ESET Mail Security 4 April 2010
|
|
|
- Barbra Hutchinson
- 7 years ago
- Views:
Transcription
1 ESET Mail Security 4 April 2010 Performance Test & Review Language: English April 2010 Last Revision: 6 th August 2010 Commissioned by ESET
2 Tested Product ESET Mail Security 4 Installed on MS Exchange 2003 and MS Exchange
3 Tested Product We tested the ESET Mail Security 4 product from ESET ( with last signature update in mid of April. All tests were done with up-to-date products; the tested products were not frozen. Performance/Stress Test The test was splitted in two categories. 1. Mail-Sending-Test 2. Exchange Server Stress and Performance Test (MS-Toolkit) Hardware Configuration We used for the tests (Exchange 2003 / Exchange 2010) 40 identical workstations and one Server. To simulate a real office environment, we did not use newest hardware in this test. Workstations HP 7600 SFF Intel Pentium IV 2.8 GHz 1 GB Ram 40 GB SATA HDD DVD-RW Server HP ProLiant DL360G4, 2x Xeon HT 3.40 GHz 8GB, 1x36GB 10k Hotplug, DVD/CD-RW SmartArray 6i, 1x PS, 1U Rack 3 -
4 Mail-Sending-Test In this test, we send and receive the mails simultaneously with 40 clients, connected via a 1GB LAN connection in order to avoid latency from the internet. This test was done using real hardware. We sent mixed mails (60% Spam, 30% Ham, 10% Malware) from 40 workstations; about 1500 mails per workstation. The result of the impact of an Security product depends mainly on the used hardware. You also have to keep in mind, that it will very rarely happen that a server (except ISP s) have to handle such a massive amount of s. In the real world, it will not happen that a SMB will receive mails during a period less than two hours through an internet connection. Usually the bottleneck is not the Exchange server with an installed security product, the bottleneck is the slow internet connection. The mails were sent within the same domain and organization. Results MS Server 2003 with Exchange Server 2003 There was no problem to process ~60000 mixed mails in a period of less than two hours. With installed ESET Mail Security 4, there was a delay of about 21%. The CPU workload toddles between 1% and 5%, with or without ESET Mail Security. The RAM usage with ESET Mail Security was about 2,8 GB (2003) and without 1,24 GB. Results MS Server 2008 R2 with Exchange Server 2010 There was no problem to process ~60000 mixed mails in a period of less than two hours. With installed ESET Mail Security 4, there was a delay of about 22%. The CPU workload toddles between 1% and 5%, with or without ESET Mail Security. The RAM usage with ESET Mail Security was about 2,8 GB and without 2GB. Exchange 2003 vs. Exchange 2010 The Exchange Server 2010 was about 19% faster than the Exchange Server 2003, both with installed ESET Mail Security
5 Table of Performance Overview 2003 with installed ESET Mail Security without installed ESET Mail Security 103 minutes + 21 % 83 minutes 2008 R2 with installed ESET Mail Security without installed ESET Mail Security 85 minutes + 22 % 67 minutes 2003 with ESET % 2008 R2 with ESET 85 Please keep in mind that the loss of time depends on the configuration of the hardware and the mails, which were used. It is not only the count of mails: It depends on the size and the type of mails (spam, malware, clean). There was no system crash and no temporarily freeze during the whole test. The solution ran absolutely stable. 5 -
6 Exchange Server Stress and Performance Test Methodology We used the automated Test Procedure provided by Microsoft that simulates a huge count of several Most common Tasks and analyzed how many tasks were able to complete in a defined period of time. This test is not done with real clients, it is only a simulation. Tasks Overview: Task Name BrowseCalendarTask BrowseContactsTask CreateContactTask CreateTaskTask LogoffTask MakeAppointmentTask ModuleInitTask PostFreeBusyTask ReadAndProcessMessagesTask RequestMeetingTask SendMailTask Browsing Calendar Tasks Browsing Contact Tasks Creating Contacts Creating Tasks Log-off and Log-on Tasks Creating Appointments Module initialization Creating and posting Free/Busy Reading and processing Message Tasks Meeting Requests Send Mail With this bunch of thousands of tasks, we were able to simulate an extremely Hardware and Software resource intensive situation. 6 -
7 Windows Server 2003 & Exchange 2003 With ESET Mail Security EXC SRV: Exchange 2003 Clients: Outlook 2003 & 2007 (online) Users: 40 Concurrent Connections: 5000 Name Succeeded Client Type Action Profile TestClients x 40 Succeeded Outlook 2003 Online Active Users Statistics Active User Count Duration 40 00:10:00 Task Execution Statistics Task Name Count BrowseCalendarTask 108 BrowseContactsTask 114 CreateContactTask 9 CreateTaskTask 6 LogoffTask 17 MakeAppointmentTask 23 ModuleInitTask 1 PostFreeBusyTask 33 ReadAndProcessMessagesTask 174 RequestMeetingTask 5 SendMailTask 39 User Count Tasks per User Day Tasks Completed Average
8 Without ESET Mail Security EXC SRV: Exchange 2003 Clients: Outlook 2003 & 2007 (online) Users: 40 Concurrent Connections: 5000 Name Succeeded Client Type TestClients x 40 Succeeded Outlook 2003 Online Active Users Statistics Action Profile User Count Tasks per User Day Tasks Completed Average Active User Count Duration 40 00:10:00 Task Execution Statistics Task Name Count BrowseCalendarTask 119 BrowseContactsTask 125 CreateContactTask 7 CreateTaskTask 9 LogoffTask 24 MakeAppointmentTask 34 ModuleInitTask 1 PostFreeBusyTask 29 ReadAndProcessMessagesTask 245 RequestMeetingTask 8 SendMailTask 94 Conclusion: The impact of ESET Mail Security was about 30%. 8 -
9 Windows Server 2008 R2 & Exchange 2010 With ESET Mail Security EXC SRV: Exchange 2010 Clients: Outlook 2003 & 2007 (online) Users: 40 Concurrent Connections: 5000 Name Succeeded Client Type Action Profile TestClients x 40 Succeeded Active Users Statistics Active User Count Outlook 2003 Online Duration 40 00:10:00 Task Execution Statistics Task Name Count BrowseCalendarTask 155 BrowseContactsTask 138 CreateContactTask 15 CreateTaskTask 13 LogoffTask 39 MakeAppointmentTask 38 ModuleInitTask 1 PostFreeBusyTask 51 ReadAndProcessMessagesTask 267 RequestMeetingTask 5 SendMailTask 46 User Count Tasks per User Day Average Tasks Completed 9 -
10 Without ESET Mail Security EXC SRV: Exchange 2010 Clients: Outlook 2003 & 2007 (online) Users: 40 Concurrent Connections: 5000 Name Succeeded Client Type Action Profile TestClients x 40 Active Users Statistics Active User Count Succeeded Outlook 2003 Online Duration 40 00:10:00 Task Execution Statistics Task Name Count BrowseCalendarTask 162 BrowseContactsTask 130 CreateContactTask 12 CreateTaskTask 16 LogoffTask 43 MakeAppointmentTask 28 ModuleInitTask 1 PostFreeBusyTask 49 ReadAndProcessMessagesTask 525 RequestMeetingTask 17 SendMailTask 108 User Count Tasks per User Day Tasks Completed Average Conclusion: The impact of ESET Mail Security was about 30% in the MS Test. 10 -
