Intelligent Face Recognition
|
|
|
- IJCSE Publication
- 8 years ago
- Views:
Transcription
1 International Journal of Computer Sciences and Engineering Open Access Technical Paper Volume-4, Issue-2 E-ISSN: Intelligent Face Recognition Akram Qureshi 1* and Ashok Kajla 2 1*,2 RTU Kota Rajasthan India Received: Jan /19/2016 Revised: Feb/02/2016 Accepted: Feb/12/2016 Accepted: Feb/29/2016 Abstract Face recognition has been an important and hard problem in computer vision application. Recently, haar cascade method has proven to be an effective method for face recognition. In this thesis, a simple and powerful approach is developed for real time multi face recognition system. A threefold stage application is developed. in the first stage face detection is done by using Haar cascade. In second stage, Haar cascade features are stored in the memory and compare with the data base faces. In third stage the matched database face is recognized for the query face and displayed with recognized face name. The three stages are mentioned as face detection, feature extraction storage & comparison and at last face recognition. The experimental results for real time multiple recognition system is shown and elaborates the benefit of using the described approach. Keywords Face detection, Face recognition, Feature extraction, Haar cascade. I. INTRODUCTION Face recognition is a technique which is used to identify a particular person in a digital image by analyzing and comparing pattern. In other word we can say Face recognition system is a different kind of computer application. This is automated software to identifying or verifying a person from a digital image or a video frame from video source. In Face recognition face image is used as a input through camera and can be classified in to two part one is static and another is dynamic. Face recognition systems recognizing a human face from scene and extract it. the system measures overall facial structure, distances between eyes, mouth and jaw edge, than compares these nodal points to the nodal points computed from a data base of pictures in order to find a match. Face recognition system is a very useful system because of quality. It has an accuracy and errorless over the other security systems. Face recognition system is advance system over other biometric methods. Face recognition systems are commonly used for security purpose. But this system is spreading all over the world in many other applications. Many companies and industries or persons use many security systems. That systems require Passwords, PIN code, tokens, cards. Password or pin code can be forgotten and it is difficult to remember all time. Card or many things such as token keys etc can be misplaced. So to minimize these problems we use biometric based technologies. There are different types of biometric based technologies. However, an individual s biological traits cannot be misplaced, forgotten, stolen or forged. Biometric-based technologies include identification based on physiological characteristics (such as face, fingerprints, finger geometry, hand geometry, hand veins, palm, iris, retina, ear and voice) and behavioral traits (such as gait, signature and keystroke dynamics).face recognition is also a biometric method. Face recognition has many advantages over some other biometric methods. These biometric technologies require fixed position in front of the camera for retina identification, for finger printing user needs to put hand on a hand rest. But by face recognition system a face images can be acquired from a distance by camera. Face recognition system is beneficial for security and surveillance purposes. In other biometric system a fingerprint security system can be risky or useless whether an epidermis tissue is damaged in some way. In other biometric system signature can be forged or modified. Voice recognition is susceptible to background noises in public places and auditory fluctuations on a phone line or tape recording. But with face recognition system face images can be obtained easily with fixed cameras. face recognition is totally non-intrusive and does not carry any such health risks. So this is the reason to make the face recognition system. I have work done on the face recognition system. This system is a combination of two techniques first is face detection and another is recognition. The face detection is performed on live acquired images. I have used Haar Cascading in face detection. Then face is detected and after that I used face recognition algorithm used to recognize the face. 2. Problem faced by researcher in face identification and recognition Main problem of this paper is to design and implement a face recognition system. The system should detect faces in live acquired images in front of the camera, and detected faces should be recognized by recognition algorithm. This system will be very useful in security system. This paper 2016, IJCSE All Rights Reserved 128
2 will be part of security system. I hope people will use this very much in future. Face recognition system will detect, extract and recognize frontal faces from acquired live images. System should work under changing lighting conditions in the laboratory. System should not extract faces if they use sunglasses. It means face should be without spectacle or without sunglasses. 3. Proposed methodology for face recognition Face recognition system is divided into three parts. 1. Detection 2. Recognition 3. Detection & Recognition In face recognition, face detection is the first step. It is very difficult to detect the face because there are combinations of many algorithms for face detection to increase accuracy and errorless. There are two methods of face detection. 1. Knowledge-Based Methods 2. Image-Based Methods Knowledge-Based methods use information about facial features, template matching or skin color. Skin color is modeled in each color spaces like RGB (Red-Green-Blue), HSV (Hue- Saturation-Value), YUV (Luminance-Blue Luminance Difference-Red Luminance Difference). YCbCr (Luminance-Blue Difference Chroma-Red Difference Chroma), and in statistical models. Facial features are important information for human faces and standard images can be generated using these information. Facial Features are used to find nose, eyes, mouth, or other facial features to detect the human faces. Face has a unique thing to differentiate from other objects and hence a template can be generated to scan and detect faces. To detect faces and facial features by extraction of skin like region with YCbCr color space and edges are detected in the skin like region. Then, eyes are found with Principal Component Analysis (PCA) on the edged region. Finally, Mouth is found based on geometrical information. To find eyes, eyebrows and mouth, color snakes are applied to verified face image. Ruan and Yin segment skin regions in YCbCr color space and faces are verified with Linear Support Vector Machine (SVM). For final verification of face, eyes and mouth are found with the information of Cb and Cr difference. For eye region Cb value is greater than Cr value and for mouth region Cr value is greater than Cb value. Figure: 1 Flow Chart I have worked on visual studio. i installed emgu cv. I have used c# language with the help of emgu library on visual studio. Perception is the first step to make this face recognition system. 1 Perception: First I have installed the camera connected to computer. After that I have used picture box and buttons from toolbox. After that I have coded the programme for camera capture. 2 Feature extraction: I have used Haar Cascade to extract the feature. this is a Viola and Jones method called Haar Cascade. The human face is a dynamic object that comes in many forms and colors. Facial recognition is not possible if the face is not isolated from the background. An image is only a collection of color and/or light intensity values. Analyzing these pixels for face detection is time consuming and difficult to accomplish because of the wide variations of shape and pigmentation within a human face. Pixels often require reanalysis for scaling and precision. Viola and Jones devised an algorithm, called Haar Classifiers, to rapidly detect any object, including human faces, using AdaBoost classifier cascades that are based on Haar-like features and not pixels. Haar cascade Haar like features use the change in contrast values between adjacent rectangular groups of pixels. The contrast variances between the pixel groups are used to determine 2016, IJCSE All Rights Reserved 129
