Concepts Design Basics Command-line MySQL Security Loophole
|
|
|
- Philip Richard
- 10 years ago
- Views:
Transcription
1 Part 2
2 Concepts Design Basics Command-line MySQL Security Loophole
3
4 Databases Flat-file Database stores information in a single table usually adequate for simple collections of information Relational Database suited for large and complex collections of information stores information across multiple related tables
5 Basic Types of Table Relationships 1. one-to-one 2. one-to-many 3. many-to-many
6 Basic Types of Table Relationships 1. one-to-one relationship exists between two tables when a related table contains exactly one record for each record in the primary table (instead of having one BIG table) Suitable when you want to break information into multiple, logical sets Why? You might want to make certain information confidential; thus, separate as another table to limit its access e.g. Employees, Payroll
7 Basic Types of Table Relationships 2. one-to-many relationship exists in a relational database when one record in a primary table has many related records in a related table suitable for eliminating redundant information in a single table. Ideally, only primary and foreign keys are the only pieces of information that should be duplicated. Breaking tables into multiple related tables to reduce redundant information is called normalisation.
8 Basic Types of Table Relationships 2. one-to-many relationship Breaking tables into multiple related tables to reduce redundant information is called normalisation. Normalisation reduces the size of the database and decreases the opportunity for error when the same information is repeated. Let s have a look at an example...
9 STRUCTURE Table: Customers CONTENTS
10 STRUCTURE Table: Products CONTENTS
11 STRUCTURE Table: Purchases CONTENTS
12 Relationship between Tables Create relationships within the database by working with two tables at a time One table in a relationship is always considered to be the primary table, and the other table is considered the related table. Primary Table (or Parent Table) the main table in a relationship that is referenced by another table. Related Table (of Child Table) references a primary table in a relational database
13 Example: Customers - Primary Table Primary key Foreign key Purchases - Related Table
14 Basic Types of Table Relationships 3. many-to-many relationship Exists in a relational database when many records in one table are related to many records in another table You must use a junction table to create a manyto-many relationship Junction table (or linking/cross-reference table) Creates a one-to-many relationship for each of the tables in a many-to-many relationship Let s have a look at an example...
15 Basic Types of Table Relationships 3. many-to-many relationship Junction table (or linking/cross-reference table) Creates a one-to-many relationship for each of the tables in a many-to-many relationship Employee_id firstname lastname Employee_id language 101 dug Dog 102 kevin Bird 101 English 101 Tagalog 101 Spanish One-to-many relationship Not normalised because the language field contains duplicate values We could use many-to-many relationship here instead 102 Spanish 102 English
16 Basic Types of Table Relationships 3. many-to-many relationship Junction table (or linking/cross-reference table) Employee_id firstname lastname Language_id language 101 dug Dog 102 kevin Bird Employee_id Language_id Proficiency level 101 English Tagalog Spanish Spanish English 8 10 English 11 Tagalog 12 Spanish 13 French 14 Finnish 15 Korean One-to-many relationship
17 Relational Database Example Read a customer record, and then show the products purchased by that customer. Tables Remember the database example we used in the previous lecture? Customers Products Purchases PurchaseProducts Example15-14.php
18 STRUCTURE Table: PurchaseProducts (data) CONTENTS
19 Database Design Cost at the time of purchase
20
21 Logging in to MySQL mysql -h host -u user -p
22 Show available databases An SQL command ends with a semicolon;
23 SQL Commands When you enter an SQL command at the mysql> command prompt you must terminate the command with a semicolon. the SQL keywords you enter in a MySQL monitor are not casesensitive. However, the case-sensitivity of database and table identifiers depends on your operating system. Convention: although you can use any case for SQL keywords, follow the convention of using uppercase letters for SQL keywords and using lowercase or mixed case for the names of databases, tables, and fields.
24 Creating a database Creates a folder for the database To use the newly created database Returns the currently active database
25 Show available databases
26 Creating a table CREATE TABLE table_name (column_name TYPE,...); Creates a table named vehicles Display table structure
27 Altering a table ALTER TABLE table_name ADD [COLUMN] (column_name TYPE,...); Add a new field to the table Display table structure To delete a Table: DROP TABLE table_name;
28 Creating user accounts GRANT privilege[,privilege] ON database_name.* TO IDENTIFIED BY "somepassword"; Create an account named dug Logging-in ALL - all privileges database_name.* - any table in the database username@"%" any host "somepassword user password
29 Common MySQL privileges Privilege ALL ALTER CREATE DELETE DROP INDEX INSERT SELECT UPDATE USAGE Description Assign All privileges to the user Allow to modify the table structure All to create databases, tables, and indices Allow to delete records Allow to delete databases and tables Allow to create and delete indexes Allow to add records Allow to select records Allow to modify records Create user with no privileges
30 Deleting a database DROP DATABASE database_name; Delete the vehicle_fleet database
31 Commands help;? Command descriptions exit quit log-out of MySQL monitor
32
33
34 SQL Injection It makes perfect sense to make use of a proper database to manage a growing user population and user authentication. However, we need to be aware of a loop hole that makes our application vulnerable to security breach. Let s have a look at an example...
