Software Vulnerability Detection using Backward Trace Analysis and Symbolic Execution
|
|
|
- Gregory Henry
- 8 years ago
- Views:
Transcription
1 Software Vulnerability Detection using Backward Trace Analysis and Symbolic Execution Hongzhe Li, Taebeom Kim, Munkhbayar Bat-Erdene and Heejo Lee Div. of Computer and Communication Engineering Korea University Seoul, South KOREA (hongzhe, ktb88, munkhbayar, Abstract Software vulnerability has long been considered an important threat to the safety of software systems. When source code is accessible, we can get much help from the information of source code to detect vulnerabilities. Static analysis has been used frequently to scan code for errors that cause security problems when source code is available. However, they often generate many false positives. Symbolic execution has also been proposed to detect vulnerabilities and has shown good performance in some researches. However, they are either ineffective in path exploration or could not scale well to large programs. During practical use, since most of paths are actually not related to security problems and software vulnerabilities are usually caused by the improper use of security-sensitive functions, the number of paths could be reduced by tracing sensitive data backwardly from security-sensitive functions so as to consider paths related to vulnerabilities only. What s more, in order to leave ourselves free from generating bug triggering test input, formal reasoning could be used by solving certain program conditions. In this research, we propose backward trace analysis and symbolic execution to detect vulnerabilities from source code. We first find out all the hot spot in source code file. Based on each hot spot, we construct a data flow tree so that we can get the possible execution traces. Afterwards, we do symbolic execution to generate program constraint(pc) and get security constraint(sc) from our predefined security requirements along each execution trace. A program constraint is a constraint imposed by program logic on program variables. A security constraint(sc) is a constraint on program variables that must be satisfied to ensure system security. Finally, this hot spot will be reported as a vulnerability if there is an assignment of values to program inputs which could satisfy PC but violates SC, in other words, satisfy P C SC. We have implemented our approach and conducted experiments on test cases which we randomly choose from Juliet Test Suites provided by US National Security Agency(NSA). The results show that our approach achieves P recision value of 83.33%, Recall value of 90.90% and F 1 V alue of 86.95% which gains the best performance among competing tools. Moreover, our approach can efficiently mitigate path explosion problem in traditional symbolic execution. Keywords-symbolic execution, program constraint, vulnerability detection, static analysis. I. INTRODUCTION Software security has long been considered an important issue due to the increasing number of attacks. In order to identifying software vulnerabilities effectively, software security testing has gained significant attention and become an active research area. In the past decade, many approaches have been proposed to detect software vulnerabilities [2] [3] [6] [9] [13]. Static analysis has been proposed to discover software vulnerabilities by analyzing source code or software binary. The advantage of this approach is the large coverage of code and the access to the internal structures or workings of a software or application. However they often approximate or even ignore runtime conditions which makes them suffer from high false positive rate. Dynamic analysis monitors program execution to detect security flaws [4] [5] [7] [8] [10]. These tools try to trigger software vulnerabilities by giving test input data to a program and monitor its runtime behavior. When there is an abnormality detected during execution, there may be a vulnerability existed. For example, the program accessed a buffer outside its bounds. Although dynamic analysis reduces false alarm rates, it requires the generation of actual bug triggering test inputs which often make us cannot find critical security flaws in a reasonable time. What s more, the coverage of the whole huge test inputs space is either too much time costly or just impractical to achieve which will cause false negatives. Researchers recognized the problems and use dynamic symbolic execution to cover the test inputs space more efficiently. Symbolic execution has been proposed to detect vulnerabilities and has shown good performance in some researches. However, they often cannot solve the problem of huge search space of program paths so that they are either ineffective in path exploration or do not scale well to large programs. What s more, most of dynamic symbolic execution works on binary level which means that they cannot get useful information from source code. SecTAC [1] works on source code level, however, they can only detect vulnerabilities from the paths they get from functional test cases which could make them to miss vulnerabilities from the paths their test cases cannot cover. The number of paths could be reduced by tracing sensitive data backwardly from security-sensitive functions so that we only consider vulnerability related paths. Whats more, formal reasoning such as solving P C SC of the program conditions by doing symbolic execution could leave us free from test inputs generation which makes the whole detecting process more efficient. In this paper, we propose a novel method to detect software vulnerabilities from source code using backward trace analysis and symbolic execution. Different from traditional one direction
2 analysis in symbolic execution, we backwardly analyze the execution traces and then performing symbolic execution forwardly. We first analyze the source code to find out all the hot spot which could possibly generate a vulnerability using pattern matching technique. A hot spot is defined as: a security-sensitive function with sensitive data among its arguments. Sensitive data is derived from untrusted input sources like input files, or network messages, command line options. Then, beginning with each hot spot, we backwardly analyze the source code and build the data flow tree of each hot spot. From the data flow tree, we could get the possible execution paths that could reach to this hot spot. Based on each execution trace, we do symbolic execution to get the program constraints(pc) and security constraints(sc). A program constraint is a constraint imposed by program logic on program variables. A security constraint(sc) is a constraint on program variables that must be satisfied to ensure system security. Finally, this hot spot will be reported as a vulnerability if there is an assignment of values to program variables which could satisfy PC but violates SC, in other words, satisfy P C SC. We try to solve this constraint by using a proper constraint solver such us SMT solver. Our evaluation tells that our approach achieves P recision value of 83.33%, Recall value of 90.90% and F 1 V alue of 86.95% which gains the best performance among competing tools. Moreover, our approach can efficiently mitigate path explosion problem in traditional symbolic execution. Our contributions could be described like this: Different from other static analysis technique, we take program trace execution conditions into consideration to detect software vulnerabilities which could dramatically decrease the false positive rate. We mitigate the path exploration problem in symbolic execution by considering only vulnerability related paths. Tracing the sensitive data used in hot spot backwardly to recover the execution paths using data flow tree makes us only focus on those branches related to sensitive data. This makes the detection process more efficient The P C SC constraint solving makes formal reasoning applicable to accurately detect software vulnerabilities. Meanwhile, it makes us free from generating actual bug triggering test inputs II. RELATED WORK Our research has been conducted based on some previous knowledge about related works. There are several works about dynamic symbolic execution and test cases generation to find software flaws which take advantage of the combination of concrete and symbolic execution. CUTE [4] and DART [9] can automatically generate test cases to traverse different execution paths by the use of a combination of symbolic and concrete execution. They improve the classical symbolic execution by making a distinction between the concrete and the symbolic state of a program. The code is basically run unchanged, and only statements that related to the program input are treated differently. EXE [17] and KLEE [18] are developed to automatically generate high-coverage test cases and to discover deep bugs and security vulnerabilities in a variety of complex code. They provide the speed necessary to quickly solve the constraints through a combination of low-level optimizations and a series of higher-level ones such as caching and irrelevant constraint elimination. However, the greatest challenge for those mechanisms is the scalability problem. We still cannot get a good answer to the question on how to handle the exponential number of paths. Hence, if a very tiny vulnerability exits in a program with millions of code statements, it will be very time consuming to find it out. Unlike these tools, our approach first identifies the potential vulnerable points by pattern matching technique and then uses backward program slicing to reduce the irrelevant paths that we need to analyze. This helps us to focus on vulnerability related paths only and quickly verify the potential vulnerable points. Automated whitebox fuzzing, implemented as a tool named SAGE [16], is a recent method to do software security testing which extends the scope of systematic dynamic test generation from unit testing to whole application testing. It is able to scale to large file programs with millions of code lines and execution traces with billions of machine instructions. However, SAGE works on binary level so it cannot take advantage of useful information from source code. There are also some static analysis tools such as CodeAuditor [15] implemented by Lei Wang which works on source code level. It analyzes the program using program slicing to extract the paths only relevant to the potential vulnerable point. They mitigate the path explosion problem in a smart way, however, they need to instrument the original source code to get the range of program variables which makes it time consuming. The closest work to ours is SecTAC [1] proposed by Dazhi Zhang. SecTAC works on source code level and it uses the test cases from traditional functional software testing to get the popular execution traces of the program. By performing symbolic execution along each trace with satisfiability analysis, it can quickly and correctly detect vulnerabilities which locate on the traces covered by the test cases. The reuse of the test cases generated from previous functional software testing helps them to avoid the problem of path exploration. However, this makes it unable to discover the vulnerabilities which are not covered by the traces. In other words, they may miss serious vulnerabilities. Our approach does not rely on any test cases. We take advantage of the common feature of the software security vulnerabilities to firstly identify all the potential vulnerable points in the whole program and then verify each potential vulnerable points known as hot spot to get the finally vulnerability report which makes us avoid the problem of false negatives.
