How to Create a Dynamic Webpage
|
|
|
- Alannah Walsh
- 3 years ago
- Views:
Transcription
1 Intro to Dynamic Web Development ACM UIUC, 2010
2 Static vs Dynamic "Static" is an adjective meaning "does not change". In the context of web programming, it can be used several different ways, but the most common is simply to refer to a webpage which is written purely in HTML/CSS -- a "static" page. More generally, a static page does not change itself before being sent from the server to the browser. "Dynamic" means the opposite. In web programming, a dynamic page is one which uses some means to change itself before being sent to the browser. We've already learned how to write static pages. Now, we'll go over what "dynamic" means in practice and how to create dynamic websites.
3 Review: How websites work Client-side: If something is client-side, it occurs after the page is sent to the web browser. For example, HTML rendering is client-side. Server-side If something is server-side, then it occurs before the page is sent to the web browser. For example, interpreting PHP is server-side.
4 How do we add dynamic content? We can only send a file to the web browser which it can "understand" Initially this meant only HTML, CSS, and images Soon, browsers were built to understand client-side scripting languages, which allow websites to change themselves after being downloaded Javascript is the most common client-side language Technically, we could write a dynamic site using these client-side languages. However, anything client-side can be viewed, changed, and tainted by the user! Doing so would expose our site logic and represent a major security hole.
5 So, we focus on the server side... Given that we can only safely send a static page to the client (Javascript for fancy effects notwithstanding), we make our site dynamic by dynamically generating the static page. So, instead of having our website directly fetch the.html file from the server's file system and send it straight to the client, we first have the server pre-process the file. The most intuitive way to do this on top of HTML is to have a special tag that gets pre-processed before the page is sent to the user's browser. This is the key idea behind PHP and ASP. A more complex model is needed for full websites, however -- more on that next week!
6 Revisiting our diagram... Note how, as far as your browser is concerned, nothing is any different. The only part that's changed is on the web server!
7 So all we need is: A web server capable of: Understanding that we want some pages to be preprocessed Preprocessing such pages before sending them back to the user These requirements are pretty minimal. We also want web servers to be able to manage user sessions, enforce security, etc., etc... but we'll worry about that later. If you want to deploy a website using a particular dynamic technology, make sure the production server you plan on using supports it. PHP is almost universally supported. Django, not so much.
8 Setting up a web server on your computer If we want to develop a dynamic website, we really need a way to test the dynamic functionality on our local computer. However, a full web server consists of several layers of applications (sometimes called the software stack)... it's a pain to set each layer up manually. The quick and easy way to do this is to install an all-in-one package Windows: WAMP ( Linux: LAMP (check your repository for a good one) Ubuntu: `sudo tasksel install lamp-server` Mac: MAMP ( LAMP = Linux, Apache, MySQL, PHP
9 Installing WAMP Installing WAMP (or the respective XAMP stack for your platform) is usually pretty easy -- just click through the installer. Make note of where the system installs to By default, C:\wamp\ On Linux, usually /var/www/ As a note, make sure your webserver is NOT listening for connections from outside (a special IP address meaning your computer and only your computer). By default, any XAMP install should be configured this way. If you need help, stop by afterward or come to my office hours 6pm in the ACM office) -- or just Google your question.
10 It's installed! Now what? Remember last week, when we discussed what a web root was for web servers? You need to find the web root for your brand-new, local web server. Probably at <installation path>/www (e.g., C:\wamp\www)
11 Making sure it worked To make sure PHP and your server are properly configured, create a file named test.php in the web root. Type in the following three lines: <?php phpinfo();?> Open your web browser and go to: 'localhost' is a shortcut for , your local computer
12 If it worked, you should see this: Now that we know PHP works, we can get started.
13 What is PHP? Remember how we wanted a script that could pre-process HTML pages and interpret server-side code? PHP stands for PHP Hypertext Preprocessor It's a relatively-simple scripting language that you can use for dynamic web programming Has some problems scaling up, due to security, language features, etc. Can be mitigated through good design Good choice for simple, cross-platform sites Uses a very-simplified, C-like syntax Expanded in version 4 to add OOP support
14 PHP Basics: Variables In PHP, variables are prefixed with dollar signs ($) to indicate that they're variables. e.g. $varname, $time, $first_name, $date Variables are dynamically typed: PHP does not care what type is stored in any given variable It is up to you to make sure your code makes sense, or you'll get weird errors! As in most C-like languages, you use the = operator to assign variables. $first_name = "string"; $var = "4"; $var = 4; // works fine, overwriting the old value.
15 More on variables: Strings A string is a variable type which holds a snippet of text. To define a string in PHP, use quotes (" or ') around the text you want to make a string. Single-quotes will not change the string as written. If you're concerned about speed, these are faster. Double-quotes will cause PHP to interpolate the string for variable references: $var = 4; echo("the value of var is $var"); will be turned into "The value of var is 4" when run! $str1 = 'This is a string.'; $metastr = "$str1 is a string"; $str1 = 'Changed?' echo($metastr); // This is a string. is a string // Caveat: interpolation is not repeated unless you ask PHP nicely.
16 PHP Basics: Statements Scripts in PHP are comprised by a series of statements. Each statement either defines something (like a class or a control structure), calls a function, or assigns a variable. Remember to end each statement with a semi-colon, unless the statement is a control structure or a class definition. initialize_some_stuff(); // function call $day_created = get_day_created(); //assgnmt. if ($day_created > 3) { echo("more than three."); } else { echo("less than or equal to 3."); }
17 PHP Basics: Control Structures A control structure somehow controls the execution of code. The two basic examples are if-then statements and while loops. If-then checks if the conditional evaluates to a non-false value, and executes the first block of code if it does. In PHP, the values 0, "", and false evaluate to false. Everything else is evaluated as true in a conditional. A block of code is a list of statements surrounded by brackets { } Think of a block as a single statement with multiple steps A while loop does the same evaluation, but continues to execute the block until the conditional evaluates as false.
18 Examples of If-Then and While if ($something = "fruit") { echo("fruit!"); echo("this is in the same block."); } else { echo("not fruit."); } while ($something!= "fruit") { echo("still not fruit!"); $something = get_new_something(); }
19 Back to variables: Arrays An array is a variable that stores a list of other variables. $arr = array("red", "green", "blue"); To add to an array, do: $arr[] = "new color"; To reference a particular item, use $arr[0], $arr[1], etc. Terminology: "key" refers to the unique identifier you use to access an array element. "value" refers to the actual element. Arrays can also have non-integer keys -- this makes them more intuitive to access. $friends = array("best" => "Joe", "worst" => "Bill"); Note the =>, which indicates a key-to-value pair. $my_best_friend = $friends["best"];
20 For-loops and For-each loops A for-loop, at its simplest, executes a block of code a certain number of times. The current iteration number can be used inside the loop if needed. for ($i = 0; $i < 10; $i++) { /* goes from 0 to 9 */ } A for-each loop iterates over the items in an array. Necessary for associative (non-integer-keyed) arrays, as we have no other way of telling what keys we have in a given array! for ($current_key => $current_value) { // do stuff with each key and value }
21 Defining functions A function is a block of statements that has arguments passed into it from another part of the program, and may return a value to the calling statement. There are hundreds of built-in PHP functions, like echo(), file_get_contents(), mysql_connect(), etc. Check php.net for arguments to these functions To define your own, do: function mycoolfunction($arg1, $arg2) { echo "doing stuff"; return $arg1 + ($arg2 * 4); }
22 Using PHP You can look up much more complete/helpful information on PHP practically anywhere on the web (php.net being your best bet). Let's move on to how we can actually use this stuff to make our webpages less boring.
