VAULTIVE & MICROSOFT: COMPLEMENTARY ENCRYPTION SOLUTIONS. White Paper
|
|
|
- Amberlynn Collins
- 8 years ago
- Views:
Transcription
1 COMPLEMENTARY ENCRYPTION SOLUTIONS White Paper
2 Table of Contents Section I: Vaultive & Microsoft: Complementary Encryption Solutions... 2 Section II: Vaultive is a Microsoft ISV Partner... Appendix A: S/MIME Message Encryption a Point-to-Point Solution... Appendix B: Office 365 Message Encryption Appendix C: Exchange Information Rights Management (IRM)
3 Vaultive & Microsoft: Complementary Encryption Solutions Leveraging the cloud for requires businesses take specific action to meet security, fiduciary, and compliance requirements. Vaultive is the only Microsoft ISV partner providing a customer controlled encryption solution across the entire message lifecycle, complimenting Microsoft s encryption. Control Your Data in Office 365 with Vaultive Vaultive Encrypts Data Across its Entire Lifecycle data exists in three states; at rest, in transit and in use, and must be encrypted in all three to ensure control. Vaultive Encrypted Data Can be Searched and Sorted server-side operations (such as search, sort, index, etc.) are performed on the encrypted data without ever decrypting the data. If data must be decrypted for server side operations to work, then the data is exposed and vulnerable. Vaultive Supports Native Exchange Functionality at the Pace of Change Vaultive fully supports native Office 365 services including e-discovery, DLP, archiving and others while the data remains encrypted. In addition, Vaultive includes detailed logging and reporting. You Own, Manage and Control your Encryption Keys according to cloud security best practices, encryption keys should be created, managed and controlled by the customer and not the cloud service provider (if encryption keys are accessible to anyone outside of the organization, it is giving up a crucial element of security and control). Microsoft Encryption Solutions: Protected Delivery of Specific Messages Based on Decisions Made by Individual End-Users S/MIME Individual users determine which messages should be encrypted as they are sent, assuring pointto-point delivery to specific people inside or outside of the organization. Messages are encrypted and only sender and recipient have access to the keys to decrypt the data. Office 365 Message Encryption Sends a clear text with the encrypted message included as an attachment. Recipients must log on to the sender s server using a compatible web browser, to read the . Outgoing messages are encrypted once they leave the Exchange server, but are stored on the Exchange server in the clear. IRM Individual users dictate (but cannot enforce) recipient permission for messages for actions such as replying, replying to all, forwarding, extracting information, saving, or printing. Important Note: When utilizing Microsoft encryption technologies; the data must be decrypted in order to search, sort, index or perform other server-side operations. The data is therefore sitting in the clear while server-side operations are performed. Encryption of Data in its Entirety every single in the inbox, outbox, sent and deleted folders is encrypted as well as message subjects, attachments, tasks, calendar items, invitation messages, folders and more. No End-User Actions or End-Point Software encryption must be applied automatically without requiring end-user action. Otherwise, it is subject to human error and guaranteed to fail. Vaultive does not require any end point software (agent, plug-in, or client application). 3
4 The following table summarizes Vaultive s feature support in direct comparison with Microsoft s various solutions. Feature Office 365 Message Encryption Exchange IRM S/MIME Vaultive Design Principles End user organization controls the keys Server-side operations (search, sort, index, and others) are performed on encrypted data Central key management Transparent to end-users Support for DLP, e-discovery and archiving on encrypted data Unified protection across multiple cloud services Encryption All messages are encrypted Inbound messages are encrypted Messages sent to only internal recipients are encrypted Messages sent to only external recipients are encrypted Messages sent to both internal and external recipients are encrypted 1 Message subjects encrypted Calendar items and invite messages encrypted Tasks and notes encrypted Items are encrypted before reaching the server 2 Messages to distribution lists from POP/IMAP/Mac Mail/Android encrypted Preview of encrypted messages 1 Unless the external recipient has S/MIME set up and has forwarded its certificate to the internal sender. 2 Unless the message is sent from Outlook. 4
5 Feature Office 365 Message Encryption Exchange IRM S/MIME Vaultive Client Support (both sending and receiving messages) Outlook OWA (IE) OWA (all browsers) Mobile OWA Mac Outlook Mac Mail Android iphone Other Mobiles (ActiveSync) POP3, IMAP 3 Key Management Keys reside on-premises Tenant organization retains exclusive access to encryption keys 4 Key recovery (integrated backup) Office 365 Features Server searches and sort DLP and policy violation scanning e-discovery Journaling Archiving According to the Encryption in Exchange presentation given at Microsoft Exchange Conference (MEC) 2014 in Austin, Texas, Microsoft does not recommend combining the various Microsoft encryption solutions. 3 Requires a browser. 4 Third party Certificate Authorities could keep generated private keys. 5
6 Vaultive is a Microsoft ISV Partner Vaultive provides a comprehensive encryption solution for Microsoft Office 365, Yammer, and Dynamics, as well as for other cloud applications. Vaultive persistently encrypts an organization s data before it leaves the trusted network, while the organization s IT retains the keys. Vaultive s encryption software protects data throughout its entire lifecycle: in transit, at rest and in use. Vaultive s persistent encryption maintains content characteristics allowing server-side operations including search, sort and index on encrypted data, and is completely transparent to the end user. How Vaultive Works Vaultive operates as a transparent network-level proxy, deployed at an organization s perimeter network, integrating with Microsoft Office 365 as well as other cloud applications. Data is persistently encrypted before it leaves the organization s trusted network and remains encrypted until it reaches its intended destination. Central Key Management via Robust Management Console The Vaultive platform provides encryption combined with central key management. The data is encrypted prior to leaving the organization so that neither the CSP nor Vaultive ever has access to your data in clear text. The data owner maintains direct control of their encryption keys and secures the keys with their own controls in place. No one can access the keys, or the data, without explicit consent of the organization. 6
7 Appendix A S/MIME Message Encryption a Point-to-Point Solution Microsoft s S/MIME message encryption provides encryption of messages in transit, as they travel between the sender and the intended recipient. Once encryption keys are exchanged, messages are encrypted prior to being sent, and then decrypted after download by the intended recipient. In order to utilize S/MIME message encryption, both the sender and recipient must have S/MIME deployed and the sender must have the recipient s public key, or certificate, on the corresponding client from which the is sent. How S/MIME Works S/MIME requires two separate but related keys a public key and a private key. A unique public key is distributed to those sending encrypted s, while the private key is maintained by the recipient. The public key is utilized for encrypting the before sending it to the recipient, and the recipient can only decrypt the incoming using the private key. The following table shows how certificates are acquired for each client and the associated limitations of each method. Client Certificate Result Outlook Outlook Web Application (OWA) on Internet Explorer (IE) ActiveSync Mac OS X, Exchange Web Services (EWS) Automatically accesses all certificates from Active Directory (AD). Automatically accesses all certificates from AD. Obtains all certificates from the Exchange Server. Obtains certificates from the AD. Outlook can access certificates for most internal recipients but very limited certificates for external recipients. OWA can only access certificates for internal recipients. S/MIME is not supported on Android 5. GAL is an internal list, Mac s can only acquire certificates for internal recipients. Because of the nature of public-key cryptography, S/MIME has two limitations which can inhibit usage: s sent to external recipients are generally not encrypted. In order for an sent externally to be encrypted, the recipient must provide the sender with his public key by sending an signed with the appropriate certificate. Incoming s are not encrypted unless they are sent from a sender that is both using S/MIME and has the recipient s public key. 5 S/MIME Limitations In addition to S/MIME s constraints encrypting messages to external recipients, the following limitations also apply: S/MIME does not encrypt subjects. The following example highlights the importance of encrypting subjects in addition to messages: Subject: Request 20% Discount for ABC Bank proposal to beat Competitor N. Messages are only encrypted when the sender has all recipient certificates. If one certificate is missing, the will not be encrypted when sent to any of the recipients, nor will it be encrypted in the sender s Sent Items folder. 7
