Configuring Event Log Monitoring With Sentry-go Quick & Plus! monitors
|
|
|
- Lindsay Haynes
- 8 years ago
- Views:
Transcription
1 Configuring Event Log Monitoring With Sentry-go Quick & Plus! monitors 3Ds (UK) Limited, November, Be Proactive, Not Reactive! Many server-based applications, as well as Windows itself write their errors to the Windows Event Log. In addition, applications such as Microsoft Exchange, SQL Server & Internet Information etc. also write messages to their own text-based log files. However, because both of these are typically located on the local machine, proactively monitoring them can be difficult. With Sentry-go, monitoring messages written to one or more Event Logs, text-based or memory mapped files is both quick & easy to achieve. In this guide System requirements... 2 Recommended settings... 2 Monitoring event logs & log files... 2 Event logs & log file settings... 3 Configuring event log monitoring... 4 Configuring text file monitoring... 7 How to monitor log files Considerations for file types Considerations for other file systems Scheduling a check Configuring an automatic response Configuring an alert Temporarily ignoring a configured check More Information... 13
2 System requirements This component is fully compatible with both Sentry-go Quick Monitors v6 and above, and Sentry-go Plus! v6 monitors and above. Recommended settings It is recommended that the System & Application Event Logs are monitored for errors being recorded. Other requirements are dependent on the software installed. Monitoring event logs & log files To set up monitoring, configure the appropriate monitor and select the Logs tab.
3 Event logs & log file settings To view or edit global settings for the log monitor, click the Settings button to display the following window o view or edit global settings for the log monitor, click the Settings button to display the following window Show only the logged message in the alert By default, the captured message text from the log file or event log will be displayed within information relating to the alert e.g. The following message was detected etc. This makes the alert message more readable when sent by e- mail or to Consoles. Tick this option to only log the message text, with no additional alert-related information shown before it. In earlier versions of Sentry-go this was the default behaviour. Ignore event log translation errors When an event log message cannot be translated (e.g. the required DLLs are not installed on the server, the message is corrupt etc.), Sentry-go will, by default, substitute an error message followed by any variables that were supplied. Tick this option to replace the error message with a default text Event log message: followed by the variables that would have been displayed (or the raw XML for later versions of Windows).
4 Configuring event log monitoring To monitor a new Event log or edit an existing one, select the Add or Edit option from the main window. From here you can define which Event Log you wish to monitor and under which conditions an alert should be triggered. Refer to this log file or check as This is the unique name of the check being made. It is this name that will be displayed on reports and when alerts are generated. It is recommended that a short descriptive name be used for this value.
5 The name/path of this file is For standard Event Logs this value is read-only and indicates the name of the selected Event Log above. There is no need to enter a path for Event Logs. For custom Event Logs, this should be the registered name of the Event Log. To find this name Run Regedit.exe on the machine being monitored to access the local registry. Do not edit the Registry values, we simply want to view them. Navigate to the key HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\Eventlog Below this key will be a number of sub-keys including Application, System etc. Other registered names will also be listed. Enter the appropriate name given here into this field to monitor the custom Event Log. Care should be taken when accessing the Registry. Unless you have been advised to do so, or you fully understand your actions, do not change any values in the Registry. Incorrect settings may cause unpredictable results or result in the server failing to boot. Do not enter the path of the Event log s.evt file in this field. The name entered must be the registered name of the file. Due to the way the Windows Event Log model works, if an incorrect Event Log name is specified, no error will be returned. Instead, the Application log will be opened and monitored & you will see false alerts being reported. See above for information on determining the registered Event Log name. The type of this file is... Select the type of Event Log you wish to monitor from the list. Event Type When checked (ticked), this optional value allows you to select the type of event you wish to filter on -e.g. errors, warnings etc. If not entered, all event types are used in the scan. Event Source When checked (ticked), this optional value allows you to define the name of event source (the source name shown in Event Viewer for a particular message - normally the name of the application generating the event) you wish to filter on. If not entered, events from all sources are used in the scan. Event ID When checked (ticked), this optional value allows you to enter the ID of the message you wish to check. Each event log message is generated with an ID that uniquely defines it within the context of the source application or system. If not entered, all IDs are used in the scan. To check for more than one ID, enter each, separated with a comma.
6 Keywords The monitor detects errors in Event Logs using Sentry-go's keyword detection technology. Keywords or phrases can be used either to detect an error, or to find errors that you do not wish to monitor. Both are defined at the bottom of this window. Add Keyword. Click this button to add a keyword or phrase that you wish to monitor to the list. If the keyword or phrase is found, an alert will be triggered, unless excluded keywords are also found. To record all events, enter [All Records] as your phrase. Add Exclude. Click this button to add a keyword or phrase that indicates that the message should be ignored. If an excluded keyword is found, the message is automatically ignored, regardless of other settings. Edit. Click Edit to edit an existing keyword or phrase listed. Delete. Click Delete to remove an existing keyword or phrase from the list. To Trigger an Alert... must be present. This option determines when an alert should be triggered & keyword detection is defined... o All Phrases. Select this option if all keywords listed must be present in the message in order to generate an alert. Excluded keywords do not count in this check o Any Phrase. Select this option to trigger an alert if one or more of the keywords listed are found in the message. When defining a message, there is no need to add complete error messages to this list - one or more keywords is usually sufficient. By default, standard messages (and all event log errors) are included when Setup installs the monitor. The keywords used depends on the file being monitored... In most cases, generic keywords can be used such as "error", "failed", "insufficient", "problem" etc. To be notified of any message that contains the word "error", simply add the word "error" to the included list (without quotation marks). To be notified of any message that contains the phrase "this is an error", simply add that phrase (without quotes) to the included list. To be notified of any message that contains the phrases "this is an error" and "database", use the [And] escape sequence within the included list. In other words, you'd add "this is an error [And] database" (without quotation
7 Configuring text file monitoring To monitor the contents of records added to a text file simply add the file to the list. You can add a new file or edit an existing one by selecting the Add or Edit option from the main window. From here you can define which log file you wish to monitor and under which conditions an alert should be triggered. Refer to this log file or check as This is the unique name of the check being made. It is this name that will be displayed on reports and when alerts are generated. It is recommended that a short descriptive name be used for this value.
8 The name/path of this file is This is the fully qualified path of the file you wish to monitor or a fully qualified path & mask of file(s) you wish to monitor If you enter a fully qualified path & filename, the contents of that file will be monitored. If you enter a fully qualified path & a mask (e.g. C:\Directory\*.log), Sentry-go will automatically search for and monitor files of the given mask (e.g. all.log files). Where wildcards (mask) is entered, the monitor will periodically scan the directory for new & deleted files & update the scan accordingly. When started, the monitor will automatically search for files of the given mask. If found, they will automatically be monitored. However, any existing records will only be scanned if Scan entire file at startup is ticked. The monitor will periodically check for new files. When a new file of the given mask is detected, it will automatically be monitored. It will also be scanned from the beginning of the file regardless of the Scan entire file at startup setting. In addition to a hard-coded path such as C:\MyLogs\AppLog.log, system environment variables, as well as a number of special place-markers may also be used within this name. For example The environment variable %WINDIR% - e.g. %WINDIR%\AppLog.log $$YY to include the 2 character year $$MM to include the 2 character month $$DD to include the 2 character day $$DD-n where n is a number greater than 1. Allows you to include a date n-days in the past. The associated month and/or year are automatically adjusted as required $$DD+n where n is a number greater than 1. Allows you to include a date n-days in the future. The associated month and/or year are automatically adjusted as required $$DD[-n] to include the 2 character day. The -n will not be altered $$DD[+n] to include the 2 character day. The +n will not be altered Additionally If date variables are used, the monitor will automatically reset the date when that date changes - e.g. at midnight and continue monitoring the new file. A log file can be defined multiple times if required, in order to specify separate actions and detect different sets of keywords etc.
