Secure Remote Photo Identification With ID card
|
|
|
- Dwain Griffith
- 8 years ago
- Views:
Transcription
1 Secure Remote Photo Identification With ID card Keith Jentoft AudioSmartCard, group
2 Basic concept: Remote Photo Authentication Cardholder s Secure File Authorities can securely identify cardholders using existing cell phones and the ncryptone Card. This card emits a secure acoustic cryptogram to the phone microphone. After strong authentication, a secure server sends the cardholder s photo to the cell phone for validation by officials. 2 Factors Biometric photo/facial recognition and Cryptogram 2 AudioSmartCard, group
3 I know the card is authentic because Symmetric Key SHA1 Message Input A4 5E F8 96 3C F DE 48 7A FC 14 2C SHA1 SHA1 Message Output 49 B1 67 C7 5F AE 78 F2 DE 21 FA 1C AES Processed Information The ncryptone card contains an advanced acoustic encryption module that emits a unique cryptogram that is delivered in acoustic tones each time the button is pushed. AES Output 81 A2 C D5 3B Card Serial # F7 Card Serial # F7 Counter Counter Offline Signature EA 4C 21 A8 1F 1C PC Cryptogram Processed Information Online Signature 81 A2 C D5 3B Telephone Cryptogram Online Signature 81 A2 C D5 3B 9-17 KHz 1-4 KHz These tones are created in various frequencies optimized for particular infrastructure and are compatible with existing Telephones, PDA s, PCs and Radios. 3 AudioSmartCard, group
4 I know the card is authentic because The acoustic cryptogram is unique. Acoustic Cryptogram Digitized Cryptogram created from Acoustic Cryptogram This Dynamic Password is digitized and linked to a Secure Radius Server. Cryptogram changes every time card is used. 4 AudioSmartCard, group
5 I know the user is authentic because Double/Triple Authentication 1. Photograph sent to Mobile phone PC Blackberry 2. Optional Cardholder Pin code On Board card itself or Using Existing Phone/PC/Radio Keypad 5 AudioSmartCard, group
6 Authentication Scenario 1. Cardholder presents card to official. 2. Official uses standard cell phone and calls 800 number to access IVR. 3. Upon reaching the IVR the official initiates card s acoustic cryptogram by pushing button. 4. IVR sends cryptogram to Radius server for card authentication. 5. After card authentication, server sends cardholder s photo via MMS to cell phone. 6. Authority verifies photo received against actual cardholder. 6 AudioSmartCard, group
7 Card Authentication (click once for animation) Voice Response Server Cryptogram Cardholder 800- valid- ID Official 1. Cardholder presents card to official. 2. Official calls 800 number to access IVR from standard cell phone. 3. Initiate card s acoustic cryptogram by pushing button on card. 4. Acoustic captured by IVR. 5. IVR sends cryptogram to Radius server for card authentication. 7 AudioSmartCard, group
8 Photo Delivered (click once for animation) MMS Server Cardholder Official 7. After card authentication, server sends cardholder s photo via MMS to cell phone. 8. Authority verifies photo received against actual cardholder. 8 AudioSmartCard, group
9 Advantages 1. Immediate deployment at Low-Cost. 2. No reader infrastructure necessary. 3. Real-time notification of revocation or status changes 4. No dependency on photos or information on card. 5. Extreme Security - Strong authentication based on most advanced cryptology. 6. Existing world-wide network and infrastructure for immediate photo delivery. 7. Compatible with existing CAC (EMV), RFID (contactless), Mag-Stripe, or other Identification card systems. 9 AudioSmartCard, group
10 Secure Remote Photo Identification With ID card Keith Jentoft AudioSmartCard, group
RF-Enabled Applications and Technology: Comparing and Contrasting RFID and RF-Enabled Smart Cards
 RF-Enabled Applications and Technology: Comparing and Contrasting RFID and RF-Enabled Smart Cards January 2007 Developed by: Smart Card Alliance Identity Council RF-Enabled Applications and Technology:
RF-Enabled Applications and Technology: Comparing and Contrasting RFID and RF-Enabled Smart Cards January 2007 Developed by: Smart Card Alliance Identity Council RF-Enabled Applications and Technology:
EMVCo Letter of Approval - Contact Terminal Level 2
 May 18, 2015 Richard Pohl Triton Systems of Delaware, LLC 21405 B Street Long Beach MS 39560 USA Re: EMV Application Kernel: Approval Number(s): EMVCo Letter of Approval - Contact Terminal Level 2 Triton
May 18, 2015 Richard Pohl Triton Systems of Delaware, LLC 21405 B Street Long Beach MS 39560 USA Re: EMV Application Kernel: Approval Number(s): EMVCo Letter of Approval - Contact Terminal Level 2 Triton
EMVCo Letter of Approval - Contact Terminal Level 2
 February 14, 2014 Marat Serpokrylov Closed joint stock company - CENTER OF FINANCIAL TECHNOLOGIES 35, Koltsovo Koltsovo, vosibirsk Region 630559 Russia Re: EMV Application Kernel: Approval Number(s): EMVCo
February 14, 2014 Marat Serpokrylov Closed joint stock company - CENTER OF FINANCIAL TECHNOLOGIES 35, Koltsovo Koltsovo, vosibirsk Region 630559 Russia Re: EMV Application Kernel: Approval Number(s): EMVCo
Acoustic Smart Cards The Emergence of Ubiquitous Security
 Acoustic Smart Cards The Emergence of Ubiquitous Security Rocky Stefano, Chief Technical Officer http://www.identita.com Identita Technologies Inc. 4580 Dufferin Street, Suite 500 Toronto, Ontario, M3H
Acoustic Smart Cards The Emergence of Ubiquitous Security Rocky Stefano, Chief Technical Officer http://www.identita.com Identita Technologies Inc. 4580 Dufferin Street, Suite 500 Toronto, Ontario, M3H
Secure your Privacy. www.jrsys.com.tw. jrsys, Inc. All rights reserved.
 Secure your Privacy www.jrsys.com.tw CNN 2013/7/16 8:25PM Man Middle In The I got your ID/Password! Mobile Secure Secure sensitive access data Random Login Web Authentication One Secure Time Channel Password
Secure your Privacy www.jrsys.com.tw CNN 2013/7/16 8:25PM Man Middle In The I got your ID/Password! Mobile Secure Secure sensitive access data Random Login Web Authentication One Secure Time Channel Password
Registration for My Profile & Administration
 Registration for My Profile & Administration Table Of Contents User Registration... 1 Registering as a New User... 1 About the IDcipherTM Card... 7 How Do I Get An IDcipher TM Card?... 8 Two-Factor Authentication...
