Bernard Montel Directeur Technique RSA. Copyright 2012 EMC Corporation. All rights reserved.
|
|
|
- Bernard Richard
- 8 years ago
- Views:
Transcription
1 Bernard Montel Directeur Technique RSA 1
2 RSA Security Management Compliance Vision Delivering Visibility, Intelligence and Governance 2
3 Traditional Security Is Not Working 99% of breaches led to compromise within days or less with 85% leading to data exfiltration in the same time 85% of breaches took weeks or more to discover Source: Verizon 2012 Data Breach Investigations Report 3
4 Reducing Attacker Free Time Attacker Surveillance Target Analysis Access Probe Attack Set-up System Intrusion Attack Begins Discovery/ Persistence Cover-up Starts Leap Frog Attacks Complete Cover-up Complete Maintain foothold TIME ATTACKER FREE TIME Need to collapse free time TIME Physical Security Threat Analysis Defender Discovery Attack Forecast Source: NERC HILF Report, June 2010 ( Monitoring & Controls Attack Identified Containment & Eradication Incident Reporting Impact Analysis Damage Identification Response System Reaction Recovery 4
5 Reducing Attacker Free Time Attacker Surveillance Target Analysis Access Probe Attack Set-up System Intrusion Attack Begins Discovery/ Persistence Cover-up Starts Leap Frog Attacks Complete Cover-up Complete Maintain foothold TIME ATTACKER FREE TIME Need to collapse free time TIME Physical Security Threat Analysis Attack Forecast Monitoring & Controls Attack Identified Source: NERC HILF Report, June 2010 ( Containment & Eradication Incident Reporting Impact Analysis Damage Identification Response System Reaction Recovery 5
6 Reducing Attacker Free Time System Intrusion Attack Begins Discovery/ Persistence Cover-up Starts Leap Frog Attacks Complete Cover-up Complete TIME ATTACKER FREE TIME Need to collapse free time Attack Forecast Monitoring & Controls Containment & Eradication Incident Reporting Attack Identified Source: NERC HILF Report, June 2010 ( 6
7 Security Is Becoming A Big Data Problem More determined adversary means more data needed to identify attacks More complex IT environment means even simple attacks can hide in plain sight Security professionals are struggling to keep up 1 40% of all survey respondents are overwhelmed with the security data they already collect 35% have insufficient time or expertise to analyze what they collect 1 EMA, The Rise of Data-Driven Security, Crawford, Aug 2012 Sample Size = 200 7
8 Today s Security Requirements Big Data Infrastructure Need a fast and scalable infrastructure to conduct short term and long term analysis High Powered Analytics Give me the speed and smarts to discover and investigate potential threats in near real time Comprehensive Visibility See everything happening in my environment and normalize it Integrated Intelligence Help me understand what to look for and what others have discovered 8
9 What is RSA Security Analytics? Unified platform for: Security monitoring Incident investigations Compliance reporting Brings together SIEM, Network Security Monitoring, Big Data Management & Analytics RSA Security Analytics is a new approach to combating advanced threats 9
10 RSA Security Analytics: Changing The Security Management Status Quo Unified platform for security monitoring, incident investigations and compliance reporting SIEM Compliance Reports Device XMLs Log Parsing RSA Security Analytics Fast & Powerful Analytics Network Security Monitoring Logs & Packets High Powered Analytics Intel, Business & IT Context Big Data Infrastructure Analytics Warehouse Integrated Intelligence SEE DATA YOU DIDN T SEE BEFORE, UNDERSTAND DATA YOU DIDN T EVEN CONSIDER BEFORE 10
11 Security Analytics Architecture Enrichment Data Logs Packets DISTRIBUTED COLLECTION EUROPE NORTH AMERICA ASIA REAL-TIME WAREHOUSE THE ANALYTICS Reporting and Alerting Investigation Malware Analytics Administration Complex Event Processing Free Text Search Correlation Metadata Tagging Incident Management Asset and Data Criticality Endpoint Visibility LONG-TERM RSA LIVE INTELLIGENCE Threat Intelligence Rules Parsers Alerts Feeds Apps Directory Services Reports and Custom Actions 11
12 RSA Security Analytics Architecture Long Term Analysis Log and packet Metadata, Raw Logs, Select Payload Correlation Real Time Investigations (hours à days) Metadata, Packets 12
13 Security Analytics Topology CEP = Stream Analytics Months to years Hadoop = Batch Analytics LOGS PKTS Correlation with Live in Real Time Meta, logs, select payload Decoder Long-term, intensive analysis CEP TEXT Warehouse Concentrator Real-time, high fidelity Security Analytics Experience Active Defense Remediate Days to weeks RSA Live 13
14 What Makes Security Analytics Different? Big Data Infrastructure Fast and scalable Security data warehouse plus proven NetWitness infrastructure Comprehensive Visibility See everything happening in an environment Normalizes diverse data including logs, packets and intelligence High Powered Analytics Speed and smarts to detect and investigate advanced threats Provides short term and long term analytics plus compliance Removes the hay versus digging for needles Integrated Intelligence Operationalize intelligence by fusing it with your data Understand what to look for and what others have found 14
15 Big Data Infrastructure Single platform for capturing and analyzing large amounts of network and log data Distributed, scale-out architecture Unique architecture to support both speed and smarts for threat analysis Security data warehouse for long term analytics & compliance Proven NetWitness infrastructure Session based, full reconstruction 15
16 High Powered Analytics Eliminates blind spots to achieve comprehensive visibility across the enterprise Real-time and after-the-fact investigations Uses the industry s most comprehensive and easily understandable analytical workbench Proven, patented analytics applies business context to security investigations Automates the generation of compliance reports and supports long term forensic analysis THE ANALYTICS Reporting and Alerting Investigation Malware Analytics Administration Complex Event Processing Free Text Search Correlation Metadata Tagging 16
17 The Security Analytics Warehouse WAREHOUSE Long Term Data Retention and Analysis Security data focused warehouse Packet & Log Metadata, Raw Logs, Select Payload Hadoop-based architecture for maximum scale and flexibility Complex Event Processing Google-like free text search Achieves requirements for compliance 17
18 Flexible Integration API flexibility allows RSA Security Analytics to form heart of security ecosystem Integrates with other security tools such as SIEM, IDS/IPS, firewalls, Splunk, DLP, etc. Integrate asset criticality and business context data from RSA Archer; data discover from RSA DLP Asset Criticality Open interface for access and transformation of collected data 18
19 Reimagining Security Analysis: Removing Hay vs. Digging For Needles All Network Traffic & Logs Terabytes of data 100% of total Downloads of executables Thousands of data points 5% of total Type does not match extension Hundreds of data points 0.2% of total! Create alerts to/from critical assets A few dozen alerts 19
20 Integrated Intelligence Know What To Look For RSA LIVE INTELLIGENCE SYSTEM Threat Intelligence Rules Parsers Alerts Feeds Apps Directory Services Reports and Custom Actions Gathers advanced threat intelligence and content Aggregates & consolidates data Automatically distributes correlation rules, blacklists, parsers, views, feeds OPERATIONALIZE INTELLIGENCE: Take advantage of what others have already found and apply against your current and historical data 20
21 RSA FirstWatch RSA s elite, highly trained global threat research & intelligence team Providing covert and strategic threat intelligence on advanced threats & actors Focused on threats unknown to the security community Malicious code & content analysis Threat research & ecosystem analysis Profiling threat actors Research operationalized automatically via RSA Live 21
22 Days of Investigation Completed In Hours ALERT!!... Multiple indicators to escalate a potential incident Abnormal EXE structure, crafted HTTP header, RSA Live indicates traffic coming from known malicious actor Session Recreated Privilege escalation, attempted FTP upload of documents, Other similar traffic from targeted account, other traffic from IP address PASSWORD Additional Context Incident involves highly critical server from the accounting department, data targeted includes company financials and PCI data 4 Incident Management Incident escalated, owner notified, remediation case opened, endpoint inspected 22
23 Suspect Attack Scenario: Data Ex-filtration ALERT!!... Suspect Network Traffic IP Address shows multiple connections tunneled over non-standard port Authorized User Logged in to AD AD Logs drill-down show user logged in from suspect IP with authorized credentials 1 2 PASSWORD Different user from same IP/Host logged into development test server, then the corporate file server VPN & Host logs show a different set of authorized credentials used to log into VPN and multiple internal servers 3 4 PASSWORD Data ex-filtration Encrypted ZIP file transferred out to Internet via FTP server 23
24 Only RSA Security Analytics Can Tell You The Impact Of The Attack Attack Step Traditional SIEM RSA Security Analytics Alert for access over non-standard port No Yes Recreate activity of suspect IP address across environment No Yes Show user activity across AD and VPN Yes Yes Alert for different credentials used for AD and VP Yes Yes Reconstruct exfiltrated data No Yes 24
