What happens when you swipe your card?
|
|
|
- Claude Stewart
- 8 years ago
- Views:
Transcription
1 What happens when you swipe your card? As hacking of top retailers make headlines, Bill Whitaker discovers how insecure your credit card information is this holiday season The following is a script of "Swiping you Card" which aired on Nov. 30, Bill Whitaker is the correspondent. David Schneider, producer. This holiday shopping season you might worry that every time you swipe your credit or debit card some criminal might be swiping your account number and with good reason. The number of reported, illegal intrusions into the computer systems of U.S. companies is at a record high this year and climbing. The hacking of Target, Home Depot, Staples and other top retailers made headlines. Behind the headlines are two separate crimes with two sets of criminals. Sophisticated cyberthieves steal your credit card information. Common criminals buy it and go on shopping sprees -- racking up billions of dollars in fraudulent purchases. The cost of the fraud is calculated into the price of every item you buy. When computer crooks swipe your card number, we all end up paying the price is becoming known as the "year of the data breach." The theft of 40 million credit cards from Target late last year was followed by news of a breach at Michaels stores involving more than two million credit cards. Then came P.F. Chang's. And in September, Home Depot announced that 56 million of its customers' credit card numbers were stolen. Dave DeWalt: Nearly every company is vulnerable. Dave DeWalt is CEO of FireEye, a cybersecurity company that gets hired to keep hackers from getting into a company's network or getting them out after there's been a breach.
2 Dave DeWalt: Even the strongest banks in the world-- banks like JPMorgan, retailers like Home Depot, retailers like Target -- can't spend enough money or hire enough people to solve this problem. Bill Whitaker: Cybersecurity is a misnomer? There is no cybersecurity it sounds like you're saying. Dave DeWalt: This isn't a lack of effort. Most of the large companies are growing their security spend. Yet 97 percent -- literally 97 percent of all companies -- are getting breached. So there's a gap here. Bill Whitaker: Ninety-seven percent? Dave DeWalt: Ninety-seven percent. In fact, we... Bill Whitaker: That's outrageous. Dave DeWalt: It is outrageous. It's pretty amazing. FireEye tracks assaults on its clients with a real time map showing where computer attacks originate and their targets. It's an eerie throwback to Cold War illustrations of what a nuclear missile attack might look like, but with cyber attacks...
3 Bill Whitaker: This goes on 24 hours a day. Charles Carmakal: 24 hours a day, yeah. Charles Carmakal leads teams of first responders for FireEye. Charles Carmakal: We are seeing hundreds of thousands of attacks on a weekly basis across the globe. Bill Whitaker: And these are just the ones that your systems are picking up. Charles Carmakal: That's right. Dave DeWalt: On average the breaches from the time of infection, from when the bad guys get in to the time they are discovered, is a whopping 229 days. 229 days. Forensic investigations reveal that 80 percent of security breaches involve stolen and weak passwords. One of the most common is: Dave DeWalt: The days when we have our username and password, which is our son or daughter's name or our cat or our dog is not enough security for, you know, for today's attackers. Breaches are inevitable. It's happening. It's just life that we live in today.
4 Bill Whitaker: Inevitable? Dave DeWalt: Inevitable. Bill Whitaker: Just accept that... Dave DeWalt: Accept that a little bit... Bill Whitaker:...they are going to get in. Dave DeWalt: They're going to get in. But don't let them access the information that's really important. Don't let them get back out with that information. Detect it sooner. Respond sooner. And ultimately that exposure is very small. Maybe they got away with a few credit cards. Maybe they didn't get away with any credit cards. But they didn't steal 56 million of them or 40 million of them. "You know, they're running a business. And frankly they're not focused on cybersecurity." Target declined our request for an on-camera interview, but the breach of its security a year ago is a case study in how hackers operate. It started when criminals stole the username and password from one of Target's vendors -- a Pennsylvania heating and air conditioning company. The credentials got them into Target's network without attracting attention. Once inside they easily spread to thousands of checkout terminals in nearly every store. The hackers then installed malicious software, or malware, to record card swipes. Dave DeWalt: The company invested a lot of money in security. It wasn't like they weren't trying to stop the bad guys. It's just the bad guys were really good, number one. Number two, they're very persistent. A security system Target recently bought from Dave DeWalt's company, did detect the intrusion, and triggered alarms. But Target's older security systems were still in place, generating millions of alerts similar to these. Most were for minor technical glitches and the warnings from FireEye were lost in the noise. Bill Whitaker: So alarms were going off? Dave DeWalt: Alarms were going off. And when you get millions of alerts a day and there's one or two alerts that are the ones blinking red, "There's a problem. There's a problem." You can miss it and it's very hard to find the needle in the haystack. So Target's problem ultimately became, "I couldn't find the needle. I couldn't see the one alert that was bright red." Last December 18, a week before Christmas, a cybersecurity blogger named Brian Krebs first reported the story publicly. Brian Krebs: The breach lasted for a little more than three weeks. But they actually managed to hit Target at the busiest time of year for them.
5 Krebs' office is like a computerized crow's nest: a high-tech perch from which he scours the cyberworld for early signs of underworld activity. Over the past year he broke the news on his blog that criminals had hacked into a dozen retailers and chain restaurants including Dairy Queen and The Home Depot. Brian Krebs: A lot of times those companies have already been notified by law enforcement, by Secret Service or the FBI. Bill Whitaker: But it sounds like it's usually discovered by people outside of the company. Brian Krebs: That's almost universally true. Yes. Bill Whitaker: Why is that? Brian Krebs: A lot of times the first indicators that you get that one of these organizations is comprised is when their customers' financial information goes up for sale in the underground. You know, they're running a business. And frankly they're not focused on cybersecurity. There are scores of sinister online shopping bazaars where cyberthieves put their goods up for sale. Think Amazon.com for thieves. This is where Krebs does his detective work. Bill Whitaker: They're just right on the Web? You can buy stolen cards by just going to this site?
6 Brian Krebs: Absolutely. Big batches of stolen card numbers are called dumps. Krebs figures out which banks have customers' stolen cards up for sale and alerts them. The banks then check to see which merchant is the common link. Brian Krebs: If they're willing to share that information with me, I can take that and go back to other banks and say, "Look, this is the pattern they're seeing. What are you seeing?" The bulk of cards sell for anywhere from 10 to 50 dollars, depending on things like the expiration date, or the credit limit. Brian Krebs: In the case of Target they stole 40 million cards. But you know how many cards they managed to sell? About five percent of those. Bill Whitaker: That's still a lot of cards. Brian Krebs: It's still a lot. And I say "only" because each of those cards, the average price was about 20 dollars per card. So that's a lot of money any way you slice it. "The banks are the victims who are actually paying for the breaches, rather than the retailers..."
7 The thieves offer volume discounts and sales and customer service includes refunds if the cards have been cancelled. Brian Krebs: If you buy from them and it comes back as declined, they'll automatically credit the amount that you bought for that card cost. So they'll automatically credit your account. Bill Whitaker: You're kidding. This stolen card will work or you'll get your money back? Brian Krebs: Yeah, absolutely. Customers are told to make payments with Western Union or other money transfer methods. Credit cards are not accepted. The masterminds behind the hacking and selling of stolen card data are sophisticated crime syndicates. Most are in Russia and Eastern Europe -- primarily Ukraine -- and out of the easy reach of American law enforcement. Ed Lowery heads the criminal division of the U.S. Secret Service, which investigates financial cybercrimes. Bill Whitaker: The fairly big breaches we've been seeing -- Target, Home Depot. Who's behind that? Ed Lowery: Well, those are professional cybercriminals. Those individuals, they make their living -- and a very good living, at times -- attacking the U.S. financial infrastructure. That level of cybercriminal. That is the new-age cartel, as it were.
