Business Process Mining for Internal Fraud Risk Reduction: Results of a Case Study
|
|
|
- Ronald Booth
- 8 years ago
- Views:
Transcription
1 Business Process Mining for Internal Fraud Risk Reduction: Results of a Case Study Mieke Jans Nadine Lybaert Koen Vanhoof Jan Martijn van der Werf Abstract Corporate fraud these days represents a huge cost to our economy. Academic literature merely concentrates on the fight against external fraud, while internal fraud also represents a major problem. In this paper we discuss the use of process mining to reduce the risk of internal fraud. This suggestion results in an extension of the IFR 2 framework, presented by Jans et al. (2009). Process mining diagnoses processes by mining event logs. This way we can expose opportunities to commit fraud in the process design. We present the extended IFR 2 framework as a complement to the internal control framework of the COSO and apply this framework in a case company. 1 Introduction Everybody can recall some kind of fraud that has been all over the news. If it were Enron, WorldCom, Lernout & Hauspie, Ahold, Société Générale or another case does not matter. Fact is that fraud has become a serious part of our life and hence a serious cost to our economy. Several studies on this phenomenon report shocking numbers: forty-three percent of companies worldwide have fallen victim to economic crime in the years 2006 and 2007 (PwC, 2007). The average financial damage to companies subjected to this survey was US$ 2.42 million per company over two years. Participants of another study (ACFE, 2006) 1 estimate a loss of five percent of a company s annual revenues to fraud. Applied to the 2006 United States Gross Domestic Product of US$ 13,246.6 billion, this would translate to approximately US$ 662 billion in fraud losses for the United States only. These numbers all address corporate fraud. 1 The Association of Certified Fraud Examiners (ACFE) is the world s premier provider of anti-fraud training and education. Together with nearly 40,000 members, the ACFE is reducing business fraud worldwide and inspiring public confidence in the integrity and objectivity within the profession. ( 1
2 There are several types of corporate fraud. The most prominent distinction one can make in fraud classification is internal versus external fraud, a classification based on the relationship the perpetrator has to the victim company. Management fraud is an example of internal fraud, where insurance fraud is a classic example of external fraud. In this paper we present the Extended IFR 2 framework, based on Jans et al. (2009) s IFR 2 framework, aimed at internal fraud risk reduction. Risk reduction comprehends both fraud detection and prevention and the framework is for both academics to investigate how to reduce internal fraud risk and for organizations. In a previous paper, the IFR 2 framework with data mining being the core to reduce internal fraud risk is presented. (Jans et al., 2009) In this paper we complement that framework with a process mining part, resulting in the extended IFR 2 framework. Process mining aims at uncovering a process model based on real transaction logs. This relative new research domain can be applied in several ways for the purpose of internal fraud risk reduction. We start the paper with an introduction in internal fraud and internal control, since our framework is suggested as a complement to the internal control framework. In the next section we present our framework, followed by an introduction in process mining. Because the concepts of continuous auditing and continuous monitoring have a lot in common with the presented work, these concepts are shortly mentioned in Section 5. In Section 6 we present the application of our framework in a case company. We end with a conclusion. 2 Internal Fraud and Internal Control In this paper, we consider the threat of internal fraud. For internal corporate fraud we rely on the definition of occupational fraud and abuse by the ACFE: The use of one s occupation for personal enrichment through the deliberate misuse or misapplication of the employing organization s resources or assets. (ACFE, 2006) This definition encompasses a wide variety of conduct by executives, employees, managers, and principals of organizations. Violations can range from asset misappropriation, fraudulent statements and corruption over pilferage and petty theft, false overtime, using company property for personal benefit to payroll and sick time abuses. Where the academic field does not pay much of attention to internal fraud (merely to external fraud), it has received a great deal of attention from other interested parties. The emergence of fraud into our economic world didn t go unnoticed. In 2002, a US fraud standard (SAS 99) was created and by the end of 2004 also an international counterpart (ISA 240) was effective. Meanwhile, the CEO s of the International Audit Networks released 2
3 a special report in November 2006: Global Capital Markets and the Global Economy: A Vision From the CEOs of the International Audit Networks. This report, issued by the six largest global audit networks, is released in the wake of corporate scandals. The authors of this report express their believe in mitigating fraud, as they name it one of the six vital elements, necessary for capital market stability, efficiency and growth. The remaining five elements concern investor needs for information, the alignment and support of the roles of various stakeholders, the auditing profession, reporting and information quality. The threat of internal fraud was first officially recognized in 1985 when the (US) National Commission on Fraudulent Financial Reporting (known as the Treadway Commission) was formed. To study the causes of fraudulent reporting and make recommendations to reduce its incidence, the Treadway Commission issued a final report in 1987 with recommendations for auditors, public companies, regulators, and educators. This report re-emphasized the importance of internal control in reducing the incidence of fraudulent financial reporting and included a recommendation for all public companies to maintain internal controls. The Committee of Sponsoring Organizations of the Treadway Commission (COSO) 2 was formed to commission the Treadway Commission to perform its task. In response to this recommendation, COSO developed an internal control framework, issued in 1992 and entitled Internal Control - Integrated Framework. According to the COSO framework, internal control is defined as: A process, effected by the entity s board of directors, management, and other personnel, designed to provide reasonable assurance regarding the achievement of objectives in the following categories: Effectiveness and efficiency of operations Reliability of financial reporting Compliance with applicable laws and regulations In meanwhile, COSO issued in 2004 a revision of the Internal Control - Integrated Framework under the title of Enterprise Risk Management Framework, expanding on internal control to the broader subject of enterprise risk management. (Cosserat, 2004; Davia et al., 2000; Whittington and Pany, 1998) Following this broad definition, internal control can both prevent and 2 The sponsoring accounting organizations include the American Institute of Certified Public Accountants (AICPA), the American Accounting Association (AAA), the Financial Executives Institute (FEI), the Institute of Internal Auditors (IIA), and the Institute of Management Accountants (IMA). 3
4 detect fraud. And although this definition is stemming from the foundation of the National Commission on Fraudulent Financial Reporting, also other classes of fraud than fraudulent financial reporting can be encountered. Also the studies of PwC and the ACFE mentioned before, reveal some information concerning the detection of internal fraud. Internal control seems to deliver an effective tool in the fight against internal fraud. So from different angles, internal control is considered to be a means that has the ability to fight internal fraud. Likewise, in a business environment internal fraud is currently dealt with by internal control. As mentioned before, internal control encompasses a wide variety of tasks and settings. Next to a qualitative approach (like for example creating a control environment), quantitative data analyzing is required. It is at this point we believe there lies an opportunity to combine academic research with practical insights. In another paper by Jans et al. (2009) a data mining approach is proposed as a complement to the internal control framework, leading to the IFR 2 framework. The focus hereby lies on fraud risk reduction, which includes both fraud prevention and fraud detection, just like internal control. For a detailed description of the IFR 2 framework, we refer to Jans et al. (2009). In this paper, we wish to introduce yet another complement to the internal control framework, a second path. Where the first complementary advise for internal fraud risk reduction is to apply a data mining approach, we now suggest to also apply a process mining approach. Process mining is a relative new research domain and aims to extract an a posteriori process model from stored transaction logs. This enables Delta analysis, i.e. detecting discrepancies between the process design constructed in the design phase and the actual execution in the enactment phase (van der Aalst et al., 2003). This kind of analysis is important in the light of defining opportunities to commit fraud. Our suggestion is poured into an extension of the IFR 2 framework, leading to the extended IFR 2 framework. We will discuss the framework and the underlying ideas in the following section. 3 The Extended IFR 2 Framework The extended IFR 2 framework, provides both a guidance for the empirical part of our study and a framework for other researchers to help in their approach to reduce internal fraud risk. In Figure 1 one can find the extended version of the original IFR 2 framework. The left (shaded) branch of the framework is the part which was introduced in the former paper so we will not go into detail about this. We refer to our previous work for more information on that part. In this paper we wish to present the right branch of the framework. The core of our extension is to apply process mining. As indicated before, 4
5 Select business process with advanced IT integration Data collection, manipulation and enrichment Domain Knowledge Transformation of data Descriptive Data Mining INTERNAL FRAUD RISK REDUCTION Process Mining Audit by domain experts: extreme values fraud circumventing procedures errors/mistakes FRAUD DETECTION & FRAUD PREVENTION Opportunity Domain Experts Fraud risk Rationalisation Incentive/Pressure Figure 1: The extended IFR 2 framework, integrating process mining this gives -for starters- the ability to perform a Delta analysis. An organization has business processes mapped out in procedures, guidelines, user guides etcetera. In the process mining step, we visualize the actual process that occurs in a certain business unit instead of the designed process. This way one can detect flows or sub flows that for example were not meant to exist. This can give insights in potential ways of misusing or abusing the system. Aside from a Delta analysis, process mining also provides the possibility to specifically monitor internal controls, like for example the four-eyes principle or the segregation of duty. As opposed to currently wide used internal control tests, the process mining approach for monitoring internal control is data oriented, and not system oriented. In other words: we are able to test whether the true transactional data (the output of the internal control system) are effectively submitted to the presumed internal controls. Instead of testing whether the internal control settings function by means of performing a set of random tests, we mine the actual submitted data and are able to test whether all conditions are met. This provides a whole new view on monitoring internal controls. 5
6 Another advantage of applying process mining is that, just like with the data mining application, it is not necessary to have a specific fraud in mind. Further surplus value is delivered by the objectivity with which the process mining techniques work, without making any presuppositions. We see the Delta analysis as a starting point to evaluate with an open mind what opportunities these deviations can mean for a perpetrator. When one has a specific fraud in mind when interpreting the analysis and looking if there are opportunities to commit this specific fraud, one can be blind for other opportunities. On the other hand, when mining the organizational and the case perspective (see below), it can be beneficial to have some specific fraud(s) in mind. This is certainly the case when monitoring internal controls. At this stage specific internal controls, motivated by specific frauds in mind, are monitored and checked. After applying process mining, feedback from and to the domain experts is needed to interpret the results. This will eventually lead to new insights whether or not there are opportunities to commit fraud. It is the element Opportunity of Cressey s hypothesis that makes it interesting to gain these insights. Cressey s hypothesis, better known as the fraud triangle, sees three elements necessary for someone to commit fraud. There has to be pressure (or a perceived non-shareable financial need ), a perceived opportunity and the perpetrator must be able to rationalize its acts. (Wells, 2005) The fraud triangle is cited many times in fraud literature and has become an important hypothesis. Opportunity is the only fraud triangle element an organization can exert influence on and hence is most important in our framework. Also according to Albrecht et al. (1984) s fraud scale opportunity is an element of influence on fraud risk. As can be seen, the process mining part of the framework works primarily on fraud prevention. However, the information gathered from this analysis, can be used as exploratory research and implemented in the data mining part. This way, process mining can indirectly also lead to fraud detection. Before turning to the case study where our extended IFR 2 framework is applied, we give a short introduction to process mining and the ProM framework. 4 Process Mining Nowadays many different information systems, like ERP, WFM, CRM and B2B systems, are characterized by the omnipresence of logs. Typically, these information systems record information about the usage of the system by its users. These logs contain information about the instances, also called cases, processed in the system, the activities executed for each instance, at what time the activities were executed and by whom. Some systems also 6
