STUDY GUIDE CHAPTER 3
|
|
|
- Beverley Thomas
- 7 years ago
- Views:
Transcription
1 STUDY GUIDE CHAPTER 3 True/False Indicate whether the statement is true or false. 1. Stereographical applications typically display satellite, aerial, or street maps used to locate places and get directions between two addresses. 2. Mobile devices typically pinpoint your location using built-in GPS or triangulating your distance from nearby cell towers. 3. Vertical market software is designed to automate specialized tasks in a specific market or business. 4. Utilities are an example of application software. 5. A(n) device driver is software that helps a peripheral device establish communication with a computer 6. Utility software refers to a type of application software that has the potential to help people get work done 7. A typical software package contains many files. 8. A(n) compressed file is designed to be started by users or automatically launched by the operating system. 9. Most Web apps work on any device with a compatible browser. 10. A(n) trademark is a form of legal protection that grants the author of the original work exclusive rights to copy, distribute, sell, and modify. 11. Public domain software has restrictions on its use. 12. Hackers can use rootkits to cloak their work. 13. A virus hoax usually arrives as a(n) A security package integrates several security modules to protect against malware. 15. Leading refers to the vertical spacing between lines in a document. 16. CAD software is designed to be used by architects and engineers. 17. When devices record your location, there is no possibility of abuse. 18. Payroll software is an example of vertical market software. 19. Third-party software companies offer additional products that extend and improve upon those supplied by the operating system. 20. Utility software includes diagnostics that track down and fix disk errors. 21. By using spell checkers and grammar checkers, you are assured your document will be error-free. 22. Spreadsheets have built-in formulas. 23. A jailbreak lasts until you accept a software update from Apple. 24. If you purchase software, it belongs to you, and you can do what you want, including copying it. 25. Local applications are installed on a local file server.
2 26. Executable files have an.exe extension. 27. Files that are zipped contain consolidated files that are compressed and ready to execute. 28. Even after the media containing portable software is removed from a computer, some traces of the software are left there. 29. A new version update usually installs in a similar way as when you installed the original version. 30. Open source software is copyrighted. 31. A zombie is a computer under the control of a bad bot. 32. A virus signature is a digitally signed certificate that certifies the file is virus-free. 33. Antivirus software does not require any updates. 34. A quarantined file is generally encrypted before storing. Multiple Choice Identify the choice that best completes the statement or answers the question. 35. A EULA is. a. an end-user license agreement for using software b. a warranty offered to customers who purchase software c. a copyright notice on software d. software supplied on a trial basis that expires, usually after a 30-day period 36. For which one of the following tasks would you be most likely to use database software? a. Keeping track of the grades you get in a c. Helping your friend who runs a preschool course and working out how well you to keep track of student names, have to do on remaining exams to get an birthdates, parents' names, addresses, A. and phone numbers. b. Creating a personal Web site that d. Managing the playlists for your ipod. contains a list of your top ten movies. 37. software is an example of utility software. a. Graphics c. Desktop publishing b. Anti-virus d. Word processing 38. When composing a document, you can use the feature to find each occurrence of frequently used words and decide whether you want to substitute a different word. a. Auto-correct c. Commenting b. Search and Replace d. Edit and Merge 39. By default, a cell reference in spreadsheet software is a(n) reference. a. absolute c. recalculated b. relative d. functional 40. software is able to access your current location and use it to show you the closest shops, restaurants, and theaters, as well as information about each location. a. Mobile c. Cloud-based b. Crowd-based d. Location-based
3 41. Both open source and can be copied an unlimited number of times, distributed for free, sold, and modified. a. proprietary software c. shareware b. free software d. demoware 42. The files supplied on software distribution disks and downloads are often to consolidate them into one large file. a. reconstituted c. uncompressed b. stripped d. zipped 43. System software is designed to accomplish tasks. a. real-world c. gaming b. computer-centric d. only operating system 44. Application software is designed to accomplish tasks. a. real-world c. gaming b. computer-centric d. only operating system 45. Examples of DVD authoring software include all the following EXCEPT. a. Roxio Creator c. ULead DVD Movie Factory b. Apple idvd d. Windows DVD Maker D graphics software provides a set of tools for creating that represent three-dimensional objects. a. stereoscopes c. wireframes b. prototypes d. photos 47. An example of mathematical modeling software is. a. SPSS Statistics c. Quicken b. Mathcad d. all answers are correct 48. Productivity software that has sophisticated features to help you produce professional-quality output is considered software. a. word processing c. Web authoring b. desktop publishing d. spreadsheet 49. Software considered to be utility software is. a. the Windows operating system c. spell check b. word processing d. hard disk backup software 50. The type of system software designed to help you monitor and configure settings for your computer system equipment is software. a. settings set c. utility b. execution d. config 51. Adobe Reader works with files stored in standard format. a. PDF c. HTML b. GIF d. both a and c 52. Word determines how your text flows from line to line by automatically moving words down to the next line as you reach the right margin in a word processing document. a. placement c. format b. wrap d. authoring 53. utilities alter a user's interface to create an accessible environment. a. Shareware c. Collaborative b. Adaptive d. Functional
4 54. An example of software most commonly associated with productivity software is. a. the Windows operating system c. word processing software b. a real-time player d. a browser 55. Productivity software that provides you with the ability to create, spell-check, edit, and format is considered software. a. word processing c. Web authoring b. desktop processing d. spreadsheet 56. When using word processing software to analyze the reading level of your document, you should use a. a. thesaurus c. readability formula b. grammar checker d. paragraph checker 57. The paragraph style that is used to assure paragraphs are aligned evenly on both the right and left is. a. both align c. fully justified b. paragraph justify d. page align 58. A page layout includes. a. headers and footers c. margins b. page numbers d. all answers are correct 59. The intersection of a column and a row on a spreadsheet is called a. a. formula c. number b. value d. cell 60. Spreadsheets are particularly useful for. a. what-if analysis c. creating tables b. use as a calculator d. none of the above 61. A formula can contain and mathematical operators. a. manipulatives c. cell references b. labels d. locations 62. To find a particular record or group of records in a database, you use a(n). a. find c. inquiry b. query d. search 63. You can use the results from a search on a database in all of these ways EXCEPT to. a. print reports c. convert formats b. export data d. create records 64. queries are questions stated in a language such as English, rather than an esoteric query language. a. Natural language c. QBE b. Keyword d. Notational 65. searches are simply a collection of words relevant to a search. a. Natural language c. QBE b. Keyword d. Notational 66. simply requires you to fill out a form with the type of data you want to locate in a database. a. Natural language modification c. QBE b. Keyword searching d. Notational resonance 67. Popular presentation software products include all of the following EXCEPT. a. Microsoft PowerPoint c. LibreOffice Impress b. iwork Keynote d. Movie Maker