8 Calendars, Invitations, tasks and other Exchange items are not encrypted. If using Post Office Protocol (POP3) or Internet Message Access Protocol (IMAP), distribution lists are not supported and s sent to distribution lists are not encrypted. Server-side operations cannot be performed on the encrypted data; therefore search, sort, indexing, DLP scanning, and e-discovery are not supported. Plug-ins are required in order for OWA to use S/ MIME in IE. In order to support S/MIME on any other browser, the private key must be installed on each device where OWA is utilized with S/MIME, and the device must be joined to the AD domain. Message previews are not supported. S/MIME Key Management S/MIME does not provide out-of-the box centralized key management for private or public keys. End-users must maintain both a certificate as well as a matching private key; and it is critical that the keys are properly stored and protected. Every user maintains the certificate and key without any standard key management procedure. It is recommended that administrators define and implement processes to securely back up user private keys, either by company policy or by setting up a key escrow and backup service. Serious security risks are introduced end-users can easily generate their own keys using a third party service, without approval or knowledge of the administrator. The third party service has access to the private key and the enterprise lacks oversight and supervision, creating a significant security gap. When using S/MIME in OWA, preview and the conversation view are not supported; and must be opened in a separate window. S/MIME Support Summary Encryption Feature S/MIME Encryption Feature Internal messages encrypted 6 Outbound messages encrypted 7 Outgoing messages encrypted before arriving at the Exchange server Incoming messages encrypted Subjects encrypted Calendar items and invites encrypted Tasks encrypted Encrypt messages sent to both S/MIME encrypted users and non-s/mime Users 8
9 Encryption Feature S/MIME Client Support Mac/OSX Support Android Support IE browser support 8 Other browser support Distribution lists supported from POP3, IMAP and Mac clients Key Management Keys cannot be accessed by Exchange Out of the box support for private key backups Centralized key management Office 365 Feature Support Server-side operations such as search and sort Message Previews e-discovery 9 support Scanning messages for policy violations DLP support Message archiving support 6 Internal messages are encrypted as long as no external recipients without available certificates are included. 7 External messages are not encrypted unless the recipient has a certificate and s it to the sender. 8 In order to support IE, each computer using S/MIME with OWA must be joined to an AD domain, and must have the user s private key installed
10 Appendix B Office 365 Message Encryption Office 365 Message Encryption, formerly called Exchange Hosted Encryption (EHE), is used for securing outbound s based on administrator-defined policy. Recipients can use OWA and recipient identities are managed as Microsoft Online Services (MSOL) accounts, requiring users to maintain an MSOL account. How Office 365 Message Encryption Works Administrators set policy-based rules and once implemented, internal users can send and receive encrypted directly from their desktops. This service sends a clear text with the encrypted message included as an attachment. Using a web browser compatible with Office 365 Message Encryption, recipients must log in to the sender s server and securely read the in its original form. Outgoing messages are encrypted once they leave the Exchange server. However, they are stored on the Exchange server in the clear. Office 365 Message Encryption Limitations While Office 365 Message Encryption is a partial solution for security, governance and compliance, it falls short in the following areas: Does not ensure all outgoing s are persistently encrypted. Does not encrypt incoming messages. Does not encrypt internal messages. Does not encrypt subjects. The following example highlights the importance of encrypting subjects in addition to messages: Subject: Request 20% Discount for ABC Bank proposal to beat Competitor N. s are not encrypted while stored in the Exchange server transport. Decrypts messages for server-side operations such as search, sort and indexing. Office 365 Message Encryption Key Management Encryption key management remains a critical aspect of cloud encryption. Whoever owns and maintains the encryption keys controls access to the data. If the cloud service provider manages the keys on behalf of the customer whether in memory or in an HSM they can access the data, and are obligated to share the data with government officials if presented with a subpoena without notifying the tenant organization. Unique Office 365 Message Encryption keys are generated for each encrypted . Keys are stored in the Office 365 data center, where Microsoft has access to the keys. Keys can be accessed from an Office 365 MSOL account using a password. Office 365 Message Encryption Support Summary The following table summarizes Office 365 Message Encryption capabilities. Is not transparent to users and administrators. Encryption Feature Office 365 Encryption Encryption Internal messages encrypted Outgoing messages encrypted Incoming messages encrypted 10
11 subjects encrypted All s consistently encrypted Calendar items and invites encrypted Tasks encrypted s encrypted while stored in the Exchange server transport Client Support Mac/OSX Support Android Support Browser Support Distribution lists supported from POP3 and IMAP clients Key Management Keys are maintained by the end-user Office 365 Feature Support Server-side operations such as search and sort on encrypted data 10 Recipient can access their seamlessly through their inbox Recipients must maintain an MSOL account Message Previews e-discovery support on encrypted data 12 Scanning encrypted messages for policy violations 13 DLP support for encrypted messages 14 Message archiving support for encrypted messages In order to provide server-side operations including search and sort, Microsoft decrypts your data and processes it in the clear
12 Appendix C Exchange Information Rights Management (IRM) IRM, built on Microsoft AD Rights Management Service (RMS), outlines content access control based on policy. The policy can be defined per message or document, and permissions are granularly defined including reading, copying and pasting, editing, or printing content. How IRM Works IRM utilizes public-key cryptography public and private keys. When IRM is applied to an message, once the item is in the Exchange system a key is generated per item to maintain restrictions and access associated with the content. The per-item key is encrypted using the RMS public key. When the item is sent, it is accompanied by a license specifying the restrictions and limitations in accessing the content. The recipient s client software must contact the RMS server in order to decrypt the message, and should respect (but cannot enforce) the attached RMS license. IRM Limitations IRM defines and provides notification of specific corporate polices for a subset of data and transfers. However, IRM is not intended for use as a security tool and is limited in the following areas: subjects are not encrypted. The following example highlights the importance of encrypting subjects in addition to messages: Subject: Request 20% Discount for ABC Bank proposal to beat Competitor N Not encrypted: Calendars, Invitations, tasks and other Exchange items. Internal messages are encrypted only after they arrive at the Exchange server unless sent from Outlook. Messages are only encrypted when sent internally. If a single recipient is external, the will not be encrypted when sent to any of the recipients, nor will it be encrypted in the sender s Sent Items folder. The Exchange server has access to the encryption keys and decrypts IRM messages when performing the following: When indexing messages for server searches DLP scanning and Transport Rule evaluations Journaling OWA views ActiveSync downloads OWA indexing The Exchange server provides bulk decryption of messages; unacceptable for many security-aware or regulated organizations. Administrators must configure a highly-available AD RMS infrastructure in order to maintain functionality. Message previews are not supported. In particular, OWA short preview and conversation view is blank. IRM Key Management Individual users are provided with private keys for decryption based on their AD identity. Public keys are generated and encrypted per message and accompany the message when sent. The AD RMS private key is either stored in an on premise RMS server, requiring a solid backup facility; or on an Office 365 RMS server with on premise hardware security module (HSM). Although the keys are stored on premises, the Exchange server constantly accesses the keys and decrypts the content to enable ActiveSync, OWA, Journaling, indexing and transport scanning. IRM Support Summary The following table summarizes IRM capabilities. Only Microsoft desktop clients, mobiles and OWA support IRM. Mac mail, POP3, IMAP, Linux and Thunderbird are not supported. 12