25 Investigation Scenario Find compromised Server or Workstation acting as SPAM host Multiple outbound SMTP connections from workstation. Multiple internet DNS connections from workstation Find out how the workstation got infected User clicked on the link and got infected by Trojan from drive-by download Recreate phishing message Determine whether targeted phishing attack at play The image cannot be displayed. Your computer may not have enough memory to open the image, or the image may have been corrupted. Restart your computer, and then open the file again. If the red x still appears, you may have to delete the image and then insert it again. 3 Analyze malware Determine whether targeted or vanilla malware in use 25
26 Only RSA Security Analytics Can Tell If This Is A Targeted Attack Attack Step Traditional SIEM RSA Security Analytics Alert for suspected SPAM host Yes Yes Show all WWW requests where executable downloaded No Yes Recreate with suspect link No Yes Analyze malware and incorporate community intelligence Determine whether attack is part of a targeted campaign No No Yes Yes 26
27 Summary Traditional security is not working Security is becoming a Big Data problem RSA Security Analytics is a new approach to combating advanced threats RSA Security Analytics brings together traditional SIEM, Network Security Monitoring, Big Data Management & Analytics Key pillar to an intelligence-driven security strategy Big Data Infrastructure Comprehensive Visibility High Powered Analytics Integrated Intelligence 27
28
29 Appendix: Intros Analyst Proof Points 29
30 SIEM Needs To Evolve Into Security Analytics Volume and Variety of Data Raw data Dedicated Security Analytics Normalized Data Security Information and Event Management Platform specific data Platform-Specific Analytics (e.g., IPS & IDS) Milliseconds Seconds Minutes Hours Speed of Analysis In real time Near real time After-thefact analysis Gartner, Information Security is Becoming a Big Data Analytics Problem, Neil Macdonald, Mar. 23,
31 Context-Aware Security Intelligence: Risk-Prioritized, Actionable Insight Gartner, Information Security is Becoming a Big Data Analytics Problem, Neil Macdonald, Mar. 23,
32 SIEM Needs To Evolve Forrester, Dissect Data to Gain Actionable INTEL, Shey & Kindervag, August 9,
33 Drivers For Big Data Security Analysis 33
34 Deployment Options 34
35 Security Analytics Deployment Choices Network collection & processing Common Analytic Infrastructure Core analytic components Security Analytics Warehouse Log collection & processing Logs Packets Customers can buy Log analysis, packet analysis or both Core components for short term analytics, warehouse for longer term & more intensive analytics, or both 35
36 Security Analytics & SIEM Network collection & processing Common Analytic Infrastructure Log collection & processing Core analytic components Security Analytics Warehouse Queries Alerts Third Party SIEM Logs Packets Security Analytics Integrates with SIEM Exports alerts as logs to SIEM Executes queries from SIEM (e.g. investigate this IP) Two separate interfaces no native correlation across logs and packet data No warehouse for complex analytics 36
37 Security Analytics & envision Network collection & processing Common Analytic Infrastructure Log collection & processing Core analytic components Security Analytics Warehouse Z-Connector Log collection & processing Report Queries Logs Packets Transition allows for mixed mode deployment Logs can be forwarded to SA to take advantage of better performance and analytic firepower Capability to query envision from within SA UI for legacy data 37
38 Technical Details 38
39 Security Analytics Warehouse (SAW) SAW Proper Data Warehouse Security data focus Hadoop-based Flexible access / analysis Network metadata and Log data RSA SA reporting and full text search UI Open interface for access and transformation of collected data PIG & HIVE Modular Scale Single to hundreds to thousands of nodes Platform Advanced security analytic tools (CEP) Archive Log Compression Resiliency and high availability 39
40 Security Analytics Warehouse (SAW) Ultra Performance for more powerful analytics A cluster of 4S appliances 1U Rackspace per node Each node 20k EPS sustained collection High Capacity for archiving and less analytics A cluster of 4S appliances with DACs 4U Rackspace per node 3 node cluster retains 6000 average EPS for 2 years Each node rated to 20k EPS sustained collection 40
41 Security Analytics Preliminary Stats Processing A single Log Decoder can process 30K EPS, with peak beyond 80K EPS, double other SIEM tools 350 supported log sources Compression SA Warehouse 9:1 50% more than other SIEM tools Consumption Security Analytics Warehouse (3 compute nodes) can consume at 500K EPS...and scale up Correlation Security Analytics Warehouse Complex Event Processing (6 compute nodes) can correlate 4.5 Billion EPS and scale up Reporting Queries that took hours now takes minutes 41
42 Security Analytics Platform Options Various platform options to meet the specific needs and use cases of customers Software-only versions of these platforms are available 42
43 Taking A Closer Look Integrated Intelligence In Action: The VOHO Campaign 43
44 Benefits of Integrated Intelligence There is intelligence and there are the tools needed to make intelligence operational. RSA Security Analytics delivers both Operationalized intelligence is far greater than detached intelligence Analysts need to understand what to look for and take advantage of what others have found RSA Live integrated the best of global intelligence as well as proprietary research from RSA FirstWatch Compare intelligence with historical data to see if indicators of compromise were found Apply in real-time to defend against future attacks 44
45 The Lifecycle Of Intelligence Know What To Look For RSA LIVE INTELLIGENCE SYSTEM Threat Intelligence Rules Parsers Alerts Feeds Apps Directory Services Reports and Custom Actions 1 Intelligence gathered from global security community and RSA FirstWatch 2 Aggregated and consolidated 3 Converted into alerts, parsers, blacklists, views and correlation rules 4 Fused with your organization s data 5 Applied to current & historical data to look for matches 6 Additional intelligence gained during investigation 7 Internal intelligence, custom reports and alerts created 45
46 What Is The VOHO Campaign? Discovered in July 2012 by RSA FirstWatch Infrastructure was shared for multiple threat campaigns Trojan payload via browser-based exploits to delivers exploits to website visitors At first glance appeared to be garden variety drive by attack However, victims seemed to be geographically clustered Further research by RSA First Watch team found campaign used brand new attack approach utilizing water holing method Multistage Campaign: Redirection with a heavy dependency on JavaScript on two specific domains for majority of promulgation 46
47 VOHO Waterholing Attack Flow Who do I want to compromise? What websites do they frequent? Where can I host my malware? How do I get my victims to the watering hole Identify Target compromise hosts Identify Target Websites Create watering hole malware site Compromise Websites to redirect to watering hole 47
48 VOHO Watering Hole Leveraged Industries and Regions Sample targeted websites (redacted) hxxp:// hxxp://xxxxxxxxxcountymd.gov hxxp://xxxxxxcenter.org hxxp:/xxxxxxxpolitics.com hxxp:// Water Hole site (redacted) hxxp://xxxxxxxcurling.com 48
49 Malware Specifics Installed Variant of Gh0st RAT on compromised endpoint Gh0st is a Remote Access Tool (RAT) allowing control of compromised endpoint Typically masquerades as Symantec or MS update Exploits zero day or known vulnerability Microsoft XML Core Services CVE Java Exploit CVE
50 How did RSA FirstWatch detect this? Look for communication with blacklisted hosts Known C2 sites Known malware domains Look for suspect network traffic Gh0st or HTTPS in first 5 packets of non-rfc compliant session Use of web redirect using xkungfoo script Indicators are automatically distributed and regularly updated via RSA Live 50
51 Indicators Defined To Help Identify Attack Look for Command and Control (C2) IP addresses à Look for Control Channel IP addresses à Parser created 51
52 Intelligence Feeds Automatically Updated RSA FirstWatch feeds updated with VOHO related IP addresses and domains Users have the ability to choose which intelligence feeds to enable 52
53 Intelligence Converted Into An Operationalized Format Indicators converted into Gh0st Protocol parser Parser helps search for specific behavior within a feed Removes hay to help find needles 53
54 Examples Of Findings Parser fused with organizational data to find compromised hosts within their environment Lateral movement indicative of promulgation found via host based forensic analysis 54
55 Examples Of Findings Parser fused with organizational data to find compromised hosts within their environment Lateral movement indicative of promulgation found via host based forensic analysis 55
56 RSA Live Subscription Offering 56
57 Summary: Intelligence Driven Security In Action Operationalized intelligence is far greater than detached intelligence Analysts need to understand what to look for and take advantage of what others have found Compare intelligence with historical data to see if indicators of compromise were found Apply in real-time to defend against future attacks 57
58 Taking A Closer Look Malware Analysis 58
59 RSA Security Analytics Malware Analysis An analytical workbench that utilizes multiple analytical methods to identification and analysis of malware-based attacks, including attacks not seen before. 59