9 The type of this file is... Select either Text-based log file or Text-based (Unicode) log file from the list of available options. On later versions of Windows, text files may be saved in UNICODE format instead of the older ANSI standard. An example of this is the SQL Server error log. If you are unsure which version your log file is... Open it using Notepad Click File/Save As Note the encoding being suggested in the 'Save As' window. If it is not ANSI, then select Text-based (Unicode) log file here. If Text-based log file is selected for a UNICODE file, you may find alerts are not triggered as expected. Scan Entire File on Startup By default, Sentry-go will monitor files for new entries added to the file after monitoring has been started. Tick this option if you want Sentry-go to scan & alert on existing entries in the file prior to monitoring for new ones. Note that each time the monitor is restarted, the file will be scanned. This may take time to complete for large files and, in some cases, may lead to duplicate alerts being generated, especially if the monitor is restarted frequently. Scan Entire File on Truncation Sentry-go will monitor files to see whether they are truncated (shortened). This can happen, for example, if the file is replaced with a new one or older records are removed by the application writing to it. By default if this happens, the monitor searches for the new end of file and continues monitoring. For systems where files can roll-over (be replaced by new ones e.g. SQL Server), there may be times when the truncated file should be treated as an entirely new file and all records therefore scanned. To do this, tick the Scan Entire File on Truncation option. Event Type Event Source Event ID These are only appropriate for Event Log monitoring and can be ignored.
10 Keywords The monitor detects errors in Event Logs using Sentry-go's keyword detection technology. Keywords or phrases can be used either to detect an error, or to find errors that you do not wish to monitor. Both are defined at the bottom of this window. Add Keyword. Click this button to add a keyword or phrase that you wish to monitor to the list. If the keyword or phrase is found, an alert will be triggered, unless excluded keywords are also found. To record all events, enter [All Records] as your phrase. Add Exclude. Click this button to add a keyword or phrase that indicates that the message should be ignored. If an excluded keyword is found, the message is automatically ignored, regardless of other settings. Edit. Click Edit to edit an existing keyword or phrase listed. Delete. Click Delete to remove an existing keyword or phrase from the list. To Trigger an Alert... must be present. This option determines when an alert should be triggered & keyword detection is defined... o All Phrases. Select this option if all keywords listed must be present in the message in order to generate an alert. Excluded keywords do not count in this check o Any Phrase. Select this option to trigger an alert if one or more of the keywords listed are found in the message. When defining a message, there is no need to add complete error messages to this list - one or more keywords is usually sufficient. By default, standard messages (and all event log errors) are included when Setup installs the monitor. The keywords used depends on the file being monitored... In most cases, generic keywords can be used such as "error", "failed", "insufficient", "problem" etc. To be notified of any message that contains the word "error", simply add the word "error" to the included list (without quotation marks). To be notified of any message that contains the phrase "this is an error", simply add that phrase (without quotes) to the included list. To be notified of any message that contains the phrases "this is an error" and "database", use the [And] escape sequence within the included list. In other words, you'd add "this is an error [And] database" (without quotation
11 How to monitor log files When deciding how to monitor your text-based log files, you can select between the following options Configure the exact path & filename to monitor Include environment & date-based variables within the path/filename in order to monitor files that dynamically change name i.e. based on date. Include wildcards e.g. *.log within the filename. In this case, Sentry-go will automatically monitor for new files and monitor them accordingly. Considerations for file types Most log files are text based. However, on newer versions of Windows you may find the file is actually stored in UNICODE format, as opposed to the older ANSI standard. An example of this is the SQL Server error log file. Although both types will display perfectly well in Notepad, they are in fact stored differently on disk and must be accessed in the appropriate fashion. When monitoring a text-based log file, you can check the format required by Open the log file using Notepad Once loaded, click File/Save As from the menu Note the encoding being suggested within the 'Save As' window. If it shows ANSI, then you should select the log type as Text-based log file. If not (e.g. it reports UNICODE, select Text-based (Unicode) log file from the dropdown list. If you notice alerts are not being triggered when you expect them, verify the type of file being configured as described above. Considerations for other file systems In addition to monitoring changes made to text files on Windows machines, it is also possible to monitor files written to other file systems, if the file is accessible from the machine running Sentry-go. For example, using NFS to map to a Unix directory. However, in this case, you should be aware of the following... The drive mapping must be available to Sentry-go and cannot simply be mapped by Windows Explorer as this will map the drive after the Sentry-go service has been started. Always define the path/file using its full UNC name as opposed to a mapped drive e.g. \\MyServer\MyShare\MyFile.txt as opposed to X:\ MyFile.txt where X: is a mapped drive. The user configured to run the monitoring service must have permission to access the file system or remote share. By default the monitor will run under the local system user account. This will normally be fine for local file access but will not allow the monitor to access remote resources. In this case, run the Sentry-go monitoring service as a domain user.
12 Scheduling a check By default, each check is performed periodically at regular intervals throughout the day. The frequency of these checks is determined by the value specified at the bottom of the main list. However, there may be times when you wish to perform the check at a different time, maybe at a set time each day, or on certain days etc. To do this, select the Schedule tab. For more information, please see the Sentry-go Monitoring Schedule guide. Configuring an automatic response In the event an error is detected, Sentry-go can be configured to optionally respond automatically - i.e. to take action itself. To configure this, select entry from the list and click Edit. On the resulting window, select the Response tab. For more information on the options available as well as details on how to configure automatic responses, please see the Configuring Automatic Responses guide. Configuring an alert In the event an error is detected and either no automatic response is defined or the response doesn t resolve the fault, an alert will be triggered. Depending on the monitor s general settings, you can either notify one or more contacts individually, or specify the alert group you wish to inform. To configure these options, select the entry from the list and click Edit. On the resulting window, select the Alert tab. For more information, please see the Configuring Sentry-go Alerts guide. Temporarily ignoring a configured check In some cases, you may wish to exclude a check from monitoring without removing it permanently. To do this, simply remove the tick or check against the entry you wish to ignore in the main list.
13 More Information If you need more help or information on this topic Read all papers/documents on-line. Watch demonstrations & walkthrough videos on-line. Visit Contact our Support Team. Sentry-go, 3Ds (UK) Limited, East Molesey, Surrey. United Kingdom T W.
Configuring SQL Server Lock (Block) Monitoring With Sentry-go Quick & Plus! monitors
 Configuring SQL Server Lock (Block) Monitoring With Sentry-go Quick & Plus! monitors 3Ds (UK) Limited, November, 2013 http://www.sentry-go.com Be Proactive, Not Reactive! To allow for secure concurrent
Configuring SQL Server Lock (Block) Monitoring With Sentry-go Quick & Plus! monitors 3Ds (UK) Limited, November, 2013 http://www.sentry-go.com Be Proactive, Not Reactive! To allow for secure concurrent
Configuring TCP/IP Port & Firewall Monitoring With Sentry-go Quick & Plus! monitors
 Configuring TCP/IP Port & Firewall Monitoring With Sentry-go Quick & Plus! monitors 3Ds (UK) Limited, November, 2013 http://www.sentry-go.com Be Proactive, Not Reactive! TCP/IP Port Monitoring TCP/IP ports
Configuring TCP/IP Port & Firewall Monitoring With Sentry-go Quick & Plus! monitors 3Ds (UK) Limited, November, 2013 http://www.sentry-go.com Be Proactive, Not Reactive! TCP/IP Port Monitoring TCP/IP ports
Configuring FTP Availability Monitoring With Sentry-go Quick & Plus! monitors
 Configuring FTP Availability Monitoring With Sentry-go Quick & Plus! monitors 3Ds (UK) Limited, November, 2013 http://www.sentry-go.com Be Proactive, Not Reactive! Many sites and external systems transfer
Configuring FTP Availability Monitoring With Sentry-go Quick & Plus! monitors 3Ds (UK) Limited, November, 2013 http://www.sentry-go.com Be Proactive, Not Reactive! Many sites and external systems transfer
Moving the TRITON Reporting Databases
 Moving the TRITON Reporting Databases Topic 50530 Web, Data, and Email Security Versions 7.7.x, 7.8.x Updated 06-Nov-2013 If you need to move your Microsoft SQL Server database to a new location (directory,
Moving the TRITON Reporting Databases Topic 50530 Web, Data, and Email Security Versions 7.7.x, 7.8.x Updated 06-Nov-2013 If you need to move your Microsoft SQL Server database to a new location (directory,
WHAT S NEW 4.5. FileAudit VERSION. www.isdecisions.com
 WHAT S NEW FileAudit 4.5 VERSION www.isdecisions.com Table of Contents 1. FileAudit Version 4... 3 1.1. File and Folder Activity Real-Time Monitoring... 3 1.2. File and Folder Activity Alerts... 3 1.3.