3 relative light and dark areas. Two or three adjacent groups with a relative contrast variance form a Haar-like feature. Haar-like features, as shown in Figure 2 are used to detect an image. Haar features can easily be scaled by increasing or decreasing the size of the pixel group being examined. This allows features to be used to detect objects of various sizes. The simple rectangular features of an image are calculated using an intermediate representation of an image, called the integral image. The integral image is an array containing the sums of the pixels intensity values located directly to the left of a pixel and directly above the pixel at location (x,y) inclusive. So if A[x,y] is the original image and AI[x,y] is the integral image then the integral image is computed as shown in equation 1 and illustrated in Figure 3. AI[x, y]= ΣA( x, y ) (1) x _< x, y _< y The features rotated by forty-five degrees, like the line feature shown in Figure 2(e), as introduced by Lienhart and Maydt, require another intermediate representation called the rotated integral image or rotated sum auxiliary image [5]. The rotated integral image is calculated by finding the sum of the pixels intensity values that are located at a forty five degree angle to the left and above for the x value and below for the y value. So if A[x, y] is the original image and AR[x, y] is the rotated integral image then the integral image is computed as shown in equation 2 an illustrated in Figure 4. AR[x, y]= ΣA( x, y ) (2) x _< x, x _< x- y-y Figure 2: Common Haar Features Lienhart and Maydt introduced the concept of a tilted (45 ) Haar-like feature. This was used to increase the dimensionaly of the set of features in an attempt to improve the detection of objects in images. This was successful, as some of these features are able to describe the object in a better way. For example, a 2-rectangle tilted Haar-like feature can indicate the existence of an edge at 45. Messom and Barczak extended the idea to a generic rotated Haar-like feature. Although the idea sounds mathematically sound, practical problems prevented the use of Haar-like features at any angle. In order to be fast, detection algorithms use low resolution images, causing rounding errors. For this reason, rotated Haar-like features are not commonly used. Figure 4 summed area of rotated integral image It only takes two passes to compute both integral image arrays, one for each array. Using the appropriate integral image and taking the difference between six to eight array elements forming two or three connected rectangles, a feature of any scale can be computed. Thus calculating a feature is extremely fast and efficient. It also means 2016, IJCSE All Rights Reserved 130
4 calculating features of various sizes requires the same effort as a feature of only two or three pixels. The detection of various sizes of the same object requires the same amount of effort and time as objects of similar sizes since scaling requires no additional effort. In Face Recognition, second step is to detect the face. We use a rectangle which shows a face in a given picture. Here we use HAAR CASCADE algorithm to detect the face. Face detection is shown in a fifure no. 6 Fast computation of Haar-like features One of the contributions of Viola and Jones was to use summed area table, which they called integral image. Integral images can be defined as two-dimensional lookup table in the form of a matrix with the same size of the original image. Each element of the integral image contains the sum of all pixels located on the up-left region of the original image (in relation to the element's position). This allows to compute sum of rectangular areas in the image, at any position or scale, using only four lookups: where points, as shown in the figure. belong to the integral image Each Haar-like feature may need more than four lookups, depending on how it was defined. Viola and Jones's 2- rectangle features need six lookups, 3-rectangle features need eight lookups, and 4-rectangle features need nine lookups. 4. Experimental work Figure 6: face detection In Face Recognition, final stage is to recognize a face of person. After detect the face detection the system recognize the face among the persons. It is shown in figure no. 7. In Face Recognition, first step is camera capture. First we install emgu library and visual studio on the computer. After that we use window form application programme using emgu cv we use toolbox and make a programme using c# language. In given figure no. 5 camera capture is shown. Figure 7: face recognition In literature, many detection algorithms based on facial features are available. Figure 5: Camera Capture 5: Face recognition algorithms 1:Eigenfaces (Eigen features) 2016, IJCSE All Rights Reserved 131
5 2: Neural networks 3: Template matching 4: Hidden markov model 5: 3D morphable model 6: Dynamic link architecture 7: Support Vector Machine (SVM) 8: Line Edge Map (LEM) 6: Applications Face recognition is used for different types of tasks: 1. Face recognition system is used in Image database investigations (missing children, immigrants and police bookings, searching image databases of licensed drivers, benefit recipients). 2. Face recognition system is used in Criminal justice systems (booking systems, post-event analysis, forensic). 3. Face recognition system is used in.general identity verification (banking, electronic commerce, identifying newborns). 4. Face recognition system is used in Security (access control to buildings, airports/seaports, ATM machines and border Check points, computer/ network security, authentication on multimedia workstations). 5. Face recognition system is used in Witness face reconstruction. 6. Face recognition system is used in Multi-media environments with adaptive human-computer interfaces. 7. Face recognition system is used in video indexing like labeling faces in video. 8. Face recognition system is used in Surveillance (a large number of CCTVs can be monitored to look for known criminals, drug offenders, etc. 7: Conclusion In this paper we have developed the face recognition system. To recognize the face, this system is divided in to some part such as perception (camera connected to the laptop), face detection, face Feature extraction, face recognition. In this system we have used Haar Cascade to detect the face and we have used eigen faces to recognize the face. In this paper, we have covered a detail discussion on the various stages of any face detection technique. Recently, face detection techniques have been employed in different applications such as face recognition, facial feature extraction, detection of facial expression, which is very important for this paper. I have shown the applications of face recognition in which area this system works. Face recognition is a challenging problem. This system solved this problem and a tremendous growth in the face recognition over the last few years. current face recognition systems have reached a certain degree of maturity when operating under constrained conditions. The ultimate goal of this paper in this area is to detect the face and recognize the face. REFERENCES [1] Y.-F. Yao, X.-Y.Jing, and H.-S. Wong, "Face and palmprint feature level fusion for single sample biometrics recognition," Neurocomputing, Vol.70, pp , [2] J. Zhou, G. Su, C. Jiang, Y. Deng, and C. Li, "A faceand fingerprint identity authentication system based on multi-route detection," Neurocomputing, Vol.70, pp , [3] C. Nastar and M. Mitschke, "Real time face recognition using feature combination," in ThirdIEEE International Conference on Automatic Faceand Gesture Recognition. Nara, Japan, 1998, pp [4] S. Gong, S. J. McKenna, and A. Psarrou, Dynamic Vision: From Images to Face Recognition ImperialCollege Press (World Scientific Publishing Company), [5] B. Moghaddam and M. H. Yang, "Learning Gender with Support Faces," IEEE Transactions on PatternAnalysis and Machine Intelligence, Vol.24, pp , [6] J. N. K. Liu, M. Wang, and B. Feng, "ibotguard: an Internet-based intelligent robot security system using invariant face recognition against intruder," IEEETransactions on Systems Man And Cybernetics PartC-Applications And Reviews, Vol.35, pp , [7] R. Brunelli and T. Poggio, "HyperBF Networks for Gender Classification," Proceedings of DARPAImage Understanding Workshop, pp , [8] A. Colmenarez, B. J. Frey, and T. S. Huang, "A probabilistic framework for embedded face and facial expression recognition," in Proceedings of theieee Conference on Computer Vision and PatternRecognition, Vol.1. Ft. Collins, CO, USA, 1999, pp [9] Y. Shinohara and N. Otsu, "Facial Expression Recognition Using Fisher Weight Maps," in SixthIEEE 2016, IJCSE All Rights Reserved 132
6 International Conference on Automatic Faceand Gesture Recognition, Vol.100, 2004, pp [10] F. Bourel, C. C. Chibelushi, and A. A. Low, "Robust Facial Feature Tracking," in British Machine VisionConference.Bristol, 2000, pp [11] K. Morik, P. Brockhausen, and T. Joachims, "Combining statistical learning with a knowledgebasedapproach -- A case study in intensive care monitoring," in 16th International Conference onmachine Learning (ICML-99). San Francisco, CA, USA: Morgan Kaufmann, 1999, pp [12] S. Singh and N. Papanikolopoulos, "Vision-based detection of driver fatigue," Department of Computer Science, University of Minnesota, Technical report [13] D. N. Metaxas, S. Venkataraman, and C. Vogler, "Image-Based Stress Recognition Using a Model- Based Dynamic Face Tracking System," InternationalConference on Computational Science, pp , [14] M. M. Rahman, R. Hartley, and S. Ishikawa, "A Passive AndMultimodal Biometric System for Personal Identification," in International Conferenceon Visualization, Imaging and Image Processing. Spain, 2005, pp , IJCSE All Rights Reserved 133
International Journal of Advanced Information in Arts, Science & Management Vol.2, No.2, December 2014
 Efficient Attendance Management System Using Face Detection and Recognition Arun.A.V, Bhatath.S, Chethan.N, Manmohan.C.M, Hamsaveni M Department of Computer Science and Engineering, Vidya Vardhaka College
Efficient Attendance Management System Using Face Detection and Recognition Arun.A.V, Bhatath.S, Chethan.N, Manmohan.C.M, Hamsaveni M Department of Computer Science and Engineering, Vidya Vardhaka College
Index Terms: Face Recognition, Face Detection, Monitoring, Attendance System, and System Access Control.
