Shadow Planner Users Group Meeting 2/23/12
|
|
|
- Rodger Glenn
- 8 years ago
- Views:
Transcription
1 Updates Michael McLaughlin from Information Systems and Computing s Technology Support Services (TSS) department spoke about how TSS can help University wide departments with loss of technology. The text of his presentation is attached at the end of this document, but here are some highlights. The Provider Desk, or ProDesk, in available to help Local Support Providers (LSPs) Monday through Friday during regular business hours, 9 am to 5 pm. After business hours, an LSP can call the ProDesk number and will be have the option to be transferred to someone who is on call for emergencies. Queries to the ProDesk are either answered by a ProDesk team member or distributed to someone else in ISC. ProDesk team members then manage the query to make sure it is answered in a timely fashion. Most are resolved within 1 2 days. In an emergency or Mission Continuity situation, the primary role of the Provider Desk will be to relay information, and you should have detailed mission continuity plans to cover for loss of technology that don t rely on ProDesk assistance. However, the ProDesk does have considerable resources to help plan for an emergency. To prevent loss of information, TSS offers a Secure Remote Backup service. TSS is also the parent organization of ISC Support On Site (SOS). Schools and Centers can engage these technology specialists either on an ongoing basis (if you prefer not to hire your own LSP for any reason) or as back ups in an emergency. In the latter situation, it s best to establish a relationship with SOS now rather than wait for the emergency to happen. TSS also provides security consulting, including Platinum level support for Symantec anti virus software. Reminders Getting help In person meetings: Janet Plantan and Anita Gelburd, of the Mission Continuity Program team, are happy to meet with staff members from your unit to talk about how best to construct Mission Continuity plans and enter them into Shadow Planner. Just e mail Anita at gelburda@isc.upenn.edu to set up a convenient time. Questions: Any questions about Mission Continuity planning or using Shadow Planner can be directed to askmc@lists.upenn.edu. Mission Continuity website: Remember that the Mission Continuity website ( has many useful tools, both for organizations that are constructing plans and those who have already constructed them and loaded them in Shadow Planner. Here are some highlights: Page 1 of 5
2 o The Pre Planning Questionnaire: use this tool to gather information before constructing a plan. You can use it to conduct interviews, or fill one or more questionnaires out for each department that needs a plan. o A plan template: use this to help construct Mission Continuity plans in Excel. You can make trial scenarios and changes in the spreadsheet, so that plans are in good condition when they are loaded into Shadow Planner. o A Lessons Learned/Best Practices report template: after your organization experiences an outage or incident you may want to debrief to think about what worked well and what worked not so well and whether you want to make any changes in your plan. The website contains a template for such a process. This is not required; it s just there as a tool if you d like to use it. o User group meeting notes: In case you miss one of the monthly user group meetings, or you d like to review what was discussed, notes from each monthly meeting are posted on the website. Using Shadow Planner Usernames for Shadow Planner: Your username to enter Shadow Planner is your full e mail address, not your PennKey username. If for any reason you are locked out of the system, send a message to askmc@lists.upenn.edu and we will help you sort out the problem. Recommended browser: The recommended browser for using Shadow Planner is Internet Explorer, version 5.5, 6 or 7. In the new version, which is expected to be released sometime this winter, other browsers are supported. Accessing the back up version of Shadow Planner: In case Shadow Planner is not available for some reason, you can always access a back up version at It is recommended that you bookmark this address as well as the URL for the main Shadow Planner site: Keeping Directory information updated: Remember that information in Shadow Planner is only as current as information in the Penn Directory, since Shadow Planner is updated from the Directory. Please remind everyone in your office to update their information in the Directory regularly. Go to: click on Update Directory Listings. Make sure to update the Penn Profile, Public Profile and UPenn Alert information, so all necessary data will appear in Shadow Planner. For people who have concerns about privacy, remind them that very few people have access to Shadow Planner, so private information is not being widely distributed. The next user group meeting will take place on 3/29/12 at noon, in the Meyerson Room of the Van Pelt Library (2 nd floor). Our guest presenter will be Mark Mills from Purchasing, to talk about loss of third party plans. Page 2 of 5
3 Presentation by: Michael McLaughlin, Information Systems and Computing s Technology Support Services (TSS) What is TSS? The branch of Information Systems and Computing that provides central IT support, guidance, and services to the University We are a client facing side of ISC focused on users and LSPs at the University The Pieces of TSS Client Services Group (CSG, aka ProDesk) LAN Technology Services (LTS) Support on Site Services (SOS) Technology Training Services (TTS) Classroom Technology Services (CTS) TSS and Mission Continuity Can TSS help in MC? Building No Equipment No Technology YES Human Resources YES 3 rd Party Partners In some cases The Provider Desk Second tier support o Exclusively for Local Support Providers o Staffed by senior level analysts with a broad range of experience o Close contact with ISC service owners When you contact the ProDesk Staff on call 9 5, M F Your call, , or web ticket enters a queue and is responded to in order of receipt Either your question will be immediately resolved or A Remedy ticket will be opened in your name Depending on the issue, the ticket will be held in the ProDesk queue or routed to the appropriate ISC group Page 3 of 5
4 ProDesk and Mission Continuity Network and network service related issues o ACD/Interactive Intelligence issues o Network performance and connectivity issues AirPennNet PennNet PennNet Phone ISC service issues o ISC Exchange and Zimbra services o WWW and Penn WebLogin o PennGroups o Listservs and Forward Only service Other ProDesk Functions Network administration requests o DNS records, IP space, third level domains Supported product questions and issues o Configuration and compatibility o 2 nd and 3 rd tier OS and software questions PennKey data issues Other ISC referrals Vendor referrals and escalations Preventative TSS Services Provider Web o Provider Notes Wiki o csg.upenn.edu Provider Tools o Provides best practices and other information for LSP oriented software like PGP Whole Disk Encryption, Ghost, etc. o Antivirus response and support o Platinum support with Symantec o Constant monitoring of virus, phishing, and worm threat levels o Distribution of the full suite of Symantec AV products virus@isc.upenn.edu Page 4 of 5
5 ISC LAN Technology Services LAN and server consulting services Expertise in firewalls, PGP, Active Directory, VMWare products, and more Secure Remote Backup Service o Encrypted, user configurable, iterative desktop backup o Encrypted data stored on servers at Penn o Accessible from other computers in case of emergency ISC Support on Site Services Support and technical consulting group Provides end user support, desktop and software support and management, web and database consulting, and other user services Supplemental staffing for large projects and staff shortages Feel free to contact with questions: Michael McLaughlin ISC TSS Client Services Group mvm@isc.upenn.edu Page 5 of 5
InsightCloud. www.insightcloud.com. Hosted Desktop Service. What is InsightCloud? What is SaaS? What are the benefits of SaaS?