13 Encryption Feature IRM Encryption Internal messages encrypted once they arrive at the Exchange server Subjects encrypted Outgoing messages encrypted at the sender's client Incoming messages encrypted Calendar items encrypted Tasks encrypted Encryption achieved seamlessly Client Support Mac/OSX Support Android Support POP, IMAP Key Management Tenant organization retains exclusive access to encryption keys Office 365 Feature Support Server-side operations such as search and sort on encrypted data 16 Message Previews e-discovery support on encrypted data 17 DLP support for encrypted messages 18 Message archiving support for encrypted messages In order to provide server-side operations including search and sort, Microsoft decrypts your data and processes it in the clear
FREQUENTLY ASKED QUESTIONS (FAQ)
 General Questions Q1: What is the Vaultive platform and what functionality does it deliver? Vaultive is an Enterprise grade encryption platform that is scalable, redundant and built for performance. Vaultive
General Questions Q1: What is the Vaultive platform and what functionality does it deliver? Vaultive is an Enterprise grade encryption platform that is scalable, redundant and built for performance. Vaultive
Mimecast Large File Send
 DATASHEET Mimecast Large File Send For sending large files, lets go back to email Mimecast Large File Send simplifies large file sharing for users by removing the complexity and frustration associated
DATASHEET Mimecast Large File Send For sending large files, lets go back to email Mimecast Large File Send simplifies large file sharing for users by removing the complexity and frustration associated
SonaVault Email Archiving Software
 SonaVault Email Archiving Software Sonasoft specifically architected it email archiving solution, SonaVault, for small and medium-sized enterprises (SME). SonaVault Email Archiving Software is a stand-alone
SonaVault Email Archiving Software Sonasoft specifically architected it email archiving solution, SonaVault, for small and medium-sized enterprises (SME). SonaVault Email Archiving Software is a stand-alone
DJIGZO EMAIL ENCRYPTION. Djigzo white paper
 DJIGZO EMAIL ENCRYPTION Djigzo white paper Copyright 2009-2011, djigzo.com. Introduction Most email is sent as plain text. This means that anyone who can intercept email messages, either in transit or
DJIGZO EMAIL ENCRYPTION Djigzo white paper Copyright 2009-2011, djigzo.com. Introduction Most email is sent as plain text. This means that anyone who can intercept email messages, either in transit or
5/20/2013. The primary design goal was for simplicity of scale, hardware utilization, and failure isolation. Microsoft Exchange Team
 Additions and Subtractions The primary design goal was for simplicity of scale, hardware utilization, and failure isolation. Microsoft Exchange Team Exchange Version Exchange Server 2003 and earlier versions
Additions and Subtractions The primary design goal was for simplicity of scale, hardware utilization, and failure isolation. Microsoft Exchange Team Exchange Version Exchange Server 2003 and earlier versions
MICROSOFT EXCHANGE, OFFERED BY INTERCALL
 MICROSOFT EXCHANGE, OFFERED BY INTERCALL Comparison Sheet The table below compares in-product or service feature availability between Microsoft 2013 on-premises and Online within. Planning and Deployment
MICROSOFT EXCHANGE, OFFERED BY INTERCALL Comparison Sheet The table below compares in-product or service feature availability between Microsoft 2013 on-premises and Online within. Planning and Deployment
CIPHERMAIL EMAIL ENCRYPTION. CipherMail white paper
 CIPHERMAIL EMAIL ENCRYPTION CipherMail white paper Copyright 2009-2014, ciphermail.com. Introduction Most email is sent as plain text. This means that anyone who can intercept email messages, either in
CIPHERMAIL EMAIL ENCRYPTION CipherMail white paper Copyright 2009-2014, ciphermail.com. Introduction Most email is sent as plain text. This means that anyone who can intercept email messages, either in
The GlobalCerts TM SecureMail Gateway TM
 Glob@lCerts PRODUCT OVERVIEW: The GlobalCerts TM SecureMail Gateway TM Automatic encryption and decryption is unique to the SecureMail Gateway. The GlobalCerts SecureMail Gateway is based on a network
Glob@lCerts PRODUCT OVERVIEW: The GlobalCerts TM SecureMail Gateway TM Automatic encryption and decryption is unique to the SecureMail Gateway. The GlobalCerts SecureMail Gateway is based on a network
Djigzo email encryption. Djigzo white paper
 Djigzo email encryption Djigzo white paper Copyright 2009-2011, djigzo.com. Introduction Most email is sent as plain text. This means that anyone who can intercept email messages, either in transit or
Djigzo email encryption Djigzo white paper Copyright 2009-2011, djigzo.com. Introduction Most email is sent as plain text. This means that anyone who can intercept email messages, either in transit or
Quality is Advantage
 Quality is Advantage Microsoft Exchange Server 2013 Configuring Course duration: 32 academic hours Exam Code: 70-662 This course is designed for novice IT specialists, who wish to master maintenance and
Quality is Advantage Microsoft Exchange Server 2013 Configuring Course duration: 32 academic hours Exam Code: 70-662 This course is designed for novice IT specialists, who wish to master maintenance and
Outlook Express POP Instructions - Bloomsburg University Students
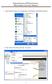 1. Open Outlook Express by clicking Start, All Programs, and Outlook Express. 2. Click on the Tools menu and click Accounts. 1 3. Click on Add Mail 4. Enter your name and click Next. 2 5. Enter your full
1. Open Outlook Express by clicking Start, All Programs, and Outlook Express. 2. Click on the Tools menu and click Accounts. 1 3. Click on Add Mail 4. Enter your name and click Next. 2 5. Enter your full
A NATURAL FIT. Microsoft Office 365 TM and Zix TM Email Encryption. By ZixCorp www.zixcorp.com
 Microsoft Office 365 TM and Zix TM Email Encryption A NATURAL FIT By ZixCorp www.zixcorp.com Microsoft Office 365 TM and Zix TM Email Encryption Page 1 INTRODUCTION IT managers and decision makers are
Microsoft Office 365 TM and Zix TM Email Encryption A NATURAL FIT By ZixCorp www.zixcorp.com Microsoft Office 365 TM and Zix TM Email Encryption Page 1 INTRODUCTION IT managers and decision makers are
MS 10135 Configuring, Managing and Troubleshooting Microsoft Exchange Server 2010 Service Pack 2
 MS 10135 Configuring, Managing and Troubleshooting Microsoft Exchange Server 2010 Service Pack 2 P a g e 1 of 10 About this Course This course will provide you with the knowledge and skills to configure
MS 10135 Configuring, Managing and Troubleshooting Microsoft Exchange Server 2010 Service Pack 2 P a g e 1 of 10 About this Course This course will provide you with the knowledge and skills to configure
Symantec Encryption Solutions for Email, Powered by PGP Technology
 Symantec Encryption Solutions for Email, Powered by PGP Technology Data Sheet: Encryption The Problem with Email Are you worried that users are emailing sensitive information openly? According to Osterman
Symantec Encryption Solutions for Email, Powered by PGP Technology Data Sheet: Encryption The Problem with Email Are you worried that users are emailing sensitive information openly? According to Osterman
PORTLANDDIOCESE.ORG Email - How to Connect Table of Contents
 1 PORTLANDDIOCESE.ORG Email - How to Connect Table of Contents Email Access via a Web Browser... 2 Email Client Setup... 3 Outlook 2013 for Windows... 3 Outlook for Mac 2011... 4 Mac OS X 10.6+... 4 iphone
1 PORTLANDDIOCESE.ORG Email - How to Connect Table of Contents Email Access via a Web Browser... 2 Email Client Setup... 3 Outlook 2013 for Windows... 3 Outlook for Mac 2011... 4 Mac OS X 10.6+... 4 iphone
Cloud. Hosted Exchange Administration Manual
 Cloud Hosted Exchange Administration Manual Table of Contents Table of Contents... 1 Table of Figures... 4 1 Preface... 6 2 Telesystem Hosted Exchange Administrative Portal... 7 3 Hosted Exchange Service...
Cloud Hosted Exchange Administration Manual Table of Contents Table of Contents... 1 Table of Figures... 4 1 Preface... 6 2 Telesystem Hosted Exchange Administrative Portal... 7 3 Hosted Exchange Service...
