Protocol and Etiquette for Effective Communication
|
|
|
- Sharleen Day
- 8 years ago
- Views:
Transcription
1 Protocol and Etiquette for Effective Communication Gabe Soumakian Ed.D. Assistant Superintendent, HR Burbank Unified School District
2 Essentials has become an essential means to communicate. Effective use of requires clear guidelines and expectations. You are expected to respond to your business related s in a timely manner. Don t respond to unknown s. You may never know who will read the content. is not private.
3 What is Your Message Use good judgment as to when to use an . Use a good descriptive subject title. Does the message require a formal attachment? Be clear in your writing. The type of message you send is a reflection of your character. Be soft on people and hard on issues there is a difference. Do not use company time to send a personal . A Personal account is easy to set up and access.
4 Etiquette for Building Relationships An opportunity to Build Relationship with our customers. Being polite goes a long way. Start your with a simple greeting. End your with a gentle good bye. Don t or respond when angry or upset. Don t send an urgent and expect everyone to act on it immediately. Don t forward an without the permission of the author. Keep editorial comments to yourself.
5 Sending to a Group Is this message appropriate to the group? Should every member of the group receive this ? Does this message apply to the members of this group? You do not always to need to respond to group e- mails. Forward s to groups when you have interacted. Behave properly with listserves and groups
6 Managing your should be viewed and responded to within 24 hours. set to auto-reply if the you cannot respond within 24 hours. should not be read during any meeting. Treat parent and student s as a phone call. should not be treated as a parent conference. CC only when you wish to inform others and you don t expect them to respond. Don t print every . Organize your s into folders. Delete and purge ALL s and folders once a week.
7 Spammer s Favorite Tricks Check address Phony subject line Numeric address formats Celebrity subject headers Doubtful content Fake unsubscribe links Phony return address Forged headers Common categories
8 Know and Observe Laws Employees is the property of the District, including the use of personal accounts on company computers. is like a postcard anyone can read it. can be subpoenaed. Not only yours but anyone you communicate with has an indefinite shelf life. In fact, governmental agencies are now required to archive all s sent on the network.
9 Employee Technology Use California School Board Policy 4040 Employees are responsible for the appropriate use of technology. Employees should be aware that computer files and communications over electronic networks, are not private. confidential information should only be transmitted with approval. All employees should have read and signed the District s Acceptable Use Policy (AUP).
10 Top Etiquette Tips Identify yourself at the beginning of the . Keep the message simple and clear. Keep harassment and discrimination policies in mind. Humor and sarcasm can backfire. Don t use to let off steam or flame a conversation. Copy with care. Reply to all with care. Be cautious sending attachments. Edit your before you hit send. Always delete spam right away.
11 Thank You Learn more about technology uses at Have a great day and make someone else s day great one too!
Proper Email Etiquette. September 12, 2013/GovMail Team
 Proper Email Etiquette September 12, 2013/GovMail Team Parts of an e-mail Header From To Date Subject From This lists the sender's e-mail address The header may also list the actual name of the sender
Proper Email Etiquette September 12, 2013/GovMail Team Parts of an e-mail Header From To Date Subject From This lists the sender's e-mail address The header may also list the actual name of the sender
Baldwin County Public Schools. Acceptable Use Policy
 Introduction Baldwin County Public Schools Acceptable Use Policy Baldwin County Public Schools (BCPS) recognizes that access to technology in school gives students greater opportunities to learn, engage,
Introduction Baldwin County Public Schools Acceptable Use Policy Baldwin County Public Schools (BCPS) recognizes that access to technology in school gives students greater opportunities to learn, engage,
Email Basics. Guidelines/Etiquette. Topics. Presented by: Software Training Services
 Email Basics Presented by: Software Training Services Topics Guidelines/Etiquette Privacy of Email Spam Chain Letters/Hoaxes Discussion Groups/Listservs Guidelines/Etiquette 1 Basic Guidelines Length Concise,
Email Basics Presented by: Software Training Services Topics Guidelines/Etiquette Privacy of Email Spam Chain Letters/Hoaxes Discussion Groups/Listservs Guidelines/Etiquette 1 Basic Guidelines Length Concise,
Email Basics Workshop
 Email Basics Workshop Electronic mail, or email, is the most frequently used service on the Internet. Being able to use email effectively and efficiently is a core skill required in today s world. WLAC
Email Basics Workshop Electronic mail, or email, is the most frequently used service on the Internet. Being able to use email effectively and efficiently is a core skill required in today s world. WLAC
CRCNET RESOURCE GUIDE. Clinical Research Community Listserv
 CRCNET RESOURCE GUIDE Clinical Research Community Listserv JOINING CRCNET CRCNet is a listserv intended for the clinical research community at BC Children s Hospital and BC Women s Hospital & Health Centre.
CRCNET RESOURCE GUIDE Clinical Research Community Listserv JOINING CRCNET CRCNet is a listserv intended for the clinical research community at BC Children s Hospital and BC Women s Hospital & Health Centre.
Email Etiquette COMMON PERSONAL AND PROFESSIONAL EMAIL RULES THE AMERICAN CENTER 13 JULY, 2011 YUKI KONDO-SHAH MIRIAM SCHIVE.
 Email Etiquette COMMON PERSONAL AND PROFESSIONAL EMAIL RULES THE AMERICAN CENTER 13 JULY, 2011 YUKI KONDO-SHAH MIRIAM SCHIVE Email Vocabulary CC Carbon Copy BCC Blind Carbon Copy Reply All Forward Delete
Email Etiquette COMMON PERSONAL AND PROFESSIONAL EMAIL RULES THE AMERICAN CENTER 13 JULY, 2011 YUKI KONDO-SHAH MIRIAM SCHIVE Email Vocabulary CC Carbon Copy BCC Blind Carbon Copy Reply All Forward Delete
Basic E- mail Skills. Google s Gmail. www.netliteracy.org
 Email it s convenient, free and easy. Today, it is the most rapidly growing means of communication. This is a basic introduction to email and we use a conversational non- technical style to explain how
Email it s convenient, free and easy. Today, it is the most rapidly growing means of communication. This is a basic introduction to email and we use a conversational non- technical style to explain how
Introduction to Email. Jan 24 th 2010
 Introduction to Email Jan 24 th 2010 Email Need special software (called email-reader or emailclient) to connect to the email-server and download the emails Email-server has limited space for each user
Introduction to Email Jan 24 th 2010 Email Need special software (called email-reader or emailclient) to connect to the email-server and download the emails Email-server has limited space for each user
DEALING WITH JUNK EMAIL GUIDE FOR STAFF
 DEALING WITH JUNK EMAIL GUIDE FOR STAFF Edinburgh Napier University currently utilises an automated email protection system. This system helps protect email users from unsolicited junk mail (also known
DEALING WITH JUNK EMAIL GUIDE FOR STAFF Edinburgh Napier University currently utilises an automated email protection system. This system helps protect email users from unsolicited junk mail (also known
1) "IS THERE A PREFERRED FORMAT TO USE FOR MESSAGES POSTED TO THE LIST (that is, to VICTORIA@indiana.edu)?"