 What is InsightCloud? InsightCloud is a web portal enabling Insight customers to purchase and provision a wide range of Cloud services in a straightforward and convenient manner. What is SaaS? Software
What is InsightCloud? InsightCloud is a web portal enabling Insight customers to purchase and provision a wide range of Cloud services in a straightforward and convenient manner. What is SaaS? Software
Monthly Fee Per Server 75/month 295/month 395/month Monthly Fee Per Desktop/Notebook/ 15/month 45/month 55/month
 SERVICE COVERAGE AND FEE SCHEDULE Base Package Fees Monthly Fee Per Server 75/month 295/month 395/month Monthly Fee Per Desktop/Notebook/ 15/month 45/month 55/month Live Desk Services Live Desk Telephone
SERVICE COVERAGE AND FEE SCHEDULE Base Package Fees Monthly Fee Per Server 75/month 295/month 395/month Monthly Fee Per Desktop/Notebook/ 15/month 45/month 55/month Live Desk Services Live Desk Telephone
IT@DUSON. IT Service Desk
 IT@DUSON Technology plays a key role in the learning process for nursing students at Duke. This is your guide to the technology used at the Duke School of Nursing and how to request assistance for all
IT@DUSON Technology plays a key role in the learning process for nursing students at Duke. This is your guide to the technology used at the Duke School of Nursing and how to request assistance for all
How To Manage Your Information Systems At Aerosoft.Com
 Your information systems are at the heart of your businesses daily operation. System down time costs businesses a significant amount of money each year. Most problems that cause down time can be prevented
Your information systems are at the heart of your businesses daily operation. System down time costs businesses a significant amount of money each year. Most problems that cause down time can be prevented
Service Level Agreement
 This document outlines the Service Level Agreement (SLA) between University Technology Services (UTS) and our Customers for the delivery of. The purpose of this agreement is threefold: 1. To clearly represent
This document outlines the Service Level Agreement (SLA) between University Technology Services (UTS) and our Customers for the delivery of. The purpose of this agreement is threefold: 1. To clearly represent
Guidelines for conducting tabletop exercises Penn Mission Continuity Program (MCP)
 All Penn organizations are advised to conduct annual tabletop exercises (TTX) to test their Mission Continuity plans. Here are some ideas to help you do that. Our thanks to the School of Arts and Sciences
All Penn organizations are advised to conduct annual tabletop exercises (TTX) to test their Mission Continuity plans. Here are some ideas to help you do that. Our thanks to the School of Arts and Sciences
SECURITY BEST PRACTICES FOR CISCO PERSONAL ASSISTANT (1.4X)
 WHITE PAPER SECURITY BEST PRACTICES FOR CISCO PERSONAL ASSISTANT (1.4X) INTRODUCTION This document covers the recommended best practices for hardening a Cisco Personal Assistant 1.4(x) server. The term
WHITE PAPER SECURITY BEST PRACTICES FOR CISCO PERSONAL ASSISTANT (1.4X) INTRODUCTION This document covers the recommended best practices for hardening a Cisco Personal Assistant 1.4(x) server. The term
System Management. What are my options for deploying System Management on remote computers?
 Getting Started, page 1 Managing Assets, page 2 Distributing Software, page 3 Distributing Patches, page 4 Backing Up Assets, page 5 Using Virus Protection, page 6 Security, page 7 Getting Started What
Getting Started, page 1 Managing Assets, page 2 Distributing Software, page 3 Distributing Patches, page 4 Backing Up Assets, page 5 Using Virus Protection, page 6 Security, page 7 Getting Started What
G-Cloud Managed Exchange SaaS. Service Description
 G-Cloud Managed Exchange SaaS Service Description Version No: 5.0g Date: 08/04/2014 Table of Contents FEATURES... 3 OPTIONAL FEATURES... 4 BENEFITS... 4 CONNECTED SERVICES... 4 SERVICE REQUIREMENTS...
G-Cloud Managed Exchange SaaS Service Description Version No: 5.0g Date: 08/04/2014 Table of Contents FEATURES... 3 OPTIONAL FEATURES... 4 BENEFITS... 4 CONNECTED SERVICES... 4 SERVICE REQUIREMENTS...
Service Support. First Level Support (Tier I) provides immediate response to emergencies and customer questions. TSD - First Level Support
 Service Support 1.1. First Level Support First Level Support (Tier I) provides immediate response to emergencies and customer questions TSD - First Level Support Office: Sub-Division: Extension: E-mail:
Service Support 1.1. First Level Support First Level Support (Tier I) provides immediate response to emergencies and customer questions TSD - First Level Support Office: Sub-Division: Extension: E-mail:
Get what s right for your business. Contact @lliance Technologies.
