A Need Hierarchy for Teams
|
|
|
- Egbert Rice
- 8 years ago
- Views:
Transcription
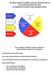
1 A Need Hierarchy for Teams Anita Sarma and André van der Hoek Department of Informatics Donald Bren School of Information and Computer Sciences University of California Irvine {asarma, ISR Technical Report : UCI-ISR-04-9 October 2004 Abstract Maslow created a hierarchy of needs for the individual. He placed the needs in a hierarchy such that only after the needs of a layer are satisfied would an individual care about the needs in the next layer. Using Maslow's insight we create a hierarchy of needs for the team. In this paper we map the needs of a software development team to the need layers that Maslow prescribed for the individual. In creating this mapping we come across an interesting observation that most collaborative tools focus on enhancing the efficiency of the team and depend on collocation to create team cohesiveness. 1 Introduction Typical software development is a multi-team effort requiring coordination among developers. It has in fact been shown that about 70 percent of a software engineer's time is spent on cooperative activities [1]. Collaboration is thus at the heart of software development. Research in collaboration has resulted in a host of collaborative tools and environments that support collaboration one way or the other. There are a number of classification frameworks that classify collaborative tools based on the capabilities of the tool or the coordination problem that they solve. These classification frameworks either focus on a particular aspect of collaboration (an area) or are frameworks for classifying a set of tools that belong to a particular area. The existing classifications and frameworks fail to provide an overview of all existing approaches to collaboration and are inadequate in providing conceptual guidance to help users choose the right kind of tool. In order to be better able to understand the collaboration technologies that exist and the problems that they address, we decided to take a step back and identify the needs that allow a team to function and excel. We adapt Maslow's hierarchy of needs for the individual from the psychology domain to create the collaboration needs of a software development team. The collaboration needs are categorized into five layers and correspond with the needs specified by Maslow. We have tried to stay as true to Maslow as possible. The rest of the paper is organized as follows. Section 2 briefly describes Maslow's hierarchy of needs. We map the needs of the team in Section 3, and conclude in Section 4 with our observations. 2 Maslow s Need Hierarchy Abraham Maslow is known for establishing the theory of a hierarchy of needs [2]. Maslow studied human subjects (exemplary people being Albert Einstein, Jane Addams, Eleanor Roosevelt, and Frederick Douglas) rather than mentally ill or neurotic people, which was radically different from the Freudian and Skinner schools of psychology. He claimed that human beings are motivated by unsatisfied needs, and that certain lower needs need to be satisfied before higher needs can be satisfied. 1
2 According to Maslow, there are general types of needs (physiological, safety, love, and esteem) that must be satisfied before a person can act unselfishly. He called these needs "deficiency needs." As long as an individual is motivated to satisfy these needs, he is on the path to growth ultimately reaching self-actualization (a growth need) once all the deficiency needs are met. He further claimed that these needs are prepotent. A prepotent need is one that has the greatest influence over our actions. Every individual has a prepotent need that may vary among individuals. For example a teenager may have a need to feel that he/she is accepted by a group whereas a heroin addict will need to satisfy his/her cravings for heroin to function normally in society, and will not worry about acceptance by other people. According to Maslow, once a deficiency need is met at once other needs (needs at the same level or higher level) emerge, and these, rather than physiological hungers, dominate the organism. When these higher needs are in turn satisfied, again new (and still higher) needs emerge, and so on. In essence as one desire is satisfied, another Figure 1. Maslow's Hierarchy of Needs pops up to take its place. The need layers in the hierarchy do not have strict transition points and the pyramid is mainly heuristic in nature. The five layers in the hierarchy of needs are explained as follows: 2.1 Physiological Needs Physiological needs are the fundamental needs that allow an organism to survive. These needs include air, water, food, sleep, etc. If the individual does not satisfy the needs at this level, they may be sick, in pain or in discomfort. Individual are thus motivated to alleviate them as soon as possible. Only once these needs are reasonably satisfied may one think of other things. 2.2 Safety Needs Once the physiological needs are relatively well gratified a new set of needs that are mostly psychological in nature emerges. Safety needs allow an individual to establish stability and consistency in a chaotic world. Needs that can be categorized into this layer are security; stability; dependency; protection; freedom from fear, anxiety, and chaos; need for structure, order, law, and limits; strength in the protector; and so on. For example an individual may need the security of a home and family before concerned about higher needs. However, if a family is dysfunctional (an abusive husband), the members in the family (the wife) cannot move to the next level as she would be constantly concerned for her safety. 2.3 Love Needs Love and belongingness are next in the hierarchy. The love needs involve giving and receiving affection. When they are unsatisfied, a person will feel keenly the absence of friends, mate, or children. Such a person will hunger for relations with people in general for a place in the group or family and will strive with great intensity to achieve this goal. Attaining such a place will matter more than anything else in the world and he or she may even forget that once, when hunger was foremost, love seemed unreal, unnecessary, and unimportant. Now the pangs of loneliness, ostracism, rejection, friendlessness, and rootlessness are preeminent. ([2], chapter 20). 2.4 Esteem Needs The esteem needs can be categorized into two types. First is self-esteem which results from competence or mastery of a task. Second, is the attention and recognition that comes from others. All people in our society (with a few pathological exceptions) have a need or desire for a stable, firmly based, usually high evaluation of themselves, for self-respect or self-esteem, and for the esteem of others. These needs may therefore be classified into two subsidiary sets. These are, first, 2
3 the desire for strength, achievement, adequacy, mastery and competence, confidence in the face of the world, and independence and freedom. Second, we have what we may call the desire for reputation or prestige (defining it as respect or esteem from other people), status, fame and glory, dominance, recognition, attention, importance, dignity, or appreciation. ([2], cahpter 21) This is similar to the belongingness level; however, wanting admiration has to do with the need for power. For example individuals who have all of their lower needs satisfied, would drive very expensive cars to raise their level of esteem. 2.5 Self-Actualization The need for self-actualization is "the desire to become more and more what one is, to become everything that one is capable of becoming." People who have everything can maximize their potential. This need is a growth need and is attained once all the deficiency needs have been fulfilled. People at this level can now seek knowledge, peace, esthetic experiences, self-fulfillment, etc. Individuals at this level need to realize their potential to be at peace with themselves. 3 Team Needs In this section we investigate the needs of a software development team. We treat the entire team as a single entity and do not distinguish roles within the team. Using the need hierarchy frame proposed by Maslow we get an insight into what are the fundamental needs for a team to function, what makes the team cohesive and how can the team be made more efficient. We create a hierarchy comprising of the deficiency needs and the growth needs. The first four layers are namely fundamental needs, safety needs, belonging needs and Esteem needs. Once the needs at a particular level are satisfied the team needs to fulfill the needs at the higher level. Once all the deficiency needs are satisfied the team is free to address its growth needs and reach self-actualization. As the requirements of an individual in a society are different from the collaboration requirements of a software development team the specific needs in a layer are different than that of the individual. In our mapping we have attempted to be as true to Maslow as possible. The five layers in our hierarchy of collaboration needs for a team are explained in the following paragraphs. We further identify areas in software engineering that address the needs in each layer. 3.1 Fundamental Needs The fundamental needs of a software development team would be the ability to create software artifacts and communicate with team members. These needs are sufficient to form the team and sustain communication between members. The team can use basic computing technologies like code editor, compiler and linker to create software programs. At this layer technology only supports implementation and testing in the software development life cycle. The rest of the software artifacts like requirements or design documents are created and maintained by the developers manually. Bare boned coordination facilities are provided by s. Research in systems programming provides solution to the needs at this layer. Basic text based clients that allow attachments can serve the communication purposes at this layer. 3.2 Safety Needs Safety for a team is different from the personal safety of an individual. We consider safety needs for the team as safety of the software artifacts that the team produces. The team at this point should be safe from hardware or system failures, mistakes from the team members, and malicious activities from outsiders. Server based storage (backups outside of personal machines) ensures safety against hardware failures to an extent. Versioning of artifacts ensures that if a team member makes a mistake the mistake can be rolled back. Access rights allow only authorized members to make changes and prohibit outsiders from breaking the software. Access rights (locking) also enable coordination within the team such that changes are not inadvertently over written. Antivirus programs and encryption further helps in keeping the software artifacts from malicious hackers. Configuration management systems [3] provide external storage, versioning and access rights facilities. There is considerable research in cryp- 3