Registration for My Profile & Administration Table Of Contents User Registration... 1 Registering as a New User... 1 About the IDcipherTM Card... 7 How Do I Get An IDcipher TM Card?... 8 Two-Factor Authentication...
SECURITY IMPLICATIONS OF NFC IN AUTHENTICATION AND IDENTITY MANAGEMENT
 SECURITY IMPLICATIONS OF NFC IN AUTHENTICATION AND IDENTITY MANAGEMENT Dmitry Barinov SecureKey Technologies Inc. Session ID: MBS-W09 Session Classification: Advanced Session goals Appreciate the superior
SECURITY IMPLICATIONS OF NFC IN AUTHENTICATION AND IDENTITY MANAGEMENT Dmitry Barinov SecureKey Technologies Inc. Session ID: MBS-W09 Session Classification: Advanced Session goals Appreciate the superior
Mobile Payment: The next step of secure payment VDI / VDE-Colloquium. Hans-Jörg Frey Senior Product Manager May 16th, 2013
 Mobile Payment: The next step of secure payment VDI / VDE-Colloquium May 16th, 2013 G&D has been growing through continuous innovation Server software and services Token and embedded security Cards for
Mobile Payment: The next step of secure payment VDI / VDE-Colloquium May 16th, 2013 G&D has been growing through continuous innovation Server software and services Token and embedded security Cards for
How Secure are Contactless Payment Systems?
 SESSION ID: HT-W01 How Secure are Contactless Payment Systems? Matthew Ngu Engineering Manager RSA, The Security Division of EMC Chris Scott Senior Software Engineer RSA, The Security Division of EMC 2
SESSION ID: HT-W01 How Secure are Contactless Payment Systems? Matthew Ngu Engineering Manager RSA, The Security Division of EMC Chris Scott Senior Software Engineer RSA, The Security Division of EMC 2
Alternative authentication methods. Niko Dukić/Mario Šale CS Computer Systems
 Alternative authentication methods Niko Dukić/Mario Šale CS Computer Systems Table of contents: Authentication and why is it important Authentication methods RSA SecureID solutions for authentication Implementation
Alternative authentication methods Niko Dukić/Mario Šale CS Computer Systems Table of contents: Authentication and why is it important Authentication methods RSA SecureID solutions for authentication Implementation
The Access Engine. Building Integration System - The Access Engine. Security Systems
 The Access Engine 1 What is BIS Access Engine? It is one of the central software modules of the Building Integration System It s a fully integrated access control solution with corresponding access hardware
The Access Engine 1 What is BIS Access Engine? It is one of the central software modules of the Building Integration System It s a fully integrated access control solution with corresponding access hardware
Contactless Smart Cards vs. EPC Gen 2 RFID Tags: Frequently Asked Questions. July, 2006. Developed by: Smart Card Alliance Identity Council
 Contactless Smart Cards vs. EPC Gen 2 RFID Tags: Frequently Asked Questions July, 2006 Developed by: Smart Card Alliance Identity Council Contactless Smart Cards vs. EPC Gen 2 RFID Tags: Frequently Asked
Contactless Smart Cards vs. EPC Gen 2 RFID Tags: Frequently Asked Questions July, 2006 Developed by: Smart Card Alliance Identity Council Contactless Smart Cards vs. EPC Gen 2 RFID Tags: Frequently Asked
Strong authentication of GUI sessions over Dedicated Links. ipmg Workshop on Connectivity 25 May 2012
 Strong authentication of GUI sessions over Dedicated Links ipmg Workshop on Connectivity 25 May 2012 Agenda Security requirements The T2S U2A 2 Factor Authentication solution Additional investigation Terminal
Strong authentication of GUI sessions over Dedicated Links ipmg Workshop on Connectivity 25 May 2012 Agenda Security requirements The T2S U2A 2 Factor Authentication solution Additional investigation Terminal
EMVCo Letter of Approval - Terminal Level 2
 April 06, 2011 Lorraine LEPINE France Telecom Direction Publiphonie (FT/OPF/MHGP/DMP/PUB) Orange Village, 1 avenue Nelson Mandela 94745 ARCUEIL France Re: EMV Application Kernel: Approval Number(s): EMVCo
April 06, 2011 Lorraine LEPINE France Telecom Direction Publiphonie (FT/OPF/MHGP/DMP/PUB) Orange Village, 1 avenue Nelson Mandela 94745 ARCUEIL France Re: EMV Application Kernel: Approval Number(s): EMVCo
GadgetTrak Mobile Security Android & BlackBerry Installation & Operation Manual
 GadgetTrak Mobile Security Android & BlackBerry Installation & Operation Manual Overview GadgetTrak Mobile Security is an advanced software application designed to assist in the recovery of your mobile
GadgetTrak Mobile Security Android & BlackBerry Installation & Operation Manual Overview GadgetTrak Mobile Security is an advanced software application designed to assist in the recovery of your mobile
POS Terminals Emerging Trends & Technology
 POS Terminals Emerging Trends & Technology Dan Loomis Product Management Dan_Loomis@VeriFone.com Security Payment Media Wireless Verticals 2 Security Security Is Not A Destination, It s A Journey From
POS Terminals Emerging Trends & Technology Dan Loomis Product Management Dan_Loomis@VeriFone.com Security Payment Media Wireless Verticals 2 Security Security Is Not A Destination, It s A Journey From
Employee Active Directory Self-Service Quick Setup Guide
 Employee Active Directory Self-Service Quick Setup Guide (V2.0) Last update: 11/5/2014 Copyright 2014 InfraDog Inc. All rights reserved Corporate Phone: +1 (416) 473-4096, Fax: +1 (888) 863-3936, Email:
Employee Active Directory Self-Service Quick Setup Guide (V2.0) Last update: 11/5/2014 Copyright 2014 InfraDog Inc. All rights reserved Corporate Phone: +1 (416) 473-4096, Fax: +1 (888) 863-3936, Email:
EMV and Chip Cards Key Information On What This Is, How It Works and What It Means
