BFC Product Evaluation and Selection Process DoD Biometrics Fusion Center. Executive Officer
|
|
|
- Camilla Leonard
- 8 years ago
- Views:
Transcription
1 BFC Product Evaluation and Selection Process DoD Biometrics Fusion Center Executive Officer 1
2 Purpose of Briefing To present the selection and acquisition process for biometric devices at the BFC. 2
3 Briefing Agenda Why Evaluate Biometrics Products? DoD Biometrics Organization Biometrics Product List BFC Biometric Product Testing Life Cycle Acquisition and Selection Process Selection & Evaluation Criteria Schedule 3
4 Why Evaluate Biometrics Products? To: Ensure compliance with Federal and DoD acquisition criteria Categorize products for appropriate DoD applications Ensure performance is in keeping with proposed application Gain information to ensure DoD usage policies and regulations keep step with technology development 4
5 DoD Biometrics Organization Chain of Command OSD Service Reps DA CIO G6 BMO BMO - Biometrics Management Office (DC) Oversight Planning / Budgeting Policy Development Acquisition DoD Requirements Coordination with non-dod Agencies DoD Awareness of Biometrics BFC Liaison Personnel BFC - Biometrics Fusion Center (WV) Biometric KnowledgeBase Standards Development Industry/Academia Point of Contact Central Repository DoD Pilot Projects/Technology Demonstrations Common Access Card Biometrics Test Database Test & Evaluation Biometric Product List 5
6 Biometrics Product List Will assist DoD members in determining appropriate biometrics technologies for their application Will assist DoD members in selecting approved biometrics products for their application Will give information on where to acquire the selected product Will give information on vendors that can integrate the selected product 6
7 How Does the DoD Evaluate Biometrics Products? BFC Biometric Product Testing Life Cycle Product Selection Product Acquisition Product Assessment Controlled Environment Testing Field Testing Posting to Biometrics Product List 7
8 How Does the DoD Acquire Products for Evaluation? Product Discovery Product Research Quarterly Product Selection Board Product Acquisition 8
9 Selection Process Product Discovery Customers Research Solicitation Evaluation Criteria Meet Criteria N Y Acquisition Product Assessment Stop Knowledge Base N Results Positive Y Controlled Environmental Test Field Test Or Pilot Biometric Product List 9
10 Product Discovery Continuous Vendor and Product Research Attend Conferences and Symposiums Internet Research Direct Contact by Vendors Upgrades for products that have undergone previous assessment and/or testing DoD BFC Customer Requests Special Project Test Request Pilot and Technology Demonstration Request 10
11 Research Product Information Collect Product Information and Documentation Send Vendor Product Questionnaire Research Cost Information Research Maintenance Research Vendor Maturity and Stability Schedule Vendor Demonstration at BFC Create Product Folder for the Quarterly Product Selection Board 11
12 Quarterly Product Selection Board Holds quarterly product selection meetings Reviews the overall needs of the organization in accordance with BMO mission statement Ensures proposed list reflects current emphasis of DoD Reviews list of products proposed to the Board Selects products to be evaluated Authorizes acquisition of products for evaluation 12
13 Product Selection Criteria Be a (COTS or GOTS) product Run on currently fielded Operating System (OS) unless the product is designed as a stand-alone product Have backup/restore capabilities Must have logging and reporting capabilities Have encryption Note: New or unique technologies that do not meet criteria may be evaluated for purposes of education and preparation for future applications 13
14 Product Selection Criteria (cont.) Adherence to DoD & Industry Standards will also be measured. Preference is given to products that fall into categories below: BioAPI (Biometric Application Program Interface) CBEFF (Common Biometric Exchange File Format) FIPS 140 Level 2 (Federal Information Processing Standards) NIAP (National Information Assurance Program) Section 508 (Section 508 of the Rehabilitation Act of 1973, as amended) ANSI B10.8 (Fingerprint Minutia Exchange Format) X9.84 (American National Standard Biometric Information Management and Security) 14
15 Projected Schedule Q2 Product Selection Research Products 9/23/02-11/15/02 Product Selection Board Meeting 11/19/02-11/19/02 Write Report/Organize Data 11/20/02-11/22/02 Procure Products 12/02/02-12/31/02 15
16 Summary Why Evaluate Biometrics Products? DoD Biometrics Organization Biometrics Product List BFC Biometric Product Testing Life Cycle Acquisition and Selection Process Selection & Evaluation Criteria Schedule 16
17 DoD BFC Vendor Contact Information DoD Biometrics Fusion Center 1400 Aviation Way Bridgeport, WV Phone: Fax:
DoD Cloud Computing Strategy Needs Implementation Plan and Detailed Waiver Process
 Inspector General U.S. Department of Defense Report No. DODIG-2015-045 DECEMBER 4, 2014 DoD Cloud Computing Strategy Needs Implementation Plan and Detailed Waiver Process INTEGRITY EFFICIENCY ACCOUNTABILITY
Inspector General U.S. Department of Defense Report No. DODIG-2015-045 DECEMBER 4, 2014 DoD Cloud Computing Strategy Needs Implementation Plan and Detailed Waiver Process INTEGRITY EFFICIENCY ACCOUNTABILITY
Department of Defense INSTRUCTION
 Department of Defense INSTRUCTION NUMBER 8440.01 December 24, 2015 DoD CIO SUBJECT: DoD Information Technology (IT) Service Management (ITSM) References: See Enclosure 1 1. PURPOSE. Pursuant to the authority
Department of Defense INSTRUCTION NUMBER 8440.01 December 24, 2015 DoD CIO SUBJECT: DoD Information Technology (IT) Service Management (ITSM) References: See Enclosure 1 1. PURPOSE. Pursuant to the authority
State of South Carolina Policy Guidance and Training
 DRAFT For Discussion Purposes Only State of South Carolina Policy Guidance and Training Policy Workshop All Agencies Information Systems (IS) Acquisitions, Development, and Maintenance Policy April/May
DRAFT For Discussion Purposes Only State of South Carolina Policy Guidance and Training Policy Workshop All Agencies Information Systems (IS) Acquisitions, Development, and Maintenance Policy April/May
Managing Open Source Code Best Practices
 Managing Open Source Code Best Practices September 24, 2008 Agenda Welcome and Introduction Eran Strod Open Source Best Practices Hal Hearst Questions & Answers Next Steps About Black Duck Software Accelerate
Managing Open Source Code Best Practices September 24, 2008 Agenda Welcome and Introduction Eran Strod Open Source Best Practices Hal Hearst Questions & Answers Next Steps About Black Duck Software Accelerate
Piloting Supply Chain Risk Management Practices for Federal Information Systems
 Piloting Supply Chain Risk Management Practices for Federal Information Systems Marianne Swanson Computer Security Division Information Technology Laboratory Agenda Terms and Background Implementing Supply
Piloting Supply Chain Risk Management Practices for Federal Information Systems Marianne Swanson Computer Security Division Information Technology Laboratory Agenda Terms and Background Implementing Supply
W3C Speaker Identification and Verification Workshop
 W3C Speaker Identification and Verification Workshop Speaker Verification in a Multi-Vendor Environment Mr Ross Summerfield (with support from Dr Ted Dunstone and Dr Clive Summerfield) What is Centrelink?
