Standard: Airwave
|
|
|
- Curtis Dalton
- 8 years ago
- Views:
Transcription
1 Standard: Airwave Page 1
2 Executive Summary Information Technology Services (ITS) recognizes the increased use and availability of various wireless technologies at SJSU. SJSU is responsible for providing a communication network that is accessible, accountable, reliable, legal, and secure. In order to guarantee this level of service IT Services manages the airspace. Maintaining security of the wireless system is crucial. Therefore, access to the wireless system will be limited to individuals authorized to use campus and Internet resources through username and password authentication. Any College, Department, Unit, or Individual who wishes to utilize wireless technology must follow stated policies, protocols, practices, and procedures. This standard outlines the roles, processes, requirements, and restrictions surrounding wireless Wi-Fi networks. Page 2
3 Information Security Standards Airwave Standard IS-A Effective Date 11/10/2015 # Version 3.0 Contact Mike Cook Phone Revision History Date Action 5/16/2014 Draft Complete 6/30/2014 Reviewed by IT Management Advisory Committee, Campus Information Security Committee, ITS Security Team 7/9/2014 Approved by CIO 01/26/2015 Reviewed. Content suggestions. Added VPN passage. Hien Huynh 11/10/2015 Incorporated changes from campus constituents Distributed to Campus. Page 3
4 Table of Contents Executive Summary... 2 Introduction and Purpose... 5 Scope... 5 Standard... 5 Security and Encryption... 5 Identification of Users... 5 Illegal Content... 5 Encryption... 5 Airwave Control... 6 Bandwidth Considerations... 6 Roles and Responsibilities... 7 Colleges, Departments, Units, Individuals... 7 IT Services IT Help Desk... 7 Page 4
5 Introduction and Purpose SJSU is responsible for providing a communication network that is accessible, reliable, legal, and secure. In order to guarantee this level of service IT Services manages the airspace. Any College, Department, Unit, or Individual who wishes to utilize wireless technology must follow stated policies, protocols, practices, and procedures. This standard outlines the roles, processes, requirements, and restrictions surrounding wireless Wi-Fi networks. Scope This policy applies to all wireless Wi-Fi networks whose transmission origin is located on a property currently owned or occupied by San José State University or its auxiliaries including but not limited to: SJSU Main Campus (including all Academic, Administrative, Auxiliary, MLK Library, Foundry, University Housing buildings and outdoor spaces), SJSU South campus (all buildings and outdoor spaces), 210 N. 4 th Street, Moss Landing Marine Labs, and Bunker Hill where WiFi is provided by campus. Standard Security and Encryption Identification of Users In order to ensure compliance with ICSUAM 8000, all wireless devices capable of accessing campus Wi-Fi systems must authenticate utilizing a username and password. IT Services will provide a mechanism to register devices incapable or infeasible of following this standard by the means of device registration. Devices will be registered to an individual and in accordance with ICSUAM 8105 that individual will be held accountable for any activities taking place on those devices. Illegal Content IT Services reserves the right to block all known malicious protocols, ports and all applications whose mainstream usage is for illegal activity (Ares, Bittorrent, IRC, etc.) or non-supported payment methods (Paypal, Square). Encryption In order to support all devices, a number of supported wireless networks exist. Users shall connect to the network with the least amount of security risk. Connection Order for Wireless Networks 1. SJSU_Premier 2. Eduroam 3. SJSU_Guest 4. SJSU_MyDevices Page 5
6 Impersonation of IT Services Supported Wireless Networks No Colleges, Departments, Units, or Individuals shall configure a wireless SSID that contain SJSU (case insensitive) within SJSU s airspace. Any users doing so will be referred to the appropriate Vice President or Judicial Affairs. Airwave Control Includes: SJSU Main Campus (including all Academic, Administrative, Auxiliary, MLK Library, Self-Support, University Housing and outdoor spaces), SJSU South campus (all buildings and outdoor spaces), 210 N. 4 th Street, Moss Landing Marine Labs, and Bunker Hill. IT Services shall provide the sole means for wireless connectivity in all supported locations. Hotspots and Printers with WiFi shall be configured to disable wireless features wherever possible. IT Services is committed to providing reliable wireless services to all on-campus buildings and select outdoor areas. Poor service in specific areas is not adequate justification for installing rogue access point. IT Services reserves the right to disable wired ports, wirelessly disable Access Points and block MAC Addresses associated with rogue wireless networks. To report on-campus areas with inadequate service, contact the IT Help Desk at ( ) or ithelpdesk@sjsu.edu For more information on wireless coverage please visit the Wireless Web Site. Unsupported Networks Colleges, Departments, Units, or Individuals shall not knowingly or willingly activate wireless networks without prior written authorization from IT Services ISO or CIO. This includes but is not limited to wireless routers and printers, which broadcast their own network. IT Services reserves the right to disconnect, flood, or block unsupported wireless networks within SJSU s airspace. Under certain circumstances IT Services may approve non-standard network communication devices for usage. Non-standard devices must meet the following criteria: The use is for a specific purpose. The device will only be used in a specific location and not moved without prior written authorization from the IT Services ISO or CIO. The device must be manageable as appropriate by either IT Services or authorized entity. If available, devices must require username/password authentication. The strongest form of encryption available must be used. IP Address assignment must be made in coordination with IT Services. Final responsibility for the data security and proper use of non-standard devices shall remain with the requestor. Any network problem caused by such a device or by any attached device(s) will result in the immediate disconnection of the device or deactivation of network port. All connections of non-standard network communication devices must be pre-approved by IT Services Change Control. Bandwidth Considerations In order to maintain adequate services for all parties, IT Services reserves the right to throttle bandwidth or cap total usage as it deems required to meet the needs of the university. Page 6
7 Roles and Responsibilities Colleges, Departments, Units, Individuals Colleges, Departments, Units, and Individuals are responsible for compliance with SJSU security policies, standards, and procedures. Colleges, Departments, Units, and Individuals are responsible for contacting the IT Help Desk (4-1530, , or with any issues and requests. Colleges, Departments, Units, and Individuals requesting unsupported devices are responsible for contacting IT services to initiate the request process, providing all requested information in relation to the service, and notifying IT Services when service is no longer needed. IT Services IT Help Desk The IT Help Desk responds to trouble tickets initiated by individuals, escalates issues as appropriate, and provides a single point of contact for all requests. Page 7
Standard: Network Security
 Standard: Network Security Page 1 Executive Summary Network security is important in the protection of our network and services from unauthorized modification, destruction, or disclosure. It is essential
Standard: Network Security Page 1 Executive Summary Network security is important in the protection of our network and services from unauthorized modification, destruction, or disclosure. It is essential
9 Simple steps to secure your Wi-Fi Network.
 9 Simple steps to secure your Wi-Fi Network. Step 1: Change the Default Password of Modem / Router After opening modem page click on management - access control password. Select username, confirm old password
9 Simple steps to secure your Wi-Fi Network. Step 1: Change the Default Password of Modem / Router After opening modem page click on management - access control password. Select username, confirm old password
Standard: Event Monitoring
 Standard: Event Monitoring Page 1 Executive Summary The Event Monitoring Standard defines the requirements for Information Security event monitoring within SJSU computing resources to ensure that information
Standard: Event Monitoring Page 1 Executive Summary The Event Monitoring Standard defines the requirements for Information Security event monitoring within SJSU computing resources to ensure that information
Standard: Information Security Awareness Training
 Standard: Information Security Awareness Training Page 1 Executive Summary San Jose State University (SJSU) is highly diversified in the information that it collects and maintains on its community members.
