Cyber Warnings E-Magazine August 2015 Edition Copyright Cyber Defense Magazine, All rights reserved worldwide
|
|
|
- Roland Gibson
- 8 years ago
- Views:
Transcription
1 1 Cyber Warnings E-Magazine August 2015 Edition
2 End-to-End Encryption for s. An Organizational Approach by Dr Burkhard Wiegel, Founder and CEO, Zertificon Solutions The threat to electronic enterprise communication used to be beyond the firewall. With the increased use of mobile devices for business , the need to secure communication from sender to recipient and within the corporate network has raised the awareness for industrial scale end-toend encryption. There are risks and pitfalls associated with the existing concepts of end-to-end encryption. Many solutions are available which deliver personal simple client-side encryption or just transport layer encryption which are not suitable for organizations. This paper will introduce an alternative organizational approach for secure end-to-end communication. Secure Channel versus Content Encryption When discussing encryption the topic of Transport Layer Encryption (TLS) always arises. TLS has become a popular and established technology but it is often mistaken for a full-blown end-toend encryption solution. TLS however, only secures the communication between two mail relay servers and not the actual message content. Not only is the message content unencrypted during transport but also whenever it is stored. This includes temporary storage on mail relay servers as well as mid-term to permanent storage in users' server-side mailboxes and archives. Any hackers who can make it through the firewall can simply help themselves to whatever they find. In case of sync, pop or push services s are also unprotected on the client device. TLS gives the appearance of being secure, but does not deliver enterprise level security. Even VPN and other secure channel methods which secure the transport but not the content have the same security problems as TLS. It is always better to secure the message. End-to-end encryption appears to be the only solution which provides real security and confidentiality. After the NSA scandal, security experts who were vocal in the media, called for the comprehensive adoption of end-to-end encryption but never came up with realistic day in, day out solutions which could be rolled-out throughout companies. Enterprise Encryption Status Quo Modern encryption is based upon asymmetric keys which commonly utilize a Public Key Infrastructure (PKI) such as S/MIME or OpenPGP. Not surprisingly, these two systems are incompatible. Although they both rely on the same cryptographic concepts their trust models are very different. OpenPGP relies on a peer based web of trust in which users vouch for each other. S/MIME on the other hand relies on a hierarchical trust model where a higher entity vouches for a lower entity and states how this trust is established (e.g. identity checks). Certification Authorities (CAs) sign the public keys and from that moment on a public key becomes a certificate. The CA publishes the certificate alongside up to date status information relating to the 10
3 validity of the certificate. Certificate servers such as collate and validate certificates from the CA servers. S/MIME is supported by all popular clients and has become the standard in the business world. Because obtaining an S/MIME certificate can involve cost, most private users utilize OpenPGP based encryption which requires usually free 3rd party software. Both S/MIME and OpenPGP use a key pair which consists of an encryption and decryption key. The encryption key is public and must be made available to the message sender whereas the recipient keeps hold of the private decryption key. Only the holder of the private key can decrypt messages encrypted with the public key. The public key also contains information which can be used to check the authenticity and validity of the key. Certificate Management Challenge It becomes clear that the real challenge for businesses is not the encryption itself, but the management of the private and public keys. Private keys for employees have to be protected, issued and revoked when staff join and leave the company whilst their public keys have to be made available to communication partners. At the same time the public keys from communication partners have to be made available to employees. Throw into the mix the fact that many communication partners may be using OpenPGP keys and the scalability of key management suddenly becomes a problem. Public keys from communication partners have to be searched for, saved, validated and checked against revocation lists in real time. The PKI challenge is to automate the full key management and make it fully transparent to employees. Centrally applied encryption with Policies Encryption and security is only guaranteed when it is applied every time it is required. Removing the encryption decision and the key management from employees and making the encryption process automated and invisible guarantees security and compliance. The solution is Secure Gateways. These fully automate the key management and use configurable policies to ensure that encryption is applied when it is required. Secure Gateways deliver a number of key advantages to businesses. Their centralized deployment removes the need for any end-user software and training. s are en-/decrypted automatically and all keys are managed centrally. Keys from 3rd parties are checked to ensure that they are valid and employee's keys are made available to communication partners. But one of the key advantages delivered by Secure Gateways, is the ability to communicate securely with any partner regardless as to whether they are using S/MIME, OpenPGP or do not have any encryption software installed at all. 11
4 Communicating without PKI Keys Secure delivery Password based encryption has become an established alternative to key based encryption. The message can be delivered directly to the recipient as an encrypted PDF file or a secure web mailer account can be created on the fly for each recipient. Only instructional messages to the recipient are communicated using non-encrypted s whilst the sensitive content is always protected. Secure PDF or web mail delivery enables businesses to communicate instantly and securely with any recipient. Limits of Gateway Security A Secure Gateway acts as an interface to the Internet at which s are en-/decrypted. Within the company network however, the s are transmitted in a plain state without any encryption. This remains a secure method to protect against foreign intelligence services and industrial spying and has been used by companies, institutions and public authorities for years. At the same time however, there are situations in which end-to-end encryption is required. When using mobile devices such as laptops, phones and tablets s are transmitted outside the company network via WiFi or mobile network in plain text. It takes little investment and only basic skills to gain access to the message content. Therefore the aim is to secure the content itself between the gateway and end users as well as between users. Securing the transport layer with TLS or VPN can add some level of protection and investment in Mobile Device Management Systems (MDM) should not be ignored. But foolproof security can only be achieved when the content is secured in transit and of course when it is stored in an encrypted state on intermediate servers and end devices. End-to-End Approach for Enterprises End-to-end encryption usually means complete content encryption between end devices and also the encrypted storage of the message on the end device. Only the recipient who is in possession of the required key can decrypt and access the message and its content. However, this highly secure communication method raises a number of problems for businesses. Employees work for the business and the information and communication they generate belongs to the company. In order to support audit compliance, archiving and business continuity, it is imperative that the company has control over its entire traffic. Companies also need be in control in order to protect themselves from spam, viruses, loss of data and even phishing attempts despite encryption. The roll-out of distributed content filtering and scanning would be simply not scalable or practicable in a standard end-to-end encryption scenario. 12