W3C Speaker Identification and Verification Workshop Speaker Verification in a Multi-Vendor Environment Mr Ross Summerfield (with support from Dr Ted Dunstone and Dr Clive Summerfield) What is Centrelink?
FSC Group 63: Alarm and Security
 General Services Administration Federal Supply Service Authorized Federal Supply Schedule Price List On-line access to contract ordering information, terms and conditions, up-to-date pricing, and the option
General Services Administration Federal Supply Service Authorized Federal Supply Schedule Price List On-line access to contract ordering information, terms and conditions, up-to-date pricing, and the option
Open Source Software in the US Government & Military. Joshua L. Davis joshua.davis@gtri.gatech.edu
 Open Source Software in the US Government & Military Joshua L. Davis joshua.davis@gtri.gatech.edu Gov IT Spending Trends Referenceh(p://www.itdashboard. Reference: h*p://www.itdashboard.gov The Current
Open Source Software in the US Government & Military Joshua L. Davis joshua.davis@gtri.gatech.edu Gov IT Spending Trends Referenceh(p://www.itdashboard. Reference: h*p://www.itdashboard.gov The Current
Product Testing Programs
 Catalog of USG Product Programs Version 1.0 November 15, 2010 NSTC Subcommittee on s and Identity Management 1. Introduction This Catalog of USG Product Programs (Catalog) supplements the Registry of USG,
Catalog of USG Product Programs Version 1.0 November 15, 2010 NSTC Subcommittee on s and Identity Management 1. Introduction This Catalog of USG Product Programs (Catalog) supplements the Registry of USG,
DoDI 8500-2 IA Control Checklist - MAC 3-Public. Version 1, Release 1.4. 28 March 2008
 DoDI 8500-2 IA Control Checklist - MAC 3-Public Version 1, Release 1.4 Developed by DISA for the DOD UNTILL FILLED IN CIRCLE ONE FOR OFFICIAL USE ONLY (mark each page) CONFIDENTIAL and SECRET (mark each
DoDI 8500-2 IA Control Checklist - MAC 3-Public Version 1, Release 1.4 Developed by DISA for the DOD UNTILL FILLED IN CIRCLE ONE FOR OFFICIAL USE ONLY (mark each page) CONFIDENTIAL and SECRET (mark each
Department of Defense DIRECTIVE
 Department of Defense DIRECTIVE NUMBER 5144.02 November 21, 2014 DCMO SUBJECT: DoD Chief Information Officer (DoD CIO) References: See Enclosure 1. PURPOSE. Under the authority vested in the Secretary
Department of Defense DIRECTIVE NUMBER 5144.02 November 21, 2014 DCMO SUBJECT: DoD Chief Information Officer (DoD CIO) References: See Enclosure 1. PURPOSE. Under the authority vested in the Secretary
Report via OMB s Integrated Data Collection (IDC), https://community.max.gov/x/lhtgjw 10
 EXECUTIVE OFFICE OF THE PRESIDENT OFFICE OF MANAGEMENT AND BUDGET WASHINGTON, D.C. 20503 June 2, 2016 M-16-12 MEMORANDUM FOR THE HEADS OF DEPARTMENTS AND AGENCIES FROM: Anne E. Rung United States Chief
EXECUTIVE OFFICE OF THE PRESIDENT OFFICE OF MANAGEMENT AND BUDGET WASHINGTON, D.C. 20503 June 2, 2016 M-16-12 MEMORANDUM FOR THE HEADS OF DEPARTMENTS AND AGENCIES FROM: Anne E. Rung United States Chief
Information Systems Security Line of Business (ISS LoB)
 Information Systems Security Line of Business (ISS LoB) Information Security and Privacy Advisory Board George Washington University Washington, DC March 22, 2007 Agenda Background Status Next Steps Background
Information Systems Security Line of Business (ISS LoB) Information Security and Privacy Advisory Board George Washington University Washington, DC March 22, 2007 Agenda Background Status Next Steps Background
Department of the Navy ebusiness Operations Office
 ebus iness Innovation DON Card Management www.don-ebusiness.navsup.navy.mil Department of the Navy ebusiness Operations Office Presented by: Ms. Karen Meloy Deputy Commander, DON ebusiness Operations Office
ebus iness Innovation DON Card Management www.don-ebusiness.navsup.navy.mil Department of the Navy ebusiness Operations Office Presented by: Ms. Karen Meloy Deputy Commander, DON ebusiness Operations Office
Department of Defense INSTRUCTION
 Department of Defense INSTRUCTION NUMBER 8320.03 November 4, 2015 USD(AT&L) SUBJECT: Unique Identification (UID) Standards for Supporting DoD Net-Centric Operations References: See Enclosure 1 1. PURPOSE.
Department of Defense INSTRUCTION NUMBER 8320.03 November 4, 2015 USD(AT&L) SUBJECT: Unique Identification (UID) Standards for Supporting DoD Net-Centric Operations References: See Enclosure 1 1. PURPOSE.
DoDI 8500-2 IA Control Checklist - MAC 2-Sensitive. Version 1, Release 1.4. 28 March 2008
 DoDI 8500-2 IA Control Checklist - MAC 2-Sensitive Version 1, Release 1.4 Developed by DISA for the DOD UNTILL FILLED IN CIRCLE ONE FOR OFFICIAL USE ONLY (mark each page) CONFIDENTIAL and SECRET (mark
DoDI 8500-2 IA Control Checklist - MAC 2-Sensitive Version 1, Release 1.4 Developed by DISA for the DOD UNTILL FILLED IN CIRCLE ONE FOR OFFICIAL USE ONLY (mark each page) CONFIDENTIAL and SECRET (mark
An E-Procurement Overview
 NC E-Procurement @ Your Service An E-Procurement Overview Department of Administration Division of Purchase and Contract Presented to House Select Committee on E-Procurement February 15, 2012 Sam Byassee
NC E-Procurement @ Your Service An E-Procurement Overview Department of Administration Division of Purchase and Contract Presented to House Select Committee on E-Procurement February 15, 2012 Sam Byassee
Department of Defense INSTRUCTION
 Department of Defense INSTRUCTION NUMBER 8523.01 April 22, 2008 ASD(NII)/DoD CIO SUBJECT: Communications Security (COMSEC) References: (a) DoD Directive C-5200.5, Communications Security (COMSEC) (U),
Department of Defense INSTRUCTION NUMBER 8523.01 April 22, 2008 ASD(NII)/DoD CIO SUBJECT: Communications Security (COMSEC) References: (a) DoD Directive C-5200.5, Communications Security (COMSEC) (U),
Department of Military Affairs. Service-disabled Veteran, Minority and Women Business Participation Plan
 Department of Military Affairs Service-disabled Veteran, Minority and Women Business Participation Plan TABLE OF CONTENTS SUBJECT PAGE Small Business Participation Mission Statement...1 Small Business
Department of Military Affairs Service-disabled Veteran, Minority and Women Business Participation Plan TABLE OF CONTENTS SUBJECT PAGE Small Business Participation Mission Statement...1 Small Business
FSIS DIRECTIVE 1306.3
 UNITED STATES DEPARTMENT OF AGRICULTURE FOOD SAFETY AND INSPECTION SERVICE WASHINGTON, DC FSIS DIRECTIVE 1306.3 REVISION 1 12/13/12 CONFIGURATION MANAGEMENT (CM) OF SECURITY CONTROLS FOR INFORMATION SYSTEMS
UNITED STATES DEPARTMENT OF AGRICULTURE FOOD SAFETY AND INSPECTION SERVICE WASHINGTON, DC FSIS DIRECTIVE 1306.3 REVISION 1 12/13/12 CONFIGURATION MANAGEMENT (CM) OF SECURITY CONTROLS FOR INFORMATION SYSTEMS
Federal Procurement Data System - FPDS
 Federal Procurement Data System - FPDS Melea Crouse Asst. Assoc. Director Office of Small Business Program 23 April 2015 US Army Corps of Engineers Session Agenda Defining the Federal Procurement Data