8 Secret Service arrests have led to the convictions of 14 people, but there are plenty of others to take their places. The criminals buying the stolen numbers don't have to be that sophisticated. Bill Whitaker: Is it fairly easy to turn those numbers you buy online into one of these cards? Ed Lowery: Now, I really don't want the general public to think that they should go out and start committing fraud. But obviously, the encoding and all takes a little higher level of sophistication. And you have to have the criminal drive to do it. But is it highly technical? In light of the intrusions we're speaking about, and the rest, it's not nearly that sophisticated. Buyers are all over the world. In the U.S., street gangs are among the crooks to use stolen cards. They buy gift cards, which are like cash, and electronics, which they resell for quick profits. Brian Krebs: If you buy a card for 20 bucks and you can make 400 dollars off each card, that's a pretty good return on your investment. Bill Whitaker: Pretty good. For many banks, news of a breach from Brian Krebs is the first sign they have of a problem. Two of his regular readers are Barry Abramowitz, chief information officer for Liberty Bank in Connecticut, and Linda Swartz, who heads up security for Westfield Bank in Massachusetts.
9 Bill Whitaker: So you don't hear about it until Brian Krebs breaks it? Linda Swartz: Pretty much. Barry Abramowitz: That's what makes his work so valuable. Linda Swartz: Exactly. If you know there's a problem, you can stop it from occurring or stop the bleeding before it gets too bad. But you need to know that information. Most banks and credit unions rely on MasterCard, Visa and other card companies to notify them when a customers' account may have been stolen, but they're not told which retailer was hacked or when. Bill Whitaker: Why don't they tell you which retailer is responsible or involved? Barry Abramowitz: I don't know. Linda Swartz: Probably so it doesn't place the blame on the merchant who was compromised. They don't want us to go back to that merchant and say, "You know, your system was compromised. You lost my customers' information." Bill Whitaker: Why not? Linda Swartz: It's business. I mean, I hate actually saying that it was Home Depot and Target, but those are the ones that are in the media. "The cards themselves are fundamentally fraud-prone." Bill Whitaker: How big a problem are these security breaches for the banks? Barry Abramowitz: Huge. Linda Swartz: Yeah. Barry Abramowitz: Huge. In 2013, stolen credit cards led to estimates as high as 11 billion dollars in fraud in the U.S. That doesn't include the cost to banks of replacing millions of cards and monitoring customers' accounts for suspicious activity. Bill Whitaker: So when the customer is told that he's not going to lose anything out of his pocket. The customers not going to pay for the fraud, somebody's paying for it. Linda Swartz: The bank.
10 Barry Abramowitz: The banks are the victims who are actually paying for the breaches, rather than the retailers that have had the information compromised. The Home Depot, like other recently breached retailers, declined our request for an on-camera interview, citing ongoing investigations. Mallory Duncan is with the National Retail Federation, the industry's largest trade group. He says the magnetic stripe cards are just too easy to counterfeit. Mallory Duncan: The underlying problem is that we have cards that were designed for the 1960s, '70s and '80s but we now have hackers who are using 21st century tools to break in. Bill Whitaker: Are the retailers really doing everything they can to secure customers' information? Mallory Duncan: We're doing everything we possibly can to secure it. Bill Whitaker: What does that mean "possibly can"? Mallory Duncan: Well, because the problem is you're trying to secure a house of straw. The cards themselves are fundamentally fraud-prone. After a year of relentless breaches, bankers, retailers and security companies all agree the technology behind credit cards is broken and needs to change. Visa and MasterCard declined to be interviewed, but said the roll out of credit cards with computer chip technology next year will make counterfeiting cards almost impossible. Bill Whitaker: Apple and Google are promoting their own payment systems to protect account information and retailers, like The Home Depot, are encrypting the data. The changes will cost billions of dollars and take years to implement. Bill Whitaker: This Christmas shopping season, you're expecting this to happen again. Linda Swartz: Absolutely. We know it's going to. It's inevitable. We feel like we're just kind of sitting and waiting for it to happen. There's not a lot we can do to stop it.
DATA SECURITY: EVERYTHING YOU NEED TO KNOW
 DATA SECURITY: EVERYTHING YOU NEED TO KNOW! Data Breaches: Where, What and Why! Federal and State Regulations to Protect Data! EMV Chip Technology! PIN or Signature?! Existing and Emerging Security Options!
DATA SECURITY: EVERYTHING YOU NEED TO KNOW! Data Breaches: Where, What and Why! Federal and State Regulations to Protect Data! EMV Chip Technology! PIN or Signature?! Existing and Emerging Security Options!
7 Steps to Protect Your Company from a Data Breach
 7 Steps to Protect Your Company from a Data Breach August 11, 2015 Michael Pinna and Stuart Nussbaum Millions of government personnel files were recently compromised as part of a malicious hacking of the
7 Steps to Protect Your Company from a Data Breach August 11, 2015 Michael Pinna and Stuart Nussbaum Millions of government personnel files were recently compromised as part of a malicious hacking of the
Top Ten Fraud Risks That Impact Your Financial Institution. Presented by Ann Davidson - VP Risk Consulting Allied Solutions LLC.
 Top Ten Fraud Risks That Impact Your Financial Institution Presented by Ann Davidson - VP Risk Consulting Allied Solutions LLC Agenda Education on understanding the fraud risk Take away.. Education to
Top Ten Fraud Risks That Impact Your Financial Institution Presented by Ann Davidson - VP Risk Consulting Allied Solutions LLC Agenda Education on understanding the fraud risk Take away.. Education to
How To Stop A Cybercriminal From Stealing A Credit Card Data From A Business Network
 2012 Payment Card Threat Report The second annual study of unencrypted payment card storage Automated Attacks and Card Data Handling In 2011, data breaches increased 42% and as such, last year was reported
2012 Payment Card Threat Report The second annual study of unencrypted payment card storage Automated Attacks and Card Data Handling In 2011, data breaches increased 42% and as such, last year was reported
The Merchant. Skimming is No Laughing Matter. A hand held skimming device. These devices can easily be purchased online.
 1 February 2010 Volume 2, Issue 1 The Merchant Serving Florida State University s Payment Card Community Individual Highlights: Skimming Scam 1 Skimming at Work 2 Safe at Home 3 Read your Statement 4 Useful
1 February 2010 Volume 2, Issue 1 The Merchant Serving Florida State University s Payment Card Community Individual Highlights: Skimming Scam 1 Skimming at Work 2 Safe at Home 3 Read your Statement 4 Useful
Cybersecurity Workshop
 Cybersecurity Workshop February 10, 2015 E. Andrew Keeney, Esq. Kaufman & Canoles, P.C. E. Andrew Keeney, Esq. Kaufman & Canoles, P.C. 150 West Main Street, Suite 2100 Norfolk, VA 23510 (757) 624-3153
Cybersecurity Workshop February 10, 2015 E. Andrew Keeney, Esq. Kaufman & Canoles, P.C. E. Andrew Keeney, Esq. Kaufman & Canoles, P.C. 150 West Main Street, Suite 2100 Norfolk, VA 23510 (757) 624-3153
National Cybersecurity Awareness Campaign
 National Cybersecurity Awareness Campaign About Stop.Think.Connect. In 2009, President Obama issued the Cyberspace Policy Review, which tasked the Department of Homeland Security with creating an ongoing
National Cybersecurity Awareness Campaign About Stop.Think.Connect. In 2009, President Obama issued the Cyberspace Policy Review, which tasked the Department of Homeland Security with creating an ongoing
With the Target breach on everyone s mind, you may find these Customer Service Q & A s helpful.