5 68. Web applications are. a. installed locally and run on the Web c. installed on the Web and run locally b. accessed and run on the Web d. all answers are correct 69. Mobile apps. a. are usually small c. often cost less than $5.00, or are even free b. typically are sold through an App store d. all answers are correct 70. ipads, iphones, and ipods are only allowed to download apps from the itunes App Store, and while apps are available from other sources, using them requires an unauthorized change to the device's software called a(n). a. protocol breach c. android b. factory reset d. jailbreak 71. The process of overcoming limitations imposed by mobile service providers on a mobile device is called. a. jailbreaking c. breaching protocol b. factory reset d. rooting 72. The Windows is a database that keeps track of your computer's peripheral devices, software, preferences, and settings. a. BIOS c. CD-ROM b. ROM d. Registry 73. applications are software that is installed on a computer s hard disk. a. Help c. Data b. Resident d. Local 74. When you install a local application, all of its files are placed in the appropriate folders on your computer's hard disk, and then your computer performs any software or hardware necessary to make sure the program is ready to run. a. authentications c. configurations b. reboots d. verifications 75. Support programs have a(n) extension. a..exe c..dll b..hlp d..spt 76. Data files containing on-screen help most likely have the file extension. a..exe c..doc b..hlp d..xls 77. Software requires many files because. a. there is too much data to store on one file c. it allows for easy maintenance b. it allows flexibility and efficiency d. it allows for quicker installation 78. A(n) installation gives you access to all features of the software. a. custom c. activated b. hash d. full 79. In a(n) installation, the setup program displays a list of software features for your selection. a. custom c. activated b. hash d. full
6 80. All the following are examples of portable applications EXCEPT. a. Firefox c. Thunderbird b. FileZilla d. Microsoft Internet Explorer 81. Portable software is. a. lighter than local software c. designed to run from removable storage b. licensed only for portable devices d. designed to run on portable devices 82. A service pack. a. unlocks computer services b. requires a service call to a technician c. provides updates to the operating system d. repairs and fixes the hardware 83. To get rid of software you no longer want, you. a. delete the icon c. run an uninstall routine b. delete the files d. both a and b 84. It is illegal to do all the following with software EXCEPT. a. copy and sell to a friend c. copy and keep as backup b. copy and give to a friend d. modify 85. Indicators of pirated software include all of the following EXCEPT software that. a. is marked as an academic product, but not purchased through an authorized dealer b. is downloaded c. has photocopied software manuals d. has CD-ROMs with handwritten labels 86. A shrink-wrap license goes into effect as soon as you. a. use it c. open it b. purchase it d. register it 87. Software that may be freely copied, distributed, and even resold is. a. shareware c. public domain b. open source d. GPL 88. is typically sold in computer stores or at Web sites. a. Commercial software c. Shareware b. Open source software d. Freeware 89. is typically available as a trial version. a. Commercial software c. Demoware b. Open source software d. Shareware 90. is typically commercial software that is marketed under a try-before-you buy policy. a. Commercial software c. Shareware b. Open source software d. Freeware 91. may be sold or distributed free of charge in compiled form but must always include the source code. a. Commercial software c. Shareware b. Open source software d. Sourceware 92. Product validation can create a(n) based on your validation code and your computer s internal serial number. a. Trojan horse c. hash value b. blueprint d. hash brown
7 93. During product activation, you must. a. run the program c. enter a product key b. create a password d. none of the above 94. A is any software that can automate a task or autonomously execute a task when commanded to do so. a. virus c. Trojan horse b. worm d. bot 95. The term rootkit refers to. a. a program that repairs the computer s hardware core b. a program that repairs the kernel c. software tools used to conceal malware and backdoors d. software tools used to conceal security tools 96. To avoid security threats, a user can. a. store all data on a thumb drive b. enable the Hide extensions option c. read as soon as it comes in d. avoid opening suspicious attachments 97. A security suite will typically include all of the following EXCEPT software. a. antivirus c. antispyware b. firewall d. browser 98. Security suites can be. a. downloaded from the Web c. purchased at electronics stores b. purchased at computer stores d. all answers are correct 99. A virus signature is a. a. type of utility that looks for and eradicates viruses b. unique series of instructions to defend against malicious code c. section of program code used to identify a known malicious program d. the personal identifier of the author of the virus 100. If virus protection software identifies a virus, it can try to take all of the following actions except. a. remove the infection c. delete the file b. put the file in quarantine d. shut down the computer
Chapter 3 Software. Computer Concepts 2013. 3 Chapter Contents. 3 Section A: Software Basics 13-09-27
 Chapter 3 Software Computer Concepts 2013 3 Chapter Contents Ø Section A: Software Basics Ø Section B: Office Suites Ø Section C: Installing Software and Upgrades Ø Section D: Buying Software Ø Section
Chapter 3 Software Computer Concepts 2013 3 Chapter Contents Ø Section A: Software Basics Ø Section B: Office Suites Ø Section C: Installing Software and Upgrades Ø Section D: Buying Software Ø Section
Chapter 3. Application Software. Chapter 3 Objectives. Application Software
 Chapter 3 Objectives Chapter 3 Application Software Identify the categories of application software Explain ways software is distributed Explain how to work with application software Identify the key features
Chapter 3 Objectives Chapter 3 Application Software Identify the categories of application software Explain ways software is distributed Explain how to work with application software Identify the key features
CSCA0101 Computing Basics CSCA0101 COMPUTING BASICS. Chapter 7 Software
 CSCA0101 COMPUTING BASICS Chapter 7 1 1. Computer Application 2. Types of Computer 3. Licensing 4. Types of License 5. Piracy 2 Computer software, or just software, is a collection of computer programs
CSCA0101 COMPUTING BASICS Chapter 7 1 1. Computer Application 2. Types of Computer 3. Licensing 4. Types of License 5. Piracy 2 Computer software, or just software, is a collection of computer programs
Discovering Computers 2008. Chapter 3 Application Software
 Discovering Computers 2008 Chapter 3 Application Software Chapter 3 Objectives Identify the categories of application software Explain ways software is distributed Explain how to work with application
Discovering Computers 2008 Chapter 3 Application Software Chapter 3 Objectives Identify the categories of application software Explain ways software is distributed Explain how to work with application
Desktop and Laptop Security Policy
 Desktop and Laptop Security Policy Appendix A Examples of Desktop and Laptop standards and guidelines 1. Implement anti-virus software An anti-virus program is necessary to protect your computer from malicious