7 Table 1: An example of an event log, used by van der Aalst et al. (2007). Case id Activity id Originator Timestamp case 1 activity A John :15.01 case 2 activity A John :15.12 case 3 activity A Sue :16.03 case 3 activity B Carol :16.07 case 1 activity B Mike :18.25 case 1 activity C John :9.23 case 2 activity C Mike :10.34 case 4 activity A Sue :10.35 case 2 activity B John :12.34 case 2 activity D Pete :12.50 case 5 activity A Sue :13.05 case 4 activity C Carol :10.12 case 1 activity D Pete :10.14 case 3 activity C Sue :10.44 case 3 activity D Pete :11.03 case 4 activity B Sue :11.18 case 5 activity E Clare :12.22 case 5 activity D Clare :14.34 case 4 activity D Pete :15.56 contain information about the data users entered for each activity. However, this data is not actively used by the organization to analyze the underlying processes supported by the system. Process mining aims to make a difference. The basic idea of process mining is to diagnose processes by mining event logs for knowledge (van der Aalst and de Medeiros, 2005). It allows to analyze these event logs, sometimes also referred to as audit trail, transaction log or history. Records in these logs are called events. In process mining, each event needs to refer to an activity for a specific case. Preferably, each event also refers to the performer, the originator of the event, and a time stamp. For each process under investigation these are the constraining assumptions. If available data fulfills these assumptions, process mining can be applied on that particular process. Table 1 shows a classic example of an event log, used by van der Aalst et al. (2007), van Dongen et al. (2005) and van der Aalst and de Medeiros (2005) amongst others. The event log shows an example with 19 events, allocated to five cases, describing five different activities, performed by six persons. Event logs are the starting point of process mining. The data of the event log can be mined and different aspects about the underlying process can be analyzed. In general, three different perspectives can be distinguished: the process perspective, the organizational perspective and the case perspective. The process perspective or the How? question focuses on the ordering of activities, i.e. it tries to answer the question Which paths are followed? 7
8 This is typically expressed in graphical process models, using a formalism like Petri Nets, Event-driven Process Chain (EPC) or BPMN. The organizational perspective or the Who? question focuses on the users, the originators, that play a role within the process. In this perspective, underlying relations between performers or between performers and tasks can be exposed. The case perspective or the What? question focuses on a case in isolation. Typically, for this analysis, the log needs to be enriched by extra data about the case. This can be data about the case, or data for a specific event, like the data submitted at the event (van der Aalst et al., 2007). In the context of internal fraud risk reduction and the broader framework we place process mining in, an important perspective to start with is the process perspective. In a later stage, we turn to the organizational and the case perspective. Therefore, in this study we will start with the process perspective to expose opportunities to commit fraud within a company. Afterwards, we turn to the other perspectives, mostly in the light of monitoring controls (see Section 5). For this study, the open-source tool ProM (??, Aal) is used. ProM consists of many different algorithms to cover the analysis of the three perspectives. ProM is designed in such a way that researchers and users can easily develop their own plugins and add them to the framework. For more information about ProM, we refer the reader to van Dongen et al. (2005) and to 5 Continuous Auditing and Monitoring Traditionally, internal audits and their related testing of controls are executed on a cyclical basis. Auditors typically check random samples, and use simple checklists to audit an organization. However, with the electronic storage of all kinds of data, easily accessible and available in large volumes, new methods of internal auditing can be developed and implemented. Already, advanced technology has been employed to perform continuous auditing. Continuous auditing is defined as a framework for issuing audit reports simultaneously with, or a short period of time after, the occurrence of the relevant events (CICA/AICPA, 1999). An important subset of continuous auditing is the continuous monitoring of business process controls (Alles et al., 2006). Continuous monitoring of controls is defined by the Institute of Internal Auditors as a process that management puts in place to ensure that its policies and procedures are adhered to, and that business processes are operating effectively. Continuous monitoring typically involves automated continuous testing of all transactions within a given business process area against a suite of controls rules. (IIA, 2005) Notice that continuous mon- 8
9 itoring is a responsibility management bears, while continuous auditing is a task of the internal audit department. However, there is an interaction effect between the efforts put into place concerning continuous monitoring and continuous auditing. When management performs continuous monitoring on a comprehensive basis, the internal audit department can partly rely on this and no longer needs to perform the same detailed techniques as it otherwise would have under continuous auditing. (IIA, 2005) In her framework, COSO also identifies the monitoring of controls as one of the five components of internal control. The remaining four components are the control environment, the entity s risk assessment process, the information system and control activities. Employees need to know that noncompliance with controls is likely to be detected (deterrence effect). Monitoring controls also provides feedback concerning these controls (Cosserat, 2004). We can conclude that the (continuous) monitoring of controls is certainly an activity that contributes to internal fraud risk reduction. The reason that we introduce the concept of continuous monitoring here, is that process mining provides a way of implementing such a continuous monitoring system. Process mining can help in different aspects of monitoring and auditing. As all actions of each case are recorded by the system, one can check the process, rather than taking random samples. Secondly, process mining can help in the discovery, analysis, implementation and verification of business controls. One example is the segregation of duties. It is a common control included in many ERP systems. If one takes the procurement business process for instance, one person may have the authority to create a purchasing order and another person has the ability to approve the invoice. This is a control on the transactional level. It can however occur that one person has both authorities, e.g. the person is allowed to create a purchasing order and to approve an invoice. A control should prohibit that this person is approving invoices of purchase orders that person created himself. Process mining can verify this property, i.e. it is checked whether there is no purchase order where an invoice is approved by the same person that created the purchase order. This example shows that process mining has the potential to assist the auditor. 6 Case Study at Epsilon For the application of our suggested framework, the corporation of a case company was acquired. This company, which chooses to stay anonymous and is called Epsilon in this study, is ranked in the top 20 of European financial institutions. The business process selected for internal fraud risk reduction is procurement, so data from the case company s procurement 9
10 cycle is the input of our study. More specifically, the creation of purchasing orders (PO s) was adopted as process under investigation. This is inspired by the lack of fraud files (at the compliance department) in this business process within the case company, while one assumes this business process is as vulnerable to fraud as every other business process. In a first part of the case study, we want to support the ideas of the domain experts about the process. For this purpose, we perform a process diagnostic step. A good methodology for process diagnostics by process mining can be found in Bozkaya et al. (2008), which will be the applied methodology in the next paragraphs. It consists of five phases: log preparation, log inspection, control flow analysis, performance analysis, and role analysis. In a second part of the case study, we turn to a verification step. During this step, we wish to check whether certain aspects and conditions of the process hold or not. This will be elaborated in section??. We now start with the five phases of process diagnostics. 7 Log Preparation As a start, a txt-dump is made out of their ERP system, SAP. All PO s that in 2007 resulted in an invoice are subject of our investigation. We restricted the database to invoices of Belgium. This raw data is then reorganized into an event log and a random sample of 10,000 process instances out of 402,108 was taken (for reasons of computability). Before creating the event log, the different activities or events a case passes through, have to be identified, in order to meet the assumptions. An important assumption at process mining is that it is possible to describe the process under consideration by sequentially recording events. These events are the activities that all together constitute the process. Aside from the possibility to determine such sequential events, it is also assumed that these events are all linked to one particular case, called a process instance. It is beyond the scope of this paper to fully describe the procurement process at Epsilon, supported by SAP. What it boils down to (based on interviewing domain experts) is that a PO is made, signed and released, the goods are received, an invoice is received and it gets paid. During this process all different kind of aspects are logged into the ERP system, from which we now have to create an event log. The first question we must ask ourselves is What would be a correct process instance to allocate events to?. After examining the feasibility of using a PO item line as process instance, this was selected as process instance to allocate events to. We established the following events as activities of the process: - Creation of the PO (parent of item line) 10
11 Table 2: Model example of event log of the purchasing process PI-ID WFMElt Event Type Timestamp Originator Create PO Complete 02 Feb 2006 John Change Line Complete 30 Nov 2006 John Sign Complete 05 Dec 2006 Paul Release Complete 06 Dec 2006 Anne GR Complete 05 Jan 2007 John IR Complete 15 Jan 2007 Matt Pay Complete 16 Feb 2007 Marianne Create PO Complete 23 Jan 2007 Doug... - (Change of the particular item line) - Sign of parent PO after last change of item line - Release of parent PO after last change of item line - Goods Receipt on item line (GR) - Invoice Receipt on item line (IR) - Payment (or Reversal) of item line The Change of an item line is no imperative event and could occur on several different moments in the process. This change can trigger a new Sign and Release, but this is not always the case. Also important to note is the double dimensionality of the events. Create PO, Sign and Release are activities that occur on the header level of a PO. The remaining events are on the level of a PO line item. This can lead for instance to a Sign and Release in an audit trail of a particular PO line item (the process instance), while these events are not actually related to this line item, but perhaps to another line item of the same parent PO. This aspect is important to be aware of when interpreting the results. The established events in our event log are also called Work Flow Model Elements (WFMElt). After reorganizing the raw data (performed in SAS software), the event log contains per Process Instance (PI, being a PO line item) different events, being a WFMElt, with a particular Timestamp and Originator for each event. Also the Event Type must be stated, but this will be set default to Complete, since we do not have information to distinguish further. In Table 2 a model event log is given. Of course, the event log based on real life data will look differently and not as clean as this example. For modeling the process underlying these activities and expecting flows, we use a Petri Net representation. A Petri Net is a dynamic structure that consists of a set of transitions, places and directed arcs that connect these transitions and places in a bipartite manner. Transitions are indicated by boxes and relate to some task, while places are indicated by circles and represent passive phases. Places may hold one or more tokens, indicated by 11
12 black dots. If all input places of a transition contain a token, this transition is enabled and may fire. When a transition fires, it consumes a token of each of the input places and produces a token for each of its output places. The Petri Net in Figure?? (Not presented yet) represents in this way the procurement process at the case company. The first activity flows are straightforward. After the parent PO of an item line (our process instance) is created, this parent PO can be signed and released, or only released. If only one signature is needed, one only has a release, otherwise this release is preceded by a sign. In reality and also depicted in our Petri Net, the item line can be changed between the creation and the Sign - Release activity. It is also possible that the item line is changed afterwards and a new sign and release could be triggered. Only after a release, an order can be sent to the supplier which will eventually result in a Goods Receipt and an Invoice Receipt. This is an AND-relation, without a specified order. Afterwards the payment can occur. Normally, both a Goods and Invoice Receipt are prerequisites, so we depicted it this way. However, in some circumstances no Goods Receipt is necessary. In these cases the goods receipt indicator must be turned off. After turning the information from the SAP data base into the suggested events and event log, this event log was converted to the MXML format, a generic XML format to store event logs in. At this format, there is also additional space for extra data, in the form of attributes. These attributes can be inserted at each level. The attributes created in our event log are listed in Table 3. On the level of a process instance, we added the following information: the document type of the parent PO, the purchasing group that entered this parent PO, and the associated supplier. Although these three attributes are actually linked to the parent PO and not to a separate item line, this is useful information. Aside from these first three attributes, we also included the order quantity and unit of the PO item line, the resulting net value and whether or not the goods receipt indicator was turned off. 3 Next to this PO related information, we also included the total quantity and total value of all Goods Receipts that are linked to this PO item line. We did the same for the related Invoice Receipts and the total value of all Payments that are associated with this process instance. On the level of the audit trail entry, a work flow model element also carries unique information. In particular four events are enriched with additional information: Change Line, IR, GR, and Pay. When the event concerns a Change Line, we store information about this change: If it was a change of the net value, what was the size of this modification? If not the net value was changed, but another field, for example the delivery address, this field 3 This is important to verify if the ERP system s internal control on this part is working efficiently. (A Pay should not occur without a GR, unless the goods receipt indicator is turned off). 12