 Welcome to VICTORIA, the online discussion forum for Victorian Studies. VICTORIA is a community devoted to the sharing of scholarly information and ideas about all aspects of 19th-century British culture
Welcome to VICTORIA, the online discussion forum for Victorian Studies. VICTORIA is a community devoted to the sharing of scholarly information and ideas about all aspects of 19th-century British culture
Code of Practice for E-mail Users
 Code of Practice for E-mail Users Page 1 of 7 May11/ver02 1. Be concise and to the point Do not make an e-mail longer than it needs to be. Remember that reading an e-mail is harder than reading printed
Code of Practice for E-mail Users Page 1 of 7 May11/ver02 1. Be concise and to the point Do not make an e-mail longer than it needs to be. Remember that reading an e-mail is harder than reading printed
Good Communication & Customer Service Basics. Brought to you by Human Resources and Information Services & Resources
 Good Communication & Customer Service Basics Brought to you by Human Resources and Information Services & Resources Presentation Contents Principles of Good Communication Telephone Guidelines Voice Mail
Good Communication & Customer Service Basics Brought to you by Human Resources and Information Services & Resources Presentation Contents Principles of Good Communication Telephone Guidelines Voice Mail
Setting up Junk Email Filters By Louise Ryan, NW District IT Expert
 The email servers on campus are no longer set up to filter junk emails from your inbox. If you are getting a significant number of junk emails in your inbox you can set up your own filters in Outlook.
The email servers on campus are no longer set up to filter junk emails from your inbox. If you are getting a significant number of junk emails in your inbox you can set up your own filters in Outlook.
Computer Basics 4 E-mail Basics
 Computer Basics 4 E-mail Basics E-MAIL E-mail or electronic mail allows you to send and receive messages from anyone in the world with an e-mail address. To access e-mail you need an e-mail account, the
Computer Basics 4 E-mail Basics E-MAIL E-mail or electronic mail allows you to send and receive messages from anyone in the world with an e-mail address. To access e-mail you need an e-mail account, the
POLICY AND PROCEDURES OFFICE OF COMMUNICATIONS. Email Best Practices. Table of Contents
 POLICY AND PROCEDURES OFFICE OF COMMUNICATIONS Email Best Practices Table of Contents PURPOSE...1 BACKGROUND...1 POLICY...1 RESPONSIBILITIES...2 PROCEDURES...2 REFERENCES...2 DEFINITIONS...3 EFFECTIVE
POLICY AND PROCEDURES OFFICE OF COMMUNICATIONS Email Best Practices Table of Contents PURPOSE...1 BACKGROUND...1 POLICY...1 RESPONSIBILITIES...2 PROCEDURES...2 REFERENCES...2 DEFINITIONS...3 EFFECTIVE
Email standards, protocol and guidance
 Email standards, protocol and guidance July 2010 1 Email standards, protocol and guidance A good guide to communications for staff Introduction The following guidance introduces good practice for writing
Email standards, protocol and guidance July 2010 1 Email standards, protocol and guidance A good guide to communications for staff Introduction The following guidance introduces good practice for writing
Your Guide to Email Security
 Your Guide to Email Security Protect your Information Email is a powerful way to connect with people. Unfortunately it also makes us vulnerable targets of scammers that can affect us from thousands of
Your Guide to Email Security Protect your Information Email is a powerful way to connect with people. Unfortunately it also makes us vulnerable targets of scammers that can affect us from thousands of
Requests to create new Distribution lists must be approved by a Vice President, President, Vice Chancellor, or the Chancellor.
 Key points for Distribution List Use Recommendations a. Polled CCC CIO s on whether their District or Institution has Institution wide DLs and whether special approval for use is required. Rec d 25 responses
Key points for Distribution List Use Recommendations a. Polled CCC CIO s on whether their District or Institution has Institution wide DLs and whether special approval for use is required. Rec d 25 responses
Grace Christian School Technology Acceptable Use Policy
 Grace Christian School Technology Acceptable Use Policy Introduction Grace Christian School recognizes that access to technology in school gives students greater opportunities to learn, engage, communicate,
Grace Christian School Technology Acceptable Use Policy Introduction Grace Christian School recognizes that access to technology in school gives students greater opportunities to learn, engage, communicate,
Laulima Tool. Reference and Use Guide. of Email Archive
 Laulima Tool Reference and Use Guide of Email Archive Brought to you by Center for Excellence in Learning, Teaching and Technology at Kapi olani Community College March 14, 2008 Table of Contents 1. Description...
Laulima Tool Reference and Use Guide of Email Archive Brought to you by Center for Excellence in Learning, Teaching and Technology at Kapi olani Community College March 14, 2008 Table of Contents 1. Description...