3 III. OUR APPROACH Discovery of vulnerabilities in a program is a key process to the development and management of secure systems. Nowadays, static analysis tools and methods cannot get rid of high positive rate. Dynamic analysis techniques such as Fuzzing depend on program input significantly which probably make us miss critical vulnerabilities located in some traces which are not covered by program input. Another problem of these techniques is the coverage of huge input space which is usually a time consuming work. Some tools using dynamic symbolic execution are powerful to detect vulnerabilities.however, the path exploration problem makes them ineffective and the process of finding bug triggering test inputs usually puts a huge burden on testers. However, we found out that during practical use, most of paths are actually not related to vulnerabilities and software vulnerabilities are usually caused by the improper use of security-sensitive functions. As a remedy, we try to mitigate the path exploration problem by tracing sensitive data backwardly from security-sensitive functions so as to consider only paths related to vulnerabilities. Afterwards, vulnerabilities are reported by solving P C SC after doing symbolic execution on those paths without finding test inputs that actually trigger vulnerabilities. Generally, Figure 1 gives us a schematic overview of our proposed approach. The process of our approach could be described as the following 5 steps. 1) Hot spot detection: A hot spot( known as sink in other related works )is defined as: a securitysensitive function with sensitive data among its arguments. Functions such as strcpy,memcpy,printf are sensitive to cause security problems. Sensitive data is derived from untrusted input sources like input files, network messages or command line options. We find all those hot spot(potential vulnerable) by simply using pattern matching strategy. This process could be finished in a short time. 2) Data flow tree construction: In order to eliminate the paths we need to analyze, we trace the sensitive data used as argument in hot spot backwardly to build a data flow tree. The tree is used for generating possible execution paths. Actually, during the process of constructing the tree, paths which are not related to hot spot or sensitive data have automatically been eliminated. 3) Possible execution paths generation: After the construction of data flow tree, possible execution paths are generated automatically from the data flow tree. 4) Program constraints(pcs) and security constraints(scs) generation: Symbolic execution is performed on generated traces to get program constraints and security constraints. 5) P C and SC verification: A satisfiability checker is used to check if P C SC is satisfiable. We have found a vulnerability if the condition could be solved. The solution given by the satisfiability checker is then used to generate test data to uncover the vulnerability. In the following part, we discuss these steps in more detail and provide examples for better illustration. A. Hot spot detection A hot spot(known as sink in other related works)is defined as: a security-sensitive function with sensitive data among its arguments. Functions such as strcpy,memcpy,printf are sensitive to cause security problems. Sensitive data is derived from untrusted input sources like input files, or network messages, command line options. Based on our study, vulnerabilities are usually caused by overflowed value used in sensitive functions. These sensitive points we called hot spot. We can classify hot spot according to the different features of sensitive functions Memory copy: The sensitive data is used as argument to be copied in a destination buffer(strcpy,memcpy). When destination buffer cannot hold the sensitive data, serious security problems may occur like buffer overflow Memory access: The sensitive data is used as an array index or a pointer offset, which may cause arbitrary bytes memory overwritten or read(e.g, an information leakage attack). Memory allocation: The sensitive data is used as argument in memory allocation functions(e.g., malloc, alloca) and it usually cause insufficient memory allocation. Format string: The sensitive data is used improperly as argument in format functions(e.g., printf, sprintf). Attacker can take use of this vulnerability to take control of the system. We analyze the given source code to find all of potential vulnerable points which we called hot spot by simply using pattern matching strategy. B. Data flow tree construction In order to eliminate the paths we need to analyze, we trace the sensitive data used in hot spot backwardly to build a data flow tree. Actually, during the process of constructing the tree, paths which are not related to hot spot or sensitive data have automatically been eliminated. Whats more, we can easily see the relationship between user inputs and function arguments to check whether the arguments in hot spot are tainted by user inputs. The tree is used for finding possible execution paths. Starting from each hot spot, we trace the arguments until we reach the origin of the sensitive data. In order to understand the process of data flow tree construction, there are several terms that we need to know. Variable Source(S): the code statements where we get the source of the variable.
4 Figure 1. A schematic overview of our mechanism The code statements where the value of the variable is assigned; V a = expression. Function declaration statements where the variable is used as argument. V a = void f(int V a,...,). Variable origin(o): the code statement where the value of the variable does not rely on any other variable. Variable origin is also variable source. Variable source could be variable origin. The code statements where the variable is assigned by a constant value; V a = const. The code statements where the variable gets its value from input files, network messages or command line options; V a = readfile(); scanf( s%,& V a ). The code statements where the variable is initiated; char V a = C. We make the hot spot statement as the root of our data flow tree. The critical part of building data flow tree process is tracing variables. This process could be explained as follows: 1) Find the variable need to be traced in a tree node. 2) For the variable need to be traced in tree node A, we find its source and put it into As child node B. If the sources of the variable are in n different exclusive branches, we put the n sources into As n child nodes respectively. 3) Repeat step 1 until the sources in a tree node become origins. 4) After finding the origin, we continue to build the child nodes by function definition-calling logic until the reaching of program entry function such as main Since this is a very important process during data flow tree construction, we try to make this process more explicitly. The tracing algorithm and process are shown in Figure 2. Figure 2. Key process for constructing the data flow tree Figure 3 shows the sample code for constructing the data flow tree and Figure 4 shows the data flow tree which comes from the source code sample. C. The generation of possible execution paths After the construction of data flow tree, we could simply get possible execution paths from the data flow tree. Figure 5 shows the possible execution paths generated from the previous sample. Take a look at the data flow tree we got from the sample code. Then, we could get 4 main execution paths from this tree. There are:(numbers mean the code lines) These execution paths are not complete execution paths. They may have more branches. However, these are several
5 main paths. Because for those small branches, most of them are not related to the sensitive data, so we had better not consider them in order to mitigate the paths explosion problem. requirements. Especially, when there is a condition statement along the execution paths, we could generate corresponding program constraints according to the current execution path. Along each possible execution path, we symbolically execute the program to generate program constraints which could be generated so far. We take the 1st path as an example. The following table shows the process of generating the program constraints through path1. Figure 3. The sample code for constructing the data flow tree Actually, this is how we solve path explosion problem in our method. Along each possible execution path, we symbolically execute the program to generate program constraints which could be generated so far. Figure 5. The generation of possible vulnerable paths In the case of path: Table I PROGRAM CONSTRAINT GENERATION PROCESS Path1 Constraints 53 60!scanf( %s, str m ) = true!scanf( %s, str n) = true sizeof(str m ) < None 8 30!scanf( %d, &c) = true sizeof(str1) < None b > 30 sizeof(src) < 50 Figure 4. An example of data flow tree D. Program constraints (PCs) and security constraints (SCs) Symbolic execution to generate program constraints (PCs): Symbolic execution is a kind of program analysis method that simulates program execution by replacing concrete values with symbolic variables for inputs. We use the symbolic executor to symbolically execute the trace to capture program constraints and check the pattern of each executed statement against the security Until now, we get a set of rough program constraints from path1. We call it a rough set because there might be more constraints on this path we haven t found yet. So, we need to find all of the program constraints in order to make our detection result more precise. Generate program constraints furthermore. To explain this part, lets understand what are traced variable and un-traced variable. Traced variable: variables we have already traced, we know its origin. Un-traced variable: variables we have not traced, we do not know its origin. The set of constraints we got from the previous table is not enough because there might be some un-traced variables in the constraint set. So we will trace the un-traced
6 variables until we find their origins. In the process of tracing un-traced variables, we might get more branches. This will cause the previous rough path split into more accurate paths. This process will be repeated until there is no un-traced variable in a constraint set. In our example, we can see that variable b in the constraint set is the untraced variable. So we trace the origin of variable b. Figure 6 shows the branch caused by tracing the variable b. In path11 and path22, there are already no un-traced variables, so these constraints could be considered as final path constraints. If there is still un-traced variable, then we still have to trace those un-traced variables until there are no un-traced variables in any path constraints. Figure 6. Branches derivated from tracing un-traced variable From this tree, we know they are 2 more branches. Then we could split Path1 into Path11 and path12. Table II shows the constraints in more detail. Path11 constraints Table II MORE COMPLETE CONSTRAINT SET!scanf( %s, str m ) = true!scanf( %s, str n ) = true Path12 constraints!scanf( %s, str m ) = true!scanf( %s, str n ) = true sizeof(str m ) < 10 sizeof(str m ) < 10!scanf(%d, &c) = true!scanf(%d, &c) = true sizeof(str1) < 5 sizeof(str1) < 5 sizeof(src) < 50 sizeof(src) < 50 C < 50 C > 50 C + 5 > 30 C 5 > 30 Security constraints(scs) generation Now, we talk about security constraints(sc). Security constraints come from our predefined security requirements. The following table has shown the predefined security requirements for some critical security functions. For each security critical function, we define a corresponding security constraint. In our example: i f ( b > 30) { i f ( s i z e o f ( s r c )< 50) { s t r c p y ( buf, s r c ) ; } } The security constraint is: buf.space > src.strlen Security sensitive functions strcpy(dst., src) Table III PREDEFINED SECURITY CONSTRAINTS Security requirements Dst.spcace > src.strlen strncpy(dst, src, n) (dst.space = n) (n = 0) strcat(dst, src) Dst.space > dst.strlen + src.strlen getcwd(buf, size) (buf.space = size) (size = 0) fgets(dst, size, f) (dst.space = size) (size = 0) printf(format,...) #offormats = #ofparameters 1 E. PC and SC verification We use a satisfiability checker to check if P C SC is satisfiable. We have found a vulnerability if the condition could be solved. The solution given by the satisfiability checker is then used to generate test data to uncover the vulnerability. We express both program and security constraints using the SMT-LIB format and use the Yices SMT-solver as the satisfiability checker. Figure 7 shows how the checker works briefly. IV. IMPLEMENTATION AND EXPERIMENTAL RESULTS In this section, we will talk about the implementation and our experimental results. We tested the effectiveness of our vulnerability detection approach on sample programs containing buffer overflows and format string bugs which we chose from Juliet Test Suite v1.1 for C/C++ test cases. Juliet Test Suite is created by US National Security Agency s(nsa) Center for Assured Software. They were made especially for testing the effectiveness of software static analysis tools. We measured the number of correctly identified vulnerabilities, as well as the number of false positives and false negatives in the results. Ideally, a static analysis tool would be able to find all vulnerabilities in a program without missing any or reporting safe code as vulnerable. The imprecise nature of static analysis makes this impossible. We can expect a certain number of false positives and false negatives from all vulnerability detection tools. False negatives indicate a failure of the analysis, because a real vulnerability was not detected. A tool which detects more vulnerabilities is better than a tool reporting false negatives instead. The number of false positives is also important, because they increase the effort required to verify the results of the analysis. When comparing different vulnerability detection approaches, the number of false positives and false negatives is a good indicator of their effectiveness. A less important factor in vulnerability detection is the speed of the analysis. However, the speed can be only measured when we test on more complex programs(usually over 1000 code of lines). We could not measure this aspect since we only did experiments on sample programs. Juliet Test Suite v1.1 for C/C++ test cases shown in figure 7 were created by the US NSAs Center for Assured Software (CAS) specifically for use in testing static analysis methods and tools.