Desktop and Laptop Security Policy Appendix A Examples of Desktop and Laptop standards and guidelines 1. Implement anti-virus software An anti-virus program is necessary to protect your computer from malicious
ESET NOD32 ANTIVIRUS 8
 ESET NOD32 ANTIVIRUS 8 Microsoft Windows 8.1 / 8 / 7 / Vista / XP / Home Server 2003 / Home Server 2011 Quick Start Guide Click here to download the most recent version of this document ESET NOD32 Antivirus
ESET NOD32 ANTIVIRUS 8 Microsoft Windows 8.1 / 8 / 7 / Vista / XP / Home Server 2003 / Home Server 2011 Quick Start Guide Click here to download the most recent version of this document ESET NOD32 Antivirus
ESET SMART SECURITY 9
 ESET SMART SECURITY 9 Microsoft Windows 10 / 8.1 / 8 / 7 / Vista / XP Quick Start Guide Click here to download the most recent version of this document ESET Smart Security is all-in-one Internet security
ESET SMART SECURITY 9 Microsoft Windows 10 / 8.1 / 8 / 7 / Vista / XP Quick Start Guide Click here to download the most recent version of this document ESET Smart Security is all-in-one Internet security
FOR MAC. Quick Start Guide. Click here to download the most recent version of this document
 FOR MAC Quick Start Guide Click here to download the most recent version of this document ESET Cyber Security Pro provides state-of-the-art protection for your computer against malicious code. Based on
FOR MAC Quick Start Guide Click here to download the most recent version of this document ESET Cyber Security Pro provides state-of-the-art protection for your computer against malicious code. Based on
ESET NOD32 ANTIVIRUS 9
 ESET NOD32 ANTIVIRUS 9 Microsoft Windows 10 / 8.1 / 8 / 7 / Vista / XP Quick Start Guide Click here to download the most recent version of this document ESET NOD32 Antivirus provides state-of-the-art protection
ESET NOD32 ANTIVIRUS 9 Microsoft Windows 10 / 8.1 / 8 / 7 / Vista / XP Quick Start Guide Click here to download the most recent version of this document ESET NOD32 Antivirus provides state-of-the-art protection
ESET SMART SECURITY 6
 ESET SMART SECURITY 6 Microsoft Windows 8 / 7 / Vista / XP / Home Server Quick Start Guide Click here to download the most recent version of this document ESET Smart Security provides state-of-the-art
ESET SMART SECURITY 6 Microsoft Windows 8 / 7 / Vista / XP / Home Server Quick Start Guide Click here to download the most recent version of this document ESET Smart Security provides state-of-the-art
Security+ Guide to Network Security Fundamentals, Third Edition. Chapter 2 Systems Threats and Risks
 Security+ Guide to Network Security Fundamentals, Third Edition Chapter 2 Systems Threats and Risks Objectives Describe the different types of software-based attacks List types of hardware attacks Define
Security+ Guide to Network Security Fundamentals, Third Edition Chapter 2 Systems Threats and Risks Objectives Describe the different types of software-based attacks List types of hardware attacks Define
Quick Heal Exchange Protection 4.0
 Quick Heal Exchange Protection 4.0 Customizable Spam Filter. Uninterrupted Antivirus Security. Product Highlights Built-in defense keeps your business communications and sensitive information secure from
Quick Heal Exchange Protection 4.0 Customizable Spam Filter. Uninterrupted Antivirus Security. Product Highlights Built-in defense keeps your business communications and sensitive information secure from
Trend Micro Incorporated reserves the right to make changes to this document and to the products described herein without notice.
 Trend Micro Incorporated reserves the right to make changes to this document and to the products described herein without notice. Before installing and using the software, please review the readme files,
Trend Micro Incorporated reserves the right to make changes to this document and to the products described herein without notice. Before installing and using the software, please review the readme files,
Oregon State Bar Software Standards 2005. Software Proficiency Expectations (Items in bold are to be demonstrated)
 Oregon State Bar Software Standards 2005 Computer Basics (all users) Software Proficiency Expectations (Items in bold are to be demonstrated) Touch typing (at least 25 words per minute). Starting, shutting
Oregon State Bar Software Standards 2005 Computer Basics (all users) Software Proficiency Expectations (Items in bold are to be demonstrated) Touch typing (at least 25 words per minute). Starting, shutting
Chapter 3. Application Software. Chapter 3 Objectives. Application Software. Application Software. Application Software. What is application software?
 Chapter 3 Objectives Chapter 3 Application Software Identify the the categories of of application software Explain ways software is is distributed Explain how to to work with application software Identify
Chapter 3 Objectives Chapter 3 Application Software Identify the the categories of of application software Explain ways software is is distributed Explain how to to work with application software Identify
Chapter Topics. Technology in Action. Productivity Software. Application Software 12/18/2008. System Software vs. Application Software
 Technology in Action Chapter 4 Application Software: Programs That Let You Work and Play 2009 Prentice-Hall, Inc. 1 Chapter Topics Application vs. system software Productivity software Multimedia software
Technology in Action Chapter 4 Application Software: Programs That Let You Work and Play 2009 Prentice-Hall, Inc. 1 Chapter Topics Application vs. system software Productivity software Multimedia software
Chapter 8 Types of Utility Programs and Operating Systems. Discovering Computers 2012. Your Interactive Guide to the Digital World
 Chapter 8 Types of Utility Programs and Operating Systems Discovering Computers 2012 Your Interactive Guide to the Digital World Objectives Overview Define system software and identify the two types of
Chapter 8 Types of Utility Programs and Operating Systems Discovering Computers 2012 Your Interactive Guide to the Digital World Objectives Overview Define system software and identify the two types of
McAfee Internet Security Suite Quick-Start Guide
 Enjoy a Worry Free Online Experience McAfee Internet Security Suite protects your PC, identity and online experience. It also includes PC and network tools, plus McAfee SiteAdvisor for safe surfing. Internet
Enjoy a Worry Free Online Experience McAfee Internet Security Suite protects your PC, identity and online experience. It also includes PC and network tools, plus McAfee SiteAdvisor for safe surfing. Internet
CHAPTER 5: PRODUCTIVITY APPLICATIONS
 CHAPTER 5: PRODUCTIVITY APPLICATIONS Multiple Choice: 1. Entering and editing text can be done most efficiently using a: A. spreadsheet. B. desktop publishing program. C. typewriter. D. word processing
CHAPTER 5: PRODUCTIVITY APPLICATIONS Multiple Choice: 1. Entering and editing text can be done most efficiently using a: A. spreadsheet. B. desktop publishing program. C. typewriter. D. word processing
DESKTOP PRODUCTIVITY SOFTWARE
 USING WINDOWS 8 UNIT 1: INTRODUCTION TO COMPUTERS Topic A: Overview of computers Topic B: How computers work Topic C: Starting the computer UNIT 2: INPUT DEVICES Topic A: Mouse and keyboard basics Topic
USING WINDOWS 8 UNIT 1: INTRODUCTION TO COMPUTERS Topic A: Overview of computers Topic B: How computers work Topic C: Starting the computer UNIT 2: INPUT DEVICES Topic A: Mouse and keyboard basics Topic
Sage ERP MAS 90 Sage ERP MAS 200 Sage ERP MAS 200 SQL. Installation and System Administrator's Guide 4MASIN450-08
 Sage ERP MAS 90 Sage ERP MAS 200 Sage ERP MAS 200 SQL Installation and System Administrator's Guide 4MASIN450-08 2011 Sage Software, Inc. All rights reserved. Sage, the Sage logos and the Sage product
Sage ERP MAS 90 Sage ERP MAS 200 Sage ERP MAS 200 SQL Installation and System Administrator's Guide 4MASIN450-08 2011 Sage Software, Inc. All rights reserved. Sage, the Sage logos and the Sage product
Software. Webroot. Spy Sweeper. User Guide. for. Webroot Software, Inc. PO Box 19816 Boulder, CO 80308 www.webroot.com. Version 6.