Lee County School District
 Lee County School District Acceptable Use Policy This Acceptable Use Policy outlines the guidelines and behaviors that users are expected to follow when using school technologies or when using personally-owned
Lee County School District Acceptable Use Policy This Acceptable Use Policy outlines the guidelines and behaviors that users are expected to follow when using school technologies or when using personally-owned
Secure Email Frequently Asked Questions
 Secure Email Frequently Asked Questions Frequently Asked Questions Contents General Secure Email Questions and Answers Forced TLS Questions and Answers SecureMail Questions and Answers Glossary Support
Secure Email Frequently Asked Questions Frequently Asked Questions Contents General Secure Email Questions and Answers Forced TLS Questions and Answers SecureMail Questions and Answers Glossary Support
TIPS AND TRICKS FOR THE NEW DMS
 TIPS AND TRICKS FOR THE NEW DMS HOW THE NEW DMS (SQUIRRELMAIL) WORKS SquirrelMail is the Webmail package used for the new DMS. It is off-the-shelf software accessed through the Web and you do not download
TIPS AND TRICKS FOR THE NEW DMS HOW THE NEW DMS (SQUIRRELMAIL) WORKS SquirrelMail is the Webmail package used for the new DMS. It is off-the-shelf software accessed through the Web and you do not download
Email Etiquette. Why do we need Email Etiquette? PROPER EMAIL FORMATTING. Email Etiquette Kelly Levander
 Email Etiquette Why do we need Email Etiquette? Professionalism: : by using proper email language you and your company will convey a professional image. Efficiency: emails that get to the point are much
Email Etiquette Why do we need Email Etiquette? Professionalism: : by using proper email language you and your company will convey a professional image. Efficiency: emails that get to the point are much
E-Mail Management First Edition
 Assessment E-Mail Management First Edition The objectives of this book are to help the user: Take control of incoming e-mail to reduce inbox clutter and increase efficiency Learn about Microsoft Outlook
Assessment E-Mail Management First Edition The objectives of this book are to help the user: Take control of incoming e-mail to reduce inbox clutter and increase efficiency Learn about Microsoft Outlook
EDEXCEL FUNCTIONAL SKILLS ICT. Study Module 8. Using ICT to communicate
 EDEXCEL FUNCTIONAL SKILLS ICT Study Module 8 Using ICT to communicate Published by Pearson Education, Edinburgh Gate, Harlow CM20 2JE Pearson Education 2010 All rights reserved. This material may be used
EDEXCEL FUNCTIONAL SKILLS ICT Study Module 8 Using ICT to communicate Published by Pearson Education, Edinburgh Gate, Harlow CM20 2JE Pearson Education 2010 All rights reserved. This material may be used
Copyright 2011 Smart VA Ltd All Rights Reserved.
 Copyright 2011 Smart VA Ltd All Rights Reserved. No part of this guide may be reproduced or transmitted in any form whatsoever, electronic, or mechanical, including photocopying, recording, or by any informational
Copyright 2011 Smart VA Ltd All Rights Reserved. No part of this guide may be reproduced or transmitted in any form whatsoever, electronic, or mechanical, including photocopying, recording, or by any informational
How To Use Webmail. Guiding you through the Universities online email
 How To Use Webmail Guiding you through the Universities online email Table of Contents LOGGING ON...2 VIEWING MESSAGES...2 SENDING A MESSAGE...3 Using the University s Address Book...3 To send a message
How To Use Webmail Guiding you through the Universities online email Table of Contents LOGGING ON...2 VIEWING MESSAGES...2 SENDING A MESSAGE...3 Using the University s Address Book...3 To send a message
Acceptable Use of ICT Policy For Staff
 Policy Document Acceptable Use of ICT Policy For Staff Acceptable Use of ICT Policy For Staff Policy Implementation Date Review Date and Frequency January 2012 Every two Years Rev 1: 26 January 2014 Policy
Policy Document Acceptable Use of ICT Policy For Staff Acceptable Use of ICT Policy For Staff Policy Implementation Date Review Date and Frequency January 2012 Every two Years Rev 1: 26 January 2014 Policy
Electronic Messaging Appropriate Use Policy
 Electronic Messaging Appropriate Use Policy This Policy is Applicable to: SYSTEM WIDE Gerber, Zeeland, SHMG, SH GR Hospitals, Outpatient/Physician Practices, Corporate, Continuing Care, Priority Health,
Electronic Messaging Appropriate Use Policy This Policy is Applicable to: SYSTEM WIDE Gerber, Zeeland, SHMG, SH GR Hospitals, Outpatient/Physician Practices, Corporate, Continuing Care, Priority Health,
Appropriate Online Behavior Social Networking Etiquette Cyber Bullying Awareness
 Appropriate Online Behavior Social Networking Etiquette Cyber Bullying Awareness Gordon Cooper Technology Center 2012 From http://onguardonline.gov/ Think Before You Share What you post could have a bigger
Appropriate Online Behavior Social Networking Etiquette Cyber Bullying Awareness Gordon Cooper Technology Center 2012 From http://onguardonline.gov/ Think Before You Share What you post could have a bigger
Outlook 2011 Window. [Day], [Work Week], [Full [Home]. Schedule and plan: Click the [New
![Outlook 2011 Window. [Day], [Work Week], [Full [Home]. Schedule and plan: Click the [New Outlook 2011 Window. [Day], [Work Week], [Full [Home]. Schedule and plan: Click the [New](/thumbs/27/11891778.jpg) MS Outlook 2011 Quick Reference for Macintosh The Ribbon consists a series of tabs giving access to buttons, menus, and dialog boxes in various groups to facilitate locating the tools required for a particular
MS Outlook 2011 Quick Reference for Macintosh The Ribbon consists a series of tabs giving access to buttons, menus, and dialog boxes in various groups to facilitate locating the tools required for a particular
Information Technology Security Awareness Training. MIS Department
 Information Technology Security Awareness Training Introduction Who am I? Why are we here? Ensure confidentiality of data Protect stability of IT infrastructure Shield District from legal liability Satisfy
Information Technology Security Awareness Training Introduction Who am I? Why are we here? Ensure confidentiality of data Protect stability of IT infrastructure Shield District from legal liability Satisfy
Microsoft Outlook 2010 contains a Junk E-mail Filter designed to reduce unwanted e-mail messages in your
 Overview of the Junk E-mail Filter in Outlook (Much of this text is extracted from the Outlook Help files.) Microsoft Outlook 2010 contains a Junk E-mail Filter designed to reduce unwanted e-mail messages
Overview of the Junk E-mail Filter in Outlook (Much of this text is extracted from the Outlook Help files.) Microsoft Outlook 2010 contains a Junk E-mail Filter designed to reduce unwanted e-mail messages
SecureMail User Guide
 SecureMail User Guide Contents Secure email at HSBC. 2 About SecureMail... 2 Receiving a secure email sent via SecureMail 3 Opening a secure email sent via SecureMail... 4 Using SecureMail to reply to
SecureMail User Guide Contents Secure email at HSBC. 2 About SecureMail... 2 Receiving a secure email sent via SecureMail 3 Opening a secure email sent via SecureMail... 4 Using SecureMail to reply to
Outlook Training. By Martha Williamson, CIC AVP Automation and Workflow Trainer Martha.williamson@oldnationalins.com (217) 304-1666 Cell
 Outlook Training By Martha Williamson, CIC AVP Automation and Workflow Trainer Martha.williamson@oldnationalins.com (217) 304-1666 Cell 1 Agenda 1. Outlook Views 2. Email Etiquette 3. Signatures 4. Out
Outlook Training By Martha Williamson, CIC AVP Automation and Workflow Trainer Martha.williamson@oldnationalins.com (217) 304-1666 Cell 1 Agenda 1. Outlook Views 2. Email Etiquette 3. Signatures 4. Out
Electronic Procedure Guide for Sections
 Electronic Procedure Guide for Sections October, 2015 This document will be available in pdf on-line at http://www.msba.org/sections/default.aspx Electronic Communication Procedure Guide TABLE OF CONTENTS
Electronic Procedure Guide for Sections October, 2015 This document will be available in pdf on-line at http://www.msba.org/sections/default.aspx Electronic Communication Procedure Guide TABLE OF CONTENTS
Email good practice. MS Outlook users will have email delivered automatically by the Unimail system.