 With the Target breach on everyone s mind, you may find these Customer Service Q & A s helpful. Breach Overview Q: Media reports are stating that Target experienced a data breach. Can you provide more
With the Target breach on everyone s mind, you may find these Customer Service Q & A s helpful. Breach Overview Q: Media reports are stating that Target experienced a data breach. Can you provide more
White Paper: Are there Payment Threats Lurking in Your Hospital?
 White Paper: Are there Payment Threats Lurking in Your Hospital? With all the recent high profile stories about data breaches, payment security is a hot topic in healthcare today. There s been a steep
White Paper: Are there Payment Threats Lurking in Your Hospital? With all the recent high profile stories about data breaches, payment security is a hot topic in healthcare today. There s been a steep
Why Data Security is Critical to Your Brand
 Why Data Security is Critical to Your Brand Why security is critical to your brand Cybercriminals do not discriminate based on industry or business size. Security is expensive. At least, it is if you wait
Why Data Security is Critical to Your Brand Why security is critical to your brand Cybercriminals do not discriminate based on industry or business size. Security is expensive. At least, it is if you wait
CYBERSECURITY FRAUD LOSS ISSUES & HOW TO ADDRESS RISKS IN TODAY'S INSURANCE MARKETPLACE 12/16/2015. December 17, 2015
 12/16/2015 CYBERSECURITY FRAUD LOSS ISSUES & HOW TO ADDRESS RISKS IN TODAY'S INSURANCE MARKETPLACE December 17, 2015 Angela R. Morelock, CPA, CFE, CFF, ABV Partner, BKD, LLP amorelock@bkd.com Jeff Eiserman
12/16/2015 CYBERSECURITY FRAUD LOSS ISSUES & HOW TO ADDRESS RISKS IN TODAY'S INSURANCE MARKETPLACE December 17, 2015 Angela R. Morelock, CPA, CFE, CFF, ABV Partner, BKD, LLP amorelock@bkd.com Jeff Eiserman
WRITTEN TESTIMONY BEFORE THE HEARING ON PROTECTING PERSONAL CONSUMER INFORMATION FROM CYBER ATTACKS AND DATA BREACHES MARCH 26, 2014 2:30 PM
 WRITTEN TESTIMONY BEFORE THE SENATE COMMITTEE ON COMMERCE, SCIENCE, & TRANSPORTATION HEARING ON PROTECTING PERSONAL CONSUMER INFORMATION FROM CYBER ATTACKS AND DATA BREACHES MARCH 26, 2014 2:30 PM TESTIMONY
WRITTEN TESTIMONY BEFORE THE SENATE COMMITTEE ON COMMERCE, SCIENCE, & TRANSPORTATION HEARING ON PROTECTING PERSONAL CONSUMER INFORMATION FROM CYBER ATTACKS AND DATA BREACHES MARCH 26, 2014 2:30 PM TESTIMONY
Mortgage Guide and Helpful Tips
 Mortgage Guide and Helpful Tips Dear Prospective Home Owner, Let me tell you that home ownership is one of the key ingredients to building wealth. Take any 100 people at the start of their working careers
Mortgage Guide and Helpful Tips Dear Prospective Home Owner, Let me tell you that home ownership is one of the key ingredients to building wealth. Take any 100 people at the start of their working careers
Proactive Credential Monitoring as a Method of Fraud Prevention and Risk Mitigation. By Marc Ostryniec, vice president, CSID
 Proactive Credential Monitoring as a Method of Fraud Prevention and Risk Mitigation By Marc Ostryniec, vice president, CSID The increase in volume, severity, publicity and fallout of recent data breaches
Proactive Credential Monitoring as a Method of Fraud Prevention and Risk Mitigation By Marc Ostryniec, vice president, CSID The increase in volume, severity, publicity and fallout of recent data breaches
Cell Phone Hijacking. >> After four months of harassing phone calls, Heather and Courtney Kuykendall were afraid to
 Cell Phone Hijacking >> After four months of harassing phone calls, Heather and Courtney Kuykendall were afraid to answer their cell phones. The graphic violent threats came at all hours, forcing the family
Cell Phone Hijacking >> After four months of harassing phone calls, Heather and Courtney Kuykendall were afraid to answer their cell phones. The graphic violent threats came at all hours, forcing the family
A: We really embarrassed ourselves last night at that business function.
 Dialog: VIP LESSON 049 - Future of Business A: We really embarrassed ourselves last night at that business function. B: What are you talking about? A: We didn't even have business cards to hand out. We
Dialog: VIP LESSON 049 - Future of Business A: We really embarrassed ourselves last night at that business function. B: What are you talking about? A: We didn't even have business cards to hand out. We
WRITTEN TESTIMONY BEFORE THE HEARING ON FEBRUARY 4, 2014 TESTIMONY OF JOHN MULLIGAN TARGET
 WRITTEN TESTIMONY BEFORE THE SENATE COMMITTEE ON THE JUDICIARY HEARING ON PRIVACY IN THE DIGITAL AGE: PREVENTING DATA BREACHES AND COMBATING CYBERCRIME FEBRUARY 4, 2014 TESTIMONY OF JOHN MULLIGAN EXECUTIVE
WRITTEN TESTIMONY BEFORE THE SENATE COMMITTEE ON THE JUDICIARY HEARING ON PRIVACY IN THE DIGITAL AGE: PREVENTING DATA BREACHES AND COMBATING CYBERCRIME FEBRUARY 4, 2014 TESTIMONY OF JOHN MULLIGAN EXECUTIVE
Target Security Breach
 Target Security Breach Lessons Learned for Retailers and Consumers 2014 Pointe Solutions, Inc. PO Box 41, Exton, PA 19341 USA +1 610 524 1230 Background In the aftermath of the Target breach that affected
Target Security Breach Lessons Learned for Retailers and Consumers 2014 Pointe Solutions, Inc. PO Box 41, Exton, PA 19341 USA +1 610 524 1230 Background In the aftermath of the Target breach that affected
What the Biggest Data Breaches in Retail Have Taught Us about Cyber Security
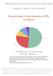 What the Biggest Data Breaches in Retail Have Taught Us about Cyber Security With the holiday season upon us, much attention turns to the retail sector, which is expected to see unprecedented activity
What the Biggest Data Breaches in Retail Have Taught Us about Cyber Security With the holiday season upon us, much attention turns to the retail sector, which is expected to see unprecedented activity
Clear and Present Payments Danger: Fraud Shifting To U.S., Getting More Complex
 Clear and Present Payments Danger: Fraud Shifting To U.S., Getting More Complex Q: Good morning, this is Alex Walsh at PYMNTS.com. I m joined by David Mattei, the vice president and product manager for
Clear and Present Payments Danger: Fraud Shifting To U.S., Getting More Complex Q: Good morning, this is Alex Walsh at PYMNTS.com. I m joined by David Mattei, the vice president and product manager for
AN INFORMATION GOVERNANCE BEST
 SMALL BUSINESS ID THEFT AND FRAUD AN INFORMATION GOVERNANCE BEST PRACTICES GUIDE FOR SMALL BUSINESS IT IS NOT A MATTER OF IF BUT WHEN AN INTRUSION WILL BE ATTEMPTED ON YOUR BUSINESS COMPUTER SYSTEM IN
SMALL BUSINESS ID THEFT AND FRAUD AN INFORMATION GOVERNANCE BEST PRACTICES GUIDE FOR SMALL BUSINESS IT IS NOT A MATTER OF IF BUT WHEN AN INTRUSION WILL BE ATTEMPTED ON YOUR BUSINESS COMPUTER SYSTEM IN
Emerging Trends in the Payment Ecosystem: The Good, the Bad and the Ugly DAN KRAMER
 Emerging Trends in the Payment Ecosystem: The Good, the Bad and the Ugly DAN KRAMER SHAZAM, Senior Vice President Agenda The Ugly Fraud The Bad EMV? The Good Tokenization and Other Emerging Payment Options
Emerging Trends in the Payment Ecosystem: The Good, the Bad and the Ugly DAN KRAMER SHAZAM, Senior Vice President Agenda The Ugly Fraud The Bad EMV? The Good Tokenization and Other Emerging Payment Options
1. Ask what your financial institution knows or has personally experienced with regard to internal and external data breaches.