11 ESET Mail Security Simple Review Installation: First, we are greeted by the Welcome page of the installation wizard: The next step is to enter the licence details, which are sent to the user by after purchasing the program. The next part of installation is the registration of the licence. After the obligatory acceptance of the End User Licence Agreement, the user can choose the installation method. We chose to use Typical, i.e. standard settings. The next stage is not very different from the installation of other ESET products. The ThreatSense.Net Early Warning System allows ESET to react quickly to new, unknown threats. When a new threat is detected, information about it is sent to ESET. 11 -
12 This function offers a high level of protection against unknown threats. However, for organisations with a high security environment in which unmonitored external communication is restricted, the feature can be disabled. The option for doing this is shown below: The potentially unwanted applications detection is also part of the Mail Security program. This option can be configured with a simple drop down menu: After this setting has been selected, the installer has enough information to complete the setup process. One last click confirms the settings and starts the installation: 12 -
13 When installation has successfully completed, ESET Mail Security starts up. The Control Center can be started from the icon in the system tray: A first glance gives the user an overview of the state of the system. You can see whether all three aspects of system security are working properly. One look at the Control Center shows that the interface is seamlessly integrated with that of other ESET products. Anyone familiar with ESET will immediately find their way around and be able to make changes easily. The interface of ESET Mail Security can be described as optimal, and the clarity of the layout makes it easy to find what you need. Under Protection Status => Watch Activity you can see a graphic representation of File Activity and Mail Server Protection Performance. Under Protection Status => Statistics you can see the history of infections and clean objects. 13 -
14 The Setup page is divided into two categories. The first is Antivirus and antispyware, and the second is Antispam protection. The sub components of each category are listed, and the enabled/disabled status is shown. These components can be configured by clicking on the blue category titles, or the additional links at the bottom of the page. Computer Scan allows the user to check for malicious code on the system. This interface is identical to that of other ESET security products. The configurable components of the Antivirus and antispyware protection category are as follows: Real time protection client protection The Update page is also familiar, and informs the user of the current update status, and versions of the program and signatures. Mail server protection Web access protection The last item on this configuration page allows temporary deactivation of the malware detection with a single click. 14 -
15 The configuration of the Antispam protection does not differ significantly from that of Antivirus protection. client protection can be configured here, and whitelists and blacklists can be defined. There are also more detailed options for configuring Mail server protection. The Help and support page follows ESET s familiar exemplary style. It provides centralised access to the following: ESET Suite Help Files Extensive FAQ Knowledge base search Version numbers for all components of the suite The opportunity to submit Customer Care enquiries The Tools page offers the following familiar functions: Log files: This provides easy access to all log files. Quarantine: Any suspicious objects which have been quarantined are shown here. Scheduler: Allows specific tasks to be run at a pre defined time. SysInspector: This provides both a summarised and a detailed Sys Inspect Log. 15 -
16 Conclusion ESET Mail Security provides optimal protection for mail servers, and combines all necessary features including Anti Virus protection of the server. The installation and configuration follow ESET s familiar simple pattern. The Control Center is well designed, and the clear structure enables users to find their way around quickly and easily, even if they are not already familiar with ESET products. There is thus no absolute need for server administrators to look in a manual. The malware detection and performance reach ESET s normal high standard, and the suite can be wholeheartedly recommended. Our only minor gripe is that there is effectively no spam logging function for the Mail Server Protection, which makes a detailed analysis of mail attacks impossible. There is just a log of detected malware in the mails. However, we hope that there may be future improvements to this. Highlights One of the important things is the very low false positive rate, which is under 0,5 % at personal mails. Even if there is system impact of round about 20%, this can be taken out of account, because it is very unusual to receive mails in a single blow. There was no system crash and also no temporarily freeze in the whole test. The solution runs absolutely stable. 16 -
17 Copyright and Disclaimer This publication is Copyright 2010 by AV-Comparatives e.v.. Any use of the results, etc. in whole or in part, is ONLY permitted after the explicit written agreement of the management board of AV- Comparatives e.v., prior to any publication. AV-Comparatives e.v. and its testers cannot be held liable for any damage or loss, which might occur as result of, or in connection with, the use of the information provided in this paper. We take every possible care to ensure the correctness of the basic data, but a liability for the correctness of the test results cannot be taken by any representative of AV-Comparatives e.v. We do not give any guarantee of the correctness, completeness, or suitability for a specific purpose of any of the information/content provided at any given time. No one else involved in creating, producing or delivering test results shall be liable for any indirect, special or consequential damage, or loss of profits, arising out of, or related to, the use or inability to use, the services provided by the website, test documents or any related data. AV-Comparatives e.v. is a registered Austrian Non-Profit-Organization. For more information about AV-Comparatives and the testing methodologies, please visit our website. AV-Comparatives e.v. (April 2010) 17 -
ESET NOD32 Antivirus 4 for Linux Desktop. Quick Start Guide
 ESET NOD32 Antivirus 4 for Linux Desktop Quick Start Guide ESET NOD32 Antivirus 4 provides state-of-the-art protection for your computer against malicious code. Based on the ThreatSense scanning engine
ESET NOD32 Antivirus 4 for Linux Desktop Quick Start Guide ESET NOD32 Antivirus 4 provides state-of-the-art protection for your computer against malicious code. Based on the ThreatSense scanning engine
Anti-Virus Comparative
 Anti-Virus Comparative On-demand Detection of Malicious Software includes false alarm and on-demand scanning speed test Language: English August 2010 Last Revision: 5 th October 2010 Table of Contents
Anti-Virus Comparative On-demand Detection of Malicious Software includes false alarm and on-demand scanning speed test Language: English August 2010 Last Revision: 5 th October 2010 Table of Contents