60 Malware Analysis The widest spectrum of malware-based attacks, including zeroday attacks Gain insight into attacks missed by both traditional and modern approaches to malware protection Consider all the network data and behavior to provide the full context of an attack Analyze attacks by utilizing a wide spectrum of investigation techniques Combine sandboxing, community intelligence, file content and network behavior analysis Automatically answer thousands of questions to help determine an attacker s intent, their potential targets and the level of threat they pose Increase the speed and accuracy of investigations Replicate and automate the workflow of an advanced malware analyst Save hours of work and ensure analysts focus on the most critical malware-related events 60
61 Malware Analysis Multiple analytical methods in one tool Likely Zero-Day Static Analysis Network Analysis Sandbox Analysis Likely Sandbox Aware Malware Community Highly Likely Malware 61
62 Replicate & Automate Advanced Analyst Workflow NETWORK Ask Hundreds of Questions About the Originating and Related Network Sessions Recursive and Referring Session Analysis Examples: Country of Origin, Time of Day, Size of Content, Referring Site, TLD and Country Match, JavaScript / Obfuscation, PDF Executable, Alerts present, Streaming Analysis of the Content, intelligence indicators, etc.. STATIC Inspection for Signs of Malicious Code Static file content malware analysis Size, Meta Tags, Cleaned, Packed, Obfuscated, etc.. COMMUNITY Community-based review by intelligence and reputation partners Extensible list of SaaS intelligence and whitelist partners Virus checking-providers, internet-based intelligence, known good/bad SANDBOX Local and cloud dynamic analysis Out-of-the-box integration with industry leading dynamic malware analysis sandbox On premise and cloud-based dynamic analysis modules 62
63 RSA Archer & DLP Integrations Enabling Business Context and Advanced Incident Management for RSA Security Analytics 63
64 What is ACI and AIMS? RSA Security Analytics Reports, Alerts Investigations Intelligence Logs, Packets ACI Business Context AIMS Incident Management Asset Details Workflows RSA Archer Asset Criticality Intelligence (ACI) q Business Context to Security Analysts to Prioritize Investigations Advanced Incident Management for Security (AIMS) q Automate incident management workflow, effectively track progress and engage key business stakeholders 64
65 Asset Criticality Intelligence Overview Asset Intelligence ü IP Address IT Info Biz Context RSA ACI ü Criticality Rating ü Business Unit ü Facility Asset List Device Owner Device Type Business Owner Device IDs Business Unit Criticality Rating RSA Security Analytics Content (DLP) Category IP/MAC Add Process RPO / RTO Security analysts now have asset intelligence and business context to better analyze and prioritize alerts. CMDBs, DLP scans, etc. 65
66 Asset Criticality Intelligence in Security Analytics Helps analyst better understand risk To prioritize investigation & response Asset criticality represented as metadata 66
67 RSA AIMS Overview Advanced Incident Management for Security Business & Security Users RSA Security Analytics RSA AIMS Capture & Analyze NW Packets, Logs & Threat Feeds Alerts Based on Rules Group Alerts Manage Workflows Provide Visibility 67
68 Advanced Incident Management Offload response from security analyst Enhances management visibility Accelerates remediation Manage entire incident lifecycle 68
69 RSA Data Discovery for Security Analytics Discover sensitive data & improve investigations with DLP SharePoint File Servers Databases RSA Data Discovery Data Discovery Feed NAS/SAN Endpoints RSA Security Analytics Content-level Intelligence Security Analyst 69
70 RSA Data Discovery for Security Analytics Investigative Interface Data Discovery attributes available in SA Investigation UI help Security Analysts identify high risk assets and prioritize investigations 70
71 Endpoint Visibility RSA Security Analytics and RSA ECAT 71
72 Introducing RSA ECAT RSA ECAT ECAT= Enterprise Compromise Assessment Tool Detect, Analyze & Respond to advanced malware on endpoints Signature-less malware detection In-depth endpoint visibility Gain actionable intelligence for rapid breach detection Increase SOC/CIRC Efficiency 72
73 RSA ECAT: Use Cases Incident Response Assessments Monitoring Ongoing Monitoring & Alerting Deploy & Scan Automate detection of malware across hosts Assess & Investigate Remediate 73
74 How RSA ECAT Works Agent Supports Windows, 32/64-bit Full system inventory Identify all executables, DLL s and drivers Agent status via UDP, full report via SSL Server Up to 5K agents Scan report 0.5MB on the wire Unknown files sent to repository, scanned and analyzed Global repository of scan results ECAT Server 74
75 RSA ECAT Key Functionality & Benefits File Whitelisting Multi-engine AV scan Certificate Validation Network Traffic analysis Full System Inventory Direct physical disk inspection Live Memory Analysis X-ray view of what s happening on endpoints Identify behavior related to malware Highlight likely infections with Machine Suspect Level (MSL) Quickly triage results to gain actionable intelligence Find other infected machines & gauge scope of breach Forensic data gathering 75
76 Complete Endpoint & Network Visibility RSA ECAT & RSA Security Analytics RSA Security Analytics Capture & Analyze NW Packets, Logs & Threat Feeds Syslog alert of high Machine Suspect Levels RSA ECAT Directly query SA from ECAT Advanced threat detection on endpoints Complete network and endpoint visibility Faster investigations to shorten attacker dwell time Detect suspicious endpoint activity 76
77 Incident Response 1 RSA Security Analytics Deploy and Scan RSA ECAT agent deployed to machine to conduct in-depth scan 2 Alert about suspicious network traffic - Beaconing, connection to known bad IP address, etc. Assess & Investigate Analyst assesses results in ECAT console to determine if the machine is infected 3 4 Remediation Reimage machine or use agent to clean 77
78 Proactive Assessments 1? Deploy and Scan RSA ECAT agent deployed to machine to conduct in-depth scan 2 Identify High-risk Assets - Executive laptops, R&D or IT endpoints, Critical servers, etc. Assess & Investigate Analyst assesses results in ECAT console to determine if the machine is infected 3 4 Remediation Reimage machine or use agent to clean 78
79
Using Network Forensics to Visualize Advanced Persistent Threats
 Using Network Forensics to Visualize Advanced Persistent Threats Dale Long, Sr. Technology Consultant, RSA Security 1 The Problem 2 Traditional Security Is Not Working 99% of breaches led to compromise
Using Network Forensics to Visualize Advanced Persistent Threats Dale Long, Sr. Technology Consultant, RSA Security 1 The Problem 2 Traditional Security Is Not Working 99% of breaches led to compromise
Advanced SOC Design. Next Generation Security Operations. Shane Harsch Senior Solutions Principal, MBA GCED CISSP RSA
 Advanced SOC Design Next Generation Security Operations Shane Harsch Senior Solutions Principal, MBA GCED CISSP RSA 1 ! Why/How security investments need to shift! Key functions of a Security Operations
Advanced SOC Design Next Generation Security Operations Shane Harsch Senior Solutions Principal, MBA GCED CISSP RSA 1 ! Why/How security investments need to shift! Key functions of a Security Operations
Joining Forces: Bringing Big Data to your Security Team
 Joining Forces: Bringing Big Data to your Security Team Alaa Abdulnabi, CISSP RSA Regional Pre-Sales Manager Turkey, Middle East & Africa @AlaaAbdulnabi 1 Facteurs de mutation du marché Appareils mobiles
Joining Forces: Bringing Big Data to your Security Team Alaa Abdulnabi, CISSP RSA Regional Pre-Sales Manager Turkey, Middle East & Africa @AlaaAbdulnabi 1 Facteurs de mutation du marché Appareils mobiles
RSA Security Anatomy of an Attack Lessons learned
 RSA Security Anatomy of an Attack Lessons learned Malcolm Dundas Account Executive John Hurley Senior Technology Consultant 1 Agenda Advanced Enterprise/ Threats The RSA Breach A chronology of the attack
RSA Security Anatomy of an Attack Lessons learned Malcolm Dundas Account Executive John Hurley Senior Technology Consultant 1 Agenda Advanced Enterprise/ Threats The RSA Breach A chronology of the attack
Getting Ahead of Advanced Threats
 Getting Ahead of Advanced Threats Advanced Security Solutions for Trusted IT Chezki Gil Territory Manager Israel & Greece 1 Threats are Evolving Rapidly Criminals Petty criminal s Unsophisticated Organized
Getting Ahead of Advanced Threats Advanced Security Solutions for Trusted IT Chezki Gil Territory Manager Israel & Greece 1 Threats are Evolving Rapidly Criminals Petty criminal s Unsophisticated Organized
Security Analytics for Smart Grid
 Security Analytics for Smart Grid Dr. Robert W. Griffin Chief Security Architect RSA, the Security Division of EMC robert.griffin@rsa.com blogs.rsa.com/author/griffin @RobtWesGriffin 1 No Shortage of Hard
Security Analytics for Smart Grid Dr. Robert W. Griffin Chief Security Architect RSA, the Security Division of EMC robert.griffin@rsa.com blogs.rsa.com/author/griffin @RobtWesGriffin 1 No Shortage of Hard
RSA Security Analytics
 RSA Security Analytics This is what SIEM was Meant to Be 1 The Original Intent of SIEM Single compliance & security interface Compliance yes, but security? Analyze & prioritize alerts across various sources
RSA Security Analytics This is what SIEM was Meant to Be 1 The Original Intent of SIEM Single compliance & security interface Compliance yes, but security? Analyze & prioritize alerts across various sources
Detect & Investigate Threats. OVERVIEW
 Detect & Investigate Threats. OVERVIEW HIGHLIGHTS Introducing RSA Security Analytics, Providing: Security monitoring Incident investigation Compliance reporting Providing Big Data Security Analytics Enterprise-wide