4 tography and anti-virus system protection that deal with safety from malicious intent of hackers. 3.3 Belonging Needs An individual in the society needs to feel accepted and have a sense of belonging to a group. The individual can perform better and strive for esteem needs once they know that they are loved. In the same vein the team needs to be close-knit and cohesive for the team members to feel accepted which enables them to further perform well. Belonging needs of the team can be separated into two tiers. One is the belonging needs of an individual in the team and the other is the belonging needs of the team in the parent group (the department or the company). When a team is cohesive, it is easier for the members to approach others when they require help. Collaboration in the team is smoother and efficient when the members feel that they belong to the team and place the needs of the team over personal needs. Companies promote team building via company sponsored picnics, retreats etc. Unfortunately these activities are most effective when the team members are collocated. An example of the feeling of belonging to a team when the members are distributed is the strong allegiance that open source developers have for their projects [4]. The team is motivated to perform well and work towards the company s goals when they feel that their team is an important part of the company and belong to it. This sense of belongingness is usually fostered by company sponsored events, cross department meetings and stock and shares. An example of this sense of belonging would be when teams put in the affiliations of their parent company when they publish research papers. A software team would be proud to be associated with a well known parent company say, IBM Research labs. As discussed earlier the feeling of belonging is currently based on collocation of the team members. There are a few technologies that allow distributed teams to be cohesive by allowing the members to interact with each other. Discussion forums and lists enhance the feeling of belonging to a group as they foster the sense of a community and soon the community members recognize each other via their Ids. CSCW applications such as TeamRooms [5], Instant messengers [6], Portholes [7], [8], JAZZ band [9], etc. promote cohesiveness in the team by allowing the team members to interact with each other either through their electronic profiles or social proxies. 3.4 Esteem Needs The esteem needs of a team are similar to that of the individual in society. The team seeks to be competent and efficient so that it can gain the respect and prestige from others. At this stage the team would like to be known for solving hard problems; produce code that is elegant, cost effective and efficient; is known in the research community. To further this goal the team seeks to publish its artifacts (research papers, good documentation, articles in trade journals) to gain recognition from the user and research body. The chief aim of project management is to allow optimum task assignment and easy task monitoring such that the team is efficient and is able to meet the development targets. There are a number of tools that aid project management. Software methodologies like code reviews, good design creation via UML or architecture strive to create good quality code. Recommendation systems and data-mining help new developers to quickly learn the system and start being productive. Net meeting and shared screen applications allow distributed developers to collaborate. Change management tools that track parallel changes allow developers create code with fewer conflicts. Formal methods and testing techniques like Junit testing, assertions, model based testing, etc., enable developers to create more robust software. Thus there is a multitude of tools and techniques both in software engineering and Computer Supported Cooperative Work that attempt to increase the efficiency of the team. In fact almost all research efforts (configuration management, groupware systems, recommendation systems, software architectures) are focused on needs at this layer. 3.5 Self-Actualization At this stage the team is well recognized in the community and has the power to negotiate to 4
5 work on projects that the team wants to work on. The team has achieved self actualization. 4 Conclusions Research in collaboration has resulted in a host of tools and environments. Attempts in creating classifying these tools are not comprehensive enough as each classification framework either focuses on a particular aspect of collaboration or the technique that tool employs. We are now at a point in time where we need to incrementally perform research and use the infrastructure already provided by other tools. We therefore take a step back and investigate the collaboration needs of a software development team and then based on those needs identify the research areas that address those needs. We use Maslow s insight into the needs of an individual to create a hierarchy of needs for the team. We have not conducted any ethnographic studies to validate our need hierarchy for the team, but believe that we can use Maslow s insight into the human psyche to extrapolate the psyche of the team. The hierarchy of needs for the team is categorized as a) fundamental needs that allows the team to function as a team and create software deliverables b) safety needs such that the software artifacts created by the team is safe from hardware failures, mistakes by the team or malicious outsiders c) belonging needs such that the team is cohesive and functions as a unit d) esteem needs allow the team to be recognized by others based on their efficiency e) and finally when the team becomes highly acclaimed, it is free to pursue the kind of work that the team desires and has reached self actualization. While creating the need hierarchy and mapping the research areas that cater to the needs in each layer of the hierarchy we observed that almost all research areas have focused in increasing the efficiency of the team. Addressing the belonging needs have been largely the responsibility of the team members. Collocation has allowed team members to build team cohesiveness via face to face meetings and collocated group activities. But as teams become distributed in nature maintaining cohesiveness via face to face interactions becomes difficult. Teams thus increasingly are getting dependent on technology to help them maintain team cohesiveness. The software research community should take advantage of Maslow s insight into the needs of an individual to understand the needs of the team while designing collaborative tools. Acknowledgements Effort partially funded by the National Science Foundation, grant numbers CCR and IIS , and an Eclipse Innovation Grant, About the Authors André van der Hoek is an assistant professor at UC Irvine, Anita Sarma is a Ph.D. student under his supervision. References [1] Vessey, I. and A.P. Sravanapudi, Tools as Collaborative Support Technologies, in Communications of the ACM p [2] Maslow, A.H., Motivation and Personality. 3rd edition ed. 1987: HarperCollins Publishers [3] Conradi, R. and B. Westfechtel, Version Models for Software Configuration Management. ACM Computing Surveys, (2): p [4] Erenkrantz, J.R. and R.N. Taylor. Supporting Distributed and Decentralized Projects: Drawing Lessons from the Open Source Community. in Proceedings of 1st Workshop on Open Source in an Industrial Context. Oct, Anaheim, California. [5] Roseman, M. and S. Greenberg. TeamRooms: Network places for collaboration. in In Proceedings of ACM Computer Supported Cooperative Work [6] Nardi, B., S. Whittaker, and E. Bradner. Interaction and Outeraction: Instant Messaging in Action. in Proceedings of Computer Supported Cooperative Work Philadelphia, PA. [7] A. Lee, A. Girgensohn, and K. Schlueter. NYNEX Portholes: Initial User Reactions and Redesign Implications. in Proceedings of the International ACM SIGGROUP Conference on Supporting Group Work, GROUP' Phoenix, AZ, USA. [8] Dourish, P. and S. Bly. Supporting Awareness in a Distributed Work Group. in Human Factors in Computing Systems, CHI' New York. [9] Cheng, L.-T., et al. Jazzing up Eclipse with Collaborative Tools. in 18th Annual ACM SIGPLAN Conference on Object-Oriented Programming, Systems, Languages, and Applications / Eclipse Technology Exchange Workshop Anaheim, CA. 5
A Need-Based Collaboration Classification Framework
 A Need-Based Collaboration Classification Framework Anita Sarma, André van der Hoek and Li-Te Cheng Department of Informatics Donald Bren School of Info & Comp Sciences University of California Irvine
A Need-Based Collaboration Classification Framework Anita Sarma, André van der Hoek and Li-Te Cheng Department of Informatics Donald Bren School of Info & Comp Sciences University of California Irvine
Maslow Holistic Dynamic Theory
 Maslow Holistic Dynamic Theory Holistic Dynamic Theory assumes that the whole person is continually being motivated by one need or another and that people have the potential to grow toward psychological
Maslow Holistic Dynamic Theory Holistic Dynamic Theory assumes that the whole person is continually being motivated by one need or another and that people have the potential to grow toward psychological
A THEORY OF HUMAN MOTIVATION. Abraham H. Maslow
 A THEORY OF HUMAN MOTIVATION Abraham H. Maslow ABRAHAM MASLOW Abraham Maslow developed the theory of human motivation now known as Maslow's Hierarchy of Needs. A psychologist, Maslow noted that some human
A THEORY OF HUMAN MOTIVATION Abraham H. Maslow ABRAHAM MASLOW Abraham Maslow developed the theory of human motivation now known as Maslow's Hierarchy of Needs. A psychologist, Maslow noted that some human
Accelerated Learning Techniques in Project Management Education Michelle LaBrosse, CEO, Cheetah Learning LLC (PMI REP)
 Accelerated Learning Techniques in Project Management Education Michelle LaBrosse, CEO, Cheetah Learning LLC (PMI REP) Abstract Accelerated Learning methodologies were developed over 40 years ago, and
Accelerated Learning Techniques in Project Management Education Michelle LaBrosse, CEO, Cheetah Learning LLC (PMI REP) Abstract Accelerated Learning methodologies were developed over 40 years ago, and
THERAPEUTIC COMMUNICATION & PATIENT TEACHING. The medical office... The Medical Assistant s role...