35 Database name: users Consider the following database example: Database Name: users, containing only one Table named users. Table users is defined with only 3 fields, as shown below: STRUCTURE Primary key
36 Database name: users for this example we have only one table named users CONTENTS Users and their passwords
37 SQL Injection-prone script! <?php $strusername = " ' OR '0 "; $strpassword = ''; An attacker could use the following combination $dblocalhost = mysql_connect("localhost", "root", "") or die("could not connect: ". mysql_error()); mysql_select_db("users", $dblocalhost) or die("could not find database: ". mysql_error()); $dbrecords = mysql_query("select * FROM users WHERE username= '$strusername' "); $intcount = mysql_num_rows($dbrecords ); echo "<p>count: ". $intcount. "</p>"; $arrrecords = mysql_fetch_array($dbrecords); echo $arrrecords["password"]; if ($strpassword!= $arrrecords["password"]) echo "<p>invalid Password/UserName</p>"; else echo "<p>password and UserName match!</p>";?> sqlinjection_prone2.php
38 SQL Injection-prone script! <?php $strusername = " ' OR '0 "; $strpassword = ' ';... mysql_query("select * FROM users WHERE username= '$strusername' "); After substitution of values, the statement becomes: mysql_query("select * FROM users WHERE username= ' ' OR '0 ' "); This statement will force the query not to return any records, and as the password is set to NULL, the if statements comparing the passwords evaluates to true. Therefore, the script thinks that the username and password matches. sqlinjection_prone2.php
39 <?php $strusername = "' OR '0"; $strpassword = ''; SQL Injection-safe script! $dblocalhost = mysql_connect("localhost", "root", " ) or die("could not connect: ". mysql_error()); mysql_select_db("users", $dblocalhost) or die("could not find database: ". mysql_error()); $strusername = mysql_real_escape_string($strusername); $dbrecords = mysql_query("select * FROM users WHERE username='$strusername'"); $arrrecords = mysql_fetch_array($dbrecords); if (mysql_num_rows($dbrecords)!= 1) echo "<p>username not found!</p>"; else { if ($strpassword!= $arrrecords["password"]) echo "<p>invalid Password/UserName</p>"; else echo "<p>password and UserName match!</p>"; }?> sqlinjection_secure.php
40 SQL Injection-safe script! <?php $strusername = " ' OR '0 "; $strpassword = ' ';... $strusername = mysql_real_escape_string($strusername); mysql_query("select * FROM users WHERE username= '$strusername' "); After substitution of values, the statement becomes: mysql_query("select * FROM users WHERE username= ' \' OR \'0 ' "); The mysql_real_escape_string function escapes quotation characters in the SQL string removing the danger of the quotes being Interpreted incorrectly by the SQL parser. In addition, it is important to count the number of records returned using mysql_num_rows() as another security measure. sqlinjection_secure.php
41
42 Database name: users Consider creating a database named users, containing only one Table named users. Table users is defined with only 3 fields, as shown below: STRUCTURE Apply MD5() function
A Brief Introduction to MySQL
 A Brief Introduction to MySQL by Derek Schuurman Introduction to Databases A database is a structured collection of logically related data. One common type of database is the relational database, a term
A Brief Introduction to MySQL by Derek Schuurman Introduction to Databases A database is a structured collection of logically related data. One common type of database is the relational database, a term
A table is a collection of related data entries and it consists of columns and rows.
 CST 250 MySQL Notes (Source: www.w3schools.com) MySQL is the most popular open-source database system. What is MySQL? MySQL is a database. The data in MySQL is stored in database objects called tables.
CST 250 MySQL Notes (Source: www.w3schools.com) MySQL is the most popular open-source database system. What is MySQL? MySQL is a database. The data in MySQL is stored in database objects called tables.
A basic create statement for a simple student table would look like the following.
 Creating Tables A basic create statement for a simple student table would look like the following. create table Student (SID varchar(10), FirstName varchar(30), LastName varchar(30), EmailAddress varchar(30));
Creating Tables A basic create statement for a simple student table would look like the following. create table Student (SID varchar(10), FirstName varchar(30), LastName varchar(30), EmailAddress varchar(30));
Retrieving Data Using the SQL SELECT Statement. Copyright 2006, Oracle. All rights reserved.
 Retrieving Data Using the SQL SELECT Statement Objectives After completing this lesson, you should be able to do the following: List the capabilities of SQL SELECT statements Execute a basic SELECT statement
Retrieving Data Using the SQL SELECT Statement Objectives After completing this lesson, you should be able to do the following: List the capabilities of SQL SELECT statements Execute a basic SELECT statement
A SQL Injection : Internal Investigation of Injection, Detection and Prevention of SQL Injection Attacks
 A SQL Injection : Internal Investigation of Injection, Detection and Prevention of SQL Injection Attacks Abhay K. Kolhe Faculty, Dept. Of Computer Engineering MPSTME, NMIMS Mumbai, India Pratik Adhikari
A SQL Injection : Internal Investigation of Injection, Detection and Prevention of SQL Injection Attacks Abhay K. Kolhe Faculty, Dept. Of Computer Engineering MPSTME, NMIMS Mumbai, India Pratik Adhikari
Tutorial on Relational Database Design
 Tutorial on Relational Database Design Introduction Relational database was proposed by Edgar Codd (of IBM Research) around 1969. It has since become the dominant database model for commercial applications
Tutorial on Relational Database Design Introduction Relational database was proposed by Edgar Codd (of IBM Research) around 1969. It has since become the dominant database model for commercial applications
SQL Injection January 23, 2013
 Web-based Attack: SQL Injection SQL Injection January 23, 2013 Authored By: Stephanie Reetz, SOC Analyst Contents Introduction Introduction...1 Web applications are everywhere on the Internet. Almost Overview...2
Web-based Attack: SQL Injection SQL Injection January 23, 2013 Authored By: Stephanie Reetz, SOC Analyst Contents Introduction Introduction...1 Web applications are everywhere on the Internet. Almost Overview...2
Introduction to Computing. Lectured by: Dr. Pham Tran Vu [email protected]
 Introduction to Computing Lectured by: Dr. Pham Tran Vu [email protected] Databases The Hierarchy of Data Keys and Attributes The Traditional Approach To Data Management Database A collection of
Introduction to Computing Lectured by: Dr. Pham Tran Vu [email protected] Databases The Hierarchy of Data Keys and Attributes The Traditional Approach To Data Management Database A collection of
Once the schema has been designed, it can be implemented in the RDBMS.
 2. Creating a database Designing the database schema... 1 Representing Classes, Attributes and Objects... 2 Data types... 5 Additional constraints... 6 Choosing the right fields... 7 Implementing a table
2. Creating a database Designing the database schema... 1 Representing Classes, Attributes and Objects... 2 Data types... 5 Additional constraints... 6 Choosing the right fields... 7 Implementing a table
SQL Injection. SQL Injection. CSCI 4971 Secure Software Principles. Rensselaer Polytechnic Institute. Spring 2010 ...