Single Product Review - Bitdefender Security for Virtualized Environments - November 2012
 Single Product Review Bitdefender Security for Virtualized Environments Language: English November 2012 Last Revision: 1 st December 2012 Review commissioned by Bitdefender - 1 - Bitdefender Security for
Single Product Review Bitdefender Security for Virtualized Environments Language: English November 2012 Last Revision: 1 st December 2012 Review commissioned by Bitdefender - 1 - Bitdefender Security for
ESET SMART SECURITY 6
 ESET SMART SECURITY 6 Microsoft Windows 8 / 7 / Vista / XP / Home Server Quick Start Guide Click here to download the most recent version of this document ESET Smart Security provides state-of-the-art
ESET SMART SECURITY 6 Microsoft Windows 8 / 7 / Vista / XP / Home Server Quick Start Guide Click here to download the most recent version of this document ESET Smart Security provides state-of-the-art
ESET NOD32 ANTIVIRUS 9
 ESET NOD32 ANTIVIRUS 9 Microsoft Windows 10 / 8.1 / 8 / 7 / Vista / XP Quick Start Guide Click here to download the most recent version of this document ESET NOD32 Antivirus provides state-of-the-art protection
ESET NOD32 ANTIVIRUS 9 Microsoft Windows 10 / 8.1 / 8 / 7 / Vista / XP Quick Start Guide Click here to download the most recent version of this document ESET NOD32 Antivirus provides state-of-the-art protection
ESET SMART SECURITY 9
 ESET SMART SECURITY 9 Microsoft Windows 10 / 8.1 / 8 / 7 / Vista / XP Quick Start Guide Click here to download the most recent version of this document ESET Smart Security is all-in-one Internet security
ESET SMART SECURITY 9 Microsoft Windows 10 / 8.1 / 8 / 7 / Vista / XP Quick Start Guide Click here to download the most recent version of this document ESET Smart Security is all-in-one Internet security
ESET NOD32 ANTIVIRUS 8
 ESET NOD32 ANTIVIRUS 8 Microsoft Windows 8.1 / 8 / 7 / Vista / XP / Home Server 2003 / Home Server 2011 Quick Start Guide Click here to download the most recent version of this document ESET NOD32 Antivirus
ESET NOD32 ANTIVIRUS 8 Microsoft Windows 8.1 / 8 / 7 / Vista / XP / Home Server 2003 / Home Server 2011 Quick Start Guide Click here to download the most recent version of this document ESET NOD32 Antivirus
Anti-Virus Comparative - Proactive/retrospective test May 2009
 Anti-Virus Comparative Proactive/retrospective test (on-demand detection of virus/malware) Language: English May 2009 Last revision: 27 th May 2009 1 - Content 1. Introduction 3 2. Description 3 3. Test
Anti-Virus Comparative Proactive/retrospective test (on-demand detection of virus/malware) Language: English May 2009 Last revision: 27 th May 2009 1 - Content 1. Introduction 3 2. Description 3 3. Test
Anti-Virus Comparative
 Anti-Virus Comparative Performance Test Impact of Anti-Virus Software on System Performance Microsoft Forefront Endpoint Protection (Release Candidate) Language: English November 2010 Last Revision: 13
Anti-Virus Comparative Performance Test Impact of Anti-Virus Software on System Performance Microsoft Forefront Endpoint Protection (Release Candidate) Language: English November 2010 Last Revision: 13
BitDefender Security for Exchange
 Quick Start Guide Copyright 2011 BitDefender 1. About This Guide This guide will help you install and get started with BitDefender Security for Exchange. For detailed instructions, please refer to the
Quick Start Guide Copyright 2011 BitDefender 1. About This Guide This guide will help you install and get started with BitDefender Security for Exchange. For detailed instructions, please refer to the
Quick Heal Exchange Protection 4.0
 Quick Heal Exchange Protection 4.0 Customizable Spam Filter. Uninterrupted Antivirus Security. Product Highlights Built-in defense keeps your business communications and sensitive information secure from
Quick Heal Exchange Protection 4.0 Customizable Spam Filter. Uninterrupted Antivirus Security. Product Highlights Built-in defense keeps your business communications and sensitive information secure from
IT Security Products for Corporate Users
 IT Security Products for Corporate Users Review of IT Security Suites for Corporate Users, 2010 Language: English October 2010 Last revision date: 11 th November 2010-1 - Contents The Dangers of Malware...
IT Security Products for Corporate Users Review of IT Security Suites for Corporate Users, 2010 Language: English October 2010 Last revision date: 11 th November 2010-1 - Contents The Dangers of Malware...
FOR MAC. Quick Start Guide. Click here to download the most recent version of this document
 FOR MAC Quick Start Guide Click here to download the most recent version of this document ESET Cyber Security Pro provides state-of-the-art protection for your computer against malicious code. Based on
FOR MAC Quick Start Guide Click here to download the most recent version of this document ESET Cyber Security Pro provides state-of-the-art protection for your computer against malicious code. Based on
Anti-Virus Comparative
 Anti-Virus Comparative File Detection Test of Malicious Software includes false alarm test Language: English September 2013 Last Revision: 10 th October 2013 Table of Contents Tested Products 3 Introduction
Anti-Virus Comparative File Detection Test of Malicious Software includes false alarm test Language: English September 2013 Last Revision: 10 th October 2013 Table of Contents Tested Products 3 Introduction
Corporate Product Review: G DATA
 Corporate Product Review: G DATA Excerpt from Review of IT Security Suites for Corporate Users, 2009 Language: English May 2009 Last revision date: 2009-05-27 G DATA Test Software: AVB10 ClientSecurity10
Corporate Product Review: G DATA Excerpt from Review of IT Security Suites for Corporate Users, 2009 Language: English May 2009 Last revision date: 2009-05-27 G DATA Test Software: AVB10 ClientSecurity10
Web. Anti- Spam. Disk. Mail DNS. Server. Backup
 Email Server Appliance N ew generation of Server Appliance, AirLive, is designed for the SMB or enterprise that needs to install an easy maintained and fully functional mail server. It not only preserves
Email Server Appliance N ew generation of Server Appliance, AirLive, is designed for the SMB or enterprise that needs to install an easy maintained and fully functional mail server. It not only preserves
Anti Phishing Test July 2013
 Anti-Phishing Test July 2013 Language: English July 2013 Last revision: 10 th August 2013 www.av-comparatives.org 1 Introduction What is Phishing? Taken from Wikipedia 1 : Phishing is a way of attempting
Anti-Phishing Test July 2013 Language: English July 2013 Last revision: 10 th August 2013 www.av-comparatives.org 1 Introduction What is Phishing? Taken from Wikipedia 1 : Phishing is a way of attempting
AVG AntiVirus Free Edition
 AVG AntiVirus Free Edition User Manual Document revision AVG.06 (16.10.2015 ) C opyright AVG Technologies C Z, s.r.o. All rights reserved. All other trademarks are the property of their respective owners.
AVG AntiVirus Free Edition User Manual Document revision AVG.06 (16.10.2015 ) C opyright AVG Technologies C Z, s.r.o. All rights reserved. All other trademarks are the property of their respective owners.