 THERAPEUTIC COMMUNICATION & PATIENT TEACHING The medical office... is a strange environment may cause hesitancy & fearfulness: new procedures medical jargon may be overwhelming may create guarded behaviors:
THERAPEUTIC COMMUNICATION & PATIENT TEACHING The medical office... is a strange environment may cause hesitancy & fearfulness: new procedures medical jargon may be overwhelming may create guarded behaviors:
Abraham Maslow: The Needs Hierachy
 Abraham Maslow: The Needs Hierachy Assoc Prof. Dr. Azizi Hj. Yahaya Faculty Of Education Universiti Teknology Malaysia Abstract Abraham Maslow is considered to be the father of Humanistic Psychology. Maslow
Abraham Maslow: The Needs Hierachy Assoc Prof. Dr. Azizi Hj. Yahaya Faculty Of Education Universiti Teknology Malaysia Abstract Abraham Maslow is considered to be the father of Humanistic Psychology. Maslow
Running Head: FORMULATION OF AN EDUCATIONAL PHILOSOPHY AND AN ORGANIZATIONAL FRAMEWORK. Lauren Jansen. Midwestern State University
 Educational Philosophy 1 Running Head: FORMULATION OF AN EDUCATIONAL PHILOSOPHY AND AN ORGANIZATIONAL FRAMEWORK Lauren Jansen Midwestern State University Educational Philosophy 2 Formulation Of An Educational
Educational Philosophy 1 Running Head: FORMULATION OF AN EDUCATIONAL PHILOSOPHY AND AN ORGANIZATIONAL FRAMEWORK Lauren Jansen Midwestern State University Educational Philosophy 2 Formulation Of An Educational
COMMUNICATION & INTERPERSONAL SKILLS Chapter 5
 COMMUNICATION & INTERPERSONAL SKILLS Chapter 5 Maslow s Hierarchy of Needs Interpersonal means between persons. Behavior is how people act, what they say and do. In conversation, a person behaves according
COMMUNICATION & INTERPERSONAL SKILLS Chapter 5 Maslow s Hierarchy of Needs Interpersonal means between persons. Behavior is how people act, what they say and do. In conversation, a person behaves according
Clinic. Richard Smith, LCSW Leonard Savage, Consumer Steven I. Aronin, MD FACP, Program Director
 Positive Psychology Peer Led Programs Waterbury Hospital Infectious Disease Clinic Richard Smith, LCSW Leonard Savage, Consumer Steven I. Aronin, MD FACP, Program Director Ryan White All Grantee Meeting
Positive Psychology Peer Led Programs Waterbury Hospital Infectious Disease Clinic Richard Smith, LCSW Leonard Savage, Consumer Steven I. Aronin, MD FACP, Program Director Ryan White All Grantee Meeting
ACCESS at Lynn. What have we learned? What are some things we ve learned to do really well? Where are we still struggling?
 ACCESS at Lynn What have we learned? What are some things we ve learned to do really well? Where are we still struggling? Maslow s Four Stages of Learning Ability exceeds confidence a boost in confidence
ACCESS at Lynn What have we learned? What are some things we ve learned to do really well? Where are we still struggling? Maslow s Four Stages of Learning Ability exceeds confidence a boost in confidence
The Psychology of a Cyber Predator;
 The Psychology of a Cyber Predator; Decoding the Deviate Mind Janice Niederhofer Peerage Consulting, Inc. Session ID: HT1-203 Session Classification: Intermediate Agenda Traits and characteristics Psychological
The Psychology of a Cyber Predator; Decoding the Deviate Mind Janice Niederhofer Peerage Consulting, Inc. Session ID: HT1-203 Session Classification: Intermediate Agenda Traits and characteristics Psychological
Financial Freedom: Three Steps to Creating and Enjoying the Wealth You Deserve
 Financial Freedom: Three Steps to Creating and Enjoying the Wealth You Deserve What does financial freedom mean to you? Does it mean freedom from having to work, yet still being able to enjoy life without
Financial Freedom: Three Steps to Creating and Enjoying the Wealth You Deserve What does financial freedom mean to you? Does it mean freedom from having to work, yet still being able to enjoy life without
129. Using Reputation System to Motivate Knowledge Contribution Behavior in Online Community
 129. Using Reputation System to Motivate Knowledge Contribution Behavior in Online Community Sarah P.W. Shek City University of Hong Kong issarah@cityu.edu.hk Choon-Ling Sia City University of Hong Kong
129. Using Reputation System to Motivate Knowledge Contribution Behavior in Online Community Sarah P.W. Shek City University of Hong Kong issarah@cityu.edu.hk Choon-Ling Sia City University of Hong Kong
Police Organization and Administration. CJ 3600 Professor James J. Drylie Week 4
 Police Organization and Administration CJ 3600 Professor James J. Drylie Week 4 Organizational Theory To better understand organizations it is important to ask the question cui bono, or who benefits Blatt
Police Organization and Administration CJ 3600 Professor James J. Drylie Week 4 Organizational Theory To better understand organizations it is important to ask the question cui bono, or who benefits Blatt
The IoT Market Analysis Using A Need-Capability-Matrix. Yuan Wang Arrow Electronics
 The IoT Market Analysis Using A Need-Capability-Matrix Yuan Wang Arrow Electronics Arrow at a Glance Founded: 1935 Ticker Symbol: Web Site: ARW (New York Stock Exchange) www.arrow.com 2014 Sales: $22.7
The IoT Market Analysis Using A Need-Capability-Matrix Yuan Wang Arrow Electronics Arrow at a Glance Founded: 1935 Ticker Symbol: Web Site: ARW (New York Stock Exchange) www.arrow.com 2014 Sales: $22.7
THE CAUSES OF DRUG ADDICTION
 1 Statistical facts associated with addiction and substance abuse are concerning, but many men and women choose to ignore the dangers. By understanding the main causes of addiction to drugs, it is possible
1 Statistical facts associated with addiction and substance abuse are concerning, but many men and women choose to ignore the dangers. By understanding the main causes of addiction to drugs, it is possible
MKT 3525 SALES MANAGEMENT FINAL
 MKT 3525 SALES MANAGEMENT FINAL Chapter 3: Territory Management Sales opportunity management - Generating new accounts - Managing existing accounts - Sales versus profits - Personal time management A process
MKT 3525 SALES MANAGEMENT FINAL Chapter 3: Territory Management Sales opportunity management - Generating new accounts - Managing existing accounts - Sales versus profits - Personal time management A process
Dealing with Difficult Behavior & The Maslow Need Hierarchy
 Dealing with Difficult Behavior & The Maslow Need Hierarchy SELF- ACTUALIZATION Pursue Inner Talent, Creativity, Fulfillment Being Needs SELF-ESTEEM Achievement Mastery Recognition Respect Deficit Needs
Dealing with Difficult Behavior & The Maslow Need Hierarchy SELF- ACTUALIZATION Pursue Inner Talent, Creativity, Fulfillment Being Needs SELF-ESTEEM Achievement Mastery Recognition Respect Deficit Needs
2350 MOTIVATION THEORY
 DEOMI SYLLABUS/NOTETAKER 740 O'Malley Rd Revised: 1 December 2000 Patrick AFB, FL 32925 MOTIVATION THEORY LESSON OBJECTIVES LEVEL MEASURE A. Define motivation Knowledge Written B. Identify levels in Maslow
DEOMI SYLLABUS/NOTETAKER 740 O'Malley Rd Revised: 1 December 2000 Patrick AFB, FL 32925 MOTIVATION THEORY LESSON OBJECTIVES LEVEL MEASURE A. Define motivation Knowledge Written B. Identify levels in Maslow
Nursing and Me. Christopher Rideout Professor Dowling, PhD RN 2/13/08
 1 Nursing and Me Christopher Rideout Professor Dowling, PhD RN 2/13/08 2 If I have learned anything about life from the experiences I have had lately it is this: training to be hero is not as easy as many
1 Nursing and Me Christopher Rideout Professor Dowling, PhD RN 2/13/08 2 If I have learned anything about life from the experiences I have had lately it is this: training to be hero is not as easy as many
A Survey of Collaborative Tools in Software Development
 Institute for Software Research University of California, Irvine A Survey of Collaborative Tools in Software Development Anita Sarma University of California, Irvine asarma@ics.uci.edu March 2005 ISR Technical
Institute for Software Research University of California, Irvine A Survey of Collaborative Tools in Software Development Anita Sarma University of California, Irvine asarma@ics.uci.edu March 2005 ISR Technical
Are They the Same Thing? An ADP White Paper
