How to hear the Web Seminar
|
|
|
- Lorin Simon
- 8 years ago
- Views:
Transcription
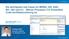
1 How to hear the Web Seminar Click on Communicate in the top menu bar Select Integrated Voice Conference in the drop down Click Join to join the conference You will be able to listen to the presenter through your computer speakers You will not be able to hear the presentation if you dial into the telephone conference *Note: We will begin at 12pm EST. Even if you have connected to the Integrated Voice Conference, you will not hear anything until 12pm. Property of PM Operations Rich Jenny - PMP, PM-ACP, PE. MBA rjenny@nc.rr.com
2 PM Operations RJenny, PMP, PM-ACP, PE Welcome Software Data Overload! Static Analysis-in-DevOps enables the Quality Edge Richard Jenny, PMP, PMI-ACP, PE veteran Program Manager, PMO Leader, DevOps Leader & Evangelist - Overture Networks Jeff Hildreth Territory Account Executive Rogue Wave Software, Inc. Larry Edelstein Sales Engr./Static Analysis Expert Rogue Wave Software, Inc. Chris Knotts, PMP New skills evangelist, Product Manager, and enterprise training specialist ASPE-SDLC Property of PM Operations Rich Jenny - PMP, PM-ACP, PE. MBA rjenny@nc.rr.com
3 Why Static Analysis-in-DevOps? For the next Big Wave PM Operations RJenny, PMP, PM-ACP, PE Do you recall this story?...april 15 Webinar Network Functions Virtualization Static Analysis in-devops helps you get here. Ref. Overture Networks NFV Strategies X86 Open Server Property of PM Operations Rich Jenny - PMP, PM-ACP, PE. MBA rjenny@nc.rr.com
4 The Next Generation, NFV PM Operations RJenny, PMP, PM-ACP, PE Static Analysis-in-DevOps Opportunities Session Border Controller Firewall Router Overture Packet Flow Connector Custom Applications. Citrix XenApp Private Branch Exchange Orchestration and Service Assurance Test and Generators/Analyzers Deep Packet Inspection and Intrusion Detection Switches Network Address Translators.Load Balancers more Property of PM Operations Rich Jenny - PMP, PM-ACP, PE. MBA rjenny@nc.rr.com
5 Static Code Analysis Approach PM Operations RJenny, PMP, PM-ACP, PE Know you re deploying high quality software Property of PM Operations Rich Jenny - PMP, PM-ACP, PE. MBA rjenny@nc.rr.com
6 Software Complexity Explosion And then there is the state explosion For example, the latest QNX kernel has about states. Multi-threaded applications on multi-core processors inherit these states and add their own. By contrast, the number of atoms in the entire observable universe is estimated to be within the range to Property of PM Operations Rich Jenny - PMP, PM-ACP, PE. MBA rjenny@nc.rr.com
7 Analysis vs. Testing Dynamic testing is generally recognised to be becoming less effective Costly and very time consuming High impact of making changes Requires specific expected results Scalability There is a point where it becomes impossible to test a software system exhaustively It is not scalable, and nor is dynamic analysis What fills the gap? Property of PM Operations Rich Jenny - PMP, PM-ACP, PE. MBA rjenny@nc.rr.com
8 Static Code Analysis Maturity Traditionally used to find simple, annoying bugs Modern, state-of-the-art SCA Model-based simulation of runtime expectation based on Interprocedural control and data-flow analysis Find complex bugs and runtime errors, such as memory leaks, concurrency violations, buffer overflows Check compliance with internationally recognized standards: Property of PM Operations Rich Jenny - PMP, PM-ACP, PE. MBA rjenny@nc.rr.com Rogue Wave Software, Inc. All Rights Reserved
9 Static Analysis in DevOps Deploy the highest quality software the first time. Find and fix customer facing issues early in-process Build Analysis / Test 50% of defects introduced here Property of PM Operations Rich Jenny - PMP, PM-ACP, PE. MBA rjenny@nc.rr.com
10 Adding Static Analysis-in-DevOps Larry Edelstein Rogue Wave Software SE UAT/Exploratory Testing Idea proposed Understand Needs & Invent Solutions Develop, Commit & Build Functional Testing Release Decision Deploy Solution Customer Value Load, Performance, Security, Testing Property of PM Operations Rich Jenny - PMP, PM-ACP, PE. MBA rjenny@nc.rr.com
11 Use Case - Uninitialized Function Property of PM Operations Rich Jenny - PMP, PM-ACP, PE. MBA rjenny@nc.rr.com
12 Use Case - Uninitialized Function Risk: If error was left in deployed software it would require a complete rework cycle to resolve Customer reports the issue Support reproduces the defect Development schedules the fix into a sprint Once the issue is fixed testing verifies the fix Operations deploys the fix to the customer Property of PM Operations Rich Jenny - PMP, PM-ACP, PE. MBA rjenny@nc.rr.com
13 Use Case - Invalidated data in a critical function call Property of PM Operations Rich Jenny - PMP, PM-ACP, PE. MBA rjenny@nc.rr.com
14 Use Case - Invalidated data in a critical function call Risk: This error could be a subtle zero day security flaw left in your system If it is discovered by a customer a hot fix rework cycle would need to be executed: Support reproduces the defect Development schedules the fix into a sprint Once the issue is fixed testing verifies the fix Operations deploys the fix to the customer Property of PM Operations Rich Jenny - PMP, PM-ACP, PE. MBA rjenny@nc.rr.com
15 Use-Case Examples Summary 1. Nearly impossible to test every SW state 2. Deploying software with known defects. Will cost time later! 3. Rework cycles are costly. Do what you can to avoid cycles! Property of PM Operations Rich Jenny - PMP, PM-ACP, PE. MBA rjenny@nc.rr.com
16 PM Operations RJenny, PMP, PM-ACP, PE DevOps Release Quality Applications Richard Jenny Property of PM Operations Rich Jenny - PMP, PM-ACP, PE. MBA rjenny@nc.rr.com
17 Static Analysis Finds/Product PM Operations RJenny, PMP, PM-ACP, PE Static Analysis Finds by Severity Products 1 n Property of PM Operations Rich Jenny - PMP, PM-ACP, PE. MBA rjenny@nc.rr.com
18 Static Analysis Finds/KLOC PM Operations RJenny, PMP, PM-ACP, PE Products 1 n Target EoL product Property of PM Operations Rich Jenny - PMP, PM-ACP, PE. MBA rjenny@nc.rr.com
19 Static Analysis-in-DevOps PM Operations RJenny, PMP, PM-ACP, PE Product 1 Prod 2 Prod 3 Prod 4 1 Prod 5 Prod 6 Zeta By Features x,y Property of PM Operations Rich Jenny - PMP, PM-ACP, PE. MBA rjenny@nc.rr.com
20 Static Analysis Finds/Category PM Operations RJenny, PMP, PM-ACP, PE Products 1 n Property of PM Operations Rich Jenny - PMP, PM-ACP, PE. MBA rjenny@nc.rr.com
21 Conclusions Software is growing exponentially Test your software early and often Know you have a releasable product; based on evidence Deploy high quality software the first time Avoid unnecessary rework Property of PM Operations Rich Jenny - PMP, PM-ACP, PE. MBA rjenny@nc.rr.com