Quick Heal Exchange Protection 4.0
 Quick Heal Exchange Protection 4.0 Customizable Spam Filter. Uninterrupted Antivirus Security. Product Highlights Built-in defense keeps your business communications and sensitive information secure from
Quick Heal Exchange Protection 4.0 Customizable Spam Filter. Uninterrupted Antivirus Security. Product Highlights Built-in defense keeps your business communications and sensitive information secure from
Nuove Features MDM ParlaMI ITALIAN SFFv2
 NUOVO RILASCIO Spamina Parla Mailbox is a cloud-based email platform with up to 30GB of mailbox space, providing enterprise-class email, calendar, collaboration and integrated security. Designed to maintain
NUOVO RILASCIO Spamina Parla Mailbox is a cloud-based email platform with up to 30GB of mailbox space, providing enterprise-class email, calendar, collaboration and integrated security. Designed to maintain
Erado Archiving & Setup Instruction Microsoft Exchange 2007 Push Journaling
 Erado Archiving & Setup Instruction Microsoft Exchange 2007 Push Journaling This document covers the following Microsoft Exchange Server Editions Microsoft Exchange Enterprise Edition 2007 Microsoft Exchange
Erado Archiving & Setup Instruction Microsoft Exchange 2007 Push Journaling This document covers the following Microsoft Exchange Server Editions Microsoft Exchange Enterprise Edition 2007 Microsoft Exchange
ONE Mail Direct for Desktop Software
 ONE Mail Direct for Desktop Software Version: 1 Document ID: 3931 Document Owner: ONE Mail Product Team Copyright Notice Copyright 2015, ehealth Ontario All rights reserved No part of this document may
ONE Mail Direct for Desktop Software Version: 1 Document ID: 3931 Document Owner: ONE Mail Product Team Copyright Notice Copyright 2015, ehealth Ontario All rights reserved No part of this document may
Configuring, Managing and Troubleshooting Microsoft Exchange Server 2010 Service Pack 2
 Course 10135B: Configuring, Managing and Troubleshooting Microsoft Exchange Server 2010 Service Pack 2 Course Details Course Outline Module 1: Deploying Microsoft Exchange Server 2010 This module describes
Course 10135B: Configuring, Managing and Troubleshooting Microsoft Exchange Server 2010 Service Pack 2 Course Details Course Outline Module 1: Deploying Microsoft Exchange Server 2010 This module describes
Implementing Transparent Security for Desktop Encryption Users
 Implementing Transparent Security for Desktop Encryption Users Solutions to automate email encryption with external parties Get this White Paper Entrust Inc. All All Rights Reserved. 1 1 Contents Introduction...
Implementing Transparent Security for Desktop Encryption Users Solutions to automate email encryption with external parties Get this White Paper Entrust Inc. All All Rights Reserved. 1 1 Contents Introduction...
MS-10135 - Configuring, Managing and Troubleshooting Microsoft Exchange Server 2010
 MS-10135 - Configuring, Managing and Troubleshooting Microsoft Exchange Server 2010 Introduction This course will provide you with the knowledge and skills to configure and manage a Microsoft Exchange
MS-10135 - Configuring, Managing and Troubleshooting Microsoft Exchange Server 2010 Introduction This course will provide you with the knowledge and skills to configure and manage a Microsoft Exchange
Hosted Exchange 2010
 Hosted Exchange 2010 More email flexibility. Less server hassle and cost. Add/remove mailboxes at any time to suit your needs Unlimited web traffic Choice of Premium or Basic mailboxes Hosted Exchange
Hosted Exchange 2010 More email flexibility. Less server hassle and cost. Add/remove mailboxes at any time to suit your needs Unlimited web traffic Choice of Premium or Basic mailboxes Hosted Exchange
FTA Computer Security Workshop. Secure Email
 FTA Computer Security Workshop Secure Email March 8, 2007 Stan Wiechert, KDOR IS Security Officer Outline of Presentation The Risks associated with Email Business Constraints Secure Email Features Some
FTA Computer Security Workshop Secure Email March 8, 2007 Stan Wiechert, KDOR IS Security Officer Outline of Presentation The Risks associated with Email Business Constraints Secure Email Features Some
Build Your Knowledge!
 About this Course This course will provide you with the knowledge and skills to configure and manage a Microsoft Exchange Server 2010 messaging environment. This course will teach you how to configure
About this Course This course will provide you with the knowledge and skills to configure and manage a Microsoft Exchange Server 2010 messaging environment. This course will teach you how to configure
Introduction. Part I Introduction to Exchange Server 2010 1
 Contents Introduction xxix Part I Introduction to Exchange Server 2010 1 Chapter 1 Introduction to Exchange Server 2010 3 Part II Brief History of Exchange Servers 4 New Features in Exchange Server 2010
Contents Introduction xxix Part I Introduction to Exchange Server 2010 1 Chapter 1 Introduction to Exchange Server 2010 3 Part II Brief History of Exchange Servers 4 New Features in Exchange Server 2010
msona mbox mgroupware 6.0 mbox mgroupware 6.0 Datasheet enterprise email, group Product Highlights
 msona mbox mgroupware 6.0 mbox mgroupware 6.0 Datasheet enterprise email, group calendaring and mobility Get the same email and mobility functionality as the big boy without the big bill! Cost-Effective
msona mbox mgroupware 6.0 mbox mgroupware 6.0 Datasheet enterprise email, group calendaring and mobility Get the same email and mobility functionality as the big boy without the big bill! Cost-Effective
BUILT FOR YOU. Contents. Cloudmore Exchange
 BUILT FOR YOU Introduction is designed so it is as cost effective as possible for you to configure, provision and manage to a specification to suit your organisation. With a proven history of delivering
BUILT FOR YOU Introduction is designed so it is as cost effective as possible for you to configure, provision and manage to a specification to suit your organisation. With a proven history of delivering
5053A: Designing a Messaging Infrastructure Using Microsoft Exchange Server 2007
 5053A: Designing a Messaging Infrastructure Using Microsoft Exchange Server 2007 Course Number: 5053A Course Length: 3 Days Course Overview This three-day instructor-led course provides students with the
5053A: Designing a Messaging Infrastructure Using Microsoft Exchange Server 2007 Course Number: 5053A Course Length: 3 Days Course Overview This three-day instructor-led course provides students with the
Office of Information Technology Connecting to Microsoft Exchange User Guide
 OVERVIEW The Office of Information Technology is migrating its messaging infrastructure from Microsoft Exchange 2003 to Microsoft Exchange 2010. Moving to the latest technology will provide many enhancements
OVERVIEW The Office of Information Technology is migrating its messaging infrastructure from Microsoft Exchange 2003 to Microsoft Exchange 2010. Moving to the latest technology will provide many enhancements
Business mail 1 MS OUTLOOK CONFIGURATION... 2
 Business mail Instructions for configuration of Outlook, 2007, 2010, 2013 and mobile devices CONTENT 1 MS OUTLOOK CONFIGURATION... 2 1.1 Outlook 2007, 2010 and 2013 adding new exchange account, automatic
Business mail Instructions for configuration of Outlook, 2007, 2010, 2013 and mobile devices CONTENT 1 MS OUTLOOK CONFIGURATION... 2 1.1 Outlook 2007, 2010 and 2013 adding new exchange account, automatic
Amazon WorkMail. User Guide Version 1.0
 Amazon WorkMail User Guide Amazon WorkMail: User Guide Copyright 2016 Amazon Web Services, Inc. and/or its affiliates. All rights reserved. Amazon's trademarks and trade dress may not be used in connection
Amazon WorkMail User Guide Amazon WorkMail: User Guide Copyright 2016 Amazon Web Services, Inc. and/or its affiliates. All rights reserved. Amazon's trademarks and trade dress may not be used in connection
Exchange 2007 Overview
 Exchange 2007 Overview Presented by: Chris Avis IT Evangelist Microsoft Corporation Seattle Windows Networking User Group February 2009 monthly meeting What Will We Cover? New features in Microsoft Exchange
Exchange 2007 Overview Presented by: Chris Avis IT Evangelist Microsoft Corporation Seattle Windows Networking User Group February 2009 monthly meeting What Will We Cover? New features in Microsoft Exchange
Hosted Exchange 101 - A Beginners Guide
 Hosted Exchange 101 Introduction The purpose of this guide is to introduce people to the advantages and benefits of hosted Microsoft Exchange as both a business and a personal email service. This guide
Hosted Exchange 101 Introduction The purpose of this guide is to introduce people to the advantages and benefits of hosted Microsoft Exchange as both a business and a personal email service. This guide
The new Exchange Work Smarter, Anywhere.