 Webroot Software User Guide for Spy Sweeper Webroot Software, Inc. PO Box 19816 Boulder, CO 80308 www.webroot.com Version 6.1 Webroot Software User Guide Version 6.1 2003 2009 Webroot Software, Inc. All
Webroot Software User Guide for Spy Sweeper Webroot Software, Inc. PO Box 19816 Boulder, CO 80308 www.webroot.com Version 6.1 Webroot Software User Guide Version 6.1 2003 2009 Webroot Software, Inc. All
HP ProtectTools Embedded Security Guide
 HP ProtectTools Embedded Security Guide Document Part Number: 364876-001 May 2004 This guide provides instructions for using the software that allows you to configure settings for the HP ProtectTools Embedded
HP ProtectTools Embedded Security Guide Document Part Number: 364876-001 May 2004 This guide provides instructions for using the software that allows you to configure settings for the HP ProtectTools Embedded
Software, Shareware and Opensource CSCU9B2
 Software, Shareware and Opensource CSCU9B2 1 Contents Commercial software vs Freeware vs Open Source software Licences GNU GPL Open source Common software examples Sources, Safety and Risks 2 Pay, Try,
Software, Shareware and Opensource CSCU9B2 1 Contents Commercial software vs Freeware vs Open Source software Licences GNU GPL Open source Common software examples Sources, Safety and Risks 2 Pay, Try,
Junos Pulse Mobile Security Dashboard
 Junos Pulse Mobile Security Dashboard User Guide Release 4.0 June 2012 R1 Copyright 2012, Juniper Networks, Inc. . Junos Pulse Mobile Security Dashboard Juniper Networks, Inc. 1194 North Mathilda Avenue
Junos Pulse Mobile Security Dashboard User Guide Release 4.0 June 2012 R1 Copyright 2012, Juniper Networks, Inc. . Junos Pulse Mobile Security Dashboard Juniper Networks, Inc. 1194 North Mathilda Avenue
Mobile Print/Scan Guide for Brother iprint&scan
 Mobile Print/Scan Guide for Brother iprint&scan Version K ENG Definitions of notes We use the following note style throughout this user s guide: specifies the operating environment, conditions for installation,
Mobile Print/Scan Guide for Brother iprint&scan Version K ENG Definitions of notes We use the following note style throughout this user s guide: specifies the operating environment, conditions for installation,
Entrust Managed Services PKI. Getting started with digital certificates and Entrust Managed Services PKI. Document issue: 1.0
 Entrust Managed Services PKI Getting started with digital certificates and Entrust Managed Services PKI Document issue: 1.0 Date of issue: May 2009 Copyright 2009 Entrust. All rights reserved. Entrust
Entrust Managed Services PKI Getting started with digital certificates and Entrust Managed Services PKI Document issue: 1.0 Date of issue: May 2009 Copyright 2009 Entrust. All rights reserved. Entrust
Word Processing Features. Creating Tables. Steps to Create a Table. Word Processing Features PowerPoint Handout 3.A.1
 Word Processing Features PROFITT Curriculum Basic Computer Skills Module 3 Introduction to Microsoft Word Adapted from CTAERN Curriculum Creating Tables Table an arrangement of text or numbers in rows
Word Processing Features PROFITT Curriculum Basic Computer Skills Module 3 Introduction to Microsoft Word Adapted from CTAERN Curriculum Creating Tables Table an arrangement of text or numbers in rows
System Compatibility. Enhancements. Operating Systems. Hardware Requirements. Email Security
 Email Security SonicWALL Email Security 7.0 for Microsoft Small Business Server System Compatibility SonicWALL Email Security 7.0 Software is supported on systems with the following: Operating Systems
Email Security SonicWALL Email Security 7.0 for Microsoft Small Business Server System Compatibility SonicWALL Email Security 7.0 Software is supported on systems with the following: Operating Systems
Secure and Safe Computing Primer Examples of Desktop and Laptop standards and guidelines
 Secure and Safe Computing Primer Examples of Desktop and Laptop standards and guidelines 1. Implement anti-virus software An anti-virus program is necessary to protect your computer from malicious programs,
Secure and Safe Computing Primer Examples of Desktop and Laptop standards and guidelines 1. Implement anti-virus software An anti-virus program is necessary to protect your computer from malicious programs,
Installation and Administration Guide
 Installation and Administration Guide Release 8 This installation guide will walk you through how to install and deploy Conga Composer, including recommended settings for the application. Contact Support:
Installation and Administration Guide Release 8 This installation guide will walk you through how to install and deploy Conga Composer, including recommended settings for the application. Contact Support:
Course Description. Course Audience. Course Outline. Course Page - Page 1 of 12
 Course Page - Page 1 of 12 Windows 7 Enterprise Desktop Support Technician M-50331 Length: 5 days Price: $2,795.00 Course Description This five-day instructor-led course provides students with the knowledge
Course Page - Page 1 of 12 Windows 7 Enterprise Desktop Support Technician M-50331 Length: 5 days Price: $2,795.00 Course Description This five-day instructor-led course provides students with the knowledge
Symantec LiveUpdate Administrator. Getting Started Guide
 Symantec LiveUpdate Administrator Getting Started Guide Symantec LiveUpdate Administrator Getting Started Guide The software described in this book is furnished under a license agreement and may be used
Symantec LiveUpdate Administrator Getting Started Guide Symantec LiveUpdate Administrator Getting Started Guide The software described in this book is furnished under a license agreement and may be used
FileMaker Pro and Microsoft Office Integration
 FileMaker Pro and Microsoft Office Integration page Table of Contents Executive Summary...3 Introduction...3 Top Reasons to Read This Guide...3 Before You Get Started...4 Downloading the FileMaker Trial
FileMaker Pro and Microsoft Office Integration page Table of Contents Executive Summary...3 Introduction...3 Top Reasons to Read This Guide...3 Before You Get Started...4 Downloading the FileMaker Trial
Common Cyber Threats. Common cyber threats include:
 Common Cyber Threats: and Common Cyber Threats... 2 Phishing and Spear Phishing... 3... 3... 4 Malicious Code... 5... 5... 5 Weak and Default Passwords... 6... 6... 6 Unpatched or Outdated Software Vulnerabilities...
Common Cyber Threats: and Common Cyber Threats... 2 Phishing and Spear Phishing... 3... 3... 4 Malicious Code... 5... 5... 5 Weak and Default Passwords... 6... 6... 6 Unpatched or Outdated Software Vulnerabilities...