 EMV and Chip Cards Key Information On What This Is, How It Works and What It Means Document Purpose This document is intended to provide information about the concepts behind and the processes involved
EMV and Chip Cards Key Information On What This Is, How It Works and What It Means Document Purpose This document is intended to provide information about the concepts behind and the processes involved
Configuration Manual
 Configuration Manual Page 1 of 20 Table of Contents Chronicall Setup...3 Standard Installation...3 Non-standard Installation (Recording Library on Separate machine)...8 Configuring Call Recording through
Configuration Manual Page 1 of 20 Table of Contents Chronicall Setup...3 Standard Installation...3 Non-standard Installation (Recording Library on Separate machine)...8 Configuring Call Recording through
Smart Card- An Alternative to Password Authentication By Ahmad Ismadi Yazid B. Sukaimi
 Smart Card- An Alternative to Password Authentication By Ahmad Ismadi Yazid B. Sukaimi Purpose This paper is intended to describe the benefits of smart card implementation and it combination with Public
Smart Card- An Alternative to Password Authentication By Ahmad Ismadi Yazid B. Sukaimi Purpose This paper is intended to describe the benefits of smart card implementation and it combination with Public
Smart Cards and Biometrics in Physical Access Control Systems
 Smart Cards and Biometrics in Physical Access Control Systems Robert J. Merkert, Sr. Vice President of Sales Americas Biometric Consortium 2005 Conference September 21, 2005 All Company and/or product
Smart Cards and Biometrics in Physical Access Control Systems Robert J. Merkert, Sr. Vice President of Sales Americas Biometric Consortium 2005 Conference September 21, 2005 All Company and/or product
Mobile MasterCard PayPass UI Application Requirements. February 2013 - Version 1.4
 Mobile MasterCard PayPass UI Application Requirements February 2013 - Version 1.4 Proprietary Rights The information contained in this document is proprietary and confidential to MasterCard International
Mobile MasterCard PayPass UI Application Requirements February 2013 - Version 1.4 Proprietary Rights The information contained in this document is proprietary and confidential to MasterCard International
Secure Global Desktop (SGD)
 Secure Global Desktop (SGD) Table of Contents Checking your Java Version...3 Preparing Your Desktop Computer...3 Accessing SGD...5 Logging into SGD...6 Using SGD to Access Your Desktop...7 Using SGD to
Secure Global Desktop (SGD) Table of Contents Checking your Java Version...3 Preparing Your Desktop Computer...3 Accessing SGD...5 Logging into SGD...6 Using SGD to Access Your Desktop...7 Using SGD to
W.A.R.N. Passive Biometric ID Card Solution
 W.A.R.N. Passive Biometric ID Card Solution Updated November, 2007 Biometric technology has advanced so quickly in the last decade that questions and facts about its cost, use, and accuracy are often confused
W.A.R.N. Passive Biometric ID Card Solution Updated November, 2007 Biometric technology has advanced so quickly in the last decade that questions and facts about its cost, use, and accuracy are often confused
Application Note. Connecting the TracKing-1 using Bluetooth
 Application Note Connecting the TracKing-1 using Bluetooth This Application note describes how to establish a Bluetooth connection between the TracKing-1 and various devices. It also explains the various
Application Note Connecting the TracKing-1 using Bluetooth This Application note describes how to establish a Bluetooth connection between the TracKing-1 and various devices. It also explains the various
Encrypting*a*Windows*7*Hard*Disk* with%bitlocker%disk%encryption!
 Encrypting*a*Windows*7*Hard*Disk* with%bitlocker%disk%encryption Thisdocumentcontainsthenecessarystepstoencryptthecontentsofaharddrive usingbitlockerandwindows7. Thefollowinginstructionsarederivedfromdocumentationat:
Encrypting*a*Windows*7*Hard*Disk* with%bitlocker%disk%encryption Thisdocumentcontainsthenecessarystepstoencryptthecontentsofaharddrive usingbitlockerandwindows7. Thefollowinginstructionsarederivedfromdocumentationat:
Re: EMVCo Letter of Approval - Contact Terminal Level 2
 April 07, 2014 Michael Li Wizarpos International Co., Ltd. Suite B904, Hi-Tech King World, 666 East Beijing Road Shanghai 200001 People's Republic of China Re: EMVCo Letter of Approval - Contact Terminal
April 07, 2014 Michael Li Wizarpos International Co., Ltd. Suite B904, Hi-Tech King World, 666 East Beijing Road Shanghai 200001 People's Republic of China Re: EMVCo Letter of Approval - Contact Terminal
Next Generation Web-Based Time & Attendance
 Next Generation Web-Based Time & Attendance PerfectTIME Take control of labor costs and workforce management Streamline PerfectTIME is an intuitive, convenient and efficient web-based time and attendance
Next Generation Web-Based Time & Attendance PerfectTIME Take control of labor costs and workforce management Streamline PerfectTIME is an intuitive, convenient and efficient web-based time and attendance
MasterCard Contactless Reader v3.0. INTRODUCTION TO MASTERCARD CONTACTLESS READER v3.0
 MasterCard Contactless Reader v3.0 INTRODUCTION TO MASTERCARD CONTACTLESS READER v3.0 Introduction to MasterCard Contactless Reader v3.0 Contents 1. Introduction...2 2. Background...3 2.1 Reader Applications...3
MasterCard Contactless Reader v3.0 INTRODUCTION TO MASTERCARD CONTACTLESS READER v3.0 Introduction to MasterCard Contactless Reader v3.0 Contents 1. Introduction...2 2. Background...3 2.1 Reader Applications...3
Table Of Contents. System Monitoring... 14 System Monitoring Display...14 Monitoring Zones...15 About Areas (partitions)...15 Area Status Display...