 Email good practice This document is written with staff users in mind. It starts with a quick summary of the basic advice that we offer to users of email. These points are followed by a detailed discussion
Email good practice This document is written with staff users in mind. It starts with a quick summary of the basic advice that we offer to users of email. These points are followed by a detailed discussion
Class 2: Manage Your Digital Footprint. Student Handbook
 Class 2: Manage Your Digital Footprint Student Handbook I Know/I Want to Know/I learned I know I want to know I learned How to keep personal information private online. Give Examples: How to keep personal
Class 2: Manage Your Digital Footprint Student Handbook I Know/I Want to Know/I learned I know I want to know I learned How to keep personal information private online. Give Examples: How to keep personal
Outlook Web App (OWA) To create a new message:
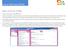 What you ll see in Mail 1. Create a new message by clicking New mail. 2. Folder list. The folder list includes the folders in your mailbox. It may include other folders, such as Favorites and archive folders.
What you ll see in Mail 1. Create a new message by clicking New mail. 2. Folder list. The folder list includes the folders in your mailbox. It may include other folders, such as Favorites and archive folders.
Secure Email User Guide
 Secure Email User Guide Contents Secure email at HSBC. 2 About SecureMail... 2 Receiving a secure email sent via SecureMail 3 Opening a secure email sent via SecureMail... 4 Resetting your SecureMail password..
Secure Email User Guide Contents Secure email at HSBC. 2 About SecureMail... 2 Receiving a secure email sent via SecureMail 3 Opening a secure email sent via SecureMail... 4 Resetting your SecureMail password..
Email Management CSCU9B2 CSCU9B2 1
 Email Management CSCU9B2 CSCU9B2 1 Contents Email clients choosing and using Email message header and content Emailing to lists of people In and out message management Mime attachments and HTML email SMTP,
Email Management CSCU9B2 CSCU9B2 1 Contents Email clients choosing and using Email message header and content Emailing to lists of people In and out message management Mime attachments and HTML email SMTP,
Gordon State College. Spam Firewall. User Guide
 Gordon State College Spam Firewall User Guide Overview The Barracuda Spam Firewall is an integrated hardware and software solution that provides powerful and scalable spam and virus-blocking capabilities
Gordon State College Spam Firewall User Guide Overview The Barracuda Spam Firewall is an integrated hardware and software solution that provides powerful and scalable spam and virus-blocking capabilities
ANNUAL SECURITY RESPONSIBILITY REVIEW
 ANNUAL SECURITY RESPONSIBILITY REVIEW For Faculty and Staff Who Use Computers Minimally in their work May 2012 Training Topics What is Information Security? Review Security Vulnerabilities Phishing email
ANNUAL SECURITY RESPONSIBILITY REVIEW For Faculty and Staff Who Use Computers Minimally in their work May 2012 Training Topics What is Information Security? Review Security Vulnerabilities Phishing email
User Guide for Kelani Mail
 User Guide for Kelani Mail Table of Contents Log in to Kelani Mail 1 Using Kelani Mail 1 Changing Password 2 Using Mail Application 3 Using email system folders 3 Managing Your Mail 4 Using your Junk folder
User Guide for Kelani Mail Table of Contents Log in to Kelani Mail 1 Using Kelani Mail 1 Changing Password 2 Using Mail Application 3 Using email system folders 3 Managing Your Mail 4 Using your Junk folder
Sibford School Student Computer Acceptable Use Policy
 Introduction Sibford School Student Computer Acceptable Use Policy The use of the latest technology is actively encouraged at Sibford School but with this comes a responsibility to protect both students
Introduction Sibford School Student Computer Acceptable Use Policy The use of the latest technology is actively encouraged at Sibford School but with this comes a responsibility to protect both students
Email Etiquette. By JOHN ROY 4/8/14
 Email Etiquette By JOHN ROY 4/8/14 AGENDA Introduction Creating Email Responding to Email Email Tidbits Resources INTRODUCTION Poor Email Etiquette A long lists of email addresses at the beginning of any
Email Etiquette By JOHN ROY 4/8/14 AGENDA Introduction Creating Email Responding to Email Email Tidbits Resources INTRODUCTION Poor Email Etiquette A long lists of email addresses at the beginning of any
Create and Maintain a Penn State Listserv May 22, 2012
 May 22, 2012 Alternative Format Statement This publication is available in alternative media upon request. Statement of Non-Discrimination The Pennsylvania State University is committed to the policy that
May 22, 2012 Alternative Format Statement This publication is available in alternative media upon request. Statement of Non-Discrimination The Pennsylvania State University is committed to the policy that
Brownsburg Community School Corporation Acceptable Use Policy 2012-2013
 Introduction Brownsburg Community School Corporation Acceptable Use Policy 2012-2013 The Brownsburg Community School Corporation (BCSC) recognizes that access to technology in school gives students greater
Introduction Brownsburg Community School Corporation Acceptable Use Policy 2012-2013 The Brownsburg Community School Corporation (BCSC) recognizes that access to technology in school gives students greater