7 It is intended for anyone who wishes to use the test cases for their own testing purposes. We chose Juliet Test Suite to test our approach over natural code due to the following reasons. Figure 7. Workflow of a satisfiability checker 1) Evaluating tool results to determine their correctness When a static analysis tool is run on natural code, each result needs to be reviewed to determine if the code in fact has the specified type of flaw at the specified location (i.e. if the result is correct or a false positive). This review is non-trivial for most results on natural code and often the correctness of a given result cannot be determined with a high degree of certainty in a reasonable amount of time. 2) Comparing results from different tools Comparing static analysis tool results on natural code is complicated because different tools report results in different manners. 3) Identifying flaws in the code that no tools find When evaluating static analysis tools, a standard list of all flaws in the code is needed in order to identify which flaws each tool failed to report. On natural code, creating this standard is difficult, especially identifying flaws that are not reported by any automated tool. the vulnerabilities and non-vulnerabilities included in the code. A. The results of our approach For testing purposes, we randomly selected 20 test cases out of 854 in the Juliet Test Suite of the buffer overflow type. The results of our sample programs are presented below. We measure the effectiveness of our approach by P recision, Recall and F 1 V alue. P recision: It is an indicator to measure the preciseness of a certain detection tool. It is calculated by P recision = T P (T P + F P ). (1) T P means True Positive and F P means False Positive Recall : It is an indicator to measure the completeness of a certain detection tool. It is calculated by Recall = T P (T P + F N). (2) T P means True Positive and F N means False Negative. F 1 V alue : It is a comprehensive indicator to measure the combine results of Precision and Recall. It is calculated by F 1 V alue = 2 P R (P + R). (3) P means Precision and R means Recall Figure 9 shows one of the vulnerability reports generated by our approach and Table 4 shows the testing results of our approach. Figure 8. Test cases from Juliet Test Suites 4) Evaluating tool performance on constructs that do not appear in the code Natural code has the limitation that even a combination of different projects will likely not contain all flawed and non-flawed constructs that the CAS wants to test. Based on these experiences and challenges, we decided to use Juliet test cases to test and analyze our vulnerability detection approach to control, identify, and locate Figure 9. Vulnerability report From figure 10, our approach can get the P recision value of 83.33%, Recall value of 90.90% and F 1 V alue of 86.95% which are all relatively high in terms of static analysis tools. We check the 4 False Positives in the results marked by the red circle and we found that all of these 4 test cases have strongly used C-structures in their codes. The FPs are produced due to the inability of our approach to handle struct in C codes. When it comes to the 2 False Negatives we found in this table, these 2 vulnerabilities are not caused by the improper use of
8 security sensitive function which is beyond the detection scope of our approach. B. Testing competing tools To evaluate the effectiveness of our system, we tested two competing vulnerability detection tools and compared their results with those of our approach. We chose Flawfinder [14] and SPLINT [15], two programs widely used in the security community. C. Path reduction rate Since the analyzing time is closely related to the total number of paths we need to analyze, we evaluate the efficiency of our approach by the path reduction ratio. The table 4 gives the definition of parameters that measure the path reduction ratio. Parameter Table IV PARAMETER EXPLANATION Description N α N β N γ θ ρ The total number of bifurcations in the program The total number of branches in the program The total number of paths in the program The percentage of the branches which are related to the hot spot over the total number of branches The percentage of the number of eliminated paths over the total number of paths Figure 10. Testing results of our approach Flawfinder is an example of the pattern matching approach to vulnerability detection, while SPLINT uses annotation based data-flow analysis. We performed the tests using the same vulnerable programs from Juliet Test Suite presented earlier in this chapter. We compare our approach, Flawfinder and SPLINT by comparing the number of detected vulnerabilities, false positives and false negatives and F 1 V alue reported by each program. Figure 12 describes the theoretical path reduction ratio in both best and worst cases. Given that the branches are uniformly distributed in bifurcations, the minimum and maximum of eliminated paths number which we called the worst case and the best case respectively are shown in figure 12. The result shows that even program paths are exponentially increased, we can efficiently eliminate the number of paths. when the taint ratio is less than 0.4, path reduction ratio ranges from 93.6% in the worst case to 99% in the best case. Normally, taint ratio of most programs is not over 0.4 since taint variables related to hot spot consist only a small portion of the codes in real-world programs. Figure 11. The comparison of 3 approaches testing on the test cases As we can see from the above figure, when testing on the same group of test cases, our approach has the highest precision compare to the other two. In terms of recall, FlawFinder has the best performance, however, at the cost of being the lowest in precision. When it comes to F 1 V alue, a more comprehensive indicator, our approach exceeds the FlawFinder by 35% while SPLINT being the lowest. Generally, our approach achieves the best performance among these three tools. Figure 12. The path reduction ratio by taint variable ratio In our test cases, we computed the average taint ratio whose value is about As a consequence, our method can efficiently mitigate path explosion problem in traditional symbolic execution. V. CONCLUSION AND LIMITATIONS In conclusion, we proposed a mechanism to detect software vulnerabilities by using source code analysis and
9 symbolic execution. Different from other static analysis, our approach takes program execution conditions into consideration so that we could dramatically the false positives. We mitigate the path exploration problem in conventional symbolic execution by considering only vulnerability related paths. Tracing the sensitive data used in hot spot backwardly to recover the execution paths using data flow tree makes us only focus on branches related to sensitive data. This makes the detection process more efficient. What s more, the P C SC constraint solving makes formal reasoning applicable to accurately detect software vulnerabilities which make us free from bug triggering input generation. To verify our approach, we implemented our mechanism and have it test with source code test cases from Juliet Test Suites. The results show that our approach achieves relatively high precision and recall. Moreover, practically speaking, our approach can detect vulnerabilities in a reasonable time. However, there are also several aspects we need to consider more. First, our approach cannot cover some types of vulnerabilities due to the incapability of handling vulnerabilities unrelated to security-sensitive functions. Then, since we haven t made our program to handle complex data types such as structures in c code, the improvement is needed to make it applicable to complex real world programs. Finally, since some programs have puzzle functions such as decryption functions and checksum functions which become obstacles when we solve constraints during symbolic execution, we will also need to devote our effort into this in the future. VI. ACKNOWLEDGEMENTS This research was supported by the MKE(The Ministry of Knowledge Economy), Korea and Microsoft under IT/SW Creative research program supervised by the NIPA(National IT Industry Promotion Agency) (H ). Additionally, this research was funded by the MSIP(Ministry of Science, ICT & Future Planning), Korea in the ICT R&D Program REFERENCES [1] Dazhi Zhang, Detecting Vulnerabilities in C Programs Using Trace-Based Testing. Proceedings of the IEEE/IFIP International Conference on Dependable Systems and Networks (DSN), [2] D. Wagner, J. Foster, E. Brewer and A. Aiken, A first step towards automated detection of buffer overrun vulnerabilities. Proceedings of Network and Distributed System Security Symposium (NDSS), [3] C. Cadar and D. Engler, Execution generated test cases :How to make systems code crash itself. Proceedings of the International SPIN Workshop on Model Checking of Software, [4] K. Sen, D. Marinov and G. Agha, CUTE: a concolic unit testing engine for C. Proceedings of the joint Meeting of the European Software Engineering Conference and the ACM SIGSOFT International Symposium on Foundations of Software Engineering, [5] E. Haugh and M. Bishop, Testing C programs for buffer overflow vulnerabilities. Proceedings of the Network and Distributed System Security Symposium (NDSS), [6] R. Hastings and B. Joyce, Purify: Fast detection of memory leaks and access errors. Proceedings of the Winter USENIX Conference, [7] G. Fink, C. Ko, M. Archer and K. Levitt, Towards a property-based testing environment with applications to security-critical software. Proceedings of the 4th Irvine Software Symposium, [8] A. Ghosh, T. O Connor and G. McGraw, An automated approach for identifying potential vulnerabilities in software. Proceedings of the IEEE Symposium on Security and Privacy, [9] P. Godefroid, N. Klarlund and K. Sen, DART : directed automated random testing. Proceedings of the ACM SIG- PLAN conference on Programming Language Design and Implementation, [10] M. Ringenburg and D. Grossman, Preventing formatstring attacks via automatic and efficient dynamic checking. Proceedings of the ACM Conference on Computer and Communications Security (CCS), [11] J. Viega, J. T.Bloch, Y. Kohno and G. McGraw, ITS4: A static vulnerability scanner for C and C++ code. Proceedings of the Annual Computer Security Applications Conference(ACSAC), [12] E. C.Sezer, P. Ning, C. Kil and J. Xu, Memsherlock: an automated debugger for unknown memory corruption vulnerabilities. Proceedings of the ACM Conference on Computer and Communications Security (CCS), [13] Wheeler and David, Flawfinder. flawfinder/ [14] Evans and David, SPLINT. [15] E. C.Sezer, P. Ning, C. Kil and J. Xu, Automated Detection of Code Vulnerabilities Based on Program Analysis and Model Checking. Eighth IEEE International Working Conference on Source Code Analysis and Manipulation, [16] P. Godefroid, M. Y.Levin and D. Molnar, Automated whitebox fuzz testing. Proceedings of the Network and Distributed Systems Security (NDSS), [17] C. Cadar, V. Ganesh, P. Pawlowski, D. Dill and D. Engler, EXE: Automatically generating inputs of death. Proceedings of the ACM Conference on Computer and Communications, [18] C. Cadar, D. Dunbar and D. Engler, Automatically generating inputs of death. Proceedings of the ACM Conference on Computer and Communications, 2008.