ESET Mail Security 4. User Guide. for Microsoft Exchange Server. Microsoft Windows 2000 / 2003 / 2008
 ESET Mail Security 4 for Microsoft Exchange Server User Guide Microsoft Windows 2000 / 2003 / 2008 Content 1. Introduction...4 1.1 System requirements... 4 1.2 Methods Used... 4 1.2.1 Mailbox scanning
ESET Mail Security 4 for Microsoft Exchange Server User Guide Microsoft Windows 2000 / 2003 / 2008 Content 1. Introduction...4 1.1 System requirements... 4 1.2 Methods Used... 4 1.2.1 Mailbox scanning
AV-Comparatives. F-Secure Freedome. Language: English. November 2014 Last revision: 20. November 2014. www.av-comparatives.org -1-
 AV-Comparatives F-Secure Freedome Language: English November 2014 Last revision: 20. November 2014-1- Introduction As mobile phone network coverage is not universal, and data tariffs tend to be expensive,
AV-Comparatives F-Secure Freedome Language: English November 2014 Last revision: 20. November 2014-1- Introduction As mobile phone network coverage is not universal, and data tariffs tend to be expensive,
TrustPort USB Antivirus
 TrustPort USB Antivirus User Guide Revision date: 10/1/2014 Copyright 2014, TrustPort, a.s., All rights reserved. About In cases where for example we use portable applications on USB keys, we do not have
TrustPort USB Antivirus User Guide Revision date: 10/1/2014 Copyright 2014, TrustPort, a.s., All rights reserved. About In cases where for example we use portable applications on USB keys, we do not have
AVG File Server. User Manual. Document revision 2015.08 (23.3.2015)
 AVG File Server User Manual Document revision 2015.08 (23.3.2015) C opyright AVG Technologies C Z, s.r.o. All rights reserved. All other trademarks are the property of their respective owners. Contents
AVG File Server User Manual Document revision 2015.08 (23.3.2015) C opyright AVG Technologies C Z, s.r.o. All rights reserved. All other trademarks are the property of their respective owners. Contents
ESET CYBER SECURITY PRO for Mac Quick Start Guide. Click here to download the most recent version of this document
 ESET CYBER SECURITY PRO for Mac Quick Start Guide Click here to download the most recent version of this document ESET Cyber Security Pro provides state-of-the-art protection for your computer against
ESET CYBER SECURITY PRO for Mac Quick Start Guide Click here to download the most recent version of this document ESET Cyber Security Pro provides state-of-the-art protection for your computer against
AVG File Server 2012. User Manual. Document revision 2012.03 (8/19/2011)
 AVG File Server 2012 User Manual Document revision 2012.03 (8/19/2011) Copyright AVG Technologies CZ, s.r.o. All rights reserved. All other trademarks are the property of their respective owners. This
AVG File Server 2012 User Manual Document revision 2012.03 (8/19/2011) Copyright AVG Technologies CZ, s.r.o. All rights reserved. All other trademarks are the property of their respective owners. This
Lab - Dual Boot - Vista & Windows XP
 Lab - Dual Boot - Vista & Windows XP Brought to you by RMRoberts.com After completing this lab activity, you will be able to: Install and configure a dual boot Windows XP and Vista operating systems. Explain
Lab - Dual Boot - Vista & Windows XP Brought to you by RMRoberts.com After completing this lab activity, you will be able to: Install and configure a dual boot Windows XP and Vista operating systems. Explain
Stellar Phoenix Exchange Server Backup
 Stellar Phoenix Exchange Server Backup Version 1.0 Installation Guide Introduction This is the first release of Stellar Phoenix Exchange Server Backup tool documentation. The contents will be updated periodically
Stellar Phoenix Exchange Server Backup Version 1.0 Installation Guide Introduction This is the first release of Stellar Phoenix Exchange Server Backup tool documentation. The contents will be updated periodically
Get Started Guide - PC Tools Internet Security
 Get Started Guide - PC Tools Internet Security Table of Contents PC Tools Internet Security... 1 Getting Started with PC Tools Internet Security... 1 Installing... 1 Getting Started... 2 iii PC Tools
Get Started Guide - PC Tools Internet Security Table of Contents PC Tools Internet Security... 1 Getting Started with PC Tools Internet Security... 1 Installing... 1 Getting Started... 2 iii PC Tools
User Guide Version 2.0
 User Guide Version 2.0 1 Overview 'Stellar Mail Backup' is a complete backup solution software for all email accounts configured in 'MS Outlook', 'Outlook Express' and 'Windows Mail' email clients on your
User Guide Version 2.0 1 Overview 'Stellar Mail Backup' is a complete backup solution software for all email accounts configured in 'MS Outlook', 'Outlook Express' and 'Windows Mail' email clients on your
ESET Endpoint Protection Advanced
 ESET Endpoint Protection Advanced Whether your business is just starting or established, there are a few things you expect from software you use daily. At ESET, we feel that running software in the business
ESET Endpoint Protection Advanced Whether your business is just starting or established, there are a few things you expect from software you use daily. At ESET, we feel that running software in the business
Anti-Virus Comparative No.22
 Anti-Virus Comparative No.22 Retrospective/Proactive test Heuristic and behavioural protection against new/unknown malicious software Language: English March 2015 Last revision: 26 th June 2015-1 - Contents
Anti-Virus Comparative No.22 Retrospective/Proactive test Heuristic and behavioural protection against new/unknown malicious software Language: English March 2015 Last revision: 26 th June 2015-1 - Contents
AV-Comparatives. Mobile Security Test. Language: English. February 2015 Last revision: 30 th March 2015. www.av-comparatives.org
 AV-Comparatives Mobile Security Test Language: English February 2015 Last revision: 30 th March 2015-1- Introduction This test covers security products for smartphones and tablets running Google's Android
AV-Comparatives Mobile Security Test Language: English February 2015 Last revision: 30 th March 2015-1- Introduction This test covers security products for smartphones and tablets running Google's Android
K7 Mail Security FOR MICROSOFT EXCHANGE SERVERS. v.109
 K7 Mail Security FOR MICROSOFT EXCHANGE SERVERS v.109 1 The Exchange environment is an important entry point by which a threat or security risk can enter into a network. K7 Mail Security is a complete
K7 Mail Security FOR MICROSOFT EXCHANGE SERVERS v.109 1 The Exchange environment is an important entry point by which a threat or security risk can enter into a network. K7 Mail Security is a complete
System Compatibility. Enhancements. Operating Systems. Hardware Requirements. Email Security
 Email Security SonicWALL Email Security 7.0 for Microsoft Small Business Server System Compatibility SonicWALL Email Security 7.0 Software is supported on systems with the following: Operating Systems
Email Security SonicWALL Email Security 7.0 for Microsoft Small Business Server System Compatibility SonicWALL Email Security 7.0 Software is supported on systems with the following: Operating Systems
Cox Business Premium Security Service FAQs
 FAQ s Content Cox Business Premium Security Service FAQs Questions before installing the software Q: Does Cox Business Premium Security Service work with other antivirus or firewall software installed
FAQ s Content Cox Business Premium Security Service FAQs Questions before installing the software Q: Does Cox Business Premium Security Service work with other antivirus or firewall software installed
Microsoft IT Increases Security and Streamlines Antimalware Management by Using Microsoft Forefront Endpoint. Protection 2010.