MAJORDOMO - CREATING AND MANAGING LISTS (ADMINISTRATORS) - REFERENCE GUIDE
 MAJORDOMO - CREATING AND MANAGING LISTS (ADMINISTRATORS) - REFERENCE GUIDE INTRODUCTION This document is designed for list administrators people who wish to create and manage mailing lists. There are three
MAJORDOMO - CREATING AND MANAGING LISTS (ADMINISTRATORS) - REFERENCE GUIDE INTRODUCTION This document is designed for list administrators people who wish to create and manage mailing lists. There are three
La Cañada Unified School District Personnel Use of Technology Regulations (AR 4163.4) Also known as the Staff Technology and Internet Use Policy
 LCUSD Personnel Use of Technology Regulations (AR 4163.4) Updated 08/21/08 p. 1 of 5 La Cañada Unified School District Personnel Use of Technology Regulations (AR 4163.4) Also known as the Staff Technology
LCUSD Personnel Use of Technology Regulations (AR 4163.4) Updated 08/21/08 p. 1 of 5 La Cañada Unified School District Personnel Use of Technology Regulations (AR 4163.4) Also known as the Staff Technology
E-mail Etiquette Quick Reference Sheet
 Crash Course: E-mail Etiquette No longer the domain of just the technically savvy, e-mail is used by just about everyone. Microsoft Outlook alone is used by an estimated 120-million-plus people worldwide.
Crash Course: E-mail Etiquette No longer the domain of just the technically savvy, e-mail is used by just about everyone. Microsoft Outlook alone is used by an estimated 120-million-plus people worldwide.
introduction to emarketing
 introduction to emarketing emarketing is typically used for promotional campaigns for attendee generation and for attendee communication. It works closely with ereg which also includes email capabilities
introduction to emarketing emarketing is typically used for promotional campaigns for attendee generation and for attendee communication. It works closely with ereg which also includes email capabilities
Email Security. 01-15-09 Fort Mac
 Email Security 01-15-09 Fort Mac Most Common Mistakes in Email Security Email Security 1. Using just one email account. 2. Holding onto spammed-out accounts too long. 3. Not closing the browser after logging
Email Security 01-15-09 Fort Mac Most Common Mistakes in Email Security Email Security 1. Using just one email account. 2. Holding onto spammed-out accounts too long. 3. Not closing the browser after logging
CITY OF BURLINGTON PUBLIC SCHOOLS MICROSOFT EXCHANGE 2010 OUTLOOK WEB APP USERS GUIDE
 CITY OF BURLINGTON PUBLIC SCHOOLS MICROSOFT EXCHANGE 2010 OUTLOOK WEB APP USERS GUIDE INTRODUCTION You can access your email account from any workstation at your school using Outlook Web Access (OWA),
CITY OF BURLINGTON PUBLIC SCHOOLS MICROSOFT EXCHANGE 2010 OUTLOOK WEB APP USERS GUIDE INTRODUCTION You can access your email account from any workstation at your school using Outlook Web Access (OWA),
Verizon Business National Unified Messaging Service Enhanced Service Guide
 USER GUIDE Voice Verizon Business National Unified Messaging Service Enhanced Service Guide What Is Unified Messaging? Verizon Business National Unified Messaging Service is an interactive voicemail system
USER GUIDE Voice Verizon Business National Unified Messaging Service Enhanced Service Guide What Is Unified Messaging? Verizon Business National Unified Messaging Service is an interactive voicemail system
SOAPM Listserv Online Archive Instructions
 Accessing the SOAPM Online Archive for the First Time 1. Visit http://listserv.aap.org/scripts/wa.exe?a0=soapm. Click on Login. To access the Online Archive, you must be a member of SOAPM currently subscribed
Accessing the SOAPM Online Archive for the First Time 1. Visit http://listserv.aap.org/scripts/wa.exe?a0=soapm. Click on Login. To access the Online Archive, you must be a member of SOAPM currently subscribed
https://my.ncocc-k12.org YOUR EMAIL ADDRESS lastname.firstname@ncocc-k12.org. @ ncocc-k12.org
 https://my.ncocc-k12.org YOUR EMAIL ADDRESS lastname.firstname@ncocc-k12.org. @ ncocc-k12.org NCOCC Last Update January 2006 CLC 2 The features of Microsoft Outlook Web Access are shown at right. Particularly
https://my.ncocc-k12.org YOUR EMAIL ADDRESS lastname.firstname@ncocc-k12.org. @ ncocc-k12.org NCOCC Last Update January 2006 CLC 2 The features of Microsoft Outlook Web Access are shown at right. Particularly
E-mailing a large amount of recipients
 E-mailing a large amount of recipients DO NOT use the TO or CC field! If you have a large list of recipients you need to send an email you, you should never try sending one large email with all of the
E-mailing a large amount of recipients DO NOT use the TO or CC field! If you have a large list of recipients you need to send an email you, you should never try sending one large email with all of the
DON T BE FOOLED BY EMAIL SPAM FREE GUIDE. Provided by: Don t Be Fooled by Spam E-Mail FREE GUIDE. December 2014 Oliver James Enterprise
 Provided by: December 2014 Oliver James Enterprise DON T BE FOOLED BY EMAIL SPAM FREE GUIDE 1 This guide will teach you: How to spot fraudulent and spam e-mails How spammers obtain your email address How
Provided by: December 2014 Oliver James Enterprise DON T BE FOOLED BY EMAIL SPAM FREE GUIDE 1 This guide will teach you: How to spot fraudulent and spam e-mails How spammers obtain your email address How
Protect Yourself. Who is asking? What information are they asking for? Why do they need it?