 Provisioning Looking for new technology? You need systems in line with your business goals. You also need those systems to interact seamlessly. We can help you get the right technology to the right place
Provisioning Looking for new technology? You need systems in line with your business goals. You also need those systems to interact seamlessly. We can help you get the right technology to the right place
University Systems Desktop Support Service Level Commitment
 University Systems Desktop Support Service Level Commitment The Purpose of this Service Level Commitment (SLC) is to formally define the level of service University Systems will provide to UVic faculty,
University Systems Desktop Support Service Level Commitment The Purpose of this Service Level Commitment (SLC) is to formally define the level of service University Systems will provide to UVic faculty,
Exhibit B5b South Dakota. Vendor Questions COTS Software Set
 Appendix C Vendor Questions Anything t Applicable should be marked NA. Vendor Questions COTS Software Set Infrastructure 1. Typically the State of South Dakota prefers to host all systems. In the event
Appendix C Vendor Questions Anything t Applicable should be marked NA. Vendor Questions COTS Software Set Infrastructure 1. Typically the State of South Dakota prefers to host all systems. In the event
Workflow Templates Library
 Workflow s Library Table of Contents Intro... 2 Active Directory... 3 Application... 5 Cisco... 7 Database... 8 Excel Automation... 9 Files and Folders... 10 FTP Tasks... 13 Incident Management... 14 Security
Workflow s Library Table of Contents Intro... 2 Active Directory... 3 Application... 5 Cisco... 7 Database... 8 Excel Automation... 9 Files and Folders... 10 FTP Tasks... 13 Incident Management... 14 Security
INSTALLATION AND CONFIGURATION GUIDE (THIS DOCUMENT RELATES TO MDAEMON v15.5.0 ONWARDS)
 Web: Overview INSTALLATION AND CONFIGURATION GUIDE (THIS DOCUMENT RELATES TO MDAEMON v15.5.0 ONWARDS) This document provides an installation and configuration guide for MDaemon Messaging Server along with
Web: Overview INSTALLATION AND CONFIGURATION GUIDE (THIS DOCUMENT RELATES TO MDAEMON v15.5.0 ONWARDS) This document provides an installation and configuration guide for MDaemon Messaging Server along with
General Service Level Agreement
 General Service Level Agreement Pricing We offer an unlimited Break / Fix for each device. Cost is below. Server Management = $199 / month per server Network Management = $199 / month per company Desktop
General Service Level Agreement Pricing We offer an unlimited Break / Fix for each device. Cost is below. Server Management = $199 / month per server Network Management = $199 / month per company Desktop
Security Policy JUNE 1, 2012. SalesNOW. Security Policy v.1.4 2012-06-01. v.1.4 2012-06-01 1
 JUNE 1, 2012 SalesNOW Security Policy v.1.4 2012-06-01 v.1.4 2012-06-01 1 Overview Interchange Solutions Inc. (Interchange) is the proud maker of SalesNOW. Interchange understands that your trust in us
JUNE 1, 2012 SalesNOW Security Policy v.1.4 2012-06-01 v.1.4 2012-06-01 1 Overview Interchange Solutions Inc. (Interchange) is the proud maker of SalesNOW. Interchange understands that your trust in us
Customized Cloud Solution
 Customized Cloud Solution (Overall Cloud Performance Expectations) Last Updated: June 5, 2012 Prepared by: Polleo Systems, Inc. Notice of Confidentiality: The enclosed material is proprietary to Polleo
Customized Cloud Solution (Overall Cloud Performance Expectations) Last Updated: June 5, 2012 Prepared by: Polleo Systems, Inc. Notice of Confidentiality: The enclosed material is proprietary to Polleo
Network Detective. HIPAA Compliance Module. 2015 RapidFire Tools, Inc. All rights reserved V20150201
 Network Detective 2015 RapidFire Tools, Inc. All rights reserved V20150201 Contents Purpose of this Guide... 3 About Network Detective... 3 Overview... 4 Creating a Site... 5 Starting a HIPAA Assessment...
Network Detective 2015 RapidFire Tools, Inc. All rights reserved V20150201 Contents Purpose of this Guide... 3 About Network Detective... 3 Overview... 4 Creating a Site... 5 Starting a HIPAA Assessment...
Information Technology Solutions
 Managed Services Information Technology Solutions A TBG Security Professional Services Offering LET TBG MANAGE YOUR INFRASTRUCTURE WITH CONFIDENCE: TBG S INTEGRATED IT AUTOMATION FRAMEWORK PROVIDES: Computer
Managed Services Information Technology Solutions A TBG Security Professional Services Offering LET TBG MANAGE YOUR INFRASTRUCTURE WITH CONFIDENCE: TBG S INTEGRATED IT AUTOMATION FRAMEWORK PROVIDES: Computer
Mail Server Scenarios and Configurations
 Mail Server Scenarios and Configurations Scenario 1: Using Wingate as the main Mail Server on your network. Computers on your LAN (Local Area Network) Internet Computers In the example above you would
Mail Server Scenarios and Configurations Scenario 1: Using Wingate as the main Mail Server on your network. Computers on your LAN (Local Area Network) Internet Computers In the example above you would
Lifecycle Solutions & Services. Managed Industrial Cyber Security Services
 Lifecycle Solutions & Services Managed Industrial Cyber Security Services Around the world, industrial firms and critical infrastructure operators partner with Honeywell to address the unique requirements
Lifecycle Solutions & Services Managed Industrial Cyber Security Services Around the world, industrial firms and critical infrastructure operators partner with Honeywell to address the unique requirements
Introduction to ITIL: A Framework for IT Service Management
 Introduction to ITIL: A Framework for IT Service Management D O N N A J A C O B S, M B A I T S E N I O R D I R E C T O R C O M P U T E R O P E R A T I O N S I N F O R M A T I O N S Y S T E M S A N D C
Introduction to ITIL: A Framework for IT Service Management D O N N A J A C O B S, M B A I T S E N I O R D I R E C T O R C O M P U T E R O P E R A T I O N S I N F O R M A T I O N S Y S T E M S A N D C
Information Security
 IT Orientation at Penn Information Security May 8, 2013 Joshua Beeman University Information Security Officer jbeeman@isc.upenn.edu (215) 746-7077 www.upenn.edu/computing/security security@isc.upenn.edu
IT Orientation at Penn Information Security May 8, 2013 Joshua Beeman University Information Security Officer jbeeman@isc.upenn.edu (215) 746-7077 www.upenn.edu/computing/security security@isc.upenn.edu
Navajo Nation Department of Information Technology (NNDIT) Helpdesk Policy P100
 Navajo Nation Department of Information Technology (NNDIT) Helpdesk Policy P100 HelpDesk Problem & Request Management Process The following discussion of Problem Management procedures is intended to provide
Navajo Nation Department of Information Technology (NNDIT) Helpdesk Policy P100 HelpDesk Problem & Request Management Process The following discussion of Problem Management procedures is intended to provide
Guardian Digital Secure Mail Suite Quick Start Guide
 Guardian Digital Secure Mail Suite Quick Start Guide Copyright c 2004 Guardian Digital, Inc. Contents 1 Introduction 1 2 Contacting Guardian Digital 2 3 Purpose of This Document 3 3.1 Terminology...............................
Guardian Digital Secure Mail Suite Quick Start Guide Copyright c 2004 Guardian Digital, Inc. Contents 1 Introduction 1 2 Contacting Guardian Digital 2 3 Purpose of This Document 3 3.1 Terminology...............................