 Situation Microsoft IT had limited monitoring and reporting functionality with its existing antimalware system. Although the system could scan for malware, there was no reporting capability or configurable
Situation Microsoft IT had limited monitoring and reporting functionality with its existing antimalware system. Although the system could scan for malware, there was no reporting capability or configurable
ESET MOBILE SECURITY FOR ANDROID
 ESET MOBILE SECURITY FOR ANDROID Installation Manual and User Guide Click here to download the most recent version of this document Contents 1. Installation...3 of ESET Mobile Security 1.1 Installation...3
ESET MOBILE SECURITY FOR ANDROID Installation Manual and User Guide Click here to download the most recent version of this document Contents 1. Installation...3 of ESET Mobile Security 1.1 Installation...3
Global Server Installation Guide
 Global Server Installation Guide AVEVA Solutions Ltd Disclaimer Information of a technical nature, and particulars of the product and its use, is given by AVEVA Solutions Ltd and its subsidiaries without
Global Server Installation Guide AVEVA Solutions Ltd Disclaimer Information of a technical nature, and particulars of the product and its use, is given by AVEVA Solutions Ltd and its subsidiaries without
ESET NOD32 Antivirus 4
 ESET NOD32 Antivirus 4 User Guide (intended for product version 4.2 and higher) Microsoft Windows 7 / Vista / XP / NT4 / 2000 / 2003 / 2008 Content 1. ESET NOD32 Antivirus 4...4 1.1 What s new... 4 1.2
ESET NOD32 Antivirus 4 User Guide (intended for product version 4.2 and higher) Microsoft Windows 7 / Vista / XP / NT4 / 2000 / 2003 / 2008 Content 1. ESET NOD32 Antivirus 4...4 1.1 What s new... 4 1.2
Parental Control Single Product Test
 Parental Control Single Product Test ESET Smart Security 8.0 Parental Control Test August 2015 Language: English August 2015 Last Revision: 14 th September 2015 Content Introduction: parental control software
Parental Control Single Product Test ESET Smart Security 8.0 Parental Control Test August 2015 Language: English August 2015 Last Revision: 14 th September 2015 Content Introduction: parental control software
Anti-Virus Comparative
 Anti-Virus Comparative Malware Removal Test Language: English September 2009 Last Revision: 24 th October 2009 Table of Contents Tested Products 3 Conditions for participation and test methodology 4 Introduction
Anti-Virus Comparative Malware Removal Test Language: English September 2009 Last Revision: 24 th October 2009 Table of Contents Tested Products 3 Conditions for participation and test methodology 4 Introduction
AVG File Server 2013. User Manual. Document revision 2013.03 (11/13/2012)
 AVG File Server 2013 User Manual Document revision 2013.03 (11/13/2012) Copyright AVG Technologies CZ, s.r.o. All rights reserved. All other trademarks are the property of their respective owners. This
AVG File Server 2013 User Manual Document revision 2013.03 (11/13/2012) Copyright AVG Technologies CZ, s.r.o. All rights reserved. All other trademarks are the property of their respective owners. This
Kaspersky Endpoint Security 10 for Windows Administrator's Guide
 Kaspersky Endpoint Security 10 for Windows Administrator's Guide APPLICATION VERSION: 10.0 MAINTENANCE RELEASE 1 Dear User, Thank you for choosing our product! We hope that you will find this documentation
Kaspersky Endpoint Security 10 for Windows Administrator's Guide APPLICATION VERSION: 10.0 MAINTENANCE RELEASE 1 Dear User, Thank you for choosing our product! We hope that you will find this documentation
AVG 8.5 Internet Security
 AVG 8.5 Internet Security User Manual Document revision 85.8 (26.10.2009) Copyright AVG Technologies CZ, s.r.o. All rights reserved. All other trademarks are the property of their respective owners. This
AVG 8.5 Internet Security User Manual Document revision 85.8 (26.10.2009) Copyright AVG Technologies CZ, s.r.o. All rights reserved. All other trademarks are the property of their respective owners. This
Getting Started Guide
 Getting Started Guide www.exclaimer.com Contents About This Guide... 2 Signature Manager Overview... 3 How does it Work?... 3 But That s Not All... 4 And There s More... 4 Licensing... 5 Licensing Information...
Getting Started Guide www.exclaimer.com Contents About This Guide... 2 Signature Manager Overview... 3 How does it Work?... 3 But That s Not All... 4 And There s More... 4 Licensing... 5 Licensing Information...
Anti-Virus Comparative
 Anti-Virus Comparative File Detection Test of Malicious Software including false alarm test Language: English March 2016 Last Revision: 14 th April 2016 Table of Contents Tested Products 3 Introduction
Anti-Virus Comparative File Detection Test of Malicious Software including false alarm test Language: English March 2016 Last Revision: 14 th April 2016 Table of Contents Tested Products 3 Introduction
The PA-4000 Series can add visibility and control into your network for webmail applications to stop incoming threats and limit uploaded data.
 Controlling Webmail Tech Note Overview Webmail interfaces are widespread and available from search providers (Yahoo, Google), software vendors (Microsoft s Hotmail), social networking sites (Myspace, Facebook),
Controlling Webmail Tech Note Overview Webmail interfaces are widespread and available from search providers (Yahoo, Google), software vendors (Microsoft s Hotmail), social networking sites (Myspace, Facebook),
SPAMfighter Mail Gateway
 SPAMfighter Mail Gateway User Manual Copyright (c) 2009 SPAMfighter ApS Revised 2009-05-19 1 Table of contents 1. Introduction...3 2. Basic idea...4 2.1 Detect-and-remove...4 2.2 Power-through-simplicity...4
SPAMfighter Mail Gateway User Manual Copyright (c) 2009 SPAMfighter ApS Revised 2009-05-19 1 Table of contents 1. Introduction...3 2. Basic idea...4 2.1 Detect-and-remove...4 2.2 Power-through-simplicity...4
Stellar Phoenix. SQL Database Repair 6.0. User Guide
 Stellar Phoenix SQL Database Repair 6.0 User Guide Overview Stellar Phoenix SQL Database Repair software is an easy to use application designed to repair corrupt or damaged Microsoft SQL Server database
Stellar Phoenix SQL Database Repair 6.0 User Guide Overview Stellar Phoenix SQL Database Repair software is an easy to use application designed to repair corrupt or damaged Microsoft SQL Server database
I.T. System Requirements 2015
 I.T. System Requirements 2015 1 Contents: page Contents 3. 4. 5. 6. Examples of incorrectly configured systems Simple server specification Standard server specification Complex server specification *DISCLAIMER*
I.T. System Requirements 2015 1 Contents: page Contents 3. 4. 5. 6. Examples of incorrectly configured systems Simple server specification Standard server specification Complex server specification *DISCLAIMER*
Stellar Phoenix. Mailbox Exchange Recovery 7.0. User Guide
 Stellar Phoenix Mailbox Exchange Recovery 7.0 User Guide Overview Stellar Phoenix Mailbox Exchange Recovery offers a complete solution to recover corrupt MS Exchange database files. The software recovers
Stellar Phoenix Mailbox Exchange Recovery 7.0 User Guide Overview Stellar Phoenix Mailbox Exchange Recovery offers a complete solution to recover corrupt MS Exchange database files. The software recovers
Email Quick Reference. Administrator Guide
 Email Quick Reference Administrator Guide Email Services Quick Reference Documentation version: 1.0 Legal Notice Legal Notice Copyright 2015 Symantec Corporation. All rights reserved. Symantec, the Symantec
Email Quick Reference Administrator Guide Email Services Quick Reference Documentation version: 1.0 Legal Notice Legal Notice Copyright 2015 Symantec Corporation. All rights reserved. Symantec, the Symantec
for Invoice Processing Installation Guide
 for Invoice Processing Installation Guide CVISION TECHNOLOGIES Copyright Technologies Trapeze for Invoice Processing CVISION TECHNOLOGIES 2013 Trapeze for Invoice Processing 3.0 Professional Installation
for Invoice Processing Installation Guide CVISION TECHNOLOGIES Copyright Technologies Trapeze for Invoice Processing CVISION TECHNOLOGIES 2013 Trapeze for Invoice Processing 3.0 Professional Installation
Sage 100 Premium ERP Version 2015 Supported Platform Matrix Created as of April 6, 2015
 The information in this document applies to Sage 100 Premium ERP Version 2015.Detailed product update information and support policies can be found on the Sage Support web site at: https://support.na.sage.com/
The information in this document applies to Sage 100 Premium ERP Version 2015.Detailed product update information and support policies can be found on the Sage Support web site at: https://support.na.sage.com/
Getting Started Guide
 Getting Started Guide www.exclaimer.com Contents About This Guide... 2 Mail Disclaimers Overview... 3 What Does Exclaimer Mail Disclaimers Do?... 3 But That s Not All... 3 And There s More... 3 How Does
Getting Started Guide www.exclaimer.com Contents About This Guide... 2 Mail Disclaimers Overview... 3 What Does Exclaimer Mail Disclaimers Do?... 3 But That s Not All... 3 And There s More... 3 How Does
Anti-Spam Test. Anti-Spam Test. (Consumer Products) Language: English. March 2016 Last Revision: 20 th April 2016. www.av-comparatives.