Detect & Investigate Threats. OVERVIEW HIGHLIGHTS Introducing RSA Security Analytics, Providing: Security monitoring Incident investigation Compliance reporting Providing Big Data Security Analytics Enterprise-wide
Discover & Investigate Advanced Threats. OVERVIEW
 Discover & Investigate Advanced Threats. OVERVIEW HIGHLIGHTS Introducing RSA Security Analytics, Providing: Security monitoring Incident investigation Compliance reporting Providing Big Data Security Analytics
Discover & Investigate Advanced Threats. OVERVIEW HIGHLIGHTS Introducing RSA Security Analytics, Providing: Security monitoring Incident investigation Compliance reporting Providing Big Data Security Analytics
場 次 :C-3 公 司 名 稱 :RSA, The Security Division of EMC 主 題 : 如 何 應 用 網 路 封 包 分 析 對 付 資 安 威 脅 主 講 人 :Jerry.Huang@rsa.com Sr. Technology Consultant GCR
 場 次 :C-3 公 司 名 稱 :RSA, The Security Division of EMC 主 題 : 如 何 應 用 網 路 封 包 分 析 對 付 資 安 威 脅 主 講 人 :Jerry.Huang@rsa.com Sr. Technology Consultant GCR Minimum Requirements of Security Management and Compliance
場 次 :C-3 公 司 名 稱 :RSA, The Security Division of EMC 主 題 : 如 何 應 用 網 路 封 包 分 析 對 付 資 安 威 脅 主 講 人 :Jerry.Huang@rsa.com Sr. Technology Consultant GCR Minimum Requirements of Security Management and Compliance
BIG DATA. Shaun McLagan General Manager, RSA Australia and New Zealand CHANGING THE REALM OF POSSIBILITY IN SECURITY
 BIG DATA CHANGING THE REALM OF POSSIBILITY IN SECURITY Shaun McLagan General Manager, RSA Australia and New Zealand 1 Things have changed #2 Buzz word 2012 Big Data only behind something called Fiscal
BIG DATA CHANGING THE REALM OF POSSIBILITY IN SECURITY Shaun McLagan General Manager, RSA Australia and New Zealand 1 Things have changed #2 Buzz word 2012 Big Data only behind something called Fiscal
Comprehensive Advanced Threat Defense
 1 Comprehensive Advanced Threat Defense June 2014 PAGE 1 PAGE 1 1 INTRODUCTION The hot topic in the information security industry these days is Advanced Threat Defense (ATD). There are many definitions,
1 Comprehensive Advanced Threat Defense June 2014 PAGE 1 PAGE 1 1 INTRODUCTION The hot topic in the information security industry these days is Advanced Threat Defense (ATD). There are many definitions,
Unified Security, ATP and more
 SYMANTEC Unified Security, ATP and more TAKE THE NEXT STEP Martin Werner PreSales Consultant, Symantec Switzerland AG MEET SWISS INFOSEC! 27.01.2016 Unified Security 2 Symantec Enterprise Security Users
SYMANTEC Unified Security, ATP and more TAKE THE NEXT STEP Martin Werner PreSales Consultant, Symantec Switzerland AG MEET SWISS INFOSEC! 27.01.2016 Unified Security 2 Symantec Enterprise Security Users
The session is about to commence. Please switch your phone to silent!
 The session is about to commence. Please switch your phone to silent! 1 Defend with Confidence Against Advanced Threats Nicholas Chia SE Manager, SEA RSA 2 TRUST? Years to earn, seconds to break 3 Market
The session is about to commence. Please switch your phone to silent! 1 Defend with Confidence Against Advanced Threats Nicholas Chia SE Manager, SEA RSA 2 TRUST? Years to earn, seconds to break 3 Market
CHANGING THE SECURITY MONITORING STATUS QUO Solving SIEM problems with RSA Security Analytics
 CHANGING THE SECURITY MONITORING STATUS QUO Solving SIEM problems with RSA Security Analytics TRADITIONAL SIEMS ARE SHOWING THEIR AGE Security Information and Event Management (SIEM) tools have been a
CHANGING THE SECURITY MONITORING STATUS QUO Solving SIEM problems with RSA Security Analytics TRADITIONAL SIEMS ARE SHOWING THEIR AGE Security Information and Event Management (SIEM) tools have been a
Advanced Persistent Threats
 Advanced Persistent Threats Craig Harwood Channel Manager SADC and Indian Ocean Islands 1 Agenda Introduction Today s Threat landscape What is an Advance persistent Threat How are these crimes perpetrated
Advanced Persistent Threats Craig Harwood Channel Manager SADC and Indian Ocean Islands 1 Agenda Introduction Today s Threat landscape What is an Advance persistent Threat How are these crimes perpetrated
Advanced Threats: The New World Order
 Advanced Threats: The New World Order Gary Lau Technology Consulting Manager Greater China gary.lau@rsa.com 1 Agenda Change of Threat Landscape and Business Impact Case Sharing Korean Incidents EMC CIRC
Advanced Threats: The New World Order Gary Lau Technology Consulting Manager Greater China gary.lau@rsa.com 1 Agenda Change of Threat Landscape and Business Impact Case Sharing Korean Incidents EMC CIRC
Rashmi Knowles Chief Security Architect EMEA
 Rashmi Knowles Chief Security Architect EMEA AGENDA Transformation of IT New cyber-security challenges Intelligence Driven Security Security Analytics Q&A 2 ENTERPRISE DATA CENTER ADVANCED SECURITY A UNIQUE
Rashmi Knowles Chief Security Architect EMEA AGENDA Transformation of IT New cyber-security challenges Intelligence Driven Security Security Analytics Q&A 2 ENTERPRISE DATA CENTER ADVANCED SECURITY A UNIQUE
BREAKING THE KILL CHAIN AN EARLY WARNING SYSTEM FOR ADVANCED THREAT
 BREAKING THE KILL CHAIN AN EARLY WARNING SYSTEM FOR ADVANCED THREAT Rashmi Knowles RSA, The Security Division of EMC Session ID: Session Classification: SPO-W07 Intermediate APT1 maintained access to
BREAKING THE KILL CHAIN AN EARLY WARNING SYSTEM FOR ADVANCED THREAT Rashmi Knowles RSA, The Security Division of EMC Session ID: Session Classification: SPO-W07 Intermediate APT1 maintained access to
The Next Generation Security Operations Center
 The Next Generation Security Operations Center Vassil Barsakov Regional Manager, CEE & CIS RSA, the Security Division of EMC 1 Threats are Evolving Rapidly Criminals Petty criminals Unsophisticated Organized
The Next Generation Security Operations Center Vassil Barsakov Regional Manager, CEE & CIS RSA, the Security Division of EMC 1 Threats are Evolving Rapidly Criminals Petty criminals Unsophisticated Organized
RSA Security Analytics the complete approach to security monitoring or how to approach advanced threats
 RSA Security Analytics the complete approach to security monitoring or how to approach advanced threats Grzegorz Mucha grzegorz.mucha@rsa.com Advanced Threats Threat Landscape Criminals Petty criminals
RSA Security Analytics the complete approach to security monitoring or how to approach advanced threats Grzegorz Mucha grzegorz.mucha@rsa.com Advanced Threats Threat Landscape Criminals Petty criminals
The Future of the Advanced SOC
 The Future of the Advanced SOC Developing a platform for more effective security management and compliance Steven Van Ormer RSA Technical Security Consultant 1 Agenda Today s Security Landscape and Why
The Future of the Advanced SOC Developing a platform for more effective security management and compliance Steven Van Ormer RSA Technical Security Consultant 1 Agenda Today s Security Landscape and Why
After the Attack. The Transformation of EMC Security Operations
 After the Attack The Transformation of EMC Security Operations Thomas Wood Senior Systems Engineer, GSNA CISSP RSA, The Security Division of EMC Thomas.WoodJr@rsa.com 1 Agenda Review 2011 Attack on RSA
After the Attack The Transformation of EMC Security Operations Thomas Wood Senior Systems Engineer, GSNA CISSP RSA, The Security Division of EMC Thomas.WoodJr@rsa.com 1 Agenda Review 2011 Attack on RSA
What s New in Security Analytics 10.4. Be the Hunter.. Not the Hunted
 What s New in Security Analytics 10.4 Be the Hunter.. Not the Hunted Attackers Are Outpacing Detection Attacker Capabilities Time To Discovery Source: VERIZON 2014 DATA BREACH INVESTIGATIONS REPORT 2 TRANSFORM
What s New in Security Analytics 10.4 Be the Hunter.. Not the Hunted Attackers Are Outpacing Detection Attacker Capabilities Time To Discovery Source: VERIZON 2014 DATA BREACH INVESTIGATIONS REPORT 2 TRANSFORM
IBM Security Strategy
 IBM Security Strategy Intelligence, Integration and Expertise Kate Scarcella CISSP Security Tiger Team Executive M.S. Information Security IBM Security Systems IBM Security: Delivering intelligence, integration
IBM Security Strategy Intelligence, Integration and Expertise Kate Scarcella CISSP Security Tiger Team Executive M.S. Information Security IBM Security Systems IBM Security: Delivering intelligence, integration
with Managing RSA the Lifecycle of Key Manager RSA Streamlining Security Operations Data Loss Prevention Solutions RSA Solution Brief
 RSA Solution Brief Streamlining Security Operations with Managing RSA the Lifecycle of Data Loss Prevention and Encryption RSA envision Keys with Solutions RSA Key Manager RSA Solution Brief 1 Who is asking
RSA Solution Brief Streamlining Security Operations with Managing RSA the Lifecycle of Data Loss Prevention and Encryption RSA envision Keys with Solutions RSA Key Manager RSA Solution Brief 1 Who is asking
DRIVE-BY DOWNLOAD WHAT IS DRIVE-BY DOWNLOAD? A Typical Attack Scenario
 DRIVE-BY DOWNLOAD WHAT IS DRIVE-BY DOWNLOAD? Drive-by Downloads are a common technique used by attackers to silently install malware on a victim s computer. Once a target website has been weaponized with
DRIVE-BY DOWNLOAD WHAT IS DRIVE-BY DOWNLOAD? Drive-by Downloads are a common technique used by attackers to silently install malware on a victim s computer. Once a target website has been weaponized with
Achieving Actionable Situational Awareness... McAfee ESM. Ad Quist, Sales Engineer NEEUR
 Achieving Actionable Situational Awareness... McAfee ESM Ad Quist, Sales Engineer NEEUR The Old SECURITY Model Is BROKEN 2 Advanced Targeted Attacks The Reality ADVANCED TARGETED ATTACKS COMPROMISE TO
Achieving Actionable Situational Awareness... McAfee ESM Ad Quist, Sales Engineer NEEUR The Old SECURITY Model Is BROKEN 2 Advanced Targeted Attacks The Reality ADVANCED TARGETED ATTACKS COMPROMISE TO
You ll learn about our roadmap across the Symantec email and gateway security offerings.