Standard: Information Security Awareness Training Page 1 Executive Summary San Jose State University (SJSU) is highly diversified in the information that it collects and maintains on its community members.
Standard: Email and Campus Communication
 Information Security Standards Email and Campus Communication Standard IS-ECC Effective Date TBD Email security@sjsu.edu # Version 2.0 Contact Mike Cook Phone 408-924-1705 Standard: Email and Campus Communication
Information Security Standards Email and Campus Communication Standard IS-ECC Effective Date TBD Email security@sjsu.edu # Version 2.0 Contact Mike Cook Phone 408-924-1705 Standard: Email and Campus Communication
The Importance of Organizing Your SJSU Information Assets
 Standard: Asset Control Page 1 Executive Summary The Asset Control Standard defines the requirements for controlling and ensuring all SJSU computing hardware, software, and confidential assets are identified,
Standard: Asset Control Page 1 Executive Summary The Asset Control Standard defines the requirements for controlling and ensuring all SJSU computing hardware, software, and confidential assets are identified,
Introduction and Purpose... 2 Scope... 2 Auxiliary units... 2. Part-Time, Temporary faculty/staff, Volunteer, Contractor and Student Assistants...
 Contents Workstation Refresh & Virtual Desktop Infrastructure Program Introduction and Purpose... 2 Scope... 2 Auxiliary units... 2 Part-Time, Temporary faculty/staff, Volunteer, Contractor and Student
Contents Workstation Refresh & Virtual Desktop Infrastructure Program Introduction and Purpose... 2 Scope... 2 Auxiliary units... 2 Part-Time, Temporary faculty/staff, Volunteer, Contractor and Student
Security Awareness. Wireless Network Security
 Security Awareness Wireless Network Security Attacks on Wireless Networks Three-step process Discovering the wireless network Connecting to the network Launching assaults Security Awareness, 3 rd Edition
Security Awareness Wireless Network Security Attacks on Wireless Networks Three-step process Discovering the wireless network Connecting to the network Launching assaults Security Awareness, 3 rd Edition
Wireless Network Standard
 Last Modified: 10/20/15 Wireless Network Standard Purpose The standard and guidelines described in this document will ensure the uniformity of wireless network access points at the University of Georgia.
Last Modified: 10/20/15 Wireless Network Standard Purpose The standard and guidelines described in this document will ensure the uniformity of wireless network access points at the University of Georgia.
1 Purpose... 2. 2 Scope... 2. 3 Roles and Responsibilities... 2. 4 Physical & Environmental Security... 3. 5 Access Control to the Network...
 Contents 1 Purpose... 2 2 Scope... 2 3 Roles and Responsibilities... 2 4 Physical & Environmental Security... 3 5 Access Control to the Network... 3 6 Firewall Standards... 4 7 Wired network... 5 8 Wireless
Contents 1 Purpose... 2 2 Scope... 2 3 Roles and Responsibilities... 2 4 Physical & Environmental Security... 3 5 Access Control to the Network... 3 6 Firewall Standards... 4 7 Wired network... 5 8 Wireless
Standard: Email Retention
 Information Security Standards Email Retention Standard IS-ER Effective Date TBD Email security@sjsu.edu # Version 2.0 Contact Mike Cook Phone 408-924-1705 Standard: Email Retention Page 1 Executive Summary
Information Security Standards Email Retention Standard IS-ER Effective Date TBD Email security@sjsu.edu # Version 2.0 Contact Mike Cook Phone 408-924-1705 Standard: Email Retention Page 1 Executive Summary
Basic Citrix Manual. Windows Computers and Laptops. Version 1.3. Created by Joshua Lindemann
 Basic Citrix Manual Version 1.3 Created by Joshua Lindemann Table of Contents Technology Services Help Desk... 3 Background... 4 Citrix Virtual Environment... 4 Wireless Access... 4 Security... 4 Configuring
Basic Citrix Manual Version 1.3 Created by Joshua Lindemann Table of Contents Technology Services Help Desk... 3 Background... 4 Citrix Virtual Environment... 4 Wireless Access... 4 Security... 4 Configuring
Network Security & Connection Policy
 Network Security & Connection Policy Effective from 17 February 2015 Version Number: 2.0 Author: Network Manager, IT Services Document Control Information Status and reason for development Revised to reflect
Network Security & Connection Policy Effective from 17 February 2015 Version Number: 2.0 Author: Network Manager, IT Services Document Control Information Status and reason for development Revised to reflect
The next generation of knowledge and expertise Wireless Security Basics
 The next generation of knowledge and expertise Wireless Security Basics HTA Technology Security Consulting., 30 S. Wacker Dr, 22 nd Floor, Chicago, IL 60606, 708-862-6348 (voice), 708-868-2404 (fax), www.hta-inc.com
The next generation of knowledge and expertise Wireless Security Basics HTA Technology Security Consulting., 30 S. Wacker Dr, 22 nd Floor, Chicago, IL 60606, 708-862-6348 (voice), 708-868-2404 (fax), www.hta-inc.com
Network Services One Washington Square, San Jose, CA 95192-0209 408-924-1530
 SJSU Premier Wi-Fi Service Network Services One Washington Square, San Jose, CA 95192-0209 408-924-1530 The SJSU Premier Wi-Fi service transmits your data across a secure, encrypted connection. This ensures
SJSU Premier Wi-Fi Service Network Services One Washington Square, San Jose, CA 95192-0209 408-924-1530 The SJSU Premier Wi-Fi service transmits your data across a secure, encrypted connection. This ensures
AirWave Help Desk Guide. Help Desk Guide: Troubleshooting WLAN Issues with AirWave. 2006, AirWave Wireless, Inc. All rights reserved.