WHAT S NEW FileAudit 4.5 VERSION www.isdecisions.com Table of Contents 1. FileAudit Version 4... 3 1.1. File and Folder Activity Real-Time Monitoring... 3 1.2. File and Folder Activity Alerts... 3 1.3.
Richmond SupportDesk Web Reports Module For Richmond SupportDesk v6.72. User Guide
 Richmond SupportDesk Web Reports Module For Richmond SupportDesk v6.72 User Guide Contents 1 Introduction... 4 2 Requirements... 5 3 Important Note for Customers Upgrading... 5 4 Installing the Web Reports
Richmond SupportDesk Web Reports Module For Richmond SupportDesk v6.72 User Guide Contents 1 Introduction... 4 2 Requirements... 5 3 Important Note for Customers Upgrading... 5 4 Installing the Web Reports
Windows PCs & Servers are often the life-blood of your IT investment. Monitoring them is key, especially in today s 24 hour world!
 + Welcome to The Sentry-go Monitoring System v6 Monitoring made quick & easy! Be Proactive, Not Reactive! 3Ds (UK) Limited http://www.sentry-go.com Welcome to Sentry-go Sentry-go is a quick & easy to use
+ Welcome to The Sentry-go Monitoring System v6 Monitoring made quick & easy! Be Proactive, Not Reactive! 3Ds (UK) Limited http://www.sentry-go.com Welcome to Sentry-go Sentry-go is a quick & easy to use
STATISTICA VERSION 9 STATISTICA ENTERPRISE INSTALLATION INSTRUCTIONS FOR USE WITH TERMINAL SERVER
 Notes: STATISTICA VERSION 9 STATISTICA ENTERPRISE INSTALLATION INSTRUCTIONS FOR USE WITH TERMINAL SERVER 1. These instructions focus on installation on Windows Terminal Server (WTS), but are applicable
Notes: STATISTICA VERSION 9 STATISTICA ENTERPRISE INSTALLATION INSTRUCTIONS FOR USE WITH TERMINAL SERVER 1. These instructions focus on installation on Windows Terminal Server (WTS), but are applicable
SQL Server Protection
 User Guide BackupAssist User Guides explain how to create and modify backup jobs, create backups and perform restores. These steps are explained in more detail in a guide s respective whitepaper. Whitepapers
User Guide BackupAssist User Guides explain how to create and modify backup jobs, create backups and perform restores. These steps are explained in more detail in a guide s respective whitepaper. Whitepapers
Moving the Web Security Log Database
 Moving the Web Security Log Database Topic 50530 Web Security Solutions Version 7.7.x, 7.8.x Updated 22-Oct-2013 Version 7.8 introduces support for the Web Security Log Database on Microsoft SQL Server
Moving the Web Security Log Database Topic 50530 Web Security Solutions Version 7.7.x, 7.8.x Updated 22-Oct-2013 Version 7.8 introduces support for the Web Security Log Database on Microsoft SQL Server
There are numerous ways to access monitors:
 Remote Monitors REMOTE MONITORS... 1 Overview... 1 Accessing Monitors... 1 Creating Monitors... 2 Monitor Wizard Options... 11 Editing the Monitor Configuration... 14 Status... 15 Location... 17 Alerting...
Remote Monitors REMOTE MONITORS... 1 Overview... 1 Accessing Monitors... 1 Creating Monitors... 2 Monitor Wizard Options... 11 Editing the Monitor Configuration... 14 Status... 15 Location... 17 Alerting...
Advanced Event Viewer Manual
 Advanced Event Viewer Manual Document version: 2.2944.01 Download Advanced Event Viewer at: http://www.advancedeventviewer.com Page 1 Introduction Advanced Event Viewer is an award winning application
Advanced Event Viewer Manual Document version: 2.2944.01 Download Advanced Event Viewer at: http://www.advancedeventviewer.com Page 1 Introduction Advanced Event Viewer is an award winning application
STATISTICA VERSION 10 STATISTICA ENTERPRISE SERVER INSTALLATION INSTRUCTIONS
 Notes: STATISTICA VERSION 10 STATISTICA ENTERPRISE SERVER INSTALLATION INSTRUCTIONS 1. The installation of the STATISTICA Enterprise Server entails two parts: a) a server installation, and b) workstation
Notes: STATISTICA VERSION 10 STATISTICA ENTERPRISE SERVER INSTALLATION INSTRUCTIONS 1. The installation of the STATISTICA Enterprise Server entails two parts: a) a server installation, and b) workstation
Installation Guide - Client. Rev 1.5.0
 Installation Guide - Client Rev 1.5.0 15 th September 2006 Introduction IntraNomic requires components to be installed on each PC that will use IntraNomic. These IntraNomic Client Controls provide advanced
Installation Guide - Client Rev 1.5.0 15 th September 2006 Introduction IntraNomic requires components to be installed on each PC that will use IntraNomic. These IntraNomic Client Controls provide advanced
TIGERPAW EXCHANGE INTEGRATOR SETUP GUIDE V3.6.0 August 26, 2015
 TIGERPAW EXCHANGE INTEGRATOR SETUP GUIDE V3.6.0 August 26, 2015 2201 Thurston Circle Bellevue, NE 68005 www.tigerpawsoftware.com Contents Tigerpaw Exchange Integrator Setup Guide v3.6.0... 1 Contents...
TIGERPAW EXCHANGE INTEGRATOR SETUP GUIDE V3.6.0 August 26, 2015 2201 Thurston Circle Bellevue, NE 68005 www.tigerpawsoftware.com Contents Tigerpaw Exchange Integrator Setup Guide v3.6.0... 1 Contents...
Table of Contents. Table of Contents... 2. 1 Installation overview... 3. 2 Create a Group Policy Object and Deploy SmartAgentSetup MSI package...
 1 Table of Contents Table of Contents... 2 1 Installation overview... 3 2 Create a Group Policy Object and Deploy SmartAgentSetup MSI package... 4 3 Change SmartAgentSetup Settings (Redeploy)... 11 4 Predefine
1 Table of Contents Table of Contents... 2 1 Installation overview... 3 2 Create a Group Policy Object and Deploy SmartAgentSetup MSI package... 4 3 Change SmartAgentSetup Settings (Redeploy)... 11 4 Predefine
NETWRIX EVENT LOG MANAGER
 NETWRIX EVENT LOG MANAGER ADMINISTRATOR S GUIDE Product Version: 4.0 July/2012. Legal Notice The information in this publication is furnished for information use only, and does not constitute a commitment
NETWRIX EVENT LOG MANAGER ADMINISTRATOR S GUIDE Product Version: 4.0 July/2012. Legal Notice The information in this publication is furnished for information use only, and does not constitute a commitment
HOW TO SILENTLY INSTALL CLOUD LINK REMOTELY WITHOUT SUPERVISION
 HOW TO SILENTLY INSTALL CLOUD LINK REMOTELY WITHOUT SUPERVISION Version 1.1 / Last updated November 2012 INTRODUCTION The Cloud Link for Windows client software is packaged as an MSI (Microsoft Installer)
HOW TO SILENTLY INSTALL CLOUD LINK REMOTELY WITHOUT SUPERVISION Version 1.1 / Last updated November 2012 INTRODUCTION The Cloud Link for Windows client software is packaged as an MSI (Microsoft Installer)
Mailbox control panel. User guide
 Mailbox control panel User guide Close this window Mailbox control panel user guide Mailbox control panels enable you to configure your settings for a specific mailbox with ease, with features ranging
Mailbox control panel User guide Close this window Mailbox control panel user guide Mailbox control panels enable you to configure your settings for a specific mailbox with ease, with features ranging
Published. Technical Bulletin: Use and Configuration of Quanterix Database Backup Scripts 1. PURPOSE 2. REFERENCES 3.