23 Scenario: Custom Links Your client wants to send out a mass campaign to each one of his customers. When they click on the link to his site inside it, he wants them to be greeted with their name. Since we already have the name of each customer, we can do this by changing the link inside each to be custom. Do we really want to have index_robert.php, index_ted. php, etc., etc...? No. Instead, we can use URL parameters to add information to each URL without having to create a brand-new page.
24 URL Parameters You've probably seen links on the web that look like: By default, Apache is configured to ignore everything after a? in a URL -- it only uses foo.php to find the file, and passes the rest of the URL to PHP to use as it likes. This extra data is often called the querystring. PHP can use what follows to get additional information. It interprets the data as a list of parameters, in the form key=value, separated by ampersands (&). So, above, it sees two parameters: lang, with a value of 'en' id, with a value of 4 We can use these to make special URLs for each customer.
25 Customizing our links If we give each client a special URL with their name passed in as a URL parameter, then when they click on it, we can get that name in PHP and display it. e.g. So, our list has the names already. We just have to modify our mailer script to generate these URLs. Note: how do we deal with spaces and weird characters? To properly encode these characters in URLs, use URL encoding (PHP has a function to do this). A space is %20, when URL encoded. e.g. welcome.php?name=mary%20jane
26 Now, the names are in the URL So how do we get them out of it? PHP has a few very special superglobal arrays: $_GET URL parameters (which we want) $_POST Form data (covered later) $_REQUEST Union of GET and POST. $_SESSION Session data (covered later) We can use the $_GET array to get our customers' names.
27 Making welcome.php <?php $customer_name = $_GET['name']; echo "Welcome, $customer_name!";?> Now, go to and see what comes up. Welcome, Robert!
28 Problem: what if there is no name? What happened? PHP by default does not like when you use uninitialized values. You can turn this off, but that's not a good idea. Instead, make sure the index 'name' exists in $_GET. Use array_key_exists($key, $array) to test
29 Update our code: <?php if (array_key_exists('name', $_GET)) { $customer_name = $_GET['name']; echo "Welcome, $customer_name!"; } else { echo "Welcome!"; }?> Now, go to and: Welcome!
30 Problem: what if the user is malicious? If we use this code as-is, we're allowing people to craft links which insert arbitrary HTML into our page. The user could craft malicious JavaScript, capable of exploiting some browsers. Even though only that user will see the page, what if they use bit.ly to encode the URL and then tweet it to all their friends? This is one type of XSS (cross-site scripting) attack, because the attack script is usually loaded from another site. Rule 1 of web programming: don't trust request data. So... no problem, we can just clean the name first. PHP has strip_tags($str), which (in this context only!) will remove any possibility of dangerous side effects.
31 New, more-secure code: <?php if (array_key_exists('name', $_GET)) { $customer_name = strip_tags($_get['name']); echo "Welcome, $customer_name!"; } else { echo "Welcome!"; }?> Now, users can't try stuff like welcome.php?name=%3cscript% 20type%3D%22javascript%22%20src%3D%22www.virus. com%2fsploit.js%22%3e That is, welcome.php?name=<script type="javascript" src="
32 However... This scheme still allows users to trivially change the content of a page, and is for that reason not ideal. Could use substr() to trim down the name string to a reasonable length Could store name values in a database with a corresponding ID, and give out URLs like: welcome.php? id=42 But for now, let's move on to another scenario.
33 Scenario 2: Simple Blog Our client wants a simple blog site that can dynamically retrieve blog entries from a database and display them. For now, we don't need to worry about providing for posting or editing blog entries, just displaying them. Questions we need to answer: What's a database? How do we retrieve data from a database?
34 Brief intro to databases A database is a means of storing data, optimized for very large amounts of data and fast retrieval. Data is organized into tables, which contain columns Think of an Excel spreadsheet with multiple pages. Simplistic attempts at storing data in such a way use a flat file approach Just a normal file with a list of data The CSV format (comma-separated values) is a good example of typical flat file Really only viable when the data does not need to be accessed, just stored. Databases store the same information that a flat file does, but more efficiently.
35 Example of a database table Here, we have a table storing information about the users of some website. id username full_name 1 rnubel test@gmail.com Robert Nubel 2 otherperson test@aol.com Other Person 3 thirduser test3@gmail.com Third User
36 Designing databases It's non-trivial to design databases, so we won't cover that here. Take CS411 if you're interested However, pulling data from a database is pretty easy, and we almost know enough to do it. Need to know how the blog posts table is designed (this is called a table's schema) Need to somehow select the correct row from the blog posts table
37 The blog posts table blog_posts: id title author content 1 Hello Blogosphere! Robert Nubel Blah blah blah. 2 Blogpost Two Other Person Trivial nonsense. 3 Probably Never Going to Update This Blog Again Third User We're done here.
38 Note: That's not really a schema While just showing what data a table holds is often enough to infer the schema from, the actual schema for the table is more like: CREATE TABLE blog_posts ( id INTEGER PRIMARY KEY, title VARCHAR(255), author VARCHAR(32), content TEXT );
39 But where do we get a database from? MySQL is a popular database management system (DBMS) that came bundled with the WAMP stack we installed earlier. To use the database, you need to start it up (Start All Services will do this) This starts the mysql daemon, which among other things will accept connections from, for example, your PHP scripts and allow you to query the database. Then, we need to run an SQL query to insert some data into the database. SQL = Structured Query Language Lets you create tables, insert data, retrieve data, etc.
40 Running an SQL query on MySQL You can use MySQL's command prompt to enter queries if you'd like, or you can use a web interface, phpmyadmin, which connects to your MySQL server and lets you manage it graphically. If you're using WAMP, left-click on the tray icon and select "phpmyadmin". Once it loads, click on the SQL tab. If you don't have phpmyadmin, find your mysql command prompt and log in. Username is probably 'root' with no password Once logged in, you're ready.
41 Run this query: CREATE DATABASE blog; USE blog; CREATE TABLE blog_posts ( id INTEGER PRIMARY KEY, title VARCHAR(255), author VARCHAR(32), content TEXT ); INSERT INTO blog_posts VALUES (1, "Title of Post", "Robert Nubel", "Blah blah blah content");
42 That's it for the database. Now, we need to write a PHP script which can connect to our database. Luckily, PHP has a set of built-in functions that let us work with MySQL: mysql_connect: connect to the server mysql_select_db: select the database to work with mysql_query: run a query on the server
43 Connecting Open up a new file and save it as blog.php. Type in this code: <?php if (!array_key_exists('post_id', $_GET)) { die("no post id provided!"); // halt execution now } $post_id = $_GET['post_id']; // what could go wrong? mysql_connect('localhost', 'root', ''); // remember localhost? mysql_select_db('blog');
44 Querying the database $sql = "SELECT * FROM blog_posts WHERE id=$post_id"; $qry = mysql_query($sql) or die(mysql_error()); // Fetch an associative array of the first row's data. If no rows // were returned, this will fail. $result = mysql_fetch_assoc($qry); echo "<h1>". $result['title']."<h1>"; echo "<h2>by ". $result['author']. "</h2>"; echo "<p>". $result['content']. "</p>";?>
45 Try it out! Go to localhost/blog.php?post_id=1 in your browser.
46 Important note: don't trust your request Try going to localhost/blog.php?post_id=' (apostrophe included) An SQL error comes up -- this means the ' is being inserted right into the query This means your database can have arbitrary SQL commands sent to it, as you've opened yourself up to SQL injection To prevent this, always sanitize your data before putting it into a query. $post_id = (int) $_GET['post_id']; This typecasts the parameter to an int. The worst that happens is you get a blog post ID that doesn't exist.