 Help Desk Guide: Troubleshooting WLAN Issues with AirWave 2006, AirWave Wireless, Inc. All rights reserved. Page 1 of 8 Overview: Wireless LAN Troubleshooting for the Help Desk In a typical IT organization,
Help Desk Guide: Troubleshooting WLAN Issues with AirWave 2006, AirWave Wireless, Inc. All rights reserved. Page 1 of 8 Overview: Wireless LAN Troubleshooting for the Help Desk In a typical IT organization,
High Speed Internet, Welcome Kit. If your apartment is served by Ethernet: How do I connect to the network if not using a router?:
 High Speed Internet, Welcome Kit We provide a WIRED High Speed Internet connection to your apartment. Your apartment will be served by a DSL modem or Ethernet jack. If you have multiple users in your apartment
High Speed Internet, Welcome Kit We provide a WIRED High Speed Internet connection to your apartment. Your apartment will be served by a DSL modem or Ethernet jack. If you have multiple users in your apartment
Edith Cowan University Information Technology Services Centre
 Information There are three wireless networks on campus which give you access to the ECU website, the staff intranet, the internet and other ECU resources: ECU This is the easiest to use and safest wireless
Information There are three wireless networks on campus which give you access to the ECU website, the staff intranet, the internet and other ECU resources: ECU This is the easiest to use and safest wireless
UAG Series. Application Note. Unified Access Gateway. Version 4.00 Edition 1, 04/2014. Copyright 2014 ZyXEL Communications Corporation
 UAG Series Unified Access Gateway Version 4.00 Edition 1, 04/2014 Application Note Copyright 2014 ZyXEL Communications Corporation Table of Contents Scenario 1 How to Activate a Paid Access Hotspot...
UAG Series Unified Access Gateway Version 4.00 Edition 1, 04/2014 Application Note Copyright 2014 ZyXEL Communications Corporation Table of Contents Scenario 1 How to Activate a Paid Access Hotspot...
HKBN Wi-Fi Service User Guide
 HKBN Wi-Fi Service User Guide Content 1. Device Requirements 2. Login Procedures and Auto Login Settings 3. Forget Username / Password 4. Manage Your Auto Login Setting at HKBN Website 5. Technical Support
HKBN Wi-Fi Service User Guide Content 1. Device Requirements 2. Login Procedures and Auto Login Settings 3. Forget Username / Password 4. Manage Your Auto Login Setting at HKBN Website 5. Technical Support
Security. TestOut Modules 12.6 12.10
 Security TestOut Modules 12.6 12.10 Authentication Authentication is the process of submitting and checking credentials to validate or prove user identity. 1. Username 2. Credentials Password Smart card
Security TestOut Modules 12.6 12.10 Authentication Authentication is the process of submitting and checking credentials to validate or prove user identity. 1. Username 2. Credentials Password Smart card
UAG4100 Support Notes
 2013 UAG4100 Support Notes CSO ZyXEL 2013/07/29 Table of Contents Scenario 1 Activate a Paid Access Hotspot... 2 Print ticket to access the Internet... 3 Pay with PayPal payment service to access the Internet...
2013 UAG4100 Support Notes CSO ZyXEL 2013/07/29 Table of Contents Scenario 1 Activate a Paid Access Hotspot... 2 Print ticket to access the Internet... 3 Pay with PayPal payment service to access the Internet...
Information Technology Services August 19, 2015 - Fall 2015
 Information Technology Services August 19, 2015 - Fall 2015 IT Services Cover All of the University and Community 2 Internally Connected University & Community Teaching & Learning Research Support R&D
Information Technology Services August 19, 2015 - Fall 2015 IT Services Cover All of the University and Community 2 Internally Connected University & Community Teaching & Learning Research Support R&D
INFORMATION TECHNOLOGY MANAGEMENT COMMITTEE LIVINGSTON, NJ WWW.LIVINGSTONNJ.ORG ITMC TECH TIP ROB COONCE, MARCH 2008
 INFORMATION TECHNOLOGY MANAGEMENT COMMITTEE LIVINGSTON, NJ WWW.LIVINGSTONNJ.ORG What is wireless technology? ITMC TECH TIP ROB COONCE, MARCH 2008 In our world today, this may mean sitting down at a coffee
INFORMATION TECHNOLOGY MANAGEMENT COMMITTEE LIVINGSTON, NJ WWW.LIVINGSTONNJ.ORG What is wireless technology? ITMC TECH TIP ROB COONCE, MARCH 2008 In our world today, this may mean sitting down at a coffee
Mac OS X. Staff members using NEIU issued laptops and computers on Active Directory can access NEIU resources that are available on the wired network.
 Mac OS X The University Technology Services is privileged to offer a secure wifi network to the university community. Connecting to this network will provide you with benefits in security and improved
Mac OS X The University Technology Services is privileged to offer a secure wifi network to the university community. Connecting to this network will provide you with benefits in security and improved
Basic Citrix Manual. Apple Computers and Laptops. Version 1.3. Created by Joshua Lindemann
 Basic Citrix Manual Version 1.3 Created by Joshua Lindemann Table of Contents Technology Services Help Desk... 3 Background... 4 Citrix Virtual Environment... 4 Wireless Access... 4 Security... 4 Configuring
Basic Citrix Manual Version 1.3 Created by Joshua Lindemann Table of Contents Technology Services Help Desk... 3 Background... 4 Citrix Virtual Environment... 4 Wireless Access... 4 Security... 4 Configuring
Troubleshooting WLAN Issues
 Troubleshooting WLAN Issues AirWave Help Desk Guide Wireless LAN Troubleshooting for the Help Desk In a typical IT organization, it is the Help Desk s job to take incoming user support calls and determine
Troubleshooting WLAN Issues AirWave Help Desk Guide Wireless LAN Troubleshooting for the Help Desk In a typical IT organization, it is the Help Desk s job to take incoming user support calls and determine
Connecting to UNOSECURE using Windows 7
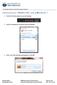 Connecting to UNOSECURE using Windows 7 1. Click the Wireless status icon on the task bar. 2. Select the unosecure connection and click connect. 3. Enter your UNO username and password. Click OK. UCC Help
Connecting to UNOSECURE using Windows 7 1. Click the Wireless status icon on the task bar. 2. Select the unosecure connection and click connect. 3. Enter your UNO username and password. Click OK. UCC Help
CONNECTING THE RASPBERRY PI TO A NETWORK
 CLASSROOM CHALLENGE CONNECTING THE RASPBERRY PI TO A NETWORK In this lesson you will learn how to connect the Raspberry Pi computer to a network with both a wired and a wireless connection. To complete
CLASSROOM CHALLENGE CONNECTING THE RASPBERRY PI TO A NETWORK In this lesson you will learn how to connect the Raspberry Pi computer to a network with both a wired and a wireless connection. To complete
OTC Student Wireless Network
 OTC Student Wireless Network (Connection Instructions for Windows 8, Windows 7, MAC OSX, and ios) Note: Unsupported Devices: Warning: The OTC student wireless network conforms to the IEEE 802.11 a/b/g
OTC Student Wireless Network (Connection Instructions for Windows 8, Windows 7, MAC OSX, and ios) Note: Unsupported Devices: Warning: The OTC student wireless network conforms to the IEEE 802.11 a/b/g
Help Desk Guide. Enterprise Troubleshooting WLAN Issues with AirWave Wireless Management Suite
 Help Desk Guide Enterprise Troubleshooting WLAN Issues with AirWave Wireless Management Suite Overview In a typical IT organization, it is the Help Desk s job to take incoming user support calls and determine
Help Desk Guide Enterprise Troubleshooting WLAN Issues with AirWave Wireless Management Suite Overview In a typical IT organization, it is the Help Desk s job to take incoming user support calls and determine
Laney Information Technology Services
 Laney Information Technology Services Mission Statement The mission of the Laney Information Technology Services (LITS) is to provide a scalable technological infrastructure, and provide innovation in
Laney Information Technology Services Mission Statement The mission of the Laney Information Technology Services (LITS) is to provide a scalable technological infrastructure, and provide innovation in