13 Table 3: Attributes of event log Level Attribute WFMElt Process Instance Document type Purchasing Group Supplier Order Quantity Order Unit Net Value Goods Receipt Indicator IR Total Quantity IR Total Value GR Total Quantity GR Total Value Pay Total Value Audit Trail Entry Modification Change Line Relative Modification Change Line Reference GR IR Reference Pay IR Quantity IR IR Value IR IR Reference IR GR Quantity GR GR Value GR GR Reference IR Pay Value Pay contains a modification of zero. The other stored attribute gives us, in case of a change in net value, the size of the modification, relative to the net value before the change (hence a percentage). When the event concerns an IR, four attributes are stored. We store the references that contain the (possible) link to the GR and Pay, the quantity of the units invoiced, and the credited amount, the value. Notice that these quantities and values only concern this specific Invoice Receipt, as opposed to the Invoice Receipt related attributes of the Process Instance. Those attributes provide summarized information of all Invoice Receipts attached to the Process Instance. Also beware that this information is not collected from an entire invoice, but only from the specific line that refers to the PO item line of this process instance. Similar to the IR, three attributes are stored when the event concerns a GR : the reference to possibly link this Goods Receipt to the associated IR (this is not always possible, only in a specific number of cases), the quantity of goods received and the resulting value that is assigned to this Goods Receipt. This value is the result of multiplying the Goods Receipt quantity with the price per unit agreed upon in the PO. The last event that is provided of attributes is Pay. The value of this payment is captured, as well as the key to create a link to an associated 13
14 IR. After collecting all the data necessary for the event log, ProMImport is used to convert our event log into the desired MXML format. 8 Log Inspection As already stated, we start with a random sample event log of 10,000 Belgian process instances. A process instance is a PO item line. The process analyzed in this paper contains seven real activities (see Table 4, original log). Notice that the event Reverse does not occur in this log. 4 The log at hand contains events in total and 290 originators participated in the process execution. All audit trails (the flow one process instance follows) start with the event Create PO, but they do not all end with Pay. The ending log events are Pay (93.85%), Change Line (5.02%), Release, IR, GR and Sign. Since not all audit trails end with Pay, we could add an artificial End task before we start mining this process. However, we might better clean up the event log further, so we have left only those audit trails that end with Pay. There are two ways we can obtain this. Or we filter out all process instances that do not end with Pay, or we keep the randomly selected process instances, but cut off the audit trail after the last Pay activity of that trail. We have chosen the latter option. This choice is inspired by the fact that if we filter out all PO s that do not end with Pay, we might filter out a certain group of PO s that behave in a different manner. We think for example of PO s that are being used over and over again. The audit trail of such a PO may look as follows: Create PO-Sign- Release-GR-IR-Pay-Change Line-Sign-Release-GR-IR-Pay-Change Line-... By filtering PO s on end task equals Pay we could create a bias on the proportion of this kind of PO s in the total data set. By cutting off the audit trail after the last payment, we preserve the original representation of PO behavior. As said before, we kept the process instances randomly selected, but left out all the audit trail entries after the last payment because we then have the entire process covered, from creating a PO until the payment of the associated goods. This resulted in an event log with audit trail entries and 285 originators. The occurrences of the audit trail entries can be found in the cleaned log part of Table 4. As can be seen are all Pay activities maintained, and there are still 10,000 process instances involved (there every audit trail starts with Create PO ). The log summary confirms that all audit trails end with the activity Pay. This cleaned log will be our process mining input. 4 Reverse is apparently not present at all in the log for Belgium (not even before random sampling). 14
15 Table 4: Log events WFMElt Occurrences (absolute) Occurrences (relative) original log cleaned log original cleaned log Pay 11,157 11, % % Release 10,651 10, % % IR 10,648 10, % % Create PO 10,000 10, % % Sign 9,794 9, % 15.62% GR 5,235 5, % 8.468% Change Line 5,045 4, % 7.305% For getting a first glance, the Fuzzy Miner (a plugin in the tool ProM) is used on the log, shown in Figure 2. The thickness of an arc indicates the frequency, which reveals Create PO-Sign-Release-IR-Pay as most frequent path. This is corresponding to the designed process model. Also the side paths are perfectly explicable. The digress onto Change Line and the use of a Goods Receipt before the Invoice Receipt are part of the designed model. Also the path of having a Goods Receipt after a payment is easy to understand in the light of a split delivery. 9 Control Flow Analysis 9.1 Uncovering the core process The third step of the followed process diagnostics methodology is analyzing the control flow. In a first part, we wish to uncover the core process that is embedded in the event log, and find confirmation that the business process functions in a way that corresponds to the designed model. When using the Performance Sequence Analysis plugin of ProM, we have a view on the patterns followed in this log. The analysis reveals 161 patterns. This is a very high number, certainly for such a relatively simple process model design. This gives us already an idea of the complexity of this process and the noise on this event log. However, five or seven patterns suffice for covering respectively 82% and 90% of the entire log (see Table 5). Looking at these patterns with the domain expert tells us already that all these patterns are ly according Epsilon s procedures. However, to discover a process model that covers the run of the mill, it is necessary to filter out the unfrequent patterns. That is why, in this section, we will only use the first five patterns (describing 82% of the log) for further analysis. This way we can extract a process model from the event log that describes the overall process. This model will in turn be compared with the designed process model, in order to assure the process in general is executed as desired. 15
16 Create PO 0,962 0,382 0,321 Change Line 0,237 0,068? 0,782 0,120 0,314 0,141 Sign 0,474 0,023 0,467 0,967 0,130 Release 0,651 0,010 0,398 0,671 0,055 IR 0,610 0,049? 1,000 0,242 0,511 0,063 Pay 1,000 0,117 1,000 0,530 0,188 0,016 0,046 GR 0,350 0,091? Figure 2: Fuzzy Miner result 16
17 Table 5: Top 7 of most occurring sequences Occurrences Total Throughput Time (days) Pattern Sequence # % % Average Min Max St.dev. 0 Create PO - Sign - Release - IR - Pay 3, % 31% Create PO - Sign - Release - GR - IR - Pay 2, % 56% Create PO - Change Line - Sign - Release - GR - IR - Pay % 70% Create PO - Change Line - Sign - Release - IR - Pay % 76% Create PO - Release - Change Line - IR - Pay % 82% Create PO - Sign - Release - Change Line - IR - Pay % 88% Create PO - Release - IR - Pay % 90% Table 6: Most unfrequent sequences Pattern(s) Occurrences Total Representation per pattern occurrences of log % % % % % % % % % % % 17
18 Taking the selection of the log with only patterns 0 till 4 (8,219 cases) and applying the Final State Machine (FSM) miner, results in the process model depicted in Figure 3. Running a conformance check reveals that 8,000 cases, or 80% of the total log, is covered by this process model. This result is used as a feedback to the domain experts. It was concluded that the general outlines of the process are clearly coming forward in the event log. This is seen as a reassuring start. 18
19 Create PO () Change Line () Sign () Release () IR () Release () Sign () Release () Figure 3: FSM Miner result Change Line () IR () GR () IR () Pay () 19
20 9.2 Exposing less frequent flows Another contribution the control flow analysis can provide, is to use the event log (i.e. without selecting only the frequent patterns) and to have a look at the resulting flows when lower thresholds are used. Lowering the threshold settings will result in a graph with more edges, exposing flows that are less frequently followed. This is a nice and convenient way (visual) of looking at the most important unfrequent paths. Turning back to the application of the Fuzzy Miner, we change the settings in such a manner more flows become apparent. Concretely, we change the Cutoff edge filter to the values 0.70 and These different settings indeed result in models with more edges. Elevating the Cutoff to 0.70 (compared to the default setting of 0.20) revealed two extra flows: Create PO Release and Sign GR. Elevating the Cutoff further to 0.85 (depicted in Figure 4) revealed even four more extra flows (on top of the other two): - Create PO GR - Release Pay - Sign IR - GR Change Line Before discussing the extra six flows, visible at the graph in Figure 4, an important aspect of interpreting these results has to be highlighted. The arcs from one event to another in a resulting graph of the Fuzzy Miner, need to be seen in an AND/OR relationship, which is not visible at this output graph. This means that for instance an arc from activity A to activity B does not per definition mean that B directly follows A. Perhaps this arc should be interpreted along with another arc, from activity A to activity C. The two flows A B and A C may represent an AND (or OR) relationship (after A, B and/or C follow) without having B per definition directly after A, the same for C. So looking at the Fuzzy Miner result gives us ideas of extra flows, but deducing direct flows between one activity and another, needs to be explicitly checked. In the next paragraphs the six extra flows are discussed with the domain experts and if necessary explicitly checked. Two flows are very normal: Create PO Release and GR Change Line. A Change Line can occur at every stage of the process and the fact that the PO is not first signed, before it is released is a realistic possibility. However, there are certain conditions attached to leaving out the Sign. These cab be verified in a later stage. The flows Create PO GR, Sign GR and Sign IR each have the same problem. A release is a prerequisite for ordering goods at a supplier (hence the name). Normally speaking, only after placing an order at 20
21 Create PO 0,962 0,382 0,321 Change Line 0,237 0,068? 0,783 0,120 0,332 0,104 0,314 0,141 Sign 0,474 0,023 0,467 0,967 0,130 0,053 0,162 Release 0,651 0,010 0,398 0,219 0,052 0,671 0,055 0,078 0,277 0,246 0,076 IR 0,610 0,049? 0,195 0,039 0,511 0,063 1,000 0,242 Pay 1,000 0,117 1,000 0,530 0,188 0,016 0,046 GR 0,350 0,091? Figure 4: Fuzzy Miner result with Cutoff =0.85 a supplier, a Goods Receipt or an Invoice Receipt could be received at a purchasing department. Following this train of thought, all three flows are contrary to the designed process, and should also not exist if the SAP settings function as they should. So before looking for explanations or going over to investigation, we need to confirm whether these flows really occur in these specific orders, or that they are part of an AND/OR relationship that takes care of the above mentioned restriction. Herefor we use the LTL- Checker plugin in ProM and test whether Eventually activity A next B with A and B being the events in question we want to check. The LTL checks reveal that out of the process instances, none showed the direct flow of Create PO GR, three instances had a direct flow Sign GR and again none had a flow Sign IR. We take the three process instances with the flow Sign GR under investigation. The first one shows a pattern of Create PO - Sign - Release - Sign - GR - Release. So a release has been taken place before the Goods Receipt 21