47 In conclusion Dynamic web programming is essential to the modern web. Many different technologies -- PHP and MySQL just being a small subset -- exist which can work together to power a website. In the next tutorial, we'll explore a design pattern used to structure large-scale websites: the MVC pattern.
CPE111 COMPUTER EXPLORATION
 CPE111 COMPUTER EXPLORATION BUILDING A WEB SERVER ASSIGNMENT You will create your own web application on your local web server in your newly installed Ubuntu Desktop on Oracle VM VirtualBox. This is a
CPE111 COMPUTER EXPLORATION BUILDING A WEB SERVER ASSIGNMENT You will create your own web application on your local web server in your newly installed Ubuntu Desktop on Oracle VM VirtualBox. This is a
PHP Tutorial From beginner to master
 PHP Tutorial From beginner to master PHP is a powerful tool for making dynamic and interactive Web pages. PHP is the widely-used, free, and efficient alternative to competitors such as Microsoft's ASP.
PHP Tutorial From beginner to master PHP is a powerful tool for making dynamic and interactive Web pages. PHP is the widely-used, free, and efficient alternative to competitors such as Microsoft's ASP.
Webapps Vulnerability Report
 Tuesday, May 1, 2012 Webapps Vulnerability Report Introduction This report provides detailed information of every vulnerability that was found and successfully exploited by CORE Impact Professional during
Tuesday, May 1, 2012 Webapps Vulnerability Report Introduction This report provides detailed information of every vulnerability that was found and successfully exploited by CORE Impact Professional during
Building Dynamic Websites With the MVC Pattern. ACM Webmonkeys @ UIUC, 2010
 Building Dynamic Websites With the MVC Pattern ACM Webmonkeys @ UIUC, 2010 Recap A dynamic website is a website which uses some serverside language to generate HTML pages PHP is a common and ubiquitous
Building Dynamic Websites With the MVC Pattern ACM Webmonkeys @ UIUC, 2010 Recap A dynamic website is a website which uses some serverside language to generate HTML pages PHP is a common and ubiquitous
Introduction to Server-Side Programming. Charles Liu
 Introduction to Server-Side Programming Charles Liu Overview 1. Basics of HTTP 2. PHP syntax 3. Server-side programming 4. Connecting to MySQL Request to a Static Site Server: 1. Homepage lookup 2. Send
Introduction to Server-Side Programming Charles Liu Overview 1. Basics of HTTP 2. PHP syntax 3. Server-side programming 4. Connecting to MySQL Request to a Static Site Server: 1. Homepage lookup 2. Send
Intro to Databases. ACM Webmonkeys 2011
 Intro to Databases ACM Webmonkeys 2011 Motivation Computer programs that deal with the real world often need to store a large amount of data. E.g.: Weather in US cities by month for the past 10 years List
Intro to Databases ACM Webmonkeys 2011 Motivation Computer programs that deal with the real world often need to store a large amount of data. E.g.: Weather in US cities by month for the past 10 years List
CSCI110 Exercise 4: Database - MySQL
 CSCI110 Exercise 4: Database - MySQL The exercise This exercise is to be completed in the laboratory and your completed work is to be shown to the laboratory tutor. The work should be done in week-8 but
CSCI110 Exercise 4: Database - MySQL The exercise This exercise is to be completed in the laboratory and your completed work is to be shown to the laboratory tutor. The work should be done in week-8 but
The following steps detail how to prepare your database.
 Using databases in Second Life or Open Sim to enhance user experience Tom Connors, SciEthis Interactive 2012 Second Life and Open Sim each have a built in system for editing the virtual world that allows
Using databases in Second Life or Open Sim to enhance user experience Tom Connors, SciEthis Interactive 2012 Second Life and Open Sim each have a built in system for editing the virtual world that allows
INSTALLING, CONFIGURING, AND DEVELOPING WITH XAMPP
 INSTALLING, CONFIGURING, AND DEVELOPING WITH XAMPP by Dalibor D. Dvorski, March 2007 Skills Canada Ontario DISCLAIMER: A lot of care has been taken in the accuracy of information provided in this article,
INSTALLING, CONFIGURING, AND DEVELOPING WITH XAMPP by Dalibor D. Dvorski, March 2007 Skills Canada Ontario DISCLAIMER: A lot of care has been taken in the accuracy of information provided in this article,
Installation Instructions
 WampServer Installation Instructions The Web pages that students create in CIT 173 PHP Programming contain code that must be processed by a Web server. It isn t possible to open PHP files directly using
WampServer Installation Instructions The Web pages that students create in CIT 173 PHP Programming contain code that must be processed by a Web server. It isn t possible to open PHP files directly using
Preventing SQL Injection and XSS Attacks. ACM Webmonkeys, 2011
 Preventing SQL Injection and XSS Attacks ACM Webmonkeys, 2011 The need for security Any website you develop, whether personal or for a business, should be reasonably secured. "Reasonably", because you
Preventing SQL Injection and XSS Attacks ACM Webmonkeys, 2011 The need for security Any website you develop, whether personal or for a business, should be reasonably secured. "Reasonably", because you
A Brief Introduction to MySQL
 A Brief Introduction to MySQL by Derek Schuurman Introduction to Databases A database is a structured collection of logically related data. One common type of database is the relational database, a term
A Brief Introduction to MySQL by Derek Schuurman Introduction to Databases A database is a structured collection of logically related data. One common type of database is the relational database, a term
G563 Quantitative Paleontology. SQL databases. An introduction. Department of Geological Sciences Indiana University. (c) 2012, P.
 SQL databases An introduction AMP: Apache, mysql, PHP This installations installs the Apache webserver, the PHP scripting language, and the mysql database on your computer: Apache: runs in the background
SQL databases An introduction AMP: Apache, mysql, PHP This installations installs the Apache webserver, the PHP scripting language, and the mysql database on your computer: Apache: runs in the background
Installing Drupal on Your Local Computer
 Installing Drupal on Your Local Computer This tutorial will help you install Drupal on your own home computer and allow you to test and experiment building a Web site using this open source software. This
Installing Drupal on Your Local Computer This tutorial will help you install Drupal on your own home computer and allow you to test and experiment building a Web site using this open source software. This
Seamless Web Data Entry for SAS Applications D.J. Penix, Pinnacle Solutions, Indianapolis, IN
 Seamless Web Data Entry for SAS Applications D.J. Penix, Pinnacle Solutions, Indianapolis, IN ABSTRACT For organizations that need to implement a robust data entry solution, options are somewhat limited
Seamless Web Data Entry for SAS Applications D.J. Penix, Pinnacle Solutions, Indianapolis, IN ABSTRACT For organizations that need to implement a robust data entry solution, options are somewhat limited
Certified PHP/MySQL Web Developer Course
 Course Duration : 3 Months (120 Hours) Day 1 Introduction to PHP 1.PHP web architecture 2.PHP wamp server installation 3.First PHP program 4.HTML with php 5.Comments and PHP manual usage Day 2 Variables,
Course Duration : 3 Months (120 Hours) Day 1 Introduction to PHP 1.PHP web architecture 2.PHP wamp server installation 3.First PHP program 4.HTML with php 5.Comments and PHP manual usage Day 2 Variables,
Web Programming with PHP 5. The right tool for the right job.