5 Organizational Approach Combining internal with external encryption For everyday use within a business environment, even with end-to-end there needs to be a point of access to the actual mail content. The organizational approach sees this single point of access at the Secure Gateway if the Gateway is deployed together with an End2End encryption solution. The task of the End2End solution is to manage an encapsulated internal PKI and enable the Gateway to bridge between the internal and external PKIs. Imagine this as encrypting in two different worlds with a passage from one world to the other. This passage is the access point that gives organizations control over their traffic. The internal world speaks only S/MIME. S/MIME is supported by all standard clients out of the box which means low administration efforts. The Gateway translates S/MIME to and from other encryption languages. An internally S/MIME encrypted can reach an external recipient as an OpenPGP encrypted mail or via secure Webmailer depending on the recipient's environment. s are stored in an encrypted state on servers and cannot be read by system administrators especially important if the company infrastructure is a third party hosted service. The also remains encrypted on the end device and can only be decrypted as needed by the user. The work flow proceeds as follows: Encrypted s reach the gateway, they are decrypted at the Gateway from which they can be routed to content filters such as virus scanners or data loss prevention tools. Those tools process the s following their own routines and send them back to the Gateway where they are re-encrypted for the next part of their journey. If the journey is internal the will be re-encrypted using the keys of the internal S/MIME PKI. Outbound s will be received by the Gateway in an S/MIME encrypted state. In order to reencrypt this for the travel over the Internet the Gateway checks the possibilities for secure delivery depending on the external recipient's data. This enables instant end-to-end encryption with virtually everyone. And the original sender does not even need to know how things work. All the sender needs to know is that the was securely encrypted without worrying about the actual technical details. This scenario is ideal for organizations and is referred to as Organizational End-to-End. Organizational End-to-End can work in parallel with the so called Personal method. Messages are fully encrypted from sender to recipient. This is analogue to the classic form of End-to-End encryption and is targeted at users with high security needs such as a board of directors. Encryption takes place on the client devices and no content filtering can take place. In fact, not even the gateway administrator can access the message content. 13
6 Spicing up the internal world As we learned standard clients support S/MIME and therefore make end to end encryption possible without any extra software. However without any additional plug-ins, the end-user is responsible for encrypting s and must be trained accordingly. Any risks can be eliminated through the deployment of client plug-ins which take over the responsibility for activating encryption and for selecting the appropriate encryption method according to centrally configured security policies. Even with state of the art technology, security is only good when it is accepted and used correctly by employees. Summary Public key infrastructures provide the corner stone of secure communication. It does not matter what encryption technologies the communication partners use or even if they have a method of decrypting messages. Secure Gateways can ensure that s are delivered securely from the employee s computer right to the recipient. For organizations, companies and public agencies that do not use use mobile end devices and do not have any secrets to hide from their mail server admins, a Secure Gateway is all they need. For all others Organizational End-to-End combined with Personal End-to-End delivers a universal solution for secure communication that protects s in transit and in rest. About The Author Dr. Burkhard Wiegel is the founder and CEO of Zertificon Solutions. He graduated in computer science and obtained his doctorate at the Technical University in Berlin. He has published many papers on secure and was a pioneer in the IT security market, long before security became a mainstream topic. His research and insights led to the development of Zertificon's Z1 Secur Gateway one of Europe's leading encryption solutions. Burkhard can be reached online at LinkedIn and our company website He will be available for meetings at the German Pavilion on next years RSA February 29 March 4, 2016 in San Francisco. Zertificon is looking for resellers in the USA. 14
Mobile Device End-to-End-Email Encryption for Organizations. San Francisco, April 20th, 2015 GABA / TeleTrusT: Security Solutions Showcase
 Mobile Device End-to-End-Email Encryption for Organizations San Francisco, April 20th, 2015 GABA / TeleTrusT: Security Solutions Showcase Secure proven server-based Email Encryption Internet PKI S/MIME
Mobile Device End-to-End-Email Encryption for Organizations San Francisco, April 20th, 2015 GABA / TeleTrusT: Security Solutions Showcase Secure proven server-based Email Encryption Internet PKI S/MIME
End-to-End Email Encryption for Everybody?
 White paper End-to-End Email Encryption for Everybody? Why private individuals and corporations need different solutions White paper End-to-End Email Encryption for Everybody? Why private individuals and
White paper End-to-End Email Encryption for Everybody? Why private individuals and corporations need different solutions White paper End-to-End Email Encryption for Everybody? Why private individuals and
Secure email in times of rising mobile communication
 White paper Secure email in times of rising mobile communication Applied cryptography: Certificates, Gateways and End-to-End Encryption White paper Secure email in times of rising mobile communication
White paper Secure email in times of rising mobile communication Applied cryptography: Certificates, Gateways and End-to-End Encryption White paper Secure email in times of rising mobile communication
Options for encrypted e-mail communication with AUDI AG Version of: 31 May 2011
 Options for encrypted e-mail communication with AUDI AG Version of: 31 May 2011 1 Options for encrypted e-mail communication with AUDI AG Confidential information may only be transmitted in encrypted form
Options for encrypted e-mail communication with AUDI AG Version of: 31 May 2011 1 Options for encrypted e-mail communication with AUDI AG Confidential information may only be transmitted in encrypted form
Implementing Transparent Security for Desktop Encryption Users
 Implementing Transparent Security for Desktop Encryption Users Solutions to automate email encryption with external parties Get this White Paper Entrust Inc. All All Rights Reserved. 1 1 Contents Introduction...
Implementing Transparent Security for Desktop Encryption Users Solutions to automate email encryption with external parties Get this White Paper Entrust Inc. All All Rights Reserved. 1 1 Contents Introduction...
The basic groups of components are described below. Fig X- 1 shows the relationship between components on a network.
 Elements of Email Email Components There are a number of software components used to produce, send and transfer email. These components can be broken down as clients or servers, although some components
Elements of Email Email Components There are a number of software components used to produce, send and transfer email. These components can be broken down as clients or servers, although some components
Secure Email Inside the Corporate Network: INDEX 1 INTRODUCTION 2. Encryption at the Internal Desktop 2 CURRENT TECHNIQUES FOR DESKTOP ENCRYPTION 3
 A Tumbleweed Whitepaper Secure Email Inside the Corporate Network: Providing Encryption at the Internal Desktop INDEX INDEX 1 INTRODUCTION 2 Encryption at the Internal Desktop 2 CURRENT TECHNIQUES FOR
A Tumbleweed Whitepaper Secure Email Inside the Corporate Network: Providing Encryption at the Internal Desktop INDEX INDEX 1 INTRODUCTION 2 Encryption at the Internal Desktop 2 CURRENT TECHNIQUES FOR
The Case For Secure Email
 The Case For Secure Email By Erik Kangas, PhD, President, Lux Scientiae, Incorporated http://luxsci.com Contents Section 1: Introduction Section 2: How Email Works Section 3: Security Threats to Your Email