 Quick Start Table Of Contents Getting Started... 2 NEware Editions...2 Installing NEware...3 Installing Languages...3 Connecting to NEware...3 Changing Your IP100 Password...4 User Codes... 5 Master Feature...5
Quick Start Table Of Contents Getting Started... 2 NEware Editions...2 Installing NEware...3 Installing Languages...3 Connecting to NEware...3 Changing Your IP100 Password...4 User Codes... 5 Master Feature...5
Lab 6.2.12a Configure Remote Access Using Cisco Easy VPN
 Lab 6.2.12a Configure Remote Access Using Cisco Easy VPN Objective Scenario Topology In this lab, the students will complete the following tasks: Enable policy lookup via authentication, authorization,
Lab 6.2.12a Configure Remote Access Using Cisco Easy VPN Objective Scenario Topology In this lab, the students will complete the following tasks: Enable policy lookup via authentication, authorization,
International Journal of Engineering Research & Management Technology
 International Journal of Engineering Research & Management Technology March- 2015 Volume 2, Issue-2 Radio Frequency Identification Security System Mr. Shailendra Kumar Assistant Professor Department of
International Journal of Engineering Research & Management Technology March- 2015 Volume 2, Issue-2 Radio Frequency Identification Security System Mr. Shailendra Kumar Assistant Professor Department of
Epicor Eagle EMV Implementation Step by Step
 Epicor Eagle EMV Implementation Step by Step Introduction This guide will provide step by step instructions to implement EMV with Eagle. This guide is only for integrated bankcard processing with Epicor
Epicor Eagle EMV Implementation Step by Step Introduction This guide will provide step by step instructions to implement EMV with Eagle. This guide is only for integrated bankcard processing with Epicor
American Express Contactless Payments
 PRODUCT CAPABILITY GUIDE American Express Contactless Payments American Express Contactless Payments Help Enable Increased Convenience For Card Members At The Point Of Sale American Express contactless
PRODUCT CAPABILITY GUIDE American Express Contactless Payments American Express Contactless Payments Help Enable Increased Convenience For Card Members At The Point Of Sale American Express contactless
Scenario: Remote-Access VPN Configuration
 CHAPTER 7 Scenario: Remote-Access VPN Configuration A remote-access Virtual Private Network (VPN) enables you to provide secure access to off-site users. ASDM enables you to configure the adaptive security
CHAPTER 7 Scenario: Remote-Access VPN Configuration A remote-access Virtual Private Network (VPN) enables you to provide secure access to off-site users. ASDM enables you to configure the adaptive security
Achieving Universal Secure Identity Verification with Convenience and Personal Privacy A PRIVARIS BUSINESS WHITE PAPER
 with Convenience and Personal Privacy version 0.2 Aug.18, 2007 WHITE PAPER CONTENT Introduction... 3 Identity verification and multi-factor authentication..... 4 Market adoption... 4 Making biometrics
with Convenience and Personal Privacy version 0.2 Aug.18, 2007 WHITE PAPER CONTENT Introduction... 3 Identity verification and multi-factor authentication..... 4 Market adoption... 4 Making biometrics
NetIQ Advanced Authentication Framework
 NetIQ Advanced Authentication Framework Security Officer Guide Version 5.2.0 1 Table of Contents 1 Table of Contents 2 Introduction 3 About This Document 3 Authenticators Management 4 Card 8 Email OTP
NetIQ Advanced Authentication Framework Security Officer Guide Version 5.2.0 1 Table of Contents 1 Table of Contents 2 Introduction 3 About This Document 3 Authenticators Management 4 Card 8 Email OTP
Use the below instructions to configure your wireless settings to connect to the secure wireless network using Microsoft Windows Vista/7.
 Use the below instructions to configure your wireless settings to connect to the secure wireless network using Microsoft Windows Vista/7. 1. Click the Windows Start button, then Control Panel How-To-WCC-Secure-Windows-7-11/4/2010-4:09
Use the below instructions to configure your wireless settings to connect to the secure wireless network using Microsoft Windows Vista/7. 1. Click the Windows Start button, then Control Panel How-To-WCC-Secure-Windows-7-11/4/2010-4:09
Digital Signatures on iqmis User Access Request Form
 Digital Signatures on iqmis User Access Request Form When a user clicks in the User Signature block on the iqmis Access Form, the following window appears: Click Save a Copy and rename it with your name,
Digital Signatures on iqmis User Access Request Form When a user clicks in the User Signature block on the iqmis Access Form, the following window appears: Click Save a Copy and rename it with your name,
Guidance Notes PCI DSS Compliance as it relates to Call Recording
 Guidance Notes PCI DSS Compliance as it relates to Call Recording Published by DMA Contact Centres & Telemarketing Council First edition Contents Disclaimer...2 1. Background...3 2. The fundamental storage
Guidance Notes PCI DSS Compliance as it relates to Call Recording Published by DMA Contact Centres & Telemarketing Council First edition Contents Disclaimer...2 1. Background...3 2. The fundamental storage
CA ArcotOTP Versatile Authentication Solution for Mobile Phones
 PRODUCT SHEET CA ArcotOTP CA ArcotOTP Versatile Authentication Solution for Mobile Phones Overview Consumers have embraced their mobile phones as more than just calling or texting devices. They are demanding
PRODUCT SHEET CA ArcotOTP CA ArcotOTP Versatile Authentication Solution for Mobile Phones Overview Consumers have embraced their mobile phones as more than just calling or texting devices. They are demanding
Installing and Configuring TrueConf Online
 Installing and Configuring TrueConf Online How to Install? How to Login? How to Configure? Creating a Conference How to Make 1-on-1 VideoCall? What modes of group conferences are available in TrueConf
Installing and Configuring TrueConf Online How to Install? How to Login? How to Configure? Creating a Conference How to Make 1-on-1 VideoCall? What modes of group conferences are available in TrueConf
2015-11-02. Electronic Payments Part 1
 Electronic Payments Part Card transactions Card-Present Smart Cards Card-Not-Present SET 3D Secure Untraceable E-Cash Micropayments Payword Electronic Lottery Tickets Peppercoin Bitcoin EITN4 - Advanced
Electronic Payments Part Card transactions Card-Present Smart Cards Card-Not-Present SET 3D Secure Untraceable E-Cash Micropayments Payword Electronic Lottery Tickets Peppercoin Bitcoin EITN4 - Advanced
Using your Encrypted BlackBerry
 Using your Encrypted BlackBerry How do I change the Language on my BlackBerry? 1. On the Home screen or in a folder, click the Options icon. 2. Click Typing and Input > Language. 3. To change the display
Using your Encrypted BlackBerry How do I change the Language on my BlackBerry? 1. On the Home screen or in a folder, click the Options icon. 2. Click Typing and Input > Language. 3. To change the display
Version 15.3 (October 2009)
 Copyright 2008-2010 Software Technology, Inc. 1621 Cushman Drive Lincoln, NE 68512 (402) 423-1440 www.tabs3.com Portions copyright Microsoft Corporation Tabs3, PracticeMaster, and the pinwheel symbol (