2.1.1 This policy and any future changes requires ratification by CAUDIT.
 1.0 Background to this document 1.1 This document sets out guidelines that cover the control of the supply and receipt of Internet access for educational purposes, that is primarily (but not exclusively)
1.0 Background to this document 1.1 This document sets out guidelines that cover the control of the supply and receipt of Internet access for educational purposes, that is primarily (but not exclusively)
TEMPLE UNIVERSITY POLICIES AND PROCEDURES MANUAL
 TEMPLE UNIVERSITY POLICIES AND PROCEDURES MANUAL Title: Computer and Network Security Policy Policy Number: 04.72.12 Effective Date: November 4, 2003 Issuing Authority: Office of the Vice President for
TEMPLE UNIVERSITY POLICIES AND PROCEDURES MANUAL Title: Computer and Network Security Policy Policy Number: 04.72.12 Effective Date: November 4, 2003 Issuing Authority: Office of the Vice President for
PIXMA MX920. series. Setup Guide
 PIXMA MX920 series Setup Guide CANON INC. 2012 Setup Guide This guide provides information for setting up a network connection for the printer. Network Connection Wireless Connection Preparation for Connection
PIXMA MX920 series Setup Guide CANON INC. 2012 Setup Guide This guide provides information for setting up a network connection for the printer. Network Connection Wireless Connection Preparation for Connection
Connecting to the University Wireless Network
 Connecting to the University Wireless Network Wifi is available to staff and registered students of University in certain areas of the three campuses of the University. This area of coverage will be expanded
Connecting to the University Wireless Network Wifi is available to staff and registered students of University in certain areas of the three campuses of the University. This area of coverage will be expanded
eduroam Overview and Device Configuration
 eduroam Overview and Device Configuration OTS PUBLICATION: WR3 REVISED 07-5-04 TRAINING@TOWSON.EDU OFFICE OF TECHNOLOGY SERVICES =Shortcut =Advice =Caution Introduction eduroam is a global wireless service
eduroam Overview and Device Configuration OTS PUBLICATION: WR3 REVISED 07-5-04 TRAINING@TOWSON.EDU OFFICE OF TECHNOLOGY SERVICES =Shortcut =Advice =Caution Introduction eduroam is a global wireless service
WiFi-SB-L3 300M WiFi Router WiFi Bridge WiFi Repeater. WiFi Router WiFi Repeater WiFi Bridge WiFi-SB-L3 Quick Setting Guide
 300M WiFi Router WiFi Repeater WiFi Bridge WiFi-SB-L3 Quick Setting Guide 1 Chapter 1 Router Mode Quick Setup Guide 1. Let WiFi-SB-L3 be powered on. 2.Turn on wireless network connection, disabled local
300M WiFi Router WiFi Repeater WiFi Bridge WiFi-SB-L3 Quick Setting Guide 1 Chapter 1 Router Mode Quick Setup Guide 1. Let WiFi-SB-L3 be powered on. 2.Turn on wireless network connection, disabled local
Instructions for connecting to winthropsecure. Windows 7/8 Quick Connect Windows 7/8 Manual Wireless Set Up Apple Quick Connect Apple Settings Check
 Instructions for connecting to winthropsecure Windows 7/8 Quick Connect Windows 7/8 Manual Wireless Set Up Apple Quick Connect Apple Settings Check Windows 7 Windows 8 Quick Connect 1. Select the Wi-Fi
Instructions for connecting to winthropsecure Windows 7/8 Quick Connect Windows 7/8 Manual Wireless Set Up Apple Quick Connect Apple Settings Check Windows 7 Windows 8 Quick Connect 1. Select the Wi-Fi
University of Texas at Arlington. Guide for Internet, TV and Phone Services
 University of Texas at Arlington Guide for Internet, TV and Phone Services Contents Notice of Service Changes... 2 Summary of Internet, TV, and Phone Services for University Residence Halls... 3 Summary
University of Texas at Arlington Guide for Internet, TV and Phone Services Contents Notice of Service Changes... 2 Summary of Internet, TV, and Phone Services for University Residence Halls... 3 Summary
MOBILE GAMING SYSTEM POLICIES
 MOBILE GAMING SYSTEM POLICIES This document is intended to provide further clarification on applicable mobile gaming Technical Standards and additionally to define policies associated with the manufacturing
MOBILE GAMING SYSTEM POLICIES This document is intended to provide further clarification on applicable mobile gaming Technical Standards and additionally to define policies associated with the manufacturing
Wireless Network Policy
 Wireless Network Policy Purpose Guide the deployment and integrity of wireless networking on the Kettering University campus to ensure reliable, compatible, and secure operation Protect the security of
Wireless Network Policy Purpose Guide the deployment and integrity of wireless networking on the Kettering University campus to ensure reliable, compatible, and secure operation Protect the security of
AirMax4GW 4G LTE + WiFi Outdoor Gateway
 4G LTE + WiFi Outdoor Gateway Solution Hardware Specification The is a standalone 4G LTE outdoor gateway that can distribute 4G or 3G Internet signal through WiFi or Ethernet connec ons. It is equipped
4G LTE + WiFi Outdoor Gateway Solution Hardware Specification The is a standalone 4G LTE outdoor gateway that can distribute 4G or 3G Internet signal through WiFi or Ethernet connec ons. It is equipped
NetDiverse, LLC Managed Internal Broadband Service (MIBS) Service Level Agreement
