started as a student with learn.gold
 Getting started as a student with learn.gold Learn.gold is the Virtual Learning Environment (VLE) at Goldsmiths which you'll use in various different ways to support your studies. This printable guide
Getting started as a student with learn.gold Learn.gold is the Virtual Learning Environment (VLE) at Goldsmiths which you'll use in various different ways to support your studies. This printable guide
BlackVue Cloud App Overview...3. Getting Started...6. Basic Menu Screens...15. BlackVue Cloud...24. BlackVue Wi-Fi...40. Internal Memory...
 Table of Contents BlackVue Cloud App Overview...3 Key Functions When Cloud is Connected...4 Key Functions When Wi-Fi Connection is Made...4 Key Features of Internal Memory...4 Supported Devices...5 Getting
Table of Contents BlackVue Cloud App Overview...3 Key Functions When Cloud is Connected...4 Key Functions When Wi-Fi Connection is Made...4 Key Features of Internal Memory...4 Supported Devices...5 Getting
What is Two-Factor Authentication?
 What is Two-Factor Authentication? Two-factor authentication adds a second layer of security to your online accounts. Verifying your identity using a second factor (like your phone or other mobile device)
What is Two-Factor Authentication? Two-factor authentication adds a second layer of security to your online accounts. Verifying your identity using a second factor (like your phone or other mobile device)
Qsync Install Qsync utility Login the NAS The address is 192.168.1.210:8080 bfsteelinc.info:8080
 Qsync Qsync is a cloud based file synchronization service empowered by QNAP Turbo NAS. Simply add files to your local Qsync folder, and they will be available on your Turbo NAS and all its connected devices.
Qsync Qsync is a cloud based file synchronization service empowered by QNAP Turbo NAS. Simply add files to your local Qsync folder, and they will be available on your Turbo NAS and all its connected devices.
USC Marshall School of Business ShareFile_With_Outlook_Client_v2.docx 6/12/13 1 of 9
 About ShareFile When you wish to send someone a file or need a file from someone else, your best option is to use ShareFile. It not only provides increased security by automatically encrypting files but
About ShareFile When you wish to send someone a file or need a file from someone else, your best option is to use ShareFile. It not only provides increased security by automatically encrypting files but
Archived Referrals. Accessing Referrals in the Archive Viewer
 NHS e-referral Service Archived Referrals In order to maintain system performance in the NHS e-referral Service, any referral which has had no actions being carried out for more than 18 months will be
NHS e-referral Service Archived Referrals In order to maintain system performance in the NHS e-referral Service, any referral which has had no actions being carried out for more than 18 months will be
supervisorapp A GUIDE TO USING THE SUPERVISOR APP For version 3.0.0
 supervisorapp A GUIDE TO USING THE SUPERVISOR APP For version 3.0.0 New to Supervisor app? Learn the basics. For version 3.0.0 What is the Supervisor App? The Supervisor App lets you submit job seeker
supervisorapp A GUIDE TO USING THE SUPERVISOR APP For version 3.0.0 New to Supervisor app? Learn the basics. For version 3.0.0 What is the Supervisor App? The Supervisor App lets you submit job seeker
RGD Portal User Guide - Online Business Re-registration (New TIN Exists)
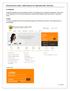 1. Introduction The RGD Portal offers all users the ability to perform an online Business / Company Re-registration. The process for Re-registration if a new TIN has already been issued by GRA through
1. Introduction The RGD Portal offers all users the ability to perform an online Business / Company Re-registration. The process for Re-registration if a new TIN has already been issued by GRA through
AUT OneDrive for Business. Instructions for Using OneDrive on Windows Platform
 AUT OneDrive for Business Instructions for Using OneDrive on Windows Platform Contents 1 What s OneDrive for Business?... 3 2 Storing Files... 5 1.1 Saving and Opening files from your Office applications...
AUT OneDrive for Business Instructions for Using OneDrive on Windows Platform Contents 1 What s OneDrive for Business?... 3 2 Storing Files... 5 1.1 Saving and Opening files from your Office applications...