 Modern Technique Of Lecture Attendance Using Face Recognition. Shreya Nallawar, Neha Giri, Neeraj Deshbhratar, Shamal Sane, Trupti Gautre, Avinash Bansod Bapurao Deshmukh College Of Engineering, Sewagram,
Modern Technique Of Lecture Attendance Using Face Recognition. Shreya Nallawar, Neha Giri, Neeraj Deshbhratar, Shamal Sane, Trupti Gautre, Avinash Bansod Bapurao Deshmukh College Of Engineering, Sewagram,
HANDS-FREE PC CONTROL CONTROLLING OF MOUSE CURSOR USING EYE MOVEMENT
 International Journal of Scientific and Research Publications, Volume 2, Issue 4, April 2012 1 HANDS-FREE PC CONTROL CONTROLLING OF MOUSE CURSOR USING EYE MOVEMENT Akhil Gupta, Akash Rathi, Dr. Y. Radhika
International Journal of Scientific and Research Publications, Volume 2, Issue 4, April 2012 1 HANDS-FREE PC CONTROL CONTROLLING OF MOUSE CURSOR USING EYE MOVEMENT Akhil Gupta, Akash Rathi, Dr. Y. Radhika
Framework for Biometric Enabled Unified Core Banking
 Proc. of Int. Conf. on Advances in Computer Science and Application Framework for Biometric Enabled Unified Core Banking Manohar M, R Dinesh and Prabhanjan S Research Candidate, Research Supervisor, Faculty
Proc. of Int. Conf. on Advances in Computer Science and Application Framework for Biometric Enabled Unified Core Banking Manohar M, R Dinesh and Prabhanjan S Research Candidate, Research Supervisor, Faculty
Mathematical Model Based Total Security System with Qualitative and Quantitative Data of Human
 Int Jr of Mathematics Sciences & Applications Vol3, No1, January-June 2013 Copyright Mind Reader Publications ISSN No: 2230-9888 wwwjournalshubcom Mathematical Model Based Total Security System with Qualitative
Int Jr of Mathematics Sciences & Applications Vol3, No1, January-June 2013 Copyright Mind Reader Publications ISSN No: 2230-9888 wwwjournalshubcom Mathematical Model Based Total Security System with Qualitative
FACE RECOGNITION BASED ATTENDANCE MARKING SYSTEM
 Available Online at www.ijcsmc.com International Journal of Computer Science and Mobile Computing A Monthly Journal of Computer Science and Information Technology IJCSMC, Vol. 3, Issue. 2, February 2014,
Available Online at www.ijcsmc.com International Journal of Computer Science and Mobile Computing A Monthly Journal of Computer Science and Information Technology IJCSMC, Vol. 3, Issue. 2, February 2014,
Efficient Attendance Management: A Face Recognition Approach
 Efficient Attendance Management: A Face Recognition Approach Badal J. Deshmukh, Sudhir M. Kharad Abstract Taking student attendance in a classroom has always been a tedious task faultfinders. It is completely
Efficient Attendance Management: A Face Recognition Approach Badal J. Deshmukh, Sudhir M. Kharad Abstract Taking student attendance in a classroom has always been a tedious task faultfinders. It is completely
A Various Biometric application for authentication and identification
 A Various Biometric application for authentication and identification 1 Karuna Soni, 2 Umesh Kumar, 3 Priya Dosodia, Government Mahila Engineering College, Ajmer, India Abstract: In today s environment,
A Various Biometric application for authentication and identification 1 Karuna Soni, 2 Umesh Kumar, 3 Priya Dosodia, Government Mahila Engineering College, Ajmer, India Abstract: In today s environment,
LOCAL SURFACE PATCH BASED TIME ATTENDANCE SYSTEM USING FACE. indhubatchvsa@gmail.com
 LOCAL SURFACE PATCH BASED TIME ATTENDANCE SYSTEM USING FACE 1 S.Manikandan, 2 S.Abirami, 2 R.Indumathi, 2 R.Nandhini, 2 T.Nanthini 1 Assistant Professor, VSA group of institution, Salem. 2 BE(ECE), VSA
LOCAL SURFACE PATCH BASED TIME ATTENDANCE SYSTEM USING FACE 1 S.Manikandan, 2 S.Abirami, 2 R.Indumathi, 2 R.Nandhini, 2 T.Nanthini 1 Assistant Professor, VSA group of institution, Salem. 2 BE(ECE), VSA
HAND GESTURE BASEDOPERATINGSYSTEM CONTROL
 HAND GESTURE BASEDOPERATINGSYSTEM CONTROL Garkal Bramhraj 1, palve Atul 2, Ghule Supriya 3, Misal sonali 4 1 Garkal Bramhraj mahadeo, 2 Palve Atule Vasant, 3 Ghule Supriya Shivram, 4 Misal Sonali Babasaheb,
HAND GESTURE BASEDOPERATINGSYSTEM CONTROL Garkal Bramhraj 1, palve Atul 2, Ghule Supriya 3, Misal sonali 4 1 Garkal Bramhraj mahadeo, 2 Palve Atule Vasant, 3 Ghule Supriya Shivram, 4 Misal Sonali Babasaheb,
Computer Vision Based Employee Activities Analysis
 Volume 03 Issue 05, September 2014 Computer Vision Based Employee Activities Analysis Md. Zahangir Alom, Nabil Tahmidul Karim, Shovon Paulinus Rozario *, Md. Rezwanul Hoque, Md. Rumman Bin Ashraf, Saikat
Volume 03 Issue 05, September 2014 Computer Vision Based Employee Activities Analysis Md. Zahangir Alom, Nabil Tahmidul Karim, Shovon Paulinus Rozario *, Md. Rezwanul Hoque, Md. Rumman Bin Ashraf, Saikat
Video Surveillance System for Security Applications
 Video Surveillance System for Security Applications Vidya A.S. Department of CSE National Institute of Technology Calicut, Kerala, India V. K. Govindan Department of CSE National Institute of Technology
Video Surveillance System for Security Applications Vidya A.S. Department of CSE National Institute of Technology Calicut, Kerala, India V. K. Govindan Department of CSE National Institute of Technology
Multimodal Biometric Recognition Security System
 Multimodal Biometric Recognition Security System Anju.M.I, G.Sheeba, G.Sivakami, Monica.J, Savithri.M Department of ECE, New Prince Shri Bhavani College of Engg. & Tech., Chennai, India ABSTRACT: Security
Multimodal Biometric Recognition Security System Anju.M.I, G.Sheeba, G.Sivakami, Monica.J, Savithri.M Department of ECE, New Prince Shri Bhavani College of Engg. & Tech., Chennai, India ABSTRACT: Security
May 2010. For other information please contact:
 access control biometrics user guide May 2010 For other information please contact: British Security Industry Association t: 0845 389 3889 f: 0845 389 0761 e: info@bsia.co.uk www.bsia.co.uk Form No. 181.
access control biometrics user guide May 2010 For other information please contact: British Security Industry Association t: 0845 389 3889 f: 0845 389 0761 e: info@bsia.co.uk www.bsia.co.uk Form No. 181.
The Implementation of Face Security for Authentication Implemented on Mobile Phone
 The Implementation of Face Security for Authentication Implemented on Mobile Phone Emir Kremić *, Abdulhamit Subaşi * * Faculty of Engineering and Information Technology, International Burch University,
The Implementation of Face Security for Authentication Implemented on Mobile Phone Emir Kremić *, Abdulhamit Subaşi * * Faculty of Engineering and Information Technology, International Burch University,
This method looks at the patterns found on a fingertip. Patterns are made by the lines on the tip of the finger.
 According to the SysAdmin, Audit, Network, Security Institute (SANS), authentication problems are among the top twenty critical Internet security vulnerabilities. These problems arise from the use of basic
According to the SysAdmin, Audit, Network, Security Institute (SANS), authentication problems are among the top twenty critical Internet security vulnerabilities. These problems arise from the use of basic
Classroom Monitoring System by Wired Webcams and Attendance Management System
 Classroom Monitoring System by Wired Webcams and Attendance Management System Sneha Suhas More, Amani Jamiyan Madki, Priya Ranjit Bade, Upasna Suresh Ahuja, Suhas M. Patil Student, Dept. of Computer, KJCOEMR,
Classroom Monitoring System by Wired Webcams and Attendance Management System Sneha Suhas More, Amani Jamiyan Madki, Priya Ranjit Bade, Upasna Suresh Ahuja, Suhas M. Patil Student, Dept. of Computer, KJCOEMR,
An Active Head Tracking System for Distance Education and Videoconferencing Applications
 An Active Head Tracking System for Distance Education and Videoconferencing Applications Sami Huttunen and Janne Heikkilä Machine Vision Group Infotech Oulu and Department of Electrical and Information
An Active Head Tracking System for Distance Education and Videoconferencing Applications Sami Huttunen and Janne Heikkilä Machine Vision Group Infotech Oulu and Department of Electrical and Information
A Real Time Driver s Eye Tracking Design Proposal for Detection of Fatigue Drowsiness
 A Real Time Driver s Eye Tracking Design Proposal for Detection of Fatigue Drowsiness Nitin Jagtap 1, Ashlesha kolap 1, Mohit Adgokar 1, Dr. R.N Awale 2 PG Scholar, Dept. of Electrical Engg., VJTI, Mumbai
A Real Time Driver s Eye Tracking Design Proposal for Detection of Fatigue Drowsiness Nitin Jagtap 1, Ashlesha kolap 1, Mohit Adgokar 1, Dr. R.N Awale 2 PG Scholar, Dept. of Electrical Engg., VJTI, Mumbai
Face detection is a process of localizing and extracting the face region from the
 Chapter 4 FACE NORMALIZATION 4.1 INTRODUCTION Face detection is a process of localizing and extracting the face region from the background. The detected face varies in rotation, brightness, size, etc.
Chapter 4 FACE NORMALIZATION 4.1 INTRODUCTION Face detection is a process of localizing and extracting the face region from the background. The detected face varies in rotation, brightness, size, etc.