Federal Procurement Data System - FPDS Melea Crouse Asst. Assoc. Director Office of Small Business Program 23 April 2015 US Army Corps of Engineers Session Agenda Defining the Federal Procurement Data
GAO MAJOR AUTOMATED INFORMATION SYSTEMS. Selected Defense Programs Need to Implement Key Acquisition Practices
 GAO United States Government Accountability Office Report to Congressional Addressees March 2013 MAJOR AUTOMATED INFORMATION SYSTEMS Selected Defense Programs Need to Implement Key Acquisition Practices
GAO United States Government Accountability Office Report to Congressional Addressees March 2013 MAJOR AUTOMATED INFORMATION SYSTEMS Selected Defense Programs Need to Implement Key Acquisition Practices
The State of DoD Biometrics
 The State of DoD Biometrics Biometrics Consortium Conference 22 Sep 2010 Mr Tom Dee Director, Defense Biometrics Director, JRAC OSD (AT&L), DDR&E thomas.dee@osd.mil 1 Agenda What We ve Done Biometrics
The State of DoD Biometrics Biometrics Consortium Conference 22 Sep 2010 Mr Tom Dee Director, Defense Biometrics Director, JRAC OSD (AT&L), DDR&E thomas.dee@osd.mil 1 Agenda What We ve Done Biometrics
Department of Defense DIRECTIVE
 Department of Defense DIRECTIVE NUMBER 5505.13E March 1, 2010 ASD(NII)/DoD CIO SUBJECT: DoD Executive Agent (EA) for the DoD Cyber Crime Center (DC3) References: See Enclosure 1 1. PURPOSE. This Directive:
Department of Defense DIRECTIVE NUMBER 5505.13E March 1, 2010 ASD(NII)/DoD CIO SUBJECT: DoD Executive Agent (EA) for the DoD Cyber Crime Center (DC3) References: See Enclosure 1 1. PURPOSE. This Directive:
Audit of the Board s Information Security Program
 Board of Governors of the Federal Reserve System Audit of the Board s Information Security Program Office of Inspector General November 2011 November 14, 2011 Board of Governors of the Federal Reserve
Board of Governors of the Federal Reserve System Audit of the Board s Information Security Program Office of Inspector General November 2011 November 14, 2011 Board of Governors of the Federal Reserve
PhillyStat. Office of Innovation & Technology (IT) Fiscal Year End Report July 11, 2012. Office of Innovation and Technology
 PhillyStat Office of Innovation & Technology (IT) Fiscal Year End Report July 11, 2012 Introduction About PhillyStat PhillyStat is the City of Philadelphia s performance management program, led by the
PhillyStat Office of Innovation & Technology (IT) Fiscal Year End Report July 11, 2012 Introduction About PhillyStat PhillyStat is the City of Philadelphia s performance management program, led by the
Journey to Peak Performance. Mountain Point. NCTA Mobility Network Agile Methodologies
 Journey to Peak Performance Mountain Point NCTA Mobility Network Agile Methodologies Background 2000: Inception U.S. Army Biometric Program 2003: Biometrics could be used to prevent the enemy in Iraq and
Journey to Peak Performance Mountain Point NCTA Mobility Network Agile Methodologies Background 2000: Inception U.S. Army Biometric Program 2003: Biometrics could be used to prevent the enemy in Iraq and
Department of Defense INSTRUCTION
 Department of Defense INSTRUCTION NUMBER 4630.09 July 15, 2015 DoD CIO SUBJECT: Communication Waveform Management and Standardization References: See Enclosure 1 1. PURPOSE. This instruction: a. Reissues
Department of Defense INSTRUCTION NUMBER 4630.09 July 15, 2015 DoD CIO SUBJECT: Communication Waveform Management and Standardization References: See Enclosure 1 1. PURPOSE. This instruction: a. Reissues
Digi Connect Wan 3G Application Guide Update the firmware, backup and restore the configuration of a Digi Connect Wan 3G using a USB flash drive.
 1. Configure and prepare required files on the USB flash drive to allow firmware update and configuration backup/restore. Objective: Step by step instructions to upgrade the firmware, backup and restore
1. Configure and prepare required files on the USB flash drive to allow firmware update and configuration backup/restore. Objective: Step by step instructions to upgrade the firmware, backup and restore
DEPARTMENT OF VETERANS AFFAIRS VA DIRECTIVE 6517 CLOUD COMPUTING SERVICES
 DEPARTMENT OF VETERANS AFFAIRS VA DIRECTIVE 6517 Washington, DC 20420 Transmittal Sheet February 28, 2012 CLOUD COMPUTING SERVICES 1. REASON FOR ISSUE: This Directive establishes the Department of Veterans
DEPARTMENT OF VETERANS AFFAIRS VA DIRECTIVE 6517 Washington, DC 20420 Transmittal Sheet February 28, 2012 CLOUD COMPUTING SERVICES 1. REASON FOR ISSUE: This Directive establishes the Department of Veterans
Department of Administration Portfolio Management System 1.3 June 30, 2010
 E 06/ 30/ 2010 EX AM PL 1. 3 06/ 28/ 2010 06/ 24/ 2010 06/ 23/ 2010 06/ 15/ 2010 06/ 18/ 2010 Portfolio System 1.3 June 30, 2010 Contents Section 1. Project Overview... 1 1.1 Project Description... 1 1.2
E 06/ 30/ 2010 EX AM PL 1. 3 06/ 28/ 2010 06/ 24/ 2010 06/ 23/ 2010 06/ 15/ 2010 06/ 18/ 2010 Portfolio System 1.3 June 30, 2010 Contents Section 1. Project Overview... 1 1.1 Project Description... 1 1.2
Technical Writing - The NCB Contract Process
 Table of Contents Chapter 5 Non-Competitively Bid (NCB) Contracts Non-Competitively Bid (NCB) Contracts...1 Chapter 5... 3 Non-Competitively Bid (NCB) Contracts... 3 Overview...3 Introduction...3 Contents...3
Table of Contents Chapter 5 Non-Competitively Bid (NCB) Contracts Non-Competitively Bid (NCB) Contracts...1 Chapter 5... 3 Non-Competitively Bid (NCB) Contracts... 3 Overview...3 Introduction...3 Contents...3
Babel Revisited: Lessons from an IPv6 Transition
 Babel Revisited: Lessons from an IPv6 Transition SESSION ID: TECH-R04A Jeffrey J. Wiley Sr. Advisor to CISO Internal Revenue Service @wiley_jay Steven F. Fox Sr. Security Architecture and Engineering Advisor
Babel Revisited: Lessons from an IPv6 Transition SESSION ID: TECH-R04A Jeffrey J. Wiley Sr. Advisor to CISO Internal Revenue Service @wiley_jay Steven F. Fox Sr. Security Architecture and Engineering Advisor
Incident Management Team The Eight Step Implementation Model. The 8 Step
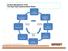 Incident Management Team The Eight Step Implementation Model The 8 Step 1 Incident Management Team Organization The 8 Step 2 The 8 Step 3 Incident Evaluation Flowchart Incident Management Team Activation
Incident Management Team The Eight Step Implementation Model The 8 Step 1 Incident Management Team Organization The 8 Step 2 The 8 Step 3 Incident Evaluation Flowchart Incident Management Team Activation
Commercial Software Licensing
 Commercial Software Licensing CHAPTER 10: (ITAM) Software Asset Management (SAM) Prepared by DoD ESI January 2013 Chapter Overview (ITAM) and Software Asset Management (SAM) allow for a complete and accurate
Commercial Software Licensing CHAPTER 10: (ITAM) Software Asset Management (SAM) Prepared by DoD ESI January 2013 Chapter Overview (ITAM) and Software Asset Management (SAM) allow for a complete and accurate
CJIS SECURITY POLICY: VERSION 5.2 CHANGES AND THE UPCOMING REQUIREMENTS.
