Reinventing Our User Database in SirsiDynix Unicorn. March 5, 2010 Paula Deutsch Marilyn White
|
|
|
- Chad Bryce Banks
- 7 years ago
- Views:
Transcription
1 Reinventing Our User Database in SirsiDynix Unicorn March 5, 2010 Paula Deutsch Marilyn White
2 Who We Are National Institute of Standards & Technology Gaithersburg Campus NIST's mission is to promote U.S. innovation and industrial competitiveness by advancing measurement science, standards, and technology in ways that enhance economic security and improve our quality of life.
3 Our Customers, Ourselves Our Customers Primarily, the researchers in the NIST laboratory programs at the Gaithersburg location Approximately 1,500 NIST researchers Approximately 1,700 guest researchers and postdoctoral students Physical, chemical, and engineering scientists
4 Our Customers, Ourselves Ourselves Information Services Division Research Library and Information Group Electronic Information and Publications Group NIST Museum and History Program
5 NIST and Cyber Security NIST is charged with developing information security standards and guidelines for non-national security federal information systems.
6 Implementing Security at NIST 1. Categorization: determine the need to protect information stored on a system based on requirements to maintain confidentiality, integrity, and availability 2. Selection of controls: determine the appropriate security controls based on that need for protection 3. Continuous monitoring
7 How This Impacts Us Need to be careful about what information lives on our ILS Maintaining our certification to be on the public network requires continuous effort
8 Once Upon A Time We received a regular data dump for populating our user database: UserID based on NIST badge number Bi-weekly updates Very kludgy system for getting that data into the user database But it worked And it was automated (mostly)
9 When All of a Sudden As concerns about physical security heightened, our security office stopped providing us badge information.
10 Hobbling Along An increasingly manual process Users created and updated on the fly Badges (and badge numbers) replaced periodically Format of badge numbers constantly changing so users are no longer sure which number to use Numbers on badges are not barcoded (can not be scanned into ILS)
11 Waiting for LDAP We kept waiting for LDAP (Lightweight Directory Access Protocol) / Our LDAP story
12 Self-Checkout Woes Began with a 3M system in the late 90 s (big improvement at the time ) Became increasingly unreliable Communication with Unicorn server via telnet Moved to a stripped down Workflows workstation (big improvement at the time ) Too easy to enter wrong user ID Java client much less amenable to this role
13 Reinvention We needed to rethink our whole approach
14 Chapter 1: Define the Issues Data source Identify a new source for our data Devise method for importing data User-friendly user IDs Base user IDs on something that stays constant Provide means for customers to scan user IDs during self-checkout Make user IDs easy to type when customers don t have a scanner (in their offices) User-friendly self-checkout station
15 Chapter 2: Find Solutions Begins with teamwork! We used a cross functional group which brought together staff from across the Information Services Division: System Administration (2) Public Services (4) Current and former circulation staff (3) Reference Librarian (1)
16 Team Tasks Select a new self check-out system Assist with migration to new user database Design procedure for creating passwords Determine means for distributing to customers their user ID as a barcode Train front-end staff on new procedures Market new equipment and procedures to customers
17 Selecting a System (1) Requirements Fully supported by SirsiDynix (from setup to regular maintenance) Reliable scanner that easily reads barcodes that are not in consistent areas on objects No moving parts Linear scanner Stationary and trigger activated
18 Selecting a System (2) Requirements (cont.) Touch screen monitor (ability to enter user IDs) Hardware that can be configured to NIST s secure desktop requirements Easily customizable Ability to add hardware for future needs (e.g. card readers)
19 Systems Considered Envisionware 3M SelfCheck BCS system ITG Apex XpressCheck
20 System comparisons. Unit Physical options Scanner: linear or moving Reads differently placed barcodes SirsiDynix supported Touch Screen Ease of use Easy to customize Customer Service Other EnvisionWare Free standing, counter top, or no furniture Linear Yes Yes Yes Has static screens to guide user Can customize with html Goodbeen around longest Uses remote messaging; store and forward app. ITG Apex XpressCheck Free standing, counter top, or no furniture Lineartrigger or stationary Yes Yes Yes Uses animations Customize with point and click apps Good 3M BCS Free standing, counter top, or no furniture Has moving partsfixed scanner Yes Yes Yes?? Good
21 Chapter 3: Implement the Solutions Simultaneous activities: Implement new self-checkout Load the new user database Inform our customers
22 Implement Self-Checkout Station Configure hardware to NIST secure desktop settings Make customization decisions Install software (done remotely by SirsiDynix) Distribute library cards to customers
23 Populating Our User Database We needed to find a data source for our user database
24 Clean Up Existing User Database Use reports to remove as much as possible (e.g. outdated requests) Manually remove any checkouts and charge items to missing Run report to remove expired users
25 Crosswalk the Data Identify fields that will move directly from NIST s people database to ILS user database Identify what data requires an interpretation process before moving it into ILS user database
26 Match Up the Data Use API tools to extract user data from Unicorn All data required to load records (user ID, library, user profile, name) All potential match points Drop ILS user data and NIST people data into Access database Run queries to find sure matches Manually examine non-matching records
27 Prepare Data for Loading Manually add data where automated queries are inconclusive Use Access reports to create required format for loading into ILS (see Record Formatting Guide, rec_format_guide_gl33.pdf, Client Care site)
28 Load User Data Copy file to Xfer directory on Unicorn server (/s/sirsi/unicorn/xfer) Run Load Users Report
29 Chapter 4: Maintaining the User Database NIST people database will be updated bi-weekly Data will be extracted by querying the Oracle people database Script will be run to format data for Load Users Report
30 Epilog: Lessons Learned Self-checkout software IT security requirements Database handshaking It s Complicated! Physical security requirements NIST databases Customer convenience Circulation staff preferences Self-checkout hardware ILS requirements
31 Moral of the Story It takes a village!
32 Thank You! Questions? Paula Deutsch Marilyn White
Team Quicken Loans: Mobile RFID Inventory Tracking System. Administrator Manual
 Team Quicken Loans: Mobile RFID Inventory Tracking System Administrator Manual TABLE OF CONTENTS Mobile RFID Inventory Tracking System Admin Manual What s the Mobile RFID Inventory Tracking System?...
Team Quicken Loans: Mobile RFID Inventory Tracking System Administrator Manual TABLE OF CONTENTS Mobile RFID Inventory Tracking System Admin Manual What s the Mobile RFID Inventory Tracking System?...