 Anti-Spam Test Anti-Spam Test (Consumer Products) Language: English March 2016 Last Revision: 20 th April 2016 Commissioned by PC Magazin Table of Contents Tested Products 3 Introduction 4 Test procedure
Anti-Spam Test Anti-Spam Test (Consumer Products) Language: English March 2016 Last Revision: 20 th April 2016 Commissioned by PC Magazin Table of Contents Tested Products 3 Introduction 4 Test procedure
ESET Mobile Security Windows Mobile
 ESET Mobile Security Windows Mobile Installation Manual and User Guide Click here to download the most recent version of this document Contents 1. Installation...3 of ESET Mobile Security 1.1 Minimum...3
ESET Mobile Security Windows Mobile Installation Manual and User Guide Click here to download the most recent version of this document Contents 1. Installation...3 of ESET Mobile Security 1.1 Minimum...3
Sage 100 Premium Version 2016 Supported Platform Matrix Created as of November 25, 2015
 The information in this document applies to Sage 100 Premium Version 2016. Detailed product update information and support policies can be found on the Sage Support web site at: https://support.na.sage.com/.
The information in this document applies to Sage 100 Premium Version 2016. Detailed product update information and support policies can be found on the Sage Support web site at: https://support.na.sage.com/.
AdminToys Suite. Installation & Setup Guide
 AdminToys Suite Installation & Setup Guide Copyright 2008-2009 Lovelysoft. All Rights Reserved. Information in this document is subject to change without prior notice. Certain names of program products
AdminToys Suite Installation & Setup Guide Copyright 2008-2009 Lovelysoft. All Rights Reserved. Information in this document is subject to change without prior notice. Certain names of program products
European developer & provider ensuring data protection User console: Simile Fingerprint Filter Policies and content filtering rules
 Cloud Email Firewall Maximum email availability and protection against phishing and advanced threats. If the company email is not protected then the information is not safe Cloud Email Firewall is a solution
Cloud Email Firewall Maximum email availability and protection against phishing and advanced threats. If the company email is not protected then the information is not safe Cloud Email Firewall is a solution
BITDEFENDER ENDPOINT SECURITY TOOLS
 BITDEFENDER ENDPOINT SECURITY TOOLS Beta Version Testing Guide Bitdefender Endpoint Security Tools Beta Version Testing Guide Publication date 2014.11.26 Copyright 2014 Bitdefender Legal Notice All rights
BITDEFENDER ENDPOINT SECURITY TOOLS Beta Version Testing Guide Bitdefender Endpoint Security Tools Beta Version Testing Guide Publication date 2014.11.26 Copyright 2014 Bitdefender Legal Notice All rights
PC Security and Maintenance
 PC Security and Maintenance by IMRAN GHANI PC Maintenance and Security-Forecast. Major sources of danger. Important steps to protect your PC. PC Security Tools. PC Maintenance Tools. Tips. PC Security-
PC Security and Maintenance by IMRAN GHANI PC Maintenance and Security-Forecast. Major sources of danger. Important steps to protect your PC. PC Security Tools. PC Maintenance Tools. Tips. PC Security-
How To Manage Your Quarantine Email On A Blackberry.Com
 Barracuda Spam Firewall User s Guide 1 Copyright Copyright 2005, Barracuda Networks www.barracudanetworks.com v3.2.22 All rights reserved. Use of this product and this manual is subject to license. Information
Barracuda Spam Firewall User s Guide 1 Copyright Copyright 2005, Barracuda Networks www.barracudanetworks.com v3.2.22 All rights reserved. Use of this product and this manual is subject to license. Information
8x8 Network Diagnostics Tool User Guide
 8x8 User Guide Version 1.0, March 2011 Table of Contents Introduction...3 Getting Accurate Results...3 Installation...4 Start and Configure...5 Tests...8 Saving and Sending Test Results...8 FAQ...12 2
8x8 User Guide Version 1.0, March 2011 Table of Contents Introduction...3 Getting Accurate Results...3 Installation...4 Start and Configure...5 Tests...8 Saving and Sending Test Results...8 FAQ...12 2
Install Guide VirusBlokAda
 Antivirus / Anti-spam Vba32 for Microsoft Exchange VirusBlokAda Copyright 1993-2011 ОДО VirusBlokAda Ltd. Documentation version: 0.5 (March 2011) All rights reserved. All contents, graphics and texts,
Antivirus / Anti-spam Vba32 for Microsoft Exchange VirusBlokAda Copyright 1993-2011 ОДО VirusBlokAda Ltd. Documentation version: 0.5 (March 2011) All rights reserved. All contents, graphics and texts,
Mailwall Remote Features Tour Datasheet
 Management Portal & Dashboard Mailwall Remote Features Tour Datasheet Feature Benefit Learn More Screenshot Cloud based portal Securely manage your web filtering policy wherever you are without need for
Management Portal & Dashboard Mailwall Remote Features Tour Datasheet Feature Benefit Learn More Screenshot Cloud based portal Securely manage your web filtering policy wherever you are without need for
ESET NOD32 Antivirus. Table of contents
 ESET NOD32 Antivirus ESET NOD32 Antivirus provides state-of-theart protection for your computer against malicious code. Based on the ThreatSense scanning engine first introduced in the awardwinning NOD32
ESET NOD32 Antivirus ESET NOD32 Antivirus provides state-of-theart protection for your computer against malicious code. Based on the ThreatSense scanning engine first introduced in the awardwinning NOD32
AVG AntiVirus Free Edition 2015
 AVG AntiVirus Free Edition 2015 User Manual Document revision 2015.18 (3.2.2015) C opyright AVG Technologies C Z, s.r.o. All rights reserved. All other trademarks are the property of their respective owners.
AVG AntiVirus Free Edition 2015 User Manual Document revision 2015.18 (3.2.2015) C opyright AVG Technologies C Z, s.r.o. All rights reserved. All other trademarks are the property of their respective owners.