 Employee Satisfaction vs. Employee Engagement: Are They the Same Thing? An ADP White Paper Executive Summary There continues to be a lot of confusion in the HR industry around employee satisfaction and
Employee Satisfaction vs. Employee Engagement: Are They the Same Thing? An ADP White Paper Executive Summary There continues to be a lot of confusion in the HR industry around employee satisfaction and
Maslow s Hierarchy of Needs and Purchasing
 Maslow s Hierarchy of Needs and Purchasing Josh Nelson Consumer Behavior Dr. Zimmer 16 April 201 In the world of consumer behavior, it can be difficult to figure out just what drives a particular decision.
Maslow s Hierarchy of Needs and Purchasing Josh Nelson Consumer Behavior Dr. Zimmer 16 April 201 In the world of consumer behavior, it can be difficult to figure out just what drives a particular decision.
Section 2.2. Self-Esteem. Objectives. Compare the effects of high and low selfesteem
 Objectives Compare the effects of high and low selfesteem on health. Describe the changes in self-esteem that can occur as people age. Identify ways to achieve and maintain high self-esteem. Summarize
Objectives Compare the effects of high and low selfesteem on health. Describe the changes in self-esteem that can occur as people age. Identify ways to achieve and maintain high self-esteem. Summarize
11.1 What is Project Management? Object-Oriented Software Engineering Practical Software Development using UML and Java. What is Project Management?
 11.1 What is Project Management? Object-Oriented Software Engineering Practical Software Development using UML and Java Chapter 11: Managing the Software Process Project management encompasses all the
11.1 What is Project Management? Object-Oriented Software Engineering Practical Software Development using UML and Java Chapter 11: Managing the Software Process Project management encompasses all the
Stanford University s Chronic Disease Self-Management Program Curriculum and Evidence
 Stanford University s Chronic Disease Self-Management Program Curriculum and Evidence What is the Chronic Disease Self-Management Program? The Chronic Disease Self-Management Program (CDSMP), developed
Stanford University s Chronic Disease Self-Management Program Curriculum and Evidence What is the Chronic Disease Self-Management Program? The Chronic Disease Self-Management Program (CDSMP), developed
1 The Unique Character of Human Existence
 1 1 The Unique Character of Human Existence Each of us is confronted with the challenge of being human, the challenge of becoming a person. It is important to emphasize this word challenge, because it
1 1 The Unique Character of Human Existence Each of us is confronted with the challenge of being human, the challenge of becoming a person. It is important to emphasize this word challenge, because it
The fully functioning person: a bio-psycho-social viewpoint
 The fully functioning person: a bio-psycho-social viewpoint Alberto Zucconi World Academy of Art and Science Person Centered Approach Institute (IACP) azucconi@iacp.it HUMANITIES AND THE CONTEMPORARY WORLD
The fully functioning person: a bio-psycho-social viewpoint Alberto Zucconi World Academy of Art and Science Person Centered Approach Institute (IACP) azucconi@iacp.it HUMANITIES AND THE CONTEMPORARY WORLD
Sometimes people live in homes where a parent or other family member drinks too
 Alcohol and Drugs What If I'm Concerned About Someone Else's Drinking? Sometimes people live in homes where a parent or other family member drinks too much. This may make you angry, scared, and depressed.
Alcohol and Drugs What If I'm Concerned About Someone Else's Drinking? Sometimes people live in homes where a parent or other family member drinks too much. This may make you angry, scared, and depressed.
OPEN COMMUNICATION WINS
 BERATUNG JUDITH ANDRESEN SESSION AGILE ON THE BEACH SEPTEMBER, 4TH 2014, PENRYN JUDITH ANDRESEN project coach! judithandresen.com @judithandresen 2 ROBERT C. MARTIN, THE CLEAN CODER The role of the professional
BERATUNG JUDITH ANDRESEN SESSION AGILE ON THE BEACH SEPTEMBER, 4TH 2014, PENRYN JUDITH ANDRESEN project coach! judithandresen.com @judithandresen 2 ROBERT C. MARTIN, THE CLEAN CODER The role of the professional
Virtual Teams and Group Collaboration Technologies:Challenges in Supporting Distributed Groups
 IT Systems Perspective Virtual Teams and Group Collaboration Technologies:Challenges in Supporting Distributed Groups Charles Steinfield Michigan State University Organizations increasingly depend on virtual
IT Systems Perspective Virtual Teams and Group Collaboration Technologies:Challenges in Supporting Distributed Groups Charles Steinfield Michigan State University Organizations increasingly depend on virtual
The Case for Good Family Development in Queensland
 Submission to the Queensland Child Protection Commission of Inquiry from: The Management Committee of Logan East Community Neighbourhood Association Inc. (LECNA) September, 2012 Commissioner Carmody, Fellow
Submission to the Queensland Child Protection Commission of Inquiry from: The Management Committee of Logan East Community Neighbourhood Association Inc. (LECNA) September, 2012 Commissioner Carmody, Fellow
CBIO Security White Paper
 One Canon Plaza Lake Success, NY 11042 www.ciis.canon.com CBIO Security White Paper Introduction to Canon Business Imaging Online Canon Business Imaging Online ( CBIO ) is a cloud platform for Canon s
One Canon Plaza Lake Success, NY 11042 www.ciis.canon.com CBIO Security White Paper Introduction to Canon Business Imaging Online Canon Business Imaging Online ( CBIO ) is a cloud platform for Canon s
From Network Security To Content Filtering
 Computer Fraud & Security, May 2007 page 1/10 From Network Security To Content Filtering Network security has evolved dramatically in the last few years not only for what concerns the tools at our disposals
Computer Fraud & Security, May 2007 page 1/10 From Network Security To Content Filtering Network security has evolved dramatically in the last few years not only for what concerns the tools at our disposals
ArchiMate Extension for Modeling the TOGAF Implementation and Migration Phases
 ArchiMate Extension for Modeling the TOGAF Implementation and Migration Phases A White Paper by: Henk Jonkers, Harmen van den Berg, Maria-Eugenia Iacob, and Dick Quartel December 2010 Copyright 2010 The
ArchiMate Extension for Modeling the TOGAF Implementation and Migration Phases A White Paper by: Henk Jonkers, Harmen van den Berg, Maria-Eugenia Iacob, and Dick Quartel December 2010 Copyright 2010 The
HOW TO CHOOSE A CLOUD BACKUP SERVICE PROVIDER
 HOW TO CHOOSE A CLOUD BACKUP SERVICE PROVIDER Why Should You Protect Your Data? Sooner or later by mischief, misfortune or mistake it is statistically likely that you will lose precious data. A 2007 Carnegie
HOW TO CHOOSE A CLOUD BACKUP SERVICE PROVIDER Why Should You Protect Your Data? Sooner or later by mischief, misfortune or mistake it is statistically likely that you will lose precious data. A 2007 Carnegie
A Framework to Map and Grow Your Data Strategy
 A Framework to Map and Grow Your Data Strategy Adapting Maslow's Hierarchy to manage multiyear data projects and a tool to monitor, predict and prevent program failure Maria Villar, Theresa Kushner Many
A Framework to Map and Grow Your Data Strategy Adapting Maslow's Hierarchy to manage multiyear data projects and a tool to monitor, predict and prevent program failure Maria Villar, Theresa Kushner Many
Improving Cognos Upgrades Methodology to Lower Costs & Improve Upgrade Management
 White Paper Improving Cognos Upgrades Methodology to Lower Costs & Improve Upgrade Management by Edwin van Megesen Motio, Inc. Executive Summary BI platforms are continuously changing. New requirements
White Paper Improving Cognos Upgrades Methodology to Lower Costs & Improve Upgrade Management by Edwin van Megesen Motio, Inc. Executive Summary BI platforms are continuously changing. New requirements
How unique are you? Activity 10.1 p136 - Make a list of the things about yourself that you think are different from other people.