ESET CYBER SECURITY PRO for Mac Quick Start Guide. Click here to download the most recent version of this document
 ESET CYBER SECURITY PRO for Mac Quick Start Guide Click here to download the most recent version of this document ESET Cyber Security Pro provides state-of-the-art protection for your computer against
ESET CYBER SECURITY PRO for Mac Quick Start Guide Click here to download the most recent version of this document ESET Cyber Security Pro provides state-of-the-art protection for your computer against
BUILDING DIGITAL LITERACY PURPOSE DEFINING DIGITAL LITERACY USING THIS GUIDE
 BUILDING PURPOSE In today s society, it is critical for students to be able to use the vast amount of technology available to them. Computer literacy will provide students with skills they need to succeed
BUILDING PURPOSE In today s society, it is critical for students to be able to use the vast amount of technology available to them. Computer literacy will provide students with skills they need to succeed
Lectures 9 Advanced Operating Systems Fundamental Security. Computer Systems Administration TE2003
 Lectures 9 Advanced Operating Systems Fundamental Security Computer Systems Administration TE2003 Lecture overview At the end of lecture 9 students can identify, describe and discuss: Main factors while
Lectures 9 Advanced Operating Systems Fundamental Security Computer Systems Administration TE2003 Lecture overview At the end of lecture 9 students can identify, describe and discuss: Main factors while
SSL VPN Technology White Paper
 SSL VPN Technology White Paper Keywords: SSL VPN, HTTPS, Web access, TCP access, IP access Abstract: SSL VPN is an emerging VPN technology based on HTTPS. This document describes its implementation and
SSL VPN Technology White Paper Keywords: SSL VPN, HTTPS, Web access, TCP access, IP access Abstract: SSL VPN is an emerging VPN technology based on HTTPS. This document describes its implementation and
Airtel PC Secure Trouble Shooting Guide
 Airtel PC Secure Trouble Shooting Guide Table of Contents Questions before installing the software Q: What is required from my PC to be able to use the Airtel PC Secure? Q: Which operating systems does
Airtel PC Secure Trouble Shooting Guide Table of Contents Questions before installing the software Q: What is required from my PC to be able to use the Airtel PC Secure? Q: Which operating systems does
Systems and Principles Unit Syllabus
 Systems and Principles Unit Syllabus Level 2 Install, configure and maintain software 7540-230 www.cityandguilds.com September 2010 Version 1.0 About City & Guilds City & Guilds is the UK s leading provider
Systems and Principles Unit Syllabus Level 2 Install, configure and maintain software 7540-230 www.cityandguilds.com September 2010 Version 1.0 About City & Guilds City & Guilds is the UK s leading provider
Word Processing programs and their uses
 Word Processing programs and their uses An application that provides extensive tools for creating all kinds of text based programs. They are not limited to working with text and enable you to add images
Word Processing programs and their uses An application that provides extensive tools for creating all kinds of text based programs. They are not limited to working with text and enable you to add images
Computer Viruses: How to Avoid Infection
 Viruses From viruses to worms to Trojan Horses, the catchall term virus describes a threat that's been around almost as long as computers. These rogue programs exist for the simple reason to cause you
Viruses From viruses to worms to Trojan Horses, the catchall term virus describes a threat that's been around almost as long as computers. These rogue programs exist for the simple reason to cause you
ESET NOD32 Antivirus 4 for Linux Desktop. Quick Start Guide
 ESET NOD32 Antivirus 4 for Linux Desktop Quick Start Guide ESET NOD32 Antivirus 4 provides state-of-the-art protection for your computer against malicious code. Based on the ThreatSense scanning engine
ESET NOD32 Antivirus 4 for Linux Desktop Quick Start Guide ESET NOD32 Antivirus 4 provides state-of-the-art protection for your computer against malicious code. Based on the ThreatSense scanning engine
Integration and Streaming Guide
 www.novell.com/documentation Integration and Streaming Guide ZENworks Application Virtualization 11.2 January 2016 Legal Notices Novell, Inc., makes no representations or warranties with respect to the
www.novell.com/documentation Integration and Streaming Guide ZENworks Application Virtualization 11.2 January 2016 Legal Notices Novell, Inc., makes no representations or warranties with respect to the
Securing end-user mobile devices in the enterprise
 IBM Global Technology Services Thought Leadership White Paper January 2012 Securing end-user mobile devices in the enterprise Develop an enforceable mobile security policy and practices for safer corporate
IBM Global Technology Services Thought Leadership White Paper January 2012 Securing end-user mobile devices in the enterprise Develop an enforceable mobile security policy and practices for safer corporate
MICROSOFT SOFTWARE LICENSE AGREEMENT WINDOWS EMBEDDED 8 STANDARD
 MICROSOFT SOFTWARE LICENSE AGREEMENT WINDOWS EMBEDDED 8 STANDARD Thank you for choosing a device preinstalled with Windows Embedded 8 Standard. This is a license agreement between you and [OEM]. This agreement
MICROSOFT SOFTWARE LICENSE AGREEMENT WINDOWS EMBEDDED 8 STANDARD Thank you for choosing a device preinstalled with Windows Embedded 8 Standard. This is a license agreement between you and [OEM]. This agreement
Service Description: Dell Preventive Maintenance
 Service Description: Preventive Maintenance Service Provider. Canada Inc. ( ), 155 Gordon Baker Road, North York, ON M2H 3N5. Terms and Conditions. is pleased to provide these in accordance with this Description
Service Description: Preventive Maintenance Service Provider. Canada Inc. ( ), 155 Gordon Baker Road, North York, ON M2H 3N5. Terms and Conditions. is pleased to provide these in accordance with this Description
Application Software
 PowerPoint Presentation to Accompany Chapter 2 Application Software Objectives 1. Identify the types and uses of business productivity software. 2. Identify types and uses of personal software. 3. Assess
PowerPoint Presentation to Accompany Chapter 2 Application Software Objectives 1. Identify the types and uses of business productivity software. 2. Identify types and uses of personal software. 3. Assess
Sage 100 ERP. Installation and System Administrator s Guide
 Sage 100 ERP Installation and System Administrator s Guide This is a publication of Sage Software, Inc. Version 2014 Copyright 2013 Sage Software, Inc. All rights reserved. Sage, the Sage logos, and the
Sage 100 ERP Installation and System Administrator s Guide This is a publication of Sage Software, Inc. Version 2014 Copyright 2013 Sage Software, Inc. All rights reserved. Sage, the Sage logos, and the
Technology in Action. Alan Evans Kendall Martin Mary Anne Poatsy. Eleventh Edition. Copyright 2015 Pearson Education, Inc.