 Part 1: Internal & External Data Breach Vulnerabilities Presented on: Thursday, February 12, 2 3 ET Co presented by: Ann Davidson VP of Risk Consulting at Allied Solutions Joe Majka CSO at Verifone 1 Breakdown
Part 1: Internal & External Data Breach Vulnerabilities Presented on: Thursday, February 12, 2 3 ET Co presented by: Ann Davidson VP of Risk Consulting at Allied Solutions Joe Majka CSO at Verifone 1 Breakdown
Statement for the Record. Richard Bejtlich. Chief Security Strategist. FireEye, Inc. Before the. U.S. House of Representatives
 Statement for the Record Richard Bejtlich Chief Security Strategist FireEye, Inc. Before the U.S. House of Representatives Committee on Energy and Commerce Subcommittee on Oversight and Investigations
Statement for the Record Richard Bejtlich Chief Security Strategist FireEye, Inc. Before the U.S. House of Representatives Committee on Energy and Commerce Subcommittee on Oversight and Investigations
Are You A Sitting Duck?
 The 7 Most Cricitcal I.T. Security Protections Every Business Must Have in Place Now to Protect Themselves from Cybercrime, Data Breaches, and Hacker Attacks Cybercrime is at an all-time high, and hackers
The 7 Most Cricitcal I.T. Security Protections Every Business Must Have in Place Now to Protect Themselves from Cybercrime, Data Breaches, and Hacker Attacks Cybercrime is at an all-time high, and hackers
Newtek, The Small Business Authority 855-2thesba www.thesba.com. thesba.com 855-2thesba
 thesba.com 855-2thesba EMV Chip Technology, Secure Electronic Payments The world of payments is evolving. We are starting to see an evolution from typical static magnetic strip cards to more intelligent
thesba.com 855-2thesba EMV Chip Technology, Secure Electronic Payments The world of payments is evolving. We are starting to see an evolution from typical static magnetic strip cards to more intelligent
YOU WILL NOT BE EFFECTIVE READING THIS.
 This is the most effective and powerful script for securing appointment with FSBO's you will ever put to use. This scrip will increase your appointment closing ratio by 50-60%. The thing to keep in mind
This is the most effective and powerful script for securing appointment with FSBO's you will ever put to use. This scrip will increase your appointment closing ratio by 50-60%. The thing to keep in mind
Target Data Breach Survey of Illinois Banks. Executive Summary
 Target Data Breach Survey of Illinois Banks Executive Summary February 2014 www.ilbanker.com Target Data Breach Survey of Illinois Banks Executive Summary In December of 2013, just days before the holidays,
Target Data Breach Survey of Illinois Banks Executive Summary February 2014 www.ilbanker.com Target Data Breach Survey of Illinois Banks Executive Summary In December of 2013, just days before the holidays,
This notice contains important information about the data breaches announced by Home Depot, Kmart and Dairy Queen.
 RECENT DATA BREACHES This notice contains important information about the data breaches announced by Home Depot, Kmart and Dairy Queen. Data security is a number one priority at Northwest. We take every
RECENT DATA BREACHES This notice contains important information about the data breaches announced by Home Depot, Kmart and Dairy Queen. Data security is a number one priority at Northwest. We take every
Why is this National Cyber Security Month? Stephen G. Austin, CPA, MBA Swenson Advisors, LLP
 Why is this National Cyber Security Month? Stephen G. Austin, CPA, MBA, LLP Created as a collaborative effort between government and industry to ensure every American has the resources they need to stay
Why is this National Cyber Security Month? Stephen G. Austin, CPA, MBA, LLP Created as a collaborative effort between government and industry to ensure every American has the resources they need to stay
Data Security, Fraud Prevention, and Cost Control. Mike Dorland, CPP Regional Marketing Representative Michigan Retailers Association
 Data Security, Fraud Prevention, and Cost Control Mike Dorland, CPP Regional Marketing Representative Michigan Retailers Association Michigan Retailers Association Incorporated in 1940 Represent retail
Data Security, Fraud Prevention, and Cost Control Mike Dorland, CPP Regional Marketing Representative Michigan Retailers Association Michigan Retailers Association Incorporated in 1940 Represent retail
CYBERSECURITY: Is Your Business Ready?
 CYBERSECURITY: Is Your Business Ready? Cybersecurity: Is your business ready? Cyber risk is just like any other corporate risk and it must be managed from the top. An organization will spend time monitoring
CYBERSECURITY: Is Your Business Ready? Cybersecurity: Is your business ready? Cyber risk is just like any other corporate risk and it must be managed from the top. An organization will spend time monitoring
$22k. Payment Card Data Breaches: What You Need to Know About Your Risk and Liability. First Data Market Insight
 Need to Know About Your Risk and Liability Many small merchants are surprised to learn that they can be held liable for tens of thousands of dollars in fines and other expenses when a card data breach
Need to Know About Your Risk and Liability Many small merchants are surprised to learn that they can be held liable for tens of thousands of dollars in fines and other expenses when a card data breach
How to Choose the Right Credit Card Processing Company
 How to Choose the Right Credit Card Processing Company How To Choose The Right Credit Card Processing Company If you're in business these days, you need to accept credit cards. The problem is, which type
How to Choose the Right Credit Card Processing Company How To Choose The Right Credit Card Processing Company If you're in business these days, you need to accept credit cards. The problem is, which type
Prepared testimony of W. Joseph Majka Head of Fraud Control and Investigations Visa Inc.
 Prepared testimony of W. Joseph Majka Head of Fraud Control and Investigations Visa Inc. Before the Subcommittee on Emerging Threats, Cybersecurity, and Science and Technology of the House Committee on
Prepared testimony of W. Joseph Majka Head of Fraud Control and Investigations Visa Inc. Before the Subcommittee on Emerging Threats, Cybersecurity, and Science and Technology of the House Committee on
FIGHTING FRAUD: IMPROVING INFORMATION SECURITY TESTIMONY OF JOHN J. BRADY VICE PRESIDENT, MERCHANT FRAUD CONTROL MASTERCARD INTERNATIONAL
 FIGHTING FRAUD: IMPROVING INFORMATION SECURITY TESTIMONY OF JOHN J. BRADY VICE PRESIDENT, MERCHANT FRAUD CONTROL MASTERCARD INTERNATIONAL Before the Subcommittee on Financial Institutions and Consumer
FIGHTING FRAUD: IMPROVING INFORMATION SECURITY TESTIMONY OF JOHN J. BRADY VICE PRESIDENT, MERCHANT FRAUD CONTROL MASTERCARD INTERNATIONAL Before the Subcommittee on Financial Institutions and Consumer
When life happens... Protect Against Identity Theft. Keeping personal information safe & what to do if it happens to you
 When life happens... Protect Against Identity Theft Keeping personal information safe & what to do if it happens to you An Identity Theft Epidemic Identity theft is a huge business in the U.S. and around
When life happens... Protect Against Identity Theft Keeping personal information safe & what to do if it happens to you An Identity Theft Epidemic Identity theft is a huge business in the U.S. and around
An Oracle White Paper July 2010 U.S. CARD FRAUD
 An Oracle White Paper July 2010 U.S. CARD FRAUD Contents Card fraud can be placed into six categories:... 3 2 Card fraud costs the U.S. card payments industry an estimated US$8.6 billion per year. Although
An Oracle White Paper July 2010 U.S. CARD FRAUD Contents Card fraud can be placed into six categories:... 3 2 Card fraud costs the U.S. card payments industry an estimated US$8.6 billion per year. Although
Remarkable Hacking-Incidents in 2013/2014
 Remarkable Hacking-Incidents in 2013/2014 Peter Panholzer Arbeitsgruppe ICS CYBER SECURITY AUSTRIA Verein zur Förderung der Sicherheit Österreichs strategischer Infrastruktur Industrial Security Control
Remarkable Hacking-Incidents in 2013/2014 Peter Panholzer Arbeitsgruppe ICS CYBER SECURITY AUSTRIA Verein zur Förderung der Sicherheit Österreichs strategischer Infrastruktur Industrial Security Control
PCI Compliance for Healthcare
 PCI Compliance for Healthcare Best practices for securing payment card data In just five years, criminal attacks on healthcare organizations are up by a stunning 125%. 1 Why are these data breaches happening?