About Connect by Hong Leong Bank
 About Connect by Hong Leong Bank Q1. What is Connect? A1. Connect brings you a host of digital banking services offered by Hong Leong Bank Vietnam (HLBVN) to its customers. At present, Connect offers Online
About Connect by Hong Leong Bank Q1. What is Connect? A1. Connect brings you a host of digital banking services offered by Hong Leong Bank Vietnam (HLBVN) to its customers. At present, Connect offers Online
Two Factor Authentication (TFA; 2FA) is a security process in which two methods of authentication are used to verify who you are.
 Two Factor Authentication Two Factor Authentication (TFA; 2FA) is a security process in which two methods of authentication are used to verify who you are. For example, one method currently utilized within
Two Factor Authentication Two Factor Authentication (TFA; 2FA) is a security process in which two methods of authentication are used to verify who you are. For example, one method currently utilized within
Connecting your Aiki phone to a network
 Connecting your Aiki phone to a network Connect to mobile networks Depending on your carrier and service plan, your phone may connect automatically to your carrier s fastest available data network. Or
Connecting your Aiki phone to a network Connect to mobile networks Depending on your carrier and service plan, your phone may connect automatically to your carrier s fastest available data network. Or
Two-Factor Authentication (2FA) Registration Instructions Symantec VIP Access
 Two-Factor Authentication (2FA) Registration Instructions Symantec VIP Access To strengthen KBR information security and safeguard company data, Information Technology will implement two-factor authentication
Two-Factor Authentication (2FA) Registration Instructions Symantec VIP Access To strengthen KBR information security and safeguard company data, Information Technology will implement two-factor authentication
Concur Travel and Expense Reporting. Mobile Application
 Questions General Information and Requirements... 3 1. How is Concur's mobile app useful?... 3 2. Does the mobile app offer the same functionality as Concur's full-featured, web-based service?... 3 3.
Questions General Information and Requirements... 3 1. How is Concur's mobile app useful?... 3 2. Does the mobile app offer the same functionality as Concur's full-featured, web-based service?... 3 3.
Configuration Guide Contigo Mobile Tracker
 Track Fleet Personnel / Vehicles with a Mobile Device Users with access to the GPS Fleet Tracker mobile app on iphone and Android can now enable a tracking session on their smartphone, turning their phone
Track Fleet Personnel / Vehicles with a Mobile Device Users with access to the GPS Fleet Tracker mobile app on iphone and Android can now enable a tracking session on their smartphone, turning their phone
TWAIN/WIA Driver. Operation Guide
 TWAIN/WIA Driver Operation Guide Introduction This Operaiton Guide explains the procedures for scanning image data by using the TWAIN Driver or WIA Driver. Image Data Scanning with TWAIN / WIA Download
TWAIN/WIA Driver Operation Guide Introduction This Operaiton Guide explains the procedures for scanning image data by using the TWAIN Driver or WIA Driver. Image Data Scanning with TWAIN / WIA Download
Amcrest 960H DVR Quick Start Guide
 Amcrest 960H DVR Quick Start Guide Welcome Thank you for purchasing our Amcrest 960H DVR! This quick start guide will help you become familiar with our DVR in a very short time. Before installation and
Amcrest 960H DVR Quick Start Guide Welcome Thank you for purchasing our Amcrest 960H DVR! This quick start guide will help you become familiar with our DVR in a very short time. Before installation and
H.264 Quick Start Guide
 Version 1.0 the world in my eyes R H.264 Quick Start Guide Contents Hardware Connection 2 ios View 2 Android View 5 PC View 8 Last, but not least 11 NOTE: Certain functions, appearance or structure mentioned
Version 1.0 the world in my eyes R H.264 Quick Start Guide Contents Hardware Connection 2 ios View 2 Android View 5 PC View 8 Last, but not least 11 NOTE: Certain functions, appearance or structure mentioned
Appearance and Buttons
 User Manual Thank you for buying the GoXtreme WiFi action camera. Before start using this product, please read this manual carefully to maximize its performance and extend the life of the product. Appearance
User Manual Thank you for buying the GoXtreme WiFi action camera. Before start using this product, please read this manual carefully to maximize its performance and extend the life of the product. Appearance