The Case For Secure Email By Erik Kangas, PhD, President, Lux Scientiae, Incorporated http://luxsci.com Contents Section 1: Introduction Section 2: How Email Works Section 3: Security Threats to Your Email
The GlobalCerts TM SecureMail Gateway TM
 Glob@lCerts PRODUCT OVERVIEW: The GlobalCerts TM SecureMail Gateway TM Automatic encryption and decryption is unique to the SecureMail Gateway. The GlobalCerts SecureMail Gateway is based on a network
Glob@lCerts PRODUCT OVERVIEW: The GlobalCerts TM SecureMail Gateway TM Automatic encryption and decryption is unique to the SecureMail Gateway. The GlobalCerts SecureMail Gateway is based on a network
White paper. Why Encrypt? Securing email without compromising communications
 White paper Why Encrypt? Securing email without compromising communications Why Encrypt? There s an old saying that a ship is safe in the harbour, but that s not what ships are for. The same can be said
White paper Why Encrypt? Securing email without compromising communications Why Encrypt? There s an old saying that a ship is safe in the harbour, but that s not what ships are for. The same can be said
Savitribai Phule Pune University
 Savitribai Phule Pune University Centre for Information and Network Security Course: Introduction to Cyber Security / Information Security Module : Pre-requisites in Information and Network Security Chapter
Savitribai Phule Pune University Centre for Information and Network Security Course: Introduction to Cyber Security / Information Security Module : Pre-requisites in Information and Network Security Chapter
CIPHERMAIL EMAIL ENCRYPTION. CipherMail white paper
 CIPHERMAIL EMAIL ENCRYPTION CipherMail white paper Copyright 2009-2014, ciphermail.com. Introduction Most email is sent as plain text. This means that anyone who can intercept email messages, either in
CIPHERMAIL EMAIL ENCRYPTION CipherMail white paper Copyright 2009-2014, ciphermail.com. Introduction Most email is sent as plain text. This means that anyone who can intercept email messages, either in
FTA Computer Security Workshop. Secure Email
 FTA Computer Security Workshop Secure Email March 8, 2007 Stan Wiechert, KDOR IS Security Officer Outline of Presentation The Risks associated with Email Business Constraints Secure Email Features Some
FTA Computer Security Workshop Secure Email March 8, 2007 Stan Wiechert, KDOR IS Security Officer Outline of Presentation The Risks associated with Email Business Constraints Secure Email Features Some
A Guide to Secure Email
 White Paper A Guide to Secure Email ABOUT THIS WHITE PAPER AND TARGET AUDIENCE This document is a whitepaper discussing the concept of secure email and the way in which M86 Security enables secure email
White Paper A Guide to Secure Email ABOUT THIS WHITE PAPER AND TARGET AUDIENCE This document is a whitepaper discussing the concept of secure email and the way in which M86 Security enables secure email
T E C H N I C A L S A L E S S O L U T I O N
 Trend Micro Email Encryption Gateway 5.0 Deployment Guide January 2009 Trend Micro, Inc. 10101 N. De Anza Blvd. Cupertino, CA 95014 USA T +1.800.228.5651 / +1.408.257.1500 F +1.408.257.2003 www.trendmicro.com
Trend Micro Email Encryption Gateway 5.0 Deployment Guide January 2009 Trend Micro, Inc. 10101 N. De Anza Blvd. Cupertino, CA 95014 USA T +1.800.228.5651 / +1.408.257.1500 F +1.408.257.2003 www.trendmicro.com
How To Secure Mail Delivery
 FortiMail Identity Based Encryption A Business Enabler WHITE PAPER FORTINET FortiMail Identity Based Encryption - A Business Enabler PAGE 2 Contents Business Need Secure Mail Delivery... 3 Challenges with
FortiMail Identity Based Encryption A Business Enabler WHITE PAPER FORTINET FortiMail Identity Based Encryption - A Business Enabler PAGE 2 Contents Business Need Secure Mail Delivery... 3 Challenges with
Entrust Managed Services PKI. Getting started with digital certificates and Entrust Managed Services PKI. Document issue: 1.0
 Entrust Managed Services PKI Getting started with digital certificates and Entrust Managed Services PKI Document issue: 1.0 Date of issue: May 2009 Copyright 2009 Entrust. All rights reserved. Entrust
Entrust Managed Services PKI Getting started with digital certificates and Entrust Managed Services PKI Document issue: 1.0 Date of issue: May 2009 Copyright 2009 Entrust. All rights reserved. Entrust
E-mail Best Practices
 CMSGu2012-06 Mauritian Computer Emergency Response Team CERT-MU SECURITY GUIDELINE 2011-02 Enhancing Cyber Security in Mauritius E-mail Best Practices National Computer Board Mauritius Version 1.0 June
CMSGu2012-06 Mauritian Computer Emergency Response Team CERT-MU SECURITY GUIDELINE 2011-02 Enhancing Cyber Security in Mauritius E-mail Best Practices National Computer Board Mauritius Version 1.0 June
Sendmail and PostX: Simplifying HIPAA Email Compliance. Providing healthcare organizations with secure outbound, inbound and internal email
 Sendmail and PostX: Simplifying HIPAA Email Compliance Providing healthcare organizations with secure outbound, inbound and internal email October 5, 2005 About Your Hosts Sendmail Complete email security
Sendmail and PostX: Simplifying HIPAA Email Compliance Providing healthcare organizations with secure outbound, inbound and internal email October 5, 2005 About Your Hosts Sendmail Complete email security
The Benefits of SSL Content Inspection ABSTRACT
 The Benefits of SSL Content Inspection ABSTRACT SSL encryption is the de-facto encryption technology for delivering secure Web browsing and the benefits it provides is driving the levels of SSL traffic
The Benefits of SSL Content Inspection ABSTRACT SSL encryption is the de-facto encryption technology for delivering secure Web browsing and the benefits it provides is driving the levels of SSL traffic
Djigzo email encryption. Djigzo white paper
 Djigzo email encryption Djigzo white paper Copyright 2009-2011, djigzo.com. Introduction Most email is sent as plain text. This means that anyone who can intercept email messages, either in transit or
Djigzo email encryption Djigzo white paper Copyright 2009-2011, djigzo.com. Introduction Most email is sent as plain text. This means that anyone who can intercept email messages, either in transit or
SSL Overview for Resellers
 Web Security Enterprise Security Identity Verification Services Signing Services SSL Overview for Resellers What We ll Cover Understanding SSL SSL Handshake 101 Market Opportunity for SSL Obtaining an
Web Security Enterprise Security Identity Verification Services Signing Services SSL Overview for Resellers What We ll Cover Understanding SSL SSL Handshake 101 Market Opportunity for SSL Obtaining an
DJIGZO EMAIL ENCRYPTION. Djigzo white paper
 DJIGZO EMAIL ENCRYPTION Djigzo white paper Copyright 2009-2011, djigzo.com. Introduction Most email is sent as plain text. This means that anyone who can intercept email messages, either in transit or
DJIGZO EMAIL ENCRYPTION Djigzo white paper Copyright 2009-2011, djigzo.com. Introduction Most email is sent as plain text. This means that anyone who can intercept email messages, either in transit or
INTERNET SECURITY: FIREWALLS AND BEYOND. Mehernosh H. Amroli 4-25-2002
 INTERNET SECURITY: FIREWALLS AND BEYOND Mehernosh H. Amroli 4-25-2002 Preview History of Internet Firewall Technology Internet Layer Security Transport Layer Security Application Layer Security Before
INTERNET SECURITY: FIREWALLS AND BEYOND Mehernosh H. Amroli 4-25-2002 Preview History of Internet Firewall Technology Internet Layer Security Transport Layer Security Application Layer Security Before
PineApp TM Mail Encryption Solution TM
 PineApp TM Mail Encryption Solution TM How to keep your outgoing messages fully secured. October 2008 Modern day challenges in E-Mail Security Throughout the years, E-Mail has evolved significantly, emerging
PineApp TM Mail Encryption Solution TM How to keep your outgoing messages fully secured. October 2008 Modern day challenges in E-Mail Security Throughout the years, E-Mail has evolved significantly, emerging
March 2005. PGP White Paper. Transport Layer Security (TLS) & Encryption: Complementary Security Tools
 March 2005 PGP White Paper Transport Layer Security (TLS) & Encryption: Complementary Security Tools PGP White Paper TLS & Encryption 1 Table of Contents INTRODUCTION... 2 HISTORY OF TRANSPORT LAYER SECURITY...