22 Static Analysis-in-DevOps PM Operations RJenny, PMP, PM-ACP, PE Thank You! Richard Jenny, PM Operations Overture Networks Program Management and DevOps Leader PMP, PM-ACP, PE, MBA Jeff Hildreth, Rogue Wave Territory Account Executive P EXT 401 M Webinar made possible by and Facilitated by ASPE-SDLC Property of PM Operations Rich Jenny - PMP, PM-ACP, PE. MBA rjenny@nc.rr.com
23 Thank you for joining us! Today s activity awards 1 PDU Today s PDU: One Category A PDU (professional development unit) WS from provider 2161, ASPE. Chris Knotts, ASPE Training Property of PM Operations Rich Jenny - PMP, PM-ACP, PE. MBA rjenny@nc.rr.com
How to Hear the Web Seminar
 How to Hear the Web Seminar Click on Communicate in the top menu bar Select Integrated Voice Conference in the drop down Click Join to join the conference You will be able to listen to the presenter through
How to Hear the Web Seminar Click on Communicate in the top menu bar Select Integrated Voice Conference in the drop down Click Join to join the conference You will be able to listen to the presenter through
Enterprise Project Management Buyer s Guide
 Considerations for Tools and Features Enterprise Project Buyer s Guide Heather Champoux, PMP hchampoux@uplandsoftware.com Agenda Introduction to EPM SaaS vs. On Premise SaaS Benefits SaaS Candidates SaaS
Considerations for Tools and Features Enterprise Project Buyer s Guide Heather Champoux, PMP hchampoux@uplandsoftware.com Agenda Introduction to EPM SaaS vs. On Premise SaaS Benefits SaaS Candidates SaaS
Maximize System Performance
 Maximize System Performance Webinar: Radiant Webinar Mini-Series for Implementation Technicians To connect to phone conference, please call: 1.800.375.2612, and then enter Participant Code: 397670 (or
Maximize System Performance Webinar: Radiant Webinar Mini-Series for Implementation Technicians To connect to phone conference, please call: 1.800.375.2612, and then enter Participant Code: 397670 (or
Developing High-Performance, Flexible SDN & NFV Solutions with Intel Open Network Platform Server Reference Architecture
 White Paper Developing Solutions with Intel ONP Server Reference Architecture Developing High-Performance, Flexible SDN & NFV Solutions with Intel Open Network Platform Server Reference Architecture Developing
White Paper Developing Solutions with Intel ONP Server Reference Architecture Developing High-Performance, Flexible SDN & NFV Solutions with Intel Open Network Platform Server Reference Architecture Developing
Development Testing for Agile Environments
 Development Testing for Agile Environments November 2011 The Pressure Is On More than ever before, companies are being asked to do things faster. They need to get products to market faster to remain competitive
Development Testing for Agile Environments November 2011 The Pressure Is On More than ever before, companies are being asked to do things faster. They need to get products to market faster to remain competitive
#!) * & /! $* - 01 $& -$ 2 1 $& -# 32# $- - + $- -*!45 $-
 ! Version Date Status Owner 1.0 2009-11-09 Released 1.1 2010-01-05 Hints for Fax added Provider hints and new layout 1.2 2010-12-17 Additional hints and corrections 1.3 2011-05-19 Updates for new STUN
! Version Date Status Owner 1.0 2009-11-09 Released 1.1 2010-01-05 Hints for Fax added Provider hints and new layout 1.2 2010-12-17 Additional hints and corrections 1.3 2011-05-19 Updates for new STUN
Eliminate Memory Errors and Improve Program Stability
 Eliminate Memory Errors and Improve Program Stability with Intel Parallel Studio XE Can running one simple tool make a difference? Yes, in many cases. You can find errors that cause complex, intermittent
Eliminate Memory Errors and Improve Program Stability with Intel Parallel Studio XE Can running one simple tool make a difference? Yes, in many cases. You can find errors that cause complex, intermittent
Agile SPL-SCM: Agile Software Product Line Configuration and Release Management
 Agile SPL-SCM: Agile Software Product Line Configuration and Release Management APLE 2006 Workshop SPLC 2006, Baltimore, MD Reto.Kurmann@phonak.com Phonak Hearing Systems Presentation Roadmap 1. Introduction
Agile SPL-SCM: Agile Software Product Line Configuration and Release Management APLE 2006 Workshop SPLC 2006, Baltimore, MD Reto.Kurmann@phonak.com Phonak Hearing Systems Presentation Roadmap 1. Introduction
Chapter 8 Software Testing
 Chapter 8 Software Testing Summary 1 Topics covered Development testing Test-driven development Release testing User testing 2 Program testing Testing is intended to show that a program does what it is
Chapter 8 Software Testing Summary 1 Topics covered Development testing Test-driven development Release testing User testing 2 Program testing Testing is intended to show that a program does what it is
Securing Virtualization with Check Point and Consolidation with Virtualized Security
 Securing Virtualization with Check Point and Consolidation with Virtualized Security consolidate security gateways with full power of Software Blades with Check Point Virtual Systems (VSX) secure virtualized
Securing Virtualization with Check Point and Consolidation with Virtualized Security consolidate security gateways with full power of Software Blades with Check Point Virtual Systems (VSX) secure virtualized
Oracle Solaris Studio Code Analyzer
 Oracle Solaris Studio Code Analyzer The Oracle Solaris Studio Code Analyzer ensures application reliability and security by detecting application vulnerabilities, including memory leaks and memory access
Oracle Solaris Studio Code Analyzer The Oracle Solaris Studio Code Analyzer ensures application reliability and security by detecting application vulnerabilities, including memory leaks and memory access
PART IV Performance oriented design, Performance testing, Performance tuning & Performance solutions. Outline. Performance oriented design
 PART IV Performance oriented design, Performance testing, Performance tuning & Performance solutions Slide 1 Outline Principles for performance oriented design Performance testing Performance tuning General
PART IV Performance oriented design, Performance testing, Performance tuning & Performance solutions Slide 1 Outline Principles for performance oriented design Performance testing Performance tuning General
NEFSIS DEDICATED SERVER
 NEFSIS TRAINING SERIES Nefsis Dedicated Server version 5.2.0.XXX (DRAFT Document) Requirements and Implementation Guide (Rev5-113009) REQUIREMENTS AND INSTALLATION OF THE NEFSIS DEDICATED SERVER Nefsis
NEFSIS TRAINING SERIES Nefsis Dedicated Server version 5.2.0.XXX (DRAFT Document) Requirements and Implementation Guide (Rev5-113009) REQUIREMENTS AND INSTALLATION OF THE NEFSIS DEDICATED SERVER Nefsis