 #SymVisionEmea In this session you will hear how Symantec continues to focus our comprehensive security expertise, global intelligence and portfolio on giving organizations proactive, targeted attack protection
#SymVisionEmea In this session you will hear how Symantec continues to focus our comprehensive security expertise, global intelligence and portfolio on giving organizations proactive, targeted attack protection
Analyzing HTTP/HTTPS Traffic Logs
 Advanced Threat Protection Automatic Traffic Log Analysis APTs, advanced malware and zero-day attacks are designed to evade conventional perimeter security defenses. Today, there is wide agreement that
Advanced Threat Protection Automatic Traffic Log Analysis APTs, advanced malware and zero-day attacks are designed to evade conventional perimeter security defenses. Today, there is wide agreement that
Defending Against Cyber Attacks with SessionLevel Network Security
 Defending Against Cyber Attacks with SessionLevel Network Security May 2010 PAGE 1 PAGE 1 Executive Summary Threat actors are determinedly focused on the theft / exfiltration of protected or sensitive
Defending Against Cyber Attacks with SessionLevel Network Security May 2010 PAGE 1 PAGE 1 Executive Summary Threat actors are determinedly focused on the theft / exfiltration of protected or sensitive
Trend Micro Cloud App Security for Office 365. October 27, 2015 Trevor Richmond
 Trend Micro Cloud App Security for Office 365 October 27, 2015 Trevor Richmond Too many malware incidents >90% Targeted Attacks Start with Email Attackers: Target specific companies or individuals Research
Trend Micro Cloud App Security for Office 365 October 27, 2015 Trevor Richmond Too many malware incidents >90% Targeted Attacks Start with Email Attackers: Target specific companies or individuals Research
IMPLEMENTING A SECURITY ANALYTICS ARCHITECTURE
 IMPLEMENTING A SECURITY ANALYTICS ARCHITECTURE Solution Brief SUMMARY New security threats demand a new approach to security management. Security teams need a security analytics architecture that can handle
IMPLEMENTING A SECURITY ANALYTICS ARCHITECTURE Solution Brief SUMMARY New security threats demand a new approach to security management. Security teams need a security analytics architecture that can handle
Stop the Maelstrom: Using Endpoint Sensor Data in a SIEM to Isolate Threats
 Stop the Maelstrom: Using Endpoint Sensor Data in a SIEM to Isolate Threats Jody C. Patilla The Johns Hopkins University Session ID: TECH-107 Session Classification: Intermediate Objectives Get more out
Stop the Maelstrom: Using Endpoint Sensor Data in a SIEM to Isolate Threats Jody C. Patilla The Johns Hopkins University Session ID: TECH-107 Session Classification: Intermediate Objectives Get more out
A New Perspective on Protecting Critical Networks from Attack:
 Whitepaper A New Perspective on Protecting Critical Networks from Attack: Why the DoD Uses Advanced Network-traffic Analytics to Secure its Network 2014: A Year of Mega Breaches A Ponemon Study published
Whitepaper A New Perspective on Protecting Critical Networks from Attack: Why the DoD Uses Advanced Network-traffic Analytics to Secure its Network 2014: A Year of Mega Breaches A Ponemon Study published
ADVANCED THREATS IN THE ENTERPRISE. Finding an Evil in the Haystack with RSA ECAT. White Paper
 ADVANCED THREATS IN THE ENTERPRISE Finding an Evil in the Haystack with RSA ECAT White Paper With thousands of workstations and servers under management, most enterprises have no way to effectively make
ADVANCED THREATS IN THE ENTERPRISE Finding an Evil in the Haystack with RSA ECAT White Paper With thousands of workstations and servers under management, most enterprises have no way to effectively make
Advanced Visibility. Moving Beyond a Log Centric View. Matthew Gardiner, RSA & Richard Nichols, RSA
 Advanced Visibility Moving Beyond a Log Centric View Matthew Gardiner, RSA & Richard Nichols, RSA 1 Security is getting measurability worse Percent of breaches where time to compromise (red)/time to Discovery
Advanced Visibility Moving Beyond a Log Centric View Matthew Gardiner, RSA & Richard Nichols, RSA 1 Security is getting measurability worse Percent of breaches where time to compromise (red)/time to Discovery
WHITE PAPER Cloud-Based, Automated Breach Detection. The Seculert Platform
 WHITE PAPER Cloud-Based, Automated Breach Detection The Seculert Platform Table of Contents Introduction 3 Automatic Traffic Log Analysis 4 Elastic Sandbox 5 Botnet Interception 7 Speed and Precision 9
WHITE PAPER Cloud-Based, Automated Breach Detection The Seculert Platform Table of Contents Introduction 3 Automatic Traffic Log Analysis 4 Elastic Sandbox 5 Botnet Interception 7 Speed and Precision 9
REVOLUTIONIZING ADVANCED THREAT PROTECTION
 REVOLUTIONIZING ADVANCED THREAT PROTECTION A NEW, MODERN APPROACH Blue Coat Advanced Threat Protection Group GRANT ASPLUND Senior Technology Evangelist 1 WHY DO I STAND ON MY DESK? "...I stand upon my
REVOLUTIONIZING ADVANCED THREAT PROTECTION A NEW, MODERN APPROACH Blue Coat Advanced Threat Protection Group GRANT ASPLUND Senior Technology Evangelist 1 WHY DO I STAND ON MY DESK? "...I stand upon my
RSA Enterprise Compromise Assessment Tool (ECAT) Date: January 2014 Authors: Jon Oltsik, Senior Principal Analyst and Tony Palmer, Senior Lab Analyst
 ESG Lab Review RSA Enterprise Compromise Assessment Tool (ECAT) Date: January 2014 Authors: Jon Oltsik, Senior Principal Analyst and Tony Palmer, Senior Lab Analyst Abstract: This ESG Lab review documents
ESG Lab Review RSA Enterprise Compromise Assessment Tool (ECAT) Date: January 2014 Authors: Jon Oltsik, Senior Principal Analyst and Tony Palmer, Senior Lab Analyst Abstract: This ESG Lab review documents
SECURITY ANALYTICS MOVES TO REAL-TIME PROTECTION
 SECURITY ANALYTICS MOVES TO REAL-TIME PROTECTION How ThreatBLADES add real-time threat scanning and alerting to the Analytics Platform INTRODUCTION: analytics solutions have become an essential weapon
SECURITY ANALYTICS MOVES TO REAL-TIME PROTECTION How ThreatBLADES add real-time threat scanning and alerting to the Analytics Platform INTRODUCTION: analytics solutions have become an essential weapon
Ovation Security Center Data Sheet
 Features Scans for vulnerabilities Discovers assets Deploys security patches transparently Allows only white-listed applications to run in workstations Provides virus protection for Ovation Windows workstations
Features Scans for vulnerabilities Discovers assets Deploys security patches transparently Allows only white-listed applications to run in workstations Provides virus protection for Ovation Windows workstations
Palo Alto Networks and Splunk: Combining Next-generation Solutions to Defeat Advanced Threats
 Palo Alto Networks and Splunk: Combining Next-generation Solutions to Defeat Advanced Threats Executive Summary Palo Alto Networks strategic partnership with Splunk brings the power of our next generation
Palo Alto Networks and Splunk: Combining Next-generation Solutions to Defeat Advanced Threats Executive Summary Palo Alto Networks strategic partnership with Splunk brings the power of our next generation
Mucho Big Data y La Seguridad para cuándo?