 NetDiverse, LLC Managed Internal Broadband Service (MIBS) Service Level Agreement Service Description: Managed Internal Broadband Service ( MIB Service, MIBS, Managed WiFi, Managed WiFi/LAN, Network as
NetDiverse, LLC Managed Internal Broadband Service (MIBS) Service Level Agreement Service Description: Managed Internal Broadband Service ( MIB Service, MIBS, Managed WiFi, Managed WiFi/LAN, Network as
VPN Overview. The path for wireless VPN users
 VPN Overview The path for wireless VPN users First, the user's computer (the blue computer) connects to an access point in the uiuc-wireless-net network and is assigned an IP address in that range (172.21.0.0
VPN Overview The path for wireless VPN users First, the user's computer (the blue computer) connects to an access point in the uiuc-wireless-net network and is assigned an IP address in that range (172.21.0.0
Defiance College Networking Handbook
 Defiance College Networking Handbook Installation Instructions and Reference Manual for Campus Network Connections including Residence Halls and Wireless Access Points Revision 20141203 Preface All residence
Defiance College Networking Handbook Installation Instructions and Reference Manual for Campus Network Connections including Residence Halls and Wireless Access Points Revision 20141203 Preface All residence
Section 12 MUST BE COMPLETED BY: 4/22
 Test Out Online Lesson 12 Schedule Section 12 MUST BE COMPLETED BY: 4/22 Section 12.1: Best Practices This section discusses the following security best practices: Implement the Principle of Least Privilege
Test Out Online Lesson 12 Schedule Section 12 MUST BE COMPLETED BY: 4/22 Section 12.1: Best Practices This section discusses the following security best practices: Implement the Principle of Least Privilege
User Guide for eduroam
 User Guide for eduroam 獲 以 下 認 證 : Certificado pela: Certified by: 澳 門 望 廈 山 Colina de Mong-Há, Macau 電 話 : (853) 8598 3120 Tel: (853) 8598 3120 傳 真 : (853) 8598 3151 Fax: (853) 8598 3151 www.ift.edu.mo
User Guide for eduroam 獲 以 下 認 證 : Certificado pela: Certified by: 澳 門 望 廈 山 Colina de Mong-Há, Macau 電 話 : (853) 8598 3120 Tel: (853) 8598 3120 傳 真 : (853) 8598 3151 Fax: (853) 8598 3151 www.ift.edu.mo
GENERAL INFORMATION. 2 Document Approver Data & Information Management Department Head 3 Minimum list of document
 Document Title Wi-Fi POLICY Page 1 of 5 1 Document type Policy GENERAL INFORMATION 2 Document Approver Data & Information Management Department Head 3 Minimum list of document users to be notified upon
Document Title Wi-Fi POLICY Page 1 of 5 1 Document type Policy GENERAL INFORMATION 2 Document Approver Data & Information Management Department Head 3 Minimum list of document users to be notified upon
Deploying secure wireless network services The Avaya Identity Engines portfolio offers flexible, auditable management for secure wireless networks.
 Table of Contents Section 1: Executive summary...1 Section 2: The challenge...2 Section 3: WLAN security...3 and the 802.1X standard Section 4: The solution...4 Section 5: Security...4 Section 6: Encrypted
Table of Contents Section 1: Executive summary...1 Section 2: The challenge...2 Section 3: WLAN security...3 and the 802.1X standard Section 4: The solution...4 Section 5: Security...4 Section 6: Encrypted
Standard: Application Service Provider Security Requirements
 Standard: Application Service Provider Security Requirements Page 1 Executive Summary SJSU has the option to select and contract with approved 3 rd parties, application service providers, services and
Standard: Application Service Provider Security Requirements Page 1 Executive Summary SJSU has the option to select and contract with approved 3 rd parties, application service providers, services and
Wireless Network Standard and Guidelines
 Wireless Network Standard and Guidelines Purpose The standard and guidelines listed in this document will ensure the uniformity of wireless network access points and provide guidance for monitoring, maintaining
Wireless Network Standard and Guidelines Purpose The standard and guidelines listed in this document will ensure the uniformity of wireless network access points and provide guidance for monitoring, maintaining
Link Layer and Network Layer Security for Wireless Networks
 White Paper Link Layer and Network Layer Security for Wireless Networks Abstract Wireless networking presents a significant security challenge. There is an ongoing debate about where to address this challenge:
White Paper Link Layer and Network Layer Security for Wireless Networks Abstract Wireless networking presents a significant security challenge. There is an ongoing debate about where to address this challenge:
Billing Platform Feature Specifications Supplement
 Billing Platform Feature Specifications Supplement Software Release v 2.0 The information in this Supplement has been carefully reviewed and is believed to be accurate. The vendor assumes no responsibility
Billing Platform Feature Specifications Supplement Software Release v 2.0 The information in this Supplement has been carefully reviewed and is believed to be accurate. The vendor assumes no responsibility
General Questions... 1. Requesting Access... 2. Client Support... 3. Downloading Issues... 4. Installation Issues... 4. Connectivity Issues...