 SQL Injection CSCI 4971 Secure Software Principles Rensselaer Polytechnic Institute Spring 2010 A Beginner s Example A hypothetical web application $result = mysql_query(
SQL Injection CSCI 4971 Secure Software Principles Rensselaer Polytechnic Institute Spring 2010 A Beginner s Example A hypothetical web application $result = mysql_query(
Teach Yourself InterBase
 Teach Yourself InterBase This tutorial takes you step-by-step through the process of creating and using a database using the InterBase Windows ISQL dialog. You learn to create data structures that enforce
Teach Yourself InterBase This tutorial takes you step-by-step through the process of creating and using a database using the InterBase Windows ISQL dialog. You learn to create data structures that enforce
Serious Threat. Targets for Attack. Characterization of Attack. SQL Injection 4/9/2010 COMP620 1. On August 17, 2009, the United States Justice
 Serious Threat SQL Injection COMP620 On August 17, 2009, the United States Justice Department tcharged an American citizen Albert Gonzalez and two unnamed Russians with the theft of 130 million credit
Serious Threat SQL Injection COMP620 On August 17, 2009, the United States Justice Department tcharged an American citizen Albert Gonzalez and two unnamed Russians with the theft of 130 million credit
Database 10g Edition: All possible 10g features, either bundled or available at additional cost.
 Concepts Oracle Corporation offers a wide variety of products. The Oracle Database 10g, the product this exam focuses on, is the centerpiece of the Oracle product set. The "g" in "10g" stands for the Grid
Concepts Oracle Corporation offers a wide variety of products. The Oracle Database 10g, the product this exam focuses on, is the centerpiece of the Oracle product set. The "g" in "10g" stands for the Grid
SQL Injection Vulnerabilities in Desktop Applications
 Vulnerabilities in Desktop Applications Derek Ditch (lead) Dylan McDonald Justin Miller Missouri University of Science & Technology Computer Science Department April 29, 2008 Vulnerabilities in Desktop
Vulnerabilities in Desktop Applications Derek Ditch (lead) Dylan McDonald Justin Miller Missouri University of Science & Technology Computer Science Department April 29, 2008 Vulnerabilities in Desktop
SQL Injection for newbie
 SQL Injection for newbie SQL injection is a security vulnerability that occurs in a database layer of an application. It is technique to inject SQL query/command as an input via web pages. Sometimes we
SQL Injection for newbie SQL injection is a security vulnerability that occurs in a database layer of an application. It is technique to inject SQL query/command as an input via web pages. Sometimes we
Information and Computer Science Department ICS 324 Database Systems Lab#11 SQL-Basic Query
 Information and Computer Science Department ICS 324 Database Systems Lab#11 SQL-Basic Query Objectives The objective of this lab is to learn the query language of SQL. Outcomes After completing this Lab,
Information and Computer Science Department ICS 324 Database Systems Lab#11 SQL-Basic Query Objectives The objective of this lab is to learn the query language of SQL. Outcomes After completing this Lab,
How to Copy A SQL Database SQL Server Express (Making a History Company)
 How to Copy A SQL Database SQL Server Express (Making a History Company) These instructions are written for use with SQL Server Express. Check with your Network Administrator if you are not sure if you
How to Copy A SQL Database SQL Server Express (Making a History Company) These instructions are written for use with SQL Server Express. Check with your Network Administrator if you are not sure if you
SQL. Short introduction
 SQL Short introduction 1 Overview SQL, which stands for Structured Query Language, is used to communicate with a database. Through SQL one can create, manipulate, query and delete tables and contents.
SQL Short introduction 1 Overview SQL, which stands for Structured Query Language, is used to communicate with a database. Through SQL one can create, manipulate, query and delete tables and contents.
SQL INJECTION ATTACKS By Zelinski Radu, Technical University of Moldova
 SQL INJECTION ATTACKS By Zelinski Radu, Technical University of Moldova Where someone is building a Web application, often he need to use databases to store information, or to manage user accounts. And
SQL INJECTION ATTACKS By Zelinski Radu, Technical University of Moldova Where someone is building a Web application, often he need to use databases to store information, or to manage user accounts. And
SQL Injection. The ability to inject SQL commands into the database engine through an existing application
 SQL Injection The ability to inject SQL commands into the database engine through an existing application 1 What is SQL? SQL stands for Structured Query Language Allows us to access a database ANSI and
SQL Injection The ability to inject SQL commands into the database engine through an existing application 1 What is SQL? SQL stands for Structured Query Language Allows us to access a database ANSI and
USING MYWEBSQL FIGURE 1: FIRST AUTHENTICATION LAYER (ENTER YOUR REGULAR SIMMONS USERNAME AND PASSWORD)
 USING MYWEBSQL MyWebSQL is a database web administration tool that will be used during LIS 458 & CS 333. This document will provide the basic steps for you to become familiar with the application. 1. To
USING MYWEBSQL MyWebSQL is a database web administration tool that will be used during LIS 458 & CS 333. This document will provide the basic steps for you to become familiar with the application. 1. To
Database Setup. Coding, Understanding, & Executing the SQL Database Creation Script
 Overview @author R.L. Martinez, Ph.D. We need a database to perform the data-related work in the subsequent tutorials. Begin by creating the falconnight database in phpmyadmin using the SQL script below.
Overview @author R.L. Martinez, Ph.D. We need a database to perform the data-related work in the subsequent tutorials. Begin by creating the falconnight database in phpmyadmin using the SQL script below.
Server side scripting and databases
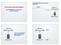 Three components used in typical web application Server side scripting and databases How Web Applications interact with server side databases Browser Web server Database server Web server Web server Apache
Three components used in typical web application Server side scripting and databases How Web Applications interact with server side databases Browser Web server Database server Web server Web server Apache
Database Security. Principle of Least Privilege. DBMS Security. IT420: Database Management and Organization. Database Security.
 Database Security Rights Enforced IT420: Database Management and Organization Database Security Textbook: Ch 9, pg 309-314 PHP and MySQL: Ch 9, pg 217-227 Database security - only authorized users can
Database Security Rights Enforced IT420: Database Management and Organization Database Security Textbook: Ch 9, pg 309-314 PHP and MySQL: Ch 9, pg 217-227 Database security - only authorized users can
Learning MySQL! Angola Africa 1246700 20609294 100990000000. SELECT name, gdp/population FROM world WHERE area > 50000000!