Copyright 2008-2010 Software Technology, Inc. 1621 Cushman Drive Lincoln, NE 68512 (402) 423-1440 www.tabs3.com Portions copyright Microsoft Corporation Tabs3, PracticeMaster, and the pinwheel symbol (
Schlumberger PKI /Corporate Badge Deployment. Neville Pattinson Director of Business Development & Technology IT & Public Sector
 Schlumberger PKI /Corporate Badge Deployment Neville Pattinson Director of Business Development & Technology IT & Public Sector 1 Overview Background Overview of the PKI and Corporate Badge components
Schlumberger PKI /Corporate Badge Deployment Neville Pattinson Director of Business Development & Technology IT & Public Sector 1 Overview Background Overview of the PKI and Corporate Badge components
Implementation of biometrics, issues to be solved
 ICAO 9th Symposium and Exhibition on MRTDs, Biometrics and Border Security, 22-24 October 2013 Implementation of biometrics, issues to be solved Eugenijus Liubenka, Chairman of the Frontiers / False Documents
ICAO 9th Symposium and Exhibition on MRTDs, Biometrics and Border Security, 22-24 October 2013 Implementation of biometrics, issues to be solved Eugenijus Liubenka, Chairman of the Frontiers / False Documents
CRYPTOGRAPHY AS A SERVICE
 CRYPTOGRAPHY AS A SERVICE Peter Robinson RSA, The Security Division of EMC Session ID: ADS R01 Session Classification: Advanced Introduction Deploying cryptographic keys to end points such as smart phones,
CRYPTOGRAPHY AS A SERVICE Peter Robinson RSA, The Security Division of EMC Session ID: ADS R01 Session Classification: Advanced Introduction Deploying cryptographic keys to end points such as smart phones,
HOSTED CLOUD-BASED PHONE SOLUTION
 HOSTED CLOUD-BASED PHONE SOLUTION VoxSun Telecom Office VoxSun Telecom Office is designed specifically for companies and for mobile professionals. When choosing the VoxSun Office service, you will have
HOSTED CLOUD-BASED PHONE SOLUTION VoxSun Telecom Office VoxSun Telecom Office is designed specifically for companies and for mobile professionals. When choosing the VoxSun Office service, you will have
2100 Series VoIP Phone
 2100 Series VoIP Phone Installation and Operations Manual Made in the USA 3 Year Warranty N56 W24720 N. Corporate Circle Sussex, WI 53089 RP8500SIP 800-451-1460 262-246-4828 (fax) Ver. 4 www.rathmicrotech.com
2100 Series VoIP Phone Installation and Operations Manual Made in the USA 3 Year Warranty N56 W24720 N. Corporate Circle Sussex, WI 53089 RP8500SIP 800-451-1460 262-246-4828 (fax) Ver. 4 www.rathmicrotech.com
User Guide Supplement. S/MIME Support Package for BlackBerry Smartphones BlackBerry Pearl 8100 Series
 User Guide Supplement S/MIME Support Package for BlackBerry Smartphones BlackBerry Pearl 8100 Series SWD-292878-0324093908-001 Contents Certificates...3 Certificate basics...3 Certificate status...5 Certificate
User Guide Supplement S/MIME Support Package for BlackBerry Smartphones BlackBerry Pearl 8100 Series SWD-292878-0324093908-001 Contents Certificates...3 Certificate basics...3 Certificate status...5 Certificate
NACCU 2013. Migrating to Contactless: 2013 1
 NACCU 2013 Migrating to Contactless: 2013 1 AGENDA The demise of cards has been predicted for many years. When will this really happen? This presentation by two card industry experts will cover the rise
NACCU 2013 Migrating to Contactless: 2013 1 AGENDA The demise of cards has been predicted for many years. When will this really happen? This presentation by two card industry experts will cover the rise
Best Practices for the Use of RF-Enabled Technology in Identity Management. January 2007. Developed by: Smart Card Alliance Identity Council
 Best Practices for the Use of RF-Enabled Technology in Identity Management January 2007 Developed by: Smart Card Alliance Identity Council Best Practices for the Use of RF-Enabled Technology in Identity
Best Practices for the Use of RF-Enabled Technology in Identity Management January 2007 Developed by: Smart Card Alliance Identity Council Best Practices for the Use of RF-Enabled Technology in Identity
Overview of Contactless Payment Cards. Peter Fillmore. July 20, 2015
 Overview of Contactless Payment Cards Peter Fillmore July 20, 2015 Blackhat USA 2015 Introduction Contactless payments have exploded in popularity over the last 10 years with various schemes being popular
Overview of Contactless Payment Cards Peter Fillmore July 20, 2015 Blackhat USA 2015 Introduction Contactless payments have exploded in popularity over the last 10 years with various schemes being popular
Improving Online Security with Strong, Personalized User Authentication
 Improving Online Security with Strong, Personalized User Authentication July 2014 Secure and simplify your digital life. Table of Contents Online Security -- Safe or Easy, But Not Both?... 3 The Traitware
Improving Online Security with Strong, Personalized User Authentication July 2014 Secure and simplify your digital life. Table of Contents Online Security -- Safe or Easy, But Not Both?... 3 The Traitware
OBM (Out of Band Management) Overview
 OBM (Out of Band Management) Overview With the growth of IP, routers deployed into an IP network must not only be accessible by the network operator for maintenance and configuration purposes, but secure
OBM (Out of Band Management) Overview With the growth of IP, routers deployed into an IP network must not only be accessible by the network operator for maintenance and configuration purposes, but secure
Cent ralized Out -Of-Band Aut hent ic at ion Syst em. Authentication Security for the 21 st Century
 Cent ralized Out -Of-Band Aut hent ic at ion Syst em Security for the 21 st Century Presented by: Southeast Europe Cybersecurity Conference Sophia, Bulgaria September 8-9, 2003 Introduction Organizations
Cent ralized Out -Of-Band Aut hent ic at ion Syst em Security for the 21 st Century Presented by: Southeast Europe Cybersecurity Conference Sophia, Bulgaria September 8-9, 2003 Introduction Organizations
Self-Service, Anywhere
 2015 Hitachi ID Systems, Inc. All rights reserved. Contents 1 Introduction 1 2 Mobile users warned of password expiry 2 3 Reset forgotten, cached password while away from the office 2 4 Unlock encrypted
2015 Hitachi ID Systems, Inc. All rights reserved. Contents 1 Introduction 1 2 Mobile users warned of password expiry 2 3 Reset forgotten, cached password while away from the office 2 4 Unlock encrypted
The Canadian Migration to EMV. Prepared By:
 The Canadian Migration to EMV Prepared By: December 1993 Everyone But The USA Is Migrating The international schemes decided Smart Cards are the way forward Europay, MasterCard & Visa International Produced
The Canadian Migration to EMV Prepared By: December 1993 Everyone But The USA Is Migrating The international schemes decided Smart Cards are the way forward Europay, MasterCard & Visa International Produced
Prerequisite. Getting Started. Email Signing and Encryption using Microsoft outlook 2007
 Email Signing and Encryption using Microsoft outlook 2007 Prerequisite a. The user s email account has been added and correctly configured into Microsoft outlook. b. The user has an authentication certificate.
Email Signing and Encryption using Microsoft outlook 2007 Prerequisite a. The user s email account has been added and correctly configured into Microsoft outlook. b. The user has an authentication certificate.