JASI / SirsiDynix Glossary of Terms
 JASI / SirsiDynix Glossary of Terms Symphony The JASI ILS server software as you know it today. The nucleus of SirsiDynix s new, holistic library technology platform named Symphony is an open, versatile,
JASI / SirsiDynix Glossary of Terms Symphony The JASI ILS server software as you know it today. The nucleus of SirsiDynix s new, holistic library technology platform named Symphony is an open, versatile,
Version 1.0 09/10. Xerox ColorQube 9301/9302/9303 Internet Services
 Version 1.0 09/10 Xerox ColorQube 9301/9302/9303 2010 Xerox Corporation. All Rights Reserved. Unpublished rights reserved under the copyright laws of the United States. Contents of this publication may
Version 1.0 09/10 Xerox ColorQube 9301/9302/9303 2010 Xerox Corporation. All Rights Reserved. Unpublished rights reserved under the copyright laws of the United States. Contents of this publication may
TIME AND ATTENDANCE MANAGEMENT WEB
 I N F I N I T Y Z U C C H E T T I TIME AND ATTENDANCE MANAGEMENT WEB TIME AND ATTENDANCE MANAGEMENT WEB The first ever entirely web-based attendance management application Time and Attendance Management
I N F I N I T Y Z U C C H E T T I TIME AND ATTENDANCE MANAGEMENT WEB TIME AND ATTENDANCE MANAGEMENT WEB The first ever entirely web-based attendance management application Time and Attendance Management
Acunetix Web Vulnerability Scanner. Getting Started. By Acunetix Ltd.
 Acunetix Web Vulnerability Scanner Getting Started V8 By Acunetix Ltd. 1 Starting a Scan The Scan Wizard allows you to quickly set-up an automated scan of your website. An automated scan provides a comprehensive
Acunetix Web Vulnerability Scanner Getting Started V8 By Acunetix Ltd. 1 Starting a Scan The Scan Wizard allows you to quickly set-up an automated scan of your website. An automated scan provides a comprehensive
Pendragon Forms Industrial
 Pendragon Forms Industrial Version 7 Installation & Reference Guide for Android Devices Contents What Is Pendragon Forms Industrial?... 2 Installing Pendragon Forms Industrial... 2 Installing Pendragon
Pendragon Forms Industrial Version 7 Installation & Reference Guide for Android Devices Contents What Is Pendragon Forms Industrial?... 2 Installing Pendragon Forms Industrial... 2 Installing Pendragon
Sample Technology Assessment Report
 ABC Company Pty Ltd 123 Sample Street Sample Town, SAMPLE ### Summary of Findings Revenue Generation 1. Web site is limited to one-page description. The organisation has the opportunity to create a more
ABC Company Pty Ltd 123 Sample Street Sample Town, SAMPLE ### Summary of Findings Revenue Generation 1. Web site is limited to one-page description. The organisation has the opportunity to create a more
DiskBoss. File & Disk Manager. Version 2.0. Dec 2011. Flexense Ltd. www.flexense.com info@flexense.com. File Integrity Monitor
 DiskBoss File & Disk Manager File Integrity Monitor Version 2.0 Dec 2011 www.flexense.com info@flexense.com 1 Product Overview DiskBoss is an automated, rule-based file and disk manager allowing one to
DiskBoss File & Disk Manager File Integrity Monitor Version 2.0 Dec 2011 www.flexense.com info@flexense.com 1 Product Overview DiskBoss is an automated, rule-based file and disk manager allowing one to
PaperCut Payment Gateway Module - CBORD Quick Start Guide
 PaperCut Payment Gateway Module - CBORD Quick Start Guide This guide is designed to supplement the Payment Gateway Module documentation and provides a guide to installing, setting up, and testing the Payment
PaperCut Payment Gateway Module - CBORD Quick Start Guide This guide is designed to supplement the Payment Gateway Module documentation and provides a guide to installing, setting up, and testing the Payment
User Manual Inventory Application
 User Manual Inventory Application (Release 1.1) Introduction This application was designed and implemented by Jester Solutions for Dr. John G. McHenry, M.D., M.P.H., P.L.L.C in August 2012. Specifically,
User Manual Inventory Application (Release 1.1) Introduction This application was designed and implemented by Jester Solutions for Dr. John G. McHenry, M.D., M.P.H., P.L.L.C in August 2012. Specifically,
Archiving. Paper Documents
 Archiving Paper Documents Digital Archiving ARCHIVING PAPER BvLArchivio provides you with the option of archiving paper documents either manually or automatically. Both processes are possible in BvLArchivio
Archiving Paper Documents Digital Archiving ARCHIVING PAPER BvLArchivio provides you with the option of archiving paper documents either manually or automatically. Both processes are possible in BvLArchivio
DJIGZO EMAIL ENCRYPTION. Djigzo white paper
 DJIGZO EMAIL ENCRYPTION Djigzo white paper Copyright 2009-2011, djigzo.com. Introduction Most email is sent as plain text. This means that anyone who can intercept email messages, either in transit or
DJIGZO EMAIL ENCRYPTION Djigzo white paper Copyright 2009-2011, djigzo.com. Introduction Most email is sent as plain text. This means that anyone who can intercept email messages, either in transit or
d yn am i c s g p c l i e n t u se r g u i d e Version 4.6.5x
 d yn am i c s g p c l i e n t u se r g u i d e Version 4.6.5x INTRODUCTION KwikTag document imaging software transforms your business documents into digital images. It works the way you work, without complicated
d yn am i c s g p c l i e n t u se r g u i d e Version 4.6.5x INTRODUCTION KwikTag document imaging software transforms your business documents into digital images. It works the way you work, without complicated
Smart Shopping Cart. Group 5. March 11, 2008. Advisor: Professor Haibo He
 Smart Shopping Cart Group 5 March 11, 2008 Advisor: Professor Haibo He ------------------------------ Group Members: Norasyikin Fadilah Siti Fatimah Ahmad Anirudh Argawal Rajwinder Singh Katherine Casella
Smart Shopping Cart Group 5 March 11, 2008 Advisor: Professor Haibo He ------------------------------ Group Members: Norasyikin Fadilah Siti Fatimah Ahmad Anirudh Argawal Rajwinder Singh Katherine Casella
AVALANCHE MC 5.3 AND DATABASE MANAGEMENT SYSTEMS
 AVALANCHE MC 5.3 AND DATABASE MANAGEMENT SYSTEMS Avalanche Mobility Center (MC) offers support for other database management systems (DBMS) as alternatives to the built-in PostgreSQL DBMS. This was prompted
AVALANCHE MC 5.3 AND DATABASE MANAGEMENT SYSTEMS Avalanche Mobility Center (MC) offers support for other database management systems (DBMS) as alternatives to the built-in PostgreSQL DBMS. This was prompted
[INSTALLING THE M2SYS BIOMETRIC SCANNING SYSTEM]
![[INSTALLING THE M2SYS BIOMETRIC SCANNING SYSTEM] [INSTALLING THE M2SYS BIOMETRIC SCANNING SYSTEM]](/thumbs/40/21650001.jpg) Installing the M2SYS BIOMetric Scanning System 2009 Fellowship Technologies, LP [INSTALLING THE M2SYS BIOMETRIC SCANNING SYSTEM] CONSULTING & DELIVERY SERVICES 7/22/2010 1 TABLE OF CONTENTS 2 Figures Index...