 Learning MySQL http://sqlzoo.net/wiki/select_basics Angola Africa 1246700 20609294 100990000000 1) Single quotes SELECT population FROM world WHERE name = Germany 2) Division SELECT name, gdp/population
Learning MySQL http://sqlzoo.net/wiki/select_basics Angola Africa 1246700 20609294 100990000000 1) Single quotes SELECT population FROM world WHERE name = Germany 2) Division SELECT name, gdp/population
SQL - QUICK GUIDE. Allows users to access data in relational database management systems.
 http://www.tutorialspoint.com/sql/sql-quick-guide.htm SQL - QUICK GUIDE Copyright tutorialspoint.com What is SQL? SQL is Structured Query Language, which is a computer language for storing, manipulating
http://www.tutorialspoint.com/sql/sql-quick-guide.htm SQL - QUICK GUIDE Copyright tutorialspoint.com What is SQL? SQL is Structured Query Language, which is a computer language for storing, manipulating
Webapps Vulnerability Report
 Tuesday, May 1, 2012 Webapps Vulnerability Report Introduction This report provides detailed information of every vulnerability that was found and successfully exploited by CORE Impact Professional during
Tuesday, May 1, 2012 Webapps Vulnerability Report Introduction This report provides detailed information of every vulnerability that was found and successfully exploited by CORE Impact Professional during
SQL Injection. Sajjad Pourali [email protected] CERT of Ferdowsi University of Mashhad
 SQL Injection Sajjad Pourali [email protected] CERT of Ferdowsi University of Mashhad SQL Injection Ability to inject SQL commands into the database engine Flaw in web application, not the DB or web
SQL Injection Sajjad Pourali [email protected] CERT of Ferdowsi University of Mashhad SQL Injection Ability to inject SQL commands into the database engine Flaw in web application, not the DB or web
Zend Framework Database Access
 Zend Framework Database Access Bill Karwin Copyright 2007, Zend Technologies Inc. Introduction What s in the Zend_Db component? Examples of using each class Using Zend_Db in MVC applications Zend Framework
Zend Framework Database Access Bill Karwin Copyright 2007, Zend Technologies Inc. Introduction What s in the Zend_Db component? Examples of using each class Using Zend_Db in MVC applications Zend Framework
Advanced PostgreSQL SQL Injection and Filter Bypass Techniques
 Advanced PostgreSQL SQL Injection and Filter Bypass Techniques INFIGO-TD TD-200 2009-04 2009-06 06-17 Leon Juranić [email protected] INFIGO IS. All rights reserved. This document contains information
Advanced PostgreSQL SQL Injection and Filter Bypass Techniques INFIGO-TD TD-200 2009-04 2009-06 06-17 Leon Juranić [email protected] INFIGO IS. All rights reserved. This document contains information
MYSQL DATABASE ACCESS WITH PHP
 MYSQL DATABASE ACCESS WITH PHP Fall 2009 CSCI 2910 Server Side Web Programming Typical web application interaction Database Server 3 tiered architecture Security in this interaction is critical Web Server
MYSQL DATABASE ACCESS WITH PHP Fall 2009 CSCI 2910 Server Side Web Programming Typical web application interaction Database Server 3 tiered architecture Security in this interaction is critical Web Server
Oracle Database 10g Express
 Oracle Database 10g Express This tutorial prepares the Oracle Database 10g Express Edition Developer to perform common development and administrative tasks of Oracle Database 10g Express Edition. Objectives
Oracle Database 10g Express This tutorial prepares the Oracle Database 10g Express Edition Developer to perform common development and administrative tasks of Oracle Database 10g Express Edition. Objectives
Database Administration with MySQL
 Database Administration with MySQL Suitable For: Database administrators and system administrators who need to manage MySQL based services. Prerequisites: Practical knowledge of SQL Some knowledge of relational
Database Administration with MySQL Suitable For: Database administrators and system administrators who need to manage MySQL based services. Prerequisites: Practical knowledge of SQL Some knowledge of relational
Understanding Sql Injection
 Understanding Sql Injection Hardik Shah Understanding SQL Injection Introduction: SQL injection is a technique used by a malicious user to gain illegal access on the remote machines through the web applications
Understanding Sql Injection Hardik Shah Understanding SQL Injection Introduction: SQL injection is a technique used by a malicious user to gain illegal access on the remote machines through the web applications
Mul$media im Netz (Online Mul$media) Wintersemester 2014/15. Übung 03 (Nebenfach)
 Mul$media im Netz (Online Mul$media) Wintersemester 2014/15 Übung 03 (Nebenfach) Online Mul?media WS 2014/15 - Übung 3-1 Databases and SQL Data can be stored permanently in databases There are a number
Mul$media im Netz (Online Mul$media) Wintersemester 2014/15 Übung 03 (Nebenfach) Online Mul?media WS 2014/15 - Übung 3-1 Databases and SQL Data can be stored permanently in databases There are a number
Magento Security and Vulnerabilities. Roman Stepanov
 Magento Security and Vulnerabilities Roman Stepanov http://ice.eltrino.com/ Table of contents Introduction Open Web Application Security Project OWASP TOP 10 List Common issues in Magento A1 Injection
Magento Security and Vulnerabilities Roman Stepanov http://ice.eltrino.com/ Table of contents Introduction Open Web Application Security Project OWASP TOP 10 List Common issues in Magento A1 Injection
P_Id LastName FirstName Address City 1 Kumari Mounitha VPura Bangalore 2 Kumar Pranav Yelhanka Bangalore 3 Gubbi Sharan Hebbal Tumkur
 SQL is a standard language for accessing and manipulating databases. What is SQL? SQL stands for Structured Query Language SQL lets you access and manipulate databases SQL is an ANSI (American National
SQL is a standard language for accessing and manipulating databases. What is SQL? SQL stands for Structured Query Language SQL lets you access and manipulate databases SQL is an ANSI (American National
IT360: Applied Database Systems. Database Security. Kroenke: Ch 9, pg 309-314 PHP and MySQL: Ch 9, pg 217-227
 IT360: Applied Database Systems Database Security Kroenke: Ch 9, pg 309-314 PHP and MySQL: Ch 9, pg 217-227 1 Database Security Rights Enforced Database security - only authorized users can perform authorized
IT360: Applied Database Systems Database Security Kroenke: Ch 9, pg 309-314 PHP and MySQL: Ch 9, pg 217-227 1 Database Security Rights Enforced Database security - only authorized users can perform authorized
Database Design Basics
 Database Design Basics Table of Contents SOME DATABASE TERMS TO KNOW... 1 WHAT IS GOOD DATABASE DESIGN?... 2 THE DESIGN PROCESS... 2 DETERMINING THE PURPOSE OF YOUR DATABASE... 3 FINDING AND ORGANIZING
Database Design Basics Table of Contents SOME DATABASE TERMS TO KNOW... 1 WHAT IS GOOD DATABASE DESIGN?... 2 THE DESIGN PROCESS... 2 DETERMINING THE PURPOSE OF YOUR DATABASE... 3 FINDING AND ORGANIZING
WebCruiser Web Vulnerability Scanner User Guide
 WebCruiser Web Vulnerability Scanner User Guide Content 1. Software Introduction...2 2. Key Features...3 2.1. POST Data Resend...3 2.2. Vulnerability Scanner...6 2.3. SQL Injection...8 2.3.1. POST SQL
WebCruiser Web Vulnerability Scanner User Guide Content 1. Software Introduction...2 2. Key Features...3 2.1. POST Data Resend...3 2.2. Vulnerability Scanner...6 2.3. SQL Injection...8 2.3.1. POST SQL
CS 2316 Data Manipulation for Engineers
 CS 2316 Data Manipulation for Engineers SQL Christopher Simpkins [email protected] Chris Simpkins (Georgia Tech) CS 2316 Data Manipulation for Engineers SQL 1 / 26 1 1 The material in this lecture
CS 2316 Data Manipulation for Engineers SQL Christopher Simpkins [email protected] Chris Simpkins (Georgia Tech) CS 2316 Data Manipulation for Engineers SQL 1 / 26 1 1 The material in this lecture
AUTHENTICATION... 2 Step 1:Set up your LDAP server... 2 Step 2: Set up your username... 4 WRITEBACK REPORT... 8 Step 1: Table structures...