 Protect Yourself Your home computer serves many purposes: email, shopping, social networking and more. As you surf the Internet, you should be aware of the various ways to protect yourself. Of primary
Protect Yourself Your home computer serves many purposes: email, shopping, social networking and more. As you surf the Internet, you should be aware of the various ways to protect yourself. Of primary
Tutorial for Horde email. Contents
 Tutorial for Horde email Contents Basics 1. Starting Horde 2. Reading emails 3. Replying / Forwarding 4. New email 5. Attachments 6. Save as Draft 7. Address books Adding contact details and accessing
Tutorial for Horde email Contents Basics 1. Starting Horde 2. Reading emails 3. Replying / Forwarding 4. New email 5. Attachments 6. Save as Draft 7. Address books Adding contact details and accessing
Advice about online security
 Advice about online security May 2013 Contents Report a suspicious email or website... 3 Security advice... 5 Genuine DWP contacts... 8 Recognising and reporting phishing and bogus emails... 9 How DWP
Advice about online security May 2013 Contents Report a suspicious email or website... 3 Security advice... 5 Genuine DWP contacts... 8 Recognising and reporting phishing and bogus emails... 9 How DWP
Email Management Information and Records Management (IRM) Email. www.canterbury.ac.nz/irm
 Email Management Information and Records Management (IRM) Email. www.canterbury.ac.nz/irm 2014 Email Management at UC This hand-out is intended to help staff manage their outlook in-boxes for their University
Email Management Information and Records Management (IRM) Email. www.canterbury.ac.nz/irm 2014 Email Management at UC This hand-out is intended to help staff manage their outlook in-boxes for their University
BULK MAIL CAMPAIGN RULES
 BULK MAIL CAMPAIGN RULES No matter what you do, or how closely you follow the guidelines we provide, the issue of spam is an ever changing and always evolving problem it is estimated that more than 70%
BULK MAIL CAMPAIGN RULES No matter what you do, or how closely you follow the guidelines we provide, the issue of spam is an ever changing and always evolving problem it is estimated that more than 70%
A Guide to Information Technology Security in Trinity College Dublin
 A Guide to Information Technology Security in Trinity College Dublin Produced by The IT Security Officer & Training and Publications 2003 Web Address: www.tcd.ie/itsecurity Email: ITSecurity@tcd.ie 1 2
A Guide to Information Technology Security in Trinity College Dublin Produced by The IT Security Officer & Training and Publications 2003 Web Address: www.tcd.ie/itsecurity Email: ITSecurity@tcd.ie 1 2
MCH Channel_e Email Best Practices for Marketers
 MCH Channel_e Email Best Practices for Marketers Best Practices for Marketers Communicating with your prospects and customers through email is a popular channel that provides almost immediate response.
MCH Channel_e Email Best Practices for Marketers Best Practices for Marketers Communicating with your prospects and customers through email is a popular channel that provides almost immediate response.
Pacific Northwest University of Health Sciences
 Effective: 7/01/06 Exec. Lead: Chief Business Officer Revised: 1/11 Approved By: Board of Trustees Expired: n/a Applies To: University-wide Pacific Northwest University of Health Sciences Policy: Computer,
Effective: 7/01/06 Exec. Lead: Chief Business Officer Revised: 1/11 Approved By: Board of Trustees Expired: n/a Applies To: University-wide Pacific Northwest University of Health Sciences Policy: Computer,
GroupWise Client. Rules. GroupWise Rules. Create a rule
 GroupWise Client Rules GroupWise Rules Use Rules to define a set of conditions and actions to be performed when an item meets those conditions. When you create a rule, you must do the following: Name the
GroupWise Client Rules GroupWise Rules Use Rules to define a set of conditions and actions to be performed when an item meets those conditions. When you create a rule, you must do the following: Name the
TIPS AND TRICKS THE DISPATCH MESSAGING SYSTEM HOW THE DISPATCH MESSAGING SYSTEM (DMS) WORKS
 TIPS AND TRICKS THE DISPATCH MESSAGING SYSTEM HOW THE DISPATCH MESSAGING SYSTEM (DMS) WORKS SquirrelMail is the Webmail package used for the DMS. It is off-the-shelf software accessed through the Web and
TIPS AND TRICKS THE DISPATCH MESSAGING SYSTEM HOW THE DISPATCH MESSAGING SYSTEM (DMS) WORKS SquirrelMail is the Webmail package used for the DMS. It is off-the-shelf software accessed through the Web and
Outlook 2013 ~ e Mail Quick Tips
 The Ribbon: Home tab New Email to send a new mail New Items to send a new mail, a new appointment, a new meeting, a new contact, a new task, a new Lync Meeting Ignore to ignore a request Clean Up to clean
The Ribbon: Home tab New Email to send a new mail New Items to send a new mail, a new appointment, a new meeting, a new contact, a new task, a new Lync Meeting Ignore to ignore a request Clean Up to clean
OFFICE 365 TRAINING GUIDE
 OFFICE 365 TRAINING GUIDE Presented by: GATEWAY UNIFIED SCHOOL DISTRICT 4411 MOUNTAIN LAKES BLVD, REDDING, CA 96003 gateway schools.org TABLE OF CONTENTS About Office 365... 2 Signing Into Email/Outlook
OFFICE 365 TRAINING GUIDE Presented by: GATEWAY UNIFIED SCHOOL DISTRICT 4411 MOUNTAIN LAKES BLVD, REDDING, CA 96003 gateway schools.org TABLE OF CONTENTS About Office 365... 2 Signing Into Email/Outlook
MICROSOFT OUTLOOK TIPS AND TRICKS
 Materials Provided by Tim McCurdy MICROSOFT OUTLOOK TIPS AND TRICKS Tips for Outlook Mail 1. Set a reminder to reply to a message 2. Add your own words to a follow-up flag for a new message 3. Send a message
Materials Provided by Tim McCurdy MICROSOFT OUTLOOK TIPS AND TRICKS Tips for Outlook Mail 1. Set a reminder to reply to a message 2. Add your own words to a follow-up flag for a new message 3. Send a message
OCT Training & Technology Solutions Training@qc.cuny.edu (718) 997-4875