 Mucho Big Data y La Seguridad para cuándo? Juan Carlos Vázquez Sales Systems Engineer, LTAM mayo 9, 2013 Agenda Business Drivers Big Security Data GTI Integration SIEM Architecture & Offering Why McAfee
Mucho Big Data y La Seguridad para cuándo? Juan Carlos Vázquez Sales Systems Engineer, LTAM mayo 9, 2013 Agenda Business Drivers Big Security Data GTI Integration SIEM Architecture & Offering Why McAfee
Cisco Advanced Malware Protection for Endpoints
 Data Sheet Cisco Advanced Malware Protection for Endpoints Product Overview With today s sophisticated malware, you have to protect endpoints before, during, and after attacks. Cisco Advanced Malware Protection
Data Sheet Cisco Advanced Malware Protection for Endpoints Product Overview With today s sophisticated malware, you have to protect endpoints before, during, and after attacks. Cisco Advanced Malware Protection
Combating a new generation of cybercriminal with in-depth security monitoring. 1 st Advanced Data Analysis Security Operation Center
 Combating a new generation of cybercriminal with in-depth security monitoring 1 st Advanced Data Analysis Security Operation Center The Challenge Don t leave your systems unmonitored. It takes an average
Combating a new generation of cybercriminal with in-depth security monitoring 1 st Advanced Data Analysis Security Operation Center The Challenge Don t leave your systems unmonitored. It takes an average
WHITE PAPER SPLUNK SOFTWARE AS A SIEM
 SPLUNK SOFTWARE AS A SIEM Improve your security posture by using Splunk as your SIEM HIGHLIGHTS Splunk software can be used to operate security operations centers (SOC) of any size (large, med, small)
SPLUNK SOFTWARE AS A SIEM Improve your security posture by using Splunk as your SIEM HIGHLIGHTS Splunk software can be used to operate security operations centers (SOC) of any size (large, med, small)
Ovation Security Center Data Sheet
 Features Scans for vulnerabilities Discovers assets Deploys security patches easily Allows only white-listed applications in workstations to run Provides virus protection for Ovation Windows stations Aggregates,
Features Scans for vulnerabilities Discovers assets Deploys security patches easily Allows only white-listed applications in workstations to run Provides virus protection for Ovation Windows stations Aggregates,
The Advanced Attack Challenge. Creating a Government Private Threat Intelligence Cloud
 The Advanced Attack Challenge Creating a Government Private Threat Intelligence Cloud The Advanced Attack Challenge One of the most prominent and advanced threats to government networks is advanced delivery
The Advanced Attack Challenge Creating a Government Private Threat Intelligence Cloud The Advanced Attack Challenge One of the most prominent and advanced threats to government networks is advanced delivery
High End Information Security Services
 High End Information Security Services Welcome Trion Logics Security Solutions was established after understanding the market's need for a high end - End to end security integration and consulting company.
High End Information Security Services Welcome Trion Logics Security Solutions was established after understanding the market's need for a high end - End to end security integration and consulting company.
GETTING REAL ABOUT SECURITY MANAGEMENT AND "BIG DATA"
 GETTING REAL ABOUT SECURITY MANAGEMENT AND "BIG DATA" A Roadmap for "Big Data" in Security Analytics ESSENTIALS This paper examines: Escalating complexity of the security management environment, from threats
GETTING REAL ABOUT SECURITY MANAGEMENT AND "BIG DATA" A Roadmap for "Big Data" in Security Analytics ESSENTIALS This paper examines: Escalating complexity of the security management environment, from threats
DYNAMIC DNS: DATA EXFILTRATION
 DYNAMIC DNS: DATA EXFILTRATION RSA Visibility Reconnaissance Weaponization Delivery Exploitation Installation C2 Action WHAT IS DATA EXFILTRATION? One of the most common goals of malicious actors is to
DYNAMIC DNS: DATA EXFILTRATION RSA Visibility Reconnaissance Weaponization Delivery Exploitation Installation C2 Action WHAT IS DATA EXFILTRATION? One of the most common goals of malicious actors is to
Combating a new generation of cybercriminal with in-depth security monitoring
 Cybersecurity Services Combating a new generation of cybercriminal with in-depth security monitoring 1 st Advanced Data Analysis Security Operation Center The Challenge Don t leave your systems unmonitored.
Cybersecurity Services Combating a new generation of cybercriminal with in-depth security monitoring 1 st Advanced Data Analysis Security Operation Center The Challenge Don t leave your systems unmonitored.
Cisco Advanced Malware Protection
 Solution Overview Cisco Advanced Malware Protection Breach Prevention, Detection, Response, and Remediation for the Real World BENEFITS Gain unmatched global threat intelligence to strengthen front-line
Solution Overview Cisco Advanced Malware Protection Breach Prevention, Detection, Response, and Remediation for the Real World BENEFITS Gain unmatched global threat intelligence to strengthen front-line
Cloud Security Primer MALICIOUS NETWORK COMMUNICATIONS: WHAT ARE YOU OVERLOOKING?
 A Cloud Security Primer : WHAT ARE YOU OVERLOOKING? LEGAL DISCLAIMER The information provided herein is for general information and educational purposes only. It is not intended and should not be construed
A Cloud Security Primer : WHAT ARE YOU OVERLOOKING? LEGAL DISCLAIMER The information provided herein is for general information and educational purposes only. It is not intended and should not be construed
CONTINUOUS DIAGNOSTICS BEGINS WITH REDSEAL
 CONTINUOUS DIAGNOSTICS BEGINS WITH REDSEAL WHAT IS CDM? The continuous stream of high profile cybersecurity breaches demonstrates the need to move beyond purely periodic, compliance-based approaches to
CONTINUOUS DIAGNOSTICS BEGINS WITH REDSEAL WHAT IS CDM? The continuous stream of high profile cybersecurity breaches demonstrates the need to move beyond purely periodic, compliance-based approaches to
RSA Security Analytics Security Analytics System Overview
 RSA Security Analytics Security Analytics System Overview Copyright 2010-2015 RSA, the Security Division of EMC. All rights reserved. Trademarks RSA, the RSA Logo and EMC are either registered trademarks
RSA Security Analytics Security Analytics System Overview Copyright 2010-2015 RSA, the Security Division of EMC. All rights reserved. Trademarks RSA, the RSA Logo and EMC are either registered trademarks
INCREASINGLY, ORGANIZATIONS ARE ASKING WHAT CAN T GO TO THE CLOUD, RATHER THAN WHAT CAN. Albin Penič Technical Team Leader Eastern Europe
 INCREASINGLY, ORGANIZATIONS ARE ASKING WHAT CAN T GO TO THE CLOUD, RATHER THAN WHAT CAN Albin Penič Technical Team Leader Eastern Europe Trend Micro 27 years focused on security software Headquartered
INCREASINGLY, ORGANIZATIONS ARE ASKING WHAT CAN T GO TO THE CLOUD, RATHER THAN WHAT CAN Albin Penič Technical Team Leader Eastern Europe Trend Micro 27 years focused on security software Headquartered
Fighting Advanced Threats
 Fighting Advanced Threats With FortiOS 5 Introduction In recent years, cybercriminals have repeatedly demonstrated the ability to circumvent network security and cause significant damages to enterprises.
Fighting Advanced Threats With FortiOS 5 Introduction In recent years, cybercriminals have repeatedly demonstrated the ability to circumvent network security and cause significant damages to enterprises.
