RECOVERABILITY Policy Number: 4.07
|
|
|
- Timothy Marsh
- 8 years ago
- Views:
Transcription
1 Policy Name: DATA SYSTEM BACKUP AND RECOVERABILITY Policy Number: 4.07 Reference: contract Effective Date: 4/2004 Revision Date(s): 3/2014 Reviewed Date: 12/2014 Approved by: PRSN Executive Board CROSS REFERENCES Plan: PRSN Disaster Response Plan Policy: Corrective Action Plans PURPOSE To ensure the Peninsula Regional Support Network (PRSN) data stored electronically is adequately backed up and plans in place to provide recoverability due to data corruption or a regional computer system failure. Mission and Scope The purpose of this policy is to ensure that all Kitsap Mental Health Services and Peninsula RSN business (IT) activities can be kept at normal or near-normal performance following an incident that has the potential to disrupt or destroy the IT infrastructure. The scope of this policy is staff and clients at Kitsap Mental Health Services as well as clinical IT functions for Peninsula Regional Support Network and all network providers (Jefferson Mental Health Services in Port Townsend, WA, Peninsula Behavioral Health in Port Angeles and West End Outreach Services in Forks, WA). Background The Peninsula Regional Support Network contracts with Kitsap Mental Health Services (KMHS) to operate and maintain the data system used by all network contractors within the PRSN. The system uses ProFiler/UNICARE software. All PRSN network providers are connected to the data system through either a VPN or a secure Point to Point T1 data connection. KMHS is responsible for maintaining the network, and transmitting required data to the Department of Social and Health Services Mental Health Division.
2 PROCEDURE Preparedness Because of the potential risk and ongoing vulnerability to loss of data, the KMHS Information Services Department has in place a backup and storage policy and procedure that is practiced every working day. These backup procedures would allow KMHS and the other network providers within the PRSN to retrieve critical information necessary for the conduct of business functions on an immediate basis, and ultimately allow a full restoration of the data system given a catastrophic failure. Backups KMHS subscribes to the Barracuda Backup service. This allows storage of backup data on a local device/hardware AND transfers copies of this data to the secure Barracuda system with retentions based on custom setup. Data backups are performed daily and at least one copy of that backup is stored on the Barracuda device locally. Items are also transferred off-site (electronically) and stored based on the retention policy defined within this document. 1. Bootable backup: Frequency: Each time any updates or changes are made to the system Copies: Two Storage: IS Lockbox (on-site), designated off-site location 2. Daily backup: Database File Specifics: Production database and files (SR for State Reporting and UNICARE1) are backed up by SQL Server jobs each night beginning at 1200 midnight. One day is maintained on the SQL server (D:/BULive directory) to allow for fast recovery. Barracuda retention: 7 Days. Frequency: 1:30 a.m.
3 System files Specifics: Images of at least one Application Server, Terminal Server and Automation Manager Systems are contained within the nightly backup for quick restoration should it be needed. 3. Situational backup: Prior to any major version upgrade to the system(s). These database and images are written to the \\NAS-1\IS-DOCS\Disaster Plan\Recovery Files for backup retention.
4 Hard Copy Reports Should temporary manual operations be required, monthly reports (data as identified in the Disaster Recovery Plan) from the data system will be written to NAS-1\IS- DOCS\Disaster Plan\RecoveryFiles\ that can be accessed from the off-site Barracuda files and opened in Word or Excel. System Restoration and Recovery Critical Need The following functions have been identified as critical: Transfer of information to WA State. This includes new data as well as any researched and corrected data. Data is sent directly via the site (logging into the PRSN domain ) or via the Provider One secure FTP site (sftp:waproviderone.org). Should the preferred secure VPN connection to MHD be unavailable for transfer (for more than 1 week), the following alternative method shall be used to deliver files to the state - files will be transferred to an external device (such as encrypted flash or CD) and delivered to MHD in person. Basic client information. This includes information such as the next 30 days scheduled appointments, client contact/ location information, caseload lists. Data will be downloaded monthly from ProFiler and written to a location in NAS-1\IS- DOCS\Disaster Plan\RecoveryFiles\ that can be accessed from the off-site Barracuda files and opened in Word or Excel. IS inventory, application and vendor information. This includes a current server inventory, IP and server listing as well as critical vendor and licensing data (i.e. Microsoft Volume Licensing login information, ProFiler and GP contract information, etc.) These are stored to NAS-1\IS-DOCS\Disaster Plan\RecoveryFiles\ that can be accessed from the off-site Barracuda files and opened in Word or Excel. PRSN eligibility data from the State on a weekly basis. The databases (Access stored on NAS-1\IS-DOCS\Projects\elig\Provider One Processing\WA_CAID_Elig_Import_2014 Access database and P1_SQL_Prod on the DW server) containing the eligibility information is backed up within the standard nightly backup at KMHS. KMHS Only: Payroll, Accounts Receivable, Protective Payee and Accounts Payable are contained within the KMHS GP/Dynamics database residing on MOOLAH server. o Backups are each weekday (M-F) beginning at 8p.m. o The two most recent backups are maintained on the MOOLAH server, E:\Backups directory (KMHS and PAYEE databases).
5 Reports of information that will be updated on NAS-1\IS-DOCS\Disaster Plan\RecoveryFiles\ that can be opened/used in Excel or MS Word o Payroll: Listing of staff pay scales, FTE, deductions (CMHC Report ACSTFALL) weekly reports. o Accounts Receivable: Listing of client balances from each funding source (AR Aging Report from ProFiler) o Protective Payee: Listing of current balances and check details for current FY. o Accounts Payable: Listing of vendors and Journal Detail/General Ledger information for the current FY. All other services could be deferred to the recovery stage. Recovery All recovery steps described in this policy will be assigned to available/appropriate personnel by the KMHS IS Director (Tracy Thompson, or ) or designee. During any scheduled absence from duty, a designee will be identified in advance of the absence. In the event of unscheduled absences, the following KMHS IS staff will be assigned designee (in order of priority: Financial Analyst, System Integration Analyst, Systems Analyst). Contact information is contained in \\NAS-1\IS- DOCS\Disaster Plan\RecoveryFiles\IS Emergency Contacts.docx and a hard-copy is maintained in the IS Safe. The main impacts of catastrophic loss of computer equipment or extended delays in resuming full processing capacity would be delays in financial and statistical procedures, reports and backlogs of client and activity information to be entered. This would not affect services to the public following an emergency, but could have effect to the provider financial stability and ability to determine impact.
6 1. The provider information systems would face difficulties in returning to full production in the face of backlogs, if the system were unavailable for more than one month, under normal circumstances. Staff shortage and unusual demand for services would make the need more critical. Business department needs would be given first priority if computer access were limited. 2. Finance could tolerate a 1-2 month delay, depending on the timing of checks to be processed. Use of On-Line Terminals during and after a system failure or natural disaster Responsibilities The most critical computer functions will be assigned to any computers that remain online at KMHS. First Priority 1. Verify that the ProFiler and GP systems are still functioning safely, and will have a source of continuous power. a. Physically inspect the computer room and status of UPS. b. An Information Systems staff (usually the IS Director) at Kitsap Mental Health Services will determine if the computer must be shut down. 2. Verify that computer locations function properly and the areas are safe to work in. Second Priority 1. After critical needs are met, allocate access for emergency use by Jefferson Mental Health, West End Outreach, Peninsula Behavioral Health and/or Peninsula Regional Support Network/CommCare staff at Kitsap Mental Health Services locations. 2. Information Services staff from Kitsap Mental Health Services will be assigned to assist each site staff at KMH locations as needed. Use of a Portable Computer as a Terminal during and after a system failure or natural disaster Responsibilities A PC may be assigned to assist in recovery. The PC must be equipped with access to a high speed Internet to connect to the PRSN VPN/Gateweay system. First Priority 1. If the Information Services offices are inaccessible, but the ProFiler, GP systems are working, assign at least one laptop. a. Set up laptop in location with electricity and data connectivity (WiFi or Ethernet).