 The new Exchange Work Smarter, Anywhere. Email on a browser Email on a phone Voicemail in your inbox Massive, low-cost mailboxes May 1997 Nov. 1997 Dec. 2001 Mar. 2004 Dec. 2006 Nov. 2008 Nov. 2009 Mission-critical,
The new Exchange Work Smarter, Anywhere. Email on a browser Email on a phone Voicemail in your inbox Massive, low-cost mailboxes May 1997 Nov. 1997 Dec. 2001 Mar. 2004 Dec. 2006 Nov. 2008 Nov. 2009 Mission-critical,
Configuring, Managing and Troubleshooting Microsoft Exchange Server 2010 Service Pack 2
 Course 10135 Configuring, Managing and Troubleshooting Microsoft Exchange Server 2010 Service Pack 2 Length: 5 Days Language(s): English Audience(s): IT Professionals Level: 200 Technology: Microsoft Exchange
Course 10135 Configuring, Managing and Troubleshooting Microsoft Exchange Server 2010 Service Pack 2 Length: 5 Days Language(s): English Audience(s): IT Professionals Level: 200 Technology: Microsoft Exchange
Configuring, Managing and Troubleshooting Microsoft Exchange Server 2010 Service Pack 2
 Course 10135B: Configuring, Managing and Troubleshooting Microsoft Exchange Server 2010 Service Pack 2 Length: 5 Days Audience(s): IT Professionals Level: 200 Technology: Microsoft Exchange Server 2010
Course 10135B: Configuring, Managing and Troubleshooting Microsoft Exchange Server 2010 Service Pack 2 Length: 5 Days Audience(s): IT Professionals Level: 200 Technology: Microsoft Exchange Server 2010
activecho Driving Secure Enterprise File Sharing and Syncing
 activecho Driving Secure Enterprise File Sharing and Syncing activecho Overview In today s enterprise workplace, employees are increasingly demanding mobile and collaborative solutions in order to get
activecho Driving Secure Enterprise File Sharing and Syncing activecho Overview In today s enterprise workplace, employees are increasingly demanding mobile and collaborative solutions in order to get
Configuring your email client to connect to your Exchange mailbox
 Configuring your email client to connect to your Exchange mailbox Contents Use Outlook Web Access (OWA) to access your Exchange mailbox... 2 Use Outlook 2003 to connect to your Exchange mailbox... 3 Add
Configuring your email client to connect to your Exchange mailbox Contents Use Outlook Web Access (OWA) to access your Exchange mailbox... 2 Use Outlook 2003 to connect to your Exchange mailbox... 3 Add
What s New with Enterprise Vault 11? Symantec Enterprise Vault 11 - What's New?
 What s New with Enterprise Vault 11? 1 Disclaimer Any information regarding pre-release Symantec offerings, future updates or other planned modifications is subject to ongoing evaluation by Symantec and
What s New with Enterprise Vault 11? 1 Disclaimer Any information regarding pre-release Symantec offerings, future updates or other planned modifications is subject to ongoing evaluation by Symantec and
Migration User Guides: The Console Email Application Setup Guide
 Migration User Guides: The Console Email Application Setup Guide Version 1.0 1 Contents Introduction 3 What are my email software settings? 3 Popular email software setup tutorials 3 Apple Mail OS Maverick
Migration User Guides: The Console Email Application Setup Guide Version 1.0 1 Contents Introduction 3 What are my email software settings? 3 Popular email software setup tutorials 3 Apple Mail OS Maverick
Personalised E-Mail package Details
 Personalised E-Mail package Details All Mail Packages provided include a UK Domain name of your choice when available (someone@yourdomainname.co.uk), the domain name will be registered in your name and
Personalised E-Mail package Details All Mail Packages provided include a UK Domain name of your choice when available (someone@yourdomainname.co.uk), the domain name will be registered in your name and
What s New in Exchange 2010?
 What s New in Exchange 2010? A quick guide to the most significant changes you will see when your account is migrated to Exchange 2010 The Top 10 Changes in Exchange 2010..2 Email Retention and Archives..3
What s New in Exchange 2010? A quick guide to the most significant changes you will see when your account is migrated to Exchange 2010 The Top 10 Changes in Exchange 2010..2 Email Retention and Archives..3
PORTLANDDIOCESE.ORG Email - How to Connect Table of Contents
 1 PORTLANDDIOCESE.ORG Email - How to Connect Table of Contents Email Access via a Web Browser... 2 Email Client Setup... 3 Outlook 2007, 2010 & 2013 for Windows... 3 Outlook for Mac 2011... 5 Mac OS X
1 PORTLANDDIOCESE.ORG Email - How to Connect Table of Contents Email Access via a Web Browser... 2 Email Client Setup... 3 Outlook 2007, 2010 & 2013 for Windows... 3 Outlook for Mac 2011... 5 Mac OS X
10135A: Configuring, Managing, and Troubleshooting Microsoft Exchange Server 2010
 10135A: Configuring, Managing, and Troubleshooting Microsoft Exchange Server 2010 Course Number: 10135A Course Length: 5 Day Course Overview This instructor-led course will provide you with the knowledge
10135A: Configuring, Managing, and Troubleshooting Microsoft Exchange Server 2010 Course Number: 10135A Course Length: 5 Day Course Overview This instructor-led course will provide you with the knowledge
Rethinking Email Encryption: Eight Best Practices for Success
 WHITE PAPER Rethinking Email Encryption: Eight Best Practices for Success Executive Summary Email continues to play a fundamental role in an organization s communications and day to day business and represents
WHITE PAPER Rethinking Email Encryption: Eight Best Practices for Success Executive Summary Email continues to play a fundamental role in an organization s communications and day to day business and represents
GREEN HOUSE DATA. E-Mail Services Guide. Built right. Just for you. greenhousedata.com. Green House Data 340 Progress Circle Cheyenne, WY 82007
 GREEN HOUSE DATA Built right. Just for you. E-Mail Services Guide greenhousedata.com 1 Green House Data 340 Progress Circle Cheyenne, WY 82007 Table of Contents Getting Started on Business Class Email
GREEN HOUSE DATA Built right. Just for you. E-Mail Services Guide greenhousedata.com 1 Green House Data 340 Progress Circle Cheyenne, WY 82007 Table of Contents Getting Started on Business Class Email
Mobile Encrypted Messaging: A Perfect Complement to MDM
 Mobile Encrypted Messaging: A Perfect Complement to MDM Robby Gulri Echoworx Chris Corbet - Fiberlink Agenda > Today s mobile landscape and challenges > Encrypted messaging and MDM as a complete solution
Mobile Encrypted Messaging: A Perfect Complement to MDM Robby Gulri Echoworx Chris Corbet - Fiberlink Agenda > Today s mobile landscape and challenges > Encrypted messaging and MDM as a complete solution
Parla, Secure Cloud Email
 Parla, Secure Cloud Email Secure Email, Instant Messaging, Calendar, Contacts, Tasks, File sharing and Notes across all devices The 1 st Secure Email and Instant Messaging from and European Security Vendor
Parla, Secure Cloud Email Secure Email, Instant Messaging, Calendar, Contacts, Tasks, File sharing and Notes across all devices The 1 st Secure Email and Instant Messaging from and European Security Vendor