 Technical Bulletin: Use and Configuration of Quanterix Database Document No: Page 1 of 11 1. PURPOSE Quanterix can provide a set of scripts that can be used to perform full database backups, partial database
Technical Bulletin: Use and Configuration of Quanterix Database Document No: Page 1 of 11 1. PURPOSE Quanterix can provide a set of scripts that can be used to perform full database backups, partial database
SQL Server Protection Whitepaper
 SQL Server Protection Contents 1. Introduction... 2 Documentation... 2 Licensing... 2 The benefits of using the SQL Server Add-on... 2 Requirements... 2 2. SQL Protection overview... 3 User databases...
SQL Server Protection Contents 1. Introduction... 2 Documentation... 2 Licensing... 2 The benefits of using the SQL Server Add-on... 2 Requirements... 2 2. SQL Protection overview... 3 User databases...
Hosting Users Guide 2011
 Hosting Users Guide 2011 eofficemgr technology support for small business Celebrating a decade of providing innovative cloud computing services to small business. Table of Contents Overview... 3 Configure
Hosting Users Guide 2011 eofficemgr technology support for small business Celebrating a decade of providing innovative cloud computing services to small business. Table of Contents Overview... 3 Configure
Idera SQL Diagnostic Manager Management Pack Guide for System Center Operations Manager. Install Guide. Idera Inc., Published: April 2013
 Idera SQL Diagnostic Manager Management Pack Guide for System Center Operations Manager Install Guide Idera Inc., Published: April 2013 Contents Introduction to the Idera SQL Diagnostic Manager Management
Idera SQL Diagnostic Manager Management Pack Guide for System Center Operations Manager Install Guide Idera Inc., Published: April 2013 Contents Introduction to the Idera SQL Diagnostic Manager Management
Timed Email Organizer User s Manual
 Timed Email Organizer User s Manual Quick Start Guide... 3 Welcome... 4 Main Rules Window... 5 Status Bar... 6 Close... 6 Save As... 7 Add/Edit Rules... 7 Conditions... 9 Actions... 12 Delete Rules...
Timed Email Organizer User s Manual Quick Start Guide... 3 Welcome... 4 Main Rules Window... 5 Status Bar... 6 Close... 6 Save As... 7 Add/Edit Rules... 7 Conditions... 9 Actions... 12 Delete Rules...
NETWRIX ACCOUNT LOCKOUT EXAMINER
 NETWRIX ACCOUNT LOCKOUT EXAMINER ADMINISTRATOR S GUIDE Product Version: 4.1 July 2014. Legal Notice The information in this publication is furnished for information use only, and does not constitute a
NETWRIX ACCOUNT LOCKOUT EXAMINER ADMINISTRATOR S GUIDE Product Version: 4.1 July 2014. Legal Notice The information in this publication is furnished for information use only, and does not constitute a
Site Monitor. Version 5.3
 Site Monitor Version 5.3 1 1 Table of contents 1 Table of contents... 2 2 Installation... 3 2.1 Components... 3 2.1.1 Monitoring Service... 3 2.1.2 Desktop User Interface... 3 2.1.3 Web User Interface...
Site Monitor Version 5.3 1 1 Table of contents 1 Table of contents... 2 2 Installation... 3 2.1 Components... 3 2.1.1 Monitoring Service... 3 2.1.2 Desktop User Interface... 3 2.1.3 Web User Interface...
EVENT LOG MANAGEMENT...
 Event Log Management EVENT LOG MANAGEMENT... 1 Overview... 1 Application Event Logs... 3 Security Event Logs... 3 System Event Logs... 3 Other Event Logs... 4 Windows Update Event Logs... 6 Syslog... 6
Event Log Management EVENT LOG MANAGEMENT... 1 Overview... 1 Application Event Logs... 3 Security Event Logs... 3 System Event Logs... 3 Other Event Logs... 4 Windows Update Event Logs... 6 Syslog... 6
User Guide Online Backup
 User Guide Online Backup Table of contents Table of contents... 1 Introduction... 2 Adding the Online Backup Service to your Account... 2 Getting Started with the Online Backup Software... 4 Downloading
User Guide Online Backup Table of contents Table of contents... 1 Introduction... 2 Adding the Online Backup Service to your Account... 2 Getting Started with the Online Backup Software... 4 Downloading
Database Operations (Backup/Restore/Move/Manage) Technical Support Engineering Rosslare Security NA For more information please see www.axtraxng.
 Database Operations (Backup/Restore/Move/Manage) Technical Support Engineering Rosslare Security NA For more information please see www.axtraxng.com Database management operations may be performed to insure
Database Operations (Backup/Restore/Move/Manage) Technical Support Engineering Rosslare Security NA For more information please see www.axtraxng.com Database management operations may be performed to insure
Online Backup by Mozy User Guide
 Online Backup by Mozy User Guide Document Revision Date: April 16, 2013 Online Backup by Mozy User Guide i Contents Overview... 3 Getting Started with Mozy... 4 Using the Settings Window... 7 Understanding
Online Backup by Mozy User Guide Document Revision Date: April 16, 2013 Online Backup by Mozy User Guide i Contents Overview... 3 Getting Started with Mozy... 4 Using the Settings Window... 7 Understanding
Installation Instruction STATISTICA Enterprise Server
 Installation Instruction STATISTICA Enterprise Server Notes: ❶ The installation of STATISTICA Enterprise Server entails two parts: a) a server installation, and b) workstation installations on each of
Installation Instruction STATISTICA Enterprise Server Notes: ❶ The installation of STATISTICA Enterprise Server entails two parts: a) a server installation, and b) workstation installations on each of
Upgrade Guide BES12. Version 12.1
 Upgrade Guide BES12 Version 12.1 Published: 2015-02-25 SWD-20150413111718083 Contents Supported upgrade environments...4 Upgrading from BES12 version 12.0 to BES12 version 12.1...5 Preupgrade tasks...5
Upgrade Guide BES12 Version 12.1 Published: 2015-02-25 SWD-20150413111718083 Contents Supported upgrade environments...4 Upgrading from BES12 version 12.0 to BES12 version 12.1...5 Preupgrade tasks...5
Monitoring Replication
 Monitoring Replication Article 1130112-02 Contents Summary... 3 Monitor Replicator Page... 3 Summary... 3 Status... 3 System Health... 4 Replicator Configuration... 5 Replicator Health... 6 Local Package
Monitoring Replication Article 1130112-02 Contents Summary... 3 Monitor Replicator Page... 3 Summary... 3 Status... 3 System Health... 4 Replicator Configuration... 5 Replicator Health... 6 Local Package
RoomWizard Synchronization Software Manual Installation Instructions
 2 RoomWizard Synchronization Software Manual Installation Instructions Table of Contents Exchange Server Configuration... 4 RoomWizard Synchronization Software Installation and Configuration... 5 System