Face Recognition Using Multi-Agent System
 International Journal of Computer Science and Engineering Open Access Review Paper Volume-4, Issue-4 E-ISSN: 2347-2693 Face Recognition Using Multi-Agent System Wasim Shaikh 1*, Hemant Shinde 2 and Grishma
International Journal of Computer Science and Engineering Open Access Review Paper Volume-4, Issue-4 E-ISSN: 2347-2693 Face Recognition Using Multi-Agent System Wasim Shaikh 1*, Hemant Shinde 2 and Grishma
Digital Identity & Authentication Directions Biometric Applications Who is doing what? Academia, Industry, Government
 Digital Identity & Authentication Directions Biometric Applications Who is doing what? Academia, Industry, Government Briefing W. Frisch 1 Outline Digital Identity Management Identity Theft Management
Digital Identity & Authentication Directions Biometric Applications Who is doing what? Academia, Industry, Government Briefing W. Frisch 1 Outline Digital Identity Management Identity Theft Management
Using Real Time Computer Vision Algorithms in Automatic Attendance Management Systems
 Using Real Time Computer Vision Algorithms in Automatic Attendance Management Systems Visar Shehu 1, Agni Dika 2 Contemporary Sciences and Technologies - South East European University, Macedonia 1 Contemporary
Using Real Time Computer Vision Algorithms in Automatic Attendance Management Systems Visar Shehu 1, Agni Dika 2 Contemporary Sciences and Technologies - South East European University, Macedonia 1 Contemporary
Face Recognition in Low-resolution Images by Using Local Zernike Moments
 Proceedings of the International Conference on Machine Vision and Machine Learning Prague, Czech Republic, August14-15, 014 Paper No. 15 Face Recognition in Low-resolution Images by Using Local Zernie
Proceedings of the International Conference on Machine Vision and Machine Learning Prague, Czech Republic, August14-15, 014 Paper No. 15 Face Recognition in Low-resolution Images by Using Local Zernie
Palmprint Classification
 Palmprint Classification Li Fang*, Maylor K.H. Leung, Tejas Shikhare, Victor Chan, Kean Fatt Choon School of Computer Engineering, Nanyang Technological University, Singapore 639798 E-mail: asfli@ntu.edu.sg
Palmprint Classification Li Fang*, Maylor K.H. Leung, Tejas Shikhare, Victor Chan, Kean Fatt Choon School of Computer Engineering, Nanyang Technological University, Singapore 639798 E-mail: asfli@ntu.edu.sg
Neural Network based Vehicle Classification for Intelligent Traffic Control
 Neural Network based Vehicle Classification for Intelligent Traffic Control Saeid Fazli 1, Shahram Mohammadi 2, Morteza Rahmani 3 1,2,3 Electrical Engineering Department, Zanjan University, Zanjan, IRAN
Neural Network based Vehicle Classification for Intelligent Traffic Control Saeid Fazli 1, Shahram Mohammadi 2, Morteza Rahmani 3 1,2,3 Electrical Engineering Department, Zanjan University, Zanjan, IRAN
Hands free HCI based on head tracking using feature extraction
 Hands free HCI based on head tracking using feature extraction Mrs. Nitty Sarah Alex 1 Senior Assistant Professor, New Horizon College of engineering, Bangalore, India Abstract The proposed system is an
Hands free HCI based on head tracking using feature extraction Mrs. Nitty Sarah Alex 1 Senior Assistant Professor, New Horizon College of engineering, Bangalore, India Abstract The proposed system is an
Circle Object Recognition Based on Monocular Vision for Home Security Robot
 Journal of Applied Science and Engineering, Vol. 16, No. 3, pp. 261 268 (2013) DOI: 10.6180/jase.2013.16.3.05 Circle Object Recognition Based on Monocular Vision for Home Security Robot Shih-An Li, Ching-Chang
Journal of Applied Science and Engineering, Vol. 16, No. 3, pp. 261 268 (2013) DOI: 10.6180/jase.2013.16.3.05 Circle Object Recognition Based on Monocular Vision for Home Security Robot Shih-An Li, Ching-Chang
DESIGN OF DIGITAL SIGNATURE VERIFICATION ALGORITHM USING RELATIVE SLOPE METHOD
 DESIGN OF DIGITAL SIGNATURE VERIFICATION ALGORITHM USING RELATIVE SLOPE METHOD P.N.Ganorkar 1, Kalyani Pendke 2 1 Mtech, 4 th Sem, Rajiv Gandhi College of Engineering and Research, R.T.M.N.U Nagpur (Maharashtra),
DESIGN OF DIGITAL SIGNATURE VERIFICATION ALGORITHM USING RELATIVE SLOPE METHOD P.N.Ganorkar 1, Kalyani Pendke 2 1 Mtech, 4 th Sem, Rajiv Gandhi College of Engineering and Research, R.T.M.N.U Nagpur (Maharashtra),
Face Recognition For Remote Database Backup System
 Face Recognition For Remote Database Backup System Aniza Mohamed Din, Faudziah Ahmad, Mohamad Farhan Mohamad Mohsin, Ku Ruhana Ku-Mahamud, Mustafa Mufawak Theab 2 Graduate Department of Computer Science,UUM
Face Recognition For Remote Database Backup System Aniza Mohamed Din, Faudziah Ahmad, Mohamad Farhan Mohamad Mohsin, Ku Ruhana Ku-Mahamud, Mustafa Mufawak Theab 2 Graduate Department of Computer Science,UUM
Development of Academic Attendence Monitoring System Using Fingerprint Identification
 164 Development of Academic Attendence Monitoring System Using Fingerprint Identification TABASSAM NAWAZ, SAIM PERVAIZ, ARASH KORRANI, AZHAR-UD-DIN Software Engineering Department Faculty of Telecommunication
164 Development of Academic Attendence Monitoring System Using Fingerprint Identification TABASSAM NAWAZ, SAIM PERVAIZ, ARASH KORRANI, AZHAR-UD-DIN Software Engineering Department Faculty of Telecommunication
Physical Security: A Biometric Approach Preeti, Rajni M.Tech (Network Security),BPSMV preetytushir@gmail.com, ratri451@gmail.com
 www.ijecs.in International Journal Of Engineering And Computer Science ISSN:2319-7242 Volume 3 Issue 2 February, 2014 Page No. 3864-3868 Abstract: Physical Security: A Approach Preeti, Rajni M.Tech (Network
www.ijecs.in International Journal Of Engineering And Computer Science ISSN:2319-7242 Volume 3 Issue 2 February, 2014 Page No. 3864-3868 Abstract: Physical Security: A Approach Preeti, Rajni M.Tech (Network
An Energy-Based Vehicle Tracking System using Principal Component Analysis and Unsupervised ART Network
 Proceedings of the 8th WSEAS Int. Conf. on ARTIFICIAL INTELLIGENCE, KNOWLEDGE ENGINEERING & DATA BASES (AIKED '9) ISSN: 179-519 435 ISBN: 978-96-474-51-2 An Energy-Based Vehicle Tracking System using Principal
Proceedings of the 8th WSEAS Int. Conf. on ARTIFICIAL INTELLIGENCE, KNOWLEDGE ENGINEERING & DATA BASES (AIKED '9) ISSN: 179-519 435 ISBN: 978-96-474-51-2 An Energy-Based Vehicle Tracking System using Principal
A secure face tracking system
 International Journal of Information & Computation Technology. ISSN 0974-2239 Volume 4, Number 10 (2014), pp. 959-964 International Research Publications House http://www. irphouse.com A secure face tracking
International Journal of Information & Computation Technology. ISSN 0974-2239 Volume 4, Number 10 (2014), pp. 959-964 International Research Publications House http://www. irphouse.com A secure face tracking
Illumination, Expression and Occlusion Invariant Pose-Adaptive Face Recognition System for Real- Time Applications
 Illumination, Expression and Occlusion Invariant Pose-Adaptive Face Recognition System for Real- Time Applications Shireesha Chintalapati #1, M. V. Raghunadh *2 Department of E and CE NIT Warangal, Andhra
Illumination, Expression and Occlusion Invariant Pose-Adaptive Face Recognition System for Real- Time Applications Shireesha Chintalapati #1, M. V. Raghunadh *2 Department of E and CE NIT Warangal, Andhra
Biometrics is the use of physiological and/or behavioral characteristics to recognize or verify the identity of individuals through automated means.