FREQUENTLY ASKED QUESTIONS
 Tip for use of FAQ: Click on questions to go to answer. GETTING STARTED... 2 Which hearing devices do I need to use the app?... 2 Why do I need the ReSound Unite Phone Clip+ to use the app?... 2 I have
Tip for use of FAQ: Click on questions to go to answer. GETTING STARTED... 2 Which hearing devices do I need to use the app?... 2 Why do I need the ReSound Unite Phone Clip+ to use the app?... 2 I have
PRU choice Travel Apps User Manual Step 1: Quick Quotation
 PRUchoice Travel Apps User Manual Prudential is pleased to present a tailor-made application for Smartphone users. With this application, Prudential offers a simple way to apply travel insurance anytime
PRUchoice Travel Apps User Manual Prudential is pleased to present a tailor-made application for Smartphone users. With this application, Prudential offers a simple way to apply travel insurance anytime
USEFUL HINTS & TIPS ALCATEL ONE TOUCH 993. better BUSINESS
 USEFUL HINTS & TIPS ALCATEL ONE TOUCH 993 We really value your feedback on this useful hints & tips guide. If you feel anything is missing, or anything could be made clearer, please send your feedback
USEFUL HINTS & TIPS ALCATEL ONE TOUCH 993 We really value your feedback on this useful hints & tips guide. If you feel anything is missing, or anything could be made clearer, please send your feedback
Troubleshooting / FAQ
 Troubleshooting / FAQ Routers / Firewalls I can't connect to my server from outside of my internal network. The server's IP is 10.0.1.23, but I can't use that IP from a friend's computer. How do I get
Troubleshooting / FAQ Routers / Firewalls I can't connect to my server from outside of my internal network. The server's IP is 10.0.1.23, but I can't use that IP from a friend's computer. How do I get
CCS sales order document flow Android 3.0 version. Content and purpose of the application
 CCS sales order document flow Android 3.0 version Content and purpose of the application From mobile device a full document workflow of sales orders can be requested. Based on a sales order number all
CCS sales order document flow Android 3.0 version Content and purpose of the application From mobile device a full document workflow of sales orders can be requested. Based on a sales order number all
Salesforce Classic Guide for iphone
 Salesforce Classic Guide for iphone Version 37.0, Summer 16 @salesforcedocs Last updated: July 12, 2016 Copyright 2000 2016 salesforce.com, inc. All rights reserved. Salesforce is a registered trademark
Salesforce Classic Guide for iphone Version 37.0, Summer 16 @salesforcedocs Last updated: July 12, 2016 Copyright 2000 2016 salesforce.com, inc. All rights reserved. Salesforce is a registered trademark
How to Remotely Access the C&CDHB Network from a Personal Device
 How to Remotely Access the C&CDHB Network from a Personal Device 13/09/2012 Contents Installing the Citrix Receiver for Windows PCs... 2 Installing the Citrix Receiver for Mac OS X... 6 Installing the
How to Remotely Access the C&CDHB Network from a Personal Device 13/09/2012 Contents Installing the Citrix Receiver for Windows PCs... 2 Installing the Citrix Receiver for Mac OS X... 6 Installing the
Downloading the GAIG Annuity App. Log In Screen. Home Page
 Downloading the GAIG Annuity App ios users: https://itunes.apple.com/us/app/gaig-annuity/id925743711?ls=1&mt=8 Android users: https://play.google.com/store/apps/details?id=com.gaig.annuity.app.mobile.android.agent
Downloading the GAIG Annuity App ios users: https://itunes.apple.com/us/app/gaig-annuity/id925743711?ls=1&mt=8 Android users: https://play.google.com/store/apps/details?id=com.gaig.annuity.app.mobile.android.agent
USB Recorder. User s Guide. Sold by: Toll Free: (877) 389-0000
 USB Recorder User s Guide Sold by: http://www.twacomm.com Toll Free: (877) 389-0000 Table of Contents 1. Getting Started 1-1...First Login 1-2...Creating a New User 2. Administration 2-1...General Administration
USB Recorder User s Guide Sold by: http://www.twacomm.com Toll Free: (877) 389-0000 Table of Contents 1. Getting Started 1-1...First Login 1-2...Creating a New User 2. Administration 2-1...General Administration
XMEye Android Mobile Monitoring Client English Manual
 XMEye Android Mobile Monitoring Client English Manual Written by: The test department Prepared Date: 2014-03-25 Version: V1.0 目 录 1. Introduction... 3 1.1. Brief Introduction... 3 1.2. Main Functions...