PCI Compliance for Healthcare Best practices for securing payment card data In just five years, criminal attacks on healthcare organizations are up by a stunning 125%. 1 Why are these data breaches happening?
How To Help Protect Yourself From Identity Theft
 How To Help Protect Yourself From Identity Theft January 20, 2015 Bryan Strong Senior Vice President and Director Information Security This complimentary interactive webinar is sponsored by Zions Bank
How To Help Protect Yourself From Identity Theft January 20, 2015 Bryan Strong Senior Vice President and Director Information Security This complimentary interactive webinar is sponsored by Zions Bank
WHITE PAPER KEEPING CLIENT AND EMPLOYEE DATA SECURE DRIVES REVENUE AND BUILDS TRUST PROTECTING THE PROTECTOR
 KEEPING CLIENT AND EMPLOYEE DATA SECURE DRIVES REVENUE AND BUILDS TRUST Protecting Identities. Enhancing Reputations. IDT911 1 DATA BREACHES AND SUBSEQUENT IDENTITY THEFT AND FRAUD THREATEN YOUR ORGANIZATION
KEEPING CLIENT AND EMPLOYEE DATA SECURE DRIVES REVENUE AND BUILDS TRUST Protecting Identities. Enhancing Reputations. IDT911 1 DATA BREACHES AND SUBSEQUENT IDENTITY THEFT AND FRAUD THREATEN YOUR ORGANIZATION
BEHIND OUR DIGITAL DOORS: CYBERSECURITY & THE CONNECTED HOME. Executive Summary
 BEHIND OUR DIGITAL DOORS: CYBERSECURITY & THE CONNECTED HOME Executive Summary In support of National Cyber Security Awareness Month (October), ESET and the National Cyber Security Alliance (NCSA) commissioned
BEHIND OUR DIGITAL DOORS: CYBERSECURITY & THE CONNECTED HOME Executive Summary In support of National Cyber Security Awareness Month (October), ESET and the National Cyber Security Alliance (NCSA) commissioned
DATA BREACHES: HOW IT IMPACTS THE CUSTOMER & THE FINANCIAL INSTITUTION. Prepared For: First Citizens Federal Credit Union 3/18/2015
 DATA BREACHES: HOW IT IMPACTS THE CUSTOMER & THE FINANCIAL INSTITUTION. Prepared For: First Citizens Federal Credit Union TABLE OF CONTENTS Data Breach Trends Financial Institutions Impact How First Citizens
DATA BREACHES: HOW IT IMPACTS THE CUSTOMER & THE FINANCIAL INSTITUTION. Prepared For: First Citizens Federal Credit Union TABLE OF CONTENTS Data Breach Trends Financial Institutions Impact How First Citizens
Transcription. Founder Interview - Panayotis Vryonis Talks About BigStash Cloud Storage. Media Duration: 28:45
 Transcription Founder Interview - Panayotis Vryonis Talks About BigStash Cloud Storage Media Duration: 28:45 Feel free to quote any passage from this interview for your articles. Please reference cloudwards.net
Transcription Founder Interview - Panayotis Vryonis Talks About BigStash Cloud Storage Media Duration: 28:45 Feel free to quote any passage from this interview for your articles. Please reference cloudwards.net
Google Lead Generation For Attorneys - Leverage The Power Of Adwords To Grow Your Law Business FAST. The Foundation of Google AdWords
 Google Lead Generation For Attorneys - Leverage The Power Of Adwords To Grow Your Law Business FAST You re about to discover the secrets of fast legal practice success with Google AdWords. Google AdWords
Google Lead Generation For Attorneys - Leverage The Power Of Adwords To Grow Your Law Business FAST You re about to discover the secrets of fast legal practice success with Google AdWords. Google AdWords
Google Lead Generation for Attorneys
 1 Google Lead Generation For Attorneys Leverage The Power Of AdWords To Grow Your Law Business FAST You re about to discover the secrets of fast legal practice success with Google AdWords. Google AdWords
1 Google Lead Generation For Attorneys Leverage The Power Of AdWords To Grow Your Law Business FAST You re about to discover the secrets of fast legal practice success with Google AdWords. Google AdWords
Your Customers Want Secure Access
 FIVE REASONS WHY Cybersecurity IS VITAL to Your retail Businesses Your Customers Want Secure Access Customer loyalty is paramount to the success of your retail business. How loyal will those customers
FIVE REASONS WHY Cybersecurity IS VITAL to Your retail Businesses Your Customers Want Secure Access Customer loyalty is paramount to the success of your retail business. How loyal will those customers
US House Energy and Commerce Committee. Commerce, Manufacturing, and Trade Subcommittee
 US House Energy and Commerce Committee Commerce, Manufacturing, and Trade Subcommittee Protecting Consumer Information: Can Data Braches Be Prevented? February 5, 2014 Congressmen in Attendance: Rep. Lee
US House Energy and Commerce Committee Commerce, Manufacturing, and Trade Subcommittee Protecting Consumer Information: Can Data Braches Be Prevented? February 5, 2014 Congressmen in Attendance: Rep. Lee
Identity Protection Services
 Identity Protection Services Overview Why are identity protection services being provided? We believe your personal information should stay that way personal. That s why we re taking industry- leading
Identity Protection Services Overview Why are identity protection services being provided? We believe your personal information should stay that way personal. That s why we re taking industry- leading
SCAMS. Action: Throw out the letter and contact Social Security directly by phone at 1-800-441-2555 or visit their website. http://www.ssa.
 SCAMS SOCIAL SECURITY SCAMS You use your Social Security number for your identity, to get a job, and to apply for Medicare and Social Security as you become older. Unfortunately though, there are a lot
SCAMS SOCIAL SECURITY SCAMS You use your Social Security number for your identity, to get a job, and to apply for Medicare and Social Security as you become older. Unfortunately though, there are a lot
Statement of. Carlos Minetti. Discover Financial Services. Before the. Subcommittee on Oversight and Investigations. of the
 Statement of Carlos Minetti Discover Financial Services Before the Subcommittee on Oversight and Investigations of the Committee on Financial Services United States House of Representatives July 21, 2005
Statement of Carlos Minetti Discover Financial Services Before the Subcommittee on Oversight and Investigations of the Committee on Financial Services United States House of Representatives July 21, 2005
Data Security. So many businesses leave their data exposed, That doesn t mean you have to. 2014 Computerbilities, Inc.