 CJIS SECURITY POLICY: VERSION 5.2 CHANGES AND THE UPCOMING REQUIREMENTS. Alan Ferretti CJIS Information Security Officer Texas Department of Public Safety CJIS Security Policy version 5.2: On 8/9/2013
CJIS SECURITY POLICY: VERSION 5.2 CHANGES AND THE UPCOMING REQUIREMENTS. Alan Ferretti CJIS Information Security Officer Texas Department of Public Safety CJIS Security Policy version 5.2: On 8/9/2013
Rising to the Challenge
 CYBERSECURITY: Rising to the Challenge Dialogues with Subject Matter Experts Advanced persistent threats. Zero-day attacks. Insider threats. Cybersecurity experts say that if IT leaders are not concerned
CYBERSECURITY: Rising to the Challenge Dialogues with Subject Matter Experts Advanced persistent threats. Zero-day attacks. Insider threats. Cybersecurity experts say that if IT leaders are not concerned
Department of Defense DIRECTIVE
 Department of Defense DIRECTIVE NUMBER 4715.1E March 19, 2005 USD(AT&L) SUBJECT: Environment, Safety, and Occupational Health (ESOH) References: (a) DoD Directive 4715.1, Environmental Security, February
Department of Defense DIRECTIVE NUMBER 4715.1E March 19, 2005 USD(AT&L) SUBJECT: Environment, Safety, and Occupational Health (ESOH) References: (a) DoD Directive 4715.1, Environmental Security, February
Directives and Instructions Regarding Wireless LAN in Department of Defense (DoD) and other Federal Facilities
 Directives and Instructions Regarding Wireless LAN in Department of Defense (DoD) and other Federal Facilities Wireless Infrastructure, Article 12-29-2011 The federal government, and the Department of
Directives and Instructions Regarding Wireless LAN in Department of Defense (DoD) and other Federal Facilities Wireless Infrastructure, Article 12-29-2011 The federal government, and the Department of
Business Participation Plan 2012-2013
 Business Participation Plan 2012-2013 Submitted to: Wilson G. Bradshaw, PhD., President Office of the President Florida Gulf Coast University 10501 FGCU Boulevard South Fort Myers, Florida 33965-6565 Submitted
Business Participation Plan 2012-2013 Submitted to: Wilson G. Bradshaw, PhD., President Office of the President Florida Gulf Coast University 10501 FGCU Boulevard South Fort Myers, Florida 33965-6565 Submitted
Essential Next Steps for the U.S. Government in the Transition to IPv6
 Essential Next Steps for the U.S. Government in the Transition to IPv6 An Executive Summary for Agency Chief Information Officers of the Latest Federal Policies and Guidance for Continuing the Enterprise
Essential Next Steps for the U.S. Government in the Transition to IPv6 An Executive Summary for Agency Chief Information Officers of the Latest Federal Policies and Guidance for Continuing the Enterprise
Published International Standards Developed by ISO/IEC JTC 1/SC 37 - Biometrics
 Published International Standards Developed by ISO/IEC JTC 1/SC 37 - Biometrics Revised October 25, 2007 These standards can be obtained (for a fee) at ANSI s estandards Store: http://webstore.ansi.org/
Published International Standards Developed by ISO/IEC JTC 1/SC 37 - Biometrics Revised October 25, 2007 These standards can be obtained (for a fee) at ANSI s estandards Store: http://webstore.ansi.org/
Commercial Solutions for Classified (CSfC)
 Commercial Solutions for Classified (CSfC) Program Overview CONFIDENCE IN CYBERSPACE Chris Magaha Deputy Program Manager c.magaha@radium.ncsc.mil Strategic Initiative CSfC Layering commercial technologies
Commercial Solutions for Classified (CSfC) Program Overview CONFIDENCE IN CYBERSPACE Chris Magaha Deputy Program Manager c.magaha@radium.ncsc.mil Strategic Initiative CSfC Layering commercial technologies
METRO REGIONAL GOVERNMENT Records Retention Schedule
 Program: Administration IS Administration provides strategic planning, direction, and central management oversight of the Information Services that includes the following programs: Desktop Support Services,
Program: Administration IS Administration provides strategic planning, direction, and central management oversight of the Information Services that includes the following programs: Desktop Support Services,
Directives and Instructions Regarding Security and Installation of Wireless LAN in DoD Federal Facilities
 Directives and Instructions Regarding Security and Installation of Wireless LAN in DoD Federal Facilities Wireless Infrastructure, Article 3-15-2012 The federal government recognizes that standards based
Directives and Instructions Regarding Security and Installation of Wireless LAN in DoD Federal Facilities Wireless Infrastructure, Article 3-15-2012 The federal government recognizes that standards based
POLICY ON WIRELESS SYSTEMS
 Committee on National Security Systems CNSSP No. 17 January 2014 POLICY ON WIRELESS SYSTEMS THIS DOCUMENT PRESCRIBES MINIMUM STANDARDS YOUR DEPARTMENT OR AGENCY MAY REQUIRE FURTHER IMPLEMENTATION CHAIR
Committee on National Security Systems CNSSP No. 17 January 2014 POLICY ON WIRELESS SYSTEMS THIS DOCUMENT PRESCRIBES MINIMUM STANDARDS YOUR DEPARTMENT OR AGENCY MAY REQUIRE FURTHER IMPLEMENTATION CHAIR
COMMAND, CONTROL, COMMUNICATIONS, COMPUTERS AND INFORMATION TECHNOLOGY (C4&IT) INFRASTRUCTURE MANAGEMENT POLICY
 Commandant United States Coast Guard 2100 Second Street, S.W. Washington, DC 20593-0001 Staff Symbol: CG-6 Phone: (202) 267-2767 Fax: (202) 267-2598 COMDTINST 5230.70 FEB 11 2005 COMMANDANT INSTRUCTION
Commandant United States Coast Guard 2100 Second Street, S.W. Washington, DC 20593-0001 Staff Symbol: CG-6 Phone: (202) 267-2767 Fax: (202) 267-2598 COMDTINST 5230.70 FEB 11 2005 COMMANDANT INSTRUCTION
2. APPLICABILITY AND SCOPE
 Department of Defense DIRECTIVE NUMBER 1000.25 July 19, 2004 Certified Current as of April 23, 2007 USD(P&R) SUBJECT: DoD Personnel Identity Protection (PIP) Program References: (a) DoD Directive 1000.22,
Department of Defense DIRECTIVE NUMBER 1000.25 July 19, 2004 Certified Current as of April 23, 2007 USD(P&R) SUBJECT: DoD Personnel Identity Protection (PIP) Program References: (a) DoD Directive 1000.22,