22 is entered into the system, confirming the SAP control settings. Because the events Sign and Release are both on the header level of a PO and hence not per definition linked to the process instance (only one line item of a PO), it could be that the GR in this case fell in between a Sign - Release flow, triggered by another line item. The other two process instances we looked into showed the same situation. The last flow, Release Pay, raises the question whether for these payments an according invoice is received. Normally, each Pay should be preceded by an IR. Again we start with checking whether there exists a direct flow of Release Pay for our process instances. We check the same formula Eventually activity A next B with A and B being Release and Pay. There are 55 instances (out of the ) showing this direct flow. There are two possible scenarios for this flow: (1) the IR has taken place before Release. This can again be explained as the Sign GR flow: a Sign - Release flow, triggered by another line item, popped in between an IR - Pay flow of this process instance. Or (2), there is no IR related to this Pay. This condition can be tested and looked into later, at the verification step. 10 Performance Analysis At the phase of performance analysis, questions like Are there any bottlenecks in the process? are answered. (Bozkaya et al., 2008) In this phase the average and maximum throughput times of cases are looked into and analyzed. Although this can be very interesting when diagnosing a process, certainly in terms of (continuous) auditing, it is of less value in terms of internal fraud risk reduction. This is why we do not include this fourth phase in this case study. 11 Role Analysis At the fifth phase of process diagnostics, role analysis, the roles in a process are analyzed. A role should be seen as a person (in this case study)that is involved in the process, by executing activities of that process. Role analysis attempts to answer questions like Who executes what activities? and Who is working with whom?. (Bozkaya et al., 2008) In this phase, it is interesting to check on the efficiency of the segregation of duty. The segregation of duty is a principle to reduce potential damage from the actions of one employee. (Elsas, 2008) Therefore it is hindered that one single employee has control over a critical combination of business transactions, such as there are for example a Sign and a Release authority in one single 22
23 purchase. By looking at the role-activity matrix, we can have a first look whether a person executing the activity Sign, also executes the activity Release. A print screen of a part of the matrix can be found in Figure 5. At this screen we find for instance one originator that executed times a release, and also signed PO s. This is the most extreme case of the event log, but other originators also combine these two tasks. This matrix however does not tell us something about whether this should be a problem or not, because if these signs and releases concern different PO s, there is nothing wrong with having both authorities in one person. We find however confirmation for the necessity to investigate this further. These checks require a case perspective of process mining, which brings us to the verification step, the second part of our analysis. Figure 5: Role-activity matrix 12 Verifying Properties After mainly looking at the process perspective, we turn to the case perspective of process mining by the verification of certain properties. In this section we wish to check whether certain conditions hold or if certain inter- 23
24 nal controls efficiently function. We classify the checks to execute in three categories: checks on the segregation of duty, case specific checks and checks on internal control. For all these checks, we use the LTL Checker plugin of ProM. In the following paragraphs the ideas are set forward, but the empirical results still need to be inserted Checks on segregation of duty As already was confirmed by the role-activity matrix, there is a need to further investigating whether the segregation of duty is respected in this business process. After, together with the domain expert, discussing what controls are interesting for a company to check whether this segregation of duty is efficient, we came to the following three checks: - Are Sign and Release always executed by two different persons? - Are GR and IR always entered by two different persons? - Are Release and GR always executed by two different persons? When designing the right formula to execute the first check, it is important to take into account that this has to be checked pairwise. If a release takes place, then a change line occurs, and the next sign is performed by the previous releaser, this does not have to pose a problem. As long as the release, following the last sign, is given by another employee, the segregation of duty is intact Case specific checks Also some very specific checks, related to the company under investigation, can be formulated. For Epsilon for example, there is always a Sign needed before a release can be given, except in two situations: - The PO document type has a certain value A and the total PO value is less then amount B. - The supplier is X and the total PO value is less then amount C Monitoring internal control Several internal control settings are possible at an ERP environment. Rather than just checking if these settings are in place at a specific moment, we can test the output data whether the internal controls function properly. In this case study, we selected two controls. The first internal control we wish to test is if it is ensured that no payment can occur without having an (approved) 24
25 invoice entered into the system. The second control checks whether the change of a PO line item appropriately triggers a new sign and/or release. For the first control, we have to use the attributes Reference Pay and Reference IR of the events IR and Pay respectively and check whether these are tuned to each other. The second control builds upon the attribute Net Value of the process instance and the Relative Modification and Modification attributes of the activity Change Line. 13 Discussion In this work we introduce the new field of process mining into the business environment. For the case of data mining, it took some decades before the application of this research domain was projected from the academic world into the business environment (and more precisely as a fraud detection mean and as a market segmentation aid). As for the case of process mining, we wish to accelerate this step and recognize already in this quite early stage which opportunities process mining offers to business practice. In our extended IFR 2 framework, we point out the usefulness of process mining in the light of internal fraud risk reduction. Process mining offers the ability to objectively extract a model out of transactional logs, so this model is not biased towards any expectations the researcher may have. In the light of finding flaws in the process under investigation, this open mind setting is a very important characteristic. Also the ability of monitoring internal controls is very promising. Not only for internal fraud risk reduction, but also for the field of continuous auditing and continuous monitoring, process mining has valuable characteristics. We hope to cause a chain of further research in the usefulness of process mining in the business practice; both in the context of fraud risk reduction, as in the context of continuous auditing and/or monitoring. We also aim to stimulate business practice to recognize the opportunity process mining offers. 14 Conclusion In this paper we present the extended IFR 2 framework, based on a previous work of Jans et al. (2009), to apply process mining in the context of internal fraud risk reduction. Process mining offers a lot of possibilities to examine a business process. Different aspects can be investigated, with all perspectives being interesting in terms of risk reduction. Also the explicit possibility to monitor internal controls, offers a new way of looking at continuous monitoring, a part of internal fraud risk reduction. 25
Business Process Mining for Internal Fraud Risk Reduction: Results of a Case Study
 Business Process Mining for Internal Fraud Risk Reduction: Results of a Case Study Mieke Jans, Nadine Lybaert, and Koen Vanhoof Hasselt University, Agoralaan Building D, 3590 Diepenbeek, Belgium http://www.uhasselt.be/
Business Process Mining for Internal Fraud Risk Reduction: Results of a Case Study Mieke Jans, Nadine Lybaert, and Koen Vanhoof Hasselt University, Agoralaan Building D, 3590 Diepenbeek, Belgium http://www.uhasselt.be/
Feature. Applications of Business Process Analytics and Mining for Internal Control. World
 Feature Filip Caron is a doctoral researcher in the Department of Decision Sciences and Information Management, Information Systems Group, at the Katholieke Universiteit Leuven (Flanders, Belgium). Jan
Feature Filip Caron is a doctoral researcher in the Department of Decision Sciences and Information Management, Information Systems Group, at the Katholieke Universiteit Leuven (Flanders, Belgium). Jan
Process Modelling from Insurance Event Log
 Process Modelling from Insurance Event Log P.V. Kumaraguru Research scholar, Dr.M.G.R Educational and Research Institute University Chennai- 600 095 India Dr. S.P. Rajagopalan Professor Emeritus, Dr. M.G.R
Process Modelling from Insurance Event Log P.V. Kumaraguru Research scholar, Dr.M.G.R Educational and Research Institute University Chennai- 600 095 India Dr. S.P. Rajagopalan Professor Emeritus, Dr. M.G.R
CHAPTER 1 INTRODUCTION
 CHAPTER 1 INTRODUCTION 1.1 Research Motivation In today s modern digital environment with or without our notice we are leaving our digital footprints in various data repositories through our daily activities,
CHAPTER 1 INTRODUCTION 1.1 Research Motivation In today s modern digital environment with or without our notice we are leaving our digital footprints in various data repositories through our daily activities,
Process Mining Of Invabyte And Event Logs
 PROCESS MINING OF EVENT LOGS IN INTERNAL AUDITING: A CASE STUDY Mieke Jans, Hasselt University, Belgium Michael Alles, Rutgers University, New Jersey Miklos Vasarhelyi, Rutgers University, New Jersey Abstract
PROCESS MINING OF EVENT LOGS IN INTERNAL AUDITING: A CASE STUDY Mieke Jans, Hasselt University, Belgium Michael Alles, Rutgers University, New Jersey Miklos Vasarhelyi, Rutgers University, New Jersey Abstract
International Journal of Accounting Information Systems
 International Journal of Accounting Information Systems 11 (2010) 17 41 Contents lists available at ScienceDirect International Journal of Accounting Information Systems Internal fraud risk reduction:
International Journal of Accounting Information Systems 11 (2010) 17 41 Contents lists available at ScienceDirect International Journal of Accounting Information Systems Internal fraud risk reduction:
ProM Framework Tutorial
 ProM Framework Tutorial Authors: Ana Karla Alves de Medeiros (a.k.medeiros@.tue.nl) A.J.M.M. (Ton) Weijters (a.j.m.m.weijters@tue.nl) Technische Universiteit Eindhoven Eindhoven, The Netherlands February
ProM Framework Tutorial Authors: Ana Karla Alves de Medeiros (a.k.medeiros@.tue.nl) A.J.M.M. (Ton) Weijters (a.j.m.m.weijters@tue.nl) Technische Universiteit Eindhoven Eindhoven, The Netherlands February
PROCESS MINING OF EVENT LOGS IN AUDITING: OPPORTUNITIES AND CHALLENGES. Mieke Jans Hasselt University Belgium
 PROCESS MINING OF EVENT LOGS IN AUDITING: OPPORTUNITIES AND CHALLENGES Mieke Jans Hasselt University Belgium Michael Alles Miklos Vasarhelyi Rutgers Business School Newark, NJ, USA Version: February 15,
PROCESS MINING OF EVENT LOGS IN AUDITING: OPPORTUNITIES AND CHALLENGES Mieke Jans Hasselt University Belgium Michael Alles Miklos Vasarhelyi Rutgers Business School Newark, NJ, USA Version: February 15,
ProM 6 Exercises. J.C.A.M. (Joos) Buijs and J.J.C.L. (Jan) Vogelaar {j.c.a.m.buijs,j.j.c.l.vogelaar}@tue.nl. August 2010
 ProM 6 Exercises J.C.A.M. (Joos) Buijs and J.J.C.L. (Jan) Vogelaar {j.c.a.m.buijs,j.j.c.l.vogelaar}@tue.nl August 2010 The exercises provided in this section are meant to become more familiar with ProM
ProM 6 Exercises J.C.A.M. (Joos) Buijs and J.J.C.L. (Jan) Vogelaar {j.c.a.m.buijs,j.j.c.l.vogelaar}@tue.nl August 2010 The exercises provided in this section are meant to become more familiar with ProM
Fraud Prevention and Detection in a Manufacturing Environment
 Fraud Prevention and Detection in a Manufacturing Environment Introduction The Association of Certified Fraud Examiners (ACFE) estimated in its 2008 Report to the Nation on Occupational Fraud and Abuse
Fraud Prevention and Detection in a Manufacturing Environment Introduction The Association of Certified Fraud Examiners (ACFE) estimated in its 2008 Report to the Nation on Occupational Fraud and Abuse
ACL WHITEPAPER. Automating Fraud Detection: The Essential Guide. John Verver, CA, CISA, CMC, Vice President, Product Strategy & Alliances
 ACL WHITEPAPER Automating Fraud Detection: The Essential Guide John Verver, CA, CISA, CMC, Vice President, Product Strategy & Alliances Contents EXECUTIVE SUMMARY..................................................................3
ACL WHITEPAPER Automating Fraud Detection: The Essential Guide John Verver, CA, CISA, CMC, Vice President, Product Strategy & Alliances Contents EXECUTIVE SUMMARY..................................................................3
Fraud Prevention and Deterrence
 Fraud Prevention and Deterrence Fraud Risk Assessment 2016 Association of Certified Fraud Examiners, Inc. What Is Fraud Risk? The vulnerability that an organization faces from individuals capable of combining
Fraud Prevention and Deterrence Fraud Risk Assessment 2016 Association of Certified Fraud Examiners, Inc. What Is Fraud Risk? The vulnerability that an organization faces from individuals capable of combining
Combination of Process Mining and Simulation Techniques for Business Process Redesign: A Methodological Approach
 Combination of Process Mining and Simulation Techniques for Business Process Redesign: A Methodological Approach Santiago Aguirre, Carlos Parra, and Jorge Alvarado Industrial Engineering Department, Pontificia
Combination of Process Mining and Simulation Techniques for Business Process Redesign: A Methodological Approach Santiago Aguirre, Carlos Parra, and Jorge Alvarado Industrial Engineering Department, Pontificia
Business Process Modeling
 Business Process Concepts Process Mining Kelly Rosa Braghetto Instituto de Matemática e Estatística Universidade de São Paulo kellyrb@ime.usp.br January 30, 2009 1 / 41 Business Process Concepts Process
Business Process Concepts Process Mining Kelly Rosa Braghetto Instituto de Matemática e Estatística Universidade de São Paulo kellyrb@ime.usp.br January 30, 2009 1 / 41 Business Process Concepts Process
An Introduction to Continuous Controls Monitoring
 An Introduction to Continuous Controls Monitoring Reduce compliance costs, strengthen the control environment and lessen the risk of unintentional errors and fraud Richard Hunt, Managing Director Marc
An Introduction to Continuous Controls Monitoring Reduce compliance costs, strengthen the control environment and lessen the risk of unintentional errors and fraud Richard Hunt, Managing Director Marc
ProM 6 Tutorial. H.M.W. (Eric) Verbeek mailto:h.m.w.verbeek@tue.nl R. P. Jagadeesh Chandra Bose mailto:j.c.b.rantham.prabhakara@tue.