Installing the M2SYS BIOMetric Scanning System 2009 Fellowship Technologies, LP [INSTALLING THE M2SYS BIOMETRIC SCANNING SYSTEM] CONSULTING & DELIVERY SERVICES 7/22/2010 1 TABLE OF CONTENTS 2 Figures Index...
How do I Install and Configure MS Remote Desktop for the Haas Terminal Server on my Mac?
 How do I Install and Configure MS Remote Desktop for the Haas Terminal Server on my Mac? In order to connect remotely to a PC computer from your Mac, we recommend the MS Remote Desktop for Mac client.
How do I Install and Configure MS Remote Desktop for the Haas Terminal Server on my Mac? In order to connect remotely to a PC computer from your Mac, we recommend the MS Remote Desktop for Mac client.
External Authentication with CiscoSecure ACS. Authenticating Users Using. SecurAccess Server. by SecurEnvoy
 External Authentication with CiscoSecure ACS Authenticating Users Using SecurAccess Server by SecurEnvoy Contact information SecurEnvoy www.securenvoy.com 0845 2600010 1210 Parkview Arlington Business
External Authentication with CiscoSecure ACS Authenticating Users Using SecurAccess Server by SecurEnvoy Contact information SecurEnvoy www.securenvoy.com 0845 2600010 1210 Parkview Arlington Business
CIPHERMAIL EMAIL ENCRYPTION. CipherMail white paper
 CIPHERMAIL EMAIL ENCRYPTION CipherMail white paper Copyright 2009-2014, ciphermail.com. Introduction Most email is sent as plain text. This means that anyone who can intercept email messages, either in
CIPHERMAIL EMAIL ENCRYPTION CipherMail white paper Copyright 2009-2014, ciphermail.com. Introduction Most email is sent as plain text. This means that anyone who can intercept email messages, either in
Version 1.0 January 2011. Xerox Phaser 3635MFP Extensible Interface Platform
 Version 1.0 January 2011 Xerox Phaser 3635MFP 2011 Xerox Corporation. XEROX and XEROX and Design are trademarks of Xerox Corporation in the United States and/or other countries. Changes are periodically
Version 1.0 January 2011 Xerox Phaser 3635MFP 2011 Xerox Corporation. XEROX and XEROX and Design are trademarks of Xerox Corporation in the United States and/or other countries. Changes are periodically
Appendix A. Functional Requirements: Document Management
 Appendix A. Functional Requirements: Document Management Document Management technology helps organizations better manage the creation, revision, and approval of electronic documents. It provides key features
Appendix A. Functional Requirements: Document Management Document Management technology helps organizations better manage the creation, revision, and approval of electronic documents. It provides key features
How to Setup Scan to SMB to a Microsoft Vista Workstation Using a bizhub C451/ C550
 How to Setup Scan to SMB to a Microsoft Vista Workstation Using a bizhub C451/ C550 Send to the SMB server You can send the data read in from the copier's ADF or the original scanning glass (scanned data)
How to Setup Scan to SMB to a Microsoft Vista Workstation Using a bizhub C451/ C550 Send to the SMB server You can send the data read in from the copier's ADF or the original scanning glass (scanned data)
Outline SSS6422 - Microsoft Windows Server 2008 Hyper-V Virtualization
 Outline SSS6422 - Microsoft Windows Server 2008 Hyper-V Virtualization Duration: Three consecutive Saturdays About this Course This instructor led course teaches students how to implement and manage Windows
Outline SSS6422 - Microsoft Windows Server 2008 Hyper-V Virtualization Duration: Three consecutive Saturdays About this Course This instructor led course teaches students how to implement and manage Windows
NetIQ Access Manager 3.2 integration
 KeyShield SSO NetIQ Access Manager 3.2 integration system integrator documentation ver. 1.0.1 (21. Mar. 2014) Na Pankráci 54, Praha 4 Introduction KeyShield SSO authenticates not only a browser session
KeyShield SSO NetIQ Access Manager 3.2 integration system integrator documentation ver. 1.0.1 (21. Mar. 2014) Na Pankráci 54, Praha 4 Introduction KeyShield SSO authenticates not only a browser session
Fairsail. Implementer. Fairsail to Active Directory Synchronization. Version 1.0 FS-PS-FSAD-IG-201310--R001.00
 Fairsail Implementer Fairsail to Active Directory Synchronization Version 1.0 FS-PS-FSAD-IG-201310--R001.00 Fairsail 2013. All rights reserved. This document contains information proprietary to Fairsail
Fairsail Implementer Fairsail to Active Directory Synchronization Version 1.0 FS-PS-FSAD-IG-201310--R001.00 Fairsail 2013. All rights reserved. This document contains information proprietary to Fairsail
Djigzo email encryption. Djigzo white paper
 Djigzo email encryption Djigzo white paper Copyright 2009-2011, djigzo.com. Introduction Most email is sent as plain text. This means that anyone who can intercept email messages, either in transit or
Djigzo email encryption Djigzo white paper Copyright 2009-2011, djigzo.com. Introduction Most email is sent as plain text. This means that anyone who can intercept email messages, either in transit or
CHAPTER 9: E-COMMERCE SOFTWARE
 MIS 300 FUNDAMENTALS OF E- COMMERCE CHAPTER 9: E-COMMERCE SOFTWARE Electronic Commerce Objectives 2 In this chapter, you will learn about: Finding and evaluating Web hosting services Basic functions of
MIS 300 FUNDAMENTALS OF E- COMMERCE CHAPTER 9: E-COMMERCE SOFTWARE Electronic Commerce Objectives 2 In this chapter, you will learn about: Finding and evaluating Web hosting services Basic functions of
LobbyWorks VMS Configuration and Technical Requirement Survey
 LobbyWorks VMS Configuration and Technical Requirement Survey Initial Date Completed: Revised Date: Sales Person: Name Office Phone: Email Address Title: Mobile Phone: Customer Contact: Name: IT Person:
LobbyWorks VMS Configuration and Technical Requirement Survey Initial Date Completed: Revised Date: Sales Person: Name Office Phone: Email Address Title: Mobile Phone: Customer Contact: Name: IT Person:
Taming a Wild Workflow and Domesticating our Digital Data
 Taming a Wild Workflow and Domesticating our Digital Data Nancy Allmang, nancy.allmang@nist.gov Paula Deutsch, paula.deutsch@nist.gov Information Services Division Technology Services Project Overview
Taming a Wild Workflow and Domesticating our Digital Data Nancy Allmang, nancy.allmang@nist.gov Paula Deutsch, paula.deutsch@nist.gov Information Services Division Technology Services Project Overview
Nessus Agents. October 2015
 Nessus Agents October 2015 Table of Contents Introduction... 3 What Are Nessus Agents?... 3 Scanning... 4 Results... 6 Conclusion... 6 About Tenable Network Security... 6 2 Introduction Today s changing
Nessus Agents October 2015 Table of Contents Introduction... 3 What Are Nessus Agents?... 3 Scanning... 4 Results... 6 Conclusion... 6 About Tenable Network Security... 6 2 Introduction Today s changing
SSO Case Study: The USPS Gives SSO Its Stamp of Approval. May 10, 2005. Wayne Grimes, Manager, Customer Care Operations, USPS
 SSO Case Study: The USPS Gives SSO Its Stamp of Approval Wayne Grimes, Manager, Customer Care Operations, USPS May 10, 2005 Today s topics An overview of the USPS USPS SSO efforts Lessons we learned along
SSO Case Study: The USPS Gives SSO Its Stamp of Approval Wayne Grimes, Manager, Customer Care Operations, USPS May 10, 2005 Today s topics An overview of the USPS USPS SSO efforts Lessons we learned along
Executive Summary On IronWASP
 Executive Summary On IronWASP CYBER SECURITY & PRIVACY FOUNDATION 1 Software Product: IronWASP Description of the Product: IronWASP (Iron Web application Advanced Security testing Platform) is an open
Executive Summary On IronWASP CYBER SECURITY & PRIVACY FOUNDATION 1 Software Product: IronWASP Description of the Product: IronWASP (Iron Web application Advanced Security testing Platform) is an open
PSG College of Technology, Coimbatore-641 004 Department of Computer & Information Sciences BSc (CT) G1 & G2 Sixth Semester PROJECT DETAILS.