AT&T Unified Communications Voice. IP Communicator Installation Guide
 AT&T Unified Communications Voice IP Communicator Installation Guide For Customer s System Administrator V1.1 July, 2015 Disclaimer The contents of the document may be revised by AT&T at any time without
AT&T Unified Communications Voice IP Communicator Installation Guide For Customer s System Administrator V1.1 July, 2015 Disclaimer The contents of the document may be revised by AT&T at any time without
Installation Guide for GigaBit Fiber Port Aggregator Tap with SFP Monitor Ports
 Installation Guide for GigaBit Fiber Port Aggregator Tap with SFP Monitor Ports (800-0037) Doc. PUBTPASXSFPU Rev., 07/08 Contents Introduction.... Key Features... Unpacking and Inspection....3 Product
Installation Guide for GigaBit Fiber Port Aggregator Tap with SFP Monitor Ports (800-0037) Doc. PUBTPASXSFPU Rev., 07/08 Contents Introduction.... Key Features... Unpacking and Inspection....3 Product
Lecture 17: Testing Strategies" Developer Testing"
 Lecture 17: Testing Strategies Structural Coverage Strategies (White box testing): Statement Coverage Branch Coverage Condition Coverage Data Path Coverage Function Coverage Strategies (Black box testing):
Lecture 17: Testing Strategies Structural Coverage Strategies (White box testing): Statement Coverage Branch Coverage Condition Coverage Data Path Coverage Function Coverage Strategies (Black box testing):
Driving Project Management Excellence at the New AT&T
 Driving Project Management Excellence at the New AT&T Jennifer Birch, PMP Jim Schneidmuller, PMP AT&T PMCOE November 1, 2007 The AT&T PMCOE is a PMI Registered Education Provider Today s Topics Introduction
Driving Project Management Excellence at the New AT&T Jennifer Birch, PMP Jim Schneidmuller, PMP AT&T PMCOE November 1, 2007 The AT&T PMCOE is a PMI Registered Education Provider Today s Topics Introduction
Carrier/WAN SDN. SDN Optimized MPLS Demo
 Carrier/WAN SDN SDN Optimized MPLS Demo Problem Statement! Service Providers around the world have large investments in highly sophisticated and feature rich IP/MPLS network infrastructures for providing
Carrier/WAN SDN SDN Optimized MPLS Demo Problem Statement! Service Providers around the world have large investments in highly sophisticated and feature rich IP/MPLS network infrastructures for providing
Best Practices for Web Application Load Testing
 Best Practices for Web Application Load Testing This paper presents load testing best practices based on 20 years of work with customers and partners. They will help you make a quick start on the road
Best Practices for Web Application Load Testing This paper presents load testing best practices based on 20 years of work with customers and partners. They will help you make a quick start on the road
Static Analysis of Dynamic Properties - Automatic Program Verification to Prove the Absence of Dynamic Runtime Errors
 Static Analysis of Dynamic Properties - Automatic Program Verification to Prove the Absence of Dynamic Runtime Errors Klaus Wissing PolySpace Technologies GmbH Argelsrieder Feld 22 82234 Wessling-Oberpfaffenhofen
Static Analysis of Dynamic Properties - Automatic Program Verification to Prove the Absence of Dynamic Runtime Errors Klaus Wissing PolySpace Technologies GmbH Argelsrieder Feld 22 82234 Wessling-Oberpfaffenhofen
VNF & Performance: A practical approach
 VNF & Performance: A practical approach Luc Provoost Engineering Manager, Network Product Group Intel Corporation SDN and NFV are Forces of Change One Application Per System Many Applications Per Virtual
VNF & Performance: A practical approach Luc Provoost Engineering Manager, Network Product Group Intel Corporation SDN and NFV are Forces of Change One Application Per System Many Applications Per Virtual
Detecting Critical Defects on the Developer s Desktop
 Detecting Critical Defects on the Developer s Desktop Seth Hallem CEO Coverity, Inc. Copyright Coverity, Inc. 2006. All Rights Reserved. This publication, in whole or in part, may not be reproduced, stored
Detecting Critical Defects on the Developer s Desktop Seth Hallem CEO Coverity, Inc. Copyright Coverity, Inc. 2006. All Rights Reserved. This publication, in whole or in part, may not be reproduced, stored
Management & Orchestration of Metaswitch s Perimeta Virtual SBC
 Metaswitch.com OvertureNetworks.com Management & Orchestration of Metaswitch s Perimeta Virtual SBC Fortify your edge and protect your core with the Perimeta Session Border Controller: Virtual The 1st
Metaswitch.com OvertureNetworks.com Management & Orchestration of Metaswitch s Perimeta Virtual SBC Fortify your edge and protect your core with the Perimeta Session Border Controller: Virtual The 1st
Contents. Page. Page 2
 C 2012 Contents Recording an Auto Attendant Greeting... 3 Auto Attendant Overview... 3 To Record or Change an Auto Attendant Greeting... 3 From any IP phone in Company Network... 3 Business Hour Menu...
C 2012 Contents Recording an Auto Attendant Greeting... 3 Auto Attendant Overview... 3 To Record or Change an Auto Attendant Greeting... 3 From any IP phone in Company Network... 3 Business Hour Menu...
Application Code Development Standards
 Application Code Development Standards Overview This document is intended to provide guidance to campus system owners and software developers regarding secure software engineering practices. These standards
Application Code Development Standards Overview This document is intended to provide guidance to campus system owners and software developers regarding secure software engineering practices. These standards
WSNetServer User Manual. Date: July 13 2003
 Date: July 13 2003 1 Revision History... 2 2 Introduction... 2 3 Installation... 2 4 Normal Operation... 2 4.1 Startup... 2 4.2 About Box... 3 4.3 Specifying The Cross Point XY Broadcast Port... 3 4.4
Date: July 13 2003 1 Revision History... 2 2 Introduction... 2 3 Installation... 2 4 Normal Operation... 2 4.1 Startup... 2 4.2 About Box... 3 4.3 Specifying The Cross Point XY Broadcast Port... 3 4.4
Carlos Villavieja, Nacho Navarro {cvillavi,nacho}@ac.upc.edu. Arati Baliga, Liviu Iftode {aratib,liviu}@cs.rutgers.edu
 Continuous Monitoring using MultiCores Carlos Villavieja, Nacho Navarro {cvillavi,nacho}@ac.upc.edu Arati Baliga, Liviu Iftode {aratib,liviu}@cs.rutgers.edu Motivation Intrusion detection Intruder gets
Continuous Monitoring using MultiCores Carlos Villavieja, Nacho Navarro {cvillavi,nacho}@ac.upc.edu Arati Baliga, Liviu Iftode {aratib,liviu}@cs.rutgers.edu Motivation Intrusion detection Intruder gets
Verizon Columbia Research on VoIP Security A Model Academia/Industry Collaboration. Gaston Ormazabal. Verizon Laboratories.