REMOTE INFRASTRUCTURE MANAGEMENT COURSE CURRICULUM
 On a Mission to Transform Talent REMOTE INFRASTRUCTURE MANAGEMENT COURSE CURRICULUM Table of Contents Module 1: Introduction to Hardware and Networking (Duration: 1.5 Weeks)...1 Module 2: Windows XP Professional
On a Mission to Transform Talent REMOTE INFRASTRUCTURE MANAGEMENT COURSE CURRICULUM Table of Contents Module 1: Introduction to Hardware and Networking (Duration: 1.5 Weeks)...1 Module 2: Windows XP Professional
Request for Proposal Technology Services Maintenance and Support
 Request for Proposal Technology Services Maintenance and Support Maintenance and Support July 19, 2014 Celerity Educational Group is seeking an IT consulting firm to manage Maintenance of our Network Systems
Request for Proposal Technology Services Maintenance and Support Maintenance and Support July 19, 2014 Celerity Educational Group is seeking an IT consulting firm to manage Maintenance of our Network Systems
IVAN WINDON - CCENT NETWORK / SYSTEMS ADMINISTRATOR AREAS OF EXPERTISE:
 IVAN WINDON - CCENT 5295 S Netherland Way, Centennial, CO 80015 720.258.6311 c https://www.l3pdu.com ivan.windon@l3pdu.com NETWORK / SYSTEMS ADMINISTRATOR Solutions-focused IT professional driven to advance
IVAN WINDON - CCENT 5295 S Netherland Way, Centennial, CO 80015 720.258.6311 c https://www.l3pdu.com ivan.windon@l3pdu.com NETWORK / SYSTEMS ADMINISTRATOR Solutions-focused IT professional driven to advance
Helpdesk and Technology Support Procedures
 Procedures: Helpdesk and Technology Procedure Date: 10/27/2009 1.0 Purpose The Information Technology Services (ITS) Helpdesk is the single point of contact for technology support for all CCBC students,
Procedures: Helpdesk and Technology Procedure Date: 10/27/2009 1.0 Purpose The Information Technology Services (ITS) Helpdesk is the single point of contact for technology support for all CCBC students,
Commute Trip Reduction (CTR) Electronic Survey. January 2013
 Commute Trip Reduction (CTR) Electronic Survey January 2013 The CTR electronic Survey What is the survey Why survey online How to administer the survey Questions One of two data collection methods for
Commute Trip Reduction (CTR) Electronic Survey January 2013 The CTR electronic Survey What is the survey Why survey online How to administer the survey Questions One of two data collection methods for
University of Pittsburgh Security Assessment Questionnaire (v1.5)
 Technology Help Desk 412 624-HELP [4357] technology.pitt.edu University of Pittsburgh Security Assessment Questionnaire (v1.5) Directions and Instructions for completing this assessment The answers provided
Technology Help Desk 412 624-HELP [4357] technology.pitt.edu University of Pittsburgh Security Assessment Questionnaire (v1.5) Directions and Instructions for completing this assessment The answers provided
Greenway Customer Support SUPPORT POLICIES. To deliver world class client experiences that delight each and every time we interact with our clients.
 Greenway Customer Support SUPPORT POLICIES To deliver world class client experiences that delight each and every time we interact with our clients. INTRODUCTION Customer Support Our Technical Support Center,
Greenway Customer Support SUPPORT POLICIES To deliver world class client experiences that delight each and every time we interact with our clients. INTRODUCTION Customer Support Our Technical Support Center,
SERVICES BRONZE SILVER GOLD PLATINUM. On-Site emergency response time 3 Hours 3 Hours 1-2 Hours 1 Hour or Less
 SERVICE SUMMARY ITonDemand provides four levels of service to choose from to meet our clients range of needs. Plans can also be customized according to more specific environment needs. SERVICES BRONZE
SERVICE SUMMARY ITonDemand provides four levels of service to choose from to meet our clients range of needs. Plans can also be customized according to more specific environment needs. SERVICES BRONZE
Information Technology and Services (IT & S)
 Information Technology and Services (IT & S) Service Level Agreement (SLA) Table of contents Mission... 3 Scope... 3 Help Desk services... 3 Helpdesk Hours of operations / Service Request... 3 Priority
Information Technology and Services (IT & S) Service Level Agreement (SLA) Table of contents Mission... 3 Scope... 3 Help Desk services... 3 Helpdesk Hours of operations / Service Request... 3 Priority
Managed Security Services SLA Document. Response and Resolution Times
 Managed Security Services SLA Document Appendix A Response and Resolution Times The following table shows the targets of response and resolution times for each priority level: Trouble Priority Response
Managed Security Services SLA Document Appendix A Response and Resolution Times The following table shows the targets of response and resolution times for each priority level: Trouble Priority Response
Network Computing Architects Inc. (NCA) Network Operations Center (NOC) Services
 Network Computing Architects Inc. (NCA), provides outsourced IT services by monitoring and managing clients computing assets. Included Services: For all systems covered under NOC Support, the following
Network Computing Architects Inc. (NCA), provides outsourced IT services by monitoring and managing clients computing assets. Included Services: For all systems covered under NOC Support, the following
IT Onsite Service Contract Proposal. For. <<Customer>> Ltd
 IT Onsite Service Contract Proposal For Ltd 1 of 14 I N T R O D U C T I O N This Service Contract for Onsite Deskside PC Support (this Service Contract ) is made effective as of February 5th,
IT Onsite Service Contract Proposal For Ltd 1 of 14 I N T R O D U C T I O N This Service Contract for Onsite Deskside PC Support (this Service Contract ) is made effective as of February 5th,
Statement of Service Enterprise Services - AID Microsoft IIS
 Statement of Service Enterprise Services - AID Microsoft IIS Customer Proprietary Rights The information in this document is confidential to Arrow Managed Services, Inc. and is legally privileged. The
Statement of Service Enterprise Services - AID Microsoft IIS Customer Proprietary Rights The information in this document is confidential to Arrow Managed Services, Inc. and is legally privileged. The
Employee Service Level Agreement
 Employee Service Level Agreement 1.0 Purpose 2.0 Term and Scope of Agreement 3.0 Scope of Service 3.1 Support Environment 3.2 Local Computer Administrative Privileges 4.0 Support Response Levels 4.1 Exceptions
Employee Service Level Agreement 1.0 Purpose 2.0 Term and Scope of Agreement 3.0 Scope of Service 3.1 Support Environment 3.2 Local Computer Administrative Privileges 4.0 Support Response Levels 4.1 Exceptions
Request for Proposals (RFP) Managed Services, Help Desk and Engineering Support for Safer Foundation www.saferfoundation.org
 Request for Proposals (RFP) Managed Services, Help Desk and Engineering Support for Safer Foundation www.saferfoundation.org IMPORTANT NOTICE All proposal question and inquiries must be sent by email to
Request for Proposals (RFP) Managed Services, Help Desk and Engineering Support for Safer Foundation www.saferfoundation.org IMPORTANT NOTICE All proposal question and inquiries must be sent by email to
Personal Online Banking & Bill Pay. Guide to Getting Started
 Personal Online Banking & Bill Pay Guide to Getting Started What s Inside Contents Security at Vectra Bank... 4 Getting Started Online... 5 Welcome to Vectra Bank Online Banking. Whether you re at home,
Personal Online Banking & Bill Pay Guide to Getting Started What s Inside Contents Security at Vectra Bank... 4 Getting Started Online... 5 Welcome to Vectra Bank Online Banking. Whether you re at home,
Step-by-Step Configuration
 Step-by-Step Configuration Kerio Technologies Kerio Technologies. All Rights Reserved. Printing Date: August 15, 2007 This guide provides detailed description on configuration of the local network which
Step-by-Step Configuration Kerio Technologies Kerio Technologies. All Rights Reserved. Printing Date: August 15, 2007 This guide provides detailed description on configuration of the local network which
Accessing the SUNYIT wireless network for the first time
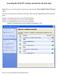 Accessing the SUNYIT wireless network for the first time Right click on your wireless network connection icon and select the View Available Wireless Networks option You may see several networks within
Accessing the SUNYIT wireless network for the first time Right click on your wireless network connection icon and select the View Available Wireless Networks option You may see several networks within
Information Security
 IT Orientation at Penn Information Security October 21, 2015 Joshua Beeman University Information Security Officer jbeeman@isc.upenn.edu (215) 746-7077 www.upenn.edu/computing/security security@isc.upenn.edu
IT Orientation at Penn Information Security October 21, 2015 Joshua Beeman University Information Security Officer jbeeman@isc.upenn.edu (215) 746-7077 www.upenn.edu/computing/security security@isc.upenn.edu
Ancero Hosted Virtual Server (HVS) and Hosted Virtual Desktop (HVD) Service Guide
 Ancero Hosted Virtual Server (HVS) and Hosted Virtual Desktop (HVD) Service Guide Table of Contents 1. DEFINITIONS... 3 2. SCOPE OF SERVICES... 3 3.1 HVD... 4 3.2 WEBHVD... 4 3.3 HVS... 4 3.4 STORAGE D3...