 AUTHENTICATION... 2 Step 1:Set up your LDAP server... 2 Step 2: Set up your username... 4 WRITEBACK REPORT... 8 Step 1: Table structures... 8 Step 2: Import Tables into BI Admin.... 9 Step 3: Creating
AUTHENTICATION... 2 Step 1:Set up your LDAP server... 2 Step 2: Set up your username... 4 WRITEBACK REPORT... 8 Step 1: Table structures... 8 Step 2: Import Tables into BI Admin.... 9 Step 3: Creating
PHP/MySQL SQL Injections: Understanding MySQL Union Poisoining. Jason A. Medeiros :: CEO :: Presented for DC619 All Content Grayscale Research 2008
 PHP/MySQL SQL Injections: Understanding MySQL Union Poisoining Jason A. Medeiros :: CEO :: Presented for DC619 All Content Grayscale Research 2008 Typical MySQL Deployment Most MySQL deployments sit on
PHP/MySQL SQL Injections: Understanding MySQL Union Poisoining Jason A. Medeiros :: CEO :: Presented for DC619 All Content Grayscale Research 2008 Typical MySQL Deployment Most MySQL deployments sit on
Criteria for web application security check. Version 2015.1
 Criteria for web application security check Version 2015.1 i Content Introduction... iii ISC- P- 001 ISC- P- 001.1 ISC- P- 001.2 ISC- P- 001.3 ISC- P- 001.4 ISC- P- 001.5 ISC- P- 001.6 ISC- P- 001.7 ISC-
Criteria for web application security check Version 2015.1 i Content Introduction... iii ISC- P- 001 ISC- P- 001.1 ISC- P- 001.2 ISC- P- 001.3 ISC- P- 001.4 ISC- P- 001.5 ISC- P- 001.6 ISC- P- 001.7 ISC-
Microsoft Access 2007 Module 1
 Microsoft Access 007 Module http://pds.hccfl.edu/pds Microsoft Access 007: Module August 007 007 Hillsborough Community College - Professional Development and Web Services Hillsborough Community College
Microsoft Access 007 Module http://pds.hccfl.edu/pds Microsoft Access 007: Module August 007 007 Hillsborough Community College - Professional Development and Web Services Hillsborough Community College
VIDEO intypedia007en LESSON 7: WEB APPLICATION SECURITY - INTRODUCTION TO SQL INJECTION TECHNIQUES. AUTHOR: Chema Alonso
 VIDEO intypedia007en LESSON 7: WEB APPLICATION SECURITY - INTRODUCTION TO SQL INJECTION TECHNIQUES AUTHOR: Chema Alonso Informática 64. Microsoft MVP Enterprise Security Hello and welcome to Intypedia.
VIDEO intypedia007en LESSON 7: WEB APPLICATION SECURITY - INTRODUCTION TO SQL INJECTION TECHNIQUES AUTHOR: Chema Alonso Informática 64. Microsoft MVP Enterprise Security Hello and welcome to Intypedia.
SQL Injection. Blossom Hands-on exercises for computer forensics and security
 Copyright: The development of this document is funded by Higher Education of Academy. Permission is granted to copy, distribute and /or modify this document under a license compliant with the Creative
Copyright: The development of this document is funded by Higher Education of Academy. Permission is granted to copy, distribute and /or modify this document under a license compliant with the Creative
Microsoft Access 2003 Module 1
 Microsoft Access 003 Module http://pds.hccfl.edu/pds Microsoft Access 003: Module June 005 006 Hillsborough Community College - Professional Development Services Hillsborough Community College - Professional
Microsoft Access 003 Module http://pds.hccfl.edu/pds Microsoft Access 003: Module June 005 006 Hillsborough Community College - Professional Development Services Hillsborough Community College - Professional
- Eliminating redundant data - Ensuring data dependencies makes sense. ie:- data is stored logically
 Normalization of databases Database normalization is a technique of organizing the data in the database. Normalization is a systematic approach of decomposing tables to eliminate data redundancy and undesirable
Normalization of databases Database normalization is a technique of organizing the data in the database. Normalization is a systematic approach of decomposing tables to eliminate data redundancy and undesirable
2874CD1EssentialSQL.qxd 6/25/01 3:06 PM Page 1 Essential SQL Copyright 2001 SYBEX, Inc., Alameda, CA www.sybex.com
 Essential SQL 2 Essential SQL This bonus chapter is provided with Mastering Delphi 6. It is a basic introduction to SQL to accompany Chapter 14, Client/Server Programming. RDBMS packages are generally
Essential SQL 2 Essential SQL This bonus chapter is provided with Mastering Delphi 6. It is a basic introduction to SQL to accompany Chapter 14, Client/Server Programming. RDBMS packages are generally
CSCE 156H/RAIK 184H Assignment 4 - Project Phase III Database Design
 CSCE 156H/RAIK 184H Assignment 4 - Project Phase III Database Design Dr. Chris Bourke Spring 2016 1 Introduction In the previous phase of this project, you built an application framework that modeled the
CSCE 156H/RAIK 184H Assignment 4 - Project Phase III Database Design Dr. Chris Bourke Spring 2016 1 Introduction In the previous phase of this project, you built an application framework that modeled the
Maintaining Stored Procedures in Database Application
 Maintaining Stored Procedures in Database Application Santosh Kakade 1, Rohan Thakare 2, Bhushan Sapare 3, Dr. B.B. Meshram 4 Computer Department VJTI, Mumbai 1,2,3. Head of Computer Department VJTI, Mumbai
Maintaining Stored Procedures in Database Application Santosh Kakade 1, Rohan Thakare 2, Bhushan Sapare 3, Dr. B.B. Meshram 4 Computer Department VJTI, Mumbai 1,2,3. Head of Computer Department VJTI, Mumbai
Guarding Against SQL Server Attacks: Hacking, cracking, and protection techniques.