 Technology in Action Alan Evans Kendall Martin Mary Anne Poatsy Eleventh Edition Technology in Action Chapter 4 System Software: The Operating System, Utility Programs, and File Management. Chapter Topics
Technology in Action Alan Evans Kendall Martin Mary Anne Poatsy Eleventh Edition Technology in Action Chapter 4 System Software: The Operating System, Utility Programs, and File Management. Chapter Topics
Curriculum Map (Computer Technology 9 th grade)
 Curriculum Map (Computer Technology 9 th grade) Month August Main Concept (General terms) Operating Systems. 1. What is the difference between operating system software and Application Software 3. Print
Curriculum Map (Computer Technology 9 th grade) Month August Main Concept (General terms) Operating Systems. 1. What is the difference between operating system software and Application Software 3. Print
2. From a control perspective, the PRIMARY objective of classifying information assets is to:
 MIS5206 Week 13 Your Name Date 1. When conducting a penetration test of an organization's internal network, which of the following approaches would BEST enable the conductor of the test to remain undetected
MIS5206 Week 13 Your Name Date 1. When conducting a penetration test of an organization's internal network, which of the following approaches would BEST enable the conductor of the test to remain undetected
Lesson Plans Microsoft s Managing and Maintaining a Microsoft Windows Server 2003 Environment
 Lesson Plans Microsoft s Managing and Maintaining a Microsoft Windows Server 2003 Environment (Exam 70-290) Table of Contents Table of Contents... 1 Course Overview... 2 Section 0-1: Introduction... 4
Lesson Plans Microsoft s Managing and Maintaining a Microsoft Windows Server 2003 Environment (Exam 70-290) Table of Contents Table of Contents... 1 Course Overview... 2 Section 0-1: Introduction... 4
COMPUTER SKILLS PLACEMENT TEST QUESTIONS MS OFFICE 2010/WINDOWS 7
 COMPUTER SKILLS PLACEMENT TEST QUESTIONS MS OFFICE 2010/WINDOWS 7 CPS Assessment Test Questions/Answers DCCCD Spring 2014 The Computer Skills Placement Test (CSP) is designed to assess the computer literacy
COMPUTER SKILLS PLACEMENT TEST QUESTIONS MS OFFICE 2010/WINDOWS 7 CPS Assessment Test Questions/Answers DCCCD Spring 2014 The Computer Skills Placement Test (CSP) is designed to assess the computer literacy
C6 Easy Imaging Total Computer Backup. User Guide
 C6 Easy Imaging Total Computer Backup User Guide Clickfree and the Clickfree logo are trademarks or registered trademarks of Storage Appliance Corporation. Other product names used in this guide are recognized
C6 Easy Imaging Total Computer Backup User Guide Clickfree and the Clickfree logo are trademarks or registered trademarks of Storage Appliance Corporation. Other product names used in this guide are recognized
Protect & License an Excel Workbook
 Protect & License an Excel Workbook Excel Software www.excelsoftware.com There are several ways to protect, license and sell an Excel workbook as a protected product with computer unique activation. The
Protect & License an Excel Workbook Excel Software www.excelsoftware.com There are several ways to protect, license and sell an Excel workbook as a protected product with computer unique activation. The
Remove ANY TOOLBAR from Internet Explorer, Firefox and Chrome
 Remove ANY TOOLBAR from Internet Explorer, Firefox and Chrome Browser toolbars have been around for years, however, in the last couple of months they became a huge mess. Unfortunately, lots of free software
Remove ANY TOOLBAR from Internet Explorer, Firefox and Chrome Browser toolbars have been around for years, however, in the last couple of months they became a huge mess. Unfortunately, lots of free software
How to Print Using the PrinterOn Hosted Service & FAQs
 How to Print Using the PrinterOn Hosted Service & FAQs Version 1.0 February 2013 1. How to Print with PrinterOn... 3 1.1. Email Printing... 3 1.2. Web Portal Printing... 3 1.3. Mobile Apps... 3 1.4. PrintWhere
How to Print Using the PrinterOn Hosted Service & FAQs Version 1.0 February 2013 1. How to Print with PrinterOn... 3 1.1. Email Printing... 3 1.2. Web Portal Printing... 3 1.3. Mobile Apps... 3 1.4. PrintWhere
A+ Guide to Software: Managing, Maintaining, and Troubleshooting, 5e. Chapter 3 Installing Windows
 : Managing, Maintaining, and Troubleshooting, 5e Chapter 3 Installing Windows Objectives How to plan a Windows installation How to install Windows Vista How to install Windows XP How to install Windows
: Managing, Maintaining, and Troubleshooting, 5e Chapter 3 Installing Windows Objectives How to plan a Windows installation How to install Windows Vista How to install Windows XP How to install Windows
What you need to know to keep your computer safe on the Internet
 What you need to know to keep your computer safe on the Internet Tip 1: Always install Operating System updates The most important steps for any computer user is to always install updates, especially security
What you need to know to keep your computer safe on the Internet Tip 1: Always install Operating System updates The most important steps for any computer user is to always install updates, especially security
VeriSign PKI Client Government Edition v 1.5. VeriSign PKI Client Government. VeriSign PKI Client VeriSign, Inc. Government.
 END USER S GUIDE VeriSign PKI Client Government Edition v 1.5 End User s Guide VeriSign PKI Client Government Version 1.5 Administrator s Guide VeriSign PKI Client VeriSign, Inc. Government Copyright 2010
END USER S GUIDE VeriSign PKI Client Government Edition v 1.5 End User s Guide VeriSign PKI Client Government Version 1.5 Administrator s Guide VeriSign PKI Client VeriSign, Inc. Government Copyright 2010
Applications Software: Getting the Work Done. Chapter 2
 Applications Software: Getting the Work Done Chapter 2 Objectives Distinguish between operating systems and applications software List the various methods by which individuals and businesses acquire software
Applications Software: Getting the Work Done Chapter 2 Objectives Distinguish between operating systems and applications software List the various methods by which individuals and businesses acquire software
Google Apps to Office 365 for business
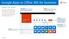 Google Apps to Office 365 for business Make the switch Office 365 for business looks different from Google Apps, so when you sign in, you ll get this view to get you started. You can choose your start
Google Apps to Office 365 for business Make the switch Office 365 for business looks different from Google Apps, so when you sign in, you ll get this view to get you started. You can choose your start
Symantec AntiVirus Corporate Edition Patch Update
 Symantec AntiVirus Corporate Edition Patch Update Symantec AntiVirus Corporate Edition Update Documentation version 10.0.1.1007 Copyright 2005 Symantec Corporation. All rights reserved. Symantec, the Symantec
Symantec AntiVirus Corporate Edition Patch Update Symantec AntiVirus Corporate Edition Update Documentation version 10.0.1.1007 Copyright 2005 Symantec Corporation. All rights reserved. Symantec, the Symantec
System Administrator Guide
 System Administrator Guide Webroot Software, Inc. PO Box 19816 Boulder, CO 80308 www.webroot.com Version 3.5 Webroot AntiSpyware Corporate Edition System Administrator Guide Version 3.5 2007 Webroot Software,
System Administrator Guide Webroot Software, Inc. PO Box 19816 Boulder, CO 80308 www.webroot.com Version 3.5 Webroot AntiSpyware Corporate Edition System Administrator Guide Version 3.5 2007 Webroot Software,
Spyware Doctor Enterprise Technical Data Sheet
 Spyware Doctor Enterprise Technical Data Sheet The Best of Breed Anti-Spyware Solution for Businesses Spyware Doctor Enterprise builds on the strength of the industry-leading and multi award-winning Spyware
Spyware Doctor Enterprise Technical Data Sheet The Best of Breed Anti-Spyware Solution for Businesses Spyware Doctor Enterprise builds on the strength of the industry-leading and multi award-winning Spyware