Ancero Hosted Virtual Server (HVS) and Hosted Virtual Desktop (HVD) Service Guide Table of Contents 1. DEFINITIONS... 3 2. SCOPE OF SERVICES... 3 3.1 HVD... 4 3.2 WEBHVD... 4 3.3 HVS... 4 3.4 STORAGE D3...
Lytecube Technologies. EnCircle Automation. User Guide
 Lytecube Technologies EnCircle Automation User Guide Lytecube Technologies 1/1/2009 Contents Installation... 3 Using Encircle... 3 Launching EnCircle as a desktop application... 3 Logon Screen... 3 EnCircle
Lytecube Technologies EnCircle Automation User Guide Lytecube Technologies 1/1/2009 Contents Installation... 3 Using Encircle... 3 Launching EnCircle as a desktop application... 3 Logon Screen... 3 EnCircle
Solution Brief: Enterprise Security
 Symantec Brightmail Gateway and VMware Solution Brief: Enterprise Security Symantec Brightmail Gateway and VMware Contents Corporate overview......................................................................................
Symantec Brightmail Gateway and VMware Solution Brief: Enterprise Security Symantec Brightmail Gateway and VMware Contents Corporate overview......................................................................................
10 Tips to Better Manage Your Service Team
 10 Tips to Better Manage Your Service Team Service Management Recurring Services Solution Development & Mgmt Marketing & Sales Project Services Service Desk Field Services Managed Services Service Desk
10 Tips to Better Manage Your Service Team Service Management Recurring Services Solution Development & Mgmt Marketing & Sales Project Services Service Desk Field Services Managed Services Service Desk
Best Practices for Information Security
 Best Practices for Information Security Suzanne Dmytrenko, Information Privacy Officer Email: suzanne@sfsu.edu. Ph: 415-338-2823 Mig Hofmann, Information Security Officer Email: mig@sfsu.edu. Ph: 415-338-3018
Best Practices for Information Security Suzanne Dmytrenko, Information Privacy Officer Email: suzanne@sfsu.edu. Ph: 415-338-2823 Mig Hofmann, Information Security Officer Email: mig@sfsu.edu. Ph: 415-338-3018
Sage Intelligence Support Desk
 Sage Intelligence Support Desk Service Level Agreement Phillippa Dekker 30 11 2015 Table of Contents 1.0 Overview 3 2.0 Services Provided 4 3.0 Services Not Provided 5 3.1 Database Issues 5 3.2 Excel and
Sage Intelligence Support Desk Service Level Agreement Phillippa Dekker 30 11 2015 Table of Contents 1.0 Overview 3 2.0 Services Provided 4 3.0 Services Not Provided 5 3.1 Database Issues 5 3.2 Excel and
Call us today 1300 724 599. Managed IT Services. Proactive, flexible and affordable
 Call us today 1300 724 599 Managed IT Services Proactive, flexible and affordable We believe technology is at its best when it s invisible. When you can focus on the task you are achieving, not the technology
Call us today 1300 724 599 Managed IT Services Proactive, flexible and affordable We believe technology is at its best when it s invisible. When you can focus on the task you are achieving, not the technology
Monthly Performance Metrics April 2015 Compliance Level Legend
 April 2015 April 2015 Department of Technology Monthly Performance Metrics April 2015 Compliance Level Legend In Compliance Out of Compliance Within Tolerance Insufficient Data Target Actual Compliance
April 2015 April 2015 Department of Technology Monthly Performance Metrics April 2015 Compliance Level Legend In Compliance Out of Compliance Within Tolerance Insufficient Data Target Actual Compliance
INSTALLATION AND CONFIGURATION GUIDE (THIS DOCUMENT RELATES TO MDAEMON v9.5.0 ONWARDS)
 Web: Overview INSTALLATION AND CONFIGURATION GUIDE (THIS DOCUMENT RELATES TO MDAEMON v9.5.0 ONWARDS) This document is designed to provide a quick installation and configuration guide for MDaemon along
Web: Overview INSTALLATION AND CONFIGURATION GUIDE (THIS DOCUMENT RELATES TO MDAEMON v9.5.0 ONWARDS) This document is designed to provide a quick installation and configuration guide for MDaemon along
Attachment E. RFP Requirements: Mandatory Requirements: Vendor must respond with Yes or No. A No response will render the vendor nonresponsive.