7 Peninsula RSN Policies and Procedures b. Ensure a secure Internet connection with the KMHS network using RDP to desktop or ProFiler via Gateway connection to gw.kmhs.org (see instruction at end of this document). Second Priority 1. After critical needs are met, allocate existing access to Jefferson Mental Health, West End Outreach and Peninsula Community Mental Health staff for maintaining data processing. Connection to and use of a CoCentrix HOT SITE during and after a system failure or natural disaster. Responsibilities Critical services for clients must be maintained by extracting or entering data in the system. If the ProFiler system is not running, an emergency backup may be run at another location. Depending upon the disaster, hot sites would include CoCentrix Inc. in Sarasota, FL, Valley Cities in Kent, WA and Frontier Mental Health in Spokane, WA. Both of these sites have been contacted and agree to provide this service in a disaster. There would be costs associated with this hot site usage that would require negotiation at the time of the need. First Priority 1. Data necessary for direct client services. a. Retrieve most recent ProFiler backup from the Barracuda off-site storage. 2. Depending on location, have staff at hot site log on and print reports designated in the Critical Need section of this document. Second Priority If staff may sustain access to the hot site, the following functions may be run, depending on time and equipment available. 1. Additional lists of staff or client or billing reports for urgent needs. 2. Data lookups or updates for service to existing clients. 3. New client registrations and services. Connection to and use of a Dynamics GP HOT SITE during and after a system failure or natural disaster. Responsibilities Critical services for financial needs of the agency must be maintained by extracting or entering data in the system. If the Dynamics GP system is not running, an emergency backup may be run at another location. Hot sites can be any SQL Server system and a local PC (client software can load on any Windows 7 or above workstation). Potential hot sites would include The Resource Group or Seitel Systems in Seattle, WA but any physical or cloud-based system could be used. There would be costs associated with this hot site usage that would require negotiation at the time of the need.
8 First Priority 1. Data necessary for emergency payments. b. Retrieve most recent GP (KMHS DB) and NAS-1 backup from the Barracuda off-site storage. 2. Data needed to provide Client balance, account information c. Retrieve most recent GP (PAYEE DB) and NAS-1 backup from the Barracuda off-site storage. 3. Depending on location, have staff at hot site log on and process payments as needed and pull designated in the Critical Need section of this document. Information Services Evacuation Plan During a Natural Disaster The following actions should be taken by KMHS IS staff upon evacuation and/or other assigned disaster prep staff upon assignment: Upon initial evacuation: IS Staff from room 508 (located on KMHS main campus) will take contents of the lockbox. This lock box is located in room 508, by door. This lock box contains: 1. Agency master key 2. Safe combination (for safe located at Sheridan facility) 3. Up-to-date IS, Agency, Cell Phone and vendor POC listing 4. Recovery procedures (data/programs, etc) Upon re-entrance/secure actions: 1. If power is on and water is present in room 508 or computer room, power should be secured via the circuit breakers. Any circuit breaker work must be coordinated with KMHS Facilities staff. 2. If power is on and water is present in phone equipment room, power should be secured via the circuit breakers. Any circuit breaker work must be coordinated with KMHS Facilities staff. 3. If additional threat, the safe located at 900 Sheridan (Bremerton, WA) should be removed from area as soon as possible.
9 How to Connect Remotely to Profiler from home: First you must find your remote desktop connection for your version of Windows. Usually this can be found under Start ->All Programs -> Accessories -> Remote Desktop Connection (see screen shots below for Windows 7): First: 1. Go to START and then All Programs. 2. Click on Accessories 3. Click on Remote Desktop Connection (Tip: If you right click and then choose send to desktop this will create a shortcut to Remote Desktop Connection on your desktop for future use)
10 4. Once you have located the Remote Desktop Connection, click on it and the window that pops up should look something like what you see below. Next, click on Show Options to expand this window 5. Fill out the #1 (Computer: ProFilerFarm.kmhs.org) and #2 as indicated below (please substitute your own user login that you use at KMHS after KITSAP.COM. Then click on the Advanced button (#3 below).
11
12 6. Next click on the Settings button (#4) and you will get a new window Peninsula RSN Policies and Procedures
13 7. Next fill in the following per the screen shot below and then click ok. Peninsula RSN Policies and Procedures 8. Now you will be back on the Advanced tab. You will now need to click on the General tab to get back to the beginning once again.
14 9. You should now be able to hit the Connect button (at the bottom) and you will now connect to a one of our servers
15 10. You will now be presented with a box that is asking you for your credentials. These are your user name and password used at KMHS. Please follow the same format outlined in step #5 above by using kitsap.com\username (For example: kitsap.com\judys). Then put in your regular password and hit enter and it should now bring you to the desktop on one of our servers. Once on the desktop you should be able to locate the Profiler icon to be able to get into Profiler. MONITORING 1. This policy is mandated by contract. This policy will be monitored by the PRSN by the following means: Kitsap Mental Health Services and the PRSN will debrief any extended downtime and/or restoration action and resolve problems identified. Annual EQRO audits and findings. The PRSN will follow-up with any assigned corrective action requirements. Annual PRSN Subdelegation Review of the regional IS system
16 4. If KMHS performs below expected standards during any of the reviews listed above a Corrective Action will be required for PRSN approval. Because KMHS contractually provides the PIHP regional Information System, the PRSN has the ability to impose penalties, modify the Subdelegation contract, or decide to not continue to contract.
17 Addendum 1- KMHS IS Staff Contact Information IS STAFFING AND RECOVERY RESPONSIBILITIES 1. All Staff have been instructed to contact Tracy Thompson for the following assigned duties: If staff are unable to contact Tracy, they have been instructed to call their office phone numbers to communicate (pick-up and leave messages for her and other team members). Tracy Thompson, IS Director Overall management and oversight of the recovery. This is the first staff to be contacted. She will direct all other staff with specific recovery actions. Office Cell Tracy maintains a list of personal contact information for all of the IS staff list- not available for distribution. Network/Phones/Hardware Jim Reichel, Telecommunications/Network Technician - Network and hardware recovery. Office Paul Benter, System Administrator/Technician Network and hardware recovery. Office Database for UNI/CARE (ProFiler) and CMHC Note specialties: Mary Anne Miller, Lead Systems Analyst Billing, Payroll, Encounters, Eligibility Office Beth Heinz, Systems Analyst Clinical systems Office Cynthia Wooten, Systems Analyst Medical services, Transcription, InPatient data Office Emily Pechia, Data Specialist - Data validation Office Adrienne Sablan, EMR Clinical Help Desk Communication with users Office
User Guide Microsoft Exchange Remote Test Instructions
 User Guide Microsoft Exchange Remote Test Instructions University of Louisville Information Technology 1.1 Who Should Use It This guide is intended for University of Louisville Faculty and Staff participating
User Guide Microsoft Exchange Remote Test Instructions University of Louisville Information Technology 1.1 Who Should Use It This guide is intended for University of Louisville Faculty and Staff participating
Tailored Technologies LLC
 685 Third Avenue New York, NY 10017 Tel: (212) 503-6300 Fax: (212) 503-6312 Date: January 9, 2014 To: The Audit File of the Hugh L. Carey Battery Park City Authority From: Tailored Technology Observations
685 Third Avenue New York, NY 10017 Tel: (212) 503-6300 Fax: (212) 503-6312 Date: January 9, 2014 To: The Audit File of the Hugh L. Carey Battery Park City Authority From: Tailored Technology Observations
Managed Security Services SLA Document. Response and Resolution Times
 Managed Security Services SLA Document Appendix A Response and Resolution Times The following table shows the targets of response and resolution times for each priority level: Trouble Priority Response
Managed Security Services SLA Document Appendix A Response and Resolution Times The following table shows the targets of response and resolution times for each priority level: Trouble Priority Response
How To Backup An Exchange Server With 25Gb And More On A Microsoft Smartfiler With A Backup From A Backup To A Backup Point Set On A Flash Drive On A Pc Or Macbook Or Ipad On A Cheap Computer (For A
 Using SmartFiler for Microsoft Exchange Server Backup Introduction The SmartFiler Backup Appliance Exchange Server backup solution is integrated with the Symantec Backup Exec System Recovery 2010. Using
Using SmartFiler for Microsoft Exchange Server Backup Introduction The SmartFiler Backup Appliance Exchange Server backup solution is integrated with the Symantec Backup Exec System Recovery 2010. Using
HOW TO CONFIGURE SQL SERVER REPORTING SERVICES IN ORDER TO DEPLOY REPORTING SERVICES REPORTS FOR DYNAMICS GP
 HOW TO CONFIGURE SQL SERVER REPORTING SERVICES IN ORDER TO DEPLOY REPORTING SERVICES REPORTS FOR DYNAMICS GP When you install SQL Server you have option to automatically deploy & configure SQL Server Reporting
HOW TO CONFIGURE SQL SERVER REPORTING SERVICES IN ORDER TO DEPLOY REPORTING SERVICES REPORTS FOR DYNAMICS GP When you install SQL Server you have option to automatically deploy & configure SQL Server Reporting
How to remotely access your Virtual Desktop from outside the college using VMware View Client. How to guide
 How to remotely access your Virtual Desktop from outside the college using VMware View Client How to guide Author: ICT Services Version: 1.0 Date: November 2015 Contents What is the VMware View Client?...