 Guarding Against SQL Server Attacks: Hacking, cracking, and protection techniques. In this information age, the data server has become the heart of a company. This one piece of software controls the rhythm
Guarding Against SQL Server Attacks: Hacking, cracking, and protection techniques. In this information age, the data server has become the heart of a company. This one piece of software controls the rhythm
Access Part 2 - Design
 Access Part 2 - Design The Database Design Process It is important to remember that creating a database is an iterative process. After the database is created and you and others begin to use it there will
Access Part 2 - Design The Database Design Process It is important to remember that creating a database is an iterative process. After the database is created and you and others begin to use it there will
B.1 Database Design and Definition
 Appendix B Database Design B.1 Database Design and Definition Throughout the SQL chapter we connected to and queried the IMDB database. This database was set up by IMDB and available for us to use. But
Appendix B Database Design B.1 Database Design and Definition Throughout the SQL chapter we connected to and queried the IMDB database. This database was set up by IMDB and available for us to use. But
Integrated Network Vulnerability Scanning & Penetration Testing SAINTcorporation.com
 SAINT Integrated Network Vulnerability Scanning and Penetration Testing www.saintcorporation.com Introduction While network vulnerability scanning is an important tool in proactive network security, penetration
SAINT Integrated Network Vulnerability Scanning and Penetration Testing www.saintcorporation.com Introduction While network vulnerability scanning is an important tool in proactive network security, penetration
Connecting to a Database Using PHP. Prof. Jim Whitehead CMPS 183, Spring 2006 May 15, 2006
 Connecting to a Database Using PHP Prof. Jim Whitehead CMPS 183, Spring 2006 May 15, 2006 Rationale Most Web applications: Retrieve information from a database to alter their on-screen display Store user
Connecting to a Database Using PHP Prof. Jim Whitehead CMPS 183, Spring 2006 May 15, 2006 Rationale Most Web applications: Retrieve information from a database to alter their on-screen display Store user
Relational Databases. Christopher Simpkins [email protected]
 Relational Databases Christopher Simpkins [email protected] Relational Databases A relational database is a collection of data stored in one or more tables A relational database management system
Relational Databases Christopher Simpkins [email protected] Relational Databases A relational database is a collection of data stored in one or more tables A relational database management system
Advanced Web Technology 10) XSS, CSRF and SQL Injection 2
 Berner Fachhochschule, Technik und Informatik Advanced Web Technology 10) XSS, CSRF and SQL Injection Dr. E. Benoist Fall Semester 2010/2011 Table of Contents Cross Site Request Forgery - CSRF Presentation
Berner Fachhochschule, Technik und Informatik Advanced Web Technology 10) XSS, CSRF and SQL Injection Dr. E. Benoist Fall Semester 2010/2011 Table of Contents Cross Site Request Forgery - CSRF Presentation
1. What is SQL Injection?
 SQL Injection 1. What is SQL Injection?...2 2. Forms of vulnerability...3 2.1. Incorrectly filtered escape characters...3 2.2. Incorrect type handling...3 2.3. Vulnerabilities inside the database server...4
SQL Injection 1. What is SQL Injection?...2 2. Forms of vulnerability...3 2.1. Incorrectly filtered escape characters...3 2.2. Incorrect type handling...3 2.3. Vulnerabilities inside the database server...4
- Suresh Khanal. http://mcqsets.com. http://www.psexam.com Microsoft Excel Short Questions and Answers 1
 - Suresh Khanal http://mcqsets.com http://www.psexam.com Microsoft Excel Short Questions and Answers 1 Microsoft Access Short Questions and Answers with Illustrations Part I Suresh Khanal Kalanki, Kathmandu
- Suresh Khanal http://mcqsets.com http://www.psexam.com Microsoft Excel Short Questions and Answers 1 Microsoft Access Short Questions and Answers with Illustrations Part I Suresh Khanal Kalanki, Kathmandu
Automated vulnerability scanning and exploitation
 Automated vulnerability scanning and exploitation Dennis Pellikaan Thijs Houtenbos University of Amsterdam System and Network Engineering July 4, 2013 Dennis Pellikaan, Thijs Houtenbos Automated vulnerability
Automated vulnerability scanning and exploitation Dennis Pellikaan Thijs Houtenbos University of Amsterdam System and Network Engineering July 4, 2013 Dennis Pellikaan, Thijs Houtenbos Automated vulnerability
 Database design 1 The Database Design Process: Before you build the tables and other objects that will make up your system, it is important to take time to design it. A good design is the keystone to creating
Database design 1 The Database Design Process: Before you build the tables and other objects that will make up your system, it is important to take time to design it. A good design is the keystone to creating
Physical Database Design Process. Physical Database Design Process. Major Inputs to Physical Database. Components of Physical Database Design
 Physical Database Design Process Physical Database Design Process The last stage of the database design process. A process of mapping the logical database structure developed in previous stages into internal
Physical Database Design Process Physical Database Design Process The last stage of the database design process. A process of mapping the logical database structure developed in previous stages into internal
Intro to Databases. ACM Webmonkeys 2011
 Intro to Databases ACM Webmonkeys 2011 Motivation Computer programs that deal with the real world often need to store a large amount of data. E.g.: Weather in US cities by month for the past 10 years List
Intro to Databases ACM Webmonkeys 2011 Motivation Computer programs that deal with the real world often need to store a large amount of data. E.g.: Weather in US cities by month for the past 10 years List
SQL 2: GETTING INFORMATION INTO A DATABASE. MIS2502 Data Analytics
 SQL 2: GETTING INFORMATION INTO A DATABASE MIS2502 Data Analytics Our relational database A series of tables Linked together through primary/foreign key relationships To create a database We need to define
SQL 2: GETTING INFORMATION INTO A DATABASE MIS2502 Data Analytics Our relational database A series of tables Linked together through primary/foreign key relationships To create a database We need to define
SQL Injection. By Artem Kazanstev, ITSO and Alex Beutel, Student
 SQL Injection By Artem Kazanstev, ITSO and Alex Beutel, Student SANS Priority No 2 As of September 2009, Web application vulnerabilities such as SQL injection and Cross-Site Scripting flaws in open-source
SQL Injection By Artem Kazanstev, ITSO and Alex Beutel, Student SANS Priority No 2 As of September 2009, Web application vulnerabilities such as SQL injection and Cross-Site Scripting flaws in open-source
iw Document Manager Cabinet Converter User s Guide
 iw Document Manager Cabinet Converter User s Guide Contents Contents.................................................................... 1 Abbreviations Used in This Guide................................................