 PSG College of Technology, Coimbatore-641 004 Department of Computer & Information Sciences BSc (CT) G1 & G2 Sixth Semester PROJECT DETAILS Project Project Title Area of Abstract No Specialization 1. Software
PSG College of Technology, Coimbatore-641 004 Department of Computer & Information Sciences BSc (CT) G1 & G2 Sixth Semester PROJECT DETAILS Project Project Title Area of Abstract No Specialization 1. Software
Endoscope Tracking System
 Endoscope Tracking System ENDORA Tracking System Workflow Storage: Displays which cabinet the endoscope is in Timestamps when endoscope enters the cabinet Procedure: Links patient ID to endoscope used
Endoscope Tracking System ENDORA Tracking System Workflow Storage: Displays which cabinet the endoscope is in Timestamps when endoscope enters the cabinet Procedure: Links patient ID to endoscope used
State of Tennessee Sourcing Event #9160 ServiceNow Preliminary Statement of Work (SOW)
 State of Tennessee Sourcing Event #9160 ServiceNow Preliminary Statement of Work (SOW) ServiceNow Implementation Project Objectives to be completed are: 1. Aide in optimizing processes and integration
State of Tennessee Sourcing Event #9160 ServiceNow Preliminary Statement of Work (SOW) ServiceNow Implementation Project Objectives to be completed are: 1. Aide in optimizing processes and integration
Installation and Configuration Document Sunflower Mobile Solution: SyncLink and MobileTrak 4.6. Department of Commerce PPMD
 Installation and Configuration Document Sunflower Mobile Solution: SyncLink and MobileTrak 4.6 Department of Commerce PPMD Prepared by Yudiann Carlo October 29, 2010 1.0 Product Overview The Department
Installation and Configuration Document Sunflower Mobile Solution: SyncLink and MobileTrak 4.6 Department of Commerce PPMD Prepared by Yudiann Carlo October 29, 2010 1.0 Product Overview The Department
CareGiver Remote Support Information Technology FAQ
 CareGiver Remote Support Information Technology FAQ CareGiver remote support Information Technology FAQ Purpose The purpose of this document is to answer Frequently Asked Questions (FAQs) regarding CareGiver
CareGiver Remote Support Information Technology FAQ CareGiver remote support Information Technology FAQ Purpose The purpose of this document is to answer Frequently Asked Questions (FAQs) regarding CareGiver
The following information is provided by ARX, Inc. to aid customers in their evaluation of CoSign for SharePoint (C4SP).
 The following information is provided by ARX, Inc. to aid customers in their evaluation of CoSign for SharePoint (C4SP). Lay Boon Tay Sales Engineering Manager ARX, Inc. 855 Folsom Street Suite 939 San
The following information is provided by ARX, Inc. to aid customers in their evaluation of CoSign for SharePoint (C4SP). Lay Boon Tay Sales Engineering Manager ARX, Inc. 855 Folsom Street Suite 939 San
Egnyte for Power and Standard Users. User Guide
 Egnyte for Power and Standard Users User Guide Egnyte Inc. 1350 West Middlefield Road. Mountain View, CA 94043, USA Phone: 877-7EGNYTE (877-734-6983) Revised June 2015 Table of Contents Chapter 1: Getting
Egnyte for Power and Standard Users User Guide Egnyte Inc. 1350 West Middlefield Road. Mountain View, CA 94043, USA Phone: 877-7EGNYTE (877-734-6983) Revised June 2015 Table of Contents Chapter 1: Getting
Transformation of POS Operations at
 Transformation of POS Operations at Retail Outlets for Australian Telco Abstract A leading Australian telecommunications service provider wanted to upgrade its Point of Sale (POS) operations at its retail
Transformation of POS Operations at Retail Outlets for Australian Telco Abstract A leading Australian telecommunications service provider wanted to upgrade its Point of Sale (POS) operations at its retail
CS 356 Lecture 25 and 26 Operating System Security. Spring 2013
 CS 356 Lecture 25 and 26 Operating System Security Spring 2013 Review Chapter 1: Basic Concepts and Terminology Chapter 2: Basic Cryptographic Tools Chapter 3 User Authentication Chapter 4 Access Control
CS 356 Lecture 25 and 26 Operating System Security Spring 2013 Review Chapter 1: Basic Concepts and Terminology Chapter 2: Basic Cryptographic Tools Chapter 3 User Authentication Chapter 4 Access Control
NAS 221 Remote Access Using Cloud Connect TM
 NAS 221 Remote Access Using Cloud Connect TM Access the files on your NAS remotely with Cloud Connect TM A S U S T O R C O L L E G E COURSE OBJECTIVES Upon completion of this course you should be able
NAS 221 Remote Access Using Cloud Connect TM Access the files on your NAS remotely with Cloud Connect TM A S U S T O R C O L L E G E COURSE OBJECTIVES Upon completion of this course you should be able
Using EMC Documentum with Adobe LiveCycle ES
 Technical Guide Using EMC Documentum with Adobe LiveCycle ES Table of contents 1 Deployment 3 Managing LiveCycle ES development assets in Documentum 5 Developing LiveCycle applications with contents in
Technical Guide Using EMC Documentum with Adobe LiveCycle ES Table of contents 1 Deployment 3 Managing LiveCycle ES development assets in Documentum 5 Developing LiveCycle applications with contents in
WHITEPAPER. SECUREAUTH 2-FACTOR AS A SERVICE 2FaaS
 WHITEPAPER SECUREAUTH 2-FACTOR AS A SERVICE 2FaaS EXECUTIVE OVERVIEW 2-Factor as a Service (2FaaS) is a 100% cloud-hosted authentication solution that offers flexible security without compromising user
WHITEPAPER SECUREAUTH 2-FACTOR AS A SERVICE 2FaaS EXECUTIVE OVERVIEW 2-Factor as a Service (2FaaS) is a 100% cloud-hosted authentication solution that offers flexible security without compromising user
Email: Gmail Or other POP3