2 RoomWizard Synchronization Software Manual Installation Instructions Table of Contents Exchange Server Configuration... 4 RoomWizard Synchronization Software Installation and Configuration... 5 System
Hands-On Microsoft Windows Server 2008
 Hands-On Microsoft Windows Server 2008 Chapter 10 Managing System Reliability and Availability Using and Configuring Event Viewer Event Viewer Houses the event logs that record information about all types
Hands-On Microsoft Windows Server 2008 Chapter 10 Managing System Reliability and Availability Using and Configuring Event Viewer Event Viewer Houses the event logs that record information about all types
AppMetrics for Transactions SCOM Management Pack Users Guide
 AppMetrics for Transactions SCOM Management Pack Users Guide Introduction SCOM Overview System Center Operations Manager enables data center operations personnel to monitor state, performance, and health
AppMetrics for Transactions SCOM Management Pack Users Guide Introduction SCOM Overview System Center Operations Manager enables data center operations personnel to monitor state, performance, and health
EVENT VIEWER IN WINDOWS 7
 EVENT VIEWER IN WINDOWS 7 Event Viewer We can open Event Viewer in different ways, such as trough Computer Management and Administrative Tools. However, the easiest way is to type "eventvwr" in search
EVENT VIEWER IN WINDOWS 7 Event Viewer We can open Event Viewer in different ways, such as trough Computer Management and Administrative Tools. However, the easiest way is to type "eventvwr" in search
Insight Video Net. LLC. CMS 2.0. Quick Installation Guide
 Insight Video Net. LLC. CMS 2.0 Quick Installation Guide Table of Contents 1. CMS 2.0 Installation 1.1. Software Required 1.2. Create Default Directories 1.3. Create Upload User Account 1.4. Installing
Insight Video Net. LLC. CMS 2.0 Quick Installation Guide Table of Contents 1. CMS 2.0 Installation 1.1. Software Required 1.2. Create Default Directories 1.3. Create Upload User Account 1.4. Installing
PageR Enterprise Monitored Objects - AS/400-5
 PageR Enterprise Monitored Objects - AS/400-5 The AS/400 server is widely used by organizations around the world. It is well known for its stability and around the clock availability. PageR can help users
PageR Enterprise Monitored Objects - AS/400-5 The AS/400 server is widely used by organizations around the world. It is well known for its stability and around the clock availability. PageR can help users
Version 2.0. Installation Guide
 Version 2.0 Installation Guide Rev. D-26/02/2001 Copyright Trademarks This document and the accompanying software package are subject to international copyright laws. No part of this document may be reproduced
Version 2.0 Installation Guide Rev. D-26/02/2001 Copyright Trademarks This document and the accompanying software package are subject to international copyright laws. No part of this document may be reproduced
BillQuick Agent 2010 Getting Started Guide
 Time Billing and Project Management Software Built With Your Industry Knowledge BillQuick Agent 2010 Getting Started Guide BQE Software, Inc. 2601 Airport Drive Suite 380 Torrance CA 90505 Support: (310)
Time Billing and Project Management Software Built With Your Industry Knowledge BillQuick Agent 2010 Getting Started Guide BQE Software, Inc. 2601 Airport Drive Suite 380 Torrance CA 90505 Support: (310)
Dell Active Administrator 8.0
 What s new in Dell Active Administrator 8.0 January 2016 Dell Active Administrator 8.0 is the upcoming release of Dell Software's complete solution for managing Microsoft Active Directory security auditing,
What s new in Dell Active Administrator 8.0 January 2016 Dell Active Administrator 8.0 is the upcoming release of Dell Software's complete solution for managing Microsoft Active Directory security auditing,
Chapter 11 Managing Core Database Downloads
 Chapter 11 Managing Core Database Downloads Research Insight versions 7.7 and higher offer automated delivery of the COMPUSTAT core databases over the Internet through the Database Manager application.
Chapter 11 Managing Core Database Downloads Research Insight versions 7.7 and higher offer automated delivery of the COMPUSTAT core databases over the Internet through the Database Manager application.
KB259302 - Windows 2000 DNS Event Messages 1 Through 1614
 Page 1 of 6 Knowledge Base Windows 2000 DNS Event Messages 1 Through 1614 PSS ID Number: 259302 Article Last Modified on 10/29/2003 The information in this article applies to: Microsoft Windows 2000 Server
Page 1 of 6 Knowledge Base Windows 2000 DNS Event Messages 1 Through 1614 PSS ID Number: 259302 Article Last Modified on 10/29/2003 The information in this article applies to: Microsoft Windows 2000 Server
Support Document: Microsoft SQL Server - LiveVault 7.6X
 Contents Preparing to create a Microsoft SQL backup policy... 2 Adjusting the SQL max worker threads option... 2 Preparing for Log truncation... 3 Best Practices... 3 Microsoft SQL Server 2005, 2008, or
Contents Preparing to create a Microsoft SQL backup policy... 2 Adjusting the SQL max worker threads option... 2 Preparing for Log truncation... 3 Best Practices... 3 Microsoft SQL Server 2005, 2008, or
020112 2008 Blackbaud, Inc. This publication, or any part thereof, may not be reproduced or transmitted in any form or by any means, electronic, or
 Point of Sale Guide 020112 2008 Blackbaud, Inc. This publication, or any part thereof, may not be reproduced or transmitted in any form or by any means, electronic, or mechanical, including photocopying,
Point of Sale Guide 020112 2008 Blackbaud, Inc. This publication, or any part thereof, may not be reproduced or transmitted in any form or by any means, electronic, or mechanical, including photocopying,
ms-help://ms.technet.2005mar.1033/enu_kbntrelease/ntrelease/308406.htm
 Page 1 of 12 Knowledge Base FRS Event Log Error Codes PSS ID Number: 308406 Article Last Modified on 10/13/2004 The information in this article applies to: Microsoft Windows 2000 Server Microsoft Windows
Page 1 of 12 Knowledge Base FRS Event Log Error Codes PSS ID Number: 308406 Article Last Modified on 10/13/2004 The information in this article applies to: Microsoft Windows 2000 Server Microsoft Windows
NovaBACKUP. Storage Server. NovaStor / May 2011
 NovaBACKUP Storage Server NovaStor / May 2011 2011 NovaStor, all rights reserved. All trademarks are the property of their respective owners. Features and specifications are subject to change without notice.
NovaBACKUP Storage Server NovaStor / May 2011 2011 NovaStor, all rights reserved. All trademarks are the property of their respective owners. Features and specifications are subject to change without notice.