Windows Operating Systems. Basic Security
 Windows Operating Systems Basic Security Objectives Explain Windows Operating System (OS) common configurations Recognize OS related threats Apply major steps in securing the OS Windows Operating System
Windows Operating Systems Basic Security Objectives Explain Windows Operating System (OS) common configurations Recognize OS related threats Apply major steps in securing the OS Windows Operating System
Free and Legal Software You Can Download By Tom Krauser
 Free and Legal Software You Can Download By Tom Krauser Here is a list of free programs that you can download for your personal use. They are legal and free for you to install. Some may have restrictions
Free and Legal Software You Can Download By Tom Krauser Here is a list of free programs that you can download for your personal use. They are legal and free for you to install. Some may have restrictions
Symantec Endpoint Protection (SEP) 11.0 Configuring the SEP Client for Self-Protection
 SYMANTEC TECHNOLOGY NETWORK: SECURITY Symantec Endpoint Protection (SEP) 11.0 Configuring the SEP Client for Self-Protection Purpose of this Whitepaper:... 3 Overview... 4 The SEP Client Interface... 5
SYMANTEC TECHNOLOGY NETWORK: SECURITY Symantec Endpoint Protection (SEP) 11.0 Configuring the SEP Client for Self-Protection Purpose of this Whitepaper:... 3 Overview... 4 The SEP Client Interface... 5
Mobile Print/Scan Guide for Brother iprint&scan
 Mobile Print/Scan Guide for Brother iprint&scan Version G ENG Definitions of notes We use the following icon throughout this user s guide: Notes tell you how you should respond to a situation that may
Mobile Print/Scan Guide for Brother iprint&scan Version G ENG Definitions of notes We use the following icon throughout this user s guide: Notes tell you how you should respond to a situation that may
Junos Pulse for Google Android
 Junos Pulse for Google Android User Guide Release 4.0 October 2012 R1 Copyright 2012, Juniper Networks, Inc. Juniper Networks, Junos, Steel-Belted Radius, NetScreen, and ScreenOS are registered trademarks
Junos Pulse for Google Android User Guide Release 4.0 October 2012 R1 Copyright 2012, Juniper Networks, Inc. Juniper Networks, Junos, Steel-Belted Radius, NetScreen, and ScreenOS are registered trademarks
Salesforce Classic Guide for iphone
 Salesforce Classic Guide for iphone Version 37.0, Summer 16 @salesforcedocs Last updated: July 12, 2016 Copyright 2000 2016 salesforce.com, inc. All rights reserved. Salesforce is a registered trademark
Salesforce Classic Guide for iphone Version 37.0, Summer 16 @salesforcedocs Last updated: July 12, 2016 Copyright 2000 2016 salesforce.com, inc. All rights reserved. Salesforce is a registered trademark
ADP Workforce Now V3.0
 ADP Workforce Now V3.0 Manual What s New Checks in and Custom ADP Reporting Grids V12 Instructor Handout Manual Guide V10171180230WFN3 V09171280269ADPR12 2011 2012 ADP, Inc. ADP s Trademarks The ADP Logo
ADP Workforce Now V3.0 Manual What s New Checks in and Custom ADP Reporting Grids V12 Instructor Handout Manual Guide V10171180230WFN3 V09171280269ADPR12 2011 2012 ADP, Inc. ADP s Trademarks The ADP Logo
Willem Wiechers 3 rd March 2015
 Willem Wiechers 3 rd March 2015 1 Why do we want Malware & Virus Protection? To make our computers save Wish to keep our data private Wish to have a safe environment to do our online banking, shopping,
Willem Wiechers 3 rd March 2015 1 Why do we want Malware & Virus Protection? To make our computers save Wish to keep our data private Wish to have a safe environment to do our online banking, shopping,
Norman Security Portal
 User Guide Norman Security Portal SECURITY PORTAL Features Cloud-based endpoint management Managed & unmanaged customers Generate client software Statistics & reports Security Module Antivirus & Antispyware
User Guide Norman Security Portal SECURITY PORTAL Features Cloud-based endpoint management Managed & unmanaged customers Generate client software Statistics & reports Security Module Antivirus & Antispyware
EZblue BusinessServer The All - In - One Server For Your Home And Business
 EZblue BusinessServer The All - In - One Server For Your Home And Business Quick Start Guide Version 3.11 1 2 3 EZblue Server Overview EZblue Server Installation EZblue Server Configuration 4 EZblue Magellan
EZblue BusinessServer The All - In - One Server For Your Home And Business Quick Start Guide Version 3.11 1 2 3 EZblue Server Overview EZblue Server Installation EZblue Server Configuration 4 EZblue Magellan
Ricoh HotSpot. Printing App. User s Guide. HotSpot Printing App supports:
 Ricoh HotSpot Printing App Mobile Printing Solution HotSpot Printing App supports: HSPA_UQR_April192013_V1 - Apple ios devices - Android devices - BlackBerry smartphone - BlackBerry PlayBook Printing App
Ricoh HotSpot Printing App Mobile Printing Solution HotSpot Printing App supports: HSPA_UQR_April192013_V1 - Apple ios devices - Android devices - BlackBerry smartphone - BlackBerry PlayBook Printing App
isecuremail User Guide for iphone
 isecuremail User Guide for iphone Page 1 CONTENTS Chapter 1: Welcome... 4 Chapter 2: Getting Started... 5 Compatability... 5 Preliminary Steps... 5 Setting up a POP3 / IMAP4/ Exchange Email Account...
isecuremail User Guide for iphone Page 1 CONTENTS Chapter 1: Welcome... 4 Chapter 2: Getting Started... 5 Compatability... 5 Preliminary Steps... 5 Setting up a POP3 / IMAP4/ Exchange Email Account...
Serif PagePlusX4. Group Listing
 File Menu New Startup Wizard New Publication New Book Open File Open Browse Files Browse Revert Close File Save Save As Save As Package Export As Picture Properties Page Setup Layout Guides Print Print
File Menu New Startup Wizard New Publication New Book Open File Open Browse Files Browse Revert Close File Save Save As Save As Package Export As Picture Properties Page Setup Layout Guides Print Print
Pcounter Mobile Guide
 Pcounter Mobile Guide Pcounter Mobile Guide 2012.06.22 Page 1 of 19 1. Overview... 3 2. Pre-requisites and Requirements... 4 2.1 Gateway server requirements... 4 2.2 Mobile device requirements... 4 2.3
Pcounter Mobile Guide Pcounter Mobile Guide 2012.06.22 Page 1 of 19 1. Overview... 3 2. Pre-requisites and Requirements... 4 2.1 Gateway server requirements... 4 2.2 Mobile device requirements... 4 2.3
Trend Micro Incorporated reserves the right to make changes to this document and to the products described herein without notice.
 Trend Micro Incorporated reserves the right to make changes to this document and to the products described herein without notice. Before installing and using the software, please review the readme files,
Trend Micro Incorporated reserves the right to make changes to this document and to the products described herein without notice. Before installing and using the software, please review the readme files,
Symantec Mail Security for Domino
 Getting Started Symantec Mail Security for Domino About Symantec Mail Security for Domino Symantec Mail Security for Domino is a complete, customizable, and scalable solution that scans Lotus Notes database
Getting Started Symantec Mail Security for Domino About Symantec Mail Security for Domino Symantec Mail Security for Domino is a complete, customizable, and scalable solution that scans Lotus Notes database
Table of Contents. Part I Welcome. Part II Introduction. Part III Getting Started. Part IV The User Interface. Part V Quick Start Tutorials
 Contents I Table of Contents Part I Welcome 5 Part II Introduction 5 1 Overview... 5 2 Product... Levels 5 3 Technical... Support 6 4 Copyright... 7 Part III Getting Started 7 1 Installation... 7 2 Register...
Contents I Table of Contents Part I Welcome 5 Part II Introduction 5 1 Overview... 5 2 Product... Levels 5 3 Technical... Support 6 4 Copyright... 7 Part III Getting Started 7 1 Installation... 7 2 Register...