EMV and Restaurants What you need to know! November 19, 2014
 EMV and Restaurants What you need to know! Mike English Executive Director of Product Development Kristi Kuehn Sr. Director, Compliance November 9, 204 Agenda EMV overview Timelines Chip Card Liability
EMV and Restaurants What you need to know! Mike English Executive Director of Product Development Kristi Kuehn Sr. Director, Compliance November 9, 204 Agenda EMV overview Timelines Chip Card Liability
SECURITY SYSTEM MANAGEMENT SOFTWARE FOR WINDOWS. Quick Start Instructions
 TM SECURITY SYSTEM MANAGEMENT SOFTWARE FOR WINDOWS Quick Start Instructions Introduction WinLoad for Windows was developed to simplify and speed up the task of programming Paradox control panels. Remote
TM SECURITY SYSTEM MANAGEMENT SOFTWARE FOR WINDOWS Quick Start Instructions Introduction WinLoad for Windows was developed to simplify and speed up the task of programming Paradox control panels. Remote
Apps for Android. Apps for iphone & ipad INS584-3
 Apps for iphone & ipad INS584-3 Apps for Android Android is a trademark of Google Inc. iphone is a trademark of Apple Inc., registered in the U.S. and other countries. ipad is a trademark of Apple Inc.,
Apps for iphone & ipad INS584-3 Apps for Android Android is a trademark of Google Inc. iphone is a trademark of Apple Inc., registered in the U.S. and other countries. ipad is a trademark of Apple Inc.,
Mobile and Contactless Payment Security
 Mobile and Contactless Payment Security v20111118 1/842 High Street East Kew 3102 Melbourne Australia Ph: +61 3 9846 2751 Fax: +61 3 9857 0350 Rambla de Catalunya 38, 8 planta 08007 Barcelona Spain Ph.
Mobile and Contactless Payment Security v20111118 1/842 High Street East Kew 3102 Melbourne Australia Ph: +61 3 9846 2751 Fax: +61 3 9857 0350 Rambla de Catalunya 38, 8 planta 08007 Barcelona Spain Ph.
GPC JagTalk Secure Wireless Network. Connection Instructions
 GPC JagTalk Secure Wireless Network Connection Instructions Contents Windows 10... 2 Windows 7... 4 Windows 8 / Surface... 6 Android... 7 BlackBerry... 9 Mac OS X... 10 Apple ios Devices... 12 1 Connecting
GPC JagTalk Secure Wireless Network Connection Instructions Contents Windows 10... 2 Windows 7... 4 Windows 8 / Surface... 6 Android... 7 BlackBerry... 9 Mac OS X... 10 Apple ios Devices... 12 1 Connecting
EMV-TT. Now available on Android. White Paper by
 EMV-TT A virtualised payment system with the following benefits: MNO and TSM independence Full EMV terminal and backend compliance Scheme agnostic (MasterCard and VISA supported) Supports transactions
EMV-TT A virtualised payment system with the following benefits: MNO and TSM independence Full EMV terminal and backend compliance Scheme agnostic (MasterCard and VISA supported) Supports transactions
Security and the Mitel Teleworker Solution
 Security and the Mitel Teleworker Solution White Paper July 2007 Copyright Copyright 2007 Mitel Networks Corporation. This document is unpublished and the following notice is affixed to protect Mitel Networks
Security and the Mitel Teleworker Solution White Paper July 2007 Copyright Copyright 2007 Mitel Networks Corporation. This document is unpublished and the following notice is affixed to protect Mitel Networks
Installation and Setup Guide
 Installation and Setup Guide Contents 1. Introduction... 1 2. Before You Install... 3 3. Server Installation... 6 4. Configuring Print Audit Secure... 11 5. Licensing... 16 6. Printer Manager... 17 7.
Installation and Setup Guide Contents 1. Introduction... 1 2. Before You Install... 3 3. Server Installation... 6 4. Configuring Print Audit Secure... 11 5. Licensing... 16 6. Printer Manager... 17 7.
Basic Software Setup Guide. www.easyclocking.com
 1 Basic Software Setup Guide www.easyclocking.com 2 Table of Contents Software registration 3 How to connect the time clock.. 5 How to turn the time clock on 5 Defining the type of connection... 5 TCP/IP
1 Basic Software Setup Guide www.easyclocking.com 2 Table of Contents Software registration 3 How to connect the time clock.. 5 How to turn the time clock on 5 Defining the type of connection... 5 TCP/IP
MOBILE AGENT BANKING SYSTEM PRODUCT BENEFITS AND FEATURES
 MOBILE AGENT BANKING SYSTEM PRODUCT BENEFITS AND FEATURES Version 1.1 January 2013 INTRODUCTION This document provides at one glance all the features of maviance Mobile Microfinance System. It aims to
MOBILE AGENT BANKING SYSTEM PRODUCT BENEFITS AND FEATURES Version 1.1 January 2013 INTRODUCTION This document provides at one glance all the features of maviance Mobile Microfinance System. It aims to
Prerequisite. Getting Started. Email Signing and Encryption using Microsoft outlook 2010
 Email Signing and Encryption using Microsoft outlook 2010 Prerequisite a. The user s email account has been added and correctly configured into Microsoft outlook. b. The user has an authentication certificate.
Email Signing and Encryption using Microsoft outlook 2010 Prerequisite a. The user s email account has been added and correctly configured into Microsoft outlook. b. The user has an authentication certificate.
Securing Card-Not-Present Transactions through EMV Authentication. Matthew Carter and Brienne Douglas December 18, 2015
 Securing Card-Not-Present Transactions through EMV Authentication Matthew Carter and Brienne Douglas December 18, 2015 Outline Problem Card-Not-Present (CNP) vs. PayPal EMV Technology EMV CNP Experiment
Securing Card-Not-Present Transactions through EMV Authentication Matthew Carter and Brienne Douglas December 18, 2015 Outline Problem Card-Not-Present (CNP) vs. PayPal EMV Technology EMV CNP Experiment
DIGIPASS Authentication for GajShield GS Series
 DIGIPASS Authentication for GajShield GS Series With Vasco VACMAN Middleware 3.0 2008 VASCO Data Security. All rights reserved. Page 1 of 1 Integration Guideline Disclaimer Disclaimer of Warranties and
DIGIPASS Authentication for GajShield GS Series With Vasco VACMAN Middleware 3.0 2008 VASCO Data Security. All rights reserved. Page 1 of 1 Integration Guideline Disclaimer Disclaimer of Warranties and
How To Industrial Networking
 How To Industrial Networking Prepared by: Matt Crites Product: Date: April 2014 Any RAM or SN 6xxx series router Legacy firmware 3.14/4.14 or lower Subject: This document provides a step by step procedure
How To Industrial Networking Prepared by: Matt Crites Product: Date: April 2014 Any RAM or SN 6xxx series router Legacy firmware 3.14/4.14 or lower Subject: This document provides a step by step procedure
FedTraveler.com. Log o FedTraveler.com using your valid Member ID and PIN.