How to remotely access your Virtual Desktop from outside the college using VMware View Client How to guide Author: ICT Services Version: 1.0 Date: November 2015 Contents What is the VMware View Client?...
EMR Link Server Interface Installation
 EMR Link Server Interface Installation Version 1.0 ** INTRODUCTION ** If you would like assistance with installation, please contact our preferred support provider at support@bonecomputer.com, or call
EMR Link Server Interface Installation Version 1.0 ** INTRODUCTION ** If you would like assistance with installation, please contact our preferred support provider at support@bonecomputer.com, or call
For Mac User Directions, see page 5
 Windows Vista, Windows 7, and Windows XP with Service Pack 3 Remote Desktop Access For Mac User Directions, see page 5 This instruction allows district staff and students to access the Commack UFSD network
Windows Vista, Windows 7, and Windows XP with Service Pack 3 Remote Desktop Access For Mac User Directions, see page 5 This instruction allows district staff and students to access the Commack UFSD network
Remote Desktop access via Faculty Terminal Server Using Internet Explorer (versions 5.x-7.x)
 Remote Desktop access via Faculty Terminal Server Using Internet Explorer (versions 5.x-7.x) Start your Internet Explorer browser and direct it to the faculty home page. Click on the link Remote Access,
Remote Desktop access via Faculty Terminal Server Using Internet Explorer (versions 5.x-7.x) Start your Internet Explorer browser and direct it to the faculty home page. Click on the link Remote Access,
System Management. What are my options for deploying System Management on remote computers?
 Getting Started, page 1 Managing Assets, page 2 Distributing Software, page 3 Distributing Patches, page 4 Backing Up Assets, page 5 Using Virus Protection, page 6 Security, page 7 Getting Started What
Getting Started, page 1 Managing Assets, page 2 Distributing Software, page 3 Distributing Patches, page 4 Backing Up Assets, page 5 Using Virus Protection, page 6 Security, page 7 Getting Started What
Contents. Instructions for Using Online HIPAA Security Plan Generation Tool
 Instructions for Using Online HIPAA Security Plan Generation Tool Contents Step 1 Set Up Account... 2 Step 2 : Fill out the main section of the practice information section of the web site.... 3 The next
Instructions for Using Online HIPAA Security Plan Generation Tool Contents Step 1 Set Up Account... 2 Step 2 : Fill out the main section of the practice information section of the web site.... 3 The next
SSL VPN Setup for Windows
 SSL VPN Setup for Windows SSL VPN allows you to connect from off campus to access campus resources such as Outlook email client, file sharing and remote desktop. These instructions will guide you through
SSL VPN Setup for Windows SSL VPN allows you to connect from off campus to access campus resources such as Outlook email client, file sharing and remote desktop. These instructions will guide you through
FAQ - Frequently Asked Questions Sections of Questions
 FAQ - Frequently Asked Questions Sections of Questions Bell Business Backup Service Installation & Setup Firewall Settings Connections & Backups Account Information Restoring Files Uninstalling the Bell
FAQ - Frequently Asked Questions Sections of Questions Bell Business Backup Service Installation & Setup Firewall Settings Connections & Backups Account Information Restoring Files Uninstalling the Bell
Hosting Users Guide 2011
 Hosting Users Guide 2011 eofficemgr technology support for small business Celebrating a decade of providing innovative cloud computing services to small business. Table of Contents Overview... 3 Configure
Hosting Users Guide 2011 eofficemgr technology support for small business Celebrating a decade of providing innovative cloud computing services to small business. Table of Contents Overview... 3 Configure
How To Write A Health Care Security Rule For A University
 INTRODUCTION HIPAA Security Rule Safeguards Recommended Standards Developed by: USF HIPAA Security Team May 12, 2005 The Health Insurance Portability and Accountability Act (HIPAA) Security Rule, as a
INTRODUCTION HIPAA Security Rule Safeguards Recommended Standards Developed by: USF HIPAA Security Team May 12, 2005 The Health Insurance Portability and Accountability Act (HIPAA) Security Rule, as a
SmartFiler Backup Appliance User Guide 2.0
 SmartFiler Backup Appliance User Guide 2.0 SmartFiler Backup Appliance User Guide 1 Table of Contents Overview... 5 Solution Overview... 5 SmartFiler Backup Appliance Overview... 5 Getting Started... 7
SmartFiler Backup Appliance User Guide 2.0 SmartFiler Backup Appliance User Guide 1 Table of Contents Overview... 5 Solution Overview... 5 SmartFiler Backup Appliance Overview... 5 Getting Started... 7
ACS Backup and Restore
 Table of Contents Implementing a Backup Plan 3 What Should I Back Up? 4 Storing Data Backups 5 Backup Media 5 Off-Site Storage 5 Strategies for Successful Backups 7 Daily Backup Set A and Daily Backup
Table of Contents Implementing a Backup Plan 3 What Should I Back Up? 4 Storing Data Backups 5 Backup Media 5 Off-Site Storage 5 Strategies for Successful Backups 7 Daily Backup Set A and Daily Backup
Setting Up Monthly Reporter
 Setting Up Monthly Reporter April 11, 2014 I. HOW IT WORKS A QUICK OVERVIEW A. AuditWare Development Company maintains a powerful, sophisticated server on which a portion of memory is assigned to each
Setting Up Monthly Reporter April 11, 2014 I. HOW IT WORKS A QUICK OVERVIEW A. AuditWare Development Company maintains a powerful, sophisticated server on which a portion of memory is assigned to each
Reflection DBR USER GUIDE. Reflection DBR User Guide. 995 Old Eagle School Road Suite 315 Wayne, PA 19087 USA 610.964.8000 www.evolveip.