 Verizon 2009 All Rights Reserved. 1 Verizon Columbia Research on VoIP Security A Model Academia/Industry Collaboration Gaston Ormazabal Verizon Laboratories May 13, 2009 June 16, 2009 Verizon 2009 All
Verizon 2009 All Rights Reserved. 1 Verizon Columbia Research on VoIP Security A Model Academia/Industry Collaboration Gaston Ormazabal Verizon Laboratories May 13, 2009 June 16, 2009 Verizon 2009 All
Center SDN & NFV. Modern Data IN THE
 SDN & NFV IN THE Modern Data Center A GUIDE TO UNDERSTANDING THE IMPACT AND BENEFITS OF SOFTWARE-DEFINED NETWORKING AND NETWORK FUNCTIONS VIRTUALIZATION TABLE OF CONTENTS OF SDN AND NFV ARE SDN AND NFV
SDN & NFV IN THE Modern Data Center A GUIDE TO UNDERSTANDING THE IMPACT AND BENEFITS OF SOFTWARE-DEFINED NETWORKING AND NETWORK FUNCTIONS VIRTUALIZATION TABLE OF CONTENTS OF SDN AND NFV ARE SDN AND NFV
COUNTERSNIPE WWW.COUNTERSNIPE.COM
 COUNTERSNIPE WWW.COUNTERSNIPE.COM COUNTERSNIPE SYSTEMS LLC RELEASE 7.0 CounterSnipe s version 7.0 is their next major release and includes a completely new IDS/IPS leveraging high performance scalability
COUNTERSNIPE WWW.COUNTERSNIPE.COM COUNTERSNIPE SYSTEMS LLC RELEASE 7.0 CounterSnipe s version 7.0 is their next major release and includes a completely new IDS/IPS leveraging high performance scalability
Detecting rogue systems
 Product Guide Revision A McAfee Rogue System Detection 4.7.1 For use with epolicy Orchestrator 4.6.3-5.0.0 Software Detecting rogue systems Unprotected systems, referred to as rogue systems, are often
Product Guide Revision A McAfee Rogue System Detection 4.7.1 For use with epolicy Orchestrator 4.6.3-5.0.0 Software Detecting rogue systems Unprotected systems, referred to as rogue systems, are often
mguard Device Manager Release Notes Version 1.6.1
 mguard Device Manager Release Notes Version 1.6.1 Innominate Security Technologies AG Rudower Chaussee 13 12489 Berlin Germany Phone: +49 30 921028 0 Fax: +49 30 921028 020 contact@innominate.com http://www.innominate.com/
mguard Device Manager Release Notes Version 1.6.1 Innominate Security Technologies AG Rudower Chaussee 13 12489 Berlin Germany Phone: +49 30 921028 0 Fax: +49 30 921028 020 contact@innominate.com http://www.innominate.com/
Managing ^ VoIP Quality and Performance
 Unified, Cloud Based, Virtualized, Hosted Managing ^ VoIP Quality and Performance Alan Clark, CEO Telchemy alan.d.clark@telchemy.com 1 Outline VoIP Performance Issues Current state of the art VoIP performance
Unified, Cloud Based, Virtualized, Hosted Managing ^ VoIP Quality and Performance Alan Clark, CEO Telchemy alan.d.clark@telchemy.com 1 Outline VoIP Performance Issues Current state of the art VoIP performance
Agile Delivery Framework Automation & Deployment With Puppet
 2015 2015 Agile Delivery Framework Automation & Deployment With Puppet Karthiga Sadasivan https://www.linkedin.com/in/karthisadasivan Email ID: Karthiga.Sadasivan@happiestminds.com Blog : www.happiestminds.com/blogs/category/devops
2015 2015 Agile Delivery Framework Automation & Deployment With Puppet Karthiga Sadasivan https://www.linkedin.com/in/karthisadasivan Email ID: Karthiga.Sadasivan@happiestminds.com Blog : www.happiestminds.com/blogs/category/devops
SSL-VPN 200 Getting Started Guide
 Secure Remote Access Solutions APPLIANCES SonicWALL SSL-VPN Series SSL-VPN 200 Getting Started Guide SonicWALL SSL-VPN 200 Appliance Getting Started Guide Thank you for your purchase of the SonicWALL SSL-VPN
Secure Remote Access Solutions APPLIANCES SonicWALL SSL-VPN Series SSL-VPN 200 Getting Started Guide SonicWALL SSL-VPN 200 Appliance Getting Started Guide Thank you for your purchase of the SonicWALL SSL-VPN
Flow Publisher v1.0 Getting Started Guide. Get started with WhatsUp Flow Publisher.
 Flow Publisher v1.0 Getting Started Guide Get started with WhatsUp Flow Publisher. Contents CHAPTER 1 Welcome Welcome to Flow Publisher... 1 About Flow Publisher... 2 Deploying Deploying Flow Publisher...
Flow Publisher v1.0 Getting Started Guide Get started with WhatsUp Flow Publisher. Contents CHAPTER 1 Welcome Welcome to Flow Publisher... 1 About Flow Publisher... 2 Deploying Deploying Flow Publisher...
ETAP FAQ # 24. Most Common Questions Asked About ETAP Webinars
 ETAP FAQ # 24 Most Common Questions Asked About ETAP Webinars 1. What is a webinar? 2. How do I participate in a webinar? 3. What kind of equipment do I need to attend? 4. Do I need to have ETAP running
ETAP FAQ # 24 Most Common Questions Asked About ETAP Webinars 1. What is a webinar? 2. How do I participate in a webinar? 3. What kind of equipment do I need to attend? 4. Do I need to have ETAP running
Implementing Continuous Integration Testing Prepared by:
 Implementing Continuous Integration Testing Prepared by: Mr Sandeep M Table of Contents 1. ABSTRACT... 2 2. INTRODUCTION TO CONTINUOUS INTEGRATION (CI)... 3 3. CI FOR AGILE METHODOLOGY... 4 4. WORK FLOW...
Implementing Continuous Integration Testing Prepared by: Mr Sandeep M Table of Contents 1. ABSTRACT... 2 2. INTRODUCTION TO CONTINUOUS INTEGRATION (CI)... 3 3. CI FOR AGILE METHODOLOGY... 4 4. WORK FLOW...
Linux Kernel. Security Report
 Linux Kernel Security Report September 25 Authors: Andy Chou, Bryan Fulton and Seth Hallem Coverity has combined two years of analysis work carried out in a commercial setting at Coverity with four years
Linux Kernel Security Report September 25 Authors: Andy Chou, Bryan Fulton and Seth Hallem Coverity has combined two years of analysis work carried out in a commercial setting at Coverity with four years
B2B Software Technologies Ltd. Service Level Agreement (SLA)
 Service Level Agreement (SLA) Overview This document describes a Service Level Agreement (SLA) between Customer and B2B Software Technologies. It outlines the services offered by B2B for NAVISION ADDON
Service Level Agreement (SLA) Overview This document describes a Service Level Agreement (SLA) between Customer and B2B Software Technologies. It outlines the services offered by B2B for NAVISION ADDON
Version Date Status Owner. 1.0 2009-02-04 Released for HiPath OpenOffice ME V1 F. Kneissl / K.-W. Weigt
 History of Change Version Date Status Owner 1.0 2009-02-04 Released for HiPath OpenOffice ME V1 F. Kneissl / K.-W. Weigt 1.1 2010-09-01 Update for OpenScape Office MX V2 and hints for Fax F. Kneissl 1.2
History of Change Version Date Status Owner 1.0 2009-02-04 Released for HiPath OpenOffice ME V1 F. Kneissl / K.-W. Weigt 1.1 2010-09-01 Update for OpenScape Office MX V2 and hints for Fax F. Kneissl 1.2
Going Linux on Massive Multicore
 Embedded Linux Conference Europe 2013 Going Linux on Massive Multicore Marta Rybczyńska 24th October, 2013 Agenda Architecture Linux Port Core Peripherals Debugging Summary and Future Plans 2 Agenda Architecture
Embedded Linux Conference Europe 2013 Going Linux on Massive Multicore Marta Rybczyńska 24th October, 2013 Agenda Architecture Linux Port Core Peripherals Debugging Summary and Future Plans 2 Agenda Architecture
EarthLink Business SIP Trunking. Asterisk 11.2 IP PBX Customer Configuration Guide
 EarthLink Business SIP Trunking Asterisk 11.2 IP PBX Customer Configuration Guide Publication History First Release: Version 1.0 August 30, 2011 CHANGE HISTORY Version Date Change Details Changed By 1.0
EarthLink Business SIP Trunking Asterisk 11.2 IP PBX Customer Configuration Guide Publication History First Release: Version 1.0 August 30, 2011 CHANGE HISTORY Version Date Change Details Changed By 1.0
Minimizing code defects to improve software quality and lower development costs.