 ProM 6 Tutorial H.M.W. (Eric) Verbeek mailto:h.m.w.verbeek@tue.nl R. P. Jagadeesh Chandra Bose mailto:j.c.b.rantham.prabhakara@tue.nl August 2010 1 Introduction This document shows how to use ProM 6 to
ProM 6 Tutorial H.M.W. (Eric) Verbeek mailto:h.m.w.verbeek@tue.nl R. P. Jagadeesh Chandra Bose mailto:j.c.b.rantham.prabhakara@tue.nl August 2010 1 Introduction This document shows how to use ProM 6 to
Steven Boyer Vice-President, Gallagher Bassett Services Inc.
 Employee Dishonesty and Fraud Motive, Rationale & Opportunity Steven Boyer Vice-President, Gallagher Bassett Services Inc. Randall Wilson, CPA/CFF, CFE, Cr.FA Partner, National Practice Director Fraud
Employee Dishonesty and Fraud Motive, Rationale & Opportunity Steven Boyer Vice-President, Gallagher Bassett Services Inc. Randall Wilson, CPA/CFF, CFE, Cr.FA Partner, National Practice Director Fraud
Fraud Prevention, Detection and Response. Dean Bunch, Ernst & Young Fraud Investigation & Dispute Services
 Fraud Prevention, Detection and Response. Dean Bunch, Ernst & Young Fraud Investigation & Dispute Services Agenda Fraud Overview Fraud Prevention Fraud Detection Fraud Response Questions Page 2 Fraud Overview
Fraud Prevention, Detection and Response. Dean Bunch, Ernst & Young Fraud Investigation & Dispute Services Agenda Fraud Overview Fraud Prevention Fraud Detection Fraud Response Questions Page 2 Fraud Overview
Deloitte Analytics Applying Process Mining in an audit context. Process Mining Camp June 4 th 2012
 Deloitte Analytics Applying Process Mining in an audit context Process Mining Camp June 4 th 2012 7 Steps 1. Interview 3 2. Data dump 4 3. Event log creation 5 4. Process mining 6 5. Audit discussion 18
Deloitte Analytics Applying Process Mining in an audit context Process Mining Camp June 4 th 2012 7 Steps 1. Interview 3 2. Data dump 4 3. Event log creation 5 4. Process mining 6 5. Audit discussion 18
4 Testing General and Automated Controls
 4 Testing General and Automated Controls Learning Objectives To understand the reasons for testing; To have an idea about Audit Planning and Testing; To discuss testing critical control points; To learn
4 Testing General and Automated Controls Learning Objectives To understand the reasons for testing; To have an idea about Audit Planning and Testing; To discuss testing critical control points; To learn
Process Mining. ^J Springer. Discovery, Conformance and Enhancement of Business Processes. Wil M.R van der Aalst Q UNIVERS1TAT.
 Wil M.R van der Aalst Process Mining Discovery, Conformance and Enhancement of Business Processes Q UNIVERS1TAT m LIECHTENSTEIN Bibliothek ^J Springer Contents 1 Introduction I 1.1 Data Explosion I 1.2
Wil M.R van der Aalst Process Mining Discovery, Conformance and Enhancement of Business Processes Q UNIVERS1TAT m LIECHTENSTEIN Bibliothek ^J Springer Contents 1 Introduction I 1.1 Data Explosion I 1.2
Online Compliance Monitoring of Service Landscapes
 Online Compliance Monitoring of Service Landscapes J.M.E.M. van der Werf 1 and H.M.W. Verbeek 2 1 Department of Information and Computing Science, Utrecht University, The Netherlands J.M.E.M.vanderWerf@UU.nl
Online Compliance Monitoring of Service Landscapes J.M.E.M. van der Werf 1 and H.M.W. Verbeek 2 1 Department of Information and Computing Science, Utrecht University, The Netherlands J.M.E.M.vanderWerf@UU.nl
Methods Commission CLUB DE LA SECURITE DE L INFORMATION FRANÇAIS. 30, rue Pierre Semard, 75009 PARIS
 MEHARI 2007 Overview Methods Commission Mehari is a trademark registered by the Clusif CLUB DE LA SECURITE DE L INFORMATION FRANÇAIS 30, rue Pierre Semard, 75009 PARIS Tél.: +33 153 25 08 80 - Fax: +33
MEHARI 2007 Overview Methods Commission Mehari is a trademark registered by the Clusif CLUB DE LA SECURITE DE L INFORMATION FRANÇAIS 30, rue Pierre Semard, 75009 PARIS Tél.: +33 153 25 08 80 - Fax: +33
Model Discovery from Motor Claim Process Using Process Mining Technique
 International Journal of Scientific and Research Publications, Volume 3, Issue 1, January 2013 1 Model Discovery from Motor Claim Process Using Process Mining Technique P.V.Kumaraguru *, Dr.S.P.Rajagopalan
International Journal of Scientific and Research Publications, Volume 3, Issue 1, January 2013 1 Model Discovery from Motor Claim Process Using Process Mining Technique P.V.Kumaraguru *, Dr.S.P.Rajagopalan
Proactive Fraud Detection with Data Mining Fear not the computer You play ball with it and it will play ball with you
 3/27/2012 Proactive Fraud Detection with Data Mining Fear not the computer You play ball with it and it will play ball with you Executive Summary The time to test fraud controls is before you have a fraud
3/27/2012 Proactive Fraud Detection with Data Mining Fear not the computer You play ball with it and it will play ball with you Executive Summary The time to test fraud controls is before you have a fraud
To Catch a Thief White Paper
 To Catch a Thief White Paper To Catch a Thief Copyright 2013 Visual Analytics Inc. TO CATCH A THIEF ABSTRACT To catch a thief, spy, money launderer, insider trader, tax evader, narcotics trafficker or
To Catch a Thief White Paper To Catch a Thief Copyright 2013 Visual Analytics Inc. TO CATCH A THIEF ABSTRACT To catch a thief, spy, money launderer, insider trader, tax evader, narcotics trafficker or
Lluis Belanche + Alfredo Vellido. Intelligent Data Analysis and Data Mining. Data Analysis and Knowledge Discovery
 Lluis Belanche + Alfredo Vellido Intelligent Data Analysis and Data Mining or Data Analysis and Knowledge Discovery a.k.a. Data Mining II An insider s view Geoff Holmes: WEKA founder Process Mining
Lluis Belanche + Alfredo Vellido Intelligent Data Analysis and Data Mining or Data Analysis and Knowledge Discovery a.k.a. Data Mining II An insider s view Geoff Holmes: WEKA founder Process Mining
Data Science. Research Theme: Process Mining
 Data Science Research Theme: Process Mining Process mining is a relatively young research discipline that sits between computational intelligence and data mining on the one hand and process modeling and
Data Science Research Theme: Process Mining Process mining is a relatively young research discipline that sits between computational intelligence and data mining on the one hand and process modeling and
U S I N G D A T A A N A L Y S I S T O M E E T T H E R E Q U I R E M E N T S O F R I S K B A S E D A U D I T I N G S T A N D A R D S
 U S I N G D A T A A N A L Y S I S T O M E E T T H E R E Q U I R E M E N T S O F R I S K B A S E D A U D I T I N G S T A N D A R D S A C a s e W a r e I D E A R e s e a r c h R e p o r t CaseWare IDEA Inc.
U S I N G D A T A A N A L Y S I S T O M E E T T H E R E Q U I R E M E N T S O F R I S K B A S E D A U D I T I N G S T A N D A R D S A C a s e W a r e I D E A R e s e a r c h R e p o r t CaseWare IDEA Inc.