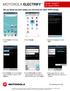 Set up Gmail account (steps are mirrored for other POP3 Email) 1.Touch Email on the home screen. 2.Touch Google. 3.Read the message and touch Next. 4.Touch Create. (Or, if you already have a Google account,
Set up Gmail account (steps are mirrored for other POP3 Email) 1.Touch Email on the home screen. 2.Touch Google. 3.Read the message and touch Next. 4.Touch Create. (Or, if you already have a Google account,
SECUREAUTH IDP AND OFFICE 365
 WHITEPAPER SECUREAUTH IDP AND OFFICE 365 STRONG AUTHENTICATION AND SINGLE SIGN-ON FOR THE CLOUD-BASED OFFICE SUITE EXECUTIVE OVERVIEW As more and more enterprises move to the cloud, it makes sense that
WHITEPAPER SECUREAUTH IDP AND OFFICE 365 STRONG AUTHENTICATION AND SINGLE SIGN-ON FOR THE CLOUD-BASED OFFICE SUITE EXECUTIVE OVERVIEW As more and more enterprises move to the cloud, it makes sense that
Integrating Autotask Service Desk Ticketing with the Cisco OnPlus Portal
 Integrating Autotask Service Desk Ticketing with the Cisco OnPlus Portal This Application Note provides instructions for configuring Apps settings on the Cisco OnPlus Portal and Autotask application settings
Integrating Autotask Service Desk Ticketing with the Cisco OnPlus Portal This Application Note provides instructions for configuring Apps settings on the Cisco OnPlus Portal and Autotask application settings
Mac - Juniper Remote Desktop Instructions
 Mac - Juniper Remote Desktop Instructions How to Set up & Remotely Connect to your Hospital Windows Workstation from your Remote Macintosh Computer Using the JSAM Feature of Juniper. Note: These instructions
Mac - Juniper Remote Desktop Instructions How to Set up & Remotely Connect to your Hospital Windows Workstation from your Remote Macintosh Computer Using the JSAM Feature of Juniper. Note: These instructions
NetIQ Advanced Authentication Framework
 NetIQ Advanced Authentication Framework Security Officer Guide Version 5.2.0 1 Table of Contents 1 Table of Contents 2 Introduction 3 About This Document 3 Authenticators Management 4 Card 8 Email OTP
NetIQ Advanced Authentication Framework Security Officer Guide Version 5.2.0 1 Table of Contents 1 Table of Contents 2 Introduction 3 About This Document 3 Authenticators Management 4 Card 8 Email OTP
Smart Card Authentication. Administrator's Guide
 Smart Card Authentication Administrator's Guide October 2012 www.lexmark.com Contents 2 Contents Overview...4 Configuring the applications...5 Configuring printer settings for use with the applications...5
Smart Card Authentication Administrator's Guide October 2012 www.lexmark.com Contents 2 Contents Overview...4 Configuring the applications...5 Configuring printer settings for use with the applications...5
U.S. Army best practices for secure network printing, scanning, and faxing.
 U.S. Army best practices for secure network printing, scanning, and faxing. Developed by Nuance Document Imaging and RICOH USA 2 Table of contents 3 Introduction Objective Overview Background in U.S. Federal
U.S. Army best practices for secure network printing, scanning, and faxing. Developed by Nuance Document Imaging and RICOH USA 2 Table of contents 3 Introduction Objective Overview Background in U.S. Federal
Training Events Database (TED) Setup Guide
 This document describes the basic process for installing the Training Events Database (TED) system. It does not cover installing FileMaker Pro or FileMaker Server, the software needed to run TED, or how
This document describes the basic process for installing the Training Events Database (TED) system. It does not cover installing FileMaker Pro or FileMaker Server, the software needed to run TED, or how
Asset Track Getting Started Guide. An Introduction to Asset Track
 Asset Track Getting Started Guide An Introduction to Asset Track Contents Introducing Asset Track... 3 Overview... 3 A Quick Start... 6 Quick Start Option 1... 6 Getting to Configuration... 7 Changing
Asset Track Getting Started Guide An Introduction to Asset Track Contents Introducing Asset Track... 3 Overview... 3 A Quick Start... 6 Quick Start Option 1... 6 Getting to Configuration... 7 Changing
Device Lifecycle Management
 Device Lifecycle Management 1 (8) Table of Contents 1. Executive summary... 3 2. Today's challenges in adapting to lifecycle management... 3 3. How is Miradore different?... 5 4. Conclusion... 8 2 (8)
Device Lifecycle Management 1 (8) Table of Contents 1. Executive summary... 3 2. Today's challenges in adapting to lifecycle management... 3 3. How is Miradore different?... 5 4. Conclusion... 8 2 (8)
915MHz RFID State of the Art RFID
 915MHz RFID State of the Art RFID LIBRARY BOOK / MEDIA MANAGEMENT and RFID TRACKING SYSTEM Executive Overview More and more libraries worldwide are utilizing RFID to automate the issue and return of books,
915MHz RFID State of the Art RFID LIBRARY BOOK / MEDIA MANAGEMENT and RFID TRACKING SYSTEM Executive Overview More and more libraries worldwide are utilizing RFID to automate the issue and return of books,
Shared License Server and Failover Support. Shared License Configuration
 Shared License Server and Failover Support The shared license server support feature included in Ascent Capture 7.0 allows system administrators to designate a primary site to handle licensing requests
Shared License Server and Failover Support The shared license server support feature included in Ascent Capture 7.0 allows system administrators to designate a primary site to handle licensing requests
Technology Plan FY 2009-2010 through FY 2012 2013
 Lee County Library System Lee County, Florida Technology Plan FY 2009-2010 through FY 2012 2013 October 2009 1 Table of Contents Vision and Mission Statements... 3 Goals and Objectives... 4 I. Public services...