Selecting Your Essential Cloud Services for Office 365
 DATASHEET Selecting Your Essential Cloud Services for Office 365 Mimecast provides a rich set of cloud services designed to meet the specific needs of Microsoft Office 365 customers. We effectively remove
DATASHEET Selecting Your Essential Cloud Services for Office 365 Mimecast provides a rich set of cloud services designed to meet the specific needs of Microsoft Office 365 customers. We effectively remove
Email Encryption Made Simple
 White Paper For organizations large or small Table of Contents Who Is Reading Your Email? 3 The Three Options Explained 3 Organization-to-organization encryption 3 Secure portal or organization-to-user
White Paper For organizations large or small Table of Contents Who Is Reading Your Email? 3 The Three Options Explained 3 Organization-to-organization encryption 3 Secure portal or organization-to-user
Windows Mail POP Instructions - Bloomsburg University Students
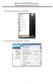 1. Open Windows Mail from your Start Menu. 2. Click on the Tools menu and click Accounts. 1 3. Click on Add to add your account. 4. Click on Email Account and then click Next. 2 5. Enter your full name
1. Open Windows Mail from your Start Menu. 2. Click on the Tools menu and click Accounts. 1 3. Click on Add to add your account. 4. Click on Email Account and then click Next. 2 5. Enter your full name
Hosted Email Managed by Email Specialists
 Hosted Email Managed by Email Specialists The Mailtrust email system is the premium hosted email platform that provides your business with powerful, secure, and reliable email with absolutely no maintenance
Hosted Email Managed by Email Specialists The Mailtrust email system is the premium hosted email platform that provides your business with powerful, secure, and reliable email with absolutely no maintenance
Rethinking Email Encryption: Eight Best Practices for Success
 White paper Rethinking Email Encryption: Eight Best Practices for Success HP Security Voltage Table of contents 3 3 4 5 5 6 7 7 8 9 9 10 Executive Summary Introduction: Growing Email Usage and Continued
White paper Rethinking Email Encryption: Eight Best Practices for Success HP Security Voltage Table of contents 3 3 4 5 5 6 7 7 8 9 9 10 Executive Summary Introduction: Growing Email Usage and Continued
Offer Specifications Dell Email Management Services (EMS): mobilencrypt
 Offer Specifications Dell Email Management Services (EMS): mobilencrypt Services Overview mobilencrypt is an on-the-device email encryption solution that enables mobile users to send and receive encrypted
Offer Specifications Dell Email Management Services (EMS): mobilencrypt Services Overview mobilencrypt is an on-the-device email encryption solution that enables mobile users to send and receive encrypted
HOW OMEGA COMPARES. Support
 HOW OMEGA COMPARES We know that choosing a cloud service provider is an important decision. Understanding the facts about your provider is essential to setting expectations on reliability, support and
HOW OMEGA COMPARES We know that choosing a cloud service provider is an important decision. Understanding the facts about your provider is essential to setting expectations on reliability, support and
Astaro Mail Archiving Getting Started Guide
 Connect With Confidence Astaro Mail Archiving Getting Started Guide About this Getting Started Guide The Astaro Mail Archiving Service is an archiving platform in the form of a fully hosted service. E-mails
Connect With Confidence Astaro Mail Archiving Getting Started Guide About this Getting Started Guide The Astaro Mail Archiving Service is an archiving platform in the form of a fully hosted service. E-mails
Configuring Managing and Troubleshooting Microsoft Exchange Server 2010
 Course Code: M10135 Vendor: Microsoft Course Overview Duration: 5 RRP: 1,980 Configuring Managing and Troubleshooting Microsoft Exchange Server 2010 Overview This course will provide you with the knowledge
Course Code: M10135 Vendor: Microsoft Course Overview Duration: 5 RRP: 1,980 Configuring Managing and Troubleshooting Microsoft Exchange Server 2010 Overview This course will provide you with the knowledge
Dispatch: A Unique Email Security Solution
 Dispatch: A Unique Email Security Solution 720 836 1222 sales / support sales@absio.com email www.absio.com web 8740 Lucent Boulevard, Ste 101 Highlands Ranch, CO, 80129 1 110-WP005-1 Organizations use
Dispatch: A Unique Email Security Solution 720 836 1222 sales / support sales@absio.com email www.absio.com web 8740 Lucent Boulevard, Ste 101 Highlands Ranch, CO, 80129 1 110-WP005-1 Organizations use
Secure Email Inside the Corporate Network: INDEX 1 INTRODUCTION 2. Encryption at the Internal Desktop 2 CURRENT TECHNIQUES FOR DESKTOP ENCRYPTION 3
 A Tumbleweed Whitepaper Secure Email Inside the Corporate Network: Providing Encryption at the Internal Desktop INDEX INDEX 1 INTRODUCTION 2 Encryption at the Internal Desktop 2 CURRENT TECHNIQUES FOR
A Tumbleweed Whitepaper Secure Email Inside the Corporate Network: Providing Encryption at the Internal Desktop INDEX INDEX 1 INTRODUCTION 2 Encryption at the Internal Desktop 2 CURRENT TECHNIQUES FOR
Overview of Active Directory Rights Management Services with Windows Server 2008 R2
 Overview of Active Directory Rights Management Services with Windows Server 2008 R2 Student Manual Module 5: Information Rights Management on Server Applications Information in this document, including
Overview of Active Directory Rights Management Services with Windows Server 2008 R2 Student Manual Module 5: Information Rights Management on Server Applications Information in this document, including
White Paper. Anywhere, Any Device File Access with IT in Control. Enterprise File Serving 2.0
 White Paper Enterprise File Serving 2.0 Anywhere, Any Device File Access with IT in Control Like it or not, cloud- based file sharing services have opened up a new world of mobile file access and collaborative
White Paper Enterprise File Serving 2.0 Anywhere, Any Device File Access with IT in Control Like it or not, cloud- based file sharing services have opened up a new world of mobile file access and collaborative
Policy Based Encryption E. Administrator Guide
 Policy Based Encryption E Administrator Guide Policy Based Encryption E Administrator Guide Documentation version: 1.2 Legal Notice Legal Notice Copyright 2012 Symantec Corporation. All rights reserved.
Policy Based Encryption E Administrator Guide Policy Based Encryption E Administrator Guide Documentation version: 1.2 Legal Notice Legal Notice Copyright 2012 Symantec Corporation. All rights reserved.
Policy Based Encryption E. Administrator Guide
 Policy Based Encryption E Administrator Guide Policy Based Encryption E Administrator Guide Documentation version: 1.2 Legal Notice Legal Notice Copyright 2012 Symantec Corporation. All rights reserved.
Policy Based Encryption E Administrator Guide Policy Based Encryption E Administrator Guide Documentation version: 1.2 Legal Notice Legal Notice Copyright 2012 Symantec Corporation. All rights reserved.