 FedTraveler.com Log o FedTraveler.com using your valid Member ID and PIN. Page 3 / 38 FedTraveler.com S een will refresh to Organizer page Page 4 / 38 Organizer 3. On he Organizer Page, click the link
FedTraveler.com Log o FedTraveler.com using your valid Member ID and PIN. Page 3 / 38 FedTraveler.com S een will refresh to Organizer page Page 4 / 38 Organizer 3. On he Organizer Page, click the link
Internet Access: Wireless WVU.Encrypted Network Connecting a Windows 7 Device
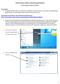 Internet Access: Wireless WVU.Encrypted Network Connecting a Windows 7 Device Prerequisites An activated MyID account is required to use ResNet s wireless network. If you have not activated your MyID account,
Internet Access: Wireless WVU.Encrypted Network Connecting a Windows 7 Device Prerequisites An activated MyID account is required to use ResNet s wireless network. If you have not activated your MyID account,
GMS GRAPHICAL MANAGEMENT SYSTEM
 GMS GRAPHICAL MANAGEMENT SYSTEM 1 GMS The integrated security management system for multi-site organizations. Pacom s Graphical Management System (GMS) is the modular client-server application that integrates
GMS GRAPHICAL MANAGEMENT SYSTEM 1 GMS The integrated security management system for multi-site organizations. Pacom s Graphical Management System (GMS) is the modular client-server application that integrates
ROAMpay powered by ROAM
 ROAMpay powered by ROAM Table of Contents 1. Introduction 2. Setting up Service 3. Supporting ROAMpay Customers 4. Helpful Links and Contacts 5. ROAMpay User s Guide Welcome to ROAMpay powered by ROAM!
ROAMpay powered by ROAM Table of Contents 1. Introduction 2. Setting up Service 3. Supporting ROAMpay Customers 4. Helpful Links and Contacts 5. ROAMpay User s Guide Welcome to ROAMpay powered by ROAM!
Increase revenue. Reduce operating costs. Improve efficiencies. Accomplish all this and more with eselectplus.
 Increase revenue. Reduce operating costs. Improve efficiencies. Accomplish all this and more with eselectplus. eselectplus makes payment simple for you, and for your customers. eselectplus is an easy-to-use,
Increase revenue. Reduce operating costs. Improve efficiencies. Accomplish all this and more with eselectplus. eselectplus makes payment simple for you, and for your customers. eselectplus is an easy-to-use,
Business Mobile App User Guide
 Business Mobile App User Guide Logging On to CNB Business Mobile Logging on to CNB Business Mobile involves the same layers of authentication as your Online For Business account does. 1. Launch the app
Business Mobile App User Guide Logging On to CNB Business Mobile Logging on to CNB Business Mobile involves the same layers of authentication as your Online For Business account does. 1. Launch the app
GOALS (2) The goal of this training module is to increase your awareness of HSPD-12 and the corresponding technical standard FIPS 201.
 PERSONAL IDENTITY VERIFICATION (PIV) OVERVIEW INTRODUCTION (1) Welcome to the Homeland Security Presidential Directive 12 (HSPD-12) Personal Identity Verification (PIV) Overview module, designed to familiarize
PERSONAL IDENTITY VERIFICATION (PIV) OVERVIEW INTRODUCTION (1) Welcome to the Homeland Security Presidential Directive 12 (HSPD-12) Personal Identity Verification (PIV) Overview module, designed to familiarize
Amlib Library Software: Equipment & Asset Tracking Management System
 Amlib Library Software: Equipment & Asset Tracking Management System Included in the Amlib Library System is a comprehensive Equipment & Asset Tracking Management System. This is implemented by a wide
Amlib Library Software: Equipment & Asset Tracking Management System Included in the Amlib Library System is a comprehensive Equipment & Asset Tracking Management System. This is implemented by a wide
Last Modified June 2008
 Payment Gateway Virtual Terminal Last Modified June 2008 E-Business the easy way! Website: www.vcs.co.za Contact: +27 (0) 11 257 6222 E-mail: sales@vcs.co.za Virtual Card Services (Pty) Ltd Registration
Payment Gateway Virtual Terminal Last Modified June 2008 E-Business the easy way! Website: www.vcs.co.za Contact: +27 (0) 11 257 6222 E-mail: sales@vcs.co.za Virtual Card Services (Pty) Ltd Registration
DIGIPASS Authentication for Citrix Access Gateway VPN Connections
 DIGIPASS Authentication for Citrix Access Gateway VPN Connections With VASCO Digipass Pack for Citrix 2006 VASCO Data Security. All rights reserved. Page 1 of 31 Integration Guideline Disclaimer Disclaimer
DIGIPASS Authentication for Citrix Access Gateway VPN Connections With VASCO Digipass Pack for Citrix 2006 VASCO Data Security. All rights reserved. Page 1 of 31 Integration Guideline Disclaimer Disclaimer
How to use Certificate in Microsoft Outlook
 How to use Certificate in Microsoft Outlook Macau Post esigntrust Version. 2006-01.01p Agenda Configure Microsoft Outlook for using esigntrust Certificate Use certificate to sign e-mail Use Microsoft Outlook
How to use Certificate in Microsoft Outlook Macau Post esigntrust Version. 2006-01.01p Agenda Configure Microsoft Outlook for using esigntrust Certificate Use certificate to sign e-mail Use Microsoft Outlook
ENHANCING ATM SECURITY USING FINGERPRINT AND GSM TECHNOLOGY
 Available Online at www.ijcsmc.com International Journal of Computer Science and Mobile Computing A Monthly Journal of Computer Science and Information Technology IJCSMC, Vol. 3, Issue. 4, April 2014,
Available Online at www.ijcsmc.com International Journal of Computer Science and Mobile Computing A Monthly Journal of Computer Science and Information Technology IJCSMC, Vol. 3, Issue. 4, April 2014,
Safe Arrival Parent Portal PARENT INSTRUCTIONS
 York Catholic District School Board Safe Arrival Parent Portal PARENT INSTRUCTIONS Introduction Our school uses the Safe Arrival program to manage student attendance reporting. The Safe Arrival program
York Catholic District School Board Safe Arrival Parent Portal PARENT INSTRUCTIONS Introduction Our school uses the Safe Arrival program to manage student attendance reporting. The Safe Arrival program