 Definition Biometrics is the use of physiological and/or behavioral characteristics to recognize or verify the identity of individuals through automated means. Description Physiological biometrics is based
Definition Biometrics is the use of physiological and/or behavioral characteristics to recognize or verify the identity of individuals through automated means. Description Physiological biometrics is based
ARM7 Based Smart ATM Access & Security System Using Fingerprint Recognition & GSM Technology
 ARM7 Based Smart ATM Access & Security System Using Fingerprint Recognition & GSM Technology Khatmode Ranjit P 1, Kulkarni Ramchandra V 2, Ghodke Bharat S 3, Prof. P. P. Chitte 4, Prof. Anap S. D 5 1 Student
ARM7 Based Smart ATM Access & Security System Using Fingerprint Recognition & GSM Technology Khatmode Ranjit P 1, Kulkarni Ramchandra V 2, Ghodke Bharat S 3, Prof. P. P. Chitte 4, Prof. Anap S. D 5 1 Student
Volume 2, Issue 9, September 2014 International Journal of Advance Research in Computer Science and Management Studies
 Volume 2, Issue 9, September 2014 International Journal of Advance Research in Computer Science and Management Studies Research Article / Survey Paper / Case Study Available online at: www.ijarcsms.com
Volume 2, Issue 9, September 2014 International Journal of Advance Research in Computer Science and Management Studies Research Article / Survey Paper / Case Study Available online at: www.ijarcsms.com
Analecta Vol. 8, No. 2 ISSN 2064-7964
 EXPERIMENTAL APPLICATIONS OF ARTIFICIAL NEURAL NETWORKS IN ENGINEERING PROCESSING SYSTEM S. Dadvandipour Institute of Information Engineering, University of Miskolc, Egyetemváros, 3515, Miskolc, Hungary,
EXPERIMENTAL APPLICATIONS OF ARTIFICIAL NEURAL NETWORKS IN ENGINEERING PROCESSING SYSTEM S. Dadvandipour Institute of Information Engineering, University of Miskolc, Egyetemváros, 3515, Miskolc, Hungary,
Laser Gesture Recognition for Human Machine Interaction
 International Journal of Computer Sciences and Engineering Open Access Research Paper Volume-04, Issue-04 E-ISSN: 2347-2693 Laser Gesture Recognition for Human Machine Interaction Umang Keniya 1*, Sarthak
International Journal of Computer Sciences and Engineering Open Access Research Paper Volume-04, Issue-04 E-ISSN: 2347-2693 Laser Gesture Recognition for Human Machine Interaction Umang Keniya 1*, Sarthak
NFC & Biometrics. Christophe Rosenberger
 NFC & Biometrics Christophe Rosenberger OUTLINE GREYC - E-payment & Biometrics Contactless transactions Biometric authentication Solutions Perspectives 2 GREYC Research Lab Research Group in Computer science,
NFC & Biometrics Christophe Rosenberger OUTLINE GREYC - E-payment & Biometrics Contactless transactions Biometric authentication Solutions Perspectives 2 GREYC Research Lab Research Group in Computer science,
Establishing the Uniqueness of the Human Voice for Security Applications
 Proceedings of Student/Faculty Research Day, CSIS, Pace University, May 7th, 2004 Establishing the Uniqueness of the Human Voice for Security Applications Naresh P. Trilok, Sung-Hyuk Cha, and Charles C.
Proceedings of Student/Faculty Research Day, CSIS, Pace University, May 7th, 2004 Establishing the Uniqueness of the Human Voice for Security Applications Naresh P. Trilok, Sung-Hyuk Cha, and Charles C.
Face Recognition Using Robotics
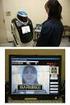 International Journal of Computer Sciences and Engineering Open Access Technical Paper Volume-4, Issue-4 E-ISSN: 2347-2693 Face Recognition Using Robotics Nitesh Pandey 1*,Abhishek Dubey 2 and Bhavesh
International Journal of Computer Sciences and Engineering Open Access Technical Paper Volume-4, Issue-4 E-ISSN: 2347-2693 Face Recognition Using Robotics Nitesh Pandey 1*,Abhishek Dubey 2 and Bhavesh
TIETS34 Seminar: Data Mining on Biometric identification
 TIETS34 Seminar: Data Mining on Biometric identification Youming Zhang Computer Science, School of Information Sciences, 33014 University of Tampere, Finland Youming.Zhang@uta.fi Course Description Content
TIETS34 Seminar: Data Mining on Biometric identification Youming Zhang Computer Science, School of Information Sciences, 33014 University of Tampere, Finland Youming.Zhang@uta.fi Course Description Content
Efficient Background Subtraction and Shadow Removal Technique for Multiple Human object Tracking
 ISSN: 2321-7782 (Online) Volume 1, Issue 7, December 2013 International Journal of Advance Research in Computer Science and Management Studies Research Paper Available online at: www.ijarcsms.com Efficient
ISSN: 2321-7782 (Online) Volume 1, Issue 7, December 2013 International Journal of Advance Research in Computer Science and Management Studies Research Paper Available online at: www.ijarcsms.com Efficient
Real Time Vehicle Theft Identity and Control System Based on ARM 9
 Real Time Vehicle Theft Identity and Control System Based on ARM 9 D.Narendar Singh Associate Professor, M.tech,Ph.d Department of Electronics and Communication Engineering Anurag group of Institutions,
Real Time Vehicle Theft Identity and Control System Based on ARM 9 D.Narendar Singh Associate Professor, M.tech,Ph.d Department of Electronics and Communication Engineering Anurag group of Institutions,
Adaptive Face Recognition System from Myanmar NRC Card
 Adaptive Face Recognition System from Myanmar NRC Card Ei Phyo Wai University of Computer Studies, Yangon, Myanmar Myint Myint Sein University of Computer Studies, Yangon, Myanmar ABSTRACT Biometrics is
Adaptive Face Recognition System from Myanmar NRC Card Ei Phyo Wai University of Computer Studies, Yangon, Myanmar Myint Myint Sein University of Computer Studies, Yangon, Myanmar ABSTRACT Biometrics is
IMPLEMENTATION OF CLASSROOM ATTENDANCE SYSTEM BASED ON FACE RECOGNITION IN CLASS
 IMPLEMENTATION OF CLASSROOM ATTENDANCE SYSTEM BASED ON FACE RECOGNITION IN CLASS Ajinkya Patil 1, Mrudang Shukla 2 1 Mtech (E&TC), 2 Assisstant Professor Symbiosis institute of Technology, Pune, Maharashtra,
IMPLEMENTATION OF CLASSROOM ATTENDANCE SYSTEM BASED ON FACE RECOGNITION IN CLASS Ajinkya Patil 1, Mrudang Shukla 2 1 Mtech (E&TC), 2 Assisstant Professor Symbiosis institute of Technology, Pune, Maharashtra,
Template-based Eye and Mouth Detection for 3D Video Conferencing
 Template-based Eye and Mouth Detection for 3D Video Conferencing Jürgen Rurainsky and Peter Eisert Fraunhofer Institute for Telecommunications - Heinrich-Hertz-Institute, Image Processing Department, Einsteinufer
Template-based Eye and Mouth Detection for 3D Video Conferencing Jürgen Rurainsky and Peter Eisert Fraunhofer Institute for Telecommunications - Heinrich-Hertz-Institute, Image Processing Department, Einsteinufer
A Survey on Face Recognition System - A Challenge
 A Survey on Face Recognition System - A Challenge Dr. Pramod Kumar 1, Mrs. Monika Agarwal 2, Miss. Stuti Nagar 3 Assistant Professor, Computer Application, Shri Ram College, MZN, India 1,2 Scholar, Suresh
A Survey on Face Recognition System - A Challenge Dr. Pramod Kumar 1, Mrs. Monika Agarwal 2, Miss. Stuti Nagar 3 Assistant Professor, Computer Application, Shri Ram College, MZN, India 1,2 Scholar, Suresh
3D Scanner using Line Laser. 1. Introduction. 2. Theory
 . Introduction 3D Scanner using Line Laser Di Lu Electrical, Computer, and Systems Engineering Rensselaer Polytechnic Institute The goal of 3D reconstruction is to recover the 3D properties of a geometric
. Introduction 3D Scanner using Line Laser Di Lu Electrical, Computer, and Systems Engineering Rensselaer Polytechnic Institute The goal of 3D reconstruction is to recover the 3D properties of a geometric
User Authentication Methods for Mobile Systems Dr Steven Furnell
 User Authentication Methods for Mobile Systems Dr Steven Furnell Network Research Group University of Plymouth United Kingdom Overview The rise of mobility and the need for user authentication A survey
User Authentication Methods for Mobile Systems Dr Steven Furnell Network Research Group University of Plymouth United Kingdom Overview The rise of mobility and the need for user authentication A survey