On the value of hybrid security testing
 On the value of hybrid security testing Saad Aloteibi and Frank Stajano Computer Laboratory University of Cambridge {firstname.lastname}@cl.cam.ac.uk Abstract. We propose a framework for designing a security
On the value of hybrid security testing Saad Aloteibi and Frank Stajano Computer Laboratory University of Cambridge {firstname.lastname}@cl.cam.ac.uk Abstract. We propose a framework for designing a security
Secure Software Programming and Vulnerability Analysis
 Secure Software Programming and Vulnerability Analysis Christopher Kruegel chris@auto.tuwien.ac.at http://www.auto.tuwien.ac.at/~chris Testing and Source Code Auditing Secure Software Programming 2 Overview
Secure Software Programming and Vulnerability Analysis Christopher Kruegel chris@auto.tuwien.ac.at http://www.auto.tuwien.ac.at/~chris Testing and Source Code Auditing Secure Software Programming 2 Overview
A Memory Model for Static Analysis of C Programs
 A Memory Model for Static Analysis of C Programs Zhongxing Xu 1, Ted Kremenek 2, and Jian Zhang 1 1 State Key Laboratory of Computer Science Institute of Software Chinese Academy of Sciences xzx@ios.ac.cn
A Memory Model for Static Analysis of C Programs Zhongxing Xu 1, Ted Kremenek 2, and Jian Zhang 1 1 State Key Laboratory of Computer Science Institute of Software Chinese Academy of Sciences xzx@ios.ac.cn
Whitebox Fuzzing for Security Testing
 Article development led by queue.acm.org SAGE has had a remarkable impact at Microsoft. SAGE: Whitebox Fuzzing for Security Testing doi:10.1145/2093548.2093564 by Patrice Godefroid, Michael Y. Levin, and
Article development led by queue.acm.org SAGE has had a remarkable impact at Microsoft. SAGE: Whitebox Fuzzing for Security Testing doi:10.1145/2093548.2093564 by Patrice Godefroid, Michael Y. Levin, and
SSVChecker: Unifying Static Security Vulnerability Detection Tools in an Eclipse Plug-In
 SSVChecker: Unifying Static Security Vulnerability Detection Tools in an Eclipse Plug-In Josh Dehlinger Dept. of Computer Science Iowa State University dehlinge@iastate.edu Qian Feng ABC Virtual Communications
SSVChecker: Unifying Static Security Vulnerability Detection Tools in an Eclipse Plug-In Josh Dehlinger Dept. of Computer Science Iowa State University dehlinge@iastate.edu Qian Feng ABC Virtual Communications
Dsc+Mock: A Test Case + Mock Class Generator in Support of Coding Against Interfaces
 Dsc+Mock: A Test Case + Mock Class Generator in Support of Coding Against Interfaces Mainul Islam, Christoph Csallner Computer Science and Engineering Department University of Texas at Arlington Arlington,
Dsc+Mock: A Test Case + Mock Class Generator in Support of Coding Against Interfaces Mainul Islam, Christoph Csallner Computer Science and Engineering Department University of Texas at Arlington Arlington,
Securing Network Software using Static Analysis
 Securing Network Software using Static Analysis Lauri Kolmonen Helsinki University of Technology lauri.kolmonen@hut.fi Abstract Writing network software is not easy and developing secure network software
Securing Network Software using Static Analysis Lauri Kolmonen Helsinki University of Technology lauri.kolmonen@hut.fi Abstract Writing network software is not easy and developing secure network software
Intrusion Detection via Static Analysis
 Intrusion Detection via Static Analysis IEEE Symposium on Security & Privacy 01 David Wagner Drew Dean Presented by Yongjian Hu Outline Introduction Motivation Models Trivial model Callgraph model Abstract
Intrusion Detection via Static Analysis IEEE Symposium on Security & Privacy 01 David Wagner Drew Dean Presented by Yongjian Hu Outline Introduction Motivation Models Trivial model Callgraph model Abstract
Automatic vs. Manual Code Analysis
 Automatic vs. Manual Code Analysis 2009-11-17 Ari Kesäniemi Senior Security Architect Nixu Oy ari.kesaniemi@nixu.com Copyright The Foundation Permission is granted to copy, distribute and/or modify this
Automatic vs. Manual Code Analysis 2009-11-17 Ari Kesäniemi Senior Security Architect Nixu Oy ari.kesaniemi@nixu.com Copyright The Foundation Permission is granted to copy, distribute and/or modify this
Applying the Blackboard Model in the Security Field
 Applying the Blackboard Model in the Security Field Simeon (simos) Xenitellis Information Security Group, Royal Holloway University of London, TW20 0EX United Kingdom S.Xenitellis@rhul.ac.uk Abstract.
Applying the Blackboard Model in the Security Field Simeon (simos) Xenitellis Information Security Group, Royal Holloway University of London, TW20 0EX United Kingdom S.Xenitellis@rhul.ac.uk Abstract.
Framework for Injecting the Attacks and Analyzing the Behaviour of Vulnerability on Server s
 Framework for Injecting the Attacks and Analyzing the Behaviour of Vulnerability on Server s Panchamukesh Ch #1, Kumar.J *2, Neelima.S *3, Sailaja.D *4 #1 Department of CSE, HITAM, Gowdavally, Hyderabad,
Framework for Injecting the Attacks and Analyzing the Behaviour of Vulnerability on Server s Panchamukesh Ch #1, Kumar.J *2, Neelima.S *3, Sailaja.D *4 #1 Department of CSE, HITAM, Gowdavally, Hyderabad,
Software Security Analysis - Execution Phase Audit
 Software Security Analysis - Execution Phase Audit Bengt Carlsson * and Dejan Baca # * School of Engineering, Blekinge Institute of Technology ; PO Box 520, S-372 25 Ronneby, SWEDEN; bengt.carlsson;@bth.se
Software Security Analysis - Execution Phase Audit Bengt Carlsson * and Dejan Baca # * School of Engineering, Blekinge Institute of Technology ; PO Box 520, S-372 25 Ronneby, SWEDEN; bengt.carlsson;@bth.se
A Test Suite for Basic CWE Effectiveness. Paul E. Black. paul.black@nist.gov. http://samate.nist.gov/
 A Test Suite for Basic CWE Effectiveness Paul E. Black paul.black@nist.gov http://samate.nist.gov/ Static Analysis Tool Exposition (SATE V) News l We choose test cases by end of May l Tool output uploaded
A Test Suite for Basic CWE Effectiveness Paul E. Black paul.black@nist.gov http://samate.nist.gov/ Static Analysis Tool Exposition (SATE V) News l We choose test cases by end of May l Tool output uploaded
How To Detect A Buffer Overflow Vulnerability In Binary Code
 Buffer Overflow Vulnerability Detection in the Binary Code Shehab Gamal El-Dien, Reda Salama, Ahmed Eshak shehab@ispofegypt.com, redasalama@hotmail.com, a_issac@sakhr.com Al-Azhar University, Faculty of
Buffer Overflow Vulnerability Detection in the Binary Code Shehab Gamal El-Dien, Reda Salama, Ahmed Eshak shehab@ispofegypt.com, redasalama@hotmail.com, a_issac@sakhr.com Al-Azhar University, Faculty of
Improving Software Security at the. Source
 Improving Software Security at the Source Greg Snyder Privacy & Security RIT January 28, 2006 Abstract While computer security has become a major focus of information technology professionals due to patching
Improving Software Security at the Source Greg Snyder Privacy & Security RIT January 28, 2006 Abstract While computer security has become a major focus of information technology professionals due to patching
Source Code Review Using Static Analysis Tools
 Source Code Review Using Static Analysis Tools July-August 05 Author: Stavros Moiras Supervisor(s): Stefan Lüders Aimilios Tsouvelekakis CERN openlab Summer Student Report 05 Abstract Many teams at CERN,
Source Code Review Using Static Analysis Tools July-August 05 Author: Stavros Moiras Supervisor(s): Stefan Lüders Aimilios Tsouvelekakis CERN openlab Summer Student Report 05 Abstract Many teams at CERN,
Experimental Comparison of Concolic and Random Testing for Java Card Applets
 Experimental Comparison of Concolic and Random Testing for Java Card Applets Kari Kähkönen, Roland Kindermann, Keijo Heljanko, and Ilkka Niemelä Aalto University, Department of Information and Computer
Experimental Comparison of Concolic and Random Testing for Java Card Applets Kari Kähkönen, Roland Kindermann, Keijo Heljanko, and Ilkka Niemelä Aalto University, Department of Information and Computer
Static Techniques for Vulnerability Detection
 Static Techniques for Vulnerability Detection Kamran Zafar Asad Ali /LQN SLQJVXQLYHUVLW\6ZHGHQ (PDLO^NDP]DDVDDO`#VWXGHQWOLXVH $EVWUDFW )RU WKH ODVW \HDUV WKH LPSRUWDQFH RI EXLOGLQJ VHFXUH VRIWZDUH LV EHFRPLQJ
Static Techniques for Vulnerability Detection Kamran Zafar Asad Ali /LQN SLQJVXQLYHUVLW\6ZHGHQ (PDLO^NDP]DDVDDO`#VWXGHQWOLXVH $EVWUDFW )RU WKH ODVW \HDUV WKH LPSRUWDQFH RI EXLOGLQJ VHFXUH VRIWZDUH LV EHFRPLQJ
Finding Execution Faults in Dynamic Web Application
 International Journal of Information and Computation Technology. ISSN 0974-2239 Volume 4, Number 5 (2014), pp. 445-452 International Research Publications House http://www. irphouse.com /ijict.htm Finding