 OCT Training & Technology Solutions Training@qc.cuny.edu (718) 997-4875 Understanding Information Security Information Security Information security refers to safeguarding information from misuse and theft,
OCT Training & Technology Solutions Training@qc.cuny.edu (718) 997-4875 Understanding Information Security Information Security Information security refers to safeguarding information from misuse and theft,
Filtering E-mail for Spam: Macintosh
 Filtering E-mail for Spam: Macintosh Last Revised: April 2003 Table of Contents Introduction... 1 Objectives... 1 Filtering E-mail for Spam... 2 What Is Spam?... 2 What Is UT Doing About Spam?... 2 What
Filtering E-mail for Spam: Macintosh Last Revised: April 2003 Table of Contents Introduction... 1 Objectives... 1 Filtering E-mail for Spam... 2 What Is Spam?... 2 What Is UT Doing About Spam?... 2 What
Email Policy For Staff and Students
 Email Policy For Staff and Students Document Version Date Policy Owner Approval Email Policy V1.2 Dec 2011 ITS Reviewed - KPMG auditor V1.3 Feb 2012 Approved - elit committee March 2012 Approved Management
Email Policy For Staff and Students Document Version Date Policy Owner Approval Email Policy V1.2 Dec 2011 ITS Reviewed - KPMG auditor V1.3 Feb 2012 Approved - elit committee March 2012 Approved Management
MSI Secure Mail Tutorial. Table of Contents
 Posted 1/12/12 Table of Contents 1 - INTRODUCTION... 1-1 INTRODUCTION... 1-1 Summary... 1-1 Why Secure Mail?... 1-1 Which Emails Must Be Encrypted?... 1-2 Receiving Email from MSI... 1-2 Sending Email
Posted 1/12/12 Table of Contents 1 - INTRODUCTION... 1-1 INTRODUCTION... 1-1 Summary... 1-1 Why Secure Mail?... 1-1 Which Emails Must Be Encrypted?... 1-2 Receiving Email from MSI... 1-2 Sending Email
Edinburg CISD Technology Department Internet Part 3 Using Microsoft Exchange E-mail
 Edinburg CISD Technology Department Internet Part 3 Using Microsoft Exchange E-mail I. Introductions and Objectives II. III. IV. Acceptable Use Policy & Exhibit C forms Logging in Procedures Exploring
Edinburg CISD Technology Department Internet Part 3 Using Microsoft Exchange E-mail I. Introductions and Objectives II. III. IV. Acceptable Use Policy & Exhibit C forms Logging in Procedures Exploring
Outlook Live Basics. for Students
 Outlook Live Basics for Students 2 Outlook Live for Support Staff Outlook Live for Support Staff 3 Getting Started... 6 Signing into your Outlook Account... 6 Migrating your Account... 8 Address Book...
Outlook Live Basics for Students 2 Outlook Live for Support Staff Outlook Live for Support Staff 3 Getting Started... 6 Signing into your Outlook Account... 6 Migrating your Account... 8 Address Book...
SPAM ARREST WORKS! Quick Start Enterprise Administrators. Take Control of Your Inbox. Protecting mailboxes since 2001
 Page 1 of 6 Quick Start Enterprise Administrators Welcome to the Quick Start Guide (QSG) for Enterprise Account Customers. The aim and purpose of this guide is to provide a quick overview of what you need
Page 1 of 6 Quick Start Enterprise Administrators Welcome to the Quick Start Guide (QSG) for Enterprise Account Customers. The aim and purpose of this guide is to provide a quick overview of what you need
UNIVERSITY OF ST ANDREWS. EMAIL POLICY November 2005
 UNIVERSITY OF ST ANDREWS EMAIL POLICY November 2005 I Introduction 1. Email is an important method of communication for University business, and carries the same weight as paper-based communications. The
UNIVERSITY OF ST ANDREWS EMAIL POLICY November 2005 I Introduction 1. Email is an important method of communication for University business, and carries the same weight as paper-based communications. The
Introduction... 2. Configuration & Spam Detection... 2. WinWare Webmail... 3. Email Accounts... 3. Email Account Notes... 4. Definitions...
 Page 1 Table of Contents Introduction... 2 Configuration & Spam Detection... 2 WinWare Webmail... 3 Email Accounts... 3 Email Account Notes... 4 Definitions... 5 Sender Policy Framework (SPF)... 5 Email
Page 1 Table of Contents Introduction... 2 Configuration & Spam Detection... 2 WinWare Webmail... 3 Email Accounts... 3 Email Account Notes... 4 Definitions... 5 Sender Policy Framework (SPF)... 5 Email
FAQ for List Owners/Moderators
 FAQ for List Owners/Moderators This FAQ is intended as a quick reference for Sympa list owners and moderators. It is only a supplement to the full built-in Sympa documentation available via the Help tab
FAQ for List Owners/Moderators This FAQ is intended as a quick reference for Sympa list owners and moderators. It is only a supplement to the full built-in Sympa documentation available via the Help tab
Early 1990s Steve Case and AOL
 Chapter 4 Email Brief History of Email 1960s Messages sent without email addresses Late 1960s Tomlinson and @ symbol 1970s improvements to email 1980 s Compuserve and MCI Mail mail to the public Early
Chapter 4 Email Brief History of Email 1960s Messages sent without email addresses Late 1960s Tomlinson and @ symbol 1970s improvements to email 1980 s Compuserve and MCI Mail mail to the public Early
(email etiquette cont.) Formating Emails
 Sending Emails 1. Make sure your e-mail includes a courteous greeting and closing. Helps to make your e-mail not seem demanding or terse. 2. Address your contact with the appropriate level of formality
Sending Emails 1. Make sure your e-mail includes a courteous greeting and closing. Helps to make your e-mail not seem demanding or terse. 2. Address your contact with the appropriate level of formality
Gloucester County Library System EMAIL BASICS
 Gloucester County Library System EMAIL BASICS Computer Classes Check online calendar for classes We offer computer courses for adults. which include basic computer skills. Our goal is to teach you what
Gloucester County Library System EMAIL BASICS Computer Classes Check online calendar for classes We offer computer courses for adults. which include basic computer skills. Our goal is to teach you what
XGENPLUS SECURITY FEATURES...