Using etoken for Securing E-mails Using Outlook and Outlook Express
 Using etoken for Securing E-mails Using Outlook and Outlook Express Lesson 15 April 2004 etoken Certification Course Securing Email Using Certificates Unprotected emails can be easily read and/or altered
Using etoken for Securing E-mails Using Outlook and Outlook Express Lesson 15 April 2004 etoken Certification Course Securing Email Using Certificates Unprotected emails can be easily read and/or altered
Symantec Managed PKI Service Deployment Options
 WHITE PAPER: SYMANTEC MANAGED PKI SERVICE DEPLOYMENT............. OPTIONS........................... Symantec Managed PKI Service Deployment Options Who should read this paper This whitepaper explains
WHITE PAPER: SYMANTEC MANAGED PKI SERVICE DEPLOYMENT............. OPTIONS........................... Symantec Managed PKI Service Deployment Options Who should read this paper This whitepaper explains
BlackBerry Enterprise Server for Microsoft Exchange Version: 5.0 Service Pack: 2. Feature and Technical Overview
 BlackBerry Enterprise Server for Microsoft Exchange Version: 5.0 Service Pack: 2 Feature and Technical Overview Published: 2010-06-16 SWDT305802-1108946-0615123042-001 Contents 1 Overview: BlackBerry Enterprise
BlackBerry Enterprise Server for Microsoft Exchange Version: 5.0 Service Pack: 2 Feature and Technical Overview Published: 2010-06-16 SWDT305802-1108946-0615123042-001 Contents 1 Overview: BlackBerry Enterprise
WineWeb Email Account Services
 As part of WineWeb s website services, we can provide email accounts under your domain name. Although this is optional, almost all of our clients use our mail server for their email accounts. We run the
As part of WineWeb s website services, we can provide email accounts under your domain name. Although this is optional, almost all of our clients use our mail server for their email accounts. We run the
HOW HOSTED EXCHANGE COMPARES WITH GOOGLE APPS
 HOW HOSTED EXCHANGE COMPARES WITH GOOGLE APPS We know that choosing a cloud service provider is an important decision. Understanding the facts about your provider is essential to setting expectations on
HOW HOSTED EXCHANGE COMPARES WITH GOOGLE APPS We know that choosing a cloud service provider is an important decision. Understanding the facts about your provider is essential to setting expectations on
Configuring, Managing and Troubleshooting Microsoft Exchange Server 2010 Service Pack 2
 About this Course This course will provide you with the knowledge and skills to configure and manage a Microsoft Exchange Server 2010 messaging environment. This course will teach you how to configure
About this Course This course will provide you with the knowledge and skills to configure and manage a Microsoft Exchange Server 2010 messaging environment. This course will teach you how to configure
Wharf T&T Cloud Backup Service User & Installation Guide
 Wharf T&T Cloud Backup Service User & Installation Guide Version 1.6 Feb 2013 Table of contents BEFORE YOU INSTALL 3 Page Section 1. Installation of Client Software 5 Section 2. Account Activation 8 Section
Wharf T&T Cloud Backup Service User & Installation Guide Version 1.6 Feb 2013 Table of contents BEFORE YOU INSTALL 3 Page Section 1. Installation of Client Software 5 Section 2. Account Activation 8 Section
Secured email Global Communication version 4.6
 Secured email Global Communication version 4.6 A new and improved way to receive Secured email Authors: Daniel Nilsson and Jeff Sherwood May 11, 2010 Content Introduction...3 Secured email...4 Sending
Secured email Global Communication version 4.6 A new and improved way to receive Secured email Authors: Daniel Nilsson and Jeff Sherwood May 11, 2010 Content Introduction...3 Secured email...4 Sending
Receiving Secure Email from Citi For External Customers and Business Partners
 Citi Secure Email Program Receiving Secure Email from Citi For External Customers and Business Partners Protecting the privacy and security of client information is a top priority at Citi. Citi s Secure
Citi Secure Email Program Receiving Secure Email from Citi For External Customers and Business Partners Protecting the privacy and security of client information is a top priority at Citi. Citi s Secure
BTC STUDENT EMAIL GUIDE
 BTC STUDENT EMAIL GUIDE All students have a BTC email account. If you are unable to access your account, please contact your instructor. Student Email Each student has an email account. Your email address
BTC STUDENT EMAIL GUIDE All students have a BTC email account. If you are unable to access your account, please contact your instructor. Student Email Each student has an email account. Your email address
ForeScout MDM Enterprise
 Highlights Features Automated real-time detection of mobile Seamless enrollment & installation of MDM agents on unmanaged Policy-based blocking of unauthorized Identify corporate vs. personal Identify
Highlights Features Automated real-time detection of mobile Seamless enrollment & installation of MDM agents on unmanaged Policy-based blocking of unauthorized Identify corporate vs. personal Identify
PolyU Connect Mobile Connection. Setup Guide
 PolyU Connect Mobile Connection Setup Guide Version 1.7 Last Update: 29 August 2014 PolyU Connect: www.polyu.edu.hk/connect ITS HelpCentre Support: www.polyu.edu.hk/hots ITS HelpCentre Support Hotline:
PolyU Connect Mobile Connection Setup Guide Version 1.7 Last Update: 29 August 2014 PolyU Connect: www.polyu.edu.hk/connect ITS HelpCentre Support: www.polyu.edu.hk/hots ITS HelpCentre Support Hotline:
Live@edu User Guide. Please visit the Helpdesk website for more information: http://www.smu.edu.sg/iits/helpdesk_support/index.asp
 IITS Main Office SINGAPORE MANAGEMENT UNIVERSITY Administration Building, Level 11 81, Victoria Street Singapore 188065 Phone: 65-6828 1930 Email: iits@smu.edu.sg Please visit the Helpdesk website for
IITS Main Office SINGAPORE MANAGEMENT UNIVERSITY Administration Building, Level 11 81, Victoria Street Singapore 188065 Phone: 65-6828 1930 Email: iits@smu.edu.sg Please visit the Helpdesk website for
The ForeScout Difference
 The ForeScout Difference Mobile Device Management (MDM) can help IT security managers secure mobile and the sensitive corporate data that is frequently stored on such. However, ForeScout delivers a complete
The ForeScout Difference Mobile Device Management (MDM) can help IT security managers secure mobile and the sensitive corporate data that is frequently stored on such. However, ForeScout delivers a complete
APPENDIX B1 - FUNCTIONALITY AND INTEGRATION REQUIREMENTS RESPONSE FORM FOR A COUNTY HOSTED SOLUTION
 APPENDIX B1 - FUNCTIONALITY AND INTEGRATION REQUIREMENTS RESPONSE FORM FOR A COUNTY HOSTED SOLUTION Response Code: Offeror should place the appropriate letter designation in the Availability column according
APPENDIX B1 - FUNCTIONALITY AND INTEGRATION REQUIREMENTS RESPONSE FORM FOR A COUNTY HOSTED SOLUTION Response Code: Offeror should place the appropriate letter designation in the Availability column according
Email DLP Quick Start
 1 Email DLP Quick Start TRITON - Email Security is automatically configured to work with TRITON - Data Security. The Email Security module registers with the Data Security Management Server when you install
1 Email DLP Quick Start TRITON - Email Security is automatically configured to work with TRITON - Data Security. The Email Security module registers with the Data Security Management Server when you install
LiveArchive. For the latest version of this document please go to: http://www.exchangedefender.com/docs. v 1.0 May 16,2011 Audience: Staff
 LiveArchive For the latest version of this document please go to: http://www.exchangedefender.com/docs v 1.0 May 16,2011 Audience: Staff Table of Contents ExchangeDefender Overview 3 ExchangeDefender LiveArchive
LiveArchive For the latest version of this document please go to: http://www.exchangedefender.com/docs v 1.0 May 16,2011 Audience: Staff Table of Contents ExchangeDefender Overview 3 ExchangeDefender LiveArchive
Evaluation Guide. eprism Messaging Security Suite. 800-782-3762 www.edgewave.com V8.200
 800-782-3762 www.edgewave.com Welcome to EdgeWave Messaging Security! This short guide is intended to help administrators setup and test the EdgeWave Messaging Security Suite for evaluation purposes. A
800-782-3762 www.edgewave.com Welcome to EdgeWave Messaging Security! This short guide is intended to help administrators setup and test the EdgeWave Messaging Security Suite for evaluation purposes. A
Rocket Mail Smartphone Configuration Guide. Version 2.0
 Rocket Mail Smartphone Configuration Guide Version 2.0 Nick Sherman 3/1/2013 Android Configuration 1. From the Applications menu, select Email. This application may be named Mail on some versions of Android.