 THE SELF The Humanistic Approach BATs Define the terms unique and free will (E) Describe the humanistic theory of Self. (D) Explain the differences between selfconcept, ideal self and self-esteem (C) How
THE SELF The Humanistic Approach BATs Define the terms unique and free will (E) Describe the humanistic theory of Self. (D) Explain the differences between selfconcept, ideal self and self-esteem (C) How
How to Choose a Cloud Backup Service Provider
 How to Choose a Cloud Backup Service Provider List Products Implemented in File- Properties Why Should You Protect Your Data? Sooner or later - by mischief, misfortune or mistake - Odds are you will experience
How to Choose a Cloud Backup Service Provider List Products Implemented in File- Properties Why Should You Protect Your Data? Sooner or later - by mischief, misfortune or mistake - Odds are you will experience
MANAGEMENT OF STRESS AT WORK POLICY
 MANAGEMENT OF STRESS AT WORK POLICY Co-ordinator: Director of HR Reviewer: Grampian Area Partnership Forum Approver: Grampian Area Partnership Forum Signature Signature Signature Identifier: NHS/OH&S/Pol
MANAGEMENT OF STRESS AT WORK POLICY Co-ordinator: Director of HR Reviewer: Grampian Area Partnership Forum Approver: Grampian Area Partnership Forum Signature Signature Signature Identifier: NHS/OH&S/Pol
Co-dependency. Fact Sheet on co-dependency from Mental Health America:
 Co-dependency Fact Sheet on co-dependency from Mental Health America: Co-dependency is a learned behavior that can be passed down from one generation to another. It is an emotional and behavioral condition
Co-dependency Fact Sheet on co-dependency from Mental Health America: Co-dependency is a learned behavior that can be passed down from one generation to another. It is an emotional and behavioral condition
Change Leadership: A Boot Camp to Drive Organizational Change
 Change Leadership: A Boot Camp to Drive Organizational Change Presented by: Rachel Schaming Radiology Ltd. Tucson, AZ 520.705.2889 Email: Rachel.Schaming@radltd.com Your Perceptions of Change What are
Change Leadership: A Boot Camp to Drive Organizational Change Presented by: Rachel Schaming Radiology Ltd. Tucson, AZ 520.705.2889 Email: Rachel.Schaming@radltd.com Your Perceptions of Change What are
EMPLOYEE ENGAGEMENT STRATEGY: A STRATEGY OF ANALYSIS TO MOVE FROM EMPLOYEE SATISFACTION TO ENGAGEMENT
 EMPLOYEE ENGAGEMENT STRATEGY: A STRATEGY OF ANALYSIS TO MOVE FROM EMPLOYEE SATISFACTION TO ENGAGEMENT Employee engagement surveys are a good tool for soliciting the ideas and opinions of your employees.
EMPLOYEE ENGAGEMENT STRATEGY: A STRATEGY OF ANALYSIS TO MOVE FROM EMPLOYEE SATISFACTION TO ENGAGEMENT Employee engagement surveys are a good tool for soliciting the ideas and opinions of your employees.
THE ABSENT MOTHER. The Psychological and Emotional Consequences of Childhood Abandonment and Neglect. Dr. Judith Arndell Clinical Psychologist
 THE ABSENT MOTHER. The Psychological and Emotional Consequences of Childhood Abandonment and Neglect Dr. Judith Arndell Clinical Psychologist The Psychological Parent The object of the child s deepest
THE ABSENT MOTHER. The Psychological and Emotional Consequences of Childhood Abandonment and Neglect Dr. Judith Arndell Clinical Psychologist The Psychological Parent The object of the child s deepest
ITIL V3 and ASL Sound Guidance for Application Management and Application Development
 For IT V3 and Sound Guidance for Application and Application Development Machteld Meijer, Mark Smalley & Sharon Taylor Alignment White Paper January 2008 V3 & : A Comparison Abstract In May 2007, the Office
For IT V3 and Sound Guidance for Application and Application Development Machteld Meijer, Mark Smalley & Sharon Taylor Alignment White Paper January 2008 V3 & : A Comparison Abstract In May 2007, the Office
How to Choose a Cloud Backup Service Provider
 How to Choose a Cloud Backup Service Provider Why Should You Protect Your Data? Sooner or later - by mischief, misfortune or mistake - Odds are you will experience a data loss. Hardware failure, accidental
How to Choose a Cloud Backup Service Provider Why Should You Protect Your Data? Sooner or later - by mischief, misfortune or mistake - Odds are you will experience a data loss. Hardware failure, accidental
MODEL OF SOFTWARE AGENT FOR NETWORK SECURITY ANALYSIS
 MODEL OF SOFTWARE AGENT FOR NETWORK SECURITY ANALYSIS Hristo Emilov Froloshki Department of telecommunications, Technical University of Sofia, 8 Kliment Ohridski st., 000, phone: +359 2 965 234, e-mail:
MODEL OF SOFTWARE AGENT FOR NETWORK SECURITY ANALYSIS Hristo Emilov Froloshki Department of telecommunications, Technical University of Sofia, 8 Kliment Ohridski st., 000, phone: +359 2 965 234, e-mail:
Essay about online college tuition >>>CLICK HERE<<<
 Essay about online college tuition. Mascar Rooney is the author of this article on Blog commenting Service. Essay about online college tuition >>>CLICK HERE
Essay about online college tuition. Mascar Rooney is the author of this article on Blog commenting Service. Essay about online college tuition >>>CLICK HERE
Systems Engineering with RUP: Process Adoption in the Aerospace/ Defense Industry
 March 2004 Rational Systems Engineering with RUP: Process Adoption in the Aerospace/ Defense Industry Why companies do it, how they do it, and what they get for their effort By Dave Brown, Karla Ducharme,
March 2004 Rational Systems Engineering with RUP: Process Adoption in the Aerospace/ Defense Industry Why companies do it, how they do it, and what they get for their effort By Dave Brown, Karla Ducharme,
LINKING KNOWLEDGE MANAGEMENT WITH HUMAN CAPITAL STRATEGY DEVELOPMENT
 LINKING KNOWLEDGE MANAGEMENT WITH HUMAN CAPITAL STRATEGY DEVELOPMENT Dr. Jay Liebowitz, Johns Hopkins University, jliebow1@jhu.edu ABSTRACT Organizations are realizing that knowledge management should
LINKING KNOWLEDGE MANAGEMENT WITH HUMAN CAPITAL STRATEGY DEVELOPMENT Dr. Jay Liebowitz, Johns Hopkins University, jliebow1@jhu.edu ABSTRACT Organizations are realizing that knowledge management should
How Psychotherapy Works: The Concepts of Control-Mastery Theory
 How Psychotherapy Works: The Concepts of Control-Mastery Theory Alan Rappoport, Ph.D. I am pleased to present Control-Mastery theory to you, the members of the Academy of Clinical Psychology. The use of
How Psychotherapy Works: The Concepts of Control-Mastery Theory Alan Rappoport, Ph.D. I am pleased to present Control-Mastery theory to you, the members of the Academy of Clinical Psychology. The use of
Infor CloudSuite. Defense-in-depth. Table of Contents. Technical Paper Plain talk about Infor CloudSuite security
 Technical Paper Plain talk about security When it comes to Cloud deployment, security is top of mind for all concerned. The Infor CloudSuite team uses best-practice protocols and a thorough, continuous
Technical Paper Plain talk about security When it comes to Cloud deployment, security is top of mind for all concerned. The Infor CloudSuite team uses best-practice protocols and a thorough, continuous