Lumension Endpoint Management and Security Suite. L.E.M.S.S. AntiVirus v8.2. Migration Guide & Frequently Asked Questions
 Lumension Endpoint Management and Security Suite L.E.M.S.S. AntiVirus v8.2 Migration Guide & Frequently Asked Questions [FOR INTERNAL USE ONLY - DO NOT DISTRIBUTE] Copyright 2015, Lumension Introduction
Lumension Endpoint Management and Security Suite L.E.M.S.S. AntiVirus v8.2 Migration Guide & Frequently Asked Questions [FOR INTERNAL USE ONLY - DO NOT DISTRIBUTE] Copyright 2015, Lumension Introduction
For Businesses with more than 25 seats. www.eset.com
 For Businesses with more than 25 seats www.eset.com ESET Endpoint Protection Standard Whether your business is just starting or Simple and Straightforward established, there are a few things you expect
For Businesses with more than 25 seats www.eset.com ESET Endpoint Protection Standard Whether your business is just starting or Simple and Straightforward established, there are a few things you expect
AVG Internet Security 2012
 AVG Internet Security 2012 User Manual Document revision 2012.24 (19.6.2012) C opyright AVG Technologies C Z, s.r.o. All rights reserved. All other trademarks are the property of their respective owners.
AVG Internet Security 2012 User Manual Document revision 2012.24 (19.6.2012) C opyright AVG Technologies C Z, s.r.o. All rights reserved. All other trademarks are the property of their respective owners.
Anti Virus Comparative Performance Test (AV Products) November 2011
 Anti-Virus Comparative Performance test (AV Products) Impact of Anti-Virus Software on System Performance Language: English November 2011 Last Revision: 8 th December 2011 www.av-comparatives.org Table
Anti-Virus Comparative Performance test (AV Products) Impact of Anti-Virus Software on System Performance Language: English November 2011 Last Revision: 8 th December 2011 www.av-comparatives.org Table
ESET Mobile Security Business Edition for Windows Mobile
 ESET Mobile Security Business Edition for Windows Mobile Installation Manual and User Guide Click here to download the most recent version of this document Contents 1. Installation...3 of ESET Mobile Security
ESET Mobile Security Business Edition for Windows Mobile Installation Manual and User Guide Click here to download the most recent version of this document Contents 1. Installation...3 of ESET Mobile Security
Molecular Devices High Content Data Management Solution Database Schema
 Molecular Devices High Content Data Management Solution Database Schema For: MetaXpress Software, MetaXpress PowerCore Software, MDCStore Data Management Solution, and AcuityXpress Software Computer and
Molecular Devices High Content Data Management Solution Database Schema For: MetaXpress Software, MetaXpress PowerCore Software, MDCStore Data Management Solution, and AcuityXpress Software Computer and
Kaspersky Small Office Security User Guide
 Kaspersky Small Office Security User Guide APPLICATION VERSION: 4.0 Dear User, Thank you for choosing our product. We hope that this document will help you in your work and will provide answers regarding
Kaspersky Small Office Security User Guide APPLICATION VERSION: 4.0 Dear User, Thank you for choosing our product. We hope that this document will help you in your work and will provide answers regarding
ESET ENDPOINT SECURITY FOR ANDROID
 ESET ENDPOINT SECURITY FOR ANDROID Installation Manual and User Guide Click here to download the most recent version of this document Contents 1...3 Installation of ESET Endpoint Security 1.1 Installation...3
ESET ENDPOINT SECURITY FOR ANDROID Installation Manual and User Guide Click here to download the most recent version of this document Contents 1...3 Installation of ESET Endpoint Security 1.1 Installation...3
AVG Internet Security
 AVG Internet Security User Manual Document revision AVG.23 (20.5.2016) C opyright AVG Technologies C Z, s.r.o. All rights reserved. All other trademarks are the property of their respective owners. Contents
AVG Internet Security User Manual Document revision AVG.23 (20.5.2016) C opyright AVG Technologies C Z, s.r.o. All rights reserved. All other trademarks are the property of their respective owners. Contents
Example - Barracuda Network Access Client Configuration
 Example - Barracuda Network Access Client Configuration Introducing an active Barracuda Network Access Client environment involves several components, such as global objects, trustzone settings, Access
Example - Barracuda Network Access Client Configuration Introducing an active Barracuda Network Access Client environment involves several components, such as global objects, trustzone settings, Access
Installation Guide. NOD32 Typical. Proactive protection against Viruses, Spyware, Worms, Trojans, Rootkits, Adware and Phishing
 NOD32 Typical Installation Guide Version 2.7 Includes Windows Vista and 64-bit protection Proactive protection against Viruses, Spyware, Worms, Trojans, Rootkits, Adware and Phishing Best Detection Fastest
NOD32 Typical Installation Guide Version 2.7 Includes Windows Vista and 64-bit protection Proactive protection against Viruses, Spyware, Worms, Trojans, Rootkits, Adware and Phishing Best Detection Fastest
How To Test For Performance On A 64 Bit Computer (64 Bit)
 Anti-Virus Comparative Performance Test Impact of Security Software on System Performance Language: English May 2015 Last Revision: 30 th June 2015 Table of Contents 1. Introduction 3 2. Tested products
Anti-Virus Comparative Performance Test Impact of Security Software on System Performance Language: English May 2015 Last Revision: 30 th June 2015 Table of Contents 1. Introduction 3 2. Tested products
Kaspersky Internet Security User Guide
 Kaspersky Internet Security User Guide APPLICATION VERSION: 15.0 Dear User, Thank you for choosing our product. We hope that this document will help you in your work and will provide answers regarding
Kaspersky Internet Security User Guide APPLICATION VERSION: 15.0 Dear User, Thank you for choosing our product. We hope that this document will help you in your work and will provide answers regarding
Barracuda Spam Firewall User s Guide
 Barracuda Spam Firewall User s Guide 1 Copyright Copyright 2005, Barracuda Networks www.barracudanetworks.com v3.2.22 All rights reserved. Use of this product and this manual is subject to license. Information
Barracuda Spam Firewall User s Guide 1 Copyright Copyright 2005, Barracuda Networks www.barracudanetworks.com v3.2.22 All rights reserved. Use of this product and this manual is subject to license. Information
About This Guide... 4. Signature Manager Outlook Edition Overview... 5
 Contents About This Guide... 4 Signature Manager Outlook Edition Overview... 5 How does it work?... 5 But That's Not All...... 6 And There's More...... 6 Licensing... 7 Licensing Information... 7 System
Contents About This Guide... 4 Signature Manager Outlook Edition Overview... 5 How does it work?... 5 But That's Not All...... 6 And There's More...... 6 Licensing... 7 Licensing Information... 7 System
Dell Enterprise Reporter 2.5. Configuration Manager User Guide
 Dell Enterprise Reporter 2.5 2014 Dell Inc. ALL RIGHTS RESERVED. This guide contains proprietary information protected by copyright. The software described in this guide is furnished under a software license
Dell Enterprise Reporter 2.5 2014 Dell Inc. ALL RIGHTS RESERVED. This guide contains proprietary information protected by copyright. The software described in this guide is furnished under a software license
Kaspersky Internet Security
 Kaspersky Internet Security User Guide APPLICATION VERSION: 16.0 Dear User, Thank you for choosing our product. We hope that this document will help you in your work and will provide answers regarding
Kaspersky Internet Security User Guide APPLICATION VERSION: 16.0 Dear User, Thank you for choosing our product. We hope that this document will help you in your work and will provide answers regarding
Single Product Review. SoftSphere Technologies. DefenseWall HIPS. Language: English May 2009 Revised last: 2009-05-20. www.av-comparatives.