 Reflection DBR USER GUIDE 995 Old Eagle School Road Suite 315 Wayne, PA 19087 USA 610.964.8000 www.evolveip.net Page 1 of 1 Table of Contents Overview 3 Reflection DBR Client and Console Installation 4
Reflection DBR USER GUIDE 995 Old Eagle School Road Suite 315 Wayne, PA 19087 USA 610.964.8000 www.evolveip.net Page 1 of 1 Table of Contents Overview 3 Reflection DBR Client and Console Installation 4
User Guide. CTERA Agent. August 2011 Version 3.0
 User Guide CTERA Agent August 2011 Version 3.0 Copyright 2009-2011 CTERA Networks Ltd. All rights reserved. No part of this document may be reproduced in any form or by any means without written permission
User Guide CTERA Agent August 2011 Version 3.0 Copyright 2009-2011 CTERA Networks Ltd. All rights reserved. No part of this document may be reproduced in any form or by any means without written permission
Supplier Information Security Addendum for GE Restricted Data
 Supplier Information Security Addendum for GE Restricted Data This Supplier Information Security Addendum lists the security controls that GE Suppliers are required to adopt when accessing, processing,
Supplier Information Security Addendum for GE Restricted Data This Supplier Information Security Addendum lists the security controls that GE Suppliers are required to adopt when accessing, processing,
Data Backup and Restore (DBR) Overview... 2. Detailed Description... 3. Pricing... 5 SLAs... 5 Service Matrix... 6. Service Description
 Service Description Data Backup and Restore (DBR) Terremark s Data Backup & Restore provides secure, streamlined online-offsite data storage and retrieval that is highly scalable and easily customizable.
Service Description Data Backup and Restore (DBR) Terremark s Data Backup & Restore provides secure, streamlined online-offsite data storage and retrieval that is highly scalable and easily customizable.
How to Access Coast Wi-Fi
 How to Access Coast Wi-Fi Below is a summary of the information required to configure your device to connect to the coast-wifi network. For further assistance in configuring your specific device, continue
How to Access Coast Wi-Fi Below is a summary of the information required to configure your device to connect to the coast-wifi network. For further assistance in configuring your specific device, continue
User Guide. Database Backup Procedures for MS SQL Server 2005 Express
 User Guide Database Backup Procedures for MS SQL Server 2005 Express System Galaxy-8 Software Addendum Documentation SG Version 8 January, 2008 ~ i ~ System Galaxy Version 8 Software Addendum Information
User Guide Database Backup Procedures for MS SQL Server 2005 Express System Galaxy-8 Software Addendum Documentation SG Version 8 January, 2008 ~ i ~ System Galaxy Version 8 Software Addendum Information
Remote Desktop Gateway. Accessing a Campus Managed Device (Windows Only) from home.
 Remote Desktop Gateway Accessing a Campus Managed Device (Windows Only) from home. Contents Introduction... 2 Quick Reference... 2 Gateway Setup - Windows Desktop... 3 Gateway Setup Windows App... 4 Gateway
Remote Desktop Gateway Accessing a Campus Managed Device (Windows Only) from home. Contents Introduction... 2 Quick Reference... 2 Gateway Setup - Windows Desktop... 3 Gateway Setup Windows App... 4 Gateway
Setting Up Your ECi Remote Backup Solution
 Setting Up Your ECi Remote Backup Solution April 2010 Rev. 1 Contents Introduction... 3 Implementing the Remote Backup Solution... 4 Using the Avamar Client Software... 5 Restoring a Backup... 5 2 Introduction
Setting Up Your ECi Remote Backup Solution April 2010 Rev. 1 Contents Introduction... 3 Implementing the Remote Backup Solution... 4 Using the Avamar Client Software... 5 Restoring a Backup... 5 2 Introduction
SAO Remote Access POLICY
 SAO Remote Access POLICY Contents PURPOSE... 4 SCOPE... 4 POLICY... 4 AUTHORIZATION... 4 PERMITTED FORMS OF REMOTE ACCESS... 5 REMOTE ACCESS USER DEVICES... 5 OPTION ONE: SAO-OWNED PC... 5 OPTION TWO:
SAO Remote Access POLICY Contents PURPOSE... 4 SCOPE... 4 POLICY... 4 AUTHORIZATION... 4 PERMITTED FORMS OF REMOTE ACCESS... 5 REMOTE ACCESS USER DEVICES... 5 OPTION ONE: SAO-OWNED PC... 5 OPTION TWO:
NETWORK SERVICES WITH SOME CREDIT UNIONS PROCESSING 800,000 TRANSACTIONS ANNUALLY AND MOVING OVER 500 MILLION, SYSTEM UPTIME IS CRITICAL.
 NETWORK SERVICES WITH SOME CREDIT UNIONS PROCESSING 800,000 TRANSACTIONS ANNUALLY AND MOVING OVER 500 MILLION, SYSTEM UPTIME IS CRITICAL. Your Credit Union information is irreplaceable. Data loss can result
NETWORK SERVICES WITH SOME CREDIT UNIONS PROCESSING 800,000 TRANSACTIONS ANNUALLY AND MOVING OVER 500 MILLION, SYSTEM UPTIME IS CRITICAL. Your Credit Union information is irreplaceable. Data loss can result
VIPERVAULT STORAGECRAFT SHADOWPROTECT SETUP GUIDE
 VIPERVAULT STORAGECRAFT SHADOWPROTECT SETUP GUIDE Solution Overview Thank you for choosing the ViperVault cloud replication, backup and disaster recovery service. Using this service you can replicate your
VIPERVAULT STORAGECRAFT SHADOWPROTECT SETUP GUIDE Solution Overview Thank you for choosing the ViperVault cloud replication, backup and disaster recovery service. Using this service you can replicate your
ScoMIS Encryption Service
 Introduction This guide explains how to install the ScoMIS Encryption Service Software onto a laptop computer. There are three stages to the installation which should be completed in order. The installation
Introduction This guide explains how to install the ScoMIS Encryption Service Software onto a laptop computer. There are three stages to the installation which should be completed in order. The installation
LAMAR STATE COLLEGE - ORANGE INFORMATION RESOURCES SECURITY MANUAL. for INFORMATION RESOURCES
 LAMAR STATE COLLEGE - ORANGE INFORMATION RESOURCES SECURITY MANUAL for INFORMATION RESOURCES Updated: June 2007 Information Resources Security Manual 1. Purpose of Security Manual 2. Audience 3. Acceptable
LAMAR STATE COLLEGE - ORANGE INFORMATION RESOURCES SECURITY MANUAL for INFORMATION RESOURCES Updated: June 2007 Information Resources Security Manual 1. Purpose of Security Manual 2. Audience 3. Acceptable
Connect to the Sheridan College / Gillette College - STUDENT Secure Wireless Network with the PEAP Client (Windows XP Pro)
 Contents Connect to the Sheridan College / Gillette College - STUDENT Secure Wireless Network with the PEAP Client (Windows XP Pro) 1. Introduction 2. Configuring the Sheridan College / Gillette College
Contents Connect to the Sheridan College / Gillette College - STUDENT Secure Wireless Network with the PEAP Client (Windows XP Pro) 1. Introduction 2. Configuring the Sheridan College / Gillette College
CHIS, Inc. Privacy General Guidelines
 CHIS, Inc. and HIPAA CHIS, Inc. provides services to healthcare facilities and uses certain protected health information (PHI) in connection with performing these services. Therefore, CHIS, Inc. is classified
CHIS, Inc. and HIPAA CHIS, Inc. provides services to healthcare facilities and uses certain protected health information (PHI) in connection with performing these services. Therefore, CHIS, Inc. is classified
Version 4.61 or Later. Copyright 2013 Interactive Financial Solutions, Inc. All Rights Reserved. ProviderPro Network Administration Guide.