 Web Programming with PHP 5 The right tool for the right job. PHP as an Acronym PHP PHP: Hypertext Preprocessor This is called a Recursive Acronym GNU? GNU s Not Unix! CYGNUS? CYGNUS is Your GNU Support
Web Programming with PHP 5 The right tool for the right job. PHP as an Acronym PHP PHP: Hypertext Preprocessor This is called a Recursive Acronym GNU? GNU s Not Unix! CYGNUS? CYGNUS is Your GNU Support
Setting Up a Development Server
 2 Setting Up a Development Server If you wish to develop Internet applications but don t have your own development server, you will have to upload every modification you make to a server somewhere else
2 Setting Up a Development Server If you wish to develop Internet applications but don t have your own development server, you will have to upload every modification you make to a server somewhere else
Integrated Network Vulnerability Scanning & Penetration Testing SAINTcorporation.com
 SAINT Integrated Network Vulnerability Scanning and Penetration Testing www.saintcorporation.com Introduction While network vulnerability scanning is an important tool in proactive network security, penetration
SAINT Integrated Network Vulnerability Scanning and Penetration Testing www.saintcorporation.com Introduction While network vulnerability scanning is an important tool in proactive network security, penetration
Web development... the server side (of the force)
 Web development... the server side (of the force) Fabien POULARD Document under license Creative Commons Attribution Share Alike 2.5 http://www.creativecommons.org/learnmore Web development... the server
Web development... the server side (of the force) Fabien POULARD Document under license Creative Commons Attribution Share Alike 2.5 http://www.creativecommons.org/learnmore Web development... the server
SQL Injection Attack Lab Using Collabtive
 Laboratory for Computer Security Education 1 SQL Injection Attack Lab Using Collabtive (Web Application: Collabtive) Copyright c 2006-2011 Wenliang Du, Syracuse University. The development of this document
Laboratory for Computer Security Education 1 SQL Injection Attack Lab Using Collabtive (Web Application: Collabtive) Copyright c 2006-2011 Wenliang Du, Syracuse University. The development of this document
CEFNS Web Hosting a Guide for CS212
 CEFNS Web Hosting a Guide for CS212 INTRODUCTION: TOOLS: In CS212, you will be learning the basics of web development. Therefore, you want to keep your tools to a minimum so that you understand how things
CEFNS Web Hosting a Guide for CS212 INTRODUCTION: TOOLS: In CS212, you will be learning the basics of web development. Therefore, you want to keep your tools to a minimum so that you understand how things
SQL Injection. Blossom Hands-on exercises for computer forensics and security
 Copyright: The development of this document is funded by Higher Education of Academy. Permission is granted to copy, distribute and /or modify this document under a license compliant with the Creative
Copyright: The development of this document is funded by Higher Education of Academy. Permission is granted to copy, distribute and /or modify this document under a license compliant with the Creative
Bug Report. Date: March 19, 2011 Reporter: Chris Jarabek (cjjarabe@ucalgary.ca)
 Bug Report Date: March 19, 2011 Reporter: Chris Jarabek (cjjarabe@ucalgary.ca) Software: Kimai Version: 0.9.1.1205 Website: http://www.kimai.org Description: Kimai is a web based time-tracking application.
Bug Report Date: March 19, 2011 Reporter: Chris Jarabek (cjjarabe@ucalgary.ca) Software: Kimai Version: 0.9.1.1205 Website: http://www.kimai.org Description: Kimai is a web based time-tracking application.
Server side scripting and databases
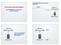 Three components used in typical web application Server side scripting and databases How Web Applications interact with server side databases Browser Web server Database server Web server Web server Apache
Three components used in typical web application Server side scripting and databases How Web Applications interact with server side databases Browser Web server Database server Web server Web server Apache
Working with forms in PHP
 2002-6-29 Synopsis In this tutorial, you will learn how to use forms with PHP. Page 1 Forms and PHP One of the most popular ways to make a web site interactive is the use of forms. With forms you can have
2002-6-29 Synopsis In this tutorial, you will learn how to use forms with PHP. Page 1 Forms and PHP One of the most popular ways to make a web site interactive is the use of forms. With forms you can have
DIPLOMA IN WEBDEVELOPMENT
 DIPLOMA IN WEBDEVELOPMENT Prerequisite skills Basic programming knowledge on C Language or Core Java is must. # Module 1 Basics and introduction to HTML Basic HTML training. Different HTML elements, tags
DIPLOMA IN WEBDEVELOPMENT Prerequisite skills Basic programming knowledge on C Language or Core Java is must. # Module 1 Basics and introduction to HTML Basic HTML training. Different HTML elements, tags
Short notes on webpage programming languages
 Short notes on webpage programming languages What is HTML? HTML is a language for describing web pages. HTML stands for Hyper Text Markup Language HTML is a markup language A markup language is a set of
Short notes on webpage programming languages What is HTML? HTML is a language for describing web pages. HTML stands for Hyper Text Markup Language HTML is a markup language A markup language is a set of
Cyber Security Workshop Ethical Web Hacking
 Cyber Security Workshop Ethical Web Hacking May 2015 Setting up WebGoat and Burp Suite Hacking Challenges in WebGoat Concepts in Web Technologies and Ethical Hacking 1 P a g e Downloading WebGoat and Burp
Cyber Security Workshop Ethical Web Hacking May 2015 Setting up WebGoat and Burp Suite Hacking Challenges in WebGoat Concepts in Web Technologies and Ethical Hacking 1 P a g e Downloading WebGoat and Burp
SECURING APACHE : THE BASICS - III
 SECURING APACHE : THE BASICS - III Securing your applications learn how break-ins occur Shown in Figure 2 is a typical client-server Web architecture, which also indicates various attack vectors, or ways
SECURING APACHE : THE BASICS - III Securing your applications learn how break-ins occur Shown in Figure 2 is a typical client-server Web architecture, which also indicates various attack vectors, or ways
Drupal CMS for marketing sites
 Drupal CMS for marketing sites Intro Sample sites: End to End flow Folder Structure Project setup Content Folder Data Store (Drupal CMS) Importing/Exporting Content Database Migrations Backend Config Unit
Drupal CMS for marketing sites Intro Sample sites: End to End flow Folder Structure Project setup Content Folder Data Store (Drupal CMS) Importing/Exporting Content Database Migrations Backend Config Unit
An Email Newsletter Using ASP Smart Mailer and Advanced HTML Editor
 An Email Newsletter Using ASP Smart Mailer and Advanced HTML Editor This tutorial is going to take you through creating a mailing list application to send out a newsletter for your site. We'll be using
An Email Newsletter Using ASP Smart Mailer and Advanced HTML Editor This tutorial is going to take you through creating a mailing list application to send out a newsletter for your site. We'll be using
Precondition for a good understanding: knowledge of a higher programming language (e.g. C, Java, Perl, Pascal, Basic,... ) basic knowledge of html
 Some Remarks about Dynamic Webpages Matthias K. Krause Hochschule für Telekommunikation, Leipzig University of Applied Sciences Deutsche Telekom krause@hft-leipzig.de Precondition for a good understanding:
Some Remarks about Dynamic Webpages Matthias K. Krause Hochschule für Telekommunikation, Leipzig University of Applied Sciences Deutsche Telekom krause@hft-leipzig.de Precondition for a good understanding:
Application security testing: Protecting your application and data
 E-Book Application security testing: Protecting your application and data Application security testing is critical in ensuring your data and application is safe from security attack. This ebook offers
E-Book Application security testing: Protecting your application and data Application security testing is critical in ensuring your data and application is safe from security attack. This ebook offers
Web Development using PHP (WD_PHP) Duration 1.5 months
 Duration 1.5 months Our program is a practical knowledge oriented program aimed at learning the techniques of web development using PHP, HTML, CSS & JavaScript. It has some unique features which are as
Duration 1.5 months Our program is a practical knowledge oriented program aimed at learning the techniques of web development using PHP, HTML, CSS & JavaScript. It has some unique features which are as
UQC103S1 UFCE47-20-1. Systems Development. uqc103s/ufce47-20-1 PHP-mySQL 1
 UQC103S1 UFCE47-20-1 Systems Development uqc103s/ufce47-20-1 PHP-mySQL 1 Who? Email: uqc103s1@uwe.ac.uk Web Site www.cems.uwe.ac.uk/~jedawson www.cems.uwe.ac.uk/~jtwebb/uqc103s1/ uqc103s/ufce47-20-1 PHP-mySQL
UQC103S1 UFCE47-20-1 Systems Development uqc103s/ufce47-20-1 PHP-mySQL 1 Who? Email: uqc103s1@uwe.ac.uk Web Site www.cems.uwe.ac.uk/~jedawson www.cems.uwe.ac.uk/~jtwebb/uqc103s1/ uqc103s/ufce47-20-1 PHP-mySQL
Advanced PostgreSQL SQL Injection and Filter Bypass Techniques
 Advanced PostgreSQL SQL Injection and Filter Bypass Techniques INFIGO-TD TD-200 2009-04 2009-06 06-17 Leon Juranić leon.juranic@infigo.hr INFIGO IS. All rights reserved. This document contains information
Advanced PostgreSQL SQL Injection and Filter Bypass Techniques INFIGO-TD TD-200 2009-04 2009-06 06-17 Leon Juranić leon.juranic@infigo.hr INFIGO IS. All rights reserved. This document contains information
Kollaborate Server Installation Guide!! 1. Kollaborate Server! Installation Guide!