March 2005 PGP White Paper Transport Layer Security (TLS) & Encryption: Complementary Security Tools PGP White Paper TLS & Encryption 1 Table of Contents INTRODUCTION... 2 HISTORY OF TRANSPORT LAYER SECURITY...
Digital certificates and SSL
 Digital certificates and SSL 20 out of 33 rated this helpful Applies to: Exchange Server 2013 Topic Last Modified: 2013-08-26 Secure Sockets Layer (SSL) is a method for securing communications between
Digital certificates and SSL 20 out of 33 rated this helpful Applies to: Exchange Server 2013 Topic Last Modified: 2013-08-26 Secure Sockets Layer (SSL) is a method for securing communications between
E-Mail Security. on your terms SOFTSCAN
 E-Mail Security on your terms SOFTSCAN With fraudulent and offensive emails delivered in vast quantities to businesses every day a foolproof email security system is essential. Setting the standards SoftScan
E-Mail Security on your terms SOFTSCAN With fraudulent and offensive emails delivered in vast quantities to businesses every day a foolproof email security system is essential. Setting the standards SoftScan
Receiving Secure Email from Citi For External Customers and Business Partners
 Citi Secure Email Program Receiving Secure Email from Citi For External Customers and Business Partners Protecting the privacy and security of client information is a top priority at Citi. Citi s Secure
Citi Secure Email Program Receiving Secure Email from Citi For External Customers and Business Partners Protecting the privacy and security of client information is a top priority at Citi. Citi s Secure
Secured Mail through PGP Mail Gateway
 Secured Mail through PGP Mail Gateway L. S. Haturusinha, Y. Y. Landersz, A. U. H. Gamage, P. N. Pathiranage, G. T. D. Rodrigo, and M. P. A. W. Gamage Abstract PGP Mail Gateway is a backend server which
Secured Mail through PGP Mail Gateway L. S. Haturusinha, Y. Y. Landersz, A. U. H. Gamage, P. N. Pathiranage, G. T. D. Rodrigo, and M. P. A. W. Gamage Abstract PGP Mail Gateway is a backend server which
(51) Int Cl.: H04L 12/58 (2006.01) H04L 29/06 (2006.01)
 (19) TEPZZ_986 8 B_T (11) EP 1 986 382 B1 (12) EUROPEAN PATENT SPECIFICATION (4) Date of publication and mention of the grant of the patent: 19.02.14 Bulletin 14/08 (1) Int Cl.: H04L 12/8 (06.01) H04L
(19) TEPZZ_986 8 B_T (11) EP 1 986 382 B1 (12) EUROPEAN PATENT SPECIFICATION (4) Date of publication and mention of the grant of the patent: 19.02.14 Bulletin 14/08 (1) Int Cl.: H04L 12/8 (06.01) H04L
Overview. SSL Cryptography Overview CHAPTER 1
 CHAPTER 1 Note The information in this chapter applies to both the ACE module and the ACE appliance unless otherwise noted. The features in this chapter apply to IPv4 and IPv6 unless otherwise noted. Secure
CHAPTER 1 Note The information in this chapter applies to both the ACE module and the ACE appliance unless otherwise noted. The features in this chapter apply to IPv4 and IPv6 unless otherwise noted. Secure
Secure Your Email with Encryption as a Service
 Secure Your Email with Encryption as a Service Janene Casella Symantec Jamie Northey Echoworx Disclaimer Any information regarding pre-release Symantec offerings, future updates or other planned modifications
Secure Your Email with Encryption as a Service Janene Casella Symantec Jamie Northey Echoworx Disclaimer Any information regarding pre-release Symantec offerings, future updates or other planned modifications
Email Privacy. Protecting Your Members. Monday, June 30, 2008 3:00 p.m. - 4:15 p.m. Dena Bauckman, Director of Product Management Zix Corporation
 What We LEARN in Vegas... Comes Home from Vegas! Email Privacy Protecting Your Members Monday, June 30, 2008 3:00 p.m. - 4:15 p.m. Dena Bauckman, Director of Product Management Zix Corporation Massachusetts
What We LEARN in Vegas... Comes Home from Vegas! Email Privacy Protecting Your Members Monday, June 30, 2008 3:00 p.m. - 4:15 p.m. Dena Bauckman, Director of Product Management Zix Corporation Massachusetts
Unifying Information Security. Implementing Encryption on the CLEARSWIFT SECURE Email Gateway
 Unifying Information Security Implementing Encryption on the CLEARSWIFT SECURE Email Gateway Contents 1 Introduction... 4 2 Encryption Options... 5 3 Basics of Encryption... 7 3.1 Public Key... 7 3.2 Private
Unifying Information Security Implementing Encryption on the CLEARSWIFT SECURE Email Gateway Contents 1 Introduction... 4 2 Encryption Options... 5 3 Basics of Encryption... 7 3.1 Public Key... 7 3.2 Private
7 Network Security. 7.1 Introduction 7.2 Improving the Security 7.3 Internet Security Framework. 7.5 Absolute Security?
 7 Network Security 7.1 Introduction 7.2 Improving the Security 7.3 Internet Security Framework 7.4 Firewalls 7.5 Absolute Security? 7.1 Introduction Security of Communications data transport e.g. risk
7 Network Security 7.1 Introduction 7.2 Improving the Security 7.3 Internet Security Framework 7.4 Firewalls 7.5 Absolute Security? 7.1 Introduction Security of Communications data transport e.g. risk
Email Security Solutions
 TECHNOLOGY REPORT Email Security Solutions 1 TECHNOLOGY REPORT SUPPLEMENT EMAIL SECURITY TECHNOLOGY REPORT IF YOUR EMAIL IS SO CRITICAL, CAN YOU BE SURE IT S REALLY REALLY PRIVATE? FIND THE FULL RESULTS
TECHNOLOGY REPORT Email Security Solutions 1 TECHNOLOGY REPORT SUPPLEMENT EMAIL SECURITY TECHNOLOGY REPORT IF YOUR EMAIL IS SO CRITICAL, CAN YOU BE SURE IT S REALLY REALLY PRIVATE? FIND THE FULL RESULTS
SSL Encryption and Traffic Inspection ADDRESSING THE INCREASED 2048-BIT PERFORMANCE DEMANDS OF 2048-BIT SSL CERTIFICATES
 SSL Encryption and Traffic Inspection ADDRESSING THE INCREASED 2048-BIT PERFORMANCE DEMANDS OF 2048-BIT SSL CERTIFICATES Contents Introduction 3 SSL Encryption Basics 3 The Need for SSL Traffic Inspection
SSL Encryption and Traffic Inspection ADDRESSING THE INCREASED 2048-BIT PERFORMANCE DEMANDS OF 2048-BIT SSL CERTIFICATES Contents Introduction 3 SSL Encryption Basics 3 The Need for SSL Traffic Inspection
E-Mail Management Solutions. Spamfinder. MailDepot. MailSealer. 100% spam protection for your business. Compliant, permanent e-mail archiving
 E-Mail Management Solutions Spamfinder MailDepot MailSealer 100% spam protection for your business Compliant, permanent e-mail archiving digital signature and e-mail encryption Spamfinder Anti-spam and
E-Mail Management Solutions Spamfinder MailDepot MailSealer 100% spam protection for your business Compliant, permanent e-mail archiving digital signature and e-mail encryption Spamfinder Anti-spam and
W H I T E PA P E R. Providing Encryption at the Internal Desktop
 W H I T E PA P E R Secure Email Inside the Corporate Network: Providing Encryption at the Internal Desktop Table of Contents Introduction 2 Encryption at the Internal Desktop 2 Current Techniques for Desktop
W H I T E PA P E R Secure Email Inside the Corporate Network: Providing Encryption at the Internal Desktop Table of Contents Introduction 2 Encryption at the Internal Desktop 2 Current Techniques for Desktop
Top 10 Features: Clearswift SECURE Email Gateway
 Top 10 Features: Clearswift SECURE Email Gateway Top 10 Features: Clearswift SECURE Email Gateway Modern business simply couldn t function without email. However, both incoming and outgoing messages can