 Data Security So many businesses leave their data exposed, That doesn t mean you have to. 2014 Computerbilities, Inc. Table of Contents: 1. Introduction 3 2. Cybersecurity: The loopholes in the system
Data Security So many businesses leave their data exposed, That doesn t mean you have to. 2014 Computerbilities, Inc. Table of Contents: 1. Introduction 3 2. Cybersecurity: The loopholes in the system
Dissecting the Recent Cyber Security Breaches. Yu Cai School of Technology Michigan Technological University
 Dissecting the Recent Cyber Security Breaches Yu Cai School of Technology Michigan Technological University Disclaimers Most information in this presentation was collected from various sources on the Internet.
Dissecting the Recent Cyber Security Breaches Yu Cai School of Technology Michigan Technological University Disclaimers Most information in this presentation was collected from various sources on the Internet.
THE FIVE Ws OF EMV BY DAVE EWALD GLOBAL EMV CONSULTANT AND MANAGER DATACARD GROUP
 THE FIVE Ws OF EMV BY DAVE EWALD GLOBAL EMV CONSULTANT AND MANAGER DATACARD GROUP WHERE IS THE U.S. PAYMENT CARD INDUSTRY NOW? WHERE IS IT GOING? Today, payment and identification cards of all types (credit
THE FIVE Ws OF EMV BY DAVE EWALD GLOBAL EMV CONSULTANT AND MANAGER DATACARD GROUP WHERE IS THE U.S. PAYMENT CARD INDUSTRY NOW? WHERE IS IT GOING? Today, payment and identification cards of all types (credit
THE SEO MANIFESTO One Method To Outrank Them All. Proven To Work With
 THE SEO MANIFESTO One Method To Outrank Them All Proven To Work With Are You At The Top Of Google When Your Clients Look For You? The fact is, your clients are on Google looking for your products and services
THE SEO MANIFESTO One Method To Outrank Them All Proven To Work With Are You At The Top Of Google When Your Clients Look For You? The fact is, your clients are on Google looking for your products and services
Basic Techniques to prevent Identity Theft and Cybercrime
 E-Guide Basic Techniques to prevent Identity Theft and Cybercrime When it comes to cybercrime, identity theft techniques often vary from the technical -- computer forensics -- to the old-school -- calling
E-Guide Basic Techniques to prevent Identity Theft and Cybercrime When it comes to cybercrime, identity theft techniques often vary from the technical -- computer forensics -- to the old-school -- calling
Figure 1: Attacker home-made terminal can read some data from your payment card in your pocket
 A Touchy Subject There are increasingly frequent claims that contactless smart payment cards are insecure because they can be read while in your wallet or pocket. Can this really be true? And if so, is
A Touchy Subject There are increasingly frequent claims that contactless smart payment cards are insecure because they can be read while in your wallet or pocket. Can this really be true? And if so, is
The Home Depot Provides Update on Breach Investigation
 The Home Depot Provides Update on Breach Investigation Breach confirmed Investigation focused on April forward No evidence of debit PIN numbers compromised No customers liable for fraudulent charges Customers
The Home Depot Provides Update on Breach Investigation Breach confirmed Investigation focused on April forward No evidence of debit PIN numbers compromised No customers liable for fraudulent charges Customers
How to Choose the Right Credit Card Processing Terminal
 How to Choose the Right Credit Card Processing Terminal How to Choose the Right Credit Card Processing Terminal Credit cards are an integral part of modern business. Even customers who don't use credit
How to Choose the Right Credit Card Processing Terminal How to Choose the Right Credit Card Processing Terminal Credit cards are an integral part of modern business. Even customers who don't use credit
How To Protect Your Restaurant From A Data Security Breach
 NAVIGATING THE PAYMENTS AND SECURITY LANDSCAPE Payment disruptions impacting restaurant owners today An NCR Hospitality white paper Almost every month we hear a news story about another data breach that
NAVIGATING THE PAYMENTS AND SECURITY LANDSCAPE Payment disruptions impacting restaurant owners today An NCR Hospitality white paper Almost every month we hear a news story about another data breach that
State of the Cyber Insurance Market
 State of the Cyber Insurance Market Ten Lessons Learned From Major Retailer Breaches August 2014 Lockton Companies There has been extensive adverse publicity surrounding what has become EMILY FREEMAN Lockton
State of the Cyber Insurance Market Ten Lessons Learned From Major Retailer Breaches August 2014 Lockton Companies There has been extensive adverse publicity surrounding what has become EMILY FREEMAN Lockton
Malware, Phishing, and Cybercrime Dangerous Threats Facing the SMB State of Cybercrime
 How to Protect Your Business from Malware, Phishing, and Cybercrime The SMB Security Series Malware, Phishing, and Cybercrime Dangerous Threats Facing the SMB State of Cybercrime sponsored by Introduction
How to Protect Your Business from Malware, Phishing, and Cybercrime The SMB Security Series Malware, Phishing, and Cybercrime Dangerous Threats Facing the SMB State of Cybercrime sponsored by Introduction
Surviving the Era of Hack Attacks Cyber Security on a Global Scale
 Surviving the Era of Hack Attacks Cyber Security on a Global Scale Dr. Adriana Sanford ASU Lincoln Professor of Global Corporate Compliance and Ethics Clinical Associate Professor of Law and Ethics This
Surviving the Era of Hack Attacks Cyber Security on a Global Scale Dr. Adriana Sanford ASU Lincoln Professor of Global Corporate Compliance and Ethics Clinical Associate Professor of Law and Ethics This
TOP TRUMPS Comparisons of how to pay for goods and services online
 Cash Cash is legal tender in the form of bank notes and coins Small value purchases e.g. cafes, shops Pocket money Repaying friends Cash is physically transferred from one person to the next, usually face-to-face
Cash Cash is legal tender in the form of bank notes and coins Small value purchases e.g. cafes, shops Pocket money Repaying friends Cash is physically transferred from one person to the next, usually face-to-face
EMV and Chip Cards Key Information On What This Is, How It Works and What It Means
 EMV and Chip Cards Key Information On What This Is, How It Works and What It Means Document Purpose This document is intended to provide information about the concepts behind and the processes involved
EMV and Chip Cards Key Information On What This Is, How It Works and What It Means Document Purpose This document is intended to provide information about the concepts behind and the processes involved
Cyber Attacks and Liabilities Why do so many Organizations keep Getting Hacked, Sued and Fined?
 Cyber Attacks and Liabilities Why do so many Organizations keep Getting Hacked, Sued and Fined? PRESENTED BY RICK SHAW, AWAREITY Webinar Objectives Employees (and third parties) are the weakest links Learn
Cyber Attacks and Liabilities Why do so many Organizations keep Getting Hacked, Sued and Fined? PRESENTED BY RICK SHAW, AWAREITY Webinar Objectives Employees (and third parties) are the weakest links Learn