International Journal of Information and Computation Technology. ISSN 0974-2239 Volume 4, Number 5 (2014), pp. 445-452 International Research Publications House http://www. irphouse.com /ijict.htm Finding
Binary search tree with SIMD bandwidth optimization using SSE
 Binary search tree with SIMD bandwidth optimization using SSE Bowen Zhang, Xinwei Li 1.ABSTRACT In-memory tree structured index search is a fundamental database operation. Modern processors provide tremendous
Binary search tree with SIMD bandwidth optimization using SSE Bowen Zhang, Xinwei Li 1.ABSTRACT In-memory tree structured index search is a fundamental database operation. Modern processors provide tremendous
Towards a Framework for Generating Tests to Satisfy Complex Code Coverage in Java Pathfinder
 Towards a Framework for Generating Tests to Satisfy Complex Code Coverage in Java Pathfinder Matt Department of Computer Science and Engineering University of Minnesota staats@cs.umn.edu Abstract We present
Towards a Framework for Generating Tests to Satisfy Complex Code Coverage in Java Pathfinder Matt Department of Computer Science and Engineering University of Minnesota staats@cs.umn.edu Abstract We present
Secure Programming with Static Analysis. Jacob West jacob@fortify.com
 Secure Programming with Static Analysis Jacob West jacob@fortify.com Software Systems that are Ubiquitous Connected Dependable Complexity U Unforeseen Consequences Software Security Today The line between
Secure Programming with Static Analysis Jacob West jacob@fortify.com Software Systems that are Ubiquitous Connected Dependable Complexity U Unforeseen Consequences Software Security Today The line between
Using Concolic Testing to Refine Vulnerability Profiles in FUZZBUSTER
 Using Concolic Testing to Refine Vulnerability Profiles in FUZZBUSTER David J. Musliner, Jeffrey M. Rye, Tom Marble Smart Information Flow Technologies (SIFT) Minneapolis, MN, USA Email: {dmusliner, jrye,
Using Concolic Testing to Refine Vulnerability Profiles in FUZZBUSTER David J. Musliner, Jeffrey M. Rye, Tom Marble Smart Information Flow Technologies (SIFT) Minneapolis, MN, USA Email: {dmusliner, jrye,
How To Trace
 CS510 Software Engineering Dynamic Program Analysis Asst. Prof. Mathias Payer Department of Computer Science Purdue University TA: Scott A. Carr Slides inspired by Xiangyu Zhang http://nebelwelt.net/teaching/15-cs510-se
CS510 Software Engineering Dynamic Program Analysis Asst. Prof. Mathias Payer Department of Computer Science Purdue University TA: Scott A. Carr Slides inspired by Xiangyu Zhang http://nebelwelt.net/teaching/15-cs510-se
Using Web Security Scanners to Detect Vulnerabilities in Web Services
 DSN 2009 Using Web Security Scanners to Detect Vulnerabilities in Web Services Marco Vieira,, Henrique Madeira {mvieira, nmsa, henrique}@dei.uc.pt CISUC Department of Informatics Engineering University
DSN 2009 Using Web Security Scanners to Detect Vulnerabilities in Web Services Marco Vieira,, Henrique Madeira {mvieira, nmsa, henrique}@dei.uc.pt CISUC Department of Informatics Engineering University
Seminar: Cryptographic Protocols Staged Information Flow for JavaScript
 Seminar: Cryptographic Protocols Staged Information Flow for JavaScript Sebastian Wild 1 Introduction JavaScript is an important component of modern web applications since it is possible to execute code
Seminar: Cryptographic Protocols Staged Information Flow for JavaScript Sebastian Wild 1 Introduction JavaScript is an important component of modern web applications since it is possible to execute code
Levels of Software Testing. Functional Testing
 Levels of Software Testing There are different levels during the process of Testing. In this chapter a brief description is provided about these levels. Levels of testing include the different methodologies
Levels of Software Testing There are different levels during the process of Testing. In this chapter a brief description is provided about these levels. Levels of testing include the different methodologies
Automating Security Testing. Mark Fallon Senior Release Manager Oracle
 Automating Security Testing Mark Fallon Senior Release Manager Oracle Some Ground Rules There are no silver bullets You can not test security into a product Testing however, can help discover a large percentage
Automating Security Testing Mark Fallon Senior Release Manager Oracle Some Ground Rules There are no silver bullets You can not test security into a product Testing however, can help discover a large percentage
Web application security: automated scanning versus manual penetration testing.
 Web application security White paper January 2008 Web application security: automated scanning versus manual penetration testing. Danny Allan, strategic research analyst, IBM Software Group Page 2 Contents
Web application security White paper January 2008 Web application security: automated scanning versus manual penetration testing. Danny Allan, strategic research analyst, IBM Software Group Page 2 Contents
Component visualization methods for large legacy software in C/C++
 Annales Mathematicae et Informaticae 44 (2015) pp. 23 33 http://ami.ektf.hu Component visualization methods for large legacy software in C/C++ Máté Cserép a, Dániel Krupp b a Eötvös Loránd University mcserep@caesar.elte.hu
Annales Mathematicae et Informaticae 44 (2015) pp. 23 33 http://ami.ektf.hu Component visualization methods for large legacy software in C/C++ Máté Cserép a, Dániel Krupp b a Eötvös Loránd University mcserep@caesar.elte.hu
Development and Industrial Application of Multi-Domain Security Testing Technologies. Innovation Sheet Model Inference Assisted Evolutionary Fuzzing
 Development and Industrial Application of Multi-Domain Security Testing Technologies Innovation Sheet Model Inference Assisted Evolutionary Fuzzing Description The technique dynamically analyzes the application
Development and Industrial Application of Multi-Domain Security Testing Technologies Innovation Sheet Model Inference Assisted Evolutionary Fuzzing Description The technique dynamically analyzes the application
X05. An Overview of Source Code Scanning Tools. Loulwa Salem. Las Vegas, NV. IBM Corporation 2006. IBM System p, AIX 5L & Linux Technical University
 X05 An Overview of Source Code Scanning Tools Loulwa Salem Las Vegas, NV Objectives This session will introduce better coding practices and tools available to aid developers in producing more secure code.
X05 An Overview of Source Code Scanning Tools Loulwa Salem Las Vegas, NV Objectives This session will introduce better coding practices and tools available to aid developers in producing more secure code.
Static Checking of C Programs for Vulnerabilities. Aaron Brown
 Static Checking of C Programs for Vulnerabilities Aaron Brown Problems 300% increase in reported software vulnerabilities SetUID programs Run with full access to the system Required to gain access to certain
Static Checking of C Programs for Vulnerabilities Aaron Brown Problems 300% increase in reported software vulnerabilities SetUID programs Run with full access to the system Required to gain access to certain
Detecting SQL Injection Vulnerabilities in Web Services
 Detecting SQL Injection Vulnerabilities in Web Services Nuno Antunes, {nmsa, mvieira}@dei.uc.pt LADC 2009 CISUC Department of Informatics Engineering University of Coimbra Outline n Web Services n Web
Detecting SQL Injection Vulnerabilities in Web Services Nuno Antunes, {nmsa, mvieira}@dei.uc.pt LADC 2009 CISUC Department of Informatics Engineering University of Coimbra Outline n Web Services n Web
Software Testing & Analysis (F22ST3): Static Analysis Techniques 2. Andrew Ireland
 Software Testing & Analysis (F22ST3) Static Analysis Techniques Andrew Ireland School of Mathematical and Computer Science Heriot-Watt University Edinburgh Software Testing & Analysis (F22ST3): Static
Software Testing & Analysis (F22ST3) Static Analysis Techniques Andrew Ireland School of Mathematical and Computer Science Heriot-Watt University Edinburgh Software Testing & Analysis (F22ST3): Static
How To Develop A Static Analysis System For Large Programs
 Towards the Industrial Scale Development of Custom Static Analyzers John Anton, Eric Bush, Allen Goldberg, Klaus Havelund, Doug Smith, Arnaud Venet Kestrel Technology LLC 4984 El Camino Real #230 Los Altos,
Towards the Industrial Scale Development of Custom Static Analyzers John Anton, Eric Bush, Allen Goldberg, Klaus Havelund, Doug Smith, Arnaud Venet Kestrel Technology LLC 4984 El Camino Real #230 Los Altos,
Why Do Software Assurance Tools Have Problems Finding Bugs Like Heartbleed?