Top 10 Features: Clearswift SECURE Email Gateway Top 10 Features: Clearswift SECURE Email Gateway Modern business simply couldn t function without email. However, both incoming and outgoing messages can
How To Understand And Understand The Security Of A Key Infrastructure
 Security+ Guide to Network Security Fundamentals, Third Edition Chapter 12 Applying Cryptography Objectives Define digital certificates List the various types of digital certificates and how they are used
Security+ Guide to Network Security Fundamentals, Third Edition Chapter 12 Applying Cryptography Objectives Define digital certificates List the various types of digital certificates and how they are used
Email Encryption Services
 Services ZixCorp provides easy-to-use email encryption services for privacy and regulatory compliance. As the largest email encryption services provider, ZixCorp protects tens of millions of members in
Services ZixCorp provides easy-to-use email encryption services for privacy and regulatory compliance. As the largest email encryption services provider, ZixCorp protects tens of millions of members in
Secure Web Delivery. Ron Miller PIM Manager
 Secure Web Delivery Ron Miller PIM Manager McAfee Email Gateway (MEG) Implemented new MEG solution in January 2014 Enterprise mail routing, virus protection, SPAM filtering, DOS protection with Quarantine
Secure Web Delivery Ron Miller PIM Manager McAfee Email Gateway (MEG) Implemented new MEG solution in January 2014 Enterprise mail routing, virus protection, SPAM filtering, DOS protection with Quarantine
FileCloud Security FAQ
 is currently used by many large organizations including banks, health care organizations, educational institutions and government agencies. Thousands of organizations rely on File- Cloud for their file
is currently used by many large organizations including banks, health care organizations, educational institutions and government agencies. Thousands of organizations rely on File- Cloud for their file
TEAL: Transparent Email Archiving Library
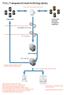 TEAL: Transparent Email Archiving Library 1. Users send & receive email as per normal 2. Existing customer filters remove spam & viruses Filters (Spam, Anti-Virus) 3. Interceptor agent takes a copy of
TEAL: Transparent Email Archiving Library 1. Users send & receive email as per normal 2. Existing customer filters remove spam & viruses Filters (Spam, Anti-Virus) 3. Interceptor agent takes a copy of
Trend Micro Email Encryption (TMEE) Delivering Secure Email. Veli-Pekka Kusmin Pre-Sales Engineer
 Trend Micro Email Encryption (TMEE) Delivering Secure Email Veli-Pekka Kusmin Pre-Sales Engineer Trend Micro Baltics & Finland October 2009 Example #1 True or false: Email is inherently insecure. Answer:
Trend Micro Email Encryption (TMEE) Delivering Secure Email Veli-Pekka Kusmin Pre-Sales Engineer Trend Micro Baltics & Finland October 2009 Example #1 True or false: Email is inherently insecure. Answer:
The DoD Public Key Infrastructure And Public Key-Enabling Frequently Asked Questions
 The DoD Public Key Infrastructure And Public Key-Enabling Frequently Asked Questions May 3, 2004 TABLE OF CONTENTS GENERAL PKI QUESTIONS... 1 1. What is PKI?...1 2. What functionality is provided by a
The DoD Public Key Infrastructure And Public Key-Enabling Frequently Asked Questions May 3, 2004 TABLE OF CONTENTS GENERAL PKI QUESTIONS... 1 1. What is PKI?...1 2. What functionality is provided by a
Consolidated Email Hygiene and Encryption Service E-Hub. Slide 1
 Consolidated Email Hygiene and Encryption Service E-Hub Slide 1 Agenda E-Hub Service Overview E-Hub Benefits & Features E-Hub Rates and Implementation Microsoft FOPE Hygiene Overview Demo Microsoft FOPE
Consolidated Email Hygiene and Encryption Service E-Hub Slide 1 Agenda E-Hub Service Overview E-Hub Benefits & Features E-Hub Rates and Implementation Microsoft FOPE Hygiene Overview Demo Microsoft FOPE
mkryptor allows you to easily send secure emails. This document will give you a technical overview of how. mkryptor is a software product from
 Technical Overview mkryptor allows you to easily send secure emails. This document will give you a technical overview of how. mkryptor is a software product from Contents What is mkryptor? 1 Mkryptor VS
Technical Overview mkryptor allows you to easily send secure emails. This document will give you a technical overview of how. mkryptor is a software product from Contents What is mkryptor? 1 Mkryptor VS
How To Configure Forefront Threat Management Gateway (Forefront) For An Email Server
 Owner of the content within this article is www.isaserver.org Written by Marc Grote www.it-training-grote.de Configuring and using the E-Mail protection feature in Microsoft Forefront Threat Management
Owner of the content within this article is www.isaserver.org Written by Marc Grote www.it-training-grote.de Configuring and using the E-Mail protection feature in Microsoft Forefront Threat Management
Voltage's Encrypted Email
 Voltage's Encrypted Email October 2004. Report #471 Ferris Research Product Brief Sponsored by Ferris Research, Inc. 408 Columbus Ave., Suite 1 San Francisco, Calif. 94133, USA Phone: +1 (415) 986-1414
Voltage's Encrypted Email October 2004. Report #471 Ferris Research Product Brief Sponsored by Ferris Research, Inc. 408 Columbus Ave., Suite 1 San Francisco, Calif. 94133, USA Phone: +1 (415) 986-1414
Secure Email Frequently Asked Questions
 Secure Email Frequently Asked Questions Frequently Asked Questions Contents General Secure Email Questions and Answers Forced TLS Questions and Answers SecureMail Questions and Answers Glossary Support
Secure Email Frequently Asked Questions Frequently Asked Questions Contents General Secure Email Questions and Answers Forced TLS Questions and Answers SecureMail Questions and Answers Glossary Support
Hosted Email Managed by Email Specialists
 Hosted Email Managed by Email Specialists The Mailtrust email system is the premium hosted email platform that provides your business with powerful, secure, and reliable email with absolutely no maintenance
Hosted Email Managed by Email Specialists The Mailtrust email system is the premium hosted email platform that provides your business with powerful, secure, and reliable email with absolutely no maintenance
Glob@lCerts. HIPAA: Briefing for Healthcare IT Security Personnel. Market Overview: HIPAA: Privacy Security and Electronic Transaction Standards
 Glob@lCerts Market Overview: HIPAA: Briefing for Healthcare IT Security Personnel HIPAA: Privacy Security and Electronic Transaction Standards Introduction: The HIPAA (Healthcare Insurance Portability
Glob@lCerts Market Overview: HIPAA: Briefing for Healthcare IT Security Personnel HIPAA: Privacy Security and Electronic Transaction Standards Introduction: The HIPAA (Healthcare Insurance Portability
Why you need secure email
 Why you need secure email WHITE PAPER CONTENTS 1. Executive summary 2. How email works 3. Security threats to your email communications 4. Symmetric and asymmetric encryption 5. Securing your email with
Why you need secure email WHITE PAPER CONTENTS 1. Executive summary 2. How email works 3. Security threats to your email communications 4. Symmetric and asymmetric encryption 5. Securing your email with
anomaly, thus reported to our central servers.