 Development solutions White paper October 2008 Minimizing code defects to improve software quality and lower development costs. IBM Rational Software Analyzer and IBM Rational PurifyPlus software Kari
Development solutions White paper October 2008 Minimizing code defects to improve software quality and lower development costs. IBM Rational Software Analyzer and IBM Rational PurifyPlus software Kari
Satisfying ASIL Requirements with Parasoft C++test Achieving Functional Safety in the Automotive Industry
 Satisfying Requirements with Parasoft C++test Achieving Functional Safety in the Automotive Industry Introduction Safety functions are increasingly being carried out by electrical, electronic, or programmable
Satisfying Requirements with Parasoft C++test Achieving Functional Safety in the Automotive Industry Introduction Safety functions are increasingly being carried out by electrical, electronic, or programmable
STATIC CODE ANALYSIS IN AN AGILE WORLD. Establishing a repeatable process to achieve working software with each iteration
 STATIC CODE ANALYSIS IN AN AGILE WORLD Establishing a repeatable process to achieve working software with each iteration To keep pace with ever-increasing customer demands on software functionality and
STATIC CODE ANALYSIS IN AN AGILE WORLD Establishing a repeatable process to achieve working software with each iteration To keep pace with ever-increasing customer demands on software functionality and
The AppSec How-To: Achieving Security in DevOps
 The AppSec How-To: Achieving Security in DevOps How do you integrate security within a Continuous Deployment (CD) environment - where every 5 minutes a feature, an enhancement, or a bug fix needs to be
The AppSec How-To: Achieving Security in DevOps How do you integrate security within a Continuous Deployment (CD) environment - where every 5 minutes a feature, an enhancement, or a bug fix needs to be
Installation Guide for GigaBit Fiber Port Aggregator Tap with SFP Monitor Ports
 Installation Guide for Gigait Fiber Port ggregator Tap with SFP Monitor Ports Doc. PUPDSXSFPU Rev., 08/06 Gigait Fiber Port ggregator Tap Contents Introduction.....................................................
Installation Guide for Gigait Fiber Port ggregator Tap with SFP Monitor Ports Doc. PUPDSXSFPU Rev., 08/06 Gigait Fiber Port ggregator Tap Contents Introduction.....................................................
Saisei and Intel Maximizing WAN Bandwidth
 Intel Network Builders Saisei Solution Brief Intel Xeon Processors Saisei and Intel Maximizing WAN Bandwidth Introduction Despite the increased capacity available on WAN links1, service providers and enterprises
Intel Network Builders Saisei Solution Brief Intel Xeon Processors Saisei and Intel Maximizing WAN Bandwidth Introduction Despite the increased capacity available on WAN links1, service providers and enterprises
Using Power to Improve C Programming Education
 Using Power to Improve C Programming Education Jonas Skeppstedt Department of Computer Science Lund University Lund, Sweden jonas.skeppstedt@cs.lth.se jonasskeppstedt.net jonasskeppstedt.net jonas.skeppstedt@cs.lth.se
Using Power to Improve C Programming Education Jonas Skeppstedt Department of Computer Science Lund University Lund, Sweden jonas.skeppstedt@cs.lth.se jonasskeppstedt.net jonasskeppstedt.net jonas.skeppstedt@cs.lth.se
ACI ON DEMAND DELIVERS PEACE OF MIND
 DELIVERS PEACE OF MIND SERVICE LINE FLYER ACI ON DEMAND ACCESS TO THE LATEST RELEASES OF FEATURE-RICH SOFTWARE AND SYSTEMS, INCLUDING INTEGRATION WITH VALUE- ADDED THIRD PARTIES IMPLEMENTATION CONFIGURED
DELIVERS PEACE OF MIND SERVICE LINE FLYER ACI ON DEMAND ACCESS TO THE LATEST RELEASES OF FEATURE-RICH SOFTWARE AND SYSTEMS, INCLUDING INTEGRATION WITH VALUE- ADDED THIRD PARTIES IMPLEMENTATION CONFIGURED
Home Phone - VoIP. Installation Guide
 Home Phone - VoIP Installation Guide Package Contents Package Contents D-link DG-102S VoIP Adapter 1 2 3 4 5 6 Serial Cable Ethernet Cable Power Adapter 1 2 3 4 5 6 Power Adapter Serial Cable Used only
Home Phone - VoIP Installation Guide Package Contents Package Contents D-link DG-102S VoIP Adapter 1 2 3 4 5 6 Serial Cable Ethernet Cable Power Adapter 1 2 3 4 5 6 Power Adapter Serial Cable Used only
Cisco Integrated Services Routers Performance Overview
 Integrated Services Routers Performance Overview What You Will Learn The Integrated Services Routers Generation 2 (ISR G2) provide a robust platform for delivering WAN services, unified communications,
Integrated Services Routers Performance Overview What You Will Learn The Integrated Services Routers Generation 2 (ISR G2) provide a robust platform for delivering WAN services, unified communications,
Ancero Managed Internet Service (MIS) & Private Network Transport (PNT) Service Guide
 Ancero Managed Internet Service (MIS) & Private Network Transport (PNT) Service Guide Contents Service Overview... 3 Managed Internet Service (MIS): Dedicated Access that Keeps You Connected... 3 Reliable,
Ancero Managed Internet Service (MIS) & Private Network Transport (PNT) Service Guide Contents Service Overview... 3 Managed Internet Service (MIS): Dedicated Access that Keeps You Connected... 3 Reliable,
Aerohive Networks Inc. Free Bonjour Gateway FAQ
 Aerohive Networks Inc. Free Bonjour Gateway FAQ 1. About the Product... 1 2. Installation... 2 3. Management... 3 4. Troubleshooting... 4 1. About the Product What is the Aerohive s Free Bonjour Gateway?
Aerohive Networks Inc. Free Bonjour Gateway FAQ 1. About the Product... 1 2. Installation... 2 3. Management... 3 4. Troubleshooting... 4 1. About the Product What is the Aerohive s Free Bonjour Gateway?