Department of Defense INSTRUCTION
 Department of Defense INSTRUCTION NUMBER 1000.13 January 23, 2014 USD(P&R) SUBJECT: Identification (ID) Cards for Members of the Uniformed Services, Their Dependents, and Other Eligible Individuals References:
Department of Defense INSTRUCTION NUMBER 1000.13 January 23, 2014 USD(P&R) SUBJECT: Identification (ID) Cards for Members of the Uniformed Services, Their Dependents, and Other Eligible Individuals References:
Department of Defense INSTRUCTION. Public Key Infrastructure (PKI) and Public Key (PK) Enabling
 Department of Defense INSTRUCTION NUMBER 8520.02 May 24, 2011 ASD(NII)/DoD CIO SUBJECT: Public Key Infrastructure (PKI) and Public Key (PK) Enabling References: See Enclosure 1 1. PURPOSE. This Instruction:
Department of Defense INSTRUCTION NUMBER 8520.02 May 24, 2011 ASD(NII)/DoD CIO SUBJECT: Public Key Infrastructure (PKI) and Public Key (PK) Enabling References: See Enclosure 1 1. PURPOSE. This Instruction:
GOVERNMENT USE OF MOBILE TECHNOLOGY
 GOVERNMENT USE OF MOBILE TECHNOLOGY Barriers, Opportunities, and Gap Analysis DECEMBER 2012 Product of the Digital Services Advisory Group and Federal Chief Information Officers Council Contents Introduction...
GOVERNMENT USE OF MOBILE TECHNOLOGY Barriers, Opportunities, and Gap Analysis DECEMBER 2012 Product of the Digital Services Advisory Group and Federal Chief Information Officers Council Contents Introduction...
Determination of Best Procurement Approach. Assisted Acquisition. [Insert title of the statement of work or requirement.]
![Determination of Best Procurement Approach. Assisted Acquisition. [Insert title of the statement of work or requirement.] Determination of Best Procurement Approach. Assisted Acquisition. [Insert title of the statement of work or requirement.]](/thumbs/40/21736325.jpg) Determination of Best Procurement Approach Assisted Acquisition Title of Effort: [Insert title of the statement of work or requirement.] Requesting Agency: [Insert name of the requirements office.] Requirements
Determination of Best Procurement Approach Assisted Acquisition Title of Effort: [Insert title of the statement of work or requirement.] Requesting Agency: [Insert name of the requirements office.] Requirements
Department of Defense MANUAL. Procedures for Ensuring the Accessibility of Electronic and Information Technology (E&IT) Procured by DoD Organizations
 Department of Defense MANUAL NUMBER 8400.01-M June 3, 2011 ASD(NII)/DoD CIO SUBJECT: Procedures for Ensuring the Accessibility of Electronic and Information Technology (E&IT) Procured by DoD Organizations
Department of Defense MANUAL NUMBER 8400.01-M June 3, 2011 ASD(NII)/DoD CIO SUBJECT: Procedures for Ensuring the Accessibility of Electronic and Information Technology (E&IT) Procured by DoD Organizations
Information Assurance Workforce (IAWF) Contracting Officer Representative (COR) & Project Manager (PM) Workshop
 Information Assurance Workforce (IAWF) Contracting Officer Representative (COR) & Project Manager (PM) Workshop Shannon Lawson Command IAM SSC Pacific Distribution Statement A. Approved for Public Release;
Information Assurance Workforce (IAWF) Contracting Officer Representative (COR) & Project Manager (PM) Workshop Shannon Lawson Command IAM SSC Pacific Distribution Statement A. Approved for Public Release;
Department of Defense Fiscal Year (FY) 2014 President's Budget Submission
 Department of Defense Fiscal Year (FY) 2014 President's Budget Submission April 2013 Defense Contract Management Agency Justification Book Research, Development, Test & Evaluation, Defense-Wide THIS PAGE
Department of Defense Fiscal Year (FY) 2014 President's Budget Submission April 2013 Defense Contract Management Agency Justification Book Research, Development, Test & Evaluation, Defense-Wide THIS PAGE
Department of Defense DIRECTIVE. SUBJECT: Management of the Department of Defense Information Enterprise
 Department of Defense DIRECTIVE SUBJECT: Management of the Department of Defense Information Enterprise References: See Enclosure 1 NUMBER 8000.01 February 10, 2009 ASD(NII)/DoD CIO 1. PURPOSE. This Directive:
Department of Defense DIRECTIVE SUBJECT: Management of the Department of Defense Information Enterprise References: See Enclosure 1 NUMBER 8000.01 February 10, 2009 ASD(NII)/DoD CIO 1. PURPOSE. This Directive:
ARC Outreach on HSPD 12 and Mandatory Use of ODIN
 ARC Outreach on HSPD 12 and Mandatory Use of ODIN August 28 & 29, 2007 Agenda Center Management Opening Remarks CIO Perspective Homeland Security Presidential Directive (HSPD) 12 Questions & Answers Mandatory
ARC Outreach on HSPD 12 and Mandatory Use of ODIN August 28 & 29, 2007 Agenda Center Management Opening Remarks CIO Perspective Homeland Security Presidential Directive (HSPD) 12 Questions & Answers Mandatory
President s Management Advisory Board Meeting. March 27, 2015
 President s Management Advisory Board Meeting March 27, 2015 1 Agenda 9:00 a.m. Welcome and Introductions 9:10 a.m. Management Priority Updates 10:00 a.m. Case Studies Business Process: Shared Services
President s Management Advisory Board Meeting March 27, 2015 1 Agenda 9:00 a.m. Welcome and Introductions 9:10 a.m. Management Priority Updates 10:00 a.m. Case Studies Business Process: Shared Services
I. Purpose - 1 MD # 0005
 Department of Homeland SecUl ity Management Directives System MD Number: 0005 Issue Date: 10/28/2004 FINANCIAL MANAGEMENT LINE OF BUSINESS INTEGRATION AND MANAGEMENT I. Purpose This Management Directive
Department of Homeland SecUl ity Management Directives System MD Number: 0005 Issue Date: 10/28/2004 FINANCIAL MANAGEMENT LINE OF BUSINESS INTEGRATION AND MANAGEMENT I. Purpose This Management Directive
Commercial Software Licensing
 Commercial Software Licensing CHAPTER 14: Prepared by DoD ESI September 2012 Chapter Overview Authorized users Who can order? All DoD components. Ordering is de-centralized. GSA. Authorized contractors.