BIOMETRIC SOLUTIONS 2013 ISSUE
 BIOMETRIC SOLUTIONS 2013 ISSUE Southern Supplies Limited (SSL) was established on January 14th 1982 with one aim in mind : "To be the preferred supplier to the industries we service." Over time, our expertise
BIOMETRIC SOLUTIONS 2013 ISSUE Southern Supplies Limited (SSL) was established on January 14th 1982 with one aim in mind : "To be the preferred supplier to the industries we service." Over time, our expertise
The next generation of knowledge and expertise Wireless Security Basics
 The next generation of knowledge and expertise Wireless Security Basics HTA Technology Security Consulting., 30 S. Wacker Dr, 22 nd Floor, Chicago, IL 60606, 708-862-6348 (voice), 708-868-2404 (fax), www.hta-inc.com
The next generation of knowledge and expertise Wireless Security Basics HTA Technology Security Consulting., 30 S. Wacker Dr, 22 nd Floor, Chicago, IL 60606, 708-862-6348 (voice), 708-868-2404 (fax), www.hta-inc.com
PkBox Technical Overview. Ver. 1.0.7
 PkBox Technical Overview Ver. 1.0.7 14 September 2015 All the information in this document is and can t be used entirely or in part without a written permission from Intesi Group S.p.A. Le informazioni
PkBox Technical Overview Ver. 1.0.7 14 September 2015 All the information in this document is and can t be used entirely or in part without a written permission from Intesi Group S.p.A. Le informazioni
2100-9 Series VoIP Phone
 2100-9 Series VoIP Phone Installation and Operations Manual Made in the USA 3 Year Warranty N56 W24720 N. Corporate Circle Sussex, WI 53089 RP8500SIP 800-451-1460 262-246-4828 (fax) Ver. 3 12/14 Thank
2100-9 Series VoIP Phone Installation and Operations Manual Made in the USA 3 Year Warranty N56 W24720 N. Corporate Circle Sussex, WI 53089 RP8500SIP 800-451-1460 262-246-4828 (fax) Ver. 3 12/14 Thank
Accessing the Media General SSL VPN
 Launching Applications and Mapping Drives Remote Desktop Outlook Launching Web Applications Full Access VPN Note: To access the Media General VPN, anti-virus software must be installed and running on your
Launching Applications and Mapping Drives Remote Desktop Outlook Launching Web Applications Full Access VPN Note: To access the Media General VPN, anti-virus software must be installed and running on your
Implementation Guide for. Juniper SSL VPN SSO with OWA. with. BlackShield ID
 Implementation Guide for Juniper SSL VPN SSO with OWA with BlackShield ID Copyright 2009 CRYPTOCard Inc. http:// www.cryptocard.com Copyright Copyright 2009, CRYPTOCard All Rights Reserved. No part of
Implementation Guide for Juniper SSL VPN SSO with OWA with BlackShield ID Copyright 2009 CRYPTOCard Inc. http:// www.cryptocard.com Copyright Copyright 2009, CRYPTOCard All Rights Reserved. No part of
Netop Remote Control Security Server
 A d m i n i s t r a t i o n Netop Remote Control Security Server Product Whitepaper ABSTRACT Security is an important factor when choosing a remote support solution for any enterprise. Gone are the days
A d m i n i s t r a t i o n Netop Remote Control Security Server Product Whitepaper ABSTRACT Security is an important factor when choosing a remote support solution for any enterprise. Gone are the days
Design and Implementation of Automatic Attendance Check System Using BLE Beacon
 , pp.177-186 http://dx.doi.org/10.14257/ijmue.2015.10.10.19 Design and Implementation of Automatic Attendance Check System Using BLE Beacon Mi-Young Bae and Dae-Jea Cho * Dept. Of Multimedia Engineering,
, pp.177-186 http://dx.doi.org/10.14257/ijmue.2015.10.10.19 Design and Implementation of Automatic Attendance Check System Using BLE Beacon Mi-Young Bae and Dae-Jea Cho * Dept. Of Multimedia Engineering,
Using Contactless Smart Cards for Secure Applications
 Using Contactless Smart Cards for Secure Applications Classification: Public (Info Level 1) Document No.: LA-11-005d-en Edition: 2010 www.legic.com LEGIC Identsystems Ltd Binzackerstrasse 41, CH-8620 Wetzikon,
Using Contactless Smart Cards for Secure Applications Classification: Public (Info Level 1) Document No.: LA-11-005d-en Edition: 2010 www.legic.com LEGIC Identsystems Ltd Binzackerstrasse 41, CH-8620 Wetzikon,
- BIOMETRIC. Tel : +65-6286 8300 Website : www.litestar.com.sg marketing@litestar.com.sg
 Security & Time Attendance System - BIOMETRIC LiteStar Singapore Pte Ltd LiteStar Singapore Pte Ltd Tel : +65-6286 8300 Website : www.litestar.com.sg marketing@litestar.com.sg Biometric Systems Biometrics
Security & Time Attendance System - BIOMETRIC LiteStar Singapore Pte Ltd LiteStar Singapore Pte Ltd Tel : +65-6286 8300 Website : www.litestar.com.sg marketing@litestar.com.sg Biometric Systems Biometrics
Verification of digitally signed PDFs
 Verification of digitally signed PDFs Configuring Adobe Reader to verify digitally signed PDFs This document is freely redistributable. You can find the latest version at: http://www.netlock.hu/useren
Verification of digitally signed PDFs Configuring Adobe Reader to verify digitally signed PDFs This document is freely redistributable. You can find the latest version at: http://www.netlock.hu/useren
DESLock+ Basic Setup Guide Version 1.20, rev: June 9th 2014
 DESLock+ Basic Setup Guide Version 1.20, rev: June 9th 2014 Contents Overview... 2 System requirements:... 2 Before installing... 3 Download and installation... 3 Configure DESLock+ Enterprise Server...
DESLock+ Basic Setup Guide Version 1.20, rev: June 9th 2014 Contents Overview... 2 System requirements:... 2 Before installing... 3 Download and installation... 3 Configure DESLock+ Enterprise Server...
Citrix Web Client Installation and CAC Registration Guide
 Citrix Web Client Installation and CAC Registration Guide Prepared By: Department of Defense Education Activity 1 Revision 1.1 To ensure a reasonably smooth process of establishing connectivity with the
Citrix Web Client Installation and CAC Registration Guide Prepared By: Department of Defense Education Activity 1 Revision 1.1 To ensure a reasonably smooth process of establishing connectivity with the