1 Billion Individual records that were hacked in 2014 3.
 783 Major data breaches in 204 up 27% from 203 2. Billion Individual records that were hacked in 204 3. 3 Fraud has changed The way we live and manage our finances today has changed radically from just
783 Major data breaches in 204 up 27% from 203 2. Billion Individual records that were hacked in 204 3. 3 Fraud has changed The way we live and manage our finances today has changed radically from just
DATA BREACHES: WHEN COMPLIANCE IS NOT ENOUGH
 DATA BREACHES: WHEN COMPLIANCE IS NOT ENOUGH Andy Watson Grant Thornton LLP. All rights reserved. CYBERSECURITY 2 SURVEY OF CHIEF AUDIT EXECUTIVES (CAEs) GRANT THORNTON'S 2014 CAE SURVEY Data privacy and
DATA BREACHES: WHEN COMPLIANCE IS NOT ENOUGH Andy Watson Grant Thornton LLP. All rights reserved. CYBERSECURITY 2 SURVEY OF CHIEF AUDIT EXECUTIVES (CAEs) GRANT THORNTON'S 2014 CAE SURVEY Data privacy and
AIS Webinar. Payment Application Security. Hap Huynh Business Leader Visa Inc. 1 April 2009
 AIS Webinar Payment Application Security Hap Huynh Business Leader Visa Inc. 1 April 2009 1 Agenda Security Environment Payment Application Security Overview Questions and Comments Payment Application
AIS Webinar Payment Application Security Hap Huynh Business Leader Visa Inc. 1 April 2009 1 Agenda Security Environment Payment Application Security Overview Questions and Comments Payment Application
Identity Theft. Goals. Technology Seminar December 8, 2015 Page
 Identity Theft Scott A. Turk Assistant State s Attorney Cyber/White-Collar Crime Division Goals Learn how to protect yourself from Identity Theft Learn how to protect your practice from Identity Theft
Identity Theft Scott A. Turk Assistant State s Attorney Cyber/White-Collar Crime Division Goals Learn how to protect yourself from Identity Theft Learn how to protect your practice from Identity Theft
Your Single Source. for credit, debit and pre-paid services. Fraud Risk and Mitigation
 Your Single Source for credit, debit and pre-paid services Fraud Risk and Mitigation Agenda Types of Fraud Fraud Identification Notifications Next Steps 11/8/2013 2 Types of Fraud Lost and Stolen Cards
Your Single Source for credit, debit and pre-paid services Fraud Risk and Mitigation Agenda Types of Fraud Fraud Identification Notifications Next Steps 11/8/2013 2 Types of Fraud Lost and Stolen Cards
Security Questions to Ask EHR Vendors
 Security Questions to Ask EHR Vendors Interview with Eric Nelson, privacy practice leader at the Lyndon Group July 13, 2010 - Howard Anderson, Managing Editor, HealthcareInfoSecurity.com Physician group
Security Questions to Ask EHR Vendors Interview with Eric Nelson, privacy practice leader at the Lyndon Group July 13, 2010 - Howard Anderson, Managing Editor, HealthcareInfoSecurity.com Physician group
STATEMENT OF DELARA DERAKHSHANI CONSUMERS UNION BEFORE THE UNITED STATES SENATE COMMITTEE ON THE JUDICIARY
 STATEMENT OF DELARA DERAKHSHANI CONSUMERS UNION BEFORE THE UNITED STATES SENATE COMMITTEE ON THE JUDICIARY ON PRIVACY IN THE DIGITAL AGE: PREVENTING DATA BREACHES AND COMBATING CYBERCRIME FEBRUARY 4, 2013
STATEMENT OF DELARA DERAKHSHANI CONSUMERS UNION BEFORE THE UNITED STATES SENATE COMMITTEE ON THE JUDICIARY ON PRIVACY IN THE DIGITAL AGE: PREVENTING DATA BREACHES AND COMBATING CYBERCRIME FEBRUARY 4, 2013
Ethical Hacking Introduction
 Ethical Hacking Introduction Table of Contents What Is "Ethical Hacking"?... 2 Why Perform "Ethical Hacking"?... 6 The Certified Ethical Hacker (CEH)... 9 Information Security Reports... 10 Internet Crime
Ethical Hacking Introduction Table of Contents What Is "Ethical Hacking"?... 2 Why Perform "Ethical Hacking"?... 6 The Certified Ethical Hacker (CEH)... 9 Information Security Reports... 10 Internet Crime
WILLIS SPECIAL REPORT: 10K DISCLOSURES HOW RETAIL COMPANIES DESCRIBE THEIR CYBER LIABILITY EXPOSURES
 WILLIS SPECIAL REPORT: 10K DISCLOSURES HOW RETAIL COMPANIES DESCRIBE THEIR CYBER LIABILITY EXPOSURES This special report examines the cyber risk disclosures made by the retail sector of the Fortune 1000.
WILLIS SPECIAL REPORT: 10K DISCLOSURES HOW RETAIL COMPANIES DESCRIBE THEIR CYBER LIABILITY EXPOSURES This special report examines the cyber risk disclosures made by the retail sector of the Fortune 1000.
Cyber Crime: You Are the Target
 Cyber Crime: You Are the Target When talking about computer crime, we often hear the observation from computer users that they aren t rich and therefore what they have isn t worth much to a cyber criminal.
Cyber Crime: You Are the Target When talking about computer crime, we often hear the observation from computer users that they aren t rich and therefore what they have isn t worth much to a cyber criminal.
Wholesaling Mark Ferguson
 TRANSCRIPT OF EPISODE 14 OF THE INVEST FOUR MORE PODCAST Wholesaling Mark Ferguson Mark: Hi everyone. Mark Ferguson here with another episode of the Invest More Real Estate podcast. Today is just going
TRANSCRIPT OF EPISODE 14 OF THE INVEST FOUR MORE PODCAST Wholesaling Mark Ferguson Mark: Hi everyone. Mark Ferguson here with another episode of the Invest More Real Estate podcast. Today is just going
Will Dormann: Sure. Fuzz testing is a way of testing an application in a way that you want to actually break the program.
 The Power of Fuzz Testing to Reduce Security Vulnerabilities Transcript Part 1: Why Fuzz Testing? Julia Allen: Welcome to CERT's podcast series: Security for Business Leaders. The CERT program is part
The Power of Fuzz Testing to Reduce Security Vulnerabilities Transcript Part 1: Why Fuzz Testing? Julia Allen: Welcome to CERT's podcast series: Security for Business Leaders. The CERT program is part
BinBase.com REPORT: credit card fraud
 BinBase.com REPORT: credit card fraud Whether you are a security specialist, an e-commerce web developer, or an online merchant, a knowledge of how credit card fraud works and what you can do to prevent
BinBase.com REPORT: credit card fraud Whether you are a security specialist, an e-commerce web developer, or an online merchant, a knowledge of how credit card fraud works and what you can do to prevent
FINAL // FOR OFFICIAL USE ONLY. William Noonan
 FINAL // FOR OFFICIAL USE ONLY William Noonan Deputy Special Agent in Charge United States Secret Service Criminal Investigative Division Cyber Operations Branch Prepared Testimony Before the United States
FINAL // FOR OFFICIAL USE ONLY William Noonan Deputy Special Agent in Charge United States Secret Service Criminal Investigative Division Cyber Operations Branch Prepared Testimony Before the United States
PROTECTING YOURSELF FROM IDENTITY THEFT. The Office of the Attorney General of Maryland Identity Theft Unit
 PROTECTING YOURSELF FROM IDENTITY THEFT The Office of the Attorney General of Maryland Identity Theft Unit CONTENTS 1) What is Identity Theft? 2) How to Protect Yourself From ID Theft. 3) How to Tell If
PROTECTING YOURSELF FROM IDENTITY THEFT The Office of the Attorney General of Maryland Identity Theft Unit CONTENTS 1) What is Identity Theft? 2) How to Protect Yourself From ID Theft. 3) How to Tell If
Network Security & Privacy Landscape
 Network Security & Privacy Landscape Presented By: Greg Garijanian Senior Underwriter Professional Liability 1 Agenda Network Security Overview -Latest Threats - Exposure Trends - Regulations Case Studies
Network Security & Privacy Landscape Presented By: Greg Garijanian Senior Underwriter Professional Liability 1 Agenda Network Security Overview -Latest Threats - Exposure Trends - Regulations Case Studies
To all GRSB debit and credit card customers:
 To all GRSB debit and credit card customers: A data breach at the Target Corporation may have exposed 40 million credit/debit cards to potential fraudulent activity. If you made purchases in a Target store
To all GRSB debit and credit card customers: A data breach at the Target Corporation may have exposed 40 million credit/debit cards to potential fraudulent activity. If you made purchases in a Target store
INTRODUCTION. Identity Theft Crime Victim Assistance Kit
 Identity Theft Crime Victim Assistance Kit INTRODUCTION In the course of a busy day, you may write a check at the grocery store, charge tickets to a ball game, rent a car, mail your tax returns, change
Identity Theft Crime Victim Assistance Kit INTRODUCTION In the course of a busy day, you may write a check at the grocery store, charge tickets to a ball game, rent a car, mail your tax returns, change
Information Governance Software that allows Organizations to Track, Monitor and Classify Data in Real Time
 ceocfointerviews.com All rights reserved! Issue: September 7, 2015 The Most Powerful Name in Corporate News Information Governance Software that allows Organizations to Track, Monitor and Classify Data
ceocfointerviews.com All rights reserved! Issue: September 7, 2015 The Most Powerful Name in Corporate News Information Governance Software that allows Organizations to Track, Monitor and Classify Data
Addressing APTs and Modern Malware with Security Intelligence Date: September 2013 Author: Jon Oltsik, Senior Principal Analyst
 ESG Brief Addressing APTs and Modern Malware with Security Intelligence Date: September 2013 Author: Jon Oltsik, Senior Principal Analyst Abstract: APTs first came on the scene in 2010, creating a wave
ESG Brief Addressing APTs and Modern Malware with Security Intelligence Date: September 2013 Author: Jon Oltsik, Senior Principal Analyst Abstract: APTs first came on the scene in 2010, creating a wave
TMCEC CYBER SECURITY TRAINING
 1 TMCEC CYBER SECURITY TRAINING Agenda What is cyber-security? Why is cyber-security important? The essential role you play. Overview cyber security threats. Best practices in dealing with those threats.