 Attachment E RFP Requirements: Mandatory Requirements: Vendor must respond with Yes or No. A No response will render the vendor nonresponsive. Questions Support for Information Security 1. The Supplier
Attachment E RFP Requirements: Mandatory Requirements: Vendor must respond with Yes or No. A No response will render the vendor nonresponsive. Questions Support for Information Security 1. The Supplier
Infrastructure Support Engineer Job Profile
 Infrastructure Support Engineer Job Profile About the HCPC The Health Professions and Care Council (HCPC) is the regulator of 16 different health and care professions, set up to protect the public. To
Infrastructure Support Engineer Job Profile About the HCPC The Health Professions and Care Council (HCPC) is the regulator of 16 different health and care professions, set up to protect the public. To
secureheller Addressing Information Security at Heller
 Addressing Information Security at Heller October 16, 2013 Welcome to the, the program focused on addressing Heller s information security. Security Awareness Data Protection Tools Simplified Usability
Addressing Information Security at Heller October 16, 2013 Welcome to the, the program focused on addressing Heller s information security. Security Awareness Data Protection Tools Simplified Usability
ManageEngine Desktop Central Training
 ManageEngine Desktop Central Training Course Objectives Who Should Attend Course Agenda Course Objectives Desktop Central training helps you IT staff learn the features offered by Desktop Central and to
ManageEngine Desktop Central Training Course Objectives Who Should Attend Course Agenda Course Objectives Desktop Central training helps you IT staff learn the features offered by Desktop Central and to
Business Online Banking & Bill Pay Guide to Getting Started
 Business Online Banking & Bill Pay Guide to Getting Started What s Inside Contents Security at Vectra Bank... 4 Getting Started Online... 5 Welcome to Vectra Bank Business Online Banking. Whether you re
Business Online Banking & Bill Pay Guide to Getting Started What s Inside Contents Security at Vectra Bank... 4 Getting Started Online... 5 Welcome to Vectra Bank Business Online Banking. Whether you re
Sentinel Platform/Managed IT Services Agreement Page 1 of 6. 1. Term of Agreement
 Page 1 of 6 1. Term of Agreement This Agreement between, herein referred to as Client, and Word of Mouth Computers and Electronics, LLC hereinafter referred to as Service Provider, is effective on the
Page 1 of 6 1. Term of Agreement This Agreement between, herein referred to as Client, and Word of Mouth Computers and Electronics, LLC hereinafter referred to as Service Provider, is effective on the
Mission Continuity Program Elements of the BETH3 Model: Loss of Technology
 Mission Continuity Program Elements of the BETH3 Model: Loss of Technology Anita Gelburd, Project Manager March 12, 2014 3/12/2014 Loss of Technology Presentation 2 Purpose of today s presentation Review:
Mission Continuity Program Elements of the BETH3 Model: Loss of Technology Anita Gelburd, Project Manager March 12, 2014 3/12/2014 Loss of Technology Presentation 2 Purpose of today s presentation Review:
Who do I contact if I have issues with Concur Travel? The following support options are available to travelers regarding Concur Travel.
 Concur Travel Frequently Asked Questions What is Concur Travel? Concur Travel is an innovative interactive travel booking system used by company employees to make their own travel arrangements. The system
Concur Travel Frequently Asked Questions What is Concur Travel? Concur Travel is an innovative interactive travel booking system used by company employees to make their own travel arrangements. The system
IT Help Desk Management Survey Questionnaire January 2007
 IT Help Desk Management Survey Questionnaire January 2007 Thank you for participating in the IT Help Desk Management study being conducted by the EDUCAUSE Center for Applied Research, or ECAR. This survey
IT Help Desk Management Survey Questionnaire January 2007 Thank you for participating in the IT Help Desk Management study being conducted by the EDUCAUSE Center for Applied Research, or ECAR. This survey
Support Common Questions
 Support Common Questions 1. How will my data get to BCNS Technologies? One of our technical representatives will call your office and we will schedule an appointment with you to retrieve your application
Support Common Questions 1. How will my data get to BCNS Technologies? One of our technical representatives will call your office and we will schedule an appointment with you to retrieve your application
Web Hosting Getting Started Guide
 Web Hosting Getting Started Guide This guide describes: - Hosting Terms and Definitions - How to sync a domain with your hosting account - How to change your domain s nameservers - How to use FTP to upload
Web Hosting Getting Started Guide This guide describes: - Hosting Terms and Definitions - How to sync a domain with your hosting account - How to change your domain s nameservers - How to use FTP to upload
PREMIER SUPPORT STANDARD SERVICES BRONZE SILVER GOLD
 SERVICE SUMMARY ITonDemand provides four levels of service to choose from to meet our clients range of needs. Plans can also be customized according to more specific environment needs. PREMIER SUPPORT
SERVICE SUMMARY ITonDemand provides four levels of service to choose from to meet our clients range of needs. Plans can also be customized according to more specific environment needs. PREMIER SUPPORT
MCSA/MCITP: Enterprise Windows Server 2008 Course 9952; 14 Days, Instructor-led
 MCSA/MCITP: Enterprise Windows Server 2008 Course 9952; 14 Days, Instructor-led Course Description Whether you are looking to learn new technology, gain Server 2008 certification, or simply improve your
MCSA/MCITP: Enterprise Windows Server 2008 Course 9952; 14 Days, Instructor-led Course Description Whether you are looking to learn new technology, gain Server 2008 certification, or simply improve your
State of Wisconsin Initial Incident Triage Service Service Offering Definition (SOD)
 State of Wisconsin Initial Incident Triage Service Service Offering Definition (SOD) Document Revision History Date Version Creator Notes 3/2/2011 1.4.1 Sandie Schultz Service tier information updated
State of Wisconsin Initial Incident Triage Service Service Offering Definition (SOD) Document Revision History Date Version Creator Notes 3/2/2011 1.4.1 Sandie Schultz Service tier information updated
ATTERCOPIA MANAGED HOSTING & DOMAIN SERVICES TERMS & CONDITIONS
 ATTERCOPIA MANAGED HOSTING & DOMAIN SERVICES TERMS & CONDITIONS Version: 2016 edition 2016 Attercopia 1 Hosting We provide a fully managed hosting solution. Our hosting partners provide servers which are
ATTERCOPIA MANAGED HOSTING & DOMAIN SERVICES TERMS & CONDITIONS Version: 2016 edition 2016 Attercopia 1 Hosting We provide a fully managed hosting solution. Our hosting partners provide servers which are
Portal Administration. Administrator Guide
 Portal Administration Administrator Guide Portal Administration Guide Documentation version: 1.0 Legal Notice Legal Notice Copyright 2013 Symantec Corporation. All rights reserved. Symantec, the Symantec
Portal Administration Administrator Guide Portal Administration Guide Documentation version: 1.0 Legal Notice Legal Notice Copyright 2013 Symantec Corporation. All rights reserved. Symantec, the Symantec
Configuring a Domain to work with your Server
 Configuring a Domain to work with your Server If you have a domain name registered with a third party and would like to use that domain with your Tagadab server (Virtual or Dedicated) then you have several
Configuring a Domain to work with your Server If you have a domain name registered with a third party and would like to use that domain with your Tagadab server (Virtual or Dedicated) then you have several
AllianceIT Managed Services
 AllianceIT Managed Services confidence predictability productivity focus Uncertainty is a business killer. To be successful, companies have to know that their critical IT systems will be available on demand
AllianceIT Managed Services confidence predictability productivity focus Uncertainty is a business killer. To be successful, companies have to know that their critical IT systems will be available on demand
SCOPE: Role Descriptions/Job Profiles
 SCOPE: Role Descriptions/Job Profiles a) Computing Infrastructure 1. Exchange Administrator Assists with ensuring the availability of email servers and applications, configuring new implementations, and
SCOPE: Role Descriptions/Job Profiles a) Computing Infrastructure 1. Exchange Administrator Assists with ensuring the availability of email servers and applications, configuring new implementations, and
Supplier Security Assessment Questionnaire
 HALKYN CONSULTING LTD Supplier Security Assessment Questionnaire Security Self-Assessment and Reporting This questionnaire is provided to assist organisations in conducting supplier security assessments.