Commercial Software Licensing CHAPTER 14: Prepared by DoD ESI September 2012 Chapter Overview Authorized users Who can order? All DoD components. Ordering is de-centralized. GSA. Authorized contractors.
RECOGNIZING ABILITIES, CREATING OPPORTUNITIES. Strategic Plan 2015-2017
 RECOGNIZING ABILITIES, CREATING OPPORTUNITIES Strategic Plan 2015-2017 Executive Summary As a result of the national and a local economic crisis, Arizona Rehabilitation Services Administration (AZRSA)
RECOGNIZING ABILITIES, CREATING OPPORTUNITIES Strategic Plan 2015-2017 Executive Summary As a result of the national and a local economic crisis, Arizona Rehabilitation Services Administration (AZRSA)
Cloud Security. Are you on the train or the tracks? ISSA CISO Executive Forum April 18, 2015. Brian Grayek CISSP, CCSK, ITILv3
 Cloud Security Are you on the train or the tracks? ISSA CISO Executive Forum April 18, 2015 Brian Grayek CISSP, CCSK, ITILv3 1 Agenda: Facts Opinions (based on experience) A little humor Some gold nuggets
Cloud Security Are you on the train or the tracks? ISSA CISO Executive Forum April 18, 2015 Brian Grayek CISSP, CCSK, ITILv3 1 Agenda: Facts Opinions (based on experience) A little humor Some gold nuggets
Conformance test specification for BSI-TR 03121 Biometrics for public sector applications
 Technical Guideline TR-03122-1 Conformance test specification for BSI-TR 03121 Biometrics for public sector applications Part 1: Framework Version 3.0 Bundesamt für Sicherheit in der Informationstechnik
Technical Guideline TR-03122-1 Conformance test specification for BSI-TR 03121 Biometrics for public sector applications Part 1: Framework Version 3.0 Bundesamt für Sicherheit in der Informationstechnik
Department of Defense DIRECTIVE
 Department of Defense DIRECTIVE NUMBER 4205.01 March 10, 2009 USD(AT&L) SUBJECT: DoD Small Business Programs References: See Enclosure 1 1. PURPOSE. This Directive: a. Reissues DoD Directive 4205.01 (Reference
Department of Defense DIRECTIVE NUMBER 4205.01 March 10, 2009 USD(AT&L) SUBJECT: DoD Small Business Programs References: See Enclosure 1 1. PURPOSE. This Directive: a. Reissues DoD Directive 4205.01 (Reference
Integrating Biometrics into the Database and Application Server Infrastructure. Shirley Ann Stern Principal Product Manager Oracle Corporation
 Integrating Biometrics into the Database and Application Server Infrastructure Shirley Ann Stern Principal Product Manager Oracle Corporation 1 Agenda! Introduction Importance of the infrastructure Role
Integrating Biometrics into the Database and Application Server Infrastructure Shirley Ann Stern Principal Product Manager Oracle Corporation 1 Agenda! Introduction Importance of the infrastructure Role
Making Your Organization Open Source-Ready
 Making Your Organization Open Source-Ready Bernard Golden CEO, Navica Copyright 2006 Navica. All rights reserved. www.navicasoft.com Agenda Introduction Overview of open source best practices Key differences
Making Your Organization Open Source-Ready Bernard Golden CEO, Navica Copyright 2006 Navica. All rights reserved. www.navicasoft.com Agenda Introduction Overview of open source best practices Key differences
Is the Device User the Device Owner? A paper prepared for Biometrics UnPlugged: Mobility Rules Executive Summit - Tampa Monday, September 16, 2013
 Is the Device User the Device Owner? A paper prepared for Biometrics UnPlugged: Mobility Rules Executive Summit - Tampa Monday, September 16, 2013 Rod Beatson President, Transaction Security, Inc. Rod.Beatson@crypto-sign.com
Is the Device User the Device Owner? A paper prepared for Biometrics UnPlugged: Mobility Rules Executive Summit - Tampa Monday, September 16, 2013 Rod Beatson President, Transaction Security, Inc. Rod.Beatson@crypto-sign.com
APPENDIX J INFORMATION TECHNOLOGY MANAGEMENT GOALS
 APPENDIX J INFORMATION TECHNOLOGY MANAGEMENT GOALS Section 5123 of the Clinger-Cohen Act requires that the Department establish goals for improving the efficiency and effectiveness of agency operations
APPENDIX J INFORMATION TECHNOLOGY MANAGEMENT GOALS Section 5123 of the Clinger-Cohen Act requires that the Department establish goals for improving the efficiency and effectiveness of agency operations
Enterprise Data Archiving. Report to the Joint Legislative Oversight Committee on Information Technology
 Enterprise Data Archiving Report to the Joint Legislative Oversight Committee on Information Technology Chris Estes State Chief Information Officer December 2013 This page left blank intentionally Contents
Enterprise Data Archiving Report to the Joint Legislative Oversight Committee on Information Technology Chris Estes State Chief Information Officer December 2013 This page left blank intentionally Contents
WHAT ARE FUEL CARDS?