iw Document Manager Cabinet Converter User s Guide Contents Contents.................................................................... 1 Abbreviations Used in This Guide................................................
Application note: SQL@CHIP Connecting the IPC@CHIP to a Database
 Application note: SQL@CHIP Connecting the IPC@CHIP to a Database 1. Introduction This application note describes how to connect an IPC@CHIP to a database and exchange data between those. As there are no
Application note: SQL@CHIP Connecting the IPC@CHIP to a Database 1. Introduction This application note describes how to connect an IPC@CHIP to a database and exchange data between those. As there are no
SQL Injection Are Your Web Applications Vulnerable?
 SQL Injection Are Your Web Applications Vulnerable? A White Paper from SPI Dynamics Author: Kevin Spett Page 1 TABLE OF CONTENTS 1. OVERVIEW AND INTRODUCTION TO WEB APPLICATIONS AND SQL INJECTION3 1.1.
SQL Injection Are Your Web Applications Vulnerable? A White Paper from SPI Dynamics Author: Kevin Spett Page 1 TABLE OF CONTENTS 1. OVERVIEW AND INTRODUCTION TO WEB APPLICATIONS AND SQL INJECTION3 1.1.
Oracle 10g PL/SQL Training
 Oracle 10g PL/SQL Training Course Number: ORCL PS01 Length: 3 Day(s) Certification Exam This course will help you prepare for the following exams: 1Z0 042 1Z0 043 Course Overview PL/SQL is Oracle's Procedural
Oracle 10g PL/SQL Training Course Number: ORCL PS01 Length: 3 Day(s) Certification Exam This course will help you prepare for the following exams: 1Z0 042 1Z0 043 Course Overview PL/SQL is Oracle's Procedural
INSTALLING, CONFIGURING, AND DEVELOPING WITH XAMPP
 INSTALLING, CONFIGURING, AND DEVELOPING WITH XAMPP by Dalibor D. Dvorski, March 2007 Skills Canada Ontario DISCLAIMER: A lot of care has been taken in the accuracy of information provided in this article,
INSTALLING, CONFIGURING, AND DEVELOPING WITH XAMPP by Dalibor D. Dvorski, March 2007 Skills Canada Ontario DISCLAIMER: A lot of care has been taken in the accuracy of information provided in this article,
In This Lecture. SQL Data Definition SQL SQL. Notes. Non-Procedural Programming. Database Systems Lecture 5 Natasha Alechina
 This Lecture Database Systems Lecture 5 Natasha Alechina The language, the relational model, and E/R diagrams CREATE TABLE Columns Primary Keys Foreign Keys For more information Connolly and Begg chapter
This Lecture Database Systems Lecture 5 Natasha Alechina The language, the relational model, and E/R diagrams CREATE TABLE Columns Primary Keys Foreign Keys For more information Connolly and Begg chapter
Fundamentals of Database Design
 Fundamentals of Database Design Zornitsa Zaharieva CERN Data Management Section - Controls Group Accelerators and Beams Department /AB-CO-DM/ 23-FEB-2005 Contents : Introduction to Databases : Main Database
Fundamentals of Database Design Zornitsa Zaharieva CERN Data Management Section - Controls Group Accelerators and Beams Department /AB-CO-DM/ 23-FEB-2005 Contents : Introduction to Databases : Main Database
Access 2007. Creating Databases - Fundamentals
 Access 2007 Creating Databases - Fundamentals Contents Database Design Objectives of database design 1 Process of database design 1 Creating a New Database... 3 Tables... 4 Creating a table in design view
Access 2007 Creating Databases - Fundamentals Contents Database Design Objectives of database design 1 Process of database design 1 Creating a New Database... 3 Tables... 4 Creating a table in design view
Resources You can find more resources for Sync & Save at our support site: http://www.doforms.com/support.
 Sync & Save Introduction Sync & Save allows you to connect the DoForms service (www.doforms.com) with your accounting or management software. If your system can import a comma delimited, tab delimited
Sync & Save Introduction Sync & Save allows you to connect the DoForms service (www.doforms.com) with your accounting or management software. If your system can import a comma delimited, tab delimited
ATTACHMENT 6 SQL Server 2012 Programming Standards
 ATTACHMENT 6 SQL Server 2012 Programming Standards SQL Server Object Design and Programming Object Design and Programming Idaho Department of Lands Document Change/Revision Log Date Version Author Description
ATTACHMENT 6 SQL Server 2012 Programming Standards SQL Server Object Design and Programming Object Design and Programming Idaho Department of Lands Document Change/Revision Log Date Version Author Description
Setting Up Database Security with Access 97
 Setting Up Database Security with Access 97 The most flexible and extensive method of securing a database is called user-level security. This form of security is similar to methods used in most network
Setting Up Database Security with Access 97 The most flexible and extensive method of securing a database is called user-level security. This form of security is similar to methods used in most network
Lab 2: PostgreSQL Tutorial II: Command Line
 Lab 2: PostgreSQL Tutorial II: Command Line In the lab 1, we learned how to use PostgreSQL through the graphic interface, pgadmin. However, PostgreSQL may not be used through a graphical interface. This
Lab 2: PostgreSQL Tutorial II: Command Line In the lab 1, we learned how to use PostgreSQL through the graphic interface, pgadmin. However, PostgreSQL may not be used through a graphical interface. This
Basic Unix/Linux 1. Software Testing Interview Prep
 Basic Unix/Linux 1 Programming Fundamentals and Concepts 2 1. What is the difference between web application and client server application? Client server application is designed typically to work in a
Basic Unix/Linux 1 Programming Fundamentals and Concepts 2 1. What is the difference between web application and client server application? Client server application is designed typically to work in a
User Migration Tool. Note. Staging Guide for Cisco Unified ICM/Contact Center Enterprise & Hosted Release 9.0(1) 1
 The (UMT): Is a stand-alone Windows command-line application that performs migration in the granularity of a Unified ICM instance. It migrates only Unified ICM AD user accounts (config/setup and supervisors)
The (UMT): Is a stand-alone Windows command-line application that performs migration in the granularity of a Unified ICM instance. It migrates only Unified ICM AD user accounts (config/setup and supervisors)
Knocker main application User manual
 Knocker main application User manual Author: Jaroslav Tykal Application: Knocker.exe Document Main application Page 1/18 U Content: 1 START APPLICATION... 3 1.1 CONNECTION TO DATABASE... 3 1.2 MODULE DEFINITION...