Lee County Library System Lee County, Florida Technology Plan FY 2009-2010 through FY 2012 2013 October 2009 1 Table of Contents Vision and Mission Statements... 3 Goals and Objectives... 4 I. Public services...
Planning, Provisioning and Deploying Enterprise Clouds with Oracle Enterprise Manager 12c Kevin Patterson, Principal Sales Consultant, Enterprise
 Planning, Provisioning and Deploying Enterprise Clouds with Oracle Enterprise Manager 12c Kevin Patterson, Principal Sales Consultant, Enterprise Manager Oracle NIST Definition of Cloud Computing Cloud
Planning, Provisioning and Deploying Enterprise Clouds with Oracle Enterprise Manager 12c Kevin Patterson, Principal Sales Consultant, Enterprise Manager Oracle NIST Definition of Cloud Computing Cloud
Feature-rich, stress-free technology for any library.
 1 Atriuum Feature-rich, stress-free technology for any library. Atriuum, our 100% Web-based integrated library system, is built on a foundation of over 25 years experience in library technology and feedback
1 Atriuum Feature-rich, stress-free technology for any library. Atriuum, our 100% Web-based integrated library system, is built on a foundation of over 25 years experience in library technology and feedback
OpenIMS 4.2. Document Management Server. User manual
 OpenIMS 4.2 Document Management Server User manual OpenSesame ICT BV Index 1 INTRODUCTION...4 1.1 Client specifications...4 2 INTRODUCTION OPENIMS DMS...5 2.1 Login...5 2.2 Language choice...5 3 OPENIMS
OpenIMS 4.2 Document Management Server User manual OpenSesame ICT BV Index 1 INTRODUCTION...4 1.1 Client specifications...4 2 INTRODUCTION OPENIMS DMS...5 2.1 Login...5 2.2 Language choice...5 3 OPENIMS
Created By: 2009 Windows Server Security Best Practices Committee. Revised By: 2014 Windows Server Security Best Practices Committee
 Windows Server Security Best Practices Initial Document Created By: 2009 Windows Server Security Best Practices Committee Document Creation Date: August 21, 2009 Revision Revised By: 2014 Windows Server
Windows Server Security Best Practices Initial Document Created By: 2009 Windows Server Security Best Practices Committee Document Creation Date: August 21, 2009 Revision Revised By: 2014 Windows Server
VALIDATION MODULE MANUAL
 VALIDATION MODULE MANUAL TABLE OF CONTENTS Chapter 1 - Before You Begin Introduction / Module Overview... 1 Installation: Tick-It! Trak Pro Validation Module Installation... 3 Registration / Module Activation...
VALIDATION MODULE MANUAL TABLE OF CONTENTS Chapter 1 - Before You Begin Introduction / Module Overview... 1 Installation: Tick-It! Trak Pro Validation Module Installation... 3 Registration / Module Activation...
Gateway Apps - Security Summary SECURITY SUMMARY
 Gateway Apps - Security Summary SECURITY SUMMARY 27/02/2015 Document Status Title Harmony Security summary Author(s) Yabing Li Version V1.0 Status draft Change Record Date Author Version Change reference
Gateway Apps - Security Summary SECURITY SUMMARY 27/02/2015 Document Status Title Harmony Security summary Author(s) Yabing Li Version V1.0 Status draft Change Record Date Author Version Change reference
Microsoft Outlook Web Access 2013 Authenticating Users Using SecurAccess Server by SecurEnvoy
 Microsoft Outlook Web Access 2013 Authenticating Users Using SecurAccess Server by SecurEnvoy Contact information SecurEnvoy www.securenvoy.com 0845 2600010 Merlin House Brunel Road Theale Reading RG7
Microsoft Outlook Web Access 2013 Authenticating Users Using SecurAccess Server by SecurEnvoy Contact information SecurEnvoy www.securenvoy.com 0845 2600010 Merlin House Brunel Road Theale Reading RG7
Onegini Token server / Web API Platform
 Onegini Token server / Web API Platform Companies and users interact securely by sharing data between different applications The Onegini Token server is a complete solution for managing your customer s
Onegini Token server / Web API Platform Companies and users interact securely by sharing data between different applications The Onegini Token server is a complete solution for managing your customer s
SharePoint AD Information Sync Installation Instruction
 SharePoint AD Information Sync Installation Instruction System Requirements Microsoft Windows SharePoint Services V3 or Microsoft Office SharePoint Server 2007. License management Click the trial link
SharePoint AD Information Sync Installation Instruction System Requirements Microsoft Windows SharePoint Services V3 or Microsoft Office SharePoint Server 2007. License management Click the trial link
JIJI AUDIT REPORTER FEATURES
 JIJI AUDIT REPORTER FEATURES JiJi AuditReporter is a web based auditing solution for live monitoring of the enterprise changes and for generating audit reports on each and every event occurring in the
JIJI AUDIT REPORTER FEATURES JiJi AuditReporter is a web based auditing solution for live monitoring of the enterprise changes and for generating audit reports on each and every event occurring in the
DISTRIBUTED DATA COLLECTION FOR REINSURANCE (RI) AND RISK ADJUSTMENT (RA): PROVISIONING. August 27, 2015 HTTPS://WWW.REGTAP.INFO/
 DISTRIBUTED DATA COLLECTION FOR REINSURANCE (RI) AND RISK ADJUSTMENT (RA): PROVISIONING August 27, 2015 Session Guidelines This is a 90-minute webinar session. For questions regarding the Distributed Data
DISTRIBUTED DATA COLLECTION FOR REINSURANCE (RI) AND RISK ADJUSTMENT (RA): PROVISIONING August 27, 2015 Session Guidelines This is a 90-minute webinar session. For questions regarding the Distributed Data
Windows Server 2008 R2 Essentials
 Windows Server 2008 R2 Essentials Installation, Deployment and Management 2 First Edition 2010 Payload Media. This ebook is provided for personal use only. Unauthorized use, reproduction and/or distribution
Windows Server 2008 R2 Essentials Installation, Deployment and Management 2 First Edition 2010 Payload Media. This ebook is provided for personal use only. Unauthorized use, reproduction and/or distribution
Apple Technical White Paper Best Practices for Deploying Mac with OS X