 Version 4.61 or Later Copyright 2013 Interactive Financial Solutions, Inc. All Rights Reserved. ProviderPro Network Administration Guide. This manual, as well as the software described in it, is furnished
Version 4.61 or Later Copyright 2013 Interactive Financial Solutions, Inc. All Rights Reserved. ProviderPro Network Administration Guide. This manual, as well as the software described in it, is furnished
General Service Level Agreement
 General Service Level Agreement Pricing We offer an unlimited Break / Fix for each device. Cost is below. Server Management = $199 / month per server Network Management = $199 / month per company Desktop
General Service Level Agreement Pricing We offer an unlimited Break / Fix for each device. Cost is below. Server Management = $199 / month per server Network Management = $199 / month per company Desktop
SPI Backup via Remote Terminal
 FLUOR SPI Backup via Remote Terminal SmartPlant Implementation Team By Mitch Fortey Copyright 2014 Fluor Corporation all rights reserved SPI Back Up via Remote Terminal Data Backup 101 Why do we backup
FLUOR SPI Backup via Remote Terminal SmartPlant Implementation Team By Mitch Fortey Copyright 2014 Fluor Corporation all rights reserved SPI Back Up via Remote Terminal Data Backup 101 Why do we backup
MSP Service Matrix. Servers
 Servers MSP Service Matrix Microsoft Windows O/S Patching - Patches automatically updated on a regular basis to the customer's servers and desktops. MS Baseline Analyzer and MS WSUS Server used Server
Servers MSP Service Matrix Microsoft Windows O/S Patching - Patches automatically updated on a regular basis to the customer's servers and desktops. MS Baseline Analyzer and MS WSUS Server used Server
SupportDesk Extensions Installation Guide Extension Service - Versions 6.9 8.5
 SupportDesk Extensions Installation Guide Extension Service - Versions 6.9 8.5 Richmond Systems Ltd, West House, West Street, Haslemere, Surrey, GU27 2AB Tel: +44 (0)1428 641616 - Fax: +44 (0)1428 641717
SupportDesk Extensions Installation Guide Extension Service - Versions 6.9 8.5 Richmond Systems Ltd, West House, West Street, Haslemere, Surrey, GU27 2AB Tel: +44 (0)1428 641616 - Fax: +44 (0)1428 641717
Contract # 04-06. Accepted on: March 29, 2005. Starling Systems. 711 S. Capitol Way, Suite 301 Olympia, WA 98501
 Disaster Recovery Plan Starling Systems Deliverable #15 - Draft I Contract # 04-06 Accepted on: March 29, 2005 Starling Systems 711 S. Capitol Way, Suite 301 Olympia, WA 98501 DISASTER RECOVERY PLAN TABLE
Disaster Recovery Plan Starling Systems Deliverable #15 - Draft I Contract # 04-06 Accepted on: March 29, 2005 Starling Systems 711 S. Capitol Way, Suite 301 Olympia, WA 98501 DISASTER RECOVERY PLAN TABLE
Network Setup Instructions
 Network Setup Instructions This document provides technical details for setting up the Elite Salon & Spa Management program in a network environment. If you have any questions, please contact our Technical
Network Setup Instructions This document provides technical details for setting up the Elite Salon & Spa Management program in a network environment. If you have any questions, please contact our Technical
Information Technology Department. Miller School of Medicine New User Guide
 Information Technology Department Miller School of Medicine New User Guide EDUCATION & COMMUNICATIONS Miller School of Medicine New User Guide 1051 NW 14 th Street #165, Miami, FL 33136 (305) 243-5999
Information Technology Department Miller School of Medicine New User Guide EDUCATION & COMMUNICATIONS Miller School of Medicine New User Guide 1051 NW 14 th Street #165, Miami, FL 33136 (305) 243-5999
2. PMP New Computer Installation. & Networking Instructions
 ONTARIO CHIROPRACTIC ASSOCIATION PATIENT MANAGEMENT PROGRAM PUTTING EXPERIENCE INTO PRACTICE PMP New Computer Installation & Networking Instructions This document provides installation instructions for
ONTARIO CHIROPRACTIC ASSOCIATION PATIENT MANAGEMENT PROGRAM PUTTING EXPERIENCE INTO PRACTICE PMP New Computer Installation & Networking Instructions This document provides installation instructions for
Online Test Administrator Quick Reference Guide Updated 08/02/2012 v.2.0
 Online Test Administrator Quick Reference Guide Updated 08/02/2012 v.2.0 M e s s a g e T e s t N a v ( W h a t D o e s T h i s M e a n? ) Login Screen The student will type in the Login ID and Test Code
Online Test Administrator Quick Reference Guide Updated 08/02/2012 v.2.0 M e s s a g e T e s t N a v ( W h a t D o e s T h i s M e a n? ) Login Screen The student will type in the Login ID and Test Code
Mobility Services Platform 3.1.1 Software Installation Guide
 Mobility Services Platform 3.1.1 Software Installation Guide Mobility Services Platform 3.1.1 Software Installation Guide 72E-100159-04 Revision D January 2008 2007 by Motorola, Inc. All rights reserved.
Mobility Services Platform 3.1.1 Software Installation Guide Mobility Services Platform 3.1.1 Software Installation Guide 72E-100159-04 Revision D January 2008 2007 by Motorola, Inc. All rights reserved.
Case Closed Installation and Setup
 1 Case Closed Installation and Setup Contents Installation Overview...2 Microsoft SQL Server Installation...3 Case Closed Software Installation...5 Register OCX for Printing...6 External Programs...7 Automatic
1 Case Closed Installation and Setup Contents Installation Overview...2 Microsoft SQL Server Installation...3 Case Closed Software Installation...5 Register OCX for Printing...6 External Programs...7 Automatic
Ohio Supercomputer Center
 Ohio Supercomputer Center IT Business Continuity Planning No: Effective: OSC-13 06/02/2009 Issued By: Kevin Wohlever Director of Supercomputer Operations Published By: Ohio Supercomputer Center Original
Ohio Supercomputer Center IT Business Continuity Planning No: Effective: OSC-13 06/02/2009 Issued By: Kevin Wohlever Director of Supercomputer Operations Published By: Ohio Supercomputer Center Original
University of Illinois at Chicago Health Sciences Colleges Information Technology Group Security Policies Summary
 University of Illinois at Chicago Health Sciences Colleges Information Technology Group Security Policies Summary This Summary was prepared March 2009 by Ian Huggins prior to HSC adoption of the most recent
University of Illinois at Chicago Health Sciences Colleges Information Technology Group Security Policies Summary This Summary was prepared March 2009 by Ian Huggins prior to HSC adoption of the most recent
Remote Desktop Connection Setup at King s College in Wilkes-Barre, PA
 Remote Desktop Connection Setup at King s College in Wilkes-Barre, PA Remote Desktop connections are granted to King s Staff only. Students do not have desktop (office) machines on campus, thus no desktop
Remote Desktop Connection Setup at King s College in Wilkes-Barre, PA Remote Desktop connections are granted to King s Staff only. Students do not have desktop (office) machines on campus, thus no desktop
Setting up Remote Desktop
 Setting up Remote Desktop Terminology: Host PC the computer you want to access remotely; the destination Client PC the computer you are actually using to access another PC; the source IP Address the numerical
Setting up Remote Desktop Terminology: Host PC the computer you want to access remotely; the destination Client PC the computer you are actually using to access another PC; the source IP Address the numerical
How To Upgrade Your Microsoft SQL Server for Accounting CS Version 2012.1
 How To Upgrade Your Microsoft SQL Server for Version 2012.1 The first step is to gather important information about your existing configuration. Identify The Database Server and SQL Server Version The
How To Upgrade Your Microsoft SQL Server for Version 2012.1 The first step is to gather important information about your existing configuration. Identify The Database Server and SQL Server Version The
RL Solutions Hosting Service Level Agreement
 RL Solutions Hosting Service Level Agreement April 2012 Table of Contents I. Context and Scope... 1 II. Defined Terms... 1 III. RL Solutions Responsibilities... 2 IV. Client Responsibilities... 4 V. The
RL Solutions Hosting Service Level Agreement April 2012 Table of Contents I. Context and Scope... 1 II. Defined Terms... 1 III. RL Solutions Responsibilities... 2 IV. Client Responsibilities... 4 V. The
BNA FEDERAL CREDIT UNION DISASTER RECOVERY PLAN
 BNA FEDERAL CREDIT UNION DISASTER RECOVERY PLAN INTRODUCTION The need for a contingency plan for business interruptions is vital to the operations of the BNA Federal Credit Union. Without such a plan,
BNA FEDERAL CREDIT UNION DISASTER RECOVERY PLAN INTRODUCTION The need for a contingency plan for business interruptions is vital to the operations of the BNA Federal Credit Union. Without such a plan,
Partner. Sage Pastel. Accounting. Installation Guide
 Sage Pastel Accounting Partner Installation Guide Sage Pastel: +27 11 304 3000 Sage Pastel Intl: +27 11 304 3400 www.pastel.co.za www.sagepastel.com info@pastel.co.za info@sagepastel.com Sage Pastel Accounting
Sage Pastel Accounting Partner Installation Guide Sage Pastel: +27 11 304 3000 Sage Pastel Intl: +27 11 304 3400 www.pastel.co.za www.sagepastel.com info@pastel.co.za info@sagepastel.com Sage Pastel Accounting
2.6.1 Creating an Acronis account... 11 2.6.2 Subscription to Acronis Cloud... 11. 3 Creating bootable rescue media... 12
 USER'S GUIDE Table of contents 1 Introduction...3 1.1 What is Acronis True Image 2015?... 3 1.2 New in this version... 3 1.3 System requirements... 4 1.4 Install, update or remove Acronis True Image 2015...