Knocker main application User manual Author: Jaroslav Tykal Application: Knocker.exe Document Main application Page 1/18 U Content: 1 START APPLICATION... 3 1.1 CONNECTION TO DATABASE... 3 1.2 MODULE DEFINITION...
How to move a SQL database from one server to another
 How to move a SQL database from one server to another Guide is applicable to these products: * Lucid CoPS, Lucid Rapid, LASS 8-11, LASS 11-15, LADS Plus and Lucid Ability (v6.0x-n) * Lucid Exact v1.xx-n
How to move a SQL database from one server to another Guide is applicable to these products: * Lucid CoPS, Lucid Rapid, LASS 8-11, LASS 11-15, LADS Plus and Lucid Ability (v6.0x-n) * Lucid Exact v1.xx-n
7. Databases and Database Management Systems
 7. Databases and Database Management Systems 7.1 What is a File? A file is a collection of data or information that has a name, called the Filename. There are many different types of files: Data files
7. Databases and Database Management Systems 7.1 What is a File? A file is a collection of data or information that has a name, called the Filename. There are many different types of files: Data files
Virtual Code Authentication User s Guide. June 25, 2015
 Virtual Code Authentication User s Guide June 25, 2015 Virtual Code Authentication User s Guide Overview of New Security Modern technologies call for higher security standards as practiced among many other
Virtual Code Authentication User s Guide June 25, 2015 Virtual Code Authentication User s Guide Overview of New Security Modern technologies call for higher security standards as practiced among many other
TIM 50 - Business Information Systems
 TIM 50 - Business Information Systems Lecture 15 UC Santa Cruz March 1, 2015 The Database Approach to Data Management Database: Collection of related files containing records on people, places, or things.
TIM 50 - Business Information Systems Lecture 15 UC Santa Cruz March 1, 2015 The Database Approach to Data Management Database: Collection of related files containing records on people, places, or things.
Setting Up ALERE with Client/Server Data
 Setting Up ALERE with Client/Server Data TIW Technology, Inc. November 2014 ALERE is a registered trademark of TIW Technology, Inc. The following are registered trademarks or trademarks: FoxPro, SQL Server,
Setting Up ALERE with Client/Server Data TIW Technology, Inc. November 2014 ALERE is a registered trademark of TIW Technology, Inc. The following are registered trademarks or trademarks: FoxPro, SQL Server,
SECURING APACHE : THE BASICS - III
 SECURING APACHE : THE BASICS - III Securing your applications learn how break-ins occur Shown in Figure 2 is a typical client-server Web architecture, which also indicates various attack vectors, or ways
SECURING APACHE : THE BASICS - III Securing your applications learn how break-ins occur Shown in Figure 2 is a typical client-server Web architecture, which also indicates various attack vectors, or ways
MySQL Manager. User Guide. July 2012
 July 2012 MySQL Manager User Guide Welcome to AT&T Website Solutions SM We are focused on providing you the very best web hosting service including all the tools necessary to establish and maintain a successful
July 2012 MySQL Manager User Guide Welcome to AT&T Website Solutions SM We are focused on providing you the very best web hosting service including all the tools necessary to establish and maintain a successful
Facebook Twitter YouTube Google Plus Website Email
 PHP MySQL COURSE WITH OOP COURSE COVERS: PHP MySQL OBJECT ORIENTED PROGRAMMING WITH PHP SYLLABUS PHP 1. Writing PHP scripts- Writing PHP scripts, learn about PHP code structure, how to write and execute
PHP MySQL COURSE WITH OOP COURSE COVERS: PHP MySQL OBJECT ORIENTED PROGRAMMING WITH PHP SYLLABUS PHP 1. Writing PHP scripts- Writing PHP scripts, learn about PHP code structure, how to write and execute
CHAPTER 5 INTELLIGENT TECHNIQUES TO PREVENT SQL INJECTION ATTACKS
 66 CHAPTER 5 INTELLIGENT TECHNIQUES TO PREVENT SQL INJECTION ATTACKS 5.1 INTRODUCTION In this research work, two new techniques have been proposed for addressing the problem of SQL injection attacks, one
66 CHAPTER 5 INTELLIGENT TECHNIQUES TO PREVENT SQL INJECTION ATTACKS 5.1 INTRODUCTION In this research work, two new techniques have been proposed for addressing the problem of SQL injection attacks, one
SQL injection attacks SQL injection user input SQL injection SQL Command parameters Database account. SQL injection attacks Data Code
 SQL Injection Attack SQL injection attacks SQL injection user input SQL injection SQL Command parameters Database account Login page application database over-privileged account database Attacker SQL injection
SQL Injection Attack SQL injection attacks SQL injection user input SQL injection SQL Command parameters Database account Login page application database over-privileged account database Attacker SQL injection
Using Database Metadata and its Semantics to Generate Automatic and Dynamic Web Entry Forms
 Using Database Metadata and its Semantics to Generate Automatic and Dynamic Web Entry Forms Mohammed M. Elsheh and Mick J. Ridley Abstract Automatic and dynamic generation of Web applications is the future
Using Database Metadata and its Semantics to Generate Automatic and Dynamic Web Entry Forms Mohammed M. Elsheh and Mick J. Ridley Abstract Automatic and dynamic generation of Web applications is the future