Rocket Mail Smartphone Configuration Guide Version 2.0 Nick Sherman 3/1/2013 Android Configuration 1. From the Applications menu, select Email. This application may be named Mail on some versions of Android.
Configuration Task 3: (Optional) As part of configuration, you can deploy rules. For more information, see "Deploy Inbox Rules" below.
 Configure the E-mail Router After the E-mail Router has been installed, you can configure several aspects of it. Some of these configuration tasks are mandatory. Others are optional in that you use them
Configure the E-mail Router After the E-mail Router has been installed, you can configure several aspects of it. Some of these configuration tasks are mandatory. Others are optional in that you use them
Email Encryption Made Simple
 Email Encryption Made Simple For organizations large or small Table of Contents Who Is Reading Your Email?....3 The Three Options Explained....3 Organization-to-organization encryption....3 Secure portal
Email Encryption Made Simple For organizations large or small Table of Contents Who Is Reading Your Email?....3 The Three Options Explained....3 Organization-to-organization encryption....3 Secure portal
Configuring, Managing and Troubleshooting Microsoft Exchange Server 2010 Service Pack 2
 Configuring, Managing and Troubleshooting Microsoft Exchange Server 2010 Service Pack 2 Course Details Course Code: Duration: 10135B 5 day(s) Elements of this syllabus are subject to change. This course
Configuring, Managing and Troubleshooting Microsoft Exchange Server 2010 Service Pack 2 Course Details Course Code: Duration: 10135B 5 day(s) Elements of this syllabus are subject to change. This course
Exchange, Kerio Comparison
 Exchange, Kerio Comparison Choosing the Best Alternative to Microsoft Exchange Server Feature Comparison IceWarp Server Microsoft Exchange Kerio Connect Exchange Alternative Education Business Solutions
Exchange, Kerio Comparison Choosing the Best Alternative to Microsoft Exchange Server Feature Comparison IceWarp Server Microsoft Exchange Kerio Connect Exchange Alternative Education Business Solutions
redcoal EmailSMS for MS Outlook and Lotus Notes
 redcoal EmailSMS for MS Outlook and Lotus Notes Technical Support: support@redcoal.com Or visit http://www.redcoal.com/ All Documents prepared or furnished by redcoal Pty Ltd remains the property of redcoal
redcoal EmailSMS for MS Outlook and Lotus Notes Technical Support: support@redcoal.com Or visit http://www.redcoal.com/ All Documents prepared or furnished by redcoal Pty Ltd remains the property of redcoal
USER GUIDE WWPass Security for Email (Outlook) For WWPass Security Pack 2.4
 USER GUIDE WWPass Security for Email (Outlook) For WWPass Security Pack 2.4 March 2014 TABLE OF CONTENTS Chapter 1 Welcome... 4 Introducing WWPass Security for Email (Outlook)... 5 Supported Outlook Products...
USER GUIDE WWPass Security for Email (Outlook) For WWPass Security Pack 2.4 March 2014 TABLE OF CONTENTS Chapter 1 Welcome... 4 Introducing WWPass Security for Email (Outlook)... 5 Supported Outlook Products...
Cloud Services. Cloud Control Panel. Admin Guide
 Cloud Services Cloud Control Panel Admin Guide 10/18/2014 CONTENTS Description of Policy Based Encryption... 2 Policy Based Encryption and Email Content Control... 2 Features Summary... 3 Creating an Encryption
Cloud Services Cloud Control Panel Admin Guide 10/18/2014 CONTENTS Description of Policy Based Encryption... 2 Policy Based Encryption and Email Content Control... 2 Features Summary... 3 Creating an Encryption
Comparing VMware Zimbra with Leading Email and Collaboration Platforms Z I M B R A C O M P E T I T I V E W H I T E P A P E R
 Comparing VMware Zimbra with Leading Email and Collaboration Platforms Z I M B R A C O M P E T I T I V E W H I T E P A P E R Introduction Email is indispensable few applications are more critical to the
Comparing VMware Zimbra with Leading Email and Collaboration Platforms Z I M B R A C O M P E T I T I V E W H I T E P A P E R Introduction Email is indispensable few applications are more critical to the
Hybrid Architecture. Office 365. On-premises Exchange org (Exchange 2007+) Provisioned via DirSync. Secure Mail flow
 Hybrid Deployment Hybrid Architecture Provisioned via DirSync Exchange 2010 (HUB/CAS) Exchange 2013 CAS & MBX Secure Mail flow Exchange Federation (Free/Busy, Mail Tips, Archive, etc.) Mailbox data via
Hybrid Deployment Hybrid Architecture Provisioned via DirSync Exchange 2010 (HUB/CAS) Exchange 2013 CAS & MBX Secure Mail flow Exchange Federation (Free/Busy, Mail Tips, Archive, etc.) Mailbox data via
Email: support@apps4rent.com Toll Free: 1-866-716-2040 International: 1-646-506-9354
 1. Check your Welcome e-mail for login credentials for the control panel. 2. Using the login details in the welcome e-mail; login at https://cp.hostallapps.com Adding Domain: 1. On the Home Page of the
1. Check your Welcome e-mail for login credentials for the control panel. 2. Using the login details in the welcome e-mail; login at https://cp.hostallapps.com Adding Domain: 1. On the Home Page of the
BOTTOM UP THINKING EMAIL SETUP INSTRUCTIONS. Unique businesses require unique solutions CLIENT GUIDE
 BOTTOM UP THINKING Unique businesses require unique solutions EMAIL SETUP INSTRUCTIONS CLIENT GUIDE INDEX How to connect a. Deciding on best method (POP or IMAP) Setting up email on devices Webmail a.
BOTTOM UP THINKING Unique businesses require unique solutions EMAIL SETUP INSTRUCTIONS CLIENT GUIDE INDEX How to connect a. Deciding on best method (POP or IMAP) Setting up email on devices Webmail a.
Copyright 2012 Trend Micro Incorporated. All rights reserved.
 Trend Micro Incorporated reserves the right to make changes to this document and to the products described herein without notice. Before installing and using the software, please review the readme files,
Trend Micro Incorporated reserves the right to make changes to this document and to the products described herein without notice. Before installing and using the software, please review the readme files,
How to install and use the File Sharing Outlook Plugin
 How to install and use the File Sharing Outlook Plugin Thank you for purchasing Green House Data File Sharing. This guide will show you how to install and configure the Outlook Plugin on your desktop.
How to install and use the File Sharing Outlook Plugin Thank you for purchasing Green House Data File Sharing. This guide will show you how to install and configure the Outlook Plugin on your desktop.
Exchange Comparison. Choosing the Best Alternative to Microsoft Exchange Server Feature Comparison. IceWarp Server Microsoft Exchange
 Exchange Comparison Choosing the Best Alternative to Microsoft Exchange Server Feature Comparison IceWarp Server Microsoft Exchange Exchange Alternative Education Business Solutions Service Providers Government
Exchange Comparison Choosing the Best Alternative to Microsoft Exchange Server Feature Comparison IceWarp Server Microsoft Exchange Exchange Alternative Education Business Solutions Service Providers Government
Workshop purpose and objective
 Messaging Workshop purpose and objective Workshop purpose Facilitate planning discussions for messaging coexistence Considerations of Office 365 limits and features Objectives Identify Microsoft Office
Messaging Workshop purpose and objective Workshop purpose Facilitate planning discussions for messaging coexistence Considerations of Office 365 limits and features Objectives Identify Microsoft Office
How To Configure And Manage An Exchange Server 2010 For Free
 Configuring, Managing and Troubleshooting Microsoft Exchange Server 2010 MOC10135 About this Course This five-day, instructor-led course will provide you with the knowledge and skills to configure and
Configuring, Managing and Troubleshooting Microsoft Exchange Server 2010 MOC10135 About this Course This five-day, instructor-led course will provide you with the knowledge and skills to configure and