Procurement Fraud Identification & Role of Data Mining
 The paper describes the known boundaries of Procurement Fraud and outlines the scope of data mining within the same. The paper also highlights some of the basic steps to be taken care of before the application
The paper describes the known boundaries of Procurement Fraud and outlines the scope of data mining within the same. The paper also highlights some of the basic steps to be taken care of before the application
Process Mining Tools: A Comparative Analysis
 EINDHOVEN UNIVERSITY OF TECHNOLOGY Department of Mathematics and Computer Science Process Mining Tools: A Comparative Analysis Irina-Maria Ailenei in partial fulfillment of the requirements for the degree
EINDHOVEN UNIVERSITY OF TECHNOLOGY Department of Mathematics and Computer Science Process Mining Tools: A Comparative Analysis Irina-Maria Ailenei in partial fulfillment of the requirements for the degree
Qi Liu Rutgers Business School ISACA New York 2013
 Qi Liu Rutgers Business School ISACA New York 2013 1 What is Audit Analytics The use of data analysis technology in Auditing. Audit analytics is the process of identifying, gathering, validating, analyzing,
Qi Liu Rutgers Business School ISACA New York 2013 1 What is Audit Analytics The use of data analysis technology in Auditing. Audit analytics is the process of identifying, gathering, validating, analyzing,
ETHICS, FRAUD, AND INTERNAL CONTROL
 CHAPTER ETHICS, FRAUD, AND INTERNAL CONTROL The three topics of this chapter are closely related. Ethics is a hallmark of the accounting profession. The principles which guide a manager s decision making
CHAPTER ETHICS, FRAUD, AND INTERNAL CONTROL The three topics of this chapter are closely related. Ethics is a hallmark of the accounting profession. The principles which guide a manager s decision making
Mercy Health System. St. Louis, MO. Process Mining of Clinical Workflows for Quality and Process Improvement
 Mercy Health System St. Louis, MO Process Mining of Clinical Workflows for Quality and Process Improvement Paul Helmering, Executive Director, Enterprise Architecture Pete Harrison, Data Analyst, Mercy
Mercy Health System St. Louis, MO Process Mining of Clinical Workflows for Quality and Process Improvement Paul Helmering, Executive Director, Enterprise Architecture Pete Harrison, Data Analyst, Mercy
AN AUDIT OF INTERNAL CONTROL OVER FINANCIAL REPORTING THAT IS INTEGRATED WITH AN AUDIT OF FINANCIAL STATEMENTS:
 1666 K Street, NW Washington, D.C. 20006 Telephone: (202) 207-9100 Facsimile: (202) 862-8430 www.pcaobus.org STAFF VIEWS AN AUDIT OF INTERNAL CONTROL OVER FINANCIAL REPORTING THAT IS INTEGRATED WITH AN
1666 K Street, NW Washington, D.C. 20006 Telephone: (202) 207-9100 Facsimile: (202) 862-8430 www.pcaobus.org STAFF VIEWS AN AUDIT OF INTERNAL CONTROL OVER FINANCIAL REPORTING THAT IS INTEGRATED WITH AN
Implementing Heuristic Miner for Different Types of Event Logs
 Implementing Heuristic Miner for Different Types of Event Logs Angelina Prima Kurniati 1, GunturPrabawa Kusuma 2, GedeAgungAry Wisudiawan 3 1,3 School of Compuing, Telkom University, Indonesia. 2 School
Implementing Heuristic Miner for Different Types of Event Logs Angelina Prima Kurniati 1, GunturPrabawa Kusuma 2, GedeAgungAry Wisudiawan 3 1,3 School of Compuing, Telkom University, Indonesia. 2 School
[RELEASE NOS. 33-8810; 34-55929; FR-77; File No. S7-24-06]
![[RELEASE NOS. 33-8810; 34-55929; FR-77; File No. S7-24-06] [RELEASE NOS. 33-8810; 34-55929; FR-77; File No. S7-24-06]](/thumbs/25/6464675.jpg) SECURITIES AND EXCHANGE COMMISSION 17 CFR PART 241 [RELEASE NOS. 33-8810; 34-55929; FR-77; File No. S7-24-06] Commission Guidance Regarding Management s Report on Internal Control Over Financial Reporting
SECURITIES AND EXCHANGE COMMISSION 17 CFR PART 241 [RELEASE NOS. 33-8810; 34-55929; FR-77; File No. S7-24-06] Commission Guidance Regarding Management s Report on Internal Control Over Financial Reporting
Checklist for Operational Risk Management
 Checklist for Operational Risk Management I. Development and Establishment of Comprehensive Operational Risk Management System by Management Checkpoints - Operational risk is the risk of loss resulting
Checklist for Operational Risk Management I. Development and Establishment of Comprehensive Operational Risk Management System by Management Checkpoints - Operational risk is the risk of loss resulting
Fighting Fraud with Data Mining & Analysis
 Fighting Fraud with Data Mining & Analysis Leonard W. Vona December 2008 Fraud Auditing, Inc. Phone: 518-784-2250 www.fraudauditing.net E-mail: leonard@leonardvona.com Copyright 2008 Leonard Vona and Fraud
Fighting Fraud with Data Mining & Analysis Leonard W. Vona December 2008 Fraud Auditing, Inc. Phone: 518-784-2250 www.fraudauditing.net E-mail: leonard@leonardvona.com Copyright 2008 Leonard Vona and Fraud
A Closer Look Financial Services Regulation
 A Closer Look Financial Services Regulation To view our other A Closer Look pieces, please visit www.pwcregulatory.com \ Model risk mitigation and cost reduction through effective documentation June 2013
A Closer Look Financial Services Regulation To view our other A Closer Look pieces, please visit www.pwcregulatory.com \ Model risk mitigation and cost reduction through effective documentation June 2013
SUPPLY CHAIN INTEGRITY by Norman Katz, CFE, Katzscan Inc.
 SUPPLY CHAIN INTEGRITY by Norman Katz, CFE, Katzscan Inc. The supply chain, as I view it, exists both internal and external to an organization s walls, encompassing the movement of raw materials, components,
SUPPLY CHAIN INTEGRITY by Norman Katz, CFE, Katzscan Inc. The supply chain, as I view it, exists both internal and external to an organization s walls, encompassing the movement of raw materials, components,
PROJECT RISK MANAGEMENT
 PROJECT RISK MANAGEMENT DEFINITION OF A RISK OR RISK EVENT: A discrete occurrence that may affect the project for good or bad. DEFINITION OF A PROBLEM OR UNCERTAINTY: An uncommon state of nature, characterized
PROJECT RISK MANAGEMENT DEFINITION OF A RISK OR RISK EVENT: A discrete occurrence that may affect the project for good or bad. DEFINITION OF A PROBLEM OR UNCERTAINTY: An uncommon state of nature, characterized
Table of Contents: Chapter 2 Internal Control
 Table of Contents: Chapter 2 Chapter 2... 2 2.1 Establishing an Effective System... 2 2.1.1 Sample Plan Elements... 5 2.1.2 Limitations of... 7 2.2 Approvals... 7 2.3 PCard... 7 2.4 Payroll... 7 2.5 Reconciliation
Table of Contents: Chapter 2 Chapter 2... 2 2.1 Establishing an Effective System... 2 2.1.1 Sample Plan Elements... 5 2.1.2 Limitations of... 7 2.2 Approvals... 7 2.3 PCard... 7 2.4 Payroll... 7 2.5 Reconciliation
(Refer Slide Time 00:56)
 Software Engineering Prof.N. L. Sarda Computer Science & Engineering Indian Institute of Technology, Bombay Lecture-12 Data Modelling- ER diagrams, Mapping to relational model (Part -II) We will continue
Software Engineering Prof.N. L. Sarda Computer Science & Engineering Indian Institute of Technology, Bombay Lecture-12 Data Modelling- ER diagrams, Mapping to relational model (Part -II) We will continue
White Paper. Imperva Data Security and Compliance Lifecycle
 White Paper Today s highly regulated business environment is forcing corporations to comply with a multitude of different regulatory mandates, including data governance, data protection and industry regulations.
White Paper Today s highly regulated business environment is forcing corporations to comply with a multitude of different regulatory mandates, including data governance, data protection and industry regulations.
Process Mining and Network Analysis
 Towards Comprehensive Support for Organizational Mining Minseok Song and Wil M.P. van der Aalst Eindhoven University of Technology P.O.Box 513, NL-5600 MB, Eindhoven, The Netherlands. {m.s.song, w.m.p.v.d.aalst}@tue.nl
Towards Comprehensive Support for Organizational Mining Minseok Song and Wil M.P. van der Aalst Eindhoven University of Technology P.O.Box 513, NL-5600 MB, Eindhoven, The Netherlands. {m.s.song, w.m.p.v.d.aalst}@tue.nl
Ethics, Fraud, and Internal Control
 Ethics, Fraud, and Internal Control SUPRIYO BHATTACHARJEE AGM & MOF CAB,RBI,PUNE 17/9/07 Objectives Broad issues pertaining to business ethics Ethics in accounting information systems Ethical issues in
Ethics, Fraud, and Internal Control SUPRIYO BHATTACHARJEE AGM & MOF CAB,RBI,PUNE 17/9/07 Objectives Broad issues pertaining to business ethics Ethics in accounting information systems Ethical issues in
Stages of the Audit Process
 Chapter 5 Stages of the Audit Process Learning Objectives Upon completion of this chapter you should be able to explain: LO 1 Explain the audit process. LO 2 Accept a new client or confirming the continuance
Chapter 5 Stages of the Audit Process Learning Objectives Upon completion of this chapter you should be able to explain: LO 1 Explain the audit process. LO 2 Accept a new client or confirming the continuance
Fraud Control Theory
 13 Fraud Control Theory Using a variation of a saying from the 1960s, fraud happens. Like all costs of doing business, fraud must be managed. Management must recognize that people commit fraudulent acts
13 Fraud Control Theory Using a variation of a saying from the 1960s, fraud happens. Like all costs of doing business, fraud must be managed. Management must recognize that people commit fraudulent acts
Consideration of Fraud in a Financial Statement Audit
 Consideration of Fraud in a Financial Statement Audit 1719 AU Section 316 Consideration of Fraud in a Financial Statement Audit (Supersedes SAS No. 82.) Source: SAS No. 99; SAS No. 113. Effective for audits
Consideration of Fraud in a Financial Statement Audit 1719 AU Section 316 Consideration of Fraud in a Financial Statement Audit (Supersedes SAS No. 82.) Source: SAS No. 99; SAS No. 113. Effective for audits
not possible or was possible at a high cost for collecting the data.
 Data Mining and Knowledge Discovery Generating knowledge from data Knowledge Discovery Data Mining White Paper Organizations collect a vast amount of data in the process of carrying out their day-to-day
Data Mining and Knowledge Discovery Generating knowledge from data Knowledge Discovery Data Mining White Paper Organizations collect a vast amount of data in the process of carrying out their day-to-day
ISO/IEC 20000 IT Service Management - Benefits and Requirements for Service Providers and Customers
 ISO/IEC 20000 IT Service Management - Benefits and Requirements for Service Providers and Customers Authors Ralf Buchsein, Manager, KESS DV-Beratung GmbH Klaus Dettmer, Product Manager, iet Solutions GmbH
ISO/IEC 20000 IT Service Management - Benefits and Requirements for Service Providers and Customers Authors Ralf Buchsein, Manager, KESS DV-Beratung GmbH Klaus Dettmer, Product Manager, iet Solutions GmbH
Types of Fraud and Recent Cases. Developing an Effective Anti-fraud Program from the Top Down
 Types of and Recent Cases Developing an Effective Anti-fraud Program from the Top Down 1 Types of and Recent Cases Chris Grippa (404-817-5945) FIDS Senior Manager with Ernst & Young LLP Works with clients
Types of and Recent Cases Developing an Effective Anti-fraud Program from the Top Down 1 Types of and Recent Cases Chris Grippa (404-817-5945) FIDS Senior Manager with Ernst & Young LLP Works with clients
Understanding the Entity and Its Environment and Assessing the Risks of Material Misstatement
 Understanding the Entity and Its Environment 1667 AU Section 314 Understanding the Entity and Its Environment and Assessing the Risks of Material Misstatement (Supersedes SAS No. 55.) Source: SAS No. 109.
Understanding the Entity and Its Environment 1667 AU Section 314 Understanding the Entity and Its Environment and Assessing the Risks of Material Misstatement (Supersedes SAS No. 55.) Source: SAS No. 109.