National Association for Self-Esteem
 National Association for Self-Esteem SELF-ESTEEM TODAY September 2008 NASE Member Newsletter In This Issue: Excerpt from a new book, Real kids in an Unreal world Excerpt from Jack Canfield's Success Strategies
National Association for Self-Esteem SELF-ESTEEM TODAY September 2008 NASE Member Newsletter In This Issue: Excerpt from a new book, Real kids in an Unreal world Excerpt from Jack Canfield's Success Strategies
Satir Transformational Systemic Therapy (in Brief)
 Satir Transformational Systemic Therapy (in Brief) What happens when a human being appears on the professional radar and, without directly challenging the prevailing system, provides new possibilities
Satir Transformational Systemic Therapy (in Brief) What happens when a human being appears on the professional radar and, without directly challenging the prevailing system, provides new possibilities
In the 1970s psychiatric rehabilitation INTEGRATING PSYCHIATRIC REHABILITATION INTO MANAGED CARE
 FALL 1996 Volume 20 Number 2 INTEGRATING PSYCHIATRIC REHABILITATION INTO MANAGED CARE WILLIAM A. ANTHONY William A. Anthony, PhD, is Executive Director of the Center for Psychiatric Rehabilitation at Boston
FALL 1996 Volume 20 Number 2 INTEGRATING PSYCHIATRIC REHABILITATION INTO MANAGED CARE WILLIAM A. ANTHONY William A. Anthony, PhD, is Executive Director of the Center for Psychiatric Rehabilitation at Boston
Data S ec e u c ri r t i y als l o F I F SMA
 Data Security also FISMA Scott Bradner University Technology Security Officer Harvard University Research Compliance Conference June 13, 2011 302-1 Issues in Research Data Security communication mindset
Data Security also FISMA Scott Bradner University Technology Security Officer Harvard University Research Compliance Conference June 13, 2011 302-1 Issues in Research Data Security communication mindset
Introduction to Workflow
 Introduction to Workflow SISTEMI INFORMATICI SUPPORTO ALLE DECISIONI AA 2006-2007 Libro di testo: Wil van der Aalst and Kees van Hee. Workflow Management: Models, Methods, and Systems. The MIT Press, paperback
Introduction to Workflow SISTEMI INFORMATICI SUPPORTO ALLE DECISIONI AA 2006-2007 Libro di testo: Wil van der Aalst and Kees van Hee. Workflow Management: Models, Methods, and Systems. The MIT Press, paperback
SharePoint Project Management: The Key to Successful User Adoption
 SharePoint Project Management: The Key to Successful User Adoption Leanne M. Bateman, PMP Principal Consultant February 2012 www.beaconstrategy.com Table of Contents ABSTRACT... 3 ABOUT THE AUTHOR... 3
SharePoint Project Management: The Key to Successful User Adoption Leanne M. Bateman, PMP Principal Consultant February 2012 www.beaconstrategy.com Table of Contents ABSTRACT... 3 ABOUT THE AUTHOR... 3
Process Addictions. Process Addiction? What is that? Why is this Important? Hagedorn MHS 6450 1. The New Gateway to Chemical Addiction?
 Process Addictions The New Gateway to Chemical Addiction? W. Bryce Hagedorn, PhD, LMHC, NCC, MAC Process Addiction? What is that? The Definition any compulsive-like behavior that interferes with normal
Process Addictions The New Gateway to Chemical Addiction? W. Bryce Hagedorn, PhD, LMHC, NCC, MAC Process Addiction? What is that? The Definition any compulsive-like behavior that interferes with normal
Main body by Glen McCallum, Wellness Wheel Counsellor
 Introduction by Vince Natomagan Main body by Glen McCallum, Wellness Wheel Counsellor As practised by the Pinehouse Reclaiming Our Community working group Honourable Mention: Dr. Tom Hengen, Pyschologist
Introduction by Vince Natomagan Main body by Glen McCallum, Wellness Wheel Counsellor As practised by the Pinehouse Reclaiming Our Community working group Honourable Mention: Dr. Tom Hengen, Pyschologist
TDWI strives to provide course books that are content-rich and that serve as useful reference documents after a class has ended.
 Previews of TDWI course books offer an opportunity to see the quality of our material and help you to select the courses that best fit your needs. The previews cannot be printed. TDWI strives to provide
Previews of TDWI course books offer an opportunity to see the quality of our material and help you to select the courses that best fit your needs. The previews cannot be printed. TDWI strives to provide
Web Security School Final Exam
 Web Security School Final Exam By Michael Cobb 1.) Which of the following services is not required to run a Windows server solely configured to run IIS and publish a Web site on the Internet? a. IIS Admin
Web Security School Final Exam By Michael Cobb 1.) Which of the following services is not required to run a Windows server solely configured to run IIS and publish a Web site on the Internet? a. IIS Admin
Designing Software Cockpits for Coordinating Distributed Software Development
 Designing Software Cockpits for Coordinating Distributed Software Development 1,2 Isabella da Silva, 1 Marcelo Alvim, 1 Roger Ripley, 1 Anita Sarma, 2 Cláudia Werner, 1 André van der Hoek 1 Department
Designing Software Cockpits for Coordinating Distributed Software Development 1,2 Isabella da Silva, 1 Marcelo Alvim, 1 Roger Ripley, 1 Anita Sarma, 2 Cláudia Werner, 1 André van der Hoek 1 Department
8 Steps for Network Security Protection
 8 Steps for Network Security Protection cognoscape.com 8 Steps for Network Security Protection Many small and medium sized businesses make the mistake of thinking they won t be the target of hackers because
8 Steps for Network Security Protection cognoscape.com 8 Steps for Network Security Protection Many small and medium sized businesses make the mistake of thinking they won t be the target of hackers because
Healthy Relationships
 Healthy Relationships March 2005 KSC/CCAFS Health Education and Wellness Program Heather Torbett, MPH Kris S. Calderon, PhD, CHES Patricia Bell, LMC Relationship Health Many relationships are not as healthy
Healthy Relationships March 2005 KSC/CCAFS Health Education and Wellness Program Heather Torbett, MPH Kris S. Calderon, PhD, CHES Patricia Bell, LMC Relationship Health Many relationships are not as healthy
8 Steps For Network Security Protection
 8 Steps For Network Security Protection 8 Steps For Network Security Protection Many small and medium sized businesses make the mistake of thinking they won t be the target of hackers because of their
8 Steps For Network Security Protection 8 Steps For Network Security Protection Many small and medium sized businesses make the mistake of thinking they won t be the target of hackers because of their
A VERITAS PERSPECTIVE: Maximize Agility, Minimize Risk In The Multi-Vendor Hybrid Cloud
 A VERITAS PERSPECTIVE: Maximize Agility, Minimize Risk In The Multi-Vendor Hybrid Cloud 1 THE HYBRID CLOUD DILEMMA Finding Agility without Adding Fragility Today, businesses have to move fast to stay competitive.