How To Use The Policy Patrol Archiver Server
 POLICY PATROL ARCHIVER FOR ADMINISTRATORS Manual MANUAL Policy Patrol Archiver For Administrators This manual, and the software described in this manual, are copyrighted. No part of this manual or the
POLICY PATROL ARCHIVER FOR ADMINISTRATORS Manual MANUAL Policy Patrol Archiver For Administrators This manual, and the software described in this manual, are copyrighted. No part of this manual or the
the computer manufacturer that distributes the software with the computer, or
 MICROSOFT SOFTWARE LICENSE TERMS WINDOWS 7 STARTER These license terms are an agreement between you and the computer manufacturer that distributes the software with the computer, or the software installer
MICROSOFT SOFTWARE LICENSE TERMS WINDOWS 7 STARTER These license terms are an agreement between you and the computer manufacturer that distributes the software with the computer, or the software installer
Computer Skills Checklist 1
 Computer Checklist 1 Computer User Levels 1 The following skills checklist is organized according to program title and categorized into three levels of computer literacy:,, and. users demonstrate little
Computer Checklist 1 Computer User Levels 1 The following skills checklist is organized according to program title and categorized into three levels of computer literacy:,, and. users demonstrate little
AD Self-Service Suite for Active Directory
 The Dot Net Factory AD Self-Service Suite for Active Directory Version 3.6 The Dot Net Factory, LLC. 2005-2011. All rights reserved. This guide contains proprietary information, which is protected by copyright.
The Dot Net Factory AD Self-Service Suite for Active Directory Version 3.6 The Dot Net Factory, LLC. 2005-2011. All rights reserved. This guide contains proprietary information, which is protected by copyright.
WHAT S NEW IN WORD 2010 & HOW TO CUSTOMIZE IT
 WHAT S NEW IN WORD 2010 & HOW TO CUSTOMIZE IT The Ribbon... 2 Default Tabs... 2 Contextual Tabs... 2 Minimizing and Restoring the Ribbon... 3 Customizing the Ribbon... 3 A New Graphic Interface... 5 Live
WHAT S NEW IN WORD 2010 & HOW TO CUSTOMIZE IT The Ribbon... 2 Default Tabs... 2 Contextual Tabs... 2 Minimizing and Restoring the Ribbon... 3 Customizing the Ribbon... 3 A New Graphic Interface... 5 Live
This manual will help you connect your Microsoft Windows XP, Vista, or 7, or Apple OS X computer to the University of Maryland campus data network.
 This manual will help you connect your Microsoft Windows XP, Vista, or 7, or Apple OS X computer to the University of Maryland campus data network. Prerequisites for Network Registration: 1. In order to
This manual will help you connect your Microsoft Windows XP, Vista, or 7, or Apple OS X computer to the University of Maryland campus data network. Prerequisites for Network Registration: 1. In order to
Sophos Computer Security Scan startup guide
 Sophos Computer Security Scan startup guide Product version: 1.0 Document date: February 2010 Contents 1 About the software...3 2 What do I need to do?...3 3 Prepare for scanning...3 4 Install the software...4
Sophos Computer Security Scan startup guide Product version: 1.0 Document date: February 2010 Contents 1 About the software...3 2 What do I need to do?...3 3 Prepare for scanning...3 4 Install the software...4
Avira Rescue System. HowTo
 Avira Rescue System HowTo Table of contents 1. Introduction... 3 2. System Requirements... 4 3. Product availability... 4 4. Product features... 5 5. Using the Rescue System... 6 5.1 The BIOS setup...6
Avira Rescue System HowTo Table of contents 1. Introduction... 3 2. System Requirements... 4 3. Product availability... 4 4. Product features... 5 5. Using the Rescue System... 6 5.1 The BIOS setup...6
Symantec Backup Exec TM 11d for Windows Servers. Quick Installation Guide
 Symantec Backup Exec TM 11d for Windows Servers Quick Installation Guide September 2006 Symantec Legal Notice Copyright 2006 Symantec Corporation. All rights reserved. Symantec, Backup Exec, and the Symantec
Symantec Backup Exec TM 11d for Windows Servers Quick Installation Guide September 2006 Symantec Legal Notice Copyright 2006 Symantec Corporation. All rights reserved. Symantec, Backup Exec, and the Symantec
PrinterOn Mobile App for ios and Android
 PrinterOn Mobile App for ios and Android User Guide Version 3.4 Contents Chapter 1: Getting started... 4 Features of the PrinterOn Mobile App... 4 Support for PrinterOn Secure Release Anywhere printer
PrinterOn Mobile App for ios and Android User Guide Version 3.4 Contents Chapter 1: Getting started... 4 Features of the PrinterOn Mobile App... 4 Support for PrinterOn Secure Release Anywhere printer
Question: 1 You type a document and you want to insert header from third page. Which of the following technique will you use to accomplish the task?
 Question: 1 You type a document and you want to insert header from third page. Which of the following technique will you use to accomplish the task? A. Go to the third page and insert header. B. Use a
Question: 1 You type a document and you want to insert header from third page. Which of the following technique will you use to accomplish the task? A. Go to the third page and insert header. B. Use a
MCTS Guide to Microsoft Windows 7. Chapter 7 Windows 7 Security Features
 MCTS Guide to Microsoft Windows 7 Chapter 7 Windows 7 Security Features Objectives Describe Windows 7 Security Improvements Use the local security policy to secure Windows 7 Enable auditing to record security
MCTS Guide to Microsoft Windows 7 Chapter 7 Windows 7 Security Features Objectives Describe Windows 7 Security Improvements Use the local security policy to secure Windows 7 Enable auditing to record security
VERITAS Backup Exec TM 10.0 for Windows Servers
 VERITAS Backup Exec TM 10.0 for Windows Servers Quick Installation Guide N134418 July 2004 Disclaimer The information contained in this publication is subject to change without notice. VERITAS Software
VERITAS Backup Exec TM 10.0 for Windows Servers Quick Installation Guide N134418 July 2004 Disclaimer The information contained in this publication is subject to change without notice. VERITAS Software
User's Manual. Intego VirusBarrier Server 2 / VirusBarrier Mail Gateway 2 User's Manual Page 1
 User's Manual Intego VirusBarrier Server 2 / VirusBarrier Mail Gateway 2 User's Manual Page 1 VirusBarrier Server 2 and VirusBarrier Mail Gateway 2 for Macintosh 2008 Intego. All Rights Reserved Intego
User's Manual Intego VirusBarrier Server 2 / VirusBarrier Mail Gateway 2 User's Manual Page 1 VirusBarrier Server 2 and VirusBarrier Mail Gateway 2 for Macintosh 2008 Intego. All Rights Reserved Intego
Free Presentations thanks to Avast Software Norbert (Bob) Gostischa (505) 250-1089 bob3160@gmail.com Presentations started on Dec 1, 2010 in AZ
 Free Presentations thanks to Avast Software Norbert (Bob) Gostischa (505) 250-1089 bob3160@gmail.com Presentations started on Dec 1, 2010 in AZ So You ve got a New Computer Now What? I promised I would
Free Presentations thanks to Avast Software Norbert (Bob) Gostischa (505) 250-1089 bob3160@gmail.com Presentations started on Dec 1, 2010 in AZ So You ve got a New Computer Now What? I promised I would
What is a Virus? What is a Worm? What is a Trojan Horse? How do worms and other viruses spread? Viruses on the Network. Reducing your virus Risk.
 C/W MARS INC. What is a Virus? What is a Worm? What is a Trojan Horse? How do worms and other viruses spread? Viruses on the Network. Reducing your virus Risk. Prevent Future Infections. Non-Booting System!
C/W MARS INC. What is a Virus? What is a Worm? What is a Trojan Horse? How do worms and other viruses spread? Viruses on the Network. Reducing your virus Risk. Prevent Future Infections. Non-Booting System!