 Cloud Email Firewall Maximum email availability and protection against phishing and advanced threats. If the company email is not protected then the information is not safe Cloud Email Firewall is a solution
Cloud Email Firewall Maximum email availability and protection against phishing and advanced threats. If the company email is not protected then the information is not safe Cloud Email Firewall is a solution
FortiMail Email Filtering. Course 221 (for FortiMail v5.0) Course Overview
 FortiMail Email Filtering Course 221 (for FortiMail v5.0) Course Overview FortiMail Email Filtering is a 2-day instructor-led course with comprehensive hands-on labs to provide you with the skills needed
FortiMail Email Filtering Course 221 (for FortiMail v5.0) Course Overview FortiMail Email Filtering is a 2-day instructor-led course with comprehensive hands-on labs to provide you with the skills needed
SIP Security Controllers. Product Overview
 SIP Security Controllers Product Overview Document Version: V1.1 Date: October 2008 1. Introduction UM Labs have developed a range of perimeter security gateways for VoIP and other applications running
SIP Security Controllers Product Overview Document Version: V1.1 Date: October 2008 1. Introduction UM Labs have developed a range of perimeter security gateways for VoIP and other applications running
Case Study for Layer 3 Authentication and Encryption
 CHAPTER 2 Case Study for Layer 3 Authentication and Encryption This chapter explains the basic tasks for configuring a multi-service, extranet Virtual Private Network (VPN) between a Cisco Secure VPN Client
CHAPTER 2 Case Study for Layer 3 Authentication and Encryption This chapter explains the basic tasks for configuring a multi-service, extranet Virtual Private Network (VPN) between a Cisco Secure VPN Client
OWA vs. MDM. Once important area to consider is the impact on security and compliance policies by users bringing their own devices (BYOD) to work.
 OWA vs. MDM Introduction SmartPhones and tablet devices are becoming a common fixture in the corporate environment. As feature phones are replaced with new devices such as iphone s, ipad s, and Android
OWA vs. MDM Introduction SmartPhones and tablet devices are becoming a common fixture in the corporate environment. As feature phones are replaced with new devices such as iphone s, ipad s, and Android
E Mail Encryption End User Guide
 E Mail Encryption End User Guide TABLE OF CONTENTS Why Use Email Encryption... 2 What is a Registered Envelope... 2 Features & Benefits... 2 Security Policies... 2 How to Compose and Send an Encrypted
E Mail Encryption End User Guide TABLE OF CONTENTS Why Use Email Encryption... 2 What is a Registered Envelope... 2 Features & Benefits... 2 Security Policies... 2 How to Compose and Send an Encrypted
Cornerstones of Security
 Internet Security Cornerstones of Security Authenticity the sender (either client or server) of a message is who he, she or it claims to be Privacy the contents of a message are secret and only known to
Internet Security Cornerstones of Security Authenticity the sender (either client or server) of a message is who he, she or it claims to be Privacy the contents of a message are secret and only known to
Email Encryption Made Simple
 Email Encryption Made Simple For organizations large or small Table of Contents Who Is Reading Your Email?....3 The Three Options Explained....3 Organization-to-organization encryption....3 Secure portal
Email Encryption Made Simple For organizations large or small Table of Contents Who Is Reading Your Email?....3 The Three Options Explained....3 Organization-to-organization encryption....3 Secure portal
Tumbleweed MailGate Secure Messenger
 EMAIL SECURITY SOLUTIONS TECHNOLOGY REPORT Tumbleweed MailGate Secure Messenger JANUARY 2007 www.westcoastlabs.org 2 EMAIL SECURITY SOLUTIONS TECHNOLOGY REPORT CONTENTS MailGate Secure Messenger Tumbleweed
EMAIL SECURITY SOLUTIONS TECHNOLOGY REPORT Tumbleweed MailGate Secure Messenger JANUARY 2007 www.westcoastlabs.org 2 EMAIL SECURITY SOLUTIONS TECHNOLOGY REPORT CONTENTS MailGate Secure Messenger Tumbleweed
ITSC Training Courses Student IT Competence Programme SIIS1 Information Security
 ITSC Training Courses Student IT Competence Programme SI1 2012 2013 Prof. Chan Yuen Yan, Rosanna Department of Engineering The Chinese University of Hong Kong SI1-1 Course Outline What you should know
ITSC Training Courses Student IT Competence Programme SI1 2012 2013 Prof. Chan Yuen Yan, Rosanna Department of Engineering The Chinese University of Hong Kong SI1-1 Course Outline What you should know
REMOTE ASSISTANCE SOLUTIONS Private Server
 REMOTE ASSISTANCE SOLUTIONS Private Server UBIQUITY components Control Center: client on the remote assistance PC Ubiquity Runtime: software installed on the remote device Ubiquity Server Infrastructure:
REMOTE ASSISTANCE SOLUTIONS Private Server UBIQUITY components Control Center: client on the remote assistance PC Ubiquity Runtime: software installed on the remote device Ubiquity Server Infrastructure:
Sending E-mails without the risk! Secure E-Mail Communications with Rohde & Schwarz
 Sending E-mails without the risk! Secure E-Mail Communications with Rohde & Schwarz Guide V1.1.1 Only the most recent version of this document is valid. Contents I List of figures... 2 1 Foreword... 3
Sending E-mails without the risk! Secure E-Mail Communications with Rohde & Schwarz Guide V1.1.1 Only the most recent version of this document is valid. Contents I List of figures... 2 1 Foreword... 3
Email Encryption Services
 Services ZixCorp provides easy-to-use email encryption services for privacy and regulatory compliance. As the largest email encryption services provider, ZixCorp protects tens of millions of members in
Services ZixCorp provides easy-to-use email encryption services for privacy and regulatory compliance. As the largest email encryption services provider, ZixCorp protects tens of millions of members in
Sync Security and Privacy Brief
 Introduction Security and privacy are two of the leading issues for users when transferring important files. Keeping data on-premises makes business and IT leaders feel more secure, but comes with technical
Introduction Security and privacy are two of the leading issues for users when transferring important files. Keeping data on-premises makes business and IT leaders feel more secure, but comes with technical
Secured email Global Communication version 4.6
 Secured email Global Communication version 4.6 A new and improved way to receive Secured email Authors: Daniel Nilsson and Jeff Sherwood May 11, 2010 Content Introduction...3 Secured email...4 Sending
Secured email Global Communication version 4.6 A new and improved way to receive Secured email Authors: Daniel Nilsson and Jeff Sherwood May 11, 2010 Content Introduction...3 Secured email...4 Sending
Evaluation Guide. eprism Messaging Security Suite. 800-782-3762 www.edgewave.com V8.200