 WHAT ARE FUEL CARDS? DESC Fuel Charge Cards are a mix of co-branded commercial charge cards, bank sponsored, or private label charge cards used to obtain fuel, fuel related supplies, & services. The acronym,
WHAT ARE FUEL CARDS? DESC Fuel Charge Cards are a mix of co-branded commercial charge cards, bank sponsored, or private label charge cards used to obtain fuel, fuel related supplies, & services. The acronym,
Analytics as a Service Overview
 U.S. General Services Administration Analytics as a Service Overview Presentation by Johan Bos-Beijer Director/Senior Advisor Analytics Services Office of Citizen Services and Innovative Technology Purpose
U.S. General Services Administration Analytics as a Service Overview Presentation by Johan Bos-Beijer Director/Senior Advisor Analytics Services Office of Citizen Services and Innovative Technology Purpose
Information Technology Asset Management
 Information Technology Asset Management HARDWARE SOFTWARE AND SERVICES AUBREY P. JONES, PMP DATA SYSTEMS ANALYSTS, INC SUMMARY Management of government/defense IT assets is an increasing target for cost
Information Technology Asset Management HARDWARE SOFTWARE AND SERVICES AUBREY P. JONES, PMP DATA SYSTEMS ANALYSTS, INC SUMMARY Management of government/defense IT assets is an increasing target for cost
Department of Defense INSTRUCTION
 Department of Defense INSTRUCTION NUMBER 8910.01 May 19, 2014 DoD CIO SUBJECT: Information Collection and Reporting References: See Enclosure 1 1. PURPOSE. This instruction: a. Reissues DoD Instruction
Department of Defense INSTRUCTION NUMBER 8910.01 May 19, 2014 DoD CIO SUBJECT: Information Collection and Reporting References: See Enclosure 1 1. PURPOSE. This instruction: a. Reissues DoD Instruction
NW Systems, Inc. Corporate Overview. 8300 Greensboro Drive, Suite 800 McLean, VA 22102 www.nw-systems.com
 NW Systems, Inc. Corporate Overview 8300 Greensboro Drive, Suite 800 McLean, VA 22102 www.nw-systems.com SUMMARY Founded in 1996 ; Professional Services Firm Supporting US Government and Commercial Clients
NW Systems, Inc. Corporate Overview 8300 Greensboro Drive, Suite 800 McLean, VA 22102 www.nw-systems.com SUMMARY Founded in 1996 ; Professional Services Firm Supporting US Government and Commercial Clients
Department of Veterans Affairs VA Directive 6403 SOFTWARE ASSET MANAGEMENT
 Department of Veterans Affairs VA Directive 6403 Washington, DC 20420 Transmittal Sheet July 02, 2015 SOFTWARE ASSET MANAGEMENT 1. REASON FOR ISSUE. This Directive establishes Department of Veterans Affairs
Department of Veterans Affairs VA Directive 6403 Washington, DC 20420 Transmittal Sheet July 02, 2015 SOFTWARE ASSET MANAGEMENT 1. REASON FOR ISSUE. This Directive establishes Department of Veterans Affairs
POLICY ON THE USE OF COMMERCIAL SOLUTIONS TO PROTECT NATIONAL SECURITY SYSTEMS
 Committee on National Security Systems CNSSP No. 7 9 December 2015 POLICY ON THE USE OF COMMERCIAL SOLUTIONS TO PROTECT NATIONAL SECURITY SYSTEMS THIS DOCUMENT PRESCRIBES MINIMUM STANDARDS YOUR DEPARTMENT
Committee on National Security Systems CNSSP No. 7 9 December 2015 POLICY ON THE USE OF COMMERCIAL SOLUTIONS TO PROTECT NATIONAL SECURITY SYSTEMS THIS DOCUMENT PRESCRIBES MINIMUM STANDARDS YOUR DEPARTMENT
An Operational Architecture for Federated Identity Management
 An Operational Architecture for Federated Identity Management March 2011 Implementing federated identity management and assurance in operational scenarios Federated Identity Solution The Federated identity
An Operational Architecture for Federated Identity Management March 2011 Implementing federated identity management and assurance in operational scenarios Federated Identity Solution The Federated identity
The DoD CIO Charter:
 George Mason University, Fairfax, VA The DoD CIO Charter: A Template for I.T. Governance? Paul A. Strassmann,October 3, 2005 1 Authority for the DoD CIO 2 Traditional Views of the CIO Roles 3 An Expansive
George Mason University, Fairfax, VA The DoD CIO Charter: A Template for I.T. Governance? Paul A. Strassmann,October 3, 2005 1 Authority for the DoD CIO 2 Traditional Views of the CIO Roles 3 An Expansive
PRIVACY IMPACT ASSESSMENT (PIA) GUIDE
 U.S. Securities and Exchange Commission Office of Information Technology Alexandria, VA PRIVACY IMPACT ASSESSMENT (PIA) GUIDE Revised January 2007 Privacy Office Office of Information Technology PRIVACY
U.S. Securities and Exchange Commission Office of Information Technology Alexandria, VA PRIVACY IMPACT ASSESSMENT (PIA) GUIDE Revised January 2007 Privacy Office Office of Information Technology PRIVACY
DOD BUSINESS SYSTEMS MODERNIZATION. Additional Action Needed to Achieve Intended Outcomes
 United States Government Accountability Office Report to Congressional Committees July 2015 DOD BUSINESS SYSTEMS MODERNIZATION Additional Action Needed to Achieve Intended Outcomes GAO-15-627 July 2015
United States Government Accountability Office Report to Congressional Committees July 2015 DOD BUSINESS SYSTEMS MODERNIZATION Additional Action Needed to Achieve Intended Outcomes GAO-15-627 July 2015
WhatsUp Log Management Installation and Migration Guide, including Getting Started Information. (Applies to v10.1.5 and later)
 WhatsUp Log Management Installation and Migration Guide, including Getting Started Information (Applies to v10.1.5 and later) C o n t e n t s Getting Started with WhatsUp Log Management Before You Begin...
WhatsUp Log Management Installation and Migration Guide, including Getting Started Information (Applies to v10.1.5 and later) C o n t e n t s Getting Started with WhatsUp Log Management Before You Begin...
OPNAVINST 4440.26A N4 5 Jun 2012. Subj: OPERATING MATERIALS AND SUPPLIES AND GOVERNMENT FURNISHED MATERIAL MANAGEMENT
 DEPARTMENT OF THE NAVY OFFICE OF THE CHIEF OF NAVAL OPERATIONS 2000 NAVY PENTAGON WASHINGTON, DC 20350-2000 OPNAVINST 4440.26A N4 OPNAV INSTRUCTION 4440.26A From: Chief of Naval Operations Subj: OPERATING
DEPARTMENT OF THE NAVY OFFICE OF THE CHIEF OF NAVAL OPERATIONS 2000 NAVY PENTAGON WASHINGTON, DC 20350-2000 OPNAVINST 4440.26A N4 OPNAV INSTRUCTION 4440.26A From: Chief of Naval Operations Subj: OPERATING
DA-70702 BIOMETRIC FINGERPRINT READER 2,5" HDD ENCLOSURE User Manual
 DA-70702 BIOMETRIC FINGERPRINT READER 2,5" HDD ENCLOSURE User Manual System Requirements System Requirements Recommended Pentium II or higher or other compatible machines. Recommended RAM of at least 128
DA-70702 BIOMETRIC FINGERPRINT READER 2,5" HDD ENCLOSURE User Manual System Requirements System Requirements Recommended Pentium II or higher or other compatible machines. Recommended RAM of at least 128
Raytheon Oakley Systems
 Raytheon Oakley Systems Michael Crouse VP, Sales & Marketing Daniel Velez Director, Program Operations Cleared for release. #IIS2013-226. Page 1 Raytheon Oakley Systems About us Founded as Oakley Networks
Raytheon Oakley Systems Michael Crouse VP, Sales & Marketing Daniel Velez Director, Program Operations Cleared for release. #IIS2013-226. Page 1 Raytheon Oakley Systems About us Founded as Oakley Networks
FOSSBazaar A Governance Initiative to manage Free and Open Source Software life cycle
 FOSSBazaar A Governance Initiative to manage Free and Open Source Software life cycle Table of contents Executive summary......2 What is FOSS Governance 3 The importance of open source governance...3 Why