Advanced Threat Protection with Dell SecureWorks Security Services
 Advanced Threat Protection with Dell SecureWorks Security Services Table of Contents Summary... 2 What are Advanced Threats?... 3 How do advanced threat actors operate?... 3 Addressing the Threat... 5
Advanced Threat Protection with Dell SecureWorks Security Services Table of Contents Summary... 2 What are Advanced Threats?... 3 How do advanced threat actors operate?... 3 Addressing the Threat... 5
Bridging the gap between COTS tool alerting and raw data analysis
 Article Bridging the gap between COTS tool alerting and raw data analysis An article on how the use of metadata in cybersecurity solutions raises the situational awareness of network activity, leading
Article Bridging the gap between COTS tool alerting and raw data analysis An article on how the use of metadata in cybersecurity solutions raises the situational awareness of network activity, leading
Endpoint Threat Detection without the Pain
 WHITEPAPER Endpoint Threat Detection without the Pain Contents Motivated Adversaries, Too Many Alerts, Not Enough Actionable Information: Incident Response is Getting Harder... 1 A New Solution, with a
WHITEPAPER Endpoint Threat Detection without the Pain Contents Motivated Adversaries, Too Many Alerts, Not Enough Actionable Information: Incident Response is Getting Harder... 1 A New Solution, with a
Cautela Labs Cloud Agile. Secured. Threat Management Security Solutions at Work
 Cautela Labs Cloud Agile. Secured. Threat Management Security Solutions at Work Security concerns and dangers come both from internal means as well as external. In order to enhance your security posture
Cautela Labs Cloud Agile. Secured. Threat Management Security Solutions at Work Security concerns and dangers come both from internal means as well as external. In order to enhance your security posture
SIEM Optimization 101. ReliaQuest E-Book Fully Integrated and Optimized IT Security
 SIEM Optimization 101 ReliaQuest E-Book Fully Integrated and Optimized IT Security Introduction SIEM solutions are effective security measures that mitigate security breaches and increase the awareness
SIEM Optimization 101 ReliaQuest E-Book Fully Integrated and Optimized IT Security Introduction SIEM solutions are effective security measures that mitigate security breaches and increase the awareness
The SIEM Evaluator s Guide
 Using SIEM for Compliance, Threat Management, & Incident Response Security information and event management (SIEM) tools are designed to collect, store, analyze, and report on log data for threat detection,
Using SIEM for Compliance, Threat Management, & Incident Response Security information and event management (SIEM) tools are designed to collect, store, analyze, and report on log data for threat detection,
End-user Security Analytics Strengthens Protection with ArcSight
 Case Study for XY Bank End-user Security Analytics Strengthens Protection with ArcSight INTRODUCTION Detect and respond to advanced persistent threats (APT) in real-time with Nexthink End-user Security
Case Study for XY Bank End-user Security Analytics Strengthens Protection with ArcSight INTRODUCTION Detect and respond to advanced persistent threats (APT) in real-time with Nexthink End-user Security
Cisco Advanced Malware Protection for Endpoints
 Data Sheet Cisco Advanced Malware Protection for Endpoints Product Overview With today s sophisticated malware, you have to protect endpoints before, during, and after attacks. Cisco Advanced Malware Protection
Data Sheet Cisco Advanced Malware Protection for Endpoints Product Overview With today s sophisticated malware, you have to protect endpoints before, during, and after attacks. Cisco Advanced Malware Protection
Evolution Of Cyber Threats & Defense Approaches
 Evolution Of Cyber Threats & Defense Approaches Antony Abraham IT Architect, Information Security, State Farm Kevin McIntyre Tech Lead, Information Security, State Farm Agenda About State Farm Evolution
Evolution Of Cyber Threats & Defense Approaches Antony Abraham IT Architect, Information Security, State Farm Kevin McIntyre Tech Lead, Information Security, State Farm Agenda About State Farm Evolution
Vulnerability Management
 Vulnerability Management Buyer s Guide Buyer s Guide 01 Introduction 02 Key Components 03 Other Considerations About Rapid7 01 INTRODUCTION Exploiting weaknesses in browsers, operating systems and other
Vulnerability Management Buyer s Guide Buyer s Guide 01 Introduction 02 Key Components 03 Other Considerations About Rapid7 01 INTRODUCTION Exploiting weaknesses in browsers, operating systems and other
PALANTIR CYBER An End-to-End Cyber Intelligence Platform for Analysis & Knowledge Management
 PALANTIR CYBER An End-to-End Cyber Intelligence Platform for Analysis & Knowledge Management INTRODUCTION Traditional perimeter defense solutions fail against sophisticated adversaries who target their
PALANTIR CYBER An End-to-End Cyber Intelligence Platform for Analysis & Knowledge Management INTRODUCTION Traditional perimeter defense solutions fail against sophisticated adversaries who target their
IBM Security. 2013 IBM Corporation. 2013 IBM Corporation
 IBM Security Security Intelligence What is Security Intelligence? Security Intelligence --noun 1.the real-time collection, normalization and analytics of the data generated by users, applications and infrastructure
IBM Security Security Intelligence What is Security Intelligence? Security Intelligence --noun 1.the real-time collection, normalization and analytics of the data generated by users, applications and infrastructure
Carbon Black and Palo Alto Networks
 Carbon Black and Palo Alto Networks Bring Together Next-Generation Endpoint and Network Security Solutions Endpoints and Servers in the Crosshairs of According to a 2013 study, 70 percent of businesses
Carbon Black and Palo Alto Networks Bring Together Next-Generation Endpoint and Network Security Solutions Endpoints and Servers in the Crosshairs of According to a 2013 study, 70 percent of businesses
Effective IDS/IPS Network Security in a Dynamic World with Next-Generation Intrusion Detection & Prevention
 Effective IDS/IPS Network Security in a Dynamic World with Next-Generation Intrusion Detection & Prevention Your Security Challenges Defending the Dynamic Network! Dynamic threats 䕬 䕬 䕬 䕬 Many threats
Effective IDS/IPS Network Security in a Dynamic World with Next-Generation Intrusion Detection & Prevention Your Security Challenges Defending the Dynamic Network! Dynamic threats 䕬 䕬 䕬 䕬 Many threats
Looking Ahead The Path to Moving Security into the Cloud
 Looking Ahead The Path to Moving Security into the Cloud Gerhard Eschelbeck Sophos Session ID: SPO2-107 Session Classification: Intermediate Agenda The Changing Threat Landscape Evolution of Application
Looking Ahead The Path to Moving Security into the Cloud Gerhard Eschelbeck Sophos Session ID: SPO2-107 Session Classification: Intermediate Agenda The Changing Threat Landscape Evolution of Application
White Paper. Why Next-Generation Firewalls Don t Stop Advanced Malware and Targeted APT Attacks
 White Paper Why Next-Generation Firewalls Don t Stop Advanced Malware and Targeted APT Attacks White Paper Executive Summary Around the world, organizations are investing massive amounts of their budgets
White Paper Why Next-Generation Firewalls Don t Stop Advanced Malware and Targeted APT Attacks White Paper Executive Summary Around the world, organizations are investing massive amounts of their budgets
Enabling Security Operations with RSA envision. August, 2009
 Enabling Security Operations with RSA envision August, 2009 Agenda What is security operations? How does RSA envision help with security operations? How does RSA envision fit with other EMC products? If
Enabling Security Operations with RSA envision August, 2009 Agenda What is security operations? How does RSA envision help with security operations? How does RSA envision fit with other EMC products? If
SANS Top 20 Critical Controls for Effective Cyber Defense
 WHITEPAPER SANS Top 20 Critical Controls for Cyber Defense SANS Top 20 Critical Controls for Effective Cyber Defense JANUARY 2014 SANS Top 20 Critical Controls for Effective Cyber Defense Summary In a
WHITEPAPER SANS Top 20 Critical Controls for Cyber Defense SANS Top 20 Critical Controls for Effective Cyber Defense JANUARY 2014 SANS Top 20 Critical Controls for Effective Cyber Defense Summary In a
GOOD GUYS VS BAD GUYS: USING BIG DATA TO COUNTERACT ADVANCED THREATS. Joe Goldberg. Splunk. Session ID: SPO-W09 Session Classification: Intermediate
 GOOD GUYS VS BAD GUYS: USING BIG DATA TO COUNTERACT ADVANCED THREATS Joe Goldberg Splunk Session ID: SPO-W09 Session Classification: Intermediate About Me Joe Goldberg Current: Splunk - Security Evangelist
GOOD GUYS VS BAD GUYS: USING BIG DATA TO COUNTERACT ADVANCED THREATS Joe Goldberg Splunk Session ID: SPO-W09 Session Classification: Intermediate About Me Joe Goldberg Current: Splunk - Security Evangelist
Endpoint Security for DeltaV Systems
 DeltaV Systems Service Data Sheet Endpoint Security for DeltaV Systems Essential protection that consolidates endpoint and data security. Reduces the time and effort spent deploying and managing security
DeltaV Systems Service Data Sheet Endpoint Security for DeltaV Systems Essential protection that consolidates endpoint and data security. Reduces the time and effort spent deploying and managing security
Modern Approach to Incident Response: Automated Response Architecture
 SESSION ID: ANF-T10 Modern Approach to Incident Response: Automated Response Architecture James Carder Director, Security Informatics Mayo Clinic @carderjames Jessica Hebenstreit Senior Manager, Security
SESSION ID: ANF-T10 Modern Approach to Incident Response: Automated Response Architecture James Carder Director, Security Informatics Mayo Clinic @carderjames Jessica Hebenstreit Senior Manager, Security
A Case for Managed Security
 A Case for Managed Security By Christopher Harper Managing Director, Security Superior Managed IT & Security Services 1. INTRODUCTION Most firms believe security breaches happen because of one key malfunction
A Case for Managed Security By Christopher Harper Managing Director, Security Superior Managed IT & Security Services 1. INTRODUCTION Most firms believe security breaches happen because of one key malfunction
Applying Internal Traffic Models to Improve Identification of High Fidelity Cyber Security Events
 Applying Internal Traffic Models to Improve Identification of High Fidelity Cyber Security Events Abstract Effective Security Operations throughout both DoD and industry are requiring and consuming unprecedented
Applying Internal Traffic Models to Improve Identification of High Fidelity Cyber Security Events Abstract Effective Security Operations throughout both DoD and industry are requiring and consuming unprecedented
The Hillstone and Trend Micro Joint Solution
 The Hillstone and Trend Micro Joint Solution Advanced Threat Defense Platform Overview Hillstone and Trend Micro offer a joint solution the Advanced Threat Defense Platform by integrating the industry
The Hillstone and Trend Micro Joint Solution Advanced Threat Defense Platform Overview Hillstone and Trend Micro offer a joint solution the Advanced Threat Defense Platform by integrating the industry
Security Analytics Topology
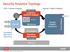 Security Analytics Topology CEP = Stream Analytics Hadoop = Batch Analytics Months to years LOGS PKTS Correlation with Live in Real Time Meta, logs, select payload Decoder Long-term, intensive analysis
Security Analytics Topology CEP = Stream Analytics Hadoop = Batch Analytics Months to years LOGS PKTS Correlation with Live in Real Time Meta, logs, select payload Decoder Long-term, intensive analysis
Cyber Security. BDS PhantomWorks. Boeing Energy. Copyright 2011 Boeing. All rights reserved.