 Best Practices for Deploying Mac with OS X OS X Mountain Lion v10.8 Contents Overview... 3 OS X Installation Basics... 3 Installer Technology... 3 OS X Recovery... 4 Internet Recovery... 4 External OS
Best Practices for Deploying Mac with OS X OS X Mountain Lion v10.8 Contents Overview... 3 OS X Installation Basics... 3 Installer Technology... 3 OS X Recovery... 4 Internet Recovery... 4 External OS
solutions that captivate and connect
 solutions that captivate and connect the best of both worlds the best of both worlds The new bibliotheca In October of 2015 we were delighted to announce that the entire former 3M Library System management
solutions that captivate and connect the best of both worlds the best of both worlds The new bibliotheca In October of 2015 we were delighted to announce that the entire former 3M Library System management
1-9 August 2003, Berlin
 World Library and Information Congress: 69th IFLA General Conference and Council 1-9 August 2003, Berlin Code Number: 132-E Meeting: 113. Information Technology Simultaneous Interpretation: - Experiences
World Library and Information Congress: 69th IFLA General Conference and Council 1-9 August 2003, Berlin Code Number: 132-E Meeting: 113. Information Technology Simultaneous Interpretation: - Experiences
What s New Guide: Version 5.6
 What s New Guide: Version 5.6 A QUEST SOFTWARE COMPANY 1. 8 0 0. 4 2 4. 9 4 1 1 w w w. s c r i p t l o g i c. c o m WHAT S NEW IN ACTIVE ADMINISTRATOR 5.6? Contents...3 Active Administrator Product Overview...3
What s New Guide: Version 5.6 A QUEST SOFTWARE COMPANY 1. 8 0 0. 4 2 4. 9 4 1 1 w w w. s c r i p t l o g i c. c o m WHAT S NEW IN ACTIVE ADMINISTRATOR 5.6? Contents...3 Active Administrator Product Overview...3
Smart Card Authentication Client. Administrator's Guide
 Smart Card Authentication Client Administrator's Guide April 2013 www.lexmark.com Contents 2 Contents Overview...3 Configuring Smart Card Authentication Client...4 Configuring printer settings for use
Smart Card Authentication Client Administrator's Guide April 2013 www.lexmark.com Contents 2 Contents Overview...3 Configuring Smart Card Authentication Client...4 Configuring printer settings for use
Network Documentation Checklist
 Network Documentation Checklist Don Krause, Creator of NetworkDNA This list has been created to provide the most elaborate overview of elements in a network that should be documented. Network Documentation
Network Documentation Checklist Don Krause, Creator of NetworkDNA This list has been created to provide the most elaborate overview of elements in a network that should be documented. Network Documentation
Inventory Software Trials
 University of Kentucky UKnowledge Library Presentations University of Kentucky Libraries 9-2011 Inventory Software Trials Kathryn Lybarger University of Kentucky, kathryn.lybarger@uky.edu Julene L. Jones
University of Kentucky UKnowledge Library Presentations University of Kentucky Libraries 9-2011 Inventory Software Trials Kathryn Lybarger University of Kentucky, kathryn.lybarger@uky.edu Julene L. Jones
Instruction Guide Practice Round 2 High School August 2015
 Instruction Guide Practice Round 2 High School August 2015 1 Maryland Cyber Challenge Practice Round Instruction Guide Table of Contents Introduction 3 Tips for Success 3 Round Times 3 Linux Virtual Machine
Instruction Guide Practice Round 2 High School August 2015 1 Maryland Cyber Challenge Practice Round Instruction Guide Table of Contents Introduction 3 Tips for Success 3 Round Times 3 Linux Virtual Machine
Introduction CDR Dicom for Windows is designed as a fully functional DICOM (Digital Imaging Communications of Medicine) based client-server
 Introduction CDR Dicom for Windows is designed as a fully functional DICOM (Digital Imaging Communications of Medicine) based client-server application. The client application can, in theory, communicate
Introduction CDR Dicom for Windows is designed as a fully functional DICOM (Digital Imaging Communications of Medicine) based client-server application. The client application can, in theory, communicate
Migrating Lotus Notes Applications to Google Apps
 Migrating Lotus Notes Applications to Google Apps Introduction.................................................... 3 Assessment..................................................... 3 Usage.........................................................
Migrating Lotus Notes Applications to Google Apps Introduction.................................................... 3 Assessment..................................................... 3 Usage.........................................................
Softerra Adaxes Enterprise Directory Solution
 Identity and Active Directory Management Softerra Adaxes Enterprise Directory Solution Product Profile make the complex simple Copyright Copyright Softerra, Ltd. Softerra, All rights Ltd. reserved. All
Identity and Active Directory Management Softerra Adaxes Enterprise Directory Solution Product Profile make the complex simple Copyright Copyright Softerra, Ltd. Softerra, All rights Ltd. reserved. All
INTEGRATION GUIDE. General Radius Config
 INTEGRATION GUIDE General Radius Config Disclaimer Disclaimer of Warranties and Limitation of Liabilities All information contained in this document is provided 'as is'; VASCO Data Security assumes no
INTEGRATION GUIDE General Radius Config Disclaimer Disclaimer of Warranties and Limitation of Liabilities All information contained in this document is provided 'as is'; VASCO Data Security assumes no
R 143 CYBERSECURITY RECOMMENDATION FOR MEDIA VENDORS SYSTEMS, SOFTWARE & SERVICES
 R 143 CYBERSECURITY RECOMMENDATION FOR MEDIA VENDORS SYSTEMS, SOFTWARE & SERVICES RECOMMENDATION Geneva April 2016 R 143 Cybersecurity Rec. for media vendors systems, software & services Cybersecurity
R 143 CYBERSECURITY RECOMMENDATION FOR MEDIA VENDORS SYSTEMS, SOFTWARE & SERVICES RECOMMENDATION Geneva April 2016 R 143 Cybersecurity Rec. for media vendors systems, software & services Cybersecurity
Understanding Task Scheduler FIGURE 33.14. Task Scheduler. The error reporting screen.