 800-782-3762 www.edgewave.com Welcome to EdgeWave Messaging Security! This short guide is intended to help administrators setup and test the EdgeWave Messaging Security Suite for evaluation purposes. A
800-782-3762 www.edgewave.com Welcome to EdgeWave Messaging Security! This short guide is intended to help administrators setup and test the EdgeWave Messaging Security Suite for evaluation purposes. A
How To Protect Your Email From Being Hacked On A Pc Or Mac Or Ipa From Being Stolen On A Network (For A Free Download) On A Computer Or Ipo (For Free) On Your Pc Or Ipom (For An Ipo
 The Case for Email Security secure, premium by Erik Kangas, President, Lux Scientiae Section 1: Introduction to Email Security You may already know that email is insecure; however, it may surprise you
The Case for Email Security secure, premium by Erik Kangas, President, Lux Scientiae Section 1: Introduction to Email Security You may already know that email is insecure; however, it may surprise you
Email Migration Project Plan for Cisco Cloud Email Security
 Sales Tool Email Migration Project Plan for Cisco Cloud Email Security 2014 Cisco and/or its affiliates. All rights reserv ed. This document is Cisco Conf idential. For Channel Partner use only. Not f
Sales Tool Email Migration Project Plan for Cisco Cloud Email Security 2014 Cisco and/or its affiliates. All rights reserv ed. This document is Cisco Conf idential. For Channel Partner use only. Not f
SIP and VoIP 1 / 44. SIP and VoIP
 What is SIP? What s a Control Channel? History of Signaling Channels Signaling and VoIP Complexity Basic SIP Architecture Simple SIP Calling Alice Calls Bob Firewalls and NATs SIP URIs Multiple Proxies
What is SIP? What s a Control Channel? History of Signaling Channels Signaling and VoIP Complexity Basic SIP Architecture Simple SIP Calling Alice Calls Bob Firewalls and NATs SIP URIs Multiple Proxies
a) Encryption is enabled on the access point. b) The conference room network is on a separate virtual local area network (VLAN)
 MIS5206 Week 12 Your Name Date 1. Which significant risk is introduced by running the file transfer protocol (FTP) service on a server in a demilitarized zone (DMZ)? a) User from within could send a file
MIS5206 Week 12 Your Name Date 1. Which significant risk is introduced by running the file transfer protocol (FTP) service on a server in a demilitarized zone (DMZ)? a) User from within could send a file
An Introduction to Secure Email. Presented by: Addam Schroll IT Security & Privacy Analyst
 An Introduction to Secure Email Presented by: Addam Schroll IT Security & Privacy Analyst Topics Secure Email Basics Types of Secure Email Walkthroughs 2 Secure Email Services Confidentiality Message Integrity
An Introduction to Secure Email Presented by: Addam Schroll IT Security & Privacy Analyst Topics Secure Email Basics Types of Secure Email Walkthroughs 2 Secure Email Services Confidentiality Message Integrity
Advanced Mail Server Settings Options for Shared Hosting Clients
 Own Web Now Corp Advanced Mail Server Settings Options for Shared Hosting Clients The following document describes the more advanced mail server settings that are optional for shared hosting clients. These
Own Web Now Corp Advanced Mail Server Settings Options for Shared Hosting Clients The following document describes the more advanced mail server settings that are optional for shared hosting clients. These
Overview of CSS SSL. SSL Cryptography Overview CHAPTER
 CHAPTER 1 Secure Sockets Layer (SSL) is an application-level protocol that provides encryption technology for the Internet, ensuring secure transactions such as the transmission of credit card numbers
CHAPTER 1 Secure Sockets Layer (SSL) is an application-level protocol that provides encryption technology for the Internet, ensuring secure transactions such as the transmission of credit card numbers
to hide away details from prying eyes. Pretty Good Privacy (PGP) utilizes many
 In the world of secure email, there are many options from which to choose from to hide away details from prying eyes. Pretty Good Privacy (PGP) utilizes many cryptographical concepts to achieve a supposedly
In the world of secure email, there are many options from which to choose from to hide away details from prying eyes. Pretty Good Privacy (PGP) utilizes many cryptographical concepts to achieve a supposedly
Parla, Secure Cloud Email
 Parla, Secure Cloud Email Secure Email, Instant Messaging, Calendar, Contacts, Tasks, File sharing and Notes across all devices The 1 st Secure Email and Instant Messaging from and European Security Vendor
Parla, Secure Cloud Email Secure Email, Instant Messaging, Calendar, Contacts, Tasks, File sharing and Notes across all devices The 1 st Secure Email and Instant Messaging from and European Security Vendor
Simple security is better security Or: How complexity became the biggest security threat
 Simple security is better security Or: How complexity became the biggest security threat Christoph Litzbach, Pre-Sales Engineer NSG 1 What do they have in common? DATA BREACH 2 Security is HARD! Components
Simple security is better security Or: How complexity became the biggest security threat Christoph Litzbach, Pre-Sales Engineer NSG 1 What do they have in common? DATA BREACH 2 Security is HARD! Components
Email Encryption Made Simple
 White Paper For organizations large or small Table of Contents Who Is Reading Your Email? 3 The Three Options Explained 3 Organization-to-organization encryption 3 Secure portal or organization-to-user
White Paper For organizations large or small Table of Contents Who Is Reading Your Email? 3 The Three Options Explained 3 Organization-to-organization encryption 3 Secure portal or organization-to-user
BUILT FOR YOU. Contents. Cloudmore Exchange
 BUILT FOR YOU Introduction is designed so it is as cost effective as possible for you to configure, provision and manage to a specification to suit your organisation. With a proven history of delivering
BUILT FOR YOU Introduction is designed so it is as cost effective as possible for you to configure, provision and manage to a specification to suit your organisation. With a proven history of delivering
Network Security Foundations
 Network Security Foundations Matthew Strebe O San SrBBC Francisco London Introduction xv Chapter 1 Security Principles 1 Why Computers Aren't Secure 2 The History of Computer Security 4-1945 5 1945-1955
Network Security Foundations Matthew Strebe O San SrBBC Francisco London Introduction xv Chapter 1 Security Principles 1 Why Computers Aren't Secure 2 The History of Computer Security 4-1945 5 1945-1955
How To Encrypt Data With Encryption
 USING ENCRYPTION TO PROTECT SENSITIVE INFORMATION Commonwealth Office of Technology Security Month Seminars Alternate Title? Boy, am I surprised. The Entrust guy who has mentioned PKI during every Security