A VERITAS PERSPECTIVE: Maximize Agility, Minimize Risk In The Multi-Vendor Hybrid Cloud 1 THE HYBRID CLOUD DILEMMA Finding Agility without Adding Fragility Today, businesses have to move fast to stay competitive.
The Seven Levels of Team Consciousness
 The Seven Levels of Team Consciousness By Richard Barrett Teams grow and develop by mastering the seven levels of team consciousness. The seven groups of needs/motivations that are associated with the
The Seven Levels of Team Consciousness By Richard Barrett Teams grow and develop by mastering the seven levels of team consciousness. The seven groups of needs/motivations that are associated with the
Management and Organizational Behavior. Historical Foundations. Classical Approaches. Historical Foundations of Management - 2
 Management and Organizational Behavior Historical Foundations of Management - 2 Historical Foundations Classical Approaches to Management Behavioral Approaches to Management Modern Approaches to Management
Management and Organizational Behavior Historical Foundations of Management - 2 Historical Foundations Classical Approaches to Management Behavioral Approaches to Management Modern Approaches to Management
Paper SS-08. Some situations that will lead to an inefficient SAS Enterprise Business Intelligence environment rollout are:
 Paper SS-08 A Step by Step Approach to Preparing for a SAS Intelligence Platform Environment Deployment/Migration Brian Varney, Experis Business Analytics Practice, Portage, Michigan ABSTRACT Getting a
Paper SS-08 A Step by Step Approach to Preparing for a SAS Intelligence Platform Environment Deployment/Migration Brian Varney, Experis Business Analytics Practice, Portage, Michigan ABSTRACT Getting a
1 Introduction. 2 What is Cloud Computing?
 1 Introduction Table of Contents 1 Introduction 2 What is Cloud Computing? 3 Why is Cloud Computing important? 4 Why Cloud deployments fail? 5 Holistic Approach to cloud computing implementation 6 Conclusion
1 Introduction Table of Contents 1 Introduction 2 What is Cloud Computing? 3 Why is Cloud Computing important? 4 Why Cloud deployments fail? 5 Holistic Approach to cloud computing implementation 6 Conclusion
Solution Brief: Enterprise Security
 Symantec Brightmail Gateway and VMware Solution Brief: Enterprise Security Symantec Brightmail Gateway and VMware Contents Corporate overview......................................................................................
Symantec Brightmail Gateway and VMware Solution Brief: Enterprise Security Symantec Brightmail Gateway and VMware Contents Corporate overview......................................................................................
DRUGS? NO THANKS! What are some of the leading factors that cause you to. become interested in experimenting with illegal drugs?
 DRUGS? NO THANKS! What are some of the leading factors that cause you to become interested in experimenting with illegal drugs? It is easily available: During adolescence, you are trying to figure out
DRUGS? NO THANKS! What are some of the leading factors that cause you to become interested in experimenting with illegal drugs? It is easily available: During adolescence, you are trying to figure out
Exploration on Security System Structure of Smart Campus Based on Cloud Computing. Wei Zhou
 3rd International Conference on Science and Social Research (ICSSR 2014) Exploration on Security System Structure of Smart Campus Based on Cloud Computing Wei Zhou Information Center, Shanghai University
3rd International Conference on Science and Social Research (ICSSR 2014) Exploration on Security System Structure of Smart Campus Based on Cloud Computing Wei Zhou Information Center, Shanghai University
2012 Endpoint Security Best Practices Survey
 WHITE PAPER: 2012 ENDPOINT SECURITY BEST PRACTICES SURVEY........................................ 2012 Endpoint Security Best Practices Survey Who should read this paper Small and medium business owners
WHITE PAPER: 2012 ENDPOINT SECURITY BEST PRACTICES SURVEY........................................ 2012 Endpoint Security Best Practices Survey Who should read this paper Small and medium business owners
Family Ties: How Parents Influence Adolescent Substance Use
 ][ Strength ening our community through education and awaren ess ][ Report from the Mercyhurst College Civic Institute Vol.1 Issue 1 Summer 2009 Additional Reports Erie County Truancy Assessment Erie County
][ Strength ening our community through education and awaren ess ][ Report from the Mercyhurst College Civic Institute Vol.1 Issue 1 Summer 2009 Additional Reports Erie County Truancy Assessment Erie County
Dowell Institute Theological Seminary. Associates of Science Christian Counseling Degree And Christian Life Coach Diploma Syllabus
 1 Welcome to. You are embarking on a journey that will undoubtedly prepare you for a rewarding career as a Christian Counselor/ Christian Life Coach. As you learn from DITS course curriculum you will develop
1 Welcome to. You are embarking on a journey that will undoubtedly prepare you for a rewarding career as a Christian Counselor/ Christian Life Coach. As you learn from DITS course curriculum you will develop
Int. J. Pharm. Sci. Rev. Res., 33(2), July August 2015; Article No. 06, Pages: 25-29
 Research Article *A.R.Shanmuga Priya, **R.Krishnaraj, ***M.Chitra *Assistant Professor, Faculty of Management, SRM University, Kattankulathur, Kancheepuram, Tamil Nadu, India. **Assistant Professor, Faculty
Research Article *A.R.Shanmuga Priya, **R.Krishnaraj, ***M.Chitra *Assistant Professor, Faculty of Management, SRM University, Kattankulathur, Kancheepuram, Tamil Nadu, India. **Assistant Professor, Faculty
Disability Management: Best Practices and Holistic Approach. Presented by Nicole Raymond October 30, 2013
 Disability Management: Best Practices and Holistic Approach Presented by Nicole Raymond October 30, 2013 AN ALARMING SITUATION 2 An alarming situation Mental health is the number one cause of disability
Disability Management: Best Practices and Holistic Approach Presented by Nicole Raymond October 30, 2013 AN ALARMING SITUATION 2 An alarming situation Mental health is the number one cause of disability
The Counselor as a Person and as a Professional
 Self-Awareness The Counselor as a Person and as a Professional Chapter 2 Psychology 475 Professional Ethics in Addictions Counseling Listen to the audio lecture while viewing these slides Without a high
Self-Awareness The Counselor as a Person and as a Professional Chapter 2 Psychology 475 Professional Ethics in Addictions Counseling Listen to the audio lecture while viewing these slides Without a high
Software Configuration Management. Context. Learning Objectives
 Software Configuration Management Wolfgang Emmerich Professor of Distributed Computing University College London http://sse.cs.ucl.ac.uk Context Requirements Inception Elaboration Construction Transition
Software Configuration Management Wolfgang Emmerich Professor of Distributed Computing University College London http://sse.cs.ucl.ac.uk Context Requirements Inception Elaboration Construction Transition
Onboarding and Engaging New Employees
 Onboarding and Engaging New Employees Onboarding is the process of helping new employees become full contributors to the institution. During onboarding, new employees evolve from institutional outsiders
Onboarding and Engaging New Employees Onboarding is the process of helping new employees become full contributors to the institution. During onboarding, new employees evolve from institutional outsiders
Intensive Application
 Intensive Application Branches Recovery Center is a faith-based, non-profit, counseling center specializing in recovery from addiction, depression and shame. We offer value centered counseling and life
Intensive Application Branches Recovery Center is a faith-based, non-profit, counseling center specializing in recovery from addiction, depression and shame. We offer value centered counseling and life
Controlling Risk, Conserving Bandwidth, and Monitoring Productivity with Websense Web Security and Websense Content Gateway
 Controlling Risk, Conserving Bandwidth, and Monitoring Productivity with Websense Web Security and Websense Content Gateway Websense Support Webinar January 2010 web security data security email security
Controlling Risk, Conserving Bandwidth, and Monitoring Productivity with Websense Web Security and Websense Content Gateway Websense Support Webinar January 2010 web security data security email security
ITIL Managing Digital Information Assets
 ITIL Managing Digital Information Assets Shirley Lacy, ConnectSphere Frieda Midgley, Digital Continuity Project Judith Riley, Digital Continuity Project Nigel Williamson, Digital Continuity Project White
ITIL Managing Digital Information Assets Shirley Lacy, ConnectSphere Frieda Midgley, Digital Continuity Project Judith Riley, Digital Continuity Project Nigel Williamson, Digital Continuity Project White
Applied Psychology. Course Descriptions
 Applied Psychology s AP 6001 PRACTICUM SEMINAR I 1 CREDIT AP 6002 PRACTICUM SEMINAR II 3 CREDITS Prerequisites: AP 6001: Successful completion of core courses. Approval of practicum site by program coordinator.