 April 22 WP003 2014 Why Do Software Assurance Tools Have Problems Finding Bugs Like Heartbleed? James A. Kupsch and Barton P. Miller University of Wisconsin-Madison In response to the Heartbleed vulnerability,
April 22 WP003 2014 Why Do Software Assurance Tools Have Problems Finding Bugs Like Heartbleed? James A. Kupsch and Barton P. Miller University of Wisconsin-Madison In response to the Heartbleed vulnerability,
Software testing. Objectives
 Software testing cmsc435-1 Objectives To discuss the distinctions between validation testing and defect testing To describe the principles of system and component testing To describe strategies for generating
Software testing cmsc435-1 Objectives To discuss the distinctions between validation testing and defect testing To describe the principles of system and component testing To describe strategies for generating
Taint-based Directed Whitebox Fuzzing
 Taint-based Directed Whitebox Fuzzing Vijay Ganesh and Tim Leek and Martin Rinard MIT Computer Science and Artificial Intelligence Lab vganesh, tleek, rinard@csail.mit.edu Abstract We present a new automated
Taint-based Directed Whitebox Fuzzing Vijay Ganesh and Tim Leek and Martin Rinard MIT Computer Science and Artificial Intelligence Lab vganesh, tleek, rinard@csail.mit.edu Abstract We present a new automated
UNCLASSIFIED Version 1.0 May 2012
 Secure By Default: Platforms Computing platforms contain vulnerabilities that can be exploited for malicious purposes. Often exploitation does not require a high degree of expertise, as tools and advice
Secure By Default: Platforms Computing platforms contain vulnerabilities that can be exploited for malicious purposes. Often exploitation does not require a high degree of expertise, as tools and advice
Application Code Development Standards
 Application Code Development Standards Overview This document is intended to provide guidance to campus system owners and software developers regarding secure software engineering practices. These standards
Application Code Development Standards Overview This document is intended to provide guidance to campus system owners and software developers regarding secure software engineering practices. These standards
Measuring the Effect of Code Complexity on Static Analysis Results
 Measuring the Effect of Code Complexity on Static Analysis Results James Walden, Adam Messer, and Alex Kuhl Department of Computer Science Northern Kentucky University Highland Heights, KY 41099 Abstract.
Measuring the Effect of Code Complexity on Static Analysis Results James Walden, Adam Messer, and Alex Kuhl Department of Computer Science Northern Kentucky University Highland Heights, KY 41099 Abstract.
Access Control Fundamentals
 C H A P T E R 2 Access Control Fundamentals An access enforcement mechanism authorizes requests (e.g., system calls) from multiple subjects (e.g., users, processes, etc.) to perform operations (e.g., read,,
C H A P T E R 2 Access Control Fundamentals An access enforcement mechanism authorizes requests (e.g., system calls) from multiple subjects (e.g., users, processes, etc.) to perform operations (e.g., read,,
AUTOMATED TEST GENERATION FOR SOFTWARE COMPONENTS
 TKK Reports in Information and Computer Science Espoo 2009 TKK-ICS-R26 AUTOMATED TEST GENERATION FOR SOFTWARE COMPONENTS Kari Kähkönen ABTEKNILLINEN KORKEAKOULU TEKNISKA HÖGSKOLAN HELSINKI UNIVERSITY OF
TKK Reports in Information and Computer Science Espoo 2009 TKK-ICS-R26 AUTOMATED TEST GENERATION FOR SOFTWARE COMPONENTS Kari Kähkönen ABTEKNILLINEN KORKEAKOULU TEKNISKA HÖGSKOLAN HELSINKI UNIVERSITY OF
Keywords: 2013, IJARCSSE All Rights Reserved Page 451
 Volume 3, Issue 9, September 2013 ISSN: 2277 128X International Journal of Advanced Research in Computer Science and Software Engineering Research Paper Available online at: www.ijarcsse.com Vulnerability
Volume 3, Issue 9, September 2013 ISSN: 2277 128X International Journal of Advanced Research in Computer Science and Software Engineering Research Paper Available online at: www.ijarcsse.com Vulnerability
Linux Kernel. Security Report
 Linux Kernel Security Report September 25 Authors: Andy Chou, Bryan Fulton and Seth Hallem Coverity has combined two years of analysis work carried out in a commercial setting at Coverity with four years
Linux Kernel Security Report September 25 Authors: Andy Chou, Bryan Fulton and Seth Hallem Coverity has combined two years of analysis work carried out in a commercial setting at Coverity with four years
Developing Secure Software, assignment 1
 Developing Secure Software, assignment 1 During development of software, faults and flaws are introduced either from the implementation or from the design of the software. During runtime these faults and
Developing Secure Software, assignment 1 During development of software, faults and flaws are introduced either from the implementation or from the design of the software. During runtime these faults and
Software security assessment based on static analysis
 Software security assessment based on static analysis Christèle Faure Séminaire SSI et méthodes formelles Réalisé dans le projet Baccarat cofinancé par l union européenne Context > 200 static tools for
Software security assessment based on static analysis Christèle Faure Séminaire SSI et méthodes formelles Réalisé dans le projet Baccarat cofinancé par l union européenne Context > 200 static tools for
Helping you avoid stack overflow crashes!
 Helping you avoid stack overflow crashes! One of the toughest (and unfortunately common) problems in embedded systems is stack overflows and the collateral corruption that it can cause. As a result, we
Helping you avoid stack overflow crashes! One of the toughest (and unfortunately common) problems in embedded systems is stack overflows and the collateral corruption that it can cause. As a result, we
Detecting Critical Defects on the Developer s Desktop
 Detecting Critical Defects on the Developer s Desktop Seth Hallem CEO Coverity, Inc. Copyright Coverity, Inc. 2006. All Rights Reserved. This publication, in whole or in part, may not be reproduced, stored
Detecting Critical Defects on the Developer s Desktop Seth Hallem CEO Coverity, Inc. Copyright Coverity, Inc. 2006. All Rights Reserved. This publication, in whole or in part, may not be reproduced, stored
Towards An Automated, Black-Box Method For Reversing Web Applications
 Association for Information Systems AIS Electronic Library (AISeL) MCIS 2009 Proceedings Mediterranean Conference on Information Systems (MCIS) 1-1-2009 Towards An Automated, Black-Box Method For Reversing
Association for Information Systems AIS Electronic Library (AISeL) MCIS 2009 Proceedings Mediterranean Conference on Information Systems (MCIS) 1-1-2009 Towards An Automated, Black-Box Method For Reversing
Physical Data Organization
 Physical Data Organization Database design using logical model of the database - appropriate level for users to focus on - user independence from implementation details Performance - other major factor
Physical Data Organization Database design using logical model of the database - appropriate level for users to focus on - user independence from implementation details Performance - other major factor
OPEN SOURCE SECURITY
 OPEN SOURCE SECURITY February 2008 The Government of the Hong Kong Special Administrative Region The contents of this document remain the property of, and may not be reproduced in whole or in part without
OPEN SOURCE SECURITY February 2008 The Government of the Hong Kong Special Administrative Region The contents of this document remain the property of, and may not be reproduced in whole or in part without
D. Best Practices D.1. Assurance The 5 th A
 Best Practices I&C School Prof. P. Janson September 2014 D. Best Practices D.1. Assurance The 5 th A 1 of 20 IT systems are insecure for two main reasons: People are fallible and systems are complex and
Best Practices I&C School Prof. P. Janson September 2014 D. Best Practices D.1. Assurance The 5 th A 1 of 20 IT systems are insecure for two main reasons: People are fallible and systems are complex and
Interactive Application Security Testing (IAST)
 WHITEPAPER Interactive Application Security Testing (IAST) The World s Fastest Application Security Software Software affects virtually every aspect of an individual s finances, safety, government, communication,
WHITEPAPER Interactive Application Security Testing (IAST) The World s Fastest Application Security Software Software affects virtually every aspect of an individual s finances, safety, government, communication,
Integrating Pattern Mining in Relational Databases
 Integrating Pattern Mining in Relational Databases Toon Calders, Bart Goethals, and Adriana Prado University of Antwerp, Belgium {toon.calders, bart.goethals, adriana.prado}@ua.ac.be Abstract. Almost a
Integrating Pattern Mining in Relational Databases Toon Calders, Bart Goethals, and Adriana Prado University of Antwerp, Belgium {toon.calders, bart.goethals, adriana.prado}@ua.ac.be Abstract. Almost a
Data Model Bugs. Ivan Bocić and Tevfik Bultan
 Data Model Bugs Ivan Bocić and Tevfik Bultan Department of Computer Science University of California, Santa Barbara, USA bo@cs.ucsb.edu bultan@cs.ucsb.edu Abstract. In today s internet-centric world, web
Data Model Bugs Ivan Bocić and Tevfik Bultan Department of Computer Science University of California, Santa Barbara, USA bo@cs.ucsb.edu bultan@cs.ucsb.edu Abstract. In today s internet-centric world, web
Fuzzing in Microsoft and FuzzGuru framework
 Fuzzing in Microsoft and FuzzGuru framework OWASP-IL May-2007 John Neystadt jney@microsoft.com Lead Program Manager Forefront Edge, Microsoft Agenda Overview Introduction to Fuzzing FuzzGuru Architecture
Fuzzing in Microsoft and FuzzGuru framework OWASP-IL May-2007 John Neystadt jney@microsoft.com Lead Program Manager Forefront Edge, Microsoft Agenda Overview Introduction to Fuzzing FuzzGuru Architecture
Software security specification and verification