STATISTICA VERSION 11 CONCURRENT NETWORK LICENSE WITH BORROWING INSTALLATION INSTRUCTIONS
 data analysis data mining quality improvement web-based analytics Notes STATISTICA VERSION 11 CONCURRENT NETWORK LICENSE WITH BORROWING INSTALLATION INSTRUCTIONS 1. The installation of the Concurrent network
data analysis data mining quality improvement web-based analytics Notes STATISTICA VERSION 11 CONCURRENT NETWORK LICENSE WITH BORROWING INSTALLATION INSTRUCTIONS 1. The installation of the Concurrent network
INTEGRATION WITH THIRD PARTY SIEM SYSTEMS
 INTEGRATION WITH THIRD PARTY SIEM SYSTEMS TECHNICAL ARTICLE November 2012. Legal Notice The information in this publication is furnished for information use only, and does not constitute a commitment from
INTEGRATION WITH THIRD PARTY SIEM SYSTEMS TECHNICAL ARTICLE November 2012. Legal Notice The information in this publication is furnished for information use only, and does not constitute a commitment from
Understanding IBM Tivoli Monitoring 6.1 Agents In A Microsoft Clustered Environment 06/01/2006
 Page 1 of 17 Introduction Understanding IBM Tivoli Monitoring 6.1 Agents In A Microsoft Clustered Environment 06/01/2006 The purpose of this document is to describe the IBM Tivoli Monitoring 6.1 agents
Page 1 of 17 Introduction Understanding IBM Tivoli Monitoring 6.1 Agents In A Microsoft Clustered Environment 06/01/2006 The purpose of this document is to describe the IBM Tivoli Monitoring 6.1 agents
Sophos for Microsoft SharePoint Help
 Sophos for Microsoft SharePoint Help Product version: 2.0 Document date: March 2011 Contents 1 About Sophos for Microsoft SharePoint...3 2 Dashboard...4 3 Configuration...5 4 Reports...27 5 Search...28
Sophos for Microsoft SharePoint Help Product version: 2.0 Document date: March 2011 Contents 1 About Sophos for Microsoft SharePoint...3 2 Dashboard...4 3 Configuration...5 4 Reports...27 5 Search...28
Installation Instruction STATISTICA Enterprise Small Business
 Installation Instruction STATISTICA Enterprise Small Business Notes: ❶ The installation of STATISTICA Enterprise Small Business entails two parts: a) a server installation, and b) workstation installations
Installation Instruction STATISTICA Enterprise Small Business Notes: ❶ The installation of STATISTICA Enterprise Small Business entails two parts: a) a server installation, and b) workstation installations
Driver Updater Manual
 Driver Updater Manual Keep your drivers up-to-date! Improve your system performance and stability by keeping your drivers updated. Automatically find, update and fix the drivers on your computer and turn
Driver Updater Manual Keep your drivers up-to-date! Improve your system performance and stability by keeping your drivers updated. Automatically find, update and fix the drivers on your computer and turn
Informatica Corporation Proactive Monitoring for PowerCenter Operations Version 3.0 Release Notes May 2014
 Contents Informatica Corporation Proactive Monitoring for PowerCenter Operations Version 3.0 Release Notes May 2014 Copyright (c) 2012-2014 Informatica Corporation. All rights reserved. Installation...
Contents Informatica Corporation Proactive Monitoring for PowerCenter Operations Version 3.0 Release Notes May 2014 Copyright (c) 2012-2014 Informatica Corporation. All rights reserved. Installation...
Outlook Synchronisation guide
 Outlook Synchronisation guide Contents Introduction... 2 Installing Outlook Synchronisation Plug-in... 3 Daily Use of Outlook and webcrm... 6 Synchronising Emails... 7 Synchronising Contacts... 8 Contact
Outlook Synchronisation guide Contents Introduction... 2 Installing Outlook Synchronisation Plug-in... 3 Daily Use of Outlook and webcrm... 6 Synchronising Emails... 7 Synchronising Contacts... 8 Contact
EMC Data Domain Management Center
 EMC Data Domain Management Center Version 1.1 Initial Configuration Guide 302-000-071 REV 04 Copyright 2012-2015 EMC Corporation. All rights reserved. Published in USA. Published June, 2015 EMC believes
EMC Data Domain Management Center Version 1.1 Initial Configuration Guide 302-000-071 REV 04 Copyright 2012-2015 EMC Corporation. All rights reserved. Published in USA. Published June, 2015 EMC believes
SELF SERVICE RESET PASSWORD MANAGEMENT IMPLEMENTATION GUIDE
 SELF SERVICE RESET PASSWORD MANAGEMENT IMPLEMENTATION GUIDE Copyright 1998-2015 Tools4ever B.V. All rights reserved. No part of the contents of this user guide may be reproduced or transmitted in any form
SELF SERVICE RESET PASSWORD MANAGEMENT IMPLEMENTATION GUIDE Copyright 1998-2015 Tools4ever B.V. All rights reserved. No part of the contents of this user guide may be reproduced or transmitted in any form
Install SQL Server 2014 Express Edition
 How To Install SQL Server 2014 Express Edition Updated: 2/4/2016 2016 Shelby Systems, Inc. All Rights Reserved Other brand and product names are trademarks or registered trademarks of the respective holders.
How To Install SQL Server 2014 Express Edition Updated: 2/4/2016 2016 Shelby Systems, Inc. All Rights Reserved Other brand and product names are trademarks or registered trademarks of the respective holders.
HDA Integration Guide. Help Desk Authority 9.0
 HDA Integration Guide Help Desk Authority 9.0 2011ScriptLogic Corporation ALL RIGHTS RESERVED. ScriptLogic, the ScriptLogic logo and Point,Click,Done! are trademarks and registered trademarks of ScriptLogic
HDA Integration Guide Help Desk Authority 9.0 2011ScriptLogic Corporation ALL RIGHTS RESERVED. ScriptLogic, the ScriptLogic logo and Point,Click,Done! are trademarks and registered trademarks of ScriptLogic
+27O.557+! RM Auditor Additions - Web Monitor. Contents
 RM Auditor Additions - Web Monitor Contents RM Auditor Additions - Web Monitor... 1 Introduction... 2 Installing Web Monitor... 2 Overview... 2 Pre-requisites for installation... 2 Server installation...
RM Auditor Additions - Web Monitor Contents RM Auditor Additions - Web Monitor... 1 Introduction... 2 Installing Web Monitor... 2 Overview... 2 Pre-requisites for installation... 2 Server installation...
AXIS 70U - Using Scan-to-File
 AXIS 70U - Using Scan-to-File Introduction This document describes the Scan-to-File feature in the AXIS 70U. The step-by-step instructions describe the process of configuring the AXIS 70U and an FTP server.
AXIS 70U - Using Scan-to-File Introduction This document describes the Scan-to-File feature in the AXIS 70U. The step-by-step instructions describe the process of configuring the AXIS 70U and an FTP server.
STATISTICA VERSION 12 STATISTICA ENTERPRISE SMALL BUSINESS INSTALLATION INSTRUCTIONS
 STATISTICA VERSION 12 STATISTICA ENTERPRISE SMALL BUSINESS INSTALLATION INSTRUCTIONS Notes 1. The installation of STATISTICA Enterprise Small Business entails two parts: a) a server installation, and b)
STATISTICA VERSION 12 STATISTICA ENTERPRISE SMALL BUSINESS INSTALLATION INSTRUCTIONS Notes 1. The installation of STATISTICA Enterprise Small Business entails two parts: a) a server installation, and b)
Installation Guide. . All right reserved. For more information about Specops Inventory and other Specops products, visit www.specopssoft.
 . All right reserved. For more information about Specops Inventory and other Specops products, visit www.specopssoft.com Copyright and Trademarks Specops Inventory is a trademark owned by Specops Software.
. All right reserved. For more information about Specops Inventory and other Specops products, visit www.specopssoft.com Copyright and Trademarks Specops Inventory is a trademark owned by Specops Software.
Deploying System Center 2012 R2 Configuration Manager
 Deploying System Center 2012 R2 Configuration Manager This document is for informational purposes only. MICROSOFT MAKES NO WARRANTIES, EXPRESS, IMPLIED, OR STATUTORY, AS TO THE INFORMATION IN THIS DOCUMENT.
Deploying System Center 2012 R2 Configuration Manager This document is for informational purposes only. MICROSOFT MAKES NO WARRANTIES, EXPRESS, IMPLIED, OR STATUTORY, AS TO THE INFORMATION IN THIS DOCUMENT.
Manual Password Depot Server 8
 Manual Password Depot Server 8 Table of Contents Introduction 4 Installation and running 6 Installation as Windows service or as Windows application... 6 Control Panel... 6 Control Panel 8 Control Panel...
Manual Password Depot Server 8 Table of Contents Introduction 4 Installation and running 6 Installation as Windows service or as Windows application... 6 Control Panel... 6 Control Panel 8 Control Panel...