Applied Psychology s AP 6001 PRACTICUM SEMINAR I 1 CREDIT AP 6002 PRACTICUM SEMINAR II 3 CREDITS Prerequisites: AP 6001: Successful completion of core courses. Approval of practicum site by program coordinator.
If the only tool you have is a hammer, you tend to see every problem as a nail.
 How do we approach addiction? ADDICTION 101 A basic primer on addiction If the only tool you have is a hammer, you tend to see every problem as a nail. (Abraham Maslow) Definition of addiction Alcoholism
How do we approach addiction? ADDICTION 101 A basic primer on addiction If the only tool you have is a hammer, you tend to see every problem as a nail. (Abraham Maslow) Definition of addiction Alcoholism
Dr.Karthik Mohandoss H UMAN RESOURCE M ANAGEMENT
 HUMAN RESOURCE MANAGEMENT 103209 CHAPTER I 1 I NTRODUCTION TO H UMAN RESOURCE M ANAGEMENT LEARNING OUTCOMES At the end of this chapter you will be able to understand and have knowledge about The definition
HUMAN RESOURCE MANAGEMENT 103209 CHAPTER I 1 I NTRODUCTION TO H UMAN RESOURCE M ANAGEMENT LEARNING OUTCOMES At the end of this chapter you will be able to understand and have knowledge about The definition
WHAT EVERY PSYCHOLOGIST SHOULD KNOW ABOUT GUIDED IMAGERY
 WHAT EVERY PSYCHOLOGIST SHOULD KNOW ABOUT GUIDED IMAGERY by David E. Bresler, Ph.D., L.Ac. Associate Clinical Professor, UCLA School of Medicine Executive Director, The Bresler Center, Los Angeles, California
WHAT EVERY PSYCHOLOGIST SHOULD KNOW ABOUT GUIDED IMAGERY by David E. Bresler, Ph.D., L.Ac. Associate Clinical Professor, UCLA School of Medicine Executive Director, The Bresler Center, Los Angeles, California
Data Center. Business Intelligence. Enterprise Computing Solutions North America. Learning Solutions IBM Training. Brand Photo Here. arrow.
 Business Intelligence Data Center Cloud Mobility Enterprise Computing Solutions North America Learning Solutions IBM Training Brand Photo Here arrow.com IBM Training At Arrow, we think Five Years Out.
Business Intelligence Data Center Cloud Mobility Enterprise Computing Solutions North America Learning Solutions IBM Training Brand Photo Here arrow.com IBM Training At Arrow, we think Five Years Out.
EHR implementation requires commitment and planning. When it s done right, everyone benefits.
 More and more medical practices are selecting and implementing electronic health records (EHR) than ever before. Statistics indicate that the number of practices purchasing an EHR has doubled over the
More and more medical practices are selecting and implementing electronic health records (EHR) than ever before. Statistics indicate that the number of practices purchasing an EHR has doubled over the
Securing Microsoft Exchange 2010 with Symantec SSL Certificates
 BUSINESS GUIDE: SECURING MICROSOFT EXCHANGE 2010 WITH SYMANTEC SSL CERTIFICATES Symantec Business Guide Securing Microsoft Exchange 2010 with Symantec SSL Certificates Best Practices for Securing Your
BUSINESS GUIDE: SECURING MICROSOFT EXCHANGE 2010 WITH SYMANTEC SSL CERTIFICATES Symantec Business Guide Securing Microsoft Exchange 2010 with Symantec SSL Certificates Best Practices for Securing Your
Substance Abuse Treatment Alternatives
 Substance Abuse Treatment Alternatives What You Should Know Tim Chapman, CSAC February 1 4, 2009 Introduction The purpose of this white paper is to provide information that will help you better understand
Substance Abuse Treatment Alternatives What You Should Know Tim Chapman, CSAC February 1 4, 2009 Introduction The purpose of this white paper is to provide information that will help you better understand
How To Understand The Legal System
 Topic: The legal system Lesson: Legalising drugs KS or Year Group: Year 10/11 Resources: 1. Resource 1 Sky News clip 1 Police chief: All drugs should be legal 2. Resource 2 Sky News clip 2 Netherlands
Topic: The legal system Lesson: Legalising drugs KS or Year Group: Year 10/11 Resources: 1. Resource 1 Sky News clip 1 Police chief: All drugs should be legal 2. Resource 2 Sky News clip 2 Netherlands
How To Get A Computer Science Degree
 MAJOR: DEGREE: COMPUTER SCIENCE MASTER OF SCIENCE (M.S.) CONCENTRATIONS: HIGH-PERFORMANCE COMPUTING & BIOINFORMATICS CYBER-SECURITY & NETWORKING The Department of Computer Science offers a Master of Science
MAJOR: DEGREE: COMPUTER SCIENCE MASTER OF SCIENCE (M.S.) CONCENTRATIONS: HIGH-PERFORMANCE COMPUTING & BIOINFORMATICS CYBER-SECURITY & NETWORKING The Department of Computer Science offers a Master of Science
Wendi Friesen ADDICTION PROJECT CLASS OUTLINE 3 Online Classes
 Wendi Friesen ADDICTION PROJECT CLASS OUTLINE 3 Online Classes IMPORTANT- This is not intended as a complete training to qualify you as a relapse prevention expert, coach or counselor. This is a portion
Wendi Friesen ADDICTION PROJECT CLASS OUTLINE 3 Online Classes IMPORTANT- This is not intended as a complete training to qualify you as a relapse prevention expert, coach or counselor. This is a portion
InterPath Financial Institution: Network Security Implementation. By Allan Feid
 InterPath Financial Institution: Network Security Implementation By Allan Feid 4/30/2008 Table of Contents InterPath Financial Institution: Network Security Implementation...1 Executive Summary...3 The
InterPath Financial Institution: Network Security Implementation By Allan Feid 4/30/2008 Table of Contents InterPath Financial Institution: Network Security Implementation...1 Executive Summary...3 The
SharePoint Project Management: The Key to Successful User Adoption
 SharePoint Project Management: The Key to Successful User Adoption Leanne M. Bateman, PMP February 2012 Leanne Bateman, 2012. All rights reserved. Table of Contents ABSTRACT... 3 ABOUT THE AUTHOR... 3
SharePoint Project Management: The Key to Successful User Adoption Leanne M. Bateman, PMP February 2012 Leanne Bateman, 2012. All rights reserved. Table of Contents ABSTRACT... 3 ABOUT THE AUTHOR... 3