HALKYN CONSULTING LTD Supplier Security Assessment Questionnaire Security Self-Assessment and Reporting This questionnaire is provided to assist organisations in conducting supplier security assessments.
Outsource or In-House?
 Article Outsource or In-House? Does it make sense to outsource your IT? There s no single right answer to this question. A great deal depends on the following: 1. Can your in-house team do the job well?
Article Outsource or In-House? Does it make sense to outsource your IT? There s no single right answer to this question. A great deal depends on the following: 1. Can your in-house team do the job well?
Computing Services Helpdesk
 s e r v i c e l e v e l a g r e e m e n t Computing Services Helpdesk This document contains an agreement between the Computing Services (CS) Helpdesk and the Faculty, Staff, and Students (FSS, or Ross
s e r v i c e l e v e l a g r e e m e n t Computing Services Helpdesk This document contains an agreement between the Computing Services (CS) Helpdesk and the Faculty, Staff, and Students (FSS, or Ross
Fully Managed IT Support. Proactive Maintenance. Disaster Recovery. Remote Support. Service Desk. Call Centre. Fully Managed Services Guide July 2007
 Fully Managed IT Support Proactive Maintenance Disaster Recovery Remote Support Service Desk Call Centre London Office ITVET Limited 2 nd Floor 145 157 St John Street London EC1V 4PY t: +44(0)8704 232
Fully Managed IT Support Proactive Maintenance Disaster Recovery Remote Support Service Desk Call Centre London Office ITVET Limited 2 nd Floor 145 157 St John Street London EC1V 4PY t: +44(0)8704 232
MCSA Objectives. Exam 70-236: TS:Exchange Server 2007, Configuring
 MCSA Objectives Exam 70-236: TS:Exchange Server 2007, Configuring Installing and Configuring Microsoft Exchange Servers Prepare the infrastructure for Exchange installation. Prepare the servers for Exchange
MCSA Objectives Exam 70-236: TS:Exchange Server 2007, Configuring Installing and Configuring Microsoft Exchange Servers Prepare the infrastructure for Exchange installation. Prepare the servers for Exchange
F-Secure Messaging Security Gateway. Deployment Guide
 F-Secure Messaging Security Gateway Deployment Guide TOC F-Secure Messaging Security Gateway Contents Chapter 1: Deploying F-Secure Messaging Security Gateway...3 1.1 The typical product deployment model...4
F-Secure Messaging Security Gateway Deployment Guide TOC F-Secure Messaging Security Gateway Contents Chapter 1: Deploying F-Secure Messaging Security Gateway...3 1.1 The typical product deployment model...4
Course: Information Security Management in e-governance. Day 1. Session 5: Securing Data and Operating systems
 Course: Information Security Management in e-governance Day 1 Session 5: Securing Data and Operating systems Agenda Introduction to information, data and database systems Information security risks surrounding
Course: Information Security Management in e-governance Day 1 Session 5: Securing Data and Operating systems Agenda Introduction to information, data and database systems Information security risks surrounding
Create a New Account Contents
 Create a New Account Contents Goals...2 Create a New Domain Account...2 Domain Information...3 Package...4 Settings...5 Reseller Settings...6 DNS Settings...6 Mail Routing Settings...7 Conclusion...7 1
Create a New Account Contents Goals...2 Create a New Domain Account...2 Domain Information...3 Package...4 Settings...5 Reseller Settings...6 DNS Settings...6 Mail Routing Settings...7 Conclusion...7 1
Ancero Managed Internet Service (MIS) & Private Network Transport (PNT) Service Guide
 Ancero Managed Internet Service (MIS) & Private Network Transport (PNT) Service Guide Contents Service Overview... 3 Managed Internet Service (MIS): Dedicated Access that Keeps You Connected... 3 Reliable,
Ancero Managed Internet Service (MIS) & Private Network Transport (PNT) Service Guide Contents Service Overview... 3 Managed Internet Service (MIS): Dedicated Access that Keeps You Connected... 3 Reliable,
Prepared by: OIC OF SOUTH FLORIDA. May 2013
 OIC OF SOUTH FLORIDA REQUEST FOR PROPOSAL INFORMATION TECHNOLOGY SUPPORT SERVICES Proposals will be received by OIC of South Florida for Information Technology Support Services. Interested vendors should
OIC OF SOUTH FLORIDA REQUEST FOR PROPOSAL INFORMATION TECHNOLOGY SUPPORT SERVICES Proposals will be received by OIC of South Florida for Information Technology Support Services. Interested vendors should
Connecting to securevirtual Workspace
 Connecting to securevirtual Workspace The following document provides information on connecting to securevirtual Workspace. This Document includes: Connecting Using Remote Desktop Connection (RDC) Connecting
Connecting to securevirtual Workspace The following document provides information on connecting to securevirtual Workspace. This Document includes: Connecting Using Remote Desktop Connection (RDC) Connecting
extranet.airproducts.com Windows XP Client Configuration
 extranet.airproducts.com Windows XP Client Configuration To successfully connect to the Air Products extranet.airproducts.com website and have full functionality, the client computer needs to have the
extranet.airproducts.com Windows XP Client Configuration To successfully connect to the Air Products extranet.airproducts.com website and have full functionality, the client computer needs to have the
Replication with TeraStation 3000/4000/5000/7000. Buffalo Technology
 Replication with TeraStation 3000/4000/5000/7000 Buffalo Technology Introduction Replication is synchronising a folder on two separate TeraStations in almost real time. It works in only one way not bi-directional,
Replication with TeraStation 3000/4000/5000/7000 Buffalo Technology Introduction Replication is synchronising a folder on two separate TeraStations in almost real time. It works in only one way not bi-directional,
Help Desk Structure Policy
 Chan & Naylor Australia Help Desk Structure Policy Support Resolution Process Chan & Naylor Australia Head Office Suite 4, 55 Grandview St PYMBLE NSW 2073 P. 02 9391 5000 F. 02 9391 5050 Distribution Establishment
Chan & Naylor Australia Help Desk Structure Policy Support Resolution Process Chan & Naylor Australia Head Office Suite 4, 55 Grandview St PYMBLE NSW 2073 P. 02 9391 5000 F. 02 9391 5050 Distribution Establishment
www.datatechhosting.com
 Hosting and Cloud Services Customer Service Level Agreement (SLA) Welcome to the Clustered Cloud Hosted Services Community. We are happy to have you aboard and look forward to assisting you with all your
Hosting and Cloud Services Customer Service Level Agreement (SLA) Welcome to the Clustered Cloud Hosted Services Community. We are happy to have you aboard and look forward to assisting you with all your
AIR FORCE ASSOCIATION S CYBERPATRIOT NATIONAL YOUTH CYBER EDUCATION PROGRAM UNIT FIVE. Microsoft Windows Security. www.uscyberpatriot.