USER'S GUIDE Table of contents 1 Introduction...3 1.1 What is Acronis True Image 2015?... 3 1.2 New in this version... 3 1.3 System requirements... 4 1.4 Install, update or remove Acronis True Image 2015...
An online up-to-date version of this document is available on the Scomis Frequently Asked Questions website http://faq.scomis.
 Hosted Applications Migration This documentation will guide you through a successful implementation of the Scomis Hosted Application Service from your current school hosted environment. It is intended
Hosted Applications Migration This documentation will guide you through a successful implementation of the Scomis Hosted Application Service from your current school hosted environment. It is intended
Backup Exec Private Cloud Services. Planning and Deployment Guide
 Backup Exec Private Cloud Services Planning and Deployment Guide Chapter 1 Introducing Backup Exec Private Cloud Services This chapter includes the following topics: About Backup Exec Private Cloud Services
Backup Exec Private Cloud Services Planning and Deployment Guide Chapter 1 Introducing Backup Exec Private Cloud Services This chapter includes the following topics: About Backup Exec Private Cloud Services
User Guide Online Backup
 User Guide Online Backup Table of contents Table of contents... 1 Introduction... 2 Adding the Online Backup Service to your Account... 2 Getting Started with the Online Backup Software... 4 Downloading
User Guide Online Backup Table of contents Table of contents... 1 Introduction... 2 Adding the Online Backup Service to your Account... 2 Getting Started with the Online Backup Software... 4 Downloading
Continuous Data Protection. PowerVault DL Backup to Disk Appliance
 Continuous Data Protection PowerVault DL Backup to Disk Appliance Continuous Data Protection Current Situation The PowerVault DL Backup to Disk Appliance Powered by Symantec Backup Exec offers the industry
Continuous Data Protection PowerVault DL Backup to Disk Appliance Continuous Data Protection Current Situation The PowerVault DL Backup to Disk Appliance Powered by Symantec Backup Exec offers the industry
LockView 4.3.1 CompX Database & Network Configuration & Installation Manual
 LockView 4.3.1 CompX Database & Network Configuration & Installation Manual Table of Contents CompX Database & Network Configuration & Installation Manual Introduction... 4 Installation Requirements...
LockView 4.3.1 CompX Database & Network Configuration & Installation Manual Table of Contents CompX Database & Network Configuration & Installation Manual Introduction... 4 Installation Requirements...
1 of 10 1/31/2014 4:08 PM
 1 of 10 1/31/2014 4:08 PM copyright 2014 How to backup Microsoft SQL Server with Nordic Backup Pro Before creating a SQL backup set within Nordic Backup Pro it is first necessary to verify that the settings
1 of 10 1/31/2014 4:08 PM copyright 2014 How to backup Microsoft SQL Server with Nordic Backup Pro Before creating a SQL backup set within Nordic Backup Pro it is first necessary to verify that the settings
FREQUENTLY ASKED QUESTIONS
 FREQUENTLY ASKED QUESTIONS Secure Bytes, October 2011 This document is confidential and for the use of a Secure Bytes client only. The information contained herein is the property of Secure Bytes and may
FREQUENTLY ASKED QUESTIONS Secure Bytes, October 2011 This document is confidential and for the use of a Secure Bytes client only. The information contained herein is the property of Secure Bytes and may
Metalogix SharePoint Backup. Advanced Installation Guide. Publication Date: August 24, 2015
 Metalogix SharePoint Backup Publication Date: August 24, 2015 All Rights Reserved. This software is protected by copyright law and international treaties. Unauthorized reproduction or distribution of this
Metalogix SharePoint Backup Publication Date: August 24, 2015 All Rights Reserved. This software is protected by copyright law and international treaties. Unauthorized reproduction or distribution of this
Disaster Recovery Checklist Disaster Recovery Plan for <System One>
 Disaster Recovery Plan for SYSTEM OVERVIEW PRODUCTION SERVER HOT SITE SERVER APPLICATIONS (Use bold for Hot Site) ASSOCIATED SERVERS KEY CONTACTS Hardware Vendor System Owners Database Owner
Disaster Recovery Plan for SYSTEM OVERVIEW PRODUCTION SERVER HOT SITE SERVER APPLICATIONS (Use bold for Hot Site) ASSOCIATED SERVERS KEY CONTACTS Hardware Vendor System Owners Database Owner
ipad Installation and Setup
 ipad Installation and Setup INDEX ipad Features Page 2 Charging.. Page 2 User Guide... Page 3 Setup for ipad use in the office (Office wireless network) Setup Office computers Verify Remote Desktop is
ipad Installation and Setup INDEX ipad Features Page 2 Charging.. Page 2 User Guide... Page 3 Setup for ipad use in the office (Office wireless network) Setup Office computers Verify Remote Desktop is
SOLUTION GUIDE AND BEST PRACTICES
 SOLUTION GUIDE AND BEST PRACTICES Last Updated December 2012 Solution Overview Combine the best in bare-metal backup with the best in remote backup to offer your customers a complete disaster recovery
SOLUTION GUIDE AND BEST PRACTICES Last Updated December 2012 Solution Overview Combine the best in bare-metal backup with the best in remote backup to offer your customers a complete disaster recovery
Malwarebytes Enterprise Edition Best Practices Guide Version 1.3 21 March 2014
 Malwarebytes Enterprise Edition Best Practices Guide Version 1.3 21 March 2014 Notices Malwarebytes products and related documentation are provided under a license agreement containing restrictions on
Malwarebytes Enterprise Edition Best Practices Guide Version 1.3 21 March 2014 Notices Malwarebytes products and related documentation are provided under a license agreement containing restrictions on
How do I use Citrix Staff Remote Desktop
 How do I use Citrix Staff Remote Desktop September 2014 Initial Log On In order to login into the new Citrix system, you need to go to the following web address. https://remotets.tees.ac.uk/ Be sure to
How do I use Citrix Staff Remote Desktop September 2014 Initial Log On In order to login into the new Citrix system, you need to go to the following web address. https://remotets.tees.ac.uk/ Be sure to
NovaBACKUP xsp Version 15.0 Upgrade Guide
 NovaBACKUP xsp Version 15.0 Upgrade Guide NovaStor / November 2013 2013 NovaStor, all rights reserved. All trademarks are the property of their respective owners. Features and specifications are subject
NovaBACKUP xsp Version 15.0 Upgrade Guide NovaStor / November 2013 2013 NovaStor, all rights reserved. All trademarks are the property of their respective owners. Features and specifications are subject