 Contents General Questions... 1 Requesting Access... 2 Client Support... 3 Downloading Issues... 4 Installation Issues... 4 Connectivity Issues... 5 Performance Issues... 7 Application Issues... 8 General
Contents General Questions... 1 Requesting Access... 2 Client Support... 3 Downloading Issues... 4 Installation Issues... 4 Connectivity Issues... 5 Performance Issues... 7 Application Issues... 8 General
Massey University Wireless Network - Client
 Massey University Wireless Network - Client Configuration Windows Mobile 5/6 Windows Mobile wireless network Requirements Information Technology Services You must have an active Massey network account,
Massey University Wireless Network - Client Configuration Windows Mobile 5/6 Windows Mobile wireless network Requirements Information Technology Services You must have an active Massey network account,
Campus wide IT Services. Student Orientation Aug 2015
 Campus wide IT Services Student Orientation Aug 2015 Campus wide IT Services Provided by: Contact point: ITServ (interlab) Helpdesk Helpdesk s contact: Campus IT Services EMAIL: helpdesk@ait.asia (use
Campus wide IT Services Student Orientation Aug 2015 Campus wide IT Services Provided by: Contact point: ITServ (interlab) Helpdesk Helpdesk s contact: Campus IT Services EMAIL: helpdesk@ait.asia (use
Integrating a Hitachi IP5000 Wireless IP Phone
 November, 2007 Avaya Quick Edition Integrating a Hitachi IP5000 Wireless IP Phone This application note explains how to configure the Hitachi IP5000 wireless IP telephone to connect with Avaya Quick Edition
November, 2007 Avaya Quick Edition Integrating a Hitachi IP5000 Wireless IP Phone This application note explains how to configure the Hitachi IP5000 wireless IP telephone to connect with Avaya Quick Edition
Appalachian Regional Commission Evaluation Report. Table of Contents. Results of Evaluation... 1. Areas for Improvement... 2
 Report No. 13-35 September 27, 2013 Appalachian Regional Commission Table of Contents Results of Evaluation... 1 Areas for Improvement... 2 Area for Improvement 1: The agency should implement ongoing scanning
Report No. 13-35 September 27, 2013 Appalachian Regional Commission Table of Contents Results of Evaluation... 1 Areas for Improvement... 2 Area for Improvement 1: The agency should implement ongoing scanning
Technical Support Information
 F1P000GNukSK Skype Phone 1: What is the F1P000GNukSK? The F1P000GNukSK is a Wi-Fi phone (IEEE 802.11b/g) designed to allow users to make Skype calls without having to use a computer anywhere that a wireless
F1P000GNukSK Skype Phone 1: What is the F1P000GNukSK? The F1P000GNukSK is a Wi-Fi phone (IEEE 802.11b/g) designed to allow users to make Skype calls without having to use a computer anywhere that a wireless
Click Main on the left hand side then click on Password at the top of the page.
 Q: How do I change the password on my router? A: Step 1. Log into the router by entering its IP address into a browser. The default IP address is http://192.168.1.1. The default username is admin with
Q: How do I change the password on my router? A: Step 1. Log into the router by entering its IP address into a browser. The default IP address is http://192.168.1.1. The default username is admin with
Network Security Policy
 Network Security Policy Policy Contents I. POLICY STATEMENT II. REASON FOR POLICY III. SCOPE IV. AUDIENCE V. POLICY TEXT VI. PROCEDURES VII. RELATED INFORMATION VIII. DEFINITIONS IX. FREQUENTLY ASKED QUESTIONS
Network Security Policy Policy Contents I. POLICY STATEMENT II. REASON FOR POLICY III. SCOPE IV. AUDIENCE V. POLICY TEXT VI. PROCEDURES VII. RELATED INFORMATION VIII. DEFINITIONS IX. FREQUENTLY ASKED QUESTIONS
Network Security Policy
 Network Security Policy I. PURPOSE Attacks and security incidents constitute a risk to the University's academic mission. The loss or corruption of data or unauthorized disclosure of information on campus
Network Security Policy I. PURPOSE Attacks and security incidents constitute a risk to the University's academic mission. The loss or corruption of data or unauthorized disclosure of information on campus
ADDENDUM 12 TO APPENDIX 8 TO SCHEDULE 3.3
 ADDENDUM 12 TO APPENDIX 8 TO SCHEDULE 3.3 TO THE Overview EXHIBIT T to Amendment No. 60 Secure Wireless Network Services are based on the IEEE 802.11 set of standards and meet the Commonwealth of Virginia
ADDENDUM 12 TO APPENDIX 8 TO SCHEDULE 3.3 TO THE Overview EXHIBIT T to Amendment No. 60 Secure Wireless Network Services are based on the IEEE 802.11 set of standards and meet the Commonwealth of Virginia
Design and Implementation Guide. Apple iphone Compatibility
 Design and Implementation Guide Apple iphone Compatibility Introduction Security in wireless LANs has long been a concern for network administrators. While securing laptop devices is well understood, new
Design and Implementation Guide Apple iphone Compatibility Introduction Security in wireless LANs has long been a concern for network administrators. While securing laptop devices is well understood, new
United States Trustee Program s Wireless LAN Security Checklist
 United States Trustee Program s Wireless LAN Security Checklist In support of a standing trustee s proposed implementation of Wireless Access Points (WAP) in ' 341 meeting rooms and courtrooms, the following
United States Trustee Program s Wireless LAN Security Checklist In support of a standing trustee s proposed implementation of Wireless Access Points (WAP) in ' 341 meeting rooms and courtrooms, the following
Enterprise Broadband Customer Service Description
 BT 2012 Issue 2_8 Table of Contents INTRODUCTION... 3 SERVICE OVERVIEW... 4 BENEFITS OF CHOOSING ENTERPRISE BROADBAND... 5 SERVICE DETAILS... 5 THE WORKPLACE... 5 COVERAGE... 5 ENTERPRISE BROADBAND...
BT 2012 Issue 2_8 Table of Contents INTRODUCTION... 3 SERVICE OVERVIEW... 4 BENEFITS OF CHOOSING ENTERPRISE BROADBAND... 5 SERVICE DETAILS... 5 THE WORKPLACE... 5 COVERAGE... 5 ENTERPRISE BROADBAND...
UCL Remote Access VPN Service Mac OS X User Guide
 INFORMATION SERVICES DIVISION (ISD) NETWORK SERVICES GROUP UCL Remote Access VPN Service Mac OS X User Guide Version 3.0 Date 14 th November 2012 Author MC Document Details N/A Last Updated 05 November
INFORMATION SERVICES DIVISION (ISD) NETWORK SERVICES GROUP UCL Remote Access VPN Service Mac OS X User Guide Version 3.0 Date 14 th November 2012 Author MC Document Details N/A Last Updated 05 November