Accessing the bank account without card and password in ATM using biometric technology
 Accessing the bank account without card and password in ATM using biometric technology Mini Agarwal [1] and Lavesh Agarwal [2] Teerthankar Mahaveer University Email: miniagarwal21@gmail.com [1], lavesh_1071985@yahoo.com
Accessing the bank account without card and password in ATM using biometric technology Mini Agarwal [1] and Lavesh Agarwal [2] Teerthankar Mahaveer University Email: miniagarwal21@gmail.com [1], lavesh_1071985@yahoo.com
Biometric For Authentication, Do we need it? Christophe Rosenberger GREYC Research Lab - France
 Biometric For Authentication, Do we need it? Christophe Rosenberger GREYC Research Lab - France OUTLINE Le pôle TES et le sans-contact Introduction User authentication GREYC - E-payment & Biometrics Introduction
Biometric For Authentication, Do we need it? Christophe Rosenberger GREYC Research Lab - France OUTLINE Le pôle TES et le sans-contact Introduction User authentication GREYC - E-payment & Biometrics Introduction
AUTOMATED ATTENDANCE CAPTURE AND TRACKING SYSTEM
 Journal of Engineering Science and Technology EURECA 2014 Special Issue January (2015) 45-59 School of Engineering, Taylor s University AUTOMATED ATTENDANCE CAPTURE AND TRACKING SYSTEM EU TSUN CHIN*, WEI
Journal of Engineering Science and Technology EURECA 2014 Special Issue January (2015) 45-59 School of Engineering, Taylor s University AUTOMATED ATTENDANCE CAPTURE AND TRACKING SYSTEM EU TSUN CHIN*, WEI
SURVEILLANCE ENHANCED FACE RECOGNITION
 SURVEILLANCE ENHANCED FACE RECOGNITION BIOMETRICS Face Recognition Biometrics technology has matured rapidly over recent years, and the use of it for security and authentication purposes has become increasingly
SURVEILLANCE ENHANCED FACE RECOGNITION BIOMETRICS Face Recognition Biometrics technology has matured rapidly over recent years, and the use of it for security and authentication purposes has become increasingly
Face Locating and Tracking for Human{Computer Interaction. Carnegie Mellon University. Pittsburgh, PA 15213
 Face Locating and Tracking for Human{Computer Interaction Martin Hunke Alex Waibel School of Computer Science Carnegie Mellon University Pittsburgh, PA 15213 Abstract Eective Human-to-Human communication
Face Locating and Tracking for Human{Computer Interaction Martin Hunke Alex Waibel School of Computer Science Carnegie Mellon University Pittsburgh, PA 15213 Abstract Eective Human-to-Human communication
Keywords image processing, signature verification, false acceptance rate, false rejection rate, forgeries, feature vectors, support vector machines.
 International Journal of Computer Application and Engineering Technology Volume 3-Issue2, Apr 2014.Pp. 188-192 www.ijcaet.net OFFLINE SIGNATURE VERIFICATION SYSTEM -A REVIEW Pooja Department of Computer
International Journal of Computer Application and Engineering Technology Volume 3-Issue2, Apr 2014.Pp. 188-192 www.ijcaet.net OFFLINE SIGNATURE VERIFICATION SYSTEM -A REVIEW Pooja Department of Computer
Head Pose Estimation on Low Resolution Images
 Head Pose Estimation on Low Resolution Images Nicolas Gourier, Jérôme Maisonnasse, Daniela Hall, James L. Crowley PRIMA, GRAVIR-IMAG INRIA Rhône-Alpes, 38349 St. Ismier. France. Abstract. This paper addresses
Head Pose Estimation on Low Resolution Images Nicolas Gourier, Jérôme Maisonnasse, Daniela Hall, James L. Crowley PRIMA, GRAVIR-IMAG INRIA Rhône-Alpes, 38349 St. Ismier. France. Abstract. This paper addresses
Multi-modal Human-Computer Interaction. Attila Fazekas. Attila.Fazekas@inf.unideb.hu
 Multi-modal Human-Computer Interaction Attila Fazekas Attila.Fazekas@inf.unideb.hu Szeged, 04 July 2006 Debrecen Big Church Multi-modal Human-Computer Interaction - 2 University of Debrecen Main Building
Multi-modal Human-Computer Interaction Attila Fazekas Attila.Fazekas@inf.unideb.hu Szeged, 04 July 2006 Debrecen Big Church Multi-modal Human-Computer Interaction - 2 University of Debrecen Main Building
Low-resolution Image Processing based on FPGA
 Abstract Research Journal of Recent Sciences ISSN 2277-2502. Low-resolution Image Processing based on FPGA Mahshid Aghania Kiau, Islamic Azad university of Karaj, IRAN Available online at: www.isca.in,
Abstract Research Journal of Recent Sciences ISSN 2277-2502. Low-resolution Image Processing based on FPGA Mahshid Aghania Kiau, Islamic Azad university of Karaj, IRAN Available online at: www.isca.in,
Simultaneous Gamma Correction and Registration in the Frequency Domain
 Simultaneous Gamma Correction and Registration in the Frequency Domain Alexander Wong a28wong@uwaterloo.ca William Bishop wdbishop@uwaterloo.ca Department of Electrical and Computer Engineering University
Simultaneous Gamma Correction and Registration in the Frequency Domain Alexander Wong a28wong@uwaterloo.ca William Bishop wdbishop@uwaterloo.ca Department of Electrical and Computer Engineering University
Parallelized Architecture of Multiple Classifiers for Face Detection
 Parallelized Architecture of Multiple s for Face Detection Author(s) Name(s) Author Affiliation(s) E-mail Abstract This paper presents a parallelized architecture of multiple classifiers for face detection
Parallelized Architecture of Multiple s for Face Detection Author(s) Name(s) Author Affiliation(s) E-mail Abstract This paper presents a parallelized architecture of multiple classifiers for face detection
A Method for Controlling Mouse Movement using a Real- Time Camera
 A Method for Controlling Mouse Movement using a Real- Time Camera Hojoon Park Department of Computer Science Brown University, Providence, RI, USA hojoon@cs.brown.edu Abstract This paper presents a new
A Method for Controlling Mouse Movement using a Real- Time Camera Hojoon Park Department of Computer Science Brown University, Providence, RI, USA hojoon@cs.brown.edu Abstract This paper presents a new
Biometric Authentication using Online Signatures
 Biometric Authentication using Online Signatures Alisher Kholmatov and Berrin Yanikoglu alisher@su.sabanciuniv.edu, berrin@sabanciuniv.edu http://fens.sabanciuniv.edu Sabanci University, Tuzla, Istanbul,
Biometric Authentication using Online Signatures Alisher Kholmatov and Berrin Yanikoglu alisher@su.sabanciuniv.edu, berrin@sabanciuniv.edu http://fens.sabanciuniv.edu Sabanci University, Tuzla, Istanbul,
Palmprint as a Biometric Identifier
 Palmprint as a Biometric Identifier 1 Kasturika B. Ray, 2 Rachita Misra 1 Orissa Engineering College, Nabojyoti Vihar, Bhubaneswar, Orissa, India 2 Dept. Of IT, CV Raman College of Engineering, Bhubaneswar,
Palmprint as a Biometric Identifier 1 Kasturika B. Ray, 2 Rachita Misra 1 Orissa Engineering College, Nabojyoti Vihar, Bhubaneswar, Orissa, India 2 Dept. Of IT, CV Raman College of Engineering, Bhubaneswar,
Microcontroller Based Smart ATM Access & Security System Using Fingerprint Recognition & GSM Technology
 Microcontroller Based Smart ATM Access & Security System Using Fingerprint Recognition & GSM Technology Bharath K M, Rohit C V Student of B.E Electronics and Communication Coorg Institute of Technology,
Microcontroller Based Smart ATM Access & Security System Using Fingerprint Recognition & GSM Technology Bharath K M, Rohit C V Student of B.E Electronics and Communication Coorg Institute of Technology,
Text Localization & Segmentation in Images, Web Pages and Videos Media Mining I
 Text Localization & Segmentation in Images, Web Pages and Videos Media Mining I Multimedia Computing, Universität Augsburg Rainer.Lienhart@informatik.uni-augsburg.de www.multimedia-computing.{de,org} PSNR_Y
Text Localization & Segmentation in Images, Web Pages and Videos Media Mining I Multimedia Computing, Universität Augsburg Rainer.Lienhart@informatik.uni-augsburg.de www.multimedia-computing.{de,org} PSNR_Y
A Fully Automatic Approach for Human Recognition from Profile Images Using 2D and 3D Ear Data