 Kollaborate Server Installation Guide 1 Kollaborate Server Installation Guide Kollaborate Server is a local implementation of the Kollaborate cloud workflow system that allows you to run the service in-house
Kollaborate Server Installation Guide 1 Kollaborate Server Installation Guide Kollaborate Server is a local implementation of the Kollaborate cloud workflow system that allows you to run the service in-house
IE Class Web Design Curriculum
 Course Outline Web Technologies 130.279 IE Class Web Design Curriculum Unit 1: Foundations s The Foundation lessons will provide students with a general understanding of computers, how the internet works,
Course Outline Web Technologies 130.279 IE Class Web Design Curriculum Unit 1: Foundations s The Foundation lessons will provide students with a general understanding of computers, how the internet works,
INTRODUCTION TO WEB TECHNOLOGY
 UNIT-I Introduction to Web Technologies: Introduction to web servers like Apache1.1, IIS, XAMPP (Bundle Server), WAMP Server(Bundle Server), handling HTTP Request and Response, installation of above servers
UNIT-I Introduction to Web Technologies: Introduction to web servers like Apache1.1, IIS, XAMPP (Bundle Server), WAMP Server(Bundle Server), handling HTTP Request and Response, installation of above servers
Project 2: Web Security Pitfalls
 EECS 388 September 19, 2014 Intro to Computer Security Project 2: Web Security Pitfalls Project 2: Web Security Pitfalls This project is due on Thursday, October 9 at 6 p.m. and counts for 8% of your course
EECS 388 September 19, 2014 Intro to Computer Security Project 2: Web Security Pitfalls Project 2: Web Security Pitfalls This project is due on Thursday, October 9 at 6 p.m. and counts for 8% of your course
External Network & Web Application Assessment. For The XXX Group LLC October 2012
 External Network & Web Application Assessment For The XXX Group LLC October 2012 This report is solely for the use of client personal. No part of it may be circulated, quoted, or reproduced for distribution
External Network & Web Application Assessment For The XXX Group LLC October 2012 This report is solely for the use of client personal. No part of it may be circulated, quoted, or reproduced for distribution
INFORMATION BROCHURE Certificate Course in Web Design Using PHP/MySQL
 INFORMATION BROCHURE OF Certificate Course in Web Design Using PHP/MySQL National Institute of Electronics & Information Technology (An Autonomous Scientific Society of Department of Information Technology,
INFORMATION BROCHURE OF Certificate Course in Web Design Using PHP/MySQL National Institute of Electronics & Information Technology (An Autonomous Scientific Society of Department of Information Technology,
CS 361S - Network Security and Privacy Fall 2015. Project #1
 CS 361S - Network Security and Privacy Fall 2015 Project #1 Due: 12:30pm CST, October 8, 2015 Submission instructions Follow the instructions in the project description. If you are submitting late, please
CS 361S - Network Security and Privacy Fall 2015 Project #1 Due: 12:30pm CST, October 8, 2015 Submission instructions Follow the instructions in the project description. If you are submitting late, please
PHP ON A FAST TRACK INTRODUCTION: ROADMAP BY JAROSLAW FRANCIK. Companion web site: http:// php.francik.name
 PHP ON A FAST TRACK BY JAROSLAW FRANCIK Companion web site: http:// php.francik.name Writing web based, database connected applications in PHP is not difficult, however many people get stuck on just the
PHP ON A FAST TRACK BY JAROSLAW FRANCIK Companion web site: http:// php.francik.name Writing web based, database connected applications in PHP is not difficult, however many people get stuck on just the
INTEGRATING MICROSOFT DYNAMICS CRM WITH SIMEGO DS3
 INTEGRATING MICROSOFT DYNAMICS CRM WITH SIMEGO DS3 Often the most compelling way to introduce yourself to a software product is to try deliver value as soon as possible. Simego DS3 is designed to get you
INTEGRATING MICROSOFT DYNAMICS CRM WITH SIMEGO DS3 Often the most compelling way to introduce yourself to a software product is to try deliver value as soon as possible. Simego DS3 is designed to get you
Getting Started with Dynamic Web Sites
 PHP Tutorial 1 Getting Started with Dynamic Web Sites Setting Up Your Computer To follow this tutorial, you ll need to have PHP, MySQL and a Web server up and running on your computer. This will be your
PHP Tutorial 1 Getting Started with Dynamic Web Sites Setting Up Your Computer To follow this tutorial, you ll need to have PHP, MySQL and a Web server up and running on your computer. This will be your
CTIS 256 Web Technologies II. Week # 1 Serkan GENÇ
 CTIS 256 Web Technologies II Week # 1 Serkan GENÇ Introduction Aim: to be able to develop web-based applications using PHP (programming language) and mysql(dbms). Internet is a huge network structure connecting
CTIS 256 Web Technologies II Week # 1 Serkan GENÇ Introduction Aim: to be able to develop web-based applications using PHP (programming language) and mysql(dbms). Internet is a huge network structure connecting
Ruby on Rails Secure Coding Recommendations
 Introduction Altius IT s list of Ruby on Rails Secure Coding Recommendations is based upon security best practices. This list may not be complete and Altius IT recommends this list be augmented with additional
Introduction Altius IT s list of Ruby on Rails Secure Coding Recommendations is based upon security best practices. This list may not be complete and Altius IT recommends this list be augmented with additional
PHP+MYSQL, EASYPHP INSTALLATION GUIDE
 PHP+MYSQL, EASYPHP INSTALLATION GUIDE EasyPhp is a tool to install and configure an Apache server along with a database manager, MySQL. Download the latest version from http://www.easyphp.org/ as seen
PHP+MYSQL, EASYPHP INSTALLATION GUIDE EasyPhp is a tool to install and configure an Apache server along with a database manager, MySQL. Download the latest version from http://www.easyphp.org/ as seen
SQL Injection. Slides thanks to Prof. Shmatikov at UT Austin
 SQL Injection Slides thanks to Prof. Shmatikov at UT Austin Dynamic Web Application GET / HTTP/1.0 Browser HTTP/1.1 200 OK Web server index.php Database server slide 2 PHP: Hypertext Preprocessor Server
SQL Injection Slides thanks to Prof. Shmatikov at UT Austin Dynamic Web Application GET / HTTP/1.0 Browser HTTP/1.1 200 OK Web server index.php Database server slide 2 PHP: Hypertext Preprocessor Server
SQL Injection Attack Lab
 Laboratory for Computer Security Education 1 SQL Injection Attack Lab Copyright c 2006-2010 Wenliang Du, Syracuse University. The development of this document is funded by the National Science Foundation