1 TMCEC CYBER SECURITY TRAINING Agenda What is cyber-security? Why is cyber-security important? The essential role you play. Overview cyber security threats. Best practices in dealing with those threats.
Data Security for the Hospitality
 M&T Bank and SecurityMetrics Present: Data Security for the Hospitality Industry Featuring Lee Pierce, SecurityMetricsStrategicStrategic Accounts Dave Ellis, SecurityMetrics Forensic Investigator Doug
M&T Bank and SecurityMetrics Present: Data Security for the Hospitality Industry Featuring Lee Pierce, SecurityMetricsStrategicStrategic Accounts Dave Ellis, SecurityMetrics Forensic Investigator Doug
The Hotel Hijackers. The Hotel Hijackers 1
 The Hotel Hijackers The Hotel Hijackers 1 The Hotel Hijackers Why hotels? After all these years we ve been in the computer security business, there is one thing we know for sure: a cyber-criminal s main
The Hotel Hijackers The Hotel Hijackers 1 The Hotel Hijackers Why hotels? After all these years we ve been in the computer security business, there is one thing we know for sure: a cyber-criminal s main
7 Secrets To Websites That Sell. By Alex Nelson
 7 Secrets To Websites That Sell By Alex Nelson Website Secret #1 Create a Direct Response Website Did you know there are two different types of websites? It s true. There are branding websites and there
7 Secrets To Websites That Sell By Alex Nelson Website Secret #1 Create a Direct Response Website Did you know there are two different types of websites? It s true. There are branding websites and there
Real Estate Investing Podcast Episode # 74 The ABCs of Finding and Training a Virtual Assistant Hosted by: Joe McCall and Alex Joungblood
 Real Estate Investing Podcast Episode # 74 The ABCs of Finding and Training a Virtual Assistant Hosted by: Joe McCall and Alex Joungblood Jesse: Hey, welcome back. This is Real Estate Investing Mastery.
Real Estate Investing Podcast Episode # 74 The ABCs of Finding and Training a Virtual Assistant Hosted by: Joe McCall and Alex Joungblood Jesse: Hey, welcome back. This is Real Estate Investing Mastery.
Information Protection
 Information Protection Security is Priority One InfoArmor solutions are created to be SSAE 16, ISO 27001 and DISA STIG compliant, requiring adherence to rigorous data storage practices. We not only passed
Information Protection Security is Priority One InfoArmor solutions are created to be SSAE 16, ISO 27001 and DISA STIG compliant, requiring adherence to rigorous data storage practices. We not only passed
Coping with Identity Theft
 Anthony L. Soave, CLU, ChFC Chartered Financial Consultant 601 Three Mile NW, Suite B Grand Rapids, MI 49544 616-647-7000 888-467-0560 tony.soave@raymondjames.com www.raymondjames.com/soave Coping with
Anthony L. Soave, CLU, ChFC Chartered Financial Consultant 601 Three Mile NW, Suite B Grand Rapids, MI 49544 616-647-7000 888-467-0560 tony.soave@raymondjames.com www.raymondjames.com/soave Coping with
State of Black Market for Stolen Credit Cards (2015) by N. Vlajic
 State of Black Market for Stolen Credit Cards (2015) by N. Vlajic http://www.informationisbeautiful.net/visualizations/worlds-biggest-data-breaches-hacks/ Worst Security Hacks of the Last Decade http://www.bloomberg.com/graphics/2014-data-breaches/
State of Black Market for Stolen Credit Cards (2015) by N. Vlajic http://www.informationisbeautiful.net/visualizations/worlds-biggest-data-breaches-hacks/ Worst Security Hacks of the Last Decade http://www.bloomberg.com/graphics/2014-data-breaches/
NORTON CYBERSECURITY INSIGHTS REPORT
 NORTON CYBERSECURITY INSIGHTS REPORT Get informed about the truths of online crime and the personal impact it has on you Table of Contents > INTRODUCTION... 3 > WE KNOW THE RISK FOR ONLINE CRIME IS HIGH...
NORTON CYBERSECURITY INSIGHTS REPORT Get informed about the truths of online crime and the personal impact it has on you Table of Contents > INTRODUCTION... 3 > WE KNOW THE RISK FOR ONLINE CRIME IS HIGH...
CYBERSECURITY IN HEALTHCARE: A TIME TO ACT
 share: TM CYBERSECURITY IN HEALTHCARE: A TIME TO ACT Why healthcare is especially vulnerable to cyberattacks, and how it can protect data and mitigate risk At a time of well-publicized incidents of cybersecurity
share: TM CYBERSECURITY IN HEALTHCARE: A TIME TO ACT Why healthcare is especially vulnerable to cyberattacks, and how it can protect data and mitigate risk At a time of well-publicized incidents of cybersecurity
Transitions in Payments: PCI Compliance, EMV & True Transactions Security
 Transitions in Payments: PCI Compliance, EMV & True Transactions Security There have been more than 600 million records compromised from approximately 4,000 data breaches since 2005 and those are just
Transitions in Payments: PCI Compliance, EMV & True Transactions Security There have been more than 600 million records compromised from approximately 4,000 data breaches since 2005 and those are just
Identity Theft Protection Plans
 Identity Theft Protection Plans Legal Resources has partnered with IdentityForce to offer two plan options for identity theft protection for employees at the City of Virginia Beach and Virginia Beach City
Identity Theft Protection Plans Legal Resources has partnered with IdentityForce to offer two plan options for identity theft protection for employees at the City of Virginia Beach and Virginia Beach City
10 Smart Ideas for. Keeping Data Safe. From Hackers
 0100101001001010010001010010101001010101001000000100101001010101010010101010010100 0100101001001010010001010010101001010101001000000100101001010101010010101010010100000 0100101001001010010001010010101001010101001000000100101001010101010010101010010100000
0100101001001010010001010010101001010101001000000100101001010101010010101010010100 0100101001001010010001010010101001010101001000000100101001010101010010101010010100000 0100101001001010010001010010101001010101001000000100101001010101010010101010010100000