FOSSBazaar A Governance Initiative to manage Free and Open Source Software life cycle Table of contents Executive summary......2 What is FOSS Governance 3 The importance of open source governance...3 Why
Accessibility and Section 508
 Federal GIS Conference February 9 10, 2015 Washington, DC Accessibility and Section 508 Clint Brown Jim McKinney Overview Background Know Your GIS Environment Section 508 and Esri Esri Product Development
Federal GIS Conference February 9 10, 2015 Washington, DC Accessibility and Section 508 Clint Brown Jim McKinney Overview Background Know Your GIS Environment Section 508 and Esri Esri Product Development
Department of Defense INSTRUCTION
 Department of Defense INSTRUCTION NUMBER 1322.19 March 14, 2013 USD(P&R) SUBJECT: Voluntary Education Programs in Overseas Areas References: See Enclosure 1. 1. PURPOSE. This instruction: a. Reissues DoD
Department of Defense INSTRUCTION NUMBER 1322.19 March 14, 2013 USD(P&R) SUBJECT: Voluntary Education Programs in Overseas Areas References: See Enclosure 1. 1. PURPOSE. This instruction: a. Reissues DoD
How To Manage Records At The Exceeda Agency
 Table of Contents Table of Contents... i I. Introduction and Background... 1 A. Challenges... 1 B. Vision and Goals... 1 II. Approach and Response... 2 A. Set up a Governance Structure... 2 B. Established
Table of Contents Table of Contents... i I. Introduction and Background... 1 A. Challenges... 1 B. Vision and Goals... 1 II. Approach and Response... 2 A. Set up a Governance Structure... 2 B. Established
CHAPTER 5 HB 418-FN FINAL VERSION 2012 SESSION
 Page 1 of 6 CHAPTER 5 HB 418-FN FINAL VERSION 15Mar2011 0733h 01/18/12 0009s 2012 SESSION 11-0741 05/10 HOUSE BILL 418-FN AN ACT relative to the use of open source software and open data formats by state
Page 1 of 6 CHAPTER 5 HB 418-FN FINAL VERSION 15Mar2011 0733h 01/18/12 0009s 2012 SESSION 11-0741 05/10 HOUSE BILL 418-FN AN ACT relative to the use of open source software and open data formats by state
Information Security Policy and Handbook Overview. ITSS Information Security June 2015
 Information Security Policy and Handbook Overview ITSS Information Security June 2015 Information Security Policy Control Hierarchy System and Campus Information Security Policies UNT System Information
Information Security Policy and Handbook Overview ITSS Information Security June 2015 Information Security Policy Control Hierarchy System and Campus Information Security Policies UNT System Information
BPA Policy 434-1 Cyber Security Program
 B O N N E V I L L E P O W E R A D M I N I S T R A T I O N BPA Policy Table of Contents.1 Purpose & Background...2.2 Policy Owner... 2.3 Applicability... 2.4 Terms & Definitions... 2.5 Policy... 5.6 Policy
B O N N E V I L L E P O W E R A D M I N I S T R A T I O N BPA Policy Table of Contents.1 Purpose & Background...2.2 Policy Owner... 2.3 Applicability... 2.4 Terms & Definitions... 2.5 Policy... 5.6 Policy
Information Resource Management Directive 5000.05 USAP Information Security Architecture
 The National Science Foundation Polar Programs United States Antarctic Program Information Resource Management Directive 5000.05 USAP Information Security Architecture Organizational Function Information
The National Science Foundation Polar Programs United States Antarctic Program Information Resource Management Directive 5000.05 USAP Information Security Architecture Organizational Function Information
Department of Defense INSTRUCTION. 1. PURPOSE. In accordance with DoD Directive (DoDD) 5124.02 (Reference (a)), this Instruction:
 Department of Defense INSTRUCTION NUMBER 6430.02 August 17, 2011 USD(P&R) SUBJECT: Defense Medical Materiel Program References: See Enclosure 1 1. PURPOSE. In accordance with DoD Directive (DoDD) 5124.02
Department of Defense INSTRUCTION NUMBER 6430.02 August 17, 2011 USD(P&R) SUBJECT: Defense Medical Materiel Program References: See Enclosure 1 1. PURPOSE. In accordance with DoD Directive (DoDD) 5124.02
Fleet Management Information System (FMIS) Deric Sims, Fleet Manager, DoD Ralph Filicko, Mercury Associates
 Fleet Management Information System (FMIS) Deric Sims, Fleet Manager, DoD Ralph Filicko, Mercury Associates Agenda Federal Systems Requirements and Best Practices DoD s Efforts to Ensure Compliance with
Fleet Management Information System (FMIS) Deric Sims, Fleet Manager, DoD Ralph Filicko, Mercury Associates Agenda Federal Systems Requirements and Best Practices DoD s Efforts to Ensure Compliance with
MCO 5220.12 LR 15 May 2009
 LR MARINE CORPS ORDER 5220.12 From: Commandant of the Marine Corps To: Distribution List Subj: MARINE CORPS CONTINUOUS PROCESS IMPROVEMENT Ref: (a) DOD Directive 5010.42, DOD-Wide Continuous Process Improvement
LR MARINE CORPS ORDER 5220.12 From: Commandant of the Marine Corps To: Distribution List Subj: MARINE CORPS CONTINUOUS PROCESS IMPROVEMENT Ref: (a) DOD Directive 5010.42, DOD-Wide Continuous Process Improvement
Software Licensing and Pricing Best Practices. Stewart Buchanan June 3, 2009 Gartner Webinar
 Software Licensing and Pricing Best Practices Stewart Buchanan June 3, 2009 Gartner Webinar How to Participate Today Audio Announcement You have joined the audio muted using your computer s speaker system
Software Licensing and Pricing Best Practices Stewart Buchanan June 3, 2009 Gartner Webinar How to Participate Today Audio Announcement You have joined the audio muted using your computer s speaker system
Software Asset Management on System z
 Software Asset Management on System z Mike Zelle Tivoli WW IT Asset Management Marketing SAM in SHARE Project Manager mzelle@us.ibm.com Agenda Why Software Asset Management (SAM) The Discipline of Software
Software Asset Management on System z Mike Zelle Tivoli WW IT Asset Management Marketing SAM in SHARE Project Manager mzelle@us.ibm.com Agenda Why Software Asset Management (SAM) The Discipline of Software
E X E C U T I V E O F F I CE O F T H E P R E S I D EN T
 EXECUTIVE OFFICE OF THE PRESIDENT OFFICE OF MANAGEMENT AND BUDGET WASHINGTON, D.C. 20503 THE DIRECTOR M-05-24 August 5, 2005 MEMORANDUM FOR THE HEADS OF ALL DEPARTMENTS AND AGENCIES FROM: SUBJECT: Joshua
EXECUTIVE OFFICE OF THE PRESIDENT OFFICE OF MANAGEMENT AND BUDGET WASHINGTON, D.C. 20503 THE DIRECTOR M-05-24 August 5, 2005 MEMORANDUM FOR THE HEADS OF ALL DEPARTMENTS AND AGENCIES FROM: SUBJECT: Joshua
All-Liaison Meeting on COMMBUYS User Roles
 All-Liaison Meeting on COMMBUYS User Roles May 26, 2015 Copyright Operational Services Division All Rights Reserved Agenda Understanding COMMBUYS User Roles Roles Defined Organization Administrator Current
All-Liaison Meeting on COMMBUYS User Roles May 26, 2015 Copyright Operational Services Division All Rights Reserved Agenda Understanding COMMBUYS User Roles Roles Defined Organization Administrator Current
The Federal Procurement Data System (FPDS) as a Market Research Tool for Small Businesses 15 June 2012
 The Federal Procurement Data System (FPDS) as a Market Research Tool for Small Businesses 15 June 2012 Anthony Braun Halfaker and Associates, LLC Support Contractor, U.S. Army Office of Small Business
The Federal Procurement Data System (FPDS) as a Market Research Tool for Small Businesses 15 June 2012 Anthony Braun Halfaker and Associates, LLC Support Contractor, U.S. Army Office of Small Business