 Cyber Security Automation of energy systems provides attack surfaces that previously did not exist Cyber attacks have matured from teenage hackers to organized crime to nation states Centralized control
Cyber Security Automation of energy systems provides attack surfaces that previously did not exist Cyber attacks have matured from teenage hackers to organized crime to nation states Centralized control
JUNIPER NETWORKS SPOTLIGHT SECURE THREAT INTELLIGENCE PLATFORM
 JUNIPER NETWORKS SPOTLIGHT SECURE THREAT INTELLIGENCE PLATFORM May 2015 Nguyễn Tiến Đức ASEAN Security Specialist Agenda Modern Malware: State of the Industry Dynamic Threat Intelligence on the Firewall
JUNIPER NETWORKS SPOTLIGHT SECURE THREAT INTELLIGENCE PLATFORM May 2015 Nguyễn Tiến Đức ASEAN Security Specialist Agenda Modern Malware: State of the Industry Dynamic Threat Intelligence on the Firewall
Machine-to-Machine Exchange of Cyber Threat Information: a Key to Mature Cyber Defense
 Machine-to-Machine Exchange of Cyber Threat Information: a Key to Mature Cyber Defense By: Daniel Harkness, Chris Strasburg, and Scott Pinkerton The Challenge The Internet is an integral part of daily
Machine-to-Machine Exchange of Cyber Threat Information: a Key to Mature Cyber Defense By: Daniel Harkness, Chris Strasburg, and Scott Pinkerton The Challenge The Internet is an integral part of daily
QRadar SIEM and FireEye MPS Integration
 QRadar SIEM and FireEye MPS Integration March 2014 1 IBM QRadar Security Intelligence Platform Providing actionable intelligence INTELLIGENT Correlation, analysis and massive data reduction AUTOMATED Driving
QRadar SIEM and FireEye MPS Integration March 2014 1 IBM QRadar Security Intelligence Platform Providing actionable intelligence INTELLIGENT Correlation, analysis and massive data reduction AUTOMATED Driving
Content Security: Protect Your Network with Five Must-Haves
 White Paper Content Security: Protect Your Network with Five Must-Haves What You Will Learn The continually evolving threat landscape is what makes the discovery of threats more relevant than defense as
White Paper Content Security: Protect Your Network with Five Must-Haves What You Will Learn The continually evolving threat landscape is what makes the discovery of threats more relevant than defense as
Symantec Advanced Threat Protection: Network
 Symantec Advanced Threat Protection: Network Data Sheet: Advanced Threat Protection The Problem Today s advanced attacks hide themselves on legitimate websites, leverage new and unknown vulnerabilities,
Symantec Advanced Threat Protection: Network Data Sheet: Advanced Threat Protection The Problem Today s advanced attacks hide themselves on legitimate websites, leverage new and unknown vulnerabilities,
What s Wrong with Information Security Today? You are looking in the wrong places for the wrong things.
 What s Wrong with Information Security Today? You are looking in the wrong places for the wrong things. AGENDA Current State of Information Security Data Breach Statics Data Breach Case Studies Why current
What s Wrong with Information Security Today? You are looking in the wrong places for the wrong things. AGENDA Current State of Information Security Data Breach Statics Data Breach Case Studies Why current
Integrating MSS, SEP and NGFW to catch targeted APTs
 #SymVisionEmea #SymVisionEmea Integrating MSS, SEP and NGFW to catch targeted APTs Tom Davison Information Security Practice Manager, UK&I Antonio Forzieri EMEA Solution Lead, Cyber Security 2 Information
#SymVisionEmea #SymVisionEmea Integrating MSS, SEP and NGFW to catch targeted APTs Tom Davison Information Security Practice Manager, UK&I Antonio Forzieri EMEA Solution Lead, Cyber Security 2 Information
THREAT VISIBILITY & VULNERABILITY ASSESSMENT
 THREAT VISIBILITY & VULNERABILITY ASSESSMENT Date: April 15, 2015 IKANOW Analysts: Casey Pence IKANOW Platform Build: 1.34 11921 Freedom Drive, Reston, VA 20190 IKANOW.com TABLE OF CONTENTS 1 Key Findings
THREAT VISIBILITY & VULNERABILITY ASSESSMENT Date: April 15, 2015 IKANOW Analysts: Casey Pence IKANOW Platform Build: 1.34 11921 Freedom Drive, Reston, VA 20190 IKANOW.com TABLE OF CONTENTS 1 Key Findings
Protecting Your Organisation from Targeted Cyber Intrusion
 Protecting Your Organisation from Targeted Cyber Intrusion How the 35 mitigations against targeted cyber intrusion published by Defence Signals Directorate can be implemented on the Microsoft technology
Protecting Your Organisation from Targeted Cyber Intrusion How the 35 mitigations against targeted cyber intrusion published by Defence Signals Directorate can be implemented on the Microsoft technology
CONTINUOUS MONITORING THE MISSING PIECE TO SECURITY OPERATION (SOC) TODAY
 CONTINUOUS MONITORING THE MISSING PIECE TO SECURITY OPERATION (SOC) TODAY MATTHIAS YEO Chief Technology Officer - APAC CISSP, CISA, CISM, PMP 1 OVER REACTING VS UNDER REACTING Reason for the world today
CONTINUOUS MONITORING THE MISSING PIECE TO SECURITY OPERATION (SOC) TODAY MATTHIAS YEO Chief Technology Officer - APAC CISSP, CISA, CISM, PMP 1 OVER REACTING VS UNDER REACTING Reason for the world today
IBM SECURITY QRADAR INCIDENT FORENSICS
 IBM SECURITY QRADAR INCIDENT FORENSICS DELIVERING CLARITY TO CYBER SECURITY INVESTIGATIONS Gyenese Péter Channel Sales Leader, CEE IBM Security Systems 12014 IBM Corporation Harsh realities for many enterprise
IBM SECURITY QRADAR INCIDENT FORENSICS DELIVERING CLARITY TO CYBER SECURITY INVESTIGATIONS Gyenese Péter Channel Sales Leader, CEE IBM Security Systems 12014 IBM Corporation Harsh realities for many enterprise
Enabling Business Beyond the Corporate Network. Secure solutions for mobility, cloud and social media
 Enabling Business Beyond the Corporate Network Secure solutions for mobility, cloud and social media 3 Trends Transforming Networks and Security Are you dealing with these challenges? Enterprise networks
Enabling Business Beyond the Corporate Network Secure solutions for mobility, cloud and social media 3 Trends Transforming Networks and Security Are you dealing with these challenges? Enterprise networks
Q1 Labs Corporate Overview
 Q1 Labs Corporate Overview The Security Intelligence Leader Who we are: Innovative Security Intelligence software company One of the largest and most successful SIEM vendors Leader in Gartner 2011, 2010,
Q1 Labs Corporate Overview The Security Intelligence Leader Who we are: Innovative Security Intelligence software company One of the largest and most successful SIEM vendors Leader in Gartner 2011, 2010,
Cyber Defense & Breach Response Privacy Issues
 Cyber Defense & Breach Response Privacy Issues Kevin Boyle Partner 17 November 2014 Latham & Watkins is the business name of Latham & Watkins (London) LLP, a registered limited liability partnership organised
Cyber Defense & Breach Response Privacy Issues Kevin Boyle Partner 17 November 2014 Latham & Watkins is the business name of Latham & Watkins (London) LLP, a registered limited liability partnership organised