1. Open your Internet Browser and enter http://192.168.1.254. 2. You will be prompted to enter a username and password.
 Connect to your Thomson modem. It is recommended that you connect your computer to your Thomson modem via an Ethernet cable. This guarantees maintainability of connection to modem and prevents loss of
Connect to your Thomson modem. It is recommended that you connect your computer to your Thomson modem via an Ethernet cable. This guarantees maintainability of connection to modem and prevents loss of
Quick Installation Guide
 0, Total 18 Quick Installation Guide Sep, 2013 1, Total 18 Thank you for purchasing Enterprise High Gain Outdoor CPE. This manual will instruct you how to configure and manage this CPE, enable you to use
0, Total 18 Quick Installation Guide Sep, 2013 1, Total 18 Thank you for purchasing Enterprise High Gain Outdoor CPE. This manual will instruct you how to configure and manage this CPE, enable you to use
Canterbury College Eduroam Wi-Fi Guide
 Canterbury College Eduroam Wi-Fi Guide Version 2.2 (Sept 2014) DG11 Phone: 01227 811144 Email: ITservicedesk@canterburycollege.ac.uk Web: ITservicedesk.cant-col.ac.uk Table of Contents I. Overview... 2
Canterbury College Eduroam Wi-Fi Guide Version 2.2 (Sept 2014) DG11 Phone: 01227 811144 Email: ITservicedesk@canterburycollege.ac.uk Web: ITservicedesk.cant-col.ac.uk Table of Contents I. Overview... 2
Edith Cowan University Information Technology Services Centre
 Information There are three wireless networks on campus which give you access to the ECU website, the staff intranet, the internet and other ECU resources: ECU This is the easiest to use and safest wireless
Information There are three wireless networks on campus which give you access to the ECU website, the staff intranet, the internet and other ECU resources: ECU This is the easiest to use and safest wireless
Network Service Policy
 Network Service Policy TABLE OF CONTENTS PURPOSE... 3 SCOPE... 3 AUDIENCE... 3 COMPLIANCE & ENFORCEMENT... 3 POLICY STATEMENTS... 4 1. General... 4 2. Administrative Standards... 4 3. Network Use... 5
Network Service Policy TABLE OF CONTENTS PURPOSE... 3 SCOPE... 3 AUDIENCE... 3 COMPLIANCE & ENFORCEMENT... 3 POLICY STATEMENTS... 4 1. General... 4 2. Administrative Standards... 4 3. Network Use... 5
How to access UCSD Restricted Library Journals off campus, including from Rady Children's hospital.
 How to access UCSD Restricted Library Journals off campus, including from Rady Children's hospital. Most library e-journals & databases are restricted to use on campus, or use off-campus only by current
How to access UCSD Restricted Library Journals off campus, including from Rady Children's hospital. Most library e-journals & databases are restricted to use on campus, or use off-campus only by current
E-Mail: SupportCenter@uhcl.edu Phone: 281-283-2828 Fax: 281-283-2969 Box: 230 http://www.uhcl.edu/uct
 A VPN (Virtual Private Network) provides a secure, encrypted tunnel from your computer to UHCL's network when off campus. UHCL offers VPN software to allow authenticated, secure access to many UHCL resources
A VPN (Virtual Private Network) provides a secure, encrypted tunnel from your computer to UHCL's network when off campus. UHCL offers VPN software to allow authenticated, secure access to many UHCL resources
Standard: Vulnerability Management and Assessment
 Standard: Vulnerability Management and Assessment Page 1 Executive Summary San Jose State University (SJSU) is highly diversified in the information that it collects and maintains on its community members.
Standard: Vulnerability Management and Assessment Page 1 Executive Summary San Jose State University (SJSU) is highly diversified in the information that it collects and maintains on its community members.
Configuration Instructions for non-tcd users of the eduroam service
 Configuration Instructions for non-tcd users of the eduroam service This document contains configuration instructions for visitors to Trinity College Dublin wishing to use the eduroam service. The configuration
Configuration Instructions for non-tcd users of the eduroam service This document contains configuration instructions for visitors to Trinity College Dublin wishing to use the eduroam service. The configuration
Link Layer and Network Layer Security for Wireless Networks
 Link Layer and Network Layer Security for Wireless Networks Interlink Networks, Inc. May 15, 2003 1 LINK LAYER AND NETWORK LAYER SECURITY FOR WIRELESS NETWORKS... 3 Abstract... 3 1. INTRODUCTION... 3 2.
Link Layer and Network Layer Security for Wireless Networks Interlink Networks, Inc. May 15, 2003 1 LINK LAYER AND NETWORK LAYER SECURITY FOR WIRELESS NETWORKS... 3 Abstract... 3 1. INTRODUCTION... 3 2.
Application Note Secure Enterprise Guest Access August 2004
 Application Note Secure Enterprise Guest Access August 2004 Introduction More and more enterprises recognize the need to provide easy, hassle-free high speed internet access to people visiting their offices,
Application Note Secure Enterprise Guest Access August 2004 Introduction More and more enterprises recognize the need to provide easy, hassle-free high speed internet access to people visiting their offices,
Viking VPN Guide Mac OSX RDP Usage
 Viking VPN Guide Mac OSX RDP Usage Table Of Contents 1 : What is RDP 2 : Enabling RDP on your Office PC 3 : Installing the RDP client on your Home Mac 4 : Connecting to your Office PC from your Home Mac
Viking VPN Guide Mac OSX RDP Usage Table Of Contents 1 : What is RDP 2 : Enabling RDP on your Office PC 3 : Installing the RDP client on your Home Mac 4 : Connecting to your Office PC from your Home Mac
ResNet Guide. Information & Learning Services. Here to support your study and research
 ResNet Guide Information & Learning Services Here to support your study and research ResNet Quick Start Guide In order to get you on-line and enjoying the service as quickly and as painlessly as possible,
ResNet Guide Information & Learning Services Here to support your study and research ResNet Quick Start Guide In order to get you on-line and enjoying the service as quickly and as painlessly as possible,
Standard: Patching and Malicious Code Management
 Standard: Patching and Malicious Code Management Page 1 Executive Summary San Jose State University (SJSU) is highly diversified in the information that it collects and maintains on its community members.
Standard: Patching and Malicious Code Management Page 1 Executive Summary San Jose State University (SJSU) is highly diversified in the information that it collects and maintains on its community members.
VPN: Virtual Private Network Setup Instructions
 VPN: Virtual Private Network Setup Instructions Virtual Private Network (VPN): For e-journals and web-based databases, plus applications like EndNote's Online Search (formerly "Connect") and business systems.
VPN: Virtual Private Network Setup Instructions Virtual Private Network (VPN): For e-journals and web-based databases, plus applications like EndNote's Online Search (formerly "Connect") and business systems.