USING ENCRYPTION TO PROTECT SENSITIVE INFORMATION Commonwealth Office of Technology Security Month Seminars Alternate Title? Boy, am I surprised. The Entrust guy who has mentioned PKI during every Security
Secure Data Exchange Solution
 Secure Data Exchange Solution I. CONTENTS I. CONTENTS... 1 II. INTRODUCTION... 2 OVERVIEW... 2 COPYRIGHTS AND TRADEMARKS... 2 III. SECURE DOCUMENT EXCHANGE SOLUTIONS... 3 INTRODUCTION... 3 Certificates
Secure Data Exchange Solution I. CONTENTS I. CONTENTS... 1 II. INTRODUCTION... 2 OVERVIEW... 2 COPYRIGHTS AND TRADEMARKS... 2 III. SECURE DOCUMENT EXCHANGE SOLUTIONS... 3 INTRODUCTION... 3 Certificates
Internet Architecture
 Internet Architecture Lecture 10: How Email Work Assistant Teacher Samraa Adnan Al-Asadi 1 How Email Works Electronic mail, or email, might be the most heavily used feature of the Internet. You can use
Internet Architecture Lecture 10: How Email Work Assistant Teacher Samraa Adnan Al-Asadi 1 How Email Works Electronic mail, or email, might be the most heavily used feature of the Internet. You can use
Securing your Online Data Transfer with SSL
 Securing your Online Data Transfer with SSL A GUIDE TO UNDERSTANDING SSL CERTIFICATES, how they operate and their application 1. Overview 2. What is SSL? 3. How to tell if a Website is Secure 4. What does
Securing your Online Data Transfer with SSL A GUIDE TO UNDERSTANDING SSL CERTIFICATES, how they operate and their application 1. Overview 2. What is SSL? 3. How to tell if a Website is Secure 4. What does
SSL VPN vs. IPSec VPN
 SSL VPN vs. IPSec VPN White Paper 254 E. Hacienda Avenue Campbell, CA 95008 www.arraynetworks.net (408) 378-6800 1 SSL VPN vs. IPSec VPN Copyright 2002 Array Networks, Inc. SSL VPN vs. IPSec VPN White
SSL VPN vs. IPSec VPN White Paper 254 E. Hacienda Avenue Campbell, CA 95008 www.arraynetworks.net (408) 378-6800 1 SSL VPN vs. IPSec VPN Copyright 2002 Array Networks, Inc. SSL VPN vs. IPSec VPN White
Network Security [2] Plain text Encryption algorithm Public and private key pair Cipher text Decryption algorithm. See next slide
![Network Security [2] Plain text Encryption algorithm Public and private key pair Cipher text Decryption algorithm. See next slide Network Security [2] Plain text Encryption algorithm Public and private key pair Cipher text Decryption algorithm. See next slide](/thumbs/24/4351346.jpg) Network Security [2] Public Key Encryption Also used in message authentication & key distribution Based on mathematical algorithms, not only on operations over bit patterns (as conventional) => much overhead
Network Security [2] Public Key Encryption Also used in message authentication & key distribution Based on mathematical algorithms, not only on operations over bit patterns (as conventional) => much overhead
WHAT S NEW IN WEBSENSE TRITON RELEASE 7.8
 WHAT S NEW IN WEBSENSE TRITON RELEASE 7.8 Overview Global organizations are constantly battling with advanced persistent threats (APTs) and targeted attacks focused on extracting intellectual property
WHAT S NEW IN WEBSENSE TRITON RELEASE 7.8 Overview Global organizations are constantly battling with advanced persistent threats (APTs) and targeted attacks focused on extracting intellectual property
Hardware and Software Security
 Today, with the big advancement of technology and the need to share data globally at all time. Security has become one of the most important topics when we talk about data sharing. This means that the
Today, with the big advancement of technology and the need to share data globally at all time. Security has become one of the most important topics when we talk about data sharing. This means that the
PKI Contacts PKI for Fraunhofer Contacts
 Fraunhofer Competence Center PKI PKI Contacts PKI for Fraunhofer Contacts User manual for communication partners of the Fraunhofer-Gesellschaft Author[s]: Uwe Bendisch, Maximilian Gottwald As at: 15.10.2013
Fraunhofer Competence Center PKI PKI Contacts PKI for Fraunhofer Contacts User manual for communication partners of the Fraunhofer-Gesellschaft Author[s]: Uwe Bendisch, Maximilian Gottwald As at: 15.10.2013
How To Secure Your Email From Being Hacked On A Pc Or Mac Or Ipad (For Free) For A Long Time (For A Long Period Of Time) For Free (For Commercial) For Your Money (For Business) For The Long Term
 CYBER-ATLAS TOOLKIT TOOLKIT: REFERENCES FREE EMAIL ENCRYPTION SOFTWARE BEFORE YOU START Limited functionality, limited capacity, limited usage, limited platforms or restrictions disallowing commercial
CYBER-ATLAS TOOLKIT TOOLKIT: REFERENCES FREE EMAIL ENCRYPTION SOFTWARE BEFORE YOU START Limited functionality, limited capacity, limited usage, limited platforms or restrictions disallowing commercial
 Securing your Online Data Transfer with SSL A GUIDE TO UNDERSTANDING SSL CERTIFICATES, how they operate and their application INDEX 1. Overview 2. What is SSL? 3. How to tell if a Website is Secure 4.
Securing your Online Data Transfer with SSL A GUIDE TO UNDERSTANDING SSL CERTIFICATES, how they operate and their application INDEX 1. Overview 2. What is SSL? 3. How to tell if a Website is Secure 4.
MESSAGING SECURITY GATEWAY. Detect attacks before they enter your network
 MESSAGING SECURITY GATEWAY Detect attacks before they enter your network OVERVIEW This document explains the functionality of F-Secure Messaging Security Gateway (MSG) what it is, what it does, and how
MESSAGING SECURITY GATEWAY Detect attacks before they enter your network OVERVIEW This document explains the functionality of F-Secure Messaging Security Gateway (MSG) what it is, what it does, and how
Internet threats: steps to security for your small business
 Internet threats: 7 steps to security for your small business Proactive solutions for small businesses A restaurant offers free WiFi to its patrons. The controller of an accounting firm receives a confidential
Internet threats: 7 steps to security for your small business Proactive solutions for small businesses A restaurant offers free WiFi to its patrons. The controller of an accounting firm receives a confidential
UNDERSTANDING PKI: CONCEPTS, STANDARDS, AND DEPLOYMENT CONSIDERATIONS, 2ND EDITION
 UNDERSTANDING PKI: CONCEPTS, STANDARDS, AND DEPLOYMENT CONSIDERATIONS, 2ND EDITION Foreword. Preface. About the Authors. I. CONCEPTS. 1. Introduction. 2. Public-Key Cryptography. Symmetric versus Asymmetric
UNDERSTANDING PKI: CONCEPTS, STANDARDS, AND DEPLOYMENT CONSIDERATIONS, 2ND EDITION Foreword. Preface. About the Authors. I. CONCEPTS. 1. Introduction. 2. Public-Key Cryptography. Symmetric versus Asymmetric
Taxonomy of E-Mail Security Protocol
 Taxonomy of E-Mail Security Protocol Ankur Dumka, Ravi Tomar, J.C.Patni, Abhineet Anand Assistant Professor, Centre for information Technology, University of Petroleum and Energy Studies,Dehradun, India
Taxonomy of E-Mail Security Protocol Ankur Dumka, Ravi Tomar, J.C.Patni, Abhineet Anand Assistant Professor, Centre for information Technology, University of Petroleum and Energy Studies,Dehradun, India