Laboratory for Computer Security Education 1 SQL Injection Attack Lab Copyright c 2006-2010 Wenliang Du, Syracuse University. The development of this document is funded by the National Science Foundation
Web Application Security
 Web Application Security John Zaharopoulos ITS - Security 10/9/2012 1 Web App Security Trends Web 2.0 Dynamic Webpages Growth of Ajax / Client side Javascript Hardening of OSes Secure by default Auto-patching
Web Application Security John Zaharopoulos ITS - Security 10/9/2012 1 Web App Security Trends Web 2.0 Dynamic Webpages Growth of Ajax / Client side Javascript Hardening of OSes Secure by default Auto-patching
Multimedia im Netz Online Multimedia Winter semester 2015/16. Tutorial 02 Minor Subject
 Multimedia im Netz Online Multimedia Winter semester 2015/16 Tutorial 02 Minor Subject Ludwig- Maximilians- Universität München Online Multimedia WS 2015/16 - Tutorial 02 for minor subject students 1 Today
Multimedia im Netz Online Multimedia Winter semester 2015/16 Tutorial 02 Minor Subject Ludwig- Maximilians- Universität München Online Multimedia WS 2015/16 - Tutorial 02 for minor subject students 1 Today
Lesson 7 - Website Administration
 Lesson 7 - Website Administration If you are hired as a web designer, your client will most likely expect you do more than just create their website. They will expect you to also know how to get their
Lesson 7 - Website Administration If you are hired as a web designer, your client will most likely expect you do more than just create their website. They will expect you to also know how to get their
Setting up a local working copy with SVN, MAMP and rsync. Agentic - 2009
 Setting up a local working copy with SVN, MAMP and rsync Agentic - 2009 Get MAMP You can download MAMP for MAC at this address : http://www.mamp.info/en/downloads/index.html Install MAMP in your APPLICATION
Setting up a local working copy with SVN, MAMP and rsync Agentic - 2009 Get MAMP You can download MAMP for MAC at this address : http://www.mamp.info/en/downloads/index.html Install MAMP in your APPLICATION
Installation of PHP, MariaDB, and Apache
 Installation of PHP, MariaDB, and Apache A few years ago, one would have had to walk over to the closest pizza store to order a pizza, go over to the bank to transfer money from one account to another
Installation of PHP, MariaDB, and Apache A few years ago, one would have had to walk over to the closest pizza store to order a pizza, go over to the bank to transfer money from one account to another
So we're set? Have your text-editor ready. Be sure you use NotePad, NOT Word or even WordPad. Great, let's get going.
 Web Design 1A First Website Intro to Basic HTML So we're set? Have your text-editor ready. Be sure you use NotePad, NOT Word or even WordPad. Great, let's get going. Ok, let's just go through the steps
Web Design 1A First Website Intro to Basic HTML So we're set? Have your text-editor ready. Be sure you use NotePad, NOT Word or even WordPad. Great, let's get going. Ok, let's just go through the steps
Installing an open source version of MateCat
 Installing an open source version of MateCat This guide is meant for users who want to install and administer the open source version on their own machines. Overview 1 Hardware requirements 2 Getting started
Installing an open source version of MateCat This guide is meant for users who want to install and administer the open source version on their own machines. Overview 1 Hardware requirements 2 Getting started
Modelling with R and MySQL. - Manual - Gesine Bökenkamp, Frauke Wiese, Clemens Wingenbach
 Modelling with R and MySQL - Manual - Gesine Bökenkamp, Frauke Wiese, Clemens Wingenbach October 27, 2014 1 Contents 1 Software Installation 3 1.1 Database...................................... 3 1.1.1
Modelling with R and MySQL - Manual - Gesine Bökenkamp, Frauke Wiese, Clemens Wingenbach October 27, 2014 1 Contents 1 Software Installation 3 1.1 Database...................................... 3 1.1.1
Secure Web Application Coding Team Introductory Meeting December 1, 2005 1:00 2:00PM Bits & Pieces Room, Sansom West Room 306 Agenda
 Secure Web Application Coding Team Introductory Meeting December 1, 2005 1:00 2:00PM Bits & Pieces Room, Sansom West Room 306 Agenda 1. Introductions for new members (5 minutes) 2. Name of group 3. Current
Secure Web Application Coding Team Introductory Meeting December 1, 2005 1:00 2:00PM Bits & Pieces Room, Sansom West Room 306 Agenda 1. Introductions for new members (5 minutes) 2. Name of group 3. Current
Build it with Drupal 8
 Build it with Drupal 8 Comprehensive guide for building common websites in Drupal 8. No programming knowledge required! Antonio Torres This book is for sale at http://leanpub.com/drupal-8-book This version
Build it with Drupal 8 Comprehensive guide for building common websites in Drupal 8. No programming knowledge required! Antonio Torres This book is for sale at http://leanpub.com/drupal-8-book This version
A SQL Injection : Internal Investigation of Injection, Detection and Prevention of SQL Injection Attacks
 A SQL Injection : Internal Investigation of Injection, Detection and Prevention of SQL Injection Attacks Abhay K. Kolhe Faculty, Dept. Of Computer Engineering MPSTME, NMIMS Mumbai, India Pratik Adhikari
A SQL Injection : Internal Investigation of Injection, Detection and Prevention of SQL Injection Attacks Abhay K. Kolhe Faculty, Dept. Of Computer Engineering MPSTME, NMIMS Mumbai, India Pratik Adhikari
Institutionen för datavetenskap
 Institutionen för datavetenskap Department of Computer and Information Science Final thesis Generating web applications containing XSS and CSRF vulnerabilities by Gustav Ahlberg LIU-IDA/LITH-EX-A--14/054--SE
Institutionen för datavetenskap Department of Computer and Information Science Final thesis Generating web applications containing XSS and CSRF vulnerabilities by Gustav Ahlberg LIU-IDA/LITH-EX-A--14/054--SE
Finding XSS in Real World
 Finding XSS in Real World by Alexander Korznikov nopernik@gmail.com 1 April 2015 Hi there, in this tutorial, I will try to explain how to find XSS in real world, using some interesting techniques. All
Finding XSS in Real World by Alexander Korznikov nopernik@gmail.com 1 April 2015 Hi there, in this tutorial, I will try to explain how to find XSS in real world, using some interesting techniques. All
MASTERTAG DEVELOPER GUIDE
 MASTERTAG DEVELOPER GUIDE TABLE OF CONTENTS 1 Introduction... 4 1.1 What is the zanox MasterTag?... 4 1.2 What is the zanox page type?... 4 2 Create a MasterTag application in the zanox Application Store...
MASTERTAG DEVELOPER GUIDE TABLE OF CONTENTS 1 Introduction... 4 1.1 What is the zanox MasterTag?... 4 1.2 What is the zanox page type?... 4 2 Create a MasterTag application in the zanox Application Store...