Develop Project Charter. Develop Project Management Plan
 Develop Charter Develop Charter is the process of developing documentation that formally authorizes a project or a phase. The documentation includes initial requirements that satisfy stakeholder needs
Develop Charter Develop Charter is the process of developing documentation that formally authorizes a project or a phase. The documentation includes initial requirements that satisfy stakeholder needs
ITRM Guideline CPM 110-01 Date: January 23, 2006 SECTION 4 - PROJECT EXECUTION AND CONTROL PHASE
 PROJECT MANAGEMENT GUIDELINE SECTION 4 - PROJECT EXECUTION AND CONTROL PHASE Table of Contents Introduction... 3 Project Execution and Control Phase Overview... 3 Activities and Documents in the Execution
PROJECT MANAGEMENT GUIDELINE SECTION 4 - PROJECT EXECUTION AND CONTROL PHASE Table of Contents Introduction... 3 Project Execution and Control Phase Overview... 3 Activities and Documents in the Execution
FRAUD PREVENTION STRATEGY FOR UGU DISTRICT MUNICIPALITY (UGU)
 FRAUD PREVENTION STRATEGY FOR UGU DISTRICT MUNICIPALITY (UGU) CONTENTS 1. Introduction.. 3 2. Characteristics of Fraud.. 5 3. Fraud Strategy..... 6 4. Building the Fraud Prevention Plan........ 8 Fraud
FRAUD PREVENTION STRATEGY FOR UGU DISTRICT MUNICIPALITY (UGU) CONTENTS 1. Introduction.. 3 2. Characteristics of Fraud.. 5 3. Fraud Strategy..... 6 4. Building the Fraud Prevention Plan........ 8 Fraud
PERFORMANCE MEASUREMENT TOOLS IN BUSINESS PROCESS MANAGEMENT A CONTEMPORARY APPROACH
 PERFORMANCE MEASUREMENT TOOLS IN BUSINESS PROCESS MANAGEMENT A CONTEMPORARY APPROACH Associate Professor PhD. VERONICA ADRIANA POPESCU 1, Professor PhD. GHEORGHE N. POPESCU 2, Lecturer PhD. Cristina Raluca
PERFORMANCE MEASUREMENT TOOLS IN BUSINESS PROCESS MANAGEMENT A CONTEMPORARY APPROACH Associate Professor PhD. VERONICA ADRIANA POPESCU 1, Professor PhD. GHEORGHE N. POPESCU 2, Lecturer PhD. Cristina Raluca
Process Mining: Using CPN Tools to Create Test Logs for Mining Algorithms
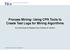 Mining: Using CPN Tools to Create Test Logs for Mining Algorithms Ana Karla Alves de Medeiros and Christian W. Günther 2 Outline Introduction Mining The need for synthetic logs MXML format Using the Logging
Mining: Using CPN Tools to Create Test Logs for Mining Algorithms Ana Karla Alves de Medeiros and Christian W. Günther 2 Outline Introduction Mining The need for synthetic logs MXML format Using the Logging
Measurement Information Model
 mcgarry02.qxd 9/7/01 1:27 PM Page 13 2 Information Model This chapter describes one of the fundamental measurement concepts of Practical Software, the Information Model. The Information Model provides
mcgarry02.qxd 9/7/01 1:27 PM Page 13 2 Information Model This chapter describes one of the fundamental measurement concepts of Practical Software, the Information Model. The Information Model provides
APPENDIX X1 - FIFTH EDITION CHANGES
 APPENDIX X1 FIFTH EDITION CHANGES The purpose of this appendix is to give a detailed explanation of the changes made to A Guide to the Project Management Body of Knowledge (PMBOK Guide) Fourth Edition
APPENDIX X1 FIFTH EDITION CHANGES The purpose of this appendix is to give a detailed explanation of the changes made to A Guide to the Project Management Body of Knowledge (PMBOK Guide) Fourth Edition
IT Governance and Control: An Analysis of CobIT 4.1. Prepared by: Mark Longo
 IT Governance and Control: An Analysis of CobIT 4.1 Prepared by: Mark Longo December 15, 2008 Table of Contents Introduction Page 3 Project Scope Page 3 IT Governance.Page 3 CobIT Framework..Page 4 General
IT Governance and Control: An Analysis of CobIT 4.1 Prepared by: Mark Longo December 15, 2008 Table of Contents Introduction Page 3 Project Scope Page 3 IT Governance.Page 3 CobIT Framework..Page 4 General
Information Technology Engineers Examination. Information Security Specialist Examination. (Level 4) Syllabus
 Information Technology Engineers Examination Information Security Specialist Examination (Level 4) Syllabus Details of Knowledge and Skills Required for the Information Technology Engineers Examination
Information Technology Engineers Examination Information Security Specialist Examination (Level 4) Syllabus Details of Knowledge and Skills Required for the Information Technology Engineers Examination
Modeling Guidelines Manual
 Modeling Guidelines Manual [Insert company name here] July 2014 Author: John Doe john.doe@johnydoe.com Page 1 of 22 Table of Contents 1. Introduction... 3 2. Business Process Management (BPM)... 4 2.1.
Modeling Guidelines Manual [Insert company name here] July 2014 Author: John Doe john.doe@johnydoe.com Page 1 of 22 Table of Contents 1. Introduction... 3 2. Business Process Management (BPM)... 4 2.1.
Business Process Measurement in small enterprises after the installation of an ERP software.
 Business Process Measurement in small enterprises after the installation of an ERP software. Stefano Siccardi and Claudia Sebastiani CQ Creativiquadrati snc, via Tadino 60, Milano, Italy http://www.creativiquadrati.it
Business Process Measurement in small enterprises after the installation of an ERP software. Stefano Siccardi and Claudia Sebastiani CQ Creativiquadrati snc, via Tadino 60, Milano, Italy http://www.creativiquadrati.it
GLOBAL PORTS INVESTMENTS PLC
 Adopted by the Directors of GLOBAL PORTS INVESTMENTS PLC Resolution of 14 July 2008 GLOBAL PORTS INVESTMENTS PLC (previously GLOBAL PORTS INVESTMENTS LTD) ANTI-FRAUD POLICY TABLE OF CONTENTS 1. INTRODUCTION.....
Adopted by the Directors of GLOBAL PORTS INVESTMENTS PLC Resolution of 14 July 2008 GLOBAL PORTS INVESTMENTS PLC (previously GLOBAL PORTS INVESTMENTS LTD) ANTI-FRAUD POLICY TABLE OF CONTENTS 1. INTRODUCTION.....
Best Practices for PCI DSS V3.0 Network Security Compliance
 Best Practices for PCI DSS V3.0 Network Security Compliance January 2015 www.tufin.com Table of Contents Preparing for PCI DSS V3.0 Audit... 3 Protecting Cardholder Data with PCI DSS... 3 Complying with
Best Practices for PCI DSS V3.0 Network Security Compliance January 2015 www.tufin.com Table of Contents Preparing for PCI DSS V3.0 Audit... 3 Protecting Cardholder Data with PCI DSS... 3 Complying with
Dan French Founder & CEO, Consider Solutions
 Dan French Founder & CEO, Consider Solutions CONSIDER SOLUTIONS Mission Solutions for World Class Finance Footprint Financial Control & Compliance Risk Assurance Process Optimization CLIENTS CONTEXT The
Dan French Founder & CEO, Consider Solutions CONSIDER SOLUTIONS Mission Solutions for World Class Finance Footprint Financial Control & Compliance Risk Assurance Process Optimization CLIENTS CONTEXT The
Mobile E-Commerce: Friend or Foe? A Cyber Security Study
 Research February 2015 Mobile E-Commerce: Friend or Foe? A A J.Gold Associates Research Report Many consumers now interact with the Internet primarily through mobile devices, avoiding traditional PC devices
Research February 2015 Mobile E-Commerce: Friend or Foe? A A J.Gold Associates Research Report Many consumers now interact with the Internet primarily through mobile devices, avoiding traditional PC devices
Nr.: Fakultät für Informatik Otto-von-Guericke-Universität Magdeburg
 Nr.: Fakultät für Informatik Otto-von-Guericke-Universität Magdeburg Nr.: Fakultät für Informatik Otto-von-Guericke-Universität Magdeburg Impressum ( 5 TMG) Herausgeber: Otto-von-Guericke-Universität Magdeburg
Nr.: Fakultät für Informatik Otto-von-Guericke-Universität Magdeburg Nr.: Fakultät für Informatik Otto-von-Guericke-Universität Magdeburg Impressum ( 5 TMG) Herausgeber: Otto-von-Guericke-Universität Magdeburg
by: Scott Baranowski, CIA
 Community Bank Auditors Group A/P, Procurement and Credit Card Internal Controls June 4, 2014 by: Scott Baranowski, CIA MEMBER OF PKF NORTH AMERICA, AN ASSOCIATION OF LEGALLY INDEPENDENT FIRMS 2013 Wolf
Community Bank Auditors Group A/P, Procurement and Credit Card Internal Controls June 4, 2014 by: Scott Baranowski, CIA MEMBER OF PKF NORTH AMERICA, AN ASSOCIATION OF LEGALLY INDEPENDENT FIRMS 2013 Wolf
IS YOUR DATA WAREHOUSE SUCCESSFUL? Developing a Data Warehouse Process that responds to the needs of the Enterprise.