 A Fully Automatic Approach for Human Recognition from Profile Images Using 2D and 3D Ear Data S. M. S. Islam, M. Bennamoun, A. S. Mian and R. Davies School of Computer Science and Software Engineering,
A Fully Automatic Approach for Human Recognition from Profile Images Using 2D and 3D Ear Data S. M. S. Islam, M. Bennamoun, A. S. Mian and R. Davies School of Computer Science and Software Engineering,
ATM Transaction Security Using Fingerprint/OTP
 ATM Transaction Security Using Fingerprint/OTP 1 Krishna Nand Pandey, 2 Md. Masoom, 3 Supriya Kumari, 4 Preeti Dhiman 1,2,3,4 Electronics & Instrumentation Engineering, Galgotias College of Engineering
ATM Transaction Security Using Fingerprint/OTP 1 Krishna Nand Pandey, 2 Md. Masoom, 3 Supriya Kumari, 4 Preeti Dhiman 1,2,3,4 Electronics & Instrumentation Engineering, Galgotias College of Engineering
A new Method for Face Recognition Using Variance Estimation and Feature Extraction
 A new Method for Face Recognition Using Variance Estimation and Feature Extraction Walaa Mohamed 1, Mohamed Heshmat 2, Moheb Girgis 3 and Seham Elaw 4 1, 2, 4 Faculty of science, Mathematical and Computer
A new Method for Face Recognition Using Variance Estimation and Feature Extraction Walaa Mohamed 1, Mohamed Heshmat 2, Moheb Girgis 3 and Seham Elaw 4 1, 2, 4 Faculty of science, Mathematical and Computer
The Role of Size Normalization on the Recognition Rate of Handwritten Numerals
 The Role of Size Normalization on the Recognition Rate of Handwritten Numerals Chun Lei He, Ping Zhang, Jianxiong Dong, Ching Y. Suen, Tien D. Bui Centre for Pattern Recognition and Machine Intelligence,
The Role of Size Normalization on the Recognition Rate of Handwritten Numerals Chun Lei He, Ping Zhang, Jianxiong Dong, Ching Y. Suen, Tien D. Bui Centre for Pattern Recognition and Machine Intelligence,
 Tracking Moving Objects In Video Sequences Yiwei Wang, Robert E. Van Dyck, and John F. Doherty Department of Electrical Engineering The Pennsylvania State University University Park, PA16802 Abstract{Object
Tracking Moving Objects In Video Sequences Yiwei Wang, Robert E. Van Dyck, and John F. Doherty Department of Electrical Engineering The Pennsylvania State University University Park, PA16802 Abstract{Object
COMPARISON OF VARIOUS BIOMETRIC METHODS
 COMPARISON OF VARIOUS BIOMETRIC METHODS Rupinder Saini, Narinder Rana Rayat Institute of Engineering and IT errupindersaini27@gmail.com, narinderkrana@gmail.com Abstract This paper presents comparison
COMPARISON OF VARIOUS BIOMETRIC METHODS Rupinder Saini, Narinder Rana Rayat Institute of Engineering and IT errupindersaini27@gmail.com, narinderkrana@gmail.com Abstract This paper presents comparison
A Method of Caption Detection in News Video
 3rd International Conference on Multimedia Technology(ICMT 3) A Method of Caption Detection in News Video He HUANG, Ping SHI Abstract. News video is one of the most important media for people to get information.
3rd International Conference on Multimedia Technology(ICMT 3) A Method of Caption Detection in News Video He HUANG, Ping SHI Abstract. News video is one of the most important media for people to get information.
Extracting a Good Quality Frontal Face Images from Low Resolution Video Sequences
 Extracting a Good Quality Frontal Face Images from Low Resolution Video Sequences Pritam P. Patil 1, Prof. M.V. Phatak 2 1 ME.Comp, 2 Asst.Professor, MIT, Pune Abstract The face is one of the important
Extracting a Good Quality Frontal Face Images from Low Resolution Video Sequences Pritam P. Patil 1, Prof. M.V. Phatak 2 1 ME.Comp, 2 Asst.Professor, MIT, Pune Abstract The face is one of the important
Introduction to Computer Graphics
 Introduction to Computer Graphics Torsten Möller TASC 8021 778-782-2215 torsten@sfu.ca www.cs.sfu.ca/~torsten Today What is computer graphics? Contents of this course Syllabus Overview of course topics
Introduction to Computer Graphics Torsten Möller TASC 8021 778-782-2215 torsten@sfu.ca www.cs.sfu.ca/~torsten Today What is computer graphics? Contents of this course Syllabus Overview of course topics
Open Access A Facial Expression Recognition Algorithm Based on Local Binary Pattern and Empirical Mode Decomposition
 Send Orders for Reprints to reprints@benthamscience.ae The Open Electrical & Electronic Engineering Journal, 2014, 8, 599-604 599 Open Access A Facial Expression Recognition Algorithm Based on Local Binary
Send Orders for Reprints to reprints@benthamscience.ae The Open Electrical & Electronic Engineering Journal, 2014, 8, 599-604 599 Open Access A Facial Expression Recognition Algorithm Based on Local Binary
Understanding The Face Image Format Standards
 Understanding The Face Image Format Standards Paul Griffin, Ph.D. Chief Technology Officer Identix April 2005 Topics The Face Image Standard The Record Format Frontal Face Images Face Images and Compression
Understanding The Face Image Format Standards Paul Griffin, Ph.D. Chief Technology Officer Identix April 2005 Topics The Face Image Standard The Record Format Frontal Face Images Face Images and Compression
User Authentication using Combination of Behavioral Biometrics over the Touchpad acting like Touch screen of Mobile Device
 2008 International Conference on Computer and Electrical Engineering User Authentication using Combination of Behavioral Biometrics over the Touchpad acting like Touch screen of Mobile Device Hataichanok
2008 International Conference on Computer and Electrical Engineering User Authentication using Combination of Behavioral Biometrics over the Touchpad acting like Touch screen of Mobile Device Hataichanok
Barcode Based Automated Parking Management System
 IJSRD - International Journal for Scientific Research & Development Vol. 2, Issue 03, 2014 ISSN (online): 2321-0613 Barcode Based Automated Parking Management System Parth Rajeshbhai Zalawadia 1 Jasmin
IJSRD - International Journal for Scientific Research & Development Vol. 2, Issue 03, 2014 ISSN (online): 2321-0613 Barcode Based Automated Parking Management System Parth Rajeshbhai Zalawadia 1 Jasmin
22 nd NISS Conference
 22 nd NISS Conference Submission: Topic: Keywords: Author: Organization: Tutorial BIOMETRICS - DEVELOPING THE ARCHITECTURE, API, ENCRYPTION AND SECURITY. INSTALLING & INTEGRATING BIOMETRIC SYSTEMS INTO
22 nd NISS Conference Submission: Topic: Keywords: Author: Organization: Tutorial BIOMETRICS - DEVELOPING THE ARCHITECTURE, API, ENCRYPTION AND SECURITY. INSTALLING & INTEGRATING BIOMETRIC SYSTEMS INTO
A PHOTOGRAMMETRIC APPRAOCH FOR AUTOMATIC TRAFFIC ASSESSMENT USING CONVENTIONAL CCTV CAMERA
 A PHOTOGRAMMETRIC APPRAOCH FOR AUTOMATIC TRAFFIC ASSESSMENT USING CONVENTIONAL CCTV CAMERA N. Zarrinpanjeh a, F. Dadrassjavan b, H. Fattahi c * a Islamic Azad University of Qazvin - nzarrin@qiau.ac.ir
A PHOTOGRAMMETRIC APPRAOCH FOR AUTOMATIC TRAFFIC ASSESSMENT USING CONVENTIONAL CCTV CAMERA N. Zarrinpanjeh a, F. Dadrassjavan b, H. Fattahi c * a Islamic Azad University of Qazvin - nzarrin@qiau.ac.ir
Application of Face Recognition to Person Matching in Trains
 Application of Face Recognition to Person Matching in Trains May 2008 Objective Matching of person Context : in trains Using face recognition and face detection algorithms With a video-surveillance camera
Application of Face Recognition to Person Matching in Trains May 2008 Objective Matching of person Context : in trains Using face recognition and face detection algorithms With a video-surveillance camera
MACHINE VISION MNEMONICS, INC. 102 Gaither Drive, Suite 4 Mount Laurel, NJ 08054 USA 856-234-0970 www.mnemonicsinc.com
 MACHINE VISION by MNEMONICS, INC. 102 Gaither Drive, Suite 4 Mount Laurel, NJ 08054 USA 856-234-0970 www.mnemonicsinc.com Overview A visual information processing company with over 25 years experience
MACHINE VISION by MNEMONICS, INC. 102 Gaither Drive, Suite 4 Mount Laurel, NJ 08054 USA 856-234-0970 www.mnemonicsinc.com Overview A visual information processing company with over 25 years experience
Keywords Input Images, Damage face images, Face recognition system, etc...