 Software security specification and verification Erik Poll Security of Systems (SoS) group Radboud University Nijmegen Software (in)security specification and verification/detection Erik Poll Security
Software security specification and verification Erik Poll Security of Systems (SoS) group Radboud University Nijmegen Software (in)security specification and verification/detection Erik Poll Security
Visualizing Information Flow through C Programs
 Visualizing Information Flow through C Programs Joe Hurd, Aaron Tomb and David Burke Galois, Inc. {joe,atomb,davidb}@galois.com Systems Software Verification Workshop 7 October 2010 Joe Hurd, Aaron Tomb
Visualizing Information Flow through C Programs Joe Hurd, Aaron Tomb and David Burke Galois, Inc. {joe,atomb,davidb}@galois.com Systems Software Verification Workshop 7 October 2010 Joe Hurd, Aaron Tomb
Transparent Monitoring of a Process Self in a Virtual Environment
 Transparent Monitoring of a Process Self in a Virtual Environment PhD Lunchtime Seminar Università di Pisa 24 Giugno 2008 Outline Background Process Self Attacks Against the Self Dynamic and Static Analysis
Transparent Monitoring of a Process Self in a Virtual Environment PhD Lunchtime Seminar Università di Pisa 24 Giugno 2008 Outline Background Process Self Attacks Against the Self Dynamic and Static Analysis
SAF: Static Analysis Improved Fuzzing
 The Interdisciplinary Center, Herzlia Efi Arazi School of Computer Science SAF: Static Analysis Improved Fuzzing M.Sc. Dissertation Submitted in Partial Fulfillment of the Requirements for the Degree of
The Interdisciplinary Center, Herzlia Efi Arazi School of Computer Science SAF: Static Analysis Improved Fuzzing M.Sc. Dissertation Submitted in Partial Fulfillment of the Requirements for the Degree of
QRCloud: Android Vulnerability Query and Push Services Based on QR Code in Cloud Computing
 Journal of Computational Information Systems 11: 11 (2015) 3875 3881 Available at http://www.jofcis.com QRCloud: Android Vulnerability Query and Push Services Based on QR Code in Cloud Computing Jingzheng
Journal of Computational Information Systems 11: 11 (2015) 3875 3881 Available at http://www.jofcis.com QRCloud: Android Vulnerability Query and Push Services Based on QR Code in Cloud Computing Jingzheng
Cloud9 Parallel Symbolic Execution for Automated Real-World Software Testing
 Cloud9 Parallel Symbolic Execution for Automated Real-World Software Testing Stefan Bucur, Vlad Ureche, Cristian Zamfir, George Candea School of Computer and Communication Sciences Automated Software Testing
Cloud9 Parallel Symbolic Execution for Automated Real-World Software Testing Stefan Bucur, Vlad Ureche, Cristian Zamfir, George Candea School of Computer and Communication Sciences Automated Software Testing
Static Analysis for Software Verification. Leon Moonen
 Static Analysis for Software Verification Leon Moonen Today s topics Software inspection it s relation to testing benefits and drawbacks Static (program) analysis potential benefits limitations and their
Static Analysis for Software Verification Leon Moonen Today s topics Software inspection it s relation to testing benefits and drawbacks Static (program) analysis potential benefits limitations and their
SECURITY B-SIDES: ATLANTA STRATEGIC PENETRATION TESTING. Presented by: Dave Kennedy Eric Smith
 SECURITY B-SIDES: ATLANTA STRATEGIC PENETRATION TESTING Presented by: Dave Kennedy Eric Smith AGENDA Penetration Testing by the masses Review of current state by most service providers Deficiencies in
SECURITY B-SIDES: ATLANTA STRATEGIC PENETRATION TESTING Presented by: Dave Kennedy Eric Smith AGENDA Penetration Testing by the masses Review of current state by most service providers Deficiencies in
A Platform Independent Testing Tool for Automated Testing of Web Applications
 A Platform Independent Testing Tool for Automated Testing of Web Applications December 10, 2009 Abstract Increasing complexity of web applications and their dependency on numerous web technologies has
A Platform Independent Testing Tool for Automated Testing of Web Applications December 10, 2009 Abstract Increasing complexity of web applications and their dependency on numerous web technologies has
Adversary Modelling 1
 Adversary Modelling 1 Evaluating the Feasibility of a Symbolic Adversary Model on Smart Transport Ticketing Systems Authors Arthur Sheung Chi Chan, MSc (Royal Holloway, 2014) Keith Mayes, ISG, Royal Holloway
Adversary Modelling 1 Evaluating the Feasibility of a Symbolic Adversary Model on Smart Transport Ticketing Systems Authors Arthur Sheung Chi Chan, MSc (Royal Holloway, 2014) Keith Mayes, ISG, Royal Holloway
Oracle Solaris Studio Code Analyzer
 Oracle Solaris Studio Code Analyzer The Oracle Solaris Studio Code Analyzer ensures application reliability and security by detecting application vulnerabilities, including memory leaks and memory access
Oracle Solaris Studio Code Analyzer The Oracle Solaris Studio Code Analyzer ensures application reliability and security by detecting application vulnerabilities, including memory leaks and memory access
A Proposed Case for the Cloud Software Engineering in Security
 A Proposed Case for the Cloud Software Engineering in Security Victor Chang and Muthu Ramachandran School of Computing, Creative Technologies and Engineering, Leeds Metropolitan University, Headinley,
A Proposed Case for the Cloud Software Engineering in Security Victor Chang and Muthu Ramachandran School of Computing, Creative Technologies and Engineering, Leeds Metropolitan University, Headinley,
Efficient Program Exploration by Input Fuzzing
 Efficient Program Exploration by Input Fuzzing towards a new approach in malcious code detection Guillaume Bonfante Jean-Yves Marion Ta Thanh Dinh Université de Lorraine CNRS - INRIA Nancy First Botnet
Efficient Program Exploration by Input Fuzzing towards a new approach in malcious code detection Guillaume Bonfante Jean-Yves Marion Ta Thanh Dinh Université de Lorraine CNRS - INRIA Nancy First Botnet
Security types to the rescue
 Security types to the rescue p. 1 Security types to the rescue David Wagner and Rob Johnson {daw,rtjohnso}@cs.berkeley.edu University of California, Berkeley Security types to the rescue p. 2 Problem statement
Security types to the rescue p. 1 Security types to the rescue David Wagner and Rob Johnson {daw,rtjohnso}@cs.berkeley.edu University of California, Berkeley Security types to the rescue p. 2 Problem statement
Using the Juliet Test Suite to compare Static Security Scanners
 Using the Juliet Test Suite to compare Static Security Scanners Andreas Wagner 1, Johannes Sametinger 2 1 GAM Project, IT Solutions, Schwertberg, Austria 2 Dept. of Information Systems Software Engineering,
Using the Juliet Test Suite to compare Static Security Scanners Andreas Wagner 1, Johannes Sametinger 2 1 GAM Project, IT Solutions, Schwertberg, Austria 2 Dept. of Information Systems Software Engineering,
Automating Mimicry Attacks Using Static Binary Analysis
 Automating Mimicry Attacks Using Static Binary Analysis Christopher Kruegel and Engin Kirda Technical University Vienna chris@auto.tuwien.ac.at, engin@infosys.tuwien.ac.at Darren Mutz, William Robertson,
Automating Mimicry Attacks Using Static Binary Analysis Christopher Kruegel and Engin Kirda Technical University Vienna chris@auto.tuwien.ac.at, engin@infosys.tuwien.ac.at Darren Mutz, William Robertson,
Integration Testing of Protocol Implementations using Symbolic Distributed Execution
 Integration Testing of Protocol Implementations using Symbolic Distributed Execution Raimondas Sasnauskas, Philipp Kaiser, Russ Lucas Jukić, and Klaus Wehrle Communication and Distributed Systems (ComSys)
Integration Testing of Protocol Implementations using Symbolic Distributed Execution Raimondas Sasnauskas, Philipp Kaiser, Russ Lucas Jukić, and Klaus Wehrle Communication and Distributed Systems (ComSys)
Coverity White Paper. Reduce Your Costs: Eliminate Critical Security Vulnerabilities with Development Testing
 Reduce Your Costs: Eliminate Critical Security Vulnerabilities with Development Testing The Stakes Are Rising Security breaches in software and mobile devices are making headline news and costing companies
Reduce Your Costs: Eliminate Critical Security Vulnerabilities with Development Testing The Stakes Are Rising Security breaches in software and mobile devices are making headline news and costing companies
Bug hunting. Vulnerability finding methods in Windows 32 environments compared. FX of Phenoelit
 Bug hunting Vulnerability finding methods in Windows 32 environments compared FX of Phenoelit The goal: 0day What we are looking for: Handles network side input Runs on a remote system Is complex enough
Bug hunting Vulnerability finding methods in Windows 32 environments compared FX of Phenoelit The goal: 0day What we are looking for: Handles network side input Runs on a remote system Is complex enough
EECS 354 Network Security. Introduction
 EECS 354 Network Security Introduction Why Learn To Hack Understanding how to break into computer systems allows you to better defend them Learn how to think like an attacker Defense then becomes second-nature
EECS 354 Network Security Introduction Why Learn To Hack Understanding how to break into computer systems allows you to better defend them Learn how to think like an attacker Defense then becomes second-nature
ensuring security the way how we do it
 ensuring security the way how we do it HUSTEF, 2015.11.18 Attila Tóth 1 Nokia Solutions and Networks 2014 Disclaimer The ideas, processes, tools are presented from a practitioner s point of view working
ensuring security the way how we do it HUSTEF, 2015.11.18 Attila Tóth 1 Nokia Solutions and Networks 2014 Disclaimer The ideas, processes, tools are presented from a practitioner s point of view working
Full System Emulation:
 Full System Emulation: Achieving Successful Automated Dynamic Analysis of Evasive Malware Christopher Kruegel Lastline, Inc. chris@lastline.com 1 Introduction Automated malware analysis systems (or sandboxes)
Full System Emulation: Achieving Successful Automated Dynamic Analysis of Evasive Malware Christopher Kruegel Lastline, Inc. chris@lastline.com 1 Introduction Automated malware analysis systems (or sandboxes)
Bypassing Memory Protections: The Future of Exploitation
 Bypassing Memory Protections: The Future of Exploitation Alexander Sotirov alex@sotirov.net About me Exploit development since 1999 Research into reliable exploitation techniques: Heap Feng Shui in JavaScript
Bypassing Memory Protections: The Future of Exploitation Alexander Sotirov alex@sotirov.net About me Exploit development since 1999 Research into reliable exploitation techniques: Heap Feng Shui in JavaScript
Enhanced Model of SQL Injection Detecting and Prevention
 Enhanced Model of SQL Injection Detecting and Prevention Srinivas Baggam, Assistant Professor, Department of Computer Science and Engineering, MVGR College of Engineering, Vizianagaram, India. b_srinio@yahoo.com
Enhanced Model of SQL Injection Detecting and Prevention Srinivas Baggam, Assistant Professor, Department of Computer Science and Engineering, MVGR College of Engineering, Vizianagaram, India. b_srinio@yahoo.com
I Control Your Code Attack Vectors Through the Eyes of Software-based Fault Isolation. Mathias Payer, ETH Zurich
 I Control Your Code Attack Vectors Through the Eyes of Software-based Fault Isolation Mathias Payer, ETH Zurich Motivation Applications often vulnerable to security exploits Solution: restrict application
I Control Your Code Attack Vectors Through the Eyes of Software-based Fault Isolation Mathias Payer, ETH Zurich Motivation Applications often vulnerable to security exploits Solution: restrict application
Software Security Testing
 Software Security Testing Elizabeth Sanders Department of Electrical & Computer Engineering Missouri University of Science and Technology ejwxcf@mst.edu 2015 Elizabeth Sanders Pop Quiz What topics am I
Software Security Testing Elizabeth Sanders Department of Electrical & Computer Engineering Missouri University of Science and Technology ejwxcf@mst.edu 2015 Elizabeth Sanders Pop Quiz What topics am I
CONFIGURATION MANAGEMENT TECHNOLOGY FOR LARGE-SCALE SIMULATIONS
 SCS M&S Magazine. Vol 3. Issue 3. A. Sekiguchi, K. Shimada, Y. Wada, A. Ooba, R. Yoshimi, and A. Matsumoto. CONFIGURATION MANAGEMENT TECHNOLOGY FOR LARGE-SCALE SIMULATIONS Atsuji Sekiguchi, Kuniaki Shimada,
SCS M&S Magazine. Vol 3. Issue 3. A. Sekiguchi, K. Shimada, Y. Wada, A. Ooba, R. Yoshimi, and A. Matsumoto. CONFIGURATION MANAGEMENT TECHNOLOGY FOR LARGE-SCALE SIMULATIONS Atsuji Sekiguchi, Kuniaki Shimada,
RIPS - A static source code analyser for vulnerabilities in PHP scripts
 RIPS - A static source code analyser for vulnerabilities in PHP scripts Johannes Dahse 1 Introduction The amount of websites have increased rapidly during the last years. While websites consisted mostly
RIPS - A static source code analyser for vulnerabilities in PHP scripts Johannes Dahse 1 Introduction The amount of websites have increased rapidly during the last years. While websites consisted mostly
Module 10. Coding and Testing. Version 2 CSE IIT, Kharagpur
 Module 10 Coding and Testing Lesson 23 Code Review Specific Instructional Objectives At the end of this lesson the student would be able to: Identify the necessity of coding standards. Differentiate between
Module 10 Coding and Testing Lesson 23 Code Review Specific Instructional Objectives At the end of this lesson the student would be able to: Identify the necessity of coding standards. Differentiate between
The Need for Fourth Generation Static Analysis Tools for Security From Bugs to Flaws
 The Need for Fourth Generation Static Analysis Tools for Security From Bugs to Flaws By Evgeny Lebanidze Senior Security Consultant Cigital, Inc. This paper discusses some of the limitations of the current
The Need for Fourth Generation Static Analysis Tools for Security From Bugs to Flaws By Evgeny Lebanidze Senior Security Consultant Cigital, Inc. This paper discusses some of the limitations of the current
https://runtimeverification.com Grigore Rosu Founder, President and CEO Professor of Computer Science, University of Illinois
 https://runtimeverification.com Grigore Rosu Founder, President and CEO Professor of Computer Science, University of Illinois Runtime Verification, Inc. (RV): startup company aimed at bringing the best
https://runtimeverification.com Grigore Rosu Founder, President and CEO Professor of Computer Science, University of Illinois Runtime Verification, Inc. (RV): startup company aimed at bringing the best
Testing Automation for Distributed Applications By Isabel Drost-Fromm, Software Engineer, Elastic
 Testing Automation for Distributed Applications By Isabel Drost-Fromm, Software Engineer, Elastic The challenge When building distributed, large-scale applications, quality assurance (QA) gets increasingly
Testing Automation for Distributed Applications By Isabel Drost-Fromm, Software Engineer, Elastic The challenge When building distributed, large-scale applications, quality assurance (QA) gets increasingly
Introduction. Figure 1 Schema of DarunGrim2
 Reversing Microsoft patches to reveal vulnerable code Harsimran Walia Computer Security Enthusiast 2011 Abstract The paper would try to reveal the vulnerable code for a particular disclosed vulnerability,
Reversing Microsoft patches to reveal vulnerable code Harsimran Walia Computer Security Enthusiast 2011 Abstract The paper would try to reveal the vulnerable code for a particular disclosed vulnerability,
How I Learned to Stop Fuzzing and Find More Bugs
 How I Learned to Stop Fuzzing and Find More Bugs Jacob West Fortify Software August 3-5, 2007 Las Vegas Agenda Introduction to fuzzing What is fuzzing? Challenges with fuzzing Introduction to static analysis
How I Learned to Stop Fuzzing and Find More Bugs Jacob West Fortify Software August 3-5, 2007 Las Vegas Agenda Introduction to fuzzing What is fuzzing? Challenges with fuzzing Introduction to static analysis
Lecture 10: Dynamic Memory Allocation 1: Into the jaws of malloc()
 CS61: Systems Programming and Machine Organization Harvard University, Fall 2009 Lecture 10: Dynamic Memory Allocation 1: Into the jaws of malloc() Prof. Matt Welsh October 6, 2009 Topics for today Dynamic
CS61: Systems Programming and Machine Organization Harvard University, Fall 2009 Lecture 10: Dynamic Memory Allocation 1: Into the jaws of malloc() Prof. Matt Welsh October 6, 2009 Topics for today Dynamic
How To Research Security And Privacy Using Data Science
 Research Topics in Security and Privacy using Data Science School of Informatics University of Edinburgh David Aspinall David.Aspinall@ed.ac.uk http://secpriv.inf.ed.ac.uk/ http://cybersec.ed.ac.uk/ Outline
Research Topics in Security and Privacy using Data Science School of Informatics University of Edinburgh David Aspinall David.Aspinall@ed.ac.uk http://secpriv.inf.ed.ac.uk/ http://cybersec.ed.ac.uk/ Outline
CHAPTER 5 INTELLIGENT TECHNIQUES TO PREVENT SQL INJECTION ATTACKS
 66 CHAPTER 5 INTELLIGENT TECHNIQUES TO PREVENT SQL INJECTION ATTACKS 5.1 INTRODUCTION In this research work, two new techniques have been proposed for addressing the problem of SQL injection attacks, one
66 CHAPTER 5 INTELLIGENT TECHNIQUES TO PREVENT SQL INJECTION ATTACKS 5.1 INTRODUCTION In this research work, two new techniques have been proposed for addressing the problem of SQL injection attacks, one
1. Software and Security
 To appear in IEEE Software, Jan/Feb 2002. Pre-publication version 31 October 2001. Not for distribution. Improving Security Using Extensible Lightweight Static Analysis David Evans and David Larochelle
To appear in IEEE Software, Jan/Feb 2002. Pre-publication version 31 October 2001. Not for distribution. Improving Security Using Extensible Lightweight Static Analysis David Evans and David Larochelle
Two Flavors in Automated Software Repair: Rigid Repair and Plastic Repair
 Two Flavors in Automated Software Repair: Rigid Repair and Plastic Repair Martin Monperrus, Benoit Baudry Dagstuhl Preprint, Seminar #13061, 2013. Link to the latest version Abstract In this paper, we
Two Flavors in Automated Software Repair: Rigid Repair and Plastic Repair Martin Monperrus, Benoit Baudry Dagstuhl Preprint, Seminar #13061, 2013. Link to the latest version Abstract In this paper, we
A Framework for Measuring Software Obfuscation Resilience Against Automated Attacks
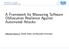 Fakultät für Informatik Technische Universität München A Framework for Measuring Software Obfuscation Resilience Against Automated Attacks Sebastian Banescu, Martín Ochoa and Alexander Pretschner Outline
Fakultät für Informatik Technische Universität München A Framework for Measuring Software Obfuscation Resilience Against Automated Attacks Sebastian Banescu, Martín Ochoa and Alexander Pretschner Outline
Obfuscation: know your enemy
 Obfuscation: know your enemy Ninon EYROLLES neyrolles@quarkslab.com Serge GUELTON sguelton@quarkslab.com Prelude Prelude Plan 1 Introduction What is obfuscation? 2 Control flow obfuscation 3 Data flow
Obfuscation: know your enemy Ninon EYROLLES neyrolles@quarkslab.com Serge GUELTON sguelton@quarkslab.com Prelude Prelude Plan 1 Introduction What is obfuscation? 2 Control flow obfuscation 3 Data flow
EXPERIMENTAL EVALUATION AND RESULT DISCUSSION OF METAMORPHIC TESTING AUTOMATION FRAMEWORK WITH NOVEL ALGORITHMS
 International Journal of Computer Engineering & Technology (IJCET) Volume 7, Issue 1, Jan-Feb 2016, pp. 26-35, Article ID: IJCET_07_01_004 Available online at http://www.iaeme.com/ijcet/issues.asp?jtype=ijcet&vtype=7&itype=1
International Journal of Computer Engineering & Technology (IJCET) Volume 7, Issue 1, Jan-Feb 2016, pp. 26-35, Article ID: IJCET_07_01_004 Available online at http://www.iaeme.com/ijcet/issues.asp?jtype=ijcet&vtype=7&itype=1