Application Visibility and Monitoring >
 White Paper Application Visibility and Monitoring > An integrated approach to application delivery Application performance drives business performance Every business today depends on secure, reliable information
White Paper Application Visibility and Monitoring > An integrated approach to application delivery Application performance drives business performance Every business today depends on secure, reliable information
SE 4C03 Winter 2005 An Introduction of Firewall Architectures and Functions. Kevin Law 26 th March, 2005-03-29
 SE 4C03 Winter 2005 An Introduction of Firewall Architectures and Functions Kevin Law 26 th March, 2005-03-29 1). Introduction A person who has used the Internet before would hear about the term firewall.
SE 4C03 Winter 2005 An Introduction of Firewall Architectures and Functions Kevin Law 26 th March, 2005-03-29 1). Introduction A person who has used the Internet before would hear about the term firewall.
Debugging A MotoHawk Application using the Application Monitor
 CONTROL SYSTEM SOLUTIONS Debugging A MotoHawk Application using the Application Monitor Author(s): New Eagle Consulting 3588 Plymouth Road, #274 Ann Arbor, MI 48105-2603 Phone: +1 (734) 929-4557 Ben Hoffman
CONTROL SYSTEM SOLUTIONS Debugging A MotoHawk Application using the Application Monitor Author(s): New Eagle Consulting 3588 Plymouth Road, #274 Ann Arbor, MI 48105-2603 Phone: +1 (734) 929-4557 Ben Hoffman
TNT SOFTWARE White Paper Series
 TNT SOFTWARE White Paper Series Event Log Monitor White Paper: Architecture T N T Software www.tntsoftware.com TNT SOFTWARE Event Log Monitor Architecture 2000 TNT Software All Rights Reserved 1308 NE
TNT SOFTWARE White Paper Series Event Log Monitor White Paper: Architecture T N T Software www.tntsoftware.com TNT SOFTWARE Event Log Monitor Architecture 2000 TNT Software All Rights Reserved 1308 NE
Integrating Citrix EasyCall Gateway with SwyxWare
 Integrating Citrix EasyCall Gateway with SwyxWare The EasyCall Gateway has been tested for interoperability with Swyx SwyxWare, versions 6.12 and 6.20. These integration tests were done by using EasyCall
Integrating Citrix EasyCall Gateway with SwyxWare The EasyCall Gateway has been tested for interoperability with Swyx SwyxWare, versions 6.12 and 6.20. These integration tests were done by using EasyCall
Augmented Search for Software Testing
 Augmented Search for Software Testing For Testers, Developers, and QA Managers New frontier in big log data analysis and application intelligence Business white paper May 2015 During software testing cycles,
Augmented Search for Software Testing For Testers, Developers, and QA Managers New frontier in big log data analysis and application intelligence Business white paper May 2015 During software testing cycles,
The Role of Virtual Routers In Carrier Networks
 The Role of Virtual Routers In Carrier Networks Sterling d Perrin Senior Analyst, Heavy Reading Agenda Definitions of SDN and NFV Benefits of SDN and NFV Challenges and Inhibitors Some Use Cases Some Industry
The Role of Virtual Routers In Carrier Networks Sterling d Perrin Senior Analyst, Heavy Reading Agenda Definitions of SDN and NFV Benefits of SDN and NFV Challenges and Inhibitors Some Use Cases Some Industry
Performance Testing. Slow data transfer rate may be inherent in hardware but can also result from software-related problems, such as:
 Performance Testing Definition: Performance Testing Performance testing is the process of determining the speed or effectiveness of a computer, network, software program or device. This process can involve
Performance Testing Definition: Performance Testing Performance testing is the process of determining the speed or effectiveness of a computer, network, software program or device. This process can involve
Informal methods A personal search for practical alternatives to moral improvement through suffering in systems research
 Informal methods A personal search for practical alternatives to moral improvement through suffering in systems research (lightning-talk version) Robert N. M. Watson University of Cambridge Computer Laboratory
Informal methods A personal search for practical alternatives to moral improvement through suffering in systems research (lightning-talk version) Robert N. M. Watson University of Cambridge Computer Laboratory
IBM Security. 2013 IBM Corporation. 2013 IBM Corporation
 IBM Security Security Intelligence What is Security Intelligence? Security Intelligence --noun 1.the real-time collection, normalization and analytics of the data generated by users, applications and infrastructure
IBM Security Security Intelligence What is Security Intelligence? Security Intelligence --noun 1.the real-time collection, normalization and analytics of the data generated by users, applications and infrastructure
PANO MANAGER CONNECTOR FOR SCVMM& HYPER-V
 PANO MANAGER CONNECTOR FOR SCVMM& HYPER-V Version 6.0.8 Published: DEC-2013 Updated: 24 MAR 2014 2005-2014 Propalms Ltd. All rights reserved. The information contained in this document represents the current
PANO MANAGER CONNECTOR FOR SCVMM& HYPER-V Version 6.0.8 Published: DEC-2013 Updated: 24 MAR 2014 2005-2014 Propalms Ltd. All rights reserved. The information contained in this document represents the current
Essential Visual Studio Team System
 Essential Visual Studio Team System Introduction This course helps software development teams successfully deliver complex software solutions with Microsoft Visual Studio Team System (VSTS). Discover how
Essential Visual Studio Team System Introduction This course helps software development teams successfully deliver complex software solutions with Microsoft Visual Studio Team System (VSTS). Discover how
YOUR GUIDE TO THE iphone MOBILE APP WITH 1st SOURCE
 YOUR GUIDE TO THE iphone MOBILE APP WITH 1st SOURCE Strong. Stable. Local. Personal. 10/12 Install, Sign On and View Account Balances 1. Visit the iphone App Store on your iphone and search for 1st Source
YOUR GUIDE TO THE iphone MOBILE APP WITH 1st SOURCE Strong. Stable. Local. Personal. 10/12 Install, Sign On and View Account Balances 1. Visit the iphone App Store on your iphone and search for 1st Source
How To Test A Web Server
 Performance and Load Testing Part 1 Performance & Load Testing Basics Performance & Load Testing Basics Introduction to Performance Testing Difference between Performance, Load and Stress Testing Why Performance
Performance and Load Testing Part 1 Performance & Load Testing Basics Performance & Load Testing Basics Introduction to Performance Testing Difference between Performance, Load and Stress Testing Why Performance
Analogue Telephone User Guide
 Analogue Telephone User Guide IP COMMUNICATIONS PLATFORM FOR THE SMALL BUSINESS Specifications subject to change without notice. Facilities described may or may not be supported by your network. This documentation
Analogue Telephone User Guide IP COMMUNICATIONS PLATFORM FOR THE SMALL BUSINESS Specifications subject to change without notice. Facilities described may or may not be supported by your network. This documentation