 Volume 5, Issue 4, 2015 ISSN: 2277 128X International Journal of Advanced Research in Computer Science and Software Engineering Research Paper Available online at: www.ijarcsse.com A Research - Face Recognition
Volume 5, Issue 4, 2015 ISSN: 2277 128X International Journal of Advanced Research in Computer Science and Software Engineering Research Paper Available online at: www.ijarcsse.com A Research - Face Recognition
Robust Real-Time Face Detection
 Robust Real-Time Face Detection International Journal of Computer Vision 57(2), 137 154, 2004 Paul Viola, Michael Jones 授 課 教 授 : 林 信 志 博 士 報 告 者 : 林 宸 宇 報 告 日 期 :96.12.18 Outline Introduction The Boost
Robust Real-Time Face Detection International Journal of Computer Vision 57(2), 137 154, 2004 Paul Viola, Michael Jones 授 課 教 授 : 林 信 志 博 士 報 告 者 : 林 宸 宇 報 告 日 期 :96.12.18 Outline Introduction The Boost
Face Recognition Application for Automatic Teller Machines (ATM)
 2012 International Conference on Information and Knowledge Management (ICIKM 2012) IPCSIT vol.45 (2012) (2012) IACSIT Press, Singapore Face Recognition Application for Automatic Teller Machines (ATM) Hossein
2012 International Conference on Information and Knowledge Management (ICIKM 2012) IPCSIT vol.45 (2012) (2012) IACSIT Press, Singapore Face Recognition Application for Automatic Teller Machines (ATM) Hossein
REAL TIME TRAFFIC LIGHT CONTROL USING IMAGE PROCESSING
 REAL TIME TRAFFIC LIGHT CONTROL USING IMAGE PROCESSING Ms.PALLAVI CHOUDEKAR Ajay Kumar Garg Engineering College, Department of electrical and electronics Ms.SAYANTI BANERJEE Ajay Kumar Garg Engineering
REAL TIME TRAFFIC LIGHT CONTROL USING IMAGE PROCESSING Ms.PALLAVI CHOUDEKAR Ajay Kumar Garg Engineering College, Department of electrical and electronics Ms.SAYANTI BANERJEE Ajay Kumar Garg Engineering
A Real Time Hand Tracking System for Interactive Applications
 A Real Time Hand Tracking System for Interactive Applications Siddharth Swarup Rautaray Indian Institute of Information Technology Allahabad ABSTRACT In vision based hand tracking systems color plays an
A Real Time Hand Tracking System for Interactive Applications Siddharth Swarup Rautaray Indian Institute of Information Technology Allahabad ABSTRACT In vision based hand tracking systems color plays an
Open-Set Face Recognition-based Visitor Interface System
 Open-Set Face Recognition-based Visitor Interface System Hazım K. Ekenel, Lorant Szasz-Toth, and Rainer Stiefelhagen Computer Science Department, Universität Karlsruhe (TH) Am Fasanengarten 5, Karlsruhe
Open-Set Face Recognition-based Visitor Interface System Hazım K. Ekenel, Lorant Szasz-Toth, and Rainer Stiefelhagen Computer Science Department, Universität Karlsruhe (TH) Am Fasanengarten 5, Karlsruhe
Android-Based Mobile Payment System Using 3 Factor Authentication
 Android-Based Mobile Payment System Using 3 Factor Authentication Saurabh Yadav 1, Pranali Patil 2, Mahesh Shinde 3, Priyanka Rane 4 1 Saurabh Yadav (BE Comp S.N.D COE & RC, YEOLA) 2 Pranali Patil (BE
Android-Based Mobile Payment System Using 3 Factor Authentication Saurabh Yadav 1, Pranali Patil 2, Mahesh Shinde 3, Priyanka Rane 4 1 Saurabh Yadav (BE Comp S.N.D COE & RC, YEOLA) 2 Pranali Patil (BE
A Learning Based Method for Super-Resolution of Low Resolution Images
 A Learning Based Method for Super-Resolution of Low Resolution Images Emre Ugur June 1, 2004 emre.ugur@ceng.metu.edu.tr Abstract The main objective of this project is the study of a learning based method
A Learning Based Method for Super-Resolution of Low Resolution Images Emre Ugur June 1, 2004 emre.ugur@ceng.metu.edu.tr Abstract The main objective of this project is the study of a learning based method
The Scientific Data Mining Process
 Chapter 4 The Scientific Data Mining Process When I use a word, Humpty Dumpty said, in rather a scornful tone, it means just what I choose it to mean neither more nor less. Lewis Carroll [87, p. 214] In
Chapter 4 The Scientific Data Mining Process When I use a word, Humpty Dumpty said, in rather a scornful tone, it means just what I choose it to mean neither more nor less. Lewis Carroll [87, p. 214] In
A Behavioral Biometric Approach Based on Standardized Resolution in Mouse Dynamics
 370 IJCSNS International Journal of Computer Science and Network Security, VOL.9 No.4, April 2009 A Behavioral Biometric Approach Based on Standardized Resolution in Mouse Dynamics S.Benson Edwin Raj Assistant
370 IJCSNS International Journal of Computer Science and Network Security, VOL.9 No.4, April 2009 A Behavioral Biometric Approach Based on Standardized Resolution in Mouse Dynamics S.Benson Edwin Raj Assistant
Recognition of Single Handed Sign Language Gestures using Contour Tracing Descriptor
 , July 3-5, 2013, London, U.K. Recognition of Single Handed Sign Language Gestures using Contour Tracing Descriptor Rohit Sharma, Yash Nemani, Sumit Kumar, Lalit Kane, Pritee Khanna, Member, IAENG Abstract
, July 3-5, 2013, London, U.K. Recognition of Single Handed Sign Language Gestures using Contour Tracing Descriptor Rohit Sharma, Yash Nemani, Sumit Kumar, Lalit Kane, Pritee Khanna, Member, IAENG Abstract
AN IMPROVED DOUBLE CODING LOCAL BINARY PATTERN ALGORITHM FOR FACE RECOGNITION
 AN IMPROVED DOUBLE CODING LOCAL BINARY PATTERN ALGORITHM FOR FACE RECOGNITION Saurabh Asija 1, Rakesh Singh 2 1 Research Scholar (Computer Engineering Department), Punjabi University, Patiala. 2 Asst.
AN IMPROVED DOUBLE CODING LOCAL BINARY PATTERN ALGORITHM FOR FACE RECOGNITION Saurabh Asija 1, Rakesh Singh 2 1 Research Scholar (Computer Engineering Department), Punjabi University, Patiala. 2 Asst.
ARM 9 BASED REAL TIME CONTROL AND VEHICLE THEFT IDENTITY SYSTEM
 ARM 9 BASED REAL TIME CONTROL AND VEHICLE THEFT IDENTITY SYSTEM Ms. Radhika D. Rathi 1, Assistant Prof. Ashish Mulajkar 2, Assistant Prof. S. S. Badhe 3 1 Student, E&TCDepartment, Dr.D.Y.Patil School of
ARM 9 BASED REAL TIME CONTROL AND VEHICLE THEFT IDENTITY SYSTEM Ms. Radhika D. Rathi 1, Assistant Prof. Ashish Mulajkar 2, Assistant Prof. S. S. Badhe 3 1 Student, E&TCDepartment, Dr.D.Y.Patil School of
Vision based Vehicle Tracking using a high angle camera
 Vision based Vehicle Tracking using a high angle camera Raúl Ignacio Ramos García Dule Shu gramos@clemson.edu dshu@clemson.edu Abstract A vehicle tracking and grouping algorithm is presented in this work
Vision based Vehicle Tracking using a high angle camera Raúl Ignacio Ramos García Dule Shu gramos@clemson.edu dshu@clemson.edu Abstract A vehicle tracking and grouping algorithm is presented in this work