2.1 To define the backup strategy for systems and data within the Cape Winelands District Municipality (CWDM).
 BACKUP POLICY POLICY ADOPTED BY COUNCIL ON 25 APRIL 2012 AT ITEM C.14.3 POLICY AMENDED BY COUNCIL ON 24 APRIL 2014 AT ITEM C.14.1 Cape Winelands District Municipality Backup Policy 1. 1. INTRODUCTION Computer
BACKUP POLICY POLICY ADOPTED BY COUNCIL ON 25 APRIL 2012 AT ITEM C.14.3 POLICY AMENDED BY COUNCIL ON 24 APRIL 2014 AT ITEM C.14.1 Cape Winelands District Municipality Backup Policy 1. 1. INTRODUCTION Computer
How To Set Up Hopkins Wireless On Windows 7 On A Pc Or Mac Or Ipad (For A Laptop) On A Network Card (For Windows 7) On Your Computer Or Ipa (For Mac Or Mac) On An Ipa Or
 Wireless Configuration Guide: Windows 7 Additional hopkins wireless network instructions and requirements for Windows XP, Vista, 8, Mac OS X, Linux, and other Mobile versions can be found at: http://www.it.johnshopkins.edu/services/network/wireless/
Wireless Configuration Guide: Windows 7 Additional hopkins wireless network instructions and requirements for Windows XP, Vista, 8, Mac OS X, Linux, and other Mobile versions can be found at: http://www.it.johnshopkins.edu/services/network/wireless/
SERVER CLOUD DISASTER RECOVERY. User Manual
 SERVER CLOUD DISASTER RECOVERY User Manual 1 Table of Contents 1. INTRODUCTION... 3 2. ACCOUNT SETUP OVERVIEW... 3 3. GETTING STARTED... 6 3.1 Sign up... 6 4. ACCOUNT SETUP... 8 4.1 AWS Cloud Formation
SERVER CLOUD DISASTER RECOVERY User Manual 1 Table of Contents 1. INTRODUCTION... 3 2. ACCOUNT SETUP OVERVIEW... 3 3. GETTING STARTED... 6 3.1 Sign up... 6 4. ACCOUNT SETUP... 8 4.1 AWS Cloud Formation
SmartFiler Backup Appliance User Guide 2.1
 SmartFiler Backup Appliance User Guide 2.1 SmartFiler Backup Appliance User Guide 1 Table of Contents Overview... 4 Solution Overview... 4 Solution 1: Two Virtual Backup Appliances... 5 Solution 2: Two
SmartFiler Backup Appliance User Guide 2.1 SmartFiler Backup Appliance User Guide 1 Table of Contents Overview... 4 Solution Overview... 4 Solution 1: Two Virtual Backup Appliances... 5 Solution 2: Two
How to Connect to UAB s Wireless Networks
 How to Connect to UAB s Wireless Networks Sections: Page: Checking Windows XP for Service Pack 3 3 Configuring Windows XP SP3 to Connect to uabwifi-nac: Part I 5 Configuring Windows Vista to Connect to
How to Connect to UAB s Wireless Networks Sections: Page: Checking Windows XP for Service Pack 3 3 Configuring Windows XP SP3 to Connect to uabwifi-nac: Part I 5 Configuring Windows Vista to Connect to
Backup Hands-On Exercises. Backup Hands-on Exercise
 Backup Hands-on Exercise 2 Chapter 10 Backup Hands-On Exercises Background Story You have been hired as the lead IT Administrator at the Florida International University (FIU) to manage the computers at
Backup Hands-on Exercise 2 Chapter 10 Backup Hands-On Exercises Background Story You have been hired as the lead IT Administrator at the Florida International University (FIU) to manage the computers at
Connecting to the FILTER Virtual Private Network (VPN)
 Create FILTER VPN Connection Filter s VPN allows computers at remote locations (e.g. home, hotels, Starbucks?) to connect directly and securely to FILTER s corporate network. Computers connected by VPNs
Create FILTER VPN Connection Filter s VPN allows computers at remote locations (e.g. home, hotels, Starbucks?) to connect directly and securely to FILTER s corporate network. Computers connected by VPNs
Backup with synchronization/ replication
 Backup with synchronization/ replication Peer-to-peer synchronization and replication software can augment and simplify existing data backup and retrieval systems. BY PAUL MARSALA May, 2001 According to
Backup with synchronization/ replication Peer-to-peer synchronization and replication software can augment and simplify existing data backup and retrieval systems. BY PAUL MARSALA May, 2001 According to
SUBJECT: SECURITY OF ELECTRONIC MEDICAL RECORDS COMPLIANCE WITH THE HEALTH INSURANCE PORTABILITY AND ACCOUNTABILITY ACT OF 1996 (HIPAA)
 UNIVERSITY OF PITTSBURGH POLICY SUBJECT: SECURITY OF ELECTRONIC MEDICAL RECORDS COMPLIANCE WITH THE HEALTH INSURANCE PORTABILITY AND ACCOUNTABILITY ACT OF 1996 (HIPAA) DATE: March 18, 2005 I. SCOPE This
UNIVERSITY OF PITTSBURGH POLICY SUBJECT: SECURITY OF ELECTRONIC MEDICAL RECORDS COMPLIANCE WITH THE HEALTH INSURANCE PORTABILITY AND ACCOUNTABILITY ACT OF 1996 (HIPAA) DATE: March 18, 2005 I. SCOPE This
ecotton System Configuration White Paper
 Table of Contents ecotton System Configuration Introduction... 1 Workstation Requirements... 1 Standalone... 2 Peer-to-Peer Network... 2 Configuring The ecotton Server... 2 Installing the ecotton Software...
Table of Contents ecotton System Configuration Introduction... 1 Workstation Requirements... 1 Standalone... 2 Peer-to-Peer Network... 2 Configuring The ecotton Server... 2 Installing the ecotton Software...
The initial set up takes a few steps, but then each time you want to connect it is just a two set process.