 Single Product Review SoftSphere Technologies DefenseWall HIPS Language: English May 2009 Revised last: 2009-05-20 Table of Contents About Softsphere Technologies 3 Website & Information 4 Help & Support
Single Product Review SoftSphere Technologies DefenseWall HIPS Language: English May 2009 Revised last: 2009-05-20 Table of Contents About Softsphere Technologies 3 Website & Information 4 Help & Support
ESET Mail Security 4. for Microsoft Exchange Server Version 4.3. Installation Manual and User Guide. Microsoft Windows Server 2000 / 2003 / 2008
 ESET Mail Security 4 for Microsoft Exchange Server Version 4.3 Installation Manual and User Guide Microsoft Windows Server 2000 / 2003 / 2008 Click here to download the most recent version of this document
ESET Mail Security 4 for Microsoft Exchange Server Version 4.3 Installation Manual and User Guide Microsoft Windows Server 2000 / 2003 / 2008 Click here to download the most recent version of this document
First Look Trend Micro Deep Discovery Inspector
 First Look Trend Micro Deep Discovery Inspector By looking for correlations in attack patterns, Trend Micro s Deep Discovery Inspector has the ability to protect networks against customised attacks and
First Look Trend Micro Deep Discovery Inspector By looking for correlations in attack patterns, Trend Micro s Deep Discovery Inspector has the ability to protect networks against customised attacks and
Installation Guide Version 2.0
 Installation Guide Version 2.0 1 Overview 'Stellar Mail Backup' is a complete backup solution software for all email accounts configured in 'MS Outlook', 'Outlook Express' and 'Windows Mail' email clients
Installation Guide Version 2.0 1 Overview 'Stellar Mail Backup' is a complete backup solution software for all email accounts configured in 'MS Outlook', 'Outlook Express' and 'Windows Mail' email clients
Norman Security Portal
 User Guide Norman Security Portal SECURITY PORTAL Features Cloud-based endpoint management Managed & unmanaged customers Generate client software Statistics & reports Security Module Antivirus & Antispyware
User Guide Norman Security Portal SECURITY PORTAL Features Cloud-based endpoint management Managed & unmanaged customers Generate client software Statistics & reports Security Module Antivirus & Antispyware
Symantec Mail Security for Microsoft Exchange
 Symantec Mail Security for Microsoft Exchange Getting Started Guide v7.0 Symantec Mail Security for Microsoft Exchange Getting Started Guide The software described in this book is furnished under a license
Symantec Mail Security for Microsoft Exchange Getting Started Guide v7.0 Symantec Mail Security for Microsoft Exchange Getting Started Guide The software described in this book is furnished under a license
Quest vworkspace Virtual Desktop Extensions for Linux
 Quest vworkspace Virtual Desktop Extensions for Linux What s New Version 7.6 2012 Quest Software, Inc. ALL RIGHTS RESERVED. Patents Pending. This guide contains proprietary information protected by copyright.
Quest vworkspace Virtual Desktop Extensions for Linux What s New Version 7.6 2012 Quest Software, Inc. ALL RIGHTS RESERVED. Patents Pending. This guide contains proprietary information protected by copyright.
Sage SalesLogix White Paper. Sage SalesLogix v8.0 Performance Testing
 White Paper Table of Contents Table of Contents... 1 Summary... 2 Client Performance Recommendations... 2 Test Environments... 2 Web Server (TLWEBPERF02)... 2 SQL Server (TLPERFDB01)... 3 Client Machine
White Paper Table of Contents Table of Contents... 1 Summary... 2 Client Performance Recommendations... 2 Test Environments... 2 Web Server (TLWEBPERF02)... 2 SQL Server (TLPERFDB01)... 3 Client Machine
ESET Endpoint Security 6 ESET Endpoint Antivirus 6 for Windows
 ESET Endpoint Security 6 ESET Endpoint Antivirus 6 for Windows Products Details ESET Endpoint Security 6 protects company devices against most current threats. It proactively looks for suspicious activity
ESET Endpoint Security 6 ESET Endpoint Antivirus 6 for Windows Products Details ESET Endpoint Security 6 protects company devices against most current threats. It proactively looks for suspicious activity
Dealing with spam mail
 Vodafone Hosted Services Dealing with spam mail User guide Welcome. This guide will help you to set up anti-spam measures on your email accounts and domains. The main principle behind dealing with spam
Vodafone Hosted Services Dealing with spam mail User guide Welcome. This guide will help you to set up anti-spam measures on your email accounts and domains. The main principle behind dealing with spam
Antivirus. Quick Start Guide. Antivirus
 Antivirus 2007 Antivirus plus I Firewall Quick Start Guide Helpful Information on Installation and Set-Up STOPS and Removes Viruses DELIVERS Proactive Firewall Protection EASY to Set Up and Use FREE Upgrades
Antivirus 2007 Antivirus plus I Firewall Quick Start Guide Helpful Information on Installation and Set-Up STOPS and Removes Viruses DELIVERS Proactive Firewall Protection EASY to Set Up and Use FREE Upgrades
Features Business Perspective. www.eset.com
 Features Business Perspective www.eset.com Endpoint Protection Antivirus / Antispyware Auto-Scan of Removable Media Host-based Intrusion Prevention System (HIPS) Client Antispam Cross-platform Protection
Features Business Perspective www.eset.com Endpoint Protection Antivirus / Antispyware Auto-Scan of Removable Media Host-based Intrusion Prevention System (HIPS) Client Antispam Cross-platform Protection
Trend Micro Incorporated reserves the right to make changes to this document and to the products described herein without notice.
 Trend Micro Incorporated reserves the right to make changes to this document and to the products described herein without notice. Before installing and using the software, please review the readme files,
Trend Micro Incorporated reserves the right to make changes to this document and to the products described herein without notice. Before installing and using the software, please review the readme files,
Guide. New Outlook Web Access - Webmail. ICT Services
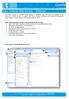 The new version of Outlook Web Access Webmail lets you take advantage of an improved e-mail service, a clearer and more stylish interface and layout and powerful tools similar to those found in Microsoft
The new version of Outlook Web Access Webmail lets you take advantage of an improved e-mail service, a clearer and more stylish interface and layout and powerful tools similar to those found in Microsoft
Anti-Virus Comparative
 Anti-Virus Comparative Malware Removal Test Language: English October 2013 Last Revision: 21 st November 2013 Table of Contents Tested Products 3 Introduction 4 Test-Procedure 4 Malware selection 4 Used
Anti-Virus Comparative Malware Removal Test Language: English October 2013 Last Revision: 21 st November 2013 Table of Contents Tested Products 3 Introduction 4 Test-Procedure 4 Malware selection 4 Used
User's Guide. Copyright 2010 BitDefender
 User's Guide Copyright 2010 BitDefender BitDefender Antivirus Pro 2011 User's Guide Published 2010.07.30 Copyright 2010 BitDefender Legal Notice All rights reserved. No part of this book may be reproduced
User's Guide Copyright 2010 BitDefender BitDefender Antivirus Pro 2011 User's Guide Published 2010.07.30 Copyright 2010 BitDefender Legal Notice All rights reserved. No part of this book may be reproduced