QoS issues in Voice over IP
 COMP9333 Advance Computer Networks Mini Conference QoS issues in Voice over IP Student ID: 3058224 Student ID: 3043237 Student ID: 3036281 Student ID: 3025715 QoS issues in Voice over IP Abstract: This
COMP9333 Advance Computer Networks Mini Conference QoS issues in Voice over IP Student ID: 3058224 Student ID: 3043237 Student ID: 3036281 Student ID: 3025715 QoS issues in Voice over IP Abstract: This
IP Telephony Management
 IP Telephony Management How Cisco IT Manages Global IP Telephony A Cisco on Cisco Case Study: Inside Cisco IT 1 Overview Challenge Design, implement, and maintain a highly available, reliable, and resilient
IP Telephony Management How Cisco IT Manages Global IP Telephony A Cisco on Cisco Case Study: Inside Cisco IT 1 Overview Challenge Design, implement, and maintain a highly available, reliable, and resilient
Software testing. Objectives
 Software testing cmsc435-1 Objectives To discuss the distinctions between validation testing and defect testing To describe the principles of system and component testing To describe strategies for generating
Software testing cmsc435-1 Objectives To discuss the distinctions between validation testing and defect testing To describe the principles of system and component testing To describe strategies for generating
CIO Update: Enterprise Security Moves Toward Intrusion Prevention
 IGG-06042003-03 J. Pescatore, R. Stiennon Article 4 June 2003 CIO Update: Enterprise Security Moves Toward Intrusion Prevention As targeted hacker attacks increase, intrusion prevention is gaining importance
IGG-06042003-03 J. Pescatore, R. Stiennon Article 4 June 2003 CIO Update: Enterprise Security Moves Toward Intrusion Prevention As targeted hacker attacks increase, intrusion prevention is gaining importance
Lab Testing Summary Report
 Key findings and conclusions: Cisco WAAS exhibited no signs of system instability or blocking of traffic under heavy traffic load Lab Testing Summary Report September 2009 Report 090815B Product Category:
Key findings and conclusions: Cisco WAAS exhibited no signs of system instability or blocking of traffic under heavy traffic load Lab Testing Summary Report September 2009 Report 090815B Product Category:
HoneyBOT User Guide A Windows based honeypot solution
 HoneyBOT User Guide A Windows based honeypot solution Visit our website at http://www.atomicsoftwaresolutions.com/ Table of Contents What is a Honeypot?...2 How HoneyBOT Works...2 Secure the HoneyBOT Computer...3
HoneyBOT User Guide A Windows based honeypot solution Visit our website at http://www.atomicsoftwaresolutions.com/ Table of Contents What is a Honeypot?...2 How HoneyBOT Works...2 Secure the HoneyBOT Computer...3
NETWORK FUNCTIONS VIRTUALIZATION FOR SECURITY (NFV-S)
 NETWORK FUNCTIONS VIRTUALIZATION FOR SECURITY (NFV-S) 2014/03/03 Wedge Networks Whitepaper Document: WEDGE-NFV-S.V1.0 Wedge Networks www.wedgenetworks.com (This page intentionally left blank for presentation
NETWORK FUNCTIONS VIRTUALIZATION FOR SECURITY (NFV-S) 2014/03/03 Wedge Networks Whitepaper Document: WEDGE-NFV-S.V1.0 Wedge Networks www.wedgenetworks.com (This page intentionally left blank for presentation
Ancero Virtual Private Network (AVPN) Service Guide
 Ancero Virtual Private Network (AVPN) Service Guide Contents Service Overview... 3 Ancero Virtual Private Network Service (AVPN): Reliable, flexible, any-to-any connectivity... 3 AVPN Benefits... 3 AVPN
Ancero Virtual Private Network (AVPN) Service Guide Contents Service Overview... 3 Ancero Virtual Private Network Service (AVPN): Reliable, flexible, any-to-any connectivity... 3 AVPN Benefits... 3 AVPN
Die wichtigsten Use Cases für MISRA, HIS, SQO, IEC, ISO und Co. - Warum Polyspace DIE Embedded Code-Verifikationslösung ist.
 Die wichtigsten Use Cases für MISRA, HIS, SQO, IEC, ISO und Co. - Warum Polyspace DIE Embedded Code-Verifikationslösung ist. Christian Guß Application Engineer The MathWorks GmbH 2015 The MathWorks, Inc.
Die wichtigsten Use Cases für MISRA, HIS, SQO, IEC, ISO und Co. - Warum Polyspace DIE Embedded Code-Verifikationslösung ist. Christian Guß Application Engineer The MathWorks GmbH 2015 The MathWorks, Inc.
Apache Jakarta Tomcat
 Apache Jakarta Tomcat 20041058 Suh, Junho Road Map 1 Tomcat Overview What we need to make more dynamic web documents? Server that supports JSP, ASP, database etc We concentrates on Something that support
Apache Jakarta Tomcat 20041058 Suh, Junho Road Map 1 Tomcat Overview What we need to make more dynamic web documents? Server that supports JSP, ASP, database etc We concentrates on Something that support
Software Engineering. Software Testing. Based on Software Engineering, 7 th Edition by Ian Sommerville
 Software Engineering Software Testing Based on Software Engineering, 7 th Edition by Ian Sommerville Objectives To discuss the distinctions between validation testing and defect t testing To describe the
Software Engineering Software Testing Based on Software Engineering, 7 th Edition by Ian Sommerville Objectives To discuss the distinctions between validation testing and defect t testing To describe the
TELE 301 Network Management
 TELE 301 Network Management Lecture 22: Diagnostics & Ethics Haibo Zhang Computer Science, University of Otago TELE301 Lecture 22: Diagnostics & Ethics 1 Fault Management Fault management It means preventing,
TELE 301 Network Management Lecture 22: Diagnostics & Ethics Haibo Zhang Computer Science, University of Otago TELE301 Lecture 22: Diagnostics & Ethics 1 Fault Management Fault management It means preventing,
Rebasoft Auditor Quick Start Guide
 Copyright Rebasoft Limited: 2009-2011 1 Release 2.1, Rev. 1 Copyright Notice Copyright 2009-2011 Rebasoft Ltd. All rights reserved. REBASOFT Software, the Rebasoft logo, Rebasoft Auditor are registered
Copyright Rebasoft Limited: 2009-2011 1 Release 2.1, Rev. 1 Copyright Notice Copyright 2009-2011 Rebasoft Ltd. All rights reserved. REBASOFT Software, the Rebasoft logo, Rebasoft Auditor are registered
The Secrets to Using MS Project Server Effectively
 The Secrets to Using MS Project Server Effectively About the Presenter: David Mack 16+ years Microsoft Project experience Instructor and mentor to several Fortune 500 companies Federal deliveries to VA,
The Secrets to Using MS Project Server Effectively About the Presenter: David Mack 16+ years Microsoft Project experience Instructor and mentor to several Fortune 500 companies Federal deliveries to VA,
Application Performance Testing Basics
 Application Performance Testing Basics ABSTRACT Todays the web is playing a critical role in all the business domains such as entertainment, finance, healthcare etc. It is much important to ensure hassle-free
Application Performance Testing Basics ABSTRACT Todays the web is playing a critical role in all the business domains such as entertainment, finance, healthcare etc. It is much important to ensure hassle-free
REQUIREMENTS AND INSTALLATION OF THE NEFSIS DEDICATED SERVER
 NEFSIS TRAINING SERIES Nefsis Dedicated Server version 5.1.0.XXX Requirements and Implementation Guide (Rev 4-10209) REQUIREMENTS AND INSTALLATION OF THE NEFSIS DEDICATED SERVER Nefsis Training Series