 Remote Access to your Desktop using VPN Overview VPN is a tool that enables you to access one computer from another. Typical uses for Pop Center members would be 1) access their pop center computer from
Remote Access to your Desktop using VPN Overview VPN is a tool that enables you to access one computer from another. Typical uses for Pop Center members would be 1) access their pop center computer from
User Guide. Active Online Backup - Secure, automatic protection
 Active Online Backup - Secure, automatic protection 1. Quick Setup... 1 2. Backup Selecting Folders and Files... 2 3. Backup - Changing Selected Folders and Files... 3 4. Checking on Your Backups... 4
Active Online Backup - Secure, automatic protection 1. Quick Setup... 1 2. Backup Selecting Folders and Files... 2 3. Backup - Changing Selected Folders and Files... 3 4. Checking on Your Backups... 4
PCGenesis Backup / Reorganization / Restore Checklist
 PCGenesis Backup / Reorganization / Restore Checklist BACKUP GUIDELINES 1 Include a full backup of K:\*.* in the site s standard server backup process Recommend full backup of K:*.* every night if possible
PCGenesis Backup / Reorganization / Restore Checklist BACKUP GUIDELINES 1 Include a full backup of K:\*.* in the site s standard server backup process Recommend full backup of K:*.* every night if possible
VPN User Guide: Own Device (Windows) Staff: Malaysia Campus
 VPN User Guide: Own Device (Windows) Staff: Malaysia Campus Contents Own PC/laptop: Windows... 2 Remote desktop to your HW PC after VPN login... 2 Windows 7: Client (preferred option)... 3 To install the
VPN User Guide: Own Device (Windows) Staff: Malaysia Campus Contents Own PC/laptop: Windows... 2 Remote desktop to your HW PC after VPN login... 2 Windows 7: Client (preferred option)... 3 To install the
Backup & Disaster Recovery Appliance User Guide
 Built on the Intel Hybrid Cloud Platform Backup & Disaster Recovery Appliance User Guide Order Number: G68664-001 Rev 1.0 June 22, 2012 Contents Registering the BDR Appliance... 4 Step 1: Register the
Built on the Intel Hybrid Cloud Platform Backup & Disaster Recovery Appliance User Guide Order Number: G68664-001 Rev 1.0 June 22, 2012 Contents Registering the BDR Appliance... 4 Step 1: Register the
North Florida Community College
 North Florida Community College Technology Plan Table of Contents Executive Summary... 3 Technology Vision... 5 Annual Initiatives... 6 2010 Data Center Expansions... 6 The Next 3 Years... 6 Technology
North Florida Community College Technology Plan Table of Contents Executive Summary... 3 Technology Vision... 5 Annual Initiatives... 6 2010 Data Center Expansions... 6 The Next 3 Years... 6 Technology
(606) 785-3450 Knott County (606) 439-3167 Perry County (606) 633-0778 Letcher County. support@tvscable.com
 TVS CableNet Technical Support Guide Effective August 15, 2006 All materials 2006 TV Service, Inc. This material may not be reproduced in any form except for personal private use by TV Service Cable Internet
TVS CableNet Technical Support Guide Effective August 15, 2006 All materials 2006 TV Service, Inc. This material may not be reproduced in any form except for personal private use by TV Service Cable Internet
DATA BACKUP & RESTORE
 DATA BACKUP & RESTORE Verizon Terremark s Data Backup & Restore provides secure, streamlined online-offsite data storage and retrieval that is highly scalable and easily customizable. Offsite backup is
DATA BACKUP & RESTORE Verizon Terremark s Data Backup & Restore provides secure, streamlined online-offsite data storage and retrieval that is highly scalable and easily customizable. Offsite backup is
USC Marshall School of Business Academic Information Services
 USC Marshall School of Business Academic Information Services Wake My PC Windows Version Connecting to a Marshall Windows PC Remotely Remote Desktop allows you to access the files and programs on a remote
USC Marshall School of Business Academic Information Services Wake My PC Windows Version Connecting to a Marshall Windows PC Remotely Remote Desktop allows you to access the files and programs on a remote
Updated: April 2010. Copyright 2005-2010 DBA Software Inc. All rights reserved. 2 Getting Started Guide
 Updated: April 2010 Copyright 2005-2010 DBA Software Inc. All rights reserved. 2 Getting Started Guide Table of Contents Welcome 4 Support Center Subscription 5 1. System Requirements 8 2. Installing the
Updated: April 2010 Copyright 2005-2010 DBA Software Inc. All rights reserved. 2 Getting Started Guide Table of Contents Welcome 4 Support Center Subscription 5 1. System Requirements 8 2. Installing the
RingStor User Manual. Version 2.1 Last Update on September 17th, 2015. RingStor, Inc. 197 Route 18 South, Ste 3000 East Brunswick, NJ 08816.
 RingStor User Manual Version 2.1 Last Update on September 17th, 2015 RingStor, Inc. 197 Route 18 South, Ste 3000 East Brunswick, NJ 08816 Page 1 Table of Contents 1 Overview... 5 1.1 RingStor Data Protection...
RingStor User Manual Version 2.1 Last Update on September 17th, 2015 RingStor, Inc. 197 Route 18 South, Ste 3000 East Brunswick, NJ 08816 Page 1 Table of Contents 1 Overview... 5 1.1 RingStor Data Protection...
SHARED WEB AND MAIL HOSTING SERVICE LEVEL AGREEMENT (SLA) 2010
 SHARED WEB AND MAIL HOSTING SERVICE LEVEL AGREEMENT (SLA) 2010 This Service Level Agreement (SLA) ( Service Level Agreement or Agreement or SLA ) is by and between Bizcom Web Services, Inc. (the "Company")
SHARED WEB AND MAIL HOSTING SERVICE LEVEL AGREEMENT (SLA) 2010 This Service Level Agreement (SLA) ( Service Level Agreement or Agreement or SLA ) is by and between Bizcom Web Services, Inc. (the "Company")
U.S. DEPARTMENT OF COMMERCE UNITED STATES PATENT AND TRADEMARK OFFICE. Privacy Impact Assessment
 U.S. DEPARTMENT OF COMMERCE UNITED STATES PATENT AND TRADEMARK OFFICE Privacy Impact Assessment Enterprise Data Warehouse (EDW) PTOC-003-00 August 5, 2015 Privacy Impact Assessment This Privacy Impact
U.S. DEPARTMENT OF COMMERCE UNITED STATES PATENT AND TRADEMARK OFFICE Privacy Impact Assessment Enterprise Data Warehouse (EDW) PTOC-003-00 August 5, 2015 Privacy Impact Assessment This Privacy Impact
BDR for ShadowProtect Solution Guide and Best Practices
 BDR for ShadowProtect Solution Guide and Best Practices Updated September 2015 - i - Table of Contents Process Overview... 3 1. Assess backup requirements... 4 2. Provision accounts... 4 3. Install ShadowProtect...
BDR for ShadowProtect Solution Guide and Best Practices Updated September 2015 - i - Table of Contents Process Overview... 3 1. Assess backup requirements... 4 2. Provision accounts... 4 3. Install ShadowProtect...
BACKUP AND CONTIGENCY PLANS (DISASTER RECOVERY)
 BACKUP AND CONTIGENCY PLANS (DISASTER RECOVERY) PURPOSE The purpose of this policy is to describe the backup and contingency plans, including disaster recovery planning, that will be implemented to ensure
BACKUP AND CONTIGENCY PLANS (DISASTER RECOVERY) PURPOSE The purpose of this policy is to describe the backup and contingency plans, including disaster recovery planning, that will be implemented to ensure
Using Remote Desktop to access your Office Computer or Faculty Remote Desktop Server August, 2005 This document consists of two main parts and an
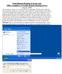 Using Remote Desktop to access your Office Computer or Faculty Remote Desktop Server August, 2005 This document consists of two main parts and an addendum. The first part will be the steps required to
Using Remote Desktop to access your Office Computer or Faculty Remote Desktop Server August, 2005 This document consists of two main parts and an addendum. The first part will be the steps required to
TECHNICAL SUPPORT. and HARDWARE/SOFTWARE/NETWORK MAINTENANCE. for TICKETING DATABASE
 IT Services Service Level Agreement TECHNICAL SUPPORT and HARDWARE/SOFTWARE/NETWORK MAINTENANCE for TICKETING DATABASE IT Services Service Level Agreement:Ticketing Database This service level agreement
IT Services Service Level Agreement TECHNICAL SUPPORT and HARDWARE/SOFTWARE/NETWORK MAINTENANCE for TICKETING DATABASE IT Services Service Level Agreement:Ticketing Database This service level agreement
QUANTIFY INSTALLATION GUIDE
 QUANTIFY INSTALLATION GUIDE Thank you for putting your trust in Avontus! This guide reviews the process of installing Quantify software. For Quantify system requirement information, please refer to the
QUANTIFY INSTALLATION GUIDE Thank you for putting your trust in Avontus! This guide reviews the process of installing Quantify software. For Quantify system requirement information, please refer to the
BEFORE YOU START... 1 Set Up Your PC Desktop Computer/Laptop... 1 Set Up Remote Desktop on Your ipad... 3
 Quick Reference Guide Using Remote Desktop With Your ipad and PC This user guide is for users connecting their ipad to a PC computer or laptop. This user guide covers how to set up your ipad to connect
Quick Reference Guide Using Remote Desktop With Your ipad and PC This user guide is for users connecting their ipad to a PC computer or laptop. This user guide covers how to set up your ipad to connect
Magaya Software Installation Guide
 Magaya Software Installation Guide MAGAYA SOFTWARE INSTALLATION GUIDE INTRODUCTION Introduction This installation guide explains the system requirements for installing any Magaya software, the steps to
Magaya Software Installation Guide MAGAYA SOFTWARE INSTALLATION GUIDE INTRODUCTION Introduction This installation guide explains the system requirements for installing any Magaya software, the steps to