Online Banking Fraud Prevention Recommendations and Best Practices
 Online Banking Fraud Prevention Recommendations and Best Practices This document provides you with fraud prevention best practices that every employee at Continental National Bank of Miami needs to know
Online Banking Fraud Prevention Recommendations and Best Practices This document provides you with fraud prevention best practices that every employee at Continental National Bank of Miami needs to know
Division of Information Technology Lehman College CUNY
 Division of Information Technology Lehman College CUNY Using Lehman s Secure Outgoing (SMTP) Server Updated April 16, 2013 Are you able to receive your Lehman email on your smart phone, laptop or tablet
Division of Information Technology Lehman College CUNY Using Lehman s Secure Outgoing (SMTP) Server Updated April 16, 2013 Are you able to receive your Lehman email on your smart phone, laptop or tablet
Virtual Private Network (VPN)
 Virtual Private Network (VPN) General information regarding VPN-connections, WLAN and VPN-tunnel Please note: Firstly, you have to connect to RUB-WLAN and then sign up with the VPN- Client. In contrast
Virtual Private Network (VPN) General information regarding VPN-connections, WLAN and VPN-tunnel Please note: Firstly, you have to connect to RUB-WLAN and then sign up with the VPN- Client. In contrast
Eduroam wireless network Apple Mac OSX 10.4
 Eduroam wireless network Apple Mac OSX 0.4 How to configure laptop computers to connect to the eduroam wireless network Contents university for the creative arts Contents Introduction Prerequisites Instructions
Eduroam wireless network Apple Mac OSX 0.4 How to configure laptop computers to connect to the eduroam wireless network Contents university for the creative arts Contents Introduction Prerequisites Instructions
Security Policy Revision Date: 23 April 2009
 Security Policy Revision Date: 23 April 2009 Remote Desktop Support Version 3.2.1 or later for Windows Version 3.1.2 or later for Linux and Mac 4 ISL Light Security Policy This section describes the procedure
Security Policy Revision Date: 23 April 2009 Remote Desktop Support Version 3.2.1 or later for Windows Version 3.1.2 or later for Linux and Mac 4 ISL Light Security Policy This section describes the procedure
Law College Computer and Technology Information
 Law College Computer and Technology Information Account Creation All law students, faculty and staff must have a University of Toledo authentication domain (UTAD) computer account. This account will allow
Law College Computer and Technology Information Account Creation All law students, faculty and staff must have a University of Toledo authentication domain (UTAD) computer account. This account will allow
Here s your guide to easy installation. Get the most out of Verizon High Speed Internet.
 Here s your guide to easy installation. Get the most out of Verizon High Speed Internet. Congratulations on choosing Verizon High Speed Internet. In this guide, you ll find everything you need to set up
Here s your guide to easy installation. Get the most out of Verizon High Speed Internet. Congratulations on choosing Verizon High Speed Internet. In this guide, you ll find everything you need to set up
Wi- Fi settings for Windows XP
 Wi- Fi settings for Windows XP On the TU/e there are four Wlan network names or SSID's available. TUE-WPA2 2 The TUE-WPA2 network has WPA2 encryption. This network can be used by both TU/e students and
Wi- Fi settings for Windows XP On the TU/e there are four Wlan network names or SSID's available. TUE-WPA2 2 The TUE-WPA2 network has WPA2 encryption. This network can be used by both TU/e students and
Information Security Office. Logging Standard
 Information Security Office Logging Standard Revision History Revision Revised By Summary of Revisions Section(s) / Date Page(s) Revised 6/01/2013 ISO Initial Release All Approvals Review Date Reviewed
Information Security Office Logging Standard Revision History Revision Revised By Summary of Revisions Section(s) / Date Page(s) Revised 6/01/2013 ISO Initial Release All Approvals Review Date Reviewed
A state-of-the-art solution that brings mobility to SCADA alarms
 A state-of-the-art solution that brings mobility to SCADA alarms SCADA-Aware Mobile far exceeds the capabilities of SMS, e-mail, and pagers, and delivers alarms to the mobile device in the most reliable
A state-of-the-art solution that brings mobility to SCADA alarms SCADA-Aware Mobile far exceeds the capabilities of SMS, e-mail, and pagers, and delivers alarms to the mobile device in the most reliable
WIRELESS SETUP FOR WINDOWS 7
 Computing & Communications WIRELESS SETUP FOR WINDOWS 7 For assistance during the configuration process please call the Computing and Communications Help Desk at 639-2049, avdesk@swgc.mun.ca Who should
Computing & Communications WIRELESS SETUP FOR WINDOWS 7 For assistance during the configuration process please call the Computing and Communications Help Desk at 639-2049, avdesk@swgc.mun.ca Who should
Robust security is a requirement for many companies deploying a wireless network. However, creating a secure wireless network has often been
 Robust security is a requirement for many companies deploying a wireless network. However, creating a secure wireless network has often been difficult and time-consuming. This paper describes the security
Robust security is a requirement for many companies deploying a wireless network. However, creating a secure wireless network has often been difficult and time-consuming. This paper describes the security
Satellite TV and communication: Please contact AsiaWorld-Expo for details of satellite TV and satellite bandwidth connections.
 ADDITIONAL ICT SERVICES FOR WORLD 2006 AsiaWorld-Expo s ICT infrastructure provides exhibitors with a wide range of services from telephony (analogue and IP, broadband and wireless internet services, ISDN
ADDITIONAL ICT SERVICES FOR WORLD 2006 AsiaWorld-Expo s ICT infrastructure provides exhibitors with a wide range of services from telephony (analogue and IP, broadband and wireless internet services, ISDN
XX-XXX Wireless Local Area Network Guidelines. Date: August 13, 2003 Date Adopted by NITC: Other:
 Nebraska Information Technology Commission TECHNICAL STANDARDS AND GUIDELINES Wireless Local Area Network Guidelines Category Title Number Security Architecture Wireless Local Area Network Guidelines Applicability
Nebraska Information Technology Commission TECHNICAL STANDARDS AND GUIDELINES Wireless Local Area Network Guidelines Category Title Number Security Architecture Wireless Local Area Network Guidelines Applicability
Basic Wireless Configuration and Security
 Basic Wireless Configuration and Security This quick start guide provides basic wireless configuration information for the ProSafe Wireless-N 8-Port Gigabit VPN Firewall FVS318N. For information about
Basic Wireless Configuration and Security This quick start guide provides basic wireless configuration information for the ProSafe Wireless-N 8-Port Gigabit VPN Firewall FVS318N. For information about
Controller Management
 Controller Management - Setup & Provisioning - 1 PRONTO SERVICE CONTROLLER (PN-CPP-A-1422) 2 PSC Key Features Fully interoperable with IEEE802.11b/g compliant products External AP support and management
Controller Management - Setup & Provisioning - 1 PRONTO SERVICE CONTROLLER (PN-CPP-A-1422) 2 PSC Key Features Fully interoperable with IEEE802.11b/g compliant products External AP support and management
Setting Up Your Personally- Owned Computer
 Setting Up Your Personally- Owned Computer For use with the Kwansei Gakuin University Computer Network On-Campus Wireless LAN Connection for Windows 10 Revised Date: Jul, 2016 Organization for Information
Setting Up Your Personally- Owned Computer For use with the Kwansei Gakuin University Computer Network On-Campus Wireless LAN Connection for Windows 10 Revised Date: Jul, 2016 Organization for Information