 1383 FIGURE.14 The error reporting screen. curring tasks into a central location, administrators gain insight into system functionality and control over their Windows Server 2008 R2 infrastructure through
1383 FIGURE.14 The error reporting screen. curring tasks into a central location, administrators gain insight into system functionality and control over their Windows Server 2008 R2 infrastructure through
How To Write A Web Site Software For A Large Business
 Introduction to e-commerce E-Commerce Software Objectives In this chapter, you will learn about: Finding and evaluating Web hosting services Basic functions of electronic commerce software Advanced functions
Introduction to e-commerce E-Commerce Software Objectives In this chapter, you will learn about: Finding and evaluating Web hosting services Basic functions of electronic commerce software Advanced functions
QliqDIRECT Active Directory Guide
 QliqDIRECT Active Directory Guide QliqDIRECT is a Windows Service with Active Directory Interface. QliqDIRECT resides in your network/server and communicates with Qliq cloud servers securely. QliqDIRECT
QliqDIRECT Active Directory Guide QliqDIRECT is a Windows Service with Active Directory Interface. QliqDIRECT resides in your network/server and communicates with Qliq cloud servers securely. QliqDIRECT
Print Management. User's Guide
 Print Management User's Guide November 2014 www.lexmark.com Contents 2 Contents Overview...3 Performing user authentication...4 Using standard authentication...4 Using Single Sign On authentication...4
Print Management User's Guide November 2014 www.lexmark.com Contents 2 Contents Overview...3 Performing user authentication...4 Using standard authentication...4 Using Single Sign On authentication...4
ERserver. iseries. Printing
 ERserver iseries Printing ERserver iseries Printing Copyright International Business Machines Corporation 1998, 2001. All rights reserved. US Government Users Restricted Rights Use, duplication or disclosure
ERserver iseries Printing ERserver iseries Printing Copyright International Business Machines Corporation 1998, 2001. All rights reserved. US Government Users Restricted Rights Use, duplication or disclosure
THE GLOBAL EVENT MANAGER
 The Big Data Mining Company THE GLOBAL EVENT MANAGER When data is available and reachable, it has to be processed and decrypted using multiple heterogeneous tools, if these are available. Each of these
The Big Data Mining Company THE GLOBAL EVENT MANAGER When data is available and reachable, it has to be processed and decrypted using multiple heterogeneous tools, if these are available. Each of these
Installation and User Guide. MQLink Version 3.0 (Java)
 Installation and User Guide MQLink Version 3.0 (Java) MQLink V3.0 (Java) User Guide Table of Contents 1 Introduction... 2 2 Installation... 2 2.1 Available from 2.2 Where to install 2.3 Installation Pre-requisites
Installation and User Guide MQLink Version 3.0 (Java) MQLink V3.0 (Java) User Guide Table of Contents 1 Introduction... 2 2 Installation... 2 2.1 Available from 2.2 Where to install 2.3 Installation Pre-requisites
Analyzing Network Servers. Disk Space Utilization Analysis. DiskBoss - Data Management Solution
 DiskBoss - Data Management Solution DiskBoss provides a large number of advanced data management and analysis operations including disk space usage analysis, file search, file classification and policy-based
DiskBoss - Data Management Solution DiskBoss provides a large number of advanced data management and analysis operations including disk space usage analysis, file search, file classification and policy-based
Active Directory Integration for Greentree
 App Number: 010044 Active Directory Integration for Greentree Last Updated 14 th February 2013 Powered by: AppsForGreentree.com 2013 1 Table of Contents Features... 3 Options... 3 Important Notes... 3
App Number: 010044 Active Directory Integration for Greentree Last Updated 14 th February 2013 Powered by: AppsForGreentree.com 2013 1 Table of Contents Features... 3 Options... 3 Important Notes... 3
HP Service Manager. Software Version: 9.40 For the supported Windows and Linux operating systems. Application Setup help topics for printing
 HP Service Manager Software Version: 9.40 For the supported Windows and Linux operating systems Application Setup help topics for printing Document Release Date: December 2014 Software Release Date: December
HP Service Manager Software Version: 9.40 For the supported Windows and Linux operating systems Application Setup help topics for printing Document Release Date: December 2014 Software Release Date: December
Technology Plan Avon Free Public Library Avon, CT. October 1, 2007 - December 31, 2010
 Technology Plan Avon Free Public Library Avon, CT. October 1, 2007 - December 31, 2010 Vision: To excel as the community s link to ideas, information and resources. Mission Statement: To serve as the center
Technology Plan Avon Free Public Library Avon, CT. October 1, 2007 - December 31, 2010 Vision: To excel as the community s link to ideas, information and resources. Mission Statement: To serve as the center
Novell Filr 1.0.x Mobile App Quick Start
 Novell Filr 1.0.x Mobile App Quick Start February 2014 Novell Quick Start Novell Filr allows you to easily access all your files and folders from your desktop, browser, or a mobile device. In addition,
Novell Filr 1.0.x Mobile App Quick Start February 2014 Novell Quick Start Novell Filr allows you to easily access all your files and folders from your desktop, browser, or a mobile device. In addition,
Security and Control Issues within Relational Databases
 Security and Control Issues within Relational Databases David C. Ogbolumani, CISA, CISSP, CIA, CISM Practice Manager Information Security Preview of Key Points The Database Environment Top Database Threats
Security and Control Issues within Relational Databases David C. Ogbolumani, CISA, CISSP, CIA, CISM Practice Manager Information Security Preview of Key Points The Database Environment Top Database Threats
Prepared by: ServiceSPAN. in cooperation with. Sun Microsystems. Application Load Test March 18, 2007 Version 3
 Prepared by: ServiceSPAN in cooperation with Sun Microsystems Application Load Test March 18, 2007 Version 3 Introduction ServiceSPAN, a provider of work center automation software to enterprise businesses,
Prepared by: ServiceSPAN in cooperation with Sun Microsystems Application Load Test March 18, 2007 Version 3 Introduction ServiceSPAN, a provider of work center automation software to enterprise businesses,
Position Description. Job Summary: Campus Job Scope:
 Position Description Report Run Date Sep 10 2015 11:07AM Position Number: 02018467 Dept: ENT APPS & INFRASTRUCTURE SVCS - 061419 Position: WNDOWS SYSTEM APPLICATION ADMINISTRATOR Approved Payroll Title
Position Description Report Run Date Sep 10 2015 11:07AM Position Number: 02018467 Dept: ENT APPS & INFRASTRUCTURE SVCS - 061419 Position: WNDOWS SYSTEM APPLICATION ADMINISTRATOR Approved Payroll Title
E-Series. Human Machine Interfaces. Evolution By Design MITSUBISHI ELECTRIC AUTOMATION, INC.
 E-Series Human Machine Interfaces E Evolution By Design MITSUBISHI ELECTRIC AUTOMATION, INC. Discover the Many Facets of Mitsubishi Electric. The Power in Automation Solutions. E-Series is a family of
E-Series Human Machine Interfaces E Evolution By Design MITSUBISHI ELECTRIC AUTOMATION, INC. Discover the Many Facets of Mitsubishi Electric. The Power in Automation Solutions. E-Series is a family of
One platform for all your print, scan and device management
 One platform for all your print, scan and device management Manage all Printing & Scanning with one single Platform. Incorporating uniflow into your document processes will lead to real improvements in
One platform for all your print, scan and device management Manage all Printing & Scanning with one single Platform. Incorporating uniflow into your document processes will lead to real improvements in
WorkTime UC Mobile Admin Guide
 WorkTime UC Mobile Admin Guide Release: 20.1.1 Android 20.1.2 ios Document Version 1.0 Table of Contents 1 About XO Hosted PBX UC Mobile Client...1 2 Use Cases...2 2.1 Placing Outbound Calls... 2 2.2 Receiving
WorkTime UC Mobile Admin Guide Release: 20.1.1 Android 20.1.2 ios Document Version 1.0 Table of Contents 1 About XO Hosted PBX UC Mobile Client...1 2 Use Cases...2 2.1 Placing Outbound Calls... 2 2.2 Receiving