 AIR FORCE ASSOCIATION S CYBERPATRIOT NATIONAL YOUTH CYBER EDUCATION PROGRAM UNIT FIVE Microsoft Windows Security www.uscyberpatriot.org AIR FORCE ASSOCIATION S CYBERPATRIOT NATIONAL YOUTH CYBER EDUCATION
AIR FORCE ASSOCIATION S CYBERPATRIOT NATIONAL YOUTH CYBER EDUCATION PROGRAM UNIT FIVE Microsoft Windows Security www.uscyberpatriot.org AIR FORCE ASSOCIATION S CYBERPATRIOT NATIONAL YOUTH CYBER EDUCATION
APPENDIX A WORK PROCESS SCHEDULE AND RELATED INSTRUCTION OUTLINE. Computer Support Specialist (Existing Title: Help Desk Technician) 15-1151.
 APPENDIX A WORK PROCESS SCHEDULE AND RELATED INSTRUCTION OUTLINE TITLE O*NET-SOC CODE RAPIDS CODE Computer Support Specialist (Existing Title: Help Desk Technician) 15-1151.00 111HY Network and Computer
APPENDIX A WORK PROCESS SCHEDULE AND RELATED INSTRUCTION OUTLINE TITLE O*NET-SOC CODE RAPIDS CODE Computer Support Specialist (Existing Title: Help Desk Technician) 15-1151.00 111HY Network and Computer
ICT HELPDESK PROCEDURES
 ICT HELPDESK PROCEDURES General Overview This section provides generalized details of the Help Desk, and ICT staff responsibilities. Help Desk: A help desk is an information and assistance resource that
ICT HELPDESK PROCEDURES General Overview This section provides generalized details of the Help Desk, and ICT staff responsibilities. Help Desk: A help desk is an information and assistance resource that
my.airproducts.com Windows Vista Client Configuration
 my.airproducts.com Windows Vista Client Configuration To successfully connect to the Air Products my.airproducts.com website, the client computer needs to have the following three pieces of software installed
my.airproducts.com Windows Vista Client Configuration To successfully connect to the Air Products my.airproducts.com website, the client computer needs to have the following three pieces of software installed
Solution Requirements and Process Flow
 CHAPTER 2 Scope The Cisco Virtual Expert Management solution is a powerful, flexible communication solution that addresses a variety of technical, business, and associated service preferences. Deployment
CHAPTER 2 Scope The Cisco Virtual Expert Management solution is a powerful, flexible communication solution that addresses a variety of technical, business, and associated service preferences. Deployment
Service Level Agreement and Management By: Harris Kern s Enterprise Computing Institute
 Service Level Agreement and Management By: Harris Kern s Enterprise Computing Institute Service Level Management Service Level Management deals with how user service requirements are understood and managed.
Service Level Agreement and Management By: Harris Kern s Enterprise Computing Institute Service Level Management Service Level Management deals with how user service requirements are understood and managed.
OCR LEVEL 3 CAMBRIDGE TECHNICAL
 Cambridge TECHNICALS OCR LEVEL 3 CAMBRIDGE TECHNICAL CERTIFICATE/DIPLOMA IN IT NETWORKED SYSTEMS SECURITY J/601/7332 LEVEL 3 UNIT 28 GUIDED LEARNING HOURS: 60 UNIT CREDIT VALUE: 10 NETWORKED SYSTEMS SECURITY
Cambridge TECHNICALS OCR LEVEL 3 CAMBRIDGE TECHNICAL CERTIFICATE/DIPLOMA IN IT NETWORKED SYSTEMS SECURITY J/601/7332 LEVEL 3 UNIT 28 GUIDED LEARNING HOURS: 60 UNIT CREDIT VALUE: 10 NETWORKED SYSTEMS SECURITY
T141 Computer Systems Technician MTCU Code 50505 Program Learning Outcomes
 T141 Computer Systems Technician MTCU Code 50505 Program Learning Outcomes Synopsis of the Vocational Learning Outcomes * The graduate has reliably demonstrated the ability to 1. analyze and resolve information
T141 Computer Systems Technician MTCU Code 50505 Program Learning Outcomes Synopsis of the Vocational Learning Outcomes * The graduate has reliably demonstrated the ability to 1. analyze and resolve information
RDPLUS. FAQs. Thank you for choosing RDPlus as the Remote Desktop Technology solution for your Business.
 RDPLUS FAQs Thank you for choosing RDPlus as the Remote Desktop Technology solution for your Business. This product is supplied and supported in Australia by Intersoft Computing Pty Ltd. For questions
RDPLUS FAQs Thank you for choosing RDPlus as the Remote Desktop Technology solution for your Business. This product is supplied and supported in Australia by Intersoft Computing Pty Ltd. For questions
COMPLETE NETWORK Management, Inc.
 - www.completenetwork.com - Cost Effective Technology Management Professional Services If your business relies on technology to deliver efficient and cost-effective goods and services to your clients,
- www.completenetwork.com - Cost Effective Technology Management Professional Services If your business relies on technology to deliver efficient and cost-effective goods and services to your clients,
Intel Security Certified Product Specialist Security Information Event Management (SIEM)
 Intel Security Certified Product Specialist Security Information Event Management (SIEM) Why Get Intel Security Certified? As technology and security threats continue to evolve, organizations are looking
Intel Security Certified Product Specialist Security Information Event Management (SIEM) Why Get Intel Security Certified? As technology and security threats continue to evolve, organizations are looking