NEFSIS TRAINING SERIES Nefsis Dedicated Server version 5.1.0.XXX Requirements and Implementation Guide (Rev 4-10209) REQUIREMENTS AND INSTALLATION OF THE NEFSIS DEDICATED SERVER Nefsis Training Series
Cloud: App-Centric Scalability, Availability, Reliability and Security. Prakash Sinha, Director, Product Management October 27, 2009
 Cloud: App-Centric Scalability, Availability, Reliability and Security Prakash Sinha, Director, Product Management October 27, 2009 Agenda Cloud Computing Evolution Creating an Enterprise Cloud Use Cases,
Cloud: App-Centric Scalability, Availability, Reliability and Security Prakash Sinha, Director, Product Management October 27, 2009 Agenda Cloud Computing Evolution Creating an Enterprise Cloud Use Cases,
Comprehensive Static Analysis Using Polyspace Products. A Solution to Today s Embedded Software Verification Challenges WHITE PAPER
 Comprehensive Static Analysis Using Polyspace Products A Solution to Today s Embedded Software Verification Challenges WHITE PAPER Introduction Verification of embedded software is a difficult task, made
Comprehensive Static Analysis Using Polyspace Products A Solution to Today s Embedded Software Verification Challenges WHITE PAPER Introduction Verification of embedded software is a difficult task, made
Edge Virtualization and the MicroCloud. Benefits and Differences between Private and Public Clouds
 WHITE PAPER Edge ization and the MicroCloud Benefits and Differences between Private and Public Clouds AUTHOR: JOEL FUTTERMAN IPHOTONIX COO & CTO www.iphotonix.com The benefits of public and private clouds
WHITE PAPER Edge ization and the MicroCloud Benefits and Differences between Private and Public Clouds AUTHOR: JOEL FUTTERMAN IPHOTONIX COO & CTO www.iphotonix.com The benefits of public and private clouds
The Virtual Ascent of Software Network Intelligence
 White Paper The Virtual Ascent of Software Network Intelligence Prepared by Jim Hodges Senior Analyst, Heavy Reading www.heavyreading.com on behalf of www.windriver.com July 2013 Introduction Although
White Paper The Virtual Ascent of Software Network Intelligence Prepared by Jim Hodges Senior Analyst, Heavy Reading www.heavyreading.com on behalf of www.windriver.com July 2013 Introduction Although
Hosting more than one FortiOS instance on. VLANs. 1. Network topology
 Hosting more than one FortiOS instance on a single FortiGate unit using VDOMs and VLANs 1. Network topology Use Virtual domains (VDOMs) to divide the FortiGate unit into two or more virtual instances of
Hosting more than one FortiOS instance on a single FortiGate unit using VDOMs and VLANs 1. Network topology Use Virtual domains (VDOMs) to divide the FortiGate unit into two or more virtual instances of
DSView 4 Management Software Transition Technical Bulletin
 DSView 4 Management Software Transition Technical Bulletin DSView, Avocent and the Avocent logo are trademarks or registered trademarks of Avocent Corporation or its affiliates in the U.S. and other countries.
DSView 4 Management Software Transition Technical Bulletin DSView, Avocent and the Avocent logo are trademarks or registered trademarks of Avocent Corporation or its affiliates in the U.S. and other countries.
Understanding Cisco IOS Naming Conventions
 Understanding Cisco IOS Naming Conventions Academy Conference 2005 John Rullan, CCNP, CCAI Objectives Evolution of Cisco trains and releases Names of trains and releases Types of trains and releases Feature
Understanding Cisco IOS Naming Conventions Academy Conference 2005 John Rullan, CCNP, CCAI Objectives Evolution of Cisco trains and releases Names of trains and releases Types of trains and releases Feature
Application Security Center overview
 Application Security overview Magnus Hillgren Presales HP Software Sweden Fredrik Möller Nordic Manager - Fortify Software HP BTO (Business Technology Optimization) Business outcomes STRATEGY Project &
Application Security overview Magnus Hillgren Presales HP Software Sweden Fredrik Möller Nordic Manager - Fortify Software HP BTO (Business Technology Optimization) Business outcomes STRATEGY Project &
Product Overview. Product Family. Product Features. Powerful intrusion detection and monitoring capacity
 NIP IDS Product Overview The Network Intelligent Police (NIP) Intrusion Detection System (IDS) is a new generation of session-based intelligent network IDS developed by Huaweisymantec. Deployed in key
NIP IDS Product Overview The Network Intelligent Police (NIP) Intrusion Detection System (IDS) is a new generation of session-based intelligent network IDS developed by Huaweisymantec. Deployed in key
Embedded Virtualization & Cyber Security for Industrial Automation HyperSecured PC-based Control and Operation
 Embedded Virtualization & Cyber Security for Industrial Automation HyperSecured PC-based Control and Operation Industrial controllers and HMIs today mostly lack protective functions for their IT and network
Embedded Virtualization & Cyber Security for Industrial Automation HyperSecured PC-based Control and Operation Industrial controllers and HMIs today mostly lack protective functions for their IT and network
Welcome to the Dawn of Open-Source Networking. Linux IP Routers Bob Gilligan gilligan@vyatta.com
 Welcome to the Dawn of Open-Source Networking. Linux IP Routers Bob Gilligan gilligan@vyatta.com Outline About Vyatta: Open source project, and software product Areas we re working on or interested in
Welcome to the Dawn of Open-Source Networking. Linux IP Routers Bob Gilligan gilligan@vyatta.com Outline About Vyatta: Open source project, and software product Areas we re working on or interested in
DevOps - en inngang til den Digtale Transformasjon Rapidly Deliver Exceptional Software
 DevOps - en inngang til den Digtale Transformasjon Rapidly Deliver Exceptional Software Pål Dragseth June 2015 Applications Are Changing the World of Business 84% Video US internet traffic by 2018 $142B
DevOps - en inngang til den Digtale Transformasjon Rapidly Deliver Exceptional Software Pål Dragseth June 2015 Applications Are Changing the World of Business 84% Video US internet traffic by 2018 $142B
Enterprise Computing Solutions
 Business Intelligence Data Center Cloud Mobility Enterprise Computing Solutions Security Solutions arrow.com Security Solutions Secure the integrity of your systems and data today with the one company
Business Intelligence Data Center Cloud Mobility Enterprise Computing Solutions Security Solutions arrow.com Security Solutions Secure the integrity of your systems and data today with the one company
CUTTING THROUGH THE HYPE: WHAT IS TRUE NEXT GENERATION SECURITY?
 CUTTING THROUGH THE HYPE: WHAT IS TRUE NEXT GENERATION SECURITY? Jennifer Ellard HP Session ID: SPO-W01B Session Classification: General Interest Agenda What is hype? What we hear from you? Separating
CUTTING THROUGH THE HYPE: WHAT IS TRUE NEXT GENERATION SECURITY? Jennifer Ellard HP Session ID: SPO-W01B Session Classification: General Interest Agenda What is hype? What we hear from you? Separating