 IS YOUR DATA WAREHOUSE SUCCESSFUL? Developing a Data Warehouse Process that responds to the needs of the Enterprise. Peter R. Welbrock Smith-Hanley Consulting Group Philadelphia, PA ABSTRACT Developing
IS YOUR DATA WAREHOUSE SUCCESSFUL? Developing a Data Warehouse Process that responds to the needs of the Enterprise. Peter R. Welbrock Smith-Hanley Consulting Group Philadelphia, PA ABSTRACT Developing
INTEGRATED MANAGEMENT SYSTEM MANUAL IMS. Based on ISO 9001:2008 and ISO 14001:2004 Standards
 INTEGRATED MANAGEMENT SYSTEM MANUAL IMS Based on ISO 9001:2008 and ISO 14001:2004 Standards Approved by Robert Melani Issue Date 30 December 2009 Issued To Management Representative Controlled Y N Copy
INTEGRATED MANAGEMENT SYSTEM MANUAL IMS Based on ISO 9001:2008 and ISO 14001:2004 Standards Approved by Robert Melani Issue Date 30 December 2009 Issued To Management Representative Controlled Y N Copy
PURCHASING CARD POLICY AND PROCEDURES
 PURCHASING CARD POLICY AND PROCEDURES 1. PURPOSE To establish policies and procedures for procuring goods and/or services using a Purchasing Card. Purchasing Cards are referred to throughout this policy
PURCHASING CARD POLICY AND PROCEDURES 1. PURPOSE To establish policies and procedures for procuring goods and/or services using a Purchasing Card. Purchasing Cards are referred to throughout this policy
Reconciliation Best Practice
 Adra Match Ltd Reconciliation Best Practice Technical whitepaper Bjørn Loe managing director London, June 2010 Introduction This whitepaper highlights some of the challenges with transaction reconciliation
Adra Match Ltd Reconciliation Best Practice Technical whitepaper Bjørn Loe managing director London, June 2010 Introduction This whitepaper highlights some of the challenges with transaction reconciliation
Standard: Information Security Incident Management
 Standard: Information Security Incident Management Page 1 Executive Summary California State University Information Security Policy 8075.00 states security incidents involving loss, damage or misuse of
Standard: Information Security Incident Management Page 1 Executive Summary California State University Information Security Policy 8075.00 states security incidents involving loss, damage or misuse of
Employee Embezzlement and Fraud. Defending Against Insider Threats
 Employee Embezzlement and Fraud Defending Against Insider Threats Today s Approach An open dialogue and sharing of information regarding a common threat of internal losses. There is no guarantee that any
Employee Embezzlement and Fraud Defending Against Insider Threats Today s Approach An open dialogue and sharing of information regarding a common threat of internal losses. There is no guarantee that any
Chapter 3: Data Mining Driven Learning Apprentice System for Medical Billing Compliance
 Chapter 3: Data Mining Driven Learning Apprentice System for Medical Billing Compliance 3.1 Introduction This research has been conducted at back office of a medical billing company situated in a custom
Chapter 3: Data Mining Driven Learning Apprentice System for Medical Billing Compliance 3.1 Introduction This research has been conducted at back office of a medical billing company situated in a custom
On the Setting of the Standards and Practice Standards for. Management Assessment and Audit concerning Internal
 (Provisional translation) On the Setting of the Standards and Practice Standards for Management Assessment and Audit concerning Internal Control Over Financial Reporting (Council Opinions) Released on
(Provisional translation) On the Setting of the Standards and Practice Standards for Management Assessment and Audit concerning Internal Control Over Financial Reporting (Council Opinions) Released on
INTERNATIONAL STANDARD ON AUDITING (UK AND IRELAND) 240 THE AUDITOR S RESPONSIBILITIES RELATING TO FRAUD IN AN AUDIT OF FINANCIAL STATEMENTS
 INTERNATIONAL STANDARD ON AUDITING (UK AND IRELAND) 240 Introduction THE AUDITOR S RESPONSIBILITIES RELATING TO FRAUD IN AN AUDIT OF FINANCIAL STATEMENTS (Effective for audits of financial statements for
INTERNATIONAL STANDARD ON AUDITING (UK AND IRELAND) 240 Introduction THE AUDITOR S RESPONSIBILITIES RELATING TO FRAUD IN AN AUDIT OF FINANCIAL STATEMENTS (Effective for audits of financial statements for
Special Purpose Reports on the Effectiveness of Control Procedures
 Auditing Standard AUS 810 (July 2002) Special Purpose Reports on the Effectiveness of Control Procedures Prepared by the Auditing & Assurance Standards Board of the Australian Accounting Research Foundation
Auditing Standard AUS 810 (July 2002) Special Purpose Reports on the Effectiveness of Control Procedures Prepared by the Auditing & Assurance Standards Board of the Australian Accounting Research Foundation
Hybrid Association Rule Learning and Process Mining for Fraud Detection
 Hybrid Association Rule Learning and Process Mining for Fraud Detection Riyanarto Sarno, Rahadian Dustrial Dewandono, Tohari Ahmad, Mohammad Farid Naufal and Fernandes Sinaga Abstract Data mining and process
Hybrid Association Rule Learning and Process Mining for Fraud Detection Riyanarto Sarno, Rahadian Dustrial Dewandono, Tohari Ahmad, Mohammad Farid Naufal and Fernandes Sinaga Abstract Data mining and process
Software Engineering Reference Framework
 Software Engineering Reference Framework Michel Chaudron, Jan Friso Groote, Kees van Hee, Kees Hemerik, Lou Somers, Tom Verhoeff. Department of Mathematics and Computer Science Eindhoven University of
Software Engineering Reference Framework Michel Chaudron, Jan Friso Groote, Kees van Hee, Kees Hemerik, Lou Somers, Tom Verhoeff. Department of Mathematics and Computer Science Eindhoven University of
Process Intelligence: An Exciting New Frontier for Business Intelligence
 February/2014 Process Intelligence: An Exciting New Frontier for Business Intelligence Claudia Imhoff, Ph.D. Sponsored by Altosoft, A Kofax Company Table of Contents Introduction... 1 Use Cases... 2 Business
February/2014 Process Intelligence: An Exciting New Frontier for Business Intelligence Claudia Imhoff, Ph.D. Sponsored by Altosoft, A Kofax Company Table of Contents Introduction... 1 Use Cases... 2 Business
Using Predictive Maintenance to Approach Zero Downtime
 SAP Thought Leadership Paper Predictive Maintenance Using Predictive Maintenance to Approach Zero Downtime How Predictive Analytics Makes This Possible Table of Contents 4 Optimizing Machine Maintenance
SAP Thought Leadership Paper Predictive Maintenance Using Predictive Maintenance to Approach Zero Downtime How Predictive Analytics Makes This Possible Table of Contents 4 Optimizing Machine Maintenance
Using Trace Clustering for Configurable Process Discovery Explained by Event Log Data
 Master of Business Information Systems, Department of Mathematics and Computer Science Using Trace Clustering for Configurable Process Discovery Explained by Event Log Data Master Thesis Author: ing. Y.P.J.M.
Master of Business Information Systems, Department of Mathematics and Computer Science Using Trace Clustering for Configurable Process Discovery Explained by Event Log Data Master Thesis Author: ing. Y.P.J.M.
Chapter 12 Analyzing Spaghetti Processes
 Chapter 12 Analyzing Spaghetti Processes prof.dr.ir. Wil van der Aalst www.processmining.org Overview Chapter 1 Introduction Part I: Preliminaries Chapter 2 Process Modeling and Analysis Chapter 3 Data
Chapter 12 Analyzing Spaghetti Processes prof.dr.ir. Wil van der Aalst www.processmining.org Overview Chapter 1 Introduction Part I: Preliminaries Chapter 2 Process Modeling and Analysis Chapter 3 Data
MEMORANDUM INTERNAL CONTROL REQUIREMENTS FOR NON-PROFITS
 DIVISION OF CHILD CARE AND EARLY CHILDHOOD EDUCATION HEALTH AND NUTRITION UNIT P O BOX 1437, SLOT S 155 501-320-8982 FAX: 501-682-2334 TDD: 501-682-1550 TO: NON-PROFIT INSTITUTIONS FROM: HEALTH AND NUTRITION
DIVISION OF CHILD CARE AND EARLY CHILDHOOD EDUCATION HEALTH AND NUTRITION UNIT P O BOX 1437, SLOT S 155 501-320-8982 FAX: 501-682-2334 TDD: 501-682-1550 TO: NON-PROFIT INSTITUTIONS FROM: HEALTH AND NUTRITION
Management Information System Prof. Biswajit Mahanty Department of Industrial Engineering & Management Indian Institute of Technology, Kharagpur
 Management Information System Prof. Biswajit Mahanty Department of Industrial Engineering & Management Indian Institute of Technology, Kharagpur Lecture - 02 Introduction Part II Welcome to all of you
Management Information System Prof. Biswajit Mahanty Department of Industrial Engineering & Management Indian Institute of Technology, Kharagpur Lecture - 02 Introduction Part II Welcome to all of you
Internal Controls for Small Organizations. Jen Parker, CPA Director of Accounting & Finance US Youth Soccer
 Internal Controls for Small Organizations Jen Parker, CPA Director of Accounting & Finance US Youth Soccer Fraud Statistics: The following statistics about fraud and white collar crime are from the Association
Internal Controls for Small Organizations Jen Parker, CPA Director of Accounting & Finance US Youth Soccer Fraud Statistics: The following statistics about fraud and white collar crime are from the Association
Identifying User Behavior in domainspecific
 Identifying User Behavior in domainspecific Repositories Wilko VAN HOEK a,1, Wei SHEN a and Philipp MAYR a a GESIS Leibniz Institute for the Social Sciences, Germany Abstract. This paper presents an analysis
Identifying User Behavior in domainspecific Repositories Wilko VAN HOEK a,1, Wei SHEN a and Philipp MAYR a a GESIS Leibniz Institute for the Social Sciences, Germany Abstract. This paper presents an analysis
Business process measurement - data mining. enn@cc.ttu.ee
 Business process measurement - data mining. enn@cc.ttu.ee Business process measurement Balanced scorecard Process mining - ProM Äriprotsessi konteksti perspektiiv Clear & measurable goals Effective solutions
Business process measurement - data mining. enn@cc.ttu.ee Business process measurement Balanced scorecard Process mining - ProM Äriprotsessi konteksti perspektiiv Clear & measurable goals Effective solutions
Development, Acquisition, Implementation, and Maintenance of Application Systems
 Development, Acquisition, Implementation, and Maintenance of Application Systems Part of a series of notes to help Centers review their own Center internal management processes from the point of view of
Development, Acquisition, Implementation, and Maintenance of Application Systems Part of a series of notes to help Centers review their own Center internal management processes from the point of view of
Dotted Chart and Control-Flow Analysis for a Loan Application Process
 Dotted Chart and Control-Flow Analysis for a Loan Application Process Thomas Molka 1,2, Wasif Gilani 1 and Xiao-Jun Zeng 2 Business Intelligence Practice, SAP Research, Belfast, UK The University of Manchester,
Dotted Chart and Control-Flow Analysis for a Loan Application Process Thomas Molka 1,2, Wasif Gilani 1 and Xiao-Jun Zeng 2 Business Intelligence Practice, SAP Research, Belfast, UK The University of Manchester,
ISAE 3000 (Revised), Assurance Engagements Other Than Audits or Reviews of Historical Financial Information
 International Auditing and Assurance Standards Board Exposure Draft April 2011 Comments requested by September 1, 2011 Proposed International Standard on Assurance Engagements (ISAE) ISAE 3000 (Revised),
International Auditing and Assurance Standards Board Exposure Draft April 2011 Comments requested by September 1, 2011 Proposed International Standard on Assurance Engagements (ISAE) ISAE 3000 (Revised),
SUPPLY CHAIN & PROCUREMENT INSIGHTS REPORT CANADA, ARE WE FALLING BEHIND?
 GRAND & TOY 2012 SUPPLY CHAIN & PROCUREMENT INSIGHTS REPORT CANADA, ARE WE FALLING BEHIND? Research conducted by TABLE OF CONTENTS Overview... 3 Procurement Tactically Focused but Evolving...4 Communication
GRAND & TOY 2012 SUPPLY CHAIN & PROCUREMENT INSIGHTS REPORT CANADA, ARE WE FALLING BEHIND? Research conducted by TABLE OF CONTENTS Overview... 3 Procurement Tactically Focused but Evolving...4 Communication
Improving Decision Making and Managing Knowledge
 Improving Decision Making and Managing Knowledge Decision Making and Information Systems Information Requirements of Key Decision-Making Groups in a Firm Senior managers, middle managers, operational managers,
Improving Decision Making and Managing Knowledge Decision Making and Information Systems Information Requirements of Key Decision-Making Groups in a Firm Senior managers, middle managers, operational managers,
D6.1: Service management tools implementation and maturity baseline assessment framework
 D6.1: Service management tools implementation and maturity baseline assessment framework Deliverable Document ID Status Version Author(s) Due FedSM- D6.1 Final 1.1 Tomasz Szepieniec, All M10 (31 June 2013)
D6.1: Service management tools implementation and maturity baseline assessment framework Deliverable Document ID Status Version Author(s) Due FedSM- D6.1 Final 1.1 Tomasz Szepieniec, All M10 (31 June 2013)
Strong Corporate Governance & Internal Controls: Internal Auditing in Higher Education
 Strong Corporate Governance & Internal Controls: Internal Auditing in Higher Education Contents Introduction Internal Audit as Trusted Advisor & Business Partner Big Ticket Items: Fraud, Revenue Leakage
Strong Corporate Governance & Internal Controls: Internal Auditing in Higher Education Contents Introduction Internal Audit as Trusted Advisor & Business Partner Big Ticket Items: Fraud, Revenue Leakage