XMEye Android Mobile Monitoring Client English Manual Written by: The test department Prepared Date: 2014-03-25 Version: V1.0 目 录 1. Introduction... 3 1.1. Brief Introduction... 3 1.2. Main Functions...
Internet Self Service FAQs
 Internet Self Service FAQs General Questions... 2 What is Mobile Banking? 2 Is Mobile Banking secure? 2 Is my personal or financial information stored on my phone? 3 Are there fees to use Mobile Banking?
Internet Self Service FAQs General Questions... 2 What is Mobile Banking? 2 Is Mobile Banking secure? 2 Is my personal or financial information stored on my phone? 3 Are there fees to use Mobile Banking?
Dynamics CRM 2011 Outlook Configuration Guide With Windows XP
 Dynamics CRM 2011 Outlook Configuration Guide With Windows XP With migrating to a new version of CRM, one of the side-affects is that the Outlook Integration Client has also been updated and needs to be
Dynamics CRM 2011 Outlook Configuration Guide With Windows XP With migrating to a new version of CRM, one of the side-affects is that the Outlook Integration Client has also been updated and needs to be
Employee Tracking System
 Software Specification Employee Tracking System By Bonrix Software Systems 1 Table of Contents No. TITLE PAGE NO. 1. Introduction 3 2. Purpose 3 3. Employee Tracking System Details 4 4. Login panel 4 5.
Software Specification Employee Tracking System By Bonrix Software Systems 1 Table of Contents No. TITLE PAGE NO. 1. Introduction 3 2. Purpose 3 3. Employee Tracking System Details 4 4. Login panel 4 5.
How can I protect against the loss of my ID if my device is lost or stolen?
 How can I protect against the loss of my if my device is lost or stolen? If your mobile device is stolen or lost, you can reactivate your user on a new device and deactivate it on your stolen or lost device.
How can I protect against the loss of my if my device is lost or stolen? If your mobile device is stolen or lost, you can reactivate your user on a new device and deactivate it on your stolen or lost device.
Airnet-Student is a new and improved wireless network that is being made available to all Staffordshire University students.
 Airnet-Student Airnet-Student is a new and improved wireless network that is being made available to all Staffordshire University students. Airnet-Student has two key advantages over the current Airnet
Airnet-Student Airnet-Student is a new and improved wireless network that is being made available to all Staffordshire University students. Airnet-Student has two key advantages over the current Airnet
Setting up Office 365 for Multi-Factor Authentication
 Setting up Office 365 for Multi-Factor Authentication Office 365 now supports multiple factors of authentications when logging into any of theservices provided by Office 365. Organizations may want to
Setting up Office 365 for Multi-Factor Authentication Office 365 now supports multiple factors of authentications when logging into any of theservices provided by Office 365. Organizations may want to
White Paper. The Principles of Tokenless Two-Factor Authentication
 White Paper The Principles of Tokenless Two-Factor Authentication Table of contents Instroduction... 2 What is two-factor authentification?... 2 Access by hardware token... 3 Advantages and disadvantages
White Paper The Principles of Tokenless Two-Factor Authentication Table of contents Instroduction... 2 What is two-factor authentification?... 2 Access by hardware token... 3 Advantages and disadvantages