Snow Inventory. Installing and Evaluating
 Snow Inventory Installing and Evaluating Snow Software AB 2002 Table of Contents Introduction...3 1. Evaluate Requirements...3 2. Download Software...3 3. Obtain License Key...4 4. Install Snow Inventory
Snow Inventory Installing and Evaluating Snow Software AB 2002 Table of Contents Introduction...3 1. Evaluate Requirements...3 2. Download Software...3 3. Obtain License Key...4 4. Install Snow Inventory
1 of 10 1/31/2014 4:08 PM
 1 of 10 1/31/2014 4:08 PM copyright 2014 How to backup Microsoft SQL Server with Nordic Backup Pro Before creating a SQL backup set within Nordic Backup Pro it is first necessary to verify that the settings
1 of 10 1/31/2014 4:08 PM copyright 2014 How to backup Microsoft SQL Server with Nordic Backup Pro Before creating a SQL backup set within Nordic Backup Pro it is first necessary to verify that the settings
FTP Service Reference
 IceWarp Server FTP Service Reference Version 10 Printed on 12 August, 2009 i Contents FTP Service 1 V10 New Features... 2 FTP Access Mode... 2 FTP Synchronization... 2 FTP Service Node... 3 FTP Service
IceWarp Server FTP Service Reference Version 10 Printed on 12 August, 2009 i Contents FTP Service 1 V10 New Features... 2 FTP Access Mode... 2 FTP Synchronization... 2 FTP Service Node... 3 FTP Service
Symantec Mail Security for Domino
 Getting Started Symantec Mail Security for Domino About Symantec Mail Security for Domino Symantec Mail Security for Domino is a complete, customizable, and scalable solution that scans Lotus Notes database
Getting Started Symantec Mail Security for Domino About Symantec Mail Security for Domino Symantec Mail Security for Domino is a complete, customizable, and scalable solution that scans Lotus Notes database
Sophos for Microsoft SharePoint startup guide
 Sophos for Microsoft SharePoint startup guide Product version: 2.0 Document date: March 2011 Contents 1 About this guide...3 2 About Sophos for Microsoft SharePoint...3 3 System requirements...3 4 Planning
Sophos for Microsoft SharePoint startup guide Product version: 2.0 Document date: March 2011 Contents 1 About this guide...3 2 About Sophos for Microsoft SharePoint...3 3 System requirements...3 4 Planning
Best Practices for Trialing the Intronis Cloud Backup and Recovery Solution
 Best Practices for Trialing the Intronis Cloud Backup and Recovery Solution Intronis Cloud Backup and Recovery is a file based backup application that allows users to back up their critical data to the
Best Practices for Trialing the Intronis Cloud Backup and Recovery Solution Intronis Cloud Backup and Recovery is a file based backup application that allows users to back up their critical data to the
HYPERION SYSTEM 9 N-TIER INSTALLATION GUIDE MASTER DATA MANAGEMENT RELEASE 9.2
 HYPERION SYSTEM 9 MASTER DATA MANAGEMENT RELEASE 9.2 N-TIER INSTALLATION GUIDE P/N: DM90192000 Copyright 2005-2006 Hyperion Solutions Corporation. All rights reserved. Hyperion, the Hyperion logo, and
HYPERION SYSTEM 9 MASTER DATA MANAGEMENT RELEASE 9.2 N-TIER INSTALLATION GUIDE P/N: DM90192000 Copyright 2005-2006 Hyperion Solutions Corporation. All rights reserved. Hyperion, the Hyperion logo, and
PCRecruiter Resume Inhaler
 PCRecruiter Resume Inhaler The PCRecruiter Resume Inhaler is a stand-alone application that can be pointed to a folder and/or to an email inbox containing resumes, and will automatically extract contact
PCRecruiter Resume Inhaler The PCRecruiter Resume Inhaler is a stand-alone application that can be pointed to a folder and/or to an email inbox containing resumes, and will automatically extract contact
Database Maintenance Guide
 Database Maintenance Guide Medtech Evolution - Document Version 5 Last Modified on: February 26th 2015 (February 2015) This documentation contains important information for all Medtech Evolution users
Database Maintenance Guide Medtech Evolution - Document Version 5 Last Modified on: February 26th 2015 (February 2015) This documentation contains important information for all Medtech Evolution users
AV Management Dashboard
 LabTech AV Management Dashboard AV MANAGEMENT DASHBOARD... 1 Overview... 1 Requirements... 1 Dashboard Overview... 2 Clients/Groups... 2 Offline AV Agents... 3 Threats... 3 AV Product... 4 Sync Agent Data
LabTech AV Management Dashboard AV MANAGEMENT DASHBOARD... 1 Overview... 1 Requirements... 1 Dashboard Overview... 2 Clients/Groups... 2 Offline AV Agents... 3 Threats... 3 AV Product... 4 Sync Agent Data
INITIAL SYNCHRONIZATION...
 Contents INTRODUCTION... 1 DATA SYNCHRONIZATION... 2 SYNCHRONIZATION RULES... 2 SYNC TOOL... 4 BILLQUICK ONLINE SYNC TOOL... 4 Synchronization Options... 4 INITIAL SYNCHRONIZATION... 11 EXISTING BILLQUICK-NEW
Contents INTRODUCTION... 1 DATA SYNCHRONIZATION... 2 SYNCHRONIZATION RULES... 2 SYNC TOOL... 4 BILLQUICK ONLINE SYNC TOOL... 4 Synchronization Options... 4 INITIAL SYNCHRONIZATION... 11 EXISTING BILLQUICK-NEW
SysPatrol - Server Security Monitor
 SysPatrol Server Security Monitor User Manual Version 2.2 Sep 2013 www.flexense.com www.syspatrol.com 1 Product Overview SysPatrol is a server security monitoring solution allowing one to monitor one or
SysPatrol Server Security Monitor User Manual Version 2.2 Sep 2013 www.flexense.com www.syspatrol.com 1 Product Overview SysPatrol is a server security monitoring solution allowing one to monitor one or
Integrating LANGuardian with Active Directory
 Integrating LANGuardian with Active Directory 01 February 2012 This document describes how to integrate LANGuardian with Microsoft Windows Server and Active Directory. Overview With the optional Identity
Integrating LANGuardian with Active Directory 01 February 2012 This document describes how to integrate LANGuardian with Microsoft Windows Server and Active Directory. Overview With the optional Identity
Kaseya 2. Quick Start Guide. for VSA 6.1
 Kaseya 2 Monitoring Configuration Quick Start Guide for VSA 6.1 January 17, 2011 About Kaseya Kaseya is a global provider of IT automation software for IT Solution Providers and Public and Private Sector
Kaseya 2 Monitoring Configuration Quick Start Guide for VSA 6.1 January 17, 2011 About Kaseya Kaseya is a global provider of IT automation software for IT Solution Providers and Public and Private Sector
User Guide to the Snare Agent Management Console in Snare Server v7.0
 User Guide to the Snare Agent Management Console in Snare Server v7.0 Intersect Alliance International Pty Ltd. All rights reserved worldwide. Intersect Alliance Pty Ltd shall not be liable for errors
User Guide to the Snare Agent Management Console in Snare Server v7.0 Intersect Alliance International Pty Ltd. All rights reserved worldwide. Intersect Alliance Pty Ltd shall not be liable for errors
Fax and SMS Quickguide
 INTRODUCTION U2 Fax and SMS allow faxes and SMS to be sent directly from a user s workstation via the Internet using U2 Webservices. This improves staff efficiency by removing the need to physically fax
INTRODUCTION U2 Fax and SMS allow faxes and SMS to be sent directly from a user s workstation via the Internet using U2 Webservices. This improves staff efficiency by removing the need to physically fax
Monitoring Windows Event Logs
 Monitoring Windows Event Logs Monitoring Windows Event Logs Using OpManager The Windows event logs are files serving as a placeholder of all occurrences on a Windows machine. This includes logs on specific
Monitoring Windows Event Logs Monitoring Windows Event Logs Using OpManager The Windows event logs are files serving as a placeholder of all occurrences on a Windows machine. This includes logs on specific
Symantec Hosted Mail Security. Console and Spam Quarantine User Guide
 Symantec Hosted Mail Security Console and Spam Quarantine User Guide Symantec Hosted Mail Security Console and Spam Quarantine User Guide The software described in this book is furnished under a license
Symantec Hosted Mail Security Console and Spam Quarantine User Guide Symantec Hosted Mail Security Console and Spam Quarantine User Guide The software described in this book is furnished under a license
How To Monitor A Log File On Kserver On A Linux Computer Or Macintosh (Amd64) On A Macintosh 2.5 (Amd32) On An Amd64 (Amd86) On Your Computer Or Your Macintosh 3.5
 Configuring Log Parsers Step-by-Step Quick Start Guide May 15, 2008 About Kaseya Kaseya is a global provider of IT automation software for IT Solution Providers and Public and Private Sector IT organizations.