SQL Injection. By Artem Kazanstev, ITSO and Alex Beutel, Student
 SQL Injection By Artem Kazanstev, ITSO and Alex Beutel, Student SANS Priority No 2 As of September 2009, Web application vulnerabilities such as SQL injection and Cross-Site Scripting flaws in open-source
SQL Injection By Artem Kazanstev, ITSO and Alex Beutel, Student SANS Priority No 2 As of September 2009, Web application vulnerabilities such as SQL injection and Cross-Site Scripting flaws in open-source
Using the Push Notifications Extension Part 1: Certificates and Setup
 // tutorial Using the Push Notifications Extension Part 1: Certificates and Setup Version 1.0 This tutorial is the second part of our tutorials covering setting up and running the Push Notifications Native
// tutorial Using the Push Notifications Extension Part 1: Certificates and Setup Version 1.0 This tutorial is the second part of our tutorials covering setting up and running the Push Notifications Native
5 Mistakes to Avoid on Your Drupal Website
 5 Mistakes to Avoid on Your Drupal Website Table of Contents Introduction.... 3 Architecture: Content.... 4 Architecture: Display... 5 Architecture: Site or Functionality.... 6 Security.... 8 Performance...
5 Mistakes to Avoid on Your Drupal Website Table of Contents Introduction.... 3 Architecture: Content.... 4 Architecture: Display... 5 Architecture: Site or Functionality.... 6 Security.... 8 Performance...
FileMaker 12. ODBC and JDBC Guide
 FileMaker 12 ODBC and JDBC Guide 2004 2012 FileMaker, Inc. All Rights Reserved. FileMaker, Inc. 5201 Patrick Henry Drive Santa Clara, California 95054 FileMaker and Bento are trademarks of FileMaker, Inc.
FileMaker 12 ODBC and JDBC Guide 2004 2012 FileMaker, Inc. All Rights Reserved. FileMaker, Inc. 5201 Patrick Henry Drive Santa Clara, California 95054 FileMaker and Bento are trademarks of FileMaker, Inc.
STABLE & SECURE BANK lab writeup. Page 1 of 21
 STABLE & SECURE BANK lab writeup 1 of 21 Penetrating an imaginary bank through real present-date security vulnerabilities PENTESTIT, a Russian Information Security company has launched its new, eighth
STABLE & SECURE BANK lab writeup 1 of 21 Penetrating an imaginary bank through real present-date security vulnerabilities PENTESTIT, a Russian Information Security company has launched its new, eighth
Real SQL Programming 1
 Real 1 We have seen only how SQL is used at the generic query interface an environment where we sit at a terminal and ask queries of a database. Reality is almost always different: conventional programs
Real 1 We have seen only how SQL is used at the generic query interface an environment where we sit at a terminal and ask queries of a database. Reality is almost always different: conventional programs
REDCap General Security Overview
 REDCap General Security Overview Introduction REDCap is a web application for building and managing online surveys and databases, and thus proper security practices must instituted on the network and server(s)
REDCap General Security Overview Introduction REDCap is a web application for building and managing online surveys and databases, and thus proper security practices must instituted on the network and server(s)
Welcome to Collage (Draft v0.1)
 Welcome to Collage (Draft v0.1) Table of Contents Welcome to Collage (Draft v0.1)... 1 Table of Contents... 1 Overview... 2 What is Collage?... 3 Getting started... 4 Searching for Images in Collage...
Welcome to Collage (Draft v0.1) Table of Contents Welcome to Collage (Draft v0.1)... 1 Table of Contents... 1 Overview... 2 What is Collage?... 3 Getting started... 4 Searching for Images in Collage...
CSE598i - Web 2.0 Security OWASP Top 10: The Ten Most Critical Web Application Security Vulnerabilities
 CSE598i - Web 2.0 Security OWASP Top 10: The Ten Most Critical Web Application Security Vulnerabilities Thomas Moyer Spring 2010 1 Web Applications What has changed with web applications? Traditional applications
CSE598i - Web 2.0 Security OWASP Top 10: The Ten Most Critical Web Application Security Vulnerabilities Thomas Moyer Spring 2010 1 Web Applications What has changed with web applications? Traditional applications
Penetration Test Report
 Penetration Test Report Acme Test Company ACMEIT System 26 th November 2010 Executive Summary Info-Assure Ltd was engaged by Acme Test Company to perform an IT Health Check (ITHC) on the ACMEIT System
Penetration Test Report Acme Test Company ACMEIT System 26 th November 2010 Executive Summary Info-Assure Ltd was engaged by Acme Test Company to perform an IT Health Check (ITHC) on the ACMEIT System
Introduction. Just So You Know... PCI Can Be Difficult
 Introduction For some organizations, the prospect of managing servers is daunting. Fortunately, traditional hosting companies offer an affordable alternative. Picking the right vendor and package is critial
Introduction For some organizations, the prospect of managing servers is daunting. Fortunately, traditional hosting companies offer an affordable alternative. Picking the right vendor and package is critial
Lecture 9 Chrome Extensions
 Lecture 9 Chrome Extensions 1 / 22 Agenda 1. Chrome Extensions 1. Manifest files 2. Content Scripts 3. Background Pages 4. Page Actions 5. Browser Actions 2 / 22 Chrome Extensions 3 / 22 What are browser
Lecture 9 Chrome Extensions 1 / 22 Agenda 1. Chrome Extensions 1. Manifest files 2. Content Scripts 3. Background Pages 4. Page Actions 5. Browser Actions 2 / 22 Chrome Extensions 3 / 22 What are browser
Drupal + Formulize. A Step-by-Step Guide to Integrating Drupal with XOOPS/ImpressCMS, and installing and using the Formulize module
 Drupal + Formulize A Step-by-Step Guide to Integrating Drupal with XOOPS/ImpressCMS, and installing and using the Formulize module May 16, 2007 Updated December 23, 2009 This document has been prepared
Drupal + Formulize A Step-by-Step Guide to Integrating Drupal with XOOPS/ImpressCMS, and installing and using the Formulize module May 16, 2007 Updated December 23, 2009 This document has been prepared
AJAX with jquery. ACM Webmonkeys 2011
 AJAX with jquery ACM Webmonkeys 2011 What is AJAX? AJAX is a technology used to facilitate real-time data changes and updates on a page without requiring a page reload. AJAX stands for Asynchronous Javascript
AJAX with jquery ACM Webmonkeys 2011 What is AJAX? AJAX is a technology used to facilitate real-time data changes and updates on a page without requiring a page reload. AJAX stands for Asynchronous Javascript
Advanced Tornado TWENTYONE. 21.1 Advanced Tornado. 21.2 Accessing MySQL from Python LAB
 21.1 Advanced Tornado Advanced Tornado One of the main reasons we might want to use a web framework like Tornado is that they hide a lot of the boilerplate stuff that we don t really care about, like escaping
21.1 Advanced Tornado Advanced Tornado One of the main reasons we might want to use a web framework like Tornado is that they hide a lot of the boilerplate stuff that we don t really care about, like escaping
Version of this tutorial: 1.06a (this tutorial will going to evolve with versions of NWNX4)
 Version of this tutorial: 1.06a (this tutorial will going to evolve with versions of NWNX4) The purpose of this document is to help a beginner to install all the elements necessary to use NWNX4. Throughout
Version of this tutorial: 1.06a (this tutorial will going to evolve with versions of NWNX4) The purpose of this document is to help a beginner to install all the elements necessary to use NWNX4. Throughout
Online shopping store
 Online shopping store 1. Research projects: A physical shop can only serves the people locally. An online shopping store can resolve the geometrical boundary faced by the physical shop. It has other advantages,
Online shopping store 1. Research projects: A physical shop can only serves the people locally. An online shopping store can resolve the geometrical boundary faced by the physical shop. It has other advantages,
Advanced Web Development SCOPE OF WEB DEVELOPMENT INDUSTRY
 Advanced Web Development Duration: 6 Months SCOPE OF WEB DEVELOPMENT INDUSTRY Web development jobs have taken thе hot seat when it comes to career opportunities and positions as a Web developer, as every
Advanced Web Development Duration: 6 Months SCOPE OF WEB DEVELOPMENT INDUSTRY Web development jobs have taken thе hot seat when it comes to career opportunities and positions as a Web developer, as every
Web Application Guidelines
 Web Application Guidelines Web applications have become one of the most important topics in the security field. This is for several reasons: It can be simple for anyone to create working code without security
Web Application Guidelines Web applications have become one of the most important topics in the security field. This is for several reasons: It can be simple for anyone to create working code without security
Multimedia im Netz Online Multimedia Winter semester 2015/16
 Multimedia im Netz Online Multimedia Winter semester 2015/16 Tutorial 04 Minor Subject Ludwig-Maximilians-Universität München Online Multimedia WS 2015/16 - Tutorial 04 (NF) - 1 Today s Agenda Repetition:
Multimedia im Netz Online Multimedia Winter semester 2015/16 Tutorial 04 Minor Subject Ludwig-Maximilians-Universität München Online Multimedia WS 2015/16 - Tutorial 04 (NF) - 1 Today s Agenda Repetition:
Web Development. Owen Sacco. ICS2205/ICS2230 Web Intelligence
 Web Development Owen Sacco ICS2205/ICS2230 Web Intelligence 2. Web Servers Introduction Web content lives on Web servers Web servers speak the platform independent HyperText Transfer Protocol (HTTP) (so
Web Development Owen Sacco ICS2205/ICS2230 Web Intelligence 2. Web Servers Introduction Web content lives on Web servers Web servers speak the platform independent HyperText Transfer Protocol (HTTP) (so