 Security Features Table of Contents TABLE OF CONTENTS... 2 1. INTRODUCTION... 3 2. XGENPLUS SECURITY FEATURES... 3 3. SERVER LEVEL FEATURES... 5 4. DOMAIN LEVEL FEATURES... 8 5. USER LEVEL FEATURES...
Security Features Table of Contents TABLE OF CONTENTS... 2 1. INTRODUCTION... 3 2. XGENPLUS SECURITY FEATURES... 3 3. SERVER LEVEL FEATURES... 5 4. DOMAIN LEVEL FEATURES... 8 5. USER LEVEL FEATURES...
Voice Messaging. Reference Guide
 Voice Messaging Reference Guide Table of Contents Voice Messaging 1 Getting Started 3 To Play a Message 4 To Answer a Message 5 To Make a Message 6 To Give a Message 7 Message Addressing Options 8 User
Voice Messaging Reference Guide Table of Contents Voice Messaging 1 Getting Started 3 To Play a Message 4 To Answer a Message 5 To Make a Message 6 To Give a Message 7 Message Addressing Options 8 User
January 2011 Report #49. The following trends are highlighted in the January 2011 report:
 January 2011 Report #49 Spam made up 81.69% of all messages in December, compared with 84.31% in November. The consistent drop in spam made us wonder, did spammers take a holiday break? Global spam volume
January 2011 Report #49 Spam made up 81.69% of all messages in December, compared with 84.31% in November. The consistent drop in spam made us wonder, did spammers take a holiday break? Global spam volume
How to minimize SPAM in your CBPref.com Inbox
 How to minimize SPAM in your CBPref.com Inbox By Jason K. Serafin As I travel through our Coldwell Banker Preferred branch offices, I hear many agents ask me the same question over and over: What can we
How to minimize SPAM in your CBPref.com Inbox By Jason K. Serafin As I travel through our Coldwell Banker Preferred branch offices, I hear many agents ask me the same question over and over: What can we
Outlook 2013 ~ Advanced
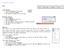 Mail Using Categories 1. Select the message that for the category. 2. Select the appropriate category. 3. The category color displays next to the message. Renaming Categories 1. Select a message. 2. Select
Mail Using Categories 1. Select the message that for the category. 2. Select the appropriate category. 3. The category color displays next to the message. Renaming Categories 1. Select a message. 2. Select
Diocese of Orlando / Office of Catholic Schools Student Technology Responsible Use Policy 2015-2016
 Diocese of Orlando / Office of Catholic Schools Student Technology Responsible Use Policy 2015-2016 1.0 Introduction St. Thomas Aquinas Catholic School recognizes that access to technology in school gives
Diocese of Orlando / Office of Catholic Schools Student Technology Responsible Use Policy 2015-2016 1.0 Introduction St. Thomas Aquinas Catholic School recognizes that access to technology in school gives
Internet E-mail address
 Electronic Mail (Email) POP Mail is email that downloads and stores your messages on your computer. You install a mail client on your computer, which then connects to your ISP s mail server. Examples:
Electronic Mail (Email) POP Mail is email that downloads and stores your messages on your computer. You install a mail client on your computer, which then connects to your ISP s mail server. Examples:
The Unified Spam-Blocking System
 The Unified Spam-Blocking System Enterprise User Guide September, 2003 Version 2.00 Copyright DigiPortal Software Inc, 2002-2003, All rights reserved Note: Any companies, services or people, other than
The Unified Spam-Blocking System Enterprise User Guide September, 2003 Version 2.00 Copyright DigiPortal Software Inc, 2002-2003, All rights reserved Note: Any companies, services or people, other than
IT Security DO s and DON Ts
 For more advice contact: IT Service Centre T: (01332) 59 1234 E: ITServiceCentre@derby.ac.uk Online: http://itservicecentre.derby.ac.uk Version: February 2014 www.derby.ac.uk/its IT Security DO s and DON
For more advice contact: IT Service Centre T: (01332) 59 1234 E: ITServiceCentre@derby.ac.uk Online: http://itservicecentre.derby.ac.uk Version: February 2014 www.derby.ac.uk/its IT Security DO s and DON
INTERMEDIATE GroupWise 7.0
 INTERMEDIATE GroupWise 7.0 Distributed by the Administrative Technology User Support Department under the Direction of Dr. Russell Clukey, Executive Director, Support Services. Feel free to contact the
INTERMEDIATE GroupWise 7.0 Distributed by the Administrative Technology User Support Department under the Direction of Dr. Russell Clukey, Executive Director, Support Services. Feel free to contact the
Paramount Unified School District Technology and Ed Services Departments Computer In-service
 4 Paramount Unified School District Technology and Ed Services Departments Computer In-service Distribute notebooks / Test logins Login information Login contexts (see Page 2) Logging in at other sites
4 Paramount Unified School District Technology and Ed Services Departments Computer In-service Distribute notebooks / Test logins Login information Login contexts (see Page 2) Logging in at other sites
Being labeled as a spammer will drive your customers way, ruin your business, and can even get you a big fine or a jail sentence!
 Getting Your Email Delivered Beware: If you send out spam mail (unsolicited emails), whether it be knowingly or not, you will put your business and your reputation at risk. Consequences for spamming have
Getting Your Email Delivered Beware: If you send out spam mail (unsolicited emails), whether it be knowingly or not, you will put your business and your reputation at risk. Consequences for spamming have
How do I start a new email message?
 Composing Email There are several preferences you can set for composing email. How do I start a new email message? How do I address an email message? How do I find an email address? How do I write an email
Composing Email There are several preferences you can set for composing email. How do I start a new email message? How do I address an email message? How do I find an email address? How do I write an email
Amy wants to use her email to view some photos her friend Sandy sent, from her vacation to Washington DC.
 E-mail Attachments Hi, I m Sarah. I m going to show you how to download files people send to you in emails, and how to send your own files to other people using your email. We ll follow along with Amy,
E-mail Attachments Hi, I m Sarah. I m going to show you how to download files people send to you in emails, and how to send your own files to other people using your email. We ll follow along with Amy,