Configuring Log Parsers Step-by-Step Quick Start Guide May 15, 2008 About Kaseya Kaseya is a global provider of IT automation software for IT Solution Providers and Public and Private Sector IT organizations.
How to Configure Microsoft System Operation Manager to Monitor Active Directory, Group Policy and Exchange Changes Using NetWrix Active Directory
 How to Configure Microsoft System Operation Manager to Monitor Active Directory, Group Policy and Exchange Changes Using NetWrix Active Directory Change Reporter Table of Contents General Information...
How to Configure Microsoft System Operation Manager to Monitor Active Directory, Group Policy and Exchange Changes Using NetWrix Active Directory Change Reporter Table of Contents General Information...
TECHNICAL REFERENCE GUIDE
 TECHNICAL REFERENCE GUIDE SOURCE TARGET Kerio Microsoft Exchange/Outlook (PST) (versions 2010, 2007) Copyright 2014 by Transend Corporation EXECUTIVE SUMMARY This White Paper provides detailed information
TECHNICAL REFERENCE GUIDE SOURCE TARGET Kerio Microsoft Exchange/Outlook (PST) (versions 2010, 2007) Copyright 2014 by Transend Corporation EXECUTIVE SUMMARY This White Paper provides detailed information
Pharos Uniprint 8.4. Maintenance Guide. Document Version: UP84-Maintenance-1.0. Distribution Date: July 2013
 Pharos Uniprint 8.4 Maintenance Guide Document Version: UP84-Maintenance-1.0 Distribution Date: July 2013 Pharos Systems International Suite 310, 80 Linden Oaks Rochester, New York 14625 Phone: 1-585-939-7000
Pharos Uniprint 8.4 Maintenance Guide Document Version: UP84-Maintenance-1.0 Distribution Date: July 2013 Pharos Systems International Suite 310, 80 Linden Oaks Rochester, New York 14625 Phone: 1-585-939-7000
WordPress File Monitor Plus Plugin Configuration
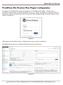 WordPress File Monitor Plus Plugin Configuration Open Source Varsity To configure the WordPress file monitor plus plugin on your WordPress driven Blog / website, login to WordPress as administrator, by
WordPress File Monitor Plus Plugin Configuration Open Source Varsity To configure the WordPress file monitor plus plugin on your WordPress driven Blog / website, login to WordPress as administrator, by
Implementing Endpoint Protection in System Center 2012 R2 Configuration Manager
 Implementing Endpoint Protection in System Center 2012 R2 Configuration Manager Implementing Endpoint Protection in System Center 2012 R2 Configuration Manager This document is for informational purposes
Implementing Endpoint Protection in System Center 2012 R2 Configuration Manager Implementing Endpoint Protection in System Center 2012 R2 Configuration Manager This document is for informational purposes
Barracuda Spam Firewall User s Guide
 Barracuda Spam Firewall User s Guide 1 Copyright Copyright 2005, Barracuda Networks www.barracudanetworks.com v3.2.22 All rights reserved. Use of this product and this manual is subject to license. Information
Barracuda Spam Firewall User s Guide 1 Copyright Copyright 2005, Barracuda Networks www.barracudanetworks.com v3.2.22 All rights reserved. Use of this product and this manual is subject to license. Information
The Welcome screen displays each time you log on to PaymentNet; it serves as your starting point or home screen.
 PaymentNet Cardholder Quick Reference Card Corporate Card ffwelcome to PaymentNet The Welcome screen displays each time you log on to PaymentNet; it serves as your starting point or home screen. PaymentNet
PaymentNet Cardholder Quick Reference Card Corporate Card ffwelcome to PaymentNet The Welcome screen displays each time you log on to PaymentNet; it serves as your starting point or home screen. PaymentNet
Server Manager Performance Monitor. Server Manager Diagnostics Page. . Information. . Audit Success. . Audit Failure
 Server Manager Diagnostics Page 653. Information. Audit Success. Audit Failure The view shows the total number of events in the last hour, 24 hours, 7 days, and the total. Each of these nodes can be expanded
Server Manager Diagnostics Page 653. Information. Audit Success. Audit Failure The view shows the total number of events in the last hour, 24 hours, 7 days, and the total. Each of these nodes can be expanded
Server & Workstation Installation of Client Profiles for Windows
 C ase Manag e m e n t by C l i e n t P rofiles Server & Workstation Installation of Client Profiles for Windows T E C H N O L O G Y F O R T H E B U S I N E S S O F L A W General Notes to Prepare for Installing
C ase Manag e m e n t by C l i e n t P rofiles Server & Workstation Installation of Client Profiles for Windows T E C H N O L O G Y F O R T H E B U S I N E S S O F L A W General Notes to Prepare for Installing
GETTING STARTED GUIDE. FileAudit VERSION. www.isdecisions.com
 GETTING STARTED GUIDE FileAudit 5 VERSION www.isdecisions.com Introduction FileAudit monitors access or access attempts to sensitive files and folders on Microsoft Windows servers. FileAudit allows you
GETTING STARTED GUIDE FileAudit 5 VERSION www.isdecisions.com Introduction FileAudit monitors access or access attempts to sensitive files and folders on Microsoft Windows servers. FileAudit allows you
Integrating with BarTender Integration Builder
 Integrating with BarTender Integration Builder WHITE PAPER Contents Overview 3 Understanding BarTender's Native Integration Platform 4 Integration Builder 4 Administration Console 5 BarTender Integration
Integrating with BarTender Integration Builder WHITE PAPER Contents Overview 3 Understanding BarTender's Native Integration Platform 4 Integration Builder 4 Administration Console 5 BarTender Integration
How To Use The Mail Control Console On A Pc Or Macbook 2.5.3 (For A Macbook)
 MX Control Console & Spam Quarantine Report User Guide Product Version: 2.5 Release Date: Document Version: ed_eug_2.5.3_gr Copyright 2004 MX Logic, Inc. RESTRICTION ON USE, PUBLICATION, OR DISCLOSURE
MX Control Console & Spam Quarantine Report User Guide Product Version: 2.5 Release Date: Document Version: ed_eug_2.5.3_gr Copyright 2004 MX Logic, Inc. RESTRICTION ON USE, PUBLICATION, OR DISCLOSURE
HELP DESK MANUAL INSTALLATION GUIDE
 Help Desk 6.5 Manual Installation Guide HELP DESK MANUAL INSTALLATION GUIDE Version 6.5 MS SQL (SQL Server), My SQL, and MS Access Help Desk 6.5 Page 1 Valid as of: 1/15/2008 Help Desk 6.5 Manual Installation
Help Desk 6.5 Manual Installation Guide HELP DESK MANUAL INSTALLATION GUIDE Version 6.5 MS SQL (SQL Server), My SQL, and MS Access Help Desk 6.5 Page 1 Valid as of: 1/15/2008 Help Desk 6.5 Manual Installation
Tracking Network Changes Using Change Audit
 CHAPTER 14 Change Audit tracks and reports changes made in the network. Change Audit allows other RME applications to log change information to a central repository. Device Configuration, Inventory, and
CHAPTER 14 Change Audit tracks and reports changes made in the network. Change Audit allows other RME applications to log change information to a central repository. Device Configuration, Inventory, and