5. At the Windows Component panel, select the Internet Information Services (IIS) checkbox, and then hit Next.
 Installing IIS on Windows XP 1. Start 2. Go to Control Panel 3. Go to Add or RemovePrograms 4. Go to Add/Remove Windows Components 5. At the Windows Component panel, select the Internet Information Services
Installing IIS on Windows XP 1. Start 2. Go to Control Panel 3. Go to Add or RemovePrograms 4. Go to Add/Remove Windows Components 5. At the Windows Component panel, select the Internet Information Services
Intro to Web Design. ACM Webmonkeys @ UIUC
 Intro to Web Design ACM Webmonkeys @ UIUC How do websites work? Note that a similar procedure is used to load images, etc. What is HTML? An HTML file is just a plain text file. You can write all your HTML
Intro to Web Design ACM Webmonkeys @ UIUC How do websites work? Note that a similar procedure is used to load images, etc. What is HTML? An HTML file is just a plain text file. You can write all your HTML
The Whole OS X Web Development System
 The Whole OS X Web Development Title slide Building PHP/MySQL Web Databases for OS X Scot Hacker Webmaster, UC Berkeley s Graduate School of Journalism The Macworld Conference on Dreamweaver January 6-7,
The Whole OS X Web Development Title slide Building PHP/MySQL Web Databases for OS X Scot Hacker Webmaster, UC Berkeley s Graduate School of Journalism The Macworld Conference on Dreamweaver January 6-7,
A table is a collection of related data entries and it consists of columns and rows.
 CST 250 MySQL Notes (Source: www.w3schools.com) MySQL is the most popular open-source database system. What is MySQL? MySQL is a database. The data in MySQL is stored in database objects called tables.
CST 250 MySQL Notes (Source: www.w3schools.com) MySQL is the most popular open-source database system. What is MySQL? MySQL is a database. The data in MySQL is stored in database objects called tables.
A REST API for Arduino & the CC3000 WiFi Chip
 A REST API for Arduino & the CC3000 WiFi Chip Created by Marc-Olivier Schwartz Last updated on 2014-04-22 03:01:12 PM EDT Guide Contents Guide Contents Overview Hardware configuration Installing the library
A REST API for Arduino & the CC3000 WiFi Chip Created by Marc-Olivier Schwartz Last updated on 2014-04-22 03:01:12 PM EDT Guide Contents Guide Contents Overview Hardware configuration Installing the library
Web Applications Security: SQL Injection Attack
 Web Applications Security: SQL Injection Attack S. C. Kothari CPRE 556: Lecture 8, February 2, 2006 Electrical and Computer Engineering Dept. Iowa State University SQL Injection: What is it A technique
Web Applications Security: SQL Injection Attack S. C. Kothari CPRE 556: Lecture 8, February 2, 2006 Electrical and Computer Engineering Dept. Iowa State University SQL Injection: What is it A technique
Drupal 101. Introduction to Drupal. October 10, 2015 nedcamp.org
 Drupal 101 Introduction to Drupal October 10, 2015 nedcamp.org Rick Hood richard.hood@commonmediainc.com richardhoodcreative@gmail.com www.drupal.org/user/54879 2011 - present Project Manager & Drupal
Drupal 101 Introduction to Drupal October 10, 2015 nedcamp.org Rick Hood richard.hood@commonmediainc.com richardhoodcreative@gmail.com www.drupal.org/user/54879 2011 - present Project Manager & Drupal
mylittleadmin for MS SQL Server 2005 from a Webhosting Perspective Anthony Wilko President, Infuseweb LLC
 mylittleadmin for MS SQL Server 2005 from a Webhosting Perspective Anthony Wilko President, Infuseweb LLC April 2008 Introduction f there's one thing constant in the IT and hosting industries, it's that
mylittleadmin for MS SQL Server 2005 from a Webhosting Perspective Anthony Wilko President, Infuseweb LLC April 2008 Introduction f there's one thing constant in the IT and hosting industries, it's that
4 Understanding. Web Applications IN THIS CHAPTER. 4.1 Understand Web page development. 4.2 Understand Microsoft ASP.NET Web application development
 4 Understanding Web Applications IN THIS CHAPTER 4.1 Understand Web page development 4.2 Understand Microsoft ASP.NET Web application development 4.3 Understand Web hosting 4.4 Understand Web services
4 Understanding Web Applications IN THIS CHAPTER 4.1 Understand Web page development 4.2 Understand Microsoft ASP.NET Web application development 4.3 Understand Web hosting 4.4 Understand Web services
Getting Started with AWS. Hosting a Static Website
 Getting Started with AWS Hosting a Static Website Getting Started with AWS: Hosting a Static Website Copyright 2016 Amazon Web Services, Inc. and/or its affiliates. All rights reserved. Amazon's trademarks
Getting Started with AWS Hosting a Static Website Getting Started with AWS: Hosting a Static Website Copyright 2016 Amazon Web Services, Inc. and/or its affiliates. All rights reserved. Amazon's trademarks
Advanced Web Security, Lab
 Advanced Web Security, Lab Web Server Security: Attacking and Defending November 13, 2013 Read this earlier than one day before the lab! Note that you will not have any internet access during the lab,
Advanced Web Security, Lab Web Server Security: Attacking and Defending November 13, 2013 Read this earlier than one day before the lab! Note that you will not have any internet access during the lab,
Smartphone Pentest Framework v0.1. User Guide
 Smartphone Pentest Framework v0.1 User Guide 1 Introduction: The Smartphone Pentest Framework (SPF) is an open source tool designed to allow users to assess the security posture of the smartphones deployed
Smartphone Pentest Framework v0.1 User Guide 1 Introduction: The Smartphone Pentest Framework (SPF) is an open source tool designed to allow users to assess the security posture of the smartphones deployed
